密码学与网络安全【英文】
密码学与网络安全课程摘要

第1章引言1、计算机安全、网络安全、internet安全。
1)计算机安全:用来保护数据和阻止黑客的工具一般称为计算机安全。
2)网络安全:在信息传输时,用来保护数据传输的网络安全措施称为网络安全。
3)internet安全:在使用公有网络进行数据传的时用来保护数据传输的网络安全措施。
2、O SI安全框架包括哪些主要内容。
OSI定义了一种系统化的方法,对安全人员来说,OSI安全框架是提供安全的一种组织方法。
安全框架对许多概念提供了一些有用或许抽象的概貌,OSI安全框架主要关注安全攻击、机制和服务。
可以简短定义如下:1)安全性攻击:任何危及企业信息系统安全的活动。
2)安全机制:用来检测、阻止攻击或者从攻击状态恢复到正常状态的过程,或实现该过程的设备。
3)安全服务:加强数据处理系统和信息传输的安全性的一种处理过程或通信服务。
其目的在于利用一种或多种安全机制进行反击攻击。
3、安全攻击的两种类型:主动攻击和被动攻击。
1)被动攻击:被动攻击的特性是对传输进行窃听和监测,目标是获得传输的信息。
主要有消息内容泄漏和流量分析(通过对传输消息的频率和长度来判断通信的性质),对于被动攻击的处理重点是预防而不是检测。
2)主动攻击:主动攻击包括对数据流进行修改或伪造数据流,分为四类:伪装、重放、消息修改和拒绝服务。
主动攻击难以预防,但容易检测,所以重点是怎样从破坏或造成的延迟中恢复过来。
4、X.800安全服务。
1)认证:同等实体认证和数据源认证。
2)访问控制:阻止对资源的非授权使用。
3)数据保密性:连接保密性、无连接保密性、选择域保密性、流量保密性。
4)数据完整性:保证收到的数据的确是授权实体所发出的数据。
5)不可否认性:源不可否认性和宿不可否认性。
5、X.800安全机制。
1)特定安全机制:加密、数字签名、访问控制、数据完整性、认证交换、流量填充、路由控制、公证。
2)普遍的安全机制:可信功能、安全标签、事件检测、安全审计跟踪、安全恢复。
《密码编码学与网络安全》复习题-朱铁英2006-4-16

《密码编码学与网络安全》复习题-朱铁英2006-4-16 《计算机安全与密码学》复习题1( 信息安全(计算机安全)目标是什么,答:机密性(confidentiality):防止未经授权的信息泄漏完整性(integrity):防止未经授权的信息篡改可用性(avialbility):防止未经授权的信息和资源截留抗抵赖性、不可否认性、问责性、可说明性、可审查性(accountability): 真实性(authenticity):验证用户身份2( 理解计算安全性(即one-time pad的理论安全性)使用与消息一样长且无重复的随机密钥来加密信息,即对每个明文每次采用不同的代换表不可攻破,因为任何明文和任何密文间的映射都是随机的,密钥只使用一次3( 列出并简要定义基于攻击者所知道信息的密码分析攻击类型。
(1)、唯密文分析(攻击),密码分析者取得一个或多个用同一密钥加密的密文;(2)、已知明文分析(攻击),除要破译的密文外,密码分析者还取得一些用同一密钥加密的密文对;(3)、选择明文分析(攻击),密码分析者可取得他所选择的任何明文所对应的密文(不包括他要恢复的明文),这些密文对和要破译的密文是用同一密钥加密的;(4)、选择密文分析(攻击),密码分析者可取得他所选择的任何密文所对应的明文(要破译的密文除外),这些密文和明文和要破译的密文是用同一解密密钥解密的,它主要应用于公钥密码体制。
4( 传统密码算法的两种基本运算是什么,代换和置换前者是将明文中的每个元素映射成另外一个元素;后者是将明文中的元素重新排列。
5( 流密码和分组密码区别是什么,各有什么优缺点,分组密码每次处理一个输入分组,对应输出一个分组;流密码是连续地处理输入元素,每次输出一个元素流密码Stream: 每次加密数据流的一位或者一个字节。
连续处理输入分组,一次输出一个元素,速度较快6( 已知密文ILPQPUN使用的是移位密码,试解密(提示:明文为有意义的英文)。
信息安全专业英语

信息安全工程师 /rk/safe/index.html信息安全专业英语1、cryptography:密码;plaintext 明文;ciphertext 密文;concealment 隐藏;cryptology 密码学;2、symmetric‐key 对称密钥;Symmetric‐key cryptography refers to encryption methods in which both the sender and receivershare the same key(or,less commonly,in which their keys are different,but related in an easily computable way).对称密钥加密是指加密方法,在该方法中,发送者和接收者共享相同的密钥3、asymmetric key 非对称密钥;Digita1 signatures 数字签名RSA and DSA are two of the most popular digital signature schemes4、elliptic curve cryptography 椭圆曲线密码5、Cryptanalysis 密码分析;quantum computer 量子计算机;6、Antivirus software 杀毒软件Network-attached storage (NAS,网络附加存储): is file-level computer data storage connected to a computer network providing data access to heterogeneous network clients.7、Penetration Testing Tools 渗透测试工具。
网络安全英语

网络安全英语网络安全(Network Security) 是指保护互联网、计算机网络和系统,免受未经授权的访问、破坏、窃取或修改的一系列措施和技术。
它的目标是确保信息和数据的机密性、完整性和可用性。
在网络安全中,有一些关键术语和概念需要理解。
其中之一是防火墙(Firewall),它是一种位于网络与外部世界之间的设备或软件。
防火墙可以监视和控制网络流量,阻止未经授权的访问和攻击。
例如,防火墙可以禁止某个IP地址或特定的网络端口与内部网络通信。
此外,入侵检测系统(Intrusion Detection System, IDS) 也是网络安全中重要的组成部分。
IDS 可以检测到可能是入侵者的行为,例如非法访问、篡改数据或破坏系统。
一旦IDS发现异常活动,它会发出警报,并触发相应的响应措施以保护系统。
密码学(Cryptography) 是网络安全的核心理论和技术,它用于保护数据的机密性和完整性。
密码学包括加密和解密算法,用于将数据转化为不可读的形式,从而只有具备相应密钥的人可以解密。
网络安全还涉及到恶意软件(Malware),包括病毒(Virus)、蠕虫(Worm)和木马(Trojan horse)等。
这些恶意软件可以入侵系统、盗取敏感信息或破坏计算机的正常运行。
为了应对这些威胁,就需要使用反病毒软件(Antivirus software)、反恶意软件软件(Antimalware software)和安全补丁(Security patches) 来保护系统和网络免受恶意软件的攻击。
网络安全是一个日益重要的领域,随着技术的不断发展,网络安全威胁也在不断增加。
因此,我们应该关注并采取适当的措施来保护我们的个人信息和网络安全。
密码学与网络安全-附录F

Joint Entropy
When we have two probability sample spaces, S1 and S2, we can define the joint entropy H(S1, S2) as
H(S1, S2) =
ΣΣ P (x, y) × [log2 1/P (x, y)]
Hmin(S) = 0 bits
In other words, the entropy of every probability sample space has a lower limit defined by the above formula.
The entropy of a probability sample space is between 0 bits and log2 n bits, where n is the number of possible outcomes.
The above two examples show that there is a relationship between the usefulness of an event and the expectation of the receiver. If the receiver is surprised when the event happens, the message contains a lot of information; otherwise, it does not. In other words, the information content of a message is inversely related to the probability of the occurrence of that message. If the event is very probable, it does not contain any information (Example F.1); if it is very improbable, it contains a lot of information (Example F.2).
英汉网络安全词典

英汉网络安全词典英汉网络安全词典1. antivirus software / 杀毒软件Antivirus software, also known as anti-malware software, is a program designed to detect, prevent and remove malicious software from a computer or network.2. firewall / 防火墙A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on predetermined security rules. It helps protect a computer or network from unauthorized access and potential threats.3. encryption / 加密Encryption is the process of converting plain text or data into an unreadable format using an algorithm and a key. It helps protect sensitive information and ensures secure communication.4. phishing / 钓鱼Phishing is a fraudulent practice where cybercriminals try to trick individuals into revealing sensitive information, such as passwords or credit card numbers, by pretending to be a legitimate entity.5. malware / 恶意软件Malware, short for malicious software, is any software designed to cause damage, disrupt operations, or gain unauthorized access to a computer or network. Common types of malware include viruses, worms, trojans, and ransomware.6. vulnerability / 漏洞A vulnerability is a weakness or flaw in a computer system or network that can be exploited by attackers. It can result in unauthorized access, data breaches, or system disruptions.7. authentication / 身份验证Authentication is the process of verifying the identity of an individual or device accessing a computer system or network. It can involve passwords, biometrics, or other means to ensure the authorized user's identity.8. intrusion detection system (IDS) / 入侵检测系统An intrusion detection system is a network security technology that monitors network traffic for malicious activity or unauthorized access. It alerts administrators or automatically takes action to prevent further damage.9. encryption key / 加密密钥An encryption key is a piece of information used in encryption algorithms to convert plain text into cipher text or vice versa. The key is necessary to decrypt the encrypted data and ensure secure communication.10. cybersecurity / 网络安全Cybersecurity refers to the practice of protecting computer systems, networks, and data from unauthorized access, damage, or theft. It involves implementing measures to prevent, detect, and respond to cyber threats.11. two-factor authentication (2FA) / 双因素身份验证Two-factor authentication is a security process that requires two different forms of identification before granting access to a computer system or network. It typically involves something the user knows (password) and something the user possesses (security token or mobile device).12. data breach / 数据泄露A data breach is an incident where unauthorized individuals gain access to protected or sensitive data without permission. It can result in the exposure or theft of personal information, financial records, or other confidential data.13. cyber attack / 网络攻击A cyber attack is an intentional act to compromise computer systems, networks, or devices by exploiting vulnerabilities. It can involve stealing sensitive data, disrupting operations, or causing damage to digital infrastructure.14. vulnerability assessment / 漏洞评估A vulnerability assessment is the process of identifying and evaluating vulnerabilities in a computer system, network, or application. It helps organizations understand their security weaknesses and take appropriate measures to mitigate risks.15. secure socket layer (SSL) / 安全套接字层Secure Socket Layer is a cryptographic protocol that ensures secure communication over a computer network. It provides encryption, authentication, and integrity, making it widely used for securing online transactions and data transfer.以上是英汉网络安全词典的部分词汇,以供参考。
信息安全基础2(密码编码学与网络安全)

The Phaistos (1700 BC)
Encryption Machines in Early 20th Century
History of Cryptography (cont‘ d)
1949~1976 – Shannon published ―The Communication Theory of Secret Systems‖ in 1949, which indicated cryptography became a formal subject. The development of computer enabled ciphers on complex computing. The security of data is based on the secrecy of secret key instead of cipher algorithm.
– Classical Encryption古典加密 Before computer was invented, cryptography was art more than science. There were some cipher algorithms, encryption machines & simple cryptanalysis密 码分析 ways. The main encryption objects are alphabet character. The security of data is based on the secrecy of algorithms.
Symmetric Cipher Ke=Kd Asymmetric Cipher Ke≠Kd Ke Kd So, make Ke public, keep Kd secret
网络信息安全-密码学基本概念
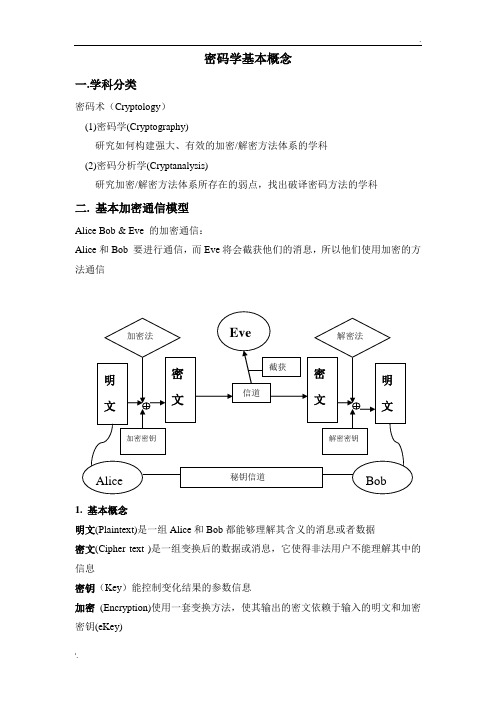
密码学基本概念一.学科分类密码术(Cryptology)(1)密码学(Cryptography)研究如何构建强大、有效的加密/解密方法体系的学科(2)密码分析学(Cryptanalysis)研究加密/解密方法体系所存在的弱点,找出破译密码方法的学科二. 基本加密通信模型Alice Bob & Eve 的加密通信:Alice和Bob 要进行通信,而Eve将会截获他们的消息,所以他们使用加密的方法通信1. 基本概念明文(Plaintext)是一组Alice和Bob都能够理解其含义的消息或者数据密文(Cipher text )是一组变换后的数据或消息,它使得非法用户不能理解其中的信息密钥(Key)能控制变化结果的参数信息加密(Encryption)使用一套变换方法,使其输出的密文依赖于输入的明文和加密密钥(eKey)解密(Decryption)使用一套变换方法,使其输出的明文依赖于输入的密文和解密密钥(dKey)用符号表示加密:Cipher text = Encryption (Plaintext, eKey)解密:Plaintext = Decryption (Cipher text, dKey)2. 体系划分以加密密钥和解密密钥的关系来划分为体系:1。
如果加密密钥(eKey)和解密密钥(dKey)相同,或者实质上相同,这样的加密体系称为单钥或对称密钥体系2。
如果加密密钥(eKey)和解密密钥(dKey)不相同,或者很难从其中一个密钥推导出另一个密钥,这样的加密体系称为双钥或非对称密钥体系三. 实例1 对称密钥在经典加密方法中使用两种类型进行变换:(1)换位法(Permutation cipher / Transposition cipher):明文中的每个字母或符号没有改变,但它们在密文中的位置进行了重新排列。
经典换位加密法(2)替换法(Substitution cipher):将明文中每个字母、数字、符号按一定规则替换成另外一个符号。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Private-Key Cryptography
traditional
private/secret/single key cryptography uses one key shared by both sender and receiver if this key is disclosed communications are compromised also is symmetric, parties are equal hence does not protect sender from receiver forging a message & claiming is sent by sender
Public-Key Cryptosystems
Public-Key Applications
can
classify uses into 3 categories:
encryption/decryption (provide secrecy) digital signatures (provide authentication) key exchange (of session keys)
some
algorithms are suitable for all uses, others are specific to one
Why Public-Key Cryptography?
developed
to address two key issues:
key distribution – how to have secure communications in general without having to trust a KDC with your key digital signatures – how to verify a message comes intact from the claimed sender
is asymmetric because
Public-Key Cryptography
Public-Key Characteristics
Public-Key algorithms rely on two keys where:
it is computationally infeasible to find decryption key knowing only algorithm & encryption key it is computationally easy to en/decrypt messages when the relevant (en/decrypt) key is known either of the two related keys can be used for encryption, with the other used for decryption (for some algorithms)
Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true or great name appears to have been carefully concealed. —The Golden Bough, Sir James George Frazer
a public-key, which may be known by anybody, and can be used to encrypt messages, and verify signatures a private-key, known only to the recipient, used to decrypt messages, and sign (create) signatures those who encrypt messages or verify signatures cannot decrypt messages or create signatures
public
invention due to Whitfield Diffie & Martin Hellman at Stanford Uni in 1976
known earlier in classified community
Public-Key Cryptography
public-key/two-key/asymmetric cryptography involves the use of two keys:
Cryptography and Network Security Chapter 9
Fourth Edition by William Stallings Lecture slides by Lawrie Brown
Chapter 9 – Public Key yptography
probably
most significant advance in the 3000 year history of cryptography uses two keys – a public & a private key asymmetric since parties are not equal uses clever application of number theoretic concepts to function complements rather than replaces private key crypto
