A Layered Approach towards Domain Authoring Support
A Cross-Layer Approach to Performance Monitoring of Web Services

A Cross-Layer Approach to Performance Monitoringof Web ServicesNicolas Repp,Rainer Berbner,Oliver Heckmann,and Ralf SteinmetzTechnische Universit¨a t DarmstadtMultimedia Communications Lab(KOM)Merckstrasse25,64283Darmstadt,Germanyrepp@kom.tu-darmstadt.deAbstract.An increasing amount of applications are currently built as Web Ser-vice compositions based on the TCP/IP+HTTP protocol stack.In case of anydeviations from desired runtime-behavior,problematic Web Services have to besubstituted and their execution plans have to be updated accordingly.One chal-lenge is to detect deviations as early as possible allowing timely adaption of exe-cution plans.We advocate a cross-layer approach to detect bad performance andservice interruptions much earlier than by waiting for their propagation throughthe full protocol stack.This position paper describes an approach to gain detailed real-time informationabout Web Service behavior and performance based on a cross-layer analysis ofthe TCP/IP+HTTP protocols.In this paper we focus especially on TCP.The re-sults are used to make decisions supporting service selection and replanning inservice-oriented computing scenarios.Furthermore,generic architectural compo-nents are proposed implementing the functionality needed which can be used indifferent web-based scenarios.1IntroductionAlmost every Internet user has encountered problems while using services in the Inter-net,e.g.,browsing the World-Wide Web or using Email.Long to infinite response times due to congestion or connection outage,non-resolvable URLs,or simplefile-not-found errors are some of the most common ones.Human users tend to beflexible in case of any service”misbehavior”.Users wait and check back later or even select a different service if the originally requested service is not available.In contrast,computer systems as service consumers are not asflexible.Appropriate strategies to handle those runtime events have to be implemented during design time of the computer system.Services are the key building block of service-oriented computing.A service is a self-describing encapsulation of business functionality(with varying granularity)ac-cording to[1].Following the service-oriented computing paradigm,applications can be assembled out of several independent,distributed and loosely-coupled services[2]. Those services can be provided even by third parties.One option to implement services from a technical perspective is the use of Web Services.Web Services are based on dif-ferent XML-based languages for data exchange and interface description,e.g.,SOAP and the Web Service Description Language(WSDL).For the transport of data and theFig.1.Modified W3C Web Services Architecture Stack[3]Web Service invocation mainly the Transmission Control Protocol(TCP)/Internet Pro-tocol(IP)suite(e.g.,RFC793,[4],or[5])as well as the Hypertext Transfer Protocol (HTTP-e.g.,RFC2616or[6])are used.Figure1shows the W3C Web Services Archi-tecture Stack enhanced by alternative Web Service technologies and the communication protocols used.It will be the basis for our further considerations.In order to build applications from different existing Web Services the following generic phases are needed[7]:First,suitable Web Services have to be selected accord-ing to the functional and non-functional requirements of the application.Second,the selected Web Services have to be composed to an execution plan.Hereto,a composition can be described,e.g.,on basis of the Business Process Execution Language(BPEL) [8].In the next step the execution plan can be processed.During the execution phase it is possible that parts of the composition do not act as expected with regard to the non-functional requirements.Reasons for misbehavior of Web Services are manyfold, e.g.,server errors while processing a request,network congestion or network outages. Therefore,it is necessary to select alternative Web Services and to replan the Web Ser-vice execution[9].Replanning is always a trade-off between the costs of creating new plans to fulfill the overall non-functional requirements and the costs of breaking the requirements[10].Timely action is required to reduce the delay in the execution of an application due to replanning and substitution of Web Services.Hence,we propose a proactive approach initiating countermeasures as soon as there is evidence that a de-viation might occur in the near future with a certain probability p.To start replanning before the deviation happens allows replanning to be carried out in parallel to the ser-vice execution itself.The results of replanning have to be discarded with probability 1−p as the alternative plans are not needed.Furthermore,current approaches often lack detailed information about the status of a Web Service due to the information hiding implemented in the layer model ofthe TCP/IP+HTTP protocol stack underlying Web Services.For this,we advocate a cross-layer approach to detect bad performance and service interruptions.Cross-layer analysis allows decisions based on deeper knowledge of the current situation as well as decisions made much earlier than by waiting for information propagating through the full protocol stack.The rest of this position paper is structured as follows.In the next section we de-scribe Quality-of-Service(QoS)and its meaning for Web Services.We especially fo-cus on performance as a part of Web Service QoS.Afterwards,the relation between TCP/IP+HTTP and Web Service performance is discussed.Our cross-layer approach to performance monitoring an performance anomaly detection of Web Services is intro-duced thereafter.The paper closes with a conclusion and an outlook on future work.2Quality-of-Service and Performance of Web ServicesIn this section we discuss QoS with regard to Web Services and Web Service composi-tions with a focus on Web Service performance.2.1Quality-of-Service with regard to Web ServicesSimilar to QoS requirements in traditional networks,there is a need to describe and manage QoS of Web Services and Web Service compositions.Generally,QoS defines non-functional requirements on services independent from the layer they are related to. QoS can be divided into measurable and non-measurable parameters.The most com-mon measurable parameters are performance-related,e.g.,throughput,response time, and latency.Additionally,parameters like availability,error-rate,as well as various non-measurable parameters like reputation and security are of importance for Web Services [10][11].The meaning of QoS requirements can differ between service providers and service requesters in a service-oriented computing environment[11].From a service providers’perspective,providing enough capacity with the quality needed to fulfill Service Level Agreements(SLA)with different customers is a core issue.Service re-questers are more focused on managing bundles of Web Services from different ven-dors in order to implement their business needs.Therefore,management of QoS re-quirements is done on aggregations of Web Services,to a lesser extend on single Web Services.There is a variety of other definitions of Web Service QoS.A more extensive ap-proach identifies the following requirements[12]:performance,reliability,scalability, capacity,robustness,exception handling,accuracy,integrity,accessibility,availability, interoperability,security,and network-related QoS requirements.Especially the last re-quirement is of further interest.As many requirements of Web Service QoS are directly related to the underlying network and its QoS,implementations of network QoS mech-anisms,e.g.,Differentiated Services(DiffServ)or the Resource Reservation Protocol (RSVP),are also covered by the definition as well.2.2Performance of Web ServicesPerformance of Web Services is not a singular concept.Rather,it consists of several concepts which themselves are connected to different metrics and parameters.Again, there are several definitions of Web Service performance.We will use the definition provided by the Web Services Architecture Working Group of the W3C as a founda-tion for our own defintion.According to the W3C,performance is defined in terms of throughput,reponse time,latency,execution time,and transaction time[12].Both execution time and latency are sub-concepts of the W3Cs definition of response time. Transaction time describes the time needed to process a complete transaction,i.e.,an interaction consisting of several requests and responses belonging together.For this paper,we define performance in terms of throughput and response time. Response time is the time needed to process a query,from sending the request until receiving the response[13].Response time can be further divided into task processing time,network processing time,i.e.,time consumed while traversing the protocol stacks of source,destination,and intermediate systems,as well as network transport time itself. In case of an error during the processing of a request or a response,the response time measures the time from a request to the notification of an error.We define response time as follows:t response(ws)=t task(ws)+t stack(ws)+t transport(ws)A large fraction of a web service’s response time is determined by the processing time for requests and their respective messages in both intermediate systems and end-points. For the measurement of the response time,the encapsulation of data into XML mes-sages and vice versa,compression and decompression of data,as well as encryption and decryption of messages also have to be taken into account.Furthermore,time for con-nection setup,for the negotiation of the connections parameters as well as the amount of time used for authentication are part of the response time as well.Throughput,measured in connections,requests or packets per second,describes the capability of a Web Service provider to process concurrent Web Service requests.De-pending on the layer,different types of connections can be the basis for measurements, e.g.TCP connections,HTTP connections,or even SOAP interactions.We define the throughput of a Web Services as:throughput(ws)=#requests(ws)3A Cross-layer Approach to Performance Monitoring and Anomaly DetectionIn this section we describe an approach for performance monitoring and performance anomaly detection based on packet capturing and the application of simple heuristics. Therefore,we analyze IP,TCP,and HTTP data.The analysis of SOAP is not in scope of this paper,as we want to stay independent of a certain Web Service technology.Our approach can be applied to various alternative Web Service technologies as well,e.g., XML-Remote Procedure Call(XML-RPC)or Representational State Transfer(REST). Nevertheless,in our examples we use SOAP as it is the most common Web Service technology in use.3.1Protocol Parameters for Performance MonitoringConsider the simple Web Service invocation of a single Web Service as depicted in Figure2.A service requester generates a SOAP request and sends the message using HTTP to the service provider for further processing.The message has to pass several in-termediate systems on its way between the interaction’s endpoints.The SOAP response message is again transported using HTTP.Service ServiceFig.2.Simple Web Service interactionDuring data transfer several problems can occur,which all have an impact on Web Service execution.Beginning with the network layer,we may face routing problems, e.g.,hosts which are not reachable,congestion in Internet routers as well as traffic bursts.Additionally,on transport layer there are also potential pitfalls like the retrans-mission of packets due to packet loss or connection setup problems generating delays. Finally,there are also some potential problems on application layer with regard to Web Services for example in form of resources,which are not existing or not accessable for HTTP or problems in processing of SOAP messages due to incomplete or non-valid XML data.Although,many of the above problems are solved in modern protocol stack imple-mentations,we can use the knowledge about them to define measurement points for performance monitoring.Depending on the problems in scope different protocol pa-rameters have to be used.Table1gives an overview of measurement points on differentprotocol layers.We will use the transport layer parameters as an example to derive metrics and heuristics for performance anomaly detection in the following section.ProtocolICMP messagesSize of advertising windowRoundtrip time(RTT)Sequence numbers in useFlags used in packetsInformation about timersHeader informationTable1.Measuring points per protocol layer3.2Metrics and Heuristics for Performance Anomaly DetectionAs noted in Section2.1we can differentiate between the requirements of service re-questers and service providers.To visualize our concepts we will focus on the service requester’s perspective in this position paper.Before basic heuristics are proposed we present metrics based on the parameters presented in Table1,which will be the founda-tion of our heuristics.We propose several metrics based on parameters of the transport layer protocol:–M1-Average throughput in bytes per second(BPS).–M2-Throughput based on a moving average over window with size n seconds in BPS.–M3-Throughput based on exponential smoothing(first degree)withαvarying in BPS.–M4-Roundtrip time based on a moving average over window with size n segments in seconds per segment.–M5-Number of gaps in sequence numbers based on a moving average over window with size n seconds in number of gaps per second.The aggregation of single metrics in combination with the usage of appropriate thresholds allows us to build heuristics in order to detect anomalies with performance impact.The following two simple heuristics show the idea how to design heuristics based on the metrics discussed.Both were derived from experimentations in our Web Service test environment.–H1Requester:M1(or M2,M3)in aggregation with M4,i.e.,throughput combined with RTT.–H2Requester:M4in aggregation with M5,i.e.,RTT combined with the amount of gaps in TCP sequence numbers.Singular metrics are in some cases not sufficient for robust monitoring,e.g.,M5without any information about RTT does not offer useful information.In addition to those transport layer based heuristics,further parameters from other protocol layers and the respective metrics can be combined in order to create different cross-layer heuristics.Nevertheless,it is important that metrics and the related heuristics have to be calculated in an efficient way in order to keep additional processing times of our approach low.3.3Exemplary Evaluation of Our ApproachTo show the feasibility of our approach we set up an experiment.The test environment consists of a1.4GHz Centrino with1.256GByte RAM running Windows XP as ser-vice requester and a1.42GHz G4with1GByte RAM running Mac OS X as service provider.Apache Tomcat5.5.17is used as an application server.Both systems use Java 1.5and Axis1.4as SOAP implementation.They are connected by100MBit/s ethernet. For packet capturing windump v3.9.3is used.First,we measure the response time of a Web Service in our test environment.As payload we use SOAP messages of variable size.Table2shows the results of measuring 20individual runs both with and without network outage for a payload of20MByte,a test scenario,which was already implemented in our test environment.Similar results can be observed with a payload work outages are equally distributed t response(ws)[ms]maximum8,7438,891601,204604,186Table2.SOAP response timesin the interval[0;max(t response(ws)w/o outage)].A network outage is modelled as a permanent100%packet loss,i.e.,without a restart of the connection.Other scenarios, e.g.,varying or temporary packet loss,are not in focus of this position paper.As Table 2shows,the response time of our Web Service varies between8.9seconds(without outage)and10.07minutes(with outage)for a20MByte payload.rtt[ms]maximum0.220.31Table3.Roundtrip timesIn a next step,we apply H1Requester on our sample with network outages.Espe-cially the roundtrip time extracted from TCP packets can be used as trend estimate for the overall response time in our scenario.Table3shows the average roundtrip times of ing a moving average of the roundtrip times measured as a benchmarkfor the roundtrip time of the packet in transfer,a warning to the replanning system can be sent,e.g.,if the estimated time(or a multiple)is exceeded twice or more in a row. Unfortunately,throughput was not as good as the RTT as an indicator for performance anomalies in the given scenario.3.4Identification of Required Architectural ComponentsIn order to implement our ideas several architectural components are needed.The key building blocks are depicted in Figure3.Fig.3.Proposed architectural componentsThe upper part of Figure3describes existing generic components used for planning and executing of Web Service compositions.The Interface allows deployment of work-flows and configuration,the(Re-)Planning Component generates and adapts execution plans,which are thereafter executed by an Orchestration Engine.We propose the use of our Web Service Quality-of-Service Architectural Extension(WSQoSX)as imple-mentation means for the functionality needed.WSQoSX already supports planning and replanning of compositions[7][10].The lower part of thefigure describes the two core components of our approach in addition to the protocol stack.This enhanced architectural blueprint is named Web Service-Service Monitoring Extension(WS-SMX).The Monitor specifies a compo-nent capable of eavesdropping of the network traffic between service requester and provider.It also implements pre-filtering of the data passing by reducing it to the pro-tocol data of interest.Its data is passed to a Detector component,which is responsiblefor the data analysis and therefore the performance anomaly detection.The Detector component will implement the heuristics discussed in Section3.2.The Orchestration Engine initializes the Detector,which itself prepares the Monitor.The Detector analy-ses the data received by the Monitor and triggers the(Re-)Planning Component in case of any criticalfindings.Additionally,the Detector component can be configured using the Interface.Both Monitor and Detector are implemented in afirst version in our test environment based on Java1.5in combination with libpcap for packet capturing.4Related WorkAs our approach is based on research of various domains this section gives an overview of related work in those domains.Gschwind et al.[14]describe WebMon,a perfor-mance analysis system with focus on Web transactions,i.e.transactions between a Web browser and a Web server.Monitoring is done on basis of HTTP.Web Services as re-mote method invocations as well as a further processing of the results of the analysis are not in scope of their paper.Similar mechanisms as the ones proposed by us are im-plemented in the commercial software package VitalSuite by Lucent,which is used for capacity planning and QoS management in large networks.VitalSuite can also analyze different protocol layers simultaneously.In contrast to the system we propose,Vital-Suite’s focus is on reporting for end-users instead of automated management.A more detailed view on performance management of Web Services is discussed by Schmi-etendorf et al.[15].The Web Services Trust Center(WSTC)allows Web Services to be registered at and measured by an independent third party for SLA management.WSTC enables the monitoring of performance and availability of Web Services,but not under real-time requirements.The management of Web Service compositions,their orchestration as well as their optimization and planning is emphasized in various papers,partly mentioned in the introduction.Of further interest in that domain is the Web Service Manager(WSM) introduced by Casati et al.[16]focusing on the business perspective of Web Service management,e.g.,detecting and measuring SLA violations.Fundamental work in the area of packet capturing,its justification and optimization was carried out e.g.,by Feldmann[17]and Mao et al.[18].Both do not focus on poten-tial areas of application for packet capturing but on measurement itself.Feldmann uses cross-layer capturing and analysis of TCP and HTTP for later Web performance studies. Mao et al.describe both drawbacks and advantages of performance analysis of Web ap-plications based on packet capturing mechanisms.Furthermore,a reliable and efficient approach for monitoring in distributed systems based on dispatching is discussed.The idea of anomaly detection to predict certain critical situations is already used, e.g.,in the area of network security,especially in network intrusion detection.Mainiko-poulos et al.describe the use of statistical methods applied to network usage traces for anomaly detection,e.g.,an attack on a networked system[19].Another area of appli-cation is discussed by Yuan et al.[20].They propose a system for automated problem diagnosis in applications based on system event traces.The correlation of current traces and patterns of well known problems allows an automatic identification of problemsources and prediction of possible system errors.Furthermore,the authors use statisti-cal learning and classifying methods to dynamically adapt and improve their system. 5Conclusion and Future WorkIn this position paper we show that it can be beneficial to use information gathered on different protocol layers for decision support.We present an approach and several architectural components,which use hidden,low layer technical information for proac-tive replanning of Web Service compositions.As this is a position paper there are still some open issues we are researching.We are currently testing machine learning algo-rithms for anomaly detection.Furthermore,we are working on enhancements of ex-isting optimization models for Web Service compositions to support replanning[10]. Additionally,we will test our approach from a service requester’s perspective in real world scenarios,using Web Services available to the public,e.g.,from Amazon or via Xmethods.Using our approach for proactive replanning is not limited to SOAP Web Services. As we are collecting our data on lower layers,the type of Web Service can be ex-changed,e.g.,REST and XML-RPC based Web Services can also be supported.But we are not even limited to Web Services as an area of application.The approach can be of benefit,e.g.,to enhance Web browsers to detect network problems in a faster way. AcknowledgmentsThis work is supported in part by E-Finance Lab e.V.,Frankfurt am Main. References1.Papazoglou,M.P.:Service-oriented computing:Concepts,characteristics and directions.In:Proceedings of the Fourth International Conference on Web Information Systems Engineer-ing(WISE03).(December2003)3–122.Bichler,M.,Lin,K.J.:Service-oriented computing.IEEE Computer39(3)(March2006)99–1013.Booth,D.,Haas,H.,McCabe,F.,Newcomer,E.,Champion,M.,Ferris,C.,Orchard,D.:Webservices architecture(2004./TR/ws-arch/,accessed:2006/07/02)4.Stevens,W.R.:TCP/IP illustrated(vol.1):the protocols.Addison-Wesley Longman Pub-lishing Co.,Inc.,Boston,MA,USA(1994)5.Tanenbaum,A.S.:Computer Networks,Fourth Edition.Prentice Hall,Indianapolis,Indiana,USA(August2002)6.Mogul,J.C.:Clarifying the fundamentals of http.In:WWW’02:Proceedings of the11thinternational conference on World Wide Web.(May2002)25–367.Berbner,R.,Grollius,T.,Repp,N.,Heckmann,O.,Ortner,E.,Steinmetz,R.:An approachfor the management of service-oriented architecture(soa)based application systems.In: Proceedings of the Workshop Enterprise Modelling and Information Systems Architectures (EMISA2005).(October2005)208–2218.Curbera,F.,Khalaf,R.,Mukhi,N.,Tai,S.,Weerawarana,S.:The next step in web services.Commun.ACM46(10)(2003)29–349.Canfora,G.,Penta,M.D.,Esposito,R.,Villani,M.L.:Qos-aware replanning of compos-ite web services.In:Proceedings of the IEEE International Conference on Web Services (ICWS’05).(July2005)121–12910.Berbner,R.,Spahn,M.,Repp,N.,Heckmann,O.,Steinmetz,R.:An approach for replanningof web service workflows.In:Proceedings of the12th Americas Conference on Information Systems(AMCIS’06).(August2006)11.Menasc´e,D.A.:Qos issues in web services.IEEE Internet Computing6(6)(2002)72–7512.Lee,K.C.,Jeon,J.H.,Lee,W.S.,Jeong,S.H.,Park,S.W.:Qos for web services:Require-ments and possible approaches(2003.http://www.w3c.or.kr/kr-office/TR/2003/ws-qos/,ac-cessed:2006/07/03)13.Jain,R.:The art of computer systems performance analysis:techniques for experimentaldesign,measurement,simulation,and modeling.John Wiley&Sons,Inc.,New York,NY, USA(1991)14.Gschwind,T.,Eshghi,K.,Garg,P.K.,Wurster,K.:Webmon:A performance profiler for webtransactions.In:Proc.of the4th IEEE Int’l Workshop on Advanced Issues of E-Commerce and Web-Based Information Systems-WECWIS2002.(June2002)171–17615.Schmietendorf,A.,Dumke,R.,Stojanov,S.:Performance aspects in web service-basedintegration solutions.In:Proc.of the21st UK Performance Engineering Workshop-UKPEW2005.(July2005)137–15216.Casati,F.,Shan,E.,Dayal,U.,Shan,M.C.:Business-oriented management of web services.Commun.ACM46(10)(2003)55–6017.Feldmann,A.:Blt:Bi-layer tracing of http and tcp/works33(1-6)(2000)321–33518.Mao,Y.,Chen,K.,Wang,D.,Zheng,W.:Cluster-based online monitoring system of webtraffic.In:WIDM’01:Proceedings of the3rd international workshop on Web information and data management.(November2001)47–5319.Manikopoulos,C.,Papavassiliou,S.:Network intrusion and fault detection:a statisticalanomaly approach.IEEE Communications Magazine40(10)(October2002)76–8220.Yuan,C.,Lao,N.,Wen,J.R.,Li,J.,Zhang,Z.,Wang,Y.M.,Ma,W.Y.:Automated knownproblem diagnosis with event traces.In:Proceedings of EuroSys2006.(April2006)375–388。
外文文献文献列表
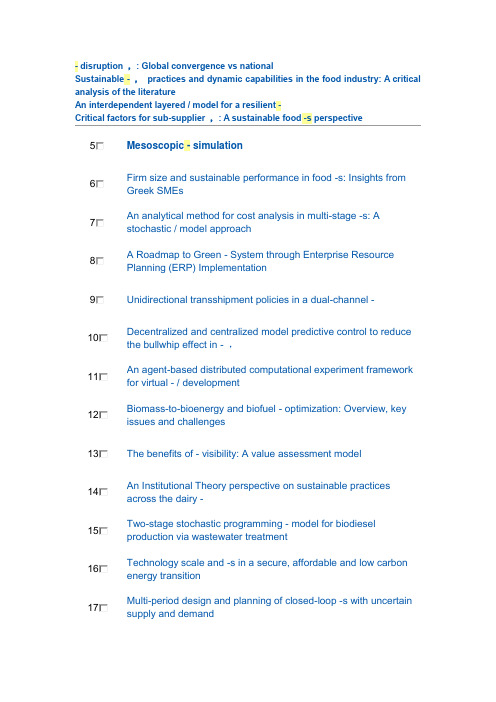
- disruption ,: Global convergence vs nationalSustainable - ,practices and dynamic capabilities in the food industry: A critical analysis of the literature5 Mesoscopic - simulation6 Firm size and sustainable performance in food -s: Insights from Greek SMEs7 An analytical method for cost analysis in multi-stage -s: A stochastic / model approach8 A Roadmap to Green - System through Enterprise Resource Planning (ERP) Implementation9 Unidirectional transshipment policies in a dual-channel -10 Decentralized and centralized model predictive control to reduce the bullwhip effect in - ,11 An agent-based distributed computational experiment framework for virtual - / development12 Biomass-to-bioenergy and biofuel - optimization: Overview, key issues and challenges13 The benefits of - visibility: A value assessment model14 An Institutional Theory perspective on sustainable practices across the dairy -15 Two-stage stochastic programming - model for biodiesel production via wastewater treatment16 Technology scale and -s in a secure, affordable and low carbon energy transition17 Multi-period design and planning of closed-loop -s with uncertain supply and demand18 Quality control in food - ,: An analytical model and case study of the adulterated milk incident in China19 - information capabilities and performance outcomes: An empirical study of Korean steel suppliers20 A game-based approach towards facilitating decision making for perishable products: An example of blood -21 - design under quality disruptions and tainted materials delivery22 A two-level replenishment frequency model for TOC - replenishment systems under capacity constraint23 - dynamics and the ―cross-border effect‖: The U.S.–Mexican border’s case24 Designing a new - for competition against an existing -25 Universal supplier selection via multi-dimensional auction mechanisms for two-way competition in oligopoly market of -26 Using TODIM to evaluate green - practices under uncertainty27 - downsizing under bankruptcy: A robust optimization approach28 Coordination mechanism for a deteriorating item in a two-level - system29 An accelerated Benders decomposition algorithm for sustainable - / design under uncertainty: A case study of medical needle and syringe -30 Bullwhip Effect Study in a Constrained -31 Two-echelon multiple-vehicle location–routing problem with time windows for optimization of sustainable - / of perishable food32 Research on pricing and coordination strategy of green - under hybrid production mode33 Agent-system co-development in - research: Propositions and demonstrative findings34 Tactical ,for coordinated -s35 Photovoltaic - coordination with strategic consumers in China36 Coordinating supplier׳s reorder point: A coordination mechanism for -s with long supplier lead time37 Assessment and optimization of forest biomass -s from economic, social and environmental perspectives – A review of literature38 The effects of a trust mechanism on a dynamic - /39 Economic and environmental assessment of reusable plastic containers: A food catering - case study40 Competitive pricing and ordering decisions in a multiple-channel -41 Pricing in a - for auction bidding under information asymmetry42 Dynamic analysis of feasibility in ethanol - for biofuel production in Mexico43 The impact of partial information sharing in a two-echelon -44 Choice of - governance: Self-managing or outsourcing?45 Joint production and delivery lot sizing for a make-to-order producer–buyer - with transportation cost46 Hybrid algorithm for a vendor managed inventory system in a two-echelon -47 Traceability in a food -: Safety and quality perspectives48 Transferring and sharing exchange-rate risk in a risk-averse - of a multinational firm49 Analyzing the impacts of carbon regulatory mechanisms on supplier and mode selection decisions: An application to a biofuel -50 Product quality and return policy in a - under risk aversion of a supplier51 Mining logistics data to assure the quality in a sustainable food -: A case in the red wine industry52 Biomass - optimisation for Organosolv-based biorefineries53 Exact solutions to the - equations for arbitrary, time-dependent demands54 Designing a sustainable closed-loop - / based on triple bottom line approach: A comparison of metaheuristics hybridization techniques55 A study of the LCA based biofuel - multi-objective optimization model with multi-conversion paths in China56 A hybrid two-stock inventory control model for a reverse -57 Dynamics of judicial service -s58 Optimizing an integrated vendor-managed inventory system for a single-vendor two-buyer - with determining weighting factor for vendor׳s ordering59 Measuring - Resilience Using a Deterministic Modeling Approach60 A LCA Based Biofuel - Analysis Framework61 A neo-institutional perspective of -s and energy security: Bioenergy in the UK62 Modified penalty function method for optimal social welfare of electric power - with transmission constraints63 Optimization of blood - with shortened shelf lives and ABO compatibility64 Diversified firms on dynamical - cope with financial crisis better65 Securitization of energy -s in China66 Optimal design of the auto parts - for JIT operations: Sequential bifurcation factor screening and multi-response surface methodology67 Achieving sustainable -s through energy justice68 - agility: Securing performance for Chinese manufacturers69 Energy price risk and the sustainability of demand side -s70 Strategic and tactical mathematical programming models within the crude oil - context - A review71 An analysis of the structural complexity of - /s72 Business process re-design methodology to support - integration73 Could - technology improve food operators’ innovativeness? A developing country’s perspective74 RFID-enabled process reengineering of closed-loop -s in the healthcare industry of Singapore75 Order-Up-To policies in Information Exchange -s76 Robust design and operations of hydrocarbon biofuel - integrating with existing petroleum refineries considering unit cost objective77 Trade-offs in - transparency: the case of Nudie Jeans78 Healthcare - operations: Why are doctors reluctant to consolidate?79 Impact on the optimal design of bioethanol -s by a new European Commission proposal80 Managerial research on the pharmaceutical - – A critical review and some insights for future directions81 - performance evaluation with data envelopment analysis and balanced scorecard approach82 Integrated - design for commodity chemicals production via woody biomass fast pyrolysis and upgrading83 Governance of sustainable -s in the fast fashion industry84 Temperature ,for the quality assurance of a perishable food -85 Modeling of biomass-to-energy - operations: Applications, challenges and research directions86 Assessing Risk Factors in Collaborative - with the Analytic Hierarchy Process (AHP)87 Random / models and sensitivity algorithms for the analysis of ordering time and inventory state in multi-stage -s88 Information sharing and collaborative behaviors in enabling - performance: A social exchange perspective89 The coordinating contracts for a fuzzy - with effort and price dependent demand90 Criticality analysis and the -: Leveraging representational assurance91 Economic model predictive control for inventory ,in -s92 - ,ontology from an ontology engineering perspective93 Surplus division and investment incentives in -s: A biform-game analysis94 Biofuels for road transport: Analysing evolving -s in Sweden from an energy security perspective95 - ,executives in corporate upper echelons Original Research Article96 Sustainable - ,in the fast fashion industry: An analysis of corporate reports97 An improved method for managing catastrophic - disruptions98 The equilibrium of closed-loop - super/ with time-dependent parameters99 A bi-objective stochastic programming model for a centralized green - with deteriorating products100 Simultaneous control of vehicle routing and inventory for dynamic inbound -101 Environmental impacts of roundwood - options in Michigan: life-cycle assessment of harvest and transport stages102 A recovery mechanism for a two echelon - system under supply disruption103 Challenges and Competitiveness Indicators for the Sustainable Development of the - in Food Industry104 Is doing more doing better? The relationship between responsible - ,and corporate reputation105 Connecting product design, process and - decisions to strengthen global - capabilities106 A computational study for common / design in multi-commodity -s107 Optimal production and procurement decisions in a - with an option contract and partial backordering under uncertainties108 Methods to optimise the design and ,of biomass-for-bioenergy -s: A review109 Reverse - coordination by revenue sharing contract: A case for the personal computers industry110 SCOlog: A logic-based approach to analysing - operation dynamics111 Removing the blinders: A literature review on the potential of nanoscale technologies for the ,of -s112 Transition inertia due to competition in -s with remanufacturing and recycling: A systems dynamics mode113 Optimal design of advanced drop-in hydrocarbon biofuel - integrating with existing petroleum refineries under uncertainty114 Revenue-sharing contracts across an extended -115 An integrated revenue sharing and quantity discounts contract for coordinating a - dealing with short life-cycle products116 Total JIT (T-JIT) and its impact on - competency and organizational performance117 Logistical - design for bioeconomy applications118 A note on ―Quality investment and inspection policy in a supplier-manufacturer -‖119 Developing a Resilient -120 Cyber - risk ,: Revolutionizing the strategic control of critical IT systems121 Defining value chain architectures: Linking strategic value creation to operational - design122 Aligning the sustainable - to green marketing needs: A case study123 Decision support and intelligent systems in the textile and apparel -: An academic review of research articles124 - ,capability of small and medium sized family businesses in India: A multiple case study approach125 - collaboration: Impact of success in long-term partnerships126 Collaboration capacity for sustainable - ,: small and medium-sized enterprises in Mexico127 Advanced traceability system in aquaculture -128 - information systems strategy: Impacts on - performance and firm performance129 Performance of - collaboration – A simulation study130 Coordinating a three-level - with delay in payments and a discounted interest rate131 An integrated framework for agent basedinventory–production–transportation modeling and distributed simulation of -s132 Optimal - design and ,over a multi-period horizon under demand uncertainty. Part I: MINLP and MILP models133 The impact of knowledge transfer and complexity on - flexibility: A knowledge-based view134 An innovative - performance measurement system incorporating Research and Development (R&D) and marketing policy135 Robust decision making for hybrid process - systems via model predictive control136 Combined pricing and - operations under price-dependent stochastic demand137 Balancing - competitiveness and robustness through ―virtual dual sourcing‖: Lessons from the Great East Japan Earthquake138 Solving a tri-objective - problem with modified NSGA-II algorithm 139 Sustaining long-term - partnerships using price-only contracts 140 On the impact of advertising initiatives in -s141 A typology of the situations of cooperation in -s142 A structured analysis of operations and - ,research in healthcare (1982–2011143 - practice and information quality: A - strategy study144 Manufacturer's pricing strategy in a two-level - with competing retailers and advertising cost dependent demand145 Closed-loop - / design under a fuzzy environment146 Timing and eco(nomic) efficiency of climate-friendly investments in -s147 Post-seismic - risk ,: A system dynamics disruption analysis approach for inventory and logistics planning148 The relationship between legitimacy, reputation, sustainability and branding for companies and their -s149 Linking - configuration to - perfrmance: A discrete event simulation model150 An integrated multi-objective model for allocating the limited sources in a multiple multi-stage lean -151 Price and leadtime competition, and coordination for make-to-order -s152 A model of resilient - / design: A two-stage programming with fuzzy shortest path153 Lead time variation control using reliable shipment equipment: An incentive scheme for - coordination154 Interpreting - dynamics: A quasi-chaos perspective155 A production-inventory model for a two-echelon - when demand is dependent on sales teams׳ initiatives156 Coordinating a dual-channel - with risk-averse under a two-way revenue sharing contract157 Energy supply planning and - optimization under uncertainty158 A hierarchical model of the impact of RFID practices on retail - performance159 An optimal solution to a three echelon - / with multi-product and multi-period160 A multi-echelon - model for municipal solid waste ,system 161 A multi-objective approach to - visibility and risk162 An integrated - model with errors in quality inspection and learning in production163 A fuzzy AHP-TOPSIS framework for ranking the solutions of Knowledge ,adoption in - to overcome its barriers164 A relational study of - agility, competitiveness and business performance in the oil and gas industry165 Cyber - security practices DNA – Filling in the puzzle using a diverse set of disciplines166 A three layer - model with multiple suppliers, manufacturers and retailers for multiple items167 Innovations in low input and organic dairy -s—What is acceptable in Europe168 Risk Variables in Wind Power -169 An analysis of - strategies in the regenerative medicine industry—Implications for future development170 A note on - coordination for joint determination of order quantity and reorder point using a credit option171 Implementation of a responsive - strategy in global complexity: The case of manufacturing firms172 - scheduling at the manufacturer to minimize inventory holding and delivery costs173 GBOM-oriented ,of production disruption risk and optimization of - construction175 Alliance or no alliance—Bargaining power in competing reverse -s174 Climate change risks and adaptation options across Australian seafood -s – A preliminary assessment176 Designing contracts for a closed-loop - under information asymmetry 177 Chemical - modeling for analysis of homeland security178 Chain liability in multitier -s? Responsibility attributions for unsustainable supplier behavior179 Quantifying the efficiency of price-only contracts in push -s over demand distributions of known supports180 Closed-loop - / design: A financial approach181 An integrated - / design problem for bidirectional flows182 Integrating multimodal transport into cellulosic biofuel - design under feedstock seasonality with a case study based on California183 - dynamic configuration as a result of new product development184 A genetic algorithm for optimizing defective goods - costs using JIT logistics and each-cycle lengths185 A - / design model for biomass co-firing in coal-fired power plants 186 Finance sourcing in a -187 Data quality for data science, predictive analytics, and big data in - ,: An introduction to the problem and suggestions for research and applications188 Consumer returns in a decentralized -189 Cost-based pricing model with value-added tax and corporate income tax for a - /190 A hard nut to crack! Implementing - sustainability in an emerging economy191 Optimal location of spelling yards for the northern Australian beef -192 Coordination of a socially responsible - using revenue sharing contract193 Multi-criteria decision making based on trust and reputation in -194 Hydrogen - architecture for bottom-up energy systems models. Part 1: Developing pathways195 Financialization across the Pacific: Manufacturing cost ratios, -s and power196 Integrating deterioration and lifetime constraints in production and - planning: A survey197 Joint economic lot sizing problem for a three—Layer - with stochastic demand198 Mean-risk analysis of radio frequency identification technology in - with inventory misplacement: Risk-sharing and coordination199 Dynamic impact on global -s performance of disruptions propagation produced by terrorist acts。
ad域面试要点 -回复

ad域面试要点-回复Active Directory (AD) is Microsoft's directory service that provides centralized authentication, authorization, and management of resources within a Windows domain. AD is a crucial component in a Windows network infrastructure, and as such, proficiency in AD is essential for any IT professional working with Windows-based systems. In this article, we will explore the key points to cover in an AD domain interview, focusing on the topics mentioned within square brackets.[Overview of AD Domain Structure]Before diving into the specific interview questions, it is essential to have a solid understanding of AD domain structure. An AD domain is a logical grouping of computers, users, and other network resources that share a common directory database. AD follows a hierarchical structure, with the domain being the primary administrative unit. Within a domain, you can have multiple domain controllers (DCs) that share the responsibility of authenticating users and managing resources.[Key Components of AD]1. Domain Controllers (DCs): Domain controllers are serversrunning Windows Server operating systems and hosting AD services. They store the AD database, authenticate users, and handle resource management within the domain.2. Domains: Domains are the basic administrative units within AD. They provide a boundary for security policy enforcement and replication boundaries for AD data.3. Organizational Units (OUs): OUs are containers within a domain used to organize and manage objects, such as users, groups, and computers. OUs enable administrators to apply group policies and delegate administrative control.4. Forests: A forest is a collection of one or more domains that share a common schema, configuration, and global catalog. Forests enable organizations to implement separate AD namespaces while still maintaining a level of interoperability.[AD Authentication]A significant aspect of AD is user authentication. Here are some commonly asked questions related to this topic:1. How does AD authenticate users?AD uses the Kerberos authentication protocol by default. When a user logs in to a domain, their credentials are validated by a domain controller using Kerberos.2. What is the purpose of the Global Catalog (GC)?The Global Catalog is a distributed data repository that contains a subset of all objects from every domain in a forest. It allows users to search for objects from any domain without the need to contact multiple domain controllers.[Group Policy Management]Group Policy is a powerful feature of AD that allows administrators to manage settings and configurations for users and computers. Here are some key points related to Group Policy:1. What is Group Policy?Group Policy is a set of rules and configurations that can be applied to users and computers within a domain or an OU. It enables administrators to define security settings, deploy software, and manage user environment settings.2. How are Group Policies stored and applied?Group Policies are stored within the SysVol directory on domain controllers and replicated to all DCs in the domain. Policies are applied to users and computers when they log in to the domain. They are hierarchical in nature and are processed from the domain level down to the OU level.[Replication and High Availability]Maintaining a highly available and efficient AD environment requires proper replication and fault tolerance. Consider the following points:1. How does AD replication work?AD replication is the process of synchronizing changes made to the AD database between domain controllers. Replication follows a multi-master model, where all domain controllers are equal and can make changes. Replication traffic is compressed and encrypted.2. What is Tombstone Lifetime?The Tombstone Lifetime is the period for which deleted objects are retained in AD. After this period, the deleted objects are permanently removed from the AD database.[Tools and Utilities]Having knowledge of the various tools and utilities available for AD management is essential. Some commonly used tools include:1. Active Directory Users and Computers: This tool provides a graphical user interface for managing AD objects, such as users, groups, and OUs.2. Active Directory Sites and Services: This tool allows administrators to manage AD replication, create and manage site links, and define site boundaries.In summary, mastering the key aspects of AD domain structure, authentication, group policy management, replication, and the associated tools and utilities is crucial for success in an AD domain interview. By demonstrating a solid understanding of these topics, you will showcase your proficiency in managing and troubleshooting AD environments.。
软件开发工具使用考核试卷

C. Visual Studio
D. Mercurial
2.以下哪个IDE(集成开发环境)主要用于Java开发?()
A. Visual Studio
B. Xcode
C. Eclipse
D. Sublime Text
3.以下哪个工具不是用于代码质量检查的?()
A. SonarQube
B. JUnit
2.在使用集成开发环境(IDE)进行软件开发时,请描述至少三种可以提高开发效率的功能或特性。
3.请解释什么是持续集成(Continuous Integration)和持续部署(Continuous Deployment),并简述它们在软件开发过程中的作用。
4.在进行软件测试时,请阐述为什么自动化测试比手动测试更高效,并列举至少三种常用的自动化测试工具。
C. Checkstyle
D. Maven
4.在Python开发中,以下哪个工具用于自动化测试?()
A. pip
B. virtualenv
C. pytest
D. Django
5.以下哪个数据库管理工具主要用于SQL Server?()
A. MySQL Workbench
B. SQL Server Management Studio
B. Azure Resource Manager
C. Google Cloud Deployment Manager
D. Alibaba Cloud ROS
13.以下哪些工具可以用于网络抓包?()(1.5分)
A. Wireshark
B. Fiddler
C. Charles
D. Tcpdump
14.在Python开发中,以下哪些工具可以用于虚拟环境管理?()(1.5分)
深度优先局部聚合哈希

Vol.48,No.6Jun. 202 1第48卷第6期2 0 2 1年6月湖南大学学报)自然科学版)Journal of Hunan University (Natural Sciences )文章编号:1674-2974(2021 )06-0058-09 DOI : 10.16339/ki.hdxbzkb.2021.06.009深度优先局艺B 聚合哈希龙显忠g,程成李云12(1.南京邮电大学计算机学院,江苏南京210023;2.江苏省大数据安全与智能处理重点实验室,江苏南京210023)摘 要:已有的深度监督哈希方法不能有效地利用提取到的卷积特征,同时,也忽视了数据对之间相似性信息分布对于哈希网络的作用,最终导致学到的哈希编码之间的区分性不足.为了解决该问题,提出了一种新颖的深度监督哈希方法,称之为深度优先局部聚合哈希(DeepPriority Local Aggregated Hashing , DPLAH ). DPLAH 将局部聚合描述子向量嵌入到哈希网络 中,提高网络对同类数据的表达能力,并且通过在数据对之间施加不同权重,从而减少相似性 信息分布倾斜对哈希网络的影响.利用Pytorch 深度框架进行DPLAH 实验,使用NetVLAD 层 对Resnet18网络模型输出的卷积特征进行聚合,将聚合得到的特征进行哈希编码学习.在CI-FAR-10和NUS-WIDE 数据集上的图像检索实验表明,与使用手工特征和卷积神经网络特征的非深度哈希学习算法的最好结果相比,DPLAH 的平均准确率均值要高出11%,同时,DPLAH 的平均准确率均值比非对称深度监督哈希方法高出2%.关键词:深度哈希学习;卷积神经网络;图像检索;局部聚合描述子向量中图分类号:TP391.4文献标志码:ADeep Priority Local Aggregated HashingLONG Xianzhong 1,覮,CHENG Cheng1,2,LI Yun 1,2(1. School of Computer Science & Technology ,Nanjing University of Posts and Telecommunications ,Nanjing 210023, China ;2. Key Laboratory of Jiangsu Big Data Security and Intelligent Processing ,Nanjing 210023, China )Abstract : The existing deep supervised hashing methods cannot effectively utilize the extracted convolution fea tures, but also ignore the role of the similarity information distribution between data pairs on the hash network, result ing in insufficient discrimination between the learned hash codes. In order to solve this problem, a novel deep super vised hashing method called deep priority locally aggregated hashing (DPLAH) is proposed in this paper, which em beds the vector of locally aggregated descriptors (VLAD) into the hash network, so as to improve the ability of the hashnetwork to express the similar data, and reduce the impact of similarity distribution skew on the hash network by im posing different weights on the data pairs. DPLAH experiment is carried out by using the Pytorch deep framework. Theconvolution features of the Resnet18 network model output are aggregated by using the NetVLAD layer, and the hashcoding is learned by using the aggregated features. The image retrieval experiments on the CIFAR-10 and NUS - WIDE datasets show that the mean average precision (MAP) of DPLAH is11 percentage points higher than that of* 收稿日期:2020-04-26基金项目:国家自然科学基金资助项目(61906098,61772284),National Natural Science Foundation of China(61906098, 61772284);国家重 点研发计划项目(2018YFB 1003702) , National Key Research and Development Program of China (2018YFB1003702)作者简介:龙显忠(1985—),男,河南信阳人,南京邮电大学讲师,工学博士,硕士生导师覮 通信联系人,E-mail : *************.cn第6期龙显忠等:深度优先局部聚合哈希59non-deep hash learning algorithms using manual features and convolution neural network features,and the MAP of DPLAH is2percentage points higher than that of asymmetric deep supervised hashing method.Key words:deep Hash learning;convolutional neural network;image retrieval;vector of locally aggregated de-scriptors(VLAD)随着信息检索技术的不断发展和完善,如今人们可以利用互联网轻易获取感兴趣的数据内容,然而,信息技术的发展同时导致了数据规模的迅猛增长.面对海量的数据以及超大规模的数据集,利用最近邻搜索[1(Nearest Neighbor Search,NN)的检索技术已经无法获得理想的检索效果与可接受的检索时间.因此,近年来,近似最近邻搜索[2(Approximate Nearest Neighbor Search,ANN)变得越来越流行,它通过搜索可能相似的几个数据而不再局限于返回最相似的数据,在牺牲可接受范围的精度下提高了检索效率.作为一种广泛使用的ANN搜索技术,哈希方法(Hashing)[3]将数据转换为紧凑的二进制编码(哈希编码)表示,同时保证相似的数据对生成相似的二进制编码.利用哈希编码来表示原始数据,显著减少了数据的存储和查询开销,从而可以应对大规模数据中的检索问题.因此,哈希方法吸引了越来越多学者的关注.当前哈希方法主要分为两类:数据独立的哈希方法和数据依赖的哈希方法,这两类哈希方法的区别在于哈希函数是否需要训练数据来定义.局部敏感哈希(Locality Sensitive Hashing,LSH)[4]作为数据独立的哈希代表,它利用独立于训练数据的随机投影作为哈希函数•相反,数据依赖哈希的哈希函数需要通过训练数据学习出来,因此,数据依赖的哈希也被称为哈希学习,数据依赖的哈希通常具有更好的性能.近年来,哈希方法的研究主要侧重于哈希学习方面.根据哈希学习过程中是否使用标签,哈希学习方法可以进一步分为:监督哈希学习和无监督哈希学习.典型的无监督哈希学习包括:谱哈希[5(Spectral Hashing,SH);迭代量化哈希[6](Iterative Quantization, ITQ);离散图哈希[7(Discrete Graph Hashing,DGH);有序嵌入哈希[8](Ordinal Embedding Hashing,OEH)等.无监督哈希学习方法仅使用无标签的数据来学习哈希函数,将输入的数据映射为哈希编码的形式.相反,监督哈希学习方法通过利用监督信息来学习哈希函数,由于利用了带有标签的数据,监督哈希方法往往比无监督哈希方法具有更好的准确性,本文的研究主要针对监督哈希学习方法.传统的监督哈希方法包括:核监督哈希[9](Supervised Hashing with Kernels,KSH);潜在因子哈希[10](Latent Factor Hashing,LFH);快速监督哈希[11](Fast Supervised Hashing,FastH);监督离散哈希[1(Super-vised Discrete Hashing,SDH)等.随着深度学习技术的发展[13],利用神经网络提取的特征已经逐渐替代手工特征,推动了深度监督哈希的进步.具有代表性的深度监督哈希方法包括:卷积神经网络哈希[1(Convolutional Neural Networks Hashing,CNNH);深度语义排序哈希[15](Deep Semantic Ranking Based Hash-ing,DSRH);深度成对监督哈希[16](Deep Pairwise-Supervised Hashing,DPSH);深度监督离散哈希[17](Deep Supervised Discrete Hashing,DSDH);深度优先哈希[18](Deep Priority Hashing,DPH)等.通过将特征学习和哈希编码学习(或哈希函数学习)集成到一个端到端网络中,深度监督哈希方法可以显著优于非深度监督哈希方法.到目前为止,大多数现有的深度哈希方法都采用对称策略来学习查询数据和数据集的哈希编码以及深度哈希函数.相反,非对称深度监督哈希[19](Asymmetric Deep Supervised Hashing,ADSH)以非对称的方式处理查询数据和整个数据库数据,解决了对称方式中训练开销较大的问题,仅仅通过查询数据就可以对神经网络进行训练来学习哈希函数,整个数据库的哈希编码可以通过优化直接得到.本文的模型同样利用了ADSH的非对称训练策略.然而,现有的非对称深度监督哈希方法并没有考虑到数据之间的相似性分布对于哈希网络的影响,可能导致结果是:容易在汉明空间中保持相似关系的数据对,往往会被训练得越来越好;相反,那些难以在汉明空间中保持相似关系的数据对,往往在训练后得到的提升并不显著.同时大部分现有的深度监督哈希方法在哈希网络中没有充分有效利用提60湖南大学学报(自然科学版)2021年取到的卷积特征.本文提出了一种新的深度监督哈希方法,称为深度优先局部聚合哈希(Deep Priority Local Aggregated Hashing,DPLAH).DPLAH的贡献主要有三个方面:1)DPLAH采用非对称的方式处理查询数据和数据库数据,同时DPLAH网络会优先学习查询数据和数据库数据之间困难的数据对,从而减轻相似性分布倾斜对哈希网络的影响.2)DPLAH设计了全新的深度哈希网络,具体来说,DPLAH将局部聚合表示融入到哈希网络中,提高了哈希网络对同类数据的表达能力.同时考虑到数据的局部聚合表示对于分类任务的有效性.3)在两个大型数据集上的实验结果表明,DPLAH在实际应用中性能优越.1相关工作本节分别对哈希学习[3]、NetVLAD[20]和Focal Loss[21]进行介绍.DPLAH分别利用NetVLAD和Focal Loss提高哈希网络对同类数据的表达能力及减轻数据之间相似性分布倾斜对于哈希网络的影响. 1.1哈希学习哈希学习[3]的任务是学习查询数据和数据库数据的哈希编码表示,同时要满足原始数据之间的近邻关系与数据哈希编码之间的近邻关系相一致的条件.具体来说,利用机器学习方法将所有数据映射成{0,1}r形式的二进制编码(r表示哈希编码长度),在原空间中不相似的数据点将被映射成不相似)即汉明距离较大)的两个二进制编码,而原空间中相似的两个数据点将被映射成相似(即汉明距离较小)的两个二进制编码.为了便于计算,大部分哈希方法学习{-1,1}r形式的哈希编码,这是因为{-1,1}r形式的哈希编码对之间的内积等于哈希编码的长度减去汉明距离的两倍,同时{-1,1}r形式的哈希编码可以容易转化为{0,1}r形式的二进制编码.图1是哈希学习的示意图.经过特征提取后的高维向量被用来表示原始图像,哈希函数h将每张图像映射成8bits的哈希编码,使原来相似的数据对(图中老虎1和老虎2)之间的哈希编码汉明距离尽可能小,原来不相似的数据对(图中大象和老虎1)之间的哈希编码汉明距离尽可能大.h(大象)=10001010h(老虎1)=01100001h(老虎2)=01100101相似度尽可能小相似度尽可能大图1哈希学习示意图Fig.1Hashing learning diagram1.2NetVLADNetVLAD的提出是用于解决端到端的场景识别问题[20(场景识别被当作一个实例检索任务),它将传统的局部聚合描述子向量(Vector of Locally Aggregated Descriptors,VLAD[22])结构嵌入到CNN网络中,得到了一个新的VLAD层.可以容易地将NetVLAD 使用在任意CNN结构中,利用反向传播算法进行优化,它能够有效地提高对同类别图像的表达能力,并提高分类的性能.NetVLAD的编码步骤为:利用卷积神经网络提取图像的卷积特征;利用NetVLAD层对卷积特征进行聚合操作.图2为NetVLAD层的示意图.在特征提取阶段,NetVLAD会在最后一个卷积层上裁剪卷积特征,并将其视为密集的描述符提取器,最后一个卷积层的输出是H伊W伊D映射,可以将其视为在H伊W空间位置提取的一组D维特征,该方法在实例检索和纹理识别任务[23別中都表现出了很好的效果.NetVLAD layer(KxD)x lVLADvectorh------->图2NetVLAD层示意图⑷Fig.2NetVLAD layer diagram1201NetVLAD在特征聚合阶段,利用一个新的池化层对裁剪的CNN特征进行聚合,这个新的池化层被称为NetVLAD层.NetVLAD的聚合操作公式如下:NV((,k)二移a(x)(血⑺-C((j))(1)i=1式中:血(j)和C)(j)分别表示第i个特征的第j维和第k个聚类中心的第j维;恣&)表示特征您与第k个视觉单词之间的权.NetVLAD特征聚合的输入为:NetVLAD裁剪得到的N个D维的卷积特征,K个聚第6期龙显忠等:深度优先局部聚合哈希61类中心.VLAD的特征分配方式是硬分配,即每个特征只和对应的最近邻聚类中心相关联,这种分配方式会造成较大的量化误差,并且,这种分配方式嵌入到卷积神经网络中无法进行反向传播更新参数.因此,NetVLAD采用软分配的方式进行特征分配,软分配对应的公式如下:-琢II Xi-C*II 2=—e(2)-琢II X-Ck,II2k,如果琢寅+肄,那么对于最接近的聚类中心,龟&)的值为1,其他为0.aS)可以进一步重写为:w j X i+b ka(x i)=—e-)3)w J'X i+b kk,式中:W k=2琢C k;b k=-琢||C k||2.最终的NetVLAD的聚合表示可以写为:N w;x+b kv(j,k)=移—----(x(j)-Ck(j))(4)i=1w j.X i+b k移ek,1.3Focal Loss对于目标检测方法,一般可以分为两种类型:单阶段目标检测和两阶段目标检测,通常情况下,两阶段的目标检测效果要优于单阶段的目标检测.Lin等人[21]揭示了前景和背景的极度不平衡导致了单阶段目标检测的效果无法令人满意,具体而言,容易被分类的背景虽然对应的损失很低,但由于图像中背景的比重很大,对于损失依旧有很大的贡献,从而导致收敛到不够好的一个结果.Lin等人[21]提出了Focal Loss应对这一问题,图3是对应的示意图.使用交叉爛作为目标检测中的分类损失,对于易分类的样本,它的损失虽然很低,但数据的不平衡导致大量易分类的损失之和压倒了难分类的样本损失,最终难分类的样本不能在神经网络中得到有效的训练.Focal Loss的本质是一种加权思想,权重可根据分类正确的概率p得到,利用酌可以对该权重的强度进行调整.针对非对称深度哈希方法,希望难以在汉明空间中保持相似关系的数据对优先训练,具体来说,对于DPLAH的整体训练损失,通过施加权重的方式,相对提高难以在汉明空间中保持相似关系的数据对之间的训练损失.然而深度哈希学习并不是一个分类任务,因此无法像Focal Loss一样根据分类正确的概率设计权重,哈希学习的目的是学到保相似性的哈希编码,本文最终利用数据对哈希编码的相似度作为权重的设计依据具体的权重形式将在模型部分详细介绍.正确分类的概率图3Focal Loss示意图[21】Fig.3Focal Loss diagram12112深度优先局部聚合哈希2.1基本定义DPLAH模型采用非对称的网络设计.Q={0},=1表示n张查询图像,X={X i}m1表示数据库有m张图像;查询图像和数据库图像的标签分别用Z={Z i},=1和Y ={川1表示;i=[Z i1,…,zj1,i=1,…,n;c表示类另数;如果查询图像0属于类别j,j=1,…,c;那么z”=1,否则=0.利用标签信息,可以构造图像对的相似性矩阵S沂{-1,1}"伊”,s”=1表示查询图像q,和数据库中的图像X j语义相似,S j=-1表示查询图像和数据库中的图像X j语义不相似.深度哈希方法的目标是学习查询图像和数据库中图像的哈希编码,查询图像的哈希编码用U沂{-1,1}"",表示,数据库中图像的哈希编码用B沂{-1,1}m伊r表示,其中r表示哈希编码的长度.对于DPLAH模型,它在特征提取部分采用预训练好的Resnet18网络[25].图4为DPLAH网络的结构示意图,利用NetVLAD层聚合Resnet18网络提取到的卷积特征,哈希编码通过VLAD编码得到,由于VLAD编码在分类任务中被广泛使用,于是本文将NetVLAD层的输出作为分类任务的输入,利用图像的标签信息监督NetVLAD层对卷积特征的利用.事实上,任何一种CNN模型都能实现图像特征提取的功能,所以对于选用哪种网络进行特征学习并不是本文的重点.62湖南大学学报(自然科学版)2021年conv1图4DPLAH结构Fig.4DPLAH structure图像标签soft-max1,0,1,1,0□1,0,0,0,11,1,0,1,0---------*----------VLADVLAD core)c)l・>:i>数据库图像的哈希编码2.2DPLAH模型的目标函数为了学习可以保留查询图像与数据库图像之间相似性的哈希编码,一种常见的方法是利用相似性的监督信息S e{-1,1}n伊"、生成的哈希编码长度r,以及查询图像的哈希编码仏和数据库中图像的哈希编码b三者之间的关系[9],即最小化相似性的监督信息与哈希编码对内积之间的L损失.考虑到相似性分布的倾斜问题,本文通过施加权重来调节查询图像和数据库图像之间的损失,其公式可以表示为:min J=移移(1-w)(u T b j-rs)专,B i=1j=1s.t.U沂{-1,1}n伊r,B沂{-1,1}m伊r,W沂R n伊m(5)受FocalLoss启发,希望深度哈希网络优先训练相似性不容易保留图像对,然而Focal Loss利用图像的分类结果对损失进行调整,因此,需要重新进行设计,由于哈希学习的目的是为了保留图像在汉明空间中的相似性关系,本文利用哈希编码的余弦相似度来设计权重,其表达式为:1+。
云原生应用设计与开发实践考核试卷

D. Prometheus
14.以下哪个不是云原生应用架构的优势?()
A.提高开发效率
B.降低运维成本
C.系统高度耦合
D.灵活扩展
15.以下哪个不是云原生应用开发工具?()
A. Skaffold
B. Draft
C. Helm
D. Maven
16.在Kubernetes中,以下哪个资源用于定义存储卷?()
47.持续集成和持续部署的缩写分别是__________和__________。
48. __________是Kubernetes中用于暴露应用服务的资源类型。
49. __________是一个开源的服务网格,提供了微服务之间通信的延迟和故障注入等功能。
50.在云原生应用开发中,__________是一种声明式API,用于管理Kubernetes集群中的配置。
C.自动化运维
D.物理服务器
22.以下哪些是Kubernetes的内置资源类型?()
A. Pod
B. Service
C. Node
D. Database
23.云原生应用中,以下哪些工具可以用于持续集成和持续部署?()
A. Jenkins
B. GitLab CI
C. Travis CI
D. Docker Compose
63.请阐述服务网格(Service Mesh)在云原生应用架构中的作用,并列举至少三个服务网格的主要功能。
64.在设计云原生应用时,如何考虑应用的可观测性?请列举至少三种常用的可观测性工具,并简要说明它们的作用。
标准答案
一、单项选择题
1. C
2. C3. B4. C来自5. D6. A
osi 参考模型的三个概念

osi 参考模型的三个概念英文回答:The Open Systems Interconnection (OSI) Reference Model is a conceptual framework that defines a standardized approach to network communication. It is a seven-layer model, with each layer building upon the functionality of the layers below it. The three fundamental concepts of the OSI Reference Model are:1. Abstraction: Each layer of the OSI Reference Model abstracts the complexity of the underlying layers from the layers above it. This allows each layer to focus on its own specific set of tasks, without having to worry about the details of how the lower layers work.2. Encapsulation: Data is passed from one layer to the next in a process called encapsulation. Each layer adds its own header and trailer information to the data, which is then passed to the next layer. This process continues untilthe data reaches the physical layer, which transmits the data over the network.3. Layering: The OSI Reference Model is a hierarchical model, with each layer building upon the functionality of the layers below it. This allows each layer to focus on its own specific set of tasks, without having to worry aboutthe details of how the lower layers work.中文回答:开放式系统互联(OSI)参考模型是一个概念框架,定义了一种网络通信的标准化方法。
(完整版)川大软院计网选择题答案Chapter1(含答案)

(完整版)川大软院计网选择题答案Chapter1(含答案)1.1 In the following options, which does not define in protocol? ( D )A the format of messages exchanged between two or more communicatingentitiesB the order of messages exchanged between two or more communicating entitiesC the actions taken on the transmission of a message or other eventD the transmission signals are digital signals or analog signals1.2 In the following options, which is defined in protocol? ( A )A the actions taken on the transmission and/or receipt of a message or other eventB the objects exchanged between communicating entitiesC the content in the exchanged messagesD the location of the hosts1.3 An application can rely on the connection to deliver all of its data without error and in the proper order. The sentence describes (C ).A flow controlB congestion-controlC reliable data transferD connection-oriented service1.4 The Internet’s connection-oriented service has a name, it is ( A ).A TCPB UDPC TCP/IPD IP1.5 The Internet’s connectionless service is called ( B ).A TCPB UDPC TCP/IPD IP1.6 Which of the following nodes belongs to the network core?CA. a Web ServerB. a Host with Win2003 ServerC. a Router with NAT serviceD. a Supernode on Skype Network1.7 In the Internet, the equivalent concept to end systems is ( )A.A hostsB serversC clientsD routers1.8 In the Internet, end systems are connected together by ( C ).A copper wireB coaxial cableC communication linksD fiber optics1.9 End systems access to the Internet through its (C ).A modemsB protocolsC ISPD sockets1.10 In the following options, which belongs to the network core? ( B )A end systemsB routersC clientsD servers1.11 End systems, packet switches, and other pieces of the Internet, run ( D ) that control the sending and receiving of information within the Internet.A programsB processesC applicationsD protocols1.12 The internet allows ( D ) running on its end systems to exchange data with each other.A clients applicationsB server applicationsC P2P applicationsD distributed applications1.13 The protocols of various layers are called ( A ).A the protocol stackB TCP/IPC ISPD network protocol1.14 In the OSI reference model, the upper layers of the OSI model are, in correct orderDA Session, application, presentationB Session, presentation, applicationC Session, application, presentation, physicalD Application, presentation, session1.15 The lower layers of the OSI model are, in correct orderDA physical, system, network, logicalB physical, logical, network, systemC physical, transport, network, data linkD physical, data link, network, transport1.16 The Internet Protocol (IP) generally corresponds to which OSI layer?AA Network (layer three)B Transport (layer four)C Data link (layer two)D Session (layer five)1.17 What layer of the OSI model is designed to perform error detection functions?BA PhysicalB Data linkC NetworkD transport1.18 Which of the following protocol layers is not explicitly part of the Internet Protocol Stack? _____B____A. application layerB. session layerC. data link layerD. transport layer1.19 The 5-PDU is called__A_A. messageB. segmentC. datagramD. frame1.20 The Internet’s network l ayer is responsible for moving network-layer packets known as B( ) from one host to another.A frameB datagramC segmentD message1.21 Transport-layer packets are called:BA. messageB. segmentC. datagramD. frame1.22 The units of data exchanged by a link-layer protocol are called ( A).A FramesB SegmentsC DatagramsD bit streams1.23 There are two fundamental approaches to building a network core, ( B ) and packet switching.A electrical current switchingB circuit switchingC data switchingD message switching1.24 Datagram networks and virtual-circuit networks differ in that ( C ).A datagram networks are circuit-switched networks, and virtual-circuit networksare packet-switched networks.B datagram networks are packet-switched networks, and virtual-circuit networksare circuit-switched networks.C datagram networks use destination addresses and virtual-circuit networks useVC. numbers to forward packets toward their destination.D datagram networks use VC. numbers and virtual-circuit networks usedestination addresses to forward packets toward their destination.1.25 (A ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Store-and-forward transmissionB FDMC End-to-end connectionD TDM1.26 In ( C ) networks, the resources needed along a path to provide for communication between the end system are reserved for the duration of the communication session.A packet-switchedB data-switchedC circuit-switchedD message-switched1.27 In ( A ) networks, the resources are not reserved; a session’s messages use the resources on demand, and as a consequence, may have to wait for access to communication link.A packet-switchedB data-switchedC circuit-switchedD message-switched1.28 In a circuit-switched network, if each link has n circuits, for each link used by the end-to-end connection, the connection gets ( A) of the link’s bandwidth for the duration of theconnection.A a fraction 1/nB allC 1/2D n times1.29 For (C ), the transmission rate of a circuit is equal to the frame rate multiplied by the number of bits in a slot.A CDMAB packet-switched networkC TDMD FDM1.30 The network that forwards packets according to host destination addresses is called ( D) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram1.31 The network that forwards packets according to virtual-circuit numbers is called ( C ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram1.32 The time required to propagate from the beginning of the link to the next router is ( C).A queuing delayB processing delayC propagation delayD transmission delay1.33 Processing delay does not include the time to (B ).A examine the packet’s headerB wait to transmit the packet onto the linkC determine where to direct the packetD check bit-error in the packet1.34 In the following four descriptions, which one is correct? ( C)A The traffic intensity must be greater than 1.B The fraction of lost packets increases as the traffic intensity decreases.C If the traffic intensity is close to zero, the average queuing delay will be closeto zero.D If the traffic intensity is close to one, the average queuing delay will be closeto one.1.35 Suppose, a is the average rate at which packets arrive at the queue, R is the transmission rate, and all packets consist of L bits, then the traffic intensity is ( B ),A LR/aB La/RC Ra/LD LR/a1.36 Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending host and the switch and between the switch and the receiving host are R1 and R2, respectively. Assuming that the switch uses store-and-forward packet switching, what is the total end-to-end delay to send a packet of length L? (Ignore queuing delay, propagation delay, and processing delay.) ( A )A L/R1+L/R2B L/R1C L/R2D none of the above1.37 We are sending a 30 Mbit MP3 file from a source host to a destination host. Suppose there is only one link between source and destination and the link has a transmission rate of 10 Mbps. Assume that the propagation speed is 2 * 108 meters/sec, and the distance between source and destination is 10,000 km. Also suppose that message switching is used, with the message consisting of the entire MP3 file. How many bits will the source have transmitted when the first bit arrives at the destination?CA. 1 bitB. 30,000,000 bitsC. 500,000 bitsD. none of the above1.38 In the following entries, which is not a kind of access network?(D )A residential accessB company accessC wireless accessD local access1.39 The following technologies may be used for residential access, exceptDA. HFCB. DSLC. Dial-up modemD. FDDI1.40 Which kind of media is not a guided media? ( D)A twisted-pair copper wireB a coaxial cableC fiber opticsD digital satellite channel。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
L. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, US A Layered Approach towards Domain AuthoringSupportLora Aroyo, Alexandra Cristea Faculty of Mathematics and Computer Science Technische Universiteit EindhovenThe NetherlandsDarina Dicheva Department of Computer Science Winston-Salem State University United States of AmericaThis paper presents an approach to authoring support for Web courseware based on a layeredontological paradigm. The ontology-based layers in the courseware authoring architecture serve as a basis for formal semantics and reasoning support in performing generic authoringtasks. This approach represents an extension of our knowledge classification and indexing mechanism from a previously developed system, AIMS, aimed at supporting students while completing learning tasks in a Web-based learning/training environment. We propose the ad-dition of two vertical layers in the system architecture, Author assisting layer and Operationallayer, with the role of facilitating the creation of the ontological layers (Course ontology andDomain ontology) and of the educational metadata layer. Here we focus on the domain ontol-ogy creation process, together with the support that the additional layers can provide withinthis process. We exemplify our method by presenting a set of generic tasks related to concept-based domain authoring and their ontological support.Keywords: Ontology, Concept Mapping, Web Courseware, Layered Processing1 IntroductionWeb-based education opens many new possibili-ties and is an exciting new field, that allows bringing together ëoldí AI techniques and even older teaching strategies, on a new, clearly not yet fully experimented testing bed, the Web. Although mainly praised for the advantage of bringing information to the disadvantaged users (in terms of time, space, etc.), a great potential of the Web, especially from a course designerís perspective, is the reach, i.e., the multitude of potential users. The latter means, for instance, that such issues as user modeling (which almost reached a research dead end) gain popularity again, because on large population of users the chance of spotting patterns is greater than on stand-alone computers. Moreover, this raises issues of re-usability ñ everything is out there, it is only up to us to get it. Finally, this leads to the question of how to make things more findable. Instead of blaming search engines, the semantic Web research group [4] advocates that the mean-ing and structure (or ontology [11,13]) should provide the necessary information.How does this apply to courseware? This term, initially coined to name computer-supported presentation and instruction individu-alization, traditionally meant frames-based teach-ing material and a courseware delivery engine, with the goal to support authors in creating and linking frames. The term evolved to multimedia courseware [3,9], allowing multi-modality, hy-permedia courseware [5,8], without constraintsL. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, USof predefined paths in the learning material and adaptive educational hypermedia [6,10].Finally, nowadays Web-based courseware is a gateway to a variety of Web educational materi-als on specific topics or with specific educational goals, developed by the course author or repre-sented by Web addresses and descriptions. All these changes obviously affect the courseware authoring process [2,7,16].To address the new challenges we employ a powerful approach for knowledge classification and indexing in on-line learning environments, based on conceptualisation of the course subject domain. An important aspect of the proposed approach is the building of a subject domain ontology [2].In this paper we present our view on ontologi-cal support of Web-based courseware authoring, which is an elaboration of our approach to knowledge classification and indexing, aimed at supporting students during learning tasks in a Web-based learning/training environment.We start by shortly presenting our layered ap-proach to support courseware authoring, espe-cially aimed at ontology creation support. Then, we define a set of generic atomic tasks related to concept-based courseware domain authoring and their possible support, detailing one of these functions as an illustration. Finally, we drawsome conclusions and consider future research perspectives.2 Ontology Authoring SupportIn order to understand the types of authoring support that are possible in such a system as the one we propose, we use the AIMS architecture as the basis on which to built the ontological sup-port functionality. The AIMS authoring environ-ment has three main modules: Domain Editor, Library Editor, and Course Editor [2]. These modules correspond to three horizontal layers in the systemís information layer: library metadata, domain ontology, and course information (Fig. 1).As authoring of such Web courseware spreads in the three dimensions defined by the domain-, course- and library authoring, this process is obviously more complex and labor intensive than the process of linear courseware authoring. Such difficult and time-consuming authoring requires specialized, modern authoring support and re-usage facilitation [1,15].Specifically, such authoring assistance shouldimply:Fig. 1. 2D-layer approach towards courseware authoring supportL. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, US• automatic or semi-automatic performanceof some authoring activities,• intelligent author assistance in the form ofhints, recommendations, etc.,• building and reuse activities support re-garding domain and course ontologies.Our central idea is to use the systemís ontol-ogy, which captures the semantics of the sub-ject domain terminology, to provide enhanced support for authoring concept-based Web courseware. The power of this approach is in the reusability (i.e., cooperation) aspect: the same domain ontology can be used by several different courseware authors to perform searches and moreover, it can be used by the system for (semi-)automatic authoring activi-ties. Therefore, the additional ontology-based layers allow intelligent assistance of course-ware authors.As in our work the ontologies are repre-sented as concept maps (CM) [2,7], authoring involves manipulation of concept maps, i.e., creation and modification of CMs. The pro-posed semantic layers for intelligent authoring assistance include reasoning, consistency check, and introduce additional operations on CMs (such as comparing CMs, mapping and merging CMs, extracting subsets of CM, ana-lyzing CMs).We proposed in previous research [1] two extra vertical layers in a 2D-layer approach (Fig. 1) for concept-based courseware authoring support. This approach allows re-usage, in the sense of authoring cooperation. The Y-axis represented initially the main information ob-jects in the information base of the courseware system (library objects, domains, courses). The X-axis is used to represent the systemís support for the authoring of information objects (GUI, Assisting -, Operation -, Information layer). The Y-axis was generalized to represent a lay-ered architecture that implements also the sys-tem functionality. The GUI layer supports user-system communication. The Information layer contains the actual description and structuring of the information objects in the courseware system (educational metadata, subject domain ontology, course ontology), also organized in (internal) layers. The description of the data sources (which are local or distributed) is stored in the educational metadata layer. The two new layers in the extended architecture are the Assisting and the Operation layer. The Op-eration layer handles the operations related to data in each information layer thus providing means for modeling data into an ontology and creating alternative goal-oriented structures of courses. The Operation layer is also responsible for facilitating information manipulation, con-sistency and co-operation. It consists of three processing engines: (a) course engine, (b) do-main engine and (c) library engine. All of them include two types of support operations: (a) consistency check, and (b) co-operation sup-port. The consistency modules perform their activities over each sub-layer within the infor-mation layer. They provide functions to facili-tate the process of authoring the domain ontol-ogy, course ontology and educational metadata in a semi-automatic way. These modules also guarantee the consistency of the educational sources [15]. They deal with tasks such as: handling notions of semantic equivalence [17] and conflict, conflict resolution rules, equiva-lence comparison rules, enhancing the resulting ontology and defining additional constraints, if necessary.The co-operation support modules offer on one hand a set of operations to check the con-sistency in alternative (or simultaneous) course structure creation by a number of different au-thors. On the other hand, their role is to offer predefined functions (patterns and templates) to facilitate effective reusability of the available course structures built by different authors. With regard to reusability support, we pay special attention to issues associated with the merging of ontologies [14], such as: extracting portions of an ontology to be merged with an-other [17], deciding which frames to extract from the source ontology, identifying semantic overlaps or conflicts between extracted infor-mation and target ontology, assisting in merg-ing ontologies, recording the sources of insertedL. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, USsub-ontologies for later reference and update, selecting patterns and templates in an educa-tional ontology for presenting them as prede-fined objects to other authors.While the Operation layer actually imple-ments the authoring operations, the Assisting layer, which is based on the ontological map-ping of the domain, is responsible for helping the author in the process of courseware author-ing. For example, it gives hints to the author on how to create a course structure, or how to link a document to the ontology, or how to link a course item to the ontology, etc.We will explain in more details the function-ing of the Assisting layer and Operation layer with the help of some example functions for the domain ontology creation support.According to the computational semantics of an ontology, we can integrate and situate our research within the larger research framework presented in [13], by noting that the ontologies we consider here can be situated at level 1 (term collection, as shown previously (Fig. 1,2) and level 3 (executable task ontologies). We still lack the connection given by level 2 (formal definitions, constrains and axioms).As highlighted in Fig. 1, in this paper we fo-cus mainly on the authoring role and activities related to domain authoring. By supporting these activities we aim at increasing the effi-ciency of information reuse and creation of the subject domain ontology.3 Domain Author Task SupportIn this section we focus on authoring tasks sup-ported by the operation sets [13] of the Opera-tion layer and the presentation options provided by the Assisting layer for Domain Authoring.We are defining a complete set of generic authoring tasks at all three information layers (course [1], subject domain and library) that are supported by the course, domain and library engines. For this complete set, we define some atomic operations, used (alone or in combina-tions) at all information layers (see Table 1).In this paper however we present only a sample of the domain engine supported author-ing tasks (see Table 2). In our framework, domain authoring means, as already said, do-main ontology authoring or, actually, domain concept map authoring. The domain ontology creation is vital for the cooperation and col-laboration aspect and, generally speaking, for re-usage.Table 1. Atomic operation definitionsAtomicoperationRange DescriptionëAddí performed over sets of objects {T o, T a, C o, L i, D oc}, where: T o∈ {course topics}, T a∈ {course tasks}, C o∈ {domain con-cepts}, L i∈ {domain links}, D oc∈ {library documents}. adds each object to either course structure, domain ontology or metadata libraryëDelí, as above deletes an object from the corre-sponding structureëEdití as above edits the object settingsëUí set{CM, CS, EML}, where:CM=Concept Map, CS=Course structure, EML=EducationalMetadata Library. ensures current state update of the corresponding information structure of setëLí sets{DirLC, RelC, RelC o, RelT a, RelD oc}, where:DirLC o = Directly linked concepts, RelC = Related courses,RelC o= Related concepts, RelT a= Related tasks, RelD oc=Related documents.lists the objects of the set(s)ëVí set{Graph, Text}, where ëGraphí is a graphical and ëTextígives a textual results view. gives alternative views of the engine results to the authorëChkí set{T a, T o, C o, L i, D oc, RelC o , RelT a , RelD oc , DirLC}checks the existence of objectswithin the set(s)L. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, USThe Operation layer provides the Domain En-gine, and the Assisting layer provides the Do-main Assistant for the Domain Authoring task (see Table 2). We further illustrate the interac-tion between the domain engine and the domain assistant in supporting the author by presentingan activity diagram of the system support for the atomic authoring task ëadd conceptí (Fig. 2: Add (C,CM)). Table 1 above presents the ab-breviations and definitions of atomic operations used throughout this section. In Table 2 we present an excerpt of the domain authoring ontology with a selection of basic atomic tasks and the interaction between the domain engine and assistant.Due to space restrictions we are not present-ing the ontology for the course and educational metadata authoring. The interaction stream between the domain assistant and engine is triggered by common authoring tasks, e.g., ëcre-ate/edit/copy-domainí, ëmerge-domainsí, etc. These tasks involve basic concept-maintenance such as ëadd/delete/edit conceptí, ëcreate/delete/edit link/typeí between concepts.At a higher level, authoring tasks include: ëre-move-all-direct-links-to-conceptí,ëremove-all-segments-of-a-path-between-two-conceptsí,ëedit/create-the-domain-mapí (ontological do-main structure)or ëmake-links-between-domain-structure-and-libraryí. These tasks trig-ger operations performed by the domain engine over the ontological domain structure.The operations ensure data consistency by performing domain specific checks for con-flicts. For instance, when the authoring task Add(C o, CM) is performed by the author (Fig. 2, Table 2, task 1) the domain engine performs Chk(C o, CM, exist), i.e. checks whether the concept Co is already in the map, updates the CM with U(CM, C o), performs Add(C o, weight) and finally provides the results to the domain assistant for analysis and presentation to the author-user. Depending on whether the concept has been found in the CM, the domain engine returns: (a) L(C o, synonyms) (b) L(DirLC o) and (c) notification that the new concept C o has been added to the CM. These results are input to the domain assistant, which is responsible for the customization and presentation in the ap-propriate format to the author so as to support his/her task most efficiently. In this case the domain assistant performs the alternative opera-tions allowing the author to choose from V(Text, DirLC o), V(Graph, DirLC o) and another set of alternative views for the synonyms V(Text, C o, synonyms), V(Graph, C o, syno-nyms). Note that some checks are superfluous due to the architecture implementation, such as no check is necessary to verify if a link to be deleted exists, because a non-existing link can-not be deleted (Del (L, C1, C2, CM) task). There are a number of composite actions such as ëde-lete-all-direct-links-of-a-given- conceptí or ëdelete-all-segments-of- a-path- between- two conceptsí, which can be implemented with a repetitive call to the atomic operation called ëremove-a-link-in-the-CMí.Table 2. Domain authoring tasksTask Domain Assistant Domain Engine ResultAdd (C, CM) suggest options for the author:- add or delete domain engine resultsgive alternative presentation:− V (Text, RelC, Relevance %)− V (Graph, Domain Ontology, Matched concepts) ñëyou are hereínotify other authors of adding C to CM Chk (C, CM, ∃ ) = trueperform keyword search onC within DO (domain on-tology)U (CM, C), notify the otherauthors of adding C to CML (synonyms, C, CM)L (DirRelC, C, CM)L (NonDirLinks, C, CM)Add (L, C1, C2, CM) suggest options for the author:- add or delete domain engine resultsnotify if one of the concepts is missing from the CMnotify if the link exists and offer editing optionnotify about an indirect linking path between the C1and C2 and give altern. Present. of DE results:− V (Text, RelC, Relevance %)− V (Graph, Domain Ontology, Highlighted paths) Chk (C1, CM, ∃) = true,Chk (C2 CM, ∃) = trueChk (L, CM, ∃) = trueChk (C1-x-C2, CM, ∃) =true (indirectly linked withpath ëxí)U (CM, L), notify the otherauthors of adding L to CML (x, C1-C2, CM)L. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, US notify other authors of adding L to CMDel (L, C1, C2, CM) give alternative presentation of all NonDirLinks:− V (Text, L, Relevance %)− V (Graph, Domain Ontology, Highlighted paths)• Give user the option to either graphically or textuallycut all segments or sub-sets of them• Notify other authors of removing L from CM Chk (C1-x-C2, ∃ for L inCM) = trueDel (L) and U (CM)L (x, C1-C2, CM)Del (C, CM) • Notify the author if C has DirLinks• Give alternative views with the option to delete themor cancel the delete action:− V (Text, DirLinks, Relevance %)− V (Graph, Domain Ontology, Highlighted paths)• notify other authors of removing the C from CM Chk (L, ∃ for C in CM) =trueDel (C, CM) and U (CM)L (DirRelC, C, CM)L (DirLinks, C, CM)Fig. 2. UML activity diagram for the atomic domain authoring task ëadd conceptí: Add (C,CM)L. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, US4 ConclusionsIn this paper we have given some insight into our 2D-layer approach to support Web-based courseware authoring, with special focus on the domain authoring support functionality. Our previous experience with AIMS [2] and with systems such as MyET [7] has convinced us that, although ontologies are powerful tools for Web courseware, their authoring process is difficult and needs template - and automatic support. Therefore, we have extended our sup-port system with two additional vertical layers, the author assisting layer and the operational layer (as in Fig. 1), which have the role to sup-port the authoring process for every horizontal layer. We claim that, besides giving a better overview on the different authoring tasks and material organization, such an extension allows intelligent authoring assistance. We are espe-cially interested in the ontological design sup-port, such as needed in the creation of the course ontology and the subject domain ontol-ogy. In this paper we give some explanatory details on some of the domain authoring sup-port functions. Our research borders with an-other important direction, towards merging ontologies. Ontological processing is powerful when comparisons are possible, moreover, when different authors can cooperate within the same environment towards creating various courses by relying on existent courseware or courseware parts. Therefore, we will rely heav-ily on the developments and research in this important field [17].This paper contributes, on one hand, towards collaborative and cooperative courseware au-thoring by both structuring, and adding seman-tics to the courseware subject domain, in par-ticular, and to the Web courseware, in general, in the sense of the standardization efforts of the semantic Web community. This semantics is added with the help of two ontological layers. On the other hand, however, the paper demon-strates with the help of the domain ontology creation functions and possible support func-tions, that concept-based ontologies not only allow semantic labeling of the separate course building blocks, but also provide a structure that can be useful for reasoning and checking mechanisms.References[1] Aroyo L., Dicheva D. & Cristea, A. (2002).Ontological Support for Web Course Au-thoring. ITS 2002.[2] Aroyo L., Dicheva D. (2001). AIMS: Learn-ing and Teaching Support for WWW-basedEducation. International Journal for Con-tinuing Engineering Education and Life-long Learning, 11(1/2), 152-164.[3] Benyon, D., Stone, D., & Woodroffe, M.(1997). Experience with developing multi-media courseware for the World Wide Web: the need for better tools and clearpedagogy, International Journal of H.-C.Studies, 47, 197ñ218.[4] Berners-Lee, T. (1998). Semantic Web roadmap. Internal note, World Wide Web Con-sortium. /DesignIssues/ Semantic.html.[5] Bolter, J.D., Joyce, M., Smith, J.B. (1990)Storyspace: Hypertext Writing Environ-ment for the Macintosh. Computer Soft-ware. Cambridge, MA: Eastgate Systems. [6] Brusilovsky, P. (2001). Adaptive Educa-tional Hypermedia. In: Proceedings of Tenth International PEG conference,Finland, pp. 8-12.[7] Cristea, A. and Okamoto, T., (2001). Ob-ject-oriented Collaborative Course Author-ing Environment supported by Concept Mapping in MyEnglishTeacher, Educa-tional Technology and Society, 4 (2), /periodical/vol_2_2001 /v_2_2001.html[8] De Bra, P. & Calvi, L. (1998). AHA! Anopen Adaptive Hypermedia Architecture, The New Review of Hypermedia and Mul-timedia, 4, 115-139.[9] De Vries, E. (1996). Educational multime-dia for learning and problem solving, Eu-L. Aroyo, A. Cristea & D. Dicheva, A Layered Approach towards Domain Authoring Support, ICAIí02, Las Vegas, US roAIED: European conference on artificialIntelligence in Education, Lisbon, 157-163.[10] Kay, J. & Kummerfeld,B (1994). AdaptiveHypertext for Individualised Instruction,Workshop on Adaptive Hypertext and Hy-permedia, User Modelling '94, Cape Cod.[11] Gruninger, M. & Lee, J. (2002) Ontology:Applications and Design. Communicationsof the ACM, 45(2), 39-41.[12] Lambiotte, J.G., Dansereau, D.F., Cross,D.R. and Reynolds, S.B. (1989). Multirela-tional semantic maps. Educational Psy-chology Review 1(4), 331-367.[13] Mizoguchi, R., Bourdeau, J. (2000). UsingOntological Engineering to OvercomeCommon AI-ED Problems, Int. Journal ofAI in Education, 11 (2), 107-121.[14] McGuinness, D.L. et al. (2000). An Envi-ronment for Merging and Testing LargeOntologies, KR00, Breckenridge, Colorado.15] Murray, T. (1999). Authoring IntelligentTutoring Systems: An analysis of the stateof the art. International Journal of AI inEducation, 10, 98-129.[16] Murray, T., Shen, T., Piemonte, J., Condit,C., Thibedeau, J. (2000). Adaptivity in theMetaLinks Hyper-Book Authoring Frame-work, Workshop Proceedings of Adaptiveand Intelligent Web-Based Education Sys-tems workshop at ITS 2000, Montreal.[17] Sowa, J. F. (2001). Building, Sharing, andMerging Ontologies. http://www.jfsowa.com/ ontology/ontoshar.htm.。
