华为防火墙USG配置
华为USG防火墙和H3C三层交换机设备组网配置简述
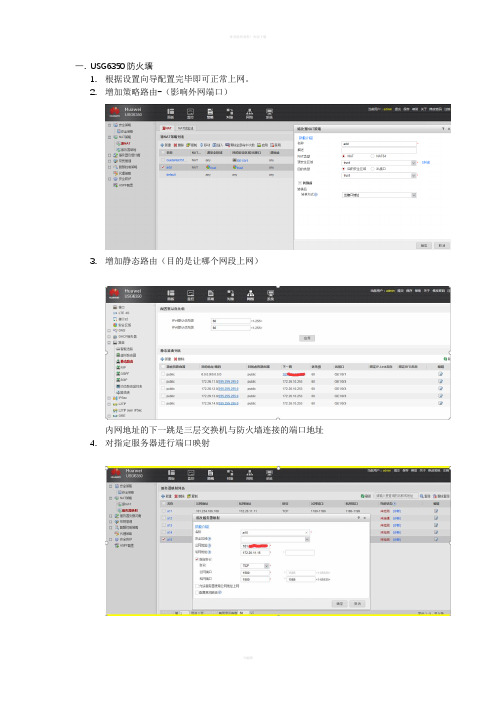
一.USG6350防火墙1.根据设置向导配置完毕即可正常上网。
2.增加策略路由-(影响外网端口)3.增加静态路由(目的是让哪个网段上网)内网地址的下一跳是三层交换机与防火墙连接的端口地址4.对指定服务器进行端口映射5.对指定网段进行限速,保证服务器有可靠的带宽,不至于被其他网段抢占全部带宽。
本项目全部带宽是100M,因为有一个无线网,限定无线网最大占用50M(1)新建一个带宽通道(2)指定网段应用于带宽通道的策略规则二、三层交换机-H3C-S5800-32C现场需求是有办公电脑,服务器、视频服务器,计划分成4个网段,分别为172.26.11.0/172.26.12.0/172.26.13.0/172.26.14.0/ 14段备用。
规划:VLAN100为172.26.10.253 port1-2 与防火墙172.26.10.254 连接VLAN101为172.26.11.254 port 3-8 与服务器连接VLAN102为 172.26.12.254 port 9-12 与客户机连接VLAN103为 172.26.13.254 port 13-18 与视频服务器连接VLAN104为 172.26.14.254 port 19-24 备用1.笔记本连接三层交换机配置口,进入命令行配置模式简述步骤:(1)设备改名创建用户和密码(2)创建VLAN,指定某端口属于这个VLAN (3)指定每个VLAN的网关(4)增加一条路由2.SysSysname H3C-5800telnet server enableLocal-user adminPassword cipher #####(此处#是输入密码)Authorization-attribute level 3Service-type ssh telnetVLAN 100Port G1/0/1 TO G1/0/2QuitVlan 101Port g1/0/3 to g1/0/8QuitVLAN 102Port G1/0/9 TO G1/0/12QuitVlan 103Port g1/0/13 to g1/0/18QuitVlan 104Port g1/0/19 to g1/0/24QuitInterface Vlan-interface 100Ip address 172.26.10.253 255.255.255.0QuitInterface Vlan-interface 101Ip address 172.26.11.254 255.255.255.0QuitInterface Vlan-interface 102Ip address 172.26.12.254 255.255.255.0QuitInterface Vlan-interface 103Ip address 172.26.13.254 255.255.255.0QuitInterface Vlan-interface 104Ip address 172.26.14.254 255.255.255.0QuitIp route-static 0.0.0.0 0.0.0.0 172.26.10.254 Dhcp enable(开通dhcp)Dhcp server ip-pool 9Network 172.26.12.0 mask 255.255.255.0Gateway-list 172.26.12.254Dns-list 8.8.8.8(根据实际修改)Quit红色字体为9口开通DHCP,可根据实际需求User-interface aux 0User-interface vty 0 4 Authentication-mode scheme User-interface vty 5 15.。
华为USG2100 防火墙配置文档-配置基础

文档版本 01 (2009-12-25)
华为专有和保密信息
i
Secoway USG2100 配置指通过 Console 口搭建本地配置环境......................................................................................................1-4 图 1-2 新建连接 ................................................................................................................................................1-5 图 1-3 选择实际连接使用的微机串口.............................................................................................................1-5 图 1-4 端口通信参数配置.................................................................................................................................1-6 图 1-5 选择终端仿真类型.................................................................................................................................1-7 图 1-6 通过局域网搭建本地配置环境.............................................................................................................1-8 图 1-7 运行 Telnet 程序.....................................................................................................................................1-8 图 1-8 通过广域网搭建远程配置环境.............................................................................................................1-9 图 1-9 运行 Telnet 程序...................................................................................................................................1-10 图 1-10 系统维护相关视图关系.....................................................................................................................1-13 图 1-11 网络互连相关视图关系.....................................................................................................................1-15 图 1-12 AAA 认证相关视图关系 ....................................................................................................................1-17 图 1-13 安全相关视图关系.............................................................................................................................1-20 图 1-14 VPN/QoS 相关视图关系 ....................................................................................................................1-23 图 1-15 实现 ping 通 USG2100(WAN 口)的组网.....................................................................................1-32 图 1-16 实现 ping 通 USG2100(LAN 口)的组网......................................................................................1-35 图 1-17 实现跨越 USG2100 的两个设备互相 ping 通的组网......................................................................1-36
华为USG防火墙IPsec怎么配置

华为USG防火墙IPsec怎么配置华为的产品主要涉及通信网络中的交换网络、传输网络、无线及有线固定接入网络和数据通信网络及无线终端产品,那么你知道华为USG防火墙IPsec 怎么配置吗?下面是店铺整理的一些关于华为USG 防火墙 IPsec 怎么配置的相关资料,供你参考。
华为USG防火墙 IPsec 配置的案例实验拓扑使用华为ensp 1.2.00.370模拟器来完成。
连接方式是client1 - USG-1 - AR1 - USG-2 - clent2 链式组网结构。
实验需求USG-1和USG-2模拟企业边缘设备,分别在2台设备上配置NAT 和IPsec 实现2边私网可以通过互相通信。
实验配置R1的IP地址配置省略USG-1配置[USG-1]firewall zone trust //配置trust区域[USG-1-zone-trust]add interface g0/0/0 //将接口加入trust区域[USG-1-zone-trust]quit[USG-1]firewall zone untrust //配置untrust区域[USG-1-zone-untrust]add int g0/0/1 //将接口加入untrust区域[USG-1-zone-untrust]quit[USG-1]int g0/0/0[USG-1-GigabitEthernet0/0/0]ip add 192.168.10.1 24[USG-1-GigabitEthernet0/0/0]int g0/0/1[USG-1-GigabitEthernet0/0/1]ip add 11.0.0.2 24[USG-1-GigabitEthernet0/0/1]quit[USG-1]ip route-static 0.0.0.0 0.0.0.0 11.0.0.1 //配置默认路由上公网[USG-1]nat-policy interzone trust untrust outbound//进入trust到untrust区域out方向的策略视图[USG-1-nat-policy-interzone-trust-untrust-outbound]policy 1 //创建一个策略[USG-1-nat-policy-interzone-trust-untrust-outbound-1]policy source 192.168.10.0 0.0.0.255[USG-1-nat-policy-interzone-trust-untrust-outbound-1]policy destination 192.168.20.0 0.0.0.255[USG-1-nat-policy-interzone-trust-untrust-outbound-1]action no-nat//以上三条命令意思是不允许将源为192.168.10.0/24网段目标为192.168.20.0/24网段的数据包进行NAT[USG-1-nat-policy-interzone-trust-untrust-outbound-1]quit [USG-1-nat-policy-interzone-trust-untrust-outbound]policy 2 //创建策略2[USG-1-nat-policy-interzone-trust-untrust-outbound-2]action source-nat//允许对源IP进行NAT[USG-1-nat-policy-interzone-trust-untrust-outbound-2]easy-ip g0/0/1//对接口G0/0/1地址复用[USG-1-nat-policy-interzone-trust-untrust-outbound-2]quit [USG-1-nat-policy-interzone-trust-untrust-outbound]quit-------阶段一---------[USG-1]ike proposal 1 //配置一个安全提议[USG-1-ike-proposal-1]authentication-method pre-share //配置IKE认证方式为预共享密钥[USG-1-ike-proposal-1]authentication-algorithm sha1 //配置IKE认证算法为sha1[USG-1-ike-proposal-1]integrity-algorithm aes-xcbc-96 //配置IKE完整性算法[USG-1-ike-proposal-1]dh group2 //配置IKE密钥协商DH组[USG-1-ike-proposal-1]quit[USG-1]ike peer USG-2 //创建一个IKE对等体名字为USG-2[USG-1-ike-peer-usg-2]pre-shared-key abc123 //配置预共享密钥[USG-1-ike-peer-usg-2]remote-address 12.0.0.2 //配置对等体IP地址[USG-1-ike-peer-usg-2]ike-proposal 1 //调用ike安全提议[USG-1-ike-peer-usg-2]quit----------阶段二----------[USG-1]ipsec proposal test //配置一个ipsec安全提议[USG-1-ipsec-proposal-test]encapsulation-mode tunnel //封装方式采用隧道[USG-1-ipsec-proposal-test]transform esp //配置IPSEC安全协议为ESP[USG-1-ipsec-proposal-test]esp encryption-algorithm aes //配置ESP协议加密算法为aes[USG-1-ipsec-proposal-test]esp authentication-algorithm sha1 //配置ESP协议认证算法[USG-1-ipsec-proposal-test]quit[USG-1]acl 3000 //创建一个ACL定义感兴趣流[USG-1-acl-adv-3000]rule permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255[USG-1]ipsec policy map 1 isakmp //创建一个安全策略,名称为map[USG-1-ipsec-policy-isakmp-map-1]ike-peer USG-2 //调用ike对等体[USG-1-ipsec-policy-isakmp-map-1]proposal test //调用IPsec安全提议[USG-1-ipsec-policy-isakmp-map-1]security acl 3000 //配置感兴趣流[USG-1-ipsec-policy-isakmp-map-1]quit[USG-1]int g0/0/1[USG-1-GigabitEthernet0/0/1]ipsec policy map //在外网口上调用安全策略区域间策略配置[USG-1]policy interzone trust untrust outbound .//进入trust到untrust区域out方向策略视图[USG-1-policy-interzone-trust-untrust-outbound]policy 1 //创建策略[USG-1-policy-interzone-trust-untrust-outbound-1]action permit//允许trust区域所有主机访问untrust区域[USG-1-policy-interzone-trust-untrust-outbound-1]quit[USG-1-policy-interzone-trust-untrust-outbound]quit[USG-1]policy interzone trust untrust inbound//进入trust区域到untrust区域的in方向策略视图[USG-1-policy-interzone-trust-untrust-inbound]policy 1[USG-1-policy-interzone-trust-untrust-inbound-1]policy source 192.168.20.0 0.0.0.255[USG-1-policy-interzone-trust-untrust-inbound-1]policy destination 192.168.10.0 0.0.0.255[USG-1-policy-interzone-trust-untrust-inbound-1]action permit//以上命令为允许数据包源地址为192.168.20.0/24网段和目标地址为192.168.10.0/24网段的流量过[USG-1-policy-interzone-trust-untrust-inbound-1]quit[USG-1-policy-interzone-trust-untrust-inbound]quit[USG-1]policy interzone local untrust inbound//进入local区域到untrust区域的in方向策略视图[USG-1-policy-interzone-local-untrust-inbound]policy 1[USG-1-policy-interzone-local-untrust-inbound-1]policy service service-set esp[USG-1-policy-interzone-local-untrust-inbound-1]policy source 12.0.0.2 0[USG-1-policy-interzone-local-untrust-inbound-1]policy destination 11.0.0.2 0[USG-1-policy-interzone-local-untrust-inbound-1]action permit//允许源地址是12.0.0.2目标地址是11.0.0.2的数据包访问esp 协议USG-2配置[USG-2]firewall zone trust[USG-2-zone-trust]add int g0/0/0[USG-2-zone-trust]quit[USG-2]firewall zone untrust[USG-2-zone-untrust]add int g0/0/1[USG-2-zone-untrust]quit[USG-2]int g0/0/0[USG-2-GigabitEthernet0/0/0]ip add 192.168.20.1 24[USG-2-GigabitEthernet0/0/0]int g0/0/1[USG-2-GigabitEthernet0/0/1]ip add 12.0.0.2 24[USG-2-GigabitEthernet0/0/1]quit[USG-2]ip route-static 0.0.0.0 0.0.0.0 12.0.0.1[USG-2]nat-policy interzone trust untrust outbound[USG-2-nat-policy-interzone-trust-untrust-outbound]policy 1[USG-2-nat-policy-interzone-trust-untrust-outbound-1]policy source 192.168.20.0 0.0.0.255[USG-2-nat-policy-interzone-trust-untrust-outbound-1]policy destination 192.168.10.0 0.0.0.255[USG-2-nat-policy-interzone-trust-untrust-outbound-1]action no-nat[USG-2-nat-policy-interzone-trust-untrust-outbound-1]quit [USG-2-nat-policy-interzone-trust-untrust-outbound]policy 2[USG-2-nat-policy-interzone-trust-untrust-outbound-2]action source-nat[USG-2-nat-policy-interzone-trust-untrust-outbound-2]easy-ip GigabitEthernet0/0/1[USG-2-nat-policy-interzone-trust-untrust-outbound-2]quit [USG-2-nat-policy-interzone-trust-untrust-outbound]quit[USG-2]ike proposal 1[USG-2-ike-proposal-1]authentication-method pre-share[USG-2-ike-proposal-1]authentication-algorithm sha1[USG-2-ike-proposal-1]integrity-algorithm aes-xcbc-96[USG-2-ike-proposal-1]dh group2[USG-2-ike-proposal-1]quit[USG-2]ike peer USG-A[USG-2-ike-peer-usg-a]pre-shared-key abc123[USG-2-ike-peer-usg-a]ike-proposal 1[USG-2-ike-peer-usg-a]remote-address 11.0.0.2[USG-2-ike-peer-usg-a]quit[USG-2]ipsec proposal test[USG-2-ipsec-proposal-test]encapsulation-mode tunnel[USG-2-ipsec-proposal-test]transform esp[USG-2-ipsec-proposal-test]esp encryption-algorithm aes[USG-2-ipsec-proposal-test]esp authentication-algorithmsha1[USG-2-ipsec-proposal-test]quit[USG-2]acl 3000[USG-2-acl-adv-3000]rule permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255[USG-2-acl-adv-3000]quit[USG-2]ipsec policy map 1 isakmp[USG-2-ipsec-policy-isakmp-map-1]ike-peer USG-A[USG-2-ipsec-policy-isakmp-map-1]proposal test[USG-2-ipsec-policy-isakmp-map-1]security acl 3000[USG-2-ipsec-policy-isakmp-map-1]quit[USG-2]int g0/0/1[USG-2-GigabitEthernet0/0/1]ipsec policy map[USG-2-GigabitEthernet0/0/1]quit[USG-2]policy interzone trust untrust outbound[USG-2-policy-interzone-trust-untrust-outbound]policy 1[USG-2-policy-interzone-trust-untrust-outbound-1]action permit[USG-2-policy-interzone-trust-untrust-outbound-1]quit[USG-2-policy-interzone-trust-untrust-outbound]quit[USG-2]policy interzone trust untrust inbound[USG-2-policy-interzone-trust-untrust-inbound]policy 1[USG-2-policy-interzone-trust-untrust-inbound-1]policy source 192.168.10.0 0.0.0.255[USG-2-policy-interzone-trust-untrust-inbound-1]policy destination 192.168.20.0 0.0.0.255[USG-2-policy-interzone-trust-untrust-inbound-1]action permit[USG-2-policy-interzone-trust-untrust-inbound-1]quit[USG-2-policy-interzone-trust-untrust-inbound]quit[USG-2]policy interzone local untrust inbound[USG-2-policy-interzone-local-untrust-inbound]policy 1 [USG-2-policy-interzone-local-untrust-inbound-1]policy source 11.0.0.2 0[USG-2-policy-interzone-local-untrust-inbound-1]policy destination 12.0.0.2 0[USG-2-policy-interzone-local-untrust-inbound-1]policy service service-set esp[USG-2-policy-interzone-local-untrust-inbound-1]action permit使用C1(192.168.10.10)去ping C2(192.168.20.10)使用dispaly ike sa和display ipsec sa来查看邻居建立情况。
华为USG6000防火墙WEB基本开局配置

华为USG6000防火墙WEB基本开局配置
方法/步骤
第一步:浏览器登录https://192.168.0.1 (缺省状态下WEB登录地址),进入防火墙WEB配置界面。
第二步:输入用户名和密码登录,用户名:admin 密码:Admin@123(缺省状态下)。
第三步:进入快速向导,根据指引进行配置,然后点击【下一步】。
第四步:配置基本信息。
(建议修改密码),然后点击【下一步】。
第五步:配置系统时间。
(建议从本地系统同步时间,如果有NTP服务器选择NTP服务器同步时间),然后点击【下一步】。
第六步:选择接入互联网的方式。
(以PPPoE拨号为例),然后点击【下一步】。
第七步:配置拨号信息。
(上网接口是连接运营商的接口,用户名密码由运营商提供,选自动获取IP),然后点击【下一步】。
第八步:配置局域网接口。
(给连接下面设备或终端的接口配置IP),然后点击【下一步】。
第九步:配置局域网DHCP服务,(起始IP要排除上一步配置的接口IP)然后点击【下一步】。
第十步:确认配置信息,点击【应用】完成配置。
END
注意事项
①、用户名密码登录错误次数过多会锁定10分钟不能登录。
②、最后点击应用的时候提示接口地址池不能超过某个数,需要计算在范围内的IP和掩码,计算方式请找度娘【IP在线计算】。
华为USG 系列防火墙性能参数表
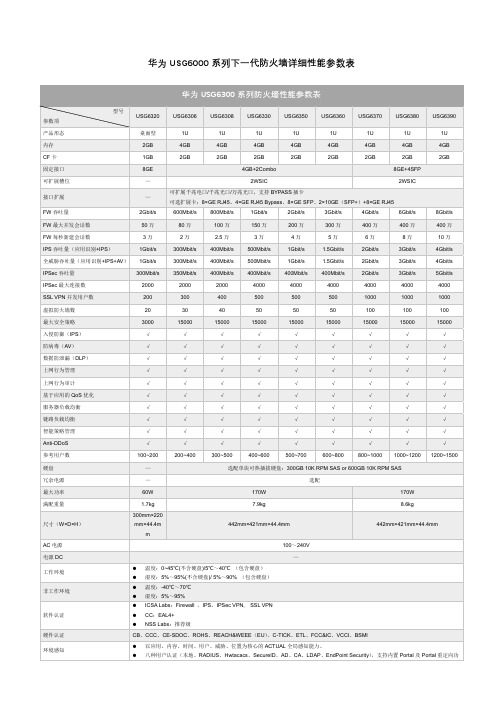
华为USG6000系列下一代防火墙详细性能参数表能,与Agile Controller配合可以实现微信认证。
应用安全●6000+应用协议识别、识别粒度细化到具体动作,自定义协议类型,可与阻断、限流、审计、统计等多种手段自由结合在线协议库升级。
注:USG6320可识别1600+应用。
●应用识别与病毒扫描结合,发现隐藏于应用中的病毒,木马和恶意软件,可检出超过500多万种病毒。
●应用识别与内容检测结合,发现应用中的文件类型和敏感信息,防范敏感信息泄露。
入侵防御●基于特征检测,支持超过3500漏洞特征的攻击检测和防御。
●基于协议检测,支持协议自识别,基于协议异常检测。
●支持自定义IPS签名。
APT防御与沙箱联动,对恶意文件进行检测和阻断。
Web安全●基于云的URL分类过滤,支持8500万URL库,80+分类。
●提供专业的安全URL分类,包括钓鱼网站库分类和恶意URL库分类。
●基于Web的防攻击支持,如跨站脚本攻击、SQL注入攻击。
●提供URL关键字过滤,和URL黑白名单。
邮件安全●实时反垃圾邮件功能,在线检测,防范钓鱼邮件。
●本地黑、白名单,远程实时黑名单、内容过滤、关键字过滤、附件类型、大小、数量。
●支持对邮件附件进行病毒检查和安全性提醒。
数据安全●基于内容感知数据防泄露,对邮件,HTTP,FTP,IM、SNS等传输的文件和文本内容进行识别过滤。
●20+文件还原和内容过滤,如Word、Excel、PPT、PDF等),60+文件类型过滤。
安全虚拟化安全全特性虚拟化,转发虚拟化、用户虚拟化、管理虚拟化、视图虚拟化、资源虚拟化(带宽、会话等)。
网络安全●DDoS攻击防护,防范多种类型DDoS攻击,如SYN flood、UDP flood、ICMP flood、HTTP flood、DNS flood、ARP flood和ARP欺骗等。
●丰富的VPN特性,IPSec VPN、SSL VPN、L2TP VPN、MPLS VPN、GRE等。
华为USG5500防火墙配置实验一

华为USG5500防火墙配置实验1、实验拓扑内网:192.168.0.0/24外网:192.168.1.0/24其他设备地址规划如图,按照拓扑图搭建网络,并配置设备地址2、具体配置命令AR1<Huawei>system-view[Huawei]sysname AR1[AR1]interface g0/0/0[AR1-GigabitEthernet0/0/0]ip address 192.168.0.150 24[AR1-GigabitEthernet0/0/0]quit 退出[AR1]ip route-static 0.0.0.0 0.0.0.0 192.168.0.1 配置默认路由AR1开启Telnet服务[AR1]user-interface vty 0 4 开启远程线程[AR1-ui-vty0-4]au[AR1-ui-vty0-4]authentication-mode password 认证方式为password Please configure the login password (maximum length 16):888 登录密码 [AR1-ui-vty0-4]user privilege level 3 设置用户等级[AR1-ui-vty0-4]AR2<Huawei>system-view[Huawei]sysname AR2[AR2]interface g0/0/0[AR2-GigabitEthernet0/0/0]ip add[AR2-GigabitEthernet0/0/0]ip address 192.168.1.150 24[AR2-GigabitEthernet0/0/0]q[AR1]ip route-static 0.0.0.0 0.0.0.0 192.168.1.1AR2配置TelnetAR2]us[AR2]user-interface v[AR2]user-interface vty 0 4[AR2-ui-vty0-4]au[AR2-ui-vty0-4]authentication-mode p[AR2-ui-vty0-4]authentication-mode passwordPlease configure the login password (maximum length 16):666 或者[AR2-ui-vty0-4]set authentication password cipher 666[AR2-ui-vty0-4]user privilege level 3[AR2-ui-vty0-4]q防火墙配置:The device is running!<SRG>system-view[SRG]sysname FW1[FW1]interface g0/0/0[FW1-GigabitEthernet0/0/0]ip add 192.168.0.1 24Warning: Address already exists! 默认接口地址已经存在,不用管[FW1-GigabitEthernet0/0/0]q[FW1]interface g0/0/1[FW1-GigabitEthernet0/0/1]ip add 192.168.1.1 24[FW1-GigabitEthernet0/0/1]q[FW1]display zone 显示区域配置localpriority is 100#trustpriority is 85interface of the zone is (1):GigabitEthernet0/0/0#untrustpriority is 5interface of the zone is (0):#dmzpriority is 50interface of the zone is (0):#[FW1][FW1]firewall zone name outside 创建一个名字为outside的区域[FW1-zone-outside]set priority 30 设置安全等级为30[FW1-zone-outside]q[FW1]firewall zone name inside[FW1-zone-inside]set priority 90[FW1-zone-inside]q[FW1]display zone[FW1]firewall zone outside 进入outside区域,把接口g0/0/1接入该区域[FW1-zone-outside]add interface GigabitEthernet 0/0/1[FW1-zone-outside]display this 显示当前的配置#firewall zone name outsideset priority 30add interface GigabitEthernet0/0/1#return[FW1-zone-outside]q[FW1]display policy all 查看策略policy zone local#policy zone trust#policy zone untrust#policy zone dmz#policy zone outside#policy zone inside#policy interzone local trust inboundfirewall default packet-filter is permit#policy interzone local trust outboundfirewall default packet-filter is permit#policy interzone local untrust inboundfirewall default packet-filter is deny#policy interzone local untrust outbound firewall default packet-filter is permit #policy interzone local dmz inboundfirewall default packet-filter is deny#policy interzone local dmz outboundfirewall default packet-filter is permit #policy interzone local outside inboundfirewall default packet-filter is deny#policy interzone local outside outbound firewall default packet-filter is permit #policy interzone local inside inboundfirewall default packet-filter is deny#policy interzone local inside outboundfirewall default packet-filter is permit #policy interzone trust untrust inboundfirewall default packet-filter is deny#policy interzone trust untrust outbound firewall default packet-filter is deny#policy interzone trust dmz inboundfirewall default packet-filter is deny#policy interzone trust dmz outboundfirewall default packet-filter is deny#policy interzone trust outside inboundfirewall default packet-filter is deny#policy interzone trust outside outbound firewall default packet-filter is deny#policy interzone inside trust inboundfirewall default packet-filter is deny#policy interzone inside trust outboundfirewall default packet-filter is deny#policy interzone dmz untrust inboundfirewall default packet-filter is deny#policy interzone dmz untrust outboundfirewall default packet-filter is deny#policy interzone outside untrust inboundfirewall default packet-filter is deny#policy interzone outside untrust outboundfirewall default packet-filter is deny#policy interzone inside untrust inboundfirewall default packet-filter is deny#policy interzone inside untrust outboundfirewall default packet-filter is deny#policy interzone dmz outside inboundfirewall default packet-filter is deny#policy interzone dmz outside outboundfirewall default packet-filter is deny#policy interzone inside dmz inboundfirewall default packet-filter is deny#policy interzone inside dmz outboundfirewall default packet-filter is deny#policy interzone inside outside inboundfirewall default packet-filter is deny#policy interzone inside outside outboundfirewall default packet-filter is deny#[FW1]创建策略放行outbound流量[FW1]policy interzone trust outside outbound 定义outbound流量 [FW1-policy-interzone-trust-outside-outbound]poli[FW1-policy-interzone-trust-outside-outbound]policy 1[FW1-policy-interzone-trust-outside-outbound-1]poli[FW1-policy-interzone-trust-outside-outbound-1]policy so[FW1-policy-interzone-trust-outside-outbound-1]policy source192.168.0.150 001:27:13 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1]poli[FW1-policy-interzone-trust-outside-outbound-1]policy de[FW1-policy-interzone-trust-outside-outbound-1]policy destination any 01:27:25 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1]ac[FW1-policy-interzone-trust-outside-outbound-1]action p[FW1-policy-interzone-trust-outside-outbound-1]action permit01:27:34 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1][FW1-policy-interzone-trust-outside-outbound-1]q01:27:37 2016/11/15[FW1-policy-interzone-trust-outside-outbound][FW1-policy-interzone-trust-outside-outbound]q01:27:38 2016/11/15[FW1][FW1][FW1]dis[FW1]display po[FW1]display poli[FW1]display policy i[FW1]display policy interzone t[FW1]display policy interzone trust o[FW1]display policy interzone trust outside outbound01:27:55 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is denypolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any[FW1]firewall packet-filter default permit interzone trust outside Warning:Setting the default packet filtering to permit poses security risks. Youare advised to configure the security policy based on the actual data flows. Are you sure you want to continue?[Y/N]y[FW1]dis[FW1]display policy interzone trust outside outbound01:28:23 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is permitpolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any恢复默认值deny[FW1]firewall packet-filter default deny interzone trust outside [FW1]display policy interzone trust outside outbound01:32:06 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is denypolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any用内网的路由Telnet AR2后,可以登录在防火墙查看会话状态[FW1]display firewall session table verbose00:58:32 2016/11/15Current Total Sessions : 2telnet VPN:public --> publicZone: trust--> outside TTL: 00:00:10 Left: 00:00:00Interface: GigabitEthernet0/0/1 NextHop: 192.168.1.150 MAC: 00-e0-fc-7a-0b-5a<--packets:18 bytes:867 -->packets:17 bytes:728192.168.0.150:49272-->192.168.1.150:23telnet VPN:public --> publicZone: trust--> outside TTL: 00:10:00 Left: 00:09:55Interface: GigabitEthernet0/0/1 NextHop: 192.168.1.150 MAC: 00-e0-fc-7a-0b-5a<--packets:16 bytes:725 -->packets:17 bytes:726192.168.0.150:49957-->192.168.1.150:23[FW1]如何允许外网的用户Telnet到内网的路由器[FW1]policy interzone trust outside inbound[FW1-policy-interzone-trust-outside-inbound]policy 1[FW1-policy-interzone-trust-outside-inbound-1]policy source 192.168.1.150 0[FW1-policy-interzone-trust-outside-inbound-1]policy destination 192.168.0.150 0[FW1-policy-interzone-trust-outside-inbound-1]policy service service-set telnet[FW1-policy-interzone-trust-outside-inbound-1]action permit验证试验效果。
网络安全之华为USG防火墙配置实例

网络安全之华为USG防火墙配置实例USG5500系列产品是华为技术有限公司面向大中型企业和下一代数据中心推出的新一代电信级统一安全网关设备。
USG5500系列产品部署于网络出口处,有效阻止Internet 上的黑客入侵、DDoS攻击,阻止内网用户访问非法网站,限制带宽,为内部网络提供一个安全可靠的网络环境。
这里华迪教育以此为例,给同学们讲解防火墙配置实例。
华为USG防火墙配置内容:(1)内部网络通过防火墙访问外部网络(NAT)(2)外部网络能够访问内部服务器的映射网站主要配置命令如下:Step 1: 设置内、外网接口IPinterface GigabitEthernet0/0/1ip address 192.168.10.1 255.255.255.0interface GigabitEthernet0/0/8ip address 211.95.1.200 255.255.255.0Step 2: 指定内网信任区和外网非信任区firewall zone trustdetect ftp (启用FTP应用层转换)add interface GigabitEthernet0/0/1firewall zone untrustadd interface GigabitEthernet0/0/8step 3 : 开启内网FTP服务映射到外网,开通区域间的通信许可firewall interzone trust untrustdetect ftp (开启内网到外网的FTP服务映射)firewall packet-filter default permit allstep 4:定义NAT地址池、配置NAT Server发布内网站点服务nat address-group 1 211.95.1.200 211.95.1.200nat server zone untrust protocol tcp global 211.95.1.200 www inside 192.168.10.254 wwwnat server zone untrust protocol tcp global 211.95.1.200 ftp inside 192.168.10.254 ftpnat server zone trust protocol tcp global 211.95.1.200 www inside 192.168.10.254 wwwnat server zone trust protocol tcp global 211.95.1.200 ftp inside 192.168.10.254 ftpStep 5 :配置nat转换,使得内网可以访问外网nat-policy interzone trust untrust outboundpolicy 1action source-natpolicy source 192.168.10.0 0.0.0.255address-group 1Step 6: 配置源地址转换,强制要求内网用户须通过映射地址访问内部服务器nat-policy zone trustpolicy 1action source-natpolicy source 192.168.10.0 0.0.0.255policy destination 211.95.1.254 0 address-group 1。
华为USG防火墙配置手册

华为USG防火墙配置手册1. 简介本手册旨在指导用户进行华为USG防火墙的配置和使用。
华为USG防火墙是一款功能强大的网络安全设备,可用于保护企业网络免受网络攻击和安全威胁。
2. 配置步骤2.1 硬件连接在配置USG防火墙之前,请确保正确连接好相关硬件设备,包括USG防火墙、路由器和服务器等。
2.2 登录USG防火墙使用SSH客户端等工具,输入USG防火墙的IP地址和管理员账号密码进行登录。
2.3 配置基本参数登录USG防火墙后,根据实际需求配置以下基本参数:- 设置管理员密码- 配置IP地址和子网掩码- 设置DNS服务器地址2.4 配置网络地址转换(NAT)根据实际网络环境,配置网络地址转换(NAT)功能。
NAT 功能可以将内部IP地址转换为合法的公网IP地址,实现内网和外网的通信。
2.5 配置访问控制策略配置访问控制策略可以限制网络流量的访问权限,确保只有授权的用户或设备可以访问特定网络资源。
2.6 配置安全服务华为USG防火墙提供多种安全服务功能,例如防病毒、入侵检测和内容过滤等。
根据实际需求,配置相应的安全服务功能。
2.7 配置远程管理和监控配置远程管理和监控功能,可以通过远程管理工具对USG防火墙进行实时监控和管理。
3. 常见问题解答3.1 如何查看防火墙日志?登录USG防火墙的Web界面,找到"日志"选项,可以查看防火墙的各种日志信息,包括安全事件、连接记录等。
3.2 如何升级USG防火墙固件版本?4. 其他注意事项- 在配置USG防火墙之前,请先备份原有的配置文件,以防配置错误或损坏设备。
- 请勿将USG防火墙暴露在不安全的网络环境中,以免受到未授权的访问和攻击。
以上是华为USG防火墙的配置手册,希望能帮助到您。
如有其他问题,请随时联系我们的技术支持。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
内网:
配置GigabitEthernet 0/0/1加入Trust区域
[USG5300] firewall zone trust
[USG5300-zone-untrust] add interface GigabitEthernet 0/0/1
外网:
配置GigabitEthernet 0/0/2加入Untrust区域
[USG5300] firewall zone untrust
[USG5300-zone-untrust] add interface GigabitEthernet 0/0/2
DMZ:
[USG5300] firewall zone dmz
[USG5300-zone-untrust] add interface GigabitEthernet 0/0/3
[USG5300-zone-untrust] quit
1.4.1 Trust和Untrust域间:允许内网用户访问公网
policy 1:允许源地址为10.10.10.0/24的网段的报文通过
[USG5300] policy interzone trust untrust outbound
[USG5300-policy-interzone-trust-untrust-outbound] policy 1
[USG5300-policy-interzone-trust-untrust-outbound-1] policy source 10.10.10.0 0.0.0.255
[USG5300-policy-interzone-trust-untrust-outbound-1] action permit
[USG5300-policy-interzone-trust-untrust-outbound-1] quit
如果是允许所有的内网地址上公网可以用以下命令:
[USG2100]firewall packet-filter default permit interzone trust untrust
direction outbound //必须
1.4.2 DMZ和Untrust域间:从公网访问内部服务器
policy 2:允许目的地址为10.10.11.2,目的端口为21的报文通过
policy 3:允许目的地址为10.10.11.3,目的端口为8080的报文通过
[USG5300] policy interzone untrust dmz inbound
[USG5300-policy-interzone-dmz-untrust-inbound] policy 2
[USG5300-policy-interzone-dmz-untrust-inbound-2] policy destination 10.10.11.3 0
[USG5300-policy-interzone-dmz-untrust-inbound-2] policy service service-set ftp
[USG5300-policy-interzone-dmz-untrust-inbound-2] action permit
[USG5300-policy-interzone-dmz-untrust-inbound-2] quit
[USG5300-policy-interzone-dmz-untrust-inbound] policy 3
[USG5300-policy-interzone-dmz-untrust-inbound-3] policy destination 10.10.11.2 0
[USG5300-policy-interzone-dmz-untrust-inbound-3] policy service service-set http
[USG5300-policy-interzone-dmz-untrust-inbound-3] action permit
[USG5300-policy-interzone-dmz-untrust-inbound-3] quit
[USG5300-policy-interzone-dmz-untrust-inbound] quit
配置内部服务器:
<USG5300> system-view
[USG5300] nat server protocol tcp global 220.10.10.16 8080 inside 10.10.11.2 www
[USG5300] nat server protocol tcp global 220.10.10.17 ftp inside 10.10.11.3 ftp
NAT
2、通过公网接口的方式
创建Trust区域和Untrust区域之间的NAT策略,确定进行NAT转换的源地址范围192.168.1.0/24网段,并且将其与外网接口GigabitEthernet 0/0/4进行绑定。
[USG] nat-policy interzone trust untrust outbound
[USG-nat-policy-interzone-trust-untrust-outbound] policy 0
[USG-nat-policy-interzone-trust-untrust-outbound-0]policy source 192.168.1.0 0.0.0.255
[USG-nat-policy-interzone-trust-untrust-outbound-0] action source-nat
[USG-nat-policy-interzone-trust-untrust-outbound-0] easy-ip GigabitEthernet 0/0/4
[USG-nat-policy-interzone-trust-untrust-outbound-0] quit
3、直接在接口启用nat
如果是针对内网用户上公网做nat,需要在内网接口使用
[USG-GigabitEthernet0/0/0]nat enable
2.10 配置策略路由
配置要求:10.10.167.0走218.201.135.177,10.10.168.0走58.57.15.53。
1、创建acl
acl number 3000
rule 1 permit ip source 10.10.167.0 0.0.0.255
acl number 3001
rule 1 permit ip source 10.10.168.0 0.0.0.255
2、创建策略路由
policy-based-route internet permit node 0
if-match acl 3000
apply ip-address next-hop 218.201.135.177
policy-based-route internet permit node 1
if-match acl 3001
apply ip-address next-hop 58.57.15.53
3、将策略路由引用到入接口(内网口)
ip policy-based-route internet
4、配置默认路由,配置策略路由的时候不需要配置明细路由。
ip route-static 0.0.0.0 0.0.0.0 218.201.135.177
ip route-static 0.0.0.0 0.0.0.0 58.57.15.53
检查配置:
dis policy-based-route。
