UMAC Fast and Secure Message Authentication
华三路由器软件升级指南

蜂鸟 M 芯片方案常见语音性能问题优化指导手册说明书
V1-0
制订: 审核: 批准:
项目组成员
日期: 日期: 日期:
2021-01-18
*The information contained in this message is confidential and should not be disclosed to any third party whether or not you are the intended addressee indicated in the message.
(3) 为什么『挑战式地』尝试误识别是不科学的? • 『挑战式地』尝试误唤醒的例子:唤醒词是:『你好魔方』,测试人员尝试『你好魔法』
(4) 关于误识别的结论; • 对于语音识别而言,识别率永远不可能为 100%,而误识别率永远不可能为 0% • 挑战式地尝试误识别是不科学的,对业界所有技术提供方这都是一个尚未解决的挑战
保密声明
本文档(包括任何附件)包含的信息是保密信息。接收人了解其获得的本文档是保密的,除用于规定的目的外 不得用于任何目的,也不得将本文档泄露给任何第三方。
本软件产品受最终用户许可协议(EULA)中所述条款和条件的约束,该协议位于产品文档和/或软件产品的联 机文档中,使用本产品,表明您已阅读并接受了 EULA 的条款。
不作保证声明
云知声智能科技股份有限公司不对此文档中的任何内容作任何明示或暗示的陈述或保证,而且不对特定目的的 适销性及适用性或者任何间接、特殊或连带的损失承担任何责任。本手册内容若有变动,恕不另行通知。本手册例 子中所用的公司、人名和数据若非特别声明,均属虚构。未得到云知声智能科技股份有限公司明确的书面许可,不 得为任何目的、以任何形式或手段(电子的或机械的)复制或传播手册的任何部分。
消息鉴别码(MAC)相关国际标准介绍
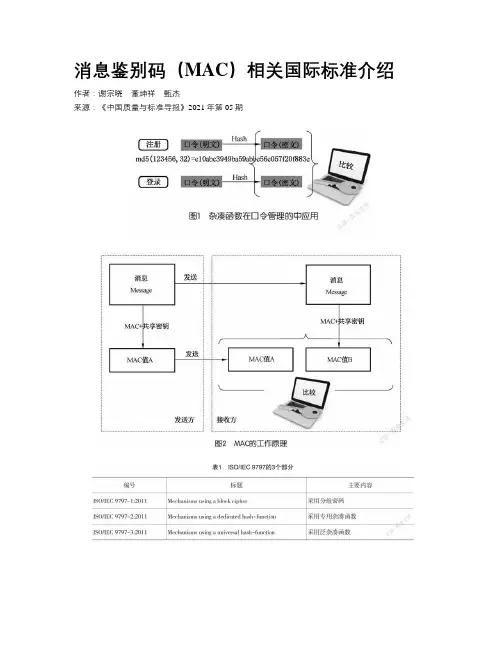
消息鉴别码(MAC)相关国际标准介绍作者:谢宗晓董坤祥甄杰来源:《中国质量与标准导报》2021年第05期1 消息鉴别码消息鉴别码(Message Authentication Code,MAC)是一种确认完整性的技术。
MAC的输入,包括任意长度的消息和一个发行者和接收者的共享密钥。
MAC的输出,则是固定长度的字符串,这个数据串称为MAC值。
显然,输入和输出的方式,与杂凑函数很类似,但是,杂凑函数不需要密钥。
换句话说,MAC可以认为是与密钥相关的杂凑函数。
杂凑函数的最典型应用,例如存储用户口令,利用MD5 算法实现的口令的比对过程见图1。
类似于口令比对的方式,也可以检测消息传输过程中是否被篡改过,也就是说可以保证消息的“完整性”。
但是有时候我们需要确认消息是谁发送的,或者说需要对消息进行鉴别(authentication),不仅仅是判断完整性,这时候就需要MAC。
此时,共享密钥的作用就显现出来了。
例如,在银行转账业务中,收到的汇款请求指令,不仅要确保消息在传输过程中未被篡改,还要确保消息不是伪造的。
这正是MAC能够解决的问题,固定长度的字符串(类似于杂凑值)可以保证消息的完整性,共享的密钥可以实现一定程度的用户鉴别,即消息确实来自正确的发送者。
其工作原理见图2。
但是,从上述机制中也可以看到MAC本身是无法抗抵赖的,因为密钥是发送方和接收方共享的,实际上,抗抵赖性的实现一般要用数字签名技术[1]。
MAC还存在一个问题,就是密钥如何共享,这与对称密码算法的密钥分发问题是一致的。
2 MAC的实现MAC是一种机制,而不是某个单独的函数。
事实上,实现MAC的途径有很多,一般在实际应用中,主要是通过杂凑函数和分组密码,也可以通过序列密码和公钥密码等。
通过杂凑函数或分组密码实现MAC,是最常见的方式,对应的就是ISO/IEC 9797的3个部分,ISO/IEC 9797 总标题为:消息鉴别码(Message Authentication Codes,MACs),基本情况见表1。
莫加 UC 系列产品说明书
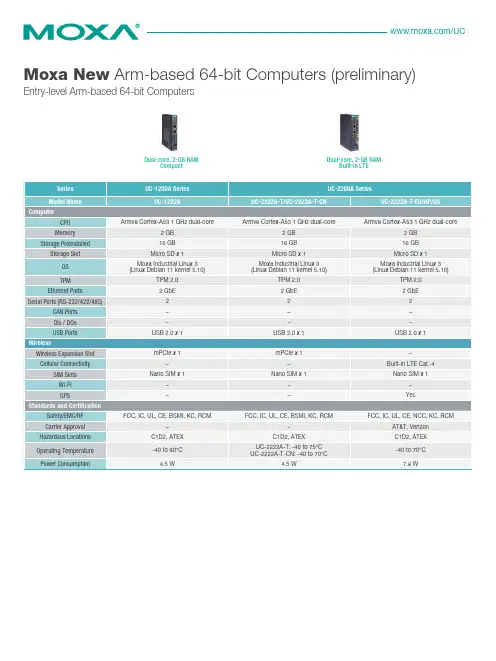
Entry-level Arm-based 64-bit ComputersDual-core, 2-GB RAMCompact Dual-core, 2-GB RAM Built-in LTEValue-added Arm-based 64-bit ComputersQuad-core, 4-GB RAMQuad-core, 4-GB RAM5G/CAN/serial IsolationBuilt-in LTEMoxa Industrial LinuxMoxa's Debian-based industrial-grade stable Linux distribution for long-term projectsFeatures and Benefits5Debian-based distribution that can use all standard Debian packages5Developed as per IEC 62443-4-1 and compliant with IEC 62443-4-2 industrialcybersecurity standards (Moxa Industrial Linux 3 Secure)5Long-term support until 2027 for Moxa Industrial Linux 1 and 2031 for MoxaIndustrial Linux 35Wireless connection management utility with automatic network keep alive andfailover5Ready-to-use APIs and library to ease access to hardware and I/O interfaces5Crash-free robust file system5Over-the air (OTA) software updatesWireless-ready Arm-based 32-bit Computers Built-in cellular or Wi-Fi module, RF type approvals, and carrier approvalsBuilt-in LTE Cat.1Built-in LTECat.1 and Wi-FiBuilt-in LTECat.1 and Wi-FiBuilt-in LTECat.4 with Wi-Fi expansion1. Wireless module is built-in. Refer to the Wireless Connection and Expansion Modules section for details.2. Wireless module must be purchased separately. Refer to the Wireless Connection and Expansion Modules section for details.1 mPCIe for cellular/Wi-Fi1 mPCIe forcellular/Wi-Fi1 mPCIe forcellular/Wi-Fi1 mPCIe forcellular/Wi-Fi1 mPCIe for cellular 1mPCIe for Wi-Fi1 mPCIe forcellular/Wi-FiArm-based 32-bit Computers With Wireless Options Flexibility to add cellular or Wi-Fi capability when needed1. Wireless module must be purchased separately. Refer to the Wireless Connection and Expansion Modules section for details.1 LAN,1 serial2 LAN 2 LAN,2 serial2 LAN,2 serial2 LAN,4 serial2 LAN,4 serial2 LAN,1 serial2 LAN,2 serial3 LAN,8 serialStandard Arm-based 32-bit Computers Low power consumption and small form factorWireless Connectivity and Expansion Modules* Details of cellular and Wi-Fi support with a list of wireless accessory models* Antennas must be purchased separatelyLast updated: Aug. 15, 2023. All specifications are subject to change without notice.。
AOC-S25G-b2S User's Guide

User's GuideRevision 1.0aAOC-S25G-b2SUser's Guide Revision 1.0aRelease Date: December 20, 2017Unless you request and receive written permission from Super Micro Computer, Inc., you may not copy any part of this document.Information in this document is subject to change without notice. Other products and companies referred to herein are trademarks or registered trademarks of their respective companies or mark holders.Copyright © 2016 by Super Micro Computer, Inc.All rights reserved. Printed in the United States of AmericaThe information in this User's Guide has been carefully reviewed and is believed to be accurate. The vendor assumes no responsibility for any inaccuracies that may be contained in this document, and makes no commitment to update or to keep current the information in this user's guide, or to notify any person or organization of the updates. Please Note: For the most up-to-date version of this user's guide, please see our Website at .Super Micro Computer, Inc. ("Supermicro") reserves the right to make changes to the product described in this user's guide at any time and without notice. This product, including software and documentation, is the property of Supermicro and/or its licensors, and is supplied only under a license. Any use or reproduction of this product is not allowed, except as expressly permitted by the terms of said license.IN NO EVENT WILL SUPER MICRO COMPUTER, INC. BE LIABLE FOR DIRECT, INDIRECT, SPECIAL, INCIDENTAL, SPECULATIVE OR CONSEQUENTIAL DAMAGES ARISING FROM THE USE OR INABILITY TO USE THIS PRODUCT OR DOCUMENTATION, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. IN PARTICULAR, SUPER MICRO COMPUTER, INC. SHALL NOT HAVE LIABILITY FOR ANY HARDWARE, SOFTWARE, OR DATA STORED OR USED WITH THE PRODUCT, INCLUDING THE COSTS OF REPAIRING, REPLACING, INTEGRATING, INSTALLING OR RECOVERING SUCH HARDWARE, SOFTWARE, OR DATA.Any disputes arising between the manufacturer and the customer shall be governed by the laws of Santa Clara County in the State of California, USA. The State of California, County of Santa Clara shall be the exclusive venue for the resolution of any such disputes. Supermicro's total liability for all claims will not exceed the price paid for the hardware product.FCC Statement: This equipment has been tested and found to comply with the limits for a ClassA digital device pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the manufacturer’s instruction manual, may cause harmful interference with radio communications. Operation of this equipment in a residential area is likely to cause harmful interference, in which case you will be required to correct the interference at your own expense.California Best Management Practices Regulations for Perchlorate Materials: This Perchlorate warning applies only to products containing CR (Manganese Dioxide) Lithium coin cells. “Perchlorate Material-special handling may apply. See /hazardouswaste/perchlorate”.WARNING: Handling of lead solder materials used in this product may expose you to lead, a chemical known to the State of California to cause birth defects and other reproductive harm.PrefaceAbout this User's GuideThis user's guide is written for system integrators, IT professionals, and knowledgeable end users. It provides information for the installation and use of the AOC-S25G-b2S add-on card.An Important Note to the UserAll graphic images and layout drawings shown in this user's guide are based upon the latest PCB revision available at the time of publishing of this user's guide. The add-on card you have received may or may not look exactly the same as the graph-ics shown in this user's guide.Returning Merchandise for ServiceA receipt or copy of your invoice marked with the date of purchase is required be-fore any warranty service will be rendered. You can obtain service by calling your vendor for a Returned Merchandise Authorization (RMA) number. When returning to the manufacturer, the RMA number should be prominently displayed on the outside of the shipping carton and mailed prepaid or hand-carried. Shipping and handling charges will be applied for all orders that must be mailed when service is complete.For faster service, RMA authorizations may be requested online (/support/rma/).This warranty only covers normal consumer use and does not cover damages in-curred in shipping or from failure due to the alteration, misuse, abuse or improper maintenance of products.During the warranty period, contact your distributor first for any product problems. Conventions Used in the User's GuidePay special attention to the following symbols for proper system installation:Warning: Important information given to ensure proper system installation and to avoid possible damage done to the components or injury to yourself.Note: Additional information given for proper system setup. PrefaceAOC-S25G-b2S Add-On Card User's GuideImportant LinksFor your system to work properly, please follow the links below to download all necessary drivers/utilities and the user’s manual for your server.• Supermicro product manuals: /support/manuals/• Product drivers and utilities: ftp://• Product safety info: /about/policies/safety_informa-tion.cfm• If you have any questions, please contact our support team at: support@ T his manual may be periodically updated without notice. Please check the Supermicro website for possible updates to the manual revision level.Preface Contacting SupermicroHeadquartersAddress:Super Micro Computer, Inc.980 Rock Ave.San Jose, CA 95131 U.S.A.Tel:+1 (408) 503-8000Fax:+1 (408) 503-8008Email:************************(GeneralInformation)**********************(TechnicalSupport)Web Site:EuropeAddress:Super Micro Computer B.V.Het Sterrenbeeld 28, 5215 ML's-Hertogenbosch, The NetherlandsTel:+31 (0) 73-6400390Fax:+31 (0) 73-6416525Email:*******************(GeneralInformation)*********************(TechnicalSupport)*****************(CustomerSupport)Web Site:www.supermicro.nlAsia-PacificAddress:Super Micro Computer, Inc.3F, No. 150, Jian 1st Rd.Zhonghe Dist., New Taipei City 235Taiwan (R.O.C)Tel:+886-(2) 8226-3990Fax:+886-(2) 8226-3992Email:**********************.twWeb Site:AOC-S25G-b2S Add-On Card User's GuideTable of ContentsPrefaceChapter 1 Introduction1-1 Overview .........................................................................................................1-1 1-2 About this Add-on Card ...................................................................................1-1 1-3 Key Features ...................................................................................................1-1 1-4 Supermicro Motherboard Support ...................................................................1-2 Chapter 2 Hardware Components2-1 Add-On Card Image and Layout .....................................................................2-1 2-2 Major Onboard Components ...........................................................................2-1 2-3 SFP28 Ethernet Connections..........................................................................2-2 SFP28 (LAN1/LAN2) Connectors...............................................................2-2SFP28 (LAN1/LAN2) Link/Activity LED Indicators .....................................2-2 2-4 NC-SI Header & PCI-E 3.0 x8 Connector ......................................................2-3 NC-SI Header .............................................................................................2-3PCI-E 3.0 x8 Connector .............................................................................2-33.3V Standby Power Enable ......................................................................2-4 2-5 Jumper Settings ..............................................................................................2-4 Explanation of Jumpers ..................................................................................2-4 Chapter 3 Installation3-1 Static-Sensitive Devices ..................................................................................3-1 Precautions .....................................................................................................3-1 3-2 Before Installation ...........................................................................................3-2 3-3 Installing the Add-on Card ..............................................................................3-2 3-4 Installing Drivers (for Broadcom®BCM57414) ................................................3-3Chapter 1: OverviewChapter 1Introduction1-1 OverviewCongratulations on purchasing your add-on card from an acknowledged leader in the industry. Supermicro products are designed with the utmost attention to detail to provide you with the highest standards in quality and performance.1-2 About this Add-on CardThe Supermicro AOC-S25G-b2S is the most advanced Network-Controller Side-band Interface (NC-SI) Ethernet LAN card in the market today. With the Broadcom® BCMBCM57414 Controller and dual optical transceiver (SFP28) ports built-in, this add-on card provides unprecedented network interface connectivity with a speed of up to 25Gbps.Featuring Asset Management for Supermicro system and server platforms, this add-on card supports the TruFlow™ Technology, SR-IOV, multi-queueing, stateless offloads, network overlay, NIC partitioning, IEEE 1588 and RDMA over Converged Ethernet (RoCE). The AOC-S25G-b2S offers high-performance connectivity and superb remote sideband manageability to meet the growing needs of high-end computing platforms. For more information regarding product support or updates, please refer to our website at /products/accessories/ addon//AOC-S25G-b2S.cfm.1-3 Key FeaturesThe key features of this add-on card include the following:• Standard PCI-E Gen3 x8 lanes host interface• Low profile, standard short-length form factor• TruFlow™ (Flow-processing engine integrated to reduce CPU overheads)• SR-IOV with up to 128 VFs• Low Latency (TX/RX combined latency = 1.5 us)AOC-S25G-b2S Add-On Card User's Guide• Multi-Queue support (NDIS, VMQ, and Net-Queue)• Stateless Offloads• RoCE (RDMA over Converged Ethernet)• Network overlay: VXLAN and NVGR• NPAR (NIC partitioning)• IEEE 1588• Asset Management (for Supermicro systems only)• Low power (less than 5W typically)• RoSH support• Cable support: copper cables, fiber cables, optic cables with optional transceiv-ers• Dimensions 2.7" (W) x 5.9" (L) (68.58cm (H) x 149.86cm (L))1-4 Supermicro Motherboard SupportThis add-on card supports the following motherboards:• X10SRD-F• X10SDV-TLN4F• X10SLA-F• X10SLX-F• X10SRA-F• X10SRG-F• X10SRH-CF• X10SRH-CLN4F• X10SRi-FChapter 1: Overview• X10SRL-F• X10SRW-F• X10DAi• X10DAC• X10DAX• X10DAL-i• X10DRC-T4+• X10DRC-LN4+• X10DRi-T4+• X10DRi-LN4+• X10DRT-P• X10DRD-iNTP• X10DRD-LTP• X10DRFF-C• X10DRFR-T• X10DRG-Q• X10DRH-C• X10DRH-iT• X10DRi-T• X10DRL-CT• X10DRL-i• X10DRT-LAOC-S25G-b2S Add-On Card User's Guide• X10DRT-LIBQ• X10DRT-LIBF• X10DRU-i+• X10DRW-E• X10DRW-N• X10DRX• X10DRD-iNT• X10DRD-LChapter 2Hardware Components 2-1 Add-On Card Image and LayoutThe AOC-S25G-b2S ImageThe AOC-S25G-b2S LayoutAOC-S25G-b2S Add-On Card User's Guide2-3 SFP28 Ethernet Connections SFP28 (LAN1/LAN2) ConnectorsTwo small form-factor pluggable (SFP28) optical transceiver connectors (SFP1/SFP2) are located on the add-on card. These SFP 28 ports provide Ethernet 25GbE/10GbE network connections. See the layout below for the locations.1. SF28 LAN12. SF28 LAN23. D2: SF28 LAN1 LED4. D3: SF28 LAN2 LED SFP28 (LAN1/LAN2) Link/Activity LED IndicatorsTwo LAN Link/Activity LED indicators are located at D2 and D3 on the add-on card. D2 is used for the SFP28 LAN1 connector, and D3, for SFP28 LAN2 connector. See the table below for the LED states.Chapter 2: Hardware Components2-4 NC-SI Header & PCI-E 3.0 x8 ConnectorNC-SI HeaderA Network-Controller Sideband Interface (NC-SI) header is located at JNCSI1 on the add-on card. Connect an appropriate cable from this header to a motherboard to provide the out-of-band (sideband) connection between the onboard Baseboard Management Controller (BMC) and a Network Interface Controller (NIC) for remote management. For the network sideband interface to work properly, you will need to use a motherboard that supports NC-SI and also need to have a special cable. Please contact Supermicro at to purchase the cable for this header. See the layout below for the location of the JNCSI1 header.PCI-E 3.0 x8 ConnectorA PCI-E 3.0 x8 connector is located at JGF1 on the add-on card. Insert this con-nector into a PCI-E 3.0 x 8 slot on a motherboard to use this add-on card. See the layout below for the location.1. NS-CI Header2. PCI-E3.0 x8 ConnectorAOC-S25G-b2S Add-On Card User's Guide2-5 Jumper SettingsExplanation of JumpersTo modify the operation of the mother-board, jumpers can be used to choosebetween optional settings. Jumpers createshorts between two pins to change thefunction of the connector. Pin 1 is identifiedwith a square solder pad on the printedcircuit board. See the motherboard layoutpages for jumper locations. 1. Standby PWR Enable3.3V Standby Power EnableThe 3.3V Standby Power Enable jumper islocated at JP2 on the add-on card. ClosePins 1 & 2 to enable 3.3V Standby Powersupport. The default setting is Disabled .Pins Jumper Cap Setting 3 2 13 2 1Chapter 3: InstallationChapter 3InstallationNote: Your system came with the AOC-S25G-b2S add-on card to beused as a part of an integrated solution. We do not recommend that anypart of your system components be removed and re-installed. However,if you do need to remove or re-install a system component, includingthis add-on card, please follow the instructions below to ensure propersystem setup. Also, be sure to remove the power cord first before adding,removing or changing any hardware components to avoid damaging thesystem or components.3-1 Static-Sensitive DevicesElectrostatic Discharge (ESD) can damage electronic com p onents. To avoid dam-aging your add-on card, it is important to handle it very carefully. The following measures are generally sufficient to protect your equipment from ESD.Precautions• Use a grounded wrist strap designed to prevent static discharge.• Touch a grounded metal object before removing the add-on card from the antistatic bag.• Handle the add-on card by its edges only; do not touch its components, or peripheral chips.• Put the add-on card back into the antistatic bags when not in use.• For grounding purposes, make sure that your system chassis provides excellent conductivity between the power supply, the case, the mounting fasteners and the add-on card.AOC-S25G-b2S Add-On Card User's Guide3-2 Before InstallationTo install the add-on card properly, be sure to follow the instructions below.1. Power down the system.2. Remove the power cord from the wall socket.3. Use industry-standard anti-static equipment (such as gloves or wrist strap)and follow the instructions listed on Page 3-1 to avoid damage caused byESD.4. Familiarize yourself with the server, motherboard, and/or chassis documenta-tion.5. Confirm that your operating system includes the latest updates and hotfixes.3-3 Installing the Add-on CardFollow the steps below to install the add-on card into your system.1. Remove the server cover and, if necessary, set aside any screws for lateruse.2. Remove the add-on card slot cover. If the case requires a screw, place thescrew aside for later use.3. Position the add-on card in the slot directly over the connector on the mother-board, and gently push down on both sides of the card until it slides into the PCI connector.4. Secure the add-on card/motherboard to the chassis. If required, use thescrew that you previously removed.5. Attach any necessary external cables to the add-on card.6. Replace the chassis cover.7. Plug the power cord into the wall socket, and power up the system.Chapter 3: Installation3-4 Installing Drivers (for Broadcom®BCM57414)To install both drivers and firmware for the AOC-S25G-b2S add-on card for either Linux and Windows, please follow the instructions below.Before Installing the Drivers for the Linux Operating SystemOnlyInfiniband-diags is a set of utilities designed to help configure, debug, and maintain infiniband fabrics. Installing them from the Linux library is necessary prior to driver installation. To to do so, please first download the following libraries:yum -y install libibverbs* infiniband-diags perftest qperf librdmacm-utilsyum -y install groupinstall "InfiniBand Support"Installing 25G Drivers for the Linux Operating System Follow the steps below to install the drivers on the Linux operating system:1. Download the Linux driver package file: netxtreme-bnxt_en-<ver>.tar.gz.Note: This driver can be found on either the SuperMicro website, or bygoing to the Linux_Driver directory from the FTP site (ftp://ftp.supermicro.AOC-S25G-b2S Add-On Card User's Guidecom/Networking_Drivers) or CDR-NIC LAN driver CD by going to thefollowing directory: Broadcom > 25G > Linux > Linux_Driver.2. Install the driver by entering the following commandstar xvzf netextreme-bnxt_en-<ver>.tar.gzcd netextreme-bnxt_en-<ver>make buildmake installRDMA over Converged Ethernet (RoCE) is a network protocol that allows remote direct memory access (RDMA) over an Ethernet network. This feature is optional, but if you would like to install with RoCE, please follow the additional steps below:1. Download the Linux driver package file: libbnxt_re-<ver>.tar.gz.Note: This driver can be found on either the SuperMicro website, or bygoing to the Linux_RoCE_Lib directory from the FTP site (ftp://ftp.super-/Networking_Drivers) or CDR-NIC LAN driver CD by going tothe following directory: Broadcom > 25G > Linux > Linux_RoCE_Lib.2. Install the library by entering the following commands:tar xvzf libbnxt_re-<ver>.tar.gzcd libbnxt_re-<ver>./configuremakemake installcp bnxt_re.driver/etc/libibverbs.decho "/usr/local/lib">>/etc/ld.so.confldconfig -vInstalling 25G Drivers for the Windows Operating System Follow the steps below to install the drivers on the Windows operating system:1. From the FTP site or CDR-NIC LAN driver CD, go to the following directory:Broadcom > 25G > Windows.2. Choose the desired Windows driver package folder.3. As the drivers are in .inf format, you can install the driver from the DeviceManager.(Disclaimer Continued)The products sold by Supermicro are not intended for and will not be used in life support systems, medical equipment, nuclear facilities or systems, aircraft, aircraft devices, aircraft/emergency com-munication devices or other critical systems whose failure to perform be reasonably expected to result in significant injury or loss of life or catastrophic property damage. Accordingly, Supermicro disclaims any and all liability, and should buyer use or sell such products for use in such ultra-hazardous ap-plications, it does so entirely at its own risk. Furthermore, buyer agrees to fully indemnify, defend and hold Supermicro harmless for and against any and all claims, demands, actions, litigation, and proceedings of any kind arising out of or related to such ultra-hazardous use or sale.。
ATECC508A Atmel密钥字符串认证设备数据手册说明书

ATECC508AAtmel CryptoAuthentication DeviceSUMMARY DATASHEETFeatures∙ Cryptographic Co-processor with Secure Hardware-based Key Storage ∙ Performs High-Speed Public Key (PKI) Algorithms– ECDSA: FIPS186-3 Elliptic Curve Digital Signature Algorithm – ECDH: FIPS SP800-56A Elliptic Curve Diffie-Hellman Algorithm ∙ NIST Standard P256 Elliptic Curve Support ∙ SHA-256 Hash Algorithm with HMAC Option ∙ Host and Client Operations ∙ 256-bit Key Length ∙ Storage for up to 16 Keys∙ Two high-endurance monotonic counters ∙ Guaranteed Unique 72-bit Serial Number∙ Internal High-quality FIPS Random Number Generator (RNG) ∙ 10Kb EEPROM Memory for Keys, Certificates, and Data ∙ Storage for up to 16 Keys∙ Multiple Options for Consumption Logging and One Time Write Information∙ Intrusion Latch for External Tamper Switch or Power-on Chip Enablement. Multiple I/O Options:– High-speed Single Pin Interface, with One GPIO Pin – 1MHz Standard I 2C Interface ∙ 2.0V to 5.5V Supply Voltage Range ∙ 1.8V to 5.5V IO levels ∙ <150nA Sleep Current∙ 8-pad UDFN, 8-lead SOIC, and 3-lead CONTACT PackagesApplications∙ IoT Node Security and ID ∙ S ecure Download and Boot ∙ E cosystem Control ∙ M essage Security ∙ A nti-CloningThis is a summary document. The complete document is available under NDA. For more information, please contact your local Atmel sales office.Secure Download and BootAuthentication and Protect Code In-transitEcosystem ControlEnsure Only OEM/Licensed Nodes and Accessories WorkAnti-cloningPrevent Building with Identical BOM or Stolen CodeMessage SecurityAuthentication, Message Integrity,and Confidentiality of Network Nodes (IoT)CryptoAuthenticationEnsures Things and Code are Real, Untampered, and ConfidentialPin Configuration and Pinouts Table 1. Pin ConfigurationFigure 1. PinoutsATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_102015221 Introduction1.1 ApplicationsThe Atmel® ATECC508A is a member of the Atmel CryptoAuthentication™ family of crypto engine authentication devices with highly secure hardware-based key storage.The ATECC508A has a flexible command set that allows use in many applications, including the following,among many others:∙Network/IoT Node ProtectionAuthenticates node IDs, ensures the integrity of messages, and supports key agreement to create sessionkeys for message encryption.∙Anti-CounterfeitingValidates that a removable, replaceable, or consumable client is authentic. Examples of clients could besystem accessories, electronic daughter cards, or other spare parts. It can also be used to validate asoftware/firmware module or memory storage element.∙Protecting Firmware or MediaValidates code stored in flash memory at boot to prevent unauthorized modifications, encrypt downloadedprogram files as a common broadcast, or uniquely encrypt code images to be usable on a single systemonly.∙Storing Secure DataStore secret keys for use by crypto accelerators in standard microprocessors. Programmable protection isavailable using encrypted/authenticated reads and writes.∙Checking User PasswordValidates user-entered passwords without letting the expected value become known, maps memorablepasswords to a random number, and securely exchanges password values with remote systems.1.2 Device FeaturesThe ATECC508A includes an EEPROM array which can be used for storage of up to 16 keys, certificates,miscellaneous read/write, read-only or secret data, consumption logging, and security configurations. Access to the various sections of memory can be restricted in a variety of ways and then the configuration can be locked to prevent changes.The ATECC508A features a wide array of defense mechanisms specifically designed to prevent physical attacks on the device itself, or logical attacks on the data transmitted between the device and the system. Hardware restrictions on the ways in which keys are used or generated provide further defense against certain styles of attack.Access to the device is made through a standard I2C Interface at speeds of up to 1Mb/s. The interface iscompatible with standard Serial EEPROM I2C interface specifications. The device also supports a Single-Wire Interface (SWI), which can reduce the number of GPIOs required on the system processor, and/or reduce the number of pins on connectors. If the Single-Wire Interface is enabled, the remaining pin is available for use as a GPIO, an authenticated output or tamper input.Using either the I2C or Single-Wire Interface, multiple ATECC508A devices can share the same bus, which saves processor GPIO usage in systems with multiple clients such as different color ink tanks or multiple spare parts, for example.Each ATECC508A ships with a guaranteed unique 72-bit serial number. Using the cryptographic protocolssupported by the device, a host system or remote server can verify a signature of the serial number to prove that the serial number is authentic and not a copy. Serial numbers are often stored in a standard Serial EEPROM;however, these can be easily copied with no way for the host to know if the serial number is authentic or if it is a clone.ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_1020153 3ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_10201544The ATECC508A can generate high-quality FIPS random numbers and employ them for any purpose, including usage as part of the device’s crypto protocols. Because each random number is guaranteed to be essentially unique from all numbers ever generated on this or any other device, their inclusion in the protocol calculation ensures that replay attacks (i.e. re-transmitting a previously successful transaction) will always fail.System integration is easy due to a wide supply voltage range (of 2.0V to 5.5V) and an ultra-low sleep current (of <150nA). Multiple package options are available.See Section 3 for information regarding compatibility with the Atmel ATSHA204 and ATECC108.1.3 Cryptographic OperationThe ATECC508A implements a complete asymmetric (public/private) key cryptographic signature solution based upon Elliptic Curve Cryptography and the ECDSA signature protocol. The device features hardware acceleration for the NIST standard P256 prime curve and supports the complete key life cycle from high quality private key generation, to ECDSA signature generation, ECDH key agreement, and ECDSA public key signature verification.The hardware accelerator can implement such asymmetric cryptographic operations from ten to one-thousand times faster than software running on standard microprocessors, without the usual high risk of key exposure that is endemic to standard microprocessors.The device is designed to securely store multiple private keys along with their associated public keys andcertificates. The signature verification command can use any stored or an external ECC public key. Public keys stored within the device can be configured to require validation via a certificate chain to speed-up subsequent device authentications.Random private key generation is supported internally within the device to ensure that the private key can never be known outside of the device. The public key corresponding to a stored private key is always returned when the key is generated and it may optionally be computed at a later time.The ATECC508A also supports a standard hash-based challenge-response protocol in order to simplifyprogramming. In its most basic instantiation, the system sends a challenge to the device, which combines that challenge with a secret key and then sends the response back to the system. The device uses a SHA-256cryptographic hash algorithm to make that combination so that an observer on the bus cannot derive the value of the secret key, but preserving that ability of a recipient to verify that the response is correct by performing the same calculation with a stored copy of the secret on the recipient’s system.Due to the flexible command set of the ATECC508A, these basic operation sets (i.e. ECDSA signatures, ECDH key agreement and SHA-256 challenge-response) can be expanded in many ways.In a host-client configuration where the host (for instance a mobile phone) needs to verify a client (for instance an OEM battery), there is a need to store the secret in the host in order to validate the response from the client. The CheckMac command allows the device to securely store the secret in the host system and hides the correct response value from the pins, returning only a yes or no answer to the system.All hashing functions are implemented using the industry-standard SHA-256 secure hash algorithm, which is part of the latest set of high-security cryptographic algorithms recommended by various government agencies and cryptographic experts. The ATECC508A employs full-sized 256 bit secret keys to prevent any kind of exhaustive attack.2 Electrical Characteristics 2.1 Absolute Maximum Ratings*Operating Temperature .......................... -40°C to 85°C Storage Temperature ........................... -65°C to 150°C Maximum Operating Voltage................................. 6.0V DC Output Current ................................................ 5mA Voltage on any pin ...................... -0.5V to (V CC + 0.5V) *Notice: Stresses beyond those listed under “AbsoluteMaximum Ratings” may cause permanent damage tothe device. This is a stress rating only and functionaloperation of the device at these or any otherconditions beyond those indicated in the operationalsections of this specification are not implied.Exposure to absolute maximum rating conditions forextended periods may affect device reliability.2.2 ReliabilityThe ATECC508A is fabricated with the Atmel high reliability of the CMOS EEPROM manufacturing technology.Table 2-1. EEPROM Reliability2.3 AC Parameters: All I/O InterfacesFigure 2-1. AC Parameters: All I/O InterfacesNote: 1. These parameters are guaranteed through characterization, but not tested.ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_1020155 5ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_102015662.3.1AC Parameters: Single-Wire InterfaceTable 2-2.AC Parameters: Single-Wire InterfaceApplicable from T A = -40°C to +85°C, V CC = +2.0V to +5.5V, CL =100pF (unless otherwise noted).Note: 1.START, ZLO, ZHI, and BIT are designed to be compatible with a standard UART running at 230.4Kbaud for both transmit and receive. The UART should be set to seven data bits, no parity and one Stop bit.2.3.2 AC Parameters: I2C InterfaceTable 2-3. AC Characteristics of I2C InterfaceApplicable over recommended operating range from TA = -40°C to + 85°C, V CC = +2.0V to +5.5V, CL = 1 TTL Gate and 100pF (unless otherwise noted).Note: 1. Values are based on characterization and are not tested.AC measurement conditions:∙RL (connects between SDA and V CC): 1.2k (for V CC +2.0V to +5.0V)∙Input pulse voltages: 0.3V CC to 0.7V CC∙Input rise and fall times: ≤ 50ns∙Input and output timing reference voltage: 0.5V CCATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_1020157 7ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_102015882.4DC Parameters: All I/O InterfacesTable 2-4. DC Parameters on All I/O Interfaces2.4.1V IH and V IL SpecificationsThe input voltage thresholds when in sleep or idle mode are dependent on the V CC level as shown in the graphbelow. When the device is active (i.e. not in sleep or idle mode), the input voltage thresholds are different depending upon the state of TTLenable (bit 1) within the ChipMode byte in the Configuration zone of theEEPROM. When a common voltage is used for the ATECC508A V CC pin and the input pull-up resistor, then this bit should be set to a one, which permits the input thresholds to track the supply.If the voltage supplied to the V CC pin of the ATECC508A is different than the system voltage to which the input pull-up resistor is connected, then the system designer may choose to set TTLenable to zero, which enables a fixed input threshold according to the following table. The following applies only when the device is active:Table 2-5. V IL , V IH on All I/O Interfaces3 Compatibility3.1 Atmel ATSHA204ATECC508A is fully compatible with the ATSHA204 and ATSHA204A devices. If properly configured, it can be used in all situations where the ATSHA204 or ATSHA204A is currently employed. Because the Configuration zone is larger, the personalization procedures for the device must be updated when personalizing theATSHA204 or ATSHA204A.3.2 Atmel ATECC108ATECC508A is designed to be fully compatible with the ATECC108 and ATECC108A devices. If properlyconfigured, can be used in all situations where ATECC108 is currently employed. In many situations, theATECC508A can also be used in an ATECC108 application without change. The new revisions providesignificant advantages as outlined below:New Features in ATECC108A vs. ATECC108∙Intrusion Detection Capability, Including Gating Key Use∙New SHA Command, Also Computes HMAC∙X.509 Certificate Verification Capability∙Programmable Watchdog Timer Length∙Programmable Power Reduction∙Shared Random Nonce and Key Configuration Validation (Gendig Command)∙Larger Slot 8 which is Extended to 416 bytes4 Ordering InformationNotes: 1. Please contact Atmel for availability.2. Please contact Atmel for thinner packages.ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_1020159 9ATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_1020151105Package Drawings5.18-lead SOICATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_10201511 115.2 8-pad UDFNATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_1020151125.33-lead CONTACTATECC508A [Summary Datasheet]Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_10201513 136 Revision HistoryATECC508A [Summary Datasheet] Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_102015114Atmel Corporation 1600 Technology Drive, San Jose, CA 95110 USA T: (+1)(408) 441.0311 F: (+1)(408) 436.4200 │ © 2015 Atmel Corporation. / Rev.:Atmel-8923BS-CryptoAuth-ATECC508A-Datasheet-Summary_102015.Atmel ®, Atmel logo and combinations thereof, Enabling Unlimited Possibilities ®, CryptoAuthentication™, and others are registered trademarks or trademarks of Atmel Corporation in U.S. and other countries.DISCLAIMER: The information in this document is provided in connection with Atmel products. No license, express or implied, by estoppel or otherwise, to any intellectual property right is granted by this document or in connection with the sale of Atmel products. EXCEPT AS SET FORTH IN THE ATMEL TERMS AND COND ITIONS OF SALES LOCATED ON THE ATMEL WEBSITE, ATMEL ASSUMES NO LIABILITY WHATSOEVER AND DISCLAIMS ANY EXPRESS, IMPLIED OR STATUTORY WARRANTY RELATING TO ITS PRODUCTS INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON -INFRINGEMENT. IN NO EVENT SHALL ATMEL BE LIABLE FOR ANY DIRECT, INDIRECT, CONSEQUENTIAL, PUNITIVE, SPECIAL OR INCIDENTAL DAMAGES (INCLUDING, WITHOUT LIMITATION, DAMAG ES FOR LOSS AND PROFITS, BUSINESS INTERRUPTION, OR LOSS OF INFORMATION) ARISING OUT OF THE USE OR INABILITY TO USE THIS DOCUMENT , EVEN IF ATMEL HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Atmel makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and products descriptions at any time without notice. Atmel does not make any commitment to update the information contained herein. Unless specifically provided otherwise, Atmel products are not suitable for, and shall not be used in, automotive applications. At mel products are not intended, authorized, or warranted for use as components in applications intended to support or sustain life.SAFETY-CRITICAL, MILITARY, AND AUTOMOTIVE APPLICATIONS DISCLAIMER: Atmel products are not designed for and will not be used in connection with any applications where the failure of such products would reasonably be expected to result in significant personal injury or death (“Safety -Critical Applications”) without an Atmel officer's specific written consent. Safety-Critical Applications include, without limitation, life support devices and systems, equipment or systems for the operation of nuclear fac ilities and weapons systems. Atmel products are not designed nor intended for use in military or aerospace applications or environments unless specifically designated by Atmel as military-grade. Atmel products are not designed nor intended for use in automotive applications unless specifically designated by Atmel as automotive -grade.。
hmac_authentication_认证方式_详解_概述及解释说明
hmac authentication 认证方式详解概述及解释说明1. 引言1.1 概述HMAC认证方式是一种基于加密哈希函数的身份验证机制,用于验证数据的完整性和真实性。
它通过使用秘密密钥和消息摘要算法来生成一个认证码,这个认证码可以被接收方用来验证发送方的身份和确保数据的完整性。
1.2 文章结构本文将详细介绍HMAC认证方式的原理、流程以及实现步骤。
同时,也会与其他常见的认证方式进行比较,以便更好地理解HMAC认证方式的优势与应用场景。
最后,在结论部分将对HMAC技术发展进行展望,并提出一些建议。
1.3 目的本文的目的是对HMAC认证方式进行深入探讨,帮助读者了解其背后的原理和流程。
通过对HMAC的详细解释和说明,读者可以更好地理解如何应用这种安全机制来保护数据传输中的身份验证和数据完整性问题。
同时,本文还旨在展望未来HMAC相关技术发展,并给出相应建议,以促进该领域技术的进一步创新和应用。
2. HMAC认证方式:2.1 HMAC基础知识:HMAC(Hash-based Message Authentication Code)是一种基于哈希函数的消息认证码。
它通过将密钥与消息进行混合,并经过多次迭代计算生成一个固定长度的认证码。
这个认证码可以保证消息的完整性和真实性,同时也能防止伪造和篡改。
2.2 HMAC认证流程:HMAC认证流程主要包括以下步骤:- 首先,选择合适的哈希函数,如SHA-256。
- 然后,生成一个随机的密钥,并将其与需要发送的消息一起进行处理。
- 对处理后的数据进行多次迭代计算,以生成最终的认证码。
- 将认证码发送给接收方。
在接收方接收到消息后,进行相同的操作来验证消息的完整性和真实性。
如果接收到的认证码与计算出来的认证码不一致,则表示消息可能被篡改或伪造。
2.3 HMAC的优势与应用场景:HMAC具有以下几个优势:- 安全性高: HMAC采用了密码学中常用的哈希函数,并且结合了密码学中常见的技术手段,使得伪造和篡改变得更加困难。
cmac认证标识 -回复
cmac认证标识-回复什么是CMAC认证标识?CMAC(Cipher-based Message Authentication Code)认证标识是一种使用对称密钥加密算法生成的认证标识,用于验证数据的完整性和真实性。
CMAC是一种基于密码学原理的身份认证和数据完整性校验技术,通常被广泛应用于各种安全通信协议和数据传输系统中。
CMAC由两个主要组件构成:一个密钥和一个消息。
在生成CMAC认证标识时,首先使用密钥对消息进行加密,然后生成一个固定长度的认证标识。
接收方将使用相同的密钥对接收到的消息进行加密,并与发送方生成的认证标识进行比较。
如果两者匹配,说明消息没有被篡改,并且是可信的。
CMAC认证标识的生成过程非常复杂,涉及多个步骤。
下面将一步一步回答生成CMAC认证标识的过程。
第一步:选择合适的加密算法和密钥长度在使用CMAC生成认证标识之前,需要选择适合的加密算法和密钥长度。
常用的加密算法包括AES、DES和3DES等。
根据不同的应用场景和安全要求,可以选择不同的算法和密钥长度。
第二步:生成密钥在使用CMAC生成认证标识之前,需要生成一个用于加密和解密的密钥。
密钥的生成过程可以使用伪随机数生成器(PRNG)或密码学安全随机数生成器(CSPRNG)来实现。
密钥可以是固定的,也可以是根据需要定期更换的。
第三步:对消息进行填充在生成CMAC认证标识之前,需要对消息进行填充。
填充的目的是使消息的长度满足加密算法的要求。
填充过程可以使用不同的方法,例如添加空白字符或特定的填充位。
填充后的消息长度应该是加密算法分组大小的倍数。
第四步:划分消息为若干分组将填充后的消息划分为若干个分组,每个分组的大小应该等于加密算法的分组大小。
如果消息长度不是分组大小的整数倍,可以添加额外的填充位来满足要求。
第五步:生成中间值对划分后的每个分组进行加密,并将结果作为中间值。
加密过程使用选择的加密算法和生成的密钥进行。
第六步:生成校验结果将每个分组的中间值进行异或操作,并生成一个最终的校验结果。
stanag 3756相关标准
stanag 3756相关标准STANAG 3756是北约(NATO)为了提高成员国间通信和数据交换的互操作性而制定的标准之一。
正式名称为“数字信息交换系统(MVCS)优选标准”,简单理解就是一种用于数据交换和通信的标准规范。
STANAG 3756定义了一系列要求和规定,以确保不同国家的军事部门在通信和数据交换方面能够高效地协作。
这个标准主要包括以下几个方面的内容:1.数据格式和编码:STANAG 3756规定了数据的格式和编码,以确保不同系统和设备之间能够正确地解读和处理数据。
这样就能够实现不同军事部门间的数据交换和共享,提高信息的准确性和实用性。
2.通信协议:STANAG 3756规定了通信协议,即在数据传输过程中,不同系统和设备之间的沟通和交互方式。
通过使用相同的通信协议,不同国家的军事部门可以实现安全、有效的通信,无论是在战斗场景中还是平时的日常工作中。
3.安全性要求:STANAG 3756要求实施安全措施,保护数据的机密性和完整性。
数据的安全性对于军事部门来说至关重要,因此STANAG3756规定了一些标准和要求,确保数据在传输过程中不会被窃取、篡改或破坏。
4.兼容性:STANAG 3756要求不同系统和设备之间可以相互兼容和交互。
这意味着即使不同军事部门使用的是不同的系统和设备,它们仍然可以共享和交换数据,实现无缝协作。
这样就能够更好地利用各个成员国的军事资源,提高整体的战斗效能。
STANAG 3756作为一个标准规范,对于北约成员国之间的军事合作具有重要意义。
通过遵循这个标准,不同国家的军事部门可以保持高水平的通信和数据交换能力,提高作战能力和效率。
同时,这个标准也为军事装备的采购和升级提供了指导,确保各国军队使用的设备能够满足北约的要求和标准。
总之,STANAG 3756标准是北约为了促进成员国间军事通信和数据交换的互操作性而制定的一套规范。
这个标准规定了数据格式和编码、通信协议、安全性要求和兼容性等方面的要求,帮助不同国家的军事部门实现高效、安全的数据交换和通信。
HP 9250C数字发送器:安全性与认证说明书
©2007 Copyright Hewlett-Packard Developmentsoftware program that can be used to control the digital sender is the HP Web Jetadmin program. This program can also be configured to require a password before any changes can be made. It should also be installed on a secure server and should be protected from unauthorized use.
A number of third-party software vendors offer services for secure e-mail delivery. The Secondary email feature is designed to work with one of these third-party software programs for users that require an extra measure of data security.
By default, the digital-sending configuration options in the embedded Web server (EWS) are disabled when the digital sender begins using the HP DSS service. The digital sender can then only be configured by using the HP MFP DSS Configuration Utility. This centralizes configuration tasks and helps control security. You should make sure that the HP DSS is installed on a secure server and that the HP MFP DSS Configuration Utility cannot be used by unauthorized users.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
This paper describes a new message authentication code, UMAC, and the theory that lies behind it. UMAC has been designed with two main goals in mind: extreme speed and provable security. We aimed to create the fastest MAC ever described, and by a wide margin. (We are speaking of speed with respect to software implementations on contemporary general-purpose computers.) But we insisted that it be demonstrably secure, in the sense of having quantitatively desirable reductions from its underlying cryptographic primitives. UMAC is certainly fast. On a 350 MHz Pentium II PC, one version of UMAC (where the adversary has 2−60 chance of forgery) gives a peak performance of 2.9 Gbits/sec (0.98 cycles/byte). Another version of UMAC (with 2−30 chance of forgery) achieves peak performance of 5.6 Gbits/sec (0.51 cycles/byte). For comparison, our SHA-1 implementation runs at 12.6 cycles/byte. (SHA-1 speed upper bounds the speed of HMAC-SHA1 [3], a software-oriented MAC representative of the speeds achieved by current practice.) The previous speed champion among proposed universal hash functions (the main ingredient for making a fast MAC; see below) was MMH [13], which runs at about 1.2 cycles/byte (for 2−30 chance of forgery) under its originally envisioned implementation.
Universal Hashing And Authentication. Our starting point is a universal hash-function family [10]. (Indeed the “U” in UMAC is meant to suggest the central role that universal hash-function families play in this MAC.) Remember that a set of hash functions is said to be “ǫ-universal” if for any pair of distinct messages, the probability that they collide (hash to the same value) is at most ǫ. The probability is over the random choice of hash function. As described in [28], a universal hash-function family can be used to build a MAC. The parties share a secret and randomly chosen hash function from the hash-function family, and a secret encryption key. A message is authenticated by hashing it with the shared hash function and then encrypting the resulting hash. Wegman and Carter showed that when the hash-function family is strongly universal (a similar but stronger property than the one we defined) and the encryption is realized by a one-time pad, the adversary cannot forge with probability better than that obtained by choosing a random string for the MAC. Why Universal Hashing? As suggested many times before [16, 25, 13], the above approach is a promising one for building a highly-secure and ultra-fast MAC. The reasoning is like this: the speed of a universal-hashing MAC depends on the speed of the hashing step and the speed of the encrypting step. But if the hash function compresses messages well (i.e., its output is short) then the encryption shouldn’t take long simply because it is a short string that is being encrypted. On the other hand, since the combinatorial property of the universal hash-function family is mathematically proven (making no cryptographic hardness assumptions), it needs no “over-design” or “safety margin” the way a cryptographic primitive would. Quite the opposite: the hash-function family might as well be the fastest, simplest thing that one can prove universal. Equally important, the above approach makes for desirable security properties. Since the cryptographic primitive is applied only to the (much shorter) hashed image of the message, we can select a cryptographically conservative design for this step and pay with only a minor impact on speed. And the fact that the underlying cryptographic primitive is used only on short and secret messages eliminates many avenues of attack. Under this approach security and efficiency are not conflicting requirements—quite the contrary, they go hand in hand. Quest For Fast Universal Hashing. At least in principle, the universalhashing paradigm has reduced the problem of fast message authentication to that of fast universal hashing. Thus there has been much work on the design of fast-tocompute universal hash-function families. Here is a glimpse of some of this work. Krawczyk [16] describes the “cryptographic CRC” which has very fast hardware
UMAC: Fast and Secure Message Authentication
J. Black1 , S. Halevi2 , H. Krawczyk2,3, T. Krovetz1, and P. Rogaway1
1
3
Department of Computer Science, University of California, Davis CA 95616 USA 2 IBM T.J. Watson Research Center, Yorktown Heights NY 10598 USA Department of Electrical Engineering, Technion – Israel Institute of Technology, 32000 Haifa ISRAEL Abstract. We describe a message authentication algorithm, UMAC, which can authenticate messages (in software, on contemporary machines) roughly an order of magnitude faster than current practice (e.g., HMAC-SHA1), and about twice as fast as times previously reported for the universal hash-function family MMH. To achieve such speeds, UMAC uses a new universal hash-function family, NH, and a design which allows effective exploitation of SIMD parallelism. The “cryptographic” work of UMAC is done using standard primitives of the user’s choice, such as a block cipher or cryptographic hash function; no new heuristic primitives are developed here. Instead, the security of UMAC is rigorously proven, in the sense of giving exact and quantitatively strong results which demonstrate an inability to forge UMAC-authenticated messages assuming an inability to break the underlying cryptographic primitive. Unlike conventional, inherently serial MACs, UMAC is parallelizable, and will have ever-faster implementation speeds as machines offer up increasing amounts of parallelism. We envision UMAC as a practical algorithm for next-generation message authentication.
