Management_of_Primary_Schlerosing_Cholangitis
微观管理英语

微观管理英语Micro-management is the practice of closely controlling and monitoring the work of employees. It is a management style that involves a manager closely overseeing and directing the work of their subordinates.Micro-management can be beneficial in certain situations, such as when a manager needs to ensure that a project is completed on time and within budget. It can also be useful when a manager needs to ensure that employees are following company policies and procedures. However, it can also be detrimental to employee morale and productivity if it is used too often or in the wrong way.The key to successful micro-management is to use it sparingly and only when necessary. It should be used to provide guidance and direction to employees, not to micromanage their every move. A manager should also be sure to provide feedback and recognition to employees when they do a good job.When micro-managing, it is important to remember that employees are not robots and should be given the freedom to make their own decisions. A manager should also be sure to provide clear instructions and expectations to employees so that they know what is expected of them.Finally, it is important to remember that micro-management should not be used as a substitute for good communication. A manager should be sure to communicate regularly with their employees and provide them with feedback and support. This will help to ensure that employees feel valued and appreciated, which can lead to increased morale and productivity.。
Probabilistic model checking of an anonymity system

Probabilistic Model Checking ofan Anonymity SystemVitaly ShmatikovSRI International333Ravenswood AvenueMenlo Park,CA94025U.S.A.shmat@AbstractWe use the probabilistic model checker PRISM to analyze the Crowds system for anonymous Web browsing.This case study demonstrates howprobabilistic model checking techniques can be used to formally analyze se-curity properties of a peer-to-peer group communication system based onrandom message routing among members.The behavior of group mem-bers and the adversary is modeled as a discrete-time Markov chain,and thedesired security properties are expressed as PCTL formulas.The PRISMmodel checker is used to perform automated analysis of the system and ver-ify anonymity guarantees it provides.Our main result is a demonstration ofhow certain forms of probabilistic anonymity degrade when group size in-creases or random routing paths are rebuilt,assuming that the corrupt groupmembers are able to identify and/or correlate multiple routing paths originat-ing from the same sender.1IntroductionFormal analysis of security protocols is a well-establishedfield.Model checking and theorem proving techniques[Low96,MMS97,Pau98,CJM00]have been ex-tensively used to analyze secrecy,authentication and other security properties ofprotocols and systems that employ cryptographic primitives such as public-key en-cryption,digital signatures,etc.Typically,the protocol is modeled at a highly ab-stract level and the underlying cryptographic primitives are treated as secure“black boxes”to simplify the model.This approach discovers attacks that would succeed even if all cryptographic functions were perfectly secure.Conventional formal analysis of security is mainly concerned with security against the so called Dolev-Yao attacks,following[DY83].A Dolev-Yao attacker is a non-deterministic process that has complete control over the communication net-work and can perform any combination of a given set of attacker operations,such as intercepting any message,splitting messages into parts,decrypting if it knows the correct decryption key,assembling fragments of messages into new messages and replaying them out of context,etc.Many proposed systems for anonymous communication aim to provide strong, non-probabilistic anonymity guarantees.This includes proxy-based approaches to anonymity such as the Anonymizer[Ano],which hide the sender’s identity for each message by forwarding all communication through a special server,and MIX-based anonymity systems[Cha81]that blend communication between dif-ferent senders and recipients,thus preventing a global eavesdropper from linking sender-recipient pairs.Non-probabilistic anonymity systems are amenable to for-mal analysis in the same non-deterministic Dolev-Yao model as used for verifica-tion of secrecy and authentication protocols.Existing techniques for the formal analysis of anonymity in the non-deterministic model include traditional process formalisms such as CSP[SS96]and a special-purpose logic of knowledge[SS99].In this paper,we use probabilistic model checking to analyze anonymity prop-erties of a gossip-based system.Such systems fundamentally rely on probabilistic message routing to guarantee anonymity.The main representative of this class of anonymity systems is Crowds[RR98].Instead of protecting the user’s identity against a global eavesdropper,Crowds provides protection against collaborating local eavesdroppers.All communication is routed randomly through a group of peers,so that even if some of the group members collaborate and share collected lo-cal information with the adversary,the latter is not likely to distinguish true senders of the observed messages from randomly selected forwarders.Conventional formal analysis techniques that assume a non-deterministic at-tacker in full control of the communication channels are not applicable in this case. Security properties of gossip-based systems depend solely on the probabilistic be-havior of protocol participants,and can be formally expressed only in terms of relative probabilities of certain observations by the adversary.The system must be modeled as a probabilistic process in order to capture its properties faithfully.Using the analysis technique developed in this paper—namely,formalization of the system as a discrete-time Markov chain and probabilistic model checking of2this chain with PRISM—we uncovered two subtle properties of Crowds that causedegradation of the level of anonymity provided by the system to the users.First,if corrupt group members are able to detect that messages along different routingpaths originate from the same(unknown)sender,the probability of identifyingthat sender increases as the number of observed paths grows(the number of pathsmust grow with time since paths are rebuilt when crowd membership changes).Second,the confidence of the corrupt members that they detected the correct senderincreases with the size of the group.Thefirstflaw was reported independently byMalkhi[Mal01]and Wright et al.[W ALS02],while the second,to the best ofour knowledge,was reported for thefirst time in the conference version of thispaper[Shm02].In contrast to the analysis by Wright et al.that relies on manualprobability calculations,we discovered both potential vulnerabilities of Crowds byautomated probabilistic model checking.Previous research on probabilistic formal models for security focused on(i)probabilistic characterization of non-interference[Gra92,SG95,VS98],and(ii)process formalisms that aim to faithfully model probabilistic properties of crypto-graphic primitives[LMMS99,Can00].This paper attempts to directly model andanalyze security properties based on discrete probabilities,as opposed to asymp-totic probabilities in the conventional cryptographic sense.Our analysis methodis applicable to other probabilistic anonymity systems such as Freenet[CSWH01]and onion routing[SGR97].Note that the potential vulnerabilities we discovered inthe formal model of Crowds may not manifest themselves in the implementationsof Crowds or other,similar systems that take measures to prevent corrupt routersfrom correlating multiple paths originating from the same sender.2Markov Chain Model CheckingWe model the probabilistic behavior of a peer-to-peer communication system as adiscrete-time Markov chain(DTMC),which is a standard approach in probabilisticverification[LS82,HS84,Var85,HJ94].Formally,a Markov chain can be definedas consisting in afinite set of states,the initial state,the transition relation such that,and a labeling functionfrom states to afinite set of propositions.In our model,the states of the Markov chain will represent different stages ofrouting path construction.As usual,a state is defined by the values of all systemvariables.For each state,the corresponding row of the transition matrix de-fines the probability distributions which govern the behavior of group members once the system reaches that state.32.1Overview of PCTLWe use the temporal probabilistic logic PCTL[HJ94]to formally specify properties of the system to be checked.PCTL can express properties of the form“under any scheduling of processes,the probability that event occurs is at least.”First,define state formulas inductively as follows:where atomic propositions are predicates over state variables.State formulas of the form are explained below.Define path formulas as follows:Unlike state formulas,which are simplyfirst-order propositions over a single state,path formulas represent properties of a chain of states(here path refers to a sequence of state space transitions rather than a routing path in the Crowds speci-fication).In particular,is true iff is true for every state in the chain;is true iff is true for all states in the chain until becomes true,and is true for all subsequent states;is true iff and there are no more than states before becomes true.For any state and path formula,is a state formula which is true iff state space paths starting from satisfy path formula with probability greater than.For the purposes of this paper,we will be interested in formulas of the form ,evaluated in the initial state.Here specifies a system con-figuration of interest,typically representing a particular observation by the adver-sary that satisfies the definition of a successful attack on the protocol.Property is a liveness property:it holds in iff will eventually hold with greater than probability.For instance,if is a state variable represent-ing the number of times one of the corrupt members received a message from the honest member no.,then holds in iff the prob-ability of corrupt members eventually observing member no.twice or more is greater than.Expressing properties of the system in PCTL allows us to reason formally about the probability of corrupt group members collecting enough evidence to success-fully attack anonymity.We use model checking techniques developed for verifica-tion of discrete-time Markov chains to compute this probability automatically.42.2PRISM model checkerThe automated analyses described in this paper were performed using PRISM,aprobabilistic model checker developed by Kwiatkowska et al.[KNP01].The toolsupports both discrete-and continuous-time Markov chains,and Markov decisionprocesses.As described in section4,we model probabilistic peer-to-peer com-munication systems such as Crowds simply as discrete-time Markov chains,andformalize their properties in PCTL.The behavior of the system processes is specified using a simple module-basedlanguage inspired by Reactive Modules[AH96].State variables are declared in thestandard way.For example,the following declarationdeliver:bool init false;declares a boolean state variable deliver,initialized to false,while the followingdeclarationconst TotalRuns=4;...observe1:[0..TotalRuns]init0;declares a constant TotalRuns equal to,and then an integer array of size,indexed from to TotalRuns,with all elements initialized to.State transition rules are specified using guarded commands of the form[]<guard>-><command>;where<guard>is a predicate over system variables,and<command>is the tran-sition executed by the system if the guard condition evaluates to mandoften has the form<expression>...<expression>, which means that in the next state(i.e.,that obtained after the transition has beenexecuted),state variable is assigned the result of evaluating arithmetic expres-sion<expression>If the transition must be chosen probabilistically,the discrete probability dis-tribution is specified as[]<guard>-><prob1>:<command1>+...+<probN>:<commandN>;Transition represented by command is executed with probability prob,and prob.Security properties to be checked are stated as PCTL formulas (see section2.1).5Given a formal system specification,PRISM constructs the Markov chain and determines the set of reachable states,using MTBDDs and BDDs,respectively. Model checking a PCTL formula reduces to a combination of reachability-based computation and solving a system of linear equations to determine the probability of satisfying the formula in each reachable state.The model checking algorithms employed by PRISM include[BdA95,BK98,Bai98].More details about the im-plementation and operation of PRISM can be found at http://www.cs.bham. /˜dxp/prism/and in[KNP01].Since PRISM only supports model checking offinite DTMC,in our case study of Crowds we only analyze anonymity properties offinite instances of the system. By changing parameters of the model,we demonstrate how anonymity properties evolve with changes in the system configuration.Wright et al.[W ALS02]investi-gated related properties of the Crowds system in the general case,but they do not rely on tool support and their analyses are manual rather than automated.3Crowds Anonymity SystemProviding an anonymous communication service on the Internet is a challenging task.While conventional security mechanisms such as encryption can be used to protect the content of messages and transactions,eavesdroppers can still observe the IP addresses of communicating computers,timing and frequency of communi-cation,etc.A Web server can trace the source of the incoming connection,further compromising anonymity.The Crowds system was developed by Reiter and Ru-bin[RR98]for protecting users’anonymity on the Web.The main idea behind gossip-based approaches to anonymity such as Crowds is to hide each user’s communications by routing them randomly within a crowd of similar users.Even if an eavesdropper observes a message being sent by a particular user,it can never be sure whether the user is the actual sender,or is simply routing another user’s message.3.1Path setup protocolA crowd is a collection of users,each of whom is running a special process called a jondo which acts as the user’s proxy.Some of the jondos may be corrupt and/or controlled by the adversary.Corrupt jondos may collaborate and share their obser-vations in an attempt to compromise the honest users’anonymity.Note,however, that all observations by corrupt group members are local.Each corrupt member may observe messages sent to it,but not messages transmitted on the links be-tween honest jondos.An honest crowd member has no way of determining whether6a particular jondo is honest or corrupt.The parameters of the system are the total number of members,the number of corrupt members,and the forwarding probability which is explained below.To participate in communication,all jondos must register with a special server which maintains membership information.Therefore,every member of the crowd knows identities of all other members.As part of the join procedure,the members establish pairwise encryption keys which are used to encrypt pairwise communi-cation,so the contents of the messages are secret from an external eavesdropper.Anonymity guarantees provided by Crowds are based on the path setup pro-tocol,which is described in the rest of this section.The path setup protocol is executed each time one of the crowd members wants to establish an anonymous connection to a Web server.Once a routing path through the crowd is established, all subsequent communication between the member and the Web server is routed along it.We will call one run of the path setup protocol a session.When crowd membership changes,the existing paths must be scrapped and a new protocol ses-sion must be executed in order to create a new random routing path through the crowd to the destination.Therefore,we’ll use terms path reformulation and proto-col session interchangeably.When a user wants to establish a connection with a Web server,its browser sends a request to the jondo running locally on her computer(we will call this jondo the initiator).Each request contains information about the intended desti-nation.Since the objective of Crowds is to protect the sender’s identity,it is not problematic that a corrupt router can learn the recipient’s identity.The initiator starts the process of creating a random path to the destination as follows: The initiator selects a crowd member at random(possibly itself),and for-wards the request to it,encrypted by the corresponding pairwise key.We’ll call the selected member the forwarder.The forwarderflips a biased coin.With probability,it delivers the request directly to the destination.With probability,it selects a crowd member at random(possibly itself)as the next forwarder in the path,and forwards the request to it,re-encrypted with the appropriate pairwise key.The next forwarder then repeats this step.Each forwarder maintains an identifier for the created path.If the same jondo appears in different positions on the same path,identifiers are different to avoid infinite loops.Each subsequent message from the initiator to the destination is routed along this path,i.e.,the paths are static—once established,they are not altered often.This is necessary to hinder corrupt members from linking multiple7paths originating from the same initiator,and using this information to compromise the initiator’s anonymity as described in section3.2.3.3.2Anonymity properties of CrowdsThe Crowds paper[RR98]describes several degrees of anonymity that may be provided by a communication system.Without using anonymizing techniques, none of the following properties are guaranteed on the Web since browser requests contain information about their source and destination in the clear.Beyond suspicion Even if the adversary can see evidence of a sent message,the real sender appears to be no more likely to have originated it than any other potential sender in the system.Probable innocence The real sender appears no more likely to be the originator of the message than to not be the originator,i.e.,the probability that the adversary observes the real sender as the source of the message is less thanupper bound on the probability of detection.If the sender is observed by the adversary,she can then plausibly argue that she has been routing someone else’s messages.The Crowds paper focuses on providing anonymity against local,possibly co-operating eavesdroppers,who can share their observations of communication in which they are involved as forwarders,but cannot observe communication involv-ing only honest members.We also limit our analysis to this case.3.2.1Anonymity for a single routeIt is proved in[RR98]that,for any given routing path,the path initiator in a crowd of members with forwarding probability has probable innocence against collaborating crowd members if the following inequality holds:(1)More formally,let be the event that at least one of the corrupt crowd members is selected for the path,and be the event that the path initiator appears in8the path immediately before a corrupt crowd member(i.e.,the adversary observes the real sender as the source of the messages routed along the path).Condition 1guarantees thatproving that,given multiple linked paths,the initiator appears more often as a sus-pect than a random crowd member.The automated analysis described in section6.1 confirms and quantifies this result.(The technical results of[Shm02]on which this paper is based had been developed independently of[Mal01]and[W ALS02],be-fore the latter was published).In general,[Mal01]and[W ALS02]conjecture that there can be no reliable anonymity method for peer-to-peer communication if in order to start a new communication session,the initiator must originate thefirst connection before any processing of the session commences.This implies that anonymity is impossible in a gossip-based system with corrupt routers in the ab-sence of decoy traffic.In section6.3,we show that,for any given number of observed paths,the adversary’s confidence in its observations increases with the size of the crowd.This result contradicts the intuitive notion that bigger crowds provide better anonymity guarantees.It was discovered by automated analysis.4Formal Model of CrowdsIn this section,we describe our probabilistic formal model of the Crowds system. Since there is no non-determinism in the protocol specification(see section3.1), the model is a simple discrete-time Markov chain as opposed to a Markov deci-sion process.In addition to modeling the behavior of the honest crowd members, we also formalize the adversary.The protocol does not aim to provide anonymity against global eavesdroppers.Therefore,it is sufficient to model the adversary as a coalition of corrupt crowd members who only have access to local communication channels,i.e.,they can only make observations about a path if one of them is se-lected as a forwarder.By the same token,it is not necessary to model cryptographic functions,since corrupt members know the keys used to encrypt peer-to-peer links in which they are one of the endpoints,and have no access to links that involve only honest members.The modeling technique presented in this section is applicable with minor mod-ifications to any probabilistic routing system.In each state of routing path construc-tion,the discrete probability distribution given by the protocol specification is used directly to define the probabilistic transition rule for choosing the next forwarder on the path,if any.If the protocol prescribes an upper bound on the length of the path(e.g.,Freenet[CSWH01]),the bound can be introduced as a system parameter as described in section4.2.3,with the corresponding increase in the size of the state space but no conceptual problems.Probabilistic model checking can then be used to check the validity of PCTL formulas representing properties of the system.In the general case,forwarder selection may be governed by non-deterministic10runCount goodbad lastSeen observelaunchnewstartrundeliver recordLast badObserve4.2Model of honest members4.2.1InitiationPath construction is initiated as follows(syntax of PRISM is described in section 2.2):[]launch->runCount’=TotalRuns&new’=true&launch’=false;[]new&(runCount>0)->(runCount’=runCount-1)&new’=false&start’=true;[]start->lastSeen’=0&deliver’=false&run’=true&start’=false;4.2.2Forwarder selectionThe initiator(i.e.,thefirst crowd member on the path,the one whose identity must be protected)randomly chooses thefirst forwarder from among all group mem-bers.We assume that all group members have an equal probability of being chosen, but the technique can support any discrete probability distribution for choosing for-warders.Forwarder selection is a single step of the protocol,but we model it as two probabilistic state transitions.Thefirst determines whether the selected forwarder is honest or corrupt,the second determines the forwarder’s identity.The randomly selected forwarder is corrupt with probability badCbe next on the path.Any of the honest crowd members can be selected as the forwarder with equal probability.To illustrate,for a crowd with10honest members,the following transition models the second step of forwarder selection: []recordLast&CrowdSize=10->0.1:lastSeen’=0&run’=true&recordLast’=false+0.1:lastSeen’=1&run’=true&recordLast’=false+...0.1:lastSeen’=9&run’=true&recordLast’=false;According to the protocol,each honest crowd member must decide whether to continue building the path byflipping a biased coin.With probability,the forwarder selection transition is enabled again and path construction continues, and with probability the path is terminated at the current forwarder,and all requests arriving from the initiator along the path will be delivered directly to the recipient.[](good&!deliver&run)->//Continue path constructionPF:good’=false+//Terminate path constructionnotPF:deliver’=true;The specification of the Crowds system imposes no upper bound on the length of the path.Moreover,the forwarders are not permitted to know their relative position on the path.Note,however,that the amount of information about the initiator that can be extracted by the adversary from any path,or anyfinite number of paths,isfinite(see sections4.3and4.5).In systems such as Freenet[CSWH01],requests have a hops-to-live counter to prevent infinite paths,except with very small probability.To model this counter,we may introduce an additional state variable pIndex that keeps track of the length of the path constructed so far.The path construction transition is then coded as follows://Example with Hops-To-Live//(NOT CROWDS)////Forward with prob.PF,else deliver13[](good&!deliver&run&pIndex<MaxPath)->PF:good’=false&pIndex’=pIndex+1+notPF:deliver’=true;//Terminate if reached MaxPath,//but sometimes not//(to confuse adversary)[](good&!deliver&run&pIndex=MaxPath)->smallP:good’=false+largeP:deliver’=true;Introduction of pIndex obviously results in exponential state space explosion, decreasing the maximum system size for which model checking is feasible.4.2.4Transition matrix for honest membersTo summarize the state space of the discrete-time Markov chain representing cor-rect behavior of protocol participants(i.e.,the state space induced by the abovetransitions),let be the state in which links of the th routing path from the initiator have already been constructed,and assume that are the honestforwarders selected for the path.Let be the state in which path constructionhas terminated with as thefinal path,and let be an auxiliary state. Then,given the set of honest crowd members s.t.,the transi-tion matrix is such that,,(see section4.2.2),i.e.,the probability of selecting the adversary is equal to the cumulative probability of selecting some corrupt member.14This abstraction does not limit the class of attacks that can be discovered using the approach proposed in this paper.Any attack found in the model where indi-vidual corrupt members are kept separate will be found in the model where their capabilities are combined in a single worst-case adversary.The reason for this is that every observation made by one of the corrupt members in the model with separate corrupt members will be made by the adversary in the model where their capabilities are combined.The amount of information available to the worst-case adversary and,consequently,the inferences that can be made from it are at least as large as those available to any individual corrupt member or a subset thereof.In the adversary model of[RR98],each corrupt member can only observe its local network.Therefore,it only learns the identity of the crowd member imme-diately preceding it on the path.We model this by having the corrupt member read the value of the lastSeen variable,and record its observations.This cor-responds to reading the source IP address of the messages arriving along the path. For example,for a crowd of size10,the transition is as follows:[]lastSeen=0&badObserve->observe0’=observe0+1&deliver’=true&run’=true&badObserve’=false;...[]lastSeen=9&badObserve->observe9’=observe9+1&deliver’=true&run’=true&badObserve’=false;The counters observe are persistent,i.e.,they are not reset for each session of the path setup protocol.This allows the adversary to accumulate observations over several path reformulations.We assume that the adversary can detect when two paths originate from the same member whose identity is unknown(see sec-tion3.2.2).The adversary is only interested in learning the identity of thefirst crowd mem-ber in the path.Continuing path construction after one of the corrupt members has been selected as a forwarder does not provide the adversary with any new infor-mation.This is a very important property since it helps keep the model of the adversaryfinite.Even though there is no bound on the length of the path,at most one observation per path is useful to the adversary.To simplify the model,we as-sume that the path terminates as soon as it reaches a corrupt member(modeled by deliver’=true in the transition above).This is done to shorten the average path length without decreasing the power of the adversary.15Each forwarder is supposed toflip a biased coin to decide whether to terminate the path,but the coinflips are local to the forwarder and cannot be observed by other members.Therefore,honest members cannot detect without cooperation that corrupt members always terminate paths.In any case,corrupt members can make their observable behavior indistinguishable from that of the honest members by continuing the path with probability as described in section4.2.3,even though this yields no additional information to the adversary.4.4Multiple pathsThe discrete-time Markov chain defined in sections4.2and4.3models construc-tion of a single path through the crowd.As explained in section3.2.2,paths have to be reformulated periodically.The decision to rebuild the path is typically made according to a pre-determined schedule,e.g.,hourly,daily,or once enough new members have asked to join the crowd.For the purposes of our analysis,we sim-ply assume that paths are reformulated somefinite number of times(determined by the system parameter=TotalRuns).We analyze anonymity properties provided by Crowds after successive path reformulations by considering the state space produced by successive execu-tions of the path construction protocol described in section4.2.As explained in section4.3,the adversary is permitted to combine its observations of some or all of the paths that have been constructed(the adversary only observes the paths for which some corrupt member was selected as one of the forwarders).The adversary may then use this information to infer the path initiator’s identity.Because for-warder selection is probabilistic,the adversary’s ability to collect enough informa-tion to successfully identify the initiator can only be characterized probabilistically, as explained in section5.4.5Finiteness of the adversary’s state spaceThe state space of the honest members defined by the transition matrix of sec-tion4.2.4is infinite since there is no a priori upper bound on the length of each path.Corrupt members,however,even if they collaborate,can make at most one observation per path,as explained in section4.3.As long as the number of path reformulations is bounded(see section4.4),only afinite number of paths will be constructed and the adversary will be able to make only afinite number of observa-tions.Therefore,the adversary only needsfinite memory and the adversary’s state space isfinite.In general,anonymity is violated if the adversary has a high probability of making a certain observation(see section5).Tofind out whether Crowds satisfies16。
Management of Active Networks

Management of Active NetworksMarcus BRUNNER, Bernhard PLATTNERComputer Engineering and Networks Laboratory, TIKSwiss Federal Institute of Technology Zürich (ETH) Gloriastr. 35, CH-8092 Zürich, SwitzerlandE-Mail: brunner@tik.ee.ethz.chICC Workshop on Active Networking and ProgrammableNetworks, Atlanta, 1998.AbstractActive networks provide the possibility to perform com-putations within the network. This feature introduces greater flexibility, but more complexity as well. There-fore, a sound management of active networks is a prereq-uisite to the acceptance of such networks. Management of large complex systems can be improved with the intro-duction of further abstraction levels and with moving the responsibility for the management down the line. Net-work management applications have two basic tasks to perform: operation of a node and control of message exe-cution. In active networks there is a need for debugging functions a user has injected into the network. For opera-tion and debugging, the monitoring of events occurring within an active network, and visualizing it, helps per-forming these tasks. Utilized and well scaling mecha-nisms for monitoring active networks are node clustering, event abstraction and filtering which have been applied to the presented prototypical implementation. We further propose a framework for monitoring and managing the active network.1IntroductionEnd systems of a network are open systems in the sense that they can be programmed with appropriate languages and tools. In contrast, intermediate network nodes are very often closed, integrated systems, whose functions are determined through long lasting stan-dardization processes. Traditional data networks trans-port bytes from one end system to another. The intermediate system neither modifies these byte or bit streams nor are they sensitive to their contents. Because the processing in intermediate nodes currently is extremely limited, it consists of header processing in packet-switched networks and signaling in connection-oriented networks.Active networks break with this tradition by letting the network perform customized computation on the data. This implies that an active network node has two tasks to perform: (1) computation on user data and (2) indi-viduals can inject functions into network nodes, thereby tailoring nodes’ processing to be application-specific. Deploying software in these intermediate nodes should be as simple as launching an end system application.With the greater flexibility gained trough the possibil-ity to program the network, a drawback on the ease of manageability of the network has been introduced. However, a huge potential to overcome several prob-lems of traditional network management systems are achieved since, such as scalability in network size, static functionality, reliability of the management application, and the problem of micro-management. With the introduction of active networks, network architecture gets very flexible, but with this flexibility an increase in complexity comes along with. There-fore, we identified an even stronger need for network management which is not handled sufficient in today’s networks. An efficient and scalable resource and net-work management is mandatory, if active networks are becoming a competition for today’s networks. The key factors in the management field is the problem of scal-ability in large networks management and the static functionality. To manage large systems two basic approaches are considered: (1) abstraction of low level structures and (2) delegating the responsibility to a lower level. The static functions are replaced with dynamic ones, with the possibility to inject programs into the network. As everyone can inject programs and users programming such functions want to debug them and want to observe their performance.For debugging and management tasks visualization tools help understanding the execution of a program and the overall network performance. It is widely accepted that visualizing data is more useful as larger amounts of data have to be presented to a user. There-fore, visualization will help to understand active net-works with a huge amount of messages transmitted. This understanding is mandatory to improve the net-work architecture, injected active messages and the management of an active network.This paper is organized as follows. Section 2, describes an active network architecture for studying resource and network management in active networks. In sec-tion 3 mechanisms for operation management and debugging of active messages are presented. Issues on the monitoring of active networks are depicted in sec-tion 4. A framework for monitoring and managing is outlined in section 5, which is followed by the conclu-sion and a brief discussion on further work.2Architecture of an Active NetworkWe propose an architecture of an active network which is used as a prototype for exploring issues of resource management and network management. This architec-ture does not focus on the performance or security, but it provides an environment to test different ideas. Since at the beginning of the work no architecture has been available for active networks, a set of general mecha-nisms, described later, has been developed which couldbe refined and may be migrated to others.2.1Network ModelA network consists of nodes which are connected via links. Moving entities in the network are “active mes-sages”, also called “capsules” in [1]. They are compa-rable with packets in traditional data networks, despite the fact that they are not only data, but also programs. An intermediate node is processing an incoming active message accessing the environment of this node. After-wards, the message chooses an outgoing link to leavethis node.A special type of nodes are end system nodes. On the node at the border of the network an active message may not only choose to leave the network via a link, but it may also choose to be delivered to an application or to access a displaying device.2.2Protocol ArchitectureDespite of the fact of manifold definitions for a proto-col, refer to [2], in our case a protocol‡ consists of a set of active messages which may be of similar or different type. Therefore, a protocol is the base unit for reserva-tion‡‡, classification, and protection. This could be done also on a per active message basis, but if more than one type of active messages is involved in a proto-col, it is impossible that one of these messages can profit from resources which another one does not con-sume. If resources have to be allocated to only one message type, more than one protocol for a communi-cation can be specified easily.2.3Node ArchitectureIn the network model depicted above, nodes receive packets and process them with the information stored in the node, such as state. This results in one or more packets being transmitted on an outgoing link. This functionality requires four major components within a node as depicted in Figure1, (1) the control of incom-ing messages, (2) the control of the outgoing messages, (3) message processing, and (4) memory to store infor-mation.The difference compared to traditional networks is based on the processing component, where nodes have static pre-installed functions processing incoming packets. However, active networks allow users to install their personalized functions in any network node. The proposed approach proceeds one step fur-ther. The function to be processed on the network node ‡Traditionally, a protocol defines a set of rules for communication. In our case these rules are speci-fied by a programming language.‡‡ In the integrated services network community the entity for resource reservation is termed a“flow”.is carried by the packet itself. Naturally, it can be avoided that each packet carries the same code along, by sending the code only the first time a packet type flows through this node, reducing the required through-put.2.4Interface of a NodeThe active message running on a node need to access the node over an interface. The tasks a message can execute are many fold. Bet the interface can be grouped into different functional areas: 1) execution,The execution interface has all the instructions a mes-sage uses to move around, to create other messages, to access the storage of the node, and it has instructions for the synchronization of messages.The information interface is used to get information about the node, e.g. how many links this node has. And there exists the possibility to install an event queue in the node. The node stores different events in this event queue if the corresponding action has been executed. The organizational interface is only by the owner of the node accessible, and has functions to change configu-ration parameters, to reboot the node, and to create new links.The configuration interface has functions to configure some parameters for a protocol, e.g. the reservation of bandwidth a protocol is using.3Network ManagementThe paradigm of management by delegation [4] can be used to move management functions to the data rather than moving data to these functions. Delegation fits very well into the concept of active networks. Active Figure 1: A Generic Network Node ArchitectureFigure 2: Interface of an active network nodemessages can retrieve data about the state of a node process this data and take appropriate action.There are three important issues associated with the management of active networks. First, the management of the network node with its resources. Second, the management of configurations, and faults. Third, the management of active messages which essentially results in the monitoring and debugging active mes-sages flowing through the network.3.1Node ManagementHere the focus is drawn to the operation, configuration, and fault management of a node. These tasks comprise functions which are not visible to normal active mes-sages flowing through a network node. They are strictly utilized by the node’s system manager to ensure an optimal operation of the node. Configuration possibility are the installation of special node compo-nents or setting run-time parameter of the components.E.g. you may change the out-bound link scheduler to have another scheduling policy on this link or you may change the minimum time quantum of the scheduler. In many cases such operation changes have to be done, not only on one node, but on several nodes in the net-work.3.2Resource ManagementIf an active network shall support guaranteed services, resources of a node have to be managed in a fashion that guarantees can be fulfilled by the network or that the messages can provide a guaranteed service to a cli-ent. Since existing resources are used by all active messages on a node, it is fundamental and mandatory to isolate the resource consumption of each group of messages (protocol) from other groups. If this is not the case, there is no way to protect a group of messages from being disturbed by other messages overconsum-ing these resource.A resource not consumed should be shared fairly among protocols, as defined in subsection 2.2, compet-ing for that particular resource. Anyway, for different classes of network traffic, where a class represents some aggregate of traffic streams being grouped according to their administrative domain, protocol, traffic type or other criteria, an unused resource shall be provided to a class member using this resource, but not to members of different classes. Therefore, the sup-port for hierarchical link sharing has already been pro-posed by [5]. In this case each resource has an associated class hierarchy, specifying the allocation policy of this resource. This hierarchy allows for build-ing virtual private networks. According to the traffic types of the messages also the resource scheduling has to be different, which leads to the need of changing the scheduler.3.3Debugging of Active MessagesEmpirical evidence shows that programmers spend the majority of their time on program maintenance tasks such as debugging [3]. A first step in all debugging purposes is to gain the understanding of the program at hand. Since active messages are programs flowing through the network, it is an even more difficult task to debug them. A more frequently applied support is a graphical visualization to present, follow, and analyze the execution of a distributed computation. The same holds for active messages. An event-based approach is typically employed for debugging distributed pro-grams. In the following, events and their collection is discussed.Observation of EventsAn event constitutes the lowest level of observable behavior. It occurs each time an to be observed action is executed. Each event represents a specific action and is typed according to the action this event represents. Thus, different events of the same type may occur, but they are separated in time, by messages, or by message type. An event is considered to have no duration, which, of course, is an ideal assumption.Actions of interest can be classified in two groups: (1) Those arising from the execution of a active message on one node, for example scheduling decisions, arrival of a message, or transmission of a message, or (2) those arising from actions happening within the node without or on unknown relation to a message, for example errors, overloads, and system errors. Events in the first class originate at the interface of the run-time environment of a node which the message is accessing during its life-time on this node. Second class event originate in active components of a node.TimeWith the occurrence of an event time is associated. This time is interesting, because (1) ordering events and (2) studying temporal aspects of the system are feasible. In distributed systems two different principles to deal with time exist. Events may be ordered partially with the introduction of the ‘happens before’ relation proposed by Lamport [6] and [7]. This means, if an event A ‘happens before’ event B, event B may be dependent on event A. Another approach implements a global time base as accurate as possible [12]. Typi-cally, timestamping techniques consist of two parts: (1) a timestamping algorithm (virtual or real clock) and (2) a timestamp test. The algorithm describes how to assign timestamps to an event and the test determines which event happens before another one.Collection of EventsSince events occur in a node, the interface of this node needs a function to register an object with a predefined interface to be called on the occurrence of this event.Furthermore, it has to be specified which events a mes-sage is interested in. Another entity has to deal with timestamping, if necessary for further calculation on events. According to the precision of the clock and the placement of the timestamping mechanism for events, the accuracy of the timestamp is determined. Times-tamping the event as near as possible with the real occurrence of the action it represents, achieves best results. Therefore, the optimal solution for an event to receive accurate timestamps is to install an opaque clock with an abstract interface into the node, deliver-ing the current time. These allows for introducing dif-ferent timestamping algorithms.Identifying MessagesIf events of the same message on different nodes have to be correlated, which is normally the case in the debugging scenario, it has to be possible to identify the message. If the nodes itself are globally unique identi-fiable, the messages can identified with identity of cre-ation node and a number which is unique on this node. This information has be transported along with the message. Another approach is to identify the message only between the sending and the receiving node. This requires the possibility to detect, if the message is lost or corrupted on the link.4Monitoring of Active NetworksFor operation, performance measurements, and debug-ging of active messages, visualization tools and tech-niques are promising. They allow for a better understanding of gathered network data. The under-standing of the network is very important, since the active network technology is new. For the operation task the interesting views are the network topology including the information, how networks actually per-form and indicating nodes with a failure situation. However, for the debugging task additional low level views are interesting. Low level in the sense that a pro-grammer focuses his attention to a small set of mes-sages, but exactly determines which executions these messages perform on their lifetime.The visualization of data greatly improves the under-standing of a topic. The more data are to be presented to a user, the more a visualization tool supports the comprehension of the state of affairs. If the new tech-nology of active networks is evolving, it is very impor-tant to employ and improve it. Still, the problem of an ever increasing network size remains in addition to a concomitant increase of collectable network measure-ment data. This large amount of data for visualizing the system calls for a reduction of the data to an amount which is feasible to be displayed on powerful graphic workstations. Concerning the debugging case, the programmer debugging his code, first wants to have a global overview of the execution of the program [9]. This can be achieved by viewing the execution at a very high abstraction level. Further detailed under-standing is more difficult, but supported by an isolation of interesting parts of the execution to be examined at a lower layer of abstraction. On different layers in debugging, a different kind and variable number of events are required.To achieve a high-level view three mechanisms are available: (1) grouping low-level events to form “abstract events”, (2) grouping single nodes to a cluster of nodes, and (3) filtering out events which are not required in a high level view. All these mechanisms can be supported well with the introduction of an active network architecture, because they distribute the computation of the visualization tool from the display-ing workstation into the network.4.1Event AbstractionThe motivation of event abstraction is to reduce com-plexity by omitting unwanted details. The abstraction should not introduce spurious precedences or hide real ones. The most general potential definition of an abstract event is an arbitrary subset of events in a ses-sion. As mentioned before, of particular importance for the analysis of the distributed processing of active mes-sages is the relation “happens before” between events [6]. This relation induces a partial order of the event set. But the relation holds for atomic events only, abstract events have a duration and probably happen on different nodes. Therefore, a number of schemes for event abstraction have been proposed, early ones in a more ad-hoc manner without firm theoretical founda-tion. In [8], the notion of molecules and atoms defining sets of primitive events with certain properties is intro-duced and a precedence relation on such abstract events is defined. [10] presents an abstraction algo-rithm on a causality graph with events as graph nodes to collapse nodes, e.g., events, into supernodes, e.g., abstract event. [11] proposes convex abstract events as good automated abstraction of events to enhance the expressiveness of the display of such abstract events. These approaches have in common that a possibility for the automated calculation is available. Low level events have to be collected from more than one node to form an abstract event.For example, assume a remote procedure call (RPC)first performing a lookup on a server to determine, where the function is implemented, afterwards calling the procedure and waiting for the result (cf. Figure3). The RPC considered as a whole is an abstract event in the execution of a program, the host lookup and the call themselves are abstract. Low level events are the arriving and leaving of messages on intermediate nodes. To construct this abstract event, the collection of the arrival and departure of messages of the RPC-protocol has to be performed. In addition involvednodes can combine these information and create an abstract request event. E.g., if the RPC-protocol is not working correctly, the top-level view shows the RPC event by starting a debugging session. Proceeding on a lower layer, for example, the call event never occurred,determining that the host lookup has failed. Stepping deeper in this hierarchy more details and, finally, the error can be detected.4.2Node ClusteringSince in modern networking environments operators deal with many nodes and links involved in the execu-tion and transmission of active messages, it is not pos-sible to visualize all these nodes together. Therefore, a clustering of nodes supports a structured overview. For monitoring purposes a clustering of highly intercon-nected nodes to one collapsed node is suitable,whereas for debugging, for example, a point-to-point protocol the programmer may choose to collapse all intermediate nodes in one visible node, only showing two end-system nodes with one intermediate in-between. If the concept of subnetworks is introduced in the active network environment too, a clustering of subnetworks can be performed easily. In general, find-ing highly interconnected nodes is a very complex task. The problem to be solved is to find an appropriate and automatically computable clustering. However,this is the problem of a programmer implementing a visualization tool. The important feature of computa-tional resources in the network is the fact that this clus-tering can take place within the network and only data of the collapsed node is sent to the displaying node.This mechanism reduces heavily the load on the net-work and the visualization workstation.4.3Event FilteringFiltering of events can take place at different locations on the path from the source to the sink. First, a selec-tion of all possible events on a node is collected. This loss of certain information happens from the begin-ning, but reducing a data stream at the source is the best way to save resources in the following computa-tion and transmission operations. Second, during the collection of events from different nodes, a filteringcan take place. For example, due to an overload situa-tion in the node or at the displaying end-system or if more than one display system is used for displaying a more precise view and an overview, filtering takes place at the branching node of the multicast tree. Third,on the workstation displaying events, a filtering can take place according to the preferences of the system manager maintaining the network. Naturally, this is not an ideal situation, because the information being trans-ferred to the displaying station should not be dis-carded. In this case, after some time filtering should happen within the network. Therefore, the filtering has to be flexible to support different requirements of a system operator.5A Framework for Monitoring and ManagementThe main design goal of the framework is to decouple hierarchical clustering of nodes, the monitoring pro-cess, and the introduction of new services for any kind of management services into the network.5.1Hierachical ClusteringTo attack the scalability to the number of nodes in the network a hierachical grouping of the nodes is suitable.So each node is a leaf in tree of clusters. Which nodes are aggregated together to a cluster, has to be open.E.g. if you want to measure performance of subnet-works, the clustering algorithm aggregates the nodes of a subnetworks. If the resources of a new connection are reserved and monitored, the cluster consists of all nodes over which this connection is running.So for each type of monitoring or management task a different tree of clusters is constructed, and held over some time. Each cluster has with it a level number identifying his depth in the tree.5.2Dynamic Data SelectionThe point to get and select node information is on the node itself. This can be done with the installation of a extraction service, which can be as dynamic as it has to be for a specific monitoring task. Typically the same service is installed on different nodes. The informationFigure 3: Example of an Event Hierarchy RPCcall look-uprequest response callreturninjectleavearrive....abstract events real low-level events Figure 4: Cluster Hierarchynodenodenode....clusters nodesnodenode123levelcan be stored in the nodes memory and accessed later by a information collector.5.3Level-specific InformationFor each cluster or node the relevant information can be stored in the memory of a node, representing the cluster. Access to this information can be level-spe-cific. E.g. the question is, how many messages of a specific type are moving thorough which networks? The lowest level cluster gathers the number of mes-sages of his nodes and stores it in his memory. The next upper node gathers the summed up values of his lower cluster. Now the manager may choose on which level he wants to get the information. This is dependent on the number of clusters, the bandwidth of the last link to the manager, the display or store capacity the managers station has.5.4Message typesIn this framework there are different predefined mes-sages to design and implement monitoring or manage-ment applications.•Installation of a service in a specific level in the cluster hierarchy. The service can be a monitoring service or a management service.•Child information collectors. They can be used to collect some information from the child clusters.This messages uses the information of the cluster tree.•Monitor information collectors. They get the infor-mation of a specific level for a monitor of the net-work. This messages reads information a service ora child information collector has stored.6ConclusionWith the introduction of active networks, we identified an even stronger need for network management which is not handled sufficiently in today’s networks, because of the increased complexity and flexibility. Therefore, an efficient and scalable network management is man-datory, if active networks are becoming a competition for today’s networks. We presented mechanisms to manage resources and global networks. The key factor in the management field is the problem of scalability to large networks and dynamic management functional-ity. To achieve scalable solutions in active networks, network management is decentralized by bringing the computation nearer to the managed objects. This results in a very flexible way to carry out management tasks with the introduction of code into the network, and provides the possibility to reduce the load on the management workstation by applying mechanisms as event abstraction, filtering, and node clustering. New management functionality may be implemented with-out changing the nodes’ interface.7References[1]Tennenhouse, D. L., Wetherall, D.J., “Towards anActive Network Architecture”, Multimedia Com-puting and Networking, San Jose, California, USA, January 1996, . [2]Tschudin, C. F., “On the Structuring of ComputerCommunications”, Dissertation 2632, University Geneve, Switzerland, 1993.[3]Buss, E., Henshaw, J., “A Software Reverse Engi-neering Experience”, Proceedings of the 1991 CAS Conference, Toronto, Canada, October 1991, pp 55-73.[4]Goldszmidt, G., Yemini, Y., “Distributed Manage-ment by Delegation”, Proceedings of the 15th International Conference on Distributed Comput-ing Systems, Vancouver, Canada, June 1995, pp 537-545.[5]Floyd, S., Jacobson, V., “Link-sharing andresource management models for packet net-works”, IEEE/ACM Transactions on Networking, vol. 3, no. 4, August 1995, pp 365-386.[6]Lamport, L., “Time, Clocks, and the Ordering ofEvents in a Distributed System”, Communication of the ACM, vol. 21, no. 7, July 1978, pp 558 -565.[7]Schwarz, R., Mattern, F.,”Detecting Casual Rela-tionships in Distributed Computations: In Search of the Holy Grail”. Distributed Computing, vol. 7, no. 3, September 1994, pp 149-174.[8]Ahuja, M., Mishra, S., “Units of Computation inFault-Tolerant Distributed Systems”, Proceedings of the 14th International Conference on Distrib-uted Computing Systems, Poland, June 1994, pp 626-633.[9]Krummer, D., Couch, A., Cybenko, G., “Debug-ging Support for Parallel Programs”, V ector and Parallel Computing: Issues in Applied Research and Development, Ellis Horwood, Chinester 1989, pp 205 - 214.[10]Zernik, D., Snir, M., Malki, D., “Using Visualiza-tion Tools to Understand Concurrency”, IEEE Software, vol. 9, no. 3, May 1992, pp 87-92. [11]Kunz, T., “High-Level Views of Distributed Exe-cution”, Proceedings of the 2nd International Workshop on Automated and Algorithmic Debug-ging, Saint Malo, France, May 1995.[12]Biersack, E. W., “Connection Management usingSynchronized Clocks”, Proceedings of the IFIP 3rd Conference on High Speed Networking, Ber-lin, Germany, March 1991, pp 225-239.。
T.W. ANDERSON (1971). The Statistical Analysis of Time Series. Series in Probability and Ma

425 BibliographyH.A KAIKE(1974).Markovian representation of stochastic processes and its application to the analysis of autoregressive moving average processes.Annals Institute Statistical Mathematics,vol.26,pp.363-387. B.D.O.A NDERSON and J.B.M OORE(1979).Optimal rmation and System Sciences Series, Prentice Hall,Englewood Cliffs,NJ.T.W.A NDERSON(1971).The Statistical Analysis of Time Series.Series in Probability and Mathematical Statistics,Wiley,New York.R.A NDRE-O BRECHT(1988).A new statistical approach for the automatic segmentation of continuous speech signals.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-36,no1,pp.29-40.R.A NDRE-O BRECHT(1990).Reconnaissance automatique de parole`a partir de segments acoustiques et de mod`e les de Markov cach´e s.Proc.Journ´e es Etude de la Parole,Montr´e al,May1990(in French).R.A NDRE-O BRECHT and H.Y.S U(1988).Three acoustic labellings for phoneme based continuous speech recognition.Proc.Speech’88,Edinburgh,UK,pp.943-950.U.A PPEL and A.VON B RANDT(1983).Adaptive sequential segmentation of piecewise stationary time rmation Sciences,vol.29,no1,pp.27-56.L.A.A ROIAN and H.L EVENE(1950).The effectiveness of quality control procedures.Jal American Statis-tical Association,vol.45,pp.520-529.K.J.A STR¨OM and B.W ITTENMARK(1984).Computer Controlled Systems:Theory and rma-tion and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.M.B AGSHAW and R.A.J OHNSON(1975a).The effect of serial correlation on the performance of CUSUM tests-Part II.Technometrics,vol.17,no1,pp.73-80.M.B AGSHAW and R.A.J OHNSON(1975b).The influence of reference values and estimated variance on the ARL of CUSUM tests.Jal Royal Statistical Society,vol.37(B),no3,pp.413-420.M.B AGSHAW and R.A.J OHNSON(1977).Sequential procedures for detecting parameter changes in a time-series model.Jal American Statistical Association,vol.72,no359,pp.593-597.R.K.B ANSAL and P.P APANTONI-K AZAKOS(1986).An algorithm for detecting a change in a stochastic process.IEEE rmation Theory,vol.IT-32,no2,pp.227-235.G.A.B ARNARD(1959).Control charts and stochastic processes.Jal Royal Statistical Society,vol.B.21, pp.239-271.A.E.B ASHARINOV andB.S.F LEISHMAN(1962).Methods of the statistical sequential analysis and their radiotechnical applications.Sovetskoe Radio,Moscow(in Russian).M.B ASSEVILLE(1978).D´e viations par rapport au maximum:formules d’arrˆe t et martingales associ´e es. Compte-rendus du S´e minaire de Probabilit´e s,Universit´e de Rennes I.M.B ASSEVILLE(1981).Edge detection using sequential methods for change in level-Part II:Sequential detection of change in mean.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-29,no1,pp.32-50.426B IBLIOGRAPHY M.B ASSEVILLE(1982).A survey of statistical failure detection techniques.In Contribution`a la D´e tectionS´e quentielle de Ruptures de Mod`e les Statistiques,Th`e se d’Etat,Universit´e de Rennes I,France(in English). M.B ASSEVILLE(1986).The two-models approach for the on-line detection of changes in AR processes. In Detection of Abrupt Changes in Signals and Dynamical Systems(M.Basseville,A.Benveniste,eds.). Lecture Notes in Control and Information Sciences,LNCIS77,Springer,New York,pp.169-215.M.B ASSEVILLE(1988).Detecting changes in signals and systems-A survey.Automatica,vol.24,pp.309-326.M.B ASSEVILLE(1989).Distance measures for signal processing and pattern recognition.Signal Process-ing,vol.18,pp.349-369.M.B ASSEVILLE and A.B ENVENISTE(1983a).Design and comparative study of some sequential jump detection algorithms for digital signals.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-31, no3,pp.521-535.M.B ASSEVILLE and A.B ENVENISTE(1983b).Sequential detection of abrupt changes in spectral charac-teristics of digital signals.IEEE rmation Theory,vol.IT-29,no5,pp.709-724.M.B ASSEVILLE and A.B ENVENISTE,eds.(1986).Detection of Abrupt Changes in Signals and Dynamical Systems.Lecture Notes in Control and Information Sciences,LNCIS77,Springer,New York.M.B ASSEVILLE and I.N IKIFOROV(1991).A unified framework for statistical change detection.Proc.30th IEEE Conference on Decision and Control,Brighton,UK.M.B ASSEVILLE,B.E SPIAU and J.G ASNIER(1981).Edge detection using sequential methods for change in level-Part I:A sequential edge detection algorithm.IEEE Trans.Acoustics,Speech,Signal Processing, vol.ASSP-29,no1,pp.24-31.M.B ASSEVILLE, A.B ENVENISTE and G.M OUSTAKIDES(1986).Detection and diagnosis of abrupt changes in modal characteristics of nonstationary digital signals.IEEE rmation Theory,vol.IT-32,no3,pp.412-417.M.B ASSEVILLE,A.B ENVENISTE,G.M OUSTAKIDES and A.R OUG´E E(1987a).Detection and diagnosis of changes in the eigenstructure of nonstationary multivariable systems.Automatica,vol.23,no3,pp.479-489. M.B ASSEVILLE,A.B ENVENISTE,G.M OUSTAKIDES and A.R OUG´E E(1987b).Optimal sensor location for detecting changes in dynamical behavior.IEEE Trans.Automatic Control,vol.AC-32,no12,pp.1067-1075.M.B ASSEVILLE,A.B ENVENISTE,B.G ACH-D EVAUCHELLE,M.G OURSAT,D.B ONNECASE,P.D OREY, M.P REVOSTO and M.O LAGNON(1993).Damage monitoring in vibration mechanics:issues in diagnos-tics and predictive maintenance.Mechanical Systems and Signal Processing,vol.7,no5,pp.401-423.R.V.B EARD(1971).Failure Accommodation in Linear Systems through Self-reorganization.Ph.D.Thesis, Dept.Aeronautics and Astronautics,MIT,Cambridge,MA.A.B ENVENISTE and J.J.F UCHS(1985).Single sample modal identification of a nonstationary stochastic process.IEEE Trans.Automatic Control,vol.AC-30,no1,pp.66-74.A.B ENVENISTE,M.B ASSEVILLE and G.M OUSTAKIDES(1987).The asymptotic local approach to change detection and model validation.IEEE Trans.Automatic Control,vol.AC-32,no7,pp.583-592.A.B ENVENISTE,M.M ETIVIER and P.P RIOURET(1990).Adaptive Algorithms and Stochastic Approxima-tions.Series on Applications of Mathematics,(A.V.Balakrishnan,I.Karatzas,M.Yor,eds.).Springer,New York.A.B ENVENISTE,M.B ASSEVILLE,L.E L G HAOUI,R.N IKOUKHAH and A.S.W ILLSKY(1992).An optimum robust approach to statistical failure detection and identification.IFAC World Conference,Sydney, July1993.B IBLIOGRAPHY427 R.H.B ERK(1973).Some asymptotic aspects of sequential analysis.Annals Statistics,vol.1,no6,pp.1126-1138.R.H.B ERK(1975).Locally most powerful sequential test.Annals Statistics,vol.3,no2,pp.373-381.P.B ILLINGSLEY(1968).Convergence of Probability Measures.Wiley,New York.A.F.B ISSELL(1969).Cusum techniques for quality control.Applied Statistics,vol.18,pp.1-30.M.E.B IVAIKOV(1991).Control of the sample size for recursive estimation of parameters subject to abrupt changes.Automation and Remote Control,no9,pp.96-103.R.E.B LAHUT(1987).Principles and Practice of Information Theory.Addison-Wesley,Reading,MA.I.F.B LAKE and W.C.L INDSEY(1973).Level-crossing problems for random processes.IEEE r-mation Theory,vol.IT-19,no3,pp.295-315.G.B ODENSTEIN and H.M.P RAETORIUS(1977).Feature extraction from the encephalogram by adaptive segmentation.Proc.IEEE,vol.65,pp.642-652.T.B OHLIN(1977).Analysis of EEG signals with changing spectra using a short word Kalman estimator. Mathematical Biosciences,vol.35,pp.221-259.W.B¨OHM and P.H ACKL(1990).Improved bounds for the average run length of control charts based on finite weighted sums.Annals Statistics,vol.18,no4,pp.1895-1899.T.B OJDECKI and J.H OSZA(1984).On a generalized disorder problem.Stochastic Processes and their Applications,vol.18,pp.349-359.L.I.B ORODKIN and V.V.M OTTL’(1976).Algorithm forfinding the jump times of random process equation parameters.Automation and Remote Control,vol.37,no6,Part1,pp.23-32.A.A.B OROVKOV(1984).Theory of Mathematical Statistics-Estimation and Hypotheses Testing,Naouka, Moscow(in Russian).Translated in French under the title Statistique Math´e matique-Estimation et Tests d’Hypoth`e ses,Mir,Paris,1987.G.E.P.B OX and G.M.J ENKINS(1970).Time Series Analysis,Forecasting and Control.Series in Time Series Analysis,Holden-Day,San Francisco.A.VON B RANDT(1983).Detecting and estimating parameters jumps using ladder algorithms and likelihood ratio test.Proc.ICASSP,Boston,MA,pp.1017-1020.A.VON B RANDT(1984).Modellierung von Signalen mit Sprunghaft Ver¨a nderlichem Leistungsspektrum durch Adaptive Segmentierung.Doctor-Engineer Dissertation,M¨u nchen,RFA(in German).S.B RAUN,ed.(1986).Mechanical Signature Analysis-Theory and Applications.Academic Press,London. L.B REIMAN(1968).Probability.Series in Statistics,Addison-Wesley,Reading,MA.G.S.B RITOV and L.A.M IRONOVSKI(1972).Diagnostics of linear systems of automatic regulation.Tekh. Kibernetics,vol.1,pp.76-83.B.E.B RODSKIY and B.S.D ARKHOVSKIY(1992).Nonparametric Methods in Change-point Problems. Kluwer Academic,Boston.L.D.B ROEMELING(1982).Jal Econometrics,vol.19,Special issue on structural change in Econometrics. L.D.B ROEMELING and H.T SURUMI(1987).Econometrics and Structural Change.Dekker,New York. D.B ROOK and D.A.E VANS(1972).An approach to the probability distribution of Cusum run length. Biometrika,vol.59,pp.539-550.J.B RUNET,D.J AUME,M.L ABARR`E RE,A.R AULT and M.V ERG´E(1990).D´e tection et Diagnostic de Pannes.Trait´e des Nouvelles Technologies,S´e rie Diagnostic et Maintenance,Herm`e s,Paris(in French).428B IBLIOGRAPHY S.P.B RUZZONE and M.K AVEH(1984).Information tradeoffs in using the sample autocorrelation function in ARMA parameter estimation.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-32,no4, pp.701-715.A.K.C AGLAYAN(1980).Necessary and sufficient conditions for detectability of jumps in linear systems. IEEE Trans.Automatic Control,vol.AC-25,no4,pp.833-834.A.K.C AGLAYAN and R.E.L ANCRAFT(1983).Reinitialization issues in fault tolerant systems.Proc.Amer-ican Control Conf.,pp.952-955.A.K.C AGLAYAN,S.M.A LLEN and K.W EHMULLER(1988).Evaluation of a second generation reconfigu-ration strategy for aircraftflight control systems subjected to actuator failure/surface damage.Proc.National Aerospace and Electronic Conference,Dayton,OH.P.E.C AINES(1988).Linear Stochastic Systems.Series in Probability and Mathematical Statistics,Wiley, New York.M.J.C HEN and J.P.N ORTON(1987).Estimation techniques for tracking rapid parameter changes.Intern. Jal Control,vol.45,no4,pp.1387-1398.W.K.C HIU(1974).The economic design of cusum charts for controlling normal mean.Applied Statistics, vol.23,no3,pp.420-433.E.Y.C HOW(1980).A Failure Detection System Design Methodology.Ph.D.Thesis,M.I.T.,L.I.D.S.,Cam-bridge,MA.E.Y.C HOW and A.S.W ILLSKY(1984).Analytical redundancy and the design of robust failure detection systems.IEEE Trans.Automatic Control,vol.AC-29,no3,pp.689-691.Y.S.C HOW,H.R OBBINS and D.S IEGMUND(1971).Great Expectations:The Theory of Optimal Stop-ping.Houghton-Mifflin,Boston.R.N.C LARK,D.C.F OSTH and V.M.W ALTON(1975).Detection of instrument malfunctions in control systems.IEEE Trans.Aerospace Electronic Systems,vol.AES-11,pp.465-473.A.C OHEN(1987).Biomedical Signal Processing-vol.1:Time and Frequency Domain Analysis;vol.2: Compression and Automatic Recognition.CRC Press,Boca Raton,FL.J.C ORGE and F.P UECH(1986).Analyse du rythme cardiaque foetal par des m´e thodes de d´e tection de ruptures.Proc.7th INRIA Int.Conf.Analysis and optimization of Systems.Antibes,FR(in French).D.R.C OX and D.V.H INKLEY(1986).Theoretical Statistics.Chapman and Hall,New York.D.R.C OX and H.D.M ILLER(1965).The Theory of Stochastic Processes.Wiley,New York.S.V.C ROWDER(1987).A simple method for studying run-length distributions of exponentially weighted moving average charts.Technometrics,vol.29,no4,pp.401-407.H.C S¨ORG¨O and L.H ORV´ATH(1988).Nonparametric methods for change point problems.In Handbook of Statistics(P.R.Krishnaiah,C.R.Rao,eds.),vol.7,Elsevier,New York,pp.403-425.R.B.D AVIES(1973).Asymptotic inference in stationary gaussian time series.Advances Applied Probability, vol.5,no3,pp.469-497.J.C.D ECKERT,M.N.D ESAI,J.J.D EYST and A.S.W ILLSKY(1977).F-8DFBW sensor failure identification using analytical redundancy.IEEE Trans.Automatic Control,vol.AC-22,no5,pp.795-803.M.H.D E G ROOT(1970).Optimal Statistical Decisions.Series in Probability and Statistics,McGraw-Hill, New York.J.D ESHAYES and D.P ICARD(1979).Tests de ruptures dans un mod`e pte-Rendus de l’Acad´e mie des Sciences,vol.288,Ser.A,pp.563-566(in French).B IBLIOGRAPHY429 J.D ESHAYES and D.P ICARD(1983).Ruptures de Mod`e les en Statistique.Th`e ses d’Etat,Universit´e deParis-Sud,Orsay,France(in French).J.D ESHAYES and D.P ICARD(1986).Off-line statistical analysis of change-point models using non para-metric and likelihood methods.In Detection of Abrupt Changes in Signals and Dynamical Systems(M. Basseville,A.Benveniste,eds.).Lecture Notes in Control and Information Sciences,LNCIS77,Springer, New York,pp.103-168.B.D EVAUCHELLE-G ACH(1991).Diagnostic M´e canique des Fatigues sur les Structures Soumises`a des Vibrations en Ambiance de Travail.Th`e se de l’Universit´e Paris IX Dauphine(in French).B.D EVAUCHELLE-G ACH,M.B ASSEVILLE and A.B ENVENISTE(1991).Diagnosing mechanical changes in vibrating systems.Proc.SAFEPROCESS’91,Baden-Baden,FRG,pp.85-89.R.D I F RANCESCO(1990).Real-time speech segmentation using pitch and convexity jump models:applica-tion to variable rate speech coding.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-38,no5, pp.741-748.X.D ING and P.M.F RANK(1990).Fault detection via factorization approach.Systems and Control Letters, vol.14,pp.431-436.J.L.D OOB(1953).Stochastic Processes.Wiley,New York.V.D RAGALIN(1988).Asymptotic solutions in detecting a change in distribution under an unknown param-eter.Statistical Problems of Control,Issue83,Vilnius,pp.45-52.B.D UBUISSON(1990).Diagnostic et Reconnaissance des Formes.Trait´e des Nouvelles Technologies,S´e rie Diagnostic et Maintenance,Herm`e s,Paris(in French).A.J.D UNCAN(1986).Quality Control and Industrial Statistics,5th edition.Richard D.Irwin,Inc.,Home-wood,IL.J.D URBIN(1971).Boundary-crossing probabilities for the Brownian motion and Poisson processes and techniques for computing the power of the Kolmogorov-Smirnov test.Jal Applied Probability,vol.8,pp.431-453.J.D URBIN(1985).Thefirst passage density of the crossing of a continuous Gaussian process to a general boundary.Jal Applied Probability,vol.22,no1,pp.99-122.A.E MAMI-N AEINI,M.M.A KHTER and S.M.R OCK(1988).Effect of model uncertainty on failure detec-tion:the threshold selector.IEEE Trans.Automatic Control,vol.AC-33,no12,pp.1106-1115.J.D.E SARY,F.P ROSCHAN and D.W.W ALKUP(1967).Association of random variables with applications. Annals Mathematical Statistics,vol.38,pp.1466-1474.W.D.E WAN and K.W.K EMP(1960).Sampling inspection of continuous processes with no autocorrelation between successive results.Biometrika,vol.47,pp.263-280.G.F AVIER and A.S MOLDERS(1984).Adaptive smoother-predictors for tracking maneuvering targets.Proc. 23rd Conf.Decision and Control,Las Vegas,NV,pp.831-836.W.F ELLER(1966).An Introduction to Probability Theory and Its Applications,vol.2.Series in Probability and Mathematical Statistics,Wiley,New York.R.A.F ISHER(1925).Theory of statistical estimation.Proc.Cambridge Philosophical Society,vol.22, pp.700-725.M.F ISHMAN(1988).Optimization of the algorithm for the detection of a disorder,based on the statistic of exponential smoothing.In Statistical Problems of Control,Issue83,Vilnius,pp.146-151.R.F LETCHER(1980).Practical Methods of Optimization,2volumes.Wiley,New York.P.M.F RANK(1990).Fault diagnosis in dynamic systems using analytical and knowledge based redundancy -A survey and new results.Automatica,vol.26,pp.459-474.430B IBLIOGRAPHY P.M.F RANK(1991).Enhancement of robustness in observer-based fault detection.Proc.SAFEPRO-CESS’91,Baden-Baden,FRG,pp.275-287.P.M.F RANK and J.W¨UNNENBERG(1989).Robust fault diagnosis using unknown input observer schemes. In Fault Diagnosis in Dynamic Systems-Theory and Application(R.Patton,P.Frank,R.Clark,eds.). International Series in Systems and Control Engineering,Prentice Hall International,London,UK,pp.47-98.K.F UKUNAGA(1990).Introduction to Statistical Pattern Recognition,2d ed.Academic Press,New York. S.I.G ASS(1958).Linear Programming:Methods and Applications.McGraw Hill,New York.W.G E and C.Z.F ANG(1989).Extended robust observation approach for failure isolation.Int.Jal Control, vol.49,no5,pp.1537-1553.W.G ERSCH(1986).Two applications of parametric time series modeling methods.In Mechanical Signature Analysis-Theory and Applications(S.Braun,ed.),chap.10.Academic Press,London.J.J.G ERTLER(1988).Survey of model-based failure detection and isolation in complex plants.IEEE Control Systems Magazine,vol.8,no6,pp.3-11.J.J.G ERTLER(1991).Analytical redundancy methods in fault detection and isolation.Proc.SAFEPRO-CESS’91,Baden-Baden,FRG,pp.9-22.B.K.G HOSH(1970).Sequential Tests of Statistical Hypotheses.Addison-Wesley,Cambridge,MA.I.N.G IBRA(1975).Recent developments in control charts techniques.Jal Quality Technology,vol.7, pp.183-192.J.P.G ILMORE and R.A.M C K ERN(1972).A redundant strapdown inertial reference unit(SIRU).Jal Space-craft,vol.9,pp.39-47.M.A.G IRSHICK and H.R UBIN(1952).A Bayes approach to a quality control model.Annals Mathematical Statistics,vol.23,pp.114-125.A.L.G OEL and S.M.W U(1971).Determination of the ARL and a contour nomogram for CUSUM charts to control normal mean.Technometrics,vol.13,no2,pp.221-230.P.L.G OLDSMITH and H.W HITFIELD(1961).Average run lengths in cumulative chart quality control schemes.Technometrics,vol.3,pp.11-20.G.C.G OODWIN and K.S.S IN(1984).Adaptive Filtering,Prediction and rmation and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.R.M.G RAY and L.D.D AVISSON(1986).Random Processes:a Mathematical Approach for Engineers. Information and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.C.G UEGUEN and L.L.S CHARF(1980).Exact maximum likelihood identification for ARMA models:a signal processing perspective.Proc.1st EUSIPCO,Lausanne.D.E.G USTAFSON, A.S.W ILLSKY,J.Y.W ANG,M.C.L ANCASTER and J.H.T RIEBWASSER(1978). ECG/VCG rhythm diagnosis using statistical signal analysis.Part I:Identification of persistent rhythms. Part II:Identification of transient rhythms.IEEE Trans.Biomedical Engineering,vol.BME-25,pp.344-353 and353-361.F.G USTAFSSON(1991).Optimal segmentation of linear regression parameters.Proc.IFAC/IFORS Symp. Identification and System Parameter Estimation,Budapest,pp.225-229.T.H¨AGGLUND(1983).New Estimation Techniques for Adaptive Control.Ph.D.Thesis,Lund Institute of Technology,Lund,Sweden.T.H¨AGGLUND(1984).Adaptive control of systems subject to large parameter changes.Proc.IFAC9th World Congress,Budapest.B IBLIOGRAPHY431 P.H ALL and C.C.H EYDE(1980).Martingale Limit Theory and its Application.Probability and Mathemat-ical Statistics,a Series of Monographs and Textbooks,Academic Press,New York.W.J.H ALL,R.A.W IJSMAN and J.K.G HOSH(1965).The relationship between sufficiency and invariance with applications in sequential analysis.Ann.Math.Statist.,vol.36,pp.576-614.E.J.H ANNAN and M.D EISTLER(1988).The Statistical Theory of Linear Systems.Series in Probability and Mathematical Statistics,Wiley,New York.J.D.H EALY(1987).A note on multivariate CuSum procedures.Technometrics,vol.29,pp.402-412.D.M.H IMMELBLAU(1970).Process Analysis by Statistical Methods.Wiley,New York.D.M.H IMMELBLAU(1978).Fault Detection and Diagnosis in Chemical and Petrochemical Processes. Chemical Engineering Monographs,vol.8,Elsevier,Amsterdam.W.G.S.H INES(1976a).A simple monitor of a system with sudden parameter changes.IEEE r-mation Theory,vol.IT-22,no2,pp.210-216.W.G.S.H INES(1976b).Improving a simple monitor of a system with sudden parameter changes.IEEE rmation Theory,vol.IT-22,no4,pp.496-499.D.V.H INKLEY(1969).Inference about the intersection in two-phase regression.Biometrika,vol.56,no3, pp.495-504.D.V.H INKLEY(1970).Inference about the change point in a sequence of random variables.Biometrika, vol.57,no1,pp.1-17.D.V.H INKLEY(1971).Inference about the change point from cumulative sum-tests.Biometrika,vol.58, no3,pp.509-523.D.V.H INKLEY(1971).Inference in two-phase regression.Jal American Statistical Association,vol.66, no336,pp.736-743.J.R.H UDDLE(1983).Inertial navigation system error-model considerations in Kalmanfiltering applica-tions.In Control and Dynamic Systems(C.T.Leondes,ed.),Academic Press,New York,pp.293-339.J.S.H UNTER(1986).The exponentially weighted moving average.Jal Quality Technology,vol.18,pp.203-210.I.A.I BRAGIMOV and R.Z.K HASMINSKII(1981).Statistical Estimation-Asymptotic Theory.Applications of Mathematics Series,vol.16.Springer,New York.R.I SERMANN(1984).Process fault detection based on modeling and estimation methods-A survey.Auto-matica,vol.20,pp.387-404.N.I SHII,A.I WATA and N.S UZUMURA(1979).Segmentation of nonstationary time series.Int.Jal Systems Sciences,vol.10,pp.883-894.J.E.J ACKSON and R.A.B RADLEY(1961).Sequential and tests.Annals Mathematical Statistics, vol.32,pp.1063-1077.B.J AMES,K.L.J AMES and D.S IEGMUND(1988).Conditional boundary crossing probabilities with appli-cations to change-point problems.Annals Probability,vol.16,pp.825-839.M.K.J EERAGE(1990).Reliability analysis of fault-tolerant IMU architectures with redundant inertial sen-sors.IEEE Trans.Aerospace and Electronic Systems,vol.AES-5,no.7,pp.23-27.N.L.J OHNSON(1961).A simple theoretical approach to cumulative sum control charts.Jal American Sta-tistical Association,vol.56,pp.835-840.N.L.J OHNSON and F.C.L EONE(1962).Cumulative sum control charts:mathematical principles applied to their construction and use.Parts I,II,III.Industrial Quality Control,vol.18,pp.15-21;vol.19,pp.29-36; vol.20,pp.22-28.432B IBLIOGRAPHY R.A.J OHNSON and M.B AGSHAW(1974).The effect of serial correlation on the performance of CUSUM tests-Part I.Technometrics,vol.16,no.1,pp.103-112.H.L.J ONES(1973).Failure Detection in Linear Systems.Ph.D.Thesis,Dept.Aeronautics and Astronautics, MIT,Cambridge,MA.R.H.J ONES,D.H.C ROWELL and L.E.K APUNIAI(1970).Change detection model for serially correlated multivariate data.Biometrics,vol.26,no2,pp.269-280.M.J URGUTIS(1984).Comparison of the statistical properties of the estimates of the change times in an autoregressive process.In Statistical Problems of Control,Issue65,Vilnius,pp.234-243(in Russian).T.K AILATH(1980).Linear rmation and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.L.V.K ANTOROVICH and V.I.K RILOV(1958).Approximate Methods of Higher Analysis.Interscience,New York.S.K ARLIN and H.M.T AYLOR(1975).A First Course in Stochastic Processes,2d ed.Academic Press,New York.S.K ARLIN and H.M.T AYLOR(1981).A Second Course in Stochastic Processes.Academic Press,New York.D.K AZAKOS and P.P APANTONI-K AZAKOS(1980).Spectral distance measures between gaussian pro-cesses.IEEE Trans.Automatic Control,vol.AC-25,no5,pp.950-959.K.W.K EMP(1958).Formula for calculating the operating characteristic and average sample number of some sequential tests.Jal Royal Statistical Society,vol.B-20,no2,pp.379-386.K.W.K EMP(1961).The average run length of the cumulative sum chart when a V-mask is used.Jal Royal Statistical Society,vol.B-23,pp.149-153.K.W.K EMP(1967a).Formal expressions which can be used for the determination of operating character-istics and average sample number of a simple sequential test.Jal Royal Statistical Society,vol.B-29,no2, pp.248-262.K.W.K EMP(1967b).A simple procedure for determining upper and lower limits for the average sample run length of a cumulative sum scheme.Jal Royal Statistical Society,vol.B-29,no2,pp.263-265.D.P.K ENNEDY(1976).Some martingales related to cumulative sum tests and single server queues.Stochas-tic Processes and Appl.,vol.4,pp.261-269.T.H.K ERR(1980).Statistical analysis of two-ellipsoid overlap test for real time failure detection.IEEE Trans.Automatic Control,vol.AC-25,no4,pp.762-772.T.H.K ERR(1982).False alarm and correct detection probabilities over a time interval for restricted classes of failure detection algorithms.IEEE rmation Theory,vol.IT-24,pp.619-631.T.H.K ERR(1987).Decentralizedfiltering and redundancy management for multisensor navigation.IEEE Trans.Aerospace and Electronic systems,vol.AES-23,pp.83-119.Minor corrections on p.412and p.599 (May and July issues,respectively).R.A.K HAN(1978).Wald’s approximations to the average run length in cusum procedures.Jal Statistical Planning and Inference,vol.2,no1,pp.63-77.R.A.K HAN(1979).Somefirst passage problems related to cusum procedures.Stochastic Processes and Applications,vol.9,no2,pp.207-215.R.A.K HAN(1981).A note on Page’s two-sided cumulative sum procedures.Biometrika,vol.68,no3, pp.717-719.B IBLIOGRAPHY433 V.K IREICHIKOV,V.M ANGUSHEV and I.N IKIFOROV(1990).Investigation and application of CUSUM algorithms to monitoring of sensors.In Statistical Problems of Control,Issue89,Vilnius,pp.124-130(in Russian).G.K ITAGAWA and W.G ERSCH(1985).A smoothness prior time-varying AR coefficient modeling of non-stationary covariance time series.IEEE Trans.Automatic Control,vol.AC-30,no1,pp.48-56.N.K LIGIENE(1980).Probabilities of deviations of the change point estimate in statistical models.In Sta-tistical Problems of Control,Issue83,Vilnius,pp.80-86(in Russian).N.K LIGIENE and L.T ELKSNYS(1983).Methods of detecting instants of change of random process prop-erties.Automation and Remote Control,vol.44,no10,Part II,pp.1241-1283.J.K ORN,S.W.G ULLY and A.S.W ILLSKY(1982).Application of the generalized likelihood ratio algorithm to maneuver detection and estimation.Proc.American Control Conf.,Arlington,V A,pp.792-798.P.R.K RISHNAIAH and B.Q.M IAO(1988).Review about estimation of change points.In Handbook of Statistics(P.R.Krishnaiah,C.R.Rao,eds.),vol.7,Elsevier,New York,pp.375-402.P.K UDVA,N.V ISWANADHAM and A.R AMAKRISHNAN(1980).Observers for linear systems with unknown inputs.IEEE Trans.Automatic Control,vol.AC-25,no1,pp.113-115.S.K ULLBACK(1959).Information Theory and Statistics.Wiley,New York(also Dover,New York,1968). K.K UMAMARU,S.S AGARA and T.S¨ODERSTR¨OM(1989).Some statistical methods for fault diagnosis for dynamical systems.In Fault Diagnosis in Dynamic Systems-Theory and Application(R.Patton,P.Frank,R. Clark,eds.).International Series in Systems and Control Engineering,Prentice Hall International,London, UK,pp.439-476.A.K USHNIR,I.N IKIFOROV and I.S AVIN(1983).Statistical adaptive algorithms for automatic detection of seismic signals-Part I:One-dimensional case.In Earthquake Prediction and the Study of the Earth Structure,Naouka,Moscow(Computational Seismology,vol.15),pp.154-159(in Russian).L.L ADELLI(1990).Diffusion approximation for a pseudo-likelihood test process with application to de-tection of change in stochastic system.Stochastics and Stochastics Reports,vol.32,pp.1-25.T.L.L A¨I(1974).Control charts based on weighted sums.Annals Statistics,vol.2,no1,pp.134-147.T.L.L A¨I(1981).Asymptotic optimality of invariant sequential probability ratio tests.Annals Statistics, vol.9,no2,pp.318-333.D.G.L AINIOTIS(1971).Joint detection,estimation,and system identifirmation and Control, vol.19,pp.75-92.M.R.L EADBETTER,G.L INDGREN and H.R OOTZEN(1983).Extremes and Related Properties of Random Sequences and Processes.Series in Statistics,Springer,New York.L.L E C AM(1960).Locally asymptotically normal families of distributions.Univ.California Publications in Statistics,vol.3,pp.37-98.L.L E C AM(1986).Asymptotic Methods in Statistical Decision Theory.Series in Statistics,Springer,New York.E.L.L EHMANN(1986).Testing Statistical Hypotheses,2d ed.Wiley,New York.J.P.L EHOCZKY(1977).Formulas for stopped diffusion processes with stopping times based on the maxi-mum.Annals Probability,vol.5,no4,pp.601-607.H.R.L ERCHE(1980).Boundary Crossing of Brownian Motion.Lecture Notes in Statistics,vol.40,Springer, New York.L.L JUNG(1987).System Identification-Theory for the rmation and System Sciences Series, Prentice Hall,Englewood Cliffs,NJ.。
管理研究方法(英文版第13版)教学课件Schindler_CH_03_Accessible

© 2019 McGraw-Hill Education.
3-3
Tasks Associated with Stage 1
Jump to long description
© 2019 McGraw-Hill Education.
3-4
The Management-Research Question Hierarchy
be affected by any considered solution.
© 2019 McGraw-Hill Education.
3-16
Questions to Ask of People Sources
What is being done? What has been tried in the past with or without success? How have things changed? Who is involved in the decisions? What problem areas can be seen? Whom can we count on to assist or participate in research on this issue/topic?
• Establish range and scope of possible management decisions.
• Establish major dimensions of research task.
• Define a set of subsidiary questions that can guide research design.
• How well is our (blank) program meeting its goals?
On_Phases
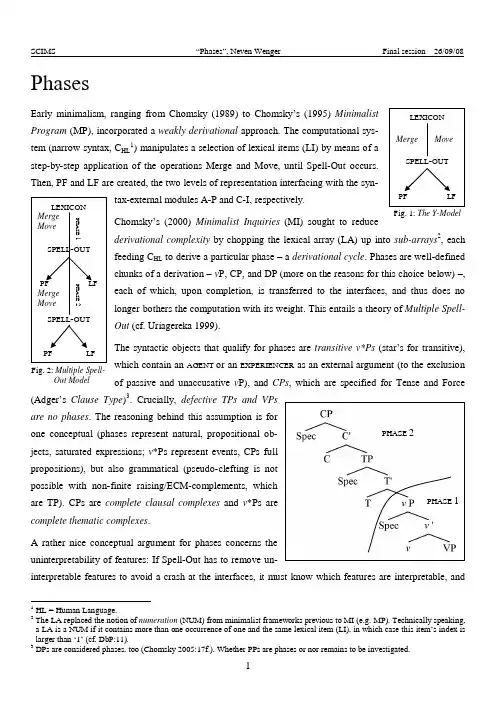
PhasesEarly minimalism, ranging from Chomsky (1989) to Chomsky’s (1995)MinimalistProgram (MP), incorporated a weakly derivational approach. The computational sys-tem (narrow syntax, C HL 1) manipulates a selection of lexical items (LI) by means of astep-by-step application of the operations Merge and Move, until Spell-Out occurs.Then, PF and LF are created, the two levels of representation interfacing with the syn-tax-external modules A-P and C-I, respectively.Chomsky’s (2000)Minimalist Inquiries (MI) sought to reduce derivational complexity by chopping the lexical array (LA) up into sub-arrays 2, each feeding C HL to derive a particular phase – a derivational cycle .Phases are well-defined chunks of a derivation –v P, CP, and DP (more on the reasons for this choice below) –,each of which, upon completion, is transferred to the interfaces, and thus does no longer bothers the computation with its weight. This entails a theory of Multiple Spell-Out (cf. Uriagereka 1999).The syntactic objects that qualify for phases are transitive v*Ps (star’s for transitive),which contain an AGENT or an EXPERIENCER as an external argument (to the exclusion of passive and unaccusative v P), and CPs , which are specified for Tense and Force(Adger’s Clause Type )3. Crucially,defective TPs and VPsare no phases . The reasoning behind this assumption is forone conceptual (phases represent natural, propositional ob-jects, saturated expressions;v *Ps represent events, CPs fullpropositions), but also grammatical (pseudo-clefting is notpossible with non-finite raising/ECM-complements, whichare TP). CPs are complete clausal complexes and v *Ps arecomplete thematic complexes .A rather nice conceptual argument for phases concerns theuninterpretability of features: If Spell-Out has to remove un-interpretable features to avoid a crash at the interfaces, it must know which features are interpretable, and 1HL = Human Language.2 The LA replaced the notion of numeration (NUM) from minimalist frameworks previous to MI (e.g. MP). Technically speaking,a LA is a NUM if it contains more than one occurrence of one and the same lexical item (LI), in which case this item’s index is larger than ‘1’ (cf. DbP:11).3 DPs are considered phases, too (Chomsky 2005:17f.). Whether PPs are phases or nor remains to be investigated.Fig.1: Y-ModelFig.2:Multiple Spell-PHASE 1 PHASE 2to be someone here] –Merge there& check EPP]D. [TP T[EPP] [VP seems [TP there T[EPP] to be someone here]]] –Merge TE. [TP there T[EPP] [VP seems [TP there T[EPP] to be someone here]]] –Move there& check EPPNow consider the derivation of the ungrammatical (2)(1), based on the same numeration, taking another option at step B.A. [TP T[EPP] to be someone here] –Merge TB.[TP someone T[EPP] to be someone here] –Move someone& check EPPD. [TP T[EPP] [VP seems [TP someone T[EPP] to be someone here]]] –Merge TE. [TP there T[EPP] [VP seems [TP someone T[EPP] to be someone here]]] –Merge there& check EPPThe derivational step B of (2) violates Merge-over-Move, moving someone instead of merging the expletive there available in the Num, which is why the derivation produces an ill-formed sentence. Defining different sub-arrays for (2), provided the phasehood of v P and CP, can capture this issue derivationally:(3)a. {{C, T}3 {seem, there, T, to}2 {be, someone, here}1}. There seems to be someone here. –(2)be a man in the room] –Move a man & check EPP]C. [CP that a man was[EPP] be a man in the room] –Merge C/thatD. [TP T[EPP] [be a rumour that a man was[EPP]be a man in the room]] –Merge TE. [CP[TP there was[EPP] be a rumour that a man was[EPP] be a man in the room]] –Merge there&check EPP Dividing Num up into lexical sub-arrays gets rid of the problem: if in the second sub-array {…}2 no exple-tive is available, subject raising can take place.Phases consist of three parts: the phase head H (v/C), its complement ZP (the internal domain), and its edge YP (the specifier domain). After completion, the phase is inaccessible to further operations, as formally cap-tured by the Phase-Impenetrability Condition(PIC): “In phase with the head H, the domain of H is not accessible to operations outside , only H and its edge are accessible to such operations” (Chomsky 2000:108).To ensure classic successive cyclic movement (DPs moving up the tree have to make stops in the Specs of other heads), Chomsky allows a phases edge, together with the phase head, to remain accessible even after completion of a given phase (e.g. as intermediate landing site for long-distance movement – an escape hatch). This means that once a phase is completed, it is no longer accessible to operations – it is impenetra-However, unlike the bulk of minimalist theory, phases have spawned critical reactions within the minimalist camp. Thus, Boeckx & Grohmann (2005), for example, critically examine phase theory, essentially identify-ing it as old wine in new bottles (islands, bounding nodes, successive cyclicity, etc.): “[Phases] simply re-code insights from the past” (ibid.:1). Still, it should be noted that it simply is Chomsky’s phase theory that is most often exposed, for he is the leading figure in mainstream generative linguistics; but there are plenty of similar proposals relying on phase-like concepts, differing from Chomsky’s proposal in one or the other relevant aspect (e.g. Uriagereka’s 1999cascades, Grohmann’s 2003prolific domains). Furthermore, there are radically derivational approaches to syntax (cf. e.g. Epstein & Seely 2006; Chomsky’s is weakly deriva-tional), which have eliminated any level of representation (LF, PF), to the effect that a derivation is dynami-cally accessed by the interfaces at every derivational step (i.e. the smallest phases ever!).This squib was supposed to be only a technical outline of the motivation for and the implementation of phases in the minimalist framework. Many interesting aspects are left untouched, of course. For example, it is worth taking a look at defective (i.e. approximately, non-finite) TPs and intransitive v P, and how they differ derivationally from their phasal counterparts. In addition, Probe-Goal theory (Agree), which has fig-ured prominently during our SCIMS, is closely associated with the introduction of phases.4 In Chomsky (2000), [EDGE] was construed as a peripheral feature [P], in Chomsky (2001, 2004) as a generalised EPP feature[EPP], in analogy to the classic T-related [EPP]:。
大五人格模型和大三人格模型的比较
LOOKING BEYOND THE FIVE-FACTOR MODEL: COLLEGE SELF-EFFICACY AS A MODERATOR OF THE RELATIONSHIPBETWEEN TELLEGEN’S BIG THREE MODEL OF PERSONALITY AND HOLLAND’S MODEL OF VOCATIONAL INTEREST TYPESBy Elizabeth A BarrettThe Five-Factor Model (FFM) of personality and Tellegen’s Big Three Model of personality were compared to determine their ability to predict Holland’s RIASEC interest types. College self-efficacy was examined as a moderator of the relationship between Tellegen’s Big Three model and the RIASEC interest types. A sample of 194 college freshmen (i.e., less than 30 credits completed) was drawn from the psychology participant pool of a mid-sized Midwestern university. Instruments included the International Personality Item Pool (IPIP) to measure the FFM; the Multidimensional Personality Questionnaire Brief Form (MPQ-BF) to measure Tellegen’s Big Three model of personality; the College Self-Efficacy Inventory (CSEI) to measure college self-efficacy; and the Self Directed Search (SDS) to measure Holland’s RIASEC model of vocational interests. Findings from correlational analyses supported previous research regarding relationships among the FFM and the RIASEC interest types, and relationships among Tellegen’s Big Three and the RIASEC interest types. As hypothesized and tested via regressions for each of the six interest types, Tellegen’s Big Three model predicted all six vocational interests types (p < .001 for all), while the FFM only predicted two types at p < .05. College self-efficacy did not moderate the relationship between Tellegen’s Big Three and the RIASEC interest types. Implications and future research are discussed.ACKNOWLEDGEMENTSSeveral people have assisted me with the completion of this thesis, and I wish to thank the following people for their help and guidance:In acknowledgement of excellent guidance of this project, Dr. McFadden chairperson, whose knowledge and encouragement pushed the progress of this thesis and my development as a writer and researcher.Dr. Adams and Dr. Miron, committee members, who graciously gave their time and shared their expertise in the completion of this project, specifically, Dr. Adams who aided with the data analysis of this project and worked through multiple analysis problems with me.iiTABLE OF CONTENTSPage INTRODUCTION (1)THEORY AND LITERATURE REVIEW (4)Personality Traits and Vocational Interests Defined (4)The Five-Factor Model (FFM) of Personality (4)Holland’s Theory of Vocational Interest Types (5)Overlap between the FFM and RIASEC (7)Criticisms and Limitations of the FFM (9)Looking Beyond the FFM: Tellegen’s Big Three Model of Personality (11)Comparing Tellegen’s Big Three and the FFM (14)College Self-Efficacy: Moderating Role (16)Conclusion (20)METHOD (22)Participants (22)Procedure (23)Measures (23)Methods of Data Analysis and Missing Data (27)RESULTS (29)Descriptive Statistics (29)Relationship between the FFM and the RIASEC Interest Types:Hypothesis 1a-1e (29)Relationship between Tellegen’s Big Three and the RIASEC InterestTypes: Hypothesis 2a-2c (30)Comparing the FFM and Tellegen’s Big Three: Hypothesis 3 (31)College Self-Efficacy as Moderator: Hypothesis 4 (32)iiiTABLE OF CONTENTS (continued) DISCUSSION (34)The Relationship between the FFM and the RIASEC Interest Types (34)The Relationship between Tellegen’s Big Three and the RIASECInterest Types (35)Comparing Tellegen’s Big Three and the FFM (36)College Self-Efficacy as a Moderator (37)Limitations (38)Implications and Future Research (39)Conclusions (41)APPENDIXES (42)Appendix A: Tables (42)Table A-1. Holland’s Vocational Personality Types Described: RIASEC.. 43 Table A-2. Overlap Between the FFM and RIASEC (44)Table A-3. The Big Three of Tellegen measured by the MPQ: HigherOrder and Primary Trait Scales (45)Table A-4. Means, Standard Deviations, and Intercorrelations (47)Table A-5. Regression Analysis: Realistic Interest Type as DependentVariable (48)Table A-6. Regression Analysis: Investigative Interest Type as DependentVariable (48)Table A-7. Regression Analysis: Artistic Interest Type as DependentVariable (49)Table A-8. Regression Analysis: Social Interest Type as DependentVariable (49)Table A-9. Regression Analysis: Enterprising Interest Type as DependentVariable (50)Table A-10. Regression Analysis: Conventional Interest Type asDependent Variable (50)Table A-11. Hierarchical Multiple Moderated Regression Analysis:Realistic Interest Type as Dependent Variable (51)Table A-12. Hierarchical Multiple Moderated Regression Analysis:Investigative Interest Type as Dependent Variable (51)Table A-13. Hierarchical Multiple Moderated Regression Analysis:Artistic Interest Type as Dependent Variable (52)Table A-14. Hierarchical Multiple Moderated Regression Analysis: SocialInterest Type as Dependent Variable (52)Table A-15. Hierarchical Multiple Moderated Regression Analysis:Enterprising Interest Type as Dependent Variable (53)ivTABLE OF CONTENTS (continued)Table A-16. Hierarchical Multiple Moderated Regression Analysis:Conventional Interest Type as Dependent Variable (53)Appendix B: Figure (54)Figure B-1. Holland’s Hexagonal Model (55)Appendix C: Information Sheet and Surveys (56)REFERENCES (73)vINTRODUCTIONPersonality traits and vocational interests are two major individual difference domains that influence numerous outcomes associated with work and life success. For example, research has shown that congruence between personality traits and one’s vocation is related to greater job performance and job satisfaction (Barrick, Mount, & Judge, 2001; Hogan & Blake, 1999; Zak, Meir, & Kraemer, 1979). Additionally, specific personality traits are hypothesized to play a role in determining job success within related career domains (Sullivan & Hansen, 2004). Personality is a relatively enduring characteristic of an individual, and therefore could serve as a stable predictor of why people choose particular jobs and careers.Personality traits and vocational interests are linked by affecting behavior through motivational processes (Holland, 1973, 1985). Personality traits and vocational interests influence choices individuals make about which tasks and activities to engage in, how much effort to exert on those tasks, and how long to persist with those tasks (Holland, 1973, 1985; Mount, Barrick, Scullen, & Rounds, 2005). Research has shown that when individuals are in environments congruent with their interests, they are more likely to be happy because their beliefs, values, interests, and attitudes are supported and reinforced by people who are similar to them (Mount, Barrick, Scullen, & Rounds, 2005). Furthermore, research has demonstrated that personality and interests may shape career decision making and behavior; personality and interests guide the development ofknowledge and skills by providing the motivation to engage in particular types of activities (Sullivan & Hansen, 2004).As relatively stable dispositions, personality traits influence an individual’s behavior in a variety of life settings, including work (Dilchert, 2007). Individuals often prefer jobs requiring them to display behaviors that match their stable tendencies. Thus individuals will indicate a liking for occupations for which job duties and job environments correspond to their personality traits. Such a match between personal tendencies and job requirements can support adjustment and eventually occupational success, making the choice of a given job personally rewarding on multiple levels (Dilchert, 2007).People applying for jobs need to try to understand themselves more fully in order to determine if they will be satisfied with their career choices based on their personality traits. This process can be aided by vocational counselors who conduct vocational assessments. The purpose of vocational assessment is to enhance client self-understanding, promote self-exploration, and assist in realistic decision making (Carless, 1999). According to a model proposed by Carless (1999), career assessment is based on the assumption that comprehensive information about the self (e.g., knowledge of one’s personality) in relation to the world of work is a necessary prerequisite for wise career decision making.Self-efficacy beliefs--personal expectations about the ability to succeed at tasks (Bandura, 1986)--are often assessed by vocational counselors. This study examines college self-efficacy--belief in one’s ability to perform tasks necessary for success incollege (Wang & Castaneda-Sound, 2008). Self-efficacy determines the degree to which individuals initiate and persist with tasks (Bandura, 1986), and research has found that personality may influence exploration of vocational interests, through high levels of self-efficacy (Nauta, 2007).There is an abundance of literature supporting that the Five-Factor Model (FFM) (discussed in depth in following sections) of personality predicts Holland’s theory of vocational interest types; however, there is little literature that extends beyond use of the Five-Factor Model. This is due to the adoption of the FFM as an overriding model of personality over the past fifteen years. However, as will be demonstrated later, several criticisms of the model have surfaced. In light of these criticisms the purpose of this study is to extend the existing literature that has established links between the FFM and Holland’s vocational interest types, while examining the relationship between an alternate personality model, Tellegen’s Big Three (as measured by the Multidimensional Personality Questionnaire (MPQ)) and Holland’s types. Furthermore, this study will examine the moderating role that college self-efficacy plays on the relationship between Tellegen’s Big Three and Holland’s interest types.THEORY AND LITERATURE REVIEWPersonality Traits and Vocational Interests DefinedPersonality traits refer to characteristics that are stable over time and are psychological in nature; they reflect who we are and in aggregate determine our affective, behavioral, and cognitive styles (Mount, Barrick, Scullen, & Rounds, 2005). Vocational interests reflect long-term dispositional traits that influence vocational behavior primarily through one’s preferences for certain environments, activities, and types of people (Mount, Barrick, Scullen, & Rounds, 2005).The Five-Factor Model (FFM) of PersonalityThe FFM, often referred to as the Big Five personality dimensions, is a major model that claims personality consists of five dimensions: Openness to Experience (i.e., imaginative, intellectual, and artistically sensitive), Conscientiousness (i.e., dependable, organized, and persistent), Extraversion (i.e., sociable, active, and energetic), Agreeableness (i.e., cooperative, considerate, and trusting), and Neuroticism, sometimes referred to positively as emotional stability (i.e., calm, secure, and unemotional) (Harris, Vernon, Johnson, & Jang, 2006; McCrae & Costa, 1986; McCrae & Costa, 1987; Mount, Barrick, Scullen, & Rounds, 2005; Nauta, 2004; Sullivan & Hansen, 2004). The FFM provides the foundation for several personality measures (e.g., NEO-PI, NEO-PI-R, NEO-FFI) that have proved to be valid and reliable and are widely utilized in research today (Costa & McCrae, 1992). There appears to be a large degree of consensusregarding the FFM of personality and the instruments used to measure the model. For instance, the FFM has been shown to have a large degree of universality (McCrae, 2001), specifically in terms of stability across adulthood (McCrae & Costa, 2003) and cultures (DeFruyt & Mervielde, 1997; Hofstede & McCrae, 2004, McCrae, 2001).Holland’s Theory of Vocational Interest TypesHolland’s theory of vocational interests has played a key role in efforts to understand vocational interests, choice, and satisfaction.Holland was very clear that he believed personality and vocational interests are related:If vocational interests are construed as an expression of personality, then theyrepresent the expression of personality in work, school subjects, hobbies,recreational activities, and preferences. In short, what we have called ‘vocational interests’ are simply another aspect of personality…If vocational interests are anexpression of personality, then it follows that interest inventories are personalityinventories. (Holland, 1973, p.7)Vocational interest types, as classified by Holland, are six broad categories (discussed later in the section) that can be used to group occupations or the people who work in them. Holland’s theory of vocational interest types and work environments states that employees’ satisfaction with a job as well as propensity to leave that job depends on the degree to which their personalities match their occupational environments (Holland, 1973, 1985). Furthermore, people are assumed to be most satisfied, successful, and stable in a work environment that is congruent with their vocational interest type. Two ofHolland’s basic assumptions are: (a) individuals in a particular vocation have similar personalities, and (b) individuals tend to choose occupational environments consistent with their personality (Holland, 1997).A fundamental proposition of Holland’s theory is that, when differentiated by their vocational interests, people can be categorized according to a taxonomy of six types, hereinafter collectively referred to as RIASEC (Holland, 1973, 1985). Holland’s theory states that six vocational interest types--Realistic, Investigative, Artistic, Social, Enterprising, and Conventional (RIASEC)--influence people to seek environments which are congruent with their characteristics (Harris, Vernon, Johnson, & Jang, 2006; Holland, 1973, 1985; Nauta, 2004; Roberti, Fox, & Tunick, 2003; Sullivan & Hansen, 2004; Zak, Meir, & Kraemer, 1979). Holland used adjective descriptors to capture the distinctive characteristics of each interest type (Hogan & Blake, 1999). These are summarized in Table A-1. Holland’s approach to the assessment of vocational interest types was based on the assumption that members of an occupational group have similar work-related preferences and respond to problems and situations in similar ways (Carless, 1999).Realistic types like the systematic manipulation of machinery, tools, or animals. Investigative types have interests that involve analytical, curious, methodical, and precise activities. The interests of Artistic types are expressive, nonconforming, original, and introspective. Social types want to work with and help others. Enterprising types seek to influence others to attain organizational goals or economic gain. Finally, Conventional types are interested in systematic manipulation of data, filing records, or reproducing materials (Tokar, Vaux, & Swanson, 1995).According to Holland’s theory, these interest types differ in their relative similarity to one another, in ways that can be represented by a hexagonal figure with the types positioned at the six points (see Figure B-1). Adjacent types (e.g., Realistic and Investigative) are most similar; opposite types (e.g., Realistic and Social) are least similar, and alternating types (e.g., Realistic and Artistic) are assumed to have an intermediate level of relationship (Holland, 1973, 1985; Tokar, Vaux, & Swanson, 1995).Overlap between the FFM and RIASECMany studies provide evidence of the links between the FFM of personality and the RIASEC interest types. An extensive review of the research investigating the links between the FFM and the RIASEC types identified ten studies that found Extraversion predicts interest in jobs that focus on Social and Enterprising interests. Ten studies showed Openness to Experience predicts interest in jobs that focus on Investigative and Artistic interests. Six studies found Agreeableness predicts interest in jobs that focus on Social interest; six studies showed Conscientiousness predicts interests in jobs that focus on Conventional interests; and one study found Neuroticism predicts interests in jobs that focus on Investigative interests (see Table A-2 for the citations). One discrepancy in this research has been Costa and McCrae’s claims that the FFM applies uniformly to all adult ages, but Mroczek, Ozer, Spiro, and Kaiser (1998) found substantial differences between the structures emerging from older individuals as compared to undergraduate students, in that the five factor structure failed to emerge in the student sample (i.e., agreeableness failed to emerge) as it did with the older sample.All of the links discussed between the FFM of personality and the RIASEC interest types provide the foundation for hypotheses 1a – 1e. Hypotheses 1a – 1e will add to the literature, previously discussed, by assessing current college students early in their college careers. These are the people who have the potential to be most influenced by vocational and career counselors. Given that research has found a discrepancy in FFM profiles of younger and older individuals, it is important to test its efficacy in predicting vocational interests.Hypothesis 1a (H1a): Extraversion will significantly positively correlate withSocial and Enterprising types, but not Realistic, Investigative, Artistic, andConventional types.Hypothesis 1b (H1b): Openness to Experience will significantly positivelycorrelate with Investigative and Artistic types, but not Realistic, Conventional,Social, and Enterprising types.Hypothesis 1c (H1c): Agreeableness will significantly positively correlate withSocial types, but not Realistic, Conventional, Enterprising, Investigative, andArtistic types.Hypothesis 1d (H1d): Conscientiousness will significantly positively correlatewith Conventional types, but not Realistic, Enterprising, Investigative, Social, and Artistic types.Hypothesis 1e (H1e): Neuroticism will significantly negatively correlate withInvestigative types, but not Realistic, Enterprising, Conventional, Social, andArtistic types.Criticisms and Limitations of the FFMThe whole enterprise of science depends on challenging accepted views, and the FFM has become one of the most accepted models in personality research. Many critiques of the FFM ask “Why are there five and only five factors? Five factor protagonists say: it is an empirical fact…via the mathematical method of factor analysis, the basic dimensions of personality have been discovered.” (McCrae & Costa, 1989, p. 120). Has psychology as a science achieved a final and absolute way of looking at personality or is there a way to further our conceptualization of personality? In the article by Costa and McCrae (1997) explaining the anticipated changes to the NEO in the new millennium, they anticipate only minor wording modifications and simplifications. Thus it appears as if the FFM is viewed as a final or almost final achievement (Block, 2001). One claimed benefit of the FFM is evidence of heritability is strong for all 5 factors, but evidence is strong for all personality factors studied; it does not single out the Costa and McCrae factors (Eysenck, 1992). In other words, all the criteria suggested by Costa and McCrae are necessary but not sufficient to mark out one model from many which also conform to this criteria.The debate that has been most prominent over the past 15 years, and which has probably attracted the most attention, concerns the number and description of the basic, fundamental, highest-order factors of personality. Evidence from meta-analyses of factorial studies provide evidence that three, not five personality factors, emerge at the highest level of analysis (Royce & Powell, 1983; Tellegen & Waller, 1991; Zuckerman, Kuhlman, & Camac, 1988; Zuckerman, Kuhlman, Thornquist, & Kiers, 1991).Altogether, Eysenck (1992) has surveyed many different models, questionnaires and inventories, reporting in most cases a break-down into 2 or 3 major factors; but never 5. Additionally, Jackson, Furnham, Forde, and Cotter (2000) and Tellegen (1985) have contradicted Costa and McCrae’s (1995) assertions that a five-factor model seems most appropriate, with results showing that a three-factor solution is both more clear and parsimonious.Another critique of the FFM lies in its development. The initial factor-analytic derivations of the Big Five were not guided by explicit psychological theory, and therefore some have asked the question, “Why these five?” (e.g., Revelle, 1987; Waller & Ben-Porath, 1987). As Briggs (1989) points out, the original studies leading to the FFM “prompted no a priori predictions as to what factors should emerge, and a coherent and falsifiable explanation for the five factors has yet to be put forward” (p. 249).A further developmental critique of the FFM is the lack of lower order factors. Theoretically, factors exist at different hierarchical levels, and the FFM only measures five higher order factors (Block, 2001). The FFM operates at a broadband level to measure the main (i.e., higher order) categories of traits (McAdams, 1992). Within each of the five categories, therefore, may be many different and more specific traits, as traits are nested hierarchically within traits (McAdams, 1992).Another limitation of the FFM lies in researchers’ inability to consistently link the personality traits to the Holland interest types. Research has found that although there is a significant overlap between the FFM and RIASEC interest types, the RIASEC types do not appear to be entirely encompassed by the Big-Five personality dimensions (Carless,1999; Church, 1994; DeFruyt & Mervielde, 1999; Tokar, Vaux, & Swanson, 1995). Three personality dimensions in the FFM predict the RIASEC types, but there is less evidence to support that the other two predict the RIASEC types. Specifically, there appears to be significant overlap with Conscientiousness, Openness, and Extraversion in predicting the RIASEC interest types, but less research has been able to find links between Agreeableness and Neuroticism with the RIASEC interest types. This is a limitation of the FFM in relating to vocational interests (Costa, McCrae, & Holland, 1984; Gottfredson, Jones, & Holland, 1993; Tokar, Vaux, & Swanson, 1995).Looking Beyond the FFM: Tellegen’s Big Three Model of PersonalityIn light of these criticisms of the FFM, it seems attention could be paid to alternate models of personality to investigate the dimensions underlying Holland’s interest types. The literature base is sparse here, and alternative personality models warrant further study, particularly with regard to vocational interests (Blake & Sackett, 1999; Church, 1994; Larson & Borgen, 2002; Staggs, Larson, & Borgen, 2003). One such model is Tellegen’s Big Three which addresses many of the criticisms of the FFM.Many vocational psychology researchers use the Big Five model of personality, often measured by the NEO-PI or NEO-PI-R, but less often the Big Three model of personality measured by the Multidimensional Personality Questionnaire (MPQ) is used (Tellegen, 1985; Tellegen & Waller, 1991). This model of personality resulted from ten years of research on focal dimensions in the personality literature (Tellegen, 1985; Tellegen & Waller, 1991). Tellegen’s (1985; Tellegen & Waller, 1991) Big Three modeldefines three higher order factors. These represent the clusters of items from a factor analysis that composed the three higher order traits. The lower order factors consist of items clustered in each of the higher order factors. The higher order factors are: Positive Emotionality (PEM), Negative Emotionality (NEM), and Constraint (CT) (Tellegen, 1985; Tellegen & Waller, 1991). These higher order traits correlate minimally with one another and encompass 11 lower order traits. Refer to Table A-3 for a description of the three higher order traits and the 11 lower order traits.There are only three published studies that have examined the Big Three model as relating to vocational interests. Blake and Sackett (1999) reported that the Artistic type moderately related with the MPQ Absorption lower order trait (Larson & Borgen, 2002). The Social type negatively related to the MPQ Aggression lower order trait; the Enterprising type related moderately to the MPQ Social Potency lower order trait; and the Conventional type related moderately to the MPQ Control lower order trait.Staggs, Larson, and Borgen (2003) also analyzed the lower order traits, specifically, as opposed to the higher order factors of PEM, NEM, and CT. They identified seven personality dimensions that have a substantial relationship with vocational interests: Absorption predicted interest in Artistic occupations; Social Potency predicted interest in Enterprising occupations; Harm Avoidance predicted interest in science and mechanical activity occupations; Achievement predicted interest in science and mathematic occupations; Social Closeness predicted interest in mechanical activity occupations; Traditionalism predicted interest in religious activities; and Stress Reaction predicted interest in athletic careers. Staggs, Larson, and Borgen (2003) used a collegestudent sample, but were not studying the RIASEC types; they were using a different conceptualization of vocational interests as measured by the Strong Interest Inventory which measures General Occupational Themes.Larson and Borgen (2002) found that the PEM factor was more strongly correlated with Social interests than with Enterprising interests; however, PEM did strongly correlate with all six RIASEC types (p < .001). This finding shows strong evidence that the PEM higher order trait relates to the RIASEC types. Larson and Borgen (2002) also found that the CT factor was negatively related to Realistic and Artistic interest types, and that the NEM factor was negatively related to Artistic interest types. Larson and Borgen (2002) utilized a sample of “gifted” adolescent students, which is a very limited and non-generalizable sample. In contrast, the current study tests a freshman college student sample, which is more generalizable to the population of students who are seeking vocational guidance.The links between the MPQ and the RIASEC interest types are under-researched. Although some vocational research has utilized the MPQ, more needs to be done to determine the relationships between Tellegen’s Big Three and Holland’s RIASEC interest types. However, the research provides support for the idea that there are alternative personality dimensions (i.e., Tellegen’s Big Three), outside of the FFM, that can significantly predict vocational interests, in particular the RIASEC types. Hypotheses 2a – 2c will test relationships between the Tellegen’s Big Three (as measured by the MPQ-BF) and the RIASEC interest types.Hypothesis 2a (H2a): The PEM factor will significantly positively correlate with all six RIASEC types.Hypothesis 2b (H2b): The CT factor will significantly negatively correlate withRealistic and Artistic types, but not with Investigative, Social, Enterprising, andConventional types.Hypothesis 2c (H2c): The NEM factor will significantly negatively correlate with Artistic types, but not with Investigative, Social, Enterprising, Realistic, andConventional types.Comparing Tellegen’s Big Three and the FFMAn earlier discussion proposed criticisms of the FFM. In light of these criticisms an alternate personality model was considered: Tellegens’ Big Three, measured by the MPQ. This model of personality resolves all the previous criticisms of the FFM: five versus 3 factors, lack of lower order factors, and model development issues.Tellegen’s (1985) understanding of personality differs from the conception of the FFM. Tellegen believes personality can be summed by three overriding traits or factors versus the 5 factors of the FFM. This is an inherent difference in the two models of personality, which guided the development of instruments used to measure these models, in terms of a three versus a five factor structure. Furthermore, Tellegen (1985) utilized a bottom-up approach to development of the MPQ, in which constructs were based on iterative cycles of data collection and item analyses designed to better differentiate the primary scales. In contrast, Tupes and Chrtistal (1961) emphasized deductive, top-down。
Intermediate Accounting Canadian edition (34)
Lisa Harvey, CPA, CA
Rotman School of Management, University of Toronto
ER 21
ACCOUNTING CHANGES AND ERROR ANALYSIS
After studying this chapter, you should be able to:
9
Copyright © John Wiley & Sons Canada, Ltd.
9
Changes in Accounting Estimates
• Future conditions and events and their effects cannot be known with certainty; therefore estimation requires exercise of judgment • Use of reasonable estimates is essential to the accounting process and does not undermine the reliability of financial statements
3
Types of Accounting Changes
1.Change in Accounting Policy
– Change in the choice of “specific principles, bases, conventions, rules, and practices applied by an entity in preparing and presenting financial statements”
•Looking ahead
SENTIWORDNET A publicly available lexical resource for opinion mining
S ENTI W ORD N ET:A Publicly Available Lexical Resourcefor Opinion MiningAndrea Esuli∗and Fabrizio Sebastiani†∗Istituto di Scienza e Tecnologie dell’Informazione,Consiglio Nazionale delle RicercheVia Giuseppe Moruzzi1,56124Pisa,ItalyE-mail:andrea.esuli@r.it†Dipartimento di Matematica Pura e Applicata,Universit`a di PadovaVia Giovan Battista Belzoni7,35131Padova,ItalyE-mail:fabrizio.sebastiani@unipd.itAbstractOpinion mining(OM)is a recent subdiscipline at the crossroads of information retrieval and computational linguistics which is concerned not with the topic a document is about,but with the opinion it expresses.OM has a rich set of applications,ranging from tracking users’opinions about products or about political candidates as expressed in online forums,to customer relationship management.In order to aid the extraction of opinions from text,recent research has tried to automatically determine the“PN-polarity”of subjective terms,i.e. identify whether a term that is a marker of opinionated content has a positive or a negative connotation.Research on determining whether a term is indeed a marker of opinionated content(a subjective term)or not(an objective term)has been,instead,much more scarce.In this work we describe S ENTI W ORD N ET,a lexical resource in which each W ORD N ET synset s is associated to three numerical scores Obj(s), P os(s)and Neg(s),describing how objective,positive,and negative the terms contained in the synset are.The method used to develop S ENTI W ORD N ET is based on the quantitative analysis of the glosses associated to synsets,and on the use of the resulting vectorial term representations for semi-supervised synset classification.The three scores are derived by combining the results produced by a committee of eight ternary classifiers,all characterized by similar accuracy levels but different classification behaviour.S ENTI W ORD N ET is freely available for research purposes,and is endowed with a Web-based graphical user interface.1.IntroductionOpinion mining(OM–also known as“sentiment classifi-cation”)is a recent subdiscipline at the crossroads of infor-mation retrieval and computational linguistics which is con-cerned not with the topic a text is about,but with the opin-ion it expresses.Opinion-driven content management has several important applications,such as determining critics’opinions about a given product by classifying online prod-uct reviews,or tracking the shifting attitudes of the general public towards a political candidate by mining online fo-rums or blogs.Within OM,several subtasks can be iden-tified,all of them having to do with tagging a given text according to expressed opinion:1.determining text SO-polarity,as in deciding whether agiven text has a factual nature(i.e.describes a given situation or event,without expressing a positive or a negative opinion on it)or expresses an opinion on its subject matter.This amounts to performing binary text categorization under categories Subjective and Ob-jective(Pang and Lee,2004;Yu and Hatzivassiloglou, 2003);2.determining text PN-polarity,as in deciding if a givenSubjective text expresses a Positive or a Negative opinion on its subject matter(Pang and Lee,2004;Turney,2002);3.determining the strength of text PN-polarity,as in de-ciding e.g.whether the Positive opinion expressed bya text on its subject matter is Weakly Positive,MildlyPositive,or Strongly Positive(Pang and Lee,2005;Wilson et al.,2004).To aid these tasks,several researchers have attempted to automatically determine whether a term that is a marker of opinionated content has a Positive or a Negative con-notation(Esuli and Sebastiani,2005;Hatzivassiloglou and McKeown,1997;Kamps et al.,2004;Kim and Hovy,2004; Takamura et al.,2005;Turney and Littman,2003),since it is by considering the combined contribution of these terms that one may hope to solve Tasks1,2and3.The con-ceptually simplest approach to this latter problem is prob-ably Turney’s(Turney,2002),who has obtained interest-ing results on Task2by considering the algebraic sum of the orientations of terms as representative of the orienta-tion of the document they belong to;but more sophisticated approaches are also possible(Hatzivassiloglou and Wiebe, 2000;Riloff et al.,2003;Whitelaw et al.,2005;Wilson et al.,2004).The task of determining whether a term is indeed a marker of opinionated content(i.e.is Subjective or Ob-jective)has instead received much less attention(Esuli and Sebastiani,2006;Riloff et al.,2003;Vegnaduzzo,2004). Note that in these works no distinction between different senses of a word is attempted,so that the term,and not its senses,are classified(although some such works(Hatzivas-siloglou and McKeown,1997;Kamps et al.,2004)distin-guish between different POSs of a word).In this paper we describe S ENTI W ORD N ET(version 1.0),a lexical resource in which each synset of W ORD-N ET(version2.0)is associated to three numerical scores Obj(s),P os(s)and Neg(s),describing how Objective, Positive,and Negative the terms contained in the synset are.The assumption that underlies our switch from terms to synsets is that different senses of the same term mayhave different opinion-related properties.Each of the three scores ranges from0.0to1.0,and their sum is1.0for each synset.This means that a synset may have nonzero scores for all the three categories,which would indicate that the corresponding terms have,in the sense indicated by the synset,each of the three opinion-related proper-ties only to a certain degree1.For example,the synset [estimable(3)]2,corresponding to the sense“may be computed or estimated”of the adjective estimable,has an Obj score of1.0(and P os and Neg scores of0.0),while the synset[estimable(1)]corresponding to the sense “deserving of respect or high regard”has a P os score of0.75,a Neg score of0.0,and an Obj score of0.25.A similar intuition had previously been presented in(Kim and Hovy,2004),whereby a term could have both a Positive and a Negative PN-polarity,each to a cer-tain degree.A similar point has also recently been made in(Andreevskaia and Bergler,2006),in which terms that possess a given opinion-related property to a higher de-gree are claimed to be also the ones on which human an-notators asked to assign this property agree more.Non-binary scores are attached to opinion-related properties also in(Turney and Littman,2003),but the interpretation here is related to the confidence in the correctness of the labelling, rather than in how strong the term is deemed to possess the property.We believe that a graded(as opposed to“hard”)eval-uation of opinion-related properties of terms can be help-ful in the development of opinion mining applications.A hard classification method will probably label as Objective any term that has no strong SO-polarity,e.g.terms such as short or alone.If a sentence contains many such terms, a resource based on a hard classification will probably miss its subtly subjective character,while a graded lexical re-source like S ENTI W ORD N ET may provide enough infor-mation to capture such nuances.The method we have used to develop S ENTI W ORD N ET is based on our previous work on determining the opinion-related properties of terms(Esuli and Sebastiani,2005; Esuli and Sebastiani,2006).The method relies on the quan-titative analysis of the glosses associated to synsets,and on the use of the resulting vectorial term representations for 1Note that associating a graded score to a synset for a certain property(e.g.Positive)may have(at least)three different inter-pretations:(i)the terms in the synset are Positive only to a cer-tain degree;(ii)the terms in the synset are sometimes used in a Positive sense and sometimes not,e.g.depending on the context of use;(iii)a combination of(i)and(ii)is the case.Interpreta-tion(i)has a fuzzy character,implying that each instance of these terms,in each context of use,have the property to a certain de-gree,while interpretation(ii)has a probabilistic interpretation(of a frequentistic type),implying that membership of a synset in the set denoted by the property must be computed by counting the number of contexts of use in which the terms have the property. We do not attempt to take a stand on this distinction,which(to our knowledge)had never been raised in sentiment analysis and that requires an in-depth linguistic study,although we tend to believe that(iii)is the case.2We here adopt the standard convention according to which a term enclosed in square bracket denotes a synset;thus [poor(7)]refers not just to the term poor but to the synset consisting of{inadequate(2),poor(7),short(4)}.semi-supervised synset classification.The three scores are derived by combining the results produced by a committee of eight ternary classifiers,each of which has demonstrated, in our previous tests,similar accuracy but different charac-teristics in terms of classification behaviour.S ENTI W ORD N ET is freely available for research pur-poses,and is endowed with a Web-based graphical user in-terface.2.Building S ENTI W ORD N ETThe method we have used to develop S ENTI W ORD N ET is an adaptation to synset classification of our method for de-ciding the PN-polarity(Esuli and Sebastiani,2005)and SO-polarity(Esuli and Sebastiani,2006)of terms.The method relies on training a set of ternary classifiers3,each of them capable of deciding whether a synset is Positive,or Nega-tive,or Objective.Each ternary classifier differs from the other in the training set used to train it and in the learn-ing device used to train it,thus producing different classi-fication results of the W ORD N ET synsets.Opinion-related scores for a synset are determined by the(normalized)pro-portion of ternary classifiers that have assigned the corre-sponding label to it.If all the ternary classifiers agree in assigning the same label to a synset,that label will have the maximum score for that synset,otherwise each label will have a score proportional to the number of classifiers that have assigned it.2.1.Training a classifierEach ternary classifier is generated using the semi-supervised method described in(Esuli and Sebastiani, 2006).A semi-supervised method is a learning process whereby only a small subset L⊂T r of the training data T r have been manually labelled.In origin the training data in U=T r−L were instead unlabelled;it is the process itself that has labelled them,automatically,by using L(with the possible addition of other publicly available resources)as input.Our method defines L as the union of three seed(i.e. training)sets L p,L n and L o of known Positive,Negative and Objective synsets,respectively4.L p and L n are two small sets,which we have defined by manually selecting the intended synsets5for14“paradig-matic”Positive and Negative terms(e.g.the Positive term nice,the Negative term nasty)which were used as seed terms in(Turney and Littman,2003).L p and L n are then iteratively expanded,in K itera-tions,into thefinal training sets T r K p and T r K n.At each iteration step k two sets T r k p and T r k n are generated,where T r k p⊃T r k−1p⊃...⊃T r1p=L p and T r k n⊃T r k−1n⊃...⊃T r1n=L n.The expansion at iteration step k consists 3An n-ary classifier is a device that attaches to each object exactly one from a predefined set of n labels.4A W ORD N ET synset represent a unique sense,which is de-fined by a unique gloss and is associated to a set of terms all with the same POS,each one associated to a sense number,(e.g.the ad-jectives blasphemous(2),blue(4),profane(1)are all contained in the same synset,whose sense is defined by the gloss “characterized by profanity or cursing”).5For example,for the term nice we have removed the synset relative to the French city of Nice.The process has resulted in47 Positive and58Negative synsets.•in adding to T r k p(resp.T r k n)all the synsets thatare connected to synsets in T r k−1p (resp.T r k−1n)byW ORD N ET lexical relations(e.g.also-see)such that the two related synsets can be taken to have the same PN-polarity;•in adding to T r k p(resp.T r k n)all the synsets thatare connected to synsets in T r k−1n (resp.T r k−1p)byW ORD N ET lexical relations(e.g.direct antonymy) such that the two related synsets can be taken to have opposite PN-polarity.The relations we have used in(Esuli and Sebastiani, 2005;Esuli and Sebastiani,2006)are synonymy and direct antonymy between terms,as is common in related litera-ture(Kamps et al.,2004;Kim and Hovy,2004;Takamura et al.,2005).In the case of synsets,synonymy cannot be used because it is the relation that defines synsets,thus it does connect different synsets.We have then followed the method used in(Valitutti et al.,2004)for the development of W ORD N ET-A FFECT,a lexical resource that tags W ORD-N ET synsets by means of a taxonomy of affective cate-gories(e.g.Behaviour,Personality,Cognitive state):af-ter hand-collecting a number of labelled terms from other resources,Valitutti and colleagues generate W ORD N ET-A FFECT by adding to them the synsets reachable by navi-gating the relations of direct antonymy,similarity,derived-from,pertains-to,attribute,and also-see,which they con-sider to reliably preserve/invert the involved labels.Given the similarity with our task,we have used exactly these relations in our expansion.Thefinal sets T r K p and T r K n, along with the set T r K o described below,are used to train the ternary classifiers.The L o set is treated differently from L p and L n,be-cause of the inherently“complementary”nature of the Ob-jective category(an Objective term can be defined as a term that does not have either Positive or Negative char-acteristics).We have heuristically defined L o as the set of synsets that(a)do not belong to either T r K p or T r K n,and (b)contain terms not marked as either Positive or Neg-ative in the General Inquirer lexicon(Stone et al.,1966). The resulting L o set consists of17,530synsets;for any K, we define T r K o to coincide with L o.We give each synset a vectorial representation,obtained by applying a standard text indexing technique(cosine-normalized tf∗id f preceded by stop word removal)to its gloss,which we thus take to be a textual representa-tion of its semantics.Our basic assumption is that terms with similar polarity tend to have“similar”glosses:for in-stance,that the glosses of honest and intrepid will both contain appreciative expressions,while the glosses of disturbing and superfluous will both contain derogative expressions.The vectorial representations of the training synsets for a given label c i are then input to a standard supervised learner,which generates two binary classifiers.One of them must discriminate between terms that belong to the Positive category and ones that belong to its complement (not Positive),while the other must discriminate between terms that belong to the Negative category and ones that belong to its complement(not Negative).Terms that have been classified both into Positive by the former classifier and into(not Negative)by the latter are deemed to be posi-tive,and terms that have been classified both into(not Posi-tive)by the former classifier and into Negative by the latter are deemed to be negative.The terms that have been clas-sified(i)into both(not Positive)and(not Negative),or (ii)into both Positive and Negative,are taken to be Ob-jective.In the training phase,the terms in T r K n∪T r K o are used as training examples of category(not Positive), and the terms in T r K p∪T r K o are used as training examples of category(not Negative).The resulting ternary classi-fierˆΦis then applied to the vectorial representations of all W ORD N ET synsets(including those in T r K−L),to pro-duce the sentiment classification of the entire W ORD N ET.2.2.Defining the committee of classifiersIn(Esuli and Sebastiani,2006)we point out how differ-ent combinations of training set and learner perform differ-ently,even though with similar accuracy.The main three observations we recall here are the following:•Low values of K produce small training sets for Pos-itive and Negative,which produces binary classifiers with low recall and high precision for these categories.By increasing K these sets get larger,and the effect of these larger numbers is to increase recall and but to also add“noise”to the training set,which decreases precision.•Learners that use information about the prior proba-bilities of categories,e.g.naive Bayesian learners and SVMs,which estimate these probabilities from the training sets,are sensitive to the relative cardinalities of the training sets,and tend to classify more items into the categories that have more positive training items.Learners that do not use this kind of infor-mation,like Rocchio,do not exhibit this kind of be-haviour.•The variability described in the previous points does not affect the overall accuracy of the method,but only the balance in classification between Subjective and Objective items,while the accuracy in discriminating between Positive and Negative items tends to be con-stant.Following these considerations,we have decided to com-bine different configurations of training set and learner into a committee,to produce thefinal S ENTI W ORD N ET scores. Specifically,we have defined four different training sets,by choosing four different values of K(0,2,4,6),and we have alternatively used two learners(Rocchio and SVMs)6;this yields a total of eight ternary classifiers.With K=0and the SVM learner we have obtained very“conservative”bi-nary classifier for Positive and Negative,with very low re-call and high precision.For K=6SVMs produced instead 6The Rocchio learner we have used is from Andrew McCallum’s Bow package (/˜mccallum/bow/), while the SVMs learner we have used is version 6.01of Thorsten Joachims’SV M light(/).“liberal”binary classifiers for these two labels,that classifymany synsets as Positive or Negative even in the presence of very little evidence of subjectivity.The Rocchio learner has a similar behaviour,although not dependent on the prior probabilities of categories.S ENTI W ORD N ET is thus ob-tained by combining,for each synset,the scores produced by the eight ternary classifiers and normalizing them to1.0.2.3.Some statisticsTable1shows some statistics about the distribution of scores in S ENTI W ORD N ET.Thefirst remarkable fact is that the synsets judged to have some degree of opinion-related properties(i.e.not fully Objective)are a consid-erable part of the whole W ORD N ET,i.e.24.63%of it. However,as the objectivity score decreases,indicating a stronger subjectivity score(either as Positive,or as Neg-ative,or as a combination of them),the number of the synsets involved decreases rapidly,from10.45%for Ob-jective<=0.5,to0.56%for Objective<=0.125.This seems to indicate that there are only few terms that are un-questionably Positive(or Negative),where“unquestion-ably”here indicates widespread agreement among different automated classifiers;in essence,this is the same observa-tion which has independently been made in(Andreevskaia and Bergler,2006),where agreement among human classi-fiers is shown to correlate strongly with agreement among automated classifiers,and where such agreement is strong only for a small subset of“core”,strongly-marked terms.Table1reports a breakdown by POS of the scores ob-tained by synsets.It is quite evident that“adverb”and“ad-jective”synsets are evaluated as(at least partially)Sub-jective(i.e.Obj(s)<1)much more frequently(39.66% and35.7%of the cases,respectively)than“verb”(11.04%) or“name”synsets(9.98%).This fact seems to indicate that,in natural language,opinionated content is most of-ten carried by parts of speech used as modifiers(i.e.ad-verbs,adjectives)rather than parts of speech used as heads (i.e.verbs,nouns),as exemplified by expressions such as a disastrous appearance or a fabulous game. This intuition might be rephrased by saying that the most frequent role of heads is to denote entities or events,while that of modifiers is(among other things)to express a judg-ment of merit on them.3.Visualizing S ENTI W ORD N ETGiven that the sum of the opinion-related scores as-signed to a synset is always1.0,it is possible to display these values in a triangle whose vertices are the maximum possible values for the three dimensions observed.Figure1shows the graphical model we have designed to display the scores of a synset.This model is used in the Web-based graphical user interface through which S ENTI W ORD N ET can be freely accessed at r.it/˜esuli/software/ SentiWordNet.Figures2and3show two screenshots of the output for the terms estimable and short.4.Evaluating S ENTI W ORD N ETHow reliable are the opinion-related scores attached to synsets in SentiWordNet?Testing the accuracy of ourScore Positive Negative ObjectiveAdjectives0.065.77%62.81%0.08%0.12512.12%7.32% 2.14%0.258.81%8.68%7.42%0.375 4.85% 5.19%11.73%0.5 3.74% 5.63%9.50%0.625 2.94% 5.53%7.65%0.75 1.28% 3.72%9.21%0.8750.47% 1.07%7.57%1.00.03%0.04%44.71%Avg0.1060.1510.743Names0.090.80%89.25%0.00%0.125 4.53% 3.93%0.23%0.25 2.37% 2.42%0.87%0.375 1.25% 1.54% 1.84%0.50.62% 1.35% 2.32%0.6250.24%0.91% 2.57%0.750.14%0.48% 3.27%0.8750.05%0.12% 5.40%1.00.00%0.00%83.50%Avg0.0220.0340.944Verbs0.089.98%87.93%0.00%0.125 4.43% 4.94%0.21%0.25 2.66% 2.95%0.64%0.375 1.55% 1.81% 1.35%0.50.84% 1.24% 2.67%0.6250.36%0.63% 3.40%0.750.10%0.42% 4.57%0.8750.07%0.08% 6.11%1.00.00%0.00%81.05%Avg0.0260.0340.940Adverbs0.043.70%76.99%0.00%0.125 6.25%9.66%0.57%0.25 6.17% 5.32% 3.00%0.37514.44% 2.51%12.83%0.522.63% 2.70%23.91%0.625 5.70% 1.72%13.56%0.75 1.06%0.82% 6.11%0.8750.05%0.27%7.04%1.00.00%0.00%32.97%Avg0.2350.0670.698All parts of speech0.085.18%84.45%0.02%0.125 5.79% 4.77%0.54%0.25 3.56% 3.58% 1.97%0.375 2.28% 2.19% 3.72%0.5 1.85% 2.07% 4.20%0.6250.87% 1.64% 3.83%0.750.35% 1.00% 4.47%0.8750.12%0.27% 5.88%1.00.01%0.01%75.37%Avg0.0430.0540.903Table1:Breakdown by part of speech of the scores ob-tained by W ORD N ET synsets,and average scores obtained for each part of speech.tagging method experimentally is impossible,since for this we would need a full manual tagging of W ORD N ET ac-cording to our three labels of interest,and the lack of such a manually tagged resource is exactly the reason why we are interested in generating it automatically.A first,approximate indication of the quality of S EN -TI W ORD N ET can be gleaned by looking at the accuracy obtained by our method in classifying the General In-quirer (Stone et al.,1966),a lexicon which is instead fully tagged according to three opinion-related labels we have been discussing;the results of this classification exercise are reported in (Esuli and Sebastiani,2006).The reader should however bear in mind a few differences between the method used in (Esuli and Sebastiani,2006)and the one used here:(i)we here classify entire synsets,while in (Esuli and Sebastiani,2006)we classified terms,which can some-times be ambiguous and thus more difficult to classify cor-rectly;(ii)as discussed in Section 2.1.,the W ORD N ET lex-ical relations used for the expansion of the training set are different.The effectiveness results reported in (Esuli and Sebastiani,2006)may thus be considered only approxi-mately indicative of the accuracy of the S ENTI W ORD N ET labelling.A second,more direct route to evaluating S ENTI -W ORD N ET is to produce a human labelling of a subset of W ORD N ET ,and to use this subset as a “gold standard”against which to evaluate the scores attached to the same synsets in S ENTI W ORD N ET .We are currently producing this labelled corpus 7,which will consist of 1000W ORD -N ET synsets tagged by five different evaluators;for each synset each evaluator will attribute,through a graphical in-terface we have designed,a score for each of the three la-bels of interest such that the three scores sum up to parisons among the scores assigned by different eval-uators to the same synsets will also allow us to obtain inter-indexer inconsistency results for this task;the five evalua-tors have initially gone through a training session in which the meaning of the labels has been clarified,which should keep inter-indexer inconsistency within reasonable bounds.Note that 1000synsets correspond to less than 1%of the total 115,000W ORD N ET synsets;this points at the fact that,again,the accuracy obtained on this benchmark may be considered only as indicative of the (unknown)level of accuracy with which SentiWordNet has been produced.Notwithstanding this fact this benchmark will prove a use-ful tool in the comparative evaluation of future systems that,like ours,tag WordNet synsets by opinion,including pos-sible future releases of SentiWordNet .5.Conclusion and future researchWe believe that SentiWordNet can prove a useful tool for opinion mining applications,because of its wide cov-erage (all WordNet synsets are tagged according to each of the three labels Objective ,Positive ,Negative )and be-cause of its fine grain,obtained by qualifying the labels by means of numerical scores.7This work is being carried out in collaboration with Andrea Sans`o from the University of Pavia,whose help we gratefully ac-knowledge.Figure 1:The graphical representation adopted by S ENTI -W ORD N ET for representing the opinion-related properties of a termsense.Figure 2:S ENTI W ORD N ET visualization of the opinion-related properties of the term estimable .We are currently testing new algorithms for tagging WordNet synsets by sentiment,and thus plan to continue the development of SentiWordNet beyond the currently released “Version 1.0”;once developed,the gold standard discussed in Section 4.will contribute to guiding this de-velopment,hopefully allowing us to make available to the scientific community more and more refined releases of SentiWordNet .6.AcknowledgmentsThis work was partially supported by Project ONTOTEXT“From Text to Knowledge for the Semantic Web”,funded by the Provincia Autonoma di Trento under the 2004–2006“Fondo Unico per la Ricerca”funding scheme.Figure3:S ENTI W ORD N ET visualization of the opinion-related properties of the term short.7.ReferencesAlina Andreevskaia and Sabine Bergler.2006.Mining WordNet for fuzzy sentiment:Sentiment tag extraction from WordNet glosses.In Proceedings of EACL-06,11th Conference of the European Chapter of the Association for Computational Lin-guistics,Trento,IT.Forthcoming.Andrea Esuli and Fabrizio Sebastiani.2005.Determining the se-mantic orientation of terms through gloss analysis.In Proceed-ings of CIKM-05,14th ACM International Conference on Infor-mation and Knowledge Management,pages617–624,Bremen, DE.Andrea Esuli and Fabrizio Sebastiani.2006.Determining term subjectivity and term orientation for opinion mining.In Pro-ceedings of EACL-06,11th Conference of the European Chap-ter of the Association for Computational Linguistics,Trento, IT.Forthcoming.Vasileios Hatzivassiloglou and Kathleen R.McKeown.1997.Predicting the semantic orientation of adjectives.In Proceed-ings of ACL-97,35th Annual Meeting of the Association for Computational Linguistics,pages174–181,Madrid,ES. Vasileios Hatzivassiloglou and Janyce M.Wiebe.2000.Effects of adjective orientation and gradability on sentence subjectivity.In Proceedings of COLING-00,18th International Conference on Computational Linguistics,pages174–181.Jaap Kamps,Maarten Marx,Robert J.Mokken,and Maarten De ing WordNet to measure semantic orienta-tion of adjectives.In Proceedings of LREC-04,4th Interna-tional Conference on Language Resources and Evaluation,vol-ume IV,pages1115–1118,Lisbon,PT.Soo-Min Kim and Eduard Hovy.2004.Determining the senti-ment of opinions.In Proceedings of COLING-04,20th In-ternational Conference on Computational Linguistics,pages 1367–1373,Geneva,CH.Bo Pang and Lillian Lee.2004.A sentimental education:Senti-ment analysis using subjectivity summarization based on min-imum cuts.In Proceedings of ACL-04,42nd Meeting of the Association for Computational Linguistics,pages271–278, Barcelona,ES.Bo Pang and Lillian Lee.2005.Seeing stars:Exploiting class relationships for sentiment categorization with respect to rat-ing scales.In Proceedings of ACL-05,43rd Meeting of the As-sociation for Computational Linguistics,pages115–124,Ann Arbor,US.Ellen Riloff,Janyce Wiebe,and Theresa Wilson.2003.Learn-ing subjective nouns using extraction pattern bootstrapping.In Proceedings of CONLL-03,7th Conference on Natural Lan-guage Learning,pages25–32,Edmonton,CA.P.J.Stone,D.C.Dunphy,M.S.Smith,and D.M.Ogilvie.1966.The General Inquirer:A Computer Approach to Content Anal-ysis.MIT Press,Cambridge,US.Hiroya Takamura,Takashi Inui,and Manabu Okumura.2005.Extracting emotional polarity of words using spin model.In Proceedings of ACL-05,43rd Annual Meeting of the Associa-tion for Computational Linguistics,pages133–140,Ann Arbor, US.Peter D.Turney and Michael L.Littman.2003.Measuring praise and criticism:Inference of semantic orientation from associ-ation.ACM Transactions on Information Systems,21(4):315–346.Peter Turney.2002.Thumbs up or thumbs down?Semantic ori-entation applied to unsupervised classification of reviews.In Proceedings of ACL-02,40th Annual Meeting of the Associa-tion for Computational Linguistics,pages417–424,Philadel-phia,US.Alessandro Valitutti,Carlo Strapparava,and Oliviero Stock.2004.Developing affective lexical resources.PsychNology Journal,2(1):61–83.Stefano Vegnaduzzo.2004.Acquisition of subjective adjectives with limited resources.In Proceedings of the AAAI Spring Symposium on Exploring Attitude and Affect in Text:Theories and Applications,Stanford,US.Casey Whitelaw,Navendu Garg,and Shlomo Argamon.2005.Using appraisal groups for sentiment analysis.In Proceedings of CIKM-05,14th ACM International Conference on Informa-tion and Knowledge Management,pages625–631,Bremen, DE.Theresa Wilson,Janyce Wiebe,and Rebecca Hwa.2004.Just how mad are you?Finding strong and weak opinion clauses.In Proceedings of AAAI-04,21st Conference of the American As-sociation for Artificial Intelligence,pages761–769,San Jose, US.Hong Yu and Vasileios Hatzivassiloglou.2003.Towards answer-ing opinion questions:Separating facts from opinions and iden-tifying the polarity of opinion sentences.In Proceedings of EMNLP-03,8th Conference on Empirical Methods in Natural Language Processing,pages129–136,Sapporo,JP.。
Oracle企业管理器错误解决方法
Oracle企业管理器错误解决方法1. "EM Configuration Assistant Failed" Error:This error occurs when the configuration assistant fails to launch during OEM installation. To resolve this issue, follow these steps:- Make sure that you have the necessary permissions to install and configure software on your system.- Verify that the environment variables are set correctly, including the PATH and ORACLE_HOME variables.- Try running the installation with administrative privileges.2. "Unable to Connect to the Database" Error:You may encounter this error when attempting to connect to the database through OEM. To fix this issue, try the following: - Verify that the database is up and running. You can use the SQL*Plus utility to connect to the database and execute queries.- Make sure that the correct hostname and port number are specified in the connection settings of OEM.- Ensure that the firewall or network settings are not blocking the connection.3. "Invalid Credentials" Error:If you are getting an "Invalid Credentials" error whentrying to log in to OEM, follow these steps to resolve it: - Double-check the username and password you are using. Ensure that you are using the correct case for the username and that the password is typed correctly.- Verify that the user has the necessary privileges to access and manage the database through OEM. Grant the required privileges if necessary.- Ensure that the user account is not locked or expired. You can use the SQL*Plus utility to unlock the account.- If the user account is using the default password profile, reset the password to a new value and try logging in again.4. "EM Console is Not Accessible" Error:- Check the status of the Oracle Management Service (OMS) and the Oracle Management Agent (OMA). Both services should be running.- Verify that the necessary ports (usually 1158 for OMS and 3872 for OMA) are not being blocked by the firewall or any other network security measures.- Review the log files located in the Oracle Base directory for any error messages or relevant information.5. "EM Configuration Assistant Failed: IOException" Error:This error can occur when the configuration assistant encounters an IOException during OEM installation. To fix this, follow these steps:- Make sure that there is enough disk space available on the system for the installation.- Disable any antivirus software temporarily as it may interfere with the installation process.- Verify that the Java Development Kit (JDK) is installed and set up correctly.- Run the installation as an administrator.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
PRACTICE GUIDELINESManagement of Primary Sclerosing CholangitisYoung-Mee Lee,M.D.,Marshall M.Kaplan,M.D.,and the Practice Guideline Committee of the ACG Division of Gastroenterology,New England Medical Center,Tufts University School of Medicine,Boston,MassachusettsPREAMBLEGuidelines for clinical practice are intended to indicate preferred approaches to medical problems as established by scientifically valid research.Double blind,placebo-con-trolled studies are preferable,but reports and expert review articles are also utilized in a thorough review of the litera-ture conducted through the National Library of Medicine’s MEDLINE.When only data that will not withstand objec-tive scrutiny are available,a recommendation is identified as a consensus of experts.Guidelines are applicable to all physicians who address the subject,without regard to spe-cialty training or interests,and are intended to indicate the preferable but not necessarily the only acceptable approach to a specific problem.Guidelines are intended to be flexible and must be distinguished from standards of care that are inflexible and rarely violated.Given the wide range of specifics in any health care problem,the physician must always choose the course best suited to the individual pa-tient and the variables in existence at the moment of deci-sion.Guidelines are developed under the auspices of the Amer-ican College of Gastroenterology and its Practice Parame-ters Committee and approved by the Board of Trustees.Each has been intensely reviewed and revised by the Com-mittee,other experts in the field,physicians who will use them,and specialists in the science of decision of analysis.The recommendations of each guideline are therefore con-sidered valid at the time of their production based on the data available.New developments in medical research and practice pertinent to each guideline will be reviewed at an established time and indicated at publication to assure con-tinued validity.(Am J Gastroenterol 2002;97:528–534.©2002by Am.Coll.of Gastroenterology)INTRODUCTIONPrimary sclerosing cholangitis (PSC)is a chronic progres-sive liver disorder that is characterized by ongoing inflam-mation,obliteration,and fibrosis of both intrahepatic and extrahepatic bile ducts.Diffuse strictures with short inter-vening segments of normal or dilated bile ducts produce the characteristic beaded appearance on cholangiography.The pathogenesis of PSC is unknown,but available data suggest that both immunological and nonimmunological host defenses may be impaired (1).Hence,the normal intestinal flora or their metabolic products may play a patho-genic role (1).The disease is usually progressive and may lead to cirrhosis and portal hypertension.PSC is an uncom-mon disorder for which there are few extensive prevalence data.The estimated prevalence of PSC in the United States,based on studies of inflammatory bowel disease,is 6.3/100,000(2).A true population-based study has only been done in Norway,where incidence and point prevalence were 1.3and 8.5per 100,000inhabitants,respectively.This com-pares to incidence and point prevalence of 1.6and 14.6for primary biliary cirrhosis.These values seem to be higher than in the rest of Europe or the United States.The recog-nition of PSC as a distinct liver disease is relatively recent.Until 1970,fewer than 100patients with PSC had been reported.However,the introduction of endoscopic retro-grade cholangiography has changed our perception of this disease.It is now recognized more frequently and is the fourth leading indication for liver transplantation in adults (3).Here we will review the clinical features of PSC,and then propose recommendations regarding appropriate diag-nostic and therapeutic strategies.There is no proven medical treatment short of liver transplantation.However,there is effective treatment of many of the symptoms associated with PSC.CLINICAL FEATURESApproximately 70%of patients with PSC are men,with a mean age at diagnosis of 40yr (4).There is a strong association between PSC and inflammatory bowel disease,particularly ulcerative colitis (2,5).PSC may occur alone and,rarely,in association with retroperitoneal or mediasti-nal fibrosis.Patients with PSC and without inflammatory bowel disease were more likely to be female (6).Of theMembers of the Practice Guideline Committee of the ACG:Nimish Vakil,M.D.,F.A.C.G.,Chair;Freda L.Arlow,M.D., F.A.C.G.;William D.Carey,M.D.,M.A.C.G.;Christopher P.Cheney,M.D.,F.A.C.G.;Sita S.Chokhavatia,M.D.;Francis A.Farraye,M.D.,F.A.C.G.;Stephen B.Hanauer,M.D.,F.A.C.G.;Kent C.Holtzmuller,M.D.;Kris V.Kowdley,M.D.;Gary R.Lichtenstein,M.D.,F.A.C.G.;George W.Meyer,M.D.,F.A.C.G.;Daniel S.Pratt,M.D.;Dawn Provenzale,M.D.,F.A.C.G.;Amy M.Tsuchida,M.D.,F.A.C.G.;J.Patrick Waring,M.D.,F.A.C.G.;Maurits J.Wiersema,M.D.,F.A.C.G.;John M.Wo,M.D.;and Marc J.Zuckerman,M.D.,F.A.C.G.T HE A MERICAN J OURNAL OF G ASTROENTEROLOGY Vol.97,No.3,2002©2002by Am.Coll.of Gastroenterology ISSN 0002-9270/02/$22.00Published by Elsevier Science Inc.PII S0002-9270(01)04147-8approximately75–90%of patients who have inflammatory bowel disease,about87%have ulcerative colitis,and13% have Crohn’s colitis.Approximately4%of patients with inflammatory bowel disease will either have or develop PSC (7).There are variations in the clinical course of patients with PSC.The majority of patients are initially asymptomatic but can usually be identified on the basis of a cholestatic pattern of liver tests—specifically,elevation of serum alkaline that is proportionately greater than elevations of the aminotrans-ferases.Some asymptomatic patients may have surprisingly advanced disease.This can be demonstrated histologically and radiologically.Some patients may remain asymptom-atic for many years.When symptoms of fatigue,pruritus, jaundice,and weight loss develop,these patients usually have advanced disease.Other patients with histologically and radiologically early disease may be symptomatic and have recurrent episodes of fever,chills,jaundice,right upper quadrant pain,or itching.Intermittent episodes of bacterial cholangitis may be present in10–15%of patients with PSC. Complications of PSC include dominant strictures with pru-ritus and/or jaundice,cholelithiasis,cholangiocarcinoma, malabsorption of fat-soluble vitamins,bleeding from stomal varices,and osteopenia.Although the majority of patients are asymptomatic at the time of diagnosis,most eventually develop fatigue,pruritus, and jaundice.Cirrhosis,portal hypertension,and liver fail-ure usually follow.Patients who were symptomatic at diag-nosis had shortened survival relative to those who were asymptomatic.The survival of asymptomatic patients is significantly shorter than that of a healthy control popula-tion.The estimated median survival time from diagnosis to liver transplantation or death is10–15yr(8,9).There is no relationship between the course of PSC and that of the accompanying inflammatory bowel disease. DIAGNOSISThe most accurate means to diagnose PSC is cholangiog-raphy.Serum liver tests usually show a cholestatic profile, particularly elevation of the serum ALP level.Although liver biopsy is usually consistent with PSC,it is rarely diagnostic.Liver biopsy is useful in staging and aids in prognosis.Neither liver histology nor cholangiography alone will reliably reflect the severity of the disease.They must be used together with symptoms,physicalfindings, blood tests,and imaging or upper endoscopy tests that indicate the presence and severity of portal hypertension. GeneralPSC must be distinguished from secondary sclerosing cholangitis due to other types of biliary disorders.These include chronic bacterial cholangitis in patients with bile duct stricture or choledocholithiasis,ischemic bile duct damage due to treatment withfloxuridine,infectious cholan-giopathy associated with AIDS,prior biliary surgery,con-genital biliary tree abnormalities,and bile duct neoplasms. Blood TestsSerum liver tests usually demonstrate a cholestatic pattern. The initial laboratory evaluation of cholestatic liver disease includes serum ALP,aminotransferases,bilirubin,albumin levels,and the antimitochondrial antibody test.The serum ALP level is usually elevated,although a small number of patients may have normal levels.Most patients have slight increases in serum aminotransferase levels.Serum albumin levels are normal early in the disease.In early stages of PSC, serum bilirubin values are usually normal,but they gradu-ally increase as the disease progresses.Occasionally,strik-ingfluctuations in bilirubin levels may occur,even at early stages.Hypergammaglobulinemia is found in about30%of pa-tients,and increased IgM levels in50%(10).Autoantibod-ies occur less frequently than in autoimmune chronic active hepatitis and primary biliary cirrhosis.Anti–smooth muscle antibodies and antinuclear antibodies are detectable in less than10–20%of patients with PSC(11).Antimitochondrial antibodies are rarely,if ever,found in patients with PSC. About30–80%of PSC patients have perinuclear antineu-trophil cytoplasmic antibodies(12),and52%have the hu-man leukocyte antigen DRw52a(13).There is still no con-sensus as to whether specific alleles in the human leukocyte antigen loci,such as DRB10301or DRB11301,are directly associated with PSC(14).As in primary biliary cirrhosis, levels of hepatic and urine copper levels are increased,as is the serum ceruloplasmin.Because copper is excreted pri-marily in bile,the amount of copper in the body increases as cholestasis worsens.CholangiographyCholangiography is the usual way to diagnose PSC.Endo-scopic retrograde cholangiography is the test of choice. Transhepatic cholangiography is performed only if endo-scopic retrograde cholangiography is unsuccessful.Mag-netic resonance cholangiography is increasingly available but does not yet visualize the intrahepatic bile ducts suffi-ciently to replace direct cholangiography.The radiological findings of PSC are characteristic and include multifocal strictures and dilations,usually involving both the intrahe-patic and the extrahepatic biliary trees.Diffuse strictures with short intervening segments of normal or dilated bile duct produce the classic beaded appearance.Some patients may have ulcerations in the larger bile ducts that resemble those seen in Crohn’s disease.The gallbladder and cystic duct are involved in up to15%of cases(15).Abnormalities of the pancreatic ducts resembling those of chronic pancre-atitis have been reported(16,17).Dominant strictures of the larger bile ducts were seen in only7%of1000patients seen at the Mayo Clinic in the last10yr.Dilation of these dominant strictures improved symptoms and blood tests (18).529AJG–March,2002Management of Primary Sclerosing CholangitisThere is one putative variant,called small duct PSC,in which the affected bile ducts are too small to be seen by cholangiography(19).The prevalence of small duct PSC is uncertain but was reported to be less than5%of PSC patients at the Mayo Clinic(19).It is diagnosed in patients with inflammatory bowel disease who have cholestatic liver tests,and characteristic liver biopsies but normal endoscopic retrograde cholangiography and negative antimitochondrial antibody tests.Histological FeaturesPSC has been divided into four histological stages(20). Stage1represents the initial lesion,and the other stages presumably develop with time and the progression of dis-ease.Stage1is characterized by the degeneration of bile duct epithelial cells and infiltration of the bile ducts by inflammatory cells,predominantly lymphocytes but occa-sionally neutrophils.There is inflammation,scarring and enlargement of portal triads,and,at times,portal edema. There may be proliferation of bile ducts in some portal triads,vacuolization of ductular epithelial cells,and con-centric layers of connective tissue surrounding bile ducts (onionskin lesion).There is typically less inflammation in the portal triads than in primary biliary cirrhosis.In stage2, the lesion is more widespread.Thefibrosis and inflamma-tion infiltrate the periportal parenchyma,and the periportal hepatocytes may be destroyed.Portal triads are often en-larged.Bile ductopenia is a prominent feature;concentric periductalfibrosis is less obvious.As the disease progresses to stage3,there is formation of portal-to-portal bridging fibrous septa.Bile ducts are absent or have undergone se-vere degenerative changes.Cholestasis may be prominent, primarily in periportal and paraseptal hepatocytes.Stage4, the end stage,is characterized by frank cirrhosis;the histo-logical features are similar to those seen in other forms of that disease.In PSC,however,there may also be changes associated with large duct obstruction,the proliferation and dilation of interlobular bile ducts,and increased numbers of periportal neutrophils.The most characteristic sign of PSC,the onionskin lesion, is rarely seen on a percutaneous liver biopsy(21).It is more common to see only a paucity of normal bile ducts with nonspecificfibrosis and inflammation in the portal triads. Therefore,a definite diagnosis must be established by cholangiography.Liver histology is used for confirmation and to determine the stage and the prognosis of disease.As sampling variation may occur with liver biopsy,histological staging requires the examination of a sufficiently large spec-imen that has at least10portal triads. MANAGEMENTThere is no proven medical therapy for PSC.The goal of management should be treatment of symptoms and compli-cations of cholestasis,as well as attempts at treating the underlying disease process.In addition,efforts should be made to recognize and treat or prevent the known compli-cations of PSC such as fat-soluble vitamin deficiency,os-teopenia,dominant biliary strictures,and cholangiocarci-noma.Liver transplantation is the only effective treatment and is recommended for patients with end-stage liver dis-ease and symptomatic portal hypertension,liver failure,and recurrent or intractable bacterial cholangitis. Management of Chronic Cholestasis and Its ComplicationsSymptoms of chronic cholestasis in PSC are similar to those of primary biliary cirrhosis.They include fatigue,pruritus, steatorrhea,and metabolic bone disease.However,unique problems result from mechanical bile duct obstruction,in-cluding bacterial cholangitis,sepsis,and the formation of pigment stones within the obstructed bile ducts.In addition, patients with PSC are at risk of developing cholangiocarci-noma.Cholangiocarcinoma may be difficult to distinguish from the bile duct strictures typical of PSC. PRURITUS.Pruritus is a common symptom of PSC and may be disabling.The precise cause of pruritus remains uncertain.Recent evidence suggests that pruritus may be mediated by an upregulation of central opioidergic receptors(22).It is not caused by the retention of bile acids in skin(23).A variety of agents have been evaluated in the man-agement of pruritus.Cholestyramine,a nonabsorbed resin, is effective in most patients as long as there is adequate bile flow(24).The usual starting dose of cholestyramine is4g t.i.d.p.o.The dose must be adjusted in individual patients. There is usually a2-to4-day interval between the time that cholestyramine is begun and pruritus remits.Colestipol hy-drochloride,another ammonium resin,is as effective as cholestyramine and may be used in those patients who cannot tolerate cholestyramine.Patients must be cautioned to take these resins2.5to3h before or after they take other medications.Many drugs will bind tightly to these resins in the intestinal tract,particularly ursodeoxycholic acid (UDCA),and will not be absorbed.Rifampin(150mg b.i.d.) is effective in many patients whose pruritus does not re-spond to cholestyramine or colestipol(25).Phenobarbital (60–100mg at bedtime)may also be helpful in this setting (26).Antihistamines are occasionally helpful in patients with mild pruritus if taken at bedtime.Naloxone(27)and naltrexone(28),opioid antagonists,may be helpful in pa-tients who do not respond to any of the rge volume plasmapheresis is almost always effective if there is intrac-table pruritus that fails to respond to all of the above(29). However,it is expensive and time consuming and usually reserved for those awaiting liver transplantation.Methyl-testosterone(30),ursodiol(31),S-adenosylmethionine(32), ondansetron(33),prednisone,and ultraviolet light(34)have been used to control pruritus in individual patients but are tried only if all else fails.Although ursodiol is commonly used for the management of pruritus,there are no controlled data supporting its use.530Lee et al.AJG–Vol.97,No.3,2002STEATORRHEA AND VITAMIN DEFICIENCY.Ste-atorrhea and malabsorption of fat-soluble vitamins may occur late in the course of PSC.Fat malabsorption in jaun-diced patients is usually related to decreased secretion of conjugated bile acids into the small intestine.Other causes are pancreatic insufficiency and celiac disease,both of which may be associated with PSC(35,36).Vitamin A deficiency has been reported in up to82%of patients with advanced PSC(37).Vitamin D and E occur in approxi-mately40–50%of patients with advanced PSC(37).Clin-ically important vitamin K deficiency rarely occurs unless the patient is chronically jaundiced and takes cholestyra-mine regularly.In PSC patients with chronic jaundice,fat-soluble vitamin levels should be monitored,and deficiencies treated with supplements.METABOLIC BONE DISEASE.Osteoporosis is a more common complication of patients with chronic cholestasis than osteomalacia(38).The pathogenesis of osteoporosis in PSC or other chronic cholestatic liver diseases is unknown. Osteoporosis is not related to vitamin D deficiency.The serum concentrations of25-hydroxyvitamin D and1,25-dihydroxyvitamin D,the physiologically active metabolites of vitamin D,are usually normal.The osteoporosis may be related to osteoblast inhibitors in cholestatic serum(39). There is no proven medical treatment for osteoporosis in PSC.Treatment with25-hydroxyvitamin D with calcium, ursodiol,calcitonin,and biphosphonates has been sug-gested,but there are no controlled data that demonstrate efficacy(40).Alendronate is more effective than etiodronate in osteopenic patients with PBC(41).However,there have been no published controlled trials of bisphosphonates in the osteoporosis associated with PSC.BACTERIAL CHOLANGITIS.Bacterial cholangitis may occur after endoscopic procedures or in patients with bile duct stones or tight strictures.Antibiotics are effective in treating recurrent episodes of ascending cholangitis but have not been shown to slow the progression of PSC.Anecdotal reports suggest that such drugs reduce the frequency and severity of attacks of recurrent bacterial cholangitis.Cipro-floxacin has been recommended for treatment and prophy-laxis of bacterial cholangitis because of its high biliary tract penetration.Alternative agents are amoxicillin or tri-methoprim-sulfamethoxazole.Tetracycline was ineffective in one small study in PSC(42).However,there have been no randomized prospective trials that have critically evalu-ated antibiotics in PSC.Additional controlled trials are needed to evaluate the efficacy of antibiotics. DOMINANT BILIARY STRICTURES.Dominant stric-tures of the extrahepatic bile duct occur in7–20%of patients with PSC(18,43).Several studies reported successful man-agement with endoscopic balloon dilation or biliary stenting of the dominant strictures(44–47).Endoscopic dilation was associated with fewer episodes of cholangitis and improve-ment of cholangiographic appearance and biochemical tests.There are no randomized controlled trials that have evalu-ated the efficacy of endoscopic therapy.There appears to be little risk and some potential benefit in this approach.In one uncontrolled trial,endoscopic dilation plus ursodiol ap-peared to prolong survival without liver transplantation when compared to the expected survival in untreated pa-tients(47).Another approach to the dominant stricture is surgical dilation or choledochojejunostomy.Surgical resec-tion of hilar and extrahepatic strictures in noncirrhotic pa-tients may postpone the need for transplantation and the development of cholangiocarcinoma in carefully selected patients(48).However,surgical resection carries the risk of postoperative infection and increases scarring in the porta-hepatis,potentially complicating future liver transplanta-tion.CHOLANGIOCARCINOMA.There is an increased inci-dence of cholangiocarcinoma in patients with PSC.The reported frequencies of cholangiocarcinomas associated with PSC range from6%to30%(49).Patients with long-standing chronic ulcerative colitis and cirrhosis are at high-est risk.Most cholangiocarcinomas occur at or near the junction of the right and left hepatic bile ducts.The lack of sensitive and specific serological tumor markers as well as the insensitivity of biliary brush cytology have hampered early diagnosis of cholangiocarcinoma.The serological tu-mor markers,such as carcinoembryonic antigen and cancer antigen19-9,have not been useful in diagnosing early, potentially treatable cholangiocarcinomas(50).In addition, it is difficult to distinguish PSC from PSC complicated by cholangiocarcinoma.Often an unsuspected cholangiocarci-noma is found after liver transplantation when the resected liver is examined in the pathology laboratory.Treatment of clinically apparent cholangiocarcinoma by resection,che-motherapy,and radiation has been discouraging,as have been the results with liver transplantation(51).Some ex-perts have suggested surgical extirpation of the biliary tree or liver transplantation before the development of cholan-giocarcinoma.The value of screening for cholangiocarci-noma has not been proven.Specific Therapy of PSCA variety of choleretic,immunosuppressive,and antifibrotic agents have been used to treat PSC.However,no drug has been shown to alter its natural history.The evaluation of treatment of PSC has been limited by the uncertainty about its cause and the unpredictable course of the disease.The course of PSC is indolent in most patients but may be rapidly progressive in some and asso-ciated with spontaneous exacerbations and remissions in others.Hence,even if a drug is effective,it will probably be years before its efficacy can be proven.UDCA.UDCA,a hydrophilic bile acid,has been widely used to treat PSC.Therapy with the drug leads to a2-to 3-fold increase in serum bile acid concentration.There is an increase in the biliary and urinary excretion of bile acids and531AJG–March,2002Management of Primary Sclerosing Cholangitisan increase in bileflow.In vitro,UDCA stabilizes liver cell membranes exposed to toxic concentrations of the naturally occurring bile acid chenodeoxycholic acid.There have been several small studies and one large controlled trial that reported improvements in symptoms and liver tests with UDCA(52–55)(Table1).The long term beneficial effects of UDCA on the natural history were unclear because these trials were of relatively short duration and included few patients.A prospective randomized dou-ble-blind placebo-controlled trial of105patients continued for2yr confirmed earlier reports that UDCA(13–15mg/kg of body weight/day)significantly improved liver tests(56). However,UDCA had no beneficial effect on time to treat-ment failure or liver transplantation.Furthermore,UDCA did not improve symptoms,cholangiographic appearance, and liver histology.A nonrandomized study of UDCA with endoscopic dila-tion of dominant stricture indicates that this combination may be more effective than UDCA alone(47).Higher dose UDCA in a pilot study appears to be prom-ising.A double-blind placebo-controlled pilot study of higher dose(20mg/kg)UDCA in patients observed for2yr showed that UDCA was associated with improvement of ALP and liver histology(57).The higher dose UDCA was well tolerated and had no significant side effects.In addi-tion,there is a trial that employs a still higher dose of UDCA,25–30mg/kg/day(58).It is as well tolerated as lower doses of UDCA.Because there are no long term data on higher doses of UDCA,their ability to improve the natural history of PSC is still unproven. IMMUNOSUPPRESSIVE AND ANTIFIBROTIC AGENTS. Despite anecdotal reports of improvement with glucocorti-coids and azathioprine in patients with PSC,there is little enthusiasm for their use(59).In addition,glucocorticoids may accelerate the onset and progression of osteoporosis and increase the likelihood of spontaneous bone fractures. Colchicine was not effective in a double blind study of85 patients with PSC(60),and neither was the combination of colchicine and prednisone(61).In a randomized trial of34 patients,cyclosporine had no beneficial effect on pruritus, fatigue,liver tests,or survival free of liver transplantation(62).Tacrolimus(FK506)appeared to improve liver tests ina small,uncontrolled pilot study of1yr duration.However, its short duration and lack of histological and cholangio-graphic data limited its value(63).Methotrexate improved liver tests and liver histology in an uncontrolled trial of10 patients(64).However,in a double blind,controlled trial of 24patients,methotrexate was not effective in prolonging survival free of liver transplantation when compared to a placebo(65).Pentoxifylline prevents the production of tu-mor necrosis factor,which has been postulated to have a role in hepatic injury in PSC.In a pilot study of20patients, pentoxifylline was not beneficial in improvement of symp-toms or liver tests(66).D-Penicillamine,a cupruretic and antifibrotic agent,was evaluated in a double-blind prospec-tive trial in70patients observed during36months(67). D-Penicillamine produced the expected cupriuresis,but had no beneficial effect on symptoms,liver tests,liver histology, or survival.OTHER AGENTS.Several other agents have been used to treat PSC,including cholestyramine and nicotine(68).The rationale for nicotine is based on the observation that PSC is less common in smokers and nicotine has a beneficial effect in some patients with ulcerative colitis.However,neither agent was effective.INDICATIONS FOR LIVER TRANSPLANTATIONFor patients with advanced PSC,liver transplantation is the only effective therapeutic option.Indications for liver transplantation include bleeding from varices or portal gastropathy,intractable ascites with or without spontaneous bacterial peritonitis,recurrent episodes of bacterial cholangitis,progressive muscle wasting,and hepatic encephalopathy.A number of transplant centers now report a3-yr survival rate of85–90%for patients with PSC (69).However,stricturing of the transplanted bile ducts is a post–liver transplantation problem that is more common in PSC patients than in other diseases that lead to liver trans-plantation.The pattern of the strictures is similar to that seen in PSC.Possible causes include recurrence of PSC,isch-emia,chronic rejection,or infectious cholangitis related to the Roux-en-Y biliary anastomosis and immunosuppres-sion.How often and when PSC recurs after liver transplan-tation is uncertain.Data from one center suggest that PSC recurs in10–20%of PSC patients(70),whereas others report lower rates of recurrence(71).In PSC patients with inflammatory bowel disease who undergo liver transplantation,inflammatory bowel syn-drome symptoms are generally improved.On the otherTable1.Controlled Trials of UDCA in PSC*Reference No.ofPatients UDCA Dose Treatment Duration SymptomsLiver FunctionTests HistologyBeuers(54)1413–15mg/kg/day12mo Unchanged Improved Improved Stiehl(47,52)20750mg/day Meanϭ45mo Unchanged Improved,exceptbilirubinImproved Lindor(56)10513–15mg/kg/day Meanϭ0.5–72mo Unchanged Improved Unchanged Mitchell(57)2420mg/kg/day24mo Unchanged Improved Improved *No study has shown improvement in the natural history of PSC.532Lee et al.AJG–Vol.97,No.3,2002。
