ml-chap09
NVIDIA DOCA 编程指南说明书

Overview GuideTable of ContentsChapter 1. Introduction (1)Chapter 2. DOCA Libraries (2)2.1. DOCA App Shield (2)2.2. DOCA Arg Parser (2)2.3. DOCA Comm Channel (2)2.4. DOCA Compress (3)2.5. DOCA Core (3)2.6. DOCA DMA (3)2.7. DOCA DPA (3)2.8. DOCA DPI (3)2.9. DOCA Erasure Coding (4)2.10. DOCA Ethernet (4)2.11. DOCA Flow (4)2.12. DOCA GPUNetIO (4)2.13. DOCA IPsec (5)2.14. DOCA RDMA (5)2.15. DOCA RegEx (5)2.16. DOCA Rivermax (5)2.17. DOCA SHA (5)2.18. DOCA Telemetry (5)2.19. DOCA UCX (6)Chapter 1.IntroductionDOCA programming guides provide the full picture of DOCA libraries and their APIs. Each guide includes an introduction, architecture, API, and many more library-specific information with the aim of making DOCA libraries easy to use.Chapter 2.DOCA LibrariesDOCA libraries are designed to serve DOCA-based software such as the provided example applications. For optimal performance, it is recommended to run these applications on the DPU. However, if necessary, DOCA libraries can be run on the host.In addition, built-in gRPC support for DOCA allows certain libraries to be used by gRPC clients running on the host that communicates with a matching gRPC server which implements the library's functionality on the DPU.2.1. DOCA App ShieldDOCA App Shield library API offers intrusion detection capabilities using the built-in hardware services of the DPU to collect data from the host's memory space. App Shield makes it possible to detect attacks on critical services in the host system. This library leverages the DPU's direct memory access (DMA) capability to monitor the host's memory space directly without involving the host's operating system nor CPU.2.2. DOCA Arg ParserDOCA Arg Parser library offers DOCA-based programs an easy and simple command-line interface. Arg Parser supports both regular command-line arguments and a JSON mode that accepts a JSON file containing the required arguments.2.3. DOCA Comm ChannelDOCA Comm Channel library creates a secure, network-independent communication channel between the host and the DPU. Comm Channel provides a client-server API. Comm Channel is reliable and message-based. It offers a notification mechanism that can be used by Linux system calls (e.g., epoll, poll, select) and support for multiple connections on the server-side.2.4. DOCA CompressThe DOCA Compress library offers a hardware-accelerated way to compress and decompress data on both DPU and host.2.5. DOCA CoreThe DOCA Core library provides a unified interface to construct standardized DOCA workflows that other libraries and applications can build upon.2.6. DOCA DMAThe DOCA Direct Memory Access (DMA) library offers an API for copying data buffers between the host and the DPU using hardware acceleration, supporting both local and remote copy. DMA allows the execution of complex memory operations in an optimized, hardware-accelerated manner.2.7. DOCA DPAThe DOCA Erasure Coding library provides an API to encode and decode data using hardware acceleration, supporting both the host and NVIDIA® BlueField® DPU memory regions.DOCA Erasure Coding recovers lost data fragments by creating generic redundancy fragments (backup). Each redundancy block that the library creates can help recover any block in the original data should total loss of a fragment occur.DOCA Erasure Coding increases data redundancy and reduces data overhead.2.8. DOCA DPIDOCA Deep Packet Inspection (DPI) library offers a deep examination of data packets as they traverse a monitored network checkpoint. DPI provides a robust mechanismfor enforcing network packet filtering, as it can be used to identify or block a range of complex threats due to efficient data stream inspection.DPI leverages the RegEx engine on the DPU which can very efficiently parse regular expressions found in packets.DOCA DPI has built-in gRPC support.2.9. DOCA Erasure CodingThe DOCA Erasure Coding library provides an API to encode and decode data using hardware acceleration, supporting both the host and NVIDIA® BlueField® DPU memory regions.DOCA Erasure Coding recovers lost data fragments by creating generic redundancy fragments (backup). Each redundancy block that the library creates can help recover any block in the original data should total loss of a fragment occur.DOCA Erasure Coding increases data redundancy and reduces data overhead.2.10. DOCA EthernetThe DOCA Ethernet library provides two APIs for receiving Ethernet packets on an RX queue and for sending Ethernet packets on a TX queue respectively.The library collects the user configuration data on the host CPU side, creates TX/RX objects, and exports them to the GPU side for execution in the data-path.2.11. DOCA FlowDOCA Flow library is the most fundamental API for building generic execution pipes in hardware. The main building block of the library is a pipe. Each pipe consists of match criteria, monitoring, and a set of actions. Pipes can be chained to create a set of complex actions to be performed on ingress packets.This library serves as an abstraction layer API for network acceleration and should be used by applications intended to offload packet processing from the operating system Kernel directly to the user space.DOCA Flow has a built-in gRPC-support.2.12. DOCA GPUNetIOThe DOCA GPUNetIO library offers building blocks to create a GPU-centric packet processing network application where CUDA kernels are capable of directly interacting with the network card without involving the CPU in the main critical path.This library provides CUDA device functions to send and receive packets. Additionally, an object named semaphore is provided to allow message passing across CUDA kernels or a CUDA kernel and a CPU thread.This library also allow allocating memory on the GPU that would be accessible from the CPU and vice versa.2.13. DOCA IPsecThe DOCA IPsec library provides an API to create the security association (SA) objects required for DOCA Flow's hardware-accelerated encryption and decryption.2.14. DOCA RDMADOCA RDMA enables direct access to the memory of remote machines, without interrupting the processing of their CPUs or operating systems. Avoiding CPU interruptions reduces context switching for I/O operations, leading to lower latency and higher bandwidth compared to traditional network communication methods.2.15. DOCA RegExDOCA RegEx library provides regular expression pattern matching to DOCA programs. It provides access to the regular expression processing (RXP) engine, a high-performance hardware-accelerated engine available on the DPU.RegEx allows the execution of complex regular expression operations in an optimized, hardware-accelerated manner.2.16. DOCA RivermaxThe DOCA Rivermax library provides an API for using NVIDIA® Rivermax®, an optimized networking SDK for media and data streaming applications. Rivermax leverages the DPU hardware streaming acceleration technology which allows data to be transferred to and from the GPU to deliver best-in-class throughput and latency.2.17. DOCA SHAThe DOCA SHA library provides a flexible and unified API to leverage the secure hash algorithm offload engine present in the NVIDIA® BlueField®-2 DPU. The SHA hardware engine supports SHA-1, SHA-256, and SHA-512 algorithms either as "single shot" or stateful calculations.2.18. DOCA TelemetryDOCA Telemetry library offers a fast and convenient way to transfer user-defined data to the DOCA Telemetry Service (DTS). Telemetry API provides the user a choice between several different outputs including saving the data directly to storage, NetFlow, Fluent Bit forwarding, or Prometheus endpoint.2.19. DOCA UCXUnified Communication X (UCX) is an optimized point-to-point communication framework. UCX exposes a set of abstract communication primitives that makes the best use of available hardware resources and offloads. UCX facilitates rapid development by providing a high-level API, masking the low-level details, while maintaining high performance and scalability.NoticeThis document is provided for information purposes only and shall not be regarded as a warranty of a certain functionality, condition, or quality of a product. NVIDIA Corporation nor any of its direct or indirect subsidiaries and affiliates (collectively: “NVIDIA”) make no representations or warranties, expressed or implied, as to the accuracy or completeness of the information contained in this document and assume no responsibility for any errors contained herein. NVIDIA shall have no liability for the consequences or use of such information or for any infringement of patents or other rights of third parties that may result from its use. This document is not a commitment to develop, release, or deliver any Material (defined below), code, or functionality.NVIDIA reserves the right to make corrections, modifications, enhancements, improvements, and any other changes to this document, at any time without notice.Customer should obtain the latest relevant information before placing orders and should verify that such information is current and complete.NVIDIA products are sold subject to the NVIDIA standard terms and conditions of sale supplied at the time of order acknowledgement, unless otherwise agreed in an individual sales agreement signed by authorized representatives of NVIDIA and customer (“Terms of Sale”). NVIDIA hereby expressly objects to applying any customer general terms and conditions with regards to the purchase of the NVIDIA product referenced in this document. No contractual obligations are formed either directly or indirectly by this document.NVIDIA products are not designed, authorized, or warranted to be suitable for use in medical, military, aircraft, space, or life support equipment, nor in applications where failure or malfunction of the NVIDIA product can reasonably be expected to result in personal injury, death, or property or environmental damage. NVIDIA accepts no liability for inclusion and/or use of NVIDIA products in such equipment or applications and therefore such inclusion and/or use is at customer’s own risk.NVIDIA makes no representation or warranty that products based on this document will be suitable for any specified use. Testing of all parameters of each product is not necessarily performed by NVIDIA. It is customer’s sole responsibility to evaluate and determine the applicability of any information contained in this document, ensure the product is suitable and fit for the application planned by customer, and perform the necessary testing for the application in order to avoid a default of the application or the product. Weaknesses in customer’s product designs may affect the quality and reliability of the NVIDIA product and may result in additional or different conditions and/or requirements beyond those contained in this document. NVIDIA accepts no liability related to any default, damage, costs, or problem which may be based on or attributable to: (i) the use of the NVIDIA product in any manner that is contrary to this document or (ii) customer product designs.No license, either expressed or implied, is granted under any NVIDIA patent right, copyright, or other NVIDIA intellectual property right under this document. Information published by NVIDIA regarding third-party products or services does not constitute a license from NVIDIA to use such products or services or a warranty or endorsement thereof. Use of such information may require a license from a third party under the patents or other intellectual property rights of the third party, or a license from NVIDIA under the patents or other intellectual property rights of NVIDIA.Reproduction of information in this document is permissible only if approved in advance by NVIDIA in writing, reproduced without alteration and in full compliance with all applicable export laws and regulations, and accompanied by all associated conditions, limitations, and notices.THIS DOCUMENT AND ALL NVIDIA DESIGN SPECIFICATIONS, REFERENCE BOARDS, FILES, DRAWINGS, DIAGNOSTICS, LISTS, AND OTHER DOCUMENTS (TOGETHER AND SEPARATELY, “MATERIALS”) ARE BEING PROVIDED “AS IS.” NVIDIA MAKES NO WARRANTIES, EXPRESSED, IMPLIED, STATUTORY, OR OTHERWISE WITH RESPECT TO THE MATERIALS, AND EXPRESSLY DISCLAIMS ALL IMPLIED WARRANTIES OF NONINFRINGEMENT, MERCHANTABILITY, AND FITNESS FOR A PARTICULAR PURPOSE. TO THE EXTENT NOT PROHIBITED BY LAW, IN NO EVENT WILL NVIDIA BE LIABLE FOR ANY DAMAGES, INCLUDING WITHOUT LIMITATION ANY DIRECT, INDIRECT, SPECIAL, INCIDENTAL, PUNITIVE, OR CONSEQUENTIAL DAMAGES, HOWEVER CAUSED AND REGARDLESS OF THE THEORY OF LIABILITY, ARISING OUT OF ANY USE OF THIS DOCUMENT, EVEN IF NVIDIA HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Notwithstanding any damages that customer might incur for any reason whatsoever, NVIDIA’s aggregate and cumulative liability towards customer for the products described herein shall be limited in accordance with the Terms of Sale for the product.TrademarksNVIDIA, the NVIDIA logo, and Mellanox are trademarks and/or registered trademarks of Mellanox Technologies Ltd. and/or NVIDIA Corporation in the U.S. and in other countries. The registered trademark Linux® is used pursuant to a sublicense from the Linux Foundation, the exclusive licensee of Linus Torvalds, owner of the mark on a world¬wide basis. Other company and product names may be trademarks of the respective companies with which they are associated.Copyright© 2023 NVIDIA Corporation & affiliates. All rights reserved.NVIDIA Corporation | 2788 San Tomas Expressway, Santa Clara, CA 95051。
Mellanox MLNX-OS 用户手册说明书

Mellanox MLNX-OS User Manual for VPI Rev 4.90Software Version 3.6.6000Table of ContentsDocument Revision History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22 About this Manual . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40 Chapter 1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431.1 System Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431.2 Ethernet Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 441.3 InfiniBand Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 441.4 Gateway Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45 Chapter 2 Getting Started. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 472.1 Configuring the Switch for the First Time. . . . . . . . . . . . . . . . . . . . . . . . . . 472.1.1 Configuring the Switch with ZTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 542.1.2 Rerunning the Wizard. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 552.2 Starting the Command Line (CLI). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 552.3 Starting the Web User Interface (WebUI) . . . . . . . . . . . . . . . . . . . . . . . . . 552.4 Zero-touch Provisioning. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 592.4.1 Running DHCP-ZTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 592.4.2 ZTP on Director Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 612.4.3 ZTP and MLNX-OS Software Upgrade . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 612.4.4 DHCPv4 Configuration Example. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 622.4.5 DHCPv6 Configuration Example. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 622.4.6 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 632.5 Licenses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 662.5.1 Installing MLNX-OS License (CLI) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 662.5.2 Installing MLNX-OS License (Web). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 662.5.3 Retrieving a Lost License Key. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 692.5.4 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70 Chapter 3 User Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 753.1 LED Indicators. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 753.2 Command Line Interface Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 753.2.1 CLI Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 753.2.2 Syntax Conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 763.2.3 Getting Help. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 773.2.4 Prompt and Response Conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 783.2.5 Using the “no” Form. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 783.2.6 Parameter Key. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 803.2.7 CLI Pipeline Operator Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 813.2.7.1 “include” and “exclude” CLI Filtration Options. . . . . . . . . . . . . . . . . . . . . 813.2.7.2 “watch” CLI Monitoring Option . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 823.2.7.3 “json-print” CLI Option . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 823.2.8 CLI Shortcuts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 833.3 Web Interface Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 843.3.1 Setup Menu. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 853.3.2 System Menu. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 863.3.3 Security Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 873.3.4 Ports Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 873.3.5 Status Menu. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 883.3.6 IB SM Mgmt. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 883.3.7 Fabric Inspector. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 893.3.8 ETH Mgmt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 903.3.9 IP Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 903.3.10 IB Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 913.3.11 Gateway. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 913.4 Secure Shell (SSH). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 913.4.1 Adding a Host and Providing an SSH Key. . . . . . . . . . . . . . . . . . . . . . . . . . . 913.4.2 Retrieving Return Codes when Executing Remote Commands. . . . . . . . . 923.5 Management Information Bases (MIBs). . . . . . . . . . . . . . . . . . . . . . . . . . . 923.6 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 963.6.1 CLI Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 963.6.2 Banner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1073.6.3 SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1153.6.4 Remote Login. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1323.6.5 Web Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135 Chapter 4 System Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1444.1 Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1444.1.1 Configuring Management Interfaces with Static IP Addresses. . . . . . . . 1444.1.2 Configuring IPv6 Address on the Management Interface . . . . . . . . . . . . 1444.1.3 Dynamic Host Configuration Protocol (DHCP) . . . . . . . . . . . . . . . . . . . . . 1454.1.4 Default Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1454.1.5 In-Band Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1454.1.6 Configuring Hostname via DHCP (DHCP Client Option 12) . . . . . . . . . . . 1464.1.7 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1474.1.7.1 Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1474.1.7.2 Hostname Resolution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1714.1.7.3 Routing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1784.1.7.4 Network to Media Resolution (ARP & NDP) . . . . . . . . . . . . . . . . . . . . . . 1824.1.7.5 DHCP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1884.1.7.6 General IPv6 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1904.1.7.7 IP Diagnostic Tools. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1914.2 NTP, Clock & Time Zones. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1964.2.1 NTP Authenticate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1964.2.2 NTP Authentication Key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1964.2.3 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197 4.3 Unbreakable Links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2154.3.1 Link Level Retransmission (LLR). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2154.3.2 Configuring Phy Profile & LLR. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2164.3.3 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218 4.4 Virtual Protocol Interconnect (VPI). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2244.4.1 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 226 4.5 System Profile. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2284.5.1 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229 4.6 Software Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2314.6.1 Upgrading MLNX-OS Software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2314.6.2 Upgrading MLNX-OS Software on Director Switches. . . . . . . . . . . . . . . . 2364.6.3 Upgrading MLNX-OS HA Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2374.6.4 Deleting Unused Images. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2384.6.5 Downgrading MLNX-OS Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2394.6.5.1 Downloading Image. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2394.6.5.2 Downgrading Image. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2404.6.5.3 Switching to Partition with Older Software Version. . . . . . . . . . . . . . . . 2414.6.6 Upgrading System Firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2424.6.6.1 After Updating MLNX-OS Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2424.6.6.2 After Inserting a Switch Spine or Leaf . . . . . . . . . . . . . . . . . . . . . . . . . . . 2434.6.6.3 Importing Firmware and Changing the Default Firmware. . . . . . . . . . . 2434.6.7 Image Maintenance via Mellanox ONIE . . . . . . . . . . . . . . . . . . . . . . . . . . 2444.6.8 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 247 4.7 Configuration Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2584.7.1 Saving a Configuration File. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2584.7.2 Loading a Configuration File. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2584.7.3 Restoring Factory Default Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . 2594.7.4 Managing Configuration Files. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2594.7.4.1 BIN Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2594.7.4.2 Text Configuration Files. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2604.7.5 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2624.7.5.1 File System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2624.7.5.2 Configuration Files. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271 4.8 Logging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2914.8.1 Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2914.8.2 Remote Logging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2914.8.3 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2924.9 Debugging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3194.9.1 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 320 4.10 Link Diagnostic Per Port. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3334.10.1 General . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3334.10.2 List of Possible Output Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3334.10.3 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 334 4.11 Event Notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3404.11.1 Supported Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3404.11.2 SNMP Trap Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3424.11.3 Terminal Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3434.11.4 Email Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3434.11.5 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3454.11.5.1 Email Notification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 345 4.12 Telemetry . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3644.12.1 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365 4.13 mDNS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3904.13.1 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 391 4.14 User Management and Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3924.14.1 User Accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3924.14.2 Authentication, Authorization and Accounting (AAA). . . . . . . . . . . . . . . 3924.14.2.1 User Re-authentication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3934.14.2.2 RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3934.14.2.3 TACACS+. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3934.14.2.4 LDAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3934.14.3 System Secure Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3944.14.4 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3964.14.4.1 User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3964.14.4.2 AAA Methods. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4014.14.4.3 RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4154.14.4.4 TACACS+. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4184.14.4.5 LDAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4224.14.4.6 System Secure Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 438 4.15 Cryptographic (X.509, IPSec) and Encryption. . . . . . . . . . . . . . . . . . . . . . 4404.15.1 System File Encryption. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4404.15.1.1 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 441 4.16 Scheduled Jobs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4574.16.1 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 457 4.17 Statistics and Alarms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4674.17.1 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 467 4.18 Chassis Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4874.18.1 System Health Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4874.18.1.1 Re-Notification on Errors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4874.18.1.2 System Health Monitor Alerts Scenarios. . . . . . . . . . . . . . . . . . . . . . . . . 4884.18.2 Power Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4934.18.2.1 Power Supply Options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4934.18.2.2 Width Reduction Power Saving . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4944.18.2.3 Managing Chassis Power. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4954.18.3 Monitoring Environmental Conditions. . . . . . . . . . . . . . . . . . . . . . . . . . . 4964.18.4 USB Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4984.18.5 Unit Identification LED. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4994.18.6 High Availability (HA) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4994.18.6.1 Chassis High Availability Nodes Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . 5004.18.6.2 Malfunctioned CPU Behavior . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5004.18.6.3 Box IP Centralized Location. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5014.18.6.4 System Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5014.18.6.5 Takeover Functionally. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5024.18.7 System Reboot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5034.18.7.1 Rebooting 1U Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5034.18.7.2 Rebooting Director Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5034.18.8 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5044.18.8.1 Chassis Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5044.18.8.2 Chassis High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 535 4.19 Network Management Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5404.19.1 SNMP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5404.19.1.1 Standard MIBs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5404.19.1.2 Private MIB. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5424.19.1.3 Proprietary Traps. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5424.19.1.4 Configuring SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5434.19.1.5 Configuring an SNMPv3 User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5444.19.1.6 Configuring an SNMP Notification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5444.19.1.7 SNMP SET Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5464.19.1.8 IF-MIB and Interface Information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5504.19.2 JSON API . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5514.19.2.1 Authentication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5514.19.2.2 Sending the Request . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5514.19.2.3 JSON Request Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5524.19.2.4 JSON Response Format. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5544.19.2.5 Supported Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5564.19.2.6 JSON Examples. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5574.19.2.7 JSON Request Using WebUI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5624.19.3 XML API . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5644.19.4 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5654.19.4.1 SNMP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5654.19.4.2 XML API Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5864.19.4.3 JSON API Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 588 4.20 Puppet Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5914.20.1 Setting the Puppet Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5914.20.2 Accepting the Switch Request. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5914.20.3 Installing Modules on the Puppet Server. . . . . . . . . . . . . . . . . . . . . . . . . 5924.20.4 Writing Configuration Classes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5924.20.5 Supported Configuration Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . 5954.20.5.1 Ethernet, InfiniBand, and Port-Channel Interface Capabilities . . . . . . . 5954.20.5.2 VLAN Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5954.20.5.3 Layer 2 Ethernet Interface Capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . 5954.20.5.4 LAG (Port-Channel) Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5964.20.5.5 Layer 3 Interface Capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5964.20.5.6 OSPF Interface Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5964.20.5.7 OSPF Area Capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5974.20.5.8 Router OSPF Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5974.20.5.9 Protocol LLDP, SNMP, IP Routing and Spanning Tree Capabilities . . . . 5974.20.5.10 Fetched Image Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5974.20.5.11 Installed Image Capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5984.20.6 Supported Resources for Each Type. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5984.20.7 Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5994.20.7.1 Switch and Server Clocks are not Synchronized . . . . . . . . . . . . . . . . . . . 5994.20.7.2 Outdated or Invalid SSL Certificates Either on the Switch or the Server 5994.20.7.3 Communications Issue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6004.20.8 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 601 4.21 Virtual Machine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6084.21.1 Virtual Machine Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6084.21.2 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6114.21.2.1 Config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6114.21.2.2 Show. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 626 4.22 Back-Up Battery Units . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6344.22.1 BBU Calibration Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6344.22.2 BBU Self-Test. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6354.22.3 BBU Shut-Off Timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6354.22.4 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 637 4.23 Control Plane Policing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6454.23.1 IP Table Filtering. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6454.23.1.1 Configuring IP Table Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6454.23.1.2 Modifying IP Table Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6474.23.1.3 Rate-limit Rule Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6474.23.2 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 648 4.24 Resource Scale . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6594.24.1 Ethernet Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 659。
AVVIO RAPIDO Router mobili 5G 安装指南说明书
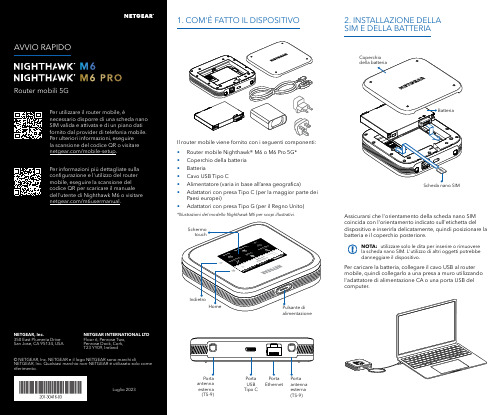
Per caricare la batteria, collegare il cavo USB al router mobile, quindi collegarlo a una presa a muro utilizzando l'adattatore di alimentazione CA o una porta USB del computer.Assicurarsi che l'orientamento della scheda nano SIM coincida con l'orientamento indicato sull'etichetta del dispositivo e inserirla delicatamente, quindi posizionare la batteria e il coperchio posteriore.NOTA: utilizzare solo le dita per inserire o rimuovere la scheda nano SIM. L'utilizzo di altri oggetti potrebbe danneggiare il dispositivo.1. COM'È FATTO IL DISPOSITIVO2. INSTALLAZIONE DELLA SIM E DELLA BATTERIAIl router mobile viene fornito con i seguenti componenti:• Router mobile Nighthawk® M6 o M6 Pro 5G*• Coperchio della batteria • Batteria• Cavo USB Tipo C• Alimentatore (varia in base all’area geografica)• Adattatori con presa Tipo C (per la maggior parte dei Paesi europei)•Adattatori con presa Tipo G (per il Regno Unito)*Illustrazioni del modello Nighthawk M6 per scopi illustrativi.antenna esterna (TS-9)antenna esterna (TS-9)USB Tipo CEthernetCONFORMITÀ NORMATIVA E NOTE LEGALIPer informazioni sulla conformità alle normative, compresala Dichiarazione di conformità UE, visitare il sito Web https:///it/about/regulatory/.Prima di collegare l'alimentazione, consultare il documento relativo alla conformità normativa.Può essere applicato solo ai dispositivi da 6 GHz: utilizzare il dispositivo solo in un ambiente al chiuso. L'utilizzo di dispositivi a 6 GHz è vietato su piattaforme petrolifere, automobili, treni, barche e aerei, tuttavia il suo utilizzo è consentito su aerei di grandi dimensioni quando volano sopra i 3000 metri di altezza. L'utilizzo di trasmettitori nella banda 5.925‑7.125 GHz è vietato per il controllo o le comunicazioni con sistemi aerei senza equipaggio.SUPPORTO E COMMUNITYDalla pagina del portale di amministrazione Web, fare clic sull'icona con i tre puntini nell'angolo in alto a destra per accedere ai file della guida e del supporto.Per ulteriori informazioni, visitare il sito netgear.it/support per accedere al manuale dell'utente completo e per scaricare gli aggiornamenti del firmware.È possibile trovare utili consigli anche nella Community NETGEAR, alla pagina /it.GESTIONE DELLE IMPOSTAZIONI TRAMITE L'APP NETGEAR MOBILEUtilizzare l'app NETGEAR Mobile per modificare il nome della rete Wi-Fi e la password. È possibile utilizzarla anche per riprodurre e condividere contenutimultimediali e accedere alle funzioni avanzate del router mobile.1. Accertarsi che il dispositivo mobile sia connesso a Internet.2. Eseguire la scansione del codice QR per scaricare l'appNETGEAR Mobile.Connessione con il nome e la password della rete Wi-Fi 1. Aprire il programma di gestione della rete Wi‑Fi deldispositivo.2. Individuare il nome della rete Wi‑Fi del router mobile(NTGR_XXXX) e stabilire una connessione.3. Only Connessione tramite EthernetPer prolungare la durata della batteria, l'opzione Ethernet è disattivata per impostazione predefinita. Per attivarla, toccare Power Manager (Risparmio energia) e passare a Performance Mode (Modalità performance).4. CONNESSIONE A INTERNETÈ possibile connettersi a Internet utilizzando il codice QR del router mobile da uno smartphone oppure selezionando manualmente il nome della rete Wi‑Fi del router e immettendo la password.Connessione tramite codice QR da uno smartphone 1. Toccare l'icona del codice QR sulla schermata inizialedello schermo LCD del router mobile.NOTA: quando è inattivo, lo schermo touch si oscura per risparmiare energia. Premere brevemente e rilasciare il pulsante di alimentazione per riattivare lo schermo.3. CONFIGURAZIONE DEL ROUTER MOBILETenere premuto il pulsante di accensione per due secondi, quindi seguire le istruzioni visualizzate sullo schermo per impostare un nome per la rete Wi‑Fi e una password univoci.La personalizzazione delle impostazioni Wi‑Fi consente di proteggere la rete Wi‑Fi del router mobile.Impostazioni APNIl router mobile legge i dati dalla scheda SIM e determina automaticamente le impostazioni APN (Access Point Name) corrette con i piani dati della maggior parte degli operatori. Tuttavia, se si utilizza un router mobile sbloccato con un operatore o un piano meno comune, potrebbe essere necessario immettere manualmente le impostazioni APN.Se viene visualizzata la schermata APN Setup Required (Configurazione APN richiesta), i dati APN dell’operatore non sono presenti nel nostro database ed è necessario inserirli manualmente. Immettere i valori fornitidall’operatore nei campi corrispondenti, quindi toccare Save (Salva) per completare la configurazione.NOTA: l’operatore determina le proprie informazioni APN e deve fornire le informazioni per il proprio piano dati. Si consiglia di contattare il proprio operatore per le impostazioni APN corrette e di utilizzare solo l’APN suggerito per il piano specifico.Schermata inizialeAl termine della configurazione, il router visualizza la schermata iniziale:Wi‑FiPotenza Carica Rete Codice QR connessione rapida Wi‑FiNome e Wi‑FiIcona del codice QR。
基于MLWE和MSIS的可验证解密方案

mlwe算法实现流程
密钥生成
首先生成密钥,用于控制加密和解密过程。
01
加密过程
使用密钥对明文进行加密,生成密文 。
02
03
解密过程
使用密钥对密文进行解密,恢复明文 。
mlwe算法优缺点
• 优点 • 安全性高:基于格的密码学提供了较高的安全性,能够抵抗现有的密码攻击。 • 效率高:mlwe算法的加密和解密效率较高,适合于实际应用。 • 缺点 • 密钥管理困难:由于基于格的密码学较为复杂,密钥生成和管理较为困难。 • 对硬件要求高:mlwe算法需要较高的计算能力和硬件支持,对于一些低性能设备可能不适用。 • 需要数学基础知识:使用mlwe算法需要进行一定的数学基础知识储备,对于非专业人士可能存在一定的学
窃取数据。
效率
03
由于采用了高效的加密和解密算法,使得方案的运行效率较高
。
05
基于mlwe和msis的可验 证解密方案实现与测试
方案实现流程
密钥生成
使用安全的密钥生成方法,如 PBKDF2、scrypt等生成密钥 。
发送密文
将密文发送给接收者。
选择适当的加密算法
选择适合应用场景的加密算法 ,如AES、RSA等。
优点
msis算法具有较高的安全性,能够抵抗各种类型的攻击;同时,msis算法也 具有较高的效率,能够快速地进行加密和解密操作。
缺点
msis算法需要较大的计算量和存储空间,这可能会使得在一些资源受限的环 境下无法使用;另外,msis算法也存在着一些数学上的攻击风险。
04
基于mlwe和msis的可验 证解密方案设计
解密算法设计
根据加密算法的设计思路,构建一个可验证的 解密算法。
各国手机格式-外贸必备

Botswana Brazil British Indian Ocean Territory British Virgin Islands Brunei
ห้องสมุดไป่ตู้
+1
246
25 29 1 29 2 29 3 29 4 29 5 +375 29 6 29 7 29 8 29 9
10 10
?
? Orange ? VivaCell-MTS
? ArmenTel
? VivaCell-MTS ? VivaCell-MTS ? VivaCell-MTS ? Orange ? Karabakh Telecom ? VivaCell-MTS ? ArmenTel ? ?
9 any
? 10 T-Mobile Austria GmbH (telering) 10 Hutchison 3G Austria GmbH (drei) 10 mobilkom Austria AG (Mobilkom, A1)
Austria
Azerbaijan Bahamas
+374
+297 +247
+61 +672
+43
+994 +1
55 77
91
92 93 94 95 97 98 99 ?? ??
4
1x 650 660 664
676
680 681 688
699
40 50 51 55 70 77 242 35x 242 45x 242 55x 31 322 33 340 341
Yesss) ? Catel ? Azercell ? Azercell ? Bakcell ? Nar Mobile ? Azerfon-Vodafone 10 10 10 8 Royal Court 8 Batelco 8 Viva 8 Viva 8 Viva
YAMAHA MOTIF XS6 XS7 XS8 说明书

NAME PLATE LOCATION: The graphic below indicates the location of the name plate. The model number, serial number, power requirements, etc., are located on this plate. You should record the model number, serial number, and the date of purchase in the spaces provided below and retain this manual as a permanent record of your purchase.
Warning: Do not attempt to recharge, disassemble, or incinerate this type of battery. Keep all batteries away from children. Dispose of used batteries promptly and as regulated by applicable laws. Note: In some areas, the servicer is required by law to return the defective parts. However, you do have the option of having the servicer dispose of these parts for you.
The above warning is located on the rear of the unit.
Explanation of Graphical Symbols
Mellanox MLNX-OS 发行说明书:IBM SX90Y3452 软件版本 3.4.0000

Mellanox MLNX-OS® Release Notes for IBM SX90Y3452Software Ver. 3.4.0000Table of ContentsChapter 1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4 Chapter 2 Supported Platforms, Firmware, Cables and Licenses . . . . . . . . . . . . . . . . . 42.1 Supported Switch Systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42.2 Supported CPU Architecture. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42.3 Supported Firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42.4 Supported Mezzanine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42.5 Supported CPLD Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42.6 Supported Software Licenses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52.7 Upgrade From Previous Releases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52.8 Supported Cables. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5 Chapter 3 Changes and New Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Chapter 4 Known Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94.1 General Known Issues. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94.2 InfiniBand Known Issues. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 Chapter 5 Bug Fixes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13 Chapter 6 Submitting a Service Request. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131IntroductionThis document is the Mellanox MLNX-OS® Release Notes for IBM SX90Y3452.MLNX-OS is a comprehensive management software solution that provides optimal perfor-mance for cluster computing, enterprise data centers, and cloud computing over MellanoxSwitchX® family. The fabric management capabilities ensure the highest fabric performancewhile the chassis management ensures the longest switch up time.The MLNX-OS documentation package includes the following documents:•User Manual – provides general information about the scope, organization and com-mand line interface of MLNX-OS as well as basic configuration examples•Release Notes – provides information on the supported platforms, changes and new fea-tures, and reports on software known issues as well as bug fixes2Supported Platforms, Firmware, Cables and Licenses 2.1Supported Switch SystemsTable 1 - Supported Switch Systems2.2Supported CPU Architecture•PPC 460 CPU families2.3Supported Firmware•SwitchX® firmware version 9.2.9190•SwitchX-2 firmware version 9.2.9190•ConnectX®-2 firmware version 2.9.1200 and higher•ConnectX-3 firmware version 2.30.8000 and higher2.4Supported Mezzanine•ConnectX-2, Mezzanine P/N 90Y3460 (MalayaP), 2.9.1316 and higher•ConnectX-2, Mezzanine P/N 90Y3480 (MalayaP-Net), 2.9.1318 and higher•ConnectX-3, Mezzanine P/N 90Y3488 (Merlin), 2.32.5100 and higher•ConnectX-3, Mezzanine P/N 90Y3484 (Nevada), 2.32.5100 and higher•ConnectX-3, Mezzanine P/N 90Y3456 (MalayaX), 2.32.5100 and higher•ConnectX-3, Mezzanine P/N 90Y3468 (MalayaX-Net), 2.32.5100 and higher2.5Supported CPLD Version• 1.0.182.6Supported Software LicensesFor the software licenses supported with MLNX-OS® software please refer to the “Licenses” section of the “Getting Started” chapter of the Mellanox MLNX-OS User Manual .2.7Upgrade From Previous ReleasesOlder versions of MLNX-OS may require upgrading to one or more intermediate versions prior to upgrading to the latest. Missing an intermediate step may lead to errors. Please refer to Table 2to identify the correct upgrade order.Table 2 - Supported Software Upgrades for SX90Y3452For upgrade instructions refer to the section “Upgrading MLNX-OS Software” in Mellanox MLNX-OS User Manual .2.8Supported CablesFor a list of the Mellanox supported cables please visit the LinkX™ Cables and Transceivers page of the Mellanox Website at /page/cables?mtag=cable_overview.When using Mellanox AOC cables longer than 50m use one VL to achieve full wirespeed.3Changes and New Features Table 3 - IBM SX90Y3452 Changes and New Features4Known IssuesThe following table describes MLNX-OS® known issues in this software release and possible workarounds.4.1General Known IssuesTable 4 - General Known Issues (Sheet 1 of 4)Table 4 - General Known Issues (Sheet 2 of 4)4.2InfiniBand Known IssuesTable 5 - InfiniBand Known Issues5Bug FixesThe following table describes MLNX-OS® bug fixes in this software release.Table 6 - Bug Fixes6Submitting a Service RequestThe Mellanox® Support Center is at your service for any issues. You may access the Warranty Service through the Web Request Form by using the following link:/content/pages.php?pg=support_index.。
Stochastic Gradient VB and the VariationalAuto-Encoder

arXiv:1312.6114v10 [stat.ML] 1 May 2014
Diederik P. Kingma Machine Learning Group Universiteit van Amsterdam dpkingma@
straightforward to extend this scenario to the case where we also perform variational inference on the global parameters; that algorithm is put in the appendix, but experiments with that case are left to future work. Note that our method can be applied to online, non-stationary settings, e.g. streaming data, but here we assume a fixed dataset for simplicity. 2.1 Problem scesome dataset X = {x(i) }N i=1 consisting of N i.i.d. samples of some continuous or discrete variable x. We assume that the data are generated by some random process, involving an unobserved continuous random variable z. The process consists of two steps: (1) a value z(i) is generated from some prior distribution pθ∗ (z); (2) a value x(i) is generated from some conditional distribution pθ∗ (x|z). We assume that the prior pθ∗ (z) and likelihood pθ∗ (x|z) come from parametric families of distributions pθ (z) and pθ (x|z), and that their PDFs are differentiable almost everywhere w.r.t. both θ and z. Unfortunately, a lot of this process is hidden from our view: the true parameters θ ∗ as well as the values of the latent variables z(i) are unknown to us. Very importantly, we do not make the common simplifying assumptions about the marginal or posterior probabilities. Conversely, we are here interested in a general algorithm that even works efficiently in the case of: 1. Intractability: the case where the integral of the marginal likelihood pθ (x) = pθ (z)pθ (x|z) dz is intractable (so we cannot evaluate or differentiate the marginal likelihood), where the true posterior density pθ (z|x) = pθ (x|z)pθ (z)/pθ (x) is intractable (so the EM algorithm cannot be used), and where the required integrals for any reasonable mean-field VB algorithm are also intractable. These intractabilities are quite common and appear in cases of moderately complicated likelihood functions pθ (x|z), e.g. a neural network with a nonlinear hidden layer. 2. A large dataset: we have so much data that batch optimization is too costly; we would like to make parameter updates using small minibatches or even single datapoints. Samplingbased solutions, e.g. Monte Carlo EM, would in general be too slow, since it involves a typically expensive sampling loop per datapoint. We are interested in, and propose a solution to, three related problems in the above scenario: 1. Efficient approximate ML or MAP estimation for the parameters θ . The parameters can be of interest themselves, e.g. if we are analyzing some natural process. They also allow us to mimic the hidden random process and generate artificial data that resembles the real data. 2. Efficient approximate posterior inference of the latent variable z given an observed value x for a choice of parameters θ . This is useful for coding or data representation tasks. 3. Efficient approximate marginal inference of the variable x. This allows us to perform all kinds of inference tasks where a prior over x is required. Common applications in computer vision include image denoising, inpainting and super-resolution. 2
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
第9章遗传算法遗传算法提供了一种大致基于模拟进化的学习方法。
其中的假设常被描述为二进制位串,位串的含义依赖于具体的应用。
然而,假设也可以被描述为符号表达式或者甚至是计算机程序。
对合适假设的搜索是从若干初始假设的群体(population)或汇集(collection)开始的。
当前群体的成员通过模仿生物进化的方式来产生下一代群体,比如说随机变异(mutation)和交叉(crossover)。
在每一步,根据给定的适应度(fitness)度量评估当前群体中的假设,而后使用概率方法选出适应度最高的假设作为产生下一代的种子。
遗传算法已被成功地应用到多种学习任务和最优化问题中。
例如,遗传算法已被用于学习机器人控制的规则集,以及优化人工神经网络的拓扑结构和学习参数。
这一章既覆盖了用位串描述假设的遗传算法(genetic algorithms),也覆盖了用计算机程序描述假设的遗传编程(genetic programming)。
9.1 动机遗传算法(GA)提供了一种受生物进化启发的学习方法。
它不再是从一般到特殊或从简单到复杂地搜索假设,而是通过变异和重组当前已知的最好假设来生成后续的假设。
在每一步,被称为当前群体(population)的一组假设被更新,方法是通过使用目前适应度最高的假设的后代替代群体的某个部分。
这个过程形成了对假设的生成并测试(generate-and-test)柱状搜索(beam-search),其中若干个最佳当前假设的变体最有可能在下一步被考虑。
GA 的普及和发展得益于以下因素:∙在生物系统中进化被认为是一种成功的自适应方法,并且具有很好的鲁棒性。
∙GA搜索的假设空间中,假设的各个部分相互作用,每一部分对总的假设适应度的影响难以建模。
∙遗传算法易于并行化,且可降低由于使用超强计算机硬件的带来的昂贵费用。
这一章描述了遗传算法,举例演示了它的用法,并分析了它搜索的假设空间的特性。
我们也描述了它的一个变体,称为遗传编程,在这种方法中,整个计算机程序向着某个适应度准则进化。
遗传算法和遗传编程是进化计算(evolutionary computation)领域的中的两种流行方法。
在本章的最后一节我们将接触一些研究生物进化的课题,包括鲍德温效应(Baldwin effect),它描述了个体的学习能力与整个群体进化速度之间有趣的相互作用。
9.2 遗传算法GA研究的问题是搜索一个候选假设的空间,以确定最佳的假设。
在GA中,“最佳假设”被定义为是使“适应度(fitness)”最优的假设,适应度是为当前问题预先定义的数字度量。
例如,如果学习任务是在给定一个未知函数的输入输出训练样例后逼近这个函数,那么适应度可被定义为假设在训练数据上的精度。
如果任务是学习下国际象棋的策略,那么适应度可被定义为该个体在当前群体中与其他个体对弈的胜率。
尽管遗传算法的不同实现在细节上有所不同,但它们都具有以下的共同结构:算法迭代更新一个假设池,这个假设池称为群体。
在每一次迭代中,根据适应度函数评估群体中的所有成员。
然后从当前群体中用概率方法选取适应度最高的个体产生新的一代。
在这些被选中的个体中,一部分保持原样地进入下一代群体,其他的被用作产生后代个体的基础,其中应用象交叉和变异这样的遗传方法。
表9-1描述了一个遗传算法原型。
算法的输入包括:用来排序候选假设的适应度函数;定义算法终止时适应度的阈值;要维持的群体大小;和决定如何产生后继群体的参数:每一代群体中被淘汰的比例和变异率。
表9-1 遗传算法原型算法中维持一个包含p 个假设的群体。
在每一次迭代中,后继群体P S 的形成通过两种途径:根据假设的适应度用概率方法选择个体,以及加入新假设。
新假设通过两种方法得到:对最高适应度假设对应用交叉算子;对通过选择和交叉产生的新一代群体中的部分假设进行单点变异。
重复这个迭代过程,直到发现适应度足够好的假设。
典型的交叉和变异算子定义在后面的表格中。
GA(Fitness , Fitness _threshold , p , r , m )Fitness :适应度评分函数,为给定假设赋予一个评估得分。
Fitness _threshold :指定终止判据的阈值。
p :群体中包含的假设数量。
r :每一步中通过交叉取代群体成员的比例。
m :变异率。
∙ 初始化群体:P ←随机产生的p 个假设∙ 评估:对于P 中的每一个h ,计算Fitness (h )∙ 当[hmax Fitness (h )]<Fitness _threshold ,做: 产生新的一代P S :1. 选择:用概率方法选择P 的(1-r )p 个成员加入P S 。
从P 中选择假设h i 的概率Pr(h i )通过下面公式计算: ∑==p j j i i h Fitness h Fitness h 1)()()Pr( 2. 交叉:根据上面给出的Pr(h i ),从P 中按概率选择r ⋅p /2对假设。
对于每一对假设<h 1, h 2>应用交叉算子产生两个后代。
把所有的后代加入P S 。
3. 变异:使用均匀的概率从P S 中选择m 百分比的成员。
对于选出的每个成员,在它的表示中随机选择一个位取反。
4. 更新:P ←P S 。
5. 评估:对于P 中的每一个h 计算Fitness (h )∙ 从P 中返回适应度最高的假设。
在这个算法的每一次迭代中,基于当前的群体产生新一代的假设。
首先,从当前的群体中选择一定数量的假设包含在下一代中。
这些假设是用概率方法选择的,其中选择假设h i的概率是通过下式计算的: ∑==pj j i i h Fitness h Fitness h 1)()()Pr( (9.1) 因此,一个假设被选择的概率与它自己的适应度成正比,并且与当前群体中其他竞争假设的适应度成反比。
在当前代的这些成员已被选入下一代群体后,再使用一种交叉操作产生其他的成员。
交叉操作将在下一节被具体定义,它从当前代中取两个双亲假设,并通过重新组合双亲的各部分产生两个后代假设。
双亲假设是从当前群体中按概率选出的,也使用公式(9.1)的概率函数。
在通过这种交叉操作产生新的成员后,新一代群体已经包含了所需数量的成员。
接下来,从这些成员中随机选出一定比例(m ),并进行随机变异。
因此,这种GA 算法执行一种随机的、并行柱状假设搜索,根据适应度函数发现较好的假设。
在下面的小节中我们将更详尽地描述这个算法中使用的假设表示和遗传算子。
9.2.1 表示假设GA 中假设经常被表示为二进制位串,这样可以很方便地用变异和交叉遗传算子来操作。
使用这样的位串表示的假设可能非常复杂。
例如,if-then 规则就可以很容易地用这种方式表示,做法是选择规则的一种编码,其中为每个规则的前件和后件分配特定的子串。
Holland (1986);Grefenstette (1988);DeJong et al.(1993)中描述了GA 系统中这种规则表示的例子。
为了说明如何把if-then 规则编码成位串,首先考虑怎样使用位串描述单个属性的值约束。
例如考虑属性Outlook ,它的值可以取以下3个值中的任一个:Sunny ,Overcast 或Rain 。
表示Outlook 约束的一个明显的方法是,使用一个长度为3的位串,每位对应一个可能值。
若某位为1表示这个属性可以取对应的值。
例如,串010表示Outlook 必须取第二个值的约束,或者说Outlook =Overcast 。
类似的,串011表示更一般的约束,Outlook 可以取两个可能值,或者说(Outlook =Overcast ∨Rain )。
注意111表示最一般的约束,表明我们不关心这个属性取哪个值。
有了表示单个属性约束的方法,那么对多个属性约束的合取可以很容易地表示为对应位串的连接。
例如,考虑第二个属性Wind ,它可以取两个值Strong 或Weak 。
那么像下面的规则前件:(Outlook =Overcast ∨Rain )∧(Wind =Strong )可被表示为长度为5的位串:Outlook Wind 011 10规则的后件(例如PlayTennis =yes )可以用相似的方式表示。
于是,整个规则表示可以通过把描述规则前件和后件的位串连接起来。
例如,下面的规则IF Wind=Strong THEN PlayTennis=yes将被表示为以下的位串:Outlook Wind PlayTennis111 10 10其中,前三位描述了对Outlook的“不关心(don’t care)”约束,接下来两位描述了对Wind的约束,最后两位描述了规则的后件(这里假定PlayTennis可以取两个值Yes或No)。
注意,表示规则的位串对假设空间中的每个属性有一个子串,即使该属性不被规则的前件所约束。
这样得到了一个固定长度的规则位串表示,其中在特定位置的子串描述对特定属性的约束。
有了单个规则的表示方法,我们可以简单地把单个规则的位串表示连接起来,从而表示规则集。
在为某个假设空间设计位串编码时,有必要让每个句法合法的位串表示一个有意义的假设。
比如,若使用上一段的规则编码方式,那么位串111 10 11表示了一个规则,它的后件不约束目标属性PlayTennis。
如果要避免考虑这个假设,可以采用不同的编码方式(例如,仅分配一个位给后件PlayTennis,表示它的值是Yes或No);或改变遗传算子以明确避免建立这样的位串;或干脆把很低的适应度赋给这样的串。
在一些GA中,假设是用符号描述来表示的,而不是用位串。
例如,在9.5节中,我们讨论了一个把假设编码为计算机程序的遗传算法。
9.2.2 遗传算子在GA中通过一系列算子(operators)来决定后代,算子对当前群体中选定的成员进行重组和变异。
表9-1中列出了用来操作位串的典型GA算子。
这些算子是生物进化中的遗传过程的理想化形式。
最常见的两个算子是交叉(crossover)和变异(mutation)。
交叉算子从两个双亲串中通过复制选定位产生两个新的后代。
每个后代的第i位是从它的某个双亲的第i位复制来的。
至于双亲中的哪一个在第i位起作用,这是由另外一个称为交叉掩码(crossover mask)的位串决定的。
下面演示一下这个过程,考虑表9-2中最上边的单点(single-point)交叉算子。
先考虑其中上面一个后代。
这个后代从第一个双亲中取前5位,其余的6位来自第二个双亲,因为交叉掩码11111000000为每个位指定这些选择。
第二个后代使用同样的交叉掩码,但交换了双亲的角色。
所以,它包含了第一个后代没有用过的位。
在单点交叉中,交叉掩码总是这样组成的,它以连续的n个1开始,后面跟随必要个数的0直至结束。
