网工英语10套练习题
Module 10 单元测试题 2
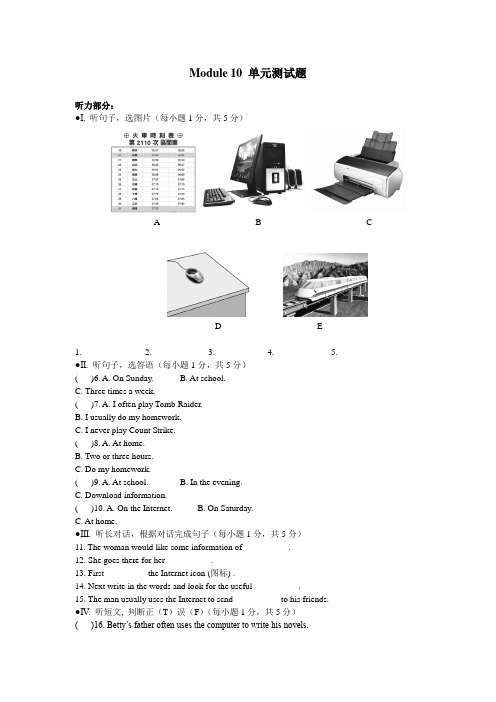
Module 10 单元测试题 听力部分: ●I. 听句子,选图片(每小题1分,共5分)
A B C D E 1.__________ 2.__________ 3.__________ 4.__________ 5.__________ ●II. 听句子,选答语(每小题1分,共5分) ( )6. A. On Sunday. B. At school. C. Three times a week. ( )7. A. I often play Tomb Raider. B. I usually do my homework. C. I never play Count Strike. ( )8. A. At home. B. Two or three hours. C. Do my homework. ( )9. A. At school. B. In the evening. C. Download information. ( )10. A. On the Internet. B. On Saturday. C. At home. ●III. 听长对话,根据对话完成句子(每小题1分,共5分) 11. The woman would like some information of __________. 12. She goes there for her __________. 13. First _________ the Internet icon (图标) . 14. Next write in the words and look for the useful __________. 15. The man usually uses the Internet to send __________ to his friends. ●IV. 听短文, 判断正(T)误(F)(每小题1分,共5分) ( )16. Betty’s father often uses the computer to write his novels. ( )17. Betty usually downloads music from the Internet. ( )18. Betty’s mother usually buys clothes online. ( )19. Sometimes Betty plays computer games on weekends. ( )20. Betty’s little brother gets some information for his homework.
网络信息安全英语练习题

网络信息安全英语练习题### Network Information Security Practice Questions1. Understanding Network Security Basics- Question: What is the primary function of a firewall in network security?- Answer: A firewall's primary function is to monitor and control incoming and outgoing network traffic based on predetermined security rules.2. Types of Network Attacks- Question: Differentiate between a DDoS attack and a phishing attack.- Answer: A DDoS (Distributed Denial of Service) attack overwhelms a website or server with a flood of traffic, making it inaccessible. A phishing attack, on the other hand, involves tricking individuals into revealing sensitive information, such as passwords or credit card numbers, through deceptive emails or websites.3. Cryptography- Question: Explain the difference between symmetric and asymmetric encryption.- Answer: Symmetric encryption uses the same key for both encryption and decryption, making it faster but requiring secure key distribution. Asymmetric encryption uses a pair of keys, a public key for encryption and a private key for decryption, which enhances security but is computationallyslower.4. Secure Communication Protocols- Question: What is SSL/TLS and why is it important for secure communication?- Answer: SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a protocol used to provide secure communication over the internet. It is important because it encrypts data being transmitted, ensuring that it cannot be intercepted and read by unauthorized parties.5. Vulnerability Management- Question: How can organizations manage and mitigate software vulnerabilities?- Answer: Organizations can manage and mitigate software vulnerabilities by regularly updating and patching software, conducting vulnerability assessments, and implementing a strong patch management policy.6. Network Security Policies- Question: What are the key components of a network security policy?- Answer: Key components of a network security policy include access control, password policies, network segmentation, incident response plan, and user education on security practices.7. Wireless Security- Question: What is WPA2 and why is it preferred over WPA for wireless security?- Answer: WPA2 (Wi-Fi Protected Access II) is a securityprotocol for wireless networks that provides stronger encryption and is more secure than WPA. It is preferred dueto its use of the Advanced Encryption Standard (AES), whichis more resistant to hacking attempts.8. Intrusion Detection Systems (IDS)- Question: What is the role of an IDS in network security? - Answer: An IDS monitors network traffic for suspicious activity or policy violations. It can detect and alert administrators to potential intrusions or attacks, allowingfor a timely response to mitigate threats.9. Social Engineering- Question: How can social engineering attacks be prevented?- Answer: Social engineering attacks can be prevented by educating employees about the tactics used in such attacks, implementing strict security policies, and encouraging a culture of skepticism towards unsolicited communications.10. Incident Response- Question: What steps should be taken when a security incident is detected?- Answer: Upon detecting a security incident, stepsshould include isolating the affected system, collecting evidence, analyzing the incident, eradicating the threat, restoring affected systems, and reviewing the incident to improve security measures.11. Data Protection- Question: What measures can be taken to protectsensitive data?- Answer: Measures to protect sensitive data include data encryption, access controls, regular backups, and secure data disposal practices.12. Compliance and Regulations- Question: Why is compliance with data protection regulations important?- Answer: Compliance with data protection regulations is important to protect the privacy of individuals, maintain trust with customers, and avoid legal penalties and reputational damage.Remember, these practice questions are designed to test your understanding of network information security concepts and practices. It is essential to stay updated with the latest security trends and technologies to effectively protect your networks and data.。
10统考英语A试题 网络教育

一、阅读理解First aid is the kind of medical care given to a victim of an accident or sudden sickness before trained medical help can arrive. First aid techniques often are simple. They can be taught to people of all ages. And learning themis important. Knowing how to treat someone in an emergency can mean the difference between life and death.Thousands of persons die each year after eating or drinking poison substances. Experts say most accidental poisonings happen in or near the home. And most are caused by substances we commonly use at home: medical supplies, insect poisons or cleaning fluids. There are several common signs of poisoning: a sudden feeling of pain or sickness, burns in the area of the mouth, or an unusual smell coming from a person's mouth.Health experts generally advise poison victims to drink water or milk. But never give liquids to someone who is not awake or to those having a violent reaction to the poison. Next, seek help from trained medical experts. Save material expelled from the mouth for doctors to examine. Save the container of the suspected poison to answer questions the doctors may have. The container also may describe a substance that stops the poison's effects. Use this substance without delay.The American Red Cross says all homes should have at least three substances to deal with poisoning. One, syrup (糖浆) of ipecac, is a fluid that helps the body expel material from the stomach. Another, activated charcoal (木炭), lessens the danger of poisons. The other material, Epsom salts, helps to speed the release of body wastes. All three should be used only on the advice of a medical expert.1、The phrase "medical supplies" in Paragraph 2 can be replaced by______.A、medicinesB、medical instrumentC、medical deviceD、medical service参考答案:A解析:空空空空空空空空空2、Which of the following statements is NOT true?A、First aid is the medical care given to a victim of an accident or sudden sickness.B、First aid skills often are simple and can be taught to teenagers.C、Syrup of ipecac is a kind of medicine to empty the stomache.D、Health experts generally advise that we should never give liquids to poison victims.参考答案:D解析:3、What is the main purpose of the passage?A、Tell people how to deal with poison.B、Tell people that first aid is essential.C、Tell people how to deal with accidental poisoning.D、Tell people that they can use three substances to deal with poisoning.参考答案:C解析:4、Which of the following is TRUE of a poison victim?A、He will die without first aid.B、He should always drink water or milk.C、He should eat any recommended substances.D、He should be given first aid or resort to medical experts.参考答案:D解析:5、The author states all the following EXCEPT that ______.A、there are thousands of poison victims each yearB、knowing how to treat someone in an emergency is a vital questionC、health experts advise poison victims not to vomit if they were poisoned by a petroleum productD、There are several common signs of poisoning such as a sudden feeling of pain or sickness, or an unusual smell coming from a person's mouth.参考答案:C解析:There’s a great story about an old Finnish woman who, without quite realizing it, was using her cell-phone to access the Internet and track her ci ty’s public transit system. When asked why she used the wireless Internet so frequently, she replied, “What are you talking about? I don’t know anything about this wireless Internet stuff. I just know the bus is here.”Regardless of whether you want to admit it, a lot of us are like that old Finnish woman. When it comes to new mobile applications, many of us do not realize the capability and power that we hold, literally, in our hands.What we are looking at today is the mobile Internet in its infancy. Now that using the Internet from home or work has saturated much of society, the next logical step is to be able to use the Net when you are far away from your desktop or laptop. Speech recognition is one way to do this, and there are a number of services, col lectively called the “voice Web”, that will make this possible. All you do is to use a phone or wireless device to call a phone number, and speak commands to an intuitive system. It will then give you the information you’re seeking, using either a synthesi zed voice or an audio file.In the United States and Europe, the hot technology for wireless devices is called WAP (Wireless Application Protocol), which is being considered as the world standard. WAP is supported by major phone companies including Nokia, Motorola and Ericsson, and is simply a means of transmitting information, much like HTML which is a means of communicating on the Internet.Currently, wireless Internet connections may give you news, sports scores, stock quotes, and the weather if you’re lucky. But if you’ve ever used this technology, you know it’s slow, costly and doesn’t seem worth the time and effort, if it works at all. All of this technology points to easier living. Perhaps you’ll need to find a restaurant for an occasional businessme eting. You’ll press a button on your mobile phone, and access the Internet to pull up a list of great restaurants in your immediate area. You’ll hit another button, say a few words into the handset and you’ve got a reservation for four.6、The author uses the story of an old Finnish woman to indicate that __________.A、she is ignorant of some common knowledgeB、public transit system contains the accessory to InternetC、many people are unaware of the function of the new appliances being usedD、the Internet is experiencing rapid growth参考答案:C解析:7、The word “saturate” (Para. 3) most probably means _________.A、stateB、utilizeC、despiseD、fill参考答案:D解析:8、According to the text, WAP is a __________.A、technology standard set by major phone companiesB、substitution of HTML which can be applied on the InternetC、means of exchanging informationD、software application for transmitting voice over telephone lines参考答案:C解析:9、We can infer from the passage that the mobile Internet is different from the previous Internet in that the former __________.A、can be accessed by desktop computersB、has no need for wire appliancesC、can be used to book a table in a restaurantD、is equipped with speech recognition systems参考答案:B解析:10、What is the attitude of the author towards the future of mobile Internet?A、IndifferentB、NeutralC、OptimisticD、Pessimistic参考答案:C解析:二、词汇与语法11、The two friends shared a _______ interest in stamp collecting.A、commonB、generalC、popularD、usual参考答案:A解析:12、_______ the fact that his initial experiments had failed, Prof. White persisted in his research.A、Because ofB、As toC、In spite ofD、In view of参考答案:C解析:13、Only after he has acquired considerable facility in speaking _______ to learn to read and write.A、he beganB、will he beginC、did he beginD、must he begin参考答案:B解析:14、Not only _______ our money, but we were also in danger of losing our lives.A、we lostB、lost weC、we did loseD、did we lose参考答案:D解析:15、That poorly dressed old man felt quite ________ at such a big party attended by many important figures.A、in the wayB、out of the wayC、out of placeD、in place参考答案:C解析:根据句意,此处应该选C,大概的句意是“…老人在…宴会上感到不自在”。
网络信息安全英语练习题

网络信息安全英语练习题网络信息安全是现代社会中一个非常重要的议题,它涉及到保护数据不被未授权访问、修改、破坏或泄露。
以下是一些英语练习题,旨在帮助学生更好地理解和掌握网络信息安全的相关概念。
1. Multiple Choice Questions (选择题)Choose the correct answer from the options provided.a) What does "cybersecurity" refer to?- A) The study of cybernetics- B) The practice of protecting information systems from theft or damage- C) The design of computer networks- D) The creation of cyberspaceb) Which of the following is a common method used by hackers to gain unauthorized access to a system?- A) Social engineering- B) Social networking- C) Social media marketing- D) Social sciencec) What is a "firewall"?- A) A physical barrier to prevent fire from spreading- B) A software or hardware that monitors and controlsincoming and outgoing network traffic- C) A type of antivirus software- D) A network protocold) What is the purpose of "encryption" in cybersecurity?- A) To make data unreadable to unauthorized users- B) To increase the speed of data transmission- C) To reduce the size of data files- D) To improve the quality of network connections2. Fill in the Blanks (填空题)Fill in the blanks with the appropriate words from the list provided.- breach, protocol, phishing, malware, vulnerabilitya) A computer virus is a type of _______ that can cause damage to a system or steal information.b) An email that appears to be from a legitimate source butis actually designed to trick the recipient into revealing sensitive information is known as _______.c) A _______ is a set of rules governing the format and transmission of data over a network.d) A _______ in a system is a weakness that can be exploited by an attacker.e) A _______ of data security occurs when unauthorized accessis gained, often resulting in data loss or corruption.3. True or False (判断题)Determine whether the statements below are true or false.a) Two-factor authentication is a security measure that requires two different methods of verification to access a system. (True / False)b) Public Wi-Fi networks are always secure and safe to usefor online banking. (True / False)c) A strong password should include a mix of upper and lower case letters, numbers, and special characters. (True / False)d) It is not necessary to update software regularly because updates are only for new features. (True / False)e) VPNs (Virtual Private Networks) can provide an extra layer of security by encrypting internet traffic. (True / False)4. Short Answer Questions (简答题)Answer the following questions in a few sentences.a) What is the significance of using strong passwords?b) Explain the concept of "zero-day" vulnerabilities.c) How can users protect themselves from phishing attacks?d) What are some best practices for maintaining network security at home?e) Describe the role of a cybersecurity analyst.These exercises are designed to test and reinforce knowledge on various aspects of network information security. By practicing with these questions, students can enhance their understanding of the subject and be better prepared to tackle real-world cybersecurity challenges.。
网络教育英语统考练习题与答案

⽹络教育英语统考练习题与答案⼤学英语B统考模拟试题及专项练习⼤学⽹络教育学院2009年11⽉⽬录⼤学英语B统考模拟题 (2)⼤学英语B统考模拟试题(⼀) (2)⼤学英语B统考模拟试题(⼆) (8)⼤学英语B统考模拟试题(三) (14)⼤学英语B统考模拟试题(四) (19)⼤学英语B统考模拟试题(五) (25)⼤学英语B统考模拟试题(六) (30)⼤学英语B统考模拟试题(七) (36)⼤学英语B统考模拟试题(⼋) (43)⼤学英语B统考模拟试题(九) (51)⼤学英语B统考模拟试题(⼗) (60)⼤学英语B统考模拟试题(⼗⼀) (68)⼤学英语B统考模拟试题(⼗⼆) (76)⼤学英语B统考模拟试题(⼗三) (85)⼤学英语B统考模拟试题(⼗四) (93)⼤学英语B统考模拟试题(⼗五) (101)⼤学英语B统考模拟试题(⼗六) (109)⼤学英语B统考模拟试题(⼗七) (117)⼤学英语B统考模拟试题(⼗⼋) (127)⼤学英语B机考专项练习 (135)专项练习(⼀) (135)专项练习(⼆) (138)专项练习(三) (141)专项练习(四) (146)专项练习(五) (148)专项练习(六) (154)⼤学英语B统考模拟题⼤学英语B统考模拟试题(⼀)I. Conversations:Choose the right answer to finish each of the following conversations. (共5⼩题;每⼩题3分,满分15分)1. –Thanks for your help.– ___A_____________A. My pleasure.B. Never mind.C. Quite right.D. Don’t ask me.2. —Hi, welcome back. Had a nice trip?— ____A_____________.A. Oh, fantastic! Fresh air, and sunshine every day.B. Come on, I’ve got lots of fun.C. By the way, I don’t like swimming very much.D. Well, I look forward to your invitation.3. –Oh, sorry to bother you.–_________A_________.A. That’s Okay.B. No, you can’t.C. That’s good.D. Oh, I don’t know.4. — How do you do? Glad to meet you.— ________B_____________.A. Fine. How are you?B. How do you do? Glad to meet you, too.C. How are you? Thank you!D. Nice. How are you?5. –How was your trip to London, Jane?– ________A_____________A. Oh, wonderful indeed.B. I went there alone.C. The guide showed me the way.D. By plane and by bus.II. Reading Comprehension (共10⼩题;每⼩题3分,满分30分)Each of the following two passages is followed by some questions or unfinished statements. For each of them there are fourchoices marked A, B, C, and D. Decide on the best choice.Brief Overview:Thailand is a rush for your senses: a bustling, exotic(异国情调的), and vividculture that never ceases to amaze visitors. On this cultural tour, you’ll visitThailand’s gilded temples, one more gorgeous than the n ext, in the cities of Bangkok,Ayutthaya, and Chiang Mai. Other highlights include a cruise through Bangkok’scanals, a visit to a rural hill tribe village, riding elephants through the jungleand exciting shopping opportunities in Chiang Mai’s famous nigh t bazaar.Continue to Cambodia, where you’ll visit the bustling capital of Phnom Penh.Tour the Royal Palace with its dazzling Silver Pagoda. Then it’s on to Angkor Wat,where you have two days to explore the spectacular carved stone temples of this WorldHeritage site.Features of this trip:Exclusive tour, guided privately by a multilingual guide throughout the trip.Customize your own itinerary(路线)to create a holiday of your dream.Designed for 4 to 5 star luxury accommodation and services. Hotels can be changedto lower budget.Depart and return whenever you choose – shorten or lengthen the tour to suityour wishes.Outstanding value, costing you 25-30% less than similar guided tours of the sameflexibility and quality.Group discounts are available. Call 020 7430 1766NOTE: Prices shown are effective as of date of publication of web page, and aresubject to changes due to currency fluctuations, changes in availability, seasonalincreases or variations in local costing at the time of booking.6. This ad is most probably made for ___B___.A. a private guideB. a travel agencyC. a countryD. a hotel7. In which of the following cities can a visitor shop in a night bazaar?CA. Bangkok.B. Phnom Penh.C. Chiang Mai.D. Ayutthaya.8. Which of the following activities shouldn’t a visitor do in Cambodia?CA. Visiting the capital.B. Touring the royal palace.C. Riding elephants.D. Traveling to a world heritage.9. Which of the following statements is true?DA. Pity this cultural tour is limited to only 10 days.B. Start prices cover all the fees including accommodation, services and flight.C. Anyone who wants to get a discount may call 020 7430 1766.D. This tour is said to be fairly easy and comfortable.10. Start prices are influenced by the following EXPECT ___A____.A. the local living conditionsB. currency fluctuationsC. changes in availabilityD. variations in local costingPassage 2The greatest recent changes have been in the lives of women. During the twentieth century there was an unusual shorteningof the time of a woman’s life spent in caring for children. A woman who got married at the end of the 19th century wouldprobably have been in her middle twenties, and would be likely to have seven or eight children, of whom four or five lived tillthey were five years old. By the time the youngest was fifteen, the mother would have been in her early fifties and wouldexpect to live a further twenty years, during which custom, chance and health made it unusual for her to get paid work. Todaywomen get married at a younger age and have fewer children. Usually a woman’s youngest child will be fifteen when she isforty-five and is likely to take paid work until retirement at sixty. Even while she has the care of children ,her work is lightenedby household appliances(家⽤电器)and convenience foods.
计算机英语试题及答案

计算机英语试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a programming language?A. JavaB. C++C. PythonD. Photoshop2. What does CPU stand for?A. Central Processing UnitB. Central Power UnitC. Central Printing UnitD. Central Programming Unit3. What is the full form of HTML?A. Hyper Text Markup LanguageB. Hyper Text Markup LanguageC. Hyper Text Markup LanguageD. Hyper Text Markup Language4. In computer networking, what does IP stand for?A. Internet ProtocolB. Internet ProgrammingC. Internet ProviderD. Internet Processor5. What is the primary function of a router?A. To print documentsB. To store dataC. To connect multiple networksD. To provide internet access6. Which of the following is a type of database management system?A. MS WordB. MS ExcelC. MS AccessD. MS PowerPoint7. What does the acronym RAM stand for?A. Random Access MemoryB. Rapid Access MemoryC. Remote Access MemoryD. Real Access Memory8. What is the term for a collection of data stored in a computer in a structured format?A. FileB. DocumentC. DatabaseD. Folder9. Which of the following is not a type of computer virus?A. TrojanB. WormC. AntivirusD. Ransomware10. What does the term "bandwidth" refer to in the context ofinternet usage?A. The width of the cableB. The speed of data transferC. The number of usersD. The quality of the connection二、填空题(每题2分,共20分)1. The basic unit of data in computing is called a ________.2. A ________ is a type of software that is designed to prevent, detect, and remove malware.3. The process of converting data into a form that can be easily transmitted or stored is known as ________.4. A ________ is a hardware device that allows a computer to connect to a network.5. The term "cybersecurity" refers to the practice of protecting systems, networks, and programs from ________ and other types of cyber attacks.6. A ________ is a collection of related data and the way it is organized.7. The ________ is a type of computer memory that retains data even when the power is off.8. The process of finding and fixing errors in a program is known as ________.9. A ________ is a type of software that allows users to create and edit documents.10. The ________ is a set of rules that define how data is formatted, transmitted, and received.三、简答题(每题10分,共30分)1. Explain the difference between a server and a client in a network.2. Describe the role of an operating system in a computer system.3. What are the key components of a computer system?四、论述题(每题30分,共30分)1. Discuss the importance of data backup and recovery in a computer system.答案:一、选择题1. D2. A3. A4. A5. C6. C7. A8. C9. C10. B二、填空题1. bit2. Antivirus3. Encoding4. Network Interface Card (NIC)5. unauthorized access6. Database7. Hard disk8. Debugging9. Word processor10. Protocol三、简答题1. In a network, a server is a computer system or device that provides resources or services to other computers, known as clients. The server manages network traffic, centralizes data storage, and provides access to shared resources, while the client is a computer that requests and uses these resourcesor services.2. An operating system is the software that manages computer hardware, software resources, and provides services for computer programs. It acts as an intermediary between theuser and the computer hardware, allowing users to interactwith the computer without needing detailed knowledge of the hardware.3. The key components of a computer system include thecentral processing unit (CPU), memory (RAM), storage devices (hard disk, SSD), input devices (keyboard, mouse), output devices (monitor, printer), and peripheral devices (scanner, webcam).四、论述题1. Data backup and recovery are critical in a computer system because they ensure that data is preserved in case ofhardware failure, data loss, or cyber attacks. Regularbackups allow for the restoration of data to a previous state, minimizing downtime and potential loss of information. This process is essential for maintaining business continuity and protecting against data loss.。
大学英语1网上测试题1-10章
大学英语1网上测试题1-10章大学英语1网上测试题11、Our English teacher advises us to look _B__our test paper before we hand it in.A、afterB、overC、onD、into2、Our house is about a mile from the railway station and there are not many houses _A__ .A、in betweenB、far apartC、among themD、from each other3、Mary wanted to avoid running down a dog but ran _A__a big tree by the roadside.A、intoB、onC、overD、up4、What is the train _C__to Shanghai?A、feeB、tipC、fareD、cost5、—Hello, I’m John Smith. —Hello, my name is Charles Miller, but_C__.A、call my CharlesB、call me at CharlesC、call me CharlesD、call Charles1.B.look over 查看;检查2.A.run into - 碰上想避开狗,却碰到树上了。
3.Ctrain fare火车票价4.C问他怎么样了,怎么了,他说还不算太坏,意思就是他还好5.D最近怎么样?和以前一样大学英语1网上测试题21、It does not alter the fact that the manwas _C__for the death of the little girl.A. accountB. guilty,C. responsible,D. obliged,the man是补足语,做题时刻将其忽略,那么这句话变为...he was ___ for the death of the little girl.A. account有认为的意思。
初中网络英语能力测试试题
精品文档 2016 1 / 6
初中网络英语能力测试试题 I 语音与拼写(0.5*10)A 从A B D 中找出下列单词黑体部分读音不相同的选项。 1. A. lud B. enugh . suth D. uth2. A. wndered B. happened . pulled D. tuhed3. A. salt B. already . always D. anial4. A.aths B.lthes .thirty D.thank5. A.nse B .hpe .ve D.pstB,选择正确答案,将单词拼写完整。6. prn __ n __ tin A.;ie B.u;ai . u; ia D.au;a7. g __ ner. A.e;a B.e;e .a;e D.a;a8. __ ent A.nu B. une .ne D.anu9.1___stA. B.a .u D.a10.t__w_ A.a; rds B.;a .; D.a;aII 单项选择(1*25)11. Be areful when yu are rssing the street. A. G fast B. Dnt stp Dnt run D. Lk ut12. Is there anyne in the r? A. sene B. anybdy . everything D. anything13. T shuted ut," Be areful!" A. laughed B. alled . siled D. fund14. The yung an was brave when he fught against the thief. A, quik B. strng . fearless D. angry15. A true an fears nthing. A. real B. brave . sad D. happy16. She was srry fr getting t shl s late. B. heard fr . regretted D. pardned17. e have enugh tie and we neednt d the wrk in suh a hurry.A. any B. plenty 精品文档 2016 2 / 6
大学英语网络测试题及答案
Part 2 Understanding Short Conversations(每小题:1 分)Directions: In this section you'll hear some short conversations. Listen carefully and choose the best answer to the questions you hear.1.A. Put on some soft music.B. Relax a spell.C. Listen to soft music.D. Go to work.2.A. The woman is 5 minutes late.B. The woman doesn't know what to say.C. The woman has eaten her lunch already.D. The woman is hungry.3.A. The woman is very lucky.B. The woman is offering a class.C. The man isn't in the job center class.D. The man isn't happy with his boss.4.A. The man is terrible.B. The man didn't realize what he had done.C. The man didn't step on the woman's foot.D. The man was taught good manners by his parents.5.A. Tests aren't so important.B. His test score wasn't worse than the last time.C. He knows enough for the next test.D. He does not have to take tests any more.Part 3 Understanding Long Conversations(每小题:1 分)Directions: In this section you'll hear a long conversation or conversations. Listen carefully and choose the best answer to the questions you hear.Questions 1 to 5 are based on the same passage or dialog.1.A. Fundamental skills.B. Thoughtful people.C. Job interviews.D. Service work.2.A. Those who appear friendly.B. Those who are thoughtful.C. Those who are good at sales.D. Those who are talkative.3.A. The direct observations made.B. The candidate's personality.C. The ability to be friendly and talkative.D. The ability to be thoughtful and quiet.4.A. The fundamental skills a person has.B. The requirements of the position.C. The personality of a person.D. The person's distinct characteristics.5.A. The man has more experience than the woman.B. The man performs his job well.C. The woman understands what is really required.D. The woman has the fundamental skills to perform well.Questions 6 to 10 are based on the same passage or dialog. 6.A. The woman's sick feeling.B. The woman's weight gain.C. The woman's poor mood.D. The woman's lunch.7.A. He tells it as a joke.B. To help the woman relax.C. To frighten the woman.D. to teach the woman a lesson.8.A. 4.B. 3.C. 2.D. 1.9.A. The woman doesn't like horror films.B. The woman has gained too much weight.C. The woman has emptied herself out.D. The woman doesn't usually eat so much.10.A. Hamburgers.B. The horror film.C. Taking a walk.D. The toilet.Part 4 Understanding Passages(每小题:1 分)Directions: In this section you'll hear a passage or passages. Listen carefully and choose the best answer to the questions you hear.Questions 1 to 5 are based on the same passage or dialog.1.A. An old woman going to Open University.B. An old woman going to Manchester University.C. An old woman teaching about World War Two.D. An old woman studying banking.2.A. Polishing her furniture.B. Improving her knowledge.C. Enjoying money and freedom.D. Teaching wonderful students.3.A. The Second World War.B. The entrance examination.C. Her hard work.D. Her housework.4.A. At least 6 years.B. Less than 2 years.C. Less than 1 year.D. Exactly 3 years.5.A. Difficulty courses.B. Bad eyesight.C. Failing memory.D. Obtaining a degree.Questions 6 to 10 are based on the same passage or dialog. 6.A. The career of a boxer.B. The best fighters in the world.C. People who are blind.D. A newspaper reporter.7.A. 18 years.B. 38 years.C. 24 years.D. 41 years.8.A. News reporters weren't able to track down Langford.B. Langford was forgotten, even when in his peak.C. Langford won more fights as a lightweight.D. People are unsure as to Langford's exact record.9.A. Author of a best-seller.B. A reporter for a New York newspaper.C. One of the best fighters in the world.D. Someone who fought Langford.10.A. They have forgotten about him.B. They think he is one of the greatest.C. They think he is the best black prizefighter.D. They think he is considered greater than he was.Questions 11 to 15 are based on the same passage or dialog.11.A. A King County Executive.B. The development of a state.C. The governor's plan.D. Efforts to help the environment.12.A. 20 pages.B. 50 pages.C. 80 pages.D. 176 pages.13.A. Sims' plan will affect the average person's life.B. Sims' plan will never be accepted by the public.C. Sims' plan has already been accepted by the Governor.D. Sims' plan is likely to cripple the economy.14.A. Sims' plan.B. State plans.C. The economy.D. The state.15.A. The government is not responding to immediate needs.B. The region must adapt to rising sea levels.C. Change is going to be difficult for people.D. Energy production is harming the fish.Part 5 Fill in the Blanks (with the right preposition or adverb)(每小题:1 分)Directions: Fill in the blanks in the following sentences with an appropriate preposition or adverb. Fill in each blank with only ONE word.1.The first time you step out, whether by accident or2.You will thus benefit from being clear in what you are aimingnot.3.We began our difficult task without once reflecting4.Money was being spent, but it could all be accounted5.and was not lost outside after all.Part 6 Multiple Choice(每小题:1 分)Directions: Choose the best answer from the four choices marked A, B, C and D.1.His health ________ as he ate too little and worked too hardfor months on end.A. broke upB. broke throughC. broke downD. broke off2.After the meeting the workers went back to their ________workshops.A. respectableB. respectiveC. respectfulD. respected3.He has an excellent ________ as a criminal lawyer.A. popularityB. fameC. regardD. reputation4.The patient cannot but ________ the doctor's instructions,though he doesn't think it necessary.A. followingB. to followC. followD. followed5.The fifth generation computers, with artificial intelligence,________ and perfected right now.A. developedB. have developedC. will have been developedD. are being developedPart 7 Cloze (with four choices provided)(每小题:0.5 分)Directions: Read the following passage carefully and choose the best answer from the four choices given for each blank. Questions 1 to 20 are based on the following passage.To get a job, you really need to know a lot about the person who ismaking the hiring decision. What will it take to 1.that person to hire you? For example, I have a Master's degree in2.field does not 3. 4.possess more 5.these 6.7.8.makes the 9.basing his decision on your skills. That is, he is not choosing youbased on your abilities, 10.you or not. If he actually 11.get angry. It would be considered an illegal hiring 12.undergraduate degree have 13.jobs. This is because I apparently am too 14.That really means the hiring manager didn't like my 15.ridiculous. I have 16.Part 8 Reading Comprehension (Banked Cloze)(每小题:1 分)Directions: Fill in the blanks in the following passage by selecting suitable words from the Word Bank. You may not use any of the words more than once.Questions 1 to 10 are based on the following passage.There is some argument against the whole idea of developing tests to measure a person's Emotional Intelligence. Tosuggest that psychologists and educators might be able to 1.tests is silly. It is simply 2.impossible task. One is that we haven't even begun to 3.comes to the brain. Setting up tests to tell how far a persongets in life is irresponsible 4.knowledge. Those who measure Emotional Intelligence areattempting to determine how well a person can 5.have been designed according to their own understanding,and biases (偏差) are inevitable. The world is far too vast toever 6.possibilities. Truly, to believe that the questions for such atest could be made to be 7.influenced by one's culture and educational background, issimply wrong. Tests that are not objective have a real 8.should rely heavily upon test results from a series ofquestions which are 9.a person's ability to solve 10.problems is a good thing. However, thinking that we canscore a person's EQ is wrong.o my profession. I have learned the most 17.out that I know too much to be 18.company. I should have spent my time 19.what these managers really wanted into my personality. I could've learned all of the trifles so that other people might think that I 20.served me better than actually learning how to do my job.Part 9 Reading Comprehension (Multiple Choice)(每小题:2 分)Directions: Read the following passages carefully and choose the best answer from the four choices marked A, B, C and D.Questions 1 to 5 are based on the same passage or dialog. Since the dawn of human ingenuity (独创性), people have devised greater and greater tools to cope with work that is dangerous, boring, burdensome, or just plain nasty. That compulsion (强制) has resulted in attempts to make robots, machines with human capabilities. And if scientists have yet to create the mechanical version of science fiction, they have begun to come close.As a result, the modern world is increasingly full of intelligent gizmos whose presence we barely notice but whose universal existence has removed much human labor. Our factories hum (忙碌) to the rhythm of robot assembly arms. Our banking is done at automated teller terminals that thank us with mechanical politeness for the transaction. Our subway trains are controlled by tireless robot drivers. And thanks to the continual miniaturization (小型化) of electronics and micro-mechanics, there are already robot systems that can perform some kinds of brain and bone surgery with perfect accuracy—far greater precision than highly skilled physicians can achieve with their hands alone.But if robots are to reach the next stage of laborsaving utility, they will have to operate with less human supervision and be able to make at least a few decisions for themselves-goals that pose a real challenge. "While we know how to tell a robot to handle a specific error," says Dave Lavery, manager of a program at NASA, "we can't yet give a robot enough 'common sense' to reliably interact with a dynamic world."Indeed the quest for true artificial intelligence has produced very mixed results. Despite a spell of initial optimism in the 1960s and 1970s when it appeared that transistor (晶体管) circuits might be able to copy the action of the human brain by the year 2010, researchers lately have begun to extend that forecast by decades if not centuries.1.Human ingenuity was initially demonstrated in ________.A. the use of machines to produce science fictionB. the wide use of machines in manufacturing industryC. the invention of tools for difficult and dangerous workD. the clever tackling of dangerous and boring work2.The word "gizmos" (paragraph 2) most probably means________.A. programsB. expertsC. devicesD. creatures3.According to the text, what is beyond man's ability now is todesign a robot that can ________.A. fulfill delicate tasks like performing brain surgeryB. interact with human beings orallyC. have a little common senseD. respond independently to a changing world4.What does the author think?A. Robots will always require supervision.B. People have both successes and failures with robots.C. The making of robots will always meet mixed successes.D. Robots and people should never be mixed.5.What made people optimistic about robots?A. Transistor circuits.B. The 60s and 70s.C. Researchers.D. The human brain.Questions 6 to 10 are based on the same passage or dialog. Could the bad old days of economic decline be about to return? Since OPEC agreed to supply-cuts in March, the price of crude oil has jumped to almost $26 a barrel, up from less than $10 last December. This near-tripling (几乎三倍) of oil prices calls up scary memories of the 1973 oil shock, when prices quadrupled (四倍的), and 1979-1980, when they also almost tripled. Both previous shocks resulted in double-digit inflation and global economicdecline. So where are the headlines warning of gloom (沮丧) and doom (厄运) this time?Yet there are good reasons to expect the economic consequences now to be less severe than in the 1970s. Rich economies are less dependent on oil than they were, and so less sensitive to swings in the oil price. Energy conservation, a shift to other fuels and a decline in the importance of heavy, energy-intensive industries have reduced oil consumption. Software, consultancy and mobile telephones use far less oil than steel or car production. For each dollar of GDP (in constant prices) rich economies now use nearly 50% less oil than in 1973. The OECD estimates in its latest Economic Outlook that if oil prices averaged $22 a barrel for a full year, compared with $13 in 1998, this would increase the oil import bill in rich economies by only 0.25-0.5% of GDP. That is less than one-quarter of the income loss in 1974 or 1980. On the other hand, oil-importing emerging economies—to which heavy industry has shifted—have become more energy-intensive, and so could be more seriously squeezed.One more reason not to lose sleep over the rise in oil prices is that, unlike the rises in the 1970s, it has not occurred against the background of general product-price inflation and global excess demand. A sizable portion of the world is only just emerging from economic decline.6.What does the author describe as frightening?A. The 1973 oil shock.B. Global economic decline.C. The gloom and doom of this time.D. OPEC supply-cuts.7.What are newspapers having people believe?A. The rise in oil is going to cause serious problems.B. The economy is going to get better.C. Oil prices are going to triple.D. Energy conservation is necessary.8.What has new technology lead to?A. Double-digit inflation.B. Reduced oil dependency.C. Steel production.D. Energy conservation.9.Why does the author tell us "not to lose sleep"?A. We will need energy from sleep.B. Worrying will not help.C. We need not worry.D. People will be seriously squeezed in the future.10.From the text we can see that the writer seems ________.A. optimisticB. sensitiveC. sadD. scared。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
第1页 网工英语10套练习题 ISDN,which stands for Integrated Services Digital Network, is a system of digital phone connections, which has been available for over a decade.This system allows data to be transmitted simultaneously across the world using (1) digital connectivity.With ISDN,voice and data are carried by bearer channels occupying a bandwith of (2) (bits per second).Some switches limit B channels to capacity of 56 Kbps.A data channel (3) handles signaling at 16Kbps or 64Kbps,depending on (4) .Note that,in ISDN terminology,”k” means (5),and not 1024(2^10) as in many computer applications;therefore,a 64Kbps channel carries data at a rate of 64000bps. A new set of standard prefixes has recently been created to handle this. Under this scheme,”K”(Kilo) means 1000(10^3),”M” (Mega) means 1000000(10^6),and soon ,and “Ki”(Kibi) means 1024 (2^10),”Mi” (Mebi) means 1048576(2^20).and soon。 (1). A.Multi-ends B.circle C.indirect D.end-to-end (2). A.34 Kbps B. 84 Kbps C. 64 Kbps D. 54 Kbps (3). A.D channel B.A channel C.B channel D.C channel (4). A.the method B.the number C.the service type D.the user type (5). A.100000(10^5) B.1000(10^3) C.10000(10^4) D.100(10^2)
答案: 1:D,2:C,3:A,4:C,5:B
Bluetooth is a universal radio interface in the (1) frequency band that enables portable celectronic devices (2) connect and 第2页
communicate (3) via short range,ad hoc networks.Each unit can simultaneously communicate with up to (4) other units per piconet. Moreover,each unit can simultaneously (5) to several piconets,Bluetooth technology which apart from Ericsson,has gained the support of Nokia,IBM,Toshiba,Intel and many other manufactures,eliminates the need for wires,cables and connectors for and between cordless or mobile phones,modems,headsets,PDAs,Computes,printers,progjectors,local ares networks,and so on ,and paves the way for new and completely different devices and applications. (1). A.2.45GHz B. 4.45GHz C. 2.95GHz D. 3.45GHz (2). A.in B. on C. to D. with (3). A.narrowly B.wirelessly C.freely D.widely (4). A.use B.sever C.host D.base (5). A.relate B.add C.close D.belong 答案:1:A,2:C,3:B,4:B,5:D
(1)is used to ensure the confidentiality,integrity and authenticity of the two end points in the private network .the(2),an application layer protocol,authenticates each peer in an IPsec transaction ,IKE negotiates security policy,determining which algorithm may be used to set up theRunnel .It also handles the exchang of session keys used for that one transaction.Networks that use (3)to secure data traffic can automatically authenticate devices by using (4) whichVerify the identities of the two users who are sending 第3页
information back and forth .IPsec can be ideal way to secure data in large networks that require (5) connections among many devices。 (1) A.Encryption B.Code C.Certificate D. Tunnel (2) A.associated links B.Internet Key Exchange C IPsec D. encryption (3) A authenticity B.password C.IPsec D. Internet Key Exchange (4) A.protocols B.keywords C.IKE D. digital certificates (5) A.free B.strict C.secure D.remote 答案:1:A,2:B,3:C,4:D,5:C
LAPB is a (1) protocol that provides complete data transparency in a (2)operation. It supports a peer-to-peer link in that neither end of the link plays the role of the permanent master station. HDLC LAPB is the (3)that is usually used by(4), the (5)standard for Packet Switched Networks. (1)A.bit-oriented synchronous B.byte-oriented synchronous C.bit-oriented asynchronous D.byte-oriented asynchronous (2)A.half-duplex point-to-point B.half-duplex point-to-points C.full-duplex point-to-point D.full-duplex point-to-points (3)A.Physical Layer B.Link Layer C.Network Layer D.Transport Layer (4)A.X.21 B.X.25 C.X.28 D.X.29 (5)A.ITU B.IEEE C.OSI D.ANSI 答案:1:A,2:C,3:B,4:B,5:A Data communications equipment(DEC) (1) the serial data stream from
the DTE and converts it to some form of (2) suitable of transmission on voice grade lines. At the (3),the DCE performs the reverse function of convering the received analog signal to serial digital data stream .The simplest form of DCE is a (4) or data set . At the transmit end, the modem can be considered a form of (5),while at the receive end, it can be considered a form of analog to
