Ethereal_HTTP
实验四 利用Ethereal分析HTTP

实验四利用Ethereal分析HTTP一、实验目的熟悉并掌握ethereal的基本操作,了解网络协议实体之间的交互和消息交换。
2、实验环境windows9x/nt/2000/xp/2021与因特网连接的计算机网络系统ethereal等软件。
三、实验原理1.深入理解网络协议,仔细观察协议实体之间交换的消息序列。
它是在模拟环境或真实网络环境(如互联网)中完成的。
观察正在运行的协议实体之间消息交换的基本工具称为包嗅探器。
通常,数据包嗅探器将存储并显示捕获的消息的每个协议头字段的内容。
ethereal是一种可以运行在windows,unix,linux等操作系统上的分组分析器。
ethereal的界面主要有五个组成部分:捕获数据包列表:按行显示捕获数据包的内容,包括:ethereal给出的数据包序列号、捕获时间、数据包的源地址和目标地址、协议类型以及数据包中包含的协议描述信息。
单击要创建的列的列名分组按指定列进行排序。
在该列表中,所显示的协议类型是发送或接收分组的最高层协议的类型。
所选数据包标头的详细信息:在捕获的数据包列表窗口中显示所选数据包的标头详细信息。
它包括:与以太网帧相关的信息和包含在数据包中的IP数据报相关的信息。
分组内容窗口(packetcontent):以ascii码和十六进制两种格式显示被俘获帧的完整内容。
显示过滤器规格:在此字段中,您可以填写协议名称或其他信息。
根据此内容,您可以在“组列表”窗口中筛选组。
4.以太的使用启动主机上的web浏览器。
开始分组俘获:选择“capture”下拉菜单中的“start”命令,设置分组俘获的选项。
首先,下载一个非常简单的HTML文件(该文件非常短,不嵌入任何对象)。
开始ethereal分组俘获。
在打开的WebBrowser窗口中输入地址(浏览器中将显示一个非常简单的HTML文件,其中只有几行文本):启动浏览器,清空浏览器的缓存(在浏览器中,选择“工具”菜单中的“internet选项”命令,在出现的对话框中,选择“删除文件”)。
Wireshark抓包实例分析 (DNS和HTTP协议)

(八)参考资料
《计算机科学网络 自顶向下的方法》 第四版 陈鸣 译 《WireShark 教程用户使用手册》 《学习用 wireshark 进行抓包分析》 罗小嘉
表单数据以及浏览记录等等。 3、单击开始,打开运行,输入'cmd',输入命令'ipconfig/flushdns',回车,即
可看到成功刷新 DNS 缓存的显示。
2、WireShark 的使用
(1) 启动 WireShark。 (2) 启动 PC 上的 IE 浏览器。 (3) 开始分组捕获:选择“抓包”下拉菜单中的“抓包参数选择”命令,在
图二
其中,第一行为该包的信息,第二行为以太网,属于链路层,第三行为 IP 协 议,属于网络层(源 IP 与目的 IP 显示在该行),第四行为 UDP 协议,属于传输 层,第五行为 DNS 的有关数据。下面将通过图三详细分析 DNS 报文的内容。
这是一个请求查询 的报文(0),该报文没有 被删节,采用的是递归调 用的查询,问题数为 1, 回答 RR 数,权威 RR 数 以及附加 RR 数均为 0。 在问题区域显示了名字 字段与被查询的问题类 型 A(即主机地址)。
计算机网络技术基础目录一封面第1页二目录第2页三内容一实验背景介绍第3页二实验目的及任务第3页三实验环境第3页四实验原理第3页五实验步骤第3页1实验前的准备工作第4页2wireshark的使用第4页六实验结果分析第4页1dns分析第45页2http分析第67页七实验总结第7页八参考资料第7页内容一实验背景介绍wireshark简介wireshark原ethereal是目前最流行的一款网络封包分析软件
实验二:Ethereal Lab —— HTTP协议

实验二:Ethereal Lab ——HTTP协议一、实验目的通过本次实验,利用Ethereal软件从以下几个方面研究 HTTP协议的运行机制:实验2-1:基本的GET/response交换;实验2-2: HTTP的有条件GET/response交互;实验2-3:利用HTTP获取大的HTML文件;实验2-4:利用HTTP获取带有嵌入式对象的HTML文件;实验2-5:HTTP认证与安全。
二、实验原理万维网(World Wide Web,WWW)是一种基于因特网的分布式信息查询系统。
WWW 的工作基于客户机/服务器模型,由Web浏览器(客户机)向Web服务器(服务器)请求由超文本标记语言(HTML)编辑的网页,Web服务器进行响应,返回相应网页,两者之间采用超文本传送协议(HTTP)进行通信。
HTTP有两种报文类型:请求报文和响应报文。
请求报文的格式如下图1,响应报文格式如下图2:图1:HTTP请求报文图2:HTTP响应报文浏览器可以缓存最近请求过的对象的拷贝,避免再次向服务器请求该对象,减少响应时间。
但是缓存的对象有可能因为服务器端最近做过修改而变得陈旧,HTTP允许浏览器证实缓存的对象是否是最新的,即条件GET方法。
条件GET方法在请求报文中使用GET方法,并包含一个If-Modified-Since首部行,含义是告诉服务器仅当自指定日期之后修改过该对象时才发送该对象。
如果服务器在指定日期后并未修改该对象,则不再返回该对象。
网页是由对象组成的,对象如HTML文件、JPEG图形文件、Java小程序等等。
多数Web页含有一个基本的HTML文件和多个引用对象,在基本的HTML文件中通过对象的URL地址对对象进行引用,对象可能存储在多个不同的服务器上,浏览器通过对象的URL地址向不同的服务器发出请求。
三、实验步骤与实验问题探讨【注:实验步骤应用(x),问题用[x]】1.基本的HTTP GET/response交互下面利用HTTP获取一个简单的HTML文件(一个非常短且不含有嵌入式对象的文件)。
Ethereal 分析数据报文

实验二利用网络嗅探工具Ethereal分析数据报文一、实验目的网络世界中,最基本的单元是数据包。
本实验内容作为将来各个实验的基础,培养对网络通讯协议底层的分析和认识,加强对网络的理解。
实验内容主要关注 ICMP、HTTP 包的检验。
1.学习网络嗅探工具 Ethereal 的使用。
2.利用抓包工具Ethereal,抓取ICMP包,完成对ICMP 包的分析工作。
明白 ICMP 包的结构。
结合 TCP/IP 的模型,分析 ICMP 包各层的功能,以及各层通信使用的地址,了解 ICMP 请求和响应包的 ICMP 协议号。
3.利用抓包工具 Ethereal,抓取 HTTP 包。
了解 HTTP 协议请求、响应包类型,结合课本学习知识完成的 HTTP 协议的剖析和掌握。
将来的课程实验中,需要使用该工具进行包分析,判断大多数安全和网络通讯问题。
二、实验环境1. 局域网环境2. Ethereal软件Ethereal 软件介绍Ethereal是一个网络数据包分析软件。
网络数据包分析软件的功能是截取网络数据包,并尽可能显示出最为详细的网络数据包资料。
网络数据包分析软件的功能可想像成"电工技师使用电表来量测电流、电压、电阻"的工作——只是将场景移植到网络上,并将网络线替换成电线。
三、实验任务1. 任务1:Ethereal 软件的基本功能使用2. 任务2:ICMP 数据报文的检测与分析3. 任务3:HTTP 数据报文的检测与分析四、实验步骤首先安装Ethereal和Winpcap。
任务1:Ethereal 软件的基本功能使用一、 打开 Ethereal,其界面如下图:二、在菜单的“capture”选项中设置抓包的相关参数,如下图:三、选择“interfaces”选项,对话框中显示可操作的网络适配器,如下图:四、通过“Prepare”或上级菜单“Option”选项,可以设置抓包模式、过滤器、数据包限制字节、存档文件模式、停止规则和名字解析等参数,如下图:设置完毕,就可以点击“Capture”,开始数据报文的捕获。
实验二 利用分组嗅探器(ethereal)分析协议HTTP
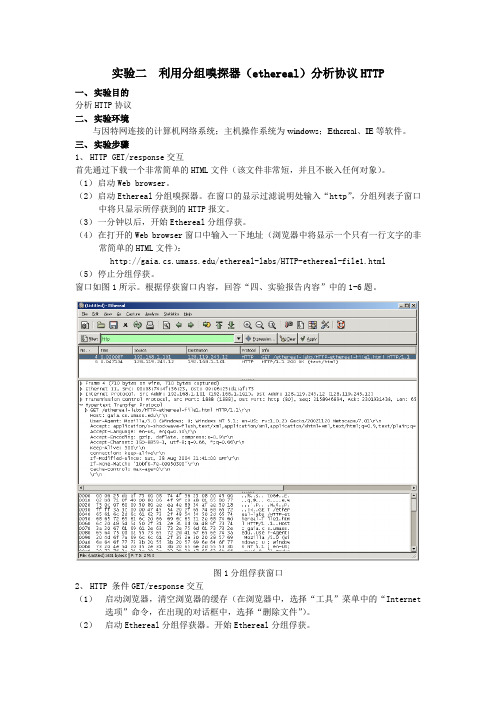
实验二利用分组嗅探器(ethereal)分析协议HTTP一、实验目的分析HTTP协议二、实验环境与因特网连接的计算机网络系统;主机操作系统为windows;Ethereal、IE等软件。
三、实验步骤1、HTTP GET/response交互首先通过下载一个非常简单的HTML文件(该文件非常短,并且不嵌入任何对象)。
(1)启动Web browser。
(2)启动Ethereal分组嗅探器。
在窗口的显示过滤说明处输入“http”,分组列表子窗口中将只显示所俘获到的HTTP报文。
(3)一分钟以后,开始Ethereal分组俘获。
(4)在打开的Web browser窗口中输入一下地址(浏览器中将显示一个只有一行文字的非常简单的HTML文件):/ethereal-labs/HTTP-ethereal-file1.html(5)停止分组俘获。
窗口如图1所示。
根据俘获窗口内容,回答“四、实验报告内容”中的1-6题。
图1分组俘获窗口2、HTTP 条件GET/response交互(1)启动浏览器,清空浏览器的缓存(在浏览器中,选择“工具”菜单中的“Internet 选项”命令,在出现的对话框中,选择“删除文件”)。
(2)启动Ethereal分组俘获器。
开始Ethereal分组俘获。
(3)在浏览器的地址栏中输入以下URL: /ethereal-labs/HTTP-ethereal-file2.html,你的浏览器中将显示一个具有五行的非常简单的HTML文件。
(4)在你的浏览器中重新输入相同的URL或单击浏览器中的“刷新”按钮。
(5)停止Ethereal分组俘获,在显示过滤筛选说明处输入“http”,分组列表子窗口中将只显示所俘获到的HTTP报文。
根据操作回答“四、实验报告内容”中的7-10题。
3、获取长文件(1)启动浏览器,将浏览器的缓存清空。
(2)启动Ethereal分组俘获器。
开始Ethereal分组俘获。
(3)在浏览器的地址栏中输入以下URL: /ethereal-labs/HTTP-ethereal-file3.html,浏览器将显示一个相当大的美国权力法案。
网络协议分析工具Ethereal的使用

⽹络协议分析⼯具Ethereal的使⽤⼤学时计算机⽹络课的实验报告,当时提不起兴趣,今天看来还挺有⽤的。
可以学习下怎样抓数据包,然后分析程序的通信协议。
⼀:学习使⽤⽹络协议分析⼯具Ethereal的⽅法,并⽤它来分析⼀些协议。
实验步骤:1.⽤“ipconfig”命令获得本机的MAC地址和缺省路由器的IP地址;(注:缺省路由器即 ”Default Gateway”)命令⾏:Start->Run->CMD->ipconfig /all >C:\Mac.txt(在命令⾏中把ipconfig命令保存在⽂本⽂档⾥⾯备⽤)结果:本机Mac地址:00.09.73.4B.8A.D7 缺省路由器IP:192.168.8.254步骤截图:图1(本机⽹络信息:Mac.txt)2.⽤“arp”命令清空本机的缓存:命令⾏:Start->Run->CMD->arp –d图2(arp命令 –d参数的帮助说明)3.运⾏Ethereal,开始捕获所有属于ARP协议或ICMP协议的,并且源或⽬的MAC地址是本机的包:图3(Capture->Options中关于⽹卡设置和Capture Filter)图4(抓包截图)4.执⾏命令:“ping” 缺省路由器的IP地址:图5(捕获包)图6(ping 过程)⼆:⽤Ethereal观察tracert命令的⼯作过程:1.⽤Ethereal语法内容及参数说明:命令⾏操作步骤:Start->Run->CMD->tracert图1(Tracert命令全部参数的帮助说明)2.运⾏Ethereal, 设定源和⽬的MAC地址是本机的包,捕获tracert命令中⽤到的消息:Tracert使⽤ICMP,相应过滤规则为:ether host 00:09:73:4B:8A:D7 and icmp图3(Capture->Options中关于⽹卡设置和Capture Filter)3.执⾏“tracert -d ” ,捕获包:执⾏命令:tracert -d :图3 (执⾏命令 tracert –d )图4(抓包截图)图5(捕获包)4.Tracert⼯作原理:Tracert使⽤ICMP消息,具体地讲,tracert发出的是Echo Request消息,触发返回的是Time Exceeded消息和Echo Reply消息。
ethereal使用以及IP协议解析

1.主界面介绍随着3G的普及,手机数据业务量(如浏览器,彩信等)的日益增长,对手机侧网络包的分析显得越来越重要。
一般来说,手机数据业务的抓包工具为QXDM,在抓LOG指导里面已经有了详细参数的配置介绍(详情见《IP数据包抓取方法.doc》)。
但需要注意的是,在将LOG转化为.pcap文件时,必须保证当前电脑里安装有Ethereal软件,否者PCAPGenerator这个工具不会出现。
(针对使用Tools->PCAPGenerator转化.isf文件出错的情况,可以做如下尝试:先使用Tools->ISF File Converter将刚刚保存的.isf文件其转化为.dlf文件,然后使用Tools->PCAPGenerator将.dlf 文件转换成.pcap文件)。
这里主要针对抓到IP包后,怎么样使用Ethereal软件对IP包进行分析,以及一些简单的TCP/IP协议介绍。
直接点击打开.pcap文件,可以看到如下图1所示界面。
图1中间彩色的区域就是IP数据包。
从左到右,字段分别是No.,Time,Source,Destination,Protocol以及Info。
IP包是按照流经手机网卡的时间顺序排列的,NO.是标示抓到的IP包是该抓包文件中的第几个,Time则是计算的所有包与第一个包之间的间隔时间,单位毫秒ms。
Source和Destination字段分别表示IP包的源地址和目的地址。
Protocol显示当前IP包的上层协议,如TCP,UDP,如果应用层协议头也在该IP包中,优先显示应用层协议,如RTSP,HTTP等。
注意中间的彩色显示,不同的颜色代表该IP包中包含了不同内容,这是方便我们对IP 包查看。
如上面的大红色,表示的是该数据包损坏,可能是只有一半的内容,也可能是指在该包与其他包的序号不连续(指在协议层不连续),中间可能出现丢包的现象。
很多时候,Ethereal是用不同颜色来区分上层协议的不同(注意IP包中必须包含上层协议的包头,才能以该应用的颜色进行标示。
Ethereal_HTTP---英文指导书

Ethereal Lab: HTTP Version: 1.0© 2005 J.F. Kurose, K.W. Ross. All Rights ReservedComputer Networking: A Top-down Approach Featuring the Internet, 3rd edition.Having gotten our feet wet with the Ethereal packet sniffer in the introductory lab, we’re now ready to use Ethereal to investigate protocols in operation. In this lab, we’ll explore several aspects of the HTTP protocol: the basic GET/response interaction, HTTP message formats, retrieving large HTML files, retrieving HTML files with embedded objects, and HTTP authentication and security. Before beginning these labs, you might want to review Section 2.2 of the text.1. The Basic HTTP GET/response interactionLet’s begin our exploration of HTTP by downloading a very simple HTML file - one that is very short, and contains no embedded objects. Do the following:1.Start up your web browser.2.Start up the Ethereal packet sniffer, as described in the Introductory lab (but don’tyet begin packet capture). Enter “http” (just the letters, not the quotation marks)in the display-filter-specification window, so that only captured HTTP messages will be displayed later in the packet-listing window. (We’re only interested in the HTTP protocol here, and don’t want to see the clutter of all captured packets).3.Wait a bit more than one minute (we’ll see why shortly), and then begin Etherealpacket capture.4.Enter the following to your browser/ethereal-labs/HTTP-ethereal-file1.htmlYour browser should display the very simple, one-line HTML file.5.Stop Ethereal packet capture.Your Ethereal window should look similar to the window shown in Figure 1. If you are unable to run Ethereal on a live network connection, you can download a packet trace that was created when the steps above were followed.11 Download the zip file /ethereal-labs/ethereal-traces.zip and extract the file http-ethereal-trace-1. The traces in this zip file were collected by Ethereal running on one of the author’s computers, while performing the steps indicated in the Ethereal lab. Once you have downloaded the trace,Figure 1: Ethereal Display after /ethereal-labs/ HTTP-ethereal-file1.html has been retrieved by your browserThe example in Figure 1 shows in the packet-listing window that two HTTP messages were captured: the GET message (from your browser to the web server) and the response message from the server to your browser. The packet-contents window shows details of the selected message (in this case the HTTP GET message, which is highlighted in the packet-listing window). Recall that since the HTTP message was carried inside a TCP segment, which was carried inside an IP datagram, which was carried within an Ethernet frame, Ethereal displays the Frame, Ethernet, IP, and TCP packet information as well. We want to minimize the amount of non-HTTP data displayed (we’re interested in HTTP here, and will be investigating these other protocols is later labs), so make sure the boxes at the far left of the Frame, Ethernet, IP and TCP information have a right-pointing arrowhead (which means there is hidden, undisplayed you can load it into Ethereal and view the trace using the File pull down menu, choosing Open, and then selecting the http-ethereal-trace-1 trace file. The resulting display should look just like Figure 1.information), and the HTTP line has a down-pointing arrowhead (which means that all information about the HTTP message is displayed).(Note: You should ignore any HTTP GET and response for favicon.ico. If you see a reference to this file, it is your browser automatically asking the server if it (the server) has a small icon filethat should be displayed next to the displayed URL in your browser. We’ll ignore references tothis pesky file in this lab.).By looking at the information in the HTTP GET and response messages, answer the following questions. When answering the following questions, you should print out the GET and response messages (see the introductory Ethereal lab for an explanation of how to do this) and indicate where in the message you’ve found the information that answers the following questions.1.Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is theserver running?2.What languages (if any) does your browser indicate that it can accept to theserver?3.What is the IP address of your computer? Of the server?4.What is the status code returned from the server to your browser?5.When was the HTML file that you are retrieving last modified at the server?6.How many bytes of content are being returned to your browser?7.By inspecting the raw data in the packet content window, do you see any headerswithin the data that are not displayed in the packet-listing window? If so, nameone.In your answer to question 5 above, you might have been surprised to find that the document you just retrieved was last modified within a minute before you downloaded the document. That’s because (for this particular file), the server is setting the file’s last-modified time to be the current time, and is doing so once per minute. Thus, if you wait a minute between accesses, the file will appear to have been recently modified, and hence your browser will download a “new” copy of the document.2. The HTTP CONDITIONAL GET/response interactionRecall from Section 2.2.5 of the text, that most web browsers perform object caching and thus perform a conditional GET when retrieving an HTTP object. Before performing the steps below, make sure your browser’s cache is empty. (To do this under Netscape 7.0, select Edit->Preferences->Advanced->Cache and clear the memory and disk cache.For Internet Explorer, select Tools->Internet Options->Delete File; these actions will remove cached files from your browser’s cache.) Now do the following: •Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/HTTP-ethereal-file2Your browser should display a very simple five-line HTML file.•Quickly enter the same URL into your browser again (or simply select the refresh button on your browser)•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed later in thepacket-listing window.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-2 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)Answer the following questions:8.Inspect the contents of the first HTTP GET request from your browser to theserver. Do you see an “IF-MODIFIED-SINCE” line in the HTTP GET?9.Inspect the contents of the server response. Did the server explicitly return thecontents of the file? How can you tell?10.Now inspect the contents of the second HTTP GET request from your browser tothe server. Do you see an “IF-MODIFIED-SINCE:” line in the HTTP GET? Ifso, what information follows the “IF-MODIFIED-SINCE:” header?11.What is the HTTP status code and phrase returned from the server in response tothis second HTTP GET? Did the server explicitly return the contents of the file?Explain.3. Retrieving Long DocumentsIn our examples thus far, the documents retrieved have been simple and short HTML files. Let’s next see what happens when we download a long HTML file. Do the following:•Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/HTTP-ethereal-file3Your browser should display the rather lengthy US Bill of Rights.•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-3 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)In the packet-listing window, you should see your HTTP GET message, followed by a multiple-packet response to your HTTP GET request. This multiple-packet response deserves a bit of explanation. Recall from Section 2.2 (see Figure 2.9 in the text) that the HTTP response message consists of a status line, followed by header lines, followed by a blank line, followed by the entity body. In the case of our HTTP GET, the entity body in the response is the entire requested HTML file. In our case here, the HTML file is rather long, and at 4500 bytes is too large to fit in one TCP packet. The single HTTP responsemessage is thus broken into several pieces by TCP, with each piece being contained within a separate TCP segment (see Figure 1.22 in the text). Each TCP segment is recorded as a separate packet by Ethereal, and the fact that the single HTTP response was fragmented across multiple TCP packets is indicated by the “Continuation” phrase displayed by Ethereal. We stress here that there is no “Continuation” message in HTTP! Answer the following questions:12.How many HTTP GET request messages were sent by your browser?13.How many data-containing TCP segments were needed to carry the single HTTPresponse?14.What is the status code and phrase associated with the response to the HTTP GETrequest?15.Are there any HTTP status lines in the transmitted data associated with a TCP-induced “Continuation”?4. HTML Documents with Embedded ObjectsNow that we’ve seen how Ethereal displays the captured packet traffic for large HTML files, we can look at what happens when your browser downloads a file with embedded objects, i.e., a file that includes other objects (in the example below, image files) that are stored on another server(s).Do the following:•Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/HTTP-ethereal-file4Your browser should display a short HTML file with two images. These twoimages are referenced in the base HTML file. That is, the images themselves are not contained in the HTML; instead the URLs for the images are contained in the downloaded HTML file. As discussed in the textbook, your browser will have to retrieve these logos from the indicated web sites. Our publisher’s logo isretrieved from the web site. The image of our book’s cover isstored at the server.•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-4 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)Answer the following questions:16.How many HTTP GET request messages were sent by your browser? To whichInternet addresses were these GET requests sent?17.Can you tell whether your browser downloaded the two images serially, orwhether they were downloaded from the two web sites in parallel? Explain.2.5 HTTP AuthenticationFinally, let’s try visiting a web site that is password-protected and examine the sequence of HTTP message exchanged for such a site. The URL/ethereal-labs/protected_pages/HTTP-ethereal-file5.html is password protected. The username is “eth-students” (without the quotes), and the password is “networks” (again, without the quotes). So let’s access this “secure” password-protected site. Do the following:•Make sure your browser’s cache is cleared, as discussed above, and close down your browser. Then, start up your browser•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/protected_pages/HTTP-ethereal-file5.htmlType the requested user name and password into the pop up box..•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed later in thepacket-listing window.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-5 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)Now let’s examine the Ethereal output. You might want to first read up on HTTP authentication by reviewing the easy-to-read material on “HTTP Access Authentication Framework” at /stories/storyReader$2159Answer the following questions:18.What is the server’s response (status code and phrase) in response to the initialHTTP GET message from your browser?19.When your browser’s sends the HTTP GET message for the second time, whatnew field is included in the HTTP GET message?The username (eth-students) and password (network) that you entered are encoded in the string of characters (ZXRoLXN0dWRlbnRzOm5ldHdvcmtz) following the “Authorization: Basic” header in the client’s HTTP GET message. While it may appear that your username and password are encrypted, they are simply encoded in a format known as Base64 format. The username and password are not encrypted! To see this, go to /tools/base64.php and enter the base64-encoded string ZXRoLXN0dWRlbnRzOm5ldHdvcmtz and press decode. Voila! You have translated from Base64 encoding to ASCII encoding, and thus should see both your username and password! Since anyone can download a tool like Ethereal and sniff packets (not just their own) passing by their network adaptor, and anyone can translatefrom Base64 to ASCII (you just did it!), it should be clear to you that simple passwords on WWW sites are not secure unless additional measures are taken.Fear not! As we will see in Chapter 7, there are ways to make WWW access more secure. However, we’ll clearly need something that goes beyond the basic HTTP authentication framework!。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Ethereal Lab: HTTP Version: 1.1 (Feb. 2005)© 2005 J.F. Kurose, K.W. Ross. All Rights ReservedComputer Networking: A Top-down Approach Featuring the Internet, 3rd edition.Having gotten our feet wet with the Ethereal packet sniffer in the introductory lab, we’re now ready to use Ethereal to investigate protocols in operation. In this lab, we’ll explore several aspects of the HTTP protocol: the basic GET/response interaction, HTTP message formats, retrieving large HTML files, retrieving HTML files with embedded objects, and HTTP authentication and security. Before beginning these labs, you might want to review Section 2.2 of the text.1. The Basic HTTP GET/response interactionLet’s begin our exploration of HTTP by downloading a very simple HTML file - one that is very short, and contains no embedded objects. Do the following:1.Start up your web browser.2.Start up the Ethereal packet sniffer, as described in the Introductory lab (but don’tyet begin packet capture). Enter “http” (just the letters, not the quotation marks)in the display-filter-specification window, so that only captured HTTP messages will be displayed later in the packet-listing window. (We’re only interested in the HTTP protocol here, and don’t want to see the clutter of all captured packets).3.Wait a bit more than one minute (we’ll see why shortly), and then begin Etherealpacket capture.4.Enter the following to your browser/ethereal-labs/HTTP-ethereal-file1.htmlYour browser should display the very simple, one-line HTML file.5.Stop Ethereal packet capture.Your Ethereal window should look similar to the window shown in Figure 1. If you are unable to run Ethereal on a live network connection, you can download a packet trace that was created when the steps above were followed.11 Download the zip file /ethereal-labs/ethereal-traces.zip and extract the file http-ethereal-trace-1. The traces in this zip file were collected by Ethereal running on one of the author’s computers, while performing the steps indicated in the Ethereal lab. Once you have downloaded the trace,Figure 1: Ethereal Display after /ethereal-labs/ HTTP-ethereal-file1.html has been retrieved by your browserThe example in Figure 1 shows in the packet-listing window that two HTTP messages were captured: the GET message (from your browser to the web server) and the response message from the server to your browser. The packet-contents window shows details of the selected message (in this case the HTTP GET message, which is highlighted in the packet-listing window). Recall that since the HTTP message was carried inside a TCP segment, which was carried inside an IP datagram, which was carried within an Ethernet frame, Ethereal displays the Frame, Ethernet, IP, and TCP packet information as well. We want to minimize the amount of non-HTTP data displayed (we’re interested in HTTP here, and will be investigating these other protocols is later labs), so make sure the boxes at the far left of the Frame, Ethernet, IP and TCP information have a right-pointing arrowhead (which means there is hidden, undisplayed you can load it into Ethereal and view the trace using the File pull down menu, choosing Open, and then selecting the http-ethereal-trace-1 trace file. The resulting display should look just like Figure 1.information), and the HTTP line has a down-pointing arrowhead (which means that all information about the HTTP message is displayed).(Note: You should ignore any HTTP GET and response for favicon.ico. If you see a reference to this file, it is your browser automatically asking the server if it (the server) has a small icon filethat should be displayed next to the displayed URL in your browser. We’ll ignore references tothis pesky file in this lab.).By looking at the information in the HTTP GET and response messages, answer the following questions. When answering the following questions, you should print out the GET and response messages (see the introductory Ethereal lab for an explanation of how to do this) and indicate where in the message you’ve found the information that answers the following questions.1.Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is theserver running?2.What languages (if any) does your browser indicate that it can accept to theserver?3.What is the IP address of your computer? Of the server?4.What is the status code returned from the server to your browser?5.When was the HTML file that you are retrieving last modified at the server?6.How many bytes of content are being returned to your browser?7.By inspecting the raw data in the packet content window, do you see any headerswithin the data that are not displayed in the packet-listing window? If so, nameone.In your answer to question 5 above, you might have been surprised to find that the document you just retrieved was last modified within a minute before you downloaded the document. That’s because (for this particular file), the server is setting the file’s last-modified time to be the current time, and is doing so once per minute. Thus, if you wait a minute between accesses, the file will appear to have been recently modified, and hence your browser will download a “new” copy of the document.2. The HTTP CONDITIONAL GET/response interactionRecall from Section 2.2.5 of the text, that most web browsers perform object caching and thus perform a conditional GET when retrieving an HTTP object. Before performing the steps below, make sure your browser’s cache is empty. (To do this under Netscape 7.0, select Edit->Preferences->Advanced->Cache and clear the memory and disk cache.For Internet Explorer, select Tools->Internet Options->Delete File; these actions will remove cached files from your browser’s cache.) Now do the following: •Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/HTTP-ethereal-file2.htmlYour browser should display a very simple five-line HTML file.•Quickly enter the same URL into your browser again (or simply select the refresh button on your browser)•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed later in thepacket-listing window.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-2 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)Answer the following questions:8.Inspect the contents of the first HTTP GET request from your browser to theserver. Do you see an “IF-MODIFIED-SINCE” line in the HTTP GET?9.Inspect the contents of the server response. Did the server explicitly return thecontents of the file? How can you tell?10.Now inspect the contents of the second HTTP GET request from your browser tothe server. Do you see an “IF-MODIFIED-SINCE:” line in the HTTP GET? Ifso, what information follows the “IF-MODIFIED-SINCE:” header?11.What is the HTTP status code and phrase returned from the server in response tothis second HTTP GET? Did the server explicitly return the contents of the file?Explain.3. Retrieving Long DocumentsIn our examples thus far, the documents retrieved have been simple and short HTML files. Let’s next see what happens when we download a long HTML file. Do the following:•Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/HTTP-ethereal-file3.htmlYour browser should display the rather lengthy US Bill of Rights.•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-3 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)In the packet-listing window, you should see your HTTP GET message, followed by a multiple-packet response to your HTTP GET request. This multiple-packet response deserves a bit of explanation. Recall from Section 2.2 (see Figure 2.9 in the text) that the HTTP response message consists of a status line, followed by header lines, followed by a blank line, followed by the entity body. In the case of our HTTP GET, the entity body in the response is the entire requested HTML file. In our case here, the HTML file is rather long, and at 4500 bytes is too large to fit in one TCP packet. The single HTTP responsemessage is thus broken into several pieces by TCP, with each piece being contained within a separate TCP segment (see Figure 1.22 in the text). Each TCP segment is recorded as a separate packet by Ethereal, and the fact that the single HTTP response was fragmented across multiple TCP packets is indicated by the “Continuation” phrase displayed by Ethereal. We stress here that there is no “Continuation” message in HTTP! Answer the following questions:12.How many HTTP GET request messages were sent by your browser?13.How many data-containing TCP segments were needed to carry the single HTTPresponse?14.What is the status code and phrase associated with the response to the HTTP GETrequest?15.Are there any HTTP status lines in the transmitted data associated with a TCP-induced “Continuation”?4. HTML Documents with Embedded ObjectsNow that we’ve seen how Ethereal displays the captured packet traffic for large HTML files, we can look at what happens when your browser downloads a file with embedded objects, i.e., a file that includes other objects (in the example below, image files) that are stored on another server(s).Do the following:•Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/HTTP-ethereal-file4.htmlYour browser should display a short HTML file with two images. These twoimages are referenced in the base HTML file. That is, the images themselves are not contained in the HTML; instead the URLs for the images are contained in the downloaded HTML file. As discussed in the textbook, your browser will have to retrieve these logos from the indicated web sites. Our publisher’s logo isretrieved from the web site. The image of our book’s cover isstored at the server.•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-4 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)Answer the following questions:16.How many HTTP GET request messages were sent by your browser? To whichInternet addresses were these GET requests sent?17.Can you tell whether your browser downloaded the two images serially, orwhether they were downloaded from the two web sites in parallel? Explain.2.5 HTTP AuthenticationFinally, let’s try visiting a web site that is password-protected and examine the sequence of HTTP message exchanged for such a site. The URL/ethereal-labs/protected_pages/HTTP-ethereal-file5.html is password protected. The username is “eth-students” (without the quotes), and the password is “networks” (again, without the quotes). So let’s access this “secure” password-protected site. Do the following:•Make sure your browser’s cache is cleared, as discussed above, and close down your browser. Then, start up your browser•Start up the Ethereal packet sniffer•Enter the following URL into your browser/ethereal-labs/protected_pages/HTTP-ethereal-file5.htmlType the requested user name and password into the pop up box..•Stop Ethereal packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed later in thepacket-listing window.•(Note: If you are unable to run Ethereal on a live network connection, you can use the http-ethereal-trace-5 packet trace to answer the questions below; seefootnote 1. This trace file was gathered while performing the steps above on oneof the author’s computers.)Now let’s examine the Ethereal output. You might want to first read up on HTTP authentication by reviewing the easy-to-read material on “HTTP Access Authentication Framework” at /stories/storyReader$2159Answer the following questions:18.What is the server’s response (status code and phrase) in response to the initialHTTP GET message from your browser?19.When your browser’s sends the HTTP GET message for the second time, whatnew field is included in the HTTP GET message?The username (eth-students) and password (network) that you entered are encoded in the string of characters (ZXRoLXN0dWRlbnRzOm5ldHdvcmtz) following the “Authorization: Basic” header in the client’s HTTP GET message. While it may appear that your username and password are encrypted, they are simply encoded in a format known as Base64 format. The username and password are not encrypted! To see this, go to /tools/base64.php and enter the base64-encoded string ZXRoLXN0dWRlbnRzOm5ldHdvcmtz and press decode. Voila! You have translated from Base64 encoding to ASCII encoding, and thus should see both your username and password! Since anyone can download a tool like Ethereal and sniff packets (not just their own) passing by their network adaptor, and anyone can translatefrom Base64 to ASCII (you just did it!), it should be clear to you that simple passwords on WWW sites are not secure unless additional measures are taken.Fear not! As we will see in Chapter 7, there are ways to make WWW access more secure. However, we’ll clearly need something that goes beyond the basic HTTP authentication framework!。
