部分作业答案.pdf
运筹学 刁在筠 部分作业的参考答案线性规划部分

第二章 线性规划73P 4. 将下面的线性规划问题化成标准形式12312312312max 2..236230316x x x s t x x x x x x x x −+⎧⎪−+≥⎪⎪+−≤⎨⎪≤≤⎪⎪−≤≤⎩解:将max 化为 min , 3x 用45x x −代替,则1245124512451245min 2()..23()62()30316,0x x x x s t x x x x x x x x x x x x −+−−⎧⎪−+−≥⎪⎪+−−≤⎪⎨≤≤⎪⎪−≤≤⎪≥⎪⎩令221x x ′=+,则1245124512451245min12()..2(1)3()62(1)()30307,0x x x x s t x x x x x x x x x x x x ′−+−−−⎧⎪′−−+−≥⎪⎪′+−−−≤⎪⎨≤≤⎪⎪′≤≤⎪≥⎪⎩将线性不等式化成线性等式,则可得原问题的标准形式12451245612457182912456789min221..23342437,,,,,,,0x x x x s t x x x x x x x x x x x x x x x x x x x x x x ′−+−+−⎧⎪′−+−−=⎪⎪′+−++=⎪⎨+=⎪⎪′+=⎪′≥⎪⎩73P 5、用图解法求解下列线性规划问题:(1) 121212min 3..206122x x s t x x x x +⎧⎪+≥⎪⎨≤≤⎪⎪≥⎩解:图2.1的阴影部分为此问题的可行区域.将目标函数的等值线123x x c +=(c 为常数)沿它的负法线方向()13T−−,移动到可行区域的边界上.于是交点T),(812就是该问题的最优解,其最优值为36.75P 16. 用单纯形法求解下列线性规划问题:(1) 123123123123min 2..360210200,1,2,3j z x x x s t x x x x x x x x x x j ⎧=−−+⎪++≤⎪⎪−+≤⎨⎪+−≤⎪⎪≥=⎩解:将此问题化成标准形式123123412351236min 2..360210200,1,2,3,4,5,6j z x x x s t x x x x x x x x x x x x x j ⎧=−−+⎪+++=⎪⎪−++=⎨⎪+−+=⎪⎪≥=⎩以456,,x x x 为基变量,可得第一张单纯形表为以1x 为进基变量,5x 为离基变量旋转得以2x 为进基变量,6x 为离基变量旋转得1x 2x 3x 4x 5x 6x RHS z2 1 -1 0 000 4x 31 1 1 0060 5x 1-121010 6x 11 -1 0 01201x 2x 3x 4x 5x 6x RHS z0 3 -5 0 -20-204x 0 4 -5 1 -3030 1x 1-1 2 0 1010 6x 02-3-11101 注意单纯形表的格式!2 要用记号把转轴元标出来 3要记住在单纯形表的左边,用进基变量代替离基变量注(零行元素的获得):先将目标函数化成求最小值的形式,再把所有变量移到等式左边,常数移到等式右边。
财务管理作业部分答案

财务管理作业部分答案一、名词解释1、时间价值:2、复利:3、复利现值4、年金5、后付年金6、先付年金7、延期年金8、永续年金二、判断题1、货币的时间价值原理,正确地揭示了不同时点上资金之间的换算关系,是财务决策的基本依据。
(对)2、由现值求终值,称为贴现,贴现时使用的利息率称为贴现率。
(错)3、n期先付年金与n期后付年金的付款次数相同,但由于付款时间的不同,n期先付年金终值比n期后付年金终值多计算-期利息。
所以,可先求出n期后付年金的终值,然后再乘以(1+i)便可求出n期先付年金的终值。
(对)4、n期先付年金现值与n期后付年金现值的付款次数相同,但由于付款时间不同,在计算现值时,n期先付年金比n期后付年金多贴现一期。
所以,可先求出n期后付年金的现值,然后再乘以(1+i)便可求出n期先付年金的现值。
(对)5、英国和加拿大有一种国债就是没有到期日的债券,这种债券的利息视为永续年金。
(对)6、复利计息频数越大,复利次数越多,终值的增长速度越快,相同期间内终值越大。
(对)7、决策者对未来的情况不仅不能完全确定,而且对其可能出现的概率也不清楚,这种情况下的决策为风险性决策。
(错)8、利用概率分布的概念,我们能够对风险进行衡量,即:预期未来收益的概率分布越集中,则该投资的风险越大。
(错)9、如果两个项目预期收益率相同、标准差不同,理性投资者会选择标准差较大,即风险较小的那个。
(错)10、在其他条件不变时,证券的风险越高,其价格便越低,从而必要收益率越高。
(对)11、如果组合中股票数量足够多,则任意单只股票的可分散风险都能够被消除。
(对)12、经济危机、通货膨胀、经济衰退以及高利率通常被认为是可分散的市场风险。
(错)13、证券组合投资要求补偿的风险只是市场风险,而不要求对可分散风险进行补偿。
(错)14、证券组合的风险收益是投资者因承担可分散风险而要求的,超过时间价值的那部分额外收益。
(错)15、有效投资组合是指在任何既定的风险程度上,提供的预期收益率最高的投资组合。
理论力学(胡运康)第三章作业答案

11
3-26 已知:M1=10kN,求FBx 、 FBy 、MB 、FAC 、 FEx 、 FEy 解: 1、整体:
∑M
∑F
MB
FBx FBy
x
B
= 0 ⇒ MB
= 0 ⇒ FBx = 0
= 0 ⇒ FBy
∑F
y
2、AB: FD
A
FEy
E
∑M
FEx
B
E
= 0 ⇒ FD
∑F
∑F
x
= 0 ⇒ FEx
= 0 ⇒ FEy
3-42 已知:q1=4kN/m , q2=2kN/m ,F =2 kN ,M=2 kN.m 。求 A、B处受力;销钉C所受的力。
F1 F2
F B FB FC1y C FC2y
C FC2y 1m
4/3 m
q 解: 1、BC: F1 = 1 ⋅ 2 = 4kN, 2
F2 =
1 q1 ⋅ ⋅ 2 = 2kN 2 2
M1 B
FE
Aቤተ መጻሕፍቲ ባይዱ
∑M
2、DC:
M2
FC
x
A
= 0, ⇒ FE
F'E
D
FE= F'E
C FCy
∑M
C
= 0, ⇒ M 2
8
3-17 求 机构平衡时力偶M1、M2的关系。
FAx FAy
A
FD F'D D
B
M1
FD= F'D
FCx
M2
C FCy
解: 1、AB: ∑ M A = 0, FD ⋅ d − M 1 = 0, ⇒ FD = M 1
2
3-3
几何法
操作系统第九版部分课后作业习题答案分析解析

CHAPTER 9 Virtual Memory Practice Exercises9.1 Under what circumstances do page faults occur? Describe the actions taken by the operating system when a page fault occurs.Answer:A page fault occurs when an access to a page that has not beenbrought into main memory takes place. The operating system veri?esthe memory access, aborting the program if it is invalid. If it is valid, a free frame is located and I/O is requested to read the needed page into the free frame. Upon completion of I/O, the process table and page table are updated and the instruction is restarted.9.2 Assume that you have a page-reference string for a process with m frames (initially all empty). The page-reference string has length p;n distinct page numbers occur in it. Answer these questions for anypage-replacement algorithms:a. What is a lower bound on the number of page faults?b. What is an upper bound on the number of page faults?Answer:a. nb. p9.3 Consider the page table shown in Figure 9.30 for a system with 12-bit virtual and physical addresses and with 256-byte pages. The list of freepage frames is D, E, F (that is, D is at the head of the list, E is second,and F is last).Convert the following virtual addresses to their equivalent physicaladdresses in hexadecimal. All numbers are given in hexadecimal. (Adash for a page frame indicates that the page is not in memory.)? 9EF? 1112930 Chapter 9 Virtual Memory? 700? 0FFAnswer:? 9E F - 0E F? 111 - 211? 700 - D00? 0F F - EFF9.4 Consider the following page-replacement algorithms. Rank thesealgorithms on a ?ve-point scale from “bad” to “perfect” according to the page-fault rate. Separate those algorithms that suffer from Belady’sanomaly from those that do not.a. LRU replacementb. FIFO replacementc. Optimal replacementd. Second-chance replacementAnswer:Rank Algorithm Suffer from Belady’s anomaly1 Optimal no2 LRU no3 Second-chance yes4 FIFO yes9.5 Discuss the hardware support required to support demand paging. Answer:For every memory-access operation, the page table needs to be consulted to check whether the corresponding page is resident or not and whetherthe program has read or write privileges for accessing the page. These checks have to be performed in hardware. A TLB could serve as a cache and improve the performance of the lookup operation.9.6 An operating system supports a paged virtual memory, using a central processor with a cycle time of 1 microsecond. It costs an additional 1 microsecond to access a page other than the current one. Pages have 1000 words, and the paging device is a drum that rotates at 3000 revolutionsper minute and transfers 1 million words per second. The following statistical measurements were obtained from the system:page other than the? 1 percent of all instructions executed accessed acurrent page.?Of the instructions that accessed another page, 80 percent accesseda page already in memory.Practice Exercises 31?When a new page was required, the replaced page was modi?ed 50 percent of the time.Calculate the effective instruction time on this system, assuming that the system is running one process only and that the processor is idle during drum transfers.Answer:(2 sec)(1sec + 0.008 ×effective access time = 0.99 ×(10,000 sec + 1,000 sec)+ 0.002 ×(10,000 sec + 1,000 sec)+ 0.001 ×9.7 Consider the two-dimensional array A:int A[][] = new int[100][100];where A[0][0] is at location 200 in a paged memory system with pages of size 200. A small process that manipulates the matrix resides in page 0 (locations 0 to 199). Thus, every instruction fetch will be from page 0. For three page frames, how many page faults are generated bythe following array-initialization loops, using LRU replacement andassuming that page frame 1 contains the process and the other two are initially empty?a. for (int j = 0; j < 100; j++)for (int i = 0; i < 100; i++)A[i][j] = 0;b. for (int i = 0; i < 100; i++)for (int j = 0; j < 100; j++)A[i][j] = 0;Answer:a. 5,000b. 509.8 Consider the following page reference string:1, 2, 3, 4, 2, 1, 5, 6, 2, 1, 2, 3, 7, 6, 3, 2, 1, 2, 3, 6.How many page faults would occur for the following replacement algorithms, assuming one, two, three, four, ?ve, six, or seven frames? Remember all frames are initially empty, so your ?rst unique pages will all cost one fault each.?LRU replacement? FIFO replacement?Optimal replacement32 Chapter 9 Virtual MemoryAnswer:Number of frames LRU FIFO Optimal1 20 20 202 18 18 153 15 16 114 10 14 85 8 10 76 7 10 77 77 79.9 Suppose that you want to use a paging algorithm that requires a referencebit (such as second-chance replacement or working-set model), butthe hardware does not provide one. Sketch how you could simulate a reference bit even if one were not provided by the hardware, or explain why it is not possible to do so. If it is possible, calculate what the cost would be.Answer:You can use the valid/invalid bit supported in hardware to simulate the reference bit. Initially set the bit to invalid. On ?rst reference a trap to the operating system is generated. The operating system will set a software bit to 1 and reset the valid/invalid bit to valid.9.10 You have devised a new page-replacement algorithm that you thinkmaybe optimal. In some contorte d test cases, Belady’s anomaly occurs. Is thenew algorithm optimal? Explain your answer.Answer:No. An optimal algorithm will not suffer from Belady’s anomaly beca an optimal algorithm replaces the page that will not—by de?nition—be used for the longest time. Belady’s anomaly occurs when a pagereplacement a lgorithm evicts a page that will be needed in theimmediatefuture. An optimal algorithm would not have selected such a page.9.11 Segmentation is similar to paging but usesnevariable-sized“pages.”De?two segment-replacement algorithms based on FIFO and LRU pagereplacement s chemes. Remember that since segments are not thesamesize, the segment that is chosen to be replaced may not be big enoughto leave enough consecutive locations for the needed segment. Considerstrategies for systems where segments cannot be relocated, and thosefor systems where they can.Answer:a. FIFO. Find the ?rst segment large enough to accommodate theincoming segment. If relocation is not possible and no one segmentis large enough, select a combination of segments whose memoriesare contiguous, which are “closest to the ?rst of the list” and which can accommodate the new segment. If relocation is possible,rearrange the memory so that the ?rstNsegments large enough forthe incoming segment are contiguous in memory. Add any leftoverspace to the free-space list in both cases.Practice Exercises 33b. LRU. Select the segment that has not been used for the longestperiod of time and that is large enough, adding any leftover spaceto the free space list. If no one segment is large enough, selecta combination of the “oldest” segments that are contiguous inmemory (if relocation is not available) and that are large enough.If relocation is available, rearrange the oldest N segments to becontiguous in memory and replace those with the new segment.9.12 Consider a demand-paged computer system where the degree of multiprogramming is currently ?xed at four. The system was recentlymeasured to determine utilization of CPU and the paging disk. The resultsare one of the following alternatives. For each case, what is happening?Can the degree of multiprogramming be increased to increase the CPU utilization? Is the paging helping?a. CPU utilization 13 percent; disk utilization 97 percentb. CPU utilization 87 percent; disk utilization 3 percentc. CPU utilization 13 percent; disk utilization 3 percentAnswer:a. Thrashing is occurring.b. CPU utilization is suf?ciently high to leave things alone, andincrease degree of multiprogramming.c. Increase the degree of multiprogramming.9.13 We have an operating system for a machine that uses base and limit registers, but we have modi?ed the ma chine to provide a page table.Can the page tables be set up to simulate base and limit registers? How can they be, or why can they not be?Answer:The page table can be set up to simulate base and limit registers provided that the memory is allocated in ?xed-size segments. In this way, the base of a segment can be entered into the page table and the valid/invalid bit used to indicate that portion of the segment as resident in the memory. There will be some problem with internal fragmentation.9.27.Consider a demand-paging system with the following time-measured utilizations:CPU utilization 20%Paging disk 97.7%Other I/O devices 5%Which (if any) of the following will (probably) improve CPU utilization? Explain your answer.a. Install a faster CPU.b. Install a bigger paging disk.c. Increase the degree of multiprogramming.d. Decrease the degree of multiprogramming.e. Install more main memory.f. Install a faster hard disk or multiple controllers with multiple hard disks.g. Add prepaging to the page fetch algorithms.h. Increase the page size.Answer: The system obviously is spending most of its time paging, indicating over-allocationof memory. If the level of multiprogramming is reduced resident processeswould page fault less frequently and the CPU utilization would improve. Another way toimprove performance would be to get more physical memory or a faster paging drum.a. Get a faster CPU—No.b. Get a bigger paging drum—No.c. Increase the degree of multiprogramming—No.d. Decrease the degree of multiprogramming—Yes.e. Install more main memory—Likely to improve CPU utilization as more pages canremain resident and not require paging to or from the disks.f. Install a faster hard disk, or multiple controllers with multiple hard disks—Also animprovement, for as the disk bottleneck is removed by faster response and morethroughput to the disks, the CPU will get more data more quickly.g. Add prepaging to the page fetch algorithms—Again, the CPU will get more datafaster, so it will be more in use. This is only the case if the paging actionis amenableto prefetching (i.e., some of the access is sequential).h. Increase the page size—Increasing the page size will result in fewer page faults ifdata is being accessed sequentially. If data access is more or less random, morepaging action could ensue because f ewer pages c an be kept in memory and moredata is transferred per page fault. So this change is as likely to decrease utilizationas it is to increase it.10.1、Is disk scheduling, other than FCFS scheduling, useful in a single-userenvironment? Explain your answer.Answer: In a single-user environment, the I/O queue usually is empty. Requests g enerally arrive from a single process for one block or for a sequence of consecutive blocks. In these cases, FCFS is an economical method of disk scheduling. But LOOK is nearly as easy to program and will give much better performance when multiple processes are performing concurrent I/O, such as when aWeb browser retrieves data in the background while the operating system is paging and another application is active in the foreground.10.2.Explain why SSTF scheduling tends to favor middle cylindersover theinnermost and outermost cylinders.The center of the disk is the location having the smallest average distance to all other tracks.Thus the disk head tends to move away from the edges of the disk.Here is another way to think of it.The current location of the head divides the cylinders into two groups.If the head is not in the center of the disk and a new request arrives,the new request is more likely to be in the group that includes the center of the disk;thus,the head is more likely to move in that direction.10.11、Suppose that a disk drive has 5000 cylinders, numbered 0 to 4999. The drive is currently serving a request at cylinder 143, and the previous request was at cylinder 125. The queue of pending requests, in FIFO order, is86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130Starting from the current head position, what is the total distance (in cylinders) that the disk arm moves to satisfy all the pending requests, for each of the following disk-scheduling algorithms?a. FCFSb. SSTFc. SCANd. LOOKe. C-SCANAnswer:a. The FCFS schedule is 143, 86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130. The total seek distance is 7081.b. The SSTF schedule is 143, 130, 86, 913, 948, 1022, 1470, 1509, 1750, 1774. The total seek distance is 1745.c. The SCAN schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 4999, 130, 86. The total seek distance is 9769.d. The LOOK schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 130, 86. The total seek distance is 3319.e. The C-SCAN schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 4999, 86, 130. The total seek distance is 9813.f. (Bonus.) The C-LOOK schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 86, 130. The total seek distance is 3363.12CHAPTERFile-SystemImplementationPractice Exercises12.1 Consider a ?le currently consisting of 100 blocks. Assume that the?lecontrol block (and the index block, in the case of indexed allocation)is already in memory. Calculate how many disk I/O operations are required for contiguous, linked, and indexed (single-level) allocation strategies, if, for one block, the following conditions hold. In the contiguous-allocation case, assume that there is no room to grow atthe beginning but there is room to grow at the end. Also assume thatthe block information to be added is stored in memory.a. The block is added at the beginning.b. The block is added in the middle.c. The block is added at the end.d. The block is removed from the beginning.e. The block is removed from the middle.f. The block is removed from the end.Answer:The results are:Contiguous Linked Indexeda. 201 1 1b. 101 52 1c. 1 3 1d. 198 1 0e. 98 52 0f. 0 100 012.2 What problems could occur if a system allowed a ?le system to be mounted simultaneously at more than one location?Answer:4344 Chapter 12 File-System ImplementationThere would be multiple paths to the same ?le, which could confuse users or encourage mistakes (deleting a ?le with one path deletes the?le in all the other paths).12.3 Why must the bit map for ?le allocation be kept on mass storage, ratherthan in main memory?Answer:In case of system crash (memory failure) the free-space list would not be lost as it would be if the bit map had been stored in main memory.12.4 Consider a system that supports the strategies of contiguous, linked, and indexed allocation. What criteria should be used in deciding which strategy is best utilized for a particular ?le?Answer:?Contiguous—if ?le is usually accessed sequentially, if ?le isrelatively small.?Linked—if ?le is large and usually accessed sequentially.? Indexed—if ?le is large and usually accessed randomly.12.5 One problem with contiguous allocation is that the user must preallocate enough space for each ?le. If the ?le grows to be larger than thespace allocated for it, special actions must be taken. One solution to this problem is to de?ne a ?le structure consisting of an initial contiguousarea (of a speci?ed size). If this area is ?lled, the operating system automatically de?nes an over?ow area that is linked to the initial contiguous area. If the over?ow area is ?lled, another over?ow areais allocated. Compare this implementation of a ?le with the standard contiguous and linked implementations.Answer:This method requires more overhead then the standard contiguousallocation. It requires less overheadthan the standard linked allocation.12.6 How do caches help improve performance? Why do systems not use more or larger caches if they are so useful?Answer:Caches allow components of differing speeds to communicate moreef?ciently by storing data from the slower device, temporarily, ina faster device (the cache). Caches are, almost by de?nition, moreexpensive than the device they are caching for, so increasing the numberor size of caches would increase system cost.12.7 Why is it advantageous for the user for an operating system to dynamically allocate its internal tables? What are the penalties to the operating system for doing so?Answer:tablesDynamic tables allow more ?exibility in system use growth —are never exceeded, avoiding arti?cial use limits. Unfortunately, kernel structures and code are more complicated, so there is more potentialfor bugs. The use of one resource can take away more system resources (by growing to accommodate the requests) than with static tables.Practice Exercises 4512.8 Explain how the VFS layer allows an operating system to support multiple types of ?le systems easily.Answer:VFS introduces a layer of indirection in the ?le system implementation. In many ways, it is similar to object-oriented programming techniques. System calls can be made generically (independent of ?le system type). Each ?le system type provides its function calls and data structuresto the VFS layer. A system call is translated into the proper speci?c functions for the target ?le system at the VFS layer. The calling program has no ?le-system-speci?c code, and the upper levels of the system call structures likewise are ?le system-independent. The translation at the VFS layer turns these generic calls into ?le-system-speci?c operations.。
飞行力学部分作业答案(1)

+ (sinθa sinφa sinψ a + cosφa cosψ a )C − (sinθa cosφa sinψ a − sinφa cosψ a )
m
dvzg dt
= −sinθT
cosϕ + cosφ cosθT sin ϕ + sinθaC + sinφa
cosθaC − cosφa
sin θ
cosφ
sinψ
− sinφ
cosψ
cosφ cosθ
Lga
=
ccoossθθaa
cosψ a sinψ a
− sinθa
sinθa sinφa cosψ a − cosφa sinψ a sinθa sinφa sinψ a + cosφa cosψ a
sin φa cosθa
+ (sinθa sinφa cosψ a − cosφa sinψ a ) C − (sinθa cosφa cosψ a + sinφa sinψ a ) L
m dvyg dt
= cosθ sinψ T cosϕ
− (sinθ cosφ sinψ
− sinφ cosψ
)T sin ϕ − cosθa sinψ a D
= 0.1019
2
2
CD = 0.014 + 0.08CL2
CD = 0.0152
D = 8771N
代入方程求得T = 38771N
3.5
χɺ = V R
得:
R
=
V ω
=
300 / 3.6 3.14 /15
=
金融部分作业答案

《财政与金融》习题四(货币与信用、利息)一、单项选择题1、当货币执行( C )职能时,只需有观念上的货币就可以了。
A、支付手段B、世界货币C、价值尺度D、贮藏手段2、最早出现的货币形式是( B )。
A、金属货币B、实物货币C、电子货币D、纸币3、下列行为中,属于货币执行流通手段职能的是( B )。
A、存款存入银行B、饭馆就餐付款C、缴纳房租、水电款D、企业发放职工工资4、在我国企业与企业之间存在的“三角债”状况,从本质上讲属于( A )。
A、商业信用B、银行信用C、国家信用D、消费信用5、流通中所需的货币量与( B )成反比。
A、商品价格总额B、货币流通速度C、商品的价值D、人们持币愿望6、在货币流通速度不变的情况下,如果商品的数量增加,而纸币的数量增加更快,则(A)。
A、纸币贬值B、纸币升值C、纸币的价值不变7、以下是足值货币的是(A)。
A、金属货币的主币B、金属货币的辅币C、纸币D、银行券8、货币制度的核心内容是(A)。
A、币材B、货币单位C、发行程序D、流通办法9、在现代信用中,最主要的信用形式是( B )。
A、商业信用B、银行信用C、民间信用D、国家信用10、必须经过承兑才具法律效力的信用工具是( D )。
A、银行本票B、银行汇票C、商业本票D、商业汇票11、单利与复利计算的主要区别是( B )。
A、本金是否计息B、利息是否计息C、利率的高低D、本息归还方式12、利息率是在( B )。
A、平均利润率以下波动B、在大于0和小于平均利润率之间波动C、平均利润率以上波动13、信用是( D )。
A、买卖行为B、救济行为C、赠予行为D、借贷行为14、借贷资本家贷出货币资本时让渡的权利是(B )。
A、资本所有权B、资本使用权C、资本所有权与使用权15、以政府作为借款人的信用形式是( C )。
A、银行信用B、商业信用C、国家信用D、国际信用16、准货币是指(A)A、M2—MlB、M2+MlC、M0+MlD、M1-MO17、我国最早放开的利率是( C )。
西南石油大学油层物理课后习题作业部分答案
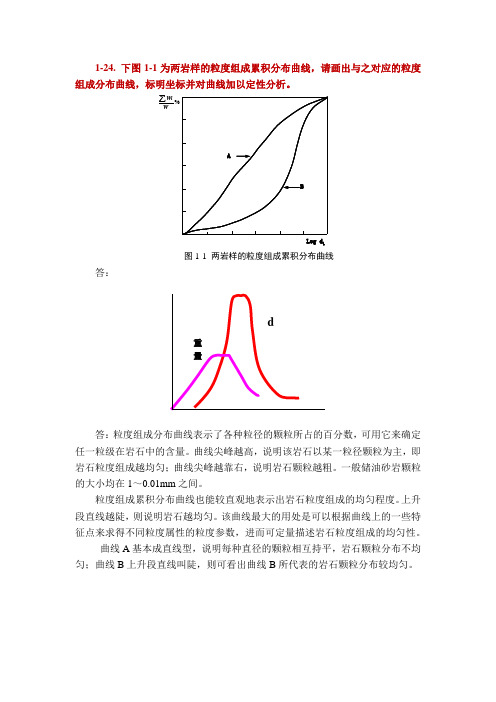
1-24. 下图1-1为两岩样的粒度组成累积分布曲线,请画出与之对应的粒度组成分布曲线,标明坐标并对曲线加以定性分析。
图1-1 两岩样的粒度组成累积分布曲线答:答:粒度组成分布曲线表示了各种粒径的颗粒所占的百分数,可用它来确定任一粒级在岩石中的含量。
曲线尖峰越高,说明该岩石以某一粒径颗粒为主,即岩石粒度组成越均匀;曲线尖峰越靠右,说明岩石颗粒越粗。
一般储油砂岩颗粒的大小均在1~0.01mm 之间。
粒度组成累积分布曲线也能较直观地表示出岩石粒度组成的均匀程度。
上升段直线越陡,则说明岩石越均匀。
该曲线最大的用处是可以根据曲线上的一些特征点来求得不同粒度属性的粒度参数,进而可定量描述岩石粒度组成的均匀性。
曲线A 基本成直线型,说明每种直径的颗粒相互持平,岩石颗粒分布不均匀;曲线B 上升段直线叫陡,则可看出曲线B 所代表的岩石颗粒分布较均匀。
Log d iWWi重量%d1-30.岩石孔隙度的一般变化范围是多少?Φa 、Φe 、Φf 的关系怎样?常用测定孔隙度的方法有哪些?影响孔隙度大小的因素有哪些?答:1)根据我国各油气田的统计资料,实际储油气层储集岩的孔隙度范围大致为:致密砂岩孔隙度自<1%~10%;致密碳酸盐岩孔隙度自<1%~5%;中等砂岩孔隙度自10%~20%;中等碳酸盐岩孔隙度自5%~10%;好的砂岩孔隙度自20%~35%;好的碳酸盐岩孔隙度自10%~20%。
2)由绝对孔隙度a φ、有效孔隙度e φ及流动孔隙度ff φ的定义可知:它们之间的关系应该是a φ>e φ>ff φ。
3)岩石孔隙度的测定方法有实验室内直接测定法和以各种测井方法为基础的间接测定法两类。
间接测定法影响因素多,误差较大。
实验室内通过常规岩心分析法可以较精确地测定岩心的孔隙度。
4)对于一般的碎屑岩 (如砂岩),由于它是由母岩经破碎、搬运、胶结和压实而成,因此碎屑颗粒的矿物成分、排列方式、分选程度、胶结物类型和数量以及成岩后的压实作用(即埋深)就成为影响这类岩石孔隙度的主要因素。
《管理学概论》记分作业部分参考答案

《管理学概论》记分作业参考答案[记分作业]计分作业11. 最容易处理的管理环境是()(单选题)A.简单—静态环境B.简单—动态环境C.复杂—动态环境D.复杂—静态环境第1题你选择了 A. 正确答案 A. 结果√2. 对各层次的管理人员都具有同等重要意义的管理技能是()(单选题)A.概念技能B.人际技能C.技术技能D.诊断技能第2题你选择了 B. 正确答案 B. 结果√3. 复杂人的假设对应了哪种管理理论()(单选题)A.科学管理理论B.权变管理理论C.系统管理理论D.行为科学管理理论第3题你选择了 B. 正确答案 B. 结果√4. 麦格雷戈的Y理论指的是()(单选题)A.理性-经济人B.社会人C.复杂人D.自我实现的人第4题你选择了 D. 正确答案 D. 结果√5. 人们在组织活动中由于兴趣、情感等因素而自发产生的团体被称之为()(单选题)A.正式组织B.正规组织C.非正式组织D.非正规组织第5题你选择了 C. 正确答案 C. 结果√6. 消费者权益保护协会的性质属于()(单选题)A.正式组织B.非正式组织C.行业协会D.团队第6题你选择了 A. 正确答案 A. 结果√7. 20世纪初,泰罗()一书的发表,是管理学成为一门独立学科的标志。
(单选题)A.《工业管理与一般管理》B.《科学管理原理》C.《社会组织与经济组织理论》D.《心理学与工业效率》第7题你选择了 B. 正确答案 B. 结果√8. 梅奥等人通过霍桑试验得出结论:人们的生产效率不仅受到物理的、生理的因素的影响,而且还受到社会环境、社会心理因素的影响。
由此创立了()学说。
(单选题)A.科学管理B.人文关系C.社会关系D.人际关系第8题你选择了 D. 正确答案 D. 结果√9. ()引起管理界的轰动,从此建立学习型组织、进行修炼成为管理理论与实践的热点。
(单选题)A.迈克尔•海默的《企业再造工程》B.孔茨的《管理学》C.德鲁克的《管理的实践》D.彼得•圣吉的《第五项修炼—学习型组织与实务》第9题你选择了 D. 正确答案 D. 结果√10. ()主张通过研究分析成功的或失败的案例来对管理问题进行剖析,从中提炼出某些一般性的管理结论或原理来指导日常工作。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
(b) G1:10.5kV;T1:一次侧 10.5kV,二次侧 121kV;
G2:10.5kV;T2: 低压侧 10.5kV,中压侧 38.5kV,高压侧 121kV
G 10kV T1
110kV
T2 35kV T3 6kV M
10kV
T4 3kV
(c) G:10.5kV;T1:一次侧 10.5kV,二次侧 121kV;T2: 低压侧 11kV,中压侧 38.5kV,高压侧 110kV;
1-6.目前我国电力系统的额定电压等级有哪些?额定电压等级选择确定原则有哪些? 答:我国电力系统的额定电压等级有 3kV、6kV、10kV、35kV、60kV、110kV、154kV、220kV、 330kV、500kV、750kV、1000kV。
额定电压等级选择确定原则有:用电设备的额定电压=系统额定电压。发电机的额定电压比系
有备用接线包括双回路放射式、干线式、链式、环式和两端供电网络。放射式、干线式、链式 供电可靠性和电压质量高,但是不经济。环式供电可靠性较高但是运行调度复杂,故障时电压质量 差。两端供电网络供电可靠性较高但是要两个或两个以上独立电源。 1-8.标出下图所示电力系统各设备的额定电压。
G1:10.5kV;T1:一次侧 10.5kV,二次侧:121kV;T2:一次侧 110kV,二次侧:38.5kV
T3:一次侧 35kV,二次侧 6.3kV;T4:一次侧 10kV,二次侧 3.15kV;M:6kV;
2
第二章 电力系统各元件的特性和数学模型
1.思考题、习题
2-1.什么是发电机的功角特性?隐极式发电机和凸极式发电机的功角特性有何区别?
2-2.什么是变压器的短路试验和空载试验?从这两个试验中可确定变压器的哪些参数?
装消弧线圈,接地点的接地相电流中增加了一个感性分量,它和容性电流分量相抵消,减小接地点的电 流。使电弧易于熄灭,提高了供电可靠性。
补偿方式有欠补偿和过补偿,欠补偿就是感性电流小于容性电流的补偿方式,过补偿就是感性电流 大于容性电流的补偿方式。电力系统一般采用过补偿方式。因为随着网络的延伸,电流也日益增大,以 致完全有可能使接地点电弧不能自行熄灭并引起弧光接地过电压,所以一般采用过补偿。
第一章 电力系统的基本概念Fra bibliotek1.思考题、习题
1-1.电力网、电力系统和动力系统的定义是什么? 答:由变压器、电力线路等变换、输送、分配电能设备所组成的网络称为电力网。 把生产、输送、分配和消费电能的各种电气设备连接在一起组成的整体称为电力系统 。 发电厂的动力部分和电力系统合在一起称为动力系统。 1-2.对电力系统运行的基本要求是什么? 答:(1)保证可靠地的持续供电(2)保证良好的电能质量(3)保证系统运行的经济性。 1-3.何为电力系统的中性点?其运行方式如何?它们有什么特点?我国电力系统中性点运行情况 如何? 答:星型连接的变压器或发电机的中性点就是电力系统的中性点。中性点的运行方式有直接接地和 不接地以及中性点经消弧线圈接地。 直接接地供电可靠性低。系统中一相接地,接地相电流很大,必须迅速切除接地相甚至三相。不接 地供电可靠性高,对绝缘水平的要求也高。系统中一相接地时,接地相电流不大,但非接地相对地电压 升高为线电压。 我国 110kV 及以上的系统中性点直接接地,60kV 及以下系统中性点不接地。 1-4.中性点不接地的电力系统发生单相接地故障时,各相对地电压有什么变化?单相接地电流的 性质如何?怎样计算?
中性点不接地的电力系统发生单相接地故障时,接地相电压为 0,非接地相电压升高为原来的 3
倍,即升高为线电压。单项接地电流为容性。接地相的对地电容电流应为其它两非接地相电容电流之和,
其幅值为 3 倍非接地相对地电容电流,也就等于正常运行时一相对地电容电流的 3 倍。(可画向量图
来解释) 1-5.消弧线圈的工作原理是什么?补偿方式有哪些?电力系统一般采用哪种补偿方式?为什么? 消弧线圈就是电抗线圈。中性点不接地系统中一相接地时,接地点的接地相电流属容性电流,通过
2-3.双绕组和三绕组变压器一般以什么样的等值电路表示?双绕组变压器的等值电路与电力线路的等
值电路有何异同?
2-4.三相三绕组降压变压器的型号为 SFPSL-120000/220,额定容量为 120000/120000/60000/kVA,额
定电压为 220/121/11kV,Pk(1-2)=601kW,Pk(1-3)=182.5kW,Pk(2-3)=132.5kW,Uk(1-2)(%)=14.85, Uk(1-3)(%)=28.25, Uk(2-3)(%)=7.96,P0=135kW,I0(%)=0.663,求该变压器的参数,并做出等值电路。 2-4.三相三绕组降压变压器的型号为 SFPSL-120000/220,额定容量为 120000/120000/60000/kVA,额
GT
=
P0 1000U
2 N
=
135 1000 * 2202
= 2.79*10−6 S
BT
= I0 %SN 100U 2N
=
0.663*120 100 * 2202
=
16.4
*10−6
S
YT = GT − jBT = (2.79 − j16.4) *10−6 S
定电压为 220/121/11kV,Pk(1-2)=601kW,Pk(1-3)=182.5kW,Pk(2-3)=132.5kW,Uk(1-2)(%)=14.85, Uk(1-3)(%)=28.25, Uk(2-3)(%)=7.96,P0=135kW,I0(%)=0.663,求该变压器的参数,并做出等值电路。
1
统额定电压高 5%。变压器一次绕组额定电压=系统额定电压,只有与发电机直接相连的变压器的 一次绕组额定电压=发电机额定电压,变压器二次绕组额定电压比系统额定电压高 10%。只有漏抗 很小,二次测直接和用电设备相连的和电压特别高的变压器,其二次绕组额定电压比系统额定电压 高 5%。 1-7.电力系统的接线方式有哪些?各自的优、缺点有哪些? 答:无备用接线包括单回路放射式、干线式、链式。无备用接线简单、经济、运行方便,但是供电 可靠性差。
