Correlation Patterns in ServiceOriented Architectures
SPSS术语中英文对照

Absolute deviation, 绝对离差Absolute number, 绝对数Absolute residuals, 绝对残差Acceleration array, 加速度立体阵Acceleration in an arbitrary direction, 任意方向上的加速度Acceleration normal, 法向加速度Acceleration space dimension , 加速度空间的维数Acceleration tangential, 切向加速度Acceleration vector, 加速度向量Acceptable hypothesis, 可接受假设Accumulation, 累积Accuracy, 准确度Actual frequency, 实际频数Adaptive estimator, 自适应估计量Addition, 相加Addition theorem, 加法定理Additivity, 可加性Adjusted rate, 调整率Adjusted value, 校正值Admissible error, 容许误差Aggregation, 聚集性Alternative hypothesis, 备择假设Among groups, 组间Amounts, 总量Analysis of correlation, 相关分析Analysis of covariance, 协方差分析Analysis of regression, 回归分析Analysis of time series, 时间序列分析Analysis of variance, 方差分析Angular transformation, 角转换ANOVA (analysis of variance ), 方差分析ANOVA Models, 方差分析模型Arcing, 弧/弧旋Arcsine transformation, 反正弦变换Area under the curve, 曲线面积AREG , 评估从一个时间点到下一个时间点回归相关时的误差ARIMA, 季节和非季节性单变量模型的极大似然估计Arithmetic grid paper, 算术格纸Arithmetic mean, 算术平均数Arrhenius relation, 艾恩尼斯关系Assessing fit, 拟合的评估Associative laws, 结合律Asymmetric distribution, 非对称分布Asymptotic bias, 渐近偏倚Asymptotic efficiency, 渐近效率Asymptotic variance, 渐近方差Attributable risk, 归因危险度Attribute data, 属性资料Attribution, 属性Autocorrelation, 自相关Autocorrelation of residuals , 残差的自相关Average, 平均数Average confidence interval length, 平均置信区间长度Average growth rate, 平均增长率Bar chart, 条形图Bar graph, 条形图Base period, 基期Bayes' theorem , Bayes定理Bell-shaped curve, 钟形曲线Bernoulli distribution, 伯努力分布Best-trim estimator, 最好切尾估计量Bias, 偏性Binary logistic regression, 二元逻辑斯蒂回归Binomial distribution, 二项分布Bisquare, 双平方Bivariate Correlate, 二变量相关Bivariate normal distributio n, 双变量正态分布Bivariate normal population,双变量正态总体Biweight interval, 双权区间Biweight M-estimator, 双权M 估计量Block, 区组/配伍组BMDP(Biomedical computer pro grams), BMDP统计软件包Boxplots, 箱线图/箱尾图Breakdown bound, 崩溃界/崩溃点Canonical correlation, 典型相关Caption, 纵标目Case-control study, 病例对照研究Categorical variable, 分类变量Catenary, 悬链线Cauchy distribution, 柯西分布Cause-and-effect relationshi p, 因果关系Cell, 单元Censoring, 终检Center of symmetry, 对称中心Centering and scaling, 中心化和定标Central tendency, 集中趋势Central value, 中心值CHAID -χ2 Automatic Interac tion Detector, 卡方自动交互检测Chance, 机遇Chance error, 随机误差Chance variable, 随机变量Characteristic equation, 特征方程Characteristic root, 特征根Characteristic vector, 特征向量Chebshev criterion of fit, 拟合的切比雪夫准则Chernoff faces, 切尔诺夫脸谱图Chi-square test, 卡方检验/χ2检验Choleskey decomposition, 乔洛斯基分解Circle chart, 圆图Class interval, 组距Class mid-value, 组中值Class upper limit, 组上限Classified variable, 分类变量Cluster analysis, 聚类分析Cluster sampling, 整群抽样Code, 代码Coded data, 编码数据Coding, 编码Coefficient of contingency, 列联系数Coefficient of determination , 决定系数Coefficient of multiple corr elation, 多重相关系数Coefficient of partial corre lation, 偏相关系数Coefficient of production-mo ment correlation, 积差相关系数Coefficient of rank correlat ion, 等级相关系数Coefficient of regression, 回归系数Coefficient of skewness, 偏度系数Coefficient of variation, 变异系数Cohort study, 队列研究Column, 列Column effect, 列效应Column factor, 列因素Combination pool, 合并Combinative table, 组合表Common factor, 共性因子Common regression coefficien t, 公共回归系数Common value, 共同值Common variance, 公共方差Common variation, 公共变异Communality variance, 共性方差Comparability, 可比性Comparison of bathes, 批比较Comparison value, 比较值Compartment model, 分部模型Compassion, 伸缩Complement of an event, 补事件Complete association, 完全正相关Complete dissociation, 完全不相关Complete statistics, 完备统计量Completely randomized design , 完全随机化设计Composite event, 联合事件Composite events, 复合事件Concavity, 凹性Conditional expectation, 条件期望Conditional likelihood, 条件似然Conditional probability, 条件概率Conditionally linear, 依条件线性Confidence interval, 置信区间Confidence limit, 置信限Confidence lower limit, 置信下限Confidence upper limit, 置信上限Confirmatory Factor Analysis , 验证性因子分析Confirmatory research, 证实性实验研究Confounding factor, 混杂因素Conjoint, 联合分析Consistency, 相合性Consistency check, 一致性检验Consistent asymptotically no rmal estimate, 相合渐近正态估计Consistent estimate, 相合估计Constrained nonlinear regres sion, 受约束非线性回归Constraint, 约束Contaminated distribution, 污染分布Contaminated Gausssian, 污染高斯分布Contaminated normal distribu tion, 污染正态分布Contamination, 污染Contamination model, 污染模型Contingency table, 列联表Contour, 边界线Contribution rate, 贡献率Control, 对照Controlled experiments, 对照实验Conventional depth, 常规深度Convolution, 卷积Corrected factor, 校正因子Corrected mean, 校正均值Correction coefficient, 校正系数Correctness, 正确性Correlation coefficient, 相关系数Correlation index, 相关指数Correspondence, 对应Counting, 计数Counts, 计数/频数Covariance, 协方差Covariant, 共变Cox Regression, Cox回归Criteria for fitting, 拟合准则Criteria of least squares, 最小二乘准则Critical ratio, 临界比Critical region, 拒绝域Critical value, 临界值Cross-over design, 交叉设计Cross-section analysis, 横断面分析Cross-section survey, 横断面调查Crosstabs , 交叉表Cross-tabulation table, 复合表Cube root, 立方根Cumulative distribution func tion, 分布函数Cumulative probability, 累计概率Curvature, 曲率/弯曲Curvature, 曲率Curve fit , 曲线拟和Curve fitting, 曲线拟合Curvilinear regression, 曲线回归Curvilinear relation, 曲线关系Cut-and-try method, 尝试法Cycle, 周期Cyclist, 周期性D test, D检验Data acquisition, 资料收集Data bank, 数据库Data capacity, 数据容量Data deficiencies, 数据缺乏Data handling, 数据处理Data manipulation, 数据处理Data processing, 数据处理Data reduction, 数据缩减Data set, 数据集Data sources, 数据来源Data transformation, 数据变换Data validity, 数据有效性Data-in, 数据输入Data-out, 数据输出Dead time, 停滞期Degree of freedom, 自由度Degree of precision, 精密度Degree of reliability, 可靠性程度Degression, 递减Density function, 密度函数Density of data points, 数据点的密度Dependent variable, 应变量/依变量/因变量Dependent variable, 因变量Depth, 深度Derivative matrix, 导数矩阵Derivative-free methods, 无导数方法Design, 设计Determinacy, 确定性Determinant, 行列式Determinant, 决定因素Deviation, 离差Deviation from average, 离均差Diagnostic plot, 诊断图Dichotomous variable, 二分变量Differential equation, 微分方程Direct standardization, 直接标准化法Discrete variable, 离散型变量DISCRIMINANT, 判断Discriminant analysis, 判别分析Discriminant coefficient, 判别系数Discriminant function, 判别值Dispersion, 散布/分散度Disproportional, 不成比例的Disproportionate sub-class n umbers, 不成比例次级组含量Distribution free, 分布无关性/免分布Distribution shape, 分布形状Distribution-free method, 任意分布法Distributive laws, 分配律Disturbance, 随机扰动项Dose response curve, 剂量反应曲线Double blind method, 双盲法Double blind trial, 双盲试验Double exponential distribut ion, 双指数分布Double logarithmic, 双对数Downward rank, 降秩Dual-space plot, 对偶空间图DUD, 无导数方法Duncan's new multiple range method, 新复极差法/Duncan新法Effect, 实验效应Eigenvalue, 特征值Eigenvector, 特征向量Ellipse, 椭圆Empirical distribution, 经验分布Empirical probability, 经验概率单位Enumeration data, 计数资料Equal sun-class number, 相等次级组含量Equally likely, 等可能Equivariance, 同变性Error, 误差/错误Error of estimate, 估计误差Error type I, 第一类错误Error type II, 第二类错误Estimand, 被估量Estimated error mean squares , 估计误差均方Estimated error sum of squar es, 估计误差平方和Euclidean distance, 欧式距离Event, 事件Event, 事件Exceptional data point, 异常数据点Expectation plane, 期望平面Expectation surface, 期望曲面Expected values, 期望值Experiment, 实验Experimental sampling, 试验抽样Experimental unit, 试验单位Explanatory variable, 说明变量Exploratory data analysis, 探索性数据分析Explore Summarize, 探索-摘要Exponential curve, 指数曲线Exponential growth, 指数式增长EXSMOOTH, 指数平滑方法Extended fit, 扩充拟合Extra parameter, 附加参数Extrapolation, 外推法Extreme observation, 末端观测值Extremes, 极端值/极值F distribution, F分布F test, F检验Factor, 因素/因子Factor analysis, 因子分析Factor Analysis, 因子分析Factor score, 因子得分Factorial, 阶乘Factorial design, 析因试验设计False negative, 假阴性False negative error, 假阴性错误Family of distributions, 分布族Family of estimators, 估计量族Fanning, 扇面Fatality rate, 病死率Field investigation, 现场调查Field survey, 现场调查Finite population, 有限总体Finite-sample, 有限样本First derivative, 一阶导数First principal component, 第一主成分First quartile, 第一四分位数Fisher information, 费雪信息量Fitted value, 拟合值Fitting a curve, 曲线拟合Fixed base, 定基Fluctuation, 随机起伏Forecast, 预测Four fold table, 四格表Fourth, 四分点Fraction blow, 左侧比率Fractional error, 相对误差Frequency, 频率Frequency polygon, 频数多边图Frontier point, 界限点Function relationship, 泛函关系Gamma distribution, 伽玛分布Gauss increment, 高斯增量Gaussian distribution, 高斯分布/正态分布Gauss-Newton increment, 高斯-牛顿增量General census, 全面普查GENLOG (Generalized liner mo dels), 广义线性模型Geometric mean, 几何平均数Gini's mean difference, 基尼均差GLM (General liner models), 一般线性模型Goodness of fit, 拟和优度/配合度Gradient of determinant, 行列式的梯度Graeco-Latin square, 希腊拉丁方Grand mean, 总均值Gross errors, 重大错误Gross-error sensitivity, 大错敏感度Group averages, 分组平均Grouped data, 分组资料Guessed mean, 假定平均数Half-life, 半衰期Hampel M-estimators, 汉佩尔M估计量Happenstance, 偶然事件Harmonic mean, 调和均数Hazard function, 风险均数Hazard rate, 风险率Heading, 标目Heavy-tailed distribution, 重尾分布Hessian array, 海森立体阵Heterogeneity, 不同质Heterogeneity of variance, 方差不齐Hierarchical classification,组内分组Hierarchical clustering meth od, 系统聚类法High-leverage point, 高杠杆率点HILOGLINEAR, 多维列联表的层次对数线性模型Hinge, 折叶点Histogram, 直方图Historical cohort study, 历史性队列研究Holes, 空洞HOMALS, 多重响应分析Homogeneity of variance, 方差齐性Homogeneity test, 齐性检验Huber M-estimators, 休伯M估计量Hyperbola, 双曲线Hypothesis testing, 假设检验Hypothetical universe, 假设总体Impossible event, 不可能事件Independence, 独立性Independent variable, 自变量Index, 指标/指数Indirect standardization, 间接标准化法Individual, 个体Inference band, 推断带Infinite population, 无限总体Infinitely great, 无穷大Infinitely small, 无穷小Influence curve, 影响曲线Information capacity, 信息容量Initial condition, 初始条件Initial estimate, 初始估计值Initial level, 最初水平Interaction, 交互作用Interaction terms, 交互作用项Intercept, 截距Interpolation, 内插法Interquartile range, 四分位距Interval estimation, 区间估计Intervals of equal probabili ty, 等概率区间Intrinsic curvature, 固有曲率Invariance, 不变性Inverse matrix, 逆矩阵Inverse probability, 逆概率Inverse sine transformation,反正弦变换Iteration, 迭代Jacobian determinant, 雅可比行列式Joint distribution function,分布函数Joint probability, 联合概率Joint probability distributi on, 联合概率分布K means method, 逐步聚类法Kaplan-Meier, 评估事件的时间长度Kaplan-Merier chart, Kaplan-Merier图Kendall's rank correlation, Kendall等级相关Kinetic, 动力学Kolmogorov-Smirnove test, 柯尔莫哥洛夫-斯米尔诺夫检验Kruskal and Wallis test, Kru skal及Wallis检验/多样本的秩和检验/H检验Kurtosis, 峰度Lack of fit, 失拟Ladder of powers, 幂阶梯Lag, 滞后Large sample, 大样本Large sample test, 大样本检验Latin square, 拉丁方Latin square design, 拉丁方设计Leakage, 泄漏Least favorable configuratio n, 最不利构形Least favorable distribution , 最不利分布Least significant difference , 最小显著差法Least square method, 最小二乘法Least-absolute-residuals est imates, 最小绝对残差估计Least-absolute-residuals fit , 最小绝对残差拟合Least-absolute-residuals lin e, 最小绝对残差线Legend, 图例L-estimator, L估计量L-estimator of location, 位置L估计量L-estimator of scale, 尺度L 估计量Level, 水平Life expectance, 预期期望寿命Life table, 寿命表Life table method, 生命表法Light-tailed distribution, 轻尾分布Likelihood function, 似然函数Likelihood ratio, 似然比line graph, 线图Linear correlation, 直线相关Linear equation, 线性方程Linear programming, 线性规划Linear regression, 直线回归Linear Regression, 线性回归Linear trend, 线性趋势Loading, 载荷Location and scale equivaria nce, 位置尺度同变性Location equivariance, 位置同变性Location invariance, 位置不变性Location scale family, 位置尺度族Log rank test, 时序检验Logarithmic curve, 对数曲线Logarithmic normal distribut ion, 对数正态分布Logarithmic scale, 对数尺度Logarithmic transformation, 对数变换Logic check, 逻辑检查Logistic distribution, 逻辑斯特分布Logit transformation, Logit 转换LOGLINEAR, 多维列联表通用模型Lognormal distribution, 对数正态分布Lost function, 损失函数Low correlation, 低度相关Lower limit, 下限Lowest-attained variance, 最小可达方差LSD, 最小显著差法的简称Lurking variable, 潜在变量Main effect, 主效应Major heading, 主辞标目Marginal density function, 边缘密度函数Marginal probability, 边缘概率Marginal probability distrib ution, 边缘概率分布Matched data, 配对资料Matched distribution, 匹配过分布Matching of distribution, 分布的匹配Matching of transformation, 变换的匹配Mathematical expectation, 数学期望Mathematical model, 数学模型Maximum L-estimator, 极大极小L 估计量Maximum likelihood method, 最大似然法Mean, 均数Mean squares between groups,组间均方Mean squares within group, 组内均方Means (Compare means), 均值-均值比较Median, 中位数Median effective dose, 半数效量Median lethal dose, 半数致死量Median polish, 中位数平滑Median test, 中位数检验Minimal sufficient statistic , 最小充分统计量Minimum distance estimation,最小距离估计Minimum effective dose, 最小有效量Minimum lethal dose, 最小致死量Minimum variance estimator, 最小方差估计量MINITAB, 统计软件包Minor heading, 宾词标目Missing data, 缺失值Model specification, 模型的确定Modeling Statistics , 模型统计Models for outliers, 离群值模型Modifying the model, 模型的修正Modulus of continuity, 连续性模Morbidity, 发病率Most favorable configuration , 最有利构形Multidimensional Scaling (AS CAL), 多维尺度/多维标度Multinomial Logistic Regress ion , 多项逻辑斯蒂回归Multiple comparison, 多重比较Multiple correlation , 复相关Multiple covariance, 多元协方差Multiple linear regression, 多元线性回归Multiple response , 多重选项Multiple solutions, 多解Multiplication theorem, 乘法定理Multiresponse, 多元响应Multi-stage sampling, 多阶段抽样Multivariate T distribution,多元T分布Mutual exclusive, 互不相容Mutual independence, 互相独立Natural boundary, 自然边界Natural dead, 自然死亡Natural zero, 自然零Negative correlation, 负相关Negative linear correlation,负线性相关Negatively skewed, 负偏Newman-Keuls method, q检验NK method, q检验No statistical significance,无统计意义Nominal variable, 名义变量Nonconstancy of variability,变异的非定常性Nonlinear regression, 非线性相关Nonparametric statistics, 非参数统计Nonparametric test, 非参数检验Nonparametric tests, 非参数检验Normal deviate, 正态离差Normal distribution, 正态分布Normal equation, 正规方程组Normal ranges, 正常范围Normal value, 正常值Nuisance parameter, 多余参数/讨厌参数Null hypothesis, 无效假设Numerical variable, 数值变量Objective function, 目标函数Observation unit, 观察单位Observed value, 观察值One sided test, 单侧检验One-way analysis of variance , 单因素方差分析Oneway ANOVA , 单因素方差分析Open sequential trial, 开放型序贯设计Optrim, 优切尾Optrim efficiency, 优切尾效率Order statistics, 顺序统计量Ordered categories, 有序分类Ordinal logistic regression , 序数逻辑斯蒂回归Ordinal variable, 有序变量Orthogonal basis, 正交基Orthogonal design, 正交试验设计Orthogonality conditions, 正交条件ORTHOPLAN, 正交设计Outlier cutoffs, 离群值截断点Outliers, 极端值OVERALS , 多组变量的非线性正规相关Overshoot, 迭代过度Paired design, 配对设计Paired sample, 配对样本Pairwise slopes, 成对斜率Parabola, 抛物线Parallel tests, 平行试验Parameter, 参数Parametric statistics, 参数统计Parametric test, 参数检验Partial correlation, 偏相关Partial regression, 偏回归Partial sorting, 偏排序Partials residuals, 偏残差Pattern, 模式Pearson curves, 皮尔逊曲线Peeling, 退层Percent bar graph, 百分条形图Percentage, 百分比Percentile, 百分位数Percentile curves, 百分位曲线Periodicity, 周期性Permutation, 排列P-estimator, P估计量Pie graph, 饼图Pitman estimator, 皮特曼估计量Pivot, 枢轴量Planar, 平坦Planar assumption, 平面的假设PLANCARDS, 生成试验的计划卡Point estimation, 点估计Poisson distribution, 泊松分布Polishing, 平滑Polled standard deviation, 合并标准差Polled variance, 合并方差Polygon, 多边图Polynomial, 多项式Polynomial curve, 多项式曲线Population, 总体Population attributable risk , 人群归因危险度Positive correlation, 正相关Positively skewed, 正偏Posterior distribution, 后验分布Power of a test, 检验效能Precision, 精密度Predicted value, 预测值Preliminary analysis, 预备性分析Principal component analysis , 主成分分析Prior distribution, 先验分布Prior probability, 先验概率Probabilistic model, 概率模型probability, 概率Probability density, 概率密度Product moment, 乘积矩/协方差Profile trace, 截面迹图Proportion, 比/构成比Proportion allocation in str atified random sampling, 按比例分层随机抽样Proportionate, 成比例Proportionate sub-class numb ers, 成比例次级组含量Prospective study, 前瞻性调查Proximities, 亲近性Pseudo F test, 近似F检验Pseudo model, 近似模型Pseudosigma, 伪标准差Purposive sampling, 有目的抽样QR decomposition, QR分解Quadratic approximation, 二次近似Qualitative classification, 属性分类Qualitative method, 定性方法Quantile-quantile plot, 分位数-分位数图/Q-Q图Quantitative analysis, 定量分析Quartile, 四分位数Quick Cluster, 快速聚类Radix sort, 基数排序Random allocation, 随机化分组Random blocks design, 随机区组设计Random event, 随机事件Randomization, 随机化Range, 极差/全距Rank correlation, 等级相关Rank sum test, 秩和检验Rank test, 秩检验Ranked data, 等级资料Rate, 比率Ratio, 比例Raw data, 原始资料Raw residual, 原始残差Rayleigh's test, 雷氏检验Rayleigh's Z, 雷氏Z值Reciprocal, 倒数Reciprocal transformation, 倒数变换Recording, 记录Redescending estimators, 回降估计量Reducing dimensions, 降维Re-expression, 重新表达Reference set, 标准组Region of acceptance, 接受域Regression coefficient, 回归系数Regression sum of square, 回归平方和Rejection point, 拒绝点Relative dispersion, 相对离散度Relative number, 相对数Reliability, 可靠性Reparametrization, 重新设置参数Replication, 重复Report Summaries, 报告摘要Residual sum of square, 剩余平方和Resistance, 耐抗性Resistant line, 耐抗线Resistant technique, 耐抗技术R-estimator of location, 位置R估计量R-estimator of scale, 尺度R 估计量Retrospective study, 回顾性调查Ridge trace, 岭迹Ridit analysis, Ridit分析Rotation, 旋转Rounding, 舍入Row, 行Row effects, 行效应Row factor, 行因素RXC table, RXC表Sample, 样本Sample regression coefficien t, 样本回归系数Sample size, 样本量Sample standard deviation, 样本标准差Sampling error, 抽样误差SAS(Statistical analysis sys tem ), SAS统计软件包Scale, 尺度/量表Scatter diagram, 散点图Schematic plot, 示意图/简图Score test, 计分检验Screening, 筛检SEASON, 季节分析Second derivative, 二阶导数Second principal component, 第二主成分SEM (Structural equation mod eling), 结构化方程模型Semi-logarithmic graph, 半对数图Semi-logarithmic paper, 半对数格纸Sensitivity curve, 敏感度曲线Sequential analysis, 贯序分析Sequential data set, 顺序数据集Sequential design, 贯序设计Sequential method, 贯序法Sequential test, 贯序检验法Serial tests, 系列试验Short-cut method, 简捷法Sigmoid curve, S形曲线Sign function, 正负号函数Sign test, 符号检验Signed rank, 符号秩Significance test, 显著性检验Significant figure, 有效数字Simple cluster sampling, 简单整群抽样Simple correlation, 简单相关Simple random sampling, 简单随机抽样Simple regression, 简单回归simple table, 简单表Sine estimator, 正弦估计量Single-valued estimate, 单值估计Singular matrix, 奇异矩阵Skewed distribution, 偏斜分布Skewness, 偏度Slash distribution, 斜线分布Slope, 斜率Smirnov test, 斯米尔诺夫检验Source of variation, 变异来源Spearman rank correlation, 斯皮尔曼等级相关Specific factor, 特殊因子Specific factor variance, 特殊因子方差Spectra , 频谱Spherical distribution, 球型正态分布Spread, 展布SPSS(Statistical package for the social science), SPSS 统计软件包Spurious correlation, 假性相关Square root transformation, 平方根变换Stabilizing variance, 稳定方差Standard deviation, 标准差Standard error, 标准误Standard error of difference , 差别的标准误Standard error of estimate, 标准估计误差Standard error of rate, 率的标准误Standard normal distribution , 标准正态分布Standardization, 标准化Starting value, 起始值Statistic, 统计量Statistical control, 统计控制Statistical graph, 统计图Statistical inference, 统计推断Statistical table, 统计表Steepest descent, 最速下降法Stem and leaf display, 茎叶图Step factor, 步长因子Stepwise regression, 逐步回归Storage, 存Strata, 层(复数)Stratified sampling, 分层抽样Stratified sampling, 分层抽样Strength, 强度Stringency, 严密性Structural relationship, 结构关系Studentized residual, 学生化残差/t化残差Sub-class numbers, 次级组含量Subdividing, 分割Sufficient statistic, 充分统计量Sum of products, 积和Sum of squares, 离差平方和Sum of squares about regress ion, 回归平方和Sum of squares between group s, 组间平方和Sum of squares of partial re gression, 偏回归平方和Sure event, 必然事件Survey, 调查Survival, 生存分析Survival rate, 生存率Suspended root gram, 悬吊根图Symmetry, 对称Systematic error, 系统误差Systematic sampling, 系统抽样Tags, 标签Tail area, 尾部面积Tail length, 尾长Tail weight, 尾重Tangent line, 切线Target distribution, 目标分布Taylor series, 泰勒级数Tendency of dispersion, 离散趋势Testing of hypotheses, 假设检验Theoretical frequency, 理论频数Time series, 时间序列Tolerance interval, 容忍区间Tolerance lower limit, 容忍下限Tolerance upper limit, 容忍上限Torsion, 扰率Total sum of square, 总平方和Total variation, 总变异Transformation, 转换Treatment, 处理Trend, 趋势Trend of percentage, 百分比趋势Trial, 试验Trial and error method, 试错法Tuning constant, 细调常数Two sided test, 双向检验Two-stage least squares, 二阶最小平方Two-stage sampling, 二阶段抽样Two-tailed test, 双侧检验Two-way analysis of variance , 双因素方差分析Two-way table, 双向表Type I error, 一类错误/α错误Type II error, 二类错误/β错误UMVU, 方差一致最小无偏估计简称Unbiased estimate, 无偏估计Unconstrained nonlinear regr ession , 无约束非线性回归Unequal subclass number, 不等次级组含量Ungrouped data, 不分组资料Uniform coordinate, 均匀坐标Uniform distribution, 均匀分布Uniformly minimum variance u nbiased estimate, 方差一致最小无偏估计Unit, 单元Unordered categories, 无序分类Upper limit, 上限Upward rank, 升秩Vague concept, 模糊概念Validity, 有效性VARCOMP (Variance component estimation), 方差元素估计Variability, 变异性Variable, 变量Variance, 方差Variation, 变异Varimax orthogonal rotation,方差最大正交旋转Volume of distribution, 容积W test, W检验Weibull distribution, 威布尔分布Weight, 权数Weighted Chi-square test, 加权卡方检验/Cochran检验Weighted linear regression m ethod, 加权直线回归Weighted mean, 加权平均数Weighted mean square, 加权平均方差Weighted sum of square, 加权平方和Weighting coefficient, 权重系数Weighting method, 加权法W-estimation, W估计量W-estimation of location, 位置W估计量Width, 宽度Wilcoxon paired test, 威斯康星配对法/配对符号秩和检验Wild point, 野点/狂点Wild value, 野值/狂值Winsorized mean, 缩尾均值Withdraw, 失访Youden's index, 尤登指数Z test, Z检验Zero correlation, 零相关Z-transformation, Z变换Summarize菜单项数值分析过程Frequencies子菜单项单变量的频数分布统计Descriptives子菜单项单变量的描述统计Explore子菜单项指定变量的综合描述统计Crosstabs子菜单项双变量或多变量的各水平组合的频数分布统计Compare Mean菜单项均值比较分析过程Means子菜单项单变量的综合描述统计Independent Sample T test子菜单项独立样本的T检验Paired Sample T test子菜单项配对样本的T检验One-Way ANOVA子菜单项一维方差分析(单变量方差分析)ANOVA Models菜单项多元方差分析过程Simple Factorial子菜单项因子设计的方差分析General Factorial子菜单项一般方差分析Multivariate子菜单项双因变量或多因变量的方差分析Repeated Factorial子菜单项因变量均值校验Correlate菜单项相关分析Bivariate子菜单项Pearson积矩相关矩阵和Kendall、Spearman非参数相关分析Partial子菜单项双变量相关分析Distance子菜单项相似性、非相似性分析Regression菜单项回归分析Liner子菜单项线性回归分析Logistic子菜单项二分变量回归分析(逻辑回归分析)Probit子菜单项概率分析Nonlinear子菜单项非线性回归分析Weight Estimation子菜单项不同权数的线性回归分析2-stage Least Squares子菜单项二阶最小平方回归分析Loglinear菜单项对数线性回归分析General子菜单项一般对数线性回归分析Hierarchical子菜单项多维交叉变量对数回归分析Logit子菜单项单因变量多自变量回归分析Classify菜单项聚类和判别分析K-means Cluster子菜单项指定分类数聚类分析Hierarchical Cluster子菜单项未知分类数聚类分析Discriminent子菜单项聚类判别函数分析Data Reduction菜单项降维、简化数据过程Factor子菜单项因子分析Correspondence Analysis子菜单项对应表(交叉表)分析Homogeneity Analysis子菜单项多重对应分析Nonlinear Components子菜单项非线性成分分析OVERALS子菜单项非线性典则相关分析Scale菜单项Reliability Ananlysis子菜单项加性等级的项目分析Multidimensional Scaling子菜单项多维等级分析Nonparametric Tests菜单项Chi-Square子菜单项相对比例假设检验Binomial子菜单项特定时间发生概率检验Run子菜单项随即序列检验1-Sample Kolmogorov Smirnov子菜单项样本分布检验2-Independent Samples子菜单项双不相关组分布分析K Independent Samples子菜单项多不相关组分布分析2 Related Samples子菜单项双相关变量分布分析McNemar' test子菜单项相关样本比例变化分析K Related Samples子菜单项相关变量分布分析Cocharn's Q test子菜单项二分变量均数检验Kendall's W子菜单项一致性判定。
Jet Impingement Heat Transfer Ch06-P020039

Jet Impingement Heat Transfer: Physics,Correlations,and Numerical ModelingN.ZUCKERMAN and N.LIORDepartment of Mechanical Engineering and Applied Mechanics,The University of Pennsylvania, Philadelphia,PA,USA;E-mail:zuckermn@;lior@I.SummaryThe applications,physics of theflow and heat transfer phenomena, available empirical correlations and values they predict,and numerical simulation techniques and results of impinging jet devices for heat transfer are described.The relative strengths and drawbacks of the k–e,k–o, Reynolds stress model,algebraic stress models,shear stress transport,and v2f turbulence models for impinging jetflow and heat transfer are compared. Select model equations are provided as well as quantitative assessments of model errors and judgments of model suitability.II.IntroductionWe seek to understand theflowfield and mechanisms of impinging jets with the goal of identifying preferred methods of predicting jet performance. Impinging jets provide an effective andflexible way to transfer energy or mass in industrial applications.A directed liquid or gaseousflow released against a surface can efficiently transfer large amounts of thermal energy or mass between the surface and thefluid.Heat transfer applications include cooling of stock material during material forming processes,heat treatment [1],cooling of electronic components,heating of optical surfaces for defogging,cooling of turbine components,cooling of critical machinery structures,and many other industrial processes.Typical mass transfer applications include drying and removal of small surface particulates. Abrasion and heat transfer by impingement are also studied as side effects of vertical/short take-off and landing jet devices,for example in the case of direct lift propulsion systems in vertical/short take-off and landing aircraft.Advances in Heat TransferVolume39ISSN0065-2717DOI:10.1016/S0065-2717(06)39006-5565Copyright r2006Elsevier Inc.All rights reservedADVANCES IN HEAT TRANSFER VOL.39566N.ZUCKERMAN AND N.LIORGeneral uses and performance of impinging jets have been discussed in a number of reviews[2–5].In the example of turbine cooling applications[6],impinging jetflows may be used to cool several different sections of the engine such as the combustor case(combustor can walls),turbine case/liner,and the critical high-temperature turbine blades.The gas turbine compressor offers a steadyflow of pressurized air at temperatures lower than those of the turbine and of the hot gasesflowing around it.The blades are cooled using pressurized bleed flow,typically available at6001C.The bleed air must cool a turbine immersed in gas of14001C total temperature[7],which requires transfer coefficients in the range of1000–3000W/m2K.This equates to a heatflux on the order of 1MW/m2.The ability to cool these components in high-temperature regions allows higher cycle temperature ratios and higher efficiency,improving fuel economy,and raising turbine power output per unit weight.Modern turbines have gas temperatures in the main turbineflow in excess of the temperature limits of the materials used for the blades,meaning that the structural strength and component life are dependent upon effective coolingflow. Compressor bleedflow is commonly used to cool the turbine blades by routing it through internal passages to keep the blades at an acceptably low temperature.The same air can be routed to a perforated internal wall to form impinging jets directed at the blade exterior wall.Upon exiting the blade,the air may combine with the turbine core airflow.Variations on this design may combine the impinging jet device with internalfins,smooth or roughened cooling passages,and effusion holes forfilm cooling.The designer may alter the spacing or locations of jet and effusion holes to concentrate theflow in the regions requiring the greatest cooling.Though the use of bleed air carries a performance penalty[8],the small amount offlow extracted has a small influence on bleed air supply pressure and temperature.In addition to high-pressure compressor air,turbofan engines provide cooler fan air at lower pressure ratios,which can be routed directly to passages within the turbine liner.A successful design uses the bleed air in an efficient fashion to minimize the bleedflow required for maintaining a necessary cooling rate. Compared to other heat or mass transfer arrangements that do not employ phase change,the jet impingement device offers efficient use of the fluid,and high transfer rates.For example,compared with conventional convection cooling by confinedflow parallel to(under)the cooled surface, jet impingement produces heat transfer coefficients that are up to three times higher at a given maximumflow speed,because the impingement boundary layers are much thinner,and often the spentflow after the impingement serves to turbulate the surroundingfluid.Given a required heat transfer coefficient,theflow required from an impinging jet device may be two orders of magnitude smaller than that required for a cooling approach usinga free wall-parallel flow.For more uniform coverage over larger surfaces multiple jets may be used.The impingement cooling approach also offers a compact hardware arrangement.Some disadvantages of impingement cooling devices are:(1)For moving targets with very uneven surfaces,the jet nozzles may have to be located too far from the surface.For jets starting at a large height above the target (over 20jet nozzle diameters)the decay in kinetic energy of the jet as it travels to the surface may reduce average Nu by 20%or more.(2)The hardware changes necessary for implementing an impinging jet device may degrade structural strength (one reason why impinging jet cooling is more easily applied to turbine stator blades than to rotor blades).(3)In static applications where very uniform surface heat or mass transfer is required,the resulting high density of the jet array and corresponding small jet height may be impractical to construct and implement,and at small spacings jet-to-jet interaction may degrade efficiency.Prior to the design of an impinging jet device,the heat transfer at the target surface is typically characterized by a Nusselt number (Nu ),and the mass transfer from the surface with a Schmidt number (Sc ).For design efficiency studies and device performance assessment,these values are tracked vs.jet flow per unit area (G )or vs.the power required to supply the flow (incremental compressor power).A.I MPINGING J ET R EGIONSThe flow of a submerged impinging jet passes through several distinct regions,as shown in Fig.1.The jet emerges from a nozzle or opening with a velocity and temperature profile and turbulence characteristics dependent upon the upstream flow.For a pipe-shaped nozzle,also called a tube nozzle or cylindrical nozzle,the flow develops into the parabolic velocity profile common to pipe flow plus a moderate amount of turbulence developed upstream.In contrast,a flow delivered by application of differential pressure across a thin,flat orifice will create an initial flow with a fairly flat velocity profile,less turbulence,and a downstream flow contraction (vena contracta).Typical jet nozzles designs use either a round jet with an axisymmetric flow profile or a slot jet ,a long,thin jet with a two-dimensional flow profile.After it exits the nozzle,the emerging jet may pass through a region where it is sufficiently far from the impingement surface to behave as a free submerged jet.Here,the velocity gradients in the jet create a shearing at the edges of the jet which transfers momentum laterally outward,pulling additional fluid along with the jet and raising the jet mass flow,as shown in Fig.2.In the process,the jet loses energy and the velocity profile is widened in spatial extent and decreased in magnitude along the sides of the jet.Flow interior to the 567JET IMPINGEMENT HEAT TRANSFERprogressively widening shearing layer remains unaffected by this momentum transfer and forms a core region with a higher total pressure,though it may experience a drop in velocity and pressure decay resulting from velocity gradients present at the nozzle exit.A free jet region may not exist if the nozzle lies within a distance of two diameters (2D )from the target.In such cases,the nozzle is close enough to the elevated static pressure in the stagnation region for this pressure to influence the flow immediately at the nozzle exit.If the shearing layer expands inward to the center of the jet prior to reaching the target,a region of core decay forms.For purposes of distinct identification,the end of the core region may be defined as the axial position where the centerline flow dynamic pressure (proportional to speed squared)reaches 95%of its original value.This decaying jet begins four to eight nozzle diameters or slot-widths downstream of the nozzle exit.In the decaying jet,the axial velocity component in the central part decreases,with theradialF IG .1.The flow regions of an impinging jet.568N.ZUCKERMAN AND N.LIORvelocity profile resembling a Gaussian curve that becomes wider and shorter with distance from the nozzle outlet.In this region,the axial velocity and jet width vary linearly with axial position.Martin [2]provided a collection of equations for predicting the velocity in the free jet and decaying jet regions based on low Reynolds number flow.Viskanta [5]further subdivided this region into two zones,the initial ‘‘developing zone,’’and the ‘‘fully developed zone’’in which the decaying free jet reaches a Gaussian velocity profile.As the flow approaches the wall,it loses axial velocity and turns.This region is labeled the stagnation region or deceleration region.The flow builds up a higher static pressure on and above the wall,transmitting the effect of the wall upstream.The nonuniform turning flow experiences high normal and shear stresses in the deceleration region,which greatly influence local transport properties.The resulting flow pattern stretches vortices in the flow and increases the turbulence.The stagnation region typically extends1.2nozzle diameters above the wall for round jets [2].Experimental work by Maurel and Solliec [9]found that this impinging zone was characterized or delineated by a negative normal-parallel velocity correlation (uv o 0).For their slot jet this region extended to 13%of the nozzle height H ,and did not vary with Re or H /D.F IG .2.The flow field of a free submerged jet.569JET IMPINGEMENT HEAT TRANSFERAfter turning,theflow enters a wall jet region where theflow moves laterally outward parallel to the wall.The wall jet has a minimum thickness within0.75–3diameters from the jet axis,and then continually thickens moving farther away from the nozzle.This thickness may be evaluated by measuring the height at which wall-parallelflow speed drops to some fraction(e.g.5%)of the maximum speed in the wall jet at that radial position.The boundary layer within the wall jet begins in the stagnation region,where it has a typical thickness of no more than1%of the jet diameter[2].The wall jet has a shearing layer influenced by both the velocity gradient with respect to the stationaryfluid at the wall(no-slip condition) and the velocity gradient with respect to thefluid outside the wall jet.As the wall jet progresses,it entrainsflow and grows in thickness,and its average flow speed decreases as the location of highestflow speed shifts progressively farther from the wall.Due to conservation of momentum,the core of the wall jet may accelerate after theflow turns and as the wall boundary layer develops.For a round jet,mass conservation results in additional deceleration as the jet spreads radially outward.B.N ONDIMENSIONAL H EAT AND M ASS T RANSFER C OEFFICIENTSA major parameter for evaluating heat transfer coefficients is the Nusselt number,Nu¼hD h=k cð1Þwhere h is the convective heat transfer coefficient defined ash¼Àk c@T.@n*T0jetÀT wallð2Þwhere@T/@n gives the temperature gradient component normal to the wall. The selection of Nusselt number to measure the heat transfer describes the physics in terms offluid properties,making it independent of the target characteristics.The jet temperature used,T0jet,is the adiabatic wall temperature of the decelerated jetflow,a factor of greater importance at increasing Mach numbers.The non-dimensional recovery factor describes how much kinetic energy is transferred into and retained in thermal form as the jet slows down:recovery factor¼T wallÀT0jetU2jet.2c pð3Þ570N.ZUCKERMAN AND N.LIORThis definition may introduce some complications in laboratory work,as a test surface is rarely held at a constant temperature,and more frequently held at a constant heat flux.Experimental work by Goldstein et al .[10]showed that the temperature recovery factor varies from 70%to 110%of the full theoretical recovery,with lowered recoveries in the stagnation region of a low-H /D jet (H /D ¼2),and 100%elevated stagnation region recoveries for jets with H /D ¼6and higher.The recovery comes closest to uniformity for intermediate spacings around H /D ¼5.Entrainment of surrounding flow into the jet may also influence jet performance,changing the fluid temperature as it approaches the target.The nondimensional Sherwood number defines the rate of mass transfer in a similar fashion:Sh ¼k i D =D ið4Þk i ¼D i @C =@n ÂÃ=C 0jet ÀC wall ÂÃð5Þwhere @C /@n gives the mass concentration gradient component normal to the wall.With sufficiently low mass concentration of the species of interest,the spatial distribution of concentration will form patterns similar to those of the temperature pattern.Studies of impinging air jets frequently use the nondimensional relation:Nu =Sh ¼Pr =Sc ÀÁ0:4ð6Þto relate heat and mass transfer rates.The nondimensional parameters selected to describe the impinging jet heat transfer problem include the fluid properties such as Prandtl number Pr (the ratio of fluid thermal diffusivity to viscosity,fairly constant),plus the following:H /D :nozzle height to nozzle diameter ratio; r /D :nondimensional radial position from the center of the jet; z /D :nondimensional vertical position measured from the wall;Tu :nondimensional turbulence intensity,usually evaluated at the nozzle; Re 0:Reynolds number U 0D /n ;M :Mach number (the flow speed divided by speed of sound in the fluid),based on nozzle exit average velocity (of smaller importance at low speeds,i.e.M o 0.3);p jet /D :jet center-to-center spacing (pitch)to diameter ratio,for multiple jets;571JET IMPINGEMENT HEAT TRANSFERAf :free area(¼1À[total nozzle exit area/total target area]);f:relative nozzle area(¼total nozzle exit area/total target area). Thefluid properties are conventionally evaluated using theflow at the nozzle exit as a reference location.Characteristics at the position provide the averageflow speed,fluid temperature,viscosity,and length scale D.In the case of a slot jet the diameter D is replaced in some studies by slot width B, or slot hydraulic diameter2B in others.A complete description of the problem also requires knowledge of the velocity profile at the nozzle exit,or equivalent information about theflow upstream of the nozzle,as well as boundary conditions at the exit of the impingement region.Part of the effort of comparing information about jet impingement is to thoroughly know the nature and magnitude of the turbulence in theflowfield.The geometry andflow conditions for the impinging jet depend upon the nature of the target and thefluid source(compressor or blower).In cases where the pressure drop associated with delivering and exhausting theflow is negligible,the design goal is to extract as much cooling as possible from a given air massflow.Turbine blade passage cooling is an example of such an application;engine compressor air is available at a pressure sufficient to choke theflow at the nozzle(or perhaps at some other point in theflow path).As the bleedflow is a small fraction of the overall compressorflow, the impinging jet nozzle pressure ratio varies very little with changes in the amount of airflow extracted.At high pressure ratios the jet emerges at a high Mach number.In the most extreme case,theflow exits the nozzle as an underexpanded supersonic jet.This jet forms complex interacting shock patterns and a stagnation or recirculation‘‘bubble’’directly below the jet (shown in Fig.3),which may degrade heat transfer[11].The details of the impingement device design affect the system pressuredrop and thus the overall device performance.In the case of adeviceF IG.3.Supersonic jetflow pattern. 572N.ZUCKERMAN AND N.LIORpowered by a blower or compressor,the blower power draw can be predicted using the required pressure rise,flow,and blower efficiency including any losses in the motor or transmission.For incompressible duct flow one can then estimate the power by multiplying the blower pressure rise D p by the volumetric flow Q and then dividing by one or more efficiency factors (e.g.,using a total efficiency of 0.52based on a 0.65blower aerodynamic efficiency times 0.80motor efficiency).This same approach works for calculating pump power when dealing with liquid jets,but becomes more complex when dealing with a turbine-cooling problem where compressibility is significant.The blower pressure rise D p depends on the total of the pressure losses in the blower intake pathway,losses in the flow path leading to the nozzle,any total pressure loss due to jet confinement and jet interaction,and any losses exiting the target region.In cases where space is not critical the intake pathway and nozzle supply pathway are relatively open,for there is no need to accelerate the flow far upstream of the nozzle exit.When possible,the flow is maintained at low speed (relative to U jet )until it nears the nozzle exit,and then accelerated to the required jet velocity by use of a smoothly contracting nozzle at the end of a wide duct or pipe.In such a case,the majority of the loss occurs at the nozzle where the dynamic pressure is greatest.For a cylindrical nozzle,this loss will be at least equal to the nozzle dump loss,giving a minimum power requirement of (0:5r U 2jet Q ).Jet impingement devices have pressure losses from the other portions of the flow path,and part of the task of improving overall device performance is to reduce these other losses.For this reason,one or more long,narrow supply pipes (common in experimental studies)may not make an efficient device due to high frictional losses approaching the nozzle exit.When orifice plate nozzles are used the upstream losses are usually small,but the orifices can cause up to 2.5times the pressure drop of short,smooth pipe nozzles (at a set Q and D ).This effect is balanced against the orifice nozzle’s larger shear layer velocity gradient and more rapid increase in turbulence in the free-jet region [12].Such orifice plates take up a small volume for the hardware,and are relatively easy and inexpensive to make.A thicker orifice plate (thickness from 0.3D to 1.5D )allows the making of orifice holes with tapered or rounded entry pathways,similar to the conical and bellmouth shapes used in contoured nozzles.This compromise comes at the expense of greater hardware volume and complexity,but reduces the losses associated with accelerating the flow as it approaches the orifice and increases the orifice discharge coefficient (effective area).Calculation of nozzle pressure loss may use simple handbook equations for a cylindrical nozzle [13,14],but for an orifice plate the calculations may require more specialized equations and test data (cf.[15,16]).573JET IMPINGEMENT HEAT TRANSFERTable I compares characteristics of the most common nozzle geometries in a qualitative fashion.C.T URBULENCE G ENERATION AND E FFECTSJet behavior is typically categorized and correlated by its Reynolds number Re ¼U 0D /n ,defined using initial average flow speed (U 0),the fluid viscosity (n )and the characteristic length that is the nozzle exit diameter D or twice the slot width,2B (the slot jet hydraulic diameter).At Re o 1000the flow field exhibits laminar flow properties.At Re 43000the flow has fully turbulent features.A transition region occurs with 1000o Re o 3000[5].Turbulence has a large effect on the heat and mass transfer rates.Fully laminar jets are amenable to analytical solution,but such jets provide less heat transfer at a given flow rate than turbulent ones,and therefore much more literature exists for turbulent impinging jets.For example,an isolated round jet at Re ¼2000(transition to turbulence),Pr ¼0.7,H /D ¼6will deliver an average Nu of 19over a circular target spanning six jet diameters,while at Re ¼100,000the average Nu on the same target will reach 212[2].In contrast,laminar jets at close target spacing will give Nu values in the range of 2–20.In general,the exponent b in the relationship Nu p Re b ranges from b ¼0.5for low-speed flows with a low-turbulence wall jet,up to b ¼0.85for high Re flows with a turbulence-dominated wall jet.As an example of the possible extremes,Rahimi et al .[17]measured local Nu values as high as 1700for a under-expanded supersonic jet at Re ¼(1.028)Â106.Typical gas jet installations for heat transfer span a Reynolds number range from 4000to 80,000.H /D typically ranges from 2to 12.Ideally,Nu increases as H decreases,so a designer would prefer to select the smallest tolerable H value,noting the effects of exiting flow,manufacturing TABLE IC OMPARISONOF N OZZLE -T YPE C HARACTERISTICS Nozzle type InitialturbulenceFree jet shearing force Pressure drop Nozzle exit velocity profile Pipe HighLow High Close to parabolic Contoured contraction LowModerate to high Low Uniform (flat)Sharp orificeLow High High Close to uniform(contracting)574N.ZUCKERMAN AND N.LIORcapabilities,and physical constraints,and then select nozzle size D accordingly.For small-scale turbomachinery applications jet arrays commonly have D values of0.2–2mm,while for larger scale industrial applications,jet diameters are commonly in the range of5–30mm. The diameter is heavily influenced by manufacturing and assembly capabilities.Modeling of the turbulentflow,incompressible except for the cases where the Mach number is high,is based on using the well-established mass, momentum,and energy conservation equations based on the velocity, pressure,and temperature:@u i@x i¼0ð7Þr @u i@tþr u i@u j@x j¼À@p@x iþ@s ij@x jþ@t ij@x jð8Þr @u i@tþr u i@u j@x j¼À@p@x iþ@@x jm@u i@x jþ@u j@x i!þ@@x jÀr0ijðalternate formÞð9Þr c p @T@tþr c p u j@T@x j¼s ij@u i@x jþ@@x jm c pPr@T@x jþ@@x jÀr c p u0j T0ÀÁþm@u0i@x jþ@u0j@x i@u0i@x jð10Þs ij¼m@u i@x jþ@u j@x ið11Þt ij¼Àr u0i u0jð12Þwhere an overbar above a single letter represents a time-averaged term, terms with a prime symbol(0)representfluctuating values,and a large overbar represents a correlation.The second moment of the time variant momentum equation,adjusted to extract thefluctuating portion of theflowfield,yields the conserva-tive transport equation for Reynolds stresses,shown for an incompressiblefluid[18]:@t ij @t þ"u k@t ij@x k¼Àt ik@"u j@x kÀt jk@"u i@x k!þp0r@u0i@x jþ@u0j@x i"#þ@@x kÀu0iu0j u0kÀp0ru0id jkþu0j d ikn o!þÀ2n@ui@x k@u0j@x k"#þn@2t ij@x k@x k!ð13ÞEach term of this equation has a specific significance.The term@t ij@t þu k@t ij@x krepresents convective transport of Reynoldsstresses.The termÀt ik@"u j@x k Àt jk@"u i@x kmeasures turbulent production of Reynoldsstresses.The term p0r@ui@x jþ0j@x imeasures the contribution of the pressure-strainrate correlation to Reynolds stresses.The term@@x kÀu0iu0j u0kÀp0ru0id jkþu0j d ikn ogives the effects of thegradient of turbulent diffusion.The termÀ2n@u0i@x kj@x krepresents the effects of turbulent dissipation.The term n@2t ij@x k@x krepresents the effects of molecular diffusion.The specific turbulent kinetic energy k,gives a measure of the intensity of the turbulentflowfield.This can be nondimensionalized by dividing it by the time-averaged kinetic energy of theflow to give the turbulence intensity, based on a velocity ratio:Tu¼ffiffiffiffiffiffiffiffiu0j u0j"u i"u isð14ÞIn addition to generation in the impinging jetflowfield itself,turbulence in theflowfield may also be generated upstream of the nozzle exit and convected into theflow.This often takes place due to the coolantflow distribution configuration,but can also be forced for increasing the heat transfer coefficients,by inserting various screens,tabs,or other obstructions in the jet supply pipe upstream of or at the nozzle.Experimental work has shown that this decreases the length of the jet core region,thus reducing theH/D at which the maximal Nu avg is reached[19].The downstreamflow and heat transfer characteristics are sensitive to both the steady time-averaged nozzle velocity profile andfluctuations in the velocity over time.Knowledge of these turbulentfluctuations and the ability to model them,including associated length scales,are vital for understanding and comparing the behavior and performance of impinging jets.In the initial jet region the primary source of turbulence is the shearflow on the edges of the jet.This shear layer may start as thin as a knife-edge on a sharp nozzle,but naturally grows in area along the axis of the jet.At higher Reynolds numbers,the shear layer generatesflow instability,similar to the Kelvin–Helmholtz instability.Figure4presents in a qualitative fashion the experimentally observed pattern of motion at the edges of the unstable free jet.At highflow speeds(Re41000)the destabilizing effects of shear forces may overcome the stabilizing effect offluid viscosity/momentum diffusion. The position of the shear layer and its velocity profile may develop oscillations in space,seemingly wandering from side to side over time. Further downstream,the magnitude and spatial extent of the oscillations grow to form large-scale eddies along the sides of the jet.The largest eddies have a length scale of the same order of magnitude as the jet diameter and persist until they either independently break up into smaller eddies or meet and interact with other downstreamflow features.The pressurefield of the stagnation region further stretches and distorts the eddies,displacing them laterally until they arrive at the wall.F IG.4.Instability in the turbulent free jet.Experiments by Hoogendorn[20]found that the development of turbulence in the free jet affected the profile of the local Nu on the target stagnation region as well as the magnitude.For pipe nozzles and for contoured nozzles at high spacing(z/D45)the Nu profiles had a peak directly under the jet axis.For contoured nozzles at z/D¼2and4with low initial turbulence(Tu$1%),the maximum Nu occurred in the range0.4o r/D o0.6 with a local minimum at r¼0,typically95%of the peak value.In the decaying jet region the shear layer extends throughout the center of the jet.This shearing promotesflow turbulence,but on smaller scales.The flow in the decaying jet may form small eddies and turbulent pockets within the center of the jet,eventually developing into a unstructured turbulent flowfield with little or no coherent structures in the entire jet core.In the deceleration region,additional mechanisms take part in influencing flowfield turbulence.The pressure gradients within theflowfield cause the flow to turn,influencing the shear layer and turning and stretching large-scale structures.The deceleration of theflow creates normal strains and stresses,which promote turbulence.Numerical models by Abe and Suga[21] showed that the transport of heat or mass in this region is dominated by large-scale eddies,in contrast to the developed wall jet where shear strains dominate.Theflow traveling along the wall may make a transition to turbulence in the fashion of a regular parallel wall jet,beginning with a laminarflow boundary layer region and then reaching turbulence at some lateral position on the wall away from the jet axis.For transitional and turbulent jets,the flow approaching the wall already has substantial turbulence.This turbulent flowfield may contain largefluctuations in the velocity component normal to the wall,a phenomenon distinctly different than those of wall-parallel shearflows[22].Large-scale turbulentflow structures in the free jet have a great effect upon transfer coefficients in the stagnation region and wall jet.The vortices formed in the free jet-shearing layer,categorized as primary vortices,may penetrate into the boundary layer and exchangefluids of differing kinetic energy and temperature(or concentration).The ability of the primary vortex to dynamically scrub away the boundary layer as it travels against and along the wall increases the local heat and mass transfer.The turbulentflowfield along the wall may also cause formation of additional vortices categorized as secondary vortices.Turbulentfluctuations in lateral/radial velocity and associated pressure gradientfluctuations can produce localflow reversals along the wall,initiating separation and the formation of the secondary vortices,as shown in Fig.5.Secondary vortices cause local rises in heat/mass transfer rates and like the primary vortices。
Correlation

CorrelationXu JiajinNational Research Center for Foreign Language Education Beijing Foreign Studies University2Key points•Why correlation?•What is correlation analysis about?•How to make a correlation analysis?–Case studiesWhy Correlation?4Three things that stats can do •1.Summarizing univariate data •2.Testing the significance of differences •3.Exploring relationships b/t variables5Three things that stats can do •1.Summarizing univariate data •2.Testing the significance of differences •3.Exploring relationships b/t variables6探究事物之间的关联•植物的生长是否浇水的多少有关系,有多大关系•足球成绩好坏是否与身体(体质、人种)有关?•兴趣高、成绩好•元认知策略使用越多,学习进步越快•学好统计学有利于身体健康Key ides of correlationanalysis8•Correlation: co ‐relation . The co ‐relation is represented by a ‘correlation coefficient , r .•The range of the coefficient: ‐1to 1.•Three critical values: ‐1, 0and 1.Strength of correlationPositive correlation Strength of correlation Direction of correlationDirection of correlation Positive correlationDirection of correlation•Less Negative correlation12Two main types of correlation•Pearson : standard type, suitable for interval data (e.g. score, freq.)•Pearson r coefficient•Spearman : suitable for ordinal/rank data•Spearman rho coefficient13Significance•Similar to t ‐test and ANOVA statistics, the correlation coefficients need to be statistically significant.< .05Sig./P 值/alpha (α)值Coefficient of Determination r Ær2Æ% of variance explained15Coefficient of Determination •The squared correlation coefficient is called the coefficient of determination .•Multiplied by 100, this proportion of variance indicates the percentage of variance that is accounted for.•Correlation coefficients of .30 account for about 9% of the variance. Correlation of .70 explains about 49% of variance.Effect sizeCase Study 1Is connector use by Chinese EFL learners correlated with theirwriting quality?SPSS ProceduresAnalyze‐Correlate‐Bivariate1921Reporting correlations•In correlation tables/matrices •Embedded in textCorrelation tablesCorrelation tables(Dörnyei2007: 227)2324Embedded in text •As one would expect from the extensive literature documenting the benefits of intrinsic motivation, there was a significant positive correlation between overall GPA and intrinsic motivation (r = .34, p < .oo1).(Dörnyei 2007: 227)Practice: CET4 and CET6 Correlational analysisHomework英语成绩是否与语文成绩有相关性?28Wrap Up & Look Forward •Correlation coefficients provide a way to determine the strength & the direction of the relationship b/t two variables.•This index does not ... demonstrate a causal association b/t two variables.29Wrap Up & Look Forward •The coefficient of determination determines how much variance in one variable is explained by another variable.•Correlation coefficients are the precursors to the more sophisticated statistics involved in multiple regression (Urdan 2005: 87).30Thank you32。
国际商务英语函电课件

The History and Development of Response
• Early Development: The use of relevance in international business can be traced back to the early days of the Industrial Revolution, when businesses need to communicate with suppliers and customers across national borders
Addressing the recipient property
Use the correct title, name, and contact information of the recipient
Clear subject line
Provide a conclusion and descriptive subject line to indicate the purpose of your message
• Documenting Transactions: Correspondence provides a written record of business transactions, which can be used for legal purposes in case of any disputes or misunderstandings
Courtesy
Be political and interested in your language, and show graduation and application when necessary
Temporal correlations of orientations
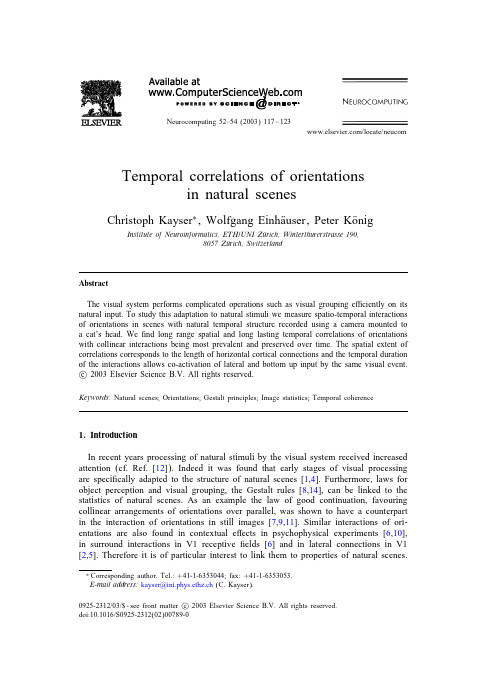
Neurocomputing52–54(2003)117–123/locate/neucom Temporal correlations of orientationsin natural scenesChristoph Kayser∗,Wolfgang Einh a user,Peter K o nigInstitute of Neuroinformatics,ETH/UNI Z u rich,Winterthurerstrasse190,8057Z u rich,SwitzerlandAbstractThe visual system performs complicated operations such as visual grouping e ciently on its natural input.To study this adaptation to natural stimuli we measure spatio-temporal interactions of orientations in scenes with natural temporal structure recorded using a camera mounted to a cat’s head.Weÿnd long range spatial and long lasting temporal correlations of orientations with collinear interactions being most prevalent and preserved over time.The spatial extent of correlations corresponds to the length of horizontal cortical connections and the temporal duration of the interactions allows co-activation of lateral and bottom up input by the same visual event.c 2003Elsevier Science B.V.All rights reserved.Keywords:Natural scenes;Orientations;Gestalt principles;Image statistics;Temporal coherence1.IntroductionIn recent years processing of natural stimuli by the visual system received increased attention(cf.Ref.[12]).Indeed it was found that early stages of visual processing are speciÿcally adapted to the structure of natural scenes[1,4].Furthermore,laws for object perception and visual grouping,the Gestalt rules[8,14],can be linked to the statistics of natural scenes.As an example the law of good continuation,favouring collinear arrangements of orientations over parallel,was shown to have a counterpart in the interaction of orientations in still images[7,9,11].Similar interactions of ori-entations are also found in contextual e ects in psychophysical experiments[6,10], in surround interactions in V1receptiveÿelds[6]and in lateral connections in V1 [2,5].Therefore it is of particular interest to link them to properties of natural scenes.∗Corresponding author.Tel.:+41-1-6353044;fax:+41-1-6353053.E-mail address:kayser@ini.phys.ethz.ch(C.Kayser).0925-2312/03/$-see front matter c 2003Elsevier Science B.V.All rights reserved.doi:10.1016/S0925-2312(02)00789-0118 C.Kayser et al./Neurocomputing52–54(2003)117–123To our knowledge,however,up to now correlations in natural scenes have only been investigated in still images.This neglects the temporal structure and it remains un-clear whether these correlations persist on time scales relevant for lateral interactions in the cortex.Given the possibly long delays for tangential connections,correlations must extend over substantial temporal periods in order to fully cover the spatial extent of long-range connections.Furthermore,some of the previous studies did not report ÿlter or correlation scales in units of degrees of visual angle leaving possible links to anatomical scales uncertain.Finally,some of the previous studies used still images captured by humans,therefore introducing a possible artistic or anthropocentric bias. Here we address these issues and study spatio-temporal interactions of orientations in a large database of natural movies captured by a camera mounted to a cat’s head.2.MethodsWe recorded movie sequences using a removable lightweight CCD-camera(Conrad electronics,Hirschau,Germany)mounted to the head of cats while taken for walks in di erent local environments like grassland,forest and the university campus.These videos contain a large variety of di erent speeds and accelerations as a result of the natural movements of the cat.Fig.1shows four sample images of our database.For this study a total of three animals was used and all procedures are in agreement with national and institutional guidelines for animal care.Videos were recorded via a cable connected to the leash onto a standard VHS-VCR (Pal)carried by the human experimenter and digitised o ine at a temporal resolution of25Hz,320×240pixels(1pixels≈12min of arc)and16bit color depth.For this study videos were converted to8-bit gray scale and12sequences(about40000frames total)were used.Before further processing the images were normalized to zero mean. The image statistics was investigated using oriented wavelets.Single frames were convolved with pairs of circular Gabor wavelets of90◦relative phase shift.Filters had a envelope of20pixel width and a spatial frequency of7(1/pixels).The amplitude of the orientation was computed by summing the squared amplitudes of two phaseFig.1.Four sample frames of our database are shown on the left.The amplitudes of the oriented energy detectors for the same frames is shown on the right.The bards indicate the orientation of the respective ÿlters used.C.Kayser et al./Neurocomputing 52–54(2003)117–123119shifted ÿlters and subjecting the result to a square root,resembling a two subunit en-ergy model.At each point the amplitudes of eight equally spaced orientations from 0◦(horizontal)to 157:5◦were computed.We deÿne the ‘prominent’orientation of each point by averaging the amplitude vectors (length =amplitude of ÿlter response ;orientation =orientation of the ÿlter)of the eight ÿlters.The resulting vector average has an orientation ,deÿning the prominent orientation of the point,and a length A ( ;x;t ),specifying the magnitude of the local orientation strength.For computa-tional convenience these orientations were binned into 16bin between 0◦and 180◦.The second order statistics of these orientations was calculated assuming transla-tion invariance of natural images.Thus correlations of two prominent orientations 1and 2were computed over all pairs of points with the same spatial separation x and temporal separation t (the mean runs over all points (x;t )with prominent orientation 1).C ( 1; 2; x; t )= (A ( 1;x;t )− A ( 1;x;t ) )∗(A ( 2;x + x;t + t )− A ( 2;x + x;t + t ) ) (A ( 1;x;t )− A ( 1;x;t ) )2 ∗ (A ( 2;x + x;t + t )− A ( 2;x + x;t + t ) )2 :Correlations were computed for temporal lags from t =0to 30frames (1:2s)and on a spatial grid of points spaced about 2◦apart.Therefore the kernels overlapped only for the smallest spatial distance used.As a control we also computed correlations using the maximally active orientation at each point instead of the ‘prominent’orientation yielding similar results as reported below.3.ResultsFirst we investigate temporal correlations at the same point in space.Fig.2A demon-strates that if an orientation is present at one point in time then the amplitude of this orientation in the next frames at the same point is also likely to be high.Temporal correlations are strongest for the cardinal orientations,i.e.horizontal and vertical.For the other orientations correlations decay faster but are still signiÿcant over several hun-dreds of milliseconds (decay time constants for 0◦:¿1s,45◦:490ms,90◦:900ms,135◦:360ms).Thus the presence of an oriented segment gives a strong prediction for the orientation at the same point later in time.Next we look at the two dimensional spatial distribution of correlations as well as correlations of di erent orientations.Fig.2B shows the correlations between segments of 4di erent orientations (0◦;45◦;90◦;135◦)situated at di erent relative locations in the same frame.Iso-orientation correlations (panels on the diagonal)are stronger than cross-orientation correlations.Furthermore the contour lines of the iso-orientation correlations are elongated along the direction of the particular orientation.This shows that collinear structures are more prevalent than parallel shifted contours.Also parallel contours occur more likely than T-junctions since the iso-orientation correlations are at all points stronger than the correlations of this orientation with the orthogonal.An example of how the spatial correlations decay independently of the spatial direction is120 C.Kayser et al./Neurocomputing52–54(2003)117–123Fig.2.(A)The correlation of orientation amplitude over time at the same pixel.Squares:0◦,stars:90◦, dashed:all other orientations(spaced22:5◦).(B)Correlations of di erent combinations of orientations and di erent spatial arrangements of the two points in the same frame.The orientations are(from top to bottom and left to right):0◦;135◦;90◦;45◦.(C)Correlations over time of points with prominent horizontal orientation but which are spatially separated by di erent distances independent of the relative orientation. Squares:2.1deg spatial distance,stars:4:2◦,dashed:6:4◦,diamonds:8:4◦.(D)Same as in B but here the two points are also separated by400ms in time.shown in Fig.2C for the horizontal(90◦)orientation.Correlations decay fastest during theÿrst2◦of spatial distance but extend well up to8◦.Our data set allows analyzing how these spatial correlations evolve over time.Fig.2D shows the same data as in Fig.2B but for segments400ms apart in time.The spatial arrangement of correlations is the same as for zero time lag but the amplitudes decayed by a factor higher than2.For the cardinal orientations again collinear interactions are prevalent.This is in agreement with Fig.2A which shows that these orientations are very stable over time.Since the oblique orientations are less well correlated over time we would expect that collinearity will here be less prominent for larger time lags.Indeed the contour lines of the correlations for the oblique orientations are more circular symmetric.To quantify these changes over time we measure the aspect ratio (length/width)of the contour lines for the di erent time lags.Collinearity means a high aspect ratio and a loss of collinearity therefore is accompanied with a decreaseC.Kayser et al./Neurocomputing52–54(2003)117–123121Fig.3.(A)Relative change of the aspect ratio of the correlation contours in Fig.2C as a function of time. Shows is the aspect ratio at each point in time divided by the aspect ratio at t=0.Squares:0◦,stars:90◦, solid:45◦,dashed:135◦.(B)Areas of strong correlations.We deÿned spatio temporal separations with a correlation over0.4as strong.Theÿgure shows these areas for the correlation diagram of Fig.2C.(C) Shows the size of these areas relative to the total patch size over time.Lines are labeled as in A.in aspect ing this measure,Fig.3A shows that collinearity is preserved over long temporal lags and is strongest for the cardinal orientations.To quantify the change in amplitude of the spatial correlations in a di erent way,we deÿne areas of strong interactions by thresholding correlations.We chose a threshold of0.4to ensure that even for zero time-lag only iso-orientation correlations exceed this threshold(Fig.3B).As expected from Fig.2the decay times are slowest for the cardinal orientations but independent of the orientation there exist points with strong correlations for at least280ms(Fig.3C).We performed controls to see how these results depend on the amount of data used. The above data were averaged over our whole database.Since one feature of our video sequences is their variety in terms of landscapes,etc.we look at the di erences between di erent sequences.In Fig.4we show the correlations for one oblique orien-tation(135◦).The mean and standard deviation over12video sequences is shown in Fig.4A.The error is rather small compared to the correlation values.More importantly, the correlation surface plus minus the error(Fig.4B)shows the same spatial structure as the mean.Also,the distinct pattern of correlations is visible in averages over shorter sequences(data not shown).Thus the distinct patterns of spatial correlations are not introduced by averaging over a large data set.As a further control,we useÿlters of a di erent spatial scale and frequency to measure the orientation content.Theÿlters used for Fig.4C are twice as large as the ones used for the other experiments.The results are basically the same as with the lower frequencyÿlters.Again collinearity is most prevalent.Therefore our results generalize over a wide range ofÿlter parameters.122 C.Kayser et al./Neurocomputing52–54(2003)117–123Fig.4.(A)For an example orientation(45◦)we show the mean(left)over12video sequences together with the standard deviation(right).(B)The mean plus=minus the standard deviation.(C)Cross orientation correlations over space forÿlters of a higher spatial frequency.4.DiscussionWe recorded natural image sequences from a camera mounted to a cat’s head closely matching the animal’s visual input.Thereby our database circumvents possible artistic or anthropocentric biases introduced in pictures and movies taken by humans.The database contains a large set of di erent environments,ranging from forest to grasslands and university campus.Furthermore the used sequences were recorded in di erent seasons and times of day providing a huge variety of lighting conditions.In respect to the temporal analysis it is worth noting that our video sequences contain natural movements of an animal,which might di er considerably from mercial movies ÿlmed by humans.In qualitative agreement with previous studies[7,9,11]weÿnd spatial correlations corresponding to the Gestalt laws.For all orientations collinear contours are more prevalent than parallel contours and correlations between orthogonal orientations are weakest.However weÿnd correlations over distances of up to8degrees of visual angle(Fig.2).This is considerably larger than distances reported in previous studies. For example Kaschube et al.[7]ÿnd that already for small distances correlations are relatively weak(¡0:15in a range from1◦to4◦).However,they do not indicate the size of their kernels in the same units.Sigman et al.[11]report similar correlations usingÿlters of size smaller than10min of arc.Our higher correlation could be due to methodological di erences to other studies besides the use of di erent and possibly larger kernels.We computed the‘prominent’orientation of a point by vector averaging the outputs of8oriented energy detectors.But correlations computed on these promi-nent orientations are very similar to correlations computed on the maximally active orientation(data not shown)a method used in Ref.[11].The spatial distances of the correlations reported hereÿt well with anatomical data on long-range horizontal connections in primary visual cortex.In cat V18◦of visualC.Kayser et al./Neurocomputing52–54(2003)117–123123 angle correspond roughly to8mm[13].This is also the extent of long-range connec-tions which preferentially connect iso-orientation domains[5]and in some mammals preferentially mediate collinear interactions[2].In the temporal domain weÿnd long lasting correlations of orientations to extend several hundreds of milliseconds preserving their spatial structure i.e.collinearity.These persist su ciently long to allow bottom up and long range lateral input to be coactive and driven by the same orientated structure even given the slow speeds of lateral con-nections reported in Ref.[3].Therefore the spatio-temporal interactions of orientations seem to fully cover the range of tangential connections and provide a substrate that could also guide the development of orientation maps and long-range connections in primary visual cortex.AcknowledgementsThis work wasÿnancially supported by the Centre of Neuroscience Zurich, (ZNZ),Honda R&D Europe(Germany)and the Swiss national fund(SNF grant No.31-65415.01).References[1]J.J.Atick,A.N.Redlich,What does the retina know about natural scenes,Neural Comput.4(1992)196–210.[2]W.H.Bosking,Y.Zhang,B.Schoÿeld,D.Fitzpatrick,Orientation selectivity and the arrangement ofhorizontal connections in tree shrew striate cortex,J.Neurosci.17(6)(1997)2112–2127.[3]V.Bringuier,F.Chavane,L.Glaeser,Y.Fregnac,Horizontal propagation of visual activity in thesynaptic integrationÿeld of area17neurons,Sci.283(1999)695–699.[4]Y.Dan,J.J.Atick,R.C.Reid,E cient coding of natural scenes in the lateral geniculate nucleus:experimental test of a computational theory,J.Neurosci.16(10)(1996)3351–3362.[5]C.D.Gilbert,T.N.Wiesel,Columnar speciÿcity of intrinsic horizontal and corticocortical connectionsin cat visual cortex,J.Neurosci.9(7)(1989)2432–2442.[6]M.K.Kapadia,M.Ito,C.D.Gilbert,G.Westheimer,Improvement in visual sensitivity by changesin local context:Parallel studies in human observers and in V1of alert monkeys,Neuron15(1995) 843–856.[7]M.Kaschube,F.Wolf,T.Geisel,S.L o wel,The prevalence of collinear contours in the real world,Neurocomputing38–40(2001)1335–1339.[8]K.Kofka,Principles of Gestalt Psychology,Harcourt&Brace,New York,1935.[9]N.Krueger,Collinearity and parallelism are statistically signiÿcant second order relations of complexcell responses,Neural Process.Lett.8(1998)117–129.[10]U.Polat,D.Sagi,Spatial interactions in human vision:from near to far via experience dependentcascades of connections,A91(1994)1206–1209.[11]M.Sigman,G.A.Cecchi,C.D.Gilbert,M.O.Magnasco,On a common circle:natural scenes and Gestaltrules,Proc.Natl.Acad.Sci.98(4)(2001)1935–1940.[12]E.P.Simoncelli,B.A.Olshausen,Natural image statistics and neural representation,Ann.Rev.Neurosci.24(2001)1193–1215.[13]R.J.Tusa,A.C.Rosenquist,L.A.Palmer,Retinotopic organization of areas18and19in the cat,p.Neurol.185(1979)657–678.[14]M.Wertheimer,Laws of Organization in the Perceptual Form,Harcourt&Brace,USA,1938.。
数据分析英语试题及答案

数据分析英语试题及答案一、选择题(每题2分,共10分)1. Which of the following is not a common data type in data analysis?A. NumericalB. CategoricalC. TextualD. Binary2. What is the process of transforming raw data into an understandable format called?A. Data cleaningB. Data transformationC. Data miningD. Data visualization3. In data analysis, what does the term "variance" refer to?A. The average of the data pointsB. The spread of the data points around the meanC. The sum of the data pointsD. The highest value in the data set4. Which statistical measure is used to determine the central tendency of a data set?A. ModeB. MedianC. MeanD. All of the above5. What is the purpose of using a correlation coefficient in data analysis?A. To measure the strength and direction of a linear relationship between two variablesB. To calculate the mean of the data pointsC. To identify outliers in the data setD. To predict future data points二、填空题(每题2分,共10分)6. The process of identifying and correcting (or removing) errors and inconsistencies in data is known as ________.7. A type of data that can be ordered or ranked is called________ data.8. The ________ is a statistical measure that shows the average of a data set.9. A ________ is a graphical representation of data that uses bars to show comparisons among categories.10. When two variables move in opposite directions, the correlation between them is ________.三、简答题(每题5分,共20分)11. Explain the difference between descriptive andinferential statistics.12. What is the significance of a p-value in hypothesis testing?13. Describe the concept of data normalization and its importance in data analysis.14. How can data visualization help in understanding complex data sets?四、计算题(每题10分,共20分)15. Given a data set with the following values: 10, 12, 15, 18, 20, calculate the mean and standard deviation.16. If a data analyst wants to compare the performance of two different marketing campaigns, what type of statistical test might they use and why?五、案例分析题(每题15分,共30分)17. A company wants to analyze the sales data of its products over the last year. What steps should the data analyst take to prepare the data for analysis?18. Discuss the ethical considerations a data analyst should keep in mind when handling sensitive customer data.答案:一、选择题1. D2. B3. B4. D5. A二、填空题6. Data cleaning7. Ordinal8. Mean9. Bar chart10. Negative三、简答题11. Descriptive statistics summarize and describe thefeatures of a data set, while inferential statistics make predictions or inferences about a population based on a sample.12. A p-value indicates the probability of observing the data, or something more extreme, if the null hypothesis is true. A small p-value suggests that the observed data is unlikely under the null hypothesis, leading to its rejection.13. Data normalization is the process of scaling data to a common scale. It is important because it allows formeaningful comparisons between variables and can improve the performance of certain algorithms.14. Data visualization can help in understanding complex data sets by providing a visual representation of the data, making it easier to identify patterns, trends, and outliers.四、计算题15. Mean = (10 + 12 + 15 + 18 + 20) / 5 = 14, Standard Deviation = √[(Σ(xi - mean)^2) / N] = √[(10 + 4 + 1 + 16 + 36) / 5] = √52 / 5 ≈ 3.816. A t-test or ANOVA might be used to compare the means ofthe two campaigns, as these tests can determine if there is a statistically significant difference between the groups.五、案例分析题17. The data analyst should first clean the data by removing any errors or inconsistencies. Then, they should transformthe data into a suitable format for analysis, such ascreating a time series for monthly sales. They might also normalize the data if necessary and perform exploratory data analysis to identify any patterns or trends.18. A data analyst should ensure the confidentiality andprivacy of customer data, comply with relevant data protection laws, and obtain consent where required. They should also be transparent about how the data will be used and take steps to prevent any potential misuse of the data.。
a customer loyalty model for e service context

A CUSTOMER LOYALTY MODEL FOR E-SERVICE CONTEXTPin LuarnDepartment of Business AdministrationNational Taiwan University of Science and Technologyluarn@.twHsin-Hui LinDepartment of Business AdministrationNational Taiwan University of Science and Technologybrenda@.twABSTRACTWhile the importance of customer loyalty has been recognized in the marketing literature for at least three decades, the conceptualization and empirical validation of a customer loyalty model for e-service context has not been addressed. This paper describes a theoretical model for investigating the three main antecedent influences on loyalty (attitudinal commitment and behavioral loyalty) for e-service context: trust, customer satisfaction, and perceived value. Based on the theoretical model, a comprehensive set of hypotheses were formulated and a methodology for testing them was outlined. These hypotheses were tested empirically to demonstrate the applicability of the theoretical model. The results indicate that trust, customer satisfaction, perceived value, and commitment are separate constructs that combine to determine the loyalty, with commitment exerting a stronger influence than trust, customer satisfaction, and perceived value. Customer satisfaction and perceived value were also indirectly related to loyalty through commitment. Finally, the authors discuss the managerial and theoretical implications of these results.Keywords: Loyalty, e-service, trust, customer satisfaction, perceived value1. IntroductionRetaining customers is a financial imperative for electronic vendor (e-vendor), especially as attracting new customers is considerably more expensive than for comparable, traditional, bricks-and-mortar stores (Reichheld and Schefter, 2000). Understanding how or why a sense of loyalty develops in customers remains one of the crucial management issues of our day. Aaker (1991) has discussed the role of loyalty in the brand equity process and has specifically noted that brand loyalty leads to certain marketing advantages such as reduced marketing costs, more new customers, and greater trade leverage. In increasingly competitive markets, being able to build loyalty in consumers is seen as the key factor in winning market share (Jarvis and Mayo, 1986) and developing sustainable competitive advantage (Kotler and Singh, 1981). While the importance of brand loyalty has been recognized in the marketing literature for at least three decades (Howard and Sheth, 1969), the conceptualization and empirical validation of a loyalty model for e-service context has not been addressed. E-commerce success, especially in the business-to-consumer area, is determined in part by whether consumers show loyalty to a particular e-service provider they cannot touch. Thus, research attention should more fruitfully focus on the development and validation of a loyalty model for e-service context.Recognizing that a vital key to retaining customers is maintaining their trust in the e-vendor (Reichheld and Schefter, 2000), this study investigates customer trust as a primary factor for customer commitment and loyalty. In addition, our study incorporates customer satisfaction and perceived value as additional explanatory variables in understanding the determinants of why online customers show attitudinal commitment and behavioral purchase loyalty to a specific e-service provider. Accordingly, the primary purpose of this study is to explore the factors (i.e., customer satisfaction, trust, and perceived value) that influence attitudinal commitment and purchase loyalty in an e-service environment. This paper is structured as follows. First, we discuss the concept of e-service. Subsequently, the study defines the constructs of interest and develops a model of the relationships between the constructs. A comprehensive review of the marketing literature provides a theoretical basis for clarifying what the constructs mean. Next, hypotheses were proposed concerning these relationships. The methods, measures, and results of this study were then presented. Finally, the results were discussed in terms of their implications for research and managerial activity. Based on the findings of this study, Internet marketers will be able to justify expenditures, which promote increased online customer loyalty.Page 1562. Conceptualization of E-ServicesThe concept of e-service seems to be inextricably linked to e-business. Several conceptualization of e-service have been offered in the literature (de Ruyter et al., 2001; van Riel et al., 2001; Featherman and Pavlou, 2002; Pollard, 2003). As de Ruyter et al. (2001) contend, the self-service kind of marketplace environment has already made more and more customers look for company access and customer support through the Internet. In addition to the provision of peripheral service such as customer support, an increasing number of service providers are using electronic ways to distributing their core products/services (de Ruyter et al., 2001). Featherman and Pavlou (2002) also suggest that e-services enable electronic communication, information gathering, transaction processing and data interchange within and between businesses across time and space. Turban et al. (2002) defined pure e-commerce as a case where the product, the agent, and the process are all digitized. In most cases, products that are traded must be physically delivered to the customer, making pure e-commerce impossible. However, with the digital product/service industry, pure e-commerce can be used in most cases, since the industry deals with contents that can be digitized easily. When companies deal with pure e-commerce, the potential advantages are the greatest, since automating the entire process (including product/service delivery) can result in a substantial cost reduction. Delivering value-added, interactive services to customers on-line, in real time, in a shared community of users seems increasingly important to gaining a competitive edge in the electronic marketplace by strengthening relationships with key constituencies (de Ruyter et al., 2001). Consequently, banks, travel agencies, airlines, car rental companies, job placement agencies, real estate agencies, insurance agencies, brokerage houses, online publishers (e.g., newspapers, magazines, music, videos, games, and other digitizable information), management consulting companies and educational institutions are increasingly opting for online service delivery to meet e-customer demand (Forrest and Mizerski, 1996; Turban et al., 2002). Aforementioned issues lead us to compose the following conceptualization of e-service: “E-service is an interactive content-centered and Internet-based customer service, driven by customer and integrated with related organizational customer support processes and technologies with the goal of strengthening the customer-service provider relationship” (de Ruyter et al., 2001, p.185). With the rapid growth and proliferation of e-service, it seems, therefore, imperative to know what factors influence customer attitudinal commitment and repeat purchase behaviors towards e-service.3. Research Model and HypothesesGiven that an e-service in the Internet context is an electronic channel through which consumers received products/services, trust in electronic channel, customer satisfaction with e-service, and perceived value of products/services provided by an e-service vendor should work together to influence the decision to participate in repeat purchase with a particular e-service vendor. The research model used to guide the study is shown in Figure 1, which suggests that customer satisfaction, trust, and perceived value are all directly and indirectly related to loyalty, with the indirect path occurring through commitment. This section elaborates on the theory base and derives the hypotheses.3.1 Definitions and ModelsOliver (1999) defines brand loyalty as “a deeply held commitment to rebuy or repatronize a preferred product/service consistently in the future, thereby causing repetitive same-brand or same brand-set purchasing, despite situational influences and marketing efforts having the potential to cause switching behavior.” This definition emphasizes the two different aspects of brand loyalty that have been described in prior studies on the concept--behavioral and attitudinal (Aaker, 1991; Jacoby and Chestnut, 1978; Oliver, 1999; Jacoby and Kyner, 1973; Day, 1969). Still, this view is not universally held, as others suggest that the two constructs are either not related (Oliva et al., 1992) or that they are synonymous and represent each other (Assael, 1987). Chaudhuri and Holbrook (2001) suggest that behavioral, or purchase, loyalty consists of repeated purchases of the brand, whereas attitudinal brand loyalty includes a degree of dispositional commitment in terms of some unique value associated with the brand. Hence, an intermediate view on the matter asserts the constructs are related, yet by definition are distinct, with commitment leading to loyalty (Beatty et al., 1988). In this study, commitment is defined as a consumer’s psychological attachment to an e-service that develops before a customer would be able to determine that their repeat purchase behavior was derived from a sense of loyalty (Beatty and Kahle, 1988). Loyalty is defined as the intention of a consumer to repurchase products/services through a particular e-service vendor.Trust has been conceptualized by previous research in a variety of ways, both theoretically and operationally, and researchers have long acknowledged the confusion in the field (e.g., Lewis and Weigert, 1985; McKnight et al., 1998, 2002; Shapiro, 1987). In e-commerce contexts, the diversity in trust conceptualization is also evident (Gefen et al., 2003). Prior studies have viewed trust as (a) trusting beliefs (Doney and Cannon, 1997; Ganesan, 1994; Gefen and Silver, 1999; McKnight et al., 1998, 2002; Gefen et al., 2003) or (b) trusting intentions (Gefen, 2000; Hosmer, 1995; Moorman et al., 1992; Mayer et al., 1995; McKnight et al., 1998, 2002). In e-commerce environment, trusting beliefs, which have also been referred to as “trustworthiness” by Mayer et al. (1995), are consumers’ perceptions of particular attributes of e-vendors, including the abilities, integrity, andPage 157benevolence exhibited by the vendors when they handle the consumers’ transactions (McKnight et al., 2002; Kim and Benbasat, 2003). Trusting intentions means “the truster is securely willing to depend, or intends to depend, on the trustee” (McKnight et al., 2002, p.337). Most researchers agree that trusting beliefs positively influence trusting intentions (McKnight et al., 1998, 2002; Kim and Benbasat, 2003; Gefen et al., 2003; Jarvenpaa and Tractinsky, 1999; Mayer and Davis, 1999; Mayer et al., 1995). Commonly discussed trust-related behavioral intentions in electronic commerce include sharing personal information, making a one time or repeating purchase, or acting on information provided by an e-vendor. Although some researchers have treated trust as a unitary concept (e.g., Rotter, 1971), most now agree that trust is multidimensional (Mayer et al., 1995; Rousseau et al., 1998; McKnight et al., 2002). In consonance with the definition of trust adopted by Gefen et al. (2003), this study defines trust is a set of specific beliefs dealing primarily with the integrity (trustee honesty and promise keeping), benevolence (trustee caring and motivation to act in the truster’s interest), competence (ability of trustee to do what the truster needs), and predictability (trustee’s behavioral consistency) of a particular e-service vendor (McKnight et al., 2002; Doney and Cannon, 1997; Ganesan, 1994; Gefen and Silver, 1999; Giffin, 1967; Larzelere and Huston, 1980). Gefen et al. (2003) suggest that this definition relies on separation between trust and actual behavioral intentions (e.g., repeat purchase intentions) in the ongoing economic relationship of customers and e-vendors, and that this trust conceptualization is akin to that of other studies dealing with ongoing economic relationships (e.g., Crosby et al., 1990; Gefen, 2002), including those with e-vendors (Jarvenpaa et al., 2000). We also included “predictability” dimension into our trust conceptualization because it is more relevant to an ongoing trust model than to an initial trust model (McKnight et al., 1998, 2002).Traditionally, user satisfaction was employed as a label of IS success (Bailey and Pearson, 1983), and therefore frequently measured in past studies. Both user information satisfaction (UIS) and end-user computing satisfaction (EUCS) scales have been used to measure user satisfaction indirectly through information quality, system quality, and other variables (Bailey and Pearson, 1983; Ives, et al., 1983; Doll and Torkzadeh, 1988). Based on seven indirect measuring factors of overall level of Web customer satisfaction, Wang et al. (2001) developed a 21-item instrument for measuring customer satisfaction with a particular Web site that markets digital products/services. However, the concept of IS and/or e-commerce success has been refined in the context of integrated IS and/or e-commerce success models, including DeLone and McLean (1992, 2003), Seddeon (1997), and Molla and Licker (2001) models, to develop causal relations between antecedents (indirect measures) of overall user/customer satisfaction (e.g., system quality and information quality), overall user/customer satisfaction, and consequents of overall user/customer satisfaction (e.g., individual impact and customer loyalty). Given our interest in capturing a overall measure of customer satisfaction with e-service and concerns about survey length and respondent convenience, the conceptualization of customer satisfaction adopted here therefore corresponds to the summary affective response or feeling of a customer in relation to her/his experience with all aspects of an e-service put in place by an organization to market its products and services (Molla and Licker, 2001).It is widely known that perceived value, the potential key determinant of loyalty, is composed of a “get” component--that is, the benefits a buyer derives from a seller’s offering--and a “give” component--that is, the buyer’s monetary and nonmonetary costs of acquiring the offering (e.g., Dodds et al., 1991; Zeithaml, 1988). This study focuses primarily on product and service quality, including Web site quality, as the get component and on time and money spent as the give component (Grewal et al., 1998; Lichtenstein et al., 1990; Zeithaml, 1988; Parasuraman and Grewal, 2000).3.2 HypothesesAs mentioned previously, it has been suggested that loyalty includes some degree of predispositional commitment toward a brand. Therefore, our notion of customer loyalty in this study includes both attitudinal commitment and behavioral purchase loyalty (see Figure 1). Based on the emerging theory of brandPage 158commitment in relationship marketing (e.g., Fournier, 1998; Gundlach et al., 1995; Morgan and Hunt, 1994; Parasuraman and Grewal, 2000; Chaudhuri and Holbrook, 2001), we propose that trust, customer satisfaction, and perceived value are each related to both commitment and loyalty, consistent with the concept of one-to-one marketing relationships.Trust is vital in many business relationships (Dasgupta, 1988; Fukuyama, 1995; Gambetta, 1988; Gulati, 1995; Kumar et al. 1995; Ganesan, 1994; Moorman et al. 1992), especially those containing an element of risk, including interacting with an e-vendor (Reichheld and Schefter, 2000; Gefen et al., 2003). Lacking effective regulation in the Internet context, consumers have to trust that the e-service vendor will not engage in harmful opportunistic behaviors, or else the overwhelming social complexity will cause them to avoid purchasing (Gefen, 2000). Some researchers have suggested that online customers generally stay away from e-vendors whom they do not trust (Jarvenpaa and Tractinsky, 1999; Reichheld and Schefter, 2000). Following McKnight et al. (1998, 2002), we integrate trust-related constructs mentioned earlier within the broad framework of the Theory of Reasoned Action (TRA) (Fishbein and Ajzen, 1975). TRA posits that beliefs lead to attitudes, which lead to behavioral intentions, which lead to the behavior itself. Applying the viewpoints of TRA, we posit that trusting beliefs (perceptions of specific e-service vendor attributes) lead to trust-related attitude (i.e., attitudinal commitment), which in turn result in intentions to engage in trust-related behaviors with a specific e-vendor (i.e., behavioral loyalty). As mentioned earlier, most researchers also agree that trusting beliefs directly influence trusting intentions (e.g., repeat purchase intentions) (McKnight et al., 1998, 2002; Kim and Benbasat, 2003; Gefen et al., 2003). We did not measure actual behavior in this study because prior research has confirmed a strong correlation between behavioral intentions and actual behavior (Sheppard et al., 1998; Venkatesh and Davis, 2000).In the marketing literature, Morgan and Hunt (1994) also suggest that brand trust leads to brand loyalty and commitment because trust creates exchange relationships that are highly valued. Thus, loyalty or commitment underlies the ongoing process of continuing and maintaining a valued and important relationship that has been created by trust (Chaudhuri and Holbrook, 2001). We suggest that trust will contribute to both commitment and loyalty. Trusted e-services should be purchased more often and should evoke a higher degree of attitudinal commitment. Thus, the following hypotheses are tested:H1a: Trust will positively affect loyalty.H1b: Trust will positively affect commitment.Dick and Basu (1994) have proposed that brand loyalty should be greater under conditions of more positive emotional mood or affect. The brands that make consumers happy or joyful or affectionate should prompt greater behavioral (purchase) loyalty and attitudinal commitment (Chaudhuri and Holbrook, 2001). Similarly, consumer satisfaction is believed to mediate consumer learning from prior experience and to explain key postpurchase behaviors, such as complaining, word of mouth, repurchase intention, and product usage (Oliver, 1980; Westbrook and Oliver, 1991). Indeed, Wang et al. (2001) has suggested that Web customer satisfaction have a significant influence on repurchase intention and postpurchase complaint. Therefore, we test the following hypotheses:H2a: Customer satisfaction will positively affect loyalty.H2b: Customer satisfaction will positively affect commitment.Perceived value is the perceived e-service utility relative to its monetary and nonmonetary costs, assessed by the consumer and based on simultaneous considerations of what is received and what is given up to received it. Clearly, quality of product/service and Web site is a logical driver of perceived value. In instances where the core of what the e-vendor offers to the customers is a digitized product/service (e.g., online banking, content aggregators, and online stock trading), there is no tangible product and, as such, it is difficult for consumers to differentiate product quality, service quality, and Web site quality. Even in instances where the e-vendor offers to the buyers is a physical product, superior presale and postsale service rendered by the e-vendor can add to the benefits received (get component) and also reduce the customer’s nonmonetary cost such as time, effort, and mental stress (give component). Furthermore, part of the “give” and “get” of the experience also involves the Web site quality. The online consumer gives time, cognition and effort to the experience of interacting with the Web site, and gets an experience enabled by the Web site that hopefully makes it easy to find needed/wanted products, to checkout quickly and to received confirmation about all important aspects of the purchase, such as order-confirmation and delivery-tracking. In this regard, the product quality, service quality, and Web site quality are also intertwined with each other.Cumulative insights from prior studies support the general notion that perceived value contributes to customer loyalty (e.g., Parasuraman and Grewal, 2000; Dodds et al., 1991; Grewal et al., 1998; Voss et al., 1998). The value-loyalty linkage is also consistent with Reichheld’s (1996) work on loyalty. Regardless ofPage 159whether the core offerings of an e-vendor are products or services, customer perceived value of products/services and Web quality provided by an e-vendor should be positively related to customer loyalty and commitment. Parasuraman and Grewal (2000) suggest that the influence of perceived value on loyalty is an issue in need of more empirical research. Therefore, this study tests the following hypotheses: H3a: Perceived value will positively affect loyalty.H3b: Perceived value will positively affect commitment.Based on the TRA mentioned earlier, attitudinal commitment positively influences intentions to engage in repeat purchase behaviors with a specific e-vendor. Previous studies of purchase behavior (Beatty and Kahle, 1988), consumer expectations (Kelley and Davis, 1994), and advertising effectiveness (Robertson, 1976) all attest to commitment’s ability to affect a variety of outcomes. Kiesler and Sakumura (1966) described customer commitment as a stable preference that was bound by an attitude of resistance to change. Crosby and Taylor (1983) also suggest that the “tendency to resist changing preference” provides the principle evidence of commitment. As the principle evidence of commitment, resistance to change is central to a variety of outcomes, the foremost of which is loyalty (Jacoby and Kyner, 1973). Therefore, this study tests the following hypothesis: H4: Commitment will have a positive effect on LoyaltyIn sum, previous researches have implied that attitudinal commitment and behavioral loyalty should be the product of trust in e-service, customer satisfaction with e-service, and perceived value of products/services provided by an e-service vendor. But these perspectives has been examined independently by IS and marketing researcher. Integrating these perspectives and empirically examining the factors that build customer loyalty in an e-service context that lacks the typical human interaction advances our understanding of these constructs and their linkage to repeat Web purchase behavior.4. Methodology4.1 MeasuresTo ensure the content validity of the scales, the items selected must represent the concept about which generalizations are to be made. Therefore, items selected for the constructs were mainly adapted from prior studies to ensure content validity. Four items for the trust construct were adapted from Gefen et al. (2003). The items to measure customer satisfaction were taken from previous measures of overall level of user satisfaction or Web customer satisfaction (Wang et al., 2001; Doll et al., 1988; Palvia, 1996; Rai et al., 2002). Perceived value was measured by three items adapted from Lassar et al. (1995). Items for the loyalty were taken from the previous validated inventory (Chaudhuri and Holbrook, 2001) and modified to fit the e-service context studied. Finally, commitment was measured by four items adapted from the Pritchard et al. (1999) “resistance to change” scales. Likert scales (1~7), with anchors ranging from “strongly disagree” to “strongly agree” were used for all questions. Pre-testing and pilot testing of the measures were conducted by selected consumers from the B2C e-commerce field, as well as experts in the e-commerce research area. The items were modified to make them relevant to the e-service context. The Appendix lists the items used in this study.4.2 SubjectsThis study used online traveling services and video on demand (VOD) as the e-service categories of reference because these two categories are among the most popular B2C e-services. Data used to test the research model was gathered from a quota sample of 180 respondents attending an e-commerce exposition and symposium held in Taiwan, with an equal quota of 90 responses from each category of the traveling and VOD e-services. Respondents were asked first whether they had bought the traveling or VOD products/services through the e-service vendors, and if they relied in the affirmative, they were asked to participate in a survey. The screened and qualified respondents self-administered a 16-item questionnaire. The first part of the questionnaire focused on demographic data, while the second part required respondents to name one e-service vendor where they had purchased the product/service in question. This served to anchor the survey to a particular e-service vendor. For each question, respondents were asked to circle the response which best described their level of agreement with the statements.A total of 572 approaches were made to obtain 180 completed surveys. Reasons for nonparticipation were either due to non-usage of the e-service category or a lack of time to complete the survey. 72 percent of the completed surveys were from male respondents. Respondents ranged from 16 to 45 years of age (mean = 32 years). 52 percent had completed one college or university degree.Page 1605. Results5.1 Measurement AssessmentConstruct validity determines the extent to which a scale measures a variable of interest. In this study, we follow the Straub’s (1989) processes of validating instruments in MIS research in terms of convergent validityand discriminant validity. Thus, a principal components factor analysis with varimax rotation was conducted to investigate the distinctions among customer satisfaction, trust, perceived value, commitment, and loyalty. In this study, Bartlett’s test of sphericity (p=0.00) indicated the statistical probability that the correlation matrix has significant correlations among at least some of the variables, and the Kaiser-Meyer-Olkin measure of sampling adequacy (0.872) showed middling sampling adequacy. As shown in Table 1, the five factors emerged with no cross-construct loadings above 0.5, indicating good discriminant validity. The instrument also demonstrated convergent validity with factor loadings exceeding 0.5 for each construct. Consequently, these results confirmthat each of the five constructs is unidimensional and factorially distinct and that all items used to operationalizea particular construct is loaded onto a single factor.Reliability was evaluated by assessing the internal consistency of the items representing each construct using Cronbach’s alpha. The reliability of each construct was as follows: customer satisfaction = 0.90; trust =0.93; perceived value = 0.91; commitment = .94; loyalty = .89. All the values were above 0.8, exceeding the common threshold values recommended by Nunnally (1978).Table 1. Factor Analysis Results: Principal Component ExtractionSatisfaction0.900C30.839C10.832C20.811C40.861T40.858T30.835T20.793T10.866V10.855V30.821V20.873S30.821S20.675S10.719 L10.615 L25.2 Hypothesis TestingThe hypothesized relationships were tested using the multiple regression analysis of SPSS 9.0 for Windows.The average scores of the items representing each construct were used in the data analysis1. The R2 was used to assess the model’s overall predictive fit. Properties of the causal paths, including standardized path coefficients,t-values, and variance explained for each equation in the hypothesized model are presented in Figure 2. In hypotheses H1a, H2a, H3a, and H4, we investigate the influence of trust, customer satisfaction, perceived value,and commitment on loyalty. As expected, trust (β=0.163, t-value=2.707, p<0.01) and customer satisfaction (β=0.219, t-value=3.588, p<0.001) had a strong positive influence on the loyalty. Also, perceived value (β=0.230,t-value=4.237, p<0.001) and commitment (β=0.392, t-value=6.755, p<0.001) had a significant positive effect onthe loyalty. Therefore, hypotheses H1a, H2a, H3a, and H4 were supported. We found that the proposed model explained a significant percentage of variance in loyalty (R2=65.7%, F=value=83.692, p<0.001). According tothe path coefficients shown in Figure 2, commitment exhibited the strongest direct effect on loyalty.Hypotheses H1b, H2b, and H3b examine the paths from trust, customer satisfaction, and perceived value to commitment. Customer satisfaction (β=0.343, t-value=4.580, p<0.001) and perceived value (β=0.302,t-value=4.534, p<0.001) had a significant positive effect on the commitment. However, trust had no significant influence on the commitment (β=0.142, t-value=1.836, p=0.068) at the 0.05 level. Thus, hypotheses H2b and1The covariance matrix used in the data analysis is available from the corresponding author upon request.Page 161。
2025届广东省两校联考高三上学期(10月)一模考试英语试题

2025届广东省两校联考高三上学期(10月)一模考试英语试题一、阅读理解Career Development in Florence: A Journey Through Craftsmanship and LearningThe art of leather craftsmanship in Florence has a rich history, dating back to the 13th century. This exploration into the city’s leather artisans offers insights into the essence of Italian leather craftsmanship.The Leather Career Development Center — PIEROTUCCIEnroll in a complimentary workshop at the PIEROTUCCI Career Development Center and immerse yourself in the intricate process of crafting a leather handbag. Witnessing the meticulous handiwork involved will demystify the premium pricing of PIEROTUCCI products, assuring you that an investment in their bags is an investment in longevity.The Footwear Training Institute — STEFANO BEMERSTEFANO BEMER is renowned for its bespoke footwear, crafted with precision and elegance. The store, which sells luxury shoes ranging from hundreds to thousands of dollars, also serves as a training ground for aspiring shoemakers, with the workshop visible to customers in the front section.The Leather Artisan School — Scuola del CuoioStep into the Scuola del Cuoio, and you’ll feel as though you’ve entered a small college campus. This historic building houses a school dedicated to creating unique leather goods and educating paying students in the art of high-quality leatherworking.The Bookbinding Atelier — Il TorchioRun by Erin Ciulla, Il Torchio is a charming bookbinding workshop. Ciulla might give you a tour of the “guillotine,” an antique-looking machine used for cutting large volumes of paper. In addition to binding books with leather covers, Ciulla also offers services to cover books, journals, and photo albums with hand-made papers.1.What is the primary benefit of attending a workshop at PIEROTUCCI?A.Learning about the history of leather-making.B.Understanding the high cost of luxury shoes.C.Gaining hands-on experience in handbag crafting.D.Observing the antique machinery used in bookbinding.2.Which institution offers a comprehensive education in leather craftsmanship?A.Il Torchio.B.Scuola del Cuoio.C.STEFANO BEMER.D.PIEROTUCCI. 3.What service does Erin Ciulla provide at Il Torchio?A.Selling high-quality leather bags.B.Customizing book covers with leather.C.Teaching courses on leatherworking.D.Manufacturing antique-looking machines.Nicole Latham, a youthful 21-year-old scholar at the University of Leeds, dedicates her time not solely to the pursuit of legal academia, but also to the rigorous domain of weightlifting contests. In parallel, she exhibits proficiency in the martial art of karate. Beyond these physical pursuits, Latham’s health journey is marked by frequent visits to medical practitioners, a consequence of her recent acquisition of a rare affliction: multiple sclerosis (MS). This condition made its insidious debut during her preparation for the A-Level examinations, a period fraught with tension for numerous scholars. Initially, she attributed her symptoms to stress, but it soon became apparent that she was experiencing the onset of MS, specifically vertigo.Despite the onset of this debilitating disease, Nicole persisted in her academic endeavors, even resorting to ocular occlusion in a bid to ameliorate her impaired vision. It was at this juncture that she resolved to revisit her physician, embarking on a regimen of numerous medications, yet to no avail. Sensing a potential misdiagnosis, she promptly sought further diagnostic scrutiny at a hospital.Subsequent to an MRI examination, her condition was confirmed as MS. Following this inaugural episode and her subsequent diagnosis, Latham remained MS-free for several years. However, in August of the year 2021, she encountered another exacerbation, this time manifesting as a persistent tremor in her left hand for a duration of two months. Undeterred by the palpable impediments imposed by her condition in her day-to-day existence, she remained undaunted and resolute in her pursuit. Her aspiration was to inspire her contemporaries with disabilities, demonstrating that a life of vibrancy and fulfillment is attainable despite the adversities posed byMS.In the present day, Nicole leverages her digital platform not only to disseminate awareness regarding MS but also to exhort individuals to heed potential symptoms, a lesson she herself learned the hard way. Moreover, she endeavors to showcase that a life replete with richness and gratification is within reach for those afflicted with MS. Her narrative seeks to illuminate both the exultant peaks and the somber troughs of living with this condition.4.How did Nicole react when the first attack happened?A.She went to the hospital immediately.B.She turned to taking more exercise.C.She took a break from studying.D.She paid no attention to it.5.How did Nicole most probably feel after taking a lot of medicines?A.Relieved.B.Worried.C.Curious.D.Inspired. 6.Which of the following statements shows Nicole’s view on overcoming difficulties?A.Rome was not built in a day.B.Prevention is better than cure.C.Strength comes from a strong will.D.All things are difficult before they are easy.7.What would be the best title for the text?A.Nicole Latham:Always be Ready to HelpB.Meet N icole Latham — a T alented AthleteC.Nicole Latham:Never Let Anyone DownD.Meet Nicole Latham — a Fighter Suffering from MSA radiant grin is a reflection of inner joy. Have you ever been in a public space and received a smile from a stranger? Perhaps you were feeling low, yet their warm and amicable expression could lift your spirits. That person’s smile had the power to shift your gloomy mood. It’s astonishing how such a minor action can influence your emotions so profoundly, and I can attest to this, as I’m sure many of you can.This phenomenon isn’t just a feeling; it’s backed by science. What causes these positive emotions? When you smile at someone, you might feel a fleeting sense of joy. This is because your brain releases endorphins, which are like natural painkillers and can boost your self-esteem.Smiling is a straightforward act of kindness that can also enhance your self-regard.To illustrate, consider someone attending a job interview with their head held high and a smile on their face. They are more likely to be successful. Employers often note that a candidate who avoids eye contact and hides their smile may seem untrustworthy. In contrast, a person with a genuine smile exudes confidence. Regardless of your appearance, a smile can speak volumes and convey sincerity.I find great satisfaction in helping individuals of all ages build their self-esteem. Witnessing the joy and newfound confidence in my clients after our sessions is immensely rewarding. I firmly believe that a genuine, heartfelt smile can bridge gaps between people, even without words. 8.What does the underlined word “low” mean in Paragraph 1?A.Depressed.B.Strengthened.C.Multiplied.D.Returned. 9.What is the role of endorphins? ______A.They induce a sense of happiness.B.They inspire acts of kindness.C.They accelerate brain function.D.They cure certain illnesses.10.Why might someone who doesn’t smile have difficulty getting a job?A.They hold their head too high.B.They look down on others.C.They appear somewhat dishonest.D.They are overly confident.11.What kind of profession might the author have?A.An educator.B.A philanthropist.C.A researcher.D.A counselor.The Renaissance of Creative Thought is burgeoning, perhaps even burgeoning. If you attempted to absorb all the wisdom available today, you would need more than 180 million years to do so. But you are mistaken to assume that all this wisdom would stimulate a surge of innovation to match the abundance of knowledge. Indeed, the last time we found ourselves in a period of significant innovation, pursuing the ideas with the most profound impact, was more than 120 years ago, in a period called the Renaissance of Insight.Innovations, both grand and modest, originate from a new idea. Often, these ideas emerge as a moment of insight — the outcome of a novel connection in our minds made between existing and new knowledge. Studies reveal insights involve quiet signals deep in the brain, just under the surface of awareness. Anything that aids us in noticing quiet signals, such as taking breaksbetween engagements, adopting essential learning approaches, or steering clear of distractions like social media, can enhance the likelihood of insights. However, it is becoming increasingly challenging to find those quiet signals with the escalating use of technology, filling every moment with emergencies and an endless supply of content.Moreover, we also aspire to elevate the quality of them — to be able to sift through grand new ideas and identify the ones that hold genuine value, which can be difficult to measure. Launched in 2015, the Insight Meter (洞察力计量器) permits us to evaluate the potency of our insight experiences on a five-point scale, which is marked by intense emotions, motivation, memory advantage, aftershocks, and subsequent ideas. The Meter consolidates these five variables into a solitary value and enables us to define the significance of a new idea. The level-5 insight, involving the richest emotion, motivation, and lasting impact, holds the utmost significance.Since insights are one of the most effective ways to stimulate engagement, innovation, and behavioral change, the Insight Meter has extensive applications for gauging and enhancing individual and organizational performance. More importantly, it can be employed to measure the impact of different types of work environments and learning approaches on participants’ development — both in the moment or afterward.For organizations to reap the benefits of another age of insight, it is not sufficient to attempt to access more data or augment the number of insights we generate. Instead, it is about creating space for the most significant ideas to emerge from all the knowledge. Utilizing the shared language of the Insight Meter as a means to measure how important ideas are, relative to each other, will enable superior decision-making toward practical and competitive outcomes. And if we are to enter a new age of insight, we must design our environments to allow for the most exceptional insight possible to surface.12.What does the underlined word “burgeoning” in Paragraph 1 probably mean?A.Stabilizing.B.Exploding.C.Shifting.D.Collapsing. 13.According to the passage, how can the likelihood of insights be increased?A.By engaging in ongoing social media interactions.B.By relying on technology to receive regular notifications.C.By stepping away from computers between engagements.D.By participating in additional training and coaching sessions.14.What can be inferred from the passage?A.The Insight Meter dictates the influence of our insights.B.Possessing minimal emotional responses is a level-5 insight.C.Both the quantity and quality of insights are essential to innovation.D.A breakthrough has been made in innovation due to a wealth of information.15.What is the author’s attitude towards the current environment for innovations?A.Uncertain.B.Optimistic.C.Unconcerned.D.Dissatisfied.How to Teach ConfidenceWhile it might seem like some people are just born confident, confidence is largely an acquired skill. 16 Start by building up their self-esteem, independent thought, and positive self—talk. Show them how to achieve goals, and how to deal with failure when it happens. With lessons like these, you can teach the people around you to become more confident.Model confident behavior far people.If you’re trying to improve someone’s confidence, be a model for how they should behave in a confident way. 17 Show them confident interpersonal relations like eye contact, handshakes, and making small talk. This lets them practice in a safe environment.Praise small accomplishments to raise a person’s self-worth.If you’re trying to build someone’s confidence, start small. Each accomplishment they complete is a cause for celebration, even if it seems small. Be happy for your friends, kids, or students. 18Give specific praise so people know what they did well.A specific praise is better than a simple “You did well”. 19 . This makes your praise more genuine and boosts the person self-esteem more by showing them their strengths.Start with a positive statement before correcting something.20 This is especially important if you’re a parent, teacher, or coach. If you do have to make criticisms or corrections, always start by saying something positive first. This raises the person’s spirits and makes it easier for them to take the critical feedback that’s coming up. A.Instead, tell the person exactly what they did well.B.It’s something you can model and teach other people.C.You may have to point out where someone needs to improve.D.Instead of feeling criticized, the person will know you’re sincere.E.Act confident around them and in your interpersonal interactions.F.Your positive energy will teach them to celebrate their achievements.G.You might show someone’s strengths to help them see the bright side.二、完形填空Boo is a 5-year -old rooster. He loves going on road trips, watching TV, and 21 with other house pets: chickens and cats. Boo enjoys many things in his life, but most of all, he 22 to hug with his human mother Mary Bowman.Before he was 23 , Boo’s life wasn’t always that beautiful. He spent the first six months of his life on a farm with many other chickens, where he was treated more like a 24 than a unique being. He was given constant feeding, which is 25 unhealthy because he can not 26 his feed consumption.His now mother adopted him after learning about him from a friend; she was 27 when knowing his unfortunate fate. She decided to help this little guy 28 the meat factory and finally live 29 .In the house, Boo stays close to his humans. When the family goes for a walk in the wild, he wanders free. He, even like a dog, 30 the family when they come home. He likes to spend time with his dad reading comics. Even though Boo can’t read, he likes to look at pictures in the 31 . They play games together as well. Boo spends time with his grandma, too. When she’s playing the piano, he is looking, learning little by little what those 32 do.Boo is an 33 pet. He knows his family and where he lives. He is the soul of the house, the brightest star in the air. Today, Boo is an active part of the local 34 and has a personal account on which he 35 his everyday life with 35K fans.21.A.working out B.hanging out C.figuring out D.carrying out 22.A.benefits B.inspires C.loves D.advocates 23.A.protected B.replaced C.selected D.adopted 24.A.performer B.chief C.product D.species25.A.occasionally B.illegally C.gradually D.extremely 26.A.control B.obey C.predict D.permit 27.A.heartbroken B.patient C.grateful D.disappointed 28.A.complain B.detect C.escape D.resist 29.A.flexibly B.safely C.gently D.regularly 30.A.proves B.assists C.welcomes D.admits 31.A.books B.riddles C.puzzles D.applications 32.A.heels B.legs C.hands D.fingers 33.A.intelligent B.abnormal C.odd D.energetic 34.A.department B.community C.authority D.charity 35.A.drafts B.illustrates C.chats D.shares三、语法填空阅读下面短文,在空白处填入1个适当的单词或括号内单词的正确形式。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
COVER SHEETBarros, Alistair P. and Decker, Gero and Dumas, Marlon and Weber, Franz (2006) Correlation Patterns in Service-Oriented Architectures. Copyright 2006 (please consult author)Accessed from .auCorrelation Patterns in Service-OrientedArchitecturesAlistair Barros1,Gero Decker2 ,Marlon Dumas3,Franz Weber41SAP Research Centre,Brisbane,Australiaalistair.barros@2Hasso-Plattner Institute,University of Potsdam,Germanygero.decker@hpi.uni-potsdam.de3Queensland University of Technology,Brisbane,Australiam.dumas@.au4SAP AG,Walldorf,Germanyfranz.weber@Abstract.When a service engages in multiple interactions concurrently,it is generally required to correlate incoming messages with messages pre-viously sent or received.Features to deal with this correlation require-ment have been incorporated into standards and tools for service imple-mentation,but the supported sets of features are ad hoc as there is a lackof an overarching framework with respect to which their expressivenesscan be evaluated.This paper introduces a set of patterns that provide abasis for evaluating languages and protocols for service implementationin terms of their support for correlation.The proposed correlation pat-terns are grounded in a formal model that views correlation mechanismsas means of grouping atomic message events into conversations and pro-cesses.The paper also provides an evaluation of relevant standards interms of the patterns,specifically WS-Addressing and BPEL,and dis-cusses how these standards have and could continue to evolve to addressa wider set of correlation scenarios.1IntroductionContemporary distributed system architectures,in particular service-oriented architectures,rely on the notion of message exchange as a basic communica-tion primitive.A message exchange is an interaction between two actors(e.g. services)composed of two events:a message send event occurring at one ac-tor and a message receive event at another actor.These events are generally typed in order to capture their purpose and the structure of the data they con-vey.Example of event types are“Purchase Order”,“Purchase Order Response”,“Cancel Order Request”,etc.Event types are described within structural in-terfaces using an interface definition language such as WSDL[1].Sometimes, message exchanges are related to one another in simple ways.For example,a message exchange corresponding to a request may be related to the message Work conducted while the author was visiting SAP Research Centre,Brisbane2Alistair Barros,Gero Decker,Marlon Dumas,Franz Weberexchange corresponding to the response to this request.Such simple relations between message exchanges are described in the structural interface as well(e.g. as a WSDL operation definition).The above abstractions are sufficient to describe simple interactions such as a weather information service that provides an operation to request the fore-casted temperature for a given location and date.However,they are insufficient to describe interactions between services that engage in long-running business transactions such as those that arise in supply chain management,procurement or logistics.In these contexts,message event types can be related in complex manners.For example,following the receipt of a purchase order containing sev-eral line items,an order management service may issue a number of stock avail-ability requests to multiple warehouses,and by gathering the responses from the warehouses(up to a timeout event),produce one or several responses for the cus-tomer.Such services are referred to as conversational services as they engage in multiple interrelated message exchanges for the purpose of fulfilling a goal.Con-versational services are often related to(business)process execution,although as we will see later,conversations and processes are orthogonal concepts.The need to support the description,implementation and execution of con-versational services is widely acknowledged.For example,enhancements to the standard SOAP messaging format and protocol[1]for correlating messages have been proposed in the context of WS-Addressing[3].WS-Addressing is now supported by the APIs of most service-oriented middleware.However,WS-Addressing merely allows a service to declare(at runtime)that a given message is a reply to a previous message referred to by an identifier.This is only one specific type of relation between interactions that has a manifestation only at runtime(i.e.it does not operate at the level of event types)and fails to capture more complicated scenarios where two message send(or receive)events are re-lated not because one is a reply to another(or is caused by another),but because there is a common event that causes both.This is the case in the above example where the stock availability requests are related because they are caused by the same purchase order receive event.Another upcoming standard,namely WS-BPEL[2],provides further support for developing conversational services.In particular WS-BPEL supports the no-tion of process instance:a set of related message send and receive events(among other kinds of events).Events in WS-BPEL are grouped into process instances through a mechanism known as instance routing,whereby a receive event that does not start a new process instance is routed to an existing process instance based on a common property between this event and a previously recorded send or receive event.This property may be the fact that both messages are exchanged in the context of the same HTTP connection,or based on a common identifier found in the WS-Addressing headers of both events,or a common element or combination of elements in the message body of both events.Thus,WS-BPEL allows developers to express event types,which are related to WSDL operations, and to relate events of these types to process instances.It also allows developersCorrelation Patterns in Service-Oriented Architectures3 to capture ordering constraints between events related to a process instance, which ultimately correspond to causal dependencies(or causal independence).Despite this limited support for message event correlation,there is currently no overarching framework capturing the kinds of event correlation that service-oriented architectures should support.As a result,different approaches to event correlation are being incorporated into standards and products in thefield,and there is no clear picture of the event correlation requirements that these stan-dards and products should fulfill.In this setting,this paper makes three complementary contributions:–A unified conceptualization of the notions of conversation,process and cor-relation in terms of atomic message events(Section2).–A set of formally defined correlation patterns that cover a spectrum of cor-relation scenarios that occur in the context of conversational services(Sec-tions3,4and5).–An evaluation of the support for these correlation patterns offered by relevant Web service standards,namely WS-Addressing and BPEL versions1.1and2.0(Section6).Together,these contributions provide a foundation to guide the design of languages and protocols for conversational services.2Classification FrameworkWhen talking about correlation we mainly deal with three different concepts: events,conversations and process instances.An event is an object that is record of an activity in a system[4].Events have attributes which describe the cor-responding activity such as the time period,the performer or the location of the activity.We assume that a type is assigned to each event.In the area of service-oriented computing,where emphasis is placed on communication in a distributed environment,the most important kinds of events include message send and receipt events and time-related events(time-outs).In addition to these “communication events”that allow to observe the public behavior of actors,we deal with“action events”being records of internal activities within actors.Mes-sage send events are results of internal actions and most message receipt events result in internal actions consuming these events.Therefore,we assume that event logs include information about the causal relationships between communi-cation events and action events.The causal relationship between corresponding message send and receipt events is also used in the remainder of this paper. Figure1illustrates this.Events can be grouped in different ways,e.g.all events occurring at one particular actor could be grouped together.Since this work deals with event correlation in the context of conversational services,we focus on two types of event grouping:conversations and process instances.Conversations are groups of communication events occurring at different actors that all correspond to achieving a certain goal.Boundaries of conversations might be defined through4Alistair Barros,Gero Decker,Marlon Dumas,Franz WeberFig.1.Action and communication eventsinteraction models(choreographies)or might not be defined in advance but rather discovered a posteriori.Process instances are groups of action events occurring at one actor.Boundaries of process instances are determined by process models.Fig.2.Framework for classifying correlation patterns Figure2illustrates a framework for classifying correlation patterns.At the bottom there are partially ordered events.The partial order stems from the temporal ordering of events occurring within one actor,combined with the re-lationships between a send event occurring at one actor and the corresponding receive event occurring at another actor.Since events may be recorded by dif-ferent actors having clocks that are not synchronized we might not be able to linearly order all the events according to their timestamps.However,we can use the timestamps to order events that were recorded by the same actor(assuming a perfect clock within one actor).In the case of different clocks within one ac-tor due to decomposition into components,causal relationships between action events occurring in different components can replace the pure timestamp-based ordering.For establishing a partial order between events that were recorded byCorrelation Patterns in Service-Oriented Architectures5 different actors we then use the relationships between corresponding message send and receipt events.Conversations and process instances are sets of correlated events.The dif-ferent patterns describing the relationships between events,conversations and process instances are grouped into four categories(for numbering see Figure2).1.Mechanisms to group events into conversations and process instances.Thesecorrelation mechanisms will be presented in section3.2.After having identified conversations we can examine how conversations arestructured.In previous work we have investigated common interaction sce-narios between participants within one conversation(cf.the Service Interac-tion Patterns[5]).The conversation patterns in section4present relation-ships between different conversations.3.Relationships between conversations and process instances are covered in theprocess instance to conversation mappings in section5.mon structures within one process instance have already been exten-sively studied e.g.in the workflow patterns([6]).Additional work has to be done to identify patterns describing the relationships between different process instances,but this is outside the scope of this paper.Below,we present a set of formally defined correlation patterns.The formal description is based on the idea of viewing events from a post-mortem perspec-tive.This could be seen as analyzing logs of past events.This view is taken for the sake of providing a unified formal description.In practice the patterns will not be necessarily be used to analyze event logs,but rather to assess the capa-bilities of existing languages that deal in one way or another with correlation in SOAs.A language will be said to support a pattern if there is a construct in the language(or a combination of constructs)that allows developers to describe or implement services which,if executed an arbitrary number of times,would generate event logs that satisfy the conditions captured in the formalization of the correlation pattern.In the rest of the paper,we use the following formal notations:–E is the set of events–CE,AE⊆E are the communication and action events(CE∩AE=∅)–A is the set of actors–function does:E→A links an event to the actor who records the corre-sponding activity–<t⊆E×E partially orders the events occurring at the same actor according to their timestamps–<c⊆E×E is the causal relation between events,including pairs of corre-sponding send and receipt events as well as corresponding communication and action events where∀e1,e2∈<c[does(e1)=does(e2)→e1<t e2]–<is a partial order relation on E being the transitive closure of<t and<c: <:=(<t∪<c)+.–Conv⊆℘(CE)and P I⊆℘(AE)are sets of sets of communication and ac-tion events corresponding to groupings of events into conversations(Conv)6Alistair Barros,Gero Decker,Marlon Dumas,Franz Weberand process instances(PI),respectively.These sets will in principle be gen-erated using correlation mechanisms as discussed below.3Correlation MechanismsThe correlation mechanism patterns focus on how events can be correlated to different process instances and more importantly to different conversations.The purpose of correlation is to group messages into traces based on their con-tents(including message headers).Current web service standards do not make a provision for messages to include a“service instance identifier”,so assuming the existence of such identifier may be unrealistic in some situations.Other monitor-ing approaches in thefield of web services have recognized this problem and have addressed it in different ways,but they usually end up relying on very specific and sometimes proprietary approaches.For example the Web Services Navigator [11]uses IBM’s Data Collector to log both the contents and context of SOAP messages.But to capture enable correlation,the Data Collector inserts a pro-prietary SOAP header element into messages.In the literature on correlation,it is often noted that correlation is different from causation.Correlation in general means that an event is(perceived to be)related to another in some way,while causation means that an event is a cause of another,which is a special type of relation.Thus,while causation implies correlation,the reverse does not hold.It is not in the scope of this paper to capture a general notion of correlation.The focus of the paper is on correlation between events in service-oriented architec-tures.In this context,we postulate that two events can be correlated in either of the following situations:1.One event is a cause of the other,either directly or transitively.2.There is a third event which is a cause(either directly or transitively)ofboth events.3.Both events are a common cause(either directly or transitively)of a thirdevent.4.Both events have a common property,e.g.there exists a function that whenapplied to both events yields the same value.For example,two events can be correlated simply because they are performed by the same actor,or because they refer to the same purchase order.In order to capture all these four types of correlation,we introduce two no-tions:key-based correlation(also called function-based correlation)and chained correlation.Differentflavors of both mechanisms will be presented.The applica-tion of a particular key-based or chained correlation mechanism or a combination of different mechanisms leads to a correlation scheme.Such schemes are sets of sets of correlated events that might be interpreted e.g.as conversations or process instances later on.Different combinations are discussed in this section.3.1Function-based CorrelationFunctions assign labels to an event.Events with common labels are then grouped together.We distinguish:Correlation Patterns in Service-Oriented Architectures7–C1.Key-based correlation.One or a set of unique identifiers are assigned to an event and all events having at least one common identifier are grouped together.E.g.a process instance identifier and conversation identifier is at-tached to an event.Identifiers can be single values or compositions of several values.WS-CDL introduces the notion of identity tokens for channel in-stances that can be used for distinguishing different conversations.In BPEL we canfind correlation sets being implemented as specialfields in a WSDL specification.These correlation sets are an example for composite identifiers.–C2.Property-based correlation.A function assigns a label to an event depending on the value of its attributes.In contrast to key-based correlation not only equality can be used in the function.Operators such as“greater”,“less”,“or”and“not”must be available in the function.E.g.all events in-volving customers living less than50km away from the city centers of Bris-bane,Sydney or Melbourne are grouped together(label=“metropolitan”) as opposed to the others(label=“rural”).–C3.Time-interval-based correlation is a special kind of property-based correlation.A timestamp is attached to an event and a corresponding label is assigned to the event if the event happened within a given interval.E.g.all events that happen in July2006could be grouped together(bel=“07/2006”)as opposed to those happening in August(label=“08/2006”).Function-based correlation can be formalized in the following way:Let Label be the set of all labels and F⊆{f|f:E→Label}a set of partial functions assigning labels to an event.Then the set of sets of correlated events is{C⊆E|∃l∈Label(∀e∈E[∃f∈F(l=f(e))↔e∈C])}As an extension to function-based correlation relationships between the labels can be considered(R L⊆Label×Label).E.g.we could assume a hierarchical order of keys where several keys have a common super-key.In this case events could be grouped according to their keys attached as well as according to some super-key higher up in the hierarchy.Let us assume e.g.a set of line items that all belong to the same order.In this example events could be grouped according to the line item ID or according to the order ID.In WS-CDL channel instances can have several identities that are used for correlation.Identities are determined by one or several tokens(keys)and corre-sponding to labels in our formalization.If two identities l1,l2share a common key,the corresponding labels are related((l1,l2)∈R L).The formalization given above uses one set of labels.However,in practice we would distinguish between different types of labels,e.g.intervals,product groups,locations.3.2Chained CorrelationThe basic idea of chained correlation is that we can identify relationships be-tween two events that have to be correlated(grouped together).This relationship8Alistair Barros,Gero Decker,Marlon Dumas,Franz Webermight be explicitly captured in an event’s attributes or might be indirectly re-trieved by comparing attribute values of two events.Starting from these binary relationships we can build chains of events that belong to the same group.Since we assume that grouping events to process instances will mostly be done by using unique identifiers,chained correlation becomes important mostly for identifying conversations within our framework.In the case of conversations we especially look at the relationships between message exchanges.–C4.Reference-based correlation.Two events are correlated,if the sec-ond event(in chronological order)contains a reference to thefirst event.Specifically,this means that if there is some way of extracting a datum from the second event(by applying a function)that is equal to another datum contained in thefirst event.This datum therefore acts as a message identifier, and the second message refers to this message identifier in some way.–C5.Moving time-window correlation.Two events involving the same actor are related if they both have the same value for a given function(like in function-based correlation)and they occur within a given duration of one another(e.g.2hours).There might be chains of events where the time passed between thefirst and last event might be very long and others where this time is rather short.Chained correlation can be formalized in the following way:Let R⊆E×E be the relations between two events that have to be grouped together.Then the set of sets of correlated events is{C⊆E|∀e1∈C,e2∈E[e1R∗e2↔e2∈C]}3.3Aggregation FunctionsSometimes only a limited number of events are grouped together although ac-cording to function-based or chaining correlation mechanisms more events would fulfill the criteria to be part of the group.E.g.only a maximum number of10 items are to be shipped together in one container.More items are requested to be shipped and might have the same destination or arrive timely according to the defined moving time window.For this additional aggregation of events,special boolean functions agg are defined over sets of correlated events(agg:℘(E)→{true,false}).4Conversation PatternsThe Service Interaction Patterns already describe some of the most recurrent interaction scenarios within one conversation.The following patterns focus on relationships between different conversations.Correlation Patterns in Service-Oriented Architectures9 4.1C6.Conversation OverlapSome interactions belong to two or more conversations.Each conversation also contains interactions that are not part of the others.E.g.during a conversation centering around delivery of goods a payment notice is exchanged.This payment notice is the starting point for a conversation centering around the payment.Two conversations C1,C2∈Conv overlap if C1∩C2=∅∧C1\C2=∅∧C2\ C1=∅.4.2C7.Hierarchical ConversationSeveral sub-conversations are spawned offand merged in a conversation.The number of sub-conversations might only be known at runtime.E.g.as part of a logistics contract negotiation between a dairy producer and a supermarket chain a set of shippers are to be selected for transporting goods from the producer to the various intermediate warehouses of the chain. Therefore,negotiation conversations are started between the chain and each potential available shipper.A conversation C1∈Conv has two sub-conversations C2,C3∈Conv if∃C p∈Conv(C1,C2,C3⊂C p∧∀e2∈C2,e3∈C3[∃e11,e12∈C1(e11<e2∧e11< e3∧e2<e12∧e3<e12)])4.3C8.ForkA conversation is split into several conversations and is not merged later on.The number of conversations that are spawned offmight only be known at runtime.E.g.an order is placed and the different line items are processed in parallel.A split from a conversation C1∈Conv into the two conversations C2,C3∈Conv is given if∃C p∈Conv(C1,C2,C3⊂C p∧∀e1∈C1,e2∈C2,e3∈C3[e1< e3∧e1<e2])4.4C9.JoinSeveral conversations that do not originate from the same fork are merged into one conversation.The number of conversations that are merged might only be known at runtime.E.g.several orders arriving within one week are merged into a batch order.A join between two conversations C1,C2∈Conv into one conversation C3∈Conv is given if∃C p∈Conv(C1,C2,C3⊂C p∧∀e1∈C1,e2∈C2,e3∈C3[e1< e3∧e2<e3])10Alistair Barros,Gero Decker,Marlon Dumas,Franz Weber4.5C10.RefactorA set of conversations is refactored to another set of conversations.The num-bers of conversations that are merged and spawned offmight only be known at runtime.E.g.goods shipped in containers on different ships have reached a harbor where they are reordered into trucks with different destinations.This pattern generalizes Fork and Join.A refactoring from two conversations C1,C2∈Conv into the two conver-sations C3,C4∈Conv is given if∃C p∈Conv(C1,C2,C3,C4⊂C p∧∀e1∈C1,e2∈C2,e3∈C3,e4∈C4[e1<e3∧e1<e4∧e2<e3∧e2<e4])5Process Instance to Conversation RelationshipsThe correlation mechanisms already describe how to get to event groupings fol-lowing the notions of conversations and process instances.We assumed so far that conversations and process instances are orthogonal concepts and that groupings can be done independently from each other.This is only partly true.The normal case is that a process instance is involved in one or several conversations and according to which conversation an event belongs to the event is assigned to a particular process instance.Or it is the other way round that an event belonging to the same process instance like a previous event might be assigned to the same conversation.For clarifying this situation we describe the most important relationships between process instances and conversations.For thefirst time we use the notion of actors that are part of the framework.We assume that a process instance is executed by exactly one actor and therefore introduce the auxiliary relation ≈∈℘(AE)×℘(AE)where p1≈p2means that the process instances p1and p2 are executed by the same actor.Furthermore,we introduce the auxiliary relation ⊆℘(CE)×℘(AE)indi-cating that at least one event in a conversation C is causally related to at least one event in a process instance p. ={(C,p)∈℘(CE)×℘(AE)|∃e1∈C e2∈p(e1<c e2∨e2<c e1)}.5.1C11.One Process Instance–One ConversationA process instance is involved in exactly one conversation and there is no other process instance involved in it and executed by the same actor.E.g.a purchase order is handled within one process instance.A one-to-one mapping for a process instance p∈P I to conversation C∈Conv is given ifp C∧∀q∈P I[(p=q∧p≈q)→¬q C]∧∀D∈Conv[C=D→¬p D]Correlation Patterns in Service-Oriented Architectures11 5.2C12.Many Process Instances–One ConversationSeveral process instances executed by the same actor are involved in the same conversation.E.g.an insurance claim is handed over from the claim management depart-ment to thefinancial department.The different departments have individual process instances to handle the case.A many-to-one mapping for a set of process instances P I ⊆P I to conver-sation C∈Conv is given if∀p1,p2∈P I [p1≈p2]∧∀p∈P I [p C]5.3C13.One Process Instance–Many ConversationsOne process instance is involved in many conversations.E.g.a seller negotiates with different shippers about shipment conditions for certain goods.The shipper offering the best conditions is selected before shipment can begin.A one-to-many mapping for a process instance p⊆P I to a set of conversa-tions Conv ∈Conv is given if∀C∈Conv [p C]We can refine this pattern by looking at the relationship between individual sub-process instances(threads)and the conversations.p1∈P I is a sub-process instance of p2∈P I if all events in p1are contained in p2:p1⊆p2.Having identified all sub-processes instances we can then analyze if they conform to one of the three mapping patterns.5.4C14.Initiator RoleA process instance has the role of the initiator of a conversation if the conversa-tion is started within the process instance.E.g.a buyer places a purchase order and triggers a conversation concerning the negotiation about the price.A process instance p∈P I is an initiator of a conversation C∈Conv if ∃e1∈p e2∈C(e1<c e2∧¬∃f∈C(f<e2)).5.5C15.Follower RoleA process instance has the role of a follower(or responder)in a conversation it participates in if the conversation was created within another process instance. The process instance might be created because of a message received in the conversation.E.g.a purchase order comes in and is processed in a new process instance.A process instance p∈P I is a follower in a conversation C∈Conv if ¬∃e1∈p e2∈C(e1<c e2∧¬∃f∈C(f<e2)).。
