Introduction to Algorithms
第1章 算法设计与分析 绪论

• 求gcd(m,n)的原理: (结构化的描述) • 第一步:如果n=0,返回m的值作为结果,结束;否则进 入第二步。 • 第二步:用n除m,余数赋值给r,进入第三步。 • 第三步:将n的值赋给m,将r的值赋给n,返回第一步。
例: gcd(60,24)=? 1-1、m=60, n=24 1-2、60 mod 24=12, r=12, 1-3、m=24, n=12 2-1、24 mod 12=0,r=0 2-2、m=12, n=0 2-3、条件“n=0”满足,返回gcd(m, n)=m=12
• 算法二:连续整数检测法
第一步:将min{m,n}赋值给t。 第二步:m除以t,如果余数为0,进入第三步,否则进入第 四步。 第三步:n除以t,如果余数为0,返回t的值;否则进入第四 步。 第四步:把t的值减1,返回第三步。 例:gcd(60, 24) t=min{60, 24}=24, m=60, n=24 60mod24=12≠0, t=23, 24 mod 23=1 ≠0 t=22, 24 mod 22=2 ≠0 t=21, 24 mod 21=3 ≠0 ….. t=12, 24 mod 12=0, 返回gcd(m, n)=t=12
第1章 绪论
1.1 什么是算法 1.2 算法问题求解基础 1.3 重要问题类型 1.4 基本数据结构 本章小结
1.1 算法的概念
• 没有一个统一的严谨的定义。一般而言, 对于计算机算法的概念是这样描述的:算 法是在有限步骤内求解某一问题所使用的 一组定义明确的指令。 • 本书采用的定义:An algorithm is a sequence of unambiguous instructions for solving a problem=算法是求解某一 问题所使用的一系列清晰的指令。
Algorithms Chapter 1 绪论

怎么处理?
30
The Design and Analysis of Algorithms
Chapter 1 Introduction to Algorithms
What’s an Algorithm?
算法是一系列解决问题的清晰指令,也就是说,能够对 一定规范的输入,在有限时间内获得所要求的输出。
16
The Design and Analysis of Algorithms
算法可以解决哪些问题
找出人类DNA中所有100000种基因,确定构成人类DNA的30亿种化学基 17 对的各种序列。
The Design and Analysis of Algorithms
算法可以解决哪些问题
快速访问和检索互联网数据
The Design and Analysis of Algorithms
例子
• “贝格尔”编排法(Beiger Arrangement) 把参赛队数分一半(参赛队为单数时,最后以“0” 表示形成双数),前一半由1号开始,自上而下写在 左边;后一半的数自下而上写在右边,然后用横线 把相对的号数连接起来。这即是第一轮的比赛。 第二轮将第一轮右上角的编号(“0”或最大的一个代 号数)移到左角上,第三轮又移到右角上,以此类推。 即单数轮次时“0”或最大的一个代号在右上角,双 数轮次时则在左上角。
//使用欧几里得算法计算gcd(m,n) //输入:两个不全为0的非负整数m,n //输出:m,n的最大公约数
28
The Design and Analysis of Algorithms
例子
• “贝格尔”编排法(Beiger Arrangement)
这种编排方法是否完美?
IntroductiontoAlgorithms第三版教学设计

Introduction to Algorithms第三版教学设计一、课程概要1.1 课程名称本课程名称为Introduction to Algorithms,是计算机科学专业必修课程。
1.2 学时安排本课程总共为72学时,每周3学时,共计24周。
1.3 教材《算法导论(原书第3版)》(英文版)(Introduction to Algorithms, Third Edition)。
1.4 教学目的本课程旨在使学生掌握算法与数据结构的基本概念、常用算法设计技巧和分析方法,并培养学生独立思考和解决问题的能力。
1.5 先修课程本课程的先修课程包括数据结构、离散数学、算法分析与设计等。
1.6 课程内容简介本课程包括以下内容:•算法基础知识•分治算法和递归•动态规划•贪心算法•图论算法•字符串匹配•NP完全性理论二、课程教学设计2.1 教学方法本课程采用理论讲授、实验操作、课堂讨论等多种教学方法相结合的方式,重视学生自主学习和动手实践的能力培养。
2.2 教学内容和教学进度本课程的教学内容和教学进度如下:第一讲:算法基础知识讲授主要内容包括算法的概念、算法的正确性和复杂度分析。
第二讲:分治算法和递归讲授主要内容包括分治算法的适用场景、递归的概念和应用。
第三讲:动态规划讲授主要内容包括动态规划的基本思想、常用动态规划算法和实践应用。
第四讲:贪心算法讲授主要内容包括贪心算法的基本思想、贪心算法设计和分析方法。
第五讲:图论算法讲授主要内容包括最短路径算法、最小生成树算法、网络流算法等。
第六讲:字符串匹配讲授主要内容包括朴素算法、KMP算法、Boyer-Moore算法等字符串匹配算法。
第七讲:NP完全性讲授主要内容包括P和NP问题的概念、NP完全性理论、NP问题求解方法等。
2.3 课堂互动与实践本课程还将开展相关实践项目,包括算法设计实验、算法实现与优化、算法竞赛和创新项目等,以培养学生动手实践和解决实际问题的能力。
Introduction_to_Algorithms

和式的界
思考题 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
第一部分 基础知识
2 在学习本篇的内容时,我们建议读者不必一次将这些数学内容全部消化。先浏览 一下这部分的各章,看看它们包含哪些内容,然后直接去读集中谈算法的章节。在阅 读这些章节时,如果需要对算法分析中所用到的数学工具有个更好的理解的话,再回 过头来看这部分。当然,读者也可顺序地学习这几章,以便很好地掌握有关的数学技 巧。 本篇各章的内容安排如下: • 第一章介绍本书将用到的算法分析和设计的框架。 • 第二章精确定义了几种渐近记号,其目的是使读者采用的记号与本书中的一致, 而不在于向读者介绍新的数学概念。 • 第三章给出了对和式求值和限界的方法,这在算法分析中是常常会遇到的。 • 第四章将给出求解递归式的几种方法。我们已在第一章中用这些方法分析了合并 排序,后面还将多次用到它们。一种有效的技术是“主方法”,它可被用来解决 分治算法中出现的递归式。第四章的大部分内容花在证明主方法的正确性,读者 若不感兴趣可以略过。 • 第五章包含了有关集合、关系、函数、图和树的基本定义和记号。这一章还给出 了这些数学对象的一些基本性质。如果读者已学过离散数学课程,则可以略过这 部分内容。 • 第六章首先介绍计数的基本原则,即排列和组合等内容。这一章的其余部分包含 基本概率的定义和性质。
求和公式和性质 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37 线性性质 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38 算术级数 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38 几何级数 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38 调和级数 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39 积分级数与微分级数 . . . . . . . . . . . . . . . . . . . . . . . . . . 39 套迭级数 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39 积 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40 数学归纳法 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41 对项的限界 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42 分解和式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43 积分近似公式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
数据结构经典书籍

数据结构经典书籍摘要:一、数据结构的重要性二、数据结构的经典书籍介绍1.《数据结构与算法分析》2.《大话数据结构》3.《数据结构与算法》4.《算法导论》5.《数据结构与算法之美》三、如何选择适合自己的数据结构书籍四、结论正文:数据结构是计算机科学中至关重要的一个领域,掌握数据结构有助于编写高效、可读和可维护的代码。
在众多数据结构书籍中,有几本被广泛认为是经典之作。
本文将介绍其中的五本,并讨论如何选择适合自己的数据结构书籍。
1.《数据结构与算法分析》(Data Structures and Algorithm Analysis in Java)作者:Mark Allen Weiss这本书以Java 语言为例,详细讲述了数据结构和算法的基本概念、原理和实现。
书中包含大量实例和习题,适合初学者入门。
2.《大话数据结构》作者:程云本书采用轻松幽默的语言和丰富的图解,讲解了数据结构的基本原理和常用算法。
内容通俗易懂,适合编程初学者。
3.《数据结构与算法》(Data Structures and Algorithms)作者:Alfred V.Aho, John E.Hopcroft, and Jeffrey D.Ullman这本书是数据结构和算法的经典教材,详细介绍了各种数据结构及其操作,以及排序、查找等基本算法。
内容较为深入,适合已经掌握基本编程技能的读者。
4.《算法导论》(Introduction to Algorithms)作者:Thomas H.Cormen, Charles E.Leiserson, Ronald L.Rivest, and Clifford Stein本书全面讲述了算法设计与分析的基本概念,涵盖了许多经典算法和数据结构。
书中包含大量实例和习题,适合对算法有一定了解的读者深入学习。
5.《数据结构与算法之美》(The Art of Computer Programming, Volume 1: Fundamental Algorithms)作者:Donald E.Knuth本书是计算机编程艺术的卷一,讲述了计算机科学的基本算法。
MIT麻省理工学院 算法导论公开课 Problem Set 4 solution
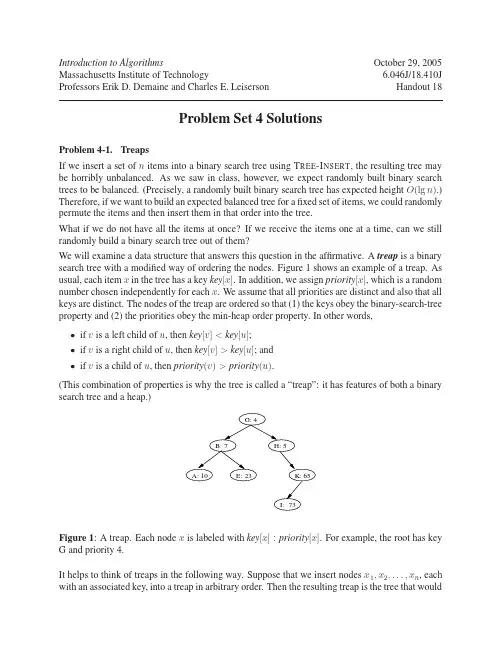
Introduction to Algorithms October 29, 2005 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik D. Demaine and Charles E. Leiserson Handout 18Problem Set 4 SolutionsProblem 4-1. TreapsIf we insert a set of n items into a binary search tree using T REE-I NSERT, the resulting tree may be horribly unbalanced. As we saw in class, however, we expect randomly built binary search trees to be balanced. (Precisely, a randomly built binary search tree has expected height O(lg n).) Therefore, if we want to build an expected balanced tree for a fixed set of items, we could randomly permute the items and then insert them in that order into the tree.What if we do not have all the items at once? If we receive the items one at a time, can we still randomly build a binary search tree out of them?We will examine a data structure that answers this question in the affirmative. A treap is a binary search tree with a modified way of ordering the nodes. Figure 1 shows an example of a treap. As usual, each item x in the tree has a key key[x]. In addition, we assign priority[x], which is a random number chosen independently for each x. We assume that all priorities are distinct and also that all keys are distinct. The nodes of the treap are ordered so that (1) the keys obey the binary-search-tree property and (2) the priorities obey the min-heap order property. In other words,•if v is a left child of u, then key[v]<key[u];•if v is a right child of u, then key[v]>key[u]; and•if v is a child of u, then priority(v)>priority(u).(This combination of properties is why the tree is called a “treap”: it has features of both a binary search tree and a heap.)Figure 1: A treap. Each node x is labeled with key[x]:p riority[x]. For example, the root has key G and priority 4.It helps to think of treaps in the following way. Suppose that we insert nodes x1,x2,...,x n, each with an associated key, into a treap in arbitrary order. Then the resulting treap is the tree that wouldhave been formed if the nodes had been inserted into a normal binary search tree in the order given by their (randomly chosen) priorities. In other words, priority[x i]<priority[x j]means that x i is effectively inserted before x j.(a) Given a set of nodes x1,x2,...,x n with keys and priorities all distinct, show that thereis a unique treap with these nodes.Solution:Prove by induction on the number of nodes in the tree. The base case is a tree withzero nodes, which is trivially unique. Assume for induction that treaps with k−1orfewer nodes are unique. We prove that a treap with k nodes is unique. In this treap, theitem x with minimum priority must be at the root. The left subtree has items with keys<key[x]and the right subtree has items with keys >key[x]. This uniquely defines theroot and both subtrees of the root. Each subtree is a treap of size ≤k−1, so they areunique by induction.Alternatively, one can also prove this by considering a treap in which nodes are inserted in order of their priority. Assume for induction that the treap with the k−1nodes with smallest priority is unique. For k=0t his is trivially true. Now considerthe treap with the k nodes with smallest priority. Since we know that the structureof a treap is the same as the structure of a binary search tree in which the keys areinserted in increasing priority order, the treap with the k nodes with smallest priorityis the same as the treap with the k−1nodes with smallest priority after inserting thek-th node. Since BST insert is a deterministic algorithm, there is only one place thek-th node could be inserted. Therefore the treap with k nodes is also unique, provingthe inductive hypothesis.(b) Show that the expected height of a treap is O(lg n), and hence the expected time tosearch for a value in the treap is O(lg n).Solution: The idea is to realize that a treap on n nodes is equivalent to a randomlybuilt binary search tree on n nodes. Recall that assigning priorities to nodes as theyare inserted into the treap is the same as inserting the n nodes in the increasing orderdefined by their priorities. So if we assign the priorities randomly, we get a randomorder of n priorities, which is the same as a random permutation of the n inputs, sowe can view this as inserting the n items in random order.The time to search for an item is O(h)where h is the height of the tree. As we saw inlecture, E[h]=O(lg n). (The expectation is taken over permutations of the n nodes,i.e., the random choices of the priorities.)Let us see how to insert a new node x into an existing treap. The first thing we do is assign x a random priority priority[x]. Then we call the insertion algorithm, which we call T REAP-I NSERT, whose operation is illustrated in Figure 2.(e) (f)Figure 2: Operation of T REAP-I NSERT. As in Figure 1, each node x is labeled with key[x]: priority[x]. (a) Original treap prior to insertion. (b) The treap after inserting a node with key C and priority 25. (c)–(d) Intermediate stages when inserting a node with key D and priority 9.(e) The treap after insertion of parts (c) and (d) is done. (f) The treap after inserting a node with key F and priority 2.(c) Explain how T REAP-I NSERT works. Explain the idea in English and give pseudocode.(Hint: Execute the usual binary search tree insert and then perform rotations to restorethe min-heap order property.)Solution: The hint gives the idea: do the usual binary search tree insert and thenperform rotations to restore the min-heap order property.T REAP-I NSERT (T,x)inserts x into the treap T(by modifying T). It requires that xhas defined key and priority values. We have used the subroutines T REE-I NSERT,R IGHT-R OTATE, and R IGHT-R OTATE as defined in CLRS.T REAP-I NSERT (T,x)1T REE-I NSERT (T,x)2 while x =root[T]and priority[x]<priority[p[x]]3 do if x=left[p[x]]4 then R IGHT-R OTATE (T,p[x])5 else L EFT-R OTATE (T,p[x])Note that parent pointers simplify the code but are not necessary. Since we only needto know the parent of each node on the path from the root to x(after the call toT REE-I NSERT), we can keep track of these ourselves.(d) Show that the expected running time of T REAP-I NSERT is O(lg n). Solution:T REAP-I NSERT first inserts an item in the tree using the normal binary search treeinsert and then performs a number of rotations to restore the min-heap property.The normal binary-search-tree insertion algorithm T REE-I NSERT always places thenew item at a new leaf of tree. Therefore the time to insert an item into a treap isproportional to the height of a randomly built binary search tree, which as we saw inlecture is O(lg n)in expectation.The maximum number of rotations occurs when the new item receives a priority lessthan all priorities in the tree. In this case it needs to be rotated from a leaf to the root.An upper bound on the number of rotations is therefore the height of a randomly builtbinary search tree, which is O(lg n)in expectation. (We will see that this is a fairlyloose bound.) Because each rotation take constant time, the expected time to rotate isO(lg n).Thus the expected running time of T REAP-I NSERT is O(lg n+lg n)=O(lg n).T REAP-I NSERT performs a search and then a sequence of rotations. Although searching and rotating have the same asymptotic running time, they have different costs in practice. A search reads information from the treap without modifying it, while a rotation changes parent and child pointers within the treap. On most computers, read operations are much faster than write operations. Thus we would like T REAP-I NSERT to perform few rotations. We will show that the expected number of rotations performed is bounded by a constant (in fact, less than 2)!(a) (b)Figure 3: Spines of a binary search tree. The left spine is shaded in (a), and the right spine is shaded in (b).In order to show this property, we need some definitions, illustrated in Figure 3. The left spine of a binary search tree T is the path which runs from the root to the item with the smallest key. In other words, the left spine is the maximal path from the root that consists only of left edges. Symmetrically, the right spine of T is the maximal path from the root consisting only of right edges. The length of a spine is the number of nodes it contains.(e) Consider the treap T immediately after x is inserted using T REAP-I NSERT. Let Cbe the length of the right spine of the left subtree of x. Let D be the length of theleft spine of the right subtree of x. Prove that the total number of rotations that wereperformed during the insertion of x is equal to C+D.Solution: Prove the claim by induction on the number of rotations performed. Thebase case is when x is the parent of y. Performing the rotation so that y is the new rootgives y exactly one child, so C+D=1.Assume for induction that the number of rotations k performed during the insertionof x equals C+D. The base case is when 0 rotations are necessary and x is insertedas a leaf. Then C+D=0. To prove the inductive step, we show that if after k−1rotations C+D=k−1, then after k rotations C+D=k. Draw a picture of aleft and right rotation and observe that C+D increases by 1 in each case. Let y bethe parent of x, and suppose x is a left child of y. After performing a right rotation, ybecomes the right child of x, and the previous right child of x becomes the left childof y. That is, the left spine of the right subtree of x before the rotation is tacked onto y, so the length of that spine increases by one. The left subtree of x is unaffectedby a right rotation. The case of a left rotation is symmetric. Therefore after one morerotation C+D increases by one and k=C+D, proving the inductive hypothesis.We will now calculate the expected values of C and D. For simplicity, we assume that the keys are 1,2,...,n. This assumption is without loss of generality because we only compare keys.�For two distinct nodes x and y , let k = key [x ]and i = key [y ], and define the indicator random variableX 1 if y is a node on the right spine of the left subtree of x (in T ),i,k =0 otherwise .(f) Show that X i,k =1if and only if (1) priority [y ]> priority [x ], (2) key [y ]< key [x ], and(3) for every z such that key [y ]< key [z ]< key [x ],we have p riority [y ]< priority [z ].Solution:To prove this statement, we must prove both directions of the “if and only if”. Firstwe prove the “if” direction. We prove that if (1) priority [y ]> priority [x ], (2) key [y ]<key [x ], and (3) for every z such that key [y ]< key [z ]< key [x ]are true, priority [y ]< priority [z ], then X i,k =1. We prove this by contradiction. Assume that X i,k =0. That is, assume that y is not on the right spine of the left subtree of x . We show thatthis leads to a contradiction. If y is not on the right spine of the left subtree of x ,it could be in one of three places:1. Suppose y is in the right subtree of x . This contradicts condition (2) becausekey [y ]< key [x ].2. Suppose y is not in one of the subtrees of x . Then x and y must share somecommon ancestor z . Since key [y ]< key [x ], we know that y is in the left subtreeof z and x is in the right subtree of z and key [y ]< key [z ] < key [x ]. Since y isbelow z in the tree, priority [z ]< priority [x ]and priority [z ]< priority [y ]. Thiscontradicts condition (3).3. Suppose that y is in the left subtree of x but not on the right spine of the leftsubtree of x . This implies that there exists some ancestor z of y in the left subtreeof x such that y is in the left subtree of z . Hence key [y ]< key [z ]< key [x ]. Sincez is an ancestor of y , priority [z ]< priority [y ], which contradicts condition (3).All possible cases lead to contradictions, and so X i,k =1.Now for the “only if” part. We prove that if X i,k =1, then statements (1), (2), and (3) are true. If X i,k =1, then y is in the right spine of the left subtree of x . Since y is ina subtree of x , y must have been inserted after x ,so p riority [y ]> priority [x ], proving(1). Since y is in the left subtree of x , key [y ]< key [x ], proving (2). We prove (3) by contradiction: suppose that X i,k =1and there exists a z such that key [y ]< key [z ]< key [x ]and priority [z ]< priority [y ]. In other words, z was inserted before y . There arethree possible cases that satisfy the condition key [z ]< key [x ]:1. Suppose z is in the right spine of the left subtree of x .For y to be inserted into theright spine of the left subtree of x , it will have to be inserted into the right subtreeof z . Since key [y ]< key [z ], this leads to a contradiction.2. Suppose z is in the left subtree of x but not in the right spine. This implies thatz is in the left subtree of some node z in the right spine of x . Therefore for y tobe inserted into the right spine of the left subtree of x , it must be inserted into theright subtree of z . This leads to a contradiction by reasoning similar to case 1.3. Suppose that z is not in one of the subtrees of x . Then z and x have a commonancestor z such that z is in the left subtree of z and x is in the right subtree of x .This implies key [z ] < key [z ] < key [x ]. Since key [y ]< key [z ]< key [z ], y cannotbe inserted into the right subtree of z . Therefore it cannot be inserted in a subtreeof x , which is a contradiction.Therefore there can be no z such that key [y ] < key [z ] < key [x ] and priority [z ] < priority [y ]. This proves statement (3). We have proven both the “if” and “only if” directions, proving the claim.(g) Show that(k − i − 1)! 1 Pr {X i,k =1} == . (k − i +1)! (k − i +1)(k − i )Solution: We showed in the previous part that X i,k =1if and only if the priorities of the items between y and x are ordered in a certain way. Since all orderings are equally likely, to calculate the probability we count the number of permutations of priorities that obey this order and divide by the number of total number of priority permutations. We proved in (e) that whether or not X i,k =1depends only on the relative ordering of the priorities of y , x , and all z such that key [y ] < key [z ] < key [x ]. Since we assumed that the keys of the items come from {1,...,n }, the keys of the items in question are i,i +1,i +2,...,k − 1,k . There are (k − i +1)!permutations of the priorities of these items. Of these permutations, the ones for which X i,k =1are those where i has minimum priority, k has the second smallest priority, and the priorities of the remaining k − i − 1 items follow in any order. There are (k − i − 1)! of these permutations. Thus the probability that we get a “bad” order is (k −i −1)!/(k −i +1)!= 1/(k − i )(k − i +1).(h) Show thatk −1 � 1 1 E [C ]= =1− . j (j +1)k j =1 Solution:X For a node x with key k , E [C ]is the expected number of nodes in the right spine of the left subtree of x . This equals the sum of the expected value of the random variables i,k for all i in the tree. Since X i,k =0for all nodes i ≥ k , we only need to consider i <k .� � � k −1 �k −1 � E [C ]=E [X i,k ]=E X i,k i =1 i =1 k −1 =Pr {X i,k =1}i =1 k −1 � 1 =(k − i )(k − i +1) i =1 k −1 � 1= j (j +1)j =1 1To simplify this sum, observe that j (j 1+1) = j +1−j = − 1 . Therefore the sumj (j +1) j j +1 telescopes and we have 1 E [C ]=1− . kIf you didn’t see this, you could have proven that the equationk −1 � 1 1 =1− j (j +1)k j =1 holds by induction on k . In the proving the inductive hypothesis you might have 11discovered 1 − = .j j +1 j (j +1)(i) Use a symmetry argument to show that1 E [D ]=1− . n − k +1Solution: The idea is to consider the treap produced if the ordering relationship amongthe keys is reversed. That is, for all items x , leave priority [x ]unchanged but replacekey [x ]with n − key [x ]+1.Let T be the binary tree we get when inserting the items (in increasing order of priority) using the original keys. Once we remap the keys and insert them into a newbinary search tree, we get a tree T whose shape is the mirror image of the shape ofT . (reflected left to right). Consider the item x with key k in T and therefore has key n − k +1 i n T . The length of the left spine of x ’s right subtree in T has becomethe length of the right spine of x ’s left subtree in T . We know by part (g) that the expected length of the right spine of a left subtree of a node y is 1− 1/idkey [y ],so the expected length of the right spine of the left subtree of x in T is 1− 1/(n − k +1), which means that 1 E [D ]=1− . n − k +1(j) Conclude that the expected number of rotations performed when inserting a node into a treap is less than 2.Solution:11 E [number of rotations ]= E [C +D ]=E [C ]+E [D ]=1− +1− k n − k +1 ≤ 1+1=2. Problem 4-2. Being balancedCall a family of trees balanced if every tree in the family has height O (lg n ), where n is the number of nodes in the tree. (Recall that the height of a tree is the maximum number of edges along any path from the root of the tree to a leaf of the tree. In particular, the height of a tree with just one node is 0.)For each property below, determine whether the family of binary trees satisfying that property is balanced. If you answer is “no”, provide a counterexample. If your answer is “yes”, give a proof (hint: it should be a proof by induction). Remember that being balanced is an asymptotic property, so your counterexamples must specify an infinite set of trees in the family, not just one tree. (a) Every node of the tree is either a leaf or it has two children.Solution: No. Counterexample is a right chain, with each node having a leaf hanging off to the left(b) The size of each subtree can be written as 2k − 1, where k is an integer (k is not the same for each subtree).Solution: Yes.Consider any subtree with root r . We know from the condition that the size of this subtree is 2k 1 − 1. We also know that the size of the subtree rooted at the left child of r is 2k 2 − 1, and the size of the subtree rooted at the right child of r is 2k 3 − 1. But the size of the subtree at r is simply the node r together with the nodes in the left and right subtrees. This leads to the equation 2k 1 − 1=1+(2k 2 − 1)+(2k 3 − 1),or 2k 1 =2k 2 +2k 3. Now we show that k 2 =k 3. This is easy to see if you consider the binary representations of k 1, k 2, and k 3.Otherwise, if we assume WLOG that k 2 ≤ k 3, then we have 2k 1−k 2 =1+2k 3−k 2. 2Now, the only pair of integer powers of 2 that could satisfy this equation are 21 and 0 . Thus k 3 − k 2 =0,or k 2 =k 3, and the left and right subtrees of r have an equal number of nodes. It follows that the tree is perfectly balanced.(c) There is a constant c>0such that, for each node of the tree, the size of the smallerchild subtree of this node is at least c times the size of the larger child subtree.Solution:Yes1. The proof is by induction. Assume that the two subtrees of x with n nodes in itssubtree has two children y and z with subtree sizes n1 and n2. By inductive hypothesis,the height of y’s subtree is at most d lg n1 and the height of z’s subtree is at most d lg n2for some constant d. We now prove that the height of x’s subtree is at most d lg n.Assume wlog that n1 ≥n2. Therefore, by the problem statement, we have n2 ≥cn1.Therefore, we have n=n1 +n2 +1≥(1+c)n1 +1≥(1+c)n1 and the height hof x’s subtree is d lg n1 +1≤d lg(n/(c+1))+1≤d lg n−d lg(1+c)+1≤d lg nif d lg(1+c)≥1. Therefore, for sufficiently large d, the height of a tree with n nodesis at most d lg n.(d) There is a constant c such that, for each node of the tree, the heights of its childrensubtrees differ by at most c.Solution: Yes1. Let n(h)be the minimum number of nodes that a tree of height h thatsatisfies the stated property can have. We show by induction that n(h)≥(1+α)h−1,for some constant 0<α≤1. We can then conclude that for a tree with n nodes,h≤log1+α(n+1)=O(lg n).For the base case, a subtree of height 0has a single node, and 1≥(1+α)0 −1forany constant α≤1.In the inductive step, assume for all trees of height k<h, that the n(k)≥(1+α)k−1.Now consider a tree of height h, and look at its two subtrees. We know one subtreemust have height h−1, and the other must have height at least h−1−c. Therefore,we known(h)≥n(h−1)+n(h−1−c)+1.Using the inductive hypothesis, we getn(h) ≥(1+α)h−1 −1+(1+α)h−1−c−1+1≥2(1+α)h−1−c−1.Suppose we picked αsmall enough so that (1+α)<21/(c+1). Then (1+α)c+1 <2.Therefore, we getn(h)≥2(1+α)h−1−c−1≥(1+α)h−1.1Note that in this problem we assume that a nil pointer is a subtree of size 0, and so a node with only one child has two subtrees, one of which has size 0. If you assume that a node with only one child has only one subtree, then the answer to this problem part is “no”.�11Handout18: Problem Set4SolutionsTherefore, we satisfy the inductive hypothesis.Note that if we plug this value for αback into h≤log1+α(n+1),we getlg(n+1)h≤≤(c+1)l g(n+1).lg(1+2c+1)(e) The average depth of a node is O(lg n). (Recall that the depth of a node x is thenumber of edges along the path from the root of the tree to x.)Solution: No.√Consider a tree with n−n nodes organized as a complete binary tree, and the other √ √n nodes sticking out as a chain of length n from the balanced tree. The height of√√√the tree is lg(n−n)+n=Ω(n), while the average depth of a node is at most�√√ √(1/n)n·(n+lg n)+(n−n)·lg n√√=(1/n)(n+n lg n+n lg n−nlgn)=(1/n)(n+n lg n)=O(lg n)√Thus, we have a tree with average node depth O(lg n), but height Ω(n).。
introduction-to-algorithms-13144
Data Structures
The IP packet forwarding is a Data Structure problem! Efficiency, scalability is very important.
Similarly, how does Google find the documents matching your query so fast? Uses sophisticated algorithms to create index structures, which are just data structures. Algorithms and data structures are ubiquitous. With the data glut created by the new technologies, the need to organize, search, and update MASSIVE amounts of information FAST is more severe than ever before.
Role of Algorithms in Modern World
Enormous amount of data Network traffic (telecom billing, monitoring) Database transactions (Sales, inventory) Scientific measurements (astrophysics, geology) Sensor networks. RFID tags Radio frequency identification (RFID) is a method of remotely storing and retrieving data using devices called RFID tags. Bioinformatics (genome, protein bank)
有关于计算机科学与技术专业的书籍
有关于计算机科学与技术专业的书籍English Answer:1. Introduction to Algorithms by Thomas H. Cormen, Charles E. Leiserson, Ronald L. Rivest, and Clifford Stein: This classic textbook provides a comprehensive introduction to the fundamental algorithms used in computer science. It covers topics such as sorting, searching, dynamic programming, and graph algorithms.2. The Art of Computer Programming by Donald E. Knuth: This multi-volume series is considered a masterpiece of computer science literature. It covers a wide range of topics, including algorithms, data structures, and programming techniques.3. Computer Architecture: A Quantitative Approach by John L. Hennessy and David A. Patterson: This textbook provides a thorough introduction to computer architecture, covering topics such as processor design, memory systems,and I/O devices.4. Operating Systems: Three Easy Pieces by Remzi H. Arpaci-Dusseau and Andrea C. Arpaci-Dusseau: This textbook provides a concise and accessible introduction to operating systems, covering topics such as processes, threads, memory management, and file systems.5. Computer Networks: A Top-Down Approach by James F. Kurose and Keith W. Ross: This textbook provides a comprehensive introduction to computer networks, covering topics such as network protocols, routing algorithms, and network security.6. Database Systems: The Complete Book by HectorGarcia-Molina, Jeffrey D. Ullman, and Jennifer Widom: This textbook provides a comprehensive introduction to database systems, covering topics such as data models, query processing, and transaction management.7. Programming Language Concepts by Robert W. Sebesta: This textbook provides a comprehensive introduction toprogramming language concepts, covering topics such as syntax, semantics, and programming paradigms.8. Software Engineering: A Practitioner's Approach by Roger S. Pressman: This textbook provides a practical introduction to software engineering, covering topics such as software development process models, software design principles, and software testing techniques.9. Artificial Intelligence: A Modern Approach by Stuart Russell and Peter Norvig: This textbook provides a comprehensive introduction to artificial intelligence, covering topics such as search algorithms, machine learning, and natural language processing.10. Machine Learning by Tom M. Mitchell: This textbook provides a comprehensive introduction to machine learning, covering topics such as supervised learning, unsupervised learning, and reinforcement learning.Chinese Answer:1. 算法导论(Thomas H. Cormen、Charles E. Leiserson、Ronald L. Rivest、Clifford Stein),这本经典教材全面介绍了计算机科学中使用的基本算法。
如何成为一个程序员
如何成为一个程序员:想成为一个游戏程序员需要有以下资料疯狂代码 / ĵ:http://GameDevelopment/Article36086.html、书籍:算法和数据结构:数据结构(C语言版)——严蔚敏、吴伟民 清华出版社我觉得其配套习题集甚至比原书更有价值每个较难题都值得做下Introduction to Algorithms第 2版 中文名算法导论有关算法标准学习教材和工程参考手册在去年CSDN网站WebSite上其翻译版竟然评为年度 2十大技术畅销书同时员杂志上开设了“算法擂台”栏目这些溯源固本举动不由得使人对中国现今浮躁不堪所谓“IT”业又产生了线希望这本厚厚书幸亏打折我才买得起虽然厚达千页但其英文通俗晓畅内容深入浅出可见经典的作往往比般水准书还耐读还能找到MIT视频教程第节课那个老教授嘻皮笑脸后面就是长发助教上课了C语言名题精选百则 窍门技巧篇——冼镜光 机械工业出版社作者花费年时间搜集了各种常见C段极具窍门技巧性编程法其内容都是大有来头而且给出了详细参考资料如个普通Fibonacci数就给出了非递归解、快速算法、扩充算法等步步深入直至几无油水可榨对于视速度如生命连个普通浮点数转化为整数都另辟蹊径以减少CPU cycle游戏员怎可不看?计算机算法基础(第 2版)—— 佘祥宣等 华中科大出版社我看到几个学校研究生拿它作教材(研究生才开算法太开玩笑了吧)这本书薄是薄了点用作者话来说倒也“精辟”其实此书是Fundamentals of Computer Algorithms缩写版不过原书出版太久了反正我是没找到The Art of Computer ProgrammingVolume 1-3作者Donald E. Knuth是我心目中和冯.诺依曼、Dijkstra、Shannon并列 4位大师这本书作者从读大学本科时开始写直写到博士时十年磨剑足见其下足了功夫可作为计算机技术核心——算法和数据结构终极参考手册创新处也颇多譬如常见Shell排序他在书中提出可用(3i-1)/2间隔这使其稍快于O(n1. 5)当然这套书描述高度数学化为此恐怕般人(我?)最好还得先看本数学预备书Concrete Mathematics(直译为混凝土数学?^-^)再说可惜是这套书才出到第 3卷并没有覆盖全部常见算法内容不过好在对于游戏员来说越常见算法用得越多这也不算是什么要命损失STL源码剖析—— 侯捷 华中科大出版社侯捷不用介绍了华人技术作家中旗舰说其有世界级水准也不为过这本书我以为是C和数据结构葵花宝典(欲练此功必先自宫)也就是说不下几层地狱很难看懂它要求预备知识太多了如STL、数据结构、泛型编程、内存管理都要很扎实(为此是不是还要看看有内存管理设计模式的称Small Memory Software这本书呢?)但是旦看懂真会是所向披靡Data Structures for Game Programmers每个数据结构例程都是个小游戏还用SDL库实现了个算法演示系统虽然内容失的于浅但起码让人了解了数据结构在游戏中作用其实游戏并不比其它特殊甚至要求基本功更加扎实所以花时间做些看似和实际应用不甚相干习题对今后工作是大有裨益而且有些应用很广算法如常被人津津乐道[Page]A*算法及其变种牵涉到图检索周游和分枝-限界法恐怕还得读些艰深论文才能充分明白运用如Donald E. KnuthAn analysis of alpha-beta cutoffs其实还有不少此类好书如Data Structures and Algorithms in C、Programming Pearls、More Programming Pearls(算法珠玑)等我却以为要先看严谨点著作再看内容随笔点书汇编:IBM-PC 汇编语言设计第 2版 国内经典教材The Art of Assembly Language这本书足有1600页噢!C语言:The C Programming Language第 2版虽然篇幅短小但每个例程都很经典(我们老师开始拿它作教材后面换为谭小强C语言书理由为:例子尽是些文本处理我就纳了闷了难道现代计算机不是将大量时间消耗在串和文本处理上吗?)C:学过C语言再学C先看这本C Primer缩写版:Essential C对C有个入门了解再看C Common Knowledge: Essential Intermediate Programming就不会有什么重要知识点完全不知所措了接下来是The C Standard Library : A Tutorial and Reference标准库当然主要是标准模板库标准学习参考手册然后最好平时边写边参悟Effective C等我是说书名以形容词 + C那些书计有 7 8本慢慢看吧罗马不是日建成(Essential C、Effective C、More Effective C、Accelerated C、Effective STL、Exceptional C、More Exceptional C、Imperfect C虽然书名格式相似但每本都绝非马虎的作)谁说C比C要慢?那就请看下面:The Design and Evolution of C知其过去才能知其未来才能应用Inside the C Object Model揭露C编译器模型Efficient C Performance Programming Techniques当算法优化已到极致在运用汇编的前最后还可看看此书有时高级和低阶都能做成相同事情还有两本特别书:Modern C Design : Generic Programming and Design Patterns Applied作者想把设计模式和泛型编程结合起来并写了个尝试提供切Loki库来实作,不过其观点并未得到C社区普遍响应尽管如此本书仍称得上思想前沿性和技术实用性结合典范C Template Metaprogramming把编译器当作计算器?本书介绍了Boost库MPL模板元编程库当然提到Boost库对于游戏员不能不提到其中Graph库有The Boost Graph Library书可看还有其中Python库号称国内首款商业 3维图形引擎起点引擎就用了Boost-Python库说实话我觉得起点引擎还是蛮不错那个自制 3维编辑器虽然界面简陋但功能还算蛮完善给游戏学院用作教学内容也不错另有个号称中国首款自主研发全套网游解决方案我看到它那个 3维编辑器心想这不就是国外个叫freeworld3D编辑器吗?虽然有点偏门但我以前还较劲尝试破解过呢还把英文界面汉化了大概用[Page]exescope这样资源修改软件Software就能搞定吧我又心想为什么要找freeworld3D这个功能并不太强大编辑器呢?仅仅是它便宜到几十美金?它唯特别点地方就是支持导出OGRE图形引擎场景格式这样想不由得使人对它图形引擎“自主”性也产生怀疑了这样“自主”研发真让人汗颜只要中国还没封sourceforge这个网站WebSite(据说以前和freeBSD网站WebSite起被封过?)国人就能“自主”研发有人还会推荐C PrimerThinking in CThe C Programming Language等书吧诚然这些书也很好但我总觉得它们太大部头了还不如多花点时间看看国外好源代码Windows编程Operating Concepts第 5版国内有些操作系统教程其实就是它缩写版Windows 95 Programming Secrets深入剖析了Windows操作系统种种种种有人爱看Linux内核完全注释有人爱看自己动手写操作系统这样煽情书但我想作为商业操作系统把Windows内核剖析到这地步也高山仰止了Programming Applications for Microsoft Windows第 4版先进程线程再虚存管理再动态链接库最多讲到消息机制作者在序言中说:“我不讲什么ActiveX, COM等等当你了解了这些基础后那些东西很快就会明白!”可以作为Programming Windows先修课计算机体系:Computer s : A Programmer’s Perspective和The Art of Computer Programming在我心中是计算机史上两本称得上伟大书计算机组成原理操作系统汇编编译原理计算机网络等等课程汇成这本千页大书计算机在作者眼中就是个整体开源阅读:Code Reading : The Open Source Perspective张大千临摹了几百张明代石涛山水画出画以假乱真后来他去敦煌潜心临摹几年回来画风大变终成大家员其实有40%时间是在读别人源代码侯捷先生说:“源码面前了无秘密”又说“天下大事必作于细”可以和他上穷碧落下黄泉源码追踪经验谈参看MFC:深入浅出MFC我实在以为没有看过侯捷先生深入浅出MFC人多半不会懂得MFC编程其实我是打算用年多时间写个给游戏美工用 3维编辑器顺便作为毕业设计图形库就用MFC吧反正也没得选择如果要用wxWidgets无非是猎奇而已还不是MFC翻版当然它跨平台了就象阻击手对自己枪械零件了如指掌样要想用MFC写出非玩具人定要了解其内部构造还有本书叫MFC深入浅出并不是同本IDE:Microsoft Visual Studio 2005 Unleashed工欲善其事必先利其器当然我认为和其用形如Source Insight、Slick Edit、Code Visualizer的类代码阅读器、图形化工具还不如用自己大脑但如果你嫌打源代码慢话可以用Visual AssistX如果嫌老是写重复相似代码话可以用Code Smith单元测试可以用CppUnitBoost库中测试框架也不错有心情可以吧Visual Studio外接[Page]Intel Compiler内嵌STLport但不是大工程性能分析没必要动不动就用下VTune吧员的路:游戏的旅——我编程领悟云风大哥在我心目中游戏员国外首推卡马克国内首推云风也许过两年我会到网易当云风大哥助理员吧It’s my dream.(^-^)他写这本书时候本着只有透彻理解东西才写出来因此内容不会很酷新但是相信我每读遍都有新收获主要还不是知识上知识是学无止境授人以鱼不如授人以渔精神上启迪才是长久诚如经典游戏仙剑奇侠传主力员兼美术指导姚壮宪(人称姚仙)在序言中所说“云风得到只是些稿费而整个中国民族游戏产业得到将是次知识推动”此言不虚矣编程高手箴言梁肇新是豪杰超级解霸作者本来每个合格员(Programmer , 而非Coder)都应该掌握东西现在变成了编程高手独家箴言不知是作者幸运还是中国IT业悲哀知识点还是讲得蛮多不过对MFC地位颇有微词我实在认为MFC名声就是那些不懂得用它人搞臭不过作者牢骚也情有可原每个具有创造力员都应该不太喜欢frameworkMasters of DOOM: How Two Guys Created an Empire and Transformed Pop Culture中文名DOOM启世录卡马克罗洛斯这些游戏史上如雷贯耳名字(现在卡马克已专注于火箭制造上罗洛斯则携妻回乡隐居)要不是没上过大学卡马克和图形学大师亚伯拉罕功勋可能到现在游戏中还不知 3维为何物勿庸置疑在计算机界历史是英雄们所推动这本书真实记录了这些尘世英雄所为所思作为员我对这几本策划和美工书也产生了浓厚兴趣以前搞过两年3DS MAX插件编程觉得用maxscript还是好过MaxSDK毕竟游戏开发中所多是模型场景数据导入导出大可不必大动干戈策划:Creating Emotion in Games : The Craft and Art of Emotioneering在壮丽煊目宏伟 3维世界背后在残酷杀戮动人心魄情节背后我们还需要什么来抓住玩家心?答对了就是emotion.真正打动人心才是深入骨髓Ultimate Game Design : Building Game Worlds从名字可以看出写给关卡设计师特别是讲室外自然场景构建颇有可取的处Developing _disibledevent=>s Guide就象名为反模式书讲软件Software团队(Team)运营样这本书讲商业运作多过技术个历经艰难现在盛大游戏员翻译了这本书美工:Digital Cinematography & Directing数字摄影导演术每当你在3DS MAX或者Maya等 3维创作软件Software中摆放摄影机设计其运动轨迹时你可曾想过你也站在导演位置上了?The Animator’s Survival Kit看着这本讲卡通角色运动规律书边产生温习猫和老鼠念头边继续对前不久新闻联播中有关中国产生了某计算机自动卡通动画生成软件Software报道蔑视这条报道称此举可大大加快中国卡通动画产量我且不从技术上探讨其是否是在放卫星(其实我知道得很清楚前文已表本人搞过两年卡通动画辅助软件Software编程)但计算机机械生成动画怎可代替人类充满灵性创作?[Page]The Dark Side of Game Texturing用Photoshop制作材质贴图还真有些学问3维图形学:搞 3维图形学首先还是要扎扎实实先看解析几何、线性代数、计算几何教材后面习题个都不能少国内数学书还是蛮好苏步青大师计算几何称得上具有世界级水准可惜中国CAD宏图被盗版给击垮了现在是我们接过接力棒时候了It’s time!Computer Graphics Geometrical Tools计算机图形学几何工具算法详解算法很多纰漏处也不少3D Math Primer for Graphics and Game Development浅易可作为 3维数学“速食“Mathematics for 3D Game Programming & Computer Graphics第 2版比上面那本深入些证明推理数学气也浓些可作为专业数学书和编程实战个过渡桥梁吧内容涉猎也广射线追踪光照计算可视裁剪碰撞检测多边形技术阴影算法刚体物理流体水波数值思路方法曲线曲面还真够丰富Vector Game Math Processors想学MMX,SSE吗那就看它吧不过从基础讲起要耐心哦DirectX:Introduction to 3D Game Programming with DirectX 9.0DirectX入门龙书作者自己写简单举例框架后面我干脆用State模式把所有例子绑到块儿去了Beginning Direct3D Game Programming作者取得律师学位后变成了游戏员真是怪也哉本书虽定位为入门级书内容颇有独特可取的处它用到举例框架是DXSDK Sample Framework而不是现在通行DXUT要想编译有两种办法吧是自己改写成用DXUT 2是找旧Sample Framework我又懒得为了个举例框架下载整个早期版本DirectX后面在Nvidia SDK 9.5中发现了Advanced Animation with DirectXDirectX高级动画技术骨骼系统渐变关键帧动画偶人技术表情变形粒子系统布料柔体动态材质不而足我常常在想从 3维创作软件Software导出种种效果变成堆text或binary先加密压缩打包再解包解压解密再用游戏重建个Lite 动画系统游戏员也真是辛苦OpenGL:NeHe OpenGL Tutorials虽是网络教程不比正式书逊本来学OpenGL就不过是看百来条C文档工夫吧,如果图形学基础知识扎实话OpenGL Shading LanguageOpenGL支持最新显卡技术要靠修修补补插件扩展所以还要配合Nvidia OpenGL Extension Specications来看为上Focus _disibledevent=>Focus _disibledevent=>Focus _disibledevent=>顾名思义 3本专论虽然都很不深但要对未知 3维模型格式作反向工程前研读Geomipmapping地形算法论文前CAD前还是要看看它们为上如果没从别处得过到基础话脚本:先看Game Scripting Mastery等自己了解了虚拟机构造可以设计出简单脚本解释执行系统了再去查Python , Lua [Page]Ruby手册吧会事半半功倍倍Programming Role Playing Games with DirectX 8.0边教学边用DirectX写出了个GameCore库初具引擎稚形Isometric Game Programming with DirectX 7.03维也是建立在 2维基础上这就是这本书现在还值得看原因Visual C网络游戏建模和实现联众员写功力很扎实讲棋牌类游戏编程特别讲了UML建模和Rotional RoseObject-Oriented Game Development套用某人话:“I like this book.”Shader:要入门可先看Shaders for Game Programmers and Artists讲在RenderMonkey中用HLSL高级着色语言写Shader.再看Direct3D ShaderX : Vertex and Pixel Shander Tips and Tricks用汇编着色语言纯银赤金3大宝库:Game Programming Gems我只见到1-6本据说第7、8本也出来了?附带源代码常有bug不过瑕不掩瑜这套世界顶级游戏员每年度技术文集涉及游戏开发各个方面我觉得富有开发经验人更能在其中找到共鸣Graphics Gems全 5本图形学编程Bible看了这套书你会明白计算机领域科学家和工程师区别的所在科学家总是说这个东西在理论上可行工程师会说要使问题在logN时限内解决我只能忍痛割爱舍繁趋简GPU Gems出了 2本Nvidia公司召集图形学Gurus写等到看懂那天我也有心情跑去Siggraph国际图形学大会上投文章碰运气游戏引擎编程:3D Game Engine Programming是ZFXEngine引擎设计思路阐释很平实冇太多惊喜3D Game Engine Design数学物理理论知识讲解较多本来这样就够了还能期待更多吗?人工智能:AI Techniques for Game Programming讲遗传算法人工神经网络主要用到位图算法书原型是根据作者发表到论坛上内容整理出来还比较切中实际AI Game Programming Wisdom相当于AI编程GemsPC游戏编程(人机博弈)以象棋为蓝本介绍了很多种搜索算法除了常见极大极小值算法及其改进--负极大值算法还有深度优先搜索以外更提供了多种改进算法如:Alpha-Beta,Fail-soft alpha-beta,Aspiration Search, Minimal Window Search,Zobrist Hash,Iterative Deepening,History Heuristic,KillerHeuristic,SSS*,DUAL*,MFD and more.琳琅满目实属难得反外挂:加密和解密(第 2版) 看雪论坛站长 段钢破解序列号和反外挂有关系么?不过世上哪两件事情的间又没有关系呢?UML Distilled Martin Fowler很多人直到看了这本书才真正学懂UMLMartin Fowler是真正大师,从早期分析模式,到这本UML精粹,革命性重构都是他提出,后来又写了企业模式书现在领导个软件Software开发咨询公司去年JavaOne中国大会他作为专家来华了吧个人网站WebSite: [Page]设计模式 3剑客:Design Patterns Elements of Reusable Object-Oriented SoftwareDesign Patterns ExplainedHead First Design Patterns重构 3板斧:Refactoring : Improving the Design of Existing CodeRefactoring to PatternsRefactoring Workbook软件Software工程:Extreme Programming Explained : Embrace Change第 2版其中SimplicityValue真是振聋发聩这就是我什么都喜欢轻量级原因Agile Software Development Principles,Patterns,and Practices敏捷真是炒得够火连企业都有敏捷说不过大师是不会这么advertisingCode Complete第 2版名著数学:数学确定性丧失M.克莱因原来数学也只不过是人类发明和臆造用不着供入神殿想起历史上那么多不食人间烟火科学家(多半是数学家)自以为发现了宇宙运作奥秘是时候走下神坛了物理:普通物理学第册 Physics for Game Developers物理我想就到此为此吧再复杂我可要用Newton Engine,ODE了等待物理卡PPU普及那天就可充分发挥PhysX功效了看过最新细胞分裂游戏Demo演示成千上万个Box疯狂Collide骨灰级玩家该边摸钱包边流口水了2、开源代码:Irrlicht著名鬼火引擎从两年前第眼看到它这个轻量级 3维图形引擎就喜欢上了它源代码优雅高效且不故弄玄虚值得每个C员读并不限于图形编程者它周边中也有不少轻量级东西如Lightfeather扩展引擎ICE、IrrlichtRPG、IrrWizard.还有IrrEdit、IrrKlang、IrrXML可用(可能是为了效率原因很多开源作者往往喜欢自己写XML解析库如以上IrrXML库,即使有现成tinyXML库可用这真会让tomcat里面塞AxisAxis里面塞JUDDI弄得像俄罗斯套娃玩具Java Web Service Coder们汗颜)OGRE排名第开源图形引擎当然规模是很大周边也很多除了以C#写就OgreStudio ofusion嵌入3DS MAX作为WYSWYG式 3维编辑器也是棒棒特别是其几个场景、地形插件值得研究以至于Pro OGRE 3D Programming书专论其使用方法搜狐天龙 8部游戏就是以其作为图形引擎当然还另外开发了引擎插块啦我早知道OGRE开发组中有个中国人谢员他以前做了很多年传统软件Software编程有次天龙 8部游戏图形模块出错信息中包含了串某员工作目录有个文件夹名即是谢员英文名我据此推断谢员即是搜狐北京主程看来中国对开源事业还是有所贡献嘛王开源哥哥努力看来不会白费!(^-^)不过我侦测手法也有些像网站WebSite数据库爆库了非君子的所为作RakNet基于UDI网络库竟还支持声音传输以后和OpenVision结合起来做个视聊试试Blender声誉最盛开源 3维动画软件Software竟还带个游戏引擎虽然操作以快捷键驱动也就是说要背上百来个快捷键才能熟练使用但是作为从商业代码变为开源的作威胁 3维商业巨头轻骑兵历经十年锤炼代码达百万行此代码只应天上有人间哪得几回看怎可不作为长期源码参考?[Page]风魂2维图形库云风大哥成名的作虽然不代表其最高水平(最高水平作为商业代码保存在广州网易互动SVN里呢)但是也可以仰风采了圣剑英雄传2维RPG几个作者已成为成都锦天主力员锦天老总从百万发家 3年时间身价过亿也是代枭雄了这份代码作为几年前学生作品也算可以了个工程讲究是 4平 8稳并不定要哪个模块多么出彩反正我是没有时间写这么个东东连个美工都找不到只能整天想着破解别人资源(^-^)BoostC准标准库我想更多时候可以参考学习其源代码Yake我遇到最好轻量级游戏框架了在以前把个工程中图形引擎从Irrlicht换成OGRE尝试中遇到了它OGRE周边工程在我看来都很庸肿没有完善文档情况下看起来和Linux内核差不多不过这个Yake引擎倒是很喜欢它以个FSM有限状态机作为实时调度核心然后每个模块:物理、图形、网络、脚本、GUI、输入等等都提供个接口接口的下再提供到每种具体开源引擎接口然后再接具体引擎通过这样层层抽象此时你是接Newton Engine,ODE还是PysX都可以;是接OGRE,Crystal Space还是Irrlicht都可以;是接RakNet还是LibCurl都可以;是接PythonLua还是Ruby都可以是接CEGUI还是others是接OIS还是others(呵呵,记不起来others)都可以所以Yake本质上不是OGRE周边虽然用Neoengine人都倒向了它但是现在版本还很早特别是我认为学习研究时定要有这种抽象的抽象接口的接口东西把思维从具体绑定打开而开发时抽象要有限度就像蔡学镛在Java夜未眠中讲面向对象用得过滥也会得OOOO症(面向对象过敏强迫症)Quake Doom系列据说很经典卡马克这种开源黑客精神就值得赞许把商业源代码放出来走自己创新的路让别人追去吧不过Quake 和Unreal引擎 3维编辑器是现在所有编辑器鼻祖看来要好好看看了Nvidia SDK 9.X3维图形编程大宝库这些Diret3D和OpenGL举例都是用来展示其最新显卡技术硬件厂商往往对软件Software产品不甚在意源代码给你看,东西给你用去吧学完了还得买我硬件Intel编译器PhysX物理引擎大概也都是这样Havok会把它Havok物理引擎免费给别人用吗?别说试用版连个Demo都看不到所以这套SDK内容可比MS DirectX SDK里面那些入门级举例酷多了反正我是如获至宝 3月不知愁滋味不过显卡要so-so哦我GeForce 6600有两 3个跑不过去,差强人意3、网站WebSite:员大本营吧软文和“新技术秀”讨厌了点blog和社区是精华的所在www.基础编程学习知识的家员起点游戏员基地文档库中还有点东西投稿接收者Seabug和圣剑英雄传主程Seabug会是同个人吗?个在成都锦天担当技术重担高手还有时间维护网站WebSite吗?我不得而知“何苦做游戏”网站WebSite名字很个性站长也是历尽几年前产业发展初期艰难才出此名字[Page]2维游戏图片资源很多站长柳柳主推RPGMaker 软件Software也可以玩玩吧但对于专业开发者来说不可当真论坛中有不少热心国外高手在活动不用说了世界最大开源代码库入金山怎可空手而返?看到国外那些学生项目动不动就像模像样(DirectX稚形就是英国学生项目在学校还被判为不合格)源代码搜索引擎,支持正则表达式,google Lab中也有当你某种功能写不出来时,可以看下开源代码如何写,当然不过是仅供参考,开源代码未必都有产品级强度说到google,可看Google Power Tools Bible书你会发现google众多产品原来也有这么多使用门道2009-2-12 4:00:21疯狂代码 /。
软件工程师必备书籍推荐
软件工程师必备书籍推荐随着科技的飞速发展,软件工程师的角色变得越来越重要。
作为一名软件工程师,不仅需要具备丰富的编程技能,还需要不断学习不同领域的知识,以不断提升自己的技术实力。
而对于软件工程师来说,阅读相关的专业书籍无疑是非常重要的途径之一。
在这篇文章中,我将向大家推荐一些软件工程师必备的书籍,希望能对大家的学习和工作有所帮助。
一、编程基础1.《算法导论》(Introduction to Algorithms)这本书由Thomas H. Cormen等人共同撰写,是计算机科学领域的经典之作。
书中详细介绍了各种基本的算法和数据结构,对于帮助软件工程师构建高效的程序非常有帮助。
2.《设计模式:可复用面向对象软件的基础》(Design Patterns: Elements of Reusable Object-Oriented Software)由Gang of Four(Erich Gamma, Richard Helm, Ralph Johnson和John Vlissides)共同著作的这本书介绍了23种常用的设计模式,对于软件开发过程中的代码重用和架构设计非常有帮助。
二、编程语言3.《Java编程思想》(Thinking in Java)由Bruce Eckel编写的这本书详细介绍了Java编程语言的核心概念和技术。
对于想要深入学习Java的软件工程师来说,这本书是必不可少的读物。
4.《Python编程:从入门到实践》(Python Crash Course)这本由Eric Matthes撰写的书介绍了Python编程语言的基础知识和实践应用。
对于想要学习Python并进行快速实践的软件工程师来说,这本书是非常适合的选择。
三、软件开发与项目管理5.《敏捷软件开发:原则、模式与实践》(Agile Software Development, Principles, Patterns, and Practices)这本书由Robert C. Martin著作,是一本介绍敏捷软件开发原则和实践的经典之作。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
• 本文對基本算法説明的基本方式
– 説明算法的基本原理 – 給出由此算法解決的實例
定義我們要解決的問題
給定有待排序的N 給定有待排序的N個項目 R1,R2,…,RN 我們稱這些項目為記錄(record),並稱N 我們稱這些項目為記錄(record),並稱N個記錄的整 個集合為一個文件(file)。每一個R 個集合為一個文件(file)。每一個Rj有一個鍵碼 (key) Kj ,支配排序過程。 排序的目標,是確定下標為{1,2,…,N}的一個排列 排序的目標,是確定下標為{1,2,…,N}的一個排列 p(1) p(2)…p(N),它以非遞降的次序來放置所有的 p(2)…p(N),它以非遞降的次序來放置所有的 鍵碼: Kp(1) ≤ Kp(2) ≤ …≤ Kp(N)
合併兩個已經排列好的序列
MERGE(A, p, q, r)
1 n1 ← q - p + 1 2 n2 ← r - q 3 create arrays L[1 ‥ n1 + 1] and R[1 ‥ n2 + 1] 4 for i ← 1 to n1 5 do L[i] ← A[p + i - 1] 6 for j ← 1 to n2 7 do R[j] ← A[q + j] 8 L[n1 + 1] ← ∞ 9 R[n2 + 1] ← ∞ 10 i ← 1 11 j ← 1 12 for k ← p to r 13 do if L[i] ≤ R[j] 14 then A[k] ← L[i] i←i+1 15 16 else A[k] ← R[j] 17 j←j+1
算法講義
目的
• 算法(algorithm)是一個優秀程序員的基本功, 算法(algorithm)
本文章介紹了算法的基本概念和一些基本 的算法,希望可以起到抛磚引玉的作用
内容
• 本講義分爲以下3大部分 本講義分爲以下3
– 基本概念 – 排序 – 基本算法
定義
• 算法是把一些輸入經過一系列的運算轉化
• The merge sort algorithm closely follows the • • •
divide-anddivide-and-conquer paradigm. Intuitively, it operates as follows. Divide: Divide the n-element sequence to be sorted into two subsequences of n/2 elements each. Conquer: Sort the two subsequences recursively using merge sort. Combine: Merge the two sorted subsequences to produce the sorted answer.
The operation of INSERTION-SORT on the array A = 〈5, 2, 4, 6, 1, 3〉. INSERTION3〉
The divide-and-conquer approach divide-and• 把一個問題切分成幾個與原問題相似,但是 把一個問題切分成幾個與原問題相似,
調整最大堆
MAXMAX-HEAPIFY(A, i)
1 l ← LEFT(i) 2 r ← RIGHT(i) 3 if l ≤ heap-size[A] and A[l] > A[i] heap4 then largest ← l 5 else largest ← i 6 if r ≤ heap-size[A] and A[r] > A[largest] heap7 then largest ← r 8 if largest ≠ i 9 then exchange A[i] ↔ A[largest] 10 MAX-HEAPIFY(A, largest) MAX-
The operation of PARTITION on a sample array.
思考
• 至今爲止介紹的排序有什麽共同點? • 排列的順序是基於比較的 排列的順序是基於比較的 • 我們稱這些排序算法為comparison sorts
The decision-tree model decision• 一個decision-tree是一棵完全二插樹,,它 一個decision-tree是一棵完全二插樹,,它
The operation of HEAPSORT.
QuickSort
• 取一個記錄,並把它移動到在排了序的文
件中它將佔據的最終位置 • 更偏愛一個無次序的序列
分割文件
PARTITION(A, p, r)
1 2 3 4 5 6 7 8
x ← A[r] i←p-1 for j ← p to r - 1 do if A[j] ≤ x then i ← i + 1
内精確的完成
算法解決了什麽
• 人類基因工程 • 網絡查詢信息 • 電子商務 • 最佳分配 • 衆多的數學問題(4色問題) 衆多的數學問題(4色問題)
對算法的説明
• 本文對排序説明的基本方式
– 説明算法的基本原理 – 給出算法的偽代碼,對任何一門語言熟悉的讀 者都將可以輕鬆的讀懂 – 給出算法的圖例
規模比原問題小的子問題, 規模比原問題小的子問題,遞歸的求解這些 子問題,最後再把這些結果組合起來, 子問題,最後再把這些結果組合起來,得到原 問題的解. 問題的解. • 分爲3個步驟: 分爲3個步驟:
– 把問題切分為子問題 – 分別解決每一個子問題 – 把子問題的解綜合得到原問題的解
MergeSort
代表了用特殊的比較算法對給定的輸入中 的元素進行的比較
The decision tree for insertion sort operating on three elements
comparison sorts的最優情況分析 sorts的最優情況分析
1 for j ← 2 to length[A] 2 do key ← A[j] 3 ▹ Insert A[j] into the sorted sequence A[1 ‥ j - 1]. 4 i←j-1 5 while i > 0 and A[i] > key 6 do A[i + 1] ← A[i] 7 i←i-1 8 A[i + 1] ← key
HeapSort
• 實際上是一種選擇排序 • 使用堆作爲數據結構,首先安排文件,使
得它形成一個堆,然後反復撤銷堆頂,並 把它傳送到適當的最後位置 • 優先隊列的實現原理就是堆
堆
• 堆,作爲一種基礎的數據結構,可以被看
成是一棵近似的完全二叉樹 • 每個節點的值都大於(小於)或等於其子節點 每個節點的值都大於(小於) 值的樹 • 分爲最大堆和最小堆 • 最大堆的性質:
爲什麽要排序
• 在算法的學習中,是最基本的問題
– 在應用中經常需要排序 – 排序算法衆多,並且運用了不同的技術 – 排序是一個有最優解決方案的算法 – 很多算法需要以排序作爲基礎 – 排序之前還需要考慮許多工程學的問題
排序分類
• 排序可分爲内部排序和外部排序 • 在内部排序中,記錄被整個的保留在計算
機的高速隨機存取存儲器中 • 當記錄比内存一次所能容納的還多時,則 使用外部排序
當著手解決一個問題的時候 當著手解決一個問題的時候 先找出某些相當明顯的解決 先找出某些相當明顯的解決 方法 然後再試圖改進它 然後再試圖改進它 往往是明智的
我們所涉及到的排序
• InsertSort • MergeSort • QuickSort • HeapSort • Counting sort • Bucket sort
– 對序列A,滿足條件A[PARENT(i)] ≥ A[i] 對序列A – 在Root保存的是堆中的最大值 Root保存的是堆中的最大值
A max-heap viewed as (a) a binary tree and (b) an array. The maxnumber within the circle at each node in the tree is the value stored at that node. The number above a node is the corresponding index in the array. Above and below the array are lines showing parentparentchild relationships; parents are always to the left of their children. The tree has height three; the node at index 4 (with value 8) has height one.
The action of MAX-HEAPIFY(A, 2), where heap-size[A] = 10. MAXheap-
創建一個堆
BUILD-MAXBUILD-MAX-HEAP(A)
1 heap-size[A] ← length[A] heap2 for i ← ⌊length[A]/2⌋ downto 1 ]/2⌋ 3 do MAX-HEAPIFY(A, i) MAX-
The operation of BUILD-MAX-HEAP, showing the data structure BUILD-MAXbefore the call to MAX-HEAPIFY MAX-
堆排序
HEAPSORT(A)
1 BUILD-MAX-HEAP(A) BUILD-MAX2 for i ← length[A] downto 2 3 do exchange A[1] ↔ A[i] 4 heapheap-size[A] ← heap-size[A] - 1 heap5 MAX-HEAPIFY(A, 1) MAX-
