NETAPP存储防火墙端口-典型NAS环境下的网络需求
家庭nas 网络安全

家庭nas 网络安全家庭NAS(Network Attached Storage)网络安全随着互联网的普及和家庭网络的发展,越来越多的家庭开始使用家庭NAS来存储和共享家庭文件。
然而,与此同时,家庭网络也面临着越来越多的网络安全威胁。
因此,在家庭NAS的网络安全方面,家庭用户需要加强安全意识,采取一些措施来保护家庭网络的安全。
首先,家庭用户应该注意家庭NAS的更新和升级。
随着网络安全技术的不断进步,家庭NAS的系统也需要及时更新和升级,以修复已知的安全漏洞。
家庭用户应该定期检查家庭NAS的系统是否有可用的更新和升级版本,并及时进行升级,以提高家庭网络的安全性。
其次,家庭用户需要设置强密码来保护家庭NAS的安全。
强密码应包含足够的字符长度和复杂性,如包含大小写字母、数字和特殊字符。
此外,家庭用户还应定期更改密码,避免使用与其他账户相同的密码。
这样可以防止黑客通过猜测密码或使用密码破解工具来入侵家庭NAS,保护家庭网络的安全。
另外,家庭用户还可以考虑使用VPN(Virtual Private Network)来加密家庭网络的数据传输。
VPN可以在家庭网络和互联网之间建立一个加密通道,使得家庭网络的数据传输更加安全。
家庭用户可以选择购买一台具有VPN功能的路由器,或者使用第三方VPN服务提供商的应用程序来保护家庭网络的安全。
此外,家庭用户还需要注意社交工程和钓鱼攻击等网络安全威胁。
社交工程是指黑客通过伪装身份和欺骗手段来获取用户的个人信息和登录凭证。
而钓鱼攻击则是指黑客通过发送伪装成合法机构的电子邮件或信息来诱骗用户点击恶意链接或下载恶意文件。
家庭用户应该提高警惕,避免随意点击可疑链接或下载未经验证的文件。
最后,家庭用户还可以考虑安装防火墙和安全软件来保护家庭网络的安全。
防火墙可以监控和控制家庭网络流量,阻止未经授权的访问。
安全软件可以检测和阻止恶意软件的安装,保护家庭网络免受病毒和恶意软件的攻击。
综上所述,家庭用户在使用家庭NAS时,需要加强网络安全意识,采取一些措施来保护家庭网络的安全。
群晖NAS服务对应的端口

群晖NAS服务对应的端口群晖NAS(Network Attached Storage)是一款由Synology公司开发的网络存储设备,它运行着群晖DiskStation Manager(DSM)操作系统,为用户提供高性能、可靠和可扩展的存储解决方案。
在使用群晖NAS 时,需要进行端口映射以允许外部网络访问NAS的各项服务。
下面是一些常用的群晖NAS服务及其对应的端口:1.文件传输服务:-文件传输协议(FTP):默认端口号为21(TCP)。
-可扩展文件传输协议(SFTP):默认端口号为22(TCP)。
-文件传输协议(TFTP):默认端口号为69(UDP)。
-网络文件系统(NFS):默认端口号为2049(TCP和UDP)。
2.网络备份服务:-网络备份协议(NBP):默认端口号为118(TCP)。
-倒置摘要备份(IDB):默认端口号为2501(UDP)。
- 远程数据备份(Rsync):默认端口号为873(TCP)。
3.网络文件共享服务:-服务器消息块(SMB):默认端口号为445(TCP)。
-网络文件系统(NFS):默认端口号为111(TCP和UDP)。
4.远程访问服务:-远程桌面协议(RDP):默认端口号为3389(TCP和UDP)。
-虚拟网络计算(VNC):默认端口号为5900(TCP和UDP)。
5. Web服务:-HTTP:默认端口号为80(TCP)。
-HTTPS:默认端口号为443(TCP)。
6.容器服务:- Docker:默认端口号为2375(TCP)。
7.多媒体服务:-媒体服务器控制协议(DLNA):默认端口号为1900(UDP)。
-媒体流传输协议(RTSP):默认端口号为554(TCP和UDP)。
8.数据库服务:-MySQL:默认端口号为3306(TCP和UDP)。
需要注意的是,以上列举的是一些常见的群晖NAS服务及其对应的默认端口号,实际使用时可能会根据具体的设置和需求进行修改。
此外,对于远程访问NAS设备的端口映射,需要将路由器上的公网IP地址映射到NAS设备的内部IP地址,并在路由器上设置端口转发规则,将外部访问请求转发到NAS设备的相应服务端口上。
NETAPP存储防火墙端口-典型NAS环境下的网络需求

网络需求所有需要执行SnapMirror数据复制的存储之间,需打开以下端口:NetApp FAS存储支持通过网络同步时钟。
如果存储和NTP服务器之间有防火墙,则打开以下端口:所有被管理的存储,必须通过IP网络与DFM服务器连通。
如果存储和DFM服务器之间有防火墙,则打开以下端口:如果有Windows机器需要管理(例如,客户端安装了OSSV备份软件),则Windows机器需要通过IP网络与DFM服务器连通。
如果Windows机器和DFM服务器之间有防火墙,则打开以下端口:启用DFM的autosupport功能,需要DFM服务器和邮件服务器连通;并且服务器需要一个不需密码验证的发送邮件的账号。
如果邮件服务器和DFM服务器之间有防火墙,则打开以下端口:附录:DOT 7.2使用的IP端口IP port usage on a storage systemAbout this appendixThis appendix describes the Data ONTAP services file that is available in the /etc directory. The /etc/services file is in the same format as its corresponding UNIX systems /etc/services file. Although this file is it not used by Data ONTAP, it is provided in this appendix as information useful to system administrators. Host identificationAlthough some port scanners are able to identify storage systems as storage systems, others port scanners report storage systems as unknown types, UNIX systems because of their NFS support, or Windows systems because of their CIFS support. There are several services that are not currently listed in the /etc/services file.Below is an example of a complete list of the file contents./etc/services NNTP and TTCP portsThe nntp and ttcp ports are unused by your storage system and should never be detected by a port scanner.Ports found in a block starting around 600The following ports are found on the storage system with NFS enabled:On other systems, the ports appear as follows:Enter the following command on UNIX systems to obtain the correct information by querying the port mapper on port 111:toaster# rpcinfo -p .or.ip.address program vers proto port service100011 1 udp 608 rquotad100021 4 tcp 607 nlockmgr100021 3 tcp 607 nlockmgr100021 1 tcp 607 nlockmgr100021 4 udp 606 nlockmgr100021 3 udp 606 nlockmgr100021 1 udp 606 nlockmgr100024 1 tcp 605 status100024 1 udp 604 status100005 3 tcp 603 mountd100005 2 tcp 603 mountd100005 1 tcp 603 mountd100005 3 udp 602 mountd100005 2 udp 602 mountd100005 1 udp 602 mountd100003 3 udp 2049 nfs100003 2 udp 2049 nfs100000 2 tcp 111 rpcbind100000 2 udp 111 rpcbindNoteThe port numbers listed for mountd, statd, lockd, and quotad are not committed port numbers. Storage systems can have these services running on other port numbers. Because the system selects these port numbers at random when it boots, they are not listed in the /etc/services file.Other ports not listed in /etc/servicesThe following ports appear in a port scan but are not listed in /etc/services file.NoteDisable open ports that you do not need.FTP•ftp-data•ftpFile transfer protocol (FTP) uses TCP ports 20 and 21. For a detailed description of the FTP support for your storage system, see the Data ONTAP File Access and Protocols Management Guide. If you use FTP to transfer filesto and from your storage system, the FTP port is required; otherwise, use FilerView or the following CLI command to disable the FTP port:options ftpd.enable offFTP is not a secure protocol for two reasons:•When users log in to the system, user names and passwords are transmitted over the network in clear text format that can easily be read by a packet sniffer program.These user names and passwords can then be used to access data and other network resources. You should establish and enforce policies that prevent the use of the same passwords to access storage systems and other network resources.•FTP server software used on platforms other than storage systems contains serious security-related flaws that allow unauthorized users to gain administrative (root) access and control over the host.SSH•sshSecure Shell (SSH) protocol is a secure replacement for RSH and runs on TCP port 22. This only appears in a port scan if the SecureAdmin TM software is installed on your storage system.There are three commonly deployed versions of the SSH protocol:•SSH version 1--is much more secure than RSH or Telnet, but is vulnerable to TCP session attacks.This vulnerability to attack lies in the SSH protocol version 1 itself andnot in the associated storage system products.•SSH version 2--has a number of feature improvements over SSH version 1 and is less vulnerable to attacks.•SSH version 1.5--is used to identify clients or servers that support both SSH versions 1 and 2.To disable SSH support or to close TCP port 22, use the following CLI command:secureadmin disable sshTelnet•telnetTelnet is used for administrative control of your storage system and uses TCP connections on port 23. Telnet is more secure than RSH, as secure as FTP, and less secure than SSH or Secure Socket Layer (SSL).Telnet is not secure because:•When users log into a system, such as your storage system, user names and passwords are transmitted over the network in clear text format.Clear text format can be read by an attacker using a packet snifferprogram. The attacker can use these user names and passwords to log in to your storage system and execute unauthorized administrativefunctions, including destruction of data on the system. If theadministrators use the same passwords on your storage system as they do on other network devices, the attacker can use these passwords toaccess those resources as well.NoteTo reduce the potential for attack, establish and enforce policiespreventing administrators from using the same passwords on yourstorage system that they use for access to other network resources.•Telnet server software used on other platforms (typically in UNIX environments) have serious security-related flaws that allow unauthorized users to gain administrative (root) control over the host.Telnet is also vulnerable to the same type of TCP session attacks as SSH protocol version 1, but because a packet sniffing attack is easier, TCP session attacks are less common.To disable Telnet, set options telnet.enable to off.SMTP•smtpThe Simple Mail Transport Protocol (SMTP) uses TCP port 25. Your storage system does not listen on this port but makes outgoing connections to mail servers using this protocol when sending AutoSupport e-mail.Time service•time•ntpYour storage system supports two different time service protocols:•TIME protocol (also known as rdate) is specified in the RFC 868 standard. This standard allows for time services to be provided on TCP or UDP port 37. Your storage systemuses only UDP port 37.•Simple network time protocol (NTP) is specified in the RFC 2030 standard and is provided only on UDP port 123.When your storage system has option timed.enable set to On and a remote protocol (rdate or ntp) is specified, the storage system synchronizes to a network time server.If the timed.enable option is set to Off, your storage system is unable to synchronize with the network time server using NTP. The rdate time protocol can still be used by manually issuing the rdate command from your storage system console.You should set the timed.enable option to On in a cluster configuration. DNS•domainThe Domain Name Service (DNS) uses UDP port 53 and TCP port 53. Your storage system does not typically listen on these ports because it does not run a domain name server. However, if DNS is enabled on your storage system, it makes outgoing connections using UDP port 53 for host name and IP address lookups. Your storage system never uses TCP port 53 because this port is used explicitly for communication between DNS servers. Outgoing DNS queries by your storage system are disabled by turning off DNS support. Turning off DNS support protects against receiving bad information from another DNS server.Because your storage system does not run a domain name server, the name service must be provided by one of the following:•Network information service (NIS)•An/etc/hosts file•Replacement of host names in the configuration files (such as /etc/exports, /etc/usermap.cfg, and so on) with IP addressesDNS must be enabled for participation in an Active Directory domain. DHCP•dhcpsClients broadcast messages to the entire network on UDP port 67 and receive responses from the Dynamic Host Configuration Protocol (DHCP) server on UDP port 68. The same ports are used for the BOOTP protocol.DHCP is used only for the first-time setup of your storage system. Detection of DHCP activity on your storage system by a port scan other than the activity during the first-time setup indicates a serious configuration or software error. TFTP•tftpTrivial File Transfer Protocol (TFTP) uses TCP port 69. It is used mostly for booting UNIX or UNIX-like systems that do not have a local disk (this process is also known as netbooting) and for storing and retrieving configuration files for devices such as Cisco routers and switches.Transfers are not secure on TFTP because it does not require authentication for clients to connect and transfer files.Your storage system's TFTP server is not enabled by default. When TFTP is enabled, the administrator must specify a directory to be used by TFTP clients, and these clients cannot access other directories. Even within the TFTP directory, access is read-only. TFTP should be enabled only if necessary. Disable TFTP using the following option:options tftpd.enable offHTTP•httpHypertext Transport Protocol (HTTP) runs on TCP port 80 and is the protocol used by web browsers to access web pages. Your storage system uses HTTP to access•Files when the HTTP protocol is enabled•FilerView for Graphical User Interface (GUI) administration•Secure FilerView when SecureAdmin is installedThe SecureAdmin SSL interface accepts connections on TCP port 443. SecureAdmin manages the details of the SSL network protocol, encrypts the connection, and then passes this traffic through to the normal HTTP FilerView interface through a loopback connection. This loopback connection does not use a physical network interface. HTTP communication takes place inside your storage system, and no clear text packets are transmitted.The HTTP protocol is not vulnerable to security attacks because it provides read-only access to documents by unauthenticated clients. Although authentication is not typically used for file access, it is frequently used for access to restricted documents or for administration purposes, such as FilerView administration. The only authentication methods defined by the HTTP protocol send credentials, such as user names and passwords, over the network without encryption. The SecureAdmin product is provided with SSL support to overcome this shortcoming.NoteIn versions of Data ONTAP earlier than 7.0, your storage system listens for new connections (by default, set to TCP port 80) even when the HTTP protocol is not licensed and FilerView is disabled. However, starting with Data ONTAP 7.0, you can stop your storage system from listening for new connections by setting the options httpd.enable and httpd.admin.enable to Off. If either of the options is set to On, your storage system will continue to listen for new connections.Kerberos•kerberos•kerberos-secThere are four Kerberos ports in the /etc/services file: TCP port 88, UDP port 88, TCP port 750, and UDP port 750. These ports are used only for outbound connections from your storage system. Your storage system does not run Kerberos servers or services and does not listen on these ports.Kerberos is used by your storage system to communicate with the Microsoft Active Directory servers for both CIFS authentication and, if configured, NFS authentication.NFS•portmap•nfsdThe Network File System (NFS) is used by UNIX clients for file access. NFS uses port 2049.NFSv3 and NFSv2 use the portmapper service on TCP or UDP port 111. The portmapper service is consulted to get the port numbers for services used with NFSv3 or NFSv2 protocols such as mountd, statd, and nlm. NFSv4 does not require the portmapper service.NFSv4 provides the delegation feature that enables your storage system to grant local file access to clients. To delegate, your storage system sets up a separate connection to the client and sends callbacks on it. To communicate with the client, your storage system uses one of the reserved ports (port numbers less than 1024). To initiate the connection, the client registers the callback program on a random port and informs the server about it.With delegations enabled, NFSv4 is not firewall friendly because several other ports need to be opened up as well.You can disable the TCP and UDP ports by setting the nfs.tcp.enable and nfs.udp.enable options to Off.To disable NFS, use the nfs off command.CIFS•netbios-name•netbios-dg•netbios-ssn•cifs-tcpThe Common Internet File Service (CIFS) is the successor to the server message block (SMB) protocol. CIFS is the primary protocol used by Windows systems for file sharing.CIFS uses UDP ports 137 and 138, and TCP ports 139 and 445. Your storage system sends and receives data on these ports while providing CIFS service. If it is a member of an Active Directory domain, your storage system also must make outbound connections destined for DNS and Kerberos.CIFS is required for Windows file service. You can disable CIFS using FilerView or by issuing the cifs terminate command on your storage system console.NoteIf you disable CIFS, be aware that your storage system's /etc/rc file can be set up to automatically enable CIFS again after a reboot.SSL•sslThe Secure Sockets Layer (SSL) protocol provides encryption and authentication of TCP connections.When SecureAdmin is installed and configured on your storage system, it listens for SSL connections on TCP port 443. It receives secure web browser connections on this port and uses unencrypted HTTP through a loopback connection to pass the traffic to FilerView, running on TCP port 80. This loopback connection is contained within your storage system and no unencrypted data is transmitted over the network.TCP port 443 can be disabled using FilerView or with the following command: secureadmin disable sslSNMP•snmpSimple Network Management Protocol (SNMP) is an industry-standard protocol used for remote monitoring and management of network devices over UDP port 161.SNMP is not secure because•Instead of using encryption keys or a user name and password pair, SNMP uses a community string for authentication. The community string is transmitted in clear textformat over the network, making it easy to capture with a packet sniffer.Within the industry, devices are typically configured at the factory to use public as the default community string. The public password allowsusers to make queries and read values but does not allow users toinvoke commands or change values. Some devices are configured atthe factory to use private as the default community string, allowingusers full read-write access.•Even if you change the read and write community string on a device to something other than private, an attacker can easily learn the new string by using the read-only publiccommunity string and asking the router for the read-write string.There are three versions of SNMP:•SNMPv1 is the original protocol and is not commonly used.•SNMPv2 is identical to SNMPv1 from a network protocol standpoint and is vulnerable to the same security problems. The only differences between the twoversions are in the messages sent, messages received, and the type ofinformation that is available. These differences are not important from a securitypoint of view. This version of SNMP is currently used on your storage systems.•SNMPv3 is the latest protocol version and includes security improvements but is difficult to implement and many vendors do not yet support it. SNMPv3 supportsseveral different types of network encryption and authentication schemes. Itallows for multiple users, each with different permissions, and solves SNMPv1security problems while maintaining an important level of compatibility withSNMPv2.SNMP is required if you want to monitor a storage system through an SNMP monitoring tool, such as DataFabric® Manager. Your storage system's SNMP implementation allows read-only access. Regardless of the community string used, the user cannot issue commands or change variables using SNMP on your storage system.You should use the snmp.access option to restrict SNMP access to a named set of trusted hosts.Set the snmp.enable option to Off to disable SNMP entirely.The snmp community delete and snmp community add commands are used to change the community string to something other than the default value.RSH•shellRemote shell protocol (RSH) is used for remote command execution and is the only protocol supported on your storage system. It is even less secure than TFTP and uses TCP port 514.RSH is not secure because passwords are not required for login and commands are easy to misconfigure. If possible, RSH should be disabled by setting the rsh.enable option to off.You should use the SSH supplied with SecureAdmin for remote command execution and login. If this is not possible, Telnet is preferred to RSH.If RSH is the only alternative, follow these guidelines when using RSH:•Specify only secure, trusted hosts in the /etc/hosts.equiv file.•Always use IP addresses rather than host names in the /etc/hosts.equiv file.•Always specify a single IP address with a single user name on each line in /etc/hosts.equiv file.•Use the rsh.access option instead of the trusted.hosts option for access control.•Make sure the ip.match_any_ifaddr option is set to off.Syslog•syslogYour storage system sends messages to hosts specified by the user in the/etc/syslog.conf file using the syslog protocol on UDP port 514. It does not listen on this port, nor does it act as a syslog server.Routed•routedThe route daemon, routed, listens on UDP port 520. It receives broadcast messages from routers or other hosts using the Routing Information Protocol (RIP). These messages are used by your storage system to update its internal routing tables to determine which network interfaces are optimal for each destination.Your storage system never broadcasts RIP messages containing routes because Data ONTAP is not capable of acting as a router.RIP is not secure because an attacker can easily send artificial RIP messages and cause hosts running the routed daemon (such as your storage system) toredirect network traffic to the attacker. The attacker can then receive and sift this traffic for passwords and other information and send it on to the actual destination, where the intrusion is undetected. This method can also be used as a starting point for TCP session attacks.Because of these security issues, use static routes (those set up using the route command on your storage system) instead of using the routed daemon. NDMP•ndmp•ndmp-localNetwork Data Management Protocol (NDMP) runs on TCP port 10000 and is used primarily for backup of network-attached storage (NAS) devices, such as your storage systems.The protocol defines three authentication methods:•NONE--allows authentication without restriction•TEXT--sends a clear text password over the network, similar to Telnet or FTP•MD5--uses the MD5 message digest algorithm along with a challenge-response message exchange to implement a secure login mechanismYour storage systems support both the TEXT and MD5 authentication methods. Most NDMP-enabled backup software uses MD5 by default.To entirely disable the TEXT authentication method, set thendmpd.authtype option to challenge.To restrict NDMP commands to certain authorized backup hosts, use the ndmp.access option.Regardless of the authentication method used, NDMP sends backup data in unencrypted format over the network, as does most other backup software. A separate network optimized for backup is a common means to increase performance while retaining data security.To disable NDMP, set the ndmp.enable option to off.SnapMirror and SnapVault•snapmirrorSnapMirror and SnapVault use TCP port 10566 for data transfer. Network connections are always initiated by the destination system; that is, SnapMirror and SnapVault pull data rather than push data.Authentication is minimal with both SnapMirror and SnapVault. To restrict inbound TCP connections on port 10566 to a list of authorized hosts or IP addresses, configure the snapmirror.access or snapvault.access option. Once a connection is established, the destination storage system communicates its host name to the source storage system, which then uses this host name to determine if a transfer is allowed. You should confirm a match between the host name and its IP address. To confirm that the host name and the IP address match, set the snapmirror.checkip.enable option to On.To disable SnapMirror, set the snapmirror.enable option to Off. To disable SnapVault, set the snapvault.enable option to Off.。
NetApp存储设备安装配置手册

NetApp存储设备配置说明修改记录目录1编写目的 (1)2专业名词和缩略语 (2)3组网方式和环境介绍 (3)4安装配置方法 (3)4.1N ET A PP硬件安装 (3)4.2设备初始化和系统设定 (4)4.2.1设备初始化 (4)4.2.2系统设定 (4)4.3操作系统安装 (6)4.3.1注册现有系统的cifs服务,将操作系统文件上传至FAS存储系统 (6)4.4应用配置 (8)4.4.1系统参数配置 (8)4.4.2注册需要使用的服务 (10)4.4.3创建一个卷并输出空间 (12)4.4.4创建一个Qtree并实施quota限制 (17)4.4.5配置autosupport (19)4.4.6配置snapshot策略及数据恢复方法 (19)4.4.7磁盘故障的数据恢复方法 (19)4.4.8配置Cluster (19)1 编写目的编写本文档的目的在于详细地说明NetApp FAS存储系统的安装、配置以及常用命令的介绍和可靠性维护、故障检查与恢复的方法,便于开发、测试、用服和工程维护人员安装、使用和维护NetApp FAS存储系统存储系统。
2 专业名词和缩略语3 组网方式和环境介绍NetAppFAS3240AESX ServerSWITCHESX Server图3.1 NetApp FAS存储系统组网结构NetApp FAS存储系统存储设备以NAS存储方式使用,通过万兆交换机与主机相连接。
4 安装配置方法4.1 NetApp硬件安装存储设备硬件的安装主要是各盘柜间线缆的连接、磁盘安装、盘柜上架、上电等,以上操作多由NetApp技术支持工程师完成。
使用存储设备随机携带的“DB-9 to RJ-45”转接线将FAS存储系统的CONSOLE端口和安装了WINDOWS操作系统的主机串口相连,在WINDOWS主机上安装SecureCRT软件,新建一个serial协议的连接,其中port参数根据所连接的是COM1还是COM2来进行选择,其余参数参考图4.1所示,通过串口连接登录到FAS存储系统。
NetApp_FAS
100TB 672 16GB 1GB 4 x 2.7GHz 18 - 44 - 16
56TB 672 12GB 512MB 4 x2.4GHz 18 - 42 - 16
84TB 336 8GB 1GB 4x2.8GH z 6 8 28 8 20
25TB 168 6GB 512MB 4x2.0Ghz 14 - 36 - 16
�
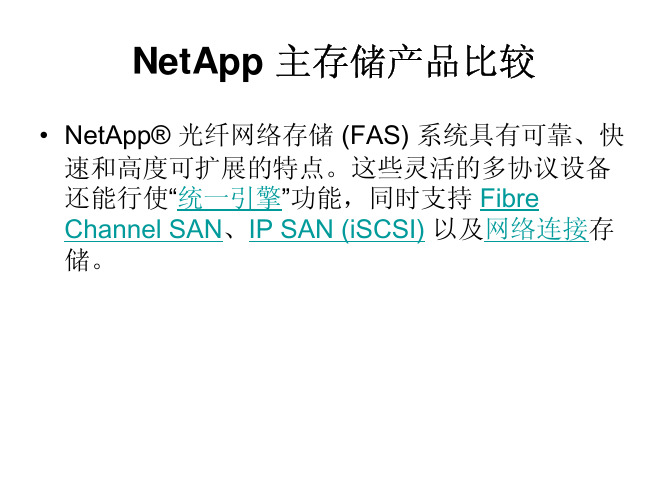
NetApp 主存储产品比较
NetApp 光纤网络存储 (FAS) 系统具有可靠,快 速和高度可扩展的特点.这些灵活的多协议设备 还能行使"统一引擎"功能,同时支持 Fibre Channel SAN,IP SAN (iSCSI) 以及网络连接存 储.
适用于大型企业的 NetApp FAS
规格 应用环境 双主动模式 (Active-Active) 最大原始容量 最大磁盘数 ECC 内存 NVRAM 处理器 PCI 扩展插槽数 最大配置 GbE 端 口数 最大配置 FC 端 口数 50TB 168 4GB 1GB 2x 2.8GHz 6 8 28 8 20 84 4GB 512MB 2 x 2.0GHz 6 - 32 - 16 FAS3020 FAS920 FAS270 FAS250 分布式企业: IP SAN,NAS 无 8TB 56 2GB 256MB 4 x 650MHz - 4 4 4 4 2TB 14 512MB 64MB 2 x 600MHz - 2 2 1 1 部门和分布式企业: FC SAN,IP SAN,NAS 有 12TB
规格 应用环境 双主动模式 (ActiveActive) 最大原始容量 最大磁盘数 ECC 内存 NVRAM 处理器 PCI 扩展插槽数 最大配置 GbE 端口数 最大配置 FC 端口数 FAS980 FAS960 FAS3050 FAS920 大型企业和技术计算:FC SAN,IP SAN,NAS 有
NetApp系列设备基本操作配置手册

NetApp FAS系列基本操作配置目录App存储系统 (3)2.系统基本操作维护指南 (5)2.1. 存储初始化配置 (5)2.2. 进入管理界面 (7)2.3. 系统基本信息 (8)2.4. 系统LOG信息 (9)2.5. 配置Autosupport (10)2.6. 设置时区、时间和日期 (10)2.7. 杂项设置 (11)2.8. 停机及重新启动 (12)2.9. 管理创建AGGR及卷 (13)2.10. 管理及创建Qtree (15)2.11. 磁盘配额 (16)2.12. SnapShot的配置和管理 (18)2.13. CIFS的相关信息 (20)2.14. CIFS共享 (23)2.15. ISCSI配置 (25)2.16. FC SAN配置 (29)2.17. 网络端口的管理 (32)2.18. 其他网络参数 (33)2.19. 更改root用户密码 (35)2.20. 系统实时状态监控 (35)附录一:磁盘更换步骤 (37)附录二:时间同步服务器的设置 (38)App存储系统NetApp 系统为各种不同平台上的用户提供了对全部企业数据的无缝访问。
NetApp全系列光纤网络存储系统在文件访问方面支持NFS 和CIFS,在块存储访问方面支持FCP 和iSCSI,确保您可以非常方便地将NetApp 存储系统集成到NAS 或SAN 环境中,并且保护原来的信息。
NetApp 的设计为专用访问环境中的应用程序服务器和服务器集群以及多用户环境中的用户提供了经过优化和整合的高性能数据访问方式。
NetApp 存储系统提供了经过实践考验的、超过99.998% 的数据可用性,减少了代价高昂的停机时间(无论是计划内的还是计划外的),最大限度地保障了对关键数据的访问。
它们在一个简单、易用的环境中实现了数据的可管理性、可扩展性、互操作性和可用性,从而降低了您的总拥有成本,加强了竞争优势。
NetApp系列产品具备真正的“统一引擎”功能,使您可以同时支持文件级和块级数据访问—而以前需要有多个系统才能完成这些过程。
NetApp存储解决方案

FAS6030A 最大缓存 最大磁盘数量 磁盘类型 32GB 840
FAS6070A 64GB 1008
FC: 146GB, 300GB (15000转) 转 146GB, 300GB (10000转) 转 SATA: 250GB, 500GB, 750GB (7200转) 转
最小端口数 最大端口数 (可扩充) 可扩充)
2000 1800 1600 1400 1200 1000 800 600 400 200 0
1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006
4
2070
46% CAGR
1597
1170 1006 798 579 289 46 93 166 892
iSCSI
Fibre Channel 光通道网络
企业千兆 以太私网
企业内网
SAN (Block数据块 数据块) 数据块
NetApp® FAS
NAS (File文件 文件) 文件
NetApp Confidential -- Do Not Distribute
9
各存储厂商的统一存储解决方案
其他厂商解决方案
FAS6070 FAS6030 FAS3070
主存储及 近线存储
FAS3050 FAS3040 FAS3020 420 TB 840 drives 504 TB 1008 drives
FAS250
4 TB 14 drives
168 TB 252 TB 504 drives 336 drives 126 TB FC 磁盘 252 drives 16 TB 84 TB SATA 磁盘 56 drives 168 drives VTL 700
Netapp Vscan 安装配置指导书

Netapp Vscan 安装配置指导书华为数据中心N E T A P P存储安装配置指导书一:Netapp Nas支持Symantec AntiVirus, Mcafee,趋势等杀毒软件的扫描杀毒以下是基于趋势杀毒软件在netapph上架构及安装应用和配置二:在netapp 的nas端操作如下1:fas270a> vscan on (把nas 对病毒扫描的服务开启)fas270a> vscan onWarning: CIFS clients will not be allowed to open files because there are no virus scanners registered with the filer. Are you sure? yesVirus scanning is enabledFas270a>useradin useradd nastest (建立nas用户并加入到域给于管理权限)fas270a> useradmin domainuser add \nastest -g "Administrators" SID = S-1-5-21-147214757-305610072-1517763936-180 618Domain User <\nastest> successfully added to Administrators.三:在病毒服务器上安装趋势杀毒软件1:安装第一步点setup2:按提示操作第二步3:按提示操作4:输入nas 的ip地址和nas能够登录的用户名和密码; 另外设定趋势使用passwd5:agent可以不安装如果使用client就要安装; 安装完成后输入刚才设定的趋势密码进入趋势杀毒管理主界面6:主界面如下:扫描netapp nas三:nas 端的显示以上显示服务器端在访问扫描nas端的文件系统, 安装配置成功!。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
网络需求所有需要执行SnapMirror数据复制的存储之间,需打开以下端口:NetApp FAS存储支持通过网络同步时钟。
如果存储和NTP服务器之间有防火墙,则打开以下端口:所有被管理的存储,必须通过IP网络与DFM服务器连通。
如果存储和DFM服务器之间有防火墙,则打开以下端口:如果有Windows机器需要管理(例如,客户端安装了OSSV备份软件),则Windows机器需要通过IP网络与DFM服务器连通。
如果Windows机器和DFM启用DFM的autosupport功能,需要DFM服务器和邮件服务器连通;并且服务器需要一个不需密码验证的发送邮件的账号。
如果邮件服务器和DFM服务器之间有防火墙,则打开以下端口:协议UDP端口TCP端口SMTP25附录:DOT 使用的IP端口IP port usage on a storage systemAbout this appendixThis appendix describes the Data ONTAP services file that is available in the /etc directory. The /etc/services file is in the same format as its corresponding UNIX systems /etc/services file. Although this file is it not used by Data ONTAP, it is provided in this appendix as information useful to system administrators.Host identificationAlthough some port scanners are able to identify storage systems as storage systems, others port scanners report storage systems as unknown types, UNIX systems because of their NFS support, or Windows systems because of their CIFS support. There are several services that are not currently listed in the /etc/services file. Below is an example of a complete list of the file contents.Service Port/ Protocol Descriptionftp-data20/tcp# File transfer protocolftp21/tcp# File transfer protocolssh22/tcp# SecureAdmin rsh replacementtelnet23/tcp# Remote login (insecure)smtp25/tcp# outbound connections for autosupporttime37/tcp# Time Servicettcp5001/udp# unused, shouldn't be listed here.ttcp5001/tcp# unused, shouldn't be listed here.ndmp10000/tcp# for network backupssnapmirro10566/tcp# also SnapVaultndmp-local32243/tcp# Internal connection inside your storage system /etc/services NNTP and TTCP portsThe nntp and ttcp ports are unused by your storage system and should never be detected by a port scanner.Ports found in a block starting around 600The following ports are found on the storage system with NFS enabled:UDP602NFS mount daemon (mountd)TCP603NFS mount daemon (mountd)UDP604NFS status daemon (statd, statmon)TCP605NFS status daemon (statd, statmon)UDP606NFS lock manager (lockd, nlockmgr)TCP607NFS lock manager (lockd, nlockmgr)UDP608NFS quota daemon (quotad, rquotad)On other systems, the ports appear as follows:UDP611NFS mount daemon (mountd)TCP612NFS mount daemon (mountd)UDP613NFS status daemon (statd, statmon)TCP614NFS status daemon (statd, statmon)UDP615NFS lock manager (lockd, nlockmgr)TCP616NFS lock manager (lockd, nlockmgr)Enter the following command on UNIX systems to obtain the correct information by querying the port mapper on port 111:toaster# rpcinfo -p vers proto port service100011 1 udp 608 rquotad100021 4 tcp 607 nlockmgr100021 3 tcp 607 nlockmgr100021 1 tcp 607 nlockmgr100021 4 udp 606 nlockmgr100021 3 udp 606 nlockmgr100021 1 udp 606 nlockmgr100024 1 tcp 605 status100024 1 udp 604 status100005 3 tcp 603 mountd100005 2 tcp 603 mountd100005 1 tcp 603 mountd100005 3 udp 602 mountd100005 2 udp 602 mountd100005 1 udp 602 mountd100003 3 udp 2049 nfs100003 2 udp 2049 nfs100000 2 tcp 111 rpcbind100000 2 udp 111 rpcbindNoteThe port numbers listed for mountd, statd, lockd, and quotad are not committed port numbers. Storage systems can have these services running on other port numbers. Because the system selects these port numbers at random when it boots, they are not listed in the /etc/services file.Other ports not listed in /etc/servicesThe following ports appear in a port scan but are not listed in /etc/services file. Protocol Port ServiceTCP22SSH (SecureAdmin)TCP443SSL (SecureAdmin)TCP3260iSCSI-TargetUDP xxxx Legato ClientPack for your storage system runs on random UDP ports and is now deprecated. It is recommended that NDMP beused to back up your storage system using Legato Networker. NoteDisable open ports that you do not need.FTPftp-dataftpFile transfer protocol (FTP) uses TCP ports 20 and 21. For a detailed description of the FTP support for your storage system, see the Data ONTAP File Access and Protocols Management Guide. If you use FTP to transfer files to and from your storage system, the FTP port is required; otherwise, use FilerView or the following CLI command to disable the FTP port:options offFTP is not a secure protocol for two reasons:When users log in to the system, user names and passwords are transmitted over the network in clear text format that can easily be read by a packet sniffer program.These user names and passwords can then be used to access data and other network resources. You should establish and enforce policies that preventthe use of the same passwords to access storage systems and other network resources.FTP server software used on platforms other than storage systems contains serioussecurity-related flaws that allow unauthorized users to gain administrative (root) access andcontrol over the host.SSHsshSecure Shell (SSH) protocol is a secure replacement for RSH and runs on TCP port 22. This only appears in a port scan if the SecureAdmin TM software is installed on your storage system.There are three commonly deployed versions of the SSH protocol:SSH version 1--is much more secure than RSH or Telnet, but is vulnerable to TCP sessionattacks.This vulnerability to attack lies in the SSH protocol version 1 itself and not inthe associated storage system products.SSH version 2--has a number of feature improvements over SSH version 1 and is less vulnerable to attacks.SSH version used to identify clients or servers that support both SSH versions 1 and 2.To disable SSH support or to close TCP port 22, use the following CLI command: secureadmin disable sshTelnettelnetTelnet is used for administrative control of your storage system and uses TCP connections on port 23. Telnet is more secure than RSH, as secure as FTP, and less secure than SSH or Secure Socket Layer (SSL).Telnet is not secure because:When users log into a system, such as your storage system, user names and passwords aretransmitted over the network in clear text format.Clear text format can be read by an attacker using a packet sniffer program.The attacker can use these user names and passwords to log in to yourstorage system and execute unauthorized administrative functions, including destruction of data on the system. If the administrators use the samepasswords on your storage system as they do on other network devices, the attacker can use these passwords to access those resources as well.NoteTo reduce the potential for attack, establish and enforce policies preventingadministrators from using the same passwords on your storage system thatthey use for access to other network resources.Telnet server software used on other platforms (typically in UNIX environments) have serioussecurity-related flaws that allow unauthorized users to gain administrative (root) control overthe host.Telnet is also vulnerable to the same type of TCP session attacks as SSH protocol version 1, but because a packet sniffing attack is easier, TCP session attacks are less common.To disable Telnet, set options to off.SMTPsmtpThe Simple Mail Transport Protocol (SMTP) uses TCP port 25. Your storage system does not listen on this port but makes outgoing connections to mail servers using this protocol when sending AutoSupport e-mail.Time servicetimentpYour storage system supports two different time service protocols:TIME protocol (also known as rdate) is specified in the RFC 868 standard. This standard allowsfor time services to be provided on TCP or UDP port 37. Your storage system uses only UDPport 37.Simple network time protocol (NTP) is specified in the RFC 2030 standard and is provided onlyon UDP port 123.When your storage system has option set to On and a remote protocol (rdate or ntp) is specified, the storage system synchronizes to a network time server.If the option is set to Off, your storage system is unable to synchronize with the network time server using NTP. The rdate time protocol can still be used by manually issuing the rdate command from your storage system console.You should set the option to On in a cluster configuration.DNSdomainThe Domain Name Service (DNS) uses UDP port 53 and TCP port 53. Your storage system does not typically listen on these ports because it does not run a domain name server. However, if DNS is enabled on your storage system, it makes outgoing connections using UDP port 53 for host name and IP address lookups. Your storage system never uses TCP port 53 because this port is used explicitly for communication between DNS servers. Outgoing DNS queries by your storage system are disabled by turning off DNS support. Turning off DNS support protects against receiving bad information from another DNS server.Because your storage system does not run a domain name server, the name service must be provided by one of the following:Network information service (NIS)An/etc/hosts fileReplacement of host names in the configuration files (such as /etc/exports, /etc/, and so on)with IP addressesDNS must be enabled for participation in an Active Directory domain.DHCPdhcpsClients broadcast messages to the entire network on UDP port 67 and receive responses from the Dynamic Host Configuration Protocol (DHCP) server on UDP port 68. The same ports are used for the BOOTP protocol.DHCP is used only for the first-time setup of your storage system. Detection of DHCP activity on your storage system by a port scan other than the activity during thefirst-time setup indicates a serious configuration or software error.TFTPtftpTrivial File Transfer Protocol (TFTP) uses TCP port 69. It is used mostly for booting UNIX or UNIX-like systems that do not have a local disk (this process is also known as netbooting) and for storing and retrieving configuration files for devices such as Cisco routers and switches.Transfers are not secure on TFTP because it does not require authentication for clients to connect and transfer files.Your storage system's TFTP server is not enabled by default. When TFTP is enabled, the administrator must specify a directory to be used by TFTP clients, and these clients cannot access other directories. Even within the TFTP directory, access is read-only. TFTP should be enabled only if necessary. Disable TFTP using the following option:options offHTTPhttpHypertext Transport Protocol (HTTP) runs on TCP port 80 and is the protocol used by web browsers to access web pages. Your storage system uses HTTP to access Files when the HTTP protocol is enabledFilerView for Graphical User Interface (GUI) administrationSecure FilerView when SecureAdmin is installedThe SecureAdmin SSL interface accepts connections on TCP port 443. SecureAdmin manages the details of the SSL network protocol, encrypts the connection, and then passes this traffic through to the normal HTTP FilerView interface through a loopback connection. This loopback connection does not use a physical network interface. HTTP communication takes place inside your storage system, and no clear text packets are transmitted.The HTTP protocol is not vulnerable to security attacks because it provides read-only access to documents by unauthenticated clients. Although authentication is not typically used for file access, it is frequently used for access to restricted documents or for administration purposes, such as FilerView administration. The only authentication methods defined by the HTTP protocol send credentials, such as user names and passwords, over the network without encryption. The SecureAdmin product is provided with SSL support to overcome this shortcoming.NoteIn versions of Data ONTAP earlier than , your storage system listens for new connections (by default, set to TCP port 80) even when the HTTP protocol is not licensed and FilerView is disabled. However, starting with Data ONTAP , you can stop your storage system from listening for new connections by setting the options and to Off. If either of the options is set to On, your storage system will continue to listen for new connections.Kerberoskerberoskerberos-secThere are four Kerberos ports in the /etc/services file: TCP port 88, UDP port 88, TCP port 750, and UDP port 750. These ports are used only for outbound connections from your storage system. Your storage system does not run Kerberos servers or services and does not listen on these ports.Kerberos is used by your storage system to communicate with the Microsoft Active Directory servers for both CIFS authentication and, if configured, NFS authentication. NFSportmapnfsdThe Network File System (NFS) is used by UNIX clients for file access. NFS uses port 2049.NFSv3 and NFSv2 use the portmapper service on TCP or UDP port 111. The portmapper service is consulted to get the port numbers for services used with NFSv3 or NFSv2 protocols such as mountd, statd, and nlm. NFSv4 does not require the portmapper service.NFSv4 provides the delegation feature that enables your storage system to grant local file access to clients. To delegate, your storage system sets up a separate connection to the client and sends callbacks on it. To communicate with the client, your storage system uses one of the reserved ports (port numbers less than 1024). To initiate the connection, the client registers the callback program on a random port and informs the server about it.With delegations enabled, NFSv4 is not firewall friendly because several other ports need to be opened up as well.You can disable the TCP and UDP ports by setting the and options to Off.To disable NFS, use the nfs off command.CIFSnetbios-namenetbios-dgnetbios-ssncifs-tcpThe Common Internet File Service (CIFS) is the successor to the server message block (SMB) protocol. CIFS is the primary protocol used by Windows systems for file sharing.CIFS uses UDP ports 137 and 138, and TCP ports 139 and 445. Your storage system sends and receives data on these ports while providing CIFS service. If it is a member of an Active Directory domain, your storage system also must make outbound connections destined for DNS and Kerberos.CIFS is required for Windows file service. You can disable CIFS using FilerView or by issuing the cifs terminate command on your storage system console.NoteIf you disable CIFS, be aware that your storage system's /etc/rc file can be set up to automatically enable CIFS again after a reboot.SSLsslThe Secure Sockets Layer (SSL) protocol provides encryption and authentication of TCP connections.When SecureAdmin is installed and configured on your storage system, it listens for SSL connections on TCP port 443. It receives secure web browser connections on this port and uses unencrypted HTTP through a loopback connection to pass the traffic to FilerView, running on TCP port 80. This loopback connection is contained within your storage system and no unencrypted data is transmitted over the network.TCP port 443 can be disabled using FilerView or with the following command: secureadmin disable sslSNMPsnmpSimple Network Management Protocol (SNMP) is an industry-standard protocol used for remote monitoring and management of network devices over UDP port 161. SNMP is not secure becauseInstead of using encryption keys or a user name and password pair, SNMP uses a communitystring for authentication. The community string is transmitted in clear text format over thenetwork, making it easy to capture with a packet sniffer.Within the industry, devices are typically configured at the factory to usepublic as the default community string. The public password allows users tomake queries and read values but does not allow users to invoke commandsor change values. Some devices are configured at the factory to use privateas the default community string, allowing users full read-write access.Even if you change the read and write community string on a device to something other thanprivate, an attacker can easily learn the new string by using the read-only public communitystring and asking the router for the read-write string.There are three versions of SNMP:SNMPv1 is the original protocol and is not commonly used.SNMPv2 is identical to SNMPv1 from a network protocol standpoint and is vulnerableto the same security problems. The only differences between the two versions are inthe messages sent, messages received, and the type of information that is available.These differences are not important from a security point of view. This version ofSNMP is currently used on your storage systems.SNMPv3 is the latest protocol version and includes security improvements but isdifficult to implement and many vendors do not yet support it. SNMPv3 supportsseveral different types of network encryption and authentication schemes. It allowsfor multiple users, each with different permissions, and solves SNMPv1 securityproblems while maintaining an important level of compatibility with SNMPv2. SNMP is required if you want to monitor a storage system through an SNMP monitoring tool, such as DataFabric® Manager. Your storage system's SNMP implementation allows read-only access. Regardless of the community string used, the user cannot issue commands or change variables using SNMP on your storage system.You should use the option to restrict SNMP access to a named set of trusted hosts.Set the option to Off to disable SNMP entirely.The snmp community delete and snmp community add commands are used to change the community string to something other than the default value.RSHshellRemote shell protocol (RSH) is used for remote command execution and is the only protocol supported on your storage system. It is even less secure than TFTP and uses TCP port 514.RSH is not secure because passwords are not required for login and commands are easy to misconfigure. If possible, RSH should be disabled by setting the option to off.You should use the SSH supplied with SecureAdmin for remote command execution and login. If this is not possible, Telnet is preferred to RSH.If RSH is the only alternative, follow these guidelines when using RSH:Specify only secure, trusted hosts in the /etc/ file.Always use IP addresses rather than host names in the /etc/ file.Always specify a single IP address with a single user name on each line in /etc/ file.Use the option instead of the option for access control.Make sure the option is set to off.SyslogsyslogYour storage system sends messages to hosts specified by the user in the /etc/ file using the syslog protocol on UDP port 514. It does not listen on this port, nor does it act as a syslog server.RoutedroutedThe route daemon, routed, listens on UDP port 520. It receives broadcast messages from routers or other hosts using the Routing Information Protocol (RIP). These messages are used by your storage system to update its internal routing tables to determine which network interfaces are optimal for each destination.Your storage system never broadcasts RIP messages containing routes because Data ONTAP is not capable of acting as a router.RIP is not secure because an attacker can easily send artificial RIP messages and cause hosts running the routed daemon (such as your storage system) to redirect network traffic to the attacker. The attacker can then receive and sift this traffic for passwords and other information and send it on to the actual destination, where the intrusion is undetected. This method can also be used as a starting point for TCP session attacks.Because of these security issues, use static routes (those set up using the route command on your storage system) instead of using the routed daemon.NDMPndmpndmp-localNetwork Data Management Protocol (NDMP) runs on TCP port 10000 and is used primarily for backup of network-attached storage (NAS) devices, such as your storage systems.The protocol defines three authentication methods:NONE--allows authentication without restrictionTEXT--sends a clear text password over the network, similar to Telnet or FTPMD5--uses the MD5 message digest algorithm along with a challenge-response messageexchange to implement a secure login mechanismYour storage systems support both the TEXT and MD5 authentication methods. Most NDMP-enabled backup software uses MD5 by default.To entirely disable the TEXT authentication method, set the option to challenge.To restrict NDMP commands to certain authorized backup hosts, use the option.Regardless of the authentication method used, NDMP sends backup data in unencrypted format over the network, as does most other backup software. A separate network optimized for backup is a common means to increase performance while retaining data security.To disable NDMP, set the option to off.SnapMirror and SnapVaultsnapmirrorSnapMirror and SnapVault use TCP port 10566 for data transfer. Network connections are always initiated by the destination system; that is, SnapMirror and SnapVault pull data rather than push data.Authentication is minimal with both SnapMirror and SnapVault. To restrict inbound TCP connections on port 10566 to a list of authorized hosts or IP addresses, configure the or option. Once a connection is established, the destination storage system communicates its host name to the source storage system, which then uses this host name to determine if a transfer is allowed. You should confirm a match between the host name and its IP address. To confirm that the host name and the IP address match, set the option to On.To disable SnapMirror, set the option to Off. To disable SnapVault, set the option to Off.。
