同态密码方案在电子投票系统中的应用(IJCNIS-V10-N1-6)

I. J. Computer Network and Information Security, 2018, 1, 44-59
Published Online January 2018 in MECS (https://www.360docs.net/doc/7a1338920.html,/)
DOI: 10.5815/ijcnis.2018.01.06
Using Homomorphic Cryptographic Solutions on
E-voting Systems
Ahmed A. Abu Aziz
Department of Computer Engineering Faculty of Engineering Islamic University of Gaza, Gaza Strip, Palestine
E-mail: a.abuaziz@https://www.360docs.net/doc/7a1338920.html,
Hasan N.Qunoo
Department of Software Engineering Faculty of Applied Engineering University of Palestine, Gaza Strip, Palestine
E-mail: hassanq@https://www.360docs.net/doc/7a1338920.html,
Aiman A. Abu Samra
Department of Computer Engineering Faculty of Engineering Islamic University of Gaza, Gaza Strip, Palestine
E-mail: aasamra@https://www.360docs.net/doc/7a1338920.html,.ps
Received: 12 August 2017; Accepted: 22 September 2017; Published: 08 January 2018
Abstract—Homomorphic Cryptography raised as a new solution used in electronic voting systems. In this research, Fully Homomorphic encryption used to design and implement an e-voting system. The purpose of the study is to examine the applicability of Fully Homomorphic encryption in real systems and to evaluate the performance of fully homomorphic encryption in e-voting systems. Most of homomorphic cryptography e-voting systems based on additive or multiplicative homomorphic encryption. In this research, fully homomorphic encryption used to provide both operations additive and multiplication, which ease the demonstration of none interactive zero-knowledge proof NIZKP. The proposed e-voting system achieved most of the important security issues of the internet-voting systems such as eligibility, privacy, accuracy, verifiability, fairness, and others. One of the most important properties of the implemented internet voting system its applicability to work on cloud infrastructure, while preserving its security characteristics. The implementation is done using homomorphic encryption library HELib. Addition and multiplication properties of fully homomorphic encryption were used to verify the correctness of vote structure as a NIZKP, and for calculating the results of the voting process in an encrypted way. The results show that the implemented internet voting system is secure and applicable for a large number of voters up to 10 million voters.
Index Terms—Fully Homomorphic Encryption, FHE, E-voting, Non-Interactive Zero Knowledge Proof, NIZKP.
I.I NTRODUCTION
Voting is a decision making system in modern societies depends on the proper administration of popular elections. In elections, each voter should be confident that his intents were correctly captured and no modification was done to his vote. In addition, all eligible votes were correctly tallied. On the other side, the voting system should ensure that each vote was done in the right way and voter coercion is unlikely. These conflicting requirements present a significant challenge. The changing from the traditional paper based voting methods used in many countries into electronic election systems removes such challenge. The challenge transferred to build secure voting systems that able to run in real life situations and preserve privacy and anonymity for voters. E-voting is an interdisciplinary subject and should be studied from different domains, such as software engineering, cryptography, network security, politics, law, economics and social science. Mostly e-voting is known as a challenging topic in cryptography because of the need to achieve privacy, anonymity and vote encryption. Many e-voting systems based on complicated encryption schemes and other based on mix net model, blind signature model, and homomorphic encryption model. Cryptographic solutions provide methods of storing or transferring data in a secure way, the amount of data generated is growing in a huge manner. So, cloud services are a suitable solution for storing such huge amount of data. Since cloud technologies are one of the most cost-saving and scalable solutions for processing and saving large data. The need to process encrypted data stored in the cloud becomes more insistent. Cryptographic techniques can separate into two general forms, Symmetric, and Asymmetric encryption: In symmetric encryption, a common secret key defined between sender and receiver. The same key is used for encryption E(m,k) and decryption D(c,k) process, where m is the message and c is the generated ciphertext after encryption. The original message could be retrieved after decrypting cipher using the secret key. In asymmetric encryption, private and public keys generated, the user can share his public key to the public, any sender can use
the public key to encrypt a message E(m,pk), then the receiver can decrypt using his private key D(c,sk). All public key cryptography depends on numeric theory and modular operations, this provides a powerful property called homomorphism, and thus preserves group operations performed on ciphertexts, add, multiply or both can be made on two ciphertexts to calculate the result, which will be the same result if this operation performed on plaintext.
Homomorphism property preserves new secure method to perform a group of operations on ciphertexts in untrusted third party without knowledge of any secret information. The ability to perform simple computation on ciphertexts leads to a lot of applications and security protocols, but the complicated structure of homomorphic cryptosystems limits applicability in some protocols that need fast computation. Anyway, it is still applicable to some protocols concern in security. Section II.A and section II.B describes in detail the homomorphic encryption.
The research structured as follow, section II introduce the homographic encryption, then presents a literature review of previous fully homomorphic encryption schemes, properties, underlying principles, and limitations. This section also focuses on e-voting systems and give a brief explanation of the previous voting systems. Section III presents the implemented e-voting system using fully homomorphic encryption, and discuss a designed method of non-interactive zero-knowledge proofs. It also describes the presentation method used and NIZKP. Section IV presents the structure of the implemented voting system and describes the programming properties of each part of the system. Section V presents analysis and results of the implemented voting system, it shows traffic analysis, performance analysis, and stored data analysis. Section VIVI the final section a conclusion and the future developments described.
II. R ELATED W ORKS
This research studies an old problem in cryptography called a privacy homomorphism. It was introduced by Rivest, Adleman and Derto uzous [1] after the invention of RSA, which is a multiplicative homomorphic encryption scheme.
A. Homomorphic Cryptography.
If the RSA public key pk = (N,e), then encryption of message x is given by E (m i )=m i e mod N , then the homomorphism property is ∏E (m i )=(∏m i i )e mod N i in other words:
E (m 1).E (m 2)= m 1e m 2e
mod N = (m 1m 2)e mod
=E (m 1.m 2)
This property led Rives et al [1]. to think about what if we have a schema that is fully homomorphic: a schema ε have an efficient Evaluate ε algorithm that can evaluate any circuit C contains any operation not just
multiplication, for any public key pk, where:
c i =Encryptε(pk,m i ) Gives: (1)
c ? Evaluateε(pk,C,c 1,…,c t ) (2)
Availed encryption of C(m 1,….,m t ) under pk. This can arbitrarily compute on encrypted data, so many applications could be applied using this theory, such as query, calculate and write to data without decryption, any operation could be applied while it could be expressed efficiently as a circuit C .
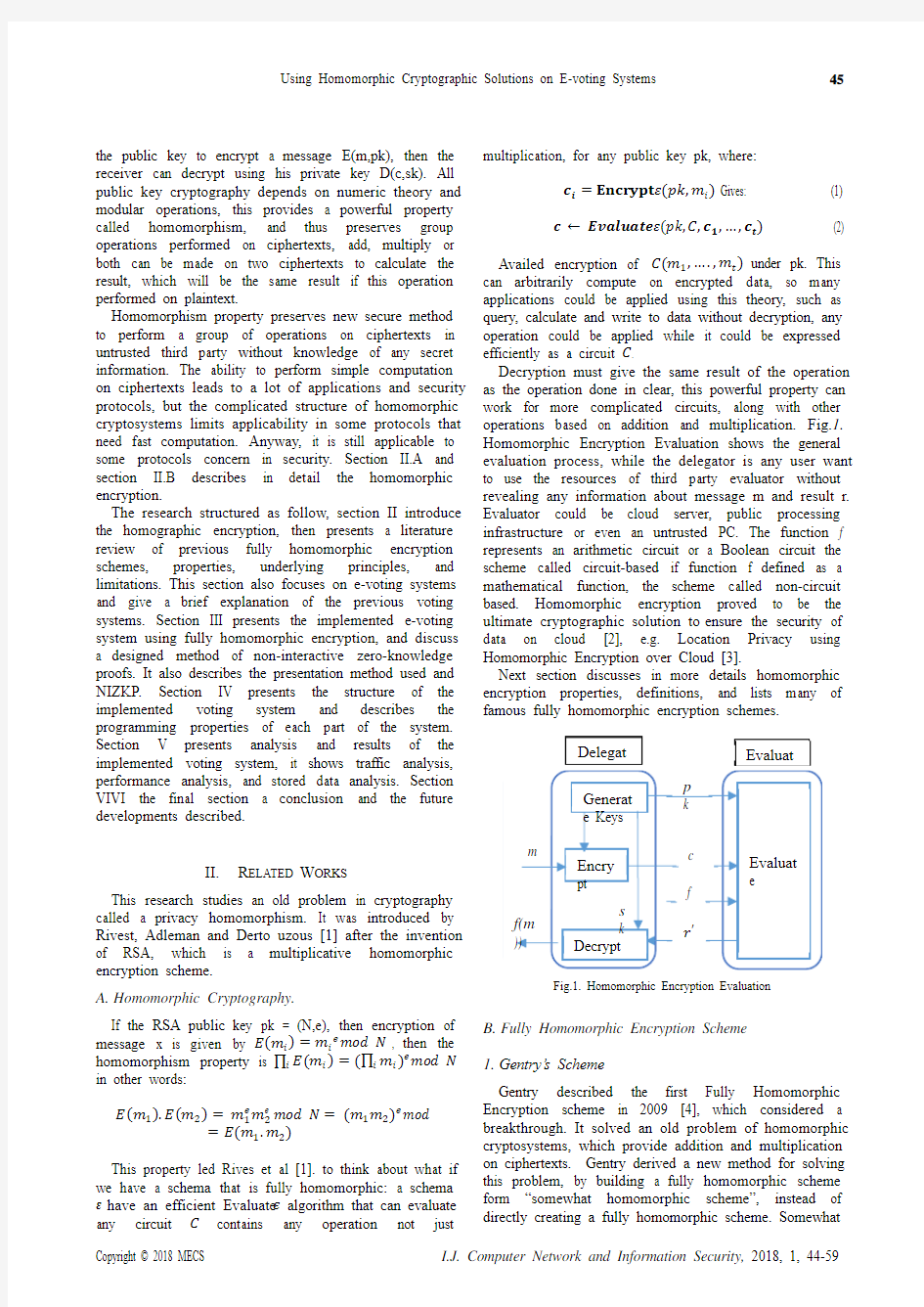
Decryption must give the same result of the operation as the operation done in clear, this powerful property can work for more complicated circuits, along with other operations based on addition and multiplication. Fig.1. Homomorphic Encryption Evaluation shows the general evaluation process, while the delegator is any user want to use the resources of third party evaluator without revealing any information about message m and result r. Evaluator could be cloud server, public processing infrastructure or even an untrusted PC. The function f represents an arithmetic circuit or a Boolean circuit the scheme called circuit-based if function f defined as a mathematical function, the scheme called non-circuit based. Homomorphic encryption proved to be the ultimate cryptographic solution to ensure the security of data on cloud [2], e.g. Location Privacy using Homomorphic Encryption over Cloud [3].
Next section discusses in more details homomorphic encryption properties, definitions, and lists many of famous fully homomorphic encryption schemes.
Fig.1. Homomorphic Encryption Evaluation
B. Fully Homomorphic Encryption Scheme 1. Gentry’s Scheme
Gentry described the first Fully Homomorphic Encryption scheme in 2009 [4], which considered a breakthrough. It solved an old problem of homomorphic cryptosystems, which provide addition and multiplication on ciphertexts. Gentry derived a new method for solving this problem, by building a fully homomorphic scheme form “somewhat homomorphic scheme”, instead of directly creating a fully homomorphic scheme. Somewhat
Delegat Evaluat
Generat e Keys
Encry pt Decrypt
s k f(m ))
Evaluat e
m
p k f r ′
c
schema was only able to evaluate low degree polynomials on the encrypted data, it can perform a limited number of addition and multiplication operations on ciphertexts. Gentry applied a breakthrough idea by evaluating the decryption of polynomial not on the bits of ciphertext and secret key directly as in regular, but he performs it homomorphically on the encryption of those ciphertexts and secret key. Instead of recovering the plaintext, it gets an encryption of bits for ciphertext, but with less noise, if the polynomial degree small enough in the ciphertext and this becomes the ciphertext for the original plaintext. This process called “ciphertext refresh” procedure which makes the refreshed ciphertext applicable for the homomorphic operation (addition or multiplication), while it’s not possible for the original ciphertext due to the noise threshold. Using this procedure, the number of permissible homomorphic operations becomes unlimited and we get a fully homomorphic encryption scheme. Finally, he applied a “bootstrapping” transformation to obtain fully homomorphic scheme. The crucial point in this process is to obtain a scheme that can evaluate polynomials of high-enough degree, and at the same time has decryption procedure that can be expressed as a polynomial of low-enough degree. Once the degree of polynomials that can be evaluated by the scheme exceeds the degree of the decryption polynomial (times two), the scheme is called “bootstrappable” and it can then be converted into a fully homomorphic scheme [5].
2.Implementation of Gentry’s blueprint - Smart-Vercauteren
The first attempt to implement Gentry’s scheme was made in 2010 by Smart and Vercauteren [6], they used a variant based on principal ideal lattices and requiring that the determinant of the lattice be a prime number. Such lattices can be represented implicitly by just two integers (regardless of their dimension), and moreover Smart and Vercauteren described a decryption method where the secret key is represented by a single integer. Smart and Vercauteren were able to implement the underlying somewhat homomorphic scheme, but they could not obtain a bootstrappable scheme or a fully homomorphic scheme.
3.Gentry-Halevi Scheme
Gentry and Halevi described the first implementation of Gentry’s scheme[5]. They follow the same direction as Smart and Vercauteren. They make some optimizations to implement the bootstrapping functionality, which not implemented by Smart and Vercauteren. The main optimization is a key-generation method, for the underlying somewhat homomorphic encryption, that does not require full polynomial inversion. They eliminate the requirement that the determinant is a prime. Additionally, they present many clever optimizations that reduce the asymptotic complexity and practically reducing the time from many hours/days to a few seconds/minutes.
4.Improvements on Gentry’s scheme a) Stehle-Steinfeld optimizations
Stehle and Steinfeld described two improvements [7] on Gentry's fully homomorphic scheme based on ideal lattices and its analysis. They provide a more aggressive analysis of one of the hardness assumptions (the one related to the Sparse Subset Sum Problem) and introduced a probabilistic decryption algorithm that can be implemented with an algebraic circuit of low multiplicative degree. Combined, these improvements lead to a faster fully homomorphic scheme. These improvements also apply to the fully homomorphic schemes of Smart and Vercauteren [6] and van Dijk et al
[8].
b) SIMD Gentry optimization
In [6] Smart and Vercauteren presented a variant of Gentry’s fully homomorphic scheme and mentioned that the scheme could support SIMD style operations. SIMD means simple instruction mutable data. While Gentry’s original schema [4] was just able to perform encryption and decryption on a plaintext of one-bit length.
Gentry and Halevi [5] addressed the slowness of key generation process of the Smart–Vercauteren system [6], but their key generation method excluded the SIMD style operation offered by Smart and Vercauteren.
c) Gentry-Halevi without squashing
Gentry and Halevi describe in [9] a new approach to construct a fully homomorphic scheme encryption without the need to squash process. Previous schemes follow Gentry’s blueprints in first constructing somewhat homomorphic encryption scheme, and next squash the decryption circuit until it is simple enough to be handled within the homomorphic capacity of the somewhat homomorphic encryption scheme. Finally, perform bootstrapping to get fully homomorphic encryption scheme.
d) Gentry-Halevi-Smart scheme
Gentry, Halevi and Smart [10] solved the bottleneck in the bootstrapping process, which need to evaluate homomorphically the reduction of one integer modulo another. This is typically done by emulating a binary modular reduction circuit, using bit operations on the binary representation of integers. Gentry, Halevi and Smart present a simpler approach that bypasses the homomorphic modular-reduction bottleneck to some extent. The method is easier to describe and implement and is likely to be faster in practice. The scheme reduced the size of the public key, and work with SIMD homomorphic computations.
5.DGHV fully homomorphic scheme over the integers DGHV fully homomorphic scheme over the integers described in [8] a fully homomorphic scheme, that constructed from very simple somewhat homomorphic encryption scheme using only elementary modular arithmetic. The somewhat homomorphic scheme merely uses addition and multiplication over the integers rather than working with ideal lattices over a polynomial ring.
The major achievement of DGVH over the original Gentry scheme was that the plaintext consisted of integers rather than single bits leading a better blueprint improve upon [11].
6.DGHV shorter public key
Coron et al, [12] reduced the public key size to o?(λ7) by encrypting with a quadratic form in the public key elements, instead of a linear form. They proved that the scheme remains semantically secure, based on a stronger variant of the approximate-GCD problem, already considered by van Dijk et al.
Coron et al, described also the first implementation of the resulting fully homomorphic scheme. Borrowing some optimizations from the Gentry-Halevi [5] implementation of Gentry’s scheme, obtained roughly the same level of efficiency. This shows that fully homomorphic encryption can be implemented using simple arithmetic operations.
7.Learning With Error LWR- FHE
Gentry’s blueprint suffers from many problems, which first all schemes based on squashing decryption, squashing use “sparse subset sum assumption” in decryption circuit. Also, the large size of keys and ciphertext, the evaluation time per gate, time of encryption and decryption. All these reasons make a bottleneck in practical deployment of FHE.
A new series works address these concerns. Brakerski and Vaikuntanathan [13] show that (leveled) FHE can be based on the hardness of the much more standard “learning with error” (LWE) problem. LEW show that it is hard to solve various short vector problems on arbitrary (not ideal) lattices in the worst case.
8.Brakerski-Gentry-Vaikuntanathan BGV scheme Brakerski, Gentry and Vaikuntanathan in [14] [15] presented a new FHE scheme based on previous work of Brakerski and Vaikuntanathan in [13]. This scheme based on LWE problem and Ring LWE. They constructed a new way of leveled fully homomorphic encryption schemes (capable of evaluating arbitrary polynomial-size circuits), without Gentry’s bootstrapping procedure. Instead of recryption, this new scheme uses other light weighted methods to refresh the ciphertexts to limit the growth of the noise so that the scheme can evaluate much deeper circuits. The recryption process will serve as an optimization to deal with over complicated circuits instead of a necessary for most circuits. The most significant development of BGV compared to [13] is the use of well-known security assumptions based on Ring Learning with Error RLWE, where the introduced RLWE over standard LWE provide a more efficient fully homomorphic scheme. Also, a fully homomorphic encryption without the need for bootstrapping achieved using modulus switching.
9.Gentry-Sahai-Waters scheme
Gentry, Sahai and Waters described in [16] a comparatively simple fully homomorphic encryption (FHE) scheme based on the learning with errors (LWE) problem. In previous LWE-based FHE schemes, multiplication is a complicated and expensive step involving "relinearization". This scheme proposed a new technique for building FHE schemes that called the "approximate eigenvector" method. Homomorphic addition and multiplication considered as just matrix addition and multiplication. This makes the scheme both asymptotically faster and easier to understand.In previous schemes, the homomorphic evaluator needs to obtain the user's "evaluation key", which consists of a chain of encrypted secret keys. This scheme has no evaluation key. The evaluator can do homomorphic operations without knowing the user's public key at all, except for some basic parameters.
10.NTRU based FHE
Lopez-Alt, Tromer and Vaikuntanathan in [17] construct a multikey FHE scheme based on NTRU, a very efficient public-key encryption scheme proposed in the 1990s. It was previously not known how to make NTRU fully homomorphic even for a single party. They viewed the construction of (multikey) FHE from NTRU encryption as the main contribution of independent interest. Although the transformation to a fully homomorphic system deteriorates the efficiency of NTRU somewhat.
C.E-voting Systems
E-voting systems have a large space of research in cryptography literature, which many secure ballot election schemes have been offered, homomorphic encryption raised as one of those solutions for election schemes, which provide security, trust, and scalability. In such scheme, a user simply sends a valid encrypted vote to the server, while the server can compute this vote while it encrypted, this property made election systems more simple and secure [18].
Electronic voting solutions or e-voting systems used by many countries around the world. Internet voting systems used for general elections by countries like Switzerland, Estonia Norway, France, Germany, Spain, Paraguay, Netherlands and the United Kingdom. These countries used special cryptosystems to preserve security for the election process [19] [20]. Electronic voting (e-voting) can be mainly classified into two different systems: machine-based systems and Internet voting (i-voting) systems. Machine-based e-voting means that both casting a vote and tallying the votes are performed using dedicated electronic devices. I-voting is a voting method that transmits casted votes via the public Internet. Development of i-voting systems has been attractive for many researchers and developers because it uses the widespread of mobiles, smartphones and personal computers. Providers can construct secure systems with new technologies like cloud via the public internet. I-voting systems still have many security and privacy concerns and there is a lot of research in this field. Counting process in i-voting systems can classified into three main methods, mix-nets model, blind signature
model, and homomorphic model.
D.I-voting Systems Models
Mix-nets model:In the mix-nets a several linked servers called mixes, each mix randomizes input messages and outputs the permutation of them, such that the input and output messages are not linkable to each other, it provides anonymity for a group of voters. Several schemes based on mix-nets are proposed in [21] [22].
The blind signatures model:In blind signature schemes, the voter first obtains a token, which is a message blindly signed by the administrator or the authority and known only to the voter himself. Later the voter sends his vote anonymously, with this token as proof of eligibility. Even if later the (un-blinded) signature is made public, it is impossible to connect the signature to the signing process, i.e. to the voter. Schemes based on blind signatures usually use anonymous channels in order to send the un-blinded signature and the encryption of the ballot to a voting authority, assuring the anonymity of the sender [23] [24] [25].
Homomorphic Model:In the homomorphic model, the tally process depends on encryption of a vote using homomorphic encryption scheme, where add or multiplication process performs homomorphically on encrypted votes to get the results. The voter needs to make proof of his valid vote; this proof must be zero-knowledge proof. Schemes based on homomorphic encryptions possess the property of verifiability while preserving privacy. As shown earlier in section A the property of homomorphism is performed on addition and multiplication (⊕,?) which also described in section 2.0. Many homomorphic voting systems derived from the theory of ElGamal cryptosystem [26], which is additive homomorphic. Another voting systems based on multiplicative homomorphic Paillier cryptosystem [27] are proposed in [28] [29]. All these systems support only additive or multiplicative homomorphism only.
[30] uses the mobile application based systems with Smart Card based E-Governance System that allows the use of a mobile application to input user identification number using the Multipurpose Electronic Card (MEC) based E-Governance system. In case of successful authentication, the voter allowed to caste the original vote.
E.Zero-Knowledge Proofs
Zero-knowledge proofs could be used to demonstrate the truth of a statement without revealing anything else. Which one party (the prover P) can prove to another party (the verifier V) that a given statement is true, without conveying any information apart from the fact that the statement is indeed true. In ZKP, the prover proves that he/she knows a secret without revealing it [31]. This statement assumed as a secret, the interactions are designed that they cannot lead to revealing or guessing the secret. After exchanging messages, the verifier only knows that the prover does or does not have the secret, nothing more. The result is a yes/no situation, just a single bit of information.
Zero-knowledge proofs need interactive communication between Prover and Verifier, where input from Verifier needed. The prover must respond with usually in the form of a challenge or challenges such that the responses from the prover will convince the verifier if and only if the statement is true. This type called Interactive Zero-knowledge proofs.
A zero-knowledge proof must satisfy three properties: Completeness: The prover can convince the verifier if the prover knows a witness testifying to the truth of the statement.
Soundness: A malicious prover cannot convince anybody if the statement is false, except with some small probability.
Zero-knowledge: A malicious verifier learns nothing except that the statement is true. This is formalized by showing that every cheating verifier has some simulator that, given only the statement to be proved (and no access to the prover), can produce a transcript that "looks like" an interaction between the honest prover and the cheating verifier [32].
F.Non-Interactive Zero-knowledge Proofs
Non-interactive zero-knowledge (NIZK) proof systems [33] yield proofs that can convince others about the truth of a statement without revealing anything but this truth. It has been shown under standard cryptographic assumptions that NIZK proofs of membership exist for all languages in NP. NIZKP does not need the interactive communications between the prover and verifier
Gentry [4] proposed a fully homomorphic encryption scheme and demonstrated that fully homomorphic encryption can be used to construct NIZK proofs whose size depends only on the size of the witness and on the security parameter, but not on the size of the circuit used to verify the witness. Gentry proposed to encrypt every bit of the witness using a fully homomorphic encryption scheme. Using the operations of the fully homomorphic encryption scheme, it is possible to evaluate the circuit on the plaintext to get a ciphertext that contains the output. Using an NIZK proof the prover then constructs a proof for the public key being valid, the encrypted inputs being valid ciphertexts and the output ciphertext being an encryption of 1 [34].
G.Homomorphic Encryption Library HELib
HElib is a software library that implements homomorphic encryption (HE). Available as an implementation of the Brakerski-Gentry-Vaikuntanathan (BGV) scheme [14], along with many optimizations to run homomorphic evaluation runs faster, focusing mostly on the effective use of the Smart-Vercauteren [35] ciphertext packing techniques and the Gentry-Halevi-Smart [36] optimizations.
At its present state, it is fairly low-level provides low-level routines (set, add, multiply, shift, etc.). This library is written in C++ and uses the NTL mathematical library (version 6.1.0 or higher). It is distributed under the terms of the GNU General Public License (GPL) [37]. Shai
Halevi and Victor Shoup developed this [38].
III. T HE P ROPOSED E-VOTING S YSTEM
The proposed E-voting system based on cloud services as an infrastructure for components of the system, the cloud provides high performance-processing capabilities and can deal with huge numbers of communications done by the voter that they want to make voting in a short period.
Cloud considered as untrusted platform for such sensitive process, but homomorphic encryption solves some of the security issues related to tallying and proving votes, which need the biggest part of processing, we needed a part of our system to secure for containing private keys and voter identification informations. Our system consists of:
Authentication Server (AS): responsible for authentication, verifying the correctness of the vote, and valid encrypted with the public key.
Voting Server (VS): responsible for masking the vote and tallying.
Bulletin Board (BB): responsible for displaying the checksum of the vote for public and other public.
A. Stages of the voting system
Registration : Voter need to have Identification information to be able to access and authenticated by the system, he needs to make registration process personally to have his secret key, which is required with other information like his national ID number , and this information provided by authority office and delivered using the secure method. Authentication : When the voting process starts, the voter needs to connect to the Authentication Server to authenticate his identity using his international ID number and secret key. This connection to server done via SSL protocol to preserve privacy, authenticity, and verifiability. Once the voter authenticated, a new Random Secret Key (RSK) generated in AS, this new RSK encrypted with AS secret key E sk (RSK). The resulted cipher sent to both Voter and Voting Server. V and VS can reveal RSK by decrypting the received cipher using Public Key of Authentication Server RSK =D pk (E sk (RSK)).
Another method to do that, once a voter authenticated, a new Random Secret Key (RSK) generated in AS, this new RSK encrypted with voter password and sent him. Also, RSK encrypted with a predefined key between VS and AS, then sent to VS.
User allowed to communicate with the Voting server using the random secret key generated by AS to be authentication secret of a session between voter and VS. The User can send Hello message to VS with encrypting M using RSK, E RSK (M) and using Hash-based message authentication code HMAC [39], which used to verify both the data integrity and the authentication of a message. VS also can send response message using the same way. The HMAC will be used for the rest of communications with RSK as the secret key.
To prevent an attacker from identifying any unencrypted messages sent between VS, AS and V, a symmetric encryption used with salting communication messages to prevent cipher duplication. The key for the symmetric encryption is the RSK generated from AS, then HMAC used along with encrypted messages. Fig.2. Voter Authentication with Authentication Server & Voting Server.
Fig.2. Voter Authentication with Authentication Server & Voting Server
Voter
Voting Server
Login using ID, SK
Via SSL
Authentication Process
E sk (RSK )
RSK =D pk (E sk (RSK )) RSK =D pk (E sk (RSK ))
Random Secret Key (RSK) Random Secret Key (RSK) Authentication with AS
Hello message from V E RSK (M ) HMAC Protected
HMAC Verification
HMAC Protected
E RSK (M )
Response message from VS
HMAC Verification
Authentication
Voting Process: suppose that the voter wants to vote for some candidates N i , where i is the number of candidates. Vote v represented by {0, 1} for each candidate, where if V is voting for C i=1 for Yes the v1= 1, if No v1= 0. Additional digit d is considered as verification of the correct tallying of votes with value of 1, where v= {v1,…..,v i,d}.
Vote Encryption: v encrypted by public key pk of VS E pk(v)=c. V need to calculate checksum of c = H c, which is used to verify that c is tallied without any modification, and it arrived correctly to VS, in this stage HMAC used to preserve integrity.
Encrypted cipher sent to VS, which calculate H(c), and store both H,c and then send H to the Bulletin Board, V can check for H in BB. If the values are identical, c arrived correctly.
Vote Verification: at this stage, we present a None Interactive Zero Knowledge proof method which the voter wants to prove that he used a valid pk and valid voting where no additional number added to some v i and restricted to i number of candidates, so that the vote is well formatted. The verifier is our system with its both separated parts AS and VS.
VS process c to make it masked, so that AS c an’t identify the original vote and still able to verify the correctness of valid encryption and formatting.
Mask function calculated for c,
M=c XOR m0+c XOR m1 (3) Where m0={01 ,…,0i+1} , m1={11 ,…,1i+1}. M is sent to AS, a decryption of masked vote is being done D sk(M)=U, so the result must be 1 for each i,U i+1=1. If it’s not, a reject flag sent to VS, V told that he tried to enter invalid c, and c,H deleted for that V. For each valid c, AS count 1 valid voting, the number of valid c in VS must be identical with number in AS.
Fig.3. Masking Process Example
As shown in Fig.3. Masking Process Example, the addition process is done in a decimal form, not in binary form, the intruder may try to add some core to a specified candidate, in such case the vote slot will increase by the value entered by an intruder, it will be calculated in the final results. This easy to cover after tallying process because the summation of the result of each result must be equal to the number of voters. No one can identify the vote that has the additional score before the tallying process. Here come the NIZKP role, to identify any invalid vote, without decrypting the vote and before the tally process. This process can be handled using FHE easily as described early. It just need to two parties to make this operation away from the voter to preserve the correctness of masking process this is shown in Fig.5. Vote Encryption & Validation with NIZKP
Tally process: after the specified period form authorities finished, the tallying process starts, let the number of valid votes is j, so ∑c j=C, which is the final result of the voting process Decryption of results processed,
D sk(C)=R, where R={r1,….,r i,j}.
R,C and sk put in the BB, so regulatory institutions can verify the tally process, this is shown in Fig.4. Votes Tally & Results Decryption.
B.Security analysis
Any voting system must be able to deal with some security issues related to preserving the privacy of voting and accuracy of results.
Eligibility: Only persons who meet certain pre-determined criteria are allowed to cast permitted number of votes. To achieve this, authority needs to verify the eligibility of voters and record their casted votes, in registration process voter need to introduce all informat ion’s to be considered eligible.
Privacy: No one except voters can know their votes. To achieve this, any traceability between voters and their votes must be removed during the whole election. In our protocol, no one can connect the user to his vote. Accuracy: In the elections, voters expect that their votes are correctly captured and that all eligible voters are correctly tallied. As we introduced, the tally process is verified by the digit d added to each vote, the number of valid votes in AS and V. Another verification done by NIZKP which satisfy accuracy and verifiability. Verifiability: Verifiability is the ability to determine whether only and all valid votes are counted in final tally or not i.e. to determine the accuracy of the election. The accuracy of election can be verified in two ways, one is the individual verifiability where only voters can verify their own votes in the tally which done by our NIZKP method. Therefore, the accuracy of the election consists of N voters is ensured when there are less than or equal to N votes and all N voters verify their votes. The other is universal verifiability, which enables any third party to verify the accuracy of the election which accomplished by putting all R, C,sk on BB for any third party to check tally process.
Fairness: In order to conduct the impartial election, anyone should not be able to compute the partial tally before the end of the election which may influence the remaining voters and may affect the voting result, and this accomplished by separating AS and VS. so sk
is
stored in AS which cannot calculate any results until it receives C form AV.
Receipt-freeness:Receipt-freeness disables anyone including voters themselves to link voters to their votes, in order to protect voters from being coerced to follow intentions of other entities. To achieve receipt-freeness, the voting system didn’t leave any information about the votes of voters. Also, votes should not include any information peculiar to the voters. Receipt-freeness shares the same notion of privacy. Our protocol is Receipt-free.
Incoercibility: Incoercibility protects voters against coercers who can communicate with the voters actively. In our protocol, we allow V to Revote which a method to overcome incoercibility. If V exposed from some incoercible person, he can revote again by authenticate to AS, then send revote to VS with his previous H, a new vote should be replaced with the old vote and new H added to BB.
Dispute-freeness: Even if dishonest voters are involved in elections, disputes among entities should be solved without involving irrelevant entities. The notion of universal verifiability is similar to dispute-freeness but it is limited to the voting and tallying stages. Dispute-freeness accomplished by a mutable verification method before considering the vote is valid, and validation using digit and counting the number of valid votes in AS and VS.
Robustness: Any entity should not be able to disrupt the voting, i.e. the voting system must be able to detect dishonest entities and to complete the voting process without the help of detecting dishonest entities, which is satisfied in our protocol, while any illegible voter does not allowed to communicate with VS, and no invalid vote stored.
Scalability: A scheme has to be extended easily to suffice computation, communication and storage requirements of large-scale elections. Our system is scalable due to cloud-based infrastructure where huge processing and communication can be done. Practicality: A scheme should not have assumptions and requirements that are difficult to implement. Our scheme is very practical because it doesn’t need any special equipment, its just need to rent some cloud servers and put your system on it for a specific period of time, it’s also cost effective.
Fig.4. Votes Tally & Results Decryption
Fig.5. Vote Encryption & Validation with NIZKP
IV. D ESIGN AND I MPLEMENTATION
The proposed E-voting system implemented using HELib library [37], the implementation done by C++ on Ubuntu 12. A. System Structure
The proposed E-voting system software consists three main programs:
? Authentication Server program ? Voting Server program ? Voter Program
All three programs can communicate with each other; all information sent between programs encrypted in different ways, depending on the type of message. The structure is shown in Figure 6. System Structure.
Fig.6. System Structure
1. Assumptions
The assumptions upon which we have built and designed this system are as follows:
Authentication server (AS) considered as a trusted party which fully controlled by authorities. AS contains sensitive data like users and passwords database, private keys and functions that generate RSK. AS should be monitored and logged and controlled by the highest
1 Authorities of the Central Election Commission. Although this monitoring process does not reveal any information about votes or leaks partial results of the election process. Which this server does not contain any votes.
2 Voting Server (VS) considered as untrusted party of the system, it’s hosted in some cloud service, and these cloud services considered as untrusted
platform, wherein some cases the vendor can access to the hosted services and serves and may reveal some sensitive data. Due to this issue, the FHE provided to solve security issues of untrusted platforms. VS could not reveal any data about users, votes and partial results. Where authentication with users done based on RSK provided by AS, and all votes and results are encrypted using FHE schema, and VS does not contain the secret key for that scheme. All data are processed in encrypted form, which prevents any untrusted party from revealing any sensitive data.
3 Voter (V) consider as untrusted party until it authenticates AS. The voter must provide secret credentials, which authenticate his identity. Then he transfers to the second level of trust, where he can authenticate VS using RSK provided by AS. A voter can encrypt his vote locally using the provided program, vote validated to check of correct encryption using a correct public key, and well-defined vote according to the condition provided by the Central Election Commission. The voter cannot prove his vote to anybody, and prevent coercion.
4 The communication between AS and VS considered as a secure connection based on VPN services, or any other secure connection services. Although all messages transferred between AS and VS are encrypted and integrity checked.
5 The communication between Votes and system considered as untrusted anonymous connections, and all messages between Voters and system are encrypted and integrity checked.
2. Authentication Server Program Authentication program responsible for: a) Key generation:
In the key generation process, public key and private key generated. Public key sent to both VS and BB.
Before key generation, some credentials must be prepared depending on the number of voters involved in the election process.
The generated Public key size was 20.3 MB, the same as Secret key, at the value of p=997, for experimental test. b) Voter authentication:
In vote generation stage, VA program listens always for new voter requests. In this stage, the program establishes SSL connection to the voter as a response to the SSL request from the voter. The voter needs to provide his international ID number and his secret password – provided by authority office in registration stage- to be verified and authenticated. This SSL connection used only for authentication stage to hide voter identity form any intruder.
The next stage of authentication is between voter and voting server. AS generates a random secret key, encrypt it with the voter secret password, sent it back to the voter with HMAC function used for message integrity. The same random secret key encrypted with the
pre-defined
Voter Program
Voting Server Program
Authentication Server Program
symmetric key between VA and VS, also it’s sent to VS.
c) Vote verification:
After voter submits his vote to VS, VS calculates a vote mask described in section 0 (vote verification procedure), AS program just always listen for mask verification requests came from VS. AS program decrypt mask and perform a check, which every field in the mask must be 1, else its invalid vote.
Validation message (valid or invalid) saluted with a random number, encrypted with symmetric encryption with RSK as a key and sent to VS.
Size of the masked vote about 204.3 kB (204,293 bytes). And the execution time of decryption is 0.019093/s. Also, decoding function used internally in this step with execution time 0.038623/s. The total execution time of decryption is 0.057716/s, this considered a very small time for decryption which makes the system applicable to work for many decryption processes.
d) Results decryption:
After the specified period of voting ends, end of vote message sent to VS. VS start tallying votes. AS program decrypt the results of voting using the private key, and finally validate the count of voters to valid vote count and send results to BB.
The execution time of the decryption function of final results came from VS is 0.011884/s and decode function is 0.0696/s, so the total decryption time is 0.081484/s.
3.Voting Server Program
The voting program responsible for
a) Voter authentication:
The VS program receives RSK for AS, decrypt it and wait for the voter to send hello message encrypted with same RSK. Once the voter provides correct RSK, he verified and become able to send the vote to VS, if the provided RSK was wrong, VS sends reject message to the user, and store logs for that wrong RSK.
b) Vote mask calculation:
The VS program calculates vote mask for every vote, each vote mask sent to AS for validation. If it's valid, vote acceptance sent to voter encrypted with RSK with HMAC.
c) Vote tallying:
After the voting ends, a message received indicate that voting period ended, vote tallying starts. All results computed in one cipher and sent to AS to decrypt and publish results.
4. Voter Program
Voter program responsible for:
a) Voter Authentication:
The first step in voter program is authentication with AS and then authenticate with VS. Voter first establishes SSL connection to AS then authenticate with his ID and password. Once authenticated he receives an RSK encrypted with his password, he decrypts it and uses it for authentication with VS. Voter sends “hello message” encrypted with RSK using a symmetric encryption algorithm.
b) Ballot preparation:
The Voter chooses his selection of candidates, and form his ballot in a specified way as described before in section III.A Voter program just presents just the candidate choices and the user selects his choice. Voter program performs the preparation process.
c) Vote Encryption:
After ballot preparation, voter program encrypts it using the public key provided on BB. The encrypted ballot size is about 136.1 kB (136,100 bytes) it’s not a constant value and varies for each user, but size almost the same with same parameters. The encryption time is
0.027659/s.
B.Security Properties
The implemented system achieved many security properties, some properties related to the voting process itself, which described in section III.B, and some other properties related to communication channels and hosting environments. This section discusses related issues.
https://www.360docs.net/doc/7a1338920.html,munication channels security
Communication is done between servers AS and VS secured with two factors:
1All messages sent between those servers are encrypted even messages like ACCEPTED or REJECTED messaged are salted to be indistinguishable in the case of symmetric key encryption. All messages are equipped with an HMAC integrity check. This prevents any eavesdropper of intercept or change the messages transmitted over the channel.
2The communication channel secured using VPN service, in this case, we suggest using OpenVPN service to secure connection, which an open source platform that provides high security and privacy of communication. OpenVPN can encrypt communications using many different symmetric key algorithms such as AES, and its use TLS protocol to provide secure commutations.
The communication between Voter side and AS and VS in other side secured using encryption and HMAC integrity check. All messages between servers and Voter are encrypted and salted. All messages are equipped with an HMAC integrity check. This prevents any eavesdropper of intercept or change the messages transmitted over the channel.
2.Hosting environment security
AS hosted on dedicated servers that secured using
Intrusion Detection Systems IDS and Intrusion Prevention Systems IPS, in addition to firewalls, to prevent an intruder from accessing AS. If such thing happened, the intruder will be able to access the most sensitive data in the system ID’s and passwords and secret keys. To prevent this, we suggest securing AS by monitoring each communication trying to connect AS server, if any suspicious activity detected the connection must terminate.
VS hosted in cloud service, it also secured using IDS and IPS, which work to prevent an intruder from accessing VS. If such thing happened, the intruder is able to delete or corrupt some votes, this will lead to damage voting results. To prevent this, all connections must be monitored and if any suspicious activity detected, the connection must be terminated and event log of this activity registered, the voter can do authentication again to be verified.
Voter requested to secure his machine, any hacking to his local machine could lose him his vote. To prevent intruders from changing the structure of vote for example by infecting the victim of viruses that can change the vote structure or change the public key or corrupting votes. VS and AS are responsible for checking the validity of each vote. If the vote is corrupted or unverified, the user told with this issue and given some instruction to secure his machine again. The implemented Voter program should not be able to change or code recover.
V.R ESULTS AND A NALYSIS
A.Traffic Analysis:
The proposed E-voting system generates communication traffic between each part of the system, voter, VS, and AS. The generated traffic achieved privacy, confidentiality, and integrity. As shown in Table 1. Traffic Tracing and Protection Function, all traffic between system parts encrypted, checked by integrity function. This prevents intruders from changing the content of transferred messages and even change the message itself, while all messages encrypted with the securely shared secret key.
Table 1. Traffic Tracing and Protection Function
B.Performance Analysis
All previous results are done with p = 997 and a small
number of candidates; p limits the number of voters. To
achieve true decryption of results p must be larger than
the number of voters because all results are calculated
modulo p. To examine the system scalability and
capability to deal with a large number of users and much
candidates choices, we design a test to examine different
p’s and its reflections on key sizes, vote and mask size,
also its reflection of encryption and decryption time.
The value of p in the test defines the maximum number
of users should vote, which restricted to the number of calculated votes. All results of final tallying and mask calculation done modulo p. If the number of resulted value greater than p, the decryption result will be incorrect. We have to choose p greater than the maximum value of the result.
Fig.7. PublicKey size and Secretkey size for Different p Values As shown in Fig.7. PublicKey size and Secretkey size for Different p Values, the secret key size and public key size is identical for same p value. However, it differs when choosing a larger value of p. The largest key size hit in this experiment when p = 10,000,019, it has reached almost 38 MB for both secret key and public key.
For public key, this considered a large size, but it is necessary when voting made from a large number of persons such 10 million. For a less, the number of users such as 1 million keys decreased to 12.4 MB, which more affordable. Nevertheless, 38MB not too much size for growing speed of the internet. We considered our system practical for such cases, because the public key will be published on BB, and the user can take their time for receiving it.
An important issue is the stored votes total size, which if we considered each vote take an average of 250 kb of disk space, it needs 2.328 terabits for 10 million users. This small size of storage compared to a large number of users, is suitable and affordable because of this storage size available from most cloud providers and even for personal computers.
Fig.8. Vote and Mask sizes for Different p Values
Fig.8. Vote and Mask sizes for Different p Values, the size of both vote and mask generally increase with greater values of p . Mask size greater than vote size, which mask is the vote itself process with a defined equation in section III.A which contains addition and multiplication operations which increase the size of the resulted mask.
The noise generated from the homomorphic addition with noise at most B is 2B and the noise generated form multiplication process is B 2. BGV provides a noise-management technique that keeps the noise under check, by reducing it after homomorphic operations, its bases on “modulus switching” technique.
Fig.7. PublicKey size and Secretkey size for Different p Values shows that the minimum recorded value public key and secret key on p = 100,003, and the maximum value of keys on p= 10,000,019.
Values show that at p=1,000,003 and p=10,000,019 gives the largest value of vote and mask sizes, while the other p values give almost the same size. This due to the change value of L=4 on p=10, 00,003 and p=10, 000,019,
which gives an incorrect decryption of mask when L=3. Because NIZKP circuit contains addition and multiplication, we need to increase the depth of the circuit to be compatible with resulted cipher while all result decryption is done modulo p. NIZKP circuit increases the ciphertext size and noise, which gives incorrect decryption. For smaller p values it succeeded to
decrypt mask correctly with smaller L=3, which the generated noise is smaller than p .
The second part of the test has distinguished the difference of encryption and decryption time for vote, mask and the result. In addition, mask calculation included which important component of system performance. Encryption and decryption time for deferent p values somewhat similar. The produced results are accept able for our system because it’s small and does not affected by changing p value. Mask calculation produced different results for different p value and in general produced higher results of encryption and decryption. This because of circuit size, which contains mutable addition and multiplication process.
The number of plaintext slots differs for each value of p; in our test, we used 31 slots for vote formulation. The vote itself takes 30 slot present voting for each candidate, the 31 slot is a check digit described in section 3. the rest plaintext value is zero, the number of plaintext slots is related to CRT technique used by HELib, described in [38] The resulted plaintext slot can fit up to 65 candidate when p =10,000,019. It’s acceptable for most countries which number of candidates usually not big. Fig.9. Vote Encryption, Mask Calculation - Decryption and Result
Decryption for Different P Values
Fig.9. Vote Encryption, Mask Calculation - Decryption and Result Decryption for Different P Values shows the time consuming in vote encryption, mask decryption, mask calculation and result decryption different p values, which indicate that vote encryption is less time than other and it does not change with changing p value. Second mask decryption and third result decryption. The result of this test was by tallying 100 votes, thus the size of the vote increase with sum calculation. The time is almost similar to vote encryption, mask decryption, and mask calculation. The major difference is in mask calculation time, which increases by increasing p value.
Another part of our experiment is examining the performance of a different number of votes, in this part, we designed a method to auto generate encrypted votes. Each vote filled randomly as a ballot between 30 candidates, and slot 31 filled with 1 as a check digit and encrypt it. For this experiment, we use p=10,000,019, which indicates the largest number of voters 10 million and the largest resulted public key. It takes about a half
hour to generate 30,000 encrypted votes. This time seems to be linear with a larger number of votes. In fact, this not as in real situations, where voters encrypt their votes at the same period separately, not in a sequential way as in this test.
The most important issue of this test is qualifying the
time of tallying a large number of votes, the largest number we examined in this test is 40,000 votes. It takes 42 minutes to tally this number of votes. The test was made on VMware virtual machine configured with 3G of RAM, 2 processors, 2 cores and 30G of hard disk. The host machine was core i5 processor.
Fig.10. Final Result Cipher Decryption Time
Fig.11. Votes Generation Time, And Vote Tally Time for Different
Number of Votes
As shown in Fig.11. Votes Generation Time, And Vote Tally Time for Different Number of Votes, tallying time is somewhat linear in the number of votes. With these results, an expected time of tallying 10 million votes will be 50 hours, using one single virtual machine with the previous specifications. In the real situation, this tally process will be done in the cloud, which may consist of several powerful nodes.
The system is scalable, and it may contain hundreds of nodes, where tailing process is can be done in several nodes and the result of each node can be tallied to gather to get final results. This scalability will reduce the time of tallying much time.
The decryption of results after tallying finish shown in Fig.10. Final Result Cipher Decryption Time, it also increases linearly with the number of tallied votes, this because the noise generated by each homomorphic addition operation. The noise is not too much because addition has a small noise effect, where the addition of two ciphers generates 2B of noise, this is small compared with multiplication noise B2.
Size of tallied results cipher is somewhat identical to a different number of votes as shown in Fig.12. Total Size of Votes for Different Number of Votes, this due to the reduction technique used by HELib.
Fig.12. Total Size of Votes for Different Number of Votes Size of all votes is a big issue, while the size of each vote is small, the total size of a large number of votes considered big. In this experiment, we examined the total size of votes at a different number of votes. As shown in Fig.12. Total Size of Votes for Different Number of Votes the largest size hit on 40,000 was 9.7/Gb. The size grows with the number of votes linearly. In an expectation for the size of 10 million votes, it will take 2.4 Terabit of size, which very affordable in cloud systems. This size available now on some personal computers. For such systems, this considered acceptable size.
C.Stored Data Analysis
At some point, each part of the system has some data, this data may be secret, public or useless data. In this section, we analyzed the data stored in each part and its security concerns.
1.Authentication Server stored data
The authentication server is the most critical part of the system, whereas it contains the most sensitive data in the system which private key, database of users – passwords and secret keys. This part of the system should be secured very well with the most recent ways of server security like an intrusion detection system IDS, intrusion prevention system IPS and firewall. It must be monitored in all the period of voting. AS also store temporary data such as RSK, mask, mask decryption, and mask validation result with its salt and HMAC’s. All these results deleted after voter commit his vote for each voter.
2.Voting Server stored data
VS stores vote cipher and a hash function of that vote, until end of voting period ends. Other temporary data stored in VS such mask, RSK and HMAC’s. Mask deleted immediately after chinking by AS. In addition, RSK deleted after the session ends with the voter.
This provides the minimum information seen by VS, which could be any cloud service that considered untrusted and could reveal some information about the
election process. Cloud provider or intruder could not have useful data can affect the voting process or clarify vote or voter personality. It also could not leak partial results while all votes encrypted.
3.Voter stored data
The voter machine contains temporarily authentication credentials, ID, and password. RSK, HMAC, vote and its encryption, which temporary data. The hash function of encrypted vote stored at the voter side for validation. Vote computed and revote process starts if coercion happens.
D.General Analysis
In general, the system divided to separated parts to prevent any intruder can access one part of the system from affecting the result of the election or leaking partial results or connect any voter to his vote.
No one other than registered users can vote or access system. Each voter can vote without revealing his identity and no one can connect a vote to a voter. Every vote checked whether it has encrypted with a valid public key and formed in the correct format of voting and no additional values added to a specified candidate to increase his result, also no fake votes made.
No one can compute partial results, or interrupt voting process, all communication processes encrypted and integrity checked. Any manipulation tries should be discovered by the system, reported and prevented. The user can revote when he felt coerced.
The system is scalable while it can deal with a large number of users at the same time, and system structure can easily expand without affecting of system functionality. It's also very practical to be used in real election processes.
The system satisfies the major properties of an optimal voting system such as eligibility, privacy, accuracy, verifiability, fairness, receipt-freeness, incoercibility, dispute-freeness, robustness, scalability, and practicality.
VI.C ONCLUSIONS AND F UTURE W ORK
This research examines the applicability of FHE in e-voting systems through designing and implementing Internet-based voting system. The implemented system able to work through cloud infrastructure. The conclusions of this work described below.
A.Conclusions
This research presented an electronic voting system based on fully homomorphic encryption as a case study, to understand how much fully homomorphic encryption is applicable in real life systems. The proposed e-voting system consists of main components, authentication server, voting server, bulletin board and on the other side voters. The separation of the authentication server and voting server let the voting server could be hosted in any cloud service provider or any datacenter service. This provides more privacy, which all votes stored in authentication server encrypted with fully homomorphic encryption and can processed or calculated in encrypted form. This led to another feature, scalability and cost effectiveness. The system could easily expand to more cloud server without compromising system structure or functionality. Using cloud services for a specified period of election obviates buying new hardware each election cycle. This is sufficient for us to afford the burden of maintaining and updating hardware for the next election cycle.
We implemented the proposed system using HELib [37] homomorphic library based on BGV [15] fully homomorphic encryption scheme. The implementation divided into three parts, authentication server program, voting server program, and voter program. We tested results where the system should deal up to 10 million voters, which meets the need of about 70% of countries over the world according to the number of eligible users. The results were applicable for public key size, vote size, mask calculation time, mask decryption time, total size of votes before tallying, tallying time and decryption result. Security concerns of voting systems considered in our work. The developed system was able to prevent intruder form make any fake votes or affect the voting process. The system disables anybody from linking between voters and their votes, even the voters themselves. Every vote checked for validation test. All communications encrypted and integrity checked. No one could calculate partial results even cloud provider. The system satisfies many security concerns eligibility, privacy, accuracy, verifiability, fairness, receipt-freeness, incoercibility, dispute-freeness, robustness, scalability, and practicality. The implemented e-voting was acceptable to work in real elections, with providing more cloud processing power.
B.Future Work
Fully homomorphic encryption has many applications, in this research we discussed in detail one of these applications, which is voting system and its applicability to deploy to cloud services.
The implemented e-voting systems need to add usability features to be more user friendly, an also compared with other systems.
In future work, we intended to discuss other types of applications that applicable to work with cloud infrastructure to study applicability performance and security issues of FHE.
The depth of the circuit in FHE considered a limitation of the practicality of FHE, we intended to examine much larger in-depth circuits to study its effects on performance and resulted ciphers.
In addition to, optimizing our implemented voting system to decrease the public key size, vote size, and mask size. In addition, to use some other functions of HELib, which deals with plaintext slots and noise optimization.
R EFERENCES
[1]R. L. Rivest, L. Adleman and M. L. Dertouzos, "On data
banks and privacy homomorphisms," Foundations of
Secure Computation, p. 169{180, 1987.
[2] A. Rohilla, M. Khurana and M. Kumari, "Homomorphic
Cryptosystem," International Journal of Computer
Network and Information Security(IJCNIS), pp. Vol.9,
No.5, pp.44-51, 2017, 2017.
[3] A. Rohilla, M. Khurana and L. Singh, "Location Privacy
using Homomorphic Encryption over Cloud,"
International Journal of Computer Network and
Information Security (IJCNIS)., 2017.
[4] C. Gentry, A Fully Homomorphic Encryption Scheme,
Stanford University, 2009.
[5] C. Gentry and S. Halevi, "Implementing Gentry ’ s Fully-
Homomorphic Encryption Scheme," Advances in
Cryptology–EUROCRYPT , pp. 1-29, 2011.
[6]N. Smart and F. Vercauteren, "Fully Homomorphic
Encryption with Relatively Small Key and Ciphertext
Sizes," Public Key Cryptography –PKC 2010 Berlin,
Heidelberg, New York, 2010.
[7] D. Stehléand R. Steinfeld, "Faster Fully Homomorphic
Encryption Damien," Advances in Cryptology-
ASIACRYPT 2010, 2010.
[8]M. van Dijk, C. Gentry, S. Halevi and V. Vaikuntanathan,
"Fully Homomorphic Encryption over the Integers,"
Advances in Cryptology–EUROCRYPT 2010, pp. 1-28,
2010.
[9] C. Gentry and S. Halevi, "ully Homomorphic Encryption
without Squashing Using Depth-3 Arithmetic Circuits,"
Foundations of Computer Science (FOCS), 2011 IEEE
52nd Annual Symposium on. IEEE, pp. 107-109, 2011. [10] C. Gentry, S. Halevi and N. . P. Smart, "Better
Bootstrapping in Fully Homomorphic Encryption," Public
Key Cryptography–PKC 2011, 2011.
[11]I. Sharma, "Fully Homomorphic Encryption Scheme with
Symmetric Keys," Master Thesis for Master of
Technology Department of Computer Science &
Engineering, Rajasthan Technical University, Kota, 2013.
[12]J. Coron and A. Mandal, "Fully homomorphic encryption
over the integers with shorter public," Advances in
Cryptology, pp. 1-24, 2011.
[13]Z. Brakerski and V. Vaikuntanathan, "Efficient Fully
Homomorphic Encryption from (Standard) LWE,"
appears in this proceedings. Also available at Cryptology
ePrint Archive,, 2011.
[14]Z. Brakerski, C. Gentry and V. Vaikuntanathan, "Fully
Homomorphic Encryption without Bootstrapping,"
Electronic Colloquium on Computational Complexity
ECCC, pp. 1-26, 2011.
[15]Z. Brakerski, C. Gentry and V. Vaikuntanathan, "(Leveled)
Fully Homomorphic Encryption without Bootstrapping,"
Proceedings of the 3rd Innovations in Theoretical
Computer Science Conference on - ITCS '12, pp. 309-325,
2012.
[16] C. Gentry, A. Sahai and B. Waters, "Homomorphic
Encryption from Learning with Errors: Conceptually-
Simpler, Asymptotically-Faster, Attribute-Based,"
Cryptology ePrint Archive, Report 2013/340, 2013. [17] A. Lopez-Alt, E. Tromer and V. Vaikuntanathan, "On-the-
Fly Multiparty Computation on the Cloud via Multikey
Fully Homomorphic Encryption," Cryptology ePrint
Archive, Report 2013/094, 2013.
[18] A. Kiayias and Y. Moti , "Tree-homomorphic encryption
and scalable Hierarical Secret-Ballot Election.," Springer,
2010.
[19]S. Drew, T. Finkenauer, Z. Durumeric, J. Kitcat, H. Hursti,
M. MacAlpine and J. A. Halderman, "Security Analysis of
the Estonian Internet Voting System.," Proceedings of the
2014 ACM SIGSAC Conference on Computer and Communications Security. ACM, pp. 703-715, 2014. [20]M. A. Bingol, F. Birinci, S. Kardas and M. S. Kiraz,
"Norwegian Internet Voting Protocol Revisited: Security and Privacy Enhancements," International Conference BulCrypt, Sofia, Bulgaria, 2012.
[21]J. K. K. Sako, "Reciept-free Mix-Type Voting Scheme,"
Advances in Cryptology—EUROCRYPT’95. Springer Berlin Heidelberg,, p. 393–403, 1995.
[22] D. C. a. M. J. A. Juels, "Coercion-Resistant Electronic
Elections," Proceedings of the 2005 ACM workshop on Privacy in the electronic society. ACM, pp. 61-70, 2005. [23] A. Huszti, "A secure electronic voting scheme.,"
Electrical Engineering 51, pp. 141-146, 2008.
[24]I. R. a. N. N. I. Ray, "An anonymous electronic voting
protocol for voting over the Internet," Third InternationalWorkshop on Advanced Issues of E-Commerce and Web-Based Information Systems (WECWIS ’01), 2001.
[25]V. N. Kumar and B. Srinivasan , "A practical privacy
preserving e-voting scheme with smart card using blind signature.," International Journal of Computer Network and Information Security , pp. 5(2), p.42., 2013.
[26]T. ElGamal, "A Public Key Cryptosystem and a Signature
Scheme Based on Discrete Logarithms," IEEE TRANSACTIONS ON INFORMATION THEORY, Vols.
IT-31,, no. 4, 1985.
[27]P. Paillier, "Public-Key Cryptosystems Based on
Composite Degree Residuosity Classes," Springer, 1999.
[28]O. Baudron, P.-A. Fouque, D. Pointcheval, J. Stern and G.
Poupard, "Practical multi-candidate election system,"
Proceedings of the twentieth annual ACM symposium on Principles of distributed computing. ACM,, 2001.
[29]I. Damgard and M. Jurik, "A generalisation, a
simplification and some applications of Paillier's probabilistic public-key system.," Public Key Cryptography. Springer Berlin Heidelberg,, 2001.
[30]R. Khatun, T. Bandopadhyay and A. Roy , "Data
Modeling for E-Voting System Using Smart Card based E-Governance System," International Journal of Information Engineering and Electronic Business, pp.
9(2), p.45., 2017.
[31] A. Mohr, "A Survey of Zero-Knowledge Proofs with
Applications to Cryptography," Southern Illinois University, Carbondale, pp. 1-12, 2007.
[32]J. Groth, "Efficient Zero-Knowledge Arguments from
Two-Tiered Homomorphic Commitments," Advances in Cryptology–ASIACRYPT 2011, 2001.
[33]M. Blum, P. Feldman and S. Micali, "Non-interactive
zero-knowledge and its applications," In STOC, p. 103–112, 1988.
[34] C. Gentry, J. Groth, C. Peikert and A. Smith, "Using Fully
Homomorphic Hybrid Encryption to Minimize Non-interative Zero-Knowledge Proofs," Journal of Cryptology (2014), pp. 1-22, 2014.
[35]N. Smart and F. Vercauteren, " Fully Homomorphic
SIMD Operations," IACR Cryptology ePrint Archive, 2011.
[36] C. Gentry, S. Halevi and N. Smart, "Homomorphic
Evaluation of the AES Circuit," CRYPTO, 2012.
[37]S. Halevi, "GitHub -HELib," 31 3 2013. [Online].
Available: https://https://www.360docs.net/doc/7a1338920.html,/shaih/HElib. [Accessed 28 4 2014].
[38]S. Halevi and V. Shoup, "Design and Implementation of a
Homomorphic-Encryption Library," 2013.
[39] M. Bellare, R. Canetti and H. Krawczyk, "Keying hash
functions for message authentication," Advances in Cryptology —CRYPTO’96. Springer Berlin Heidelberg,, 1996.
Authors ’ Profiles
Ahmed Abu Aziz , is an enthusiastic information security engineer, experienced in Networks, Systems administration, Programming, Information Security training and consulting Ahmed has his MSc degree in Computer Engineering form the Islamic University of Gaza in 2015 in the field of
Information Security and Cryptography. He has his BSC degree in Computer Systems Engineering from Palestine Technical Collage. He is very interested in systems and cloud security. He is working as a systems administrator and information security engineer in a local company.
Hasan Qunoo , is a young and active lecturer and researcher in computing. Hasan has a PhD and MSc degrees in Computer Security from the University of Birmingham and an extended experience and training in diverse and interactive teaching in the UK and Gaza.
He has taught a number of courses and has been an active member of the curriculum review committees at the department and faculty levels. He is a researcher and lecturer in Computing
and Computer Security. He is a member of Computer Security Group at the University of Birmingham. He is now an Assistant Professor at the University of Palestine and was the head of department between 2014 - 2016. He has authored the Palestinian Information Technology Association of Companies strategy (2015-2018). In addition, he has worked in various other technical projects.
Dr. Aiman A. Abu Samra , is an Associate Professor at the Computer Engineering Department at the Islamic University of Gaza. He received his PhD degree from the National Technical University of Ukraine in 1996.
Dr. Aiman was the Assistant Vice President of IT Affairs at IUG between
2011- 2014. He was a supervisor of many Master thesis in mobile computer networks, computer security and other topics. His research interests include computer networks and mobile computing. Dr. Aiman is a member of the Technical Committee of the International Arab Journal of Information Technology (IAJIT). He was recognized as one of the most active reviewers during the year 2016.
How to cite this paper: Ahmed A. Abu Aziz, Hasan N.Qunoo, Aiman A. Abu Samra,"Using Homomorphic Cryptographic Solutions on E-voting Systems", International Journal of Computer Network and Information
Security(IJCNIS), Vol.10, No.1, pp.44-59, 2018.DOI: 10.5815/ijcnis.2018.01.06
国产密码改造方案
****单位 办公系统国产密码改造方案 方案设计时间 2020.4
目录 1 国产密码算法背景 (3) 2 网络及业务现状分析 (5) 3 ****单位密码应用现状分析 (6) 3.1 ****单位密码应用现状 (6) 3.2 面临的问题 (6) 4 建设原则 (8) 5 建设目标 (10) 6 设计依据 (11) 7 国密改造方案 (12) 7.1 技术路线选择 (12) 7.2 总体架构 (15) 7.3 改造方案 (17) 7.3.1 可信密码认证机制 (17) 7.3.2 数据存储保护机制 (24) 7.3.3 数据传输保护机制 (24) 7.3.4 运行维护保护机制 (26) 8 整体投资估算 (29) 8.1 国产密码整体改造投资预算 (29) 8.2 ****单位2020年分步实施预算 (30)
1国产密码算法背景 2011年6月,工程院多名院士联合上书,建议在金融、重要政府单位领域率先采用国产密码算法,国务院相关领导作出重要批示。2011年11月,工信部和公安部通告了RSA1024算法被破解的风险,同时人行起草了使用国产密码算法的可行性报告。国家密码管理局在《关于做好公钥密码算法升级工作的函》中要求2011年7月1日以后建立并使用公钥密码的信息系统,应当使用SM2算法;已经建设完成的系统,应尽快进行系统升级,使用SM2算法。 近几年,国家密码管理局发布实施了《证书认证系统密码及其相关技术规范》、《数字证书认证系统密码协议规范》、《数字证书认证系统检测规范》、《证书认证密钥管理系统检测规范》等标准规范,2010年,发布实施了《密码设备应用接口规范》、《通用密码服务接口规范》、《证书应用综合服务接口规范》及《智能IC卡及智能密码钥匙密码应用接口规范》等包含SM1、SM2、SM3、SM4等算法使用的标准规范,而且也有部分厂商依据这些标准规范研制开发了一些产品,为实施国产密码算法升级提供了技术基础。 本项目是落实《中共中央办公厅印(关于加强重要领域密码应用的指导意见)的通知》、《金融和重要领域密码应用与创新发展工作规划(2018-2022年)》、《2019年全省金融和重要领域密码应用与创新发展工作任务分解》等一系列国家和省有关国产密码建设文件精神的重要举措。****单位的协同办公管理平台全面实现国产密码应用推
国产密码算法及应用报告材料
国产密码算法及应用 商用密码,是指能够实现商用密码算法的加密、解密和认证等功能的技术。(包括密码算法编程技术和密码算法芯片、加密卡等的实现技术)。商用密码技术是商用密码的核心,国家将商用密码技术列入国家秘密,任何单位和个人都有责任和义务保护商用密码技术的秘密。 商用密码的应用领域十分广泛,主要用于对不涉及国家秘密内容但又具有敏感性的内部信息、行政事务信息、经济信息等进行加密保护。比如各种安全认证、网上银行、数字签名等。 为了保障商用密码安全,国家商用密码管理办公室制定了一系列密码标准,包括SSF33、SM1(SCB2)、SM2、SM3、SM4、SM7、SM9、祖冲之密码算法等等。其中SSF33、SM1、SM4、SM7、祖冲之密码 是对称算法;SM2、SM9是非对称算法;SM3是哈希算法。 目前已经公布算法文本的包括SM2椭圆曲线公钥密码算法、SM3密码杂凑算法、SM4分组密码算法等。 一、国密算法简介 1.SM1对称密码 国密SM1算法是由国家密码管理局编制的一种商用密码分组标准对称算法,分组长度为128位,密钥长度都为128比特,算法安全
保密强度及相关软硬件实现性能与AES相当,算法不公开,仅以IP 核的形式存在于芯片中。 采用该算法已经研制了系列芯片、智能IC卡、智能密码钥匙、加密卡、加密机等安全产品,广泛应用于电子政务、电子商务及国民经济的各个应用领域(包括国家政务通、警务通等重要领域)。 2.SM2椭圆曲线公钥密码算法 SM2算法就是ECC椭圆曲线密码机制,但在签名、密钥交换方面不同于ECDSA、ECDH等国际标准,而是采取了更为安全的机制。国密SM2算法标准包括4个部分,第1部分为总则,主要介绍了ECC基本的算法描述,包括素数域和二元扩域两种算法描述,第2部分为数字签名算法,这个算法不同于ECDSA算法,其计算量大,也比ECDSA复杂些,也许这样会更安全吧,第3部分为密钥交换协议,与ECDH功能相同,但复杂性高,计算量加大,第4部分为公钥加密算法,使用ECC公钥进行加密和ECC私钥进行加密算法,其实现上是在ECDH上分散出流密钥,之后与明文或者是密文进行异或运算,并没有采用第3部分的密钥交换协议产生的密钥。对于SM2算法的总体感觉,应该是国家发明,其计算上比国际上公布的ECC算法复杂,相对来说算法速度可能慢,但可能是更安全一点。 设需要发送的消息为比特串M,len为M的比特长度。为了对明文M进行加密,作为加密者的用户应实现以下运算步骤: 步骤1:用随机数发生器产生随机数k∈[1,n -1];
电子投票箱选举系统
环宇电子投票箱选举统计软件介绍 ●前言 随着政治文明建设进程的不断推进,各种会议中的人事选举,议案表决,工作测评越来越受到了社会各界的广泛应用,传统的投票选举程序繁杂,费时耗力,仍然不能保证测评的效果和公正性,而最为突出的问题是工作效率低下,存在统计误差。环宇电子智能投票箱系统就能有效的解决这些弊端,帮助各级党委、人大、政协、工会等单位更方便、快捷、高效地完成选举工作。 ●功能描述 环宇电子投票箱系统可实现会议选举时投票与计票及输出选举报告的智能化自动化处理,其工作流程为:接受投票、读票、选票投入方向及正反面的智能辨别与自动调整、选票内容自动定位及智能化分析处理、数据的智能化调度及分配与自动传输、自动统计与汇总、自动数据校对、自动输出各种选举报告。 环宇电子投票箱系统在线工作运行,控制和管理所有在线的电子投票箱、另提他人处理机、废票处理机、大屏幕显示控制机,实时接收每台电子票箱的数据,进行实时处理,实时统计分析。每个电子票箱都有触摸屏控制器,也可显示投票状态。给出大会选举中所必须的准确数据:计票结果、选举结果、其他信息结果,供大会主席团决策。其具有以下功能特征: 1、用户所使用的选票,可以通过WORD或者EXCEL、WPS等任何文字编辑器里制作选票,对票样无任何要求;可现场普通纸、普通打印机打印票样。 2、模板制作轻松方便:根据用户的投票样式,系统软件可以自动模糊识别出识别区域,点击鼠标就可完成模板制作工作。 3、对纸张要求不高,普通打印纸通过打印、复印都能识别,具有自动纠正倾斜功能,出错故障率较低。为区分不同的填表人身份,用户可以选用彩色打印纸,对统计结果无干扰,无影响。 4、OMR涂点图像识别功能,误码率低于百万分之一的要求。 5、支持对全黑白选票的识别,选票打印或印刷时产生偏移、倾斜、放大或缩小,都不影响对选票的正确识别。 6、支持多种涂卡方式:打勾、画圈、数字或字母上画横线,或者涂黑。对笔没有任何要求。 7、支持等额选举、差额选举或等额差额混合型选举,允许同时使用多种不同模板的选票,允许同一张选票上有多种不同类型的候选人并分别计算与处理,比如:同一张选票上可以是人大常委会主任、副主任、秘书长、常委会委员选举,其中某类候选人无效时,其他类别不受影响,仍然有效。 8、投票方向及正反面不受任何限制,支持同一张选票正反两面可印制不同或相同的选票模板。
动态密码系统解决方案
动态密码系统解决方案 2011年末爆发了中国互联网史上最为严重的网站数据泄漏事件,很多中招用户开始修改自己的密码,“今天你改密码了吗?”成了最流行的网络问候语,很多用户都在抱怨改密码改到手软。想起互联网刚刚在国内兴起时候的一个名词:“网上冲浪”,现在看来,如今的互联网用户依然是在用一个账号+一个密码在互联网上肆无忌惮的“冲浪”。随着黑客技术的不断进步,这种传统的账号+密码的身份验证方式是否依然适合今天的互联网? 1、传统“账号+密码”身份验证方式的优缺点 传统的“账号+密码”身份验证方式中提及的密码为静态密码,是由用户自己设定的一串静态数据,静态密码一旦设定之后,除非用户更改,否则将保持不变。陈达谈到,这也就导致了静态密码的安全性缺点,比如容易被偷看、猜测、字典攻击、暴力破解、窃取、监听、重放攻击、木马攻击等。为了从一定程度上提高静态密码的安全性,用户可以定期对密码进行更改,但是这又导致了静态密码在使用和管理上的困难,特别是当一个用户有几个甚至几十个密码需要处理时,非常容易造成密码记错和密码遗忘等问题,而且也很难要求所有的用户都能够严格执行定期修改密码的操作,即使用户定期修改,密码也会有相当一段时间是固定的。从总体上来说,静态密码的缺点和不足主要表现在以下几个方面: (1)、静态密码的易用性和安全性互相排斥,两者不能兼顾,简单容易记忆的密码安全性弱,复杂的静态密码安全性高但是不易记忆和维护; (2)、静态密码安全性低,容易遭受各种形式的安全攻击; (3)、静态密码的风险成本高,一旦泄密将可能造成最大程度的损失,而且在发生损失以前,通常不知道静态密码已经泄密; (4)、静态密码的使用和维护不便,特别一个用户有几个甚至十几个静态密码需要使用和维护时,静态密码遗忘及遗忘以后所进行的挂失、重置等操作通常需要花费不少的时间和精力,非常影响正常的使用感受。 因此,静态密码机制虽然使用和部署非常简单,但从安全性上讲,静态密码属于单因素的身份认证方式,已无法满足互联网对于身份认证安全性的需求。 2、企业/个人到底需要什么样的身份验证方式? 无论是确保个人信息的隐私性,还是企业保护核心数据的安全性,采用全新的身份验证方式已经是势在必行。我们盘点了目前可以用的大部分身份验证方式,除了静态密码之外,今天可以采用的身份验证方式还有如下几种: (1)、动态令牌 动态令牌是用于产生动态口令的身份认证终端设备,它需要配合后台认证系统进行使用。动态口令也称一次性口令。动态口令是变动的口令,其变动来源于产生口令的运算因子的变化,比如时间、次数、交易金额、对方帐号、交易流水号等信息。动态口令的产生因子一般都采用多运算因子:其一为令牌的种子密钥,它是代表用户身份的识别码,是固定不变的;其二为变动因子,正是这些变动因子的不断变化,才产生了不断变动的动态口令。 动态令牌简单、易用,且由于口令不断变化,口令用过之后立即作废,所以安全性较静态口令有较大
浅谈电子投票系统在课堂中的应用
龙源期刊网 https://www.360docs.net/doc/7a1338920.html, 浅谈电子投票系统在课堂中的应用 作者:袁振宇 来源:《中文信息》2019年第01期 摘要:本文从电子投票系统应用于课堂的可行性入手,着重分析了电子投票系统在课堂 中的作用,探索了电子投票系统应用于课堂存在的问题,并提出了相关解决策略,以优化电子投票系统在课堂中的应用。 关键词:电子投票系统课堂应用作用策略 中图分类号:G712 文献标识码:A 文章编号:1003-9082(2019)01-0-01 随着教育的信息化发展,越来越多的信息化设备被运用到教学之中,电子白板、蓝墨云班课软件等已经成为常用的教育载体。而这些信息化设备和软件中的电子投票系统对课堂教学有着重要作用,能够促进课堂互动与交流,激发学生兴趣,形成教学反馈。然而,由于电子投票系统在课堂教学中的应用时间较短,电子投票系统的应用仍存在着教师能力不足、教学方法不科学、问题设置不合理等问题需要解决。因此,各学校积极探索电子投票系统在课堂中的科学应用方法。研究电子投票系统在课堂中的应用不仅能够有效提高课堂教学质量,而且对教育信息化、现代化发展意义深刻。 一、电子投票系统应用于课堂的可行性分析 1.电子投票系统的工作原理 电子投票系统主要包括接收器、投票器、电脑终端和软件。教师使用电脑终端设备和投影仪为学生展示问题及备选答案,学生使用投票器来选择答案,教师使用接收器接受学生的答案选择。这一过程速度非常快,能够有效节省课堂时间。并且,电脑终端中的软件能够将学生的选择数据导入到其他软件之中,以图形的形式展示在屏幕上,以体现选择每个备选答案的人数。教师通过电子投票系统能够了解到学生对问题的掌握程度和学习效果,学生也可以了解到其他学生对答案的选择情况。 2.电子投票系统的使用步骤 首先,在课堂上,教师需要为学生出示问题和备选答案,而这些问题都是教师提前准备好的。教师可以使用PPT来展示问题,也可以口述问题。然后让学生用投票器进行作答。接 着,电脑软件会显示出学生的作答结果,教师可以根据学生的作答情况组织学生进行讨论。之后,教师可以组织学生进行二次投票,得到再次的反馈。最后,教师进行总结并为学生解释正确的答案。 二、电子投票系统在课堂中的作用
企业电子投票系统
企业电子投票系统 目录 第1部分概述 (2) 第2部分分析部分 (4) 2.1.功能需求 (4) 第3部分系统设计 (5) 3.1.功能模块设计 (5) 3.2.数据库的设计 (5) 第4部分系统开发 (5) 4.1.数据库 (5) 4.1.1.创建数据库 (5) 4.1.2.创建表 (6) 4.1.3.连接数据库 (6) 4.2.功能的实现 (7) 4.3.问题及解决 (7) 第5部分运行部分 (7) 5.1.系统的安装 (7) 5.2.系统的使用 (8) 第6部分附录 (10) 附录1运行环境 (10) 1.1硬件要求 (10) 1.2.软件要求 (11) 附录2设计代码 (11)
第1部分概述 J2EE是一种利用Java 2平台来简化诸多与多级企业解决方案的开发、部署和管理相关的复杂问题的体系结构。J2EE技术的基础就是核心Java平台或Java 2平台的标准版,J2EE 不仅巩固了标准版中的许多优点,例如“编写一次、到处运行”的特性、方便存取数据库的JDBC API、CORBA技术以及能够在Internet应用中保护数据的安全模式等等,同时还提供了对EJB(Enterprise JavaBeans)、Java Servlets API、JSP(Java Server Pages)以及XML技术的全面支持。 J2EE体系包括java server pages(JSP) ,java SERVLET, enterprise bean,WEB service等技术。这些技术的出现给电子商务时代的WEB应用程序的开发提供了一个非常有竞争力的选择。怎样把这些技术组合起来形成一个适应项目需要的稳定架构是项目开发过程中一个非常重要的步骤。完成这个步骤可以形成一个主要里程碑基线。 J2EE架构是当前主流的架构之一,目前大多数企业采用J2EE技术的结构设计与解决方案。J2EE体系结构提供中间层集成框架用来满足无需太多费用而又需要高可用性、高可靠性以及可扩展性的应用的需求。通过提供统一的开发平台,J2EE降低了开发多层应用的费用和复杂性,同时提供对现有应用程序集成强有力支持,完全支持Enterprise JavaBeans,有良好的向导支持打包和部署应用,添加目录支持,增强了安全机制,提高了性能。 随着Internet和企业计算在90年代的腾飞,HTTP、HTML和Java平台逐渐演变成为针对客户机计算的标准,这带动了服务器上集中商业逻辑的发展以及电子商务的普及。在服务器端,CGI(Common Gateway Interface,公共网关接口)、NSAPI(Netscape Server API)和ISAPI(Internet Server API)等多种编程和连通性模型日趋流行,极大地增加了编程和维护的工作量。 5年前,Sun公司的Java软件就以其提供的跨平台应用程序开发与配置手段震撼了整个Web世界。几年来,Java技术从一个网站工具发展到了可驾驭从智能卡、小型消费类设备到大型数据中心服务器等一系列系统的端到端Java 2平台,它使软件开发商、服务提供商和设备制造商更容易抢占市场机遇。 目前,Java 2平台有3个版本,它们是适用于小型设备和智能卡的Java 2平台Micro版(Java 2 Platform Micro Edition,J2ME)、适用于桌面系统的Java 2平台标准版(Java 2 Platform Standard Edition,J2SE)、适用于创建服务器应用程序和服务的Java 2平台企业版(Java 2 Platform Enterprise Edition,J2EE)。 Sun公司在企业版中增加了一整套核心企业应用程序编程界面,而所有这些界面均为标准的模块化组件。J2EE技术还为这些组件提供一整套企业服务,通过自动化的方式完成应用程序开发中的诸多耗时且费力的艰难工作,为用户提供一种可创建广泛兼容的企业解决方案而无需进行复杂编程的平台。利用这一优势可以方便地开发出高质量的、适合企业使用的应用程序,还可极大地减少产品研发上市时间、成本和风险。 企业级应用是指那些为商业组织、大型企业而创建并部署的解决方案及应用。这些大型企业级应用的结构复杂,涉及的外部资源众多、事务密集、数据量大、用户数多,有较强的安全性考虑。 当代的企业级应用决不可能是一个个的独立系统。在企业中,一般都会部署多个彼此连接的、相互通过不同集成层次进行交互的企业级应用,同时这些应用又都有可能与其它企业的相关应用连接,从而构成一个结构复杂的、跨越Intranet和Internet的分布式企业应用群
C语言课程设计报告电子投票系统
C语言课程设计报告 电子投票系统 学院计算机学院 专业 年级 姓名 学号 教师 年月日 广东工业大学计算机学院制 一.设计题目 电子投票系统 二.课程设计目的 了解软件工程中的一些系统分析,模块分析,代码设计的概念,利用WIN-TC 实现学生成绩管理系统的录入、查询、删除、统计等基本操作,使用单链表结构实现学生成绩管理,了解数据库管理的基本功能,掌握C语言中的结构体、指针、函数(系统函数、自定义函数)、文件操作等知识。通过对系统的分析和设计,进一步巩固C语言的学习,以提高对开发环境的进一步认识和综合编程能力。 三.系统功能 本系统程序功能: (1)投票者功能
a.浏览所有候选人资料 b.查询要了解的候选人的信息 c.在了解候选人之后进行投票 (2)管理员功能 a.创建新的候选人资料 b.创建新的用户资料 c.查询要了解的候选人资料 d.浏览所有的候选人资料 e.对候选人票数进行统计并排序 四.系统功能模块结构图 本程序利用单链表存储结构完成对学生成绩的动态管理,其基本功能模块如下图所示: 1.数据结构 链表是线形表的一种,线形表分为顺序存储结构和链式存储结构。线形表的顺序存储结构的特点是逻辑关系上相邻的两个元素物理位置上也相邻,因此可以随机存取表中任一元素。链式存储结构的特点是用一组任意的存储单元存储
线形表的数据元素。链表的最大的优点是对表的添加、删除、查找、排序等操作比较方便,因此采用链表来存储候选人,投票人相关信息。且对结点的定义如下: ttypedef struct candidate sort()整理所有投票 先调用read()读取候选人信息,利用for语句,使用选择法对投票数进行排序,并输出。 11.vote()投票者投票 先调用read()读取候选人信息,输入候选人相应编号,利用for语句,将对应候选人的投票数+1,并返回到文档中,输出投票结果。若查无此编号,输出“投票失败!您要投票的号码不存在”。 六.结果 初始界面 分别输入1,1进入管理员界面 创建新候选人 输出候选人信息 投票者界面 投票以及投票结果 候选人票数排序结果 七.心得体会 在本次课程设计中,先使用结构化分析方法对系统进行分析,将整个系统细分为几个模块,再针对每个小模块编写代码。通过本次课程设计的学习以及老师的指导,学会了很多东西,了解了开发一个系统的一些步骤。尽管大部分都
安恒信息数据安全防“脱库”解决方案
安恒信息数据安全防“脱库”解决方案 1.前言 近日不断有黑客陆续在互联网上公开提供国内多家知名网站部分用户数据库下载,国内外媒体频繁报道,影响恶劣,引起社会广泛关注。其中涉及到游戏类、社区类、交友类等网站用户数据正逐步公开,各报道中也针对系列事件向用户提出密码设置策略等安全建议。 注册用户数据作为网站所有者的核心信息资产,涉及到网站及关联信息系统的实质业务,对其保密性的要求强度不言而喻。随着网站及微博实名制规定的陆续出台,如果在实名制的网站出现用户数据泄露事件,将会产生更恶劣的影响。 针对近期部分互联网站信息泄露事件,工信部于2011年12月28日发布通告要求:各互联网站要高度重视用户信息安全工作,把用户信息保护作为关系行业健康发展和企业诚信建设的重要工作抓好抓实。发生用户信息泄露的网站,要妥善做好善后工作,尽快通过网站公告、电子邮件、电话、短信等方式向用户发出警示,提醒用户修改在本网站或其他网站使用的相同用户名和密码。未发生用户信息泄露的网站,要加强安全监测,必要时提醒用户修改密码。 各互联网站要引以为戒,开展全面的安全自查,及时发现和修复安全漏洞。要加强系统安全防护,落实相关网络安全防护标准,提高系统防入侵、防窃取、防攻击能力。要采用加密方式存储用户信息,保障用户信息安全。一旦发生网络安全事件,要在开展应急处置的同时,按照规定向互联网行业主管部门及时报告。 工信部同时提醒广大互联网用户提高信息安全意识,密切关注相关网站发布的公告,并根据网站安全提示修改密码。提高密码的安全强度并定期修改。 2.信息泄密的根源 2.1.透过现象看本质 2.1.1.攻击者因为利益铤而走险 攻击者为什么会冒着巨大的法律风险去获取用户信息? 2001年随着网络游戏的兴起,虚拟物品和虚拟货币的价值逐步被人们认可,网络上出现了多种途径可以将虚拟财产转化成现实货币,针对游戏账号攻击的逐步兴起,并发展成庞大的虚拟资产交易市场;
(决策管理)广州市业主决策电子投票工作指引
广州市业主决策电子投票工作指引 一、适用范围 本市行政区域内按照法律、法规、规章和规范性文件规定以及管理规约、业主大会议事规则约定需要业主共同决定的事项,使用电子投票表决的活动适用于《广州市业主决策电子投票暂行规则》。 电子投票,是指以市住房和城乡建设行政主管部门提供的业主决策电子投票系统(以下简称投票系统)为平台,业主通过微信、短信、网站等互联网、移动通信技术手段,对物业管理活动中的业主共同决定事项投票表决的活动。 二、表决事项 物业管理区域内需由业主共同决定的下列事项,可以使用电子投票表决: (一)制定和修改业主大会议事规则; (二)制定和修改管理规约; (三)选举业主委员会或者更换业主委员会委员; (四)决定是否设立业主监事会; (五)制定物业服务内容、标准以及物业服务收费方案; (六)选聘和解聘物业服务企业;
(七)筹集和使用物业专项维修资金,制定物业专项维修资金管理制度; (八)改建、重建建筑物及其附属设施; (九)改变共用部位、共用设施设备的用途; (十)决定或者授权业主委员会决定共用部位、共用设施设备的经营方式,管理、使用经营收益; (十一)听取和审查业主委员会的工作报告和收支预算结算报告、业主监事会的工作报告; (十二)改变或者撤销本物业管理区域内部分业主、业主委员会作出的与业主大会决定相抵触的决议; (十三)法律、法规、规章规定或者管理规约、业主大会议事规则约定应由业主共同决定的事项。 三、主管部门 市住房和城乡建设行政主管部门组织实施本规则,负责投票系统的建设、维护和管理,负责全市电子投票活动的监督管理工作。 区住房和建设行政主管部门负责本辖区电子投票活动的监督管理工作。 街道办事处、镇人民政府会同区住房和建设行政主管部门负责指导、协助、监督本辖区投票组织者开展电子投票活动,调解处理电子投票活动中的纠纷。 居民委员会、村民委员会协助街道办事处、镇人民政
消费机系统应用解决方案
消费机系统应用解决方案 本文的内容包括: 消费管理系统的主要构成; 消费系统的类型; 中控的消费管理系统基本工作原理; 中控消费机的主要构成; 中控消费机的优势; 消费机应用领域。 1 系统的主要构成 消费管理系统图如下: 图 1
以下是消费管理系统的主要构成部分及其功能需求说明: 1.1消费管理服务器 用于安装存储消费的数据库与消费终端机配套使用的应用软件,它能收集终端机的交易记录并储存到数据库(如:MySQL Server 、 Microsoft SQL Server 2005),具体的功能模块如下描述: ●人事管理:部门、人员资料的导入导出,人员档案管理、人员照片管理等, 也包括人像卡的打印。 ●卡片管理:用户卡片的发卡、卡片充值、挂失解挂、退款、退卡等操作,以 及对一些管理卡如:管理员卡、操作员卡等的发行管理。 ●结算中心:生成用户所需要的多种财务报表,如:资金收支、个人对帐、消 费统计、月(天)结算报表。 ●设备管理包括设备状态、数据采集、下载名单、设备设置功能。 ⑴设备状态:测试消费机是否正常连接,可扩充电子地图,实时监控设备状态; ⑵数据采集:根据选定的机号采集消费机中的消费数据; 定时采集,可设定系统每天定时采集时间点; 实时采集,可设定实时采集数据的笔数和采集速度; ⑶下载名单:当需挂失或解挂用户时,通过该功能将名单下载到消费机; 可选择单张卡片挂失、解挂或者全部刷新挂失、解挂; ⑷设备设置:设置设备的工作模式、通讯方式、通讯参数(机号、IP、速率等)、同步 设备时间、设置不同工作模式下的设备参数; 在不同的消费模式,可设置卡类使用限制、刷卡次数限制、刷卡金额限 制、刷卡频率限制、有效工作时间及超额消费的验证方式; ●补助功能:在系统里批量添加补助人员信息,设置充值金额。然后开启补助 充值模式,自动校验卡片的有效性,完成已设置补助充值;也可以选择从自助服务器终端发放补助; ●系统设置包括系统设置、卡类设置、营业员管理、操作员管理、设备管理功 能。 ⑴系统设置:有设置早、中、晚餐和夜宵的起止时间; ⑵卡类设置:设置卡类的名称、应收押金、优惠费率、发卡有效期、最大卡金额; ⑶营业员管理:提供增加、修改营业员,以及制作营业员卡、注销营业员卡等功能;
最新Web应用安全解决方案资料
××Web应用安全解决方案 一、应用安全需求 1.针对Web的攻击 现代的信息系统,无论是建立对外的信息发布和数据交换平台,还是建立内部的业务应用系统,都离不开W eb应用。W eb应用不仅给用户提供一个方便和易用的交互手段,也给信息和服务提供者构建一个标准技术开发和应用平台。 网络的发展历史也可以说是攻击与防护不断交织发展的过程。目前,全球网络用户已近20 亿,用户利用互联网进行购物、银行转账支付和各种软件下载,企业用户更是依赖于网络构建他们的核心业务,对此,W eb 安全性已经提高一个空前的高度。 然而,随着黑客们将注意力从以往对网络服务器的攻击逐步转移到了对W eb 应用的攻击上,他们针对W eb网站和应用的攻击愈演愈烈,频频得手。根据Gartner的最新调查,信息安全攻击有75%都是发生在W eb应用而非网络层面上。同时,数据也显示,三分之二的W eb站点都相当脆弱,易受攻击。 另外,据美国计算机安全协会(CSI)/美国联邦调查局(FBI)的研究表明,在接受调查的公司中,2004年有52%的公司的信息系统遭受过外部攻击(包括系统入侵、滥用W eb应用系统、网页置换、盗取私人信息及拒绝服务等等),这些攻击给269家受访公司带来的经济损失超过 1.41亿美元,但事实上他们
之中有98%的公司都装有防火墙。早在2002年,IDC 就曾在报告中认为, “网络防火墙对应用层的安全已起不到什么作用了,因为为了确保通信,网络防火墙内的W eb 端口都必须处于开放状态。” 目前,利用网上随处可见的攻击软件,攻击者不需要对网络协议深厚理解,即可完成诸如更换W eb 网站主页、盗取管理员密码、破坏整个网站数据等等攻击。而这些攻击过程中产生的网络层数据,和正常数据没有什么区别。 2.Web 安全防范 在W eb 应用的各个层面,都会使用不同的技术来确保安全性,如图示1所示。为了保证用户数据传输到企业 W eb 服务器的传输安全,通信层通常会使用 SSL 技术加密数据;企业会使用防火墙和IDS/IPS 来保证仅允许特定的访问, 所有不必要暴露的端口和非法的访问,在这里都会被阻止。 图示 1 Web 应用的安全防护 防火墙 IDS/IPS DoS 攻击 端口扫描网络层模式攻击 已知Web 服务器漏洞跨站脚本 注入式攻击 恶意执行 网页篡改 W eb 服务器 数据库服务器 Web 应用 应用服务器
C学生电子投票平台系统报告
VC++课程设计报告 2016年 12月 1问题描述 学生电子投票平台设计是通过界面录入候选人的信息(姓名、编号、数学成绩、英语成绩、C++成绩),运行过后能够显示候选人的信息,并且统计总成绩和排名。接下来进行投票,投票人为候选人投票,显示投票结果,且能在进行增加候选人信息和查询候选人信息及排名情况。(1)、运用C++面向对象的知识,解决学生电子投票平台设计。 (2)、利用结构体、类、继承、析构函数、构造函数及对以前积累知识来设计这一学生电子投票系统。 (3)、全面提高学生的程序设计能力和开发能力。 2基本要求 课 程: C++课程设计 系 别: 计算机系 班 级: 学 号: 姓 名: 选题名称: 学生电子投票平台 起止时间: 指导教师:
1)功能齐全:界面操作灵活方便,至少实现以下基本功能: ●候选人为5名,投票人数最少为10人; ●候选人信息包括:编号、姓名和本学期三门课程的成绩(英语、数学、C++程序设计 语言); ●程序运行时显示简单菜单,菜单内容包括: ①录入数据:录入候选人信息; ②显示数据:显示候选人信息并统计三门课程总成绩; ③投票; ④投票结果:显示票数统计结果,并按得票数排序; ⑤查询:输入编号查询某候选人信息。 2) 友好性:界面友好、输入有提示、尽量展示人性化。 3) 可读性:源程序代码清晰、有层次、主要程序段有注释。 4) 健壮性:用户输入非法数据时,系统应及时给出警告信息。 5) 在规定的时间内完成课程设计任务 6) 完成课程设计报告 3需求分析 1主要任务 录入5个候选人的信息(编号,姓名,英语成绩,数学成绩,C++成绩),至少10人为这5个候选人进行投票。统计候选人总成绩以及票数,可以对票数进行排序。输入编号可以查询候选人的详细信息。 2.输入与输出 输入:该系统的输入主要分成2个部分,第一个部分即系统录入信息的过程,其中又分成2个部分,即录入数据和投票;第二的部分是系统功能的查询,通过输入序号来实现不同的查询。输出:当用户输入真确的指令时,输出结果;当用户输入错的指令时会提示错误(例如:“无法识别指令,请重新输入:”),然后让用户重新输入指令。 3.程序功能 1)录入候选人信息
密码卫士安全控件系统解决方案
密码卫士安全控件系统 解决方案 V1.0 北京得安信息技术有限公司 2018-01-02
目录 一、前言 (2) 1.1 范围 (2) 1.2 修订历史 (2) 二、项目背景 (3) 三、建设目标 (4) 四、密码卫士安全控件介绍 (4) 五、密码卫士安全控件系统设计 (5) 5.1系统整体架构设计 (5) 5.2系统核心技术设计 (6) 5.2.1物理密码键盘和密码控件的对比 (6) 5.2.2软键盘密码控件原理和攻击方法 (7) 5.2.3软键盘式密码控件 (8) 5.2.4低级键盘钩子式密码控件 (9) 5.3系统安全通信设计 (10) 5.3系统安全技术原理 (12) 六、密码卫士安全控件实施应用 (12) 6.1系统集群部署 (12) 6.2操作系统应用 (12) 6.3浏览器应用 (13) 6.4兼容性 (13) 6.5服务端的平台和语言 (13) 6.6国密算法支持 (13) 6.7扩展性 (13) 6.8适用范围 (13) 6.9安装升级 (13) 七、项目实施周期 (14) 7.1 开发周期 (14) 7.1 项目实施计划 (15) 八、技术支持及售后服务方案 (16) 8.1 技术服务框架 (17) 8.2 技术服务标准 (18) 8.2.1 故障等级分类 (18) 8.2.2 项目实施服务 (18) 8.2.3 验收测试 (19)
8.2.4 软件维护 (19) 九、培训方案 (19) 9.1 培训对象 (19) 9.2 培训人员 (20) 9.3 培训教材与讲义 (20) 9.4 培训时间 (20) 9.5 培训方式 (20) 十、项目预算及报价 (21)
XX公司国产密码自查及应用整体规划
XX公司 国产密码自查及应用整体规划 XX局: 我公司按照XX局《XXXXXX》要求,对信息系统国产密码应用情况进行了一次详细的自查和整体性的规划,现将具体情况汇报如下: 一、工作开展情况 我公司高度重视此次国产密码应用规划工作,为确保工作顺利开展,专门组织技术部、合规部召开了工作会议,集中学习了领导讲话精神及相关的监管文件。并成立了由总经理任组长,相关部门经理任副组长的国产密码应用规划小组。 组长: 副组长: 组员: 二、信息系统国产密码应用情况 目前整个金融行业普遍使用国外的软件、硬件产品,国产密码应用的比例很小。我公司目前使用密码的硬件设备总数为XX台,其中服务器XX台,存储盘柜XX台,交换机XX台,路由器XX台,防火墙XX台,均为国外品牌。含有密码应用的系统XX套。除网站系统应用国产密码产品外,其余的都是使用国外密码产品或算法。 三、信息系统国产密码应用整体规划 我公司计划下一步采取先外围后核心、先分支后总部的策略,稳
步扩大国产密码产品的应用范围,提高国产密码产品的应用比例,降低对国外密码产品的依赖。 在服务器和网络硬件的采购中,对国产品牌和国外品牌的性能进行比对,在不影响信息系统性能的前提下,优先采购国产品牌的产品,在信息系统中逐步增加国内品牌产品的比例,以加大硬件方面国产密码的应用。 在软件方面,我们计划与开发商进行协商,督促其对系统进行改造,使用国产的密码产品和加密算法。并与国家行业CA认证体系进行对接,按照国家标准设计、使用密码产品。 这样在软件、硬件两方面双管齐下,逐步增加国产密码产品在信息系统中的应用比例。 XX公司 XXXX年XX月XX日
(可直接使用)软件技术整体解决方案.doc
软件开发技术方案 1.开发框架 开发的系统中所应用的技术都是基于JavaEE,技术成熟稳定又能保持先进性。采用B/S架构使系统能集中部署分布使用,有利于系统升级维护;采用MVC 的开发模式并参考SOA体系架构进行功能设计,使得能快速扩展业务功能而不会影响现有系统功能的正常使用,可根据实际业务量进行部分功能扩容,在满足系统运行要求的同时实现成本最小化。系统采用分布式部署,系统功能隔离运行,保障系统整体运行的稳定性。 图1.开发框架与体系结构图 1.1.web端技术栈 (1)前端采用elementUI/jquery/bootstrap/vue实现,前端和Controller交换数据基于json格式。 1.2业务端技术栈 (1)业务端基于springboot、springMVC、JPA、SpringData技术栈构建,对于复杂的系统则采用springCloud构建。 (2)四层分隔:controller(Facade)/service/dao/entity,其中fa?ade主要用于生成json,实现和前端的数据交换。 (2)命名:按照功能模块划分各层包名,各层一致。
2.系统安全保障 2.1 访问安全性 权限管理是系统安全的重要方式,必须是合法的用户才可以访问系统(用户认证),且必须具有该资源的访问权限才可以访问该资源(授权)。 我们系统设计权限模型,标准权限数据模型包括:用户、角色、权限(包括资源和权限)、用户角色关系、角色权限关系。权限分配:通过UI界面方便给用户分配权限,对上边权限模型进行增、删、改、查操作。 基于角色的权限控制策略根据角色判断是否有操作权限,因为角色的变化性较高,如果角色修改需要修改控制代码。 而基于资源的权限控制:根据资源权限判断是否有操作权限,因为资源较为固定,如果角色修改或角色中权限修改不需要修改控制代码,使用此方法系统可维护性很强。建议使用。 2.2 数据安全性 可以从三个层面入手:操作系统;应用系统;数据库;比较常用的是应用系统和数据库层面的安全保障措施。 在操作系统层面通过防火墙的设置。如设置成端口8080只有自己的电脑能访问。应用系统层面通过登陆拦截,拦截访问请求的方式。密码不能是明文,必须加密;加密算法必须是不可逆的,不需要知道客户的密码。密码的加密算法{ MD5--不安全,可被破解。需要把MD5的32位字符串再次加密(次数只有你自己知道),不容易破解;加密多次之后,登录时忘记密码,只能重置密码,它不会告诉你原密码,因为管理员也不知道。 3.项目计划的编制和管理 本公司项目基于敏捷过程的方式组织,项目计划基于需求和团队反复讨论的过程。在开发系统时都经过了解需求,开需求分析会议,确定开发任务,推进开发进度,测试,试点,交付等开发步骤,其中具体内容有: 1,了解需求:跟客户沟通,充分了解对方的需求,然后对需求进行过滤,最后整体成需求文档 2,需求分析会议:也就是项目启动会议之后要做的事情,对拿来的需求进行讨论,怎么做满足需求。主要对需求进行全面的梳理,让开发,产品,项目都熟悉
Web应用安全解决方案(0001)
Web应用安全解决方案
××Web应用安全解决方案 一、应用安全需求 1.针对Web的攻击 现代的信息系统,无论是建立对外的信息发布和数据交换平台,还是建立内部的业务应用系统,都离不开Web应用。Web应用不仅给用户提供一个方便和易用的交互手段,也给信息和服务提供者构建一个标准技术开发和应用平台。 网络的发展历史也可以说是攻击与防护不断交织发展的过程。目前,全球网络用户已近20 亿,用户利用互联网进行购物、银行转账支付和各种软件下载,企业用户更是依赖于网络构建他们的核心业务,对此,Web 安全性已经提高一个空前的高度。
然而,随着黑客们将注意力从以往对网络服务器的攻击逐步转移到了对Web 应用的攻击上,他们针对Web网站和应用的攻击愈演愈烈,频频得手。根据Gartner的最新调查,信息安全攻击有75%都是发生在Web应用而非网络层面上。同时,数据也显示,三分之二的Web站点都相当脆弱,易受攻击。 另外,据美国计算机安全协会(CSI)/美国联邦调查局(FBI)的研究表明,在接受调查的公司中,2004年有52%的公司的信息系统遭受过外部攻击(包括系统入侵、滥用Web应用系统、网页置换、盗取私人信息及拒绝服务等等),这些攻击给269家受访公
司带来的经济损失超过1.41亿美元,但事实上他们之中有98%的公司都装有防火墙。早在2002年,IDC就曾在报告中认为,“网络防火墙对应用层的安全已起不到什么作用了,因为为了确保通信,网络防火墙内的Web端口都必须处于开放状态。” 目前,利用网上随处可见的攻击软件,攻击者不需要对网络协议深厚理解,即可完成诸如更换Web网站主页、盗取管理员密码、破坏整个网站数据等等攻击。而这些攻击过程中产生的网络层数据,和正常数据没有什么区别。 2.Web安全防范 在Web应用的各个层面,都会使用不同的
电子投票平台管理系统
综合性实验报告 题目:电子投票平台管理系统 课程名称:C语言程序设计 院系名称:计算机科学与技术学院 专业班级: 09计算机(非师范) 学生姓名:赵紫尧 学号: 20091202069 任课教师:张震
一、实验目的: C语言课程设计是计算机学院重要的教学环节,它为学生提供了一个既动手又动脑,将课本上的理论知识和实际有机的结合起来,独立分析和解决实际问题的机会。 1. 进一步巩固和复习C程序设计的基础知识。 2. 培养学生结构化程序,模块化程序设计的方法和能力。 3. 提高学生调试程序的技巧和软件设计的能力。 4. 提高学生分析问题、解决问题以及综合利用C语言进行程序设计的能力。 5. 了解软件的编制过程。 二、实验要求: 1.主要操作包括:数据输入、输出、插入、删除、查找、修改、排序等。 2. 用C语言编程实现上述实验内容的结构定义和相关功能,要求程序能够正确执行,最后提交源程序代码及实验报告。 三、系统分析 电子投票平台有两大功能是:管理员操作和游客操作。它包括功能选择;身份验证;投票人管理模块;候选人管理模块;投票区和得票结果管理六大模块。保证了不同人有自己的操作,同时又不能执行别人的操作,具有安全性,并且又有一定的实用性。 本程序包含六个功能模块:功能选择;身份验证;投票人管理模块;候选人管理模块和投票区。 ①功能选择:功能选择模块为系统提供类似于菜单的功能,让用户输入功能选择项,并进入相应的功能执行程序。系统按权限分为管理员的功能选择和投票人的功能选择。分别在admin()和gust()函数中。
②身份验证:该模块判断要使用该系统的是投票人还是管理员,首先获取登录者的用户名和密码,当用户名和密码相符时,判断用户的权限并进入相应功能选择函数。当用户忘记密码时,给用户机会进行重新输入。源程序包含在denglu()中。 ③候选人管理模块:候选人管理模块完成候选人的初始化、候选人信息的浏览、候选人信息修改、3个主要功能。源程序包含在chushihua();liulan();xiugai()。 ④投票区管理:投票区完成该系统的主体功能。当投票人顺得登录系统后,输入要投票的候选人的姓名,即可完成投票。候选人的得票信息会随时刷新。每个投票人投票后就会失去投票的权利,避免重复投票。投票后立刻显示各个候选人的得票数。 四、程序操作说明书 ①. 用户类型操作 ②.输入1进行管理员操作。输入帐号和密码。进行下一步操作。 ③.输入1进行候选人初始化,并输入各个候选人的资料。
应用集成解决方案
应用集成 1.应用集成现状分析 企事业单位面临着21世纪的激烈竞争,为有效提高自身的管理与监控,从而使自己在竞争当中处于一个有利的位置,企事业的信息化建设是一项必不可少的措施。 企事业的信息化建设本身不是一项短时间可以完全建设起来的工程,企事业在自身的信息化建设当中一般会是采取先针对某些需求迫切,投入较小而效果明显的信息化系统,优先进行系统的建设,然后再针对其它方面的信息化需求进行相应系统的建设,最后形成了企事业信息化道路上的多套应用系统。沿着企事业应用系统逐套建设,上线运行的方式来打造整个企事业的整个信息化平台, 如果在前期的规划当中没有未能按统一,长远规划来实施的话,那么多套应用系统之间很容易形成各自孤立的情况。每一套应用系统都是孤立的一套完整的系统,有自己的用户界面,系统用户,系统认证,系统角色与权限,业务处理功能与流程,技术平台,数据库与业务数据等。 1.1 多套用户界面 有多套用户界面,意味着用户使用多个应用系统的时候需要面对多套用户的操作界面。为了能顺利地使用各个应用系统进行日常的事务处理,用户首先就得熟悉多套应用系统的操作方式,用户对于系统的熟悉需要花很多的时间与精力,最终可能会导致用户形成了多种操作习惯的冲突,而不能很好地在多处应用系统进行顺利地操作切换。 如,在A系统中,操作菜单是放置在界面的左边,用户选择了一项功能后,主要在界面的右边进行相关的操作。右边界面中的按钮都是放置于右下角。而在系统B中,右边界面的按钮都是放置于左边。这就形成了一种反差,用户使用A系统的时间成了就会习惯于到右边,去找相关按钮进行点击,那么他在B系统里就会经常发现右边没按钮,再移动鼠标到左边去点击相关按钮。 1.2 多套系统用户 有多套系统用户,每个系统各自一套,意味着同一个普通用户有多套应用系统账号,管理员维护一个用户的信息得到多个系统中去进行相应的账号维护。 首先针对普通用户,他在每一个应用系统中都有一套账号,账号包含了登录的用户ID 与密码等信息。为了正常地使用多套应用系统,他就必须得记住他在多套应用系统下的账号。除非多套账号都是一样的,否则这对普通用户来说要同时记住多套应用系统的账号,确实是一件痛苦的事情。在日常的使用中,多套账号很容易相互冲突,导致混乱。 其次针对管理员,添加删除一个普通用户,他需要到多个应用系统各进行相应的添加与删除,大大增加了管理员的工作量,而且这样的重复性工作容易导致出错。
