卡巴斯基防病毒软件安装手册(本地版)
卡巴斯基linux手册

卡巴斯基linux手册卡巴linux 反病毒8.0快捷安装、配置手册安装准备:卡巴斯基linux反病毒8.0文件服务器版卡巴网络代理linux版本安装程序卡巴斯基linux产品管理插件SSH Secure Shell工具Key文件系统环境配置(本人使用suse linux 11):查看并配置ip地址配置gcc编译环境关闭防火墙注:新的卡巴斯基linux反病毒产品,提供KDE和Gnome 界面的支持,安装简便很多,可以图形化操作,这边主要说一下命令行的安装过程,以及如何通过卡巴管理工具管理linux主机产品安装:1、使用SSH Secure Shell工具连接到linux目的主机2、上传卡巴斯基linux反病毒8.0文件服务器版、卡巴网络代理linux版本安装程序、Key文件,3个文件到root目录。
3、安装网络代理( rpm -ivh /root/klnagent-8.5.0-643.i386.rpm)1)运行脚本/opt/kaspersky/klnagent/lib/bin/setup/postinstall.pl进入卡巴网络代理快速配置向导,按提示进行操作:2)需要进行如下配置a.指定的DNS名称或管理服务器的IP地址。
b.指定管理服务器的端口号或使用默认端口号(__)。
c.指定管理服务器或使用默认端口号(__)的SSL端口号。
d. SSL连接的定义,是否应该用于数据传输。
默认情况下,启用SSL连接。
4、安装卡巴反病毒程序(rpm -ivh /root/kav4fs-8.0.0-136.i386\ \(2\).rpm)1)运行脚本/opt/kaspersky/kav4fs/bin/kav4fs-setup.pl进入卡巴反病毒程序的快速配置向导,按提示进行操作:2)需要进行如下配置a.审查许可协议b.选择区域设置的c.安装授权(输入路径,如果授权加载不成功,可以通过管理工具推送授权)d.设置代理服务器e.下载病毒库f.预订更新时间g.配置实时保护(编译内核,需要提供内核路径,并配置gcc编译环境,不编译,实时保护无法开启)h.Samba服务器的设置实时保护i.设置web控制台密码j.启动实时保护任务5、管理WEB管理控制台服务(开启/etc/init.d/kav4fs-wmconsole start)6、访问Web管理控制台(端口号9080)7、在卡巴管理服务器上管理linux主机a.安装管理插件,并添加linux主机到管理组b.建立linux管理策略c.建立linux升级病毒库的任务d.建立linux病毒扫描任务8、Linux主机的策略和任务的设置(web控制的界面很简单,我这边主要说一下管理工具里linux主机的策略和任务的配置)设置项有4个,后面为保护区域和排除区域,主要的配置在保护区域进行,可以添加保护区域,设置不同的保护区域,并制定不同的保护规则依次是:区域、访问权限(添加帐户)、设置(设置扫描和保护)、处理动作(发现病毒如何处理)、排除区域和普通的windows 病毒扫描任务一样,需要设置后面三项:扫描区域、扫描设置、扫描时间。
卡巴斯基安装步骤

卡巴斯基说俄罗斯一款著名的网络版企业级杀毒软件,具备防病毒/杀毒/防火墙等多重功能。
可以提供对PC机和移动终端设备的防毒需求。
现在最新的版本是卡巴斯基网络版8.0,本文中测试所使用的版本是当前应用最广泛的卡巴斯基网络版6.0 。
以下内容摘录自官方文档:部署方案的选择取决于以下几个主要因素:l 企业网络结构:不同网段之间的传输速度,以及每个网段中的客户端计算机数量。
l 企业组织结构。
l IT部门中为反病毒保护系统提供维护服务的员工人数,以及员工的不同职责划分。
l 能够用于安装反病毒保护管理系统(管理服务器、更新代理)的现有硬件资源。
l 企业网络内能够分配给反病毒保护系统各功能组件之间进行通讯的网络通道的容量。
l 企业网络内允许用于执行关键管理操作的最长时间,如数据库更新包的发布和客户端计算机的策略更改。
反病毒保护的部署通常可以分为以下几个方案:l 一个管理服务器。
l 一个管理服务器和一些更新代理。
l 分级式管理服务器。
l 分级式管理服务器和一些更新代理。
建议采用以下步骤来分析网络和硬件架构:1.确定网络配置,以及将反病毒保护部署在何处。
其中主要的配置为:网络中的网段数。
每个网段之间的连接速度。
每个网段中管理的计算机数。
能够分配给反病毒保护系统各功能组件之间进行通讯的网络通道的容量。
2.确定对企业网络内所有管理的计算机,允许用于执行关键管理操作的最长时间。
3.使用收集到的信息,确定以下问题:管理所有的客户端计算机,需要多少台管理服务器?是否需要使用分级式管理服务器?理服务器要在允许的时间内对所有客户端计算机进行维护,需要怎样的硬件配置?为了减轻网络流量压力,是否需要中间层的更新数据库和安装包发布中心(更新代理)?在回答完以上问题后,管理员应该能够列出一些可选的部署方案,并从其中选出最适合的。
当我们确定了最合适的部署方式之后,下面就可以开始卡巴斯基的部署了。
首先我们来部署卡巴斯基的管理工具。
卡巴斯基管理工具由以下三个主要部分组成:l 管理服务器执行信息的集中化存储功能,这些信息包括:企业网络中所有已安装的卡巴斯基实验室产品信息,和这些程序的管理信息。
计算机技术使用中的防病毒软件安装步骤

计算机技术使用中的防病毒软件安装步骤随着计算机技术的发展,我们每天都在使用计算机进行各种操作,这也使得我们的计算机更加容易受到病毒的侵害。
为了保护计算机的安全,防病毒软件成为了必备的工具之一。
在本文中,将为您详细介绍计算机技术使用中的防病毒软件安装步骤。
首先,在安装防病毒软件之前,我们需要选择一款可靠、兼容性好的软件。
对于普通用户来说,常见的防病毒软件有卡巴斯基、诺顿、金山毒霸等。
可以根据自己的需求和喜好来选择。
一般来说,网络上会有许多关于防病毒软件的评测和排行榜,可以参考一下这些信息来做出选择。
一旦选择了适合的防病毒软件,接下来就是正式的安装步骤。
首先,在官方网站下载防病毒软件的安装包。
注意要从官方渠道下载,避免从不可信的网站下载,以免下载到带有病毒的安装包。
下载完成后,双击运行安装包。
在运行安装程序之前,系统可能会提示您授予程序管理员权限,以便进行安装。
点击“是”或者“是(Y)”按钮,以确保能够顺利进行后续的安装操作。
接下来,安装程序将会展示软件的许可协议。
仔细阅读这些协议,如果您同意其中的条款,请点击“我接受”或者“同意”按钮,继续进行安装。
如果您不同意某些条款,可以选择取消安装。
安装程序之后,将会询问您选择软件的安装路径或者使用默认的安装路径。
如果您希望将软件安装在其他位置,可以点击“浏览”按钮选择相应的文件夹路径,否则可以直接点击“下一步”或者“继续”按钮继续使用默认的安装路径。
在确认安装路径后,安装程序可能会询问您是否要安装附加组件。
附加组件可以提供一些额外的功能,如浏览器的插件、系统清理工具等。
根据自己的需要选择是否安装这些组件,然后点击“下一步”或者“继续”按钮。
安装过程可能需要一些时间,请耐心等待。
安装完成之后,防病毒软件将会自动启动,并进行一些初始化设置。
根据软件的提示,您可能需要注册账号、进行在线更新等操作,以确保软件能够正常工作。
完成这些设置后,防病毒软件将会开始进行全盘扫描,并对计算机中的病毒进行清理和隔离。
SEP客户端安装操作手册

SEPM客户端安装操作手册赛门铁克软件(北京)有限公司2010年1月页脚内容1文档属性文档变更页脚内容2第1章............................................................................ 客户端安装综述6第2章 ........................................................................... 客户端安装要求72.1 ......................................................................................... 客户端运行系统/硬件要求72.2 .......................................................................................... 客户端安装软件环境要求82.3 ..................................................................................................................... 权限要求92.4 ........................................................................................ SEP安装包功能及系统要求9页脚内容3第3章 ........................................................ 客户端安装步骤(全新安装)123.1 ........................................................................................... 检查客户端系统配置状况123.2 ...................................................................................................... 获取客户端安装包133.3 ................................................................................................................. 安装客户端143.4 ..........................................................................................................客户端安装验证16第4章 .................................. 客户端安装步骤(替换原非SEP防病毒软件)194.1 ................................................................................................... 检查客户端配置状况194.2 ........................................................................... 卸载第三方防病毒或者防火墙软件204.3 ...................................................................................................... 获取客户端安装包214.4 ................................................................................................................. 安装客户端22页脚内容44.5 ..........................................................................................................客户端安装验证24第5章 ..................................................................................... 问题处理27页脚内容5第1章客户端安装综述由于辽宁移动防病毒系统部署的现状不同,此次 SEP客户端的部署安装方式针对不同情况有不同的安装部署方式。
Symantec杀毒软件安装步骤
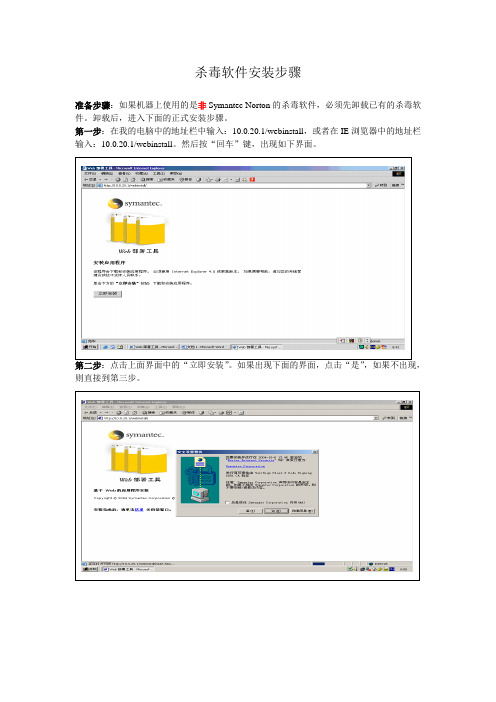
杀毒软件安装步骤
准备步骤:如果机器上使用的是非Symantec Norton的杀毒软件,必须先卸载已有的杀毒软件。
卸载后,进入下面的正式安装步骤。
第一步:在我的电脑中的地址栏中输入:10.0.20.1/webinstall,或者在IE浏览器中的地址栏输入:10.0.20.1/webinstall。
然后按“回车”键,出现如下界面。
第二步:点击上面界面中的“立即安装”。
如果出现下面的界面,点击“是”,如果不出现,则直接到第三步。
第三步:出现下面界面时,点击“下一步”。
第四步:当出现下面界面是,点击并选择“我接受……”选项后,点击“下一步”。
第五步:当出现下面界面时,选择“完全”,然后点击“下一步”。
第六步:当出现下面界面时,点击“安装”。
第七步:当出现下面界面时,点击“完成”。
第八步:大部分机器,出现下面界面,需要重新启动,点击“是”,重新启动即可。
第九步:安装完成后,桌面的右下角出现黄色盾牌形状的图标(名称为:symantec-antivirus),此即为杀毒软件防护程序。
双击黄色盾牌,显示以下界面。
安装后,界面中的程序应显示为:10.1.X.X,病毒定义文件版本为最近一周内的日期。
今后,所有安装的计算机会自动进行更新病毒定义,不必人工操作。
如果安装后发现病毒的计算机,请点击下面第二个界面中的“全面扫描”进行计算机杀毒扫描。
业务科2006.11.27。
卡巴斯基授权文件的安装方法
卡巴斯基授权文件的安装方法(卡巴斯基KEY被打入黑名单的解决方法)使用网上下载的卡巴斯基的用户经常会遇到授权文件被打入黑名单的(因为你不是付费用户,没出过一分钱),下面的方法可以解这个问题。
一、弄清楚自己使用的版本卡巴斯基的版本有很多种,通常所见到的是KA V和KIS两种:卡巴斯基反病毒软件7.0 这个就是我们所说的(KA V7)了。
卡巴斯基互联网安全套装7.0 这个就是我们所说的(KIS7)了。
卡巴斯基反病毒软件2009 这个就是我们所说的(KA V8)了。
卡巴斯基全功能安全软件2009 这个就是我们所说的(KIS8)了。
卡巴斯基反病毒软件2010 这个就是我们所说的(KA V9)了。
卡巴斯基全功能安全软件2010 这个就是我们所说的(KIS9)了。
以上是文字说明,我再来抓图给大家分辨。
二、下载卡巴斯基的授权文件(即key)网上有很多网站都有卡巴斯基的授权文件下载,但一定要下载那些最新的key。
其中,中国杀毒网里面就经常会发布一些最新的key。
网址是/,还有另一个网“久要卡巴”,网址是/。
在这些网页中找到最新的授权文件下载地址,点击其链接并下载。
下载得来的往往是压缩文件,首先要将其解压出来,对应自己的卡巴斯基版本,把自己所用版本的key保留下来(可要记得要针对自己所用的版本啊)。
其余的(没用的)都把它删除掉。
如下图所示的,就是KIS 8.0的授权文件:三、卡巴斯基的授权文件(即key)的删除及安装卡巴斯基的授权文件(即key)被打入黑名单之后,这旧的授权文件就要先删除掉,然后再添加新的授权文件(即上面第二步所说的那些可用的最新key)。
下面以KIS 8.0为例说明一下授权文件(即key)的删除及安装方法,这方法对于其它版本的也同样适用。
卡巴斯基KIS 8.0 KEY 安装方法:点击“激活”选项(下图红色框),要是8.0版本的则点击“许可”选项然后先删除以前的KEY ,即点击“添加/删除”(注意:如果没有删除选项,则跳过此步骤)点击“添加/删除”选项之后,将出现下图的界面,然后就点击“删除授权许可文件”再点击“是”这样,原来的授权文件就已经删除掉了。
Kaspersky IT安全手册说明书

Hunting the huntersLearn more on #bringonthefuture A systemic approach to protectionIntroductionAs corporate processes undergo extensive, across-the-board automation, businesses are becoming increasingly dependent on information technologies. This, in turn, means the risks associated with disruption to core business processes are steadily shiftingto the IT field. The developers of automation tools are aware of this and, in an attempt to address possible risks, are increasingly investing in IT security – a key characteristic of any IT system along with reliability, flexibility and cost. The last couple of decades have seen a dramatic improvement in the security of software products - virtuallyall global software manufacturers now publish documents dedicated to safety configurations and the secure use of their products, while the information security market is flooded with offers to ensure protection in one form or another.On the flipside, the more a company’s business is dependent on IT, the more attractive the idea of hacking its information systems, justifying any additional investmentin resources required to carry out a successful attack in the face of increased IT security levels.A systemic approach to protectionIncreased software security levels and constantly evolving protection technologies make mounting a successful attack more challenging. So cybercriminals, having invested in penetrating multiple layers of defenses, want to spend plenty of time inside the target infrastructure, maximizing their profits by doing as much damage as possible. Hencethe emergence of targeted attacks.These attacks are carefully planned and implemented - along with automated tools, they require the direct and deep involvement of professional attackers to penetrate the systems. Counteracting these professional attackers can only be undertaken effectively by professionals who are no less qualified and who are equippedwith the latest tools for detecting and preventing computer attacks.From a risk management standpoint, an organization’s security goals are considered achieved when the cost to the attacker of compromising the system exceeds the value to that attacker of the information assets gained. And, as we’ve said, penetrating multiple security layers is expensive and challenging. But there is a way of dramatically cutting the costs of an advanced attack, while almost certainly remaining undetected by built-in security software. You simply incorporate a combination of widely known legitimate tools and techniques into your advanced attack armory.Today’s operating systems actually contain everything needed to attack them, without having to resort to malicious tools, dramatically cutting the cost of hacking. This ‘dual functionality’ of OS built-in tools is what system administrators work with, so distinguishing their legitimate activities from those of a threat actor is very difficult, and virtually impossible through automation alone. The only way to counter such threats is to adopt a systemic approach to protection (Figure 1). This implies prompt detection if a threat is impossible to prevent, and if automatic detection is impossible, then having proactiveHiding in plain sightAt Kaspersky, we can say with a degree of confidence that the list of threat detection and prevention technologies we’ve developed over the years, including the latest research on big data and machine learning, means our security products can neutralize any attack that can be detected and prevented automatically. But automatic detection and prevention is just the beginning. More than 20 years of researching and preventing computer attacks have given us an even more powerful tool to tackle those areas when automation just isn’t enough – unequalled human expertise.Targeted attacks take the protection tools available to their victims into consideration and are developed accordingly, bypassing automatic detection and prevention systems. These kinds of attack are often carried out without any software being used, and the attackers’ actions are barely distinguishable from those that an ITor information security officer would normally perform.The following are just some of the techniques applied in today’s attacks:• The use of tools to hamper digital forensics, e.g. by securely deleting artefactson the hard drive or by implementing attacks solely within a computer’s memory• The use of legitimate tools that IT and information security departments routinely use • Multi-stage attacks, when traces of preceding stages are securely deleted• Interactive work by a professional team (similar to that used during penetration testing)Such attacks can only be identified after the target asset has been compromised,as only then can suspicious behavior indicative of malicious activity be detected. A key element here is the involvement of a professional analyst. A human presence withinthe event analysis chain helps compensate for weaknesses inherent in automated threat detection logic. And when pentest-like attacks involve an active human attacker, that human undoubtedly has an advantage when it comes to bypassing automated technologies. The opposing presence of a suitable armed human analyst then becomes the only sure way to counter the attack.IT security talent crunchMeanwhile, IT security personnel recruitment is at crisis levels. The number of unfilled positions globally stands at 4.07 million, up from 2.93 million this time last year.The growing demand for IT security expertise also means that it’s tough not justto find skilled professionals, but also to justify the high costs involved in hiring them. So if you don’t currently have a full complement of security specialists for threat hunting, investigation and response, it’s no good banking on being able to attract more. You need to find another way.Managed Detection and Response (MDR) products and services can be an effective solution for organizations seeking to establish and to improve their early, effective threat detection and response but lacking sufficient internal expert IT security resources (Figure 2). Outsourcing skills-hungry security tasks, e.g. threat hunting, to an experiencedThe needle in the haystackThe Kaspersky SOC continuously monitors more than 250k endpoints worldwide, and this number is constantly growing. We collect and process a huge amount of telemetry from each of these sensors. While the majority of threats are detected and prevented automatically, and only a small number of them go to human validation, the amount of raw telemetry requiring additional review is still enormous, and analyzing all this manually to provide threat hunting to customers in the form of an operational service would be impossible. The answer is to single out for further review by the SOC analyst those raw events which are in some way related to known (or even just theoretically possible) malicious activity.In our SOC, we call these types of event ‘hunts’, officially known as ‘Indicators of Attack’ or IoAs, as they help to automate the threat hunting process. IoA creation is an art, and like most art forms there’s more to it than just systematic performance. Questions need to be asked and answered, like ‘Which techniques need detecting as a priority, and which can wait a little?’ or ‘Which techniques would a real attacker be most likely to use’? This is where a knowledge of adversary methods is of so much value.Kaspersky identifies almost half of all incidents through the analysis of malicious actions or objects detected using IoAs, demonstrating the general efficiency of this approach in detecting advanced threats and sophisticated malware-less attacks. However, the more a malicious behavior mimics the normal behavior of users and administrators, the higher the potential rate of false positives and, consequently, the lower the conversion rate from alerts. So this is something that needs to be addressed.Jumping the queueAdvanced attackers often use the same tools, from the same workstations, addressing the same systems, and at the same time intervals as a real system administrator would – with no anomalies, no outliers - nothing. Faced with this, only a human analyst can make the final decision, attributing observed activity as malicious or legitimate, or even doing something as simple as asking the IT staff if they really performed these actions.However, SOC analysts can only work with finite throughput. As a human analyst is needed to verify and prioritize automatic detections for further investigation and response, it’s very important to determine as soon as possible whether the observed behavior is normal for a particular IT infrastructure. Having a baseline for what’s normal activity will help reduce the number of false alerts and raise the effectiveness of threat detection.High false positive rates and significant alert flows requiring verification and investigation can significantly affect the mean-time-to-respond to real incidents. This is where Machine Learning (ML) comes in. ML models can be trained on alerts previously validated and labeled by SOC analysts. By providing alerts with specific scoring ML model can assist with prioritization, filtering, queuing and so on. Kaspersky’s proprietary ML model enables the automation of the initial incident triage and minimizes the mean-time-to-respond by significantly increasing analyst throughput.IoA-based detection is applied to post-exploitation activity, where the tools used by attackers are not explicitly malicious, but their hostile usage is. Standard but suspicious functionality is identified in legitimate utilities, where classifying the observed behavior as malicious through automation would be impossible.Examples of IoAs:• Start command line (or bat/PowerShell) script within a browser, office application or server application (such as SQL server, SQL server agent, nginx, JBoss, Tomcat, etc.);• Suspicious use of certutil for file download (example command: certutil -verifyctl -f -split https[:]///wce.exe);• File upload with BITS (Background Intelligent Transfer Service);• whoami command from SYSTEM account, and many others.The devil is in the detailAlerts from protected assets require correlation as attackers move laterally from host to host. To define the most effective response strategy, it’s important to identify all affected hosts and gain complete visibility into their actions. In some cases, additional investigation may be required. Analysts gather as much context as possible to determine the severity of an incident. Incident severity is based on a combination of factors, including threat actor, attack stage at the time of incident detection (e.g. cyber kill chain), the number and types of assets affected, details about the threat and how it may be relevant to a customer’s business, the identified impact on infrastructure, complexity of remediation measures and more. To understand what’s actually going on, you need to maintain access to continuously updated knowledge about your attackers, their motivation, their methods and tools, and the potential damage they could inflict. Generating this intelligence requires constant dedication and high levels of expertise.Kaspersky SOC analyzes the received data utilizing all our knowledge about tactics, techniques and procedures used by adversaries worldwide (Figure 3). We gather information from constant threat research, the MITRE ATT&CK knowledge base, dozens Pulling the switchOnce the response strategy is defined, it’s time to take action. Usually, MDR services end here. Customers receive incident reports with response recommendations – then it’s their responsibility to apply them to their systems. Considering that a lack of IT security expertise may have caused the customer to opt for MDR in the first place, and the fact that such recommendations can be highly technical and not always clear and actionable, timely and effective response may be jeopardized. Absence of a centralized automated response capability adds to the problem significantly, compromising the potential benefits gained from such engagements.Kaspersky MDR relies on leading-edge security technologies based on unique ongoing threat intelligence and advanced machine learning. It automatically prevents the majority of threats while validating all product alerts to ensure the effectiveness of automatic prevention, and proactively analyzes system activity metadata for any signs of an active or impending attack. Our MDR shares the same agent with Kaspersky Endpoint Detection and Response and Kaspersky Sandbox, providing extended functionality once activated. The agent allows infected hosts to be isolated, unauthorized processes to be terminated, and malicious files to be quarantined and deleted – all done remotely at a single click.Depending on your requirements, the service offers a completely managed or guided disruption and containment of threats, while keeping all response actions under your full control. Incident response guidelines are actionable and delivered in plain English allowing for quick and effective execution. Kaspersky MDR customers can use the functionality of the EDR agent to centrally initiate recommended response actions themselves, or authorize Kaspersky to automatically launch remote incident response for certain types of incidents.KASPERSKYAnalysis workflow:•Situational awareness •Investigation of borderline cases•Overall process improvement Macro correlation, hypotheses:All TTP knowledge:•MITRE ATT&CK •Internal research •Security assessment/red teaming •Incident response practice•Security monitoring practiceCUSTOMERMicro correlation:•All EPP and network detection technologies •Reputation (through cloud)AUTOMATED AND GUIDED INCIDENTRESPONSEFigure 3. Incident analysis flow in Kaspersky MDRConclusionNeither automated threat detection and prevention tools nor cyberthreat hunting alone is a silver bullet for the entire spectrum of today’s threats. However, a combinationof traditional detection and prevention tools activated before a compromise occurs, plus a post-compromise iterative process of searching for new threats missed by automated tools, can be highly effective. Kaspersky Managed Detection and Response maximizes the value of your Kaspersky security solutions by delivering fully managed, individually tailored ongoing detection, prioritization, investigation and response.Countering targeted attacks requires extensive experience as well as constant learning. As the first vendor to establish, almost a decade ago, a dedicated center for investigating complex threats, Kaspersky has detected more sophisticated targeted attacks than any other security solution provider. Leveraging this unique expertise, you can gain allthe major benefits from having your own Security Operations Center without havingto actually establish one. 2021 A O K A S P E R S K Y L A B . R E G I S T E R E D T R A D E M A R K S A N D S E R V I C E M A R K S A R E T H E P R O P E R T Y O F T H E I R R E S P E C T I V E O W N E R S .Cyber Threats News: IT Security News: /。
卡巴斯基客户端安装说明手册

杀毒软件安装说明手册卡巴斯基花桥华拓数码科技(昆山)有限公司系统运维部版本V1.0 2016-1-25目录一. 安装前确认事项二. 卡巴斯基杀毒软件安装一. 安装前确认事项说明:①本次的软件安装针对所有需要使用公司台式电脑;②安装软件前请先卸载本地杀毒软件(如360杀毒软件,包括注册表);③如果因电脑硬件设施过旧导致系统操作缓慢的,建议更换硬件设施。
④Windows8和Windows10系统安装10.2版本卡巴,其他Windows系统安装10.0版本卡巴。
1.系统版本确认:•请确认电脑系统版本为WindowsXP、Windows7、Windows2003、Windows2008、Windows8、Window10 •如果电脑不是以上系统版本,请自行更换系统。
2.删除360safe注册表项•依次单击“开始”、“运行”,键入regedit,然后单击“确定”。
•删除[HKEY_CURRENT_USER\SOFTWARE]目录下的360safe项二. 卡巴斯基杀毒软件安装1. 卡巴斯基获取地址从FTP共享文件夹“K卡巴斯基”或者从每个管理端的共享文件夹“Packages“中下载至本地电脑FTP地址:ftp://172.16.16.16账号:admin密码:*********共享地址:\\172.16.99.9(172.16.1.246)\\172.16.99.40(172.16.1.243)\\172.16.99.7(172.16.1.251)\\172.16.99.140(10.1.101.10)\\172.16.99.145(10.1.101.11)账号:administrator 密码:*********2. 卡巴斯基安装步骤说明:完整版卡巴斯基包括应用程序(KES_10.1.0.867)和网络代理(NetAgent_10.0.3361)第一步:安装应用程序(KES_10.1.0.867),打开软件,进入安装界面说明:服务器地址在项目上线之前告知二. 卡巴斯基杀毒软件安装第六步:标签栏填写客户端应属管理组说明:10.2版本相比10.0版本新增代理标签功能,安装时在标签栏填写客户端应属的管理组,客户端安装完成之后管理端自动将客户加入对应的管理组,无需再登陆管理端手动添加客户端,很好的提高工作效率第七步:单击下一步第八步:单击完成,网络代理安装完成。
