Intransitive Noninterference in Dependence Graphs
GSMR接口需求规范

ERTMS/ETCS – Class 1GSM-R InterfacesClass 1 RequirementsREF : SUBSET-093ISSUE : 2.3.0DATE : 10-Oct-2005Company Technical Approval Management approval ALCATELALSTOMANSALDO SIGNALBOMBARDIERINVENSYS RAILSIEMENS1. M ODIFICATION H ISTORYIssue NumberDateSection Number Modification / Description Author0.1.0 (8-Aug-02) Creation based on subset052LK0.1.1 (8-Aug-02) All Minor editorial changes LK0.1.1ec All englishcheck JH0.2.0 (9-Sep-02) 3., 4.2, 4.1, 6.3, 7.2,8.2 Updated after email discussionLK0.3.0 (24-Oct-02) All Updated after FlorencemeetingLK+TS0.4.0 (14-Nov-02) All Updated after LondonmeetingLK0.5.0 (5-Dec-02) 4.2, 5.6.1, 6.2, 7.1,7.3, 9.2 Updated after Berlin meetingLK0.6.0 (12-Dec-02) 3., 6.3., 10.4.3 Email comments included TS+LK2.0.0 (12-Dec-02) Erroneous versionnumber 2.2.0correctedFinal issue LK2.1.0 (28-March-03)3.1.1.1, 6.3.1.3,7.1.1.1, 8.1.1.1 Update acc. to super group commentsLK2.2.0 (28-March-03) - Final version LK2.2.2.31-03-03 Versionnumberchangedfor release to the usersGroupWLH2.2.3 (12-June-03) All Update after Brussels mtg.and GSM-R Op. grp.commentsLK2.2.4 (26-June-03) editorial Draft release to UsersGroupJH2.2.5 - FormalreleaseJH 2.2.5.1 4.2, 6.2, 6.3, new 6.4 Update after Paris mtg. andGSM-R Op. grp. commentsLK2.2.5.2 Various update after further GSM-ROp grp reviewJH2.2.5.3 cleanversion JH 2.2.5.4 6.4 Updated after further GSM-R Op grp requestRB2.2.6 CleanversionRB2.2.6 revA (31-Jan-05) 4.2, 6.3, 6.4, Annex A Proposal for QoS parametervaluesLK2.2.6 revB (14-Feb-05) 6.3, 6.4, Annex A Updated after QoSmeeting#6 BrusselsLK2.2.6 revC (24-Feb-05) 6.3, 6.4, Annex A,Annex B added Updated during BerlinmeetingLK2.2.6 revD (25-Feb-05) 6.2, 6.3.5, 10.3, 10.5.2 Email comments inserted LK2.2.6 revE (6-Apr-05)3.1., 3.2,4.1,5.1,6.3,10.1, 10.3, 10.5, 10.7 Updated after QoSmeeting#7 BrusselsLK2.2.6 revF (25-Apr-05)3.1,4.1,5.1,6.3, 6.4,10.1, 10.3, 10.5, 10.6,10.7Edinburgh meeting TS+LK2.2.6revG (20-May-05)3.1, 5.1, 6.3, 6.4, 8.2 Changes according toBrussels meetingLK2.2.6revH (1-Sep-05) 4.1, 5.1, 6.3, 6.4, 7.2,10.3, 10.4, 10.5 Comments from SG andEEIGLK2.2.6revI (8-Sep-05) 5.1, 6.3, 6.4, 10.4 Zürich meeting PL+LK 2.3.0 (10-Oct-05) update for issue JH2. T ABLE OF C ONTENTS1.M ODIFICATION H ISTORY (2)2.T ABLE OF C ONTENTS (4)3.R EFERENCES (6)3.1Normative Documents (6)3.2Informative Documents (7)4.T ERMS AND DEFINITIONS (8)4.1Abbreviations (8)4.2Definitions (9)5.G ENERAL (10)5.1Scope of this document (10)5.2Introduction (10)6.E ND-TO-END SERVICE REQUIREMENTS TO GSM-R NETWORKS (12)6.1Data bearer service requirements (12)6.2Additional services (12)6.3Quality of Service requirements (13)6.3.1General (13)6.3.2Connection establishment delay (14)6.3.3Connection establishment error ratio (14)6.3.4Transfer delay (15)6.3.5Connection loss rate (15)6.3.6Transmission interference (15)6.3.7GSM-R network registration delay (16)6.4Summary of QoS requirements (16)7.R EQUIREMENTS TO FIXED NETWORK INTERFACE (17)7.1Foreword (17)7.2Interface definition (17)7.3Communication signalling procedures (17)8.R EQUIREMENTS TO MOBILE NETWORK INTERFACE (18)8.1Foreword (18)8.2Interface definition (18)9.A NNEX A(I NFORMATIVE) TRANSMISSION INTERFERENCE AND RECOVERY (19)9.1General (19)9.2Transmission interference in relation to HDLC (19)10.A NNEX B(INFORMATIVE)J USTIFICATION OF Q O S PARAMETER VALUES (22)10.1General (22)10.2Connection establishment delay (22)10.3Connection establishment error ratio (22)10.4Transfer delay (23)10.5Connection loss rate (23)10.5.1QoS targets (23)10.5.2Conclusions (24)10.6Transmission interference (24)10.7Network registration delay (26)3. R EFERENCESDocuments3.1 Normative3.1.1.1 This document list incorporates by dated or undated references, provisions from otherpublications. These normative references are cited at the appropriate place in the textand the publications are listed hereafter. For dated references, subsequentamendments to or revisions of any of these publications apply to this document onlywhen incorporated in it by amendment or revision. For undated references the latestedition of the publication referred to apply.Reference DateTitleU-SRS 02.02 ERTMS/ETCS Class 1; Subset 026; Unisig SRS, version 2.2.2 Subset 037 07.03 ERTMS/ETCS Class 1; Subset 037; EuroRadio FIS; Class1requirements, version 2.2.5EIRENE FRS 10.03 UIC Project EIRENE; Functional Requirements Specification.Version 6.0, CLA111D003EIRENE SRS 10.03 UIC Project EIRENE; System Requirements Specification.Version 14.0, CLA111D004ETS 300011 1992 ISDN; Primary rate user-network interface; Layer 1 specificationand test principlesETS 300102-1 1990 ISDN; User-network interface layer 3; Specification for basiccall controlETS 300125 1991 ISDN; User-network interface data link layer specificationsGSM04.21 12.00 Rate Adaptation on the MS-BSS Interface, v.8.3.0GSM 07.0711.98 ETSI TS 100916; Digital cellular telecommunications system(Phase 2+); AT command set for GSM Mobile Equipment (ME),GSM TS 07.07 version 6.5.0 Release 1997ITU-T V.24 02.00 List of definitions for interchange circuits between data terminalequipment (DTE) and data circuit-terminating equipment (DCE)ITU-T V.25ter 07/97 Serial asynchronous dialling and controlITU-T V.110 02.00 Support of data terminal equipments (DTEs) with V-series typeinterfaces by an integrated services digital network (ISDN) EuroRadio FFFIS 09.03 UIC ERTMS/GSM-R Unisig; Euroradio Interface Group; RadioTransmission FFFIS for Euroradio; A11T6001; version 12O-2475 09.03 UIC ERTMS/GSM-R Operators Group; ERTMS/GSM-R Qualityof Service Test Specification; O-2475; version 1.0Documents3.2 InformativeTitleReference DateEEIG 04E117 12.04 ETCS/GSM-R Quality of Service - Operational Analysis, v0.q(draft)ERQoS 08.04 GSM-R QoS Impact on EuroRadio and ETCS application,Unisig_ALS_ERQoS, v.0104. T ERMS AND DEFINITIONS4.1 AbbreviationsAT ATtention command setATD AT command DialB channel User channel of ISDNB m channel User channel of GSM PLMN on the air interfaceBRI Basic Rate InterfaceByte 1 start bit + 8 data bits + 1 stop bitDCE Data Circuit EquipmentDCD Data Carrier DetectD channel Control channel of ISDND m channel Control channel of GSM PLMN on the air interfaceDTE Data Terminal EquipmenteMLPP enhanced Multi-Level Precedence and Pre-emptionFIS Functional Interface SpecificationGPRS General Packet Radio Service (a phase 2+ GSM service) GSM-R Global System for Mobile communication/RailwayHDLC High level Data Link ControlISDN Integrated Services Digital NetworkMLPP Multi-Level Precedence and Pre-emption (ISDN service) MOC Mobile Originated CallMS Mobile Station (a GSM entity)Termination/Terminated MT MobileMTC Mobile Terminated CallMTBD Mean Time Between DisturbanceUnitOBU On-BoardPLMN Public Land Mobile NetworkPRI Primary Rate InterfaceQoS Quality of ServicesRBC Radio Block CentreT TI Duration of Transmission Interference periodT REC Duration of Recovery periodUDI Unrestricted Digital4.2 Definitions4.2.1.1 Definitions for the purpose of this specification are inserted in the respective sections.5. G ENERAL5.1 Scope of this document5.1.1.1 The scope of this document is to specify the Radio Communication Systemrequirements to the GSM-R network services (including fixed side access) andinterfaces and also the pre-requisites to be fulfilled by GSM-R networks and ETCSinfrastructures. Presently the requirements for high-speed lines are covered,requirements for conventional lines may be included in future versions of thisdocument.5.1.1.2 The data transmission part of the communication protocols is fully described in theEuroRadio FIS [Subset 037].5.1.1.3 The Radio Transmission FFFIS for EuroRadio [EuroRadio FFFIS] specifies thephysical, electrical and functional details related to the interfaces.5.1.1.4 All requirements apply to GSM-R unless indicated otherwise .5.2 Introduction5.2.1.1 The definition of the GSM services and associated physical and communicationsignalling protocols on the air interface are fully standardised in the specificationsproduced by the ETSI GSM Technical Committee for the public GSM implementationas well as for the GSM-R. Additionally, some railway specific services are alsospecified in the EIRENE SRS. However, in both cases, not all are required for ERTMSclass 1 system definition.5.2.1.2 The following ETSI GSM phases 1/2/2+ services are required:a) Transparent data bearer serviceb) Enhanced multi-level precedence and pre-emption (eMLPP).5.2.1.3 Other ETSI GSM phases 1/2/2+ services are not required for Class 1. These are thefollowing :a) GSM supplementary services:• Call forwardingb) General packet radio service (GPRS)5.2.1.4 Other ETSI GSM phases 1/2/2+ services are not required. Examples of these are thefollowing :a) Non-transparent data bearer serviceb) GSM supplementary services:• Line identification•Call waiting and hold• Multiparty•Closed User Group•Advice of charge• Call Barringc) Short message service point to point or cell broadcastd) Voice broadcast servicee) Voice group call service5.2.1.5 The following EIRENE railway specific service [EIRENE SRS] is required:a) Location dependent addressing5.2.1.6 The following EIRENE specific services [EIRENE SRS] are not required :a) Functional addressingb) Enhanced location dependent addressingc) Calling and connected line presentation of functional identitiesd) Emergency callse) Shunting modef) Multiple driver communications6. E ND-TO-END SERVICE REQUIREMENTS TO GSM-RNETWORKS6.1 Data bearer service requirements6.1.1.1 For the transmission of information between OBU and RBC, the EuroRadio protocoluses the bearer services of a GSM-R network. The service provider makes these databearer services available at defined interfaces.6.1.1.2 The data bearer services are described as data access and transfer in the GSMnetwork from Terminal Equipment (TE) on the mobile side (i.e. OBU) to a networkgateway interworking with Public Switched Telephonic Network (PSTN) or IntegratedServices Digital Network (ISDN) on the fixed side (i.e. RBC).6.1.1.3 The following features and attributes of the required bearer service shall be provided:a) Data transfer in circuit switched modeb) Data transfer allowing multiple rate data streams which are rate-adapted[GSM04.21] and [ITU-T V.110]c) Unrestricted Digital Information (UDI) – only supported through ISDN interworking(no analogue modem in the transmission path)d) Radio channel in full ratee) Transfer of data only (no alternate speech/data)f) Transfer in asynchronous transparent modeg) The required data rates are listed in the following table:Bearer service Requirement24. Asynchronous 2.4 kbps T O25. Asynchronous 4.8 kbps T M26. Asynchronous 9.6 kbps T MT: Transparent; M: Mandatory; O: OptionalTable1 GSM-R bearer servicesservices6.2 Additional6.2.1.1 The following supplementary services shall be provided:a) Enhanced multi-level precedence and pre-emption.b) The selection of a particular mobile network shall be possible on-demand.6.2.1.2 The priority value for command control (safety) shall be assigned to according to[EIRENE FRS §10.2] and [EIRENE SRS §10.2].6.2.1.3 The following railway specific service shall be provided by GSM-R networks:a) Location dependent addressing based on the use of short dialling codes inconjunction with cell dependent routing.6.3 Quality of Service requirements6.3.1 General6.3.1.1 As an end-to-end bearer service is used, a restriction of requirements on the servicequality placed on the air interface is not sufficient.6.3.1.2 End-to-end quality of service has to be considered at the service access points.6.3.1.3 The service access points are:•the service access points to the signalling stack for the establishment or release of a physical connection,•the service access points to the data channel.6.3.1.4 The network shall be able to support transparent train-to-trackside and trackside-to-train data communications at speeds up to 500 km/h e.g. in tunnels, cuttings, onelevated structures, at gradients, on bridges and stations.6.3.1.5 The network shall provide a Quality of Service for ETCS data transfer that is at least asgood as listed below1. The parameters are valid for one end-to-end connection for onetrain running under all operational conditions.6.3.1.6 The required QoS parameters shall not depend on network load.6.3.1.7 These performance figures reflect railway operational targets [EEIG 04E117].6.3.1.8 Note: A justification of the performance figures is given by Annex B.6.3.1.9 QoS requirements are specified independently of the method of measurement (refer to[O-2475] for specification of testing).6.3.1.10 Conventional line quality of service requirements may be included in future versions ofthis document. Also the values may not be applied at all locations and times (e.g.discontinuous radio coverage at some locations).6.3.1.11 Given the performance constraints of GSM-R, pre-conditions may be necessary tomeet the railway operational targets of [EEIG 04E117]. If different operational QoStargets are required, then other pre-conditions on ETCS application may be necessary.1 Early experience suggests that GSM-R performance can be better than these parameters suggest, after network optimisation and tuning.Such a case is not covered by this specification and this aspect of ETCS SystemPerformance becomes the responsibility of whoever specifies different operationaltargets.6.3.2 Connection establishment delay6.3.2.1 Connection establishment delay is defined as:Value of elapsed time between the connection establishment request and theindication of successful connection establishment.6.3.2.2 In case of mobile originated calls, the delay is defined between the request bycommand ATD and indication by the later of the two events response CONNECT ortransition of DCD to ON.6.3.2.3 The connection establishment delay of mobile originated calls shall be <8.5s (95%),≤10s (100%).6.3.2.4 Delays>10s shall be evaluated as connection establishment errors.6.3.2.5 The required connection establishment delay shall not depend on user data rate of theasynchronous bearer service.6.3.2.6 The required connection establishment delay is not valid for location dependentaddressing.6.3.3 Connection establishment error ratio6.3.3.1 The Connection establishment error ratio is defined as:Ratio of the number of unsuccessful connection establishment attempts to the totalnumber of connection establishment attempts.6.3.3.2 “Unsuccessful connection establishment attempt” covers all possible types ofconnection establishment errors caused by end-to-end bearer service.6.3.3.3 Connection establishment delays >10s shall be evaluated as connection establishmenterrors.6.3.3.4 The GSM-R networks should be designed in such a way, that at least two consecutiveconnection establishment attempts will be possible (pre-condition on GSM-Rnetworks), e.g. regarding GSM-R radio coverage related to maximal possible trainspeed.6.3.3.5 If the operational QoS targets of [EEIG 04E117] are wanted, then the ETCSinfrastructure should be designed in such a way, that at least two consecutiveconnection establishment attempts will be possible (Recommended pre-condition forETCS infrastructure).6.3.3.6 The connection establishment error ratio of mobile originated calls shall be <10-2 foreach attempt .6.3.3.7 Note: entry into Level 2 is of particular importance; commonly, a time of 40s may berequired in the case the GSM-R mobile station is already registered with the GSM-Rnetwork (see [ERQoS]).6.3.4 Transfer delay6.3.4.1 The end-to-end transfer delay of a user data block is defined as:Value of elapsed time between the request for transfer of a user data block and theindication of successfully transferred end-to-end user data block6.3.4.2 The delay is defined between the delivery of the first bit of the user data block at theservice access point of transmitting side and the receiving of the last bit of the sameuser data block at the service access point of the receiving side.6.3.4.3 The end-to-end transfer delay of a user data block of 30 bytes shall be ≤0.5s (99%).6.3.5 Connection loss rate6.3.5.1 The Connection loss rate is defined as:Number of connections released unintentionally per accumulated connection time.6.3.5.2 The requirements for connection loss rate varies depending on ETCS system variablessuch as T_NVCONTACT and the possible train reactions after connection loss (seesection 10.5).6.3.5.3 If the operational QoS-targets of [EEIG 04E117] are wanted, then the ETCSinfrastructure should be designed in such a way, that at least the following conditionsare fulfilled (Recommended pre-condition for ETCS infrastructure):• T_NVCONTACT ≥ 41s and• M_NVCONTACT different to train trip and• a new MA reach the OBU before standstill.6.3.5.4 If the connection establishment error ratio is <10-2, then the connection loss rate shallbe <10-2/h.6.3.6 Transmission interference6.3.6.1 A transmission interference period T TI is the period during the data transmission phaseof an existing connection in which, caused by the bearer service, no error-freetransmission of user data units of 30 bytes is possible.6.3.6.2 A transmission interference happens, if the received data units of 30 bytes deviatepartially or completely from the associated transmitted data units.6.3.6.3 The transmission interference period shall be < 0.8s (95%), <1s (99%).6.3.6.4 An error-free period T Rec shall follow every transmission interference period to re-transmit user data units in error (e.g. wrong or lost) and user data units waiting to beserved.6.3.6.5 The error-free period shall be >20s (95%), >7s(99%).6.3.7 GSM-R network registration delay6.3.7.1 The GSM-R network registration delay is defined as:Value of elapsed time from the request for registration to indication of successfulregistration by +CREG response.6.3.7.2 The GSM-R network registration delay shall be ≤30s (95%), ≤35s (99%).6.3.7.3 GSM-R network registration delays > 40 s are evaluated as registration errors.6.4 Summary of QoS requirements6.4.1.1 Table 2 contains the summary of QoS requirements at GSM-R interface.QoS Parameter Value (see 6.3) Connection establishment delay of mobile< 8.5s (95%), ≤10s (100%) originated callsConnection establishment error ratio <10-2≤ 0.5s (99%)Maximum end-to-end transfer delay (of 30 bytedata block)Connection loss rate ≤ 10-2 /hTransmission interference period < 0.8s (95%), <1s (99%)Error-free period >20s (95%), >7s(99%)Network registration delay ≤30s (95%), ≤35s (99%), ≤40s (100%)Table 2 Summary of QoS requirements7. R EQUIREMENTS TO FIXED NETWORK INTERFACE7.1 Foreword7.1.1.1 This part of the specification does not define mandatory requirements forinteroperability. It is a preferred solution, in case interchangeability between tracksideRBC and access point to the fixed network is required for a given implementation.7.1.1.2 This section gives only limited information. [EuroRadio FFFIS] must be used for fullcompliance.7.1.1.3 Note: The requirements to fixed network interface refer to a set of ETSI specifications[ETS 300011, ETS 300125, ETS 300102-1]. This set is the basis of conformancerequirements for network terminations. Instead of these specifications updatedspecifications can be referred, if they state that they are compatible with the followingrequirements.7.2 Interfacedefinition7.2.1.1 The ISDN Primary Rate Interface (PRI) shall be provided as specified by [ETS300011].7.2.1.2 The service access point on the fixed network side corresponds with the S2M interfaceat the T-reference point.7.2.1.3 The Basic Rate interface might also be used as an option in some particular cases likeradio infill unit.7.2.1.4 In addition to these interfaces, the V.110 rate adaptation scheme shall be applied tothe user data channel. The RA2, RA1 and RA0 steps are mandatory.7.2.1.5 End-to-end flow control in layer 1 shall not be used.7.3 Communication signalling procedures7.3.1.1 The signalling protocols shall be provided as specified by:a) Link Access Procedure on the D channel [ETS 300125]b) User-network interface layer 3 using Digital Subscriber Signalling [ETS 300102-1]7.3.1.2 ISDN multi-level precedence and pre-emption (MLPP) supplementary service shall beprovided according to the EIRENE specification [EIRENE SRS].7.3.1.3 The SETUP message contains Information Elements including the bearer capabilityand the low layer compatibility (refer to [EuroRadio FFFIS] specifying the Euroradiodata bearer service requirements.8. R EQUIREMENTS TO MOBILE NETWORK INTERFACE8.1 Foreword8.1.1.1 This part of the specification does not define mandatory requirements forinteroperability. It is a preferred solution, in case interchangeability between OBU andMobile Terminal is required for a given implementation.8.1.1.2 This section gives only limited information. [EuroRadio FFFIS] must be used for fullcompliance.definition8.2 Interface8.2.1.1 If an MT2 interface is used at the mobile side, the service access point at the mobilestation corresponds with the R-reference point of the MT2.8.2.1.2 [GSM 07.07] specifies a profile of AT commands and recommends that this profile beused for controlling Mobile Equipment functions and GSM network services through aTerminal Adapter.8.2.1.3 For the mobile termination type MT2 the signalling over the V interface has to be inaccordance with [GSM 07.07], using the V.25ter command set.8.2.1.4 The online command state shall not be used to guarantee interoperability. To avoiddifferent behaviour, it is recommended to enable/disable this escape sequence usingthe appropriate AT command usually referred as ATS2=<manufacturer defined value>.This particular command shall be sent to the mobile terminal as part of its initialisationstring.8.2.1.5 State control using physical circuits is mandatory.8.2.1.6 The V-interface shall conform to recommendation ITU-T V.24. The signals required arespecified in [EuroRadio FFFIS].8.2.1.7 Note that in the case of class 1 mobile originated calls, it is allowed to set the priorityvalue “command control (safety)” at subscription time.8.2.1.8 The call control commands, interface control commands and responses used on the V-interface at the R reference point are specified in [EuroRadio FFFIS].9. A NNEX A(I NFORMATIVE) TRANSMISSION INTERFERENCEAND RECOVERY9.1 General9.1.1.1 The usual QoS parameter used as measure of accuracy of data transmission viatransparent B/B m channels is the bit error rate.9.1.1.2 The QoS parameter relevant for layer 2 accuracy is the HDLC frame error rate.9.1.1.3 It is not possible to define relationships between both rates. The channel behaviour isnot known: error bursts and interruptions of data transmission during radio cellhandover can happen.9.1.1.4 Additionally, statistical distributions of values such as error rates do not accurately mapthe requirements from the ETCS point of view. Transfer of user data is requested inbursts; the transfer delay can be critical for the application. It has to be guaranteed forsome application messages that data can be transferred to the train in a defined timeinterval.9.1.1.5 A model of service behaviour is necessary reflecting all relevant features of GSM-Rnetworks.9.1.1.6 This model can be used as a normative reference for acceptance tests and for networkmaintenance during ETCS operation. It enables the ETCS supplier to demonstrate thecorrect operation of ETCS constituents during conformance testing without thevariations of real world GSM-R networks.9.1.1.7 Transmission interference and recovery is a first approximation of such a servicebehaviour model.9.2 Transmission interference in relation to HDLC9.2.1.1 Transmission interference is characterised by a period in the received data streamduring which the received data units deviate partially or completely from those of thetransmitted data stream. The service user cannot see the causes of transmissioninterference.9.2.1.2 The user data units erroneously transmitted or omitted during the transmissioninterference must be corrected by re-transmission. These re-transmissions result in atime delay and in higher load in the B/B m channel. Therefore, after transmissioninterference a period of error-free transmission, called the recovery period, must follow.9.2.1.3 In the normal data transfer phase after recovery, user data units are transmitted toprovide the data throughput requested by application messages.9.2.1.4 Figure 1 shows a simplified relationship of B/B m channel and HDLC errors: because ofthe selected options for the HDLC protocol (e.g. multi selective reject) the recoveryperiod and the normal data transfer phase are not strictly separated.error-free frameHDLC statecorrupted frameerror-freeChannel stateerroneousFigure 1 B/B m channel and HDLC errors9.2.1.5 Some special cases exist in Figure 1:A Beginning of HDLC frame (corrupted by transmission) is earlier than beginning oftransmission interferenceB Error-free time is not sufficient for transfer of HDLC frameC No HDLC frame is ready for transferD End of corrupted HDLC frame is later than end of transmission interference9.2.1.6 Figure 2 shows as an example the HDLC behaviour in case of transmissioninterference.Figure 2 Event "Transmission interference"9.2.1.7 The sender does not receive an acknowledgement in the case of a corrupted last Iframe of a sequence of I frames. The timer T1 expires and a RR (poll bit set) frame willbe sent.9.2.1.8 After receiving an RR frame with an indication of successful transmission of thepreceding I frame, the lost I frame will be re-transmitted.9.2.1.9 Again the sender does not receive an acknowledgement and requests for thesequence number. Eventually, the transmission is successful but the delivery of userdata will be delayed towards the receiver.9.2.1.10 The occurrence of the above defined event represents a QoS event “Transmissioninterference” at the sender side. The beginning and the end of the transmissioninterference are not exactly known. But the second repetition clearly indicates an event“Transmission interference”:a) The transmission interference time was too long orb) The recovery time was too short.。
医学遗传学名词解释及问答题

名词解释chromosome disease染色体病——染色体数目或结构异常引起的疾病称为染色体病。
dynamic mutation动态突变——又称不稳定三核苷酸重复序列突变。
突变是由基因组中脱氧三核苷酸串联重复拷贝数增加,拷贝数的增加随着世代的传递而不断扩增。
frame shift mutation移码突变——基因组链中插入或缺失一个或多个碱基对,从而使该点之后的部分或所有三联体遗传密码子组合发黄色呢个改变的基因突变形式。
genetic disease 遗传病——因遗传因素而罹患的疾病称为遗传性疾病,简称遗传病。
family基因家族——从已克隆的基因来看,它们并不都是单拷贝,有的是重复的多拷贝,这一部分基因属于两个或多个相似基因的家族,称为基因家族。
genetic imprinting 遗传印记——一个个体来自双亲的某些同源染色体或等位基因存在着功能上的差异,因此当它们发生相同的改变时,所形成的表型却不同,这种现象称为遗传印记,也称基因组印记(genomicimprinting)或亲代印记(parental imprinting)。
mutation基因突变——基因在结构上发生碱基对组成或排列顺序的改变称为基因突变。
genetic load遗传负荷——一个群体由于致死基因或有害基因的存在而使群体适合度降低的现象。
遗传负荷主要有突变负荷和分离负荷,受近亲婚配和环境因素的影响。
diagnosis基因诊断——基因诊断又称诊断或分子诊断,通过分子生物学和分子遗传学的技术,直接检测患者体内遗传物质的结构或表达水平是否异常而作出或辅助临床诊断的技术。
therapy基因治疗——运用重组技术,将具有正常基因及其表达所需的序列导入到病变细胞或体细胞中,以替代或补偿缺陷基因的功能,或抑制基因的过度表达,从而达到治疗的目的。
replacement基因替代——去除整个变异基因,用有功能的正常基因取代之,使致病基因得到永久性地更正。
生化反应干扰实验

第二种方法:评价个别有代表性的病人结果 与高特异性的比较方法的结果偏倚(用病 人标本评价干扰)
干扰筛选
将阳性干扰物加入测定样品中,与不加的 对照组比较有无偏移,称为“配对差异”实验。 一般最有效的方法是在较高浓度下对系列可能 的干扰物作初步筛选,如果临床显著意义,则 该物质不是干扰物,无须进一步实验。反之, 具有临床显著意义的,应进一步评价以确定干 扰物浓度与干扰程度间的关系,这类实验称为 “剂量效应”(dose-response)实验
合适的冰冻或冻干样本 ,确认测试材料是否与临床样本 相似
计算所需样本量 测定基础标本中分析物的浓度并用合适的纯物质调整测 试管的分析物浓度到医学决定浓度,应避免加入分析物 时引入其他物质,推荐的分析物测试浓度见附录 B。
实验材料 2. 贮存液
获得合适而纯的潜在干扰物,或者该物质 最接近体内循环状态的形式
干扰实验的判断标准
1. 临床可接受标准 基于生理变异 源于临床经验 基于被分析物变异
干扰实验的判断标准
2. 统计学意义
在确定一个物质是否存在干扰前,首先确定所得 到的结果是否有统计学意义。
3.分析物检测浓度
干扰应该在两种医学决定浓度被评估,如果在一 种浓度上进行测试,要注意有可能漏过在其他分 析物浓度水平上有临床意义的干扰。
术语
✓ 分析物(Analyte):实验室测试的物质或者成分 ✓ 干扰物(Interferent):样本中不同于分析物并能
引起测量偏倚的成分 ✓ 干扰:在临床生化中,由于另一成分影响或样本
的特性,待测一定浓度的被分析物出现有临床意 义的偏倚 ✓ 干扰标准:干扰物所允许的最大结果偏倚 ✓ 干扰敏感度:某一分析方法对来自其他成分或者 样本特性的干扰引起误差的敏感性
医学统计学第5版中英文对照名词解释

医学统计学第5版中英文对照名词解释
以下是一些医学统计学第5版中英文对照名词解释:
同质(Homogeneity):医学研究对象具有的某种共性。
变异 (Variation) :同质研究对象变量值之间的差异。
总体 (Population):根据研究目的确定的所有同质的观察单位某项观测值的全体称为总体。
样本 (Sample):来自于总体的部分观察单位的观测值称为样本。
参数 (Parameter):由总体中全部观测值所计算出的反映总体特征的统计指标。
统计量 (Statistic):由样本观测值所计算出的反映样本特征的统计指标。
变量 (Variable) :指观察单位的某项特征。
随机误差 (Random error):是由于一系列实验或观察条件等因素的随机波动造成的测量值与真实值之间的差异。
系统误差 (Systematic error) :实际观测中,由于仪器未校正,测量者感官的某种偏差,医生掌握疗效标准偏高或偏低等,而使观测值有方向性、系统性或周期性地偏离真值。
以上名词解释仅供参考,如需更多医学统计学第5版中英文对照名词解释,建议查阅相关书籍或文献。
【生命科学知识讲解】RNA干涉(RNAInterference,RNAi)

RNA干涉(RNA Interference,RNAi)基因沉默(gene silencing)是生物体内特定基因由于种种原因不表达的遗传现象。
一方面,基因沉默是生物遗传操作创造新的遗传修饰生物(genetically modified organisms)的障碍,另一方面,它又是植物抵抗外来核酸入侵(如病毒)的一种反应,为植物抗病毒的遗传育种提供了具有实用价值的策略:RNA 介导的病毒抗性(RNA mediated virus resistance, RMVR)。
近年来,在不同的研究领域和生物中发现了许多新的使基因关闭或沉默的类型,并赋予其不同的名称:在植物中称为RNA 共抑制(co-suppression),在真菌中叫RNA 压制(quelling),动物中则叫RNA干涉(interference)。
RNA干涉是指短的dsRNA 可以降解内源的同源RNA,,而使相应基因沉默的现象,简称RNAi。
1995年,康乃尔大学 Su Guo博士,于试图阻断线虫(C. elegans)中 par-1基因时,发现了一个意想不到的现象:她们本来利用anti-sense RNA 技术,可达到特异性阻断 par-1基因的表达,同时亦在其对照组实验中,注射sense RNA 到线虫体内,预期可能观察到此基因表现的增强。
但得到的结果竟是二者都切断了par-1基因的表达途径。
这与传统上对 anti-sense RNA 技术的解释竟是正好相反。
研究小组一直没能把这个意外结果予以合理的解释。
直到1998年2月,华盛顿卡耐基研究院的 Andrew Fire 和马萨诸塞大学医学院的 Craig Mello才首次揭开这个悬疑之谜。
通过大量艰苦的工作,他们证实,Su Guo 博士遇到的sense RNA 抑制基因表达的现象,以及过去的 anti sense RNA 技术对基因表达的阻断,都是由于体外转录所得 RNA 中污染了微量双链RNA而引起。
分子生物学中的RNA interference技术

分子生物学中的RNA interference技术RNA干扰技术是一种既方便又快捷的工具,用于压制基因表达,以便进行遗传学研究。
这一技术的应用非常广泛,主要包括基因功能分析、治疗和预防疾病,以及生物物种的研究。
该技术基于小分子RNA(siRNA)和microRNA(miRNA)的物质,它们通过靶向特定mRNA分子,从而起到抑制基因表达的作用。
这种技术也称为siRNA或miRNA,或用作RNAi(RNA干涉)。
RNA干扰技术的原理RNA干扰技术的基本原理是通过引入RNA干扰分子,对靶向mRNA的特定序列进行“切割”,从而抑制该mRNA的翻译,进而抑制蛋白质的合成。
RNA干扰技术可分为三个方面的应用:siRNA,miRNA和shRNA。
siRNAsiRNA由21-23个核苷酸组成,分子结构呈双螺旋状,其中一个链(反义链)可定向提供特定基因mRNA的靶向信号。
这种分子常用于研究单个基因和疾病,对基因组表达的克隆,聚合酶链反应(PCR)和RNA病原体的检测也有较大作用。
miRNAmiRNA由22个核苷酸组成,分子结构也呈双螺旋状。
miRNA 作为一种内源性RNA干扰分子,主要与启动子区配对,负责抑制转录因子的合成。
这类分子对于复杂的多因素性疾病,并不是有着较明显的作用。
shRNAshRNA,全称为环状寄生物RNA,是siRNA和miRNA的结合体,由15-29个核苷酸组成。
shRNA可通过嵌入适当载体的plasmid质粒,用于基因敲除和谷物转基因(GM)技术。
RNA干扰技术的应用RNA干扰技术在利用了先进的基因工程技术后,在许多领域都产生了重要的应用。
其中,使用这种技术处理复杂疾病的方法已得到了许多科学家的广泛关注。
治疗和预防癌症RNA干扰技术与基因治疗的结合,人们希望通过这种技术的运用降低癌症的发病率。
科学家们最大的难点是如何能够将RNA干扰分子引导到癌细胞中,以便达到治疗作用。
借助近年来纳米技术等相关研究的不断提升,RNA干扰技术的应用在治疗癌症方面也实现了一定的突破。
【国家自然科学基金】_干涉检查_基金支持热词逐年推荐_【万方软件创新助手】_20140801
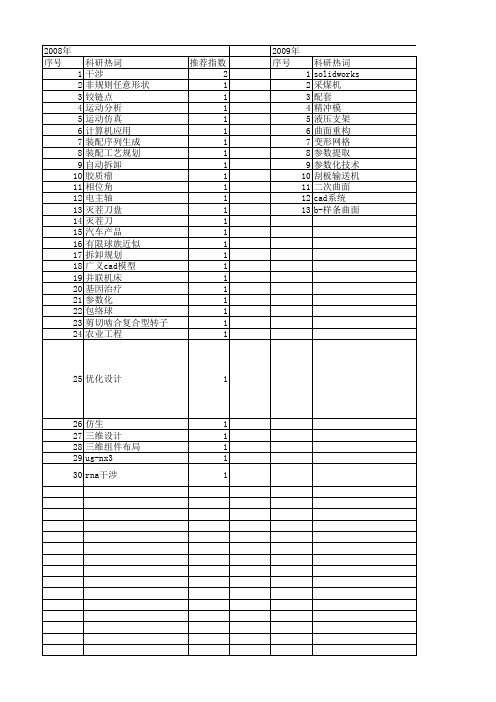
推荐指数 2 1 1 1 1 1 1 1 1 1 1 1 1
2010年 序号 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
科研热词 齿轮 齿廓 非圆齿轮 非圆锥齿轮 送料系统 装配模型 螺杆泵 虚拟机床 约束驱动 磨齿机 磨削 直旋机构 滚珠丝杠 机械设计 机床建模 数值方法 建模 尺寸驱动 多工位压力机 同圆回珠 参数化设计 加工仿真 仿真 vericut pro/e adams
2012年 序号 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
科研热词 推荐指数 干涉检查 2 轿车后地板前段 1 路径控制点(rcp) 1 装焊夹具 1 螺杆 1 虚拟操控 1 自动调整 1 自动布线 1 查 1 成形铣刀 1 快速设计 1 廓形方程 1 应力分析 1 广义 1 干涉 1 布尔可满足性 1 安全政策 1 刀盘 1 刀刃 1 三维电气布线 1 intransitive generalized noninterference, 1 quantif catia 1
推荐指数 2 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
2009年 序号 1 2 3 4 5 6 7 8 9 10 11 12 13
科研热词 solidworks 采煤机 配套 精冲模 液压支架 曲面重构 变形网格 参数提取 参数化技术 刮板输送机 二次曲面 cad系统 b-样条曲面
2008年 序号 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30
常用遗传学中英文词汇

常用遗传学中英文词汇近端着丝粒染色体(Acrocentric chromosome)--着丝粒靠近染色体端部的染色体。
加和原则(Additivity principle)--如果两个事件相互排斥,那么获得其中一个或另一个的概率为它们的各自概率之和。
等位基因(Allele)--在一既定基因座上一个基因的替换形式。
等位基因特异性寡核苷酸(Allele-specific oligonucleotide,ASO)--设计合成的寡核苷酸,可在适当条件下与特异序列杂交而不与其相关的序列杂交。
用针对每个等位基因序列设计的ASO甚至可容易地检出单个核苷酸的变异。
在几种设计相似、用来区分密切相关等位基因的方法中,ASO还可用作PCR引物。
等位基因异质性(Allelic heterogeneity)--在同一遗传基因座上,由不同的突变等位基因引起的相同或相似的表型。
α1-抗胰蛋白酶(α1-Antitrypsin)--是抑制弹性蛋白酶活性的一种丝氨酸蛋白酶抑制剂,该抑制剂的缺乏(如α1-抗胰蛋白酶不足)将导致严重的慢性肺和肝脏疾病。
Alu重复序列(Alu repetitive sequence)--位于基因间或内含子DNA中的中等重复序列,含有限制性内切酶AluⅠ的识别位点,这些序列长约300bp,并在人类基因组中重复出现约500,000次。
羊膜穿刺术(Amniocentesis)--一种产前诊断的方法,通常在妊娠4至6月抽取羊膜囊内婴儿四周的羊水进行。
扩增(Amplification)--一段DNA序列多个拷贝的产生。
非整倍体(Aneuploid)--指单倍体非整倍数的任何染色体数目。
通常非整倍体是指单条染色体的额外拷贝(三体性),或缺少单条染色体(单体性)。
由减数分裂或有丝分裂过程中染色体不分离所致。
早现遗传(Anticipation)--指一种遗传性疾病在较早年龄发病或在连续后代中严重程度增加。
DNA反义链(Antisense strand of DNA)--指DNA双链中的非编码链,它与mRNA互补,是mRNA合成的模板。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1 2 3 4 5
if ( confidential ==1) public = 42 else public = 17; public = 0;
Fig. 1. A secure program fragment
I. I Information Flow Control (IFC) is an important technique for discovering security leaks in software. IFC has two main tasks: • guarantee that confidential data cannot leak to public variables (confidentiality); • guarantee that critical computations cannot be manipulated from outside (integrity). State-of-the-art IFC exploits program analysis to assign and propagate security levels to variables and expressions, guaranteeing that any potential security leak is found. LanguageBased IFC [1] utilizes the program source code alone to discover security leaks. This has the huge advantage that it can exploit a long history of research on program analysis, and will discover any security leaks caused by software itself, though this approach may miss information flow through e.g. physical side channels, which are usually handled by separate approaches. In their recent overview article, Sabelfeld and Myers [1] survey contemporary IFC approaches based on program analysis. Most contemporary analysis methods are based on nonstandard type systems. Security levels are coded as types for variables (and fields in object-oriented software) and the typing rules catch illegal flow of information [2], [3]. Most of the type-based approaches partition the set of variables (and fields in object-oriented software) into disjoint sets (such as secure and public data). If information illicitly flows e.g. from the secure to the public partition, then the program is already considered insecure, even if the public variable is no longer live after that flow. The original intention was, however, different: Classic noninterference states that the two streams of (public) output of the same program should be indistinguishable even if they differentiate on (secret) input, or
Frank Nodes
University of Passau, Germany
Abstract— In classic information flow control (IFC), noninterference guarantees that no information flows from secret input channels to public output channels. However, this notion turned out to be overly restrictive as many intuitively secure programs do allow some release. In this paper we define a static analysis that allows intransitive noninterference in combination with contextsensitive analysis for Java bytecode programs. In contrast to type systems that annotate variables, our approach annotates information sources and sinks. To the best of our knowledge this is the first IFC technique which is flow-, context-, and objectsensitive. It allows IFC for realistic languages like Java or C and offers a mechanism for declassification to accommodate some information leakage for cases where traditional noninterference is too restrictive.
in other words secure input is not allowed to flow to public output channels. So we really should not worry about secret data in a variable as long as its content is not fed to output. Besides, type-based analysis is usually not flowsensitive, context-sensitive, nor object-sensitive. This leads to imprecision and thus to a high number of false alarms. For example, the well-known program fragment in Figure 1 is considered insecure by type-based IFC, as type-based IFC is not flow-sensitive. It does not see that the potential information flow from confidential to public in the if-statement is guaranteed to be killed by the following assignment. Type-based IFC performs even worse in the presence of unstructured control flow or exceptions. Therefore, type systems greatly overapproximate information flow control, resulting in too many secure programs rejected (false positives). First steps towards flow-sensitive type systems have been proposed, but are restricted to rudimentary languages like While-languages [4], or languages with no support for unstructured control flow [5]. Fortunately, program analysis has much more to offer than just sophisticated type systems. In particular, the program dependence graph (PDG) [6] has become a standard data structure allowing various kinds of powerful program analyses and in particular, efficient program slicing [7]. The first information flow control algorithm based on PDGs for full C was presented by Snelting et al. [8]. Recently, a theorem connecting PDGs to the classical noninterference criterion was proven [9]. Later, Hammer et al. developed a precise PDG for full Java [10], which is much more difficult than C due to the effects of inheritance and dynamic dispatch. Today, we can handle realistic C and Java programs and thus have a powerful tool for IFC available that is much more precise than conventional approaches. In this paper, we augment PDGs with Denning-Style security level lattices. We focus mainly on the precise interprocedural analysis with declassification in called methods, a feature that our previous work [11] could only handle in a conservative
