RSP Dev tutorial streamezzo
DEVC基础教程之函数

DEVC基础教程之函数函数是程序中非常重要的一部分,通过函数可以将一段代码封装起来,实现代码的重用和模块化。
在DEVC编程语言中,函数使用起来也非常简单,本教程将详细介绍函数的基本概念、语法和用法。
1.函数的定义在DEVC中,函数的定义使用`func`关键字,后面跟着函数名和一对小括号。
函数名可以根据需要来命名,但最好能够描述函数的功能。
小括号中可以放置函数的参数,参数用逗号分隔。
```func 函数名(参数1, 参数2, 参数3, ...)//函数体```2.函数的调用在DEVC中,函数调用使用函数名和一对小括号,如果函数有参数,可以在小括号中传入参数的值。
传入的参数按照参数的定义顺序进行匹配。
```函数名(参数1,参数2,参数3,...)```3.函数的返回值函数可以有返回值,使用`-> 返回类型`来指定返回值的类型。
在函数体中,使用`return`关键字来返回结果。
```func 函数名(参数1, 参数2, 参数3, ...) -> 返回类型//函数体return 结果```4.函数的参数在函数定义中,可以指定参数和参数的类型,参数可以有默认值。
调用函数时,可以传入参数的值,也可以使用默认值。
```func 函数名(参数1: 类型1 = 默认值1, 参数2: 类型2 = 默认值2, ...)//函数体```5.可变参数有时候,函数需要接受变长的参数,DEVC提供了可变参数的功能。
在参数列表中使用`...`来表示可变参数。
```func 函数名(参数1, 参数2, 参数3: 类型...)//函数体```在函数体中,可以使用`参数名.count`来获取可变参数的数量。
6.匿名函数在DEVC中,可以使用匿名函数来定义一个没有函数名的函数。
匿名函数常用于函数参数的传递。
```{(参数1, 参数2, ...) -> 返回类型 in//函数体return 结果```7.函数作为参数在DEVC中,函数可以作为参数传递给其他函数。
DevSecOps教程说明书

DevSecOpsWhat Why and How?Anant Shrivastava@anantshriNotSoSecure Global ServicesDirector NotSoSecure Global ServicesSysadmin / Development / SecurityTrainer / Speaker: BlackHat, Nullcon, RootConf, RuxCon, IPExpo, C0c0n Project Owner: Android Tamer, Code VigilantContributor: null, G4H, OWASP and morehttps:// (@anantshri on social platforms)About: Anant ShrivastavaAgenda●What is DevSecOps?●Why do we need DevSecOps?●How do we do DevSecOps?●Integrate Security in DevOps Pipeline●Tools of Trade●Sample Implementation (On Prem and Cloud Native)●Case StudiesDisclaimer●I will be listing a lot of tools, It’s not an exhaustive list ●I don't endorse or recommend any specific tool / vendor ●Every environment is different: Test and validate beforeimplementing any ideasWhat is DevSecOps? Effort to strive for “Secure by Default”●Integrate Security via tools●Create Security as Code culture●Promote cross skillingWhy do we need DevSecOps?●DevOps moves at rapid pace, traditional security just can’tkeep up●DevSecOps makes it easier to manage rapid pace ofdevelopment & large scale secure deployments●DevSecOps allows for much smoother scaling of process ●Security as part of process is the only way to ensure safetyDeveloperSource Code RepositoryBuildCI/CD Server Staging /QAProduction MonitoringSuite of Security Test1 SQL Injection Fewer Man Day Effort No New DeploymentsAutomated Source Code ReviewDeveloperSource Code RepositoryBuildCI/CD ServerStaging /QA Production MonitoringSuite of Security TestHow do we do DevSecOps?●DevSecOps is Automation + Cultural Changes●Integrate security tools into your DevOps Pipeline●Enable cultural changes to embrace DevSecOpsPre-Commit Hooks IDE PluginsDeveloperSecretsManagementCode RepositoryCI/CD ServerStatic Application SecurityTesting(SAST)SourceComposition Analysis (SCA)Pre-BuildDynamic Application SecurityTesting(DAST)Post-BuildBuild Artifacts versioning against code commitsArtifact RepositoryManual Web Application Pentesting Business Logic FlawsQA/StagingSecurity in Iaac Compliance as CodeAlerting & MonitoringProductionVulnerability ManagementInjecting Sec in DevOpsDevOps ---> DevSecOps DevOps PipelineDevSecOps PipelinePre-Commit Hooks●Sensitive information such as the access keys, accesstokens, SSH keys etc. are often erroneously leaked due to accidental git commits●Pre-commit hooks can be installed on developer’sworkstations to avoid the same●Work on pure Regex-based approach for filtering sensitivedata●If developers want they can circumvent this step hence useit like a defense in depth but don't fully rely on itIDE Security Plugin●IDE Plugin's provide quick actionable pointer to developers ●It is useful to stop silly security blunders●Work on pure Regex-based approach●If developers want they can circumvent this step hence useit like a defense in depth but don't fully rely on itSecrets Management●Often credentials are stored in config files●Leakage can result in abuse scenario●Secrets Management allows you totokenize the informationSoftware Composition Analysis●We don’t write software's, we build on frameworks●Biggest portion of software is now third party libraries●Major languages provide module managements●PIP, NPM, Gems, go get, perl cpan, php packager and more●Software Composition Analysis performs checks to identifyvulnerable/outdated 3rd party librariesStatic Analysis Security Testing●White-box security testing using automated tools●Useful for weeding out low-hanging fruits like SQL Injection,Cross-Site Scripting, insecure libraries etc●Tool by default configured with generic setting, needsmanual oversight for managing false-positivesDynamic Analysis Security Testing●Black/Grey-box security testing using automated tools●SAST may not get full picture without application deployment ●DAST will help in picking out deployment specific issues●Results from DAST and SAST can be compared to weed outfalse-positives●Tools may need prior set of configuration settings to givegood resultsSecurity in Infrastructure as Code●Infrastructure as a code allows you to document andversion control the infra●It also allows you to perform audit on the infrastructure●Docker / K8s infra relies on base images●Environment is as secure as the base image●Base images need to be minimal in nature and need to beassessed to identify inherited vulnerabilitiesCompliance as Code●Compliance could be industry standard (PCI DSS, HIPAA,SOX) or org specific●Compliance is essentially a set of rules and hence can beconverted into written test cases●Having written code format this can again be versioncontrolledVulnerability Management●All the tools discussed above result in report fatigue●Every tool has a different style of presentation● A central dashboard is required to normalize the data●Vulnerability Management System can then be integrated tobug tracking systems to allow devs to work on itemsAlerting and Monitoring●Monitoring is needed for two end goals●Understand if our security controls are effective●What and where we need to improve●To test Security control effectiveness:●When did an attack occur●Was it blocked or not●What level of access was achieved●what data was bought in and bought outAsset Monitoring●With recent advancements assets now should includeanything and everything where organization data resides●With rapid development & provisioning the asset inventorycan't be a static inventory●We need to monitor the assets constantly both on premiseand CloudReference: https:///blog/redifining-assets-a-modern-perspective.htmlSample Implementation - Java A simplistic flow of DevSecOps Pipeline incorporating various stagesPre-Commit Hooks Software Composition AnalysisStatic Analysis Security Testing(SAST)Secret Management Threat Modelling Tools ThreatSpec Microsoft ThreatModeling ToolRetire.js IDE Plugins Git HoundtruffleHog KeywhizDynamic Analysis Security Testing (DAST)Security in Infrastructure asCodeCompliance as Code Vulnerability ManagementWAFDocker Bench for SecurityTo be or Not to Be in Pipeline ●API / command line access●Execution start to final output should be 15 minutes max ●Tools should be Containerizable / scriptable●Minimal licensing limitations (parallel scans or threads)●Output format parsable / machine readable (no to stdout,yes to json / xml)●Configurable to counter false negatives / false positivesPipeline Optimization●Pipeline to be tweaked based on Milestone (Initiative/Epic/Story)●Remember initial onboarding is tedious●Ensure dataset dependent tool get frequent data refresh●Sample optimization●Only CSS Changes: no need for SCA●Only pom.xml or gradle changes: no need of SAST●If Infra as code has zero changes skip or fast track infra scan●Ensure to run full (non optimized) pipeline periodicallyDoes Programming Language Matter ●Different programming languages need different tools forstatic analysis and software composition analysis●Some tools support multiple languages like sonarqube●Others are focused on one languageLanguage Specific ToolsJAVAPHPPythonRuby/RailsLanguagesSoftware Composition Analysis Source Code Static Analysis .NETDotNET Retire SafeNuGet ClearlyDefined Node JS ClearlyDefinedgraudit graudit graudit DotNet Security Guard Brakeman graudit NodeJsScan npm-checkDevSecOps Lab - RubyDevSecOps Lab - PHPDevSecOps Lab - PythonDevSecOps Lab - NodeJS●The Threat Landscape changes-Identity and Access Management -Asset Inventory -Billing●Infrastructure as Code allows quick audit / linting ●Focus more on:-Security groups-Permissions to resources -Rogue / shadow admins-Forgotten resources (compromises / billing)What about CloudCloud Native Approach to Security●Different Service Providers Approach Security Differently ●All of them provide some of the ingredient in-house●Irrespective of Cloud provider some tools will still need tobe sourced●Static Code Analysis Tool●Dynamic Code Analysis Tool●Software Composition Analysis●Vulnerability Management ToolAWS Cloud Native DevSecOpsCloud Native Dev[Sec]OpsConventional Infra AWS Azure GCPSource Code Management Bitbucket, Github, Gitlab etc..AWS CloudCommit Azure Repos Cloud Source Repositories Infrastructure As a Code Chef, Puppet, Ansible more..Amazon CloudFormation Azure DevTest Labs Cloud CodeCI/CD Server Jenkins, Bamboo, Gitlab,Travis CI, Circleci moreAWS CodeBuildAWS CodeDeployAWS CodePipelineAzure Pipelines, Azure Test Plans Cloud Build, TektonArtifactory RepositoryjFrog Artifactory,Sonatype Nexus, more..Amazon S3Azure Artifacts Cloud FirestoreStg/Prod ServersVMWare,On-premises serversEC2ECS (Elastic Containers)EKS (Elastic Kubernetes)Virtual Machines,Azure Lab Services,Azure Kubernetes Service (AKS)Compute Engine,App Engine,Shielded VMsMonitoring & Alert Nagios, Graphite, Grafana AWS CloudWatch Azure Monitor, Network Watcher Access TransparencyFirewall Modsecurity AWS Firewall Manager, AWSWAFAzure Firewall Application GatewayDLP MyDLP, OpenDLP Amazon Macie Azure Information Protection Cloud Data Loss PreventionThreat Detection Snort, Kismet Amazon GuardDuty Azure Advanced ThreatProtectionEvent Threat Detection (beta)Vulnerability Scanning OpenVAS, Nessus Amazon Inspector Azure Security Center Cloud Security Scanner Secrets Management Hashicorp Vault, Docker Secrets AWS Secrets Manager Azure Key Vault Secrets management●Automation alone will not solve the problems●Encourage security mindset especially if outside sec team ●Cultivate/Identify common goals for greater good ●Build allies (security champions) in company ●Focus on collaboration and inclusive culture ●Avoid Blame GameSecurity team should try to eliminate the need of dedicated security teamCultural AspectSecurity Champion●Bridge between Dev, Sec and Ops teams●Single Person per team●Everyone provided with similar cross skilling opportunities ●Incentivize other teams to collaborate with Sec team○Internal Bug bounties○Sponsor Interactions (Parties / get-togethers)○Sponsor cross skilling trainings for other teamsSecurity EnablersPeople•Build relationships between teams, don’t isolate•Identify, nurture security conscious individuals•Empower Dev / ops todeliver better and fasterand secure, instead ofblocking.•Focus on solutions instead of blamingProcess•Involve security from get-go(design or ideation phase)•Fix by priority, don’tattempt to fix it all•Security Controls must beprogrammable andautomated whereverpossible•DevSecOps Feedbackprocess must be smoothand governedTechnology•Templatize scripts/tools perlanguage/platform•Adopt security to devopsflow don’t expect others toadopt security•Keep an eye out for simplerand better options and bepragmatic to test and usenew toolsGeneric Case StudyNegative Case StudiesC l o u d A ss e t sM i s co n f ig u r at i o nPrevention: Continuous monitoring and review of cloud assets and configIs it Enough?●Rite of passage by periodic pen test and continuous bug bounty●It's not just important to get feedback but to also action on them●Risk Acceptance Documentation should be the worst case scenarionot your first bet●Did we secure the security controls●DevSecOops : If attacker controls securitytools / build chain It has limitless power●Ensure the same practice is followed backagain for these tools●Security role doesn't means you get tocircumvent the rules●Follow basic security hygiene we alwayskeep talking about●Secure configuration●Patching PolicyWho Watches the WatcherReferences•https:///docs/us-17/thursday/us-17-Lackey-Practical%20Tips-for-Defendin g-Web-Applications-in-the-Age-of-DevOps.pdf•https:///hubfs/2018%20State%20of%20the%20Software%20Supply%20 Chain%20Report.pdf•https://snyk.io/opensourcesecurity-2019/•https:///•https:///state-of-software-security-reportKey Takeaways●Security is everyone responsibility●Embrace security as an integral part of the process, use feedback torefine the process●DevSecOps is not a one size fit all: your mileage will vary*********************。
devcpp_教程

前言对于现在越来越多得关于编程方面得问题和商业公司对版权问题的担心。
所以向各位推荐一款类似于VC的IDE。
这款IDE所使用的编译程序是 GCC的Win32版本 Mingw32。
而IDE本身也是GPL协议的产物。
所以,不论是商业用户,还是个人用户都能够自由的使用她,而不必为使用盗版软件而提心吊胆的。
另外,由于Mingw32是GCC的Win32版本。
所以,也为Win32的程序员可以了解一下Unix和类Unix下的编程感觉。
而且,Mingw32对Win32函数的支持也是很不错的。
希望,我们的Mingw32之旅可以带给你快乐。
介绍有关Dev-Cpp的介绍,我在这里不想多做解释。
因为下面会具体的介绍和讲解的。
我在这里只是想要介绍一下有关GCC的内容。
因为,Dev-Cpp所使用的Mingw32是一款GCC编译器。
所以,对GCC的了解有助于使用Dev-Cpp。
gcc.exe这是一个C语言的编译器,负责编译C语言。
这个也许大家都知道。
不过,在这里我要先向大家说明一下。
gcc只是一个C语言的编译器。
不能识别C++代码。
所以,以前所说的gcc可以编写C++是一个误传。
因为,我们通常所说的GCC不是gcc.exe而是GCC的一套程序。
其中就包括可以编译C++语言的g++.exe如果,你不确定这个gcc的版本,可以用如下的命令查看。
gcc -v关于编译,gcc可以通过命令符编译。
gcc source.c -o binary以上的命令,是让gcc直接由.c代码编译成可执行代码。
也可以这样。
gcc -c source.c -o code.ogcc code.o -o binary这样就生成了一组二进制代码,然后在通过二进制代码生成可执行程序。
g++.exe刚才已经说过了,这个是一个用于编译C++代码的程序。
基本用法和gcc一样。
所以这里不再介绍了。
只是让各位了解一下,这个程序是编译C++代码的。
gdb.exe用于调试程序的。
c++中实现调用外部程序的方法linux__概述及解释说明

c++中实现调用外部程序的方法linux 概述及解释说明1. 引言1.1 概述本篇文章旨在探讨在C++语言中如何调用外部程序,并着重介绍在Linux环境下的具体方法。
调用外部程序是在软件开发中常见的需求,通过调用外部程序可以实现更多功能和交互方式。
本文将从基本原理以及注意事项开始阐述,然后详细介绍在C++中实现调用外部程序的方法,并给出示例代码进行解析。
1.2 文章结构本文将按照以下结构组织内容:首先,在引言部分进行概述和明确目的;然后在第2节中,详细讲解在C++中调用外部程序的方法,包括基本原理和Linux环境下的注意事项;紧接着,在第3节中,将通过示例及代码解析展示具体的调用外部程序的实现过程;最后,在第4节中,介绍使用第三方库实现更复杂交互方式的方法,并给出相关示例;最后一节为结论与总结。
1.3 目的本文旨在提供读者关于C++语言中如何通过调用外部程序来扩展功能和实现更灵活交互方式方面的详尽解释。
通过了解基本原理以及学习具体实践案例,读者可获得掌握在C++中调用外部程序的能力。
另外,引入第三方库实现更复杂交互方式的方法也将拓宽读者的知识面和技能应用范围。
最终,通过全面而清晰地阐述调用外部程序的方法,本文旨在提供有关调用外部程序的详尽指南,并启示读者对未来可能发展方向的展望。
以上是关于文章“1. 引言”部分内容的详细说明。
2. 调用外部程序的方法:在C++中,调用外部程序是一种常见的需求,可以通过多种方式实现。
本节将介绍C++中调用外部程序的基本原理、在Linux环境下调用外部程序时需要注意的事项以及具体的实现方法介绍。
2.1 C++中调用外部程序的基本原理:在C++中,调用外部程序可以借助操作系统提供的系统调用或库函数来实现。
常见的方法包括使用system函数、使用fork和exec函数族以及使用popen 函数等。
2.2 Linux环境下调用外部程序的注意事项:在Linux环境下调用外部程序时,需要注意以下几个方面:- 文件路径:确保正确地指定待执行的外部程序文件路径,在使用相对路径时要考虑当前工作目录。
DevCPP使用指南要点

DevCPP使用指南要点Dev-C++是一个Windows平台下的C/C++编程开发工具,可以帮助程序员更高效地编写代码,提供了各种实用的功能和工具。
本文将介绍DevCPP的使用要点,帮助新手更快速地上手。
一、安装和基本设置1.安装Dev-C++:从官网下载安装包,双击运行后一路确认即可安装完成。
2.默认设置:打开Dev-C++后,可以看到主界面,点击“Tools”菜单,选择“Compiler Options”,设置默认编译器路径为安装目录下的bin文件夹中的g++.exe。
同时将“Linker for dynamic libs”设置为mingw32-gcc.exe,其他默认设置无需更改。
3.设置快捷键:点击“Tools”菜单,选择“Editor Options”,找到“Keybindings”选项,勾选“Emulate Borland IDE”选项,启用经典快捷键。
二、基本操作1.创建源文件:点击“File”菜单,选择“New”,在提示框中输入文件名,选择保存路径,确定后即可创建新的源文件。
2.编写代码:在新建源文件中输入C或C++代码,保存后即可进行编译和运行操作。
3.编译和运行:点击菜单栏的“Execute”,再选择“Compile & Run”即可编译并运行程序。
4.调试程序:点击菜单栏的“Execute”,再选择“Debug”即可进入调试模式,F7键可以逐行执行程序,F8键可以直接跳过当前行。
三、常用功能1.代码自动补全:在源文件中输入函数名或变量名的一部分,按下“Ctrl”+“空格”组合键即可弹出自动补全列表。
2.语法错误提示:编写代码时可以通过下划线、颜色等方式对代码进行语法检查和提示。
3.查找和替换:点击菜单栏的“Search”选项,选择“Find”或“Replace”即可进行查找和替换操作。
4.代码折叠:将光标移动到代码行左侧的折叠图标上方,点击即可折叠或展开代码。
四、常见问题1.编译出错:根据错误提示检查代码,如果无法解决可以尝试通过卸载并重新安装软件来解决问题。
EclipseRCPTutorial(中文教程)

EclipseRCPTutorial(中文教程)(RCP教程)Tutorial(RCPEclipse RCP TutorialLars Vogel4.6((版本4.6)Version4.6Copyright?2007-2010Lars Vogel28.06.2010028.06.201翻译:廖永为(武汉纺织大学)2010-09-27Eclipse RCP这篇文章介绍了如何开发eclipse RCP应用程序(基于eclipse3.6平台eclipse Helios)。
目录1.Eclipse RCP (1)1.1概述 (1)1.2.RCP体系结构 (2)1.3.RCP的主要组成部分 (3)1.4.配置文件 (3)2.Eclipse安装 (4)2.1.Eclipse安装 (4)2.2.升级Java IDE (4)3.创建RCP应用程序 (5)3.1.创建RCP应用程序 (5)3.2.运行RCP应用程序 (9)4.启动过程和指导 (11)5.运行配置 (12)Overview””标签项 (12)5.1.“Overview5.2.检查运行时配置 (13)6.命令 (15)6.1.概述 (15)6.2.定义命令 (15)6.3.在菜单中使用命令 (18)7.系统托盘 (22)8.视图 (26)8.1.概述 (26)8.2.创建一个视图 (26)8.3.给透视图增加视图 (27)8.4.结果 (28)8.5.通过代码把视图添加到透视图 (28)8.6.编辑器/视图联合使用 (29)9.对话框 (30)9.1.概述 (30)9.2.使用预定义对话框 (30)9.3.选择 (31)9.4.用户定义的对话框 (33)10.区域帮助 (38)11.向导 (40)11.1.概述 (40)11.2.例子 (40)12.增加状态栏 (45)12.1.加上状态栏 (45)12.2.共享状态栏 (46)13.透视图 (50)13.1.给应用程序增加透视图 (50) 13.2.选择透视图 (52)14.产品和绑定 (54)14.1.应用程序和产品 (54)14.2.产品配置 (54)14.3.创建产品配置文件 (54)14.4.依赖项 (57)14.5.运行产品 (58)14.6.闪屏 (59)14.7.绑定你的产品 (60)14.8.定制启动图标和参数 (61)15.产品部署 (63)16.技能技巧 (66)16.1.保存用户布局 (66)16.2.查找不可用的依赖 (67)16.3.用你的RCP应用程序部署你自己的JRE (68)16.4.多用户设置 (68)17.进一步学习 (69)18.鸣谢 (69)19.问题讨论 (69)20.相关链接和文献 (70)20.1.源代码 (70)20.2.Eclipse资源 (70)20.3.vogella资源 (70)1.Eclipse RCP下面假设你已经了解如何使用eclipse IDE集成开发环境。
devcpp-使用手册
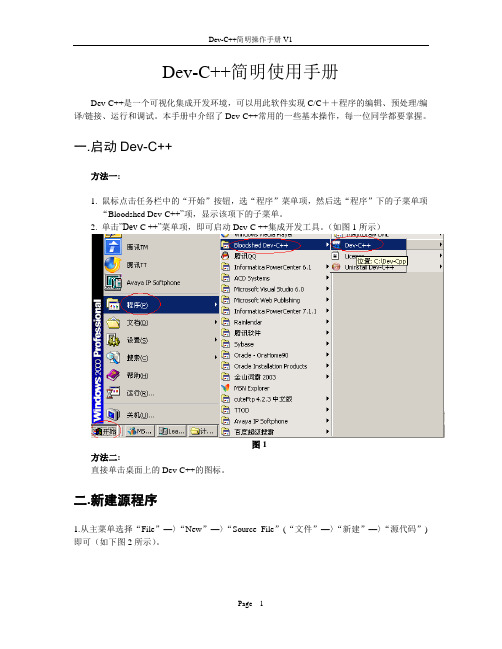
Dev-C++简明使用手册Dev-C++是一个可视化集成开发环境,可以用此软件实现C/C++程序的编辑、预处理/编译/链接、运行和调试。
本手册中介绍了Dev-C++常用的一些基本操作,每一位同学都要掌握。
一.启动Dev-C++方法一:1. 鼠标点击任务栏中的“开始”按钮,选“程序”菜单项,然后选“程序”下的子菜单项“Bloodshed Dev-C++”项,显示该项下的子菜单。
2. 单击”Dev-C ++”菜单项,即可启动Dev-C ++集成开发工具。
(如图1所示)图1方法二:直接单击桌面上的Dev-C++的图标。
二.新建源程序1.从主菜单选择“File”—〉“New”—〉“Source File”(“文件”—〉“新建”—〉“源代码”)即可(如下图2所示)。
图2如果大家看到界面上的字是中文的,则可以根据以下操作将界面改为英文。
点击主菜单“工具”->”环境选项”,在弹出的对话框中选择界面页,在Language下拉列表中选择Chinese 即可,如下图所示。
此时界面上的菜单、工具条等全部以英文命名。
2.此时屏幕右下侧出现一片白色区域,可以在此输入程序。
如下图3所示。
菜单工具栏源程序编辑区域输出标签页图33.保存源程序到硬盘一个好的习惯是创建了一个新程序后,在还未输入代码之前先将该程序保存到硬盘某个目录下,然后在程序的编辑过程中经常性地保存程序,以防止机器突然断电或者死机。
要保存程序,只需从主菜单选择“File”—〉”Save”就可以将文件保存到指定的硬盘目录。
如图4所示。
图4此时会弹出一个对话框,如图5所示。
在此你需要指定文件要存放的目录(此处为F:\temp),文件名称(此处为test)以及保存类型。
需要注意的是,在保存类型处一定要选择 C sourcefiles(*.c),意思是保存地是一个C文件。
在点击右下脚的保存按钮后,在temp目录下将会出现一个名为test.c的源文件。
图54.在程序编辑区域编辑程序,如图6所示。
dev c++编译过程讲解

dev c++编译过程讲解
Dev-C++ 是一个用于 C 和 C++ 编程的集成开发环境(IDE)。
以下是 Dev-C++ 的编译过程的基本步骤:
编写代码:在 Dev-C++ 中,你可以编写 C 或 C++ 代码。
这个过程涉及到在文本编辑器中输入代码,并在保存文件时指定文件类型(例如 .cpp 表示 C++ 文件)。
保存文件:在完成代码编写后,你需要保存你的文件。
在保存时,你需要确保文件类型与你的代码语言相匹配(例如 .cpp 文件用于 C++ 代码)。
编译代码:在 Dev-C++ 中,你可以通过菜单栏中的 "Execute" -> "Compile & Run" 来编译和运行你的代码。
或者你可以简单地按 F9 键来编译和运行你的代码。
Dev-C++ 将把你的源代码文件(例如 .cpp 文件)转换成可执行文件。
运行程序:如果编译过程没有错误,Dev-C++ 将自动运行你的程序。
你可以在 Dev-C++ 的输出窗口中看到程序的输出。
调试代码:如果编译过程中出现错误,你需要修复这些错误然后重新编译。
Dev-C++ 提供了一个调试器,可以帮助你找到并修复代码中的错误。
以上就是 Dev-C++ 的基本编译过程。
具体的步骤可能会根据 Dev-C++ 的版本或者你的开发环境有所不同,但大体流程应该是相似的。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
What is RSP ? (1)
RSP Language describe UPDATES to the scene on the client The finality is to describe a scene, or one part of a scene in one rsp Most of the updates will (should) be incremental (like AJAX) RSP has a syntax similar to JSP that is: Build an XML tree using Java language to compute static parts Compiled to Java then to .class Execution result is a binary stream that can be read by the client XML syntax representing basic objects understood by the player
RSP Development Tutorial
7
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
Exercise 1
1) Write a menu with the following aspect: 2) Have the green bar change position when pressing UP or DOWN
Root
Transform
Shape (rectangle)
Transform
Shape A (ellipse)
Text (hello)
rendering orderRSP Development Tutorial
5
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
<% if (i+1 != n) { %> <Text string="<%= "Item " + (i+1) %>" vertAlign="MIDDLE" horizAlign="CENTERED" /> <% } %>
RSP Development Tutorial
10
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
Working with Java (2)
To interact with the outside world Import libraries: (at the beginning of the page) <%@ page import="java.awt.Rectangle" %> <%@ page import="java.awt.Color" %> Declare helper classes and functions <%! Rectangle.Float sizeOnly(Rectangle.Float r) { […] %> Get data from the back and prepare it before generating the UI
Basic nodes and attributes (1)
Transform
<Transform DEF=“MyTr" translation="10 20" scale="1 2"> [Children] </Transform>
Shape
<Shape DEF="Grayed“ color="#CCCCCC“ filled="true" points="0 10 240 -10 0 -10 />
RSP Development Tutorial
3
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
What is RSP ? (3)
The nodes are represented in a tree in the client The client renders that tree by browsing it once per frame That tree is modified using « updates » Insert: add a node inside another Delete Replace: a node or one of its attribute Nodes and updates are XML elements of the RSP language Nodes have a name « DEF » and an activity Nodes with a DEF can be modified by other nodes Nodes not active are ignored by the renderer Updates usually have a target node
Unlike the web, RSP has a time line Several parts may be sent individually and executed at different times The minimal « part » is called a unit, the player can’t decode less than one unit. There are media units, (images, video frames …) And scene description units « AUnit » or « access units » The scene description is composed of « nodes »: Visual nodes (Images, video, vector objects, texts, …) Logic nodes (can modify the other nodes) Animations nodes (with interpolation) One grouping node : « Transform » All types nodes can be mixed with no restrictions
scene.stz (pre executed RSP)
HTTP
scene.rsp
content
Service stub
resources
RSP Development Tutorial
1
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
Conditional: update tags at runtime
<Conditional startTime="20000"> <Replace target="MyText" field="Text.string" stringvalue="A new text" /> </Conditional>
Logic Logic Logic Logic Logic
RSP Development Tutorial
2
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
What is RSP ? (2)
RSP Development Tutorial
8
Copyright © Streamezzo SA – 2008 All rights Reserved Confidential and Proprietary
Geometry in the RME
Everything is centered if not mentionned otherwise The Transform node is the main target for geometrical effects, transfer the property to its children When specifying coordinates, X is the first value, Y is the second Use the « delta » attribute of a Transform to position its children in a list.
RSP Development tutorial
Streamezzo Service architecture
Rich Media Client
Application
The web
Rich Media Server
Webapp Service
request build dynamic content
240 10 0 10"
Action
<Action keyCodes="FIRE"> <ActionKey hideObject="Grayed" /> </Action> ActionKey is NOT a node.
