Comment on "Symbolic Computation and q-Deformed Function Solutions of the (2+1)-Dimensional
数值计算方法

HTML and Java
Software
Higher-Order Programming
Maple - Mathematical Programming Language Mathematica - Mathematical Programming Language Java - Internet Programming Language Matlab - Matrix Laboratory
Linear Systems - Setting up multiple sets of
equations and solution techniques.
LU Decomposition - Technique to decompose
matrices
Eigen-analysis - finding the eigenvalues and
Topics
Matlab - Mathematical Program (Vectors) Computer Errors - Recognition and solutions Roots f(x) = 0
Linear Methods Nonlinear Methods
Topics
MatLab
Variable Types
Integers Real
Values (float and double) Complex Numbers (a + ib)
a - real value b - imaginary value (“i” is the square root of 1)
Transpose vector
x x 1 , x 2 , x 3 , x 4
信息与计算科学相关的英文综述范文

信息与计算科学相关的英文综述范文English:With the rapid advancement of technology, the field of information and computer science has become increasingly indispensable in today's society. Information and computer science is a multidisciplinary field that encompasses a wide range of topics, including data analysis, artificial intelligence, machine learning, cybersecurity, and more. This field plays a crucial role in various industries, such as healthcare, finance, education, and government. Information and computer science also has a significant impact on daily life, as it is involved in the development of various digital technologies, social media platforms, and mobile applications. Research in this field aims to address complex challenges and create innovative solutions to improve efficiency, security, and accessibility of information systems. Overall, the study of information and computer science is essential for understanding and navigating the ever-evolving digital world.中文翻译:随着科技的快速发展,信息与计算科学领域在当今社会变得日益不可或缺。
计算机b类刊物与会议分类信息
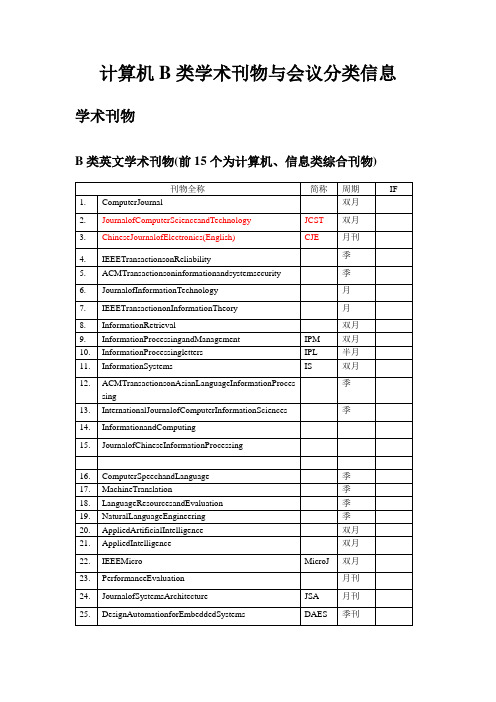
月
31.
ACMTransactionsonInternetTechnology
季
32.
JournalofParallelandDistributedComputing
JPDC
月
33.
ACMTransactionsonEmbeddedComputingSystems
TECS
月
34.
IEEETransactionsonSystems,ManandCybernetics
113.
InternationalJournalofPatternRecognitionandArtificialIntelligence
IJPRAI
双月刊
114.
IEEETransactionsonSystem,Man,andCybernetics
SMC
月刊
115.
InternationalJournalofDocumentAnalysisandRecognition
AIR
月刊
106.
ArtificialLife
AF
月刊
107.
EvolutionaryComputation
EC
双月刊
108.
NeuralNetworks
NN
9/12
2
109.
InternationalJournalofKnowledge-BasedandIntelligentEngineeringSystems
KES
月刊
110.
ArtificialIntelligenceinEngineering
AIE
月刊
111.
ComputationalIntelligence:AnInternationalJournal
Computational_and_Information_Sciences_-_副本

• • • •
Operations Research Philosophy Psychology Sociology
Ant Colony Optimization(ACO) used in finding the shortest way
• ACO which simulate ants find food. And this method returns us a shorteomated theorem proving software based on an internal computer algebra system. It can be used on proving algebra and geometry theorems.
Computational and Information Sciences
GROUP 11 李帆 仲建群 邱位辉 乔宽宽
Let us begin with these questions:
• • • • What? Why important? used for? Advance development?
First Question
What CIS?
• A mathematics subject concerning specific computations and algorithms(算法) • classified with the area of mathematics to which the computations are applied.
Advance Development
• Mathematics Mechanization and Automated Reasoning Platform • (数学机械化自动推理平台)
结合提升小波和QR码的盲水印实现

(5)
1.2 提升小波变换
提升小波 [5] 是由第一代小波变换的提升来实现的。提升 小波既有第一代小波的优点, 又克服了它的局限性。它运算 速度快、 允许完全原位计算, 并且其逆变换是正变换的反运 算。因此应用提升小波进行变换, 可以很好地恢复原始图像。 提升小波的正向提升过程分为 3 个过程: 分裂、 预测和修 正。首先假设已知需要处理的序列集为 λ0 , 具体实现过程为: (1) 分裂。将 λ0 分解为 λ -1 和 γ -1 两个子集。
水印嵌入过程用来将水印信息嵌入到载体图像内, 包括 如下 6 个步骤。 2.3.1 针对原始图像的提升小波变换 假设原始图像 O 的大小为 N ´ N 像素, 将图像 O 进行提 升小波变换, 得到提升小波变换的 4 个分量, 包括逼近子图和 Oh 、 Ov 、 水平、 垂直、 对角线方向的细节子图, 分别记为 Oa 、 Od , 4 个分量的大小均为 N ´ N 4 。 2.3.2 元胞自动机处理 为了提高水印的鲁棒性, 将水印嵌入到提升小波变换的 逼近子图 Oa 中。对 Oa 进行元胞自动机运算, 即将 Oa 分解 为 3 ´ 3 大小的子块, 按照 2.1 节所介绍的方法更改子块中 E 点 的像素值。处理后的图像记为 Oc 。 2.3.3 针对水印信息的 QR 码处理 假定水印信息为 S , 采用 Psytec QR Code Editor v2.11 将 S 处理为 QR 码图像 Sw 。 2.3.4 混沌加密处理 应用 2.2 节所介绍内容, 将图像 Sw 进行置乱, 得到置乱后 的图像 Sw1 。 2.3.5 水印嵌入 应用 2.1 节中公式 (3) 将水印信息嵌入到载体图像中。公 α 的值越小, α的 式中 α 为嵌入强度, 则水印的透明性越好; 值越大, 则水印的鲁棒性越高。因此, 为了在高鲁棒性与良好 的透明性之间取得平衡, 需要对 α 的取值进行控制。通过大 α 的取值为 3 时可以较好地在鲁棒性和透明性之 量实验测试, 间取得平衡。此时, 将处理后的图像 Oc 记为 Oce 。 2.3.6 逆提升小波变换 Od 一起参与逆提升小波 Ov 、 将 Oce 与 2.3.1 节中的 Oh 、 运算, 得到嵌入水印的载体图像 Oe 。 嵌入过程结束, 此时 Oe 即为能够进行版权认证的含有水 印信息的版权图像。
Quantum Computing for Computer Scientists

More informationQuantum Computing for Computer ScientistsThe multidisciplinaryfield of quantum computing strives to exploit someof the uncanny aspects of quantum mechanics to expand our computa-tional horizons.Quantum Computing for Computer Scientists takes read-ers on a tour of this fascinating area of cutting-edge research.Writtenin an accessible yet rigorous fashion,this book employs ideas and tech-niques familiar to every student of computer science.The reader is notexpected to have any advanced mathematics or physics background.Af-ter presenting the necessary prerequisites,the material is organized tolook at different aspects of quantum computing from the specific stand-point of computer science.There are chapters on computer architecture,algorithms,programming languages,theoretical computer science,cryp-tography,information theory,and hardware.The text has step-by-stepexamples,more than two hundred exercises with solutions,and program-ming drills that bring the ideas of quantum computing alive for today’scomputer science students and researchers.Noson S.Yanofsky,PhD,is an Associate Professor in the Departmentof Computer and Information Science at Brooklyn College,City Univer-sity of New York and at the PhD Program in Computer Science at TheGraduate Center of CUNY.Mirco A.Mannucci,PhD,is the founder and CEO of HoloMathics,LLC,a research and development company with a focus on innovative mathe-matical modeling.He also serves as Adjunct Professor of Computer Sci-ence at George Mason University and the University of Maryland.QUANTUM COMPUTING FORCOMPUTER SCIENTISTSNoson S.YanofskyBrooklyn College,City University of New YorkandMirco A.MannucciHoloMathics,LLCMore informationMore informationcambridge university pressCambridge,New York,Melbourne,Madrid,Cape Town,Singapore,S˜ao Paulo,DelhiCambridge University Press32Avenue of the Americas,New York,NY10013-2473,USAInformation on this title:/9780521879965C Noson S.Yanofsky and Mirco A.Mannucci2008This publication is in copyright.Subject to statutory exceptionand to the provisions of relevant collective licensing agreements,no reproduction of any part may take place withoutthe written permission of Cambridge University Press.First published2008Printed in the United States of AmericaA catalog record for this publication is available from the British Library.Library of Congress Cataloging in Publication dataYanofsky,Noson S.,1967–Quantum computing for computer scientists/Noson S.Yanofsky andMirco A.Mannucci.p.cm.Includes bibliographical references and index.ISBN978-0-521-87996-5(hardback)1.Quantum computers.I.Mannucci,Mirco A.,1960–II.Title.QA76.889.Y352008004.1–dc222008020507ISBN978-0-521-879965hardbackCambridge University Press has no responsibility forthe persistence or accuracy of URLs for external orthird-party Internet Web sites referred to in this publicationand does not guarantee that any content on suchWeb sites is,or will remain,accurate or appropriate.More informationDedicated toMoishe and Sharon Yanofskyandto the memory ofLuigi and Antonietta MannucciWisdom is one thing:to know the tho u ght by which all things are directed thro u gh allthings.˜Heraclitu s of Ephe s u s(535–475B C E)a s quoted in Dio g ene s Laertiu s’sLives and Opinions of Eminent PhilosophersBook IX,1. More informationMore informationContentsPreface xi1Complex Numbers71.1Basic Definitions81.2The Algebra of Complex Numbers101.3The Geometry of Complex Numbers152Complex Vector Spaces292.1C n as the Primary Example302.2Definitions,Properties,and Examples342.3Basis and Dimension452.4Inner Products and Hilbert Spaces532.5Eigenvalues and Eigenvectors602.6Hermitian and Unitary Matrices622.7Tensor Product of Vector Spaces663The Leap from Classical to Quantum743.1Classical Deterministic Systems743.2Probabilistic Systems793.3Quantum Systems883.4Assembling Systems974Basic Quantum Theory1034.1Quantum States1034.2Observables1154.3Measuring1264.4Dynamics1294.5Assembling Quantum Systems1325Architecture1385.1Bits and Qubits138viiMore informationviii Contents5.2Classical Gates1445.3Reversible Gates1515.4Quantum Gates1586Algorithms1706.1Deutsch’s Algorithm1716.2The Deutsch–Jozsa Algorithm1796.3Simon’s Periodicity Algorithm1876.4Grover’s Search Algorithm1956.5Shor’s Factoring Algorithm2047Programming Languages2207.1Programming in a Quantum World2207.2Quantum Assembly Programming2217.3Toward Higher-Level Quantum Programming2307.4Quantum Computation Before Quantum Computers2378Theoretical Computer Science2398.1Deterministic and Nondeterministic Computations2398.2Probabilistic Computations2468.3Quantum Computations2519Cryptography2629.1Classical Cryptography2629.2Quantum Key Exchange I:The BB84Protocol2689.3Quantum Key Exchange II:The B92Protocol2739.4Quantum Key Exchange III:The EPR Protocol2759.5Quantum Teleportation27710Information Theory28410.1Classical Information and Shannon Entropy28410.2Quantum Information and von Neumann Entropy28810.3Classical and Quantum Data Compression29510.4Error-Correcting Codes30211Hardware30511.1Quantum Hardware:Goals and Challenges30611.2Implementing a Quantum Computer I:Ion Traps31111.3Implementing a Quantum Computer II:Linear Optics31311.4Implementing a Quantum Computer III:NMRand Superconductors31511.5Future of Quantum Ware316Appendix A Historical Bibliography of Quantum Computing319 by Jill CirasellaA.1Reading Scientific Articles319A.2Models of Computation320More informationContents ixA.3Quantum Gates321A.4Quantum Algorithms and Implementations321A.5Quantum Cryptography323A.6Quantum Information323A.7More Milestones?324Appendix B Answers to Selected Exercises325Appendix C Quantum Computing Experiments with MATLAB351C.1Playing with Matlab351C.2Complex Numbers and Matrices351C.3Quantum Computations354Appendix D Keeping Abreast of Quantum News:QuantumComputing on the Web and in the Literature357by Jill CirasellaD.1Keeping Abreast of Popular News357D.2Keeping Abreast of Scientific Literature358D.3The Best Way to Stay Abreast?359Appendix E Selected Topics for Student Presentations360E.1Complex Numbers361E.2Complex Vector Spaces362E.3The Leap from Classical to Quantum363E.4Basic Quantum Theory364E.5Architecture365E.6Algorithms366E.7Programming Languages368E.8Theoretical Computer Science369E.9Cryptography370E.10Information Theory370E.11Hardware371Bibliography373Index381More informationPrefaceQuantum computing is a fascinating newfield at the intersection of computer sci-ence,mathematics,and physics,which strives to harness some of the uncanny as-pects of quantum mechanics to broaden our computational horizons.This bookpresents some of the most exciting and interesting topics in quantum computing.Along the way,there will be some amazing facts about the universe in which we liveand about the very notions of information and computation.The text you hold in your hands has a distinctflavor from most of the other cur-rently available books on quantum computing.First and foremost,we do not assumethat our reader has much of a mathematics or physics background.This book shouldbe readable by anyone who is in or beyond their second year in a computer scienceprogram.We have written this book specifically with computer scientists in mind,and tailored it accordingly:we assume a bare minimum of mathematical sophistica-tion,afirst course in discrete structures,and a healthy level of curiosity.Because thistext was written specifically for computer people,in addition to the many exercisesthroughout the text,we added many programming drills.These are a hands-on,funway of learning the material presented and getting a real feel for the subject.The calculus-phobic reader will be happy to learn that derivatives and integrals are virtually absent from our text.Quite simply,we avoid differentiation,integra-tion,and all higher mathematics by carefully selecting only those topics that arecritical to a basic introduction to quantum computing.Because we are focusing onthe fundamentals of quantum computing,we can restrict ourselves to thefinite-dimensional mathematics that is required.This turns out to be not much more thanmanipulating vectors and matrices with complex entries.Surprisingly enough,thelion’s share of quantum computing can be done without the intricacies of advancedmathematics.Nevertheless,we hasten to stress that this is a technical textbook.We are not writing a popular science book,nor do we substitute hand waving for rigor or math-ematical precision.Most other texts in thefield present a primer on quantum mechanics in all its glory.Many assume some knowledge of classical mechanics.We do not make theseassumptions.We only discuss what is needed for a basic understanding of quantumxiMore informationxii Prefacecomputing as afield of research in its own right,although we cite sources for learningmore about advanced topics.There are some who consider quantum computing to be solely within the do-main of physics.Others think of the subject as purely mathematical.We stress thecomputer science aspect of quantum computing.It is not our intention for this book to be the definitive treatment of quantum computing.There are a few topics that we do not even touch,and there are severalothers that we approach briefly,not exhaustively.As of this writing,the bible ofquantum computing is Nielsen and Chuang’s magnificent Quantum Computing andQuantum Information(2000).Their book contains almost everything known aboutquantum computing at the time of its publication.We would like to think of ourbook as a usefulfirst step that can prepare the reader for that text.FEATURESThis book is almost entirely self-contained.We do not demand that the reader comearmed with a large toolbox of skills.Even the subject of complex numbers,which istaught in high school,is given a fairly comprehensive review.The book contains many solved problems and easy-to-understand descriptions.We do not merely present the theory;rather,we explain it and go through severalexamples.The book also contains many exercises,which we strongly recommendthe serious reader should attempt to solve.There is no substitute for rolling up one’ssleeves and doing some work!We have also incorporated plenty of programming drills throughout our text.These are hands-on exercises that can be carried out on your laptop to gain a betterunderstanding of the concepts presented here(they are also a great way of hav-ing fun).We hasten to point out that we are entirely language-agnostic.The stu-dent should write the programs in the language that feels most comfortable.Weare also paradigm-agnostic.If declarative programming is your favorite method,gofor it.If object-oriented programming is your game,use that.The programmingdrills build on one another.Functions created in one programming drill will be usedand modified in later drills.Furthermore,in Appendix C,we show how to makelittle quantum computing emulators with MATLAB or how to use a ready-madeone.(Our choice of MATLAB was dictated by the fact that it makes very easy-to-build,quick-and-dirty prototypes,thanks to its vast amount of built-in mathematicaltools.)This text appears to be thefirst to handle quantum programming languages in a significant way.Until now,there have been only research papers and a few surveyson the topic.Chapter7describes the basics of this expandingfield:perhaps some ofour readers will be inspired to contribute to quantum programming!This book also contains several appendices that are important for further study:Appendix A takes readers on a tour of major papers in quantum computing.This bibliographical essay was written by Jill Cirasella,Computational SciencesSpecialist at the Brooklyn College Library.In addition to having a master’s de-gree in library and information science,Jill has a master’s degree in logic,forwhich she wrote a thesis on classical and quantum graph algorithms.This dualbackground uniquely qualifies her to suggest and describe further readings.More informationPreface xiii Appendix B contains the answers to some of the exercises in the text.Othersolutions will also be found on the book’s Web page.We strongly urge studentsto do the exercises on their own and then check their answers against ours.Appendix C uses MATLAB,the popular mathematical environment and an es-tablished industry standard,to show how to carry out most of the mathematicaloperations described in this book.MATLAB has scores of routines for manip-ulating complex matrices:we briefly review the most useful ones and show howthe reader can quickly perform a few quantum computing experiments with al-most no effort,using the freely available MATLAB quantum emulator Quack.Appendix D,also by Jill Cirasella,describes how to use online resources to keepup with developments in quantum computing.Quantum computing is a fast-movingfield,and this appendix offers guidelines and tips forfinding relevantarticles and announcements.Appendix E is a list of possible topics for student presentations.We give briefdescriptions of different topics that a student might present before a class of hispeers.We also provide some hints about where to start looking for materials topresent.ORGANIZATIONThe book begins with two chapters of mathematical preliminaries.Chapter1con-tains the basics of complex numbers,and Chapter2deals with complex vectorspaces.Although much of Chapter1is currently taught in high school,we feel thata review is in order.Much of Chapter2will be known by students who have had acourse in linear algebra.We deliberately did not relegate these chapters to an ap-pendix at the end of the book because the mathematics is necessary to understandwhat is really going on.A reader who knows the material can safely skip thefirsttwo chapters.She might want to skim over these chapters and then return to themas a reference,using the index and the table of contents tofind specific topics.Chapter3is a gentle introduction to some of the ideas that will be encountered throughout the rest of the ing simple models and simple matrix multipli-cation,we demonstrate some of the fundamental concepts of quantum mechanics,which are then formally developed in Chapter4.From there,Chapter5presentssome of the basic architecture of quantum computing.Here one willfind the notionsof a qubit(a quantum generalization of a bit)and the quantum analog of logic gates.Once Chapter5is understood,readers can safely proceed to their choice of Chapters6through11.Each chapter takes its title from a typical course offered in acomputer science department.The chapters look at that subfield of quantum com-puting from the perspective of the given course.These chapters are almost totallyindependent of one another.We urge the readers to study the particular chapterthat corresponds to their favorite course.Learn topics that you likefirst.From thereproceed to other chapters.Figure0.1summarizes the dependencies of the chapters.One of the hardest topics tackled in this text is that of considering two quan-tum systems and combining them,or“entangled”quantum systems.This is donemathematically in Section2.7.It is further motivated in Section3.4and formallypresented in Section4.5.The reader might want to look at these sections together.xivPrefaceFigure 0.1.Chapter dependencies.There are many ways this book can be used as a text for a course.We urge instructors to find their own way.May we humbly suggest the following three plans of action:(1)A class that provides some depth might involve the following:Go through Chapters 1,2,3,4,and 5.Armed with that background,study the entirety of Chapter 6(“Algorithms”)in depth.One can spend at least a third of a semester on that chapter.After wrestling a bit with quantum algorithms,the student will get a good feel for the entire enterprise.(2)If breadth is preferred,pick and choose one or two sections from each of the advanced chapters.Such a course might look like this:(1),2,3,4.1,4.4,5,6.1,7.1,9.1,10.1,10.2,and 11.This will permit the student to see the broad outline of quantum computing and then pursue his or her own path.(3)For a more advanced class (a class in which linear algebra and some mathe-matical sophistication is assumed),we recommend that students be told to read Chapters 1,2,and 3on their own.A nice course can then commence with Chapter 4and plow through most of the remainder of the book.If this is being used as a text in a classroom setting,we strongly recommend that the students make presentations.There are selected topics mentioned in Appendix E.There is no substitute for student participation!Although we have tried to include many topics in this text,inevitably some oth-ers had to be left out.Here are a few that we omitted because of space considera-tions:many of the more complicated proofs in Chapter 8,results about oracle computation,the details of the (quantum)Fourier transforms,and the latest hardware implementations.We give references for further study on these,as well as other subjects,throughout the text.More informationMore informationPreface xvANCILLARIESWe are going to maintain a Web page for the text at/∼noson/qctext.html/The Web page will containperiodic updates to the book,links to interesting books and articles on quantum computing,some answers to certain exercises not solved in Appendix B,anderrata.The reader is encouraged to send any and all corrections tonoson@Help us make this textbook better!ACKNOLWEDGMENTSBoth of us had the great privilege of writing our doctoral theses under the gentleguidance of the recently deceased Alex Heller.Professor Heller wrote the follow-ing1about his teacher Samuel“Sammy”Eilenberg and Sammy’s mathematics:As I perceived it,then,Sammy considered that the highest value in mathematicswas to be found,not in specious depth nor in the overcoming of overwhelmingdifficulty,but rather in providing the definitive clarity that would illuminate itsunderlying order.This never-ending struggle to bring out the underlying order of mathematical structures was always Professor Heller’s everlasting goal,and he did his best to passit on to his students.We have gained greatly from his clarity of vision and his viewof mathematics,but we also saw,embodied in a man,the classical and sober ideal ofcontemplative life at its very best.We both remain eternally grateful to him.While at the City University of New York,we also had the privilege of inter-acting with one of the world’s foremost logicians,Professor Rohit Parikh,a manwhose seminal contributions to thefield are only matched by his enduring com-mitment to promote younger researchers’work.Besides opening fascinating vis-tas to us,Professor Parikh encouraged us more than once to follow new directionsof thought.His continued professional and personal guidance are greatly appre-ciated.We both received our Ph.D.’s from the Department of Mathematics in The Graduate Center of the City University of New York.We thank them for providingus with a warm and friendly environment in which to study and learn real mathemat-ics.Thefirst author also thanks the entire Brooklyn College family and,in partic-ular,the Computer and Information Science Department for being supportive andvery helpful in this endeavor.1See page1349of Bass et al.(1998).More informationxvi PrefaceSeveral faculty members of Brooklyn College and The Graduate Center were kind enough to read and comment on parts of this book:Michael Anshel,DavidArnow,Jill Cirasella,Dayton Clark,Eva Cogan,Jim Cox,Scott Dexter,EdgarFeldman,Fred Gardiner,Murray Gross,Chaya Gurwitz,Keith Harrow,JunHu,Yedidyah Langsam,Peter Lesser,Philipp Rothmaler,Chris Steinsvold,AlexSverdlov,Aaron Tenenbaum,Micha Tomkiewicz,Al Vasquez,Gerald Weiss,andPaula Whitlock.Their comments have made this a better text.Thank you all!We were fortunate to have had many students of Brooklyn College and The Graduate Center read and comment on earlier drafts:Shira Abraham,RachelAdler,Ali Assarpour,Aleksander Barkan,Sayeef Bazli,Cheuk Man Chan,WeiChen,Evgenia Dandurova,Phillip Dreizen,C.S.Fahie,Miriam Gutherc,RaveHarpaz,David Herzog,Alex Hoffnung,Matthew P.Johnson,Joel Kammet,SerdarKara,Karen Kletter,Janusz Kusyk,Tiziana Ligorio,Matt Meyer,James Ng,SeverinNgnosse,Eric Pacuit,Jason Schanker,Roman Shenderovsky,Aleksandr Shnayder-man,Rose B.Sigler,Shai Silver,Justin Stallard,Justin Tojeira,John Ma Sang Tsang,Sadia Zahoor,Mark Zelcer,and Xiaowen Zhang.We are indebted to them.Many other people looked over parts or all of the text:Scott Aaronson,Ste-fano Bettelli,Adam Brandenburger,Juan B.Climent,Anita Colvard,Leon Ehren-preis,Michael Greenebaum,Miriam Klein,Eli Kravits,Raphael Magarik,JohnMaiorana,Domenico Napoletani,Vaughan Pratt,Suri Raber,Peter Selinger,EvanSiegel,Thomas Tradler,and Jennifer Whitehead.Their criticism and helpful ideasare deeply appreciated.Thanks to Peter Rohde for creating and making available to everyone his MAT-LAB q-emulator Quack and also for letting us use it in our appendix.We had a gooddeal of fun playing with it,and we hope our readers will too.Besides writing two wonderful appendices,our friendly neighborhood librar-ian,Jill Cirasella,was always just an e-mail away with helpful advice and support.Thanks,Jill!A very special thanks goes to our editor at Cambridge University Press,HeatherBergman,for believing in our project right from the start,for guiding us through thisbook,and for providing endless support in all matters.This book would not existwithout her.Thanks,Heather!We had the good fortune to have a truly stellar editor check much of the text many times.Karen Kletter is a great friend and did a magnificent job.We also ap-preciate that she refrained from killing us every time we handed her altered draftsthat she had previously edited.But,of course,all errors are our own!This book could not have been written without the help of my daughter,Hadas-sah.She added meaning,purpose,and joy.N.S.Y.My dear wife,Rose,and our two wondrous and tireless cats,Ursula and Buster, contributed in no small measure to melting my stress away during the long andpainful hours of writing and editing:to them my gratitude and love.(Ursula is ascientist cat and will read this book.Buster will just shred it with his powerful claws.)M.A.M.。
中科院考博英语真题200203

中国科学院2002年3月博士研究生入学考试试题PAPT Ⅱ STRUCTURE & VOCABULARY (25 minutes, 15 points)Section A (0.5 point each)Directions: Choose the word or words below each sentence that best complete the statement, and mark the corresponding letter of your choice with a single bar across the square brackets on your Machine scoring Answer Sheet.16. Knowing that the cruel criminal has done a lot of unlawful things, I feel sure that I have no__________ but to report him to the local police.A. timeB. chanceC. authorityD. alternative17. Behind his large smiles and large cigars, his eyes often seemed to _______regret.A. teem withB. brim withC. come withD. look with18. There is only one difference between an old man and a young one: the young one has aglorious future before him and the old one has a __________future behind him.A. splendidB. conspicuousC. uproariousD. imminent19. That tragedy distressed me so much that I used to keep indoors and go out only __________necessity.A. within reach ofB. for fear ofC. by means ofD. in case of20. A young man sees a sunset and, unable to understand or express the emotion that it__________in him, concludes that it must be the gateway to a world that lies beyond.A. reflectsB. retainsC. rousesD. radiates21. __________the heat to a simmer and continue to cook for another 8-10 minutes or until mostof the water has evaporated.A. Turn offB. Turn overC. Turn downD. Turn up22. Banks shall be unable to__________, or claim relief against the first 15% of any loan orbankrupted debt left with them.A. write offB. put asideC. shrink fromD. come over23. I am to inform you, that you may, if you wish, attend the inquiry, and at the inspectorsdiscretion state your case __________or through an entrusted representative.A. in personB. in depthC. in secretD. in excess24. In his view, though Hong Kong has no direct cultural identity, local art is thriving by “being__________,”being open to all kinds of art.A. gratifyingB. predominatingC. excellingD. accommodating25. In some countries preschool education in nursery schools or kindergartens _________the lstgrade.A. leadsB. precedesC. forwardsD. advances26. Desert plants __________two categories according to the way they deal with the problem ofsurviving drought.A. break downB. fall intoC. differ inD. refer to27. In the airport, I could hear nothing except the roar of aircraft engines which _____all othersounds.A. dwarfedB. diminishedC. drownedD. devastated28. Criticism without suggesting areas of improvement is not __________and should be avoidedif possible.A. constructiveB. productiveC. descriptiveD. relative29. The Committee pronounced four members expelled for failure to provide information in the__________of investigations.A. caseB. chaseC. causeD. course30. Since neither side was ready to _____what was necessary for peace, hostility was resumed in1980.A. precedeB. recedeC. concedeD. intercede31. Such an __________act of hostility can only lead to war.A. overtB. episodicC. ampleD. ultimate32. __________both in working life and everyday living to different sets of values, andexpectations places a severe strain on the individual.A. RecreationB. TransactionC. DisclosureD. Exposure33. It would then be replaced by an interim government, which would __________be replaced bya permanent government after four months.A. in stepB. in turnC. in practiceD. in haste34. Haven't I told you I don't want you keeping _______with those awful riding-about bicycleboys?A. companyB. acquaintanceC. friendsD. place35. Consumers deprived of the information and advice they needed were quite simply________every cheat in the marketplace.A. at the mercy ofB. in lieu ofC. by courtesy ofD. for the price ofPART Ⅲ CLOZE TEST (15 minutes, 15 points)Directions: There are 15 questions in this part of the test. Read the passage through. Then, go back and choose one suitable word or phrase marked A, B, C or D for each blank in the passage. Mark the corresponding letter of the word or phrase you have chosen with a single bar across the square brackets on your Machine-scoring Answer Sheet.At least since the Industrial Revolution, gender roles have been in a state of transition. As a result, cultural scripts about marriage have undergone change. One of the more obvious__46__has occurred in the roles that women__47__. Women have moved into the world of work and have become adept at meeting expectations in that arena,__48__maintaining their family roles of nurturing and creating a (n)__49__that is a haven for all family members.__50__many women experience strain from trying to “do it all,” they often enjoy t he increased__51__that can result from playing multiple roles. As women's roles have changed, changing expectations about men's roles have become more__52__. Many men are relinquishing their major responsibility__53__the family provider. Probably the most significant change in men's roles, however, is in the emotional__54__of family life. Men are increasingly__55__to meet the emotional needs of their families,__56__their wives.In fact, expectations about the emotional domain of marriage have become more significant for marriage in general. Research on__57__marriage has changed over recent decades points to the increasing importance of the emotional side of the relationships and the importance of sharing in the “emotion work”__58__to nourish marriages and other famil y relationships. Men and women want to experience marriages that are interdependent,__59__both partners nurture each other, attend and respond to each other, and encourage and promote each other. We are thus seeingmarriages in which men's and women's roles are becoming increasingly more__60__.46. A. incidents B. changes C. results D. effects47. A. take B. do C. play D. show48. A. by B. while C. hence D. thus49. A. home B. garden C. arena D. paradise50. A. When B. Even though C. Since D. Nevertheless51. A. rewards B. profits C. privileges D. incomes52. A. general B. acceptable C. popular D. apparent53. A. as B. of C. from D. for54. A. section B. constituent C. domain D. point55. A. encouraged B. expected C. advised D. predicted56. A. not to mention B. as will as C. including D. especially57. A. how B. what C. why D. if58. A. but B. only C. enough D. necessary59. A. unless B. although C. where D. because60. A. pleasant B. important C. similar D. manageablePART ⅣREADING COMPREHENSION (60 minutes, 30 points)Directions: Below each of the following passages you will find some questions or incomplete statements. Each question or statement is followed by four choices marked A, B, C and D. Read each passage carefully, and then select the choice that best answers the question square brackets on your Machine scoring Answer Sheet.Passage 1The man who invented Coca-cola was not a native Atlantan, but on the day of his funeral every drugstore in town testimonially shut up shop. He was John Styth Pemberton, born in 1883 in Knoxville, Georgia, eighty miles away. Sometimes known as Doctor, Pemberton was a pharmacist who,during the Civil War, led a cavalry troop under General Joe Wheeler. He settled in Atlanta in 1869, and soon began brewing such patent medicines as Triplex liver Pills and Globe of Flower Cough Syrup. In 1885, he registered a trademark for something called French Wine Coca—Ideal Nerve and Tonic Stimulant; a few months later he formed the Pemberton Chemical Company and recruited the services of a bookkeeper named Frank M. Robinson, who not only had a good head for figures but, attached to it, so exceptional a nose that he could audit the composition of a botch of syrup merely by sniffling it. In 1886—year in which, as contemporary Coca-Cola officials like to point out, Conan Doyle unveiled Sherlock Holmes and France unveiled the Statue of Liberty—Pemberton unveiled a syrup that he called Coca-Cola. It was a modification of his French Wine Coca. He had taken out the wine and added a pinch of caffeine, and, when the end product tasted awful, had thrown in some extract of cola nut and a few other oils, blending the mixture in a three-legged iron pot in his back yard and swishing it around with an oar. He distributed it to soda fountains in used beer bottles, and Robinson, with his flowing bookkeeper's script, presently devised a label, on which “Coca-Cola” was written in the fashion that is still employed. Pemberton looked upon his mixture less as a refreshment than as a headache cure, especially for people whose headache could be traced to over-indulgence.On a morning late in 1886, one such victim of the night before dragged himself into an Atlanta drugstore and asked for a dollop of Coca-Cola. Druggists customarily stirred a teaspoonful of syrup into a glass of water, but in this instance the man on duty was too lazy to walk to thefresh-water tap, a couple of feet off. Instead, he mixed the syrup with some soda water, which was closer at hand. The suffering customer perked up almost at once, and word quickly spread that the best Coca-Cola was a fizzy one.61. What does the passage tell us about John Styth Pemberton?A. He was highly respected by Atlantans.B. He ran a drug store that also sells wine.C. He had been a doctor until the Civil War.D. He made a lot of money with his pharmacy.62. Which of the following was unique to Frank M. Robinson, working with the Pemberton'sCompany?A. Skills to make French wine.B. He ran a drug store that also sells wine.C. He had been a doctor until the Civil War.D. Ability to work with numbers.63. Why was the year 1886 so special to Pemberton?A. He took to doing a job like Sherlock Holmes's.B. He brought a quite profitable product into being.C. He observed the founding ceremony of Statue of Liberty.D. He was awarded by Coca-Cola for his contribution.64. One modification made of French Wine Coca formula was__________.A. used beer bottles were chosen as containersB. the amount of caffeine in it was increasedC. it was blended with oils instead of waterD. Cola nut extract was added to taste65. According to the passage, Coca-Cola was in the first place prepared especially for__________.A. the young as a soft drinkB. a replacement of French Wine CocaC. the relief of a hangoverD. a cure for the common headache66. The last paragraph mainly tells__________.A. the complaint against the lazy shop-assistantB. a real test of Coca-Cola as a headache cureC. the mediocre service of the drugstoreD. a happy accident that gave birth to Coca-ColaPassage 2Between 1883 and 1837, the publishers of a “penny press” proved that a low-priced paper, edited to interest ordinary people, could win what amounted to a mass circulation for the times and thereby attract an advertising volume that would make it independent. These were papers for the common citizen and were not tied to the interests of the business community, like the mercantile press, or dependent for financial support upon political party allegiance. It did not necessarily follow that all the penny papers would be superior in their handling of the news and opinion functions. But the door was open for some to make important journalistic advances.The first offerings of a penny paper tended to be highly sensational; human interest storiesovershadowed important news, and crime and sex stories were written in full detail. But as the penny paper attracted readers from various social and economic brackets, its sensationalism was modified. The ordinary reader came to want a better product, too. A popularized style of writing and presentation of news remained, but the penny paper became a respectable publication that offered significant information and editorial leadership. Once the first of the successful penny papers had shown the way, later ventures could enter the competition at the higher level of journalistic responsibility the pioneering papers had reached.This was the pattern of American newspapers in the years following the founding of the New York sun in 1833. The Sun, published by Benjamin Day, entered the lists against 11 other dailies. It was tiny in comparison; but it was bright and readable, and it preferred human interest features to important but dull political speech reports. It had a police reporter writing squibs of crime news in the style already proved successful by some other papers. And, most important, it sold for a penny, whereas its competitors sold for six cents. By 1837 the Sun was printing 30,000 copies a day, which was more than the total of all 11 New York daily newspapers combined when the Sun first appeared. In those same four years James Gordon Bennett brought out his New York Herald (1835), and a trio of New York printers who were imitating Day's success founded the Philadelphia Public Ledger (1836) and the Baltimore Sun (1837). The four penny sheets all became famed newspapers.67. What does the first p aragraph say about the “penny press?”A. It was known for its in-depth news reporting.B. It had an involvement with some political parties.C. It depended on the business community for survival.D. It aimed at pleasing the general public.68. In its early days, a penny paper often__________.A. paid much attention to political partiesB. provided stories that hit the pubic tasteC. offered penetrating editorials on various issuesD. covered important news with inaccuracy69. As the readership was growing more diverse, the penny paper__________.A. improved its contentB. changed its writing styleC. developed a more sensational styleD. became a tool for political parties70. The underlined word “ventures” in Paragraph 2 can best be replaced by__________.A. editorsB. reportersC. newspapersD. companies71. What is true about the Philadelphia Public Ledger and the Baltimore Sun?A. They turned out to be failures.B. They were later purchased by James Gordon Bennett.C. They were also founded by Benjamin Day.D. They became well-known newspapers in the U.S.72. This passage is probably taken from a book on__________.A. the work ethics of the American mediaB. the technique in news reportingC. the history of sensationalism in American mediaD. the impact of mass media on American societyPassage 3Forget what Virginia Woolf said about what a writer needs—a room of one‟s own. The writer she has in mind wasn't at work on a novel in cyberspace, one with multiple hypertexts, animated graphics and downloads of trancey, charming music. For that you also need graphic interfaces, RealPlayer and maybe even a computer laboratory at Brown University. That was where Mark Amerika—his legally adopted name; don't ask him about his birth name—composed much of his novel Grammatron isn't just a story. It's an online narrative(grammatron. com) that uses the capabilities of cyberspace to tie the conventional story line into complicated knots. IN the four years it took to produce—it was completed in 1997—each new advance in computer software became another potential story device. “I became sort of dependent on the industry,” jokes Amerika, who is also the author of two novels printed on paper. “That's unusual for a writer, because if you just write on paper the …technology‟is pretty stable.”Nothing about Grammatron is stable. At its center, if there is one, is Abe Golam, the inventor of Nanoscript, a quasi-mystical computer code that some unmystical corporations are itching to acquire. For much of the story, Abe wanders through Prague-23, a virtual“city” in cyberspace where visitors indulge in fantasy encounters and virtual sex, which can get fairly graphic. The reader wanders too, because most of Grammatron's 1,000-plus text screens contain several passages in hypertext. To reach the next screen just double-click. But each of those hypertexts is a trapdoor that can plunge you down a different pathway of the story. Choose one and you drop into a corporate-strategy memo. Choose another and there's a XXX-rated sexual rant. The story you read is in some sense the story you make.Amerika teaches digital art at the University of Colorado, where his students develop works that straddle the lines between art, film and literature. “I tell them not to get ca ught up in mere plot,” he says. Some avant-garde writers-Julio Cortazar, Italo Calvino-have also experimented with novels that wander out of their author's control. “But what makes the Net so exciting,” says Amerika, “is that you can add sound, randomly ge nerated links, 3-D modeling, animation.” That room of one's own is turning into a fun house.73. The passage is mainly to tell__________.A. differences between conventional and modern novelsB. how Mark Amerika composed his novel GrammatronC. common features of all modern electronic novelsD. why mark Amerika took on a new way of writing74. Why does the author ask the reader to forget what Virginia Woolf said about the necessities ofa writer?A. Modern writers can share rooms to do the writing.B. It is not necessarily that a writer writes inside a room.C. Modern writers will get nowhere without a word processor.D. It is no longer sufficient for the writing in cyberspace.75. As an on-line narrative, Grammatron is anything but stable because it__________.A. provides potentials for the story developmentB. is one of the novels at grammatron. comC. can be downloaded free of chargeD. boasts of the best among cyber stories76. By saying that he became sort of dependent on the industry, Mark Amerika meant that ______.A. he could not help but set his Grammatron and others in Industrial RevolutionB. conventional writers had been increasingly challenged by high technologyC. much of his Grammatron had proved to be cybernetic dependentD. he couldn't care less new advance in computer software77. As the passage shows, Grammatron makes it possible for readers to__________.A. adapt the story for a video versionB. “walk in” the story and interact with itC. develop the plots within the author's controlD. steal the show and become the main character78. Amerika told his students not to__________.A. immerse themselves only in creating the plotB. be captivated by the plot alone while readingC. be lagged far behind in the plot developmentD. let their plot get lost in the on-going storyPassage 4In 1993, a mall security camera captured a shaky image of two 10-year-old boys leading much smaller boy out of a Liverpool, England, shopping center. The boys lured James Bulger, 2,away from his mother, who was shopping, and led him on a long walk across town. The excursion ended at a railroad track. There, inexplicably, the older boys tortured the toddler, kicking him, smearing paint on his face and pummeling him to death with bricks before leaving him on the track to be dismembered by a train. The boys, Jon Venables and Robert Thompson, then went off to watch cartoon.Today the boys are 18-year-old men, and after spending eight years in juvenile facilities, they have been deemed fit for release-probably this spring. The dilemma now confronting the English justice system is how to reintegrate the notorious duo into a society that remains horrified by their crimes and skeptical about their rehabilitation. Last week Judge Elizabeth Butler-Sloss decided the young men were in so much danger that they needed an unprecedented shield to protect them upon release. For the rest of their lives, Venables and Thompson will have a right to anonymity. All English madia outlets are banned from publishing any information about their whereabouts or the new identities the government will help them establish. Photos of the two or even details about their current looks art also prohibited.In the U. S., which is harder on juvenile criminals than England, such a ruling seems inconceivable. “We're clearly the most punitive in the industrialized world,” says Laurence Steinberg, a Temple University professor who studies juvenile justice. Over the past decade, the trend in the U. S. has been to allow publication of ever more information about underage offenders. U. S. courts also give more weight to press freedom than English courts, which, for example, ban all video cameras.But even for Britain, the order is extraordinary. The victim's family is enraged, as are the ever-eager British tabloids. “What right have they got to be given special protection as adults?” asks Bulger's mother Denise Fergus. Newspaper editorials have insisted that citizens have a right to know if Venables or Thompson move in next door. Says conservative Member of Parliament Humfrey Malins:“It almost leaves you with the feeling that the nastier the crime, the greater the chance for a passpor to a completely new life.”79. What occurred as told at the beginning of the passage?A. 2 ten-year-olds killed James by accident in play.B. James Bulger was killed by his two brothers.C. Two mischievous boys forged a train accident.D. A little kid was murdered by two older boys.80. According to the passage, Jon Venables and Robert Thompson__________.A. have been treated as juvenile delinquentsB. have been held in protective custody for their murder gameC. were caught while watching cartoons eight years agoD. have already served out their 10 years in prison81. The British justice system is afraid that the two young men would__________.A. hardly get accustomed to a horrifying general publicB. be doomed to become social outcasts after releaseC. still remain dangerous and destructive if set freeD. be inclined to commit a recurring crime82. According to the British courts, after their return to society, the two adults will be__________.A. banned from any kind of press interviewB. kept under constant surveillance by policeC. shielded from being identified as killersD. ordered to report to police their whereabouts83. From the passage we can infer that a US counterpart of Vanables or Thompson would__________.A. have no freedom to go wherever he wantsB. serve a life imprisoment for the crimeC. be forbidden to join many of his relativesD. no doubt receive massive publicity in the U. S.84. As regards the mentioned justice ruling, the last paragraph mainly tells that__________.A. it is controversial as it goes without precedentB. the British media are sure to do the contraryC. Bulger's family would enter all appeal against itD. conservatives obviously conflict with LiberalsPassage 5Can the Internet help patients jump the line at the doctor's office? The Silicon Valley Employers Forum, a sophisticated group of technology companies, is launching a pilot program to test online “virtual visits” between doctors at three big local medical groups about and 6,000 employees and their families. The six employers taking part in the Silicon Valley initiative, including heavy hitters such as Oracle and Cisco Systems, hope that online visits will mean employees won't have to skip work to tend to minor ailments or to follow up on chronic conditions. “Which our long commutes and traffic, driving 40 miles to your doctor in your hometown can be a big chunk of time,” says Cindy Conway, benefits director at Cadence Design Systems, one of the participating companies.Doctors aren't clamoring to chat with patients online for free; they spend enough unpaid time on the phone. Only 1 in 5 has ever E-mailed a patient, and just 9 percent are interested in doing so,according to the research firm Cyber Dialogue. “We are not stupid,” says Stirling Somers, executive director of the Silicon Valley employers group. “Doctors getting paid is a critical p iece in getting this to work.” In the pilot program, physicians will get $ 20 per online consultation, obout what they get for a simple office visit.Doctors also fear they'll be swamped by rambling E-mails that tell everything but what's needed to make a diagnosis. So the new program will use technology supplied by Healinx, an Alameda, Calif—based start-up. Healinx's “Smart Symptom Wizard” questions patients and turns answers into a succinct message. The company has online dialogues for 60 common conditions. The doctor can then diagnose the problem and outline a treatment plan, which could include E-mailing a prescription or a face-to-face visit.Can E-mail replace the doctor's office? Many conditions, such as persistent cough, require stethoscope to discover what's wrong-and to avoid a malpractice suit. Even Larry Bonham, head of one of the doctor's groups in the pilot, believes the virtual doctor's visits offer a “very narrow” sliver of service between phone calls to an advice nurse and a visit to the clinic.The pilot program, set to end in nine months, also hopes to determine whether online visits will boost worker productivity enough to offset the cost of the service. So far, the Internet's record in the health field has been underwhelming. The experi ment is “a huge roll of the dice for Healinx”, notes Michael Barrett, an analyst at Internet consulting firm Forester Research. If the “Web visits” succeed, expect some HMOs (Health Maintenance Organizations) to pay for online visits. If doctors, employers, and patients aren't satisfied, figure on one more E-health start-up to stand down.85. The Silicon Valley employers promote the E-health program for the purpose of__________.A. rewarding their employeesB. gratifying the local hospitalsC. boosting worker productivityD. testing a sophisticated technology86. What can be learned about the on-line doctors' visits?A. They are a quite promising business.B. They are funded by the local government.C. They are welcomed by all the patients.D. They are very much under experimentation.87. Of the following people, who are not involved in the program?A. Cisco System employees.B. Advice nurses in the clinic.C. Doctors at three local hospitals.D. Oracle at three local hospitals.88. According to Paragraph 2, doctors are__________.A. reluctant to serve online for nothingB. not interested in Web consultationC. too tired to talk to the patients onlineD. content with $ 20 paid per Web visit89. “Smart Symptom Wizard” is capable of__________.A. making diagnosesB. producing prescriptionsC. profiling patients's illnessD. offering a treatment plan90. It can be inferred from the passage that the future of online visits will mostly depend onwhether__________.A. the employers would remain confident in themB. they could effectively replace office visitsC. HMOs would cover the cost of the serviceD. new technologies would be available to improve the E-health projectPAPER TWOPART ⅤTRANSLATION (25 minutes, 10 points)Directions: Put the following passage into English. Write your English version in the proper space on your Answer Sheet Ⅱ.伟大艺术的美学鉴赏和伟大的科学观念的理解都需要智慧。
清华大学本科计算机课程介绍

课号:00240013 学分: 3 课程名称 中文 课程属性:全校任选 英文 开课学期:秋、春 Fundamentals of Computer-aided Design 出版社 清华大学出版社 出版年月 2002 年 8 月
计算机辅助设计技术基础 书名 作者
使用教材
计算机辅助设计技术基 础教程
本课程是计算机科学与技术系为全校本科生开设的一门重要的计算机专业基础 课,目的是培养学生的软件工程素质,提高学生的软件开发能力。 本课程以软件生命周期的主要活动为主线,从软件及软件工程的历史和发展、软 件开发过程、需求分析、软件设计、程序编码、软件测试、软件维护、软件项目管理、 标准及规范等方面全面介绍软件工程的基本理论、方法、技术和工具。
课号: 30240273 课程名称
学分: 3 中文
课程属性:本科必修 开课学期: 春季 数据结构 书名 作者 英文 Data Structure 出版社 出版年月 1997
使用教材 参考书 讲课对象 课 程 简 介
数据结构(C 语言版)
严蔚敏,吴伟民 清华大学出版社
[1] Kruse, et.al. Data Structures & Program Desing in C. [2] Knuth. The Art of Computer Programming. Volume 1. 本科生 适用专业 工业工程系 先修课 C 语言程序设计
This course focuses on the basic concepts, principles, algorithms and applications of computer-aided design(CAD), it mainly consists of the following topics: software and hardware system of CAD, two-dimensional transformations, line clipping, raster display of 2D graphics, curves Introduction and surfaces, solid modeling, three-dimensional transformations, three-dimensional viewing, visible-surface determination, basic illumination models, and introductions to AutoCAD, 3DMAX 5.0 and OpenGL. It is an ideal choice for students who want to learn the rudiments of this dynamic and exciting CAD technology. 姓 名 讲 课 教 师 职称 主要教学和科研领域 主要教学领域: (1)承担全校计算机辅助设计技术基础 课教学; (2)承担研究生的小波分析及其应用课教学; 主要研究领域:小波分析及其应用,科学计算可视化, 计算机图形学,几何造型和图象处理。 (1)承担全校计算机辅助设计技术基础课教学
