L29 Software Testing slides
富山牌工业缝纫机说明书

为了您的安全使用 Safety Instructions
1.安全使用的标记及其意义 Safety indications and their meanings
本使用说明书及产品所使用的标记和图案记号是为了您的安全而正确的使用产品,防止您及其他人受到危害和损 害。表示方法机含义如下 This instruction manual and the indications and symbols that are used on the machine itself are provided in order to ensure safe operation of this machine and to prevent accidents and injury to yourself or other people.
安 装 Installation
请让受过培训的技术人员来安装缝纫机。
请委托购买商店货电气专业人员进行电气配线。
缝纫机重量约 50Kg,安装工作必须由两人以上 来完成。
在安装完成前,请不要连接电源,如果误按启动 开关,缝纫机动作会导致受伤。
请在切断电源后,再拔掉电插头。 不然易成为控制箱发生故障的原因。
工业缝纫机的特性之一,因为要在机针和旋梭等运动部件附近进行操作,而这些零部件很容易引起受伤的危险, 所以请在受过培训的人或熟练人员的安全操作知识的指导下,正确的使用本缝纫机。 With industrial sewing machines, it is normal to carry out work while positioned directly in front of moving parts such as the needle and thread take-up, and consequently there is always a danger of injury that can be caused operation before operating the machine so that you will know how to use it correctly.
简述l2switch的处理流程

简述l2switch的处理流程下载温馨提示:该文档是我店铺精心编制而成,希望大家下载以后,能够帮助大家解决实际的问题。
文档下载后可定制随意修改,请根据实际需要进行相应的调整和使用,谢谢!并且,本店铺为大家提供各种各样类型的实用资料,如教育随笔、日记赏析、句子摘抄、古诗大全、经典美文、话题作文、工作总结、词语解析、文案摘录、其他资料等等,如想了解不同资料格式和写法,敬请关注!Download tips: This document is carefully compiled by theeditor.I hope that after you download them,they can help yousolve practical problems. The document can be customized andmodified after downloading,please adjust and use it according toactual needs, thank you!In addition, our shop provides you with various types ofpractical materials,such as educational essays, diaryappreciation,sentence excerpts,ancient poems,classic articles,topic composition,work summary,word parsing,copy excerpts,other materials and so on,want to know different data formats andwriting methods,please pay attention!简述OpenDaylight L2Switch的处理流程OpenDaylight(ODL)是一个开源的软件定义网络(SDN)控制器平台,它提供了丰富的功能,包括二层(L2)交换服务。
BOPPPS_教学模式在专业课教学中的探索与实践

个小组的学习成效。 当然,BOPPPS 作为一种新型的
课堂教学设计模式,必然需要教师在实践中不断总
结、迭代、完善,最终能达到越来越好的教学效果。
5 结语
综上所述,坚持秉承立德树人理念,全面深化“ 三
全育人” 综合改革,基于 BOPPPS 线上线下混合式教
参与式教学,力求学生能在课堂上充分发挥主观能动
BOPPPS 与线下线上相结合的混合式教学模式,有效
一课堂教学效果,激发学生的学习热情,激发学生对
后续专业核心课程的学习兴趣,加强线下与班主任协
同育人作用,鼓励实践,拓展课后第二课堂的延伸,以
期在落实好教学实践任务的基础上,有效达成全员、
全过程、全方位的三全育人目标,最终为国家和社会
学习习惯逐步养成 ( 见图 2) ; 学生综合素质普 遍提
高,校内外活动的参与积极性高,比如省级职业技能比
赛、1+X 证书考核、大学生创新创业训练项目等。 同时
在教师的教科研能力方面也形成了反噬效果,获得江
苏省级教学比赛二等奖,江苏省职业技能大赛三等级,
江苏省创新创业训练项目,市级职业教育课程教学优
无线互联科技·研究创新
要环节,学生可以通过这个环节更了解自己对知识的
掌握情况,而教师可以进一步反思,及时调整教学设
计,完成二次备课。
2. 6 总结
总结部分主要包含课堂和课后两个环节。 第一
个环节:课堂的最后通过学生自主归纳这节课的知识
点,理清知识脉络,总结当堂课自己已掌握的知识点
和学习中有困难的点。 在此基础上教师进一步就重
学模式课程教育体系建设,是我国未来高职教育人才
培养和专业人才教育能力的关键。 以问题为导向,运
维泰克2客户信-clsi折点性能参数补充说明书

VITEK 2客户信编号: CSN 4757-2尊敬的生物梅里埃用户:2020年7月, 生物梅里埃发布了客户信CSN-4757通知VITEK®2用户梅里埃已经完成了气单胞菌和弧菌多个抗生素CLSI折点的验证工作。
如果您在2020年7月收到通知后已经更新了折点, 我们抱歉地通知您当时发布的客户信表2性能参数部分存在笔误。
此次客户信的表2已经进行了更新,为便于识别,更新部分用黄色高亮显示。
该客户信其它部分同此前版本保持一致。
该评估使终端用户可以在VITEK® 2软件中应用CLSI折点。
表1中的CLSI折点都已经成功验证,均满足可接受标准,可用于患者或其它菌株测试,某些情况下需要增加一些限制信息.为了应用这些折点,需要在AES中创建自定义参数。
请参考VITEK® 2软件用户手册(修改折点部分)中的详细信息。
这些折点会被整合进未来新版本VITEK® 2软件Global CLSI-based参数集。
表2提供了应用CLSI折点下这些抗菌药物的性能参数信息。
之前出版的VITEK® 2文档尚未公布这些性能参数信息。
假如您选择实施这些CLSI折点,请留存该客户信。
附录1:举例如何创建高级报告工具(BIOART)规则,用于管理该客户信5-8页中的局限。
做为我们持续改善项目的一部分,梅里埃致力于提升产品质量,功能和易用性。
感谢您选择使用VITEK® 2系统,如果您有任何问题,请随时联系您当地的生物梅里埃代表。
此致敬礼梅里埃诊断产品(上海)有限公司2022年5月10日bioMérieux (Shanghai) Company Limited/梅里埃诊断产品(上海)有限公司表1:使用更新后的CLSI折点,表格中抗菌药物性能满足要求bioMérieux (Shanghai) Company Limited/梅里埃诊断产品(上海)有限公司*以下抗生素/细菌组合的结果存在局限,需要屏蔽报告。
I-9 用户手册说明书

I-9 User Guide Online I-9 & E-VerifyProcessUpdated June 2023Table of ContentsOnline I-9 & E-Verify Process 2 I-9 Compliance 3 Section 1 – Employee Information 4 Accessing the System 11 New Hire Center 13 Section 2 – Employer Review 16 Photo Matching 22 Terminations 33 Special Circumstances 33Online I-9 and E-Verify ProcessAbout Electronic I-9s and E-Verify•Implemented to automate the process of documenting that each new employee is authorized to work in the United States•Complies with mandate from the Governor of Virginia to process all new hires and rehires through E-Verify•E-Verify allows employers to automatically determine eligibility of their employees to work in the United States•Online I-9 Management system is hosted by external vendor•Electronic I-9s are stored in a central database•Eliminates the need to complete a paper I-9 and submit to HRWhat is an I-9?• A form used to document verification of identity and employment eligibility of all employees (both citizen and non-citizen) hired to work in the United States after November 6, 1986•Required to comply with the Federal Immigration Reform and Control Act•Regulated by the U.S. Citizenship and Immigration Services (USCIS) division of Department of Homeland Securities (DHS)Some Penalties for Non-Compliance•Employers who violate the law may be subject to:o Civil fineso Criminal penalties (when there is a pattern or practice of violations)o Debarment from government contractso A court order requiring the payment of back pay to the individualdiscriminated againsto A court order requiring the employer to hire the individual discriminated against•More information is available at: /i-9-central/penaltiesI-9 ComplianceIs an I-9 Required?•Open Banner form PZII9HS for the employee•Does the employee have an E-Verify case number?o If NO, continue with I-9 processo If YES, open Banner form PWIEMPV•Review job start/end dates/last paid date•If there is a break in service or break in pay for more than one year, a new I-9 must be completed•For non-residents, the employment authorization documents could have changed - review carefully•Contact HR with questions if an I-9 is neededPWIEMPVTIPS: You can find the Last Paid Date on page PWIEMPVSection 1: Employee Information•Section 1 should be completed and signed by employee on or before the first day of work•Employee will receive two emails from **********************. One will have the link to the New Hire Center and the other will have the password to login. The password is only valid for the original login.*Please note, wage employees must have a job in Banner before they will be sent to the New Hire Center and receive these email*•Once logged in, employee will need to complete all forms in the New Hire Center before completing section 1 of the I9.Section 1:TIPS:•All fields are required EXCEPT:o Other Nameso Apt. Numbero Email Addresso Telephone Number•If the employee does not have a Middle Name, enter N/A•Foreign nationals without a Social Security number- check the “SSN Applied For”button below the Social Security number fieldTIPS:•Employee attests to citizenship•If number 4, An alien authorized to work until, is selected the new hire should indicate the “authorized to work until date” on the i9. The date should be listed on their form I-20, DS2019, or another form of work authorization.•If someone other than employee prepares section 1 on behalf of employee, thePreparer and/or Translator Certification must be completed•Click Continue to save•Review the data foraccuracy•Scroll to bottom of page•Employee signs the form by checking the attestation box•Employee’s initials must correspond to the name asit was keyed (not casesensitive)•If the employee hasmultiple first namesand/or last names, onlyenter the first, first nameinitial and the first, lastname initial•Click ContinueTIPS:•Print the receipt code page if section 2 will be completed by a remote completer. The remote completer will need the receipt number to pull up the I9.•New Hire will receive an email confirmation once Section 1 has been completed •Scroll to bottom of page to review acceptable documents to present for completingSection 2•Click continue to finish section 1TIPS:•List A document to prove identity and work authorization OR List B document to prove identity AND List C document to prove work authorization• A full list of acceptable documents can be found at https:///i-9-central/form-i-9-acceptable-documents•All documents must be original. Only exception is certified copy of birth certificate •All documents must be unexpired by the first day of work. For Foreign Nationals, Transfer Pending documents may not be used•Must present a document with a photo•Reminder – employee must present original documentation within three business days of starting workGetting access the I9 SystemFor employees needing access to the I9 system for processing purposes, departments need to complete the following steps:•Employer access only – for I9 access, complete the following steps:•Online Banner HR access request form on (https:///vt/prod/vtirm.irm_forms_main.entry) •Login and select Add/Change Administrative System Access•Enter employee’s ID and select Request additional access•Select Human Resources and check the Online I-9 option•Submit electronic form•Print copy for signature approval•Must be signed by employee AND dean, director, or department head•Send a signed copy to the HR Apps Team through the HR Dropbox (The dropbox link is located on )Completing Section 2 of the I9This section focuses on how to search for employees and complete section 2 of the I-9•Click on Login to New Hire CenterConsent to Information Release•Each time an I9 processor logs in, the Consent to Information Release screen will appear. Verify the VT Username and ID number, then click the SharebuttonNew Hire Center Welcome Screen•Click on Search Employee to verify all forms have been completed and Section 2 is ready to be completed•Enter First and Last Name, then press View•Verify Status says Document Complete - Waiting on Section 2 of I9•Click on the NameClick Complete I9•Verify the start date is the first day the employee began working. If the date listed is not the first day of physical work, please update this date.•Enter the VT ID. Do not include dashes•Visa type is not applicable to US Citizen•Select the document(s) presented by employee•Select documents from valid list of options provided in drop down list. The list provided will be based on the citizenship status indicated in Section 1•If employee is terminated before completing I-9, choose that option and continue•Click Continue to save•Examine documents and record verification information•Complete all fields provided•Click Continue to saveTIPS:•Fields may vary depending on documents presented•Click on Sample Document link to view valid examples of selected document type •Do not include dashes in Document number•If there is no Document number, include several zeros• Carefully review all information entered • Check the box stating you have read and agree with certification statement • Click Continue to saveE-Verify Status•Unique case number is assigned to I-9•I-9 verified against SSA and DHS databases•Receive initial status response within seconds•How to proceed depends on E-Verify status. One of the following messages will appear:o Employment authorized▪Employment authorized - with additional verification optional▪Employment authorized - with additional verification requested automaticallyo Photo matching requiredo Current I-9 is not eligible for verificationo SSA or DHS tentative non-confirmation; this status will be handled by the Central HR I9 Coordinators•Temporary initial responses, requiring more time or more steps include: o Initial verification not processed▪Review/Edit employee data (may indicate minor error/typo) o DHS verification in processo SSA or DHS continuanceo DHS referral to SSAo SSA/DHS case incomplete•I-9 wassuccessfullyadded•Next actiondepends onE-Verifyresponse•Always click“View CaseDetails” totakeappropriateaction•E-Verify has assigned a Case Number•Status at bottom of page shows Employment Authorized (If anything other than Employment Authorized or Manual Review is showing, please contact *********) •Case Resolved should be displayed at bottom of page•Logout or click Back to Compliance Center and proceed with another I-9Photo Matching•Required when employee presents any of the following eligibility documents: o U.S. Passport or Cardo I-551 Permanent Resident Card (green card)o I-766 Employment Authorization Document (EAD)•E-Verify requires I-9 administrators to match the photo provided with the one on file with the United States Citizenship and Immigration Services (USCIS)• A securely scanned copy of the photo document must be attached to the electronic I-9 as supporting documentation.•DO NOT ATTACH OTHER DOCUMENTS.Attaching Photos•Securely scan the image•Save the file with a name you will recognize•Attach the scanned image to the electronic I-9•Open the attached document to confirm legibility•Delete the file or encrypt it if retainedo Do not send any scanned documents to HRSECTION 2 – Uploading DocumentsTIPS:• Use List A to select US Passport or US Passport card, Permanent Resident Card, or Employment Authorization Document (EAD).• Attach both the front and back of the card. This can be attached as two separate documents• Click Continue to saveTIPS:• Examine the employee’s document(s) and record verification data • Enter Expiration Date (check box if there is not one)• Click Continue to saveTIPS:• Get started by uploading the image file• Select the Attach File link – Do not click on Upload I9. This will overwrite the currentI9 document in the fileTIPS:• Select document from list of valid options• Scroll to the bottom of the pageTIPS:• Select document from list of valid options• Be sure to use image files in one of the supported formats • Use the Choose File button to select from your computer • Click UploadTIPS:• An image of the attachment appears• Select Correct if this document does not have any errors • Select Incorrect if there are errors presentTIPS:• Notice theUploadStatus nowshows acheck mark• Press theFinishedbuttonTIPS:• E-Verify hascaught upand displaysthe PhotoMatchingstatus• Click viewcase detailsor scroll tothe bottom ofthe pageTIPS:• Verifylegibilityand closethe windowTIPS:• Click thePhotoMatchingbutton toproceed• Compare the photo shown to the photo on the ID cardSelect Yes:• If the photo on the document matches the photo on file• If there is no photograph in the database• Click Continue to proceedSelect No:• If the photo on the ID does not match the database• E-Verify response will be a Tentative Non-Confirmation• Notify *********• Click Continue to proceedSelect No Photo Displayed:• If not photo shows, click the No Photo Displayed button and click ContinueTIPS:• E-Verify has assigned a Case Number • Scroll to the bottom of the page• Make sure the case is closed• I-9 circumstances that may warrant terminationo Employee does not present documentation to complete Section 2 within three business days of the first day of worko Employee refuses to furnish a Social Security Number for E-Verify purposeso Employee elects not to contest a negative E-Verify finding• Complete Section 2 using the option at bottom of the Review and Verification page indicating that employee has terminatedSpecial Circumstances• SSN Applied For:o E-Verify requires employee’s social security number (SSN) on Section 1 in order to for the I9 to be Authorizedo Select the SSN Applied For option in the Employee Information and Verification section for someone who does not yet have a SSN. The I9 will bein a holding status until the SSN is providedo Employee MUST apply for an SSN and provide it to Payroll. Payroll will update the number in the I9 system and will submit to E-verify at that time• Receipts:o Employer may be required to accept a receipt in lieu of the List A, B, or C documento When receipt is presented, check the “Receipt” box next to the type of identification document on Section 2; a copy of the receipt should beattached to the I9Acceptable receipts an employee can present for identification• For Non-residents with a SSN - Always use the Non-everify location at beginning of semester!o Foreign nationals must be updated in the Federal SEVIS database before being processed in E-Verifyo If this is not done, submission to E-Verify needs to be delayed▪If individual’s “Applied for SSN” submission is automatically delayed▪If individual has an SSN, department must manually delay submission using the “non-E-Verify” locationo Complete Section 2 by entering the special non-E-Verify location, “000001”in the Location fieldo HR will follow up with the E-Verify process and updating the location data Directanyquestionsto:**********************。
slides_chapter_18

Figure 1 8 .3 Dat a t ree for aSafeHom e c om ponent
8
Analysis Classes
Analysis classes are derived by examining each use-case A grammatical parse is used to identify candidate classes A UML class diagram is developed for each analysis class
Hale Waihona Puke 11Sequence Diagram
:Room
new cust o mer
:FloorPlan
:Product Component
:Billof Mat erials
FloorPlan Reposit ory
BoM Reposit ory
d e sc ri b e s ro o m * p l a c e s ro o m in f loor plan
10
The Interaction Model
Composed of four elements:
use-cases sequence diagrams state diagrams a user interface prototype Each of these is an important UML notation
Comprehensible—all stakeholders understand the purpose of the package Cohesive—the package addresses functions that are closely related to one another Loosely coupled—functions or classes within the package collaborate with one another, but collaboration outside the package are kept to a minimum. Hierarchically shallow—deep functional hierarchies are difficult to navigate and hard for end-users to understand; therefore, the number of levels within a use-case hierarchy should be minimized whenever possible.
Defensicsuzz测试软件说明说明书
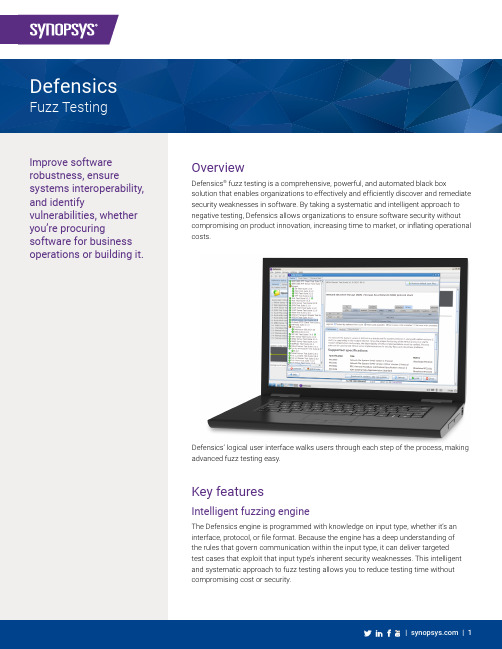
Improve software robustness, ensure systems interoperability, and identify vulnerabilities, whether you’re procuring software for business operations or building it.OverviewDefensics® fuzz testing is a comprehensive, powerful, and automated black box solution that enables organizations to effectively and efficiently discover and remediate security weaknesses in software. By taking a systematic and intelligent approach to negative testing, Defensics allows organizations to ensure software security without compromising on product innovation, increasing time to market, or inflating operational costs.Key featuresIntelligent fuzzing engineThe Defensics engine is programmed with knowledge on input type, whether it’s an interface, protocol, or file format. Because the engine has a deep understanding ofthe rules that govern communication within the input type, it can deliver targetedtest cases that exploit that input type’s inherent security weaknesses. This intelligent and systematic approach to fuzz testing allows you to reduce testing time without compromising cost or security.Defensics’ logical user interface walks users through each step of the process, making advanced fuzz testing easy.• Choose from five new vertical solution bundles: automotive, ICS, IoT, networking, andtelecom. Vertical solution bundles include foundational protocols in addition to protocolsrelevant to that vertical market.Fits into most development life cyclesDefensics contains workflows that enable it to fit almost any environment from atechnological and process standpoint. Whether you employ a traditional SDL or a CIdevelopment life cycle, Defensics brings fuzz testing into development early, allowingyou to catch and remediate vulnerabilities more cost-effectively. Got an unconventionaldevelopment life cycle? Our experienced Professional Services team can help you identifyfuzz testing checkpoints, define fuzz testing metrics, and establish a fuzz testing maturityprogram.It’s not just about fitting into the development process; it’s also about working withsurrounding technologies. API and data export capabilities allow Defensics to share data foradditional reporting and analysis, making Defensics a true plug-and-play fuzzer.Detailed, data-rich reports for efficient remediation• Contextualized logs. Remediation logs detail the protocol path and message sequencesbetween Defensics and the system under test (SUT) to help you identify the trigger andtechnical impact of each vulnerability.• Vulnerability mapping. Defensics maps each vulnerability to industry standards such asCWE and injection type to enhance information discovery and expedite remediation.• Issue re-creation. Defensics narrows the vulnerability trigger to a single test case so youcan re-create the issue and verify the fix.• Remediation packages. Generate encrypted remediation packages for your softwaresuppliers to facilitate secure, collaborative remediation across the supply chain.Scale fuzz testing with automationFrom scanning for the test target to determining the number of layers to connect to,Defensics offers a rich set of APIs for flexible, scalable automation to meet all your needs:• Test single devices• Set up repeatable automation to ensure test plans are followed every time• Reduce testing times with the latest in scalable virtualizationDefensics reports contain messagesequence logs to help users identify theroot cause of an anomalous reaction.Defensics offers automated capabilitiesthroughout the testing process, such asDevice Explorer, to relieve users of theburden of manual configuration.Authentication, Authorization, and Accounting (AAA)• Diameter Client/Server • EAPOL Server • Kerberos Server• LDAPv3 Client/Server • RADIUS Client/Server • TACACS+ Client/Server • MACsec ServerApplication• FIX• JSON Format • Web Application• WebSocket Client/Server • XML SOAP Client/Server • XML File • XMPP Server • AMQP Server • WAMP Server • OWAMP Server • TWAMP Server Automotive *• CAN Bus • CAN FD • DoIP Server • gPTP Server • SOME/IP • SRP ServerCellular Core• BICC/M3UA • GRE• GTP Prime • GTPv0• PMIPv6 Client/Server • SCTP Client/Server • SMPP• SMS (SMPP injection)• SMS (file injection)• MAP • BSSAP • BSSAP+• CAP • INAP • ISUP• MTP3 / M2UA|M2PA • TCAP / SCCP / M3UA •SBI Client/ServerDefensics Fuzz Testing | Test Suite CatalogCore IP• DHCP/BOOTP Client/Server • DHCPv6 Client/Server • DNS Client/Server • FTP Client/Server • HTTP Client/Server • HTTP/2 Client/Server • HTTP/3 Server • ICAP Server •IPv4 Package–ARP Client/Server –ICMP –IGMP –IPv4–TCP for IPv4 Client/Server •IPv6 Package –ICMPv6 –IPv6–TCP for IPv6 Client/Server • SOCKS Client/Server • Multicast DNS• PPP over L2TP Client • PPPoEEmail• IMAP4 Client/Server • MIME• POP3 Server•SMTP Client/ServerGeneral Purpose• SDK Express• Universal ASN.1 BER • Universal FuzzerICS *• 60870-5-104 (iec104) Client/Server • 61850/Goose/SV• 61850/MMS Client/Server • BACNET • CIP Server • COAP Server• DNP3 Client/Server • MQTT Client/Server • Modbus Master • Modbus PLC • OPC UA Server • Profinet DCP• Profinet PTCP Client/Server • DLMS/COSEM Client/Server •ISASecure Testing SolutionIoT *• Thread • BT• Wi-Fi AP • gRPC •ZigbeeLink Management• LACP (802.3ad)• STP/RSTP/MSTP/ESTPMedia• Archives Package–GZIP –JAR –ZIP• Audio Package–MP3–MPEG4 (M4A/MP4) –OGG –WAV–Windows Media (WMA/WMV)• Images Package–GIF –JPEG –PNG –TIFF• Video Package–H.264 File Suite –H.264 RTP Format –MPEG2-TS–MPEG4 (M4A/MP4) –OGG–Windows Media (WMA/WMV)Medical• DICOM Server • HL7v2 Server• FHIR Client/ServerMetro Ethernet• BFD• CFM (802.1ag, Y.1731)• E-LMI (MEF-16)• Ethernet (802.3, 802.1Q)• GARP (802.1D)• LLDP (802.1AB)• OAM (802.3ah)• PBB-TE Server•Synchronous Ethernet (ESMC)Networking*• BGP• SNMP• IPv4/IPv6• SIP• Metro EthernetPublic Key Infrastructure (PKI)• CMPv2 Client/Server• CSRRemote Management• CWMP (TR-69) ACS• CWMP (TR-69) CPE• IPMI Server• NETCONF• PCP Server• SNMP trap• SNMPv2c Server• SNMPv3 Server• SSHv1 Server• SSHv2 Server• Syslog• TFTP Server• Telnet ServerRouting• BGP4+ Client/Server• IS-IS• LDP• MPLS Server• MSDP• OSPFv2• OSPFv3• Openflow controller• Openflow switch• PIM-SM/DM• RIP• RIPng• RSVP• TRILL Server• VRRP• COPS Client/Server Telecom*• 5G• SMS• Pre-5GTime Synchronization• IEEE1588 PTP Client/Server• NTP Client/ServerUniversal Plug and Play• UPnP Package–UPnP Multicast Eventing–UPnP SOAP–UPnP SSDP Control Point–UPnP SSDP DeviceVoIP• H.323 Client/Server• H.248 GW Binary/Text• H.248 MGC Binary/Text• MGCP Server• MSRP Server• RTP/RTCP/SRTP• RTSP Client/Server• SIP UAC• SIP UAS (+TT)• SIP-I Server• STUN Client/Server• TURN Client/Server• SigComp ServerVPN• DTLS Client/Server• IKEv2 Client/Server• IPSec• ISAKMP/IKEv1 Client/Server• L2TPv2/v3 Client/Server• OCSP Client/Server• SCEP• SSTP• TLS/SSL Client/Server• X.509v3 Certificates• VXLANWireless• Zigbee Package–FuzzBox Zigbee APS–FuzzBox Zigbee MAC–FuzzBox Zigbee NWK• Thread package–FuzzBox Thread 6LoWPAN–FuzzBox Thread MAC• Bluetooth LE Package–ATT Client/Server–Advertisement–HOGP Host–Health–L2CAP Server–LL Peripheral–Profiles–SMP Client/Server• Bluetooth Package–A2DP–AVRCP–BNEP–HFP AG/Unit–HSP AG/Unit–L2CAP–MAP Client–OBEX-Server–PBAP Client–RFCOMM–SDP• Wi-Fi AP Package–802.11 WLAN AP–802.11 WPA AP–802.11 WPA3 AP• Wi-Fi Client Package–802.11 WLAN Client–802.11 WPA Client–802.11 WPA3 Client5G technology• GTPv2-C Client/Server• S1AP/NAS Client/Server• GTPv1 Client/Server• E1AP Client/Server• NGAP/NAS Client/ServerMonitoring and engine capabilities Instrumentation• Valid case• Syslog• Agent• SNMP• Custom scripting at each testing executionSafeGuard checkers• Amplification• Authentication bypass• Blind LDAP injection• Blind SQL injection• Certificate validation• Compressed signer’s name in RRSIG record • Cross-site request forgery• Cross-site scripting• ECDH Public Key validation• Extra cookie compared to valid case• Heartbleed• Information leakage• Insufficient randomness• LDAP injection in response• Malformed HTTP• Remote execution• SQL injection in response• SMP insecure pairing parameters• Unexpected data• Unprotected credentials• Weak cryptographyAnomaly categories• ASN.1/BER anomalies• Credential anomalies• Deep packet inspection• EICAR antivirus test file• GTUBE (generic test for unsolicited bulkemail)• Control plane injection anomalies• Integer anomalies• Network address anomalies• Overflow anomalies• Underflow anomaliesNote: We add test suites frequently. Pleasecontact us for the latest list.。
ISO、IEC29119SoftwareTesting(英文版)PPT(共24页)

Organisational Test Process
Develop test specification
Draft Test Specification
Gain consensus on test
specification
Approved Test Specification
[Major revision required]
Testing vocabulary
Part 2: Testing Processes
Organisational Test Proses
Static Test Processes
Dynamic Test Processes
Instantiating Testing Processes
ISO 29119 – Scope & Structure
Part 1 Concepts & Vocabulary
BS 7925-1
Part 4 Testing Techniques
BS 7925-2
Part 2 Processes
BS 7925-2 IEEE 1008
Part 3 Documentation
IEEE 829
Part 1: Concepts & Vocabulary
Software testing concepts
Introduction to software testing Relationship between testing,
development & maintenance Implications of lifecycle models Approaches to testing
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Software Engineering I States and Test Cases
LOs
•Remember the definition of state.
•Get to know the elements of the UML statecharts.•Use UML statecharts to design test cases.
Statecharts
David Harel. Statecharts: a visual formalism for complex systems.
Science of Computer Programming, Vol. 8, pp. 231-274 (1987)
Statecharts
Nested states
State in testing
•Scenario template (Given –When –Then)
–GIVEN: status = OFF //preconditions, the initial state
–WHEN: power() //what caused the transition
–THEN: status = ON //post-conditions, the expected state
–GIVEN: light = YELLOW
–WHEN: nextState()
–THEN: light = RED
Grouping software elements
•Unit
–Smallest grouping that can be executed independently.
•Module
–Smallest grouping of units.
•Component
–Top-level division of a system as defined by its software architecture.
•System
–The entire codebase under study.
V-model
Best coding practices •Write short units of code
•Write simple units of code
•Write code once
•Keep unit interfaces small
•Separate concerns in modules or packages
Good design principles
•Separation of concerns
•DRY (Don’t Repeat Yourself)
•Don’t reinvent the wheel
•YAGNI (You Ain’t Gonna Need It)
•Single Responsibility principle
•KISS (Keep It Simple, Stupid)
•Low coupling, high cohesion
LOs
•Remember the definition of state.
•Get to know the elements of the UML statecharts.•Use UML statecharts to design test cases.。
