软件工程中英文翻译
软件工程(外文翻译文献)

外文文献资料1、Software EngineeringSoftware is the sequences of instructions in one or more programming languages that comprise a computer application to automate some business function. Engineering is the use of tools and techniques in problem solving. Putting the two words together, software engineering is the systemtic application of tools and techniques in the development of computer-based applications.The software engineering process describes the steps it takes to deelop the system. We begin a development project with the notion that there is a problem to be solved via automation. The process is how you get from problem recognition to a working solution. A quality process is desirable because it is more likely to lead to a quality product. The process followed by a project team during the development life cycle of an application should be orderly, goal-oriented, enjoyable, and a learning experience.Object-oriented methodology is an approach to system lifecycle development that takes a top-down view of data objects, their allowable actions, and the underlying communication requirement to define a system architecture. The data and action components are encapsulated, that is , they are combined together, to form abstract data types Encapsulation means that if I know what data I want ,I also know the allowable processes against that data. Data are designed as lattice hierarchies of relationships to ensure that top-down, hierarchic inheritance and side ways relationships are accommodated. Encapsulated objects are constrained only to communicate via messages. At a minimum, messages indicate the receiver and action requested. Messages may be more elaborate, including the sender and data to be acted upon.That we try to apply engineering discipline to software development does not mean that we have all the answers about how to build applications. On the contrary, we still build systems that are not useful and thus are not used. Part of the reason for continuing problems in application development, is that we are constantly trying to hita moving target. Both the technology and the type of applications needed by businesses are constantly changing and becoming more complex. Our ability to develop and disseminate knowledge about how to successfully build systems for new technologies and new application types seriously lags behind technological and business changes.Another reason for continuing problems in application development is that we aren’t always free to do what we like and it is hard to change habits and cultures from the old way of doing things, as well as get users to agree with a new sequence of events or an unfamiliar format for documentation.You might ask then, if many organizations don’t use good software engineering practices, why should I bother learning them? There are two good answers to this question. First, if you never know the right thing to do, you have no chance of ever using it. Second, organizations will frequently accept evolutionary, small steps of change instead of revolutionary, massive change. You can learn individual techniques that can be applied without complete devotion to one way of developing systems. In this way, software engineering can speed changee in their organizations by demonstrating how the tools and techniques enhance th quality of both the product and the process of building a system.2、Data Base System1、IntroductionThe development of corporate databases will be one of the most important data-processing activities for the rest of the 1970s. Date will be increasingly regarded as a vital corporate resource, which must be organized so as to maximize their value. In addition to the databases within an organization, a vast new demand is growing for database services, which will collect, organize, and sell data.The files of data which computers can use are growing at a staggering rate. The growth rate in the size of computer storage is greater than the growth in the size or power of any other component in the exploding data processing industry. The more data the computers have access to, the greater is their potential power. In all walks of life and in all areas of industry, data banks will change the areas of what it is possiblefor man to do. In the end of this century, historians will look back to the coming of computer data banks and their associated facilities as a step which changed the nature of the evolution of society, perhaps eventually having a greater effect on the human condition than even the invention of the printing press.Some most impressive corporate growth stories of the generation are largely attributable to the explosive growth in the need of information.The vast majority of this information is not yet computerized. However, the cost of data storage hardware is dropping more rapidly than other costs in data processing. It will become cheaper to store data on computer files than to store them on paper. Not only printed information will be stored. The computer industry is improving its capability to store line drawing, data in facsimile form, photo-graphs, human speech, etc. In fact, any form of information other than the most intimate communications between humans can be transmitted and stored digitally.There are two main technology developments likely to become available in the near future. First, there are electromagnetic devices that will hold much more data than disks but have much longer access time. Second, there are solid-state technologies that will give microsecond access time but capacities are smaller than disks.Disks themselves may be increased in capacity somewhat. For the longer term future there are a number of new technologies which are currently working in research labs which may replace disks and may provide very large microsecond-access-time devices. A steady stream of new storage devices is thus likely to reach the marketplace over the next 5 years, rapidly lowering the cost of storing data.Given the available technologies, it is likely that on-line data bases will use two or three levels of storage. One solid-state with microsecond access time, one electromagnetic with access time of a fraction of a second. If two ,three ,or four levels of storage are used, physical storage organization will become more complex ,probably with paging mechanisms to move data between the levels; solid-state storage offers the possibility of parallel search operation and associativememory.Both the quantity of data stored and the complexity of their organization are going up by leaps and bounds. The first trillion bit on-line stores are now in use . in a few year’s time ,stores of this size may be common.A particularly important consideration in data base design is to store the data so that the can be used for a wide variety of applications and so that the way they can be changed quickly and easily. On computer installation prior to the data base era it has been remarkably difficult to change the way data are used. Different programmers view the data in different ways and constantly want to modify them as new needs arise modification , however ,can set off a chain reaction of changes to existing programs and hence can be exceedingly expensive to accomplish .Consequently , data processing has tended to become frozen into its old data structures .To achieve flexibility of data usage that is essential in most commercial situations . Two aspects of data base design are important. First, it should be possible to interrogate and search the data base without the lengthy operation of writing programs in conventional programming languages. Second ,the data should be independent of the programs which use them so that they can be added to or restructured without the programs being changed .The work of designing a data base is becoming increasing difficult , especially if it is to perform in an optimal fashion . There are many different ways in which data can be structured ,and they have different types of data need to be organized in different ways. Different data have different characteristics , which ought to effect the data organization ,and different users have fundamentally different requirements. So we need a kind of data base management system(DBMS)to manage data.Data base design using the entity-relationship model begins with a list of the entity types involved and the relationships among them. The philosophy of assuming that the designer knows what the entity types are at the outset is significantly different from the philosophy behind the normalization-based approach.The entity-relationship(E-R)approach uses entity-relationship diagrams. The E-Rapproach requires several steps to produre a structure that is acceptable by the particular DBMS. These steps are:(1) Data analysis(2) Producing and optimizing the entity model.(3) Logical schema development(4) Physical data base design process.Developing a data base structure from user requirements is called data bases design. Most practitioners agree that there are two separate phases to the data base design process. The design of a logical database structure that is processable by the data base management system(DBMS)d escribes the user’s view of data, and is the selection of a physical structure such as the indexed sequential or direct access method of the intended DBMS.Current data base design technology shows many residual effects of its outgrowth from single-record file design methods. File design is primarily application program dependent since the data has been defined and structured in terms of individual applications to use them. The advent of DBMS revised the emphasis in data and program design approaches.There are many interlocking questions in the design of data-base systems and many types of technique that one can use is answer to the question so many; in fact, that one often sees valuable approaches being overlooked in the design and vital questions not being asked.There will soon be new storage devices, new software techniques, and new types of data bases. The details will change, but most of the principles will remain. Therefore, the reader should concentrate on the principles.2、Data base systemThe conception used for describing files and data bases has varied substantially in the same organization.A data base may be defined as a collection of interrelated data stored together with as little redundancy as possible to serve on or more applications in an optimal fashion; the data are stored so that they are independent of programs which use thedata; a common and controlled approach is used in adding new data and in modifying and retrieving existing data within the data base. One system is said to contain a collection of data bases if they are entirely separate in structure.A data base may be designed for batch processing, real-time processing, or in-line processing. A data base system involve application program, DBMS, and data base.One of the most important characteristics of most data bases is that they will constantly need to change and grow. Easy restructuring of the data base must be possible as new data types and new applications are added. The restructuring should be possible without having to rewrite the application program and in general should cause as little upheaval as possible. The ease with which a data base can be changed will have a major effect on the rate at which data-processing application can be developed in a corporation.The term data independence is often quoted as being one of the main attributes of a data base. It implies that the data and the application programs which use them are independent so that either may be changed without changing the other. When a single set of data items serves a variety of applications, different application programs perceive different relationships between the data items. To a large extent, data-base organization is concerned with the representation of relationship between data items and records as well as how and where the data are stored. A data base used for many applications can have multiple interconnections between the data item about which we may wish to record. It can describes the real world. The data item represents an attribute, and the attribute must be associated with the relevant entity. We design values to the attributes, one attribute has a special significance in that it identifies the entity.An attribute or set of attribute which the computer uses to identify a record or tuple is referred to as a key. The primary key is defined as that key used to uniquely identify one record or tuple. The primary key is of great importance because it is used by the computer in locating the record or tuple by means of an index or addressing algorithm.If the function of a data base were merely to store data, its organization would be simple. Most of the complexities arise from the fact that is must also show the relationships between the various items of data that are stored. It is different to describe the data in logical or physical.The logical data base description is referred to as a schema .A schema is a chart of the types of data that one used. It gives the names of the entities and attributes, and specifics the relations between them. It is a framework into which the values of the data-items can be fitted.We must distinguish between a record type and a instance of the record. When we talk about a “personnel record”,this is really a record type.There are no data values associated with it.The term schema is used to mean an overall chart of all of the dataitem types and record types stored in a data he uses. Many different subschema can be derived from one schema.The schema and the subschema are both used by the data-base management system, the primary function of which is to serve the application programs by executing their data operations.A DBMS will usually be handing multiple data calls concurrently. It must organize its system buffers so that different data operations can be in process together. It provides a data definition language to specify the conceptual schema and most likely, some of the details regarding the implementation of the conceptual schema by the physical schema. The data definition language is a high-level language, enabling one to describe the conceptual schema in terms of a “data model” .The choice of a data model is a difficult one, since it must be rich enough in structure to describe significant aspects of the real world, yet it must be possible to determine fairly automatically an efficient implementation of the conceptual schema by a physical schema. It should be emphasized that while a DBMS might be used to build small data bases, many data bases involve millions of bytes, and an inefficient implementation can be disastrous.We will discuss the data model in the following.3、Three Data ModelsLogical schemas are defined as data models with the underlying structure of particular database management systems superimposed on them. At the present time, there are three main underlying structures for database management systems. These are :RelationalHierarchicalNetworkThe hierarchical and network structures have been used for DBMS since the 1960s. The relational structure was introduced in the early 1970s.In the relational model, the entities and their relationships are represented by two-dimensional tables. Every table represents an entity and is made up of rows and columns. Relationships between entities are represented by common columns containing identical values from a domain or range of possible values.The last user is presented with a simple data model. His and her request are formulated in terms of the information content and do not reflect any complexities due to system-oriented aspects. A relational data model is what the user sees, but it is not necessarily what will be implemented physically.The relational data model removes the details of storage structure and access strategy from the user interface. The model provides a relatively higher degree of data. To be able to make use of this property of the relational data model however, the design of the relations must be complete and accurate.Although some DBMS based on the relational data model are commercially available today, it is difficult to provide a complete set of operational capabilities with required efficiency on a large scale. It appears today that technological improvements in providing faster and more reliable hardware may answer the question positively.The hierarchical data model is based on a tree-like structure made up of nodes and branches. A node is a collection of data attributes describing the entity at that point.The highest node of the hierarchical tree structure is called a root. The nodes at succeeding lower levels are called children .A hierarchical data model always starts with a root node. Every node consists of one or more attributes describing the entity at that node. Dependent nodes can follow the succeeding levels. The node in the preceding level becomes the parent node of the new dependent nodes. A parent node can have one child node as a dependent or many children nodes. The major advantage of the hierarchical data model is the existence of proven database management systems that use the hierarchical data model as the basic structure. There is a reduction of data dependency but any child node is accessible only through its parent node, the many-to –many relationship can be implemented only in a clumsy way. This often results in a redundancy in stored data.The network data model interconnects the entities of an enterprise into a network. In the network data model a data base consists of a number of areas. An area contains records. In turn, a record may consist of fields. A set which is a grouping of records, may reside in an area or span a number of areas. A set type is based on the owner record type and the member record type. The many-to many relation-ship, which occurs quite frequently in real life can be implemented easily. The network data model is very complex, the application programmer must be familiar with the logical structure of the data base.4、Logical Design and Physical DesignLogical design of databases is mainly concerned with superimposing the constructs of the data base management system on the logical data model. There are three mainly models: hierarchical, relational, network we have mentioned above.The physical model is a framework of the database to be stored on physical devices. The model must be constructed with every regard given to the performance of the resulting database. One should carry out an analysis of the physical model with average frequencies of occurrences of the grou pings of the data elements, with expected space estimates, and with respect to time estimates for retrieving and maintaining the data.The database designer may find it necessary to have multiple entry points into a database, or to access a particular segment type with more than one key. To provide this type of access; it may be necessary to invert the segment on the keys. Thephysical designer must have expertise in knowledge of the DBMS functions and understanding of the characteristics of direct access devices and knowledge of the applications.Many data bases have links between one record and another, called pointers. A pointer is a field in one record which indicates where a second record is located on the storage devices.Records that exist on storage devices is a given physical sequence. This sequencing may be employed for some purpose. The most common pupose is that records are needed in a given sequence by certain data-processing operations and so they are stored in that sequences.Different applications may need records in different sequences.The most common method of ordering records is to have them in sequence by a key —that key which is most commonly used for addressing them. An index is required to find any record without a lengthy search of the file.If the data records are laid out sequentially by key, the index for that key can be much smaller than they are nonsequential.Hashing has been used for addressing random-access storages since they first came into existence in the mid-1950s. But nobody had the temerity to use the word hashing until 1968.Many systems analysis has avoided the use of hashing in the suspicion that it is complicated. In fact, it is simple to use and has two important advantages over indexing. First, it finds most records with only one seek and second, insertion and deletions can be handled without added complexity. Indexing, however, can be used with a file which is sequential by prime key and this is an overriding advantage, for some batch-pro-cessing applications.Many data-base systems use chains to interconnect records also. A chain refers to a group of records scatters within the files and interconnected by a sequence of pointers. The software that is used to retrive the chained records will make them appear to the application programmer as a contiguous logical file.The primary disadvantage of chained records is that many read operations areneeded in order to follow lengthy chains. Sometimes this does not matter because the records have to be read anyway. In most search operations, however, the chains have to be followed through records which would not otherwise to read. In some file organizations the chains can be contained within blocked physical records so that excessive reads do not occur.Rings have been used in many file organizations. They are used to eliminate redundancy. When a ring or a chain is entered at a point some distance from its head, it may be desirable to obtain the information at the head quickly without stepping through all the intervening links.5、Data Description LanguagesIt is necessary for both the programmers and the data administrator to be able to describe their data precisely; they do so by means of data description languages. A data description language is the means of declaring to data-base management system what data structures will be used.A data description languages giving a logical data description should perform the folloeing functions:It should give a unique name to each data-item type, file type, data base and other data subdivision.It should identify the types of data subdivision such as data item segment , record and base file.It may define the type of encoding the program uses in the data items (binary , character ,bit string , etc.)It may define the length of the data items and the range of the values that a data item can assume .It may specify the sequence of records in a file or the sequence of groups of record in the data base .It may specify means of checking for errors in the data .It may specify privacy locks for preventing unauthorized reading or modification of the data .These may operate at the data-item ,segment ,record, file or data-base level and if necessary may be extended to the contents(value) of individual data items .The authorization may , on the other hand, be separate defined .It is more subject to change than the data structures, and changes in authorization proceduresshould not force changes in application programs.A logical data description should not specify addressing ,indexing ,or searching techniques or specify the placement of data on the storage units ,because these topics are in the domain of physical ,not logical organization .It may give an indication of how the data will be used or of searching requirement .So that the physical technique can be selected optimally but such indications should not be logically limiting.Most DBMS have their own languages for defining the schemas that are used . In most cases these data description languages are different to other programmer language, because other programmer do not have the capability to define to variety of relationship that may exit in the schemas.附录 B 外文译文1、软件工程软件是指令的序列,该指令序列由一种或者多种程序语言编写,它能使计算机应用于某些事物的运用自动化。
软件工程中英文对照外文翻译文献

中英文对照外文翻译(文档含英文原文和中文翻译)Application FundamentalsAndroid applications are written in the Java programming language. The compiled Java code — along with any data and resource files required by the application — is bundled by the aapt tool into an Android package, an archive file marked by an .apk suffix. This file is the vehicle for distributing the application and installing it on mobile devices; it's the file users download to their devices. All the code in a single .apk file is considered to be one application.In many ways, each Android application lives in its own world:1. By default, every application runs in its own Linux process. Android starts the process when any of the application's code needs to be executed, and shuts down the process when it's no longer needed and system resources are required by other applications.2. Each process has its own virtual machine (VM), so application code runs in isolation from the code of all other applications.3. By default, each application is assigned a unique Linux user ID. Permissions are set so that the application's files are visible only to that user and only to the application itself — although there are ways to export them to other applications as well.It's possible to arrange for two applications to share the same user ID, in which case they will be able to see each other's files. To conserve system resources, applications with the same ID can also arrange to run in the same Linux process, sharing the sameVM.Application ComponentsA central feature of Android is that one application can make use of elements of other applications (provided those applications permit it). For example, if your application needs to display a scrolling list of images and another application has developed a suitable scroller and made it available to others, you can call upon that scroller to do the work, rather than develop your own. Your application doesn't incorporate the code of the other application or link to it. Rather, it simply starts up that piece of the other application when the need arises.For this to work, the system must be able to start an application process when any part of it is needed, and instantiate the Java objects for that part. Therefore, unlike applications on most other systems, Android applications don't have a single entry point for everything in the application (no main() function, for example). Rather, they have essential components that the system can instantiate and run as needed. There are four types of components:ActivitiesAn activity presents a visual user interface for one focused endeavor the user can undertake. For example, an activity might present a list of menu items users can choose from or it might display photographs along with their captions. A text messaging application might have one activity that shows a list of contacts to send messages to, a second activity to write the message to the chosen contact, and other activities to review old messages or change settings. Though they work together to form a cohesive user interface, each activity is independent of the others. Each one is implemented as a subclass of the Activity base class.An application might consist of just one activity or, like the text messaging application just mentioned, it may contain several. What the activities are, and how many there are depends, of course, on the application and its design. Typically, one of the activities is marked as the first one that should be presented to the user when the application is launched. Moving from one activity to another is accomplished by having the current activity start the next one.Each activity is given a default window to draw in. Typically, the window fills the screen, but it might be smaller than the screen and float on top of other windows. An activity can also make use of additional windows — for example, a pop-up dialog that calls for a user response in the midst of the activity, or a window that presents users with vital information when they select a particular item on-screen.The visual content of the window is provided by a hierarchy of views — objects derived from the base View class. Each view controls a particular rectangular space within the window. Parent views contain and organize the layout of their children. Leaf views (those at the bottom of the hierarchy) draw in the rectangles they control and respond to user actions directed at that space. Thus, views are where the activity's interaction with the user takes place.For example, a view might display a small image and initiate an action when the user taps that image. Android has a number of ready-made views that you can use —including buttons, text fields, scroll bars, menu items, check boxes, and more.A view hierarchy is placed within an activity's window by theActivity.setContentView() method. The content view is the View object at the root of the hierarchy. (See the separate User Interface document for more information on views and the hierarchy.)ServicesA service doesn't have a visual user interface, but rather runs in the background for an indefinite period of time. For example, a service might play background music as the user attends to other matters, or it might fetch data over the network or calculate something and provide the result to activities that need it. Each service extends the Service base class.A prime example is a media player playing songs from a play list. The player application would probably have one or more activities that allow the user to choose songs and start playing them. However, the music playback itself would not be handled by an activity because users will expect the music to keep playing even after they leave the player and begin something different. To keep the music going, the media player activity could start a service to run in the background. The system would then keep the music playback service running even after the activity that started it leaves the screen.It's possible to connect to (bind to) an ongoing service (and start the service if it's not already running). While connected, you can communicate with the service through an interface that the service exposes. For the music service, this interface might allow users to pause, rewind, stop, and restart the playback.Like activities and the other components, services run in the main thread of the application process. So that they won't block other components or the user interface, they often spawn another thread for time-consuming tasks (like music playback). See Processes and Threads, later.Broadcast receiversA broadcast receiver is a component that does nothing but receive and react to broadcast announcements. Many broadcasts originate in system code — for example, announcements that the timezone has changed, that the battery is low, that a picture has been taken, or that the user changed a language preference. Applications can also initiate broadcasts — for example, to let other applications know that some data has been downloaded to the device and is available for them to use.An application can have any number of broadcast receivers to respond to any announcements it considers important. All receivers extend the BroadcastReceiver base class.Broadcast receivers do not display a user interface. However, they may start an activity in response to the information they receive, or they may use the NotificationManager to alert the user. Notifications can get the user's attention in various ways — flashing the backlight, vibrating the device, playing a sound, and so on. They typically place a persistent icon in the status bar, which users can open to get the message.Content providersA content provider makes a specific set of the application's data available to other applications. The data can be stored in the file system, in an SQLite database, or in anyother manner that makes sense. The content provider extends the ContentProvider base class to implement a standard set of methods that enable other applications to retrieve and store data of the type it controls. However, applications do not call these methods directly. Rather they use a ContentResolver object and call its methods instead. A ContentResolver can talk to any content provider; it cooperates with the provider to manage any interprocess communication that's involved.See the separate Content Providers document for more information on using content providers.Whenever there's a request that should be handled by a particular component, Android makes sure that the application process of the component is running, starting it if necessary, and that an appropriate instance of the component is available, creating the instance if necessary.Activating components: intentsContent providers are activated when they're targeted by a request from a ContentResolver. The other three components — activities, services, and broadcast receivers — are activated by asynchronous messages called intents. An intent is an Intent object that holds the content of the message. For activities and services, it names the action being requested and specifies the URI of the data to act on, among other things. For example, it might convey a request for an activity to present an image to the user or let the user edit some text. For broadcast receivers, theIntent object names the action being announced. For example, it might announce to interested parties that the camera button has been pressed.There are separate methods for activating each type of component:1. An activity is launched (or given something new to do) by passing an Intent object toContext.startActivity() or Activity.startActivityForResult(). The responding activity can look at the initial intent that caused it to be launched by calling its getIntent() method. Android calls the activity's onNewIntent() method to pass it any subsequent intents. One activity often starts the next one. If it expects a result back from the activity it's starting, it calls startActivityForResult() instead of startActivity(). For example, if it starts an activity that lets the user pick a photo, it might expect to be returned the chosen photo. The result is returned in an Intent object that's passed to the calling activity's onActivityResult() method.2. A service is started (or new instructions are given to an ongoing service) by passing an Intent object to Context.startService(). Android calls the service's onStart() method and passes it the Intent object. Similarly, an intent can be passed to Context.bindService() to establish an ongoing connection between the calling component and a target service. The service receives the Intent object in an onBind() call. (If the service is not already running, bindService() can optionally start it.) For example, an activity might establish a connection with the music playback service mentioned earlier so that it can provide the user with the means (a user interface) for controlling the playback. The activity would call bindService() to set up that connection, and then call methods defined by the service to affect the playback.A later section, Remote procedure calls, has more details about binding to a service.3. An application can initiate a broadcast by passing an Intent object to methods like Context.sendBroadcast(), Context.sendOrderedBroadcast(), andContext.sendStickyBroadcast() in any of their variations.Android delivers the intent to all interested broadcast receivers by calling their onReceive() methods. For more on intent messages, see the separate article, Intents and Intent Filters.Shutting down componentsA content provider is active only while it's responding to a request from a ContentResolver. And a broadcast receiver is active only while it's responding to a broadcast message. So there's no need to explicitly shut down these components. Activities, on the other hand, provide the user interface. They're in a long-running conversation with the user and may remain active, even when idle, as long as the conversation continues. Similarly, services may also remain running for a long time. So Android has methods to shut down activities and services in an orderly way:1. An activity can be shut down by calling its finish() method. One activity can shut down another activity (one it started with startActivityForResult()) by calling finishActivity().2. A service can be stopped by calling its stopSelf() method, or by calling Context.stopService().Components might also be shut down by the system when they are no longer being used or when Android must reclaim memory for more active components. A later section, Component Lifecycles, discusses this possibility and its ramifications in more detail.The manifest fileBefore Android can start an application component, it must learn that the component exists. Therefore, applications declare their components in a manifest file that's bundled into the Android package, the .apk file that also holds the application's code, files, and resources.The manifest is a structured XML file and is always named AndroidManifest.xml for all applications. It does a number of things in addition to declaring the application's components, such as naming any libraries the application needs to be linked against (besides the default Android library) and identifying any permissions the application expects to be granted.But the principal task of the manifest is to inform Android about the application's components. For example, an activity might be declared as follows:The name attribute of the <activity> element names the Activity subclass that implements the activity. The icon and label attributes point to resource files containing an icon and label that can be displayed to users to represent the activity.The other components are declared in a similar way — <service> elements for services, <receiver> elements for broadcast receivers, and <provider> elements for content providers. Activities, services, and content providers that are not declared in the manifest are not visible to the system and are consequently never run. However, broadcast receivers can either be declared in the manifest, or they can be created dynamically in code (as BroadcastReceiver objects) and registered with the system by calling Context.registerReceiver().For more on how to structure a manifest file for your application, see The Android Manifest.xml File.Intent filtersAn Intent object can explicitly name a target component. If it does, Android finds that component (based on the declarations in the manifest file) and activates it. But if a target is not explicitly named, Android must locate the best component to respond to the intent. It does so by comparing the Intent object to the intent filters of potential targets. A component's intent filters inform Android of the kinds of intents the component is able to handle. Like other essential information about the component, they're declared in the manifest file. Here's an extension of the previous example that adds two intent filters to the activity:The first filter in the example — the combination of the action"android.intent.action.MAIN" and the category"UNCHER" — is a common one. It marks the activity as one that should be represented in the application launcher, the screen listing applications users can launch on the device. In other words, the activity is the entry point for the application, the initial one users would see when they choose the application in the launcher.The second filter declares an action that the activity can perform on a particular type of data.A component can have any number of intent filters, each one declaring a different set of capabilities. If it doesn't have any filters, it can be activated only by intents that explicitly name the component as the target.For a broadcast receiver that's created and registered in code, the intent filter is instantiated directly as an IntentFilter object. All other filters are set up in the manifest. For more on intent filters, see a separate document, Intents and Intent Filters.应用程序基础Android DevelopersAndroid应用程序使用Java编程语言开发。
广东商学院各院及其专业(中英文翻译)1

广东商学院各院及其专业(中英文翻译) (GUANG DONG UNIVERSITY OF BUSINESS STUDIES)一、工商管理学院:The College of Business Administration1、物流管理:Logistics Management2、人力资源:Human Resources3、市场营销专业:Marketing Program4、工商管理专业:Business Administration Program二、会计学院: the College of Accounting1、审计学:Auditing2、会计学专业:Accounting Professional3、财务管理专业: Financial Management Major4、审计学(注册会计师)Auditing(Certified Public Accountant (CPA))三、财税学院:the College of Taxation1、财政学:Public Finance2、税务:Financial Affairs3、资产评估专业:MSc Property Appraisal and Management四、公共管理学院:School of Public Administration1、行政管理专业:General Administration Program2、劳动与社会保障:Labor and Social Security3、文化产业管理: Culture Industry Management4、公共事业管理(城市管理):City Management五、金融学院:College of Finance1、金融学:Finance2、国际金融:International Finance3、金融工程:Financial Engineering4、保险:Insurance5、投资学:Investment Principles六、经济贸易与统计学院:the College of Economic and Statistics1、经济学:Economics2、国际经济与贸易:International Economics And Trade3、统计学:Statistics4、国际商务:International Business七、法学院:The College of Law1、法学(国际法):The International Law2、法学(民商法):Civil and Commercial Law3、法学:Science of Law4、治安学:Science of Public Order八、旅游学院:College of Tourism1、酒店管理:Hotel Management2、旅游管理:Tourism Management3、会展经济与管理:Exhibition Economy and Management九、资源与环境学院:College of Resource and Environment1、土地资源管理:Land Resources Management2、资源环境与城乡规划管理:Resources-Environment and Urban-Rural Planning Management3、房地产经营管理:Administration and Management of Real Estate十、外国语学院:College of Foreign Language1、英语(国际商务管理):International Business Management2、英语(国际商务翻译):International Business English Translation3、日语(国际商务管理):nternational Business Management十一、人文与传播学院: College of Humanities and Communications1、汉语言文学:Chinese Language and Literature2、新闻学:Advocacy Journalism3、新闻学(编辑出版方向)News Editing4、社会工作:Social work5、社会学:Sociology6、播音与主持艺术:Techniques of Broadcasting and Anchoring7、广播电视编导:Radio and Television Editing and Directing十二、艺术学院:Academy of Fine Arts1、广告学(广告策划与经营管理方向):Advertisement2、艺术设计(广告设计方向):Art and Design(Advertising Design)3、艺术设计(玩具与游戏设计方向):Art and Design4、艺术设计(商业空间设计方向):Commercial Space Design5、艺术设计(展示设计):Display Design6、动画专业:Science of Animated Cartoon Program十三、信息学院:College of Information1、信息管理与信息系统:Information Management and Information System2、计算机科学与技术:Computer Science and Technology3、电子商务:Electronic Commerce4、软件工程:Software Engineering十四、数学与计算科学学院:Collegeof Mathematics and Computer Science1、信息与计算科学:Information and Computing Science2、数学与应用数学:Mathematics and Applied Mathematics十五、人文与传播学院:College of Humanities and Communications1、应用心理学: Applied Psychology2、商务文秘:Business secretary3、对外汉语:Teaching Chinese as a Foreign Language。
软件工程专业词汇中英对照

Acceptance Testing--可接受性测试一般由用户/客户进行的确认是否可以接受一个产品的验证性测试。
actual outcome--实际结果被测对象在特定的条件下实际产生的结果。
Ad Hoc Testing--随机测试测试人员通过随机的尝试系统的功能,试图使系统中断。
algorithm--算法一个定义好的有限规则集,用于在有限步骤内解决一个问题;(2)执行一个特定任务的任何操作序列。
algorithm analysis--算法分析一个软件的验证确认任务,用于保证选择的算法是正确的、合适的和稳定的,并且满足所有精确性、规模和时间方面的要求。
Alpha Testing--Alpha测试由选定的用户进行的产品早期性测试。
这个测试一般在可控制的环境下进行的。
analysis--分析分解到一些原子部分或基本原则,以便确定整体的特性;(2)一个推理的过程,显示一个特定的结果是假设前提的结果;(3)一个问题的方法研究,并且问题被分解为一些小的相关单元作进一步详细研究。
anomaly--异常在文档或软件操作中观察到的任何与期望违背的结果。
application software--应用软件满足特定需要的软件。
architecture--构架一个系统或组件的组织结构。
ASQ--自动化软件质量(Automated Software Quality)使用软件工具来提高软件的质量。
assertion--断言指定一个程序必须已经存在的状态的一个逻辑表达式,或者一组程序变量在程序执行期间的某个点上必须满足的条件。
assertion checking--断言检查用户在程序中嵌入的断言的检查。
audit--审计一个或一组工作产品的独立检查以评价与规格、标准、契约或其它准则的符合程度。
audit trail--审计跟踪系统审计活动的一个时间记录。
Automated Testing--自动化测试使用自动化测试工具来进行测试,这类测试一般不需要人干预,通常在GUI、性能等测试中用得较多。
广东商学院各院及其专业(中英文翻译)1

广东商学院各院及其专业(中英文翻译)(GUANG DONG UNIVERSITY OF BUSINESS STUDIES)一、工商管理学院:The College of Business Administration1、物流管理:Logistics Management2、人力资源:Human Resources3、市场营销专业:Marketing Program4、工商管理专业:Business Administration Program二、会计学院: the College of Accounting1、审计学:Auditing2、会计学专业:Accounting Professional3、财务管理专业: Financial Management Major4、审计学(注册会计师)Auditing(Certified Public Accountant (CPA))三、财税学院:the College of Taxation1、财政学:Public Finance2、税务:Financial Affairs3、资产评估专业:MSc Property Appraisal and Management四、公共管理学院:School of Public Administration1、行政管理专业:General Administration Program2、劳动与社会保障:Labor and Social Security3、文化产业管理: Culture Industry Management4、公共事业管理(城市管理):City Management五、金融学院:College of Finance1、金融学:Finance2、国际金融:International Finance3、金融工程:Financial Engineering4、保险:Insurance5、投资学:Investment Principles六、经济贸易与统计学院:the College of Economic and Statistics1、经济学:Economics2、国际经济与贸易:International Economics And Trade3、统计学:Statistics4、国际商务:International Business七、法学院:The College of Law1、法学(国际法):The International Law2、法学(民商法):Civil and Commercial Law3、法学:Science of Law4、治安学:Science of Public Order八、旅游学院:College of Tourism1、酒店管理:Hotel Management2、旅游管理:Tourism Management3、会展经济与管理:Exhibition Economy and Management九、资源与环境学院:College of Resource and Environment1、土地资源管理:Land Resources Management2、资源环境与城乡规划管理:Resources-Environment and Urban-Rural Planning Management3、房地产经营管理:Administration and Management of Real Estate十、外国语学院:College of Foreign Language1、英语(国际商务管理):International Business Management2、英语(国际商务翻译):International Business English Translation3、日语(国际商务管理):nternational Business Management十一、人文与传播学院: College of Humanities and Communications1、汉语言文学:Chinese Language and Literature2、新闻学:Advocacy Journalism3、新闻学(编辑出版方向)News Editing4、社会工作:Social work5、社会学:Sociology6、播音与主持艺术:Techniques of Broadcasting and Anchoring7、广播电视编导:Radio and Television Editing and Directing十二、艺术学院:Academy of Fine Arts1、广告学(广告策划与经营管理方向):Advertisement2、艺术设计(广告设计方向):Art and Design(Advertising Design)3、艺术设计(玩具与游戏设计方向):Art and Design4、艺术设计(商业空间设计方向):Commercial Space Design5、艺术设计(展示设计):Display Design6、动画专业:Science of Animated Cartoon Program十三、信息学院:College of Information1、信息管理与信息系统:Information Management and Information System2、计算机科学与技术:Computer Science and Technology3、电子商务:Electronic Commerce4、软件工程:Software Engineering十四、数学与计算科学学院:Collegeof Mathematics and Computer Science1、信息与计算科学:Information and Computing Science2、数学与应用数学:Mathematics and Applied Mathematics十五、人文与传播学院:College of Humanities and Communications1、应用心理学: Applied Psychology2、商务文秘:Business secretary3、对外汉语:Teaching Chinese as a Foreign Language。
软件工程用英语怎么说

软件工程用英语怎么说问题一:软件工程用英语怎么说?Software engineering问题二:软件开发用英语怎么说软件开发(software development)软件工程(software engineering)问题三:我毕业于xx学校软件工程专业英语怎么说I graduated from XX �niversity and my major is software engineering.问题四:软件工程硕士的英文怎么说软件工程硕士[网络] MSE; Master of Software Engineering; software engineering; MSc Software Engineering;[例句]第一个软件工程硕士学位设立了西雅图大学于1979年。
The first software engineering Master's degree was established at Seattle University in1979.问题五:请问“信息学院”和“软件学院”的用英语怎么说?信息学院:Information Institute软件学院:Software Institute如果是厂信息系:Information Department软件系:Software Department希望对您有帮助问题六:软件工程专业用英语吗可以不用。
但是用和不用差别很大,从学校到工作岗位,它都会限制你的发展。
学校里,软工的一般都要大量刷编程题,一些是英文的题。
还有计算机相关的高新技术、论文,英文的比较多,尤其是前沿技术。
工作后,当你写出来的东西没有英文,全是拼音时,管理会认为你的水平不高,只能被淘汰到小公司去上班。
问题七:我来自软件工程1班。
英语怎么翻译I am from class one of Software Engineering. 问题八:软件工程中二次开发专业术语用英文怎么说?redevelope/reexploit。
软件工程英文文献原文及翻译

英文文献原文及译文学生姓名:赵凡学号:1021010639学院:软件学院专业:软件工程指导教师:武敏顾晨昕2014年 6月英文文献原文The use of skinWhat is a skin? In the role of setting, the preparations made for the animation in the final process is skinning. The so-called skinning skinning tool is to use role-model role do with our skeletal system to help set the course together. After this procedure, fine role model can be rendered on real numbers can be made into animation. Bones in skinning process, in which the position is called Bind Pose. After the skin, bone deformation of the skin caused by the Games. However, sometimes inappropriate distortion, which requires bone or skin to make the appropriate changes, then you can make use of relevant command to restore the bone binding position, and then disconnect the association between bone and skin. In Maya, you can always put the bones and skin disconnected or reconnected. There is a direct way to skin the skin (skin flexible rigid skinning) and indirect skin (or wrap the lattice deformation of flexible or rigid skinning skinning joint use).In recent years, more and more 3D animation software, a great competition in the market, software companies are constantly developing and updating the relevant software only more humane, but in three-dimensional animation maya mainstream animation software. Able to create bone, meat, God's role is that each CG digital artists dream. Whether the digital characters charm, the test is the animator of life, understanding of life. Digital character to have bone and meat producers are required for the role of the body and has a full grasp of motor function. In addition, the roles of whether there is realism, the key lies in the design and production of the skin, which is skinning animation software for skilled technical and creative mastery is essential. Skin is ready to work in animation final steps, after this procedure, you can do the movements designed, if the skin did not do the work, after the animation trouble, so the skin is very important.As the three-dimensional animation with accuracy and authenticity, the current three-dimensional animation is rapidly developing country, nowadays the use ofthree-dimensional animation everywhere, the field of architecture, planning areas, landscape areas, product demonstrations, simulated animation, film animation, advertising, animation, character animation, virtual reality and other aspects of three-dimensional animation fully reflects the current importance. If compared to the three-dimensional animation puppet animation in real life, then the doll puppet animation equivalent of Maya modeling, puppet performers equivalent Maya animators and puppet steel joints in the body is the skeletal system. Bones in the animation will not be the final rendering, its role is only equivalent to a bracket that can simulate real bones set of major joints to move, rotate, etc.. When the bones are set, we will be bound to the skeleton model, this step is like a robot mounted to a variety of external parts, like hanging, and then through the various settings, add a keyframe animation on bone, and then drive to be bound by the bones corresponding to the model on the joints. Thus, in the final animation, you can see the stiffness of a stationary model with vitality. The whole process from the rigging point of view, may not compare more tedious keyframe animation, rigging, but it is the core of the whole three-dimensional animation, and soul.Rigging plays a vital role in a three-dimensional animation. Good rigging easy animation production, faster and more convenient allows designers to adjust the action figures. Each step are bound to affect the skeleton final animation, binding is based on the premise of doing animation, animators animate convenient, good binding can make animation more fluid, allowing the characters to life even more performance sex. In addition to rigging as well as expression of the binding character, but also to let people be able to speak or behave different facial expressions. Everything is done in order to bind the animation is set, it is bound to set a good animation is mainly based on the entire set of styles and processes. Rigging is an indispensable part in the three-dimensional animation.Three-dimensional animation production process: model, texture, binding, animation, rendering, special effects, synthesis. Each link is associated. Model and material determines the style of animation, binding, and animation determine fluency animation, rendering, animation effects, and synthetic colors and determine the finalresult.Three-dimensional animation, also known as 3D animation, is an emerging technology. Three-dimensional animation gives a three-dimensional realism, even subtle animal hair, this effect has been widely applied to the production of film and television in many areas, education, and medicine. Movie Crash, deformed or fantasy scenes are all three-dimensional animation in real life. Designers in the first three-dimensional animation software to create a virtual scene, and then create the model according to the proportion, according to the requirements set trajectory models, sports, and other parameters of the virtual camera animation, and finally as a model assigned a specific material, and marked the lights , the final output rendering, generating the final screen. DreamWorks' "Shrek" and Pixar's "Finding Nemo" is so accomplished visual impact than the two-dimensional animation has.Animated film "Finding Nemo" extensive use of maya scene technology. Produced 77,000 jellyfish animation regardless of the technical staff or artist is one of the most formidable challenge. This pink translucent jellyfish is most needed is patience and skill, you can say, jellyfish appeared animated sea creatures taken a big step. His skin technology can be very good. The use of film roles skinning techniques is very good, so that each character is vivid, is not related to expression, or action is so smooth, these underwater underwater world is so beautiful. Maya maya technology for the creation of the first to have a full understanding and knowledge. He first thought of creative freedom virtual capacity, but the use of technology has limitations. When the flexible skinning animation technique many roles in the smooth bound for editing, re-allocation tools needed to adjust the skeletal model for the control of the weight through the right point, every detail clownfish are very realistic soft. In the joint on the affected area should smear, let joints from other effects, this movement was not wearing a tie. Used less rigid, rigid lattice bound objects must be created in a position to help the bones of the joint motion. Animated film "Finding Nemo," the whole movie a lot of facial animation, facial skin but also a good technique to make facial expressions, the facial animation is also animated, and now more and more animated facial animationtechnology increasingly possible, these should be good early skin behind it will not affect the expression, there is therefore the creation of the film how maya digital technology, play his video works styling advantages and industrial processes are needed to explore creative personnel, all and three-dimensional figures on the production of content, from maya part. Two-dimensional hand-painted parts, post-synthesis of several parts, from a technical production, artistic pursuit. Several angles to capture the entire production cycle of creation. Maya techniques used in the animated film "Finding Nemo", the flexible skinning performance of many, clown face on with a lot of smooth binding, so more people-oriented, maya application of technical advantages in certain limited extent. Realistic three-dimensional imaging technology in the animation depth spatial density, the sense of space, mysterious underwater world to play the most. Because lifelike action, it also brings the inevitable footage and outdoor sports realistic density, but also to explore this movie maya main goal of the three-dimensional animation.英文文献译文蒙皮的运用什么是蒙皮?在角色设定中,为动画所作的准备工作里的最后一道工序就是蒙皮。
《软件工程》英汉专业词汇对照表
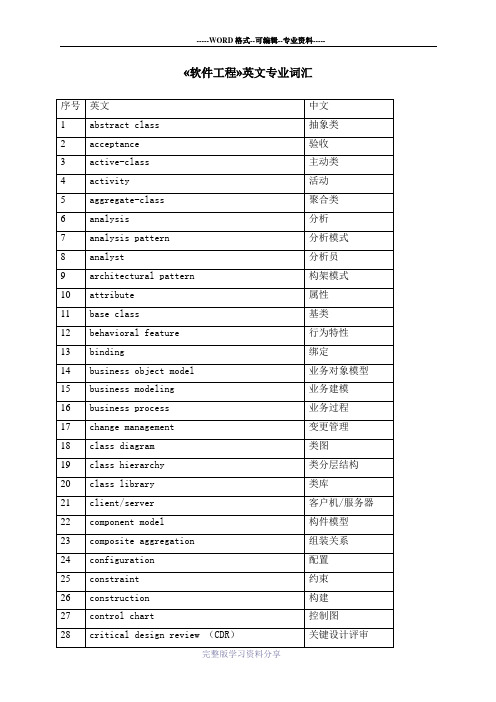
10
attribute
属性
11
base class
基类
12
behavioral feature
行为特性
13
binding
绑定
14
business object model
业务对象模型
15
business modeling
业务建模
16
business process
业务过程
17
change management
86
Unified Modeling Language(UML)
统一建模语言
87
use case
用例
88
use-case model
用例模型
89
user interface (UI)
用户界面
90
validation
确认
91
verification
验证
92
version
版本
93
virtual machine(VM)
inheritance
继承
47
inspection effectiveness
审查有效性
48
integrated development environment (IDE)
集成开发环境
49
interaction
交互
50
interaction diagram
交互图
51
interface
接口/界面
52
management
77
reuse
复用
78
stub
桩模块
79
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Internet of electronic information resourcesdevelopment and utilizationThe development and utilization of Internet richness of the electronic information resource, which can be directly consider E-mail, file transfer, Telnet approach, also can indirectly consider using several common information retrieval tool, the paper made a detailed introduction and analysis, aims to help help user well using the Internet. For information institutions or library is concerned, to learn and use well, not only can enlarge Internet information resources development and utilization of the scope, but also able to enhance the level of service to users.Keywords Internet electronic information resources development and utilizationExploitation andUtilization of Electronic Information Resources on Internet- The Internet can be extensive communication in the world every person, connect all the computer and provides a wealth of information resources, and provide A variety of service tool to obtain these resources. Information institutions or libraries in the Internet for information resources, retrieval electricity The son journals and newspapers, orders and electronic publications, retrieval online catalogue and union catalog, a searchable database system, access journals to discuss, through the file transfer (FTP) receiving documents. So we can use Internet richness of the information resources to expand its collection, still can use directly these information resources to carry on the information retrieval consulting services. In searching available in the email, database retrieval, file transfer, remote login, and information query tools etc. In order to enrich the exploitation and utilization of Internet information resources, the author thinks that should through the following ways.1 directly use the InternetE-mail (hereinafter Email) Electronicmail,E-mail is a based on computer network to store, forward form various data, images, and exchange information in words of exchange System, sending and receiving and managementare in computer Internet E-mail systems management software. Email software generally provide teleport, browse, storage, transfer, delete, restore E-mail and the reply, and other functions, can match a communication, also can spread, each user has a particular coding mailbox, can with any users online information transmission, spontaneous since the received or forwardingletters. User simply equipped with a modem, a telephone lines and thcorresponding communication software, can in any part of the microcomputer with communication phase even on sending and receiving information, to realize communication. Email take storage, forwarding way, open E-mail program is adopted, the web server machine online way 24 hours working around-the-clock, always receive emails from all of the world, no matter what, when and where will the computer connected server only, can scoop out your E-mail. Need to send electronic information, users first the arbitrary length of letters for its input computer plus addressee address, and send button, the information being sent to the information high male road. On the other side of the addressee opena computer, information will be sent into his E-mail, can be read. Through E-mail can access the Internet richness of the database and files resources. But on the Internet use E-mail to the other party requests, told to want borrowed books or want to copy a in the journal papers. Users can also use E-mail to information institutions (or library) rapporteur retrieval request, will soon be in the home received E-mail sent back the retrieval results.via E-mail to obtain information resources of several ways(1) what service(2) information serviceProvide consulting services, get all kinds of information resources on the network.Internet information service center compiled the Mail server (E-mail Erver), so as to let the user's query the information they provide. Archie server to send an email, the mail service Device will automatically read, analyze mail, and will executecommands in the results by E-mail sent users. When the user wants to nets thespecific information service center inquires the material, can be directly to thecenter send an contains a series of electric information query command son Mail, the center's Mail server (E-mail erver) of procedures will automatically collect read, analyze received E-mail of life makes, then for users to search, retrieval results by E-mail sent back to the user E-mail.(3) electronic Bulletin Board system (Bulletin Board ystem, abbreviation BB)The electronic bulletin board content includes news, notification, conference news, composition, the latest weather conditions, the telephone directory and so on, can to a group of users, and not a single user provide telecommunication services, 24 hour at all times to located in the world of a group of people to transmit information, is the information communication is a very effective tool.(4) user group discussion group) (i.e. User group(Mailing List) is in accordance with the different project organization, attract the world 56,936 or have a common interest Old people to the discussion, exchange views. To become a discussion group members, users need to apply a paneldiscussion of the principal (usually send an electronic mail), he (she) name wasincluded in the recipient list, then duly received networks offer letter interest, the user can his ideas entry computer, transmitted to other members of the group inside, so everyone may at any time, any place engage in conversation. In a foreign country, by E-mail for academic discussion already commonly, the same professional orrelated field experts, scholars between academic discussions and informationexchange. Join or exit the group of users only to the relevant E-mail send ancontaining have join (by) or exit (unsubscribe) the E-mail address.(5) electronic journal (EJournal)Subscriber may through email to E-mail server @ RTFM. MIT. Edu address can be checked to the electronic periodical catalog and their E-mail address, emailaddresses to it issued to order the whole of periodicals or ordering the relatedarticles in the journal letters. There are many online free of electronic journals, as long as you apply for subscription, subscription publications will automatically send to youElectronic mailbox.(6) online meetingElectronic conference in time and place of great flexibility, although lackingattendees mutual infection, but for travelFee less groups speaking, have certain appeal.library or information institutions using email approach(1) information consulting servicesFor readers request access to the literature material, ask knotty problems, find the latest information, when library cannot be resolved, they can make E-mail outside other information or advice, turn to deal with them.2) information retrieval serviceOCLC and DIALOG system, etc. By E-mail way for users provide query and retrieving service always respond to user All of the information required, and user'srequirements to a user's literature deliver E-mail.(3) provide online sdi intelligence servicesE-mail system, user use online inter-library loan system (ILL), first in the unity on the cataloguing books information retrieval, then choose 1! 5 housed thebibliography, sends out the library borrowingBook apply, Receive borrowed request of library via E-mail take each other need literature transmission in the past.(5) book purchasing and newspapers and periodicals orderMany books wholesalers and publishers and set up their own electronic ordering system, used for the transmission of various books tradeFile, data and information, ordering personnel want to use based on the systematic terminals, can get from all over the world from the book information such asE-mail.(6) literature material exchange business,(7) collect user opinion(8) to release a new books catalogues, news and noticethrough Email realized on the various service with Internet access service provided(1) through Email do FTP,(2) by Email do Archic;(3) by Email do Gophcr;(4) by Email do Veronica,(5) by Email do Usenet;(6) by Email do WAI retrieval;(7) by Email do WWW,(8) by Email do Finger,(9) by Email do WHOI;(10) by Email to do the other services.File Transfer Protocol (FTP Protocol File, abbreviation) 'Is stored in the remote computer system of documents access tool. Need to userlogin user name and password files Sharing agreement. According to the FTP access to resources can be considered a special library (or information center), at any time to each take place Need, but not limited to place, also need not dependent on inter-library loan. In any between two computers to transmit data (documents), it is to use Elihu access Internet rich resources important method. File transfer protocol of the basic operation steps: ∀ and file transfer protocol clothing Affairs editor on-line, # login each other host, ∃ find necessary files; % definitions are send files the type; & access files, ∋exit The other system. Document transmission, the first login to the other computer, just can undertake and file search, transmission related operation, such as the following documents directory, change the current document catalogue, set transport parameters, transfer files etc, using FTP can obtain any field letter interest resources, still can obtain thousands of computer program software.The FTP connection only being used for searching and transmit various documents, and usually is the literature of full text, allows users to nonlocal calculation In-flight file transfer to this unit hosts, and then set of records to oneself of micro computer reading, printing, or other processing. In the file transfer process, user once found useful information, can immediately they retrieved, sets of record and print them out.130 Telnet (Telnet)This is in the TCP/interconnection Protocol (Transission Control Protocol/Internet Protocol, abbreviation TCP/IP) of communication protocol terminal agreement Telnet, under the support of user's computer through Internet nets temporarily become one Sets the remote computer terminal process. Users first in Telnet command given in the remote computer's communication domain name or IP address, but according to the other system after the inquiry, the key in the user name and password. In the remote computer user, the first to become ubiquitous tasseled legitimate user, and have corresponding account number and password. Remote login step: with the other system online; ∀ # login each other department experience.meanwhile, ∃ decide oneself use terminals, in order to complete simulation type network terminal display data, % of all kinds of resources to the other system using, & exit each other. Once the user login successfully, can be real-time use remote computer opening of all resources. It is unnecessary to consider how far is from another country, users of computer system as connected next door, through remote system as easily as recorded connection, you immediately AD and can search Princeton university library online public readers, as if you were in use directory of the school an online directory public readers terminal. Use this function to use the remote computer on the information resources, to realize information sharing, and can make the information processing. Scientific computing, thus greatly expanded their available resources.2 the indirectly USES the InternetIf well track of the information network, find appropriate database, grasp well below the network information inspectionCable tools can be easier, fully, more effectively on the Internet queried and available information resource.information query software Gop erApril 1991 by the university of Minnesota's earliest development of a menu-driveninteractive type retrieval software, then browse in readers retrieval Internet on the various information resources. Will all kinds of information resources according to the hierarchical menus forms are properly described later to give users access, From top to bottom layers, thus accessing the menu was necessary information. Will the user requests automatically converts FTP or Telnet command, it's common functions are: search text files, The user's query recorded, Call FTP access files.Gopher integrated FTP functions, use Telnet or can be directly obtained menu-driven documents.Veronica (2.2 VeryEasyRodentOriented leads to a Computerized Arc ives) retrieval System This is a based on the pace of Gopher information retrieval system, to Gopher pace menu further index. User input retrieval words, the system will searching out all containing the search term menu items. Veronica tell users you find food single shown below (documents describing levels). Can retrieve out and retrieval model matching menu, so that the user can be directly enter phase shut menu, get necessary information.Jug eadThe basic function and Veronica is same, also be retrieval Gopher pace system of a kind of tool, Veronica's search rangeAre the Gopher pace, and Jughead only check Gopher pace is a particular area.global information nets WWW (Web) number1992 by European particle research center (CERN) launched the based on a super text (Hypertext) multimedia letterCoupon retrieval or query tool, is a menu type browsing tool, is the tree structure, the user can through cadres menu listWay, inquires into his the information she needed. Using the WWW can not only visit Hypermedia (Hypermedia) organization, and informationAnd still can visit Gopher, WAI, FTP, Archie and Usenet on the various information, and can obtain X500 andWhois and other network directory services. It will be located at Internet at different sites related literatures, data and information organically plait knit together, the use requirements, but only put forward inquires where and how to query is composed of query WWW automatically. The WWW searchable online with nearly all of the information resources, namely a link on the Internet computers in zentraedi, WWW software worldwide information immediately illustrated to appear vividly eyes, even with sound color animation or films, videos slice. Library users can be collected in today's world, WWW various hypertext literature, to build a virtual library. WWW retrieval tools (retrieval engine.this earch search) many, such as Yahoo is an excellent collection Engine, can be said to be a huge libraries of directory room, their web site is: HTTP: / /; 1996 mid-may Hong Kong optimal couplet grams international Co., LTD launched high intelligence collection of Chinese Goyoyo, inquires the material when engine, can according to its classification project retrieval, may also directly enter the keywords to find necessary Chinese material, quite convenient, their web site is:http://WWW. Goyoyo. Com.Arc ie document query systemBy Canada MCGILL university develops, allow the user to enter a through may appear in the key needed database nameWord on the Internet to inquires resources. User input keywords, Archie can be automatically query online documentation, and willname descriptorClose inquires the conditions of the database retrieval out. Users are searching the types of files with hope filename, document server (ArchieServer) can point out that in which the FTP server to deposit such documents.For according to index search and find articles according to content with strong function, can use one or more keywords to search rapidly, tulameen bottom of information, can be in millions of database searches for any information Internet service tool, is a kind of keywords search information relevant documents in the host address, document catalogue and filenames) tool, is an information retrieval system, can cycle connected to the world of anonymous FTP server, will these servers offer can carry document file name and path collect together to form Archie database, and through the retrieval procedure for Internet users provide compulsory inspection cable service. Archic search out a file of the corresponding anonymous FTP address, namely tell users you seek filename where (filename level). Can help inquires the carrying specified file or directory anonymous FTP, and returning to our information.2.6 wide-area information server WAIS (Wide AreaInformation Service)Apple Computer, know by Dow Jones Machines and jointly sponsored by know Machines Develop and provide the user inquires the distribution in the Internet on each kind of database of a generic interface software. Is a distributionType information retrieval system, searchable database, involving more than 500 index range of content is great, suitable for searching text files, reading newspapers around the world, scanning all kinds of professional database. Using the WAI than other tools can more accurately retrieving of user's file.Internet 电子信息资源的开发和利用开发和利用Internet 上丰富的电子信息资源, 可直接考虑电子邮件、文件传输、远程登录的途径,也可间接考虑利用各种常用的信息检索工具, 本文分别作了较详细的介绍和分析, 旨在帮助用户很好地使用Internet。
