FALLS MANAGEMENT FILE
克罗韦尔 P.DATA主处理器模块 数据表

AllenĆBradleyMain Processor Module(Cat. No. 1775-L1, -L2)Product DataDescriptionThe main processor module is used in PLC-3 programmable controllersystems to provide:program executionmemory managementThe module occupies two slots in the processor chassis. We recommendthat you install the module in the two, left-most slots. The module receivesits power and communicates with other modules through the PLC-3 chassisbackplane.Two main processor modules are available for your PLC-3 system:cat. no. 1775-L1cat. no. 1775-L212Both main processor modules contain many of the same features (table A). One of the major differences between the two modules is the level of program instructions they are able to execute. The cat. no. 1775-L1 processor module uses the “level 1” instruction set; the 1775-L2 uses the “level 2” instruction set. Refer to table B for a listing of the level 1 and 2 instructions sets.Table ABenefits, Features, and Functions3Table BPLCĆ3 Level 1 and 2 Instruction Sets4Program ExecutionTo provide effective program execution, the main processor module: uses AMD 2903 bit-slice microprocessorsmaintains an on-board I/O image table for high-speed processing of I/O pointsquickly determines if the outputs are true or false using a high-speed program scanning techniqueMemory ManagementThe memory in the main processor module is divided into dedicated, expandable areas:system statussystem pointersmodule statusdata tableuser programmessagessystem symbolsforce tableThis type of memory configuration allows you to:effectively handle a wide variety of applicationseasily increase the size of memory as your application needs changeFlexible Data TableThe data table is one of the most important areas of memory. It is completely expandable provided the memory space is available. The data table consists of the following sections:output imageinput imagetimercounterinteger5floating point (available on the cat. 1775-L2 module only)decimal binary ASCIIhigh order integer (available on the cat. no. 1775-L2 module only)pointer statusLocation Environmental ConditionsG Two, leftĆmost slots(recommended location)MicroprocessorsG 4 AMD 2903's (bit slice)Current Requirements G 9.4A at +5V DC G 40ma at +15V DCG Operating Temperature:0 to 60°C (32 to 140°F)G Storage Temperature:Ć40 to 85° C (Ć40 to 185° F)G Relative Humidity:5 to 95% (without condensation)© 1986 Allen-Bradley CompanyPLC is a registered trademark of Allen-Bradley CompanySpecifications6With offices in major cities worldwideWORLDHEADQUARTERS Allen-Bradley1201 South Second Street Milwaukee, WI 53204 USA Tel: (1) 414 382-2000Telex: 43 11 016FAX: (1) 414 382-4444EUROPE/MIDDLE EAST/AFRICA HEADQUARTERSAllen-Bradley Europe B.V .Amsterdamseweg 151422 AC Uithoorn The Netherlands Tel: (31) 2975/43500Telex: (844) 18042FAX: (31) 2975/60222ASIA/PACIFIC HEADQUARTERSAllen-Bradley (Hong Kong)LimitedRoom 1006, Block B, Sea View Estate 28 Watson Road Hong KongTel: (852) 887-4788Telex: (780) 64347FAX: (852) 510-9436CANADAHEADQUARTERS Allen-Bradley Canada Limited135 Dundas StreetCambridge, Ontario N1R 5X1CanadaTel: (1) 519 623-1810FAX: (1) 519 623-8930LATIN AMERICA HEADQUARTERS Allen-Bradley1201 South Second Street Milwaukee, WI 53204 USA Tel: (1) 414 382-2000Telex: 43 11 016FAX: (1) 414 382-2400As a subsidiary of Rockwell International, one of the world’s largest technologycompanies — Allen-Bradley meets today’s challenges of industrial automation with over 85 years of practical plant-floor experience. More than 11,000 employees throughout the world design, manufacture and apply a wide range of control and automation products and supporting services to help our customers continuously improve quality, productivity and time to market. These products and services not only control individual machines but integrate the manufacturing process, while providing access to vital plant floor data that can be used to support decision-making throughout the enterprise.Publication 1775-2.2 — December, 1984Supersedes Publication 1775-901 — February, 1982PN955096-55。
文件管理制度英文

文件管理制度英文1. PurposeThe purpose of this File Management Policy is to establish guidelines for the proper creation, management, storage, and retention of electronic and physical files within the organization. This policy aims to ensure that all files are organized, secure, and easily accessible to authorized individuals.2. ScopeThis policy applies to all employees, contractors, and third-party vendors who create, manage, or access files on behalf of the organization. It covers electronic files stored on servers, databases, and other digital platforms, as well as physical files kept in office spaces or off-site storage facilities.3. File Creation and Naming ConventionAll employees are responsible for creating and naming files in a consistent and descriptive manner. File names should accurately reflect the content of the file, making it easy for users to search for and identify the information they need. File names should not contain special characters, lengthy abbreviations, or spaces.4. File Organization and StructureIt is important to organize files in a logical and consistent manner to facilitate efficient retrieval and sharing of information. Employees should adhere to a standardized file structure, with clearly defined folders and subfolders for various departments, projects, or categories. The use of meaningful folder names and hierarchical organization helps to minimize confusion and duplication of files.5. Access Control and PermissionsAccess to electronic files should be restricted to authorized individuals based on their role and responsibilities within the organization. File permissions should be set to limit the ability to view, modify, or delete files to only those who have a legitimate business need. Regular reviews of user access rights should be conducted to ensure that unauthorized access is prevented.6. File Storage and BackupAll electronic files should be stored on secure, centralized servers or cloud-based platforms that are regularly backed up to prevent data loss. Employees should refrain from storing files on local hard drives or personal devices to minimize the risk of unauthorized access or loss of data. Regular backups should be scheduled to ensure that all files are protected in the event of a system failure or security breach.7. File Retention and DisposalThe organization is required to maintain records of its activities in accordance with legal and regulatory requirements. Employees should adhere to the organization's record retention policy and schedule, which stipulates the minimum and maximum retention periods for various types of files. Files that have exceeded their retention period should be securely destroyed to prevent unauthorized access and comply with data protection regulations.8. File Security and EncryptionConfidential and sensitive files should be encrypted to prevent unauthorized access or disclosure of sensitive information. Employees should be trained on the proper handling and storage of sensitive files, including the use of encryption tools and secure transfer methods. Access to sensitive files should be restricted to authorized individuals and monitored for suspicious activities.9. File Sharing and CollaborationEmployees may need to share and collaborate on files with internal or external parties. When sharing files, employees should use secure methods such as encrypted email attachments or secure file-sharing platforms. Employees should refrain from using personal email accounts or unsecured platforms to share sensitive information to prevent data breaches and unauthorized access.10. Compliance and MonitoringThe organization's IT department is responsible for establishing and monitoring compliance with this File Management Policy. Regular audits and assessments should be conducted to ensure that employees are following the guidelines outlined in this policy. Non-compliance with this policy may result in disciplinary actions and revocation of access privileges.11. Training and AwarenessAll employees should receive training on the organization's File Management Policy upon their onboarding and periodically thereafter. Training should cover the proper creation, management, and storage of files, as well as the importance of data security and confidentiality. Employees should be made aware of their responsibilities in adhering to this policy to protect the organization's information assets.ConclusionEffective file management is essential for maintaining the integrity, security, and accessibility of an organization's information assets. This File Management Policy provides clear guidelines for employees on the proper creation, organization, storage, and disposal of electronic and physical files. By following these guidelines, the organization can minimizethe risk of data loss, unauthorized access, and non-compliance with legal and regulatory requirements.。
Sound Intelligence Axis ACAP Application Version 3

Milestone Plug-in InstallationGuideSound IntelligenceAxis ACAP ApplicationVersion 3.1.1Last update: 2020-01-29 Sound Intelligence ● Maanlander 14N ● 3824 MP Amersfoort ● NetherlandsInstallation GuideThis guide is to help you through installation of the SoundIntelligence plug-in which enables you to monitor and verify sound analytics notifications in Milestone.1.Supported versions2018R3 and higher three detectors per camera are supported2.Install Plugin folders*Pause all Milestone services before replacing folders.**Before unzipping folder, ensure that it is Unblocked: Right-click main folder and go to Properties and check Unblock if it is available.***If the Milestone Management Server and the Milestone Event Server are on independent machines, please place folders (according to the below) on both machines.On the device with the Milestone Management Server copy SoundIntelAdmin, SoundIntel and SoundIntelClient plugins files to “MIPPlugins” folder in Milestone installation directory (default C:\Program Files\Milestone\MIPPlugins): SoundIntelClient ==> XProtect Smart Client\MIPPluginsInstall on each PC where Milestone Smart Client will be used (so if the Mainserver is also the Client save this also there)SoundIntelAdmin ==> XProtect Management Client\MIPPluginsInstall on the main PC with Milestone Management server installedSoundIntel ==> XProtect Event Server\MIPPluginsInstall on the main PC with Milestone Event server installedIf the Smart Client user does not belong to the “Administrators” role, go to Security => Roles section, to check if the user has access to alarms.NOTEFor 2018 R2 and newer, replacing the VideoOS.Platform DLL is not needed.It is advised to make a back-up folder at the location where the file is present and move it there before copying the new dll file in this folder.3.Set-up Milestone settings in ACAP (from 2018R2 or higher)=Go to the advanced settings in Milestone Management Client and click Manage Milestoneevents:Make sure the mapping is enabled. It is advised not to use 1 as it is sometimes used forother purposes. The events need to be mapped in order to have the index numbers correspond with the different events generated by the Sound Detector. So now thesenumbers will also need to be used when configuring the camera is the Milestone Management Client.4.Set-up Milestone Management ClientIn Milestone Management Client for each camera with the Sound Detector installed:v2018R3 and higheradd the following event(s):Video analytics event started with the index number corresponding to the set-up in the ACAP (see previous section 3, f.e Analytic event index 2 for Aggression and Analytic event index 3 for Gunshot).In “Rules and Events” sectionIn “Rules and Events” section, add a rule:Perform an action on <event>: Sound Intelligence Start Recording (SoundIntelligence)from: SIcamsSelect actions to perform: start recording on <devices>: 5 seconds before (-5seconds) on the devices from metadataPerform stop action after <time>: 5 seconds after (5 Seconds)Stop recording immediatelyOptionally add Bookmark to rule to mark exact time of alert:Perform an action on Sound Intelligence Start Recording (Sound Intelligence)from SIcamsstart recording 5 seconds before on the devices from metadataand Create bookmark $EventName$ on $DeviceName$ on the devices frommetadataPerform action 5 seconds afterStop recording immediatelyNow Restart Milestone Event server.Re-Launch Milestone Management Client1In MIP Plug-ins sectionOpen ‘Sound intelligence’ and enter a name of the event (e.g. Aggression detected, Gunshot detected). Event indices are automatically picked up from the ACAP when this has been configured in advanced (See “Setting up Milestone Events in the ACAP”).1To retrieve camera credentials the Management Client on server PC should be always launchedIn Camera sectionNavigate to the camera running Sound Detector and under events click “Add” and locate Video analytics event started. The event index corresponds to the event name configured in previous step. For instance, 1 corresponds to Aggression, 2 corresponds to Gunshot and so on.Recording audio based on analytics events triggering onlyIt is possible to change the rules / settings such that the system is only recording audio when the analytic event has been triggered (few seconds before and after). Audio will still be heard when live viewing the camera, but it’s not being recorded. Upon the event triggering, it is logged, and the audio is recorded. The following steps need to be taken:1.Go to the camera device and the “record” tab. Uncheck the option in the camerato “Record on related devices”. This se parates the triggering of the audiorecording from the camera video recording so they can start and stopindependently from each other.2.Go to the microphone for that device, make sure “Recording” IS checked.a.Note it will take a few moments for this to take effect in the software, butafter a short time, you should see the icon for the microphone, changesuch that the red dot indicating recording disappears, but the greentriangle remains. This indicates that audio is streaming, but not recording.3.In the rules engine, you now will need to setup a rule that specifically instructsthe audio to start and stop recording. Make a rule that the trigger is youranalytic, and the action it performs is “Start recording on <devices>. Click<devices> and choose the microphone as the device. Click Next, and set the stopaction after <time> (when the analytic stops) to stop recording audio on the mic device.In this way it will configure the system to not record audio normally (because nothing has told it to do so), and when your analytic activates and deactivates, the rule that is watching for the analytic event will trigger the audio recording will start and stop along with it.Note that this does not stop the camera from streaming audio 24/7, meaning that an operat or can always listen LIVE to the camera’s mic anytime, but the audio from it is not being recorded based on motion detection. Audio will however be recorded if the operator manually clicks the “record” button in the Smart Client, or, if your analytic event triggers the rules engine to command the system to begin recording audio. NOTEMake sure to restart the event server after the camera settings are done.Also, when Adding a Camera, refresh the mapping in SI plug-in (or it will have the default mapping).estone Smart ClientThe Smart Client will have the SoundIntelligence plug-in as view option in the Live view:Under properties you can change the height of the list. By changing the width of the columns, you can choose to change the size of the rows and spectrogram images. You can also change the size of the cam live and recorded view.By selecting the live view of the camera, sensitivity settings of the detector can be changed instantly for the detectors running on that camera:Under the options button (top left wheel icon marked by orange arrow in above view), general settings of the view can be changed:6.SupportShould you require any technical assistance, please contact your Sound Intelligence Reseller. If your questions cannot be answered immediately, your reseller will forward your queries through the appropriate channels to ensure a rapid response.。
档案室管理制度英文缩写

档案室管理制度英文缩写1. IntroductionThe File Room Management System is designed to efficiently manage and organize all files and documents within the organization. The system aims to streamline the process of filing, storage, retrieval, and disposal of files to ensure easy access and compliance with regulatory requirements. This policy outlines the guidelines and procedures for the management of the file room.2. ScopeThis policy applies to all employees who access and manage files within the organization. It encompasses all physical and electronic files, including documents, records, and other forms of information.3. Responsibilities3.1 File Room ManagerThe File Room Manager is responsible for overseeing the operations of the file room, including the maintenance of file systems, tracking of file movements, and the implementation of security measures to protect sensitive information.3.2 File Room StaffFile Room Staff are responsible for assisting in the filing, retrieval, and organization of files as directed by the File Room Manager. They are also responsible for maintaining the cleanliness and orderliness of the file room.3.3 EmployeesAll employees are responsible for filing documents in the designated file room, following the file room management procedures, and ensuring the accuracy and completeness of the files they handle.4. File ClassificationAll files should be classified according to their nature, purpose, and retention requirements. File classification should be clear and consistent to facilitate easy retrieval and disposal. 4.1 Confidential FilesConfidential files contain sensitive information that should be accessed only by authorized personnel. These files should be stored in a secure area within the file room and access should be strictly controlled.4.2 Active FilesActive files are regularly accessed and updated. These files should be readily accessible within the file room to facilitate efficient workflow.4.3 Inactive FilesInactive files are no longer actively used but are still required to be retained for legal or regulatory purposes. These files should be stored in a separate area within the file room and should be clearly labeled for easy identification.5. File StorageFile storage should be designed to maximize space and ensure the safety and security of the files. The following guidelines should be followed for file storage:5.1 Physical FilesPhysical files should be stored in cabinets or shelving units, organized by classification and labeled clearly for easy retrieval. File room staff should regularly audit the physical files to ensure they are properly stored and organized.5.2 Electronic FilesElectronic files should be stored on secure servers or cloud-based storage systems. Access to electronic files should be restricted to authorized personnel only, and regular backups should be performed to prevent data loss.6. File RetrievalEmployees requiring access to files should submit a request to the File Room Manager or designated file room staff. The request should include the file name, classification, and any other relevant details. File room staff should then retrieve the requested file and log the file movement accordingly.7. File DisposalFiles that have reached the end of their retention period should be disposed of in accordance with the organization's retention and disposal policy. Confidential files should be shredded or otherwise securely destroyed to prevent unauthorized access.8. Record KeepingA record of all file movements, including file retrieval, returns, and disposals, should be maintained by the File Room Manager. This record should include details such as the date of the movement, the name of the requesting employee, and the reason for the file movement.9. Security MeasuresThe file room should be equipped with security measures such as access controls, surveillance cameras, and alarm systems to prevent unauthorized access and theft of files. Access to the file room should be restricted to authorized personnel only.10. TrainingAll employees who handle files should receive training on file room management procedures, including filing, retrieval, and disposal. This training should be conducted regularly to ensure employees are familiar with the file room policies and procedures.11. ComplianceThe File Room Management System should comply with all relevant legal and regulatory requirements, including data protection laws and industry-specific regulations. The File Room Manager should regularly review and update the system to ensure compliance.12. Policy ReviewThis File Room Management System policy should be reviewed regularly to ensure its effectiveness and relevance to the organization's needs. Any necessary updates or changes should be made to improve the management of the file room.13. ConclusionThe File Room Management System policy aims to establish clear guidelines and procedures for the efficient management of files within the organization. By following these guidelines, the organization can ensure that files are properly stored, organized, and accessed in a secure and compliant manner.。
关于老人摔倒的英语作文题目

关于老人摔倒的英语作文题目英文回答:Elderly Falls: A Global Problem with Devastating Consequences.Falls among older adults are a major public health concern, affecting millions of individuals worldwide and leading to significant morbidity and mortality. As populations age globally, the incidence of falls is expected to increase, placing a significant burden on healthcare systems and societies.Causes of Falls.The causes of falls in elderly individuals are complex and multifactorial, involving a combination of intrinsic and extrinsic factors. Intrinsic factors include age-related physiological changes, such as decreased muscle strength, impaired balance, and reduced sensory function.Extrinsic factors encompass environmental hazards, such as slippery floors, poor lighting, and loose rugs.Consequences of Falls.Falls can have a wide range of consequences, from minor injuries to severe trauma and even death. The most common injuries resulting from falls include hip fractures, head injuries, and broken bones. In addition to physical trauma, falls can also have significant psychological and emotional consequences, including fear of falling, loss of independence, and reduced quality of life.Prevention of Falls.Preventing falls in elderly individuals requires a comprehensive approach that addresses both intrinsic and extrinsic risk factors. Interventions aimed at improving balance, muscle strength, and gait stability have been shown to be effective in reducing fall risk. Environmental modifications, such as installing grab bars in bathrooms and improving lighting, can also help to prevent falls.Management of Falls.When falls do occur, it is important to assess the patient's injuries and underlying risk factors to develop an appropriate management plan. In cases of serious injuries, immediate medical attention is crucial. For less severe falls, a thorough evaluation and follow-up can help to identify and address any underlying conditions that may increase the risk of future falls.Rehabilitation and Recovery.Following a fall, rehabilitation and recovery are essential to restore function and prevent future falls. Physical therapy can help to improve balance, strength, and mobility. Occupational therapy can assist with activities of daily living and home safety modifications. Psychological support can also be beneficial in addressing the fear of falling and improving overall well-being.Conclusion.Falls among older adults are a serious public health problem with significant consequences for individuals and societies. By understanding the causes and consequences of falls, we can develop effective prevention and management strategies. A comprehensive approach that addresses both intrinsic and extrinsic risk factors is crucial to reducing fall risk and improving the health and well-being of older adults.中文回答:老年人跌倒,一项具有毁灭性后果的全球性问题。
儿科病房跌倒坠床预警管理的开展及价值评定
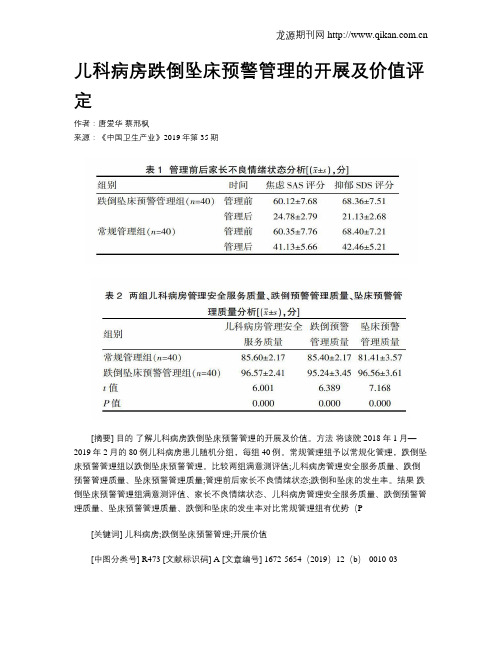
儿科病房跌倒坠床预警管理的开展及价值评定作者:唐爱华蔡邢枫来源:《中国卫生产业》2019年第35期[摘要] 目的了解儿科病房跌倒坠床预警管理的开展及价值。
方法将该院2018年1月—2019年2月的80例儿科病房患儿随机分组,每组40例。
常规管理组予以常规化管理,跌倒坠床预警管理组以跌倒坠床预警管理。
比较两组满意测评值;儿科病房管理安全服务质量、跌倒预警管理质量、坠床预警管理质量;管理前后家长不良情绪状态;跌倒和坠床的发生率。
结果跌倒坠床预警管理组满意测评值、家长不良情绪状态、儿科病房管理安全服务质量、跌倒预警管理质量、坠床预警管理质量、跌倒和坠床的发生率对比常规管理组有优势(P[关键词] 儿科病房;跌倒坠床预警管理;开展价值[中图分类号] R473 [文献标识码] A [文章编号] 1672-5654(2019)12(b)-0010-03Development and Value Assessment of Early Warning Management of Falling Crib in Pediatric WardTANG Ai-hua, CAI Xing-fengDepartment of Pediatrics, Affiliated Hospital of Nantong University, Nantong, Jiangsu Province, 226001 China[Abstract] Objective To understand the development and value of early warning management of fall secration in pediatric wards. Methods 80 children in pediatric wards from January 2018 to February 2019 were randomly divided into two groups with 40 cases each. The regular management team will be routinely managed, and the fall-sleeping early warning management team will be responsible for the fall-sleeping early warning management. Compare the two groups of satisfactory evaluation values; the quality of pediatric ward management safety service, the quality of fall warning management, the quality of clinical warning of falling bed; the bad emotional state of parents before and after management; the incidence of falls and falling bed. Results Satisfaction evaluation value of fall bed early warning management group, parental bad mood state, quality of paediatric ward management safety service, fall warning management quality, quality of fall-back warning management, incidence of falls and falling bed have advantages compared with conventional management group(P<0.05). Conclusion Children in pediatric wards can achieve better results by implementing fall-of-bed warning management, which can improve the quality of pediatric ward management and service, reduce the negative emotions of parents and reduce the incidence of falls and falling of beds.[Key words] Pediatric ward; Falling bed early warning management; Development value兒童年龄较小,表达不准确,跌倒原因多样化,预防方法不规范,预防跌倒已成为儿科管理的重点和难点。
滑倒绊倒跌倒风险预防英文版

Preventing Slips, Trips, Falls (STF)
"Our loss control service is advisory only. We assume no responsibility for management or control of customer safety activities nor for implementation of recommended corrective measures. This presentation is based on information supplied by the customer and/or observations of conditions and practices at the time of the consultation. We have not tried to
• Surfaces colored safety yellow (ISO 3864, ANSI Z535.1) "most visually detectable“ (US Access Board Research)
• Contrast on curbs, step risers, stair nosing and landings
identify all hazards. We do not warrant that requirements of any federal, state, or local law, regulation or ordinance have or have not been met.”
Do’s
• Actively participate by contributing
检测文件是否含有数字签名

检测⽂件是否含有数字签名//检测⽂件是否含有数字签名unit uSimpleTrustCheck;interfacefunction CheckFileTrust(const sFilename: string): Boolean;procedure EnumerateMember(const sFileName : PChar);implementationusesWindows, SysUtils;constWTD_CHOICE_FILE = 1;WTD_CHOICE_CATALOG = 2;//Konstanten für dwStateActionWTD_STATEACTION_IGNORE = 0;WTD_STATEACTION_VERIFY = 1;//UI Konstanten für WINTRUST_DATAWTD_UI_NONE = 2; //kein UI anzeigen//Konstanten zur Prüfung auf zurückgezogene ZertifikateWTD_REVOKE_NONE = 0; // keine zus?tzliche Prüfun//Konstanten für TrustProviderWTD_SAFER_FLAG = 256; // für Winxp Sp2 ben?tigt//Wintrust Action GUID?sWINTRUST_ACTION_GENERIC_VERIFY_V2: TGUID = '{00AAC56B-CD44-11d0-8CC2-00C04FC295EE}'; typeCATALOG_INFO = recordcbStruct: DWORD; // = sizeof(WINTRUST_CATALOG_INFO)sCatalogFile: array[0..MAX_PATH] of WCHAR; // Dateiname incl. Pfad zur CAT Dateiend;PCATALOG_INFO = ^CATALOG_INFO;WINTRUST_CATALOG_INFO = recordcbStruct: DWORD; // = sizeof(WINTRUST_CATALOG_INFO)dwCatalogVersion: DWORD; // optionalpcwszCatalogFilePath: LPCWSTR; // ben?tigt, Dateiname incl. Pfad zur CAT DateipcwszMemberTag: LPCWSTR; // ben?tigt, tag zum Mitglied im KatalogpcwszMemberFilePath: LPCWSTR; // ben?tigt, Dateiname incl. PfadhMemberFile: THANDLE; // optionalend;PWINTRUST_CATALOG_INFO = ^WINTRUST_CATALOG_INFO;WINTRUST_FILE_INFO = recordcbStruct: DWORD; // = sizeof(WINTRUST_FILE_INFO)pcwszFilePath: LPCWSTR; // ben?tigt, Dateiname incl. PfadpgKnownSubject: PGUID; // optionalhFile: THANDLE; // optionalend;PWINTRUST_FILE_INFO = ^WINTRUST_FILE_INFO;WINTRUST_DATA = packed recordcbStruct: DWORD; // = sizeof(WINTRUST_DATA)pPolicyCallbackData: pointer; // optional - auf 0 setzenpSIPClientData: pointer; // optional - auf 0 setzendwUIChoice: DWORD; // ben?tigt, UI auswahlfdwRevocationChecks: DWORD; // ben?tigt, auf zurückgezogene Zertifikate prüfen (online ben.)dwUnionChoice: DWORD; // ben?tigt, welche Datenstruktur soll verwendet werdenpWTDINFO: pointer; // Pointer zu einer der Wintrust_X_Info StrukturenpFake: pointer; //Fake Pointer - n?tig damit der Speicer wieder freigegeben wirdpFake1: pointer; //Fake Pointer - n?tig damit der Speicer wieder freigegeben wirdpFake2: pointer; //Fake Pointer - n?tig damit der Speicer wieder freigegeben wirdpFake3: pointer; //Fake Pointer - n?tig damit der Speicer wieder freigegeben wirddwStateAction: DWORD;hWVTStateData: THANDLE;pwszURLReference: PWChar;dwProvFlags: DWORD;dwUIContext: DWORD;end;PWINTRUST_DATA = ^WINTRUST_DATA;//Handle und Pointer auf KatalogAdminKontextHCatAdmin = THANDLE;PHCatAdmin = ^HCatAdmin;//Add by Alan on 2010-7-15CRYPT_ATTR_BLOB = packed recordcbData : DWORD;pbData : pointer;end;PCRYPT_ATTR_BLOB = ^CRYPT_ATTR_BLOB;CRYPTCATMEMBER = packed recordcbStruct : DWORD;pwszReferenceTag : PChar;pwszFileName : PChar;gSubjectTpe : TGUID;fdwMemberFlags : DWORD;pIndirectData : Pointer;dwCertVersion : DWORD;dwReserved : DWORD;hReserved : THandle;sEncodedIndirectData : CRYPT_ATTR_BLOB;sEncodedMemberInfo : CRYPT_ATTR_BLOB;end;PCRYPTCATMEMBER = ^CRYPTCATMEMBER;varhLibWintrust : THANDLE;//dynamische Dll Aufrufe - keine Statische einbindung m?glichCryptCATAdminAcquireContext : function(PHCatAdmin: PHCatAdmin; pgSubsystem: PGUID; dwFlags: DWORD): BOOL; stdcall;CryptCATAdminReleaseContext : function(HCatAdmin: HCatAdmin; dwFlags: DWORD): BOOL; stdcall;CryptCATAdminCalcHashFromFileHandle: function(hFile: THANDLE; pHashSize: PDWORD; pbHash: PByteArray; dwFlags: DWORD): BOOL; stdcall;CryptCATAdminEnumCatalogFromHash: function(HCatAdmin: HCatAdmin; pbHash: PByteArray; pHashSize: DWORD; dwFlags: DWORD; phPrevCatInfo: PHandle): THANDLE; stdcall;CryptCATCatalogInfoFromContext: function(hCatInfo: THANDLE; psCatInfo: PCATALOG_INFO; dwFlags: DWORD): BOOL; stdcall;CryptCATAdminReleaseCatalogContext: function(HCatAdmin: HCatAdmin; hCatInfo: THANDLE; dwFlags: DWORD): BOOL; stdcall;WinVerifyTrust : function(hwnd: THANDLE; pgActionID: PGUID; pWintrustData: PWINTRUST_DATA): Longint; stdcall; //Add by Alan on 2010-7-15CryptCATOpen : function(pwszFileName : PChar; fdwOpenFlags : DWORD; hProv : THandle; dwPublicVersion : DWORD; dwEncodingType : DWORD) : THandle;CryptCATClose : function(hCatalog : THandle) : Boolean;CryptCATEnumerateMember : function(hCatalog : THandle; pPrevMember : PCRYPTCATMEMBER) : CRYPTCATMEMBER;{-----------------------------------------------------------------------------Funcktion: CheckFileTrustDate: 02-Mrz-2005Arguments: const sFilename: stringResult: BooleanDescription: Prüft ob die angegebene Datei Trusted ist-----------------------------------------------------------------------------}function CheckFileTrust(const sFilename: string): Boolean;var//Byte Array und CounteraByteHash : array[0..255] of Byte;iByteCount : Integer;hCatAdminContext : HCatAdmin;WTrustData : WINTRUST_DATA;WTDCatalogInfo : WINTRUST_CATALOG_INFO;WTDFileInfo : WINTRUST_FILE_INFO;CatalogInfo : CATALOG_INFO;hFile : THANDLE;hCatalogContext : THANDLE;swFilename : WideString;swMemberTag : WideString;ilRet : Longint;x : Integer;begin//Standard Result setzenResult := False;//Sicherheitsabfrage ob Datei existiertif FileExists(sFilename) = False then Exit;//String in Widestring wandelnswFilename := sFilename;ZeroMemory(@CatalogInfo, SizeOf(CatalogInfo));ZeroMemory(@WTDFileInfo, SizeOf(WTDFileInfo));ZeroMemory(@WTDCatalogInfo, SizeOf(WTDCatalogInfo));ZeroMemory(@WTrustData, SizeOf(WTrustData));//Catalog Admin Kontext ?ffnen und falls nicht m?glich Prozedur verlassenif CryptCATAdminAcquireContext(@hCatAdminContext, nil, 0) = False then Exit;//Filehandle auf die zu prüfende Datei holenhFile := CreateFile(PChar(string(sFilename)), GENERIC_READ, FILE_SHARE_READ, nil, OPEN_EXISTING, FILE_ATTRIBUTE_NORMAL, 0);//Wenn das Handle nicht erhalten wurde Prozedur verlassenif hFile = INVALID_HANDLE_VALUE then Exit;//iaBytescount nach gr??e des Arrays setzeniByteCount := SizeOf(aByteHash);//ByteArray mit Hash füllen lassen und die Gr??e in iByteCount bekommenCryptCATAdminCalcHashFromFileHandle(hFile, @iByteCount, @aByteHash, 0);// MemberTag brechnen (vom ByteArray auf HEX)for x := 0 to iByteCount - 1 dobeginswMemberTag := swMemberTag + IntToHex(aByteHash[x], 2);end;//FileHandle schlie?en - wird nicht mehr gebrauchtCloseHandle(hFile);//Erste Prüfung erfolgt mit WINTRUST_DATA.dwUnionChoice := WTD_CHOICE_CATALOG;//also muss WINTRUST_CATALOG_INFO gefüllt werden////Handle auf den Katalog Kontext holenhCatalogContext := CryptCATAdminEnumCatalogFromHash(hCatAdminContext, @aByteHash, iByteCount, 0, nil); //Wenn das Handle 0 ist muss die Prüfung mit der//WINTRUST_DATA.dwUnionChoice := WTD_CHOICE_FILE; Struktur durchgeführt werdenif hCatalogContext = 0 thenbegin//CatalogContext = 0 also////WINTRUST_FILE_INFO Struktur initialisieren und füllenWTDFileInfo.cbStruct := SizeOf(WTDFileInfo);WTDFileInfo.pcwszFilePath := PWideChar(swFilename);WTDFileInfo.pgKnownSubject := nil;WTDFileInfo.hFile := 0;//WINTRUST_DATA Struktur initialisieren und füllenWTrustData.cbStruct := SizeOf(WTrustData);WTrustData.dwUnionChoice := WTD_CHOICE_FILE; //WINTRUST_FILE_INFO Struktur w?hlenWTrustData.pWTDINFO := @WTDFileInfo; //Pointer zu WINTRUST_FILE_INFOWTrustData.dwUIChoice := WTD_UI_NONE;WTrustData.fdwRevocationChecks := WTD_REVOKE_NONE;WTrustData.dwStateAction := WTD_STATEACTION_IGNORE;WTrustData.dwProvFlags := WTD_SAFER_FLAG; //UI bei XP SP2 unterbindenWTrustData.hWVTStateData := 0;WTrustData.pwszURLReference := nil;endelsebegin//CatalogContext <> 0 also CATALOG_INFO benutzen////CATALOG_INFO Struktur füllenCryptCATCatalogInfoFromContext(hCatalogContext, @CatalogInfo, 0);//WINTRUST_CATALOG_INFO Struktur initialisieren und füllenWTDCatalogInfo.cbStruct := SizeOf(WTDCatalogInfo);WTDCatalogInfo.pcwszCatalogFilePath := CatalogInfo.sCatalogFile;WTDCatalogInfo.pcwszMemberFilePath := PWideChar(swFilename);WTDCatalogInfo.pcwszMemberTag := PWideChar(swMemberTag);//WINTRUST_DATA Struktur initialisieren und füllenWTrustData.cbStruct := SizeOf(WTrustData);WTrustData.dwUnionChoice := WTD_CHOICE_CATALOG; //WINTRUST_CATALOG_INFO Struktur w?hlenWTrustData.pWTDINFO := @WTDCatalogInfo; //Pointer zu WINTRUST_CATALOG_INFOWTrustData.dwUIChoice := WTD_UI_NONE;WTrustData.fdwRevocationChecks := WTD_REVOKE_NONE;WTrustData.pPolicyCallbackData := nil;WTrustData.pSIPClientData := nil;WTrustData.dwStateAction := WTD_STATEACTION_VERIFY;WTrustData.dwProvFlags := 0; //WTD_SAFER_FLAG; //UI bei XP SP2 unterbindenWTrustData.hWVTStateData := 0;WTrustData.pwszURLReference := nil;end;//WinVerifyTrust aufrufen um die Prüfung durchzuführenilRet := WinVerifyTrust(INVALID_HANDLE_VALUE, @WINTRUST_ACTION_GENERIC_VERIFY_V2, @WTrustData); //Wenn Erg. 0 ist dann ist das File Trusted - alle anderen Werte sind Fehlercodesif ilRet = 0 thenbeginResult := TrueendelseResult := False;//Handle zum Catalogfile schlie?enCryptCATAdminReleaseCatalogContext(hCatAdminContext, hCatalogContext, 0);//Catalog Admin Kontext schlie?enCryptCATAdminReleaseContext(hCatAdminContext, 0);end;procedure EnumerateMember(const sFileName : PChar);varpMember : PCRYPTCATMEMBER;Member : CRYPTCATMEMBER;catalogHandle : THandle;begincatalogHandle := CryptCATOpen(sFileName, 0, 0, 0, 0);tryMember := CryptCATEnumerateMember(catalogHandle, pMember);while pMember <> nil dobeginMember := CryptCATEnumerateMember(catalogHandle, pMember);pMember := @Member;end;finallyif catalogHandle <> 0 thenCryptCATClose(catalogHandle);end;end;initialization//Dynamisches laden der Dll und deren FunktionenhLibWintrust := LoadLibrary('wintrust.dll');if hLibWintrust >= 32 then { success }beginCryptCATAdminAcquireContext := GetProcAddress(hLibWintrust, 'CryptCATAdminAcquireContext');CryptCATAdminReleaseContext := GetProcAddress(hLibWintrust, 'CryptCATAdminReleaseContext');CryptCATAdminCalcHashFromFileHandle := GetProcAddress(hLibWintrust, 'CryptCATAdminCalcHashFro mFileHandle');CryptCATAdminEnumCatalogFromHash := GetProcAddress(hLibWintrust, 'CryptCATAdminEnumCatalogFromHash'); CryptCATCatalogInfoFromContext := GetProcAddress(hLibWintrust, 'CryptCATCatalogInfoFromContext');CryptCATAdminReleaseCatalogContext := GetProcAddress(hLibWintrust, 'CryptCATAdminReleaseCatalogContext'); WinVerifyTrust := GetProcAddress(hLibWintrust, 'WinVerifyTrust');//Add by Alan on 2010-7-15CryptCATOpen := GetProcAddress(hLibWintrust, 'CryptCATOpen');CryptCATClose := GetProcAddress(hLibWintrust, 'CryptCATClose');CryptCATEnumerateMember := GetProcAddress(hLibWintrust, 'CryptCATClose');end;finalizationFreeLibrary(hLibWintrust);end.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
General Consequences of Falls
Leading cause of death from injury in over 75’s Fallers 2.5 times more likely to go into a nursing home 10% of all call-outs for London Ambulance Service are for over 65’s who have fallen 31% of falls result in minor injury and 6 - 9.9% in serious injury (Morse et al 1987, Chu et al, 1999)
Environmental Hazards Postural Hypotension Transfers Walking Nutrition and Alcohol Reduced Confidence Coping Strategies Comprehension/Memory
History of Falls
Parkinson’s Disease
Does the patient have a diagnosis of Parkinson’s disease? Postural Instability inevitable Medication can cause postural hypotension Unsteady gait with small steps, p
16 Point Screening Tool
History of falls 4 or more medications Parkinsons Disease or Stroke Balance Standing Up Footwear and Footcare Vision Hearing
16 Point Screening Tool
Physical Injury
Hip fracture Wrist fracture Cuts/Lacerations Deep bruising Soft tissue injuries Dislocations Sprains Joint pain
Long Lie
Over one hour in length Can predict death within 6 months Increased mortality rate. Medical complications. Access to help.
What is a Fall?
“Unexpectedly arriving at a lower level than intended” (Tinetti) “an event which results in a persons coming to rest inadvertently on the ground or other lower level” (Kellog) “a trip or slip that results in a person, with or without consciousness unintentionally landing on the floor or lower level” (Skelton and Dinan)
Reduced Muscle FALL Strength, Balance & Confidence
Reduction in activity
Risk Assessment
NSF states Falls Risk Assessment should be implemented by April 2003 No suitable validated tool available: MORSE; STRATIFY; FRASE. Therefore suggest use of Multiprofessional 16 point screening tool to identify and address falls risk factors
Associated with reduced arm function Decreased response times Decreased balance reactions Misjudgement of depth, distance ect Lack of concentration Poor quality of movement
Consequence of Falls for Individuals
Fractures Cuts and Bruising Dislocations Strains and Sprains Increase in joint pains Long lie (over 1 hr) Falls and instability contribute to 40% of nursing home admissions Post Fall Synfrome Depression Social Isolation Reduction in Activity Dependence
Parkinson’ Disease
66.6-90% Fall at some stage Turning and reaching most common cause of falls High anxiety of falls even among those who haven’t fallen Co-morbidity Cognitive Impairment
Physio Romaine Ellul
Falls Nurse Specialist Nicky Rice
Falls Service Provision
Falls clinic Friday morning MRI Domiciliary visits from Multi-disciplinary Team for assessment and treatment Postural stability exercise classes 2 x week Education, Advise and Liaison Resource to Acute and Community Trusts In-patient assessments if warranted
Post-Fall Syndrome
Fallers & Non-Fallers Social Isolation Dependence Depression Reduction in/Avoidance of activity Fear of falling Anxious when walking or transferring?
Background: NSF for Older People March 2001
Standard Six: Falls ‘The NHS, working in partnership with councils, takes action to prevent falls and reduce resultant fractures or other injuries in their populations of older people. Older people who have fallen receive effective treatment and rehabilitation and with their carers, receive advice on prevention through a specialised falls service’.
Stroke
At higher risk than the general population 14-39% have one of more falls in hospital 75% have one or more falls post dischargen ?R CVA > L CVA
Stroke
Referral Criteria
Over 65 with a history of or a high risk of falling Score 4 or more on 5 pt risk assessment tool Resident within Central Manchester Acute Trust boundary or registered with a Central Manchester GP Previously seen by Community Falls Team and more specialist assessment required Multi-Disciplinary needs ie Medical, Nursing and Therapy
Cost of Falls to NHS
Fractures cost NHS 1.6 billion per year Hospital spending > £10 billion Local authority, residential care > £3 billion Non-residential care > £2 billion
FALLS MANAGEMENT FILE
Compiled by:
Bernie O’Dowd Clinical Specialist Physio Nicky Rice Falls Nurse Specialist March 2006
The Falls Team
Consultant Physician Dr. Hanley Rehab Assistant Tracey Andrews Clinical Specialist Physio Bernie O’ Dowd Occupational Therapist Vacant
