A Dual-Processor Solution for the MAC Layer of a Software Defined Radio Terminal ABSTRACT
MACDISMCUHALOFS
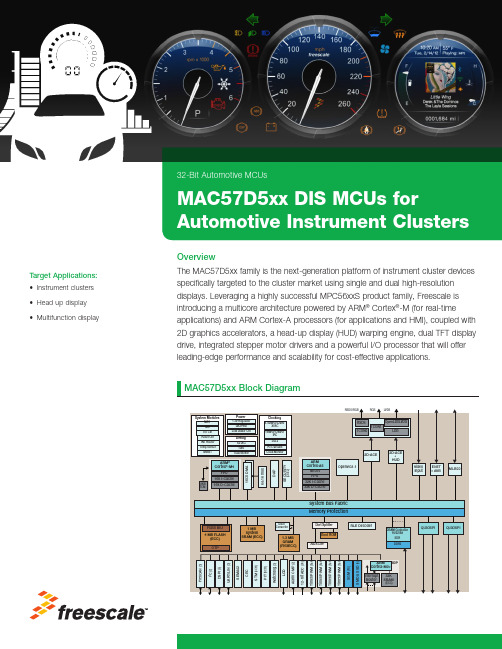
32-Bit Automotive MCUsMAC57D5xx DIS MCUs forOverviewThe MAC57D5xx family is the next-generation platform of instrument cluster devices specifically targeted to the cluster market using single and dual high-resolution displays. Leveraging a highly successful MPC56xxS product family, Freescale is introducing a multicore architecture powered by ARM ® Cortex ®-M (for real-timeapplications) and ARM Cortex-A processors (for applications and HMI), coupled with 2D graphics accelerators, a head-up display (HUD) warping engine, dual TFT display drive, integrated stepper motor drivers and a powerful I/O processor that will offer leading-edge performance and scalability for cost-effective applications.Target Applications:• Instrument clusters • Head up display • Multifunction displayFor current information about MAC57D5xx family of DIS MCUsproducts and documentation, please visit /MAC57D5xxFreescale and the Freescale logo are trademarks of Freescale Semiconductor, Inc., Reg. U.S. Pat. & Tm. Off. All other product or service names are the property of their respective owners. ARM and Cortex are registered trademarks of ARM Limited (or its subsidiaries) in the EU and/or elsewhere. All rights reserved. ©2014 Freescale Semiconductor, Inc.Document Number: MACDISMCUHALOFS REV 0This family supports up to two WVGA resolution displays, including one with in-line HUD hardware warping. Graphics content is generated using a powerful Vivante 2D graphics processing unit (GPU) supporting OpenVG1.1, and the 2D animation and composition engine (2D-ACE), which significantly reduces memory footprint for content creation. Embedded memories include up to 4 MB flash, 1 MB SRAM with ECC and up to 1.3 MB of graphics SRAM without ECC. Memory expansion is available through DDR2 and SDR DRAM interfaces while two flexible QuadSPI modules provide SDR and DDR serial flash expansion. In response to the growing desire for security and functional safety, the MAC57D5xx family integrates Freescale’s latest SHE-compliant Cryptographic Services Engine (CSE2) engine and delivers support for ISO26262 ASIL-B functional safety compliance.FeaturesCortex-A5, 32-bit CPU (Application processor)• FPU supporting double-precision floating-point operations • NEON Media Processing Engine • Memory management unit • Up to 320 MHzCortex-M4, 32-bit CPU (Vehicle processor)• 64 KB tightly-coupled memory (TCM)• Single precision FPU • Up to 160 MHzCortex-M0+, 32-bit CPU (I/O processor)• Intelligent stepper motor drive• Low-power mode peripheral managementMemory sub-system• System memory protection unit• 4 MB on-chip flash including small sectors for EEPROM emulation• 1 MB on-chip SRAM with ECC • 1.3 MB on-chip graphics SRAM with FlexECCExpandable Memory Interfaces• 2 x Dual QuadSPI serial flash controllers (including HyperFlash ™ support)• Supports SDR and DDR serial flash • DRAM controller supporting SDR and DDR2Graphics Features• Vivante GC355 GPU supporting OpenVG ™ 1.1• 2 x 2D-ACE display controllers supporting up to 2 x WVGA displays• In-line hardware HUD warping engine • Digital RGB, TCON0 (RSDS), TCON1 and OpenLDI/LVDS output options • Digital video input (VIU)• RLE decoder for memory-memory decompressionSafety and Security• Latest CSE2 security—Secure Boot, Secure Mileage & Component Protection • ISO 26262 ASIL-B Compliant MCUPeripherals:• 6 Stepper Motor Drivers with Freescale patented Stall Detection technology • Sound Generator Module (SGM) with PWM and I 2S outputs• Autonomous RTC (self calibrating)• Rich set of communication peripherals, including Ethernet-AVB, MLB50, CAN-FD, LIN, SPI, I 2C• Up to 32 Timer/PWM channels • 12-bit ADC and Analogue ComparatorsKey Electrical Characteristics• –40 °C to +105 °C (ambient)Package options• 516 MAPBGA, 208 LQFP , 176 LQFPEnablement• Software Support: AutoSAR, 2D-ACE, OpenVG, TinyUI, IOP/Stepper Motor, SGM, EthernetTools• Debugger: Green Hills, Lauterbach, IAR • Multicore compiler: ARM, Green Hills**Not all feature differences shown in table above, refer to Datasheet for specific feature details。
半导体传感器AD7324BRUZ中文规格书

The following is the list of Analog Devices, Inc. processors supported by the IAR Embedded WorkBench®develop-ment tools. For information about the IAR Embedded WorkBench product and software download, The ADSP-CM40x processors are based on the ARM Cortex®-M4 core and are designed for motor controland industrial applications.The ADSP-CM41x processors are based on the ARM Cortex-M4 and ARM Cortex-M0 cores and are de-signed for motor control and industrial applications.Product InformationProduct information can be obtained from the Analog Devices Web site and CrossCore Embedded Studio online Help system.Analog Devices Web SiteThe Analog Devices Web site, provides information about a broad range of products—ana-log integrated circuits, amplifiers, converters, and digital signal processors.To access a complete technical library for each processor family, go to:The manuals selection opens a list of current manuals related to the product as well as a link to the previ-ous revisions of the manuals. When locating your manual title, note a possible errata check mark next to the title that leads to the current correction report against the manual.Also note, is a free feature of the Analog Devices Web site that allows customization of a Web page to display only the latest information about products you are interested in. You can choose to receive weekly e-mail notifications containing updates to the Web pages that meet your interests, including documentation errata against all manuals. provides access to books, application notes, data sheets, code examples, and more. Visit to sign up. If you are a registered user, just log on. Your user name is your e-mail address. EngineerZoneEngineerZone is a technical support forum from Analog Devices. It allows you direct access to ADI technical sup-port engineers. You can search FAQs and technical information to get quick answers to your embedded processing and DSP design questions.Use EngineerZone to connect with other DSP developers who face similar design challenges. You can also use this open forum to share knowledge and collaborate with the ADI support team and your peers. Visit http:// to sign up.ADSP-BF7xx Blackfin+ Processor xxxNotation ConventionsText conventions used in this manual are identified and described as follows. Additional conventions, which apply only to specific chapters, may appear throughout this document.Example DescriptionFile > Close Titles in reference sections indicate the location of an item within the CrossCoreEmbedded Studio IDE's menu system (for example, the Close command appearson the File menu).{this | that}Alternative required items in syntax descriptions appear within curly brackets andseparated by vertical bars; read the example as this or that. One or the other isrequired.[this | that]Optional items in syntax descriptions appear within brackets and separated byvertical bars; read the example as an optional this or that.[this, …]Optional item lists in syntax descriptions appear within brackets delimited bycommas and terminated with an ellipse; read the example as an optional comma-separated list of this..SECTION Commands, directives, keywords, and feature names are in text with LetterGothic font.filename Non-keyword placeholders appear in text with italic style format.NOTE:NOTE: For correct operation, ...A note provides supplementary information on a related topic. In the online ver-sion of this book, the word NOTE: appears instead of this symbol. CAUTION:CAUTION: Incorrect device operation may result if ...CAUTION: Device damage may result if ...A caution identifies conditions or inappropriate usage of the product that couldlead to undesirable results or product damage. In the online version of this book,the word CAUTION: appears instead of this symbol.ATTENTION:ATTENTION: Injury to device users may result if ...A warning identifies conditions or inappropriate usage of the product that couldlead to conditions that are potentially hazardous for devices users. In the onlineversion of this book, the word ATTENTION: appears instead of this symbol. Register Documentation ConventionsRegister diagrams use the following conventions:•The descriptive name of the register appears at the top with the short form of the name.•If a bit has a short name, the short name appears first in the bit description, followed by the long name.•The reset value appears in binary in the individual bits and in hexadecimal to the left of the register.•Bits marked X have an unknown reset value. Consequently, the reset value of registers that contain such bits is undefined or dependent on pin values at reset.ADSP-BF7xx Blackfin+ Processor xxxiIntroduction 1 IntroductionThis Blackfin+ Processor Programming Reference provides details on the assembly language instructions used by Black-fin+ processors. The Blackfin+ architecture extends the Micro Signal Architecture (MSA) core developed jointly by Analog Devices, Inc. and Intel Corporation. This manual applies to all ADSP-BF7xx processor derivatives. All devi-ces provide an identical core architecture and instruction set. Additional architectural features are only supported by some devices and are identified in the manual as being optional features. A read-only memory-mapped register, FEATURE0, enables run-time software to query the optional features implemented in a particular derivative. Some details of the implementation may vary between derivatives. This is generally not visible to software, but system and test code may depend on very specific aspects of the memory microarchitecture. Differences and commonalities at a global level are discussed in the Memory chapter. For a full description of the system architecture beyond the Black-fin+ core, refer to the specific hardware reference manual for your derivative. This section points out some of the conventions used in this document.The Blackfin+ processor combines a dual-MAC signal processing engine, an orthogonal RISC-like microprocessor instruction set, flexible Single Instruction, Multiple Data (SIMD) capabilities, and multimedia features into a single instruction set architecture.Core ArchitectureThe Blackfin+ processor core contains two 16-bit multipliers (MACs), one 32-bit MAC, two 40-bit accumulators, one 72-bit accumulator, two 40-bit Arithmetic Logic Units (ALUs), four 8-bit video ALUs, and a 40-bit shifter, shown in the Processor Core Architecture figure. The Blackfin+ processors work on 8-, 16-, or 32-bit data from the register file.ADSP-BF7xx Blackfin+ Processor1–1。
IK Multimedia Installation and Authorization Manua

IK MultimediaInstallation and AuthorizationManualInstallation and Authorization ManualChapter 1 System RequirementsThe following are the system requirements for using your IKMultimedia product.Macintosh®- Power PC based MacintoshMinimum: 866 MHz G4 processor, 512 MB of RAM, Mac OS X 10.4or later.Suggested: dual 1.25 GHz G4 or G5 processor, 1 GB of RAM, Mac OSX 10.4 or later.- Intel based MacintoshMinimum: 1.5 GHz Intel Core Solo processor, 512 MB of RAM, MacOS X 10.4.4 or later.Suggested: 1.66 GHz Intel Core Duo processor, 1 GB of RAM, MacOS X 10.4.4 or later.Windows®Minimum: Pentium 1 GHz / Athlon XP 1.33 GHz, 512 MB of RAM,Windows XP/Vista.Suggested: Pentium 2.4 GHz / Athlon XP 1.33 GHz, 1 GB of RAM,Windows XP/Vista.2Installation and Authorization ManualChapter 2 InstallationMacintosh®NOTE: in order to be able to install and uninstall IK Multimediaproducts in your Macintosh computer (Power PC or Intel based) youmust be a user with Administrator rights.Double-click on the ‘Install’ icon and follow the onscreen instructions.The Standalone version is installed in your “Applications” folder.Documentation is placed in:Library / Documentation / IK Multimedia /UninstallDouble-click on the ‘Uninstall’ icon and follow the onscreen instruc-tions.Windows®NOTE: in order to be able to install and uninstall IK Multimediaproducts in a computer equipped with Windows Vista, you must bea user with Administrator rights.Double-click on the ‘Install’ icon and follow the onscreen instructions.The installer asks you to confirm the destination folder. In the desti-nation folder you will also find the documentation.To launch the Standalone version go to:Start menu, All ProgramsThe default destination folder is:Program Files \ IK Multimedia \UninstallIn the ‘Start’ menu, select ‘Control Panel’.Double-click ‘Add or Remove Programs’. A list of the softwareinstalled in your system is displayed.Select the IK Multimedia product you want to uninstall and click the‘Remove’ button. All the components will be removed from your sys-tem. If you added or changed files after the installation, it may bethat some files and folders are not removed. Delete them manually,from the destination folder you selected during installation.3Installation and Authorization ManualChapter 3 How the Authorization System worksYour IK Multimedia product must be authorized to work with unre-stricted functionality. It will run with full features for 10 days (graceperiod) which will start when launched for the first time, and revertto demo mode after. You will need to authorize the product withinthis time frame to enable permanent unrestricted functionality.To authorize your IK Multimedia product you’ll need three numbers:- Serial Number: this is written on the Registration Card(included with your IK boxed product, inside the license enve-lope) or the one that has been delivered to you (e.g. Onlinepurchase, such as a Digital Delivery, or update).- Digital ID: this will be shown during the authorization pro-cess and linked to the hardware where you are running thesoftware.- Authorization Code: this will be generated online by regis-tering and inserting the Serial Number and Digital ID. If youare a registered IK Multimedia user, having your User Nameand Password on hand, will help speed up the authorizationprocess.45Installation and Authorization ManualChapter 4 AuthorizationA built in software Wizard helps you in the authorization of your IK software. The first time the software is launched the Wizard is displayed (Step 1. Wizard Introduction). Click Cancel to return to the software and use the software within the 10 days grace period. Click Next to go to the Wizard’s next Step and authorize the software.The next Step (Step 2. Enter Serial Number) is for inserting the Serial Number. The Serial Number is written on the Registration Card (included with your IK boxed product, inside the license envelope) or the one that has been delivered to you (e.g. Online purchase, such as a Digital Delivery, or update). Type the Serial Number in the fields (using the TAB key to move from one field to the other). Once the Serial Number has beenStep 1. Wizard introductionStep 2. Enter Serial Number6Installation and Authorization Manualproperly inserted a green icon will display, showing that the number has been entered correctly. If a red icon is displayed the Serial Number inserted is not correct and you will be asked to re-type it in the fields. Once the Serial Number has been typed correctly, the Next button will enable you to move to the next Step of the Wizard.Now the Wizard will ask you if you are requesting an Authorization Code for the first time, or if you intend on reauthorizing your software with an Authorization Code previously received (Step 3. Authorization / Reauthorization). For a new authorization click the first option. If you choose the second option because you need to RE-AUTHORIZE your product, you’ll proceed directly to Step 7. In order to obtain the Authorization Code you’ll need to go online using an internet connection. In this window, (Step 4. Connect to Internet)Step 4. Connect to the InternetStep 3. Authorization/Reauthorization7Installation and Authorization Manual you are asked if you will connect to the internet using your current computer or a separate one. Make your choice and click on the Next button (if you connect to the internet using a different computer you’ll proceed directly to Step 6).In this page of the Wizard (Step 5. User Name and Password) you should type your IK Multimedia User Name and Password. If you have already registered any other IK Multimedia product you should use the same User Name and Password that you used previously to access the IK Multimedia User Area (where you can download updates and upgrades, requests new authorizations, manage your registration data, etc...). If you have never registered any other IK Multimedia product or if you can’t remember your previous registration informa-tion click on the second option. Once you are done click Next.Step 6a. Online registration on the same computerStep 5. User Name and Password8Installation and Authorization ManualAt this point the Wizard presents you with a window where you can find your Serial Number and the Digital ID required to register online (Step 6a. Online registration on the same computer). By clicking Register On Line, your default browser will be opened and directed to the IK Multimedia Registration Page (if the machine that you are installing on has an internet connection). Now simply fill out the mandatory fields of the Registration Page with your data. Your Serial Number and Digital ID should have been pre filled-in (otherwise COPY and PASTE them from your Wizard window to the Registration Page fields). If you would have inserted your User Name and Password, as a previously registered IK Multimedia user, the Registration Page will be pre-filled with your personal data making the authorization process faster.If you are authorizing your software from a separate computer, the Wizard will display a page (Step 6b. Online Registration on a separate computer) where you are asked to access the IK Multimedia Registration Page, online here:/IKReg.htmland register your software to obtain the Authorization Code. In this case, please carefully type your Serial Number and Digital ID in the corresponding field of the Registration Page. Be sure to fill out all the mandatory fields as well. Once your registration process has been completed, an Authorization Code will be displayed in the check out page of your IK Multimedia online registration (as well as sent to you by email). Copy the Authorization Code and click Next on the Wizard.You will now be prompted to paste the Authorization Code in the new Wizard window (Step7. Paste Authorization Code). Point the cursorStep 6b. Online Registrationon a separate computer9Installation and Authorization Manualin the first field of the Authorization Code in the Wizard and click on the Paste button. All the separated fields will be filled and a green icon will display, showing the Authorization Code has been entered correctly. If a red icon is displayed, the Serial Number inserted is not correct and you will be asked to re-type it in the fields (if you typed it manually).Once the green icon is displayed, click Next and the last page of the Wizard will appear (Step 8. Authorization Completed) listing your Serial Number, Digital ID and Authorization Code as a reference. Click Finish to start using your IK Multimedia product with unrestricted functionality.Step 7. Paste Authorization CodeStep 8. Authorization CompletedInstallation and Authorization ManualIf you have no access to the Internet, in the software CD you’ll find aPDF file called Authorization Request Form.Europe, Africa, Asia and Australia:Open the file (with Acrobat Reader), print the form, fill the requiredfields and fax everything to +39-059-2861671 to receive yourAuthorization Code within 24 hours of your fax (standard Europeanbusiness hours). Please write clearly: if we can’t decipher the codes, wewon’t be able to generate a working Authorization Code. If you don’thave access to a fax machine fill the aforementioned AuthorizationCode Request Form and mail it to the following address:IK Multimedia Production srlVia Dell’Industria 4641100 ModenaItalyNorth and South America:Open the file (with Acrobat Reader), print the form, fill therequired fields and fax everything to 954-846-9077 to receive yourAuthorization Code within 24 hours of your fax (10am-6pm EST).Please write clearly: if we can’t decipher the codes, we won’t be ableto generate a working Authorization Code. If you don’t have accessto a fax machine fill the aforementioned Authorization Code RequestForm and mail it to the following address:IK Multimedia US LLC1153 Sawgrass Corporate ParkwaySunrise, FL 33323USAYou’ll be given your Authorization Code by return mail within 15working days.For any question you may have, please refer to the FAQ at:/FAQ.phpwhere you’ll find answers to the most common questions.To submit a Technical Support Form, go to:/Support.phpTo contact US Tech Support Service by phone, please call at:(954) 846-9866For other requests such as Product, Sales, Web info or LicenseTransfer, please go to:/ContactIKForm.php1011Installation and Authorization ManualChapter 5 TroubleshootingWhere can I find my IK product Serial Number?The Serial Number is written in the Registration Card (included with your IK product, inside the license envelope). In the snap-shot, please check its exact location.For a clear characters identification, please analyze the leg-end. IMPORTANT: the number zero can easily be identified in your Serial Number because it is crossed by a line.Why is the Wizard rejecting my Serial Number?Probably because it found a typo, so please analyze the common errors:* Typing a 0 (“zero” number) instead of an O (“o” letter)* Typing 1 (“one” number) instead of an I (“i” letter)* Typing 2 (“two” number) instead of an Z (“z” letter)* Typing 5 (“five” number) instead of an S (“s” letter)* Typing 8 (“eight” number) instead of an B (“b” letter)* Typing a “.” (point) instead of a “-” (minus)1) Here you can find your SERIAL NUMBER2) At the bottom of the registration card a legend helps you identify the characters in your SERIAL NUMBER12Installation and Authorization Manual Suggestions:- When is possible, please copy and paste the information.- Cut off all the leading and trailing spaces. - Please type all codes UPPERCASE during the installation and registration process. - Check that the Serial number that you are entering is in correlation with the product installed.During the Product Registration process I received this message: The Serial Number is already registered...Remember that you are able to register your product only once. So, if you are trying to get a new Authorization Code, please read the related FAQ.Where can I find my Digital ID?The Digital ID is displayed in the Authorization window of your IK product. Why is my Digital ID being rejected during the Online Registration process?There probably is a typo on it. Remember that the Digital ID has NO letter “I” and “O”, only the numbers “1” (one) and “0” (zero). In order to prevent any further mistakes, please Copy the Digital ID from the Authorization Form to the RegistrationForm.Installation and Authorization ManualWhere can I find my Serial Number, Digital ID and the Authorization Code of a registered IK Product?In your IK product interface, locate the Authorization button and click on it. If your product version has no Authorization but-ton, you can also log in into the User Area and click on Requesta new Authorization Code. You will be able to check all the maininformation about your registered products.How can I get a new Authorization Code?Please log in into the User Area athttps:///Login/IKLogin.cgiThen, click on Request a new Authorization Code.I’ve already registered my product online, but I didn’t get an Authorization Code.Usually, this happens because the Digital ID was not submit-ted during the registration process. In order to get a new Authorization Code, please read the How can I get a new Authorization Code? FAQ.I need to log in into the User Area but I forgot my User Name and Password. What should I do?Please go to the User Area and enter your registered email address (in the proper empty box). You will receive an email with the necessary information to Log in.I have already installed, registered and authorized my IK product in my main computer. What do I have to do to use my IK product in other computers?You need to install the program and get a new Authorization Code. To learn how to get a new Authorization Code, please refer to “How can I get a new Authorization Code” paragraph in this chapter.I just bought an IK software. What should I do to register and authorize my new product?In the Support area of our website click on the Product Registration link, or click on the Tech Support Page link and click on option 1 (Register your product).13Installation and Authorization ManualIn the Serial Number field of the Product Registration Form,please insert the Serial Number written on the RegistrationCard (included with your IK boxed product, inside the licenseenvelope) or the one that has been delivered to you (e.g. Onlinepurchase, such as a Digital Delivery, or update).Complete the Registration Form and click Submit.Regarding the Authorization process, if you already typed yourDigital ID while filling the Product Registration Form, you willreceive an email from us with your Authorization Code. If not,after you launch the program the Product Authorization Wizardwill appear. Please read and follow the instructions provided ineach of the wizard’s windows and get an Authorization Code.14Installation and Authorization ManualIK Multimedia Production, Via dell’Industria 46, 41100, Modena, Italy.Phone: +39-059-285496 - Fax: +39-059-2861671IK Multimedia US LLC, 1153 Sawgrass Corporate Pkwy. Sunrise, FL 33323Phone: (954) 846-9101 - Fax: (954) 846-9077All specifications are subject to change without further notice.© 2007 IK Multimedia Production srl.Mac and the Mac logo are trademarks of Apple Computer, Inc.,registered in the U.S. and other countries.Windows Vista and the Windows logo are trademarks or registered trademarksof Microsoft Corporation in the United States and/or other countries.15P N : M N I -I K -0002。
Marketing in Practice 3

Marketing in Practice ProjectAbout apple1. Wants are the form human needs takes as they are shaped by culture and individual personality.Human needs are states of felt deprivation. They include basic physical needs for food, clothing, warmth, and safety; social needs for belonging and affection;and individual needs for knowledge and safe-expression.So ipad as a product in order to fulfill the customers’ wants, having a lot of functions:IPad 2 mobility.Apple has been very focused on iPad 2 mobility. iPad2 are thinner than the old version is about 33%, but also much lighter than the old version of the iPad, although these differences is not obvious, but enough to help Apple sell more of these products. Tablet PC with the mobility, is able to carry the equipment around lightly, more lightly if the device smaller, of course, the better, Apple seems to understand this and respect the iPad 2 under the foot work, as all this functions show ipad2 features.The entertainment factorAt today's event, Apple spent a long time to introduce iPad 2 focus on entertainment features included. One major feature is that today's iPad 2 Tablet PC to support HDMI (high-definition output line) output function, which can output the user some video content to other devices on a higher resolution, such as TV sets. In addition, iPad 2 of the new operating system also has the AirPlay iOS 4.3 feature that allows users to enter the built-in slide show function. In addition, iPad 2 will also have iMovie and Garage Band functions, which they can help users edit video and audio content, so we will easily see, iPad 2 is already higher than the old version has been greatly improved.The battery lifeIf the Tablet PC's battery life will soon be consumed dry, then this is certainly not a good thing. The longer battery life, the Tablet PC will more attractive. Apple's well known that, according to Apple's side said the new iPad 2 tablet computer battery can achieve 10 hours duration, while the standby time to about a month or even longer. All in all, iPad 2 will be an effective platform, consumers will be happy to hear this news.Built-in 3G capabilities can be connected to the network AT & T and VerizonIPad first one of the main problem is that it only allows users to connect AT & T's wireless network, if users want to connect to Verizon's network, it may still need to install additional products, such as MiFi 2200 Hotspot and so on. But the good news is that the new iPad 2 has been able to allow users to connect this product to AT & T's 3G network or Verizon's 3G networks is not need to install other add-on products, which may also be a lot of consumers’ wants iPad 2.2. Describe the segment of market for iPad in China.Through market segmentation, companies divide large, heterogeneous markets into smaller segments that can be reached more efficiently and effectively with products and services that match their unique needs. So the segments of ipad in china are as follows:● Segmenting consumer markets in china● Segmenting business markets in chinaBusiness markets also use some additional variables, such as customer characteristics purchasing approaches, situational factors, and personal characteristics. And ipads’ business markets are as follows:a) Corporations,For large corporate customers, the company offers a lot services, which including travel management services, and so on.b) Small business customers Income(amonth)RMBPsychographics User rates Students’ iPad Under$2000 Fashion seek for myselfLighter userBusiness’ iPad$2000~$4000 ambition Medium user Loyal’ iPad $4000 and over authoritarian Heavy userFor small business customers, the company offers many services, which including special usage rewards, and so on3. Marketing intermediaries help the company to promote, sell, and distributeits products to final buyers; they include resellers, physical distribution firms, marketing services agencies, and financial intermediaries.●Resellers are distribution firms help the company to stock and move goodsfrom their points of origin to their destinations.●Physical distribution firms help the company to stock and move goods fromtheir points of origins to their destinations.●Marketing services agencies are the marketing research firms, advertisingagencies, media firms, and marketing consulting firms that help the company target and promote its products to the right markets.●Financial intermediaries include banks, credits companies, insurancecompanies, and other businesses that help finance transactions or insure against the risks associated with the buying and selling of goods.(b) A product’s position is the way the product is defined by consumers onimportant attributes-the place the product occupies in consumers’minds relatives to competing products.The low price strategy of IPad1400UnitPrice 1000(Dollars)600200PerformanceOrientationImac ipod touch ipod classic iphoneiPad4. Demographic is the study of human population in terms of size, density,location, age, gender, race, occupation, and other statistics. TheDemographic environment is of major interest to marketers because itinvolves people, and people make up markets.Population environment,which including population growth, population age structure, ethnic composition, educational level, family structure anddemographic migration. The case from iPad can be seen that the greatest impact on ipad’s marketing is the age composition of the population and the education level of population.●From the population age structure, Apple is taking the product innovationand its products to high performance, elegant design of the main. This is the object of many young people to follow, young people like innovation, like the good-looking designs. Ipad’s product innova tion, fashionmarketing strategy precisely fit the shape of a young consumerpsychology. The elderly are less demanding for the appearance andperformance requirements for the computer is not high. Therefore, ipad marketing in China mainly targeted at young people.●Also from the level of education, the major consumer groups of ipad arethe above white-collar workers or college students. Especially the senior staffs of the computer’s requirements are relatively high. They not only require a computer's performance, but also for the appearance ofcomputers and match their status with the company. Ipad marketingstrategy is that high-end line. While Apple's market share of Chinesestudents is not high, but most students are quite popular on the ipad. This part of the college students are ipad potential consumers, so this part of the market is needed for ipad.5. The technological environment is perhaps the most dramatic force nowshaping our destiny. Technology has released such wonders asantibiotics, robotic surgery, miniaturized electronics, laptop computer,and the internet. So the there are some technological environmentfactors that affect the Product development of iPad as follows:●The Mac OS systems are proprietary systems, under normalcircumstances can not be installed on a normal PC operating system.Apple MAC not only produced most of the hardware, even the MACoperating systems are used in the development of its own. Mac'soperating system is Mac OS X, the UNIX-based core system enhances the system stability, performance and responsiveness. It through the full symmetric multi-processing advantages of a dual-processor, providing unparalleled 2D, 3D and multimedia graphics performance and a wide range of font support and integration of PDA (personal digital processing) functions.●This technology is now Apple has a strong advantage. The current use ofordinary PC, mostly developed by Microsoft WINDOWS or LINUXoperating system, WINDOWS has a strong compatibility, LINUX humane of the graphical interface, and Mac OS operating system, both theadvantages of both, such as compatibility with standard and aesthetic user interface, which makes Apple's Mac OS systems in the currenttechnological environment is unique, has a strong competitive edge.●Apple computer technology the higher gold content, and rapidtechnological innovation. However, the technology surroundingenvironment is constantly changing, these changes include accelerating changes in technology, opportunities for technological change, increased investment in research and development of regulations and technicalinnovations continue to increase. For example, the April 19, LenovoGroup announced yesterday that its business area from a traditional PC to the mobile Internet development. This is the largest in recent years, Lenovo Group, a business transformation, founder of Lenovo, Lenovo chairman Liu at an unprecedented high-profile propaganda, said,"Lenovo will be desperate to put to stop the mobile Internet market,"Financial News for NetEase The title of the "determination and Lenovo Mobile Internet transition, Apple Last Stand", it is clear competitionLenovo and Apple market share, while Lenovo's mobile Internet strategy is still faced with many challenges, but Apple will undoubtedly adversely affect the market.●Because economic development is bound to promote technologicalprogress, technology innovation, made computer technology ininnovation, as the domestic computer products and technology, Apple Computer technology in China will gradually lose the advantage, ofcourse, it takes a long period of time, but in the long run, the domestic computer products, technical progress is an inevitable trend, which will certainly have future sales of Apple computers in China have animportant impact.6. (a) Using an Undifferentiated Marketing strategy, a firm might decide to ignore market segment differences and target the whole market with one offer. The Undifferentiated Marketing strategy focuses on what is in common in the needs of consumers rather than on what is different. The company designs a product and a marketing program that will appeal to the largest number of buyers. And the advantages and disadvantages of ipad use an Undifferentiated Marketing strategy.Ipad use an Undifferentiated Marketing strategy.●Undifferentiated Marketing strategy advantages is its low cost. Ipad’sSingle product line can produce the relative scale efficiency, storage and transport are also relatively convenient, advertising, logistics and other resources are concentrated in a product, it will help strengthen brand image.●Also, Undifferentiated Marketing strategy has its own shortcomings anddeficiencies, it can not meet the diverse needs of consumers, there aredifferences in some areas, no difference in the implementation of marketing, but companies ignore the objective is the existence of such differences can easily cause competitors find a breakthrough point, lose some customers. Therefore, an enterprise through a brand of a product to meet the diverse needs of consumers, it is almost impossible. Therefore, the enterprise was no difference in the choice of development strategy as the time to study its adaptability. In general, steel, cement and other businesses are more suited to this strategy.(b) Using a differentiated Marketing strategy, a firm might decide to targetseveral market segment and designs separate offers for each. and theadvantages and disadvantages of ipad use an differentiated Marketing strategy.●When ipad use an differentiated Marketing strategy, the advantages areas follows:Customers can better meet different needs, but also so that eachsub-markets to maximize the sales potential of the excavation, which will help to expand their market share. But also greatly reduce the operational risks; the failure of a sub-market will not cause trouble throughout the enterprise. Differentiated marketing strategy has greatly enhanced the competitiveness of enterprises, ipad set up several brands, companies can greatly increase consumer trust in products and purchase rates. A variety of advertising and multi-channel distribution, a variety of market research costs, management fees, are limited barriers to entry of small businesses, so, for the strong financial resources, robust technology, with high-quality products business, the difference of marketing is a good choice.●When ipad use an differentiated Marketing strategy,the disadvantagesare as follows:Meanwhile, there are differences of their own limitations, the biggest drawback is the high cost of marketing, and production is generally small quantities, so that the relative increase in the cost per unit of product, non-economic. In addition, market research, sales analysis, marketing plans, channel establishment, advertising, and many other aspects of logistics and distribution costs will no doubt increase substantially. This is why many companies do marketing differentiation, market share expansion, and sales increased, profits decreased the reason.(c)Concentrated MarketingUsing a concentrated Marketing strategy, instead of going after a small share of a large market, the firm goes after a large share of one or a few smaller segments or niches.●The advantages of ipad use a concentrated Marketing strategy. first theipad can achieves a strong market position because of its greaterknowledge of consumers needs in the niches it serves and the special reputation it requires. Second it can market more effectively byfine-tuning its products, prices, and program to the needs of carefullydefined segments. Third it can also market more efficiently, targeting its products or services, channels, and communication programs towardonly consumers that it can serve best and most profitably.●The disadvantages of iPad use a concentrated Marketing strategy. firstowing to the segments are fairly large and normally attract severalcompetitors, niches are smaller and may attract only or a fewcompetitors. Many companies start as nicher that may be unimportant to or overlooked by larger competitors. So iPad will have a lot of potential competitors.7. Describe some of the actions taken by Apple to build a brand for the Company’s product in the following areas:(a) Brand positioningMarketers need to position their brands clearly in target cu stomers’ minds. They can position brands at any of three levels. At the lowest level, they can position the brand on products’ attributes. And a brand can be better Positioned by associating its name with a desirable benefit. And the strongest brands go beyond attribute or benefit positioning; they are positioned on strong beliefs and values.、个性、与众不同、创新电脑产品有很多,它们是同质化的商品,但苹果不是,它的个性风格太强烈了,一眼就能识别,品牌忠诚度很高。
科技英语 主编 田文杰 课文翻译

Unit 1Artificial intelligence is the science and engineering of making intelligent machines,especially intelligent computer programs.人工智能是制造智能机器的科学与工程,特别是智能化的计算机程序。
It is related to the similar task of using computers to understand human intelligence,but AI does not have to confine itself to methods that are biologically observable.这与使用计算机来理解人类智能的类似任务有关,但是人工智能不需要把它局限在生物可观察的方法上。
In this unit,the two passages present a general picture of AI research .在这个单元,两个章节提出了人工智能研究的概况。
Text A briefly introduces the definition of AI,some kinds of architectures of AI system,essential capabilities to AI programs and so on.文章A简要介绍了人工智能的定义,人工智能的系统的几种体系结构、基本功能以及程序等等。
Text B explains a particular area of AI research--natural language processing including its definition and a legendary Turing’s Test.文章A解释特定地区研究人工智能的自然语言处理包括定义和传说中的图灵测试。
MIC5332中文资料
MIC5332
Micro-Power High Performance Dual 300mA ULDO™
General Description
The MIC5332 is a tiny dual low quiescent current LDO ideal for applications that are power sensitive. The MIC5332 integrates two high performance 300mA LDOs, and a POR generator into a 2mm x 2mm Thin MLF® package. This solution occupies the same PC board area of a single SOT-23 package.
Micrel Inc. • 2180 Fortune Drive • San Jose, CA 95131 • USA • tel +1 (408) 944-0800 • fax + 1 (408) 474-1000 •
January 2007
M9999-011608-A
Pin Configuration
VIN 1 GND 2 POR2 3 EN2 4
8 VOUT1 7 VOUT2 6 CSET2 5 EN1
8-Pin 2mm x 2mm Thin MLF® (MT) (Top View)
Pin Description
Pin Number 1 2 3
4
5
6
7 8
Pin Name VIN GND
Regulator Output – LDO2.
Regulator Output – LDO1.
DS-A82系列混合SAN产品介绍说明书

FeaturesReliable System●Modular and no-cable design.●Dual controller.●Real-time cache.●Optional BBU (Backup Battery Unit).High-Performance and Extendable Hardware Platform ●64-bit multi-core processor.●PCI-E 2.0 bus.●Four 1000M Ethernet interfaces per controller.●SAS interface for storage enclosure.●High-density chassis. 4U chassis: 24 HDDs.HDD Detection and Repair/RAID Optimization●Detection before operation.●Detection in operation.●Fault repair.●RAID 0, 1, 3, 5, 6, 10, 50.●Global and local hot spare.●Quick RAID building.●Capability of cascading up to two storage enclosuresbehind a single SAS port.Advanced Data Protection●Synchronous backup of key information in system diskand HDD.●RAID-based tamper-proof data technology.●Auto data synchronization between devices.Energy Efficient●CPU load balance.●Auto fan tuning.User-Friendly UI●Quick configuration.●Various alarm management.●SADP protocol supported.●SNMP supported.Surveillance-Specialized Stream Media Direct Storage (Direct Streaming Mode)●Space pre-allocation strategy.●Direct storage for video stream and picture stream.●Supports direct IP camera/DVR/NVR streaming andrecording.●Supports camera access through RTSP, ONVIF, and PSIAprotocol.●Supports alarm/scheduled/manual recording.●N+1 technology.●Automatic network replenishment (ANR), timelyuploading, and video loss alarm.●Lock key videos.●Supports both Direct Streaming Mode and IPSAN Mode.●Search, play, and download videos by video type or videotime.IntroductionThe DS-A82 series is a dual controller-structure Hybrid SAN(Storage Area Network). Hikvision Hybrid SAN product creates a network with access to data storage servers, and it integrates Hikvision’s unique video direct streaming technology as well as supports IPSAN/FCSAN. This flexible, cost-effective solution features ONVIF-support tothird-party cameras, support for RTSP, and SIP protocols, and extended data retention. With no recording server needed, Hikvision’s Hybrid SAN systems truly make applications simple, flexible, and budget-friendlySpecificationModel DS-A82024DPerformance Direct Streaming mode:video (2 Mbps) + picture448-ch (recording + playback) IPSAN256-ch (recording + playback)Controller Controller Dual controllerProcessor64-bit multi-core processorCache per controller8 GB (extendable to 32 GB)/controllerHDD HDD slot24Interface/capacity SSD (optional), SAS/1TB, 2TB, 3TB, 4TB, 6TB,8TB,10TB,12TB,14TB,16TB Hot-swapping SupportedHDD support S ingle, RAID(Enterprise Hard Disk)RAID RAID0, 1, 3, 5, 6, 10, 50, JBOD, Hot-SpareNetwork Protocol iSCSI, RTSP, ONVIF, PSIAInterfaces Data network interfaceper controller4, 1000M Ethernet interface (4 × GbE or 2 × 10GbE is extendable)Management networkinterface1, 1000M Ethernet interface/ControllerMiniSAS interface SupportedVGA per controller1USB per controller3General Power supply RedundantConsumption (withHDDs)●Working: ≤ 507 W (1729 BTU with 24 HDDs);●Rated: ≤ 800 WEnvironmenttemperature●Working: +5 °C to +35 °C (41 °F to 95 °F)●Storing: -20 °C to +70 °C (-4 °F to 158 °F) Environment humidity●Working: 20% to 80%RH (non-condensing/frozen);●Storing: 5% to 90%RH (non-condensing/frozen) Chassis19-inch 4UDimensions (W × H × D)447 x 172 x 550 mm (17.6 x 6.8 x 21.7 in)Weight (without HDDs)≤ 33.5 Kg (73.9 lb)Typical ApplicationAvailable ModelsDS-A82024D000204170207。
AADvance培训手册中文版

AADvance培训⼿册中⽂版系统培训⼿册操作系统构建配置编程排除故障维护AADvance可编程控制器指南1.5版本2012年5⽉2AADvance System Training Manual, version 1.5注意The content of this document is confidential to ICS Triplex and their partners. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this documentation may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, for any purpose, without the express written permission of ICS Triplex.该⽂件内容对于ICS Triplex和他们的合作⽅均是机密的。
本⽂档包含有受版权保护的专有信息,公司保留其所有权。
没有ICS Triplex明确的书⾯许可,本⽂档的任何部分都不允许以任何电⼦或机械的形式或⽅式被复制和传播,包括复印和记录。
The information contained in this document is subject to change without notice. The reader should, in all cases, consult ICS Triplex to determine whether any such changes have been made.本⽂档所包含信息可以随时更改,不另⾏通知。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A Dual-Processor Solution for the MAC Layer of a SoftwareDefined Radio TerminalHyunseok Lee,Trevor MudgeAdvanced Computer Architecture LaboratoryDepartment of Electrical Engineering and Computer ScienceUniversity of Michigan{leehzz,tnm}@ABSTRACTConsiderable work has been devoted to studyingflexible computation structures for the physical layer of a software defined radio(SDR)terminal.However there has been al-most no research on protocol processors for the upper layer protocols such as the media access control(MAC)and link protocol.A general purpose processor(GPP)is sufficient for the protocol processing of a single mode terminal.How-ever,in the case of a multi-mode system required for SDR, there is a very wide set of possibilities for the MAC layer.In principle these too could be handled by a GPP.However, we show that a better solution is to use a GPP augmented by a small supplemental processor.The GPP is responsi-ble for the relatively complex protocol operations in the ac-tive mode,and the supplemental processor handles the idle mode operations.This separation of responsibilities simpli-fies the implementation of hard real-time responses required by some protocols(for example IEEE802.11),while main-taining the programmability needed to handle a wide rangeof protocols.In addition,this organization allows a signif-icant power savings in the idle mode.This is important because the protocol processor must process a large num-ber of tiny idle mode tasks whose aggregate effect over time dominates the power consumption in a wireless terminal.As part of our study we develop a hardware model of the supplemental processor in Verilog and its software model in ing commercial CAD tools we synthesized out design and evaluated the power consumption and response time of the platform.Our results show that the proposed platform meets the real-time deadlines at low power while maintain-ing programmability.Categories and Subject DescriptorsC.1.4[Processor Architectures]:Other Architecture Styles–Mobile processorsPermission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.CASES’05,September24–27,2005,San Francisco,California,USA. Copyright2005ACM1-59593-149-X/05/0009...$5.00.General TermsDesign,PerformanceKeywordsWireless platform,SDR terminal,Protocol processing1.INTRODUCTIONSoftware defined radio(SDR)is a wireless communication system whose function blocks are implemented by software routines so that various wireless protocols can easily be sup-ported by simple software changes.The concept of SDR originated in the military,but now it is emerging as im-portant commercial technology.For instance,4G,the next generation of wireless communication systems requires that multiple wireless protocols be supported[15].Although the concept of SDR is very attractive,there are many obstacles on the way to its commercialization;the particularly power consumption.There has been a lot of research effort on the physical layer but there has been almost no research on protocol proces-sors executing upper layer protocols.In the past this was implemented on aflexible general purpose processor(GPP) for single mode terminals.In this paper,we analyze the im-pact of multiple wireless protocols on the architecture of the protocol processor and propose a dual-processor hardware solution.To derive the requirements of the protocol processor we analyzed a collection of differnt wireless communication stan-dards including Bluetooth,IEEE802.11a/b/g,GSM,IS-95, IS-2000,and W-CDMA.One important requirement is the need for a tight response time of10us in the case of the IEEE 802.11protocol.Fast response time is needed because the whole channel is occupied by a terminal when it is generatinga response message.Thus,the protocol processor must re-spond quickly in order to maximize channel throughput.In addition,as explained in Section3.2,wireless terminals per-form many operations even during idle periods.A common characteristic of these idle period operations is a light work-load-a simplefield matching in most cases.Although the power consumption of each idle operation is very small,the aggregated idle power becomes dominant because a wireless terminal is idle most of the time.As shown in Figure1,we propose a heterogeneous dual-processor architecture consisting of a conventional main proces-sor and a simple supplemental processor.The main proces-sor provides the processing power needed for heavily loadedFigure1:Proposed hardware platform for upper layer protocol processing in an SDR terminalactive state protocol operations,whereas the supplemental processor provides an adequate but power efficient process-ing capability for the idle mode.As we will show in Section4.1,other candidate platforms employing a single GPP ora GPP plus ASICs have problems with scheduling or pro-grammability.The reason for using a GPP with minimal functionality as the supplemental processor is to achieve programming flexibility.However a GPP is power inefficient and slower than an ASIC solution.To see how these points impact the system we develop both hardware and software models for the supplemental processor and evaluate it with commercial CAD tools.The evaluation results are presented in Sec-tion5.They show that the supplemental processor provides flexibility with very little power overhead.The use of multiprocessor architectures for power reduc-tion purposes is not new.The paper by Olsen showed that a heterogeneous multiprocessor architecture is power effi-cient for hand held devices such as a personal data assis-tant(PDA),because it allows the user idle period to be efficiently managed[14].The paper by Kumar showed that a heterogeneous multiprocessor with a single instruction set architecture(ISA)is also power efficient even for general applications[9].The contribution of our study is to apply the heterogeneous multiprocessor concept to SDR for the upper layer protocol processing.There have been several studies on small microprocessors that consume less than1 mW power employing asynchronous logic or sub-threshold circuits[7][12].However,in this work we implement the supplemental processor using a conventional designflow,be-cause results in Section5.5show that any additional power gain will not be significant.2.OVERVIEW2.1Wireless Communication Networks Roughly speaking it is possible to classify wireless com-munication systems into three types:wireless personal area networks(WPAN),wireless local area networks(WLAN), and wireless wide area networks(WWAN).The WPAN sys-tem enables users to connect to various personal devices over short distances without wires.An application might be syn-chronizing data between a PDA and a desktop computer. Bluetooth is the most popular system at the moment. WLAN systems originated from wired LAN systems.They aim to replace existing wired LANs by high speed wireless channels.A typical terminal in this network is a laptop hav-ing wireless access.IEEE802.11a/b/g systems are the most widely used WLAN systems.Finally WWAN systems evolved from a telephone net-work.The early generation of WWAN systems such as AMPS,GSM,and IS-95provide voice service without spa-tial limitations.The3rd generation systems provide mul-timedia services like video telephony on wireless channels. The CDMA-2000and W-CDMA systems are common ex-ample.In the future,we will need terminals that simultaneously support many of the above protocols to seamless span WPANs, WLANs,WWANs,plus their future derivatives.2.2Wireless Protocol StackWe can divide the wireless protocol stacks into two cat-egories by workload characteristics:the physical layer and the upper layers.The physical layer consists of various real-time and computation intensive operations such as forward error correction and modulation.Due to the tight power budget and high computation requirements it is common to implement the physical layer in ASICs.In contrast the upper layer protocols consist of various control intensive operations such as media access control,re-transmission of corrupted frames,terminal mobility support, and radio resource control.Thus the upper layer protocols are implemented on a GPP except for some hard realtime operations such as MAC response generation and encryp-tion/decryption.Although both physical and upper layers are within the scope of SDR,we only focus on upper layer protocol process-ing in this paper.2.3SDR terminalConverging the features of several single mode terminals into one SDR terminal allows us more convenient wireless network access.For instance,we commonly use both cellu-lar phone and wireless LAN card.A cellular phone provides a low speed but seamless wireless connection whereas a wire-less LAN card provides a high speed Internet connection at limited area.The SDR technology enables us to adaptively select optimal network according to environment. Furthermore there exist several different wireless protocols even for almost identical services,for example W-CDMA and cdma2000.Some countries deploy the W-CDMA sys-tem for wireless multimedia service and other countries do cdma2000.The SDR allows international roaming with one terminal.3.SYSTEM REQUIREMENTS3.1Hard Realtime ResponseSourceTerminalDestinationTerminalFigure2:Data transmission procedure for IEEE 802.11networksPICH PCHSignal from basestation to terminalsTerminal1No paging message to terminal 1 There is a paging message to terminal 1 Figure 3:Paging Procedure of cdma2000and W-CDMA networksThe IEEE 802.11network differs from other wireless net-works in having short intervals between control packets as part of the data transmission.As shown in Figure 2,the transmitter and receiver exchange the request to send (RTS)and clear to send (CTS)MAC control packets prior to data transmission.This reserves a wireless channel,and the re-ceiver transmits an acknowledge (ACK)packet after data transmission to release the wireless channel.Because the re-served link cannot be used by other terminals while prepar-ing a MAC response,the IEEE 802.11protocol requires a very fast MAC response in order to maximize network throughput.For the MAC response generation,we need to analyze the header of the received MAC packet after decryp-tion.3.2Processing Tiny Operations3.2.1Paging in cdma200and W-CDMAPaging is a procedure whereby a network identifies the base-stations having the best wireless paths to a destina-tion terminal before establishing a user session.A terminal must be in its ready state to receive paging messages from base-stations during idle mode.WWAN networks have a two phase paging procedure so as to minimize the power consumed for paging message reception.In phase one,ter-minals periodically wake-up and decode the paging indica-tion channel (PICH)that carries simple on/offinformation indicating the existence of a paging message in the following paging channel (PCH)slot.The bits on the PICH are not protected by a forward error correction scheme such as a convolutional code.The reason for using an uncoded chan-nel is to save power by powering offerror correction,because it is one of the most power consuming blocks in a wireless terminal.In phase two,the terminals that have detected the transmission of a paging message through decoding the PICH start decoding the PCH with full functionality includ-ing error correction.In Figure 3,the first PICH bits indicate that there is no paging message in the following PCH slot,so the termi-nal turns of its receiver to save power.However the second PICH indicates that a paging message will be transmitted in the following PCH slot.Thus the terminal starts PCH de-coding.Although PCH decoding is a small task,the proto-col processor must be activated,because the paging message includes upper layer information.3.2.2Location Update in cdma2000and W-CDMADuring the idle mode,the terminals of a WWAN can drift in any direction.If there is no rough estimation of a termi-ATIM windowATIM windowTerminal 1Terminal 2Terminal 3Figure 4:Power management procedure of IEEE 802.11networknal location,a network needs to broadcast a paging mes-sage on the entire network.This is inefficient and avoided by a location update procedure.Several base stations logi-cally comprise a location update area.Whenever a terminal passes the boundary of a location update area,it sends a lo-cation update message to the base-stations in order to notify that it is moving to an adjacent location update area.Thus the network can limit the broadcasting range of a paging message to within the current location update area.3.2.3Power Management Procedures in IEEE 802.11NetworkIn an IEEE 802.11network,packet transmission is only allowed during the ad hoc network indication map (ATIM)windows.This restriction is to minimize terminal power consumption during the idle periods between packet bursts.As show in Figure 4,all terminals simultaneously wake up in ATIM windows.The terminals that have buffered traffic exchange ATIM request and ACK messages with the desti-nation terminals,so that the destination terminals remain awake in the following idle period.In the interval between ATIM windows,source and destination terminals perform actual traffic transmission while the remaining terminals turn offtheir receivers to save power.To decode the ATIM packet,the MAC layer and the encryption engine must be involved.3.2.4Operation StatesWWAN and WPAN networks have several operation states for terminal power saving and better radio resource uti-lization.Busy periods,short idle periods,and long idle periods between packet arrivals are mapped on different operation states that have different power and radio re-source overhead requirements.A W-CDMA network has Cell DCH,Cell FACH,Cell PCH,and URA PCH states,and a CDMA-2000network has Active,Control Hold,Sus-pended and Dormant states.Similarly Bluetooth has Ac-tive,Sniff,Hold and Park states.Among the above states,Cell PCH,URA PCH,Suspended,Dormant,Sniffand Park states are defined for idle period handling.They should be low power state.In these states the terminal performs vari-ous operations based on simple field matching.(a) (b) (c)Figure 5:Candidate platforms for the protocol processor of an SDR terminal4.PLATFORM DESIGN 4.1Platform ComparisonFor multiple wireless protocol processing we can consider three types of processor platforms:1)a single GPP;2)a GPP with ASICs;and 3)two or more GPP cores.The sin-gle GPP based platform,shown in Figure 5(a),provides the highest level of flexibility but has a scheduling problem.As we saw in Section 3.1,the protocol processor must generate a MAC response message within 10usec in order to support the IEEE 802.11protocol.In addition generally it is nec-essary to use a realtime operating system (RTOS)to cope with the algorithm complexity of the upper layer protocols.However,RTOSs are not able to context switch that fast e.g.uClinux,a Linux based RTOS,requires more than 10usec [5].This rules out organization (a).Another candidate platform is shown in Figure 5(b).A GPP is assisted by ASICs that cover idle periods and re-altime operations.Many commercial IEEE 802.11modems are based on this architecture to satisfy hard realtime re-sponse requirement [11][4][8].The GPP can be scheduled ef-ficiently because the ASICs take over the burden of hard re-altime MAC protocol processing,and ASICs are also power efficient.However,it is difficult to accommodate future pro-tocol extensions with this architecture,because of the hard-wired nature of ASICs.As an alternative to either of these extremes,we propose the dual-processor platform shown in Figure 5(c).Because both processors are programmable,they provide a high de-gree of flexibility.Two processors can be schedule inde-pendently by a task partitioning:complex tasks requiring an RTOS on the main processor,and simple hard realtime tasks on the supplemental processor.The simple tasks on the supplemental processor can be programmed without an RTOS.It allows us to meet the requirement of hard realtime response.As we will see in Section 5.5,the power consump-tion of the supplemental processor is almost as low as an ASIC without sacrificing flexibility.4.2Task PartitioningIn this subsection we explore the task partitioning and its mapping to the hardware.Two major issues of the task partitioning are the number of tasks mapped onto the sup-plemental processor and the complexity of the interface be-tween two processors.In this paper we propose assigning only idle period tasks and hard realtime tasks to the sup-Figure 6:Proposed dual-processor platform for the protocol processor of an SDR terminalplemental processor.This assignment minimizes power and simplifies the interface between the two processors.The number of tasks that can be placed onto the supplemental processor is limited by the hard realtime scheduling require-ments.If complex algorithms are mapped onto the supple-mental processor,it becomes difficult to program without the assistance of an RTOS.As we discussed in Section 4.1,it is impossible to meet the response time requirements if we use an RTOS.In addition,the heavy workload would result in complex hardware and raise power overhead during idle period oper-ations.The interface between two processors remains sim-ple only if we map idle mode tasks onto the supplemental processor.Most idle period tasks discussed in the previous section are essentially just a simple field match except for the IEEE 802.11networks where additional decryption of packets may be required.Therefore the length of the data needed for this field matching is less than packet header size -smaller than several tens of bytes in wireless communica-tions.The supplemental processor’s program can thus be very simple and does not require the support of an RTOS.4.3Proposed Platform4.3.1Main ProcessorThe data rate of applications executed on the main proces-sor varies widely from voice at 9.6Kbps to packet data at several Mbps.To support such widely differing date rates with minimum power consumption,dynamic voltage scal-ing (DVS)and dynamic frequency scaling (DFS)techniques are essential for the main processor.The quality of service (QoS)parameters,determined at an initial session setup,can be used to indicate voltage and frequency scaling.For example,information that an established session has a con-stant bit rate permits aggressive processor scheduling with-out any slack.At short idle periods between packet bursts,a clock gating technique can be applied instead of DVS or DFS.Because the supplemental processor covers long idle periods the main processor has no need for leakage current reduction schemes such as adaptive body biasing -it can simply be shut off.This simplifies the main processor if it has a supplemental processor compared to the typical low power GPP for other portable devices [13][6].4.3.2Supplemental ProcessorThe simplicity of tasks performed on the supplemental processor allows us to minimize its functionality.The in-struction set of this processor consists only of the essential instructions required to perform small control actions like paging message decoding.The width of the datapath needs to be32bit for fast packet processing.However,we used a processor model with an8bit datapath for our experiments because it was difficult tofind a small32bit commercial model with a complete programming environment.In Sec-tion5.3.2,we will show how a32bit datapath yields better power performance than an8bit datapath.Thus our power studies using a8bit processor are a worst case.The supplemental processor requires a timer to generate events because many operations in wireless protocols are timer based.The timer events are processed by interrupt handling logic.The supplemental processor has two inter-rupt ports,one for an interrupt from the baseband modem indicating the arrival of a new packet,and another port for an interrupt from the timer.A clock gating technique is used in the supplemental processor to reduce the power dis-sipation during idle periods between interrupt events.The timer,interrupt handling logic,and clock gating provide an efficient implementation method for event driven applica-tions.In addition,the supplemental processor is equipped with a hardware comparator.The hardware comparator is de-signed for thefield matching operation that the supplemen-tal processor is frequently called on to perform.The supplemental processor needs a hardware random number generator(RNG)that is used for a random back-offoperation performed in the MAC layer.The execution time of a software based RNG is too long to meet the tim-ing requirements.The randomness required for the back-offoperation need not be of a high quality,so a linear feed-back shift register(LFSR)is adequate.However we need to consider the impact of the initial seed of the LFSR.The initial value of aflip-flop is not random because small dif-ferences in the size of the transistors in aflip-flop lead to bias.This in turn can induce a load sharing problem in the ad hoc mode of the IEEE802.11network.The overhead of periodic beacon packet transmission is unevenly distributed if we use a LFSR without a proper random seed.To avoid such a situation we place a direct access path so that the power manager can load the initial seed into the LFSR. 4.3.3MemoriesAs shown in Figure6,the memory in our platform can be classified into three types,program memory,state mem-ory,and data memory.The program memory stores the execution code of the processors.The program memory of the supplemental processor is accessed by both the main and supplemental processor.The main processor loads the execution program of the supplemental processor prior to activating it.A single port SRAM is used for the program memories of both processors.Meanwhile the state memory stores protocol state infor-mation such as a terminal identifier and the QoS parameters of established sessions.When supporting the IEEE802.11 protocol,both the main and supplemental processor need to be activated at the same time and simultaneously access the state memory.Thus a dual port memory is used for the state memory.The size of this memory varies according to the protocol.However,because the supplemental processor needs just a small portion of the state information,the size of the state memory need not exceed several hundred bytes.BasebandmodemSupplemetnalprocessorMainprocessorTimeFigure7:Packet reception procedure while execut-ing the IEEE802.11protocolThe data memory stores user traffic processed by the pro-tocol layers.The baseband modem stores packets which are received from antenna at the data memory of the supple-mental processor.The processed packet is passed to the main processor by memory copy to the data memory of the main processor.For transmission,packets are copied in the reverse direction.4.3.4Power ManagerA power manager controls the power state of all blocks in a wireless terminal.Therefore,it is always powered even at idle periods.It has a timer to trigger a periodic wake-up event.There are three input ports in the power manager. One input port from the main processor is used to config-ure the operation mode of the power manager according to the operating state change of a protocol.Another input port is assigned to the supplemental processor.Through this port,a request for the activation of the main proces-sor is transmitted when the supplemental processor receives a communication request.The third port is connected to the baseband modem.If the baseband modem detects a signal on a PICH,it requests activation of the supplemen-tal processor for PCH decoding through the third interrupt port.4.4Application ExamplesBecause the protocol processor discussed in this paper aims to support multiple wireless protocols,its operation procedure changes according to the type of protocol loaded onto the platform.Figure7shows the interaction between the main processor and the supplemental processor when the IEEE802.11protocol is loaded onto the protocol processor. The operation procedure shown in Figure7is when the data packet matches with the terminal’s address.When this oc-curs the supplemental processor assists the main processor by independently generating MAC response messages dur-ing the data reception procedure.Figure8shows the paging procedure when the W-CDMA protocol is loaded onto the platform.The operation proce-dure shown in Figure8is when the destination of the paging message matches with the terminal.After periodically be-ing activated by the power manager,the baseband modem wakes up the supplemental processor if the PICH bits in-dicate there will be a paging message on the PCH channel. Only the supplemental processor is activated while decoding a paging message.The main processor is not activated un-Baseband modem Power manager Main processorSupplemental processor Figure 8:Paging message reception procedure while executing the W-CDMA protocoltil the supplemental processor decodes the paging message completely.5.EXPERIMENT AND ANALYSIS 5.1Models for Experiment5.1.1Main ProcessorAs our main processor model we used the OPENRISC1200,a 32bit open source RISC processor [3].The features of OPENRISC are very similar to other commercial GPPs used in mobile devices except that it does not support power re-duction techniques like DVS,DFS,and clock gating.How-ever,this is not important because this model is only used for wake-up power measurement,where these techniques are not involved.We don’t measure the dynamic power of the main processor,because it consumes far more power than the supplemental processor.The features of our HDL model for the main processor are as follows.•32bit RISC processor•Single issue 5-stage pipeline in-order machine •Harvard architecture •32bit Hardware Multiplier •8K data cache with MMU •8K instruction cache with MMU5.1.2Supplemental ProcessorAlthough we will show that a 32bit processor is optimal for the supplemental processor in Section 5.2.2,we take as a base the architecture of a commercial 8bit processor,Mi-crochip’s 16F84,in order to develop a power model of the supplemental processor [1].It is used for a sensor network node that has similar requirements.We added a RNG,a hardware comparator,and a data memory interface for fast packet processing.Figure 9shows the architecture of the supplemental processor model.The detailed configuration of the supplemental processor is as follows.•8bit RISC architecture•Single issue 2-stage pipeline in-order machine •Harvard architecture•33instructions •68x 8bit registers•Hardware timer,interrupt handler,and clock gating •Hardware random number generator•Interface to data memory •Hardware 48bit comparator •4K x 14bit program memory •4K x 8bit dual-port state memory5.1.3Application SoftwareFor this study we selected the power managment proce-dures for the IEEE 802.11protocol,which is depicted in Figure 4,as the application model for our dynamic power measurements.This procedure was selected because it is currently one of the most complex and time constrained ap-plications for packet reception.The IEEE 802.11application model is divided into two parts:an interrupt service routine and the main routine.In order to avoid an event loss,the interrupt service rou-tine performs only a minimal number of operations such as hardware re-initialization.The main routine consists of an infinite loop.At the beginning of each iteration,the main routine checks the event flags.If there are no events,the main routine enters a clock-gated mode to save power by executing sleep instructions.If an interrupt is generated by the timer or the baseband modem,the main routine acti-vates the clock signal and checks the event flags to identify the interrupt source.In the event of a packet reception,the main routine loads the packet header into the hardware comparator to analyze whether the packet matches with the terminal’s address or the broadcast address.If the packet matches and is valid,the main routine performs the ap-propriate actions like generating a response message and informing the main processor of a packet reception.5.2Dynamic PowerDynamic power is only consumed during instruction exe-cution.To measure it we synthesized our hardware model using Synopsys’Design Compiler and extracted power re-sults with PrimePower.Memory was created with Artisan’s memory compiler.Figure 10shows the experiment flow used for dynamic power measurement.We did not consider the power consumption due to interconnection wire because gen-erally it is not dominating factor at 0.18u technology which we used for the experiment.5.2.1Power Consumption Profile of the Supplemen-tal ProcessorFigure 11shows the power consumption profile of the sup-plemental processor when it executes the software model outlined at Section 5.1.3.We see that the blocks that con-sume the most powers in the supplemental processor are the timer and the program memory.The timer is power hun-gry because it has to continuously monitor when to wake-up.Reducing power consumption of the timer will have a notice-able impact on the supplemental processor’s dynamic power.In addition,its program memory consumes a large fraction of power because it is relatively large compared to other blocks on the supplemental processor.Thus it is important。
