android安全-Hotmobile 2012 Demo L4Android Security Framework
《自主代客泊车系统总体技术要求》(征求意见稿)

6.1 停车场场地规范 ................................................................ 19 6.1.1 场地分级规范 .............................................................. 19 6.1.2 车场匹配 .................................................................. 21 6.1.3 场地标识规范 .............................................................. 22 6.1.3.1 位置标识 ................................................................ 22 6.1.3.2 跨层标识 ................................................................ 23 6.1.3.3 十字路口处标识 .......................................................... 24 6.1.3.4 丁字路口处标识 .......................................................... 24 6.1.3.5 闸口/收费口标识.......................................................... 25 6.1.3.6 上下车点标识 ............................................................ 25
IEC60601-1第三版(中文版)

国际标准 IEC60601-1 医用电气设备—— 第一部分:安全通用要求和基本准则
MEDICAL ELECTRICAL EQUIPMENT – Part 1: General requirements for basic safety and essential pe.......................................................................................................................8 1.1 范围 ........................................................................................................................................8 1.2 目标 ........................................................................................................................................8 1.3 * 并列标准 ................................................................................................................................8 1.4 * 专用标准 ................................................................................................................................8
华为SecoManager安全控制器产品介绍说明书

Huawei SecoManager Security ControllerIn the face of differentiated tenant services and frequent service changes, how to implementautomatic analysis, visualization, and management of security services, security policy optimization,and compliance analysis are issues that require immediate attention. Conventional O&M relies onmanual management and configuration of security services and is therefore inefficient. Securitypolicy compliance check requires dedicated personnel for analysis. Therefore, the approval is usuallynot timely enough, and risky policies may be omitted. The impact of security policy delivery onservices is unpredictable. That is, the impact of policies on user services cannot be evaluated beforepolicy deployment. In addition, as the number of security policies continuously increases, it becomesdifficult for security O&M personnel to focus on key risky policies. The industry is in urgent needof intelligent and automated security policy management across the entire lifecycle of securitypolicies to help users quickly and efficiently complete policy changes and ensure policy deliverysecurity and accuracy, thereby effectively improving O&M efficiency and reducing O&M costs.The SecoManager Security Controller is a unified security controller provided by Huawei for differentscenarios such as DCs, campus networks, Branch. It provides security service orchestration andunified policy management, supports service-based and visualized security functions, and forms aproactive network-wide security protection system together with network devices, security devices,and Big Data intelligent analysis system for comprehensive threat detection, analysis, and response.Product AppearancesProduct HighlightsMulti-dimensional and automatic policy orchestration, security service deployment within minutes• Application mutual access mapping and application-based policy management: Policymanagement transitions from the IP address-based perspective to the application mutual access relationship-based perspective. Mutual-access relationships of applications on the network are abstracted with applications at the core to visualize your application services so that you can gain full visibility into the services, effectively reducing the number of security policies. The model-based application policy model aims to reduce your configuration workload and simplify network-wide policy management.• Policy management based on service partitions: Policy management transitions from thesecurity zone-based perspective to the service partition-based perspective. Conventional network zones are divided into security zones, such as the Trust, Untrust, DMZ, and Local zones. In a scenario with a large number of security devices and a large network scale, factors of security zone, device, policy, service rollout, and service change are intertwined, making it difficult to visualize services and to effectively guide the design of security policies. However, if security policies are managed, controlled, and maintained from the perspective of service partitions, users need to pay attention only to service partitions and security services but not the mapping among security zones, devices, and services, which effectively reduces the complexity of security policy design.Service partition-based FW1untrusttrustDMZ XXX FW2untrust trustDMZ XXX FW3untrust trust DMZ XXX InternetGuest partition R&D partition Data storage partitionExternal service partition Internal service partition• Management scope of devices and policies defined by protected network segments to facilitate policy orchestration: A protected network segment is a basic model of security service orchestration and can be considered as a range of user network segments protected by a firewall.It can be configured manually or through network topology learning. The SecoManager Security Controller detects the mapping between a user service IP address and a firewall. During automatic policy orchestration, the SecoManager Security Controller automatically finds the firewall that carries a policy based on the source and destination addresses of the policy.• Automatic security service deployment: Diversified security services bring security assurance for data center operations. Technologies such as protected network segment, automatic policy orchestration, and automatic traffic diversion based on service function chains (SFCs) enable differentiated tenant security policies. Policies can be automatically tiered, split, and combined so that you can gain visibility into policies.Intelligent policy O&M to reduce O&M costs by 80%• Policy compliance check: Security policy compliance check needs to be confirmed by the security approval owner. The average number of policies to be approved per day ranges from several to hundreds. Because the tool does not support all rules, the policies need to be manually analyzed one by one, resulting in a heavy approval workload and requiring a dedicated owner to spend hours in doing so. The SecoManager Security Controller supports defining whitelists, risk rules, and hybrid rules for compliance check. After a policy is submitted to the SecoManager Security Controller, the SecoManager Security Controller checks the policy based on the defined check rules and reports the check result and security level to the security approval owner in a timely manner.In this way, low-risk policies can be automatically approved, and the security approval owner needs to pay attention only to non-compliant policy items, improving the approval efficiency and avoiding the issues that the approval is not timely and that a risky policy is omitted.• Policy simulation: Based on the learning result of service mutual access relationships, the policies to be deployed are compared, and their deployment is simulated to assess the impact of the deployment, effectively reducing the risks brought by policy deployment to services.• Redundant policy deletion: After a policy is deployed, redundancy analysis and hit analysis are performed for policies on the entire network, and the policy tuning algorithm is used, deleting redundant policies and helping you focus on policies closely relevant to services.Network collaboration and security association for closed-loop threat handling within minutes • Collaboration with network for threat handling: In a conventional data center, application deployment often takes a long time. The application service team relies on the network team to deploy the network; the network team needs to understand the requirements of the application service team to deploy a network that is suitable for the application service team. The SecoManager Security Controller learns mappings between service policies and security policies based on the network topology, and collaborates with the data center SDN management and control system (IMaster NCE-Fabric) or campus SDN management and control system to divert tenant traffic to corresponding security devices based on SFCs on demand. The SecoManager Security Controller automatically synchronizes information about the tenants, VPCs, network topology (including logical routers, logical switches, logical firewalls, and subnets), EPGs, and SFCs from the SDN management and control system and combines the learned application service mutual access relationships to automatically orchestrate and deliver security policies, implementing security-network synergy.• Collaboration with security: Advanced persistent threats (APTs) threaten national infrastructure of the finance, energy, government, and other sectors. Attackers exploit 0-day vulnerabilities, use advanced evasion techniques, combine multiple attack means such as worm and ransomware, and may remain latent for a long period of time before they actually initiate attacks. The Big Data security product HiSec Insight can effectively identify unknown threats based on network behavior analysis and correlation analysis technologies. The threat handling method, namely isolation or blocking, is determined based on the threat severity. For north-south threats, the SecoManager Security Controller delivers quintuple blocking policies to security devices. For east-west threats, isolation requests are delivered to the network SDN management and control system to control switches or routers to isolate threatened hosts.Product Deployment• Independent deployment: The SecoManager Security Controller is deployed on a server or VM as independent software.• Integrated deployment: The SecoManager Security Controller and SDN management and control system are deployed on the same physical server and same VM.Database• Collaboration with the SDN management and control system to detect network topology changes and implement tenant-based automatic security service deployment.• North-south threat blocking, east-west threat isolation, and refined SDN network security control through SFC-based traffic diversion.• Interworking with the cloud platform to automatically convert service policies to security policies. Product SpecificationsOrdering InformationNote: This product ordering list is for reference only. For product subscription, please consult Huawei representatives. GENERAL DISCLAIMERThe information in this document may contain predictive statement including, without limitation, statements regarding the future financial and operating results, future product portfolios, new technologies, etc. There are a number of factors that could cause actual results and developments to differ materially from those expressed or implied in the predictive statements. Therefore, such information is provided for reference purpose only and constitutes neither an offer nor an acceptance. Huawei may change the information at any time without notice.Copyright © 2020 HUAWEI TECHNOLOGIES CO., LTD. All Rights Reserved.。
腾讯移动安全实验室2012年手机安全报告

文章来源: /dirs/1497.htm腾讯移动安全实验室2012年手机安全报告第一章手机安全报告摘要2012年,随着Android智能手机的大热与普及,手机病毒也发展迅猛。
在Android平台,2012年的手机病毒增长呈现直线上升的趋势,安全形势堪忧。
2012年,腾讯移动安全实验室共检测截获手机病毒总量达到177407个,超过90%的病毒包集中在Android平台,Android已经成为手机病毒肆虐的主战场。
2012年,在被病毒感染最多的前十款软件中,神庙逃亡、水果忍者、植物大战僵尸OL和捕鱼达人这四款最热门游戏无一幸免。
2012年,腾讯手机管家共为手机用户查出了5699万次手机病毒。
广东省2012年连续12个月手机中毒用户数均位居第一位,全年手机中毒用户比例达到1 4.7%,广东、江苏、浙江、北京市、辽宁四省一市位居前五,中毒手机用户比例分别为:14.7%、7.53%、6.5%、6.25%、5.23%。
感染比例共占据了全国的40.21%的比例。
2012年,腾讯手机管家用户主动举报垃圾短信总量达到3.04亿条,其中,广告类垃圾短信占据79.1%的比例,位居所有垃圾短信类型之首。
2012年,各种恶意广告进一步泛滥,截至2012年12月,腾讯手机管家已检测出含恶意广告的软件包共467026个,占已发现所有软件包比例13.31%。
自2012年9月份腾讯手机管家上线广告拦截功能以来,截至12月底,在客户端已经为用户一共拦截了240386 56次恶意广告。
2012年二维码大热的背后,安全风险暗藏。
据腾讯移动安全实验室监测,腾讯手机管家从2012年7月为灵动快拍提供二维码安全检测以来,7月~12月共为灵动快拍检测网址达9 56万条以上,拦截恶意网址达20.6万条。
报告正文第二章2012年全年手机安全现状2012年,随着国内Android系统的设备的持续大幅增长,Android系统市场占有率占据主流地位,而Android系统的手机病毒包也呈现爆发式增长态势,手机病毒的技术日渐成熟,在2012年,手机病毒包全年呈现前所未有的高速增长。
Android应用安全专利技术综述

Android应用安全专利技术综述摘要Android操作系统已成为全球第一大操作系统,其安全性关乎海量用户的信息和财产安全。
本文对Android应用安全技术领域专利技术进行分析和整理,以Android应用安全检测技术和安全加固技术为主线,重点关注了本领域的全球专利申请趋势、技术发展走向以及主要技术方案,有助于全面了解Android应用安全技术领域的发展态势。
关键词Android系统;安全技术;专利1 Android系统简介及其安全性分析Android(中文俗称“安卓”),是一个基于Linux内核的开源移动操作系统,由Google成立的开放手机联盟(Open Handset Alliance)持续领导与开发,主要设计用于智能手机等移动终端。
2017年3月,Android全球网络流量和设备超越了Windows,成为全球第一大操作系统。
Android操作系统架构自底向上分为4个层次:Linux内核层、系统库层、应用框架层、应用层[1]。
其中应用层为用户提供各式各样的应用程序,是Android 系统面临的安全风险和威胁的“重灾区”。
Android应用层安全研究和相关技术聚焦于Android应用本身的安全,包括了2个主要技术分支:一是针对应用是否存在恶意行为、漏洞等进行安全检测,规避安全风险,保证系统及其他应用不受恶意行为、漏洞的影响;二是针对应用进行安全加固,保护应用安全[2-5]。
2 Android应用安全技术专利申请情况2.1 国内外相关专利申请趋势分析Android应用安全技术的专利申请趋势总体上可以分为二个阶段,其中:2008-2010年为萌芽期:在该阶段,国外由于先发技术优势在申请量上领先于国内,国内起步时间相对略有滞后。
2011-2016年为增长期:自2011年开始Android 应用安全领域专利申请量开始明显地快速增长并在2016年达到峰值。
2.2 全球专利申请来源国/地区分布截至2018年5月,Android应用安全技术全球专利申请的来源国/地区主要为中国、美国、韩国。
AndroidO限制系统全屏进一步遏制手机勒索

Android O限制系统全屏进一步遏制手机勒索引言近期谷歌发布了最新手机操作系统Android O的开发者预览版,一如往常,Android O又带来了多项新功能与优化升级,其中一项有关系统窗口管理的优化给Android手机勒索软件带来了严重冲击。
简述Android系统与勒索软件对抗史手机勒索软件是一种特殊的恶意软件,其通常将自身伪装为看似无害的软件或是利用社会工程学诱导受害者下载安装,随后通过恶意利用操作系统正常功能或者缺陷强制锁住用户桌面使得用户无法正常使用设备,并几乎都会要求受害者缴纳赎金以解锁设备。
手机勒索的解锁费用通常为20、30或50元不等,通常情况下当用户设备感染勒索软件后,出于设备被锁定的焦急心理与不高的赎金金额,用户一般都会通过勒索软件锁屏界面提供的联系方式联系制马人以尝试解锁设备,因此这种“薄利多销”且制作成本低廉的点对点式直接性敲诈软件颇受制马人的青睐。
此外,这类软件通常具有很高的可变性,制马人只需简单调整软件代码或锁屏样式便可生成新的勒索软件。
360烽火实验室一直密切关注国内外手机勒索软件动向,先后发布了多篇对手机勒索软件的研究成果。
纵观Android系统尤其是高版本系统史,每一版都在遏制勒索软件方面做出了积极的应对:♦Android L(Android 5.0-5.1)在早期Android版本中,通过getRunningTasks 方法可获取当前运行栈顶程序,但自Android 5.0起该方法被弃用,同时getRunningAppProcesses与get AppTasks方法的使用也受到了限制,由此抑制了劫持Activity类勒索软件的出现。
♦Android M(Android 6.0)大部分手机勒索软件的惯用伎俩是通过SYSTEM_ALERT_WINDOW权限来打开特定系统类型窗口并将其显示在所有其他应用程序和窗口之上,以此达到锁定用户设备的目的。
Android M的出现使得勒索软件制马人在实施手机勒索时遇到了一大瓶颈——动态权限申请,由于自Android M起,SYSTE M_ALERT_WINDOW开始被列为一种危险程度较高的权限而被特殊处理——即需要用户动态授权。
Android平台网络连接架构分析-connectivityservice框架流程word版本
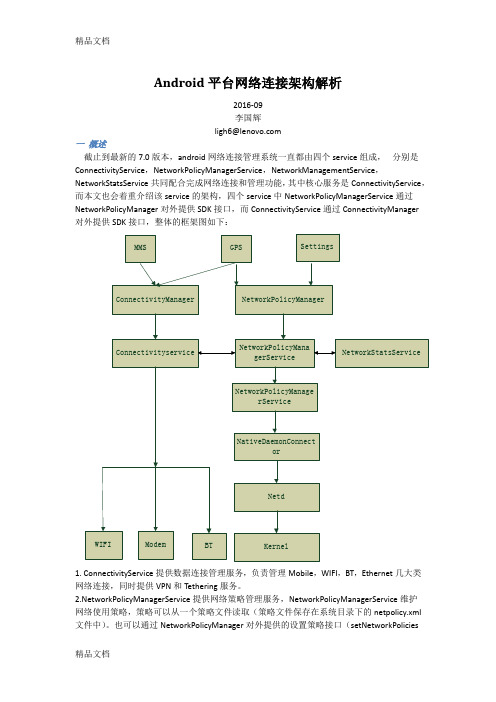
Android平台网络连接架构解析2016-09李国辉ligh6@一概述截止到最新的7.0版本,android网络连接管理系统一直都由四个service组成,分别是ConnectivityService,NetworkPolicyManagerService,NetworkManagementService,NetworkStatsService共同配合完成网络连接和管理功能,其中核心服务是ConnectivityService,而本文也会着重介绍该service的架构,四个service中NetworkPolicyManagerService通过NetworkPolicyManager对外提供SDK接口,而ConnectivityService通过ConnectivityManager对外提供SDK接口,整体的框架图如下:1. ConnectivityService提供数据连接管理服务,负责管理Mobile,WIFI,BT,Ethernet几大类网络连接,同时提供VPN和Tethering服务。
workPolicyManagerService提供网络策略管理服务,NetworkPolicyManagerService维护网络使用策略,策略可以从一个策略文件读取(策略文件保存在系统目录下的netpolicy.xml 文件中)。
也可以通过NetworkPolicyManager对外提供的设置策略接口(setNetworkPolicies及setUidPolicy)进行设置,NetworkPolicyManagerService能够根据这些设置或从策略文件中读取的策略控制网络连接。
另外NetworkPolicyManagerService还具有动态调节网络连接限额及动态设置网络连接的功能,动态调节网络连接限额机制是通过INetworkStatsService访问NetworkStatsService服务获得上面设置或读取的策略匹配的网络连接类型的传输统计信息(NetworkPolicyManagerService采用NetworkTemplate进行网络连接类型的匹配),并根据这些信息生成有效的规则,并提交给ConnectivityService服务,并调用NetworkManagementService 的setInterfaceQuota函数对网络连接的带宽限额。
SOTI 移动安全解决方案

目前,摩托罗拉的Windows Mobile,CE和Android设备正在 陆续预装MobiControl Stage
谢谢!
MobiControl
中兴
华为
MobiControl
通过了超过70家OEM厂商的支持
基Байду номын сангаас标准的跨平台框架
构建一个通用的模块化框架
全生命周期的移动管理
为您提供完整的安全策略
安全保障移动设备管理生命周期的每一步
• 安全的设备注册
•
• • • • • • •
应用管理
内容管理 系统加密,防病毒 设备功能管理 屏幕应用锁定 证书管理 失联策略 应用沙箱,Samsung Knox, Google AFW, Graphite Software
移动安全管理解决方案
为您提供端到端的移动安全管理解决方案
全生命周期的移动设备管理
• 业界独有的安卓加技术,大量专利内核级API, 对设备进行内核级的管控。 • 与硬件厂家深度合作,真正多种厂家设备兼容,满足安全管理的需求。 • 一个平台可以管理几乎所有的智能移动设备,统一的功能模块化设计。 • 高可扩展性,与第三方应用的结合,支持自定义数据,自定义属性,功能脚本等。 • 实用的功能设计,切实解决用户碰到的问题。
MobiControl 移动设备安全及管理功能
设备监控和报告
能够随时查看设备当前信
息,通过报表查看设备使 用状况,在线情况分组状
况等。便于企业对设备进
行资产管理。
真正的远程控制和实时 远程查看,实时支持
Mobicontrol的远程控制是Android和Windows 设备最快的和最可靠的交互式远程控制,能够提 供最优秀的远程控制和故障排除,还可以为iOS设 备提供远程查看和先进的设备管理。 这些一流的远程桌面功能使管理员毫不费力的支
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Hotmobile2012Demo:L4Android Security Framework
on the Samsung Galaxy S2
Matthias Lange a Steffen Liebergeld a
Adam Lackorzynski b Alexander Warg b
Janis Danisevskis a Jan C.Nordholz a
a Security in Telecommunications,TU Berlin,Germany
b Chair of Operating Systems,TU Dresden,Germany
There is a recent trend to use privately owned mobile devices in corporate environments. This poses serious threats on the security of corporate data.In this demo we show how we applied an efficient sandboxing mechanism to the Android software stack.This allows us to run multiple instances of Android securely isolated side-by-side on one device.We implemented a prototype on the Samsung Galaxy S2.
I.Introduction
Virtualization,a technology well known from server and desktop computers,gained interest in the mobile handset market to employ multiple personalities on one device.As described by[1,2]virtualization also allows for high-assurance isolation between secure and insecure components which is required by emerg-ing applications such as micro payment via NFC or mobile banking.
As smartphones are heavily used in today’s busi-nesses they are usually provisioned by the corporate’s IT department to prevent unsolicited data revelation. This often makes these devices cumbersome to use and consequently many carry an additional private phone with them.Running both tasks on one device is highly desirable.
In this demo we show how we leveraged the fea-tures of the L4Android[3]security framework on the Samsung Galaxy S2to implement two virtual ma-chines running on the device.
II.System Architecture
Our system architecture is depicted in Figure1.The system is based on a modern third-generation micro-kernel.The system does not require hardware-assisted virtualization capabilities.Instead the Android ker-nel has been modified to run as an userspace appli-cation on the microkernel.We run two instances of L4Android where one is for private and the other for business purposes.Access to the graphics hardware and input devices is multiplexed by a secure GUI. The board support package provides a generic in-terface to device drivers.Android implements this generic interface in its hardware abstraction layer.
Figure1:Two instances of Android running in paral-lel on one device.
While still providing the same interface the board sup-port package can be changed without the need to adapt Android.
III.Demo Setup
We implemented our demo on the Samsung Galaxy S2 smartphone.It features a dual core ARM Cortex-A9 CPU with1GB of RAM.We ported the microkernel to the Exynos4SoC of the Galaxy S2and implemented the board support package(BSP).The BSP contains various drivers for devices such as display,input de-vices,real time clock and accelerometer.Our proto-type is capable of connecting to the mobile network
for sending and receiving SMS as well as data con-nectivity.
We run two instances of Android concurrently.The Android version is the latest Gingerbread release from the Android open source project.The L4Android ker-nel version is Linux3.1.
References
[1]G UDETH,K.,P IRRETTI,M.,H OEPER,K.,AND
B USKEY,R.Delivering secure applications on
commercial mobile devices:the case for bare metal hypervisors.In Proceedings of the1st ACM workshop on Security and privacy in smartphones and mobile devices(2011),SPSM’11,ACM. [2]L ANGE,M.,L IEBERGELD,S.,L ACKORZYN-
SKI, A.,W ARG, A.,AND P ETER,M.
L4Android:A Generic Operating System Frame-work for Secure Smartphones.In Proceedings of the1st ACM workshop on Security and privacy in smartphones and mobile devices(2011),SPSM ’11,ACM.
[3]L ANGE,M.,L IEBERGELD,S.L4Android:An-
droid on top of L4.http://www.l4android.o rg,January2012.。
