ALEWIFE SYSTEMS MEMO #11 The LimitLESS Cache Coherence Protocol
wifeofbath

wifeofbathScene oneOn the way of pilgrimage, Mrs. Bath, a tall and strong woman, with ruddy complexion, wearing a big hat. She is quiet well-off, travelling all around the world, married to 5 five husband but now they are all dead.“I am so well-deserved to be an expert in a relationship; I’ve been with five different men!” Ms Bath brags. Now I will tell you guys a story about the relationship between husband and wife.A long time ago when king Arthur ruled the land, there was a great knight who lived all the pleasures of life. But one day, a lady of the court told the king that the knight had attacked her. Arthur was very angry and said that the knight must die.Scene twoL: My lord. Some rumors go that knight commit a serious crime. He attacked a lady of the court. He insults our chivalry. I hope my lord can make a fair judgment and punish him.K: Well, I wonder. Solder! Send him here to me! I want to interrogate him personally.B: My lord.K: You attacked a lady of the court, didn’t you.B: Yes, my lord. But I can explain.K: How dare you! You insult our chivalry. You must die.Everybody: CUT OFF HIS HEAD.Q:oh ,please,my lord.the knight is such a great person.he has been loyal and faithful to this country.and he deserves a second chance for the mistake he made this time. Please give him to me ,and I will find a proper way to deal with him,and I promisehe will never make the same mistake again.King: well my dear queen rules.Scene threeQ:I have the power to let you live or die, you will live only if you can answer one questionB: My majesty. Thank you for giving me this precious opportunity. Could I know what the question it is?Q: What is it that women most desire?B: Oh! Ask you pardon my majesty. It’s too difficult. As you know women always have a lot of desires. We don’t know how to please them, because we don’t know what they most desire.Q: if you can’t tell me at this moment ,you may go away for a year and a day to find the answer. But if you return without the answer ,remember this :the axe is sharp!B: I have no choice but to find the answer.Scene fourThe knight travelled through the whole country, from coast to coast, looking for the answer. He knocked on every door. “What is it that women most desire?” he asked. But he could not find two people who agreed.B: Oh! GOD! It’s too late to regret my sin. If I hadn’t committed that crime, I wouldn’t have been punished. There is a bar. I think I should have a cup of beer, and clear up the answers.B:Please give me a glass of beer.L: Hi! Buddy! You look so upset. What’s up?B: Don’ mention that. I’m looking for the answer to “what is it that women most desire.” If I can’t find the answer, I will die.L: Oh….Let’s see…..I think w omen want to be rich, so that they can buy lots of jewelry andclothes. As they like to compare with each other, they are easy to be jealous. Money can gratify women’s vanity. Yes, women desire money most.B: En…you may be right, but this is not the best a nswer. Anyway, thank you.L: welcome.L and Q: fruitL: Hey young boy. What’s eating you? I think an apple can make you better.B: Well, I did have some trouble. I will buy your apple if you can answer my question.L: Say that see. Maybe I know the answer.B: what is it that women most desire??L: Well. As a woman, I want a good reputation. You know, I am not young. I needn’t beautiful clothes or much money. I just hope everyone can respect me.Q: No! No! Women want pleasure of course. We want to be spoilt and flattered. I am going to a party and I am sure I can enjoy myself. Will you join us? Mr.knight.?B: Thank you for your invitation, my lady. I would like to, but I have to go no my journey. Also thank you for your answer, madam. I will buy some apple to keep my promise.L: Here you are. I hope my answer will help you.在中世纪,巴斯妇的婚姻观念算是前卫的,在当时她算是领潮者。
NETGEAR GS305v3和GS308v3无管理5 8口巨量以太网开关安装指南说明书
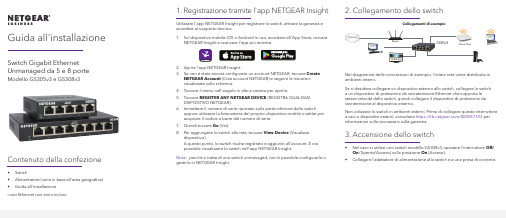
Guida all'installazione Switch Gigabit Ethernet Unmanaged da 5 e 8 porte Modello GS305v3 e GS308v3Contenuto della confezione• Switch• Alimentatore (varia in base all'area geografica)• Guida all'installazionei cavi Ethernet non sono inclusi.1. Registrazione tramite l'app NETGEAR InsightUtilizzare l'app NETGEAR Insight per registrare lo switch, attivare la garanzia eaccedere al supporto tecnico.1. Sul dispositivo mobile iOS o Android in uso, accedere all'App Store, cercareNETGEAR Insight e scaricare l'app più recente.2. Aprire l'app NETGEAR Insight.3. Se non è stato ancora configurato un account NETGEAR, toccare CreateNETGEAR Account (Crea account NETGEAR) e seguire le istruzionivisualizzate sullo schermo.4. Toccare il menu nell'angolo in alto a sinistra per aprirlo.5. Toccare REGISTER ANY NETGEAR DEVICE (REGISTRA QUALSIASIDISPOSITIVO NETGEAR).6. Immettere il numero di serie riportato sulla parte inferiore dello switchoppure utilizzare la fotocamera del proprio dispositivo mobile o tablet peracquisire il codice a barre del numero di serie.7. Quindi toccare Go (Vai).8. Per aggiungere lo switch alla rete, toccare View Device (Visualizzadispositivo).A questo punto, lo switch risulta registrato e aggiunto all'account. È orapossibile visualizzare lo switch nell'app NETGEAR Insight.Nota: poiché si tratta di uno switch unmanaged, non è possibile configurarlo ogestirlo in NETGEAR Insight.2. Collegamento dello switchNel diagramma delle connessioni di esempio, l'intera rete viene distribuita inambienti interni.Se si desidera collegare un dispositivo esterno allo switch, collegare lo switcha un dispositivo di protezione da sovratensione Ethernet che supporta lestesse velocità dello switch, quindi collegare il dispositivo di protezione dasovratensione al dispositivo esterno.Non utilizzare lo switch in ambienti esterni. Prima di collegare questo interruttorea cavi o dispositivi esterni, consultare https:///000057103 perinformazioni sulla sicurezza e sulla garanzia.3. Accensione dello switch• Nel caso si utilizzi uno switch modello GS308v3, spostare l'interruttore Off/On (Spento/Acceso) sulla posizione On (Acceso).•Collegare l'adattatore di alimentazione allo switch e a una presa di corrente.Access PointRouterGS305v3Collegamenti di esempioNETGEAR, Inc.piazza della Repubblica 32 20124 Milano NETGEAR INTL LTDFloor 1, Building 3, University Technology Centre Curraheen Road, Cork,T12EF21, Irlanda© NETGEAR, Inc. NETGEAR e il logo NETGEAR sono marchi di NETGEAR, Inc. Qualsiasi marchio non‑NETGEAR è utilizzato solo come riferimento.Supporto e CommunityVisita /support per trovare le risposte alle tue domande e accedere agli ultimi download.Puoi cercare anche utili consigli nella nostra Community NETGEAR, visitando la pagina .Conformità normativa e note legaliPer la conformità alle normative vigenti, compresa la Dichiarazione di conformità UE, visitare il sito Web https:///about/regulatory/.Prima di collegare l'alimentazione, consultare il documento relativo alla conformità normativa.I LED indicano lo stato.LED DescrizionePower (Alimentazione)• Acceso. Lo switch è collegato all'alimentazione.• Spento. Lo switch non è collegato all'alimentazione.Porta• Verde senza intermittenza. Lo switch ha rilevato uncollegamento con un dispositivo acceso su questa porta.• Lampeggia in verde. La porta invia o riceve traffico.• Spento. Lo switch non rileva nessun collegamento suquesta porta.Aprile 2020。
My ideal wife

Hello everyone, today I’ll show my ideal wife to you.As we all know, when people on the wedding, they always oath : To have and to hold, from this day forward, for better, for worse, for richer, for poorer, in sickness and in health, until death do us apart.That is to say, wife must stay with her husband no matter what happened. Never give up and never abandon.But who is my ideal wife? The clean and pure one? The sexy one or the one like chun brother?First, I think my ideal wife should be clean, healthy, declining to non-mainstream. Health is the most important thing, rather than pretty. If you are not excellent enough, in this world, beautiful women may be too dangerous. My ideal wife’s clothing may be like as following, fashion style, neat, China without demon, plain and dignitaries.Second, the wife is not required to have a lovely face, a very rich background, and a good shape of body, but she must act gracefully and have an inner sprite in her heart. When her husband is ill, she can take good care of him. when her husband is faced with some difficulties, they can work together to find ways to solve these problems. Life will never be boring with her, because she has a good sense of humor. She is kind to every people around her .Third, our parents are the forces of life, so we must cherish them. The woman who knows how to honor their parents and respect for the elders is of great wisdom.Fourth, the most important one is faith. Love can only be used to water a pool instead of pouring the earth. No matter how the situation turns, if she choose to get married with me, she must love me all her life.Zhou enlai and Deng yingchao have set an example for us young. Couples should love, respect, encourage, comfort, humility, forgive, help and learn each other.。
译林版高中英语选择性必修第二册 UNIT 2 Sports culture 单元提能强化练

3.What does the underlined word “them” in paragraph 4 refer to?
A.Vampires.
B.Teenagers.
C.Different styles. D.Her works.
答案 A 解析 词义猜测题。根据第四段中的“But vampires were the first characters
ⅠⅡⅢⅣ
However,some have been keen to point out that yes,martial arts in every school would be great,but finding those who are trained and qualified (合格的) to teach martial arts could probably prove to be challenging.They believe it is a chicken and egg situation,where without compulsory (强制的) curriculum of martial arts,those who are good at it may never find themselves in a dojo (武 术馆) to find out.But to bring it to everyone you need experienced trainers who can teach the martial arts without fear of mishap (不幸事故) or physical damage. 【语篇导读】本文是一篇议论文,主要论述的是武术是否应该被列入学校 的主要课程。
贝隆夫人生平介绍

字体大小:大| 中| 小2006-06-24 10:37 - 阅读:3444 - 评论:10Evita是阿根廷前总统贝隆的夫人,她出生贫寒,做过舞女和影视演员,她靠姿色和手腕成为贝隆夫人后,为阿根廷的社会、劳工、医疗等方面均做出过卓越的贡献,逝世时年仅33岁。
贝隆夫人的传奇经历一向是剧作家非常感兴趣的题材,1976年,韦伯首先推出了由朱丽叶•科文顿(Julie Covington)演唱的单曲《阿根廷别为我哭泣》(Don’t cry for me Argentina),随着这首歌的轰动,由寇姆韦尔金森加盟的唱片随即发行,而且不出意料地广受欢迎。
1978年,在万千音乐剧迷的企盼下,《贝隆夫人》在伦敦爱德华王子剧院正式上演,创下了连演八年的惊人纪录。
次年9月,它又登上了百老汇的舞台,拉开了英国音乐剧攻陷百老汇的序幕。
这里介绍的DVD是1996年由麦当娜、班德拉斯和普莱斯主演的电影版本,其中移植了舞台剧的所有歌曲。
正如《万世巨星》被宗教人士认为贬低耶稣一样,这部电影由于描写了贝隆夫人早年的风尘生涯,在开拍时就遭到了阿根廷群众的抗议和抵制,再加上导演挑选以性感出位的表演而闻名的歌星麦当娜来出演阿根廷的国母,更是屡遭非议。
后来的事实证明,麦当娜的演出风格无损于她对角色的精当把握,也不会遏制她的艺术天分和敬业精神,尽管韦伯为适应麦当娜的音域特地把《阿根廷别为我哭泣》降了几度,但她的演绎自然贴切,歌声真切感人,不但在拍摄时感动了全体摄制组,还使了整个阿根廷完全接受了麦当娜扮演的这个角色,为这种名曲增添了新的光彩。
麦当娜因此获得当年金球奖最佳女主角奖实非侥幸。
对于这样一部唱做俱佳的DVD,音乐剧迷实在没有不收的理由.阿根廷,别为我哭泣”(Don’t Cry for Me, Argentina)是1996年电影《贝隆夫人》(Evita)的主题曲。
该片由歌坛天后麦当娜(Madonna)和安东尼奥.班德拉斯(Antonio Banderas)主演,描写的是阿根廷的第一夫人——艾薇塔的悲欢离合、大起大落、享尽荣华富贵,也尝遍心酸坎坷的一生:她出生贫寒,但对未来充满憧憬,但在那个时代,经过不懈的努力,具有美丽容颜的她很快在一个摄影师的镜头下成名,从此辗转在富人和官员中,直到她遇到贝隆上校——一个声望上升的军官,她才脱颖而出,成为耀眼的政治明星。
黑龙江省龙东十校2024-2025学年高二上学期开学考试英语试题

黑龙江省龙东十校2024-2025学年高二上学期开学考试英语试题一、阅读理解We are currently seeking a qualified and experienced individual to join our team as a marketing manager. As a key leadership position within our organization, the marketing manager will play a crucial role in driving the department’s success and contributing to our overall business objectives.Qualifications:*Bachelor’s degree in business administration, management or related fields.*Proven experience in a marketing role, with a track record of successfully leading teams and achieving results.*Strong communication, interpersonal and problem-solving skills.*Proficiency in relevant software apps.Responsibilities:*Overseeing daily operations of the department, including staff management, budgeting and goal setting.*Developing and implementing strategies to meet departmental targets and enhance efficiency.*Cooperating with cross-functional teams to ensure seamless coordination and communication.*Providing leadership and guidance to team members to develop a positive work culture and professional growth.If you are a motivated and enthusiastic leader with a passion for driving organizational success, we invite you to apply for the position. Join us in shaping the future of our department and making a lasting impact on our company.To apply, please submit your resume and a cover letter detailing your relevant experience and why you are the ideal candidate for this role. We look forward to welcoming a dedicated and ************************************************************.1.What is a must to apply for the position?A.A master’s degree.B.A strong body.C.The related work experience.D.The ability to develop software.2.What does the marketing manager have to do?A.Communicate with consumers regularly.B.Assist the leaders to develop annual plans.C.Achieve the overall goal of the industry.D.Help co-workers develop their business. 3.How can you get in touch with the interviewer?A.By filling out a form.B.By sending an email.C.By writing a letter.D.By making a phone call.Over the weekend, a Pennsylvania man risked his life to save his neighbors from a burning home, as captured in dramatic video footage.Oscar Rivera was playing with his children in his backyard on April 14 when he heard a loud boom (响声). Rushing to the front yard, he saw that the house across the street was engulfed in flames, with his neighbors trapped inside.According to WFMZ-TV, Rivera didn’t hesitate. He climbed up the three-story building, which was already covered in flames. On a narrow ledge (窗台) at the burning home, a woman was trying to pull a man out of an attic window as smoke poured out. The man was calling for help.Rivera and a neighbor quickly grabbed a ladder and rushed to assist. “I just started jumping, jumping and jumping,” Rivera told WFMZ-TV. He managed to reach the top floor and pulled the man from the window, who had yelled, “Help me. I can’t walk.”Eyewitness Janeen Huth, who recorded the rescue, praised Rivera for risking his life while his young children watched from the door. “Come on! Come on!” Huth can be heard shouting in the video, as other onlookers and firefighters worked to assist. “Rivera is a true hero,” she told The Morning Call. Rivera managed to get the victim onto the ledge, and firefighters then took over, bringing the man to safety.The rescued man sustained critical burns and was taken to the hospital, according to WFMZ-TV. The fire damaged six homes and led to the evacuation (疏散) of 20 people. The cause of the fire is currently under investigation. “I hope he’s okay,” Rivera said about the man he saved.4.What does the text describe?A.An investigation into a fire.B.A man’s heroic rescue.C.A fire department’s response.D.A fire that destroyed several homes. 5.What made Rivera rush to the front yard?A.Hearing a loud boom.B.Seeing the flame.C.Hearing a call for help.D.Being informed about the fire.6.What did Rivera do in the rescue?A.He provided first aid.B.He helped guide firefighters.C.He called emergency services.D.He pulled the man out.7.How did Janeen Huth react to Rivera’s action?A.She was indifferent.B.She admired his bravery.C.She criticized him for risking his life.D.She thought he should wait for firefighters.The immune (免疫的) system has special defense and attack strategies reserved for viruses (病毒). These involve tagging the viruses with antibodies and killing cells infected (使感染) by the virus. A global health crisis can bring the world to its knees, highlighting the huge impact a virus can have. This tiny organism, invisible under a normal microscope, can wreak havoc on worldwide.There are more viruses on Earth than stars in the universe, so why haven’t we always been maintaining social distance? Primarily because not all viruses can infect us, and for those that do, the body handles them quite well. To put it simply, viruses are extremely small parasites that infect all sorts of life, from the smallest bacteria to the largest mammals; they are considered parasites because they can’t survive by themselves. Viruses infect health y host cells and use their cellular “tools” to make more copies of themselves.Viruses are everywhere—in the air we breathe, the water we drink, and the land on which we walk. Yet, even after being bombarded with viruses, our body still manages to stay strong. This is because of our immune system and its clever strategies to fight back against viral attacks! Fortunately, with our modern healthcare advancements, we have extra help to fight viruses. These include vaccines, antiviral drugs, and other health technologies to keep us going in this never-ending war.As time goes by and our bodies encounter more viruses, we develop better immunological memory. This is the body’s way of remembering past infections, making it better prepared for future ones.8.Which can replace the underlined phrase “wreak havoc on” in paragraph 1?A.Depend heavily on.B.Have a bad effect on.C.Take the side effect off.D.Cut the whole power off.9.Why do we always fail to maintain social distance despite lots of viruses?A.Not all viruses infect humans.B.Not all viruses are small.C.Viruses need host cells.D.Viruses infect all life forms.10.What is one of the strategies our body uses to fight viral attacks?A.Reducing the number of viruses in the environment.B.Avoiding contacting with infected individuals.C.Taking advantage of the immune system.D.Increasing exposure to viruses.11.What can be the best title for the text?A.What is the definition of unusual viruses?B.How to know well the immune system?C.How does our body fight viruses?D.How to break down the viruses?A major tech company has expanded options for keeping personal information from online searches. The company stated earlier this week that it would allow people to request the removal of more types of content, such as personal contact information like phone numbers, email addresses, and physical addresses, from search results. The new policy also permits the removal of other information that may pose a risk for identity theft, such as confidential (机密的) login accounts.In a statement, the company said that open access to information is vital. “But so is empowering (授权) people with the tools they need to protect themselves and keep their sensitive, personally identifiable information private,” the statement continued. “Privacy and online safety go hand in hand. And when you’re using the Internet, it’s important to have control over how your sensitive, personally identifiable information can be found.”Previously, the company had allowed people to request the removal of highly personalcontent that could cause direct harm. This included information such as bank account or credit card numbers that could be used for fraud (欺诈).“However, as information increasingly appears in unexpected places and is used in new ways, policies need to evolve,” the company said. Having personal contact information openly available online can also pose a threat, and the company reported receiving requests to remove such content as well. It states that when it receives such requests, it will review all the content on the web page to avoid limiting the availability of useful information or content on public record on government or other official websites. “It’s important to remember that removing content from our search results won’t remove it from the Internet, which is why you may wish to contact the hosting site directly, if you’re comfortable doing so,” the company advised.12.What can we learn from the company’s statement?A.Keeping online private information safe is a must.B.Improving the net environment for citizens is a dream.C.The exposure of public information causes a discussion.D.Making a balanced approach to online safety is a fashion.13.Why does the company review web page content before removing personal information?A.To obey data privacy laws.B.To take down the entire website.C.To increase online personal information.D.To avoid removing useful or publicinformation.14.What is the main idea of the text?A.Personal information can be removed from online searches.B.Tech companies can find more images and information.C.Privacy risks arise from publishing private information.D.Tech companies know what you’ve done over the years.15.What is the text likely to be?A.A research paper on online privacy.B.A new approach to using a search engine.C.An advertisement for a data privacy service.D.A news report about privacy protection.Do you know what carpet cleaning is and how it works? This article will discuss it with you.Carpet cleaning is a service to remove the dirt, stains and other things from carpets and make them clean. People hire different carpet cleaning services to make their carpets look cleaner, more appealing and away from harmful infections. According to experts, people must clean their carpets once or twice a year. 16 .According to carpet manufacturers, hot water extraction is one of the most professional and recommended ways of cleaning carpets. 17Dry cleaning is also used for cleaning the carpets but this is far easier than wet cleaning.18 However, it is still used for cleaning the carpets which are not that dirty.Vacuum (真空) cleaning is mostly used in offices and houses by people themselves. People use a vacuum cleaner to clean the carpets and it is an effective method.19 Therefore, carpet cleaning must be done minimum 1-2 times a year to prevent yourself from infections, allergies, and so on. Another benefit is that it saves you a lot of money. If you don’t clean them on a regular basis, you have to purchase them.You have understood a lot about carpet cleaning. 20 Do not regard this as a trivial (琐碎的) matter. It concerns the health of you and your family.A.It is time for you to take action.B.Prepare yourself before you begin.C.It is not that better than wet cleaning.D.Dirty carpets damage your health a lot.E.Dry cleaning is more effective than wet cleaning.F.Now, the question is what methods are used to clean them.G.It can remove the dirt and other things deep from the carpets.二、完形填空My husband and I had been married for ten years when I got Stevens-Johnson syndrome (综合征). With painful blisters (水疱) all over my body, I, who had been independent, rapidly became 21 .My husband, Scott, was occupied taking care of kids and cooking dinners. He also became my personal caretaker, applying the 22 to all of my blisters because my hands couldn’t dothe job. I was 23 at total reliance on someone other than myself. At one point, I mentally and physically hit 24 , thinking I was a weak person. And that 25 me.I recovered from my illness, but I couldn’t recover from the negative 26 . This loss of27 affected the rest of my recovery. Fortunately, things 28 . Recently Scott and I went ona long bike ride. At one point with sharp pain 29 in my tired legs, I couldn’t go any further. Seeing me 30 , Scott stopped in front of me, saying, “Stay close behind me.” Scott was 31 me along. My legs quit burning 32 as my cycling became easier, and I was able to catch my breath.I now 33 that love between us is powerful. True love is forged (锻造) by the fire of late nights with sick family and days of 34 to make ends meet. I also believe that during these 35 times, love has the power to make us become stronger. 21.A.worthless B.helpless C.fearless D.homeless 22.A.medicine B.disease C.mission D.strategy 23.A.shocked B.amused C.embarrassed D.puzzled 24.A.goal B.bottom C.future D.desire 25.A.taught B.forgave C.inspired D.troubled 26.A.thought B.plan C.comment D.aspect 27.A.direction B.confidence C.dream D.success 28.A.took over B.showed off C.turned around D.stood out 29.A.extending B.reducing C.escaping D.disappearing 30.A.relieve B.complain C.leave D.struggle 31.A.walking B.sending C.pulling D.bringing 32.A.frequently B.initially C.strangely D.quickly 33.A.hope B.argue C.permit D.believe 34.A.trying B.daring C.choosing D.promising 35.A.common B.difficult C.pleasant D.primary三、语法填空阅读下面短文,在空白处填入1个适当的单词或括号内单词的正确形式。
安全数据表(SDS)单号:1796009-ENG-06,发布日期:1998年2月18日,修订日期:2
Safety Data SheetDocument number First issued Revised date Revision Issued by Page 1796009-ENG-06 1998-02-18 2008-01-29 5 Jeanette Hasseson 1 of 4Alpacon 0091. Identification of the substance/preparation and of the company/undertakingTrade Name: Supplier:Alpacon 009 ALFA LAVAL ABHans Stahles vägProduct Type: S-147 80 TumbaEmulsion breaker SwedenTel: +46 8 530 650 00e-mail:Emergency number: +46 8 33 70 43 open 24 h2. Hazard identificationThe surfactant might cause serious damage to eyes and may cause long-term adverse effects in the aquatic environmentIf the product is used as recommended the surfactants will be soluble in oil and therefore they will be excluded in the water- phase.3. Composition/information on the ingredientsHazardous ingredients Weight-% CAS No ECNoClassification Risk PhrasesPolymer 5 – 15 - - NoneSurfactants 5 – 10 68989-03-7 - Xi, N R41, 51/53 See section 16 for explanations to R-phrases.4. First –aid measuresFirst aid – Inhalation Move to fresh air.First aid – Skin contact Wash off with plenty of water.First aid – Eye contact Rinse immediately with tepid water for several minutes. Proceedthe rinse during transport to hospital.Obtain medical attention.First aid – Ingestion Rinse mouth and drink at least 1-2 glasses of water. Do notinduce vomiting.Obtain medical attention.5. Fire- fighting measuresExtinguishing media All extinguishing media are suitable.Special hazards of product The product is not flammable. In case of fire the product mightform hazardous gases as NOx and COx.Protective equipment for fire fighting Not applicable.Fire –fight If the fire is extinguished with water environmental dangeroussubstances might be entering the environment.6. Accidental release measuresPersonal precautions Wear suitable goggles and gloves.Environmental precautions Prevent spills from reaching sewage, wells and watercourses. Spillage Absorb spills with sand, earth or other inert material. Collect andremove for destruction.Large spillage Contact local authority7. Handling and storageHandling Do not mix with other chemicals. Use recommended personalprotection according to section 8.Storage Store in a closed container.8. Exposure control / personal protectionRespiratory protection Appropriate ventilation. Provide facilities for rinsing eyes.Skin protection Protective gloves of nitrile.Eye protection Safety goggles.Ingestion Do not eat or drink during use. Wash hands before eating.9. Physical and chemical propertiesPhysical state Clear liquid.Colour Slightly yellow.Odour Weak smell.Density at 20 °C (g/ml) 1.025± 0.005.pH (as is) at 20 °C 7-9°brix 17.8±0.6.Viscosity at 25 °C (SP01/20 rpm) (cP) 1368±130.Cloud point during heating (°C) 50ºC.Flash point >100 º C10. Stability and reactivityStability The product is stable under normal conditions, but it decomposesat high temperatures.Conditions to avoid Extreme heatMaterials to avoid None knownHazardous decomposition products None known if the product is handled as recommended. In caseof fire the product might form hazardous gases as NOx and COx.11. Toxicological informationSkin At prolonged or frequently use of the product blush might occur.Eyes The product might cause serious damage to eyes.Consumption Low acute toxicity . Might be irritating to mucous membrane.LD50 oral rat 4500mg/kgSkin irritation test rabbit Slightly irritatingEye irritation test rabbit Strongly irritatingSensibillisation Not allergenicGen toxicity Not mutagenic12. Ecological informationLC50 96h (fish) >100mg/lNOEC 96 h (fish) > 100mg/lEC50 48h (Daphnia magna) > 100mg/lNOEC 48 h (Daphnia magna) > 100 mg/lDegradation No readily bodegradable13. Disposal considerationsDisposal of product: State and local disposal regulations may differ from federaldisposal regulations. Always dispose in accordance with federal,state and local requirements.Disposal of containers: Containers should be reused or disposed of by landfill orincineration as appropriate.14. Transport informationNot classified as a hazardous substance according to transport regulations.15. Regulatory informationLabel Symbol(s): XiIrritantRisk Phrases: R36 Irritating to eyes.R52/53 Harmful to aquatic organisms, may cause long-termadverse effects in the aquatic environment.Safety Phrases: S39 Wear eye/ face protection.16. Other informationExplanations to R-phrases in section 2 R41 Risk of serious damage to eyes.R51/53 Toxic to aquatic organisms, may cause long-term adverse effects in the aquatic environment.See also product label for product applications.Important changes have been made in section: 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12 and 15.DISCLAIM OF RESPONSIBILITYAlfa Laval provides the information contained herein in good faith but makes no representation as to its comprehensiveness or accuracy. This document is only a guide to the potential hazards of the product. All individuals working with or around the product should be properly trained. Persons coming into contact with the product must be capable of exercising their own independent judgment concerning the conditions or methods of handling, storage and usage of the product. Alfa Laval will not be responsible for claims, losses, or damages of any kind resulting from the information provided in this Safety Data Sheet or the use, handling, storage or disposal of the product. Alfa Laval makes no representations or warranties, either express or implied, including without limitation any warranties of merchantability or fitness for a particular purpose with respect to the information set out herein or the product to which the information refers.。
女性裸露是争取权益还是迎合直男

◎ 编辑|程建兰|文化|女性裸露自第二波女性主义兴起,身体开始成为焦点后,女性的“裸体呈现”,在观念上发生了怎样的变迁?当女性用裸露来争取权益,这些“坏女孩儿”该如何应对“裸体羞耻者”发出的“浅薄女性主义”质疑?是争取权益还是迎合直男1975年,英国女性主义电影理论家劳拉·穆尔维(Laura Mulvey)发表杂文《视觉快感与叙事电影》(Visual Pleasure and Narrative Cinema),这篇文章使用精神分析的方法,提出经典好莱坞电影的“窥淫癖”(scopophilia),即在电影中,女性角色是一种“奇观”,接受摄像机后面的人、电影中的男性角色和观众的共同凝视;而这种凝视,是异性恋的、男性化的目光。
自此,“男性凝视”(Male Gaze)作为一个完整的概念,被女性主义媒介分析沿用至今。
在好莱坞电影典型的叙事方式中,“男性凝视”投射到了风格化的女性身体上,女性的身体被编码为强烈的视觉与色情符号,女性的在场只为满足“男性凝视”,男性通过这种“窥淫癖”满足性欲,获出现女性裸露镜头,就是“迎合直男”吗?近期走红的网飞(Netflix)系列动画短片《爱,死亡和机器人》 (网友昵称“爱死机”),正在因这个问题而引发争论。
许多人认为“女性主义”是“爱死机”的亮点,但这也成为它引发争议的地方。
片中有多处女性角色裸露身体的场景,有网友认为这是“消费女性身体”、“迎合直男”;国外也有影评人指出“爱死机”带有性别歧视的色彩。
反对派则认为,将女性身体裸露等同于羞耻,是把所有女性看为潜在的性对象,这才是对于女性的真正歧视。
这种对于身体裸露与女性主义的争论并不新鲜。
比如2017年,著名影星艾玛·沃森(Emma Watson)的性感写真就引发了不小的争议,批评者认为拍摄裸露乳房的照片与她“女性主义者”的身份不符;也有许多人为沃森辩护,称这些批评的声音显示了平权之路道阻且长。
自第二波女性主义兴起,身体开始成为焦点后,各种观点在此交织碰撞;半个多世纪过去了,关于女性身体的争议未见平息之势,女性的身体,仍然是战场。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Dir1NB
Dir2NB
Dir4NB
Full-Map
| 0.00
| 0.40
| 0.80
| | 1.20 1.60 Execution Time (Mcycles)
Figure 1: Weather, 64 Processors, Perfect optimization. shows several coherence schemes on the vertical axis, and the horizontal axis shows the total execution time (in millions of cycles) required to complete a xed portion of the application. These measurements are from ASIM, the Alewife system simulator. Both the two-pointer limited directory (Dir2NB ) and the four-pointer limited directory (Dir4NB ) perform about as well as the full-map directory. How is it possible for these limited directory protocols to be successful? If the multiprocessor exhibits processor locality in the sense that in any given interval of time only a small subset of all the processors access a given memory word, then a limited directory is sucient to capture this small worker-set of processors. The results in Figure 1 show that the two-pointer and the four-pointer directories capture the worker-sets in Weather. The performance of the one-pointer directory (Dir1NB ) su ers slightly, because it does not capture the worker-set of all of Weather's variables. But, what happens if a multiprocessor's software is not properly optimized for the limited directory protocol? Figure 2 gives the execution times for the same application as above, except that one variable in the Weather application has not been properly optimized. The Weather application initializes this variable at the beginning of the program, allows all processors to read the variable, but never writes to the variable after initialization. In fact, the cache coherence protocol implemented in ASIM provides a special data fetch mechanism to allow the system's software to optimize for this type of \write-once" data. The optimization, which bypasses the normal coherence scheme, was used by the software system to achieve the performance results presented in Figure 1, but was not used for the results in Figure 2. The dramatic di erence between the performance of the protocols shown in Figures 1 and 2 is entirely due to neglecting the optimization of just one word of shared memory! That is, when the worker-set of one location in memory is much larger than the size of a limited directory, the whole system may su er from the hot-spot access to this location. So, limited directory protocols are extremely sensitive to the size of an application's worker-set. If a multiprocessor's software is not perfectly optimized, then limited directory thrashing may negate the bene ts of caching shared data. The LimitLESS protocol avoids the sensitivity displayed by limited directories by taking advantage of the fact that each processing node in Alewife contains both a processor and a shared-memory module. (See Figure 3.) While the shared-memory module can implement a limited directory in its cache controller, the local processor can emulate a full-map directory 2
The LimitLESS Cache Coherence Protocol
David Chaiken (chaiken@) Laboratory for Computer Science Room NE43-633
ALEWIFE SYSTEMS MEMO #11
|
August 10,calable cache coherence protocols led to the study of two cache coherence protocols that use directories to store locations of cached data: a full-map directory protocol and a limited directory protocol. Full-map directories [1] store enough state associated with each block in global memory so that every cache in the system can simultaneously store a copy of any block of data. That is, each directory entry contains N pointers, where N is the number of processors in the system. Limited directories [2] di er from full-map directories in that they have a xed number of pointers per entry, regardless of the number of processors in the system. See [3] for a detailed tutorial on the di erences between these two protocols, in terms of both implementation and scalability. For the purposes of understanding the LimitLESS protocol, it is sucient to understand two important properties of these protocols: First, while the full-map protocol provides a useful upper bound for the performance of directory-based cache coherence, it is not scalable with respect to memory overhead. Second, the limited directory protocol is scalable, and it can provide performance similar to the full-map protocol when multiprocessor software is optimized for the protocol. The LimitLESS protocol uses a combination of hardware and software techniques to realize the performance of the full-map directory protocol and the scalability of the limited directory protocol, without the limited directory's sensitivity to software optimization. This new coherence scheme takes advantage of the fact that, in the Alewife architecture, shared-memory modules are distributed to the nodes that contain the processors. The LimitLESS scheme implements a small set of pointers in the memory modules (as does the limited directory). But when necessary, the scheme uses the Alewife processors to emulate a full-map directory by storing pointers that over ow the hardware directory in local blocks of shared memory. Figure 1 presents results for a Weather Forecasting program that illustrate the fact that | assuming the software optimizes for synchronization, read-only, and rarely written data types | a limited directory protocol can perform as well as a full-map directory protocol. The graph
