CISCO网络组网工程配置案例_
Cisco基于策略路由的配置实例

问题描述您可以定义自己的规则来进行数据包的路由而不仅仅由目的地地址所决定。
在这里您可以学到怎么使用基于策略路由的办法来解决这一问题。
在具体的应用中,基于策略的路由有:☆基于源IP地址的策略路由☆基于数据包大小的策略路由☆基于应用的策略路由☆通过缺省路由平衡负载这里,讲述了第一种情况的路由策略。
举例在这个例子中,防火墙的作用是:把10.0.0.0/8内部网地址翻译成可路由的172.16 .255.0/24子网地址。
下面的防火墙配置是为了完整性而加进去的,它不是策略路由配置所必需的。
在这里的防火墙可以被其它类似的产品代替,如PIX或其它类似防火墙设备。
这里的防火墙的配置如下:!ip nat pool net-10 172.16.255.1 172.16.255.254 prefix-length 24ip nat inside source list 1 pool net-10!interface Ethernet0ip address 172.16.20.2 255.255.255.0ip nat outside!interface Ethernet1ip address 172.16.39.2 255.255.255.0ip nat inside!router eigrp 1redistribute staticnetwork 172.16.0.0default-metric 10000 100 255 1 1500!ip route 172.16.255.0 255.255.255.0 Null0access-list 1 permit 10.0.0.0 0.255.255.255!end在我们的例子中,Cisco WAN路由器上运行策略路由来保证从10.0.0.0/8网络来的P数据包被发送到防火墙去。
配置中定义了两条net-10策略规则。
第一条策略就定义了从10.0.0.0/8网络来的IP数据包被发送到防火墙去(我们很快会看到这里的配置有问题)。
Cisco组建中小型企业网络实例
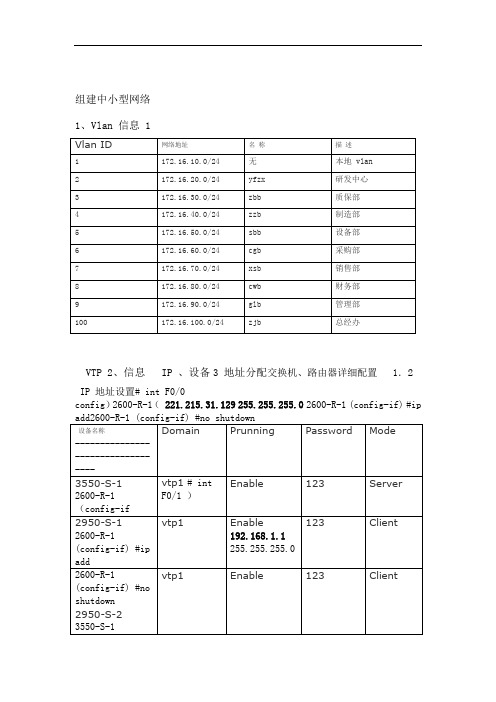
组建中小型网络1、Vlan 信息 1VTP 2、信息 IP 、设备3 地址分配交换机、路由器详细配置 1.2IP 地址设置# int F0/0config)2600-R-1( 221.215.31.129 255.255.255.0 2600-R-1 (config-if) #ip3550-S-1 (config-if) # ip add 172.16.10.1 if) # int vlan 2……………研发中心3550-S-1 (config- 255.255.255.02. (config-if) 3550-S-1 int vlan 3……………质保部(config-if)3550-S-1 255.255.255.0 172.16.30.1ip add(config-if) 3550-S-1 int vlan 4……………制造部(config-if) 3550-S-1 255.255.255.0 ip add172.16.40.1(config-if) 3550-S-1 int vlan 5……………设备部(config-if) 3550-S-1 255.255.255.0 ip add 172.16.50.1(config-if) 3550-S-1 int vlan 6……………采购部(config-if) 3550-S-1 255.255.255.0 ip add172.16.60.1(config-if) 3550-S-1 int vlan 7……………销售部(config-if) 3550-S-1 255.255.255.0 172.16.70.1ip add(config-if) 3550-S-1 int vlan 8……………财务部(config-if) 3550-S-1 255.255.255.0172.16.80.1ip add(config-if) 3550-S-1 int vlan 9……………管理部(config-if) 3550-S-1 255.255.255.0 172.16.90.1ipadd(config-if)3550-S-1 int vlan 100…………总经办(config-if)3550-S-1 255.255.255.0 172.16.100.1ip add 配置VTP3550-S-1 # vlan database3550-S-1 (vlan) # vtp domain vtp13550-S-1 (vlan) # vtp server3550-S-1 (vlan) # vtp password 1233550-S-1 (vlan) # vtp pruning……………………………..修剪 3550-S-1 (vlan) # vlan 2 name yfzx………………………..研发中心 3550-S-1 (vlan) # vlan 3 name zbb………………………..质保部 3550-S-1 (vlan) # vlan 4 name zzb…………………………制造部 1 (vlan) # vlan 5 name sbb…………………………设备部3550-S- 1 (vlan) # vlan 6 name cgb…………………………采购部3550-S- 销售部3550-S-1 (vlan) # vlan 7 name xsb………………………# vlan 8 name xsb………………………...财务部3550-S-1 (vlan) …………………………管理部3550-S-1 (vlan) # vlan 9 namexsb-----------------------------------------------------------2950-S-1 (vlan) #vtp domain vtp1)(配置修改编号清零2950-S-1 (vlan) #vtp tran…………………透明模式客户模式2950-S-1 (vlan) #vtp client2950-S-1 (vlan) #vtp password 1232950-S-2 (vlan) #vtp domain vtp1)配置修改编号清零2 (vlan) #vtp tran…………………透明模式(2950-S-客户模式2950-S-2 (vlan) #vtp client2950-S-2 (vlan) #vtp password 1232950-S-3 (vlan) #vtp domain vtp1)(3 (vlan) #vtp tran…………………透明模式配置修改编号清零2950-S-客户模式2950-S-3 (vlan) #vtp client 3. 2950-S-3 password 123 (vlan) #vtp2950-S-4 domain vtp1(vlan) #vtp 2950-S-4 tran…………………透明模式(#vtp 配置修改编号清零(vlan) )客户模式client2950-S-4 #vtp (vlan)password 123#vtp 2950-S-4(vlan)3.路由配置2600-R-1(config)# ip route 0.0.0.0 0.0.0.0 f0/2……………...缺省路由2600-R-1(config)# ip route 192.168.0.0 255.255.0.0 192.168.1.2 3550-R-1 (config) # ip route 0.0.0.0 0.0.0.0 192.168.1.1 4.5. NAT 2600-R-1(config)# access-list 101 permit ip 192.168.0.00.0.255.255 192.168.0.00.0.255.255……………………………...内部局部地址2600-R-1(config)# ip nat pool WAN 221.215.31.131221.215.31.134 prefix-len 29 ………………………………定义合法 IP 地址池2600-R-1(config)# ip nat inside sour list 101 pool WAN ……….实现地址转换2600-R-1(config)# int f0/12600-R-1(config-if)#ip nat inside………………………….定义 NAT inside 2600-R-1(config)# int f0/02600-R-1(config-if)# ip nat outside………………………..定义 NAT outside 端口Vlan 流量控制制造部、设备部 vlan 实现互访,禁止访问其它部门 vlan制造部、设备部上班时间禁止访问 internet(8:00-12:00 2:00-6:00)研发中心、质保部 vlan 实现互访,禁止访问其它部门 vlan财务部 vlan 实现与采购部、销售部 vlan 的单向访问总经办 vlan 实现与财务部、管理部 vlan 的单向访问管理部 vlan 禁止访问其它部门 vlan各部门 vlan 都能访问服务器区3550-S-1(config) # time-range restrict3550-S-1(config-time-range) # periodic daily start 12:00 to 2:00 ……….设置时间范围3550-S-1 (config) # ip access-list extend yfzx……….研发中心 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.20.00.0.0.255…...….访问质保部4.3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any3550-S-1 (config) # ip access-list extend zbb……….质保部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.10.00.0.0.255…...….访问研发中心3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any-------------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend zzb……….制造部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.40.00.0.0.255…...….访问设备部3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any time-range restrict ……….上班时间禁止上网3550-S-1 (config) # ip access-list extend sbb……….设备部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.30.0 0.0.0.255 …...….访问制造部3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any-----------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend cgb……….采购部 ACL3550-S-1 (config-ext-nacl) # evaluate cwb-cgb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2555.3550-S-1 (config-ext-nacl) #permit ip any any----------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend xsb……….销售部 ACL3550-S-1 (config-ext-nacl) # evaluate cwb-xsb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2553550-S-1 (config-ext-nacl) #permit ip any any---------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend cwb……….财务部 ACL3550-S-1 (config-ext-nacl) # permint ip any 172.16.60.00.0.0.255 reflect cwb-cgb ………...创建自反 ACL cwb-cgb3550-S-1 (config-ext-nacl) # permint ip any 172.16.70.00.0.0.255 reflect cwb-xsb ………...创建自反 ACL cwb-xsb3550-S-1 (config-ext-nacl) # evaluate zjb-cwb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any--------------------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend cwb……….管理部 ACL3550-S-1 (config-ext-nacl) # evaluate zjb-glb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any----------------------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend zjb……….总经办 ACL3550-S-1 (config-ext-nacl) # permint ip any 172.16.80.00.0.0.255 reflect zjb-cwb ………...创建自反 ACL zjb-cwb3550-S-1 (config-ext-nacl) # permint ip any 172.16.90.00.0.0.255 reflect zjb-glb ………...创建自反 ACL zjb-glb3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 6.………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any anyACL 应用:3550-S-13550-S-1 (config) # int vlan 2 …………..研发中心3550-S-1 (config-if) #ip access-group yfzx in3550-S-1 (config) # int vlan 3 …………..质保部3550-S-1 (config-if) #ip access-group zbb in3550-S-1 (config) # int vlan 4 ……………制造部(config-if) #ip access-group zzb in…(略)附:关键字 established 的 ACL 应用(单向访问)3550-S-1 (config) # ip access-list extend cgb……….采购部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.80.0 0.0.0.0.255 estab3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2553550-S-1 (config-ext-nacl) #permit ip any any3550-S-1 (config) # ip access-list extend xsb……….销售部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.80.0 0.0.0.0.255 estab3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2553550-S-1 (config-ext-nacl) #permit ip any any1、Vlan 信息 7网络地址名称描述Vlan ID无本地 vlan 172.16.10.0/24 1研发中心 yfzx2172.16.20.0/24VTP 2、信息 IP 、设备3交换机、路由器详细配置地址分配.18IP 地址设置)# int F0/0 (config2600-R-1质保部zbb3 172.16.30.0/24 221.215.31.129 255.255.255.02600-R-1 (config-if) #ip add制造部zzb4 172.16.40.0/24设备部sbb 5 172.16.50.0/24采购部cgb 172.16.60.0/24 6销售部xsb 7 172.16.70.0/24财务部cwb 172.16.80.0/24 8管理部glb 9 172.16.90.0/24总经办zjb100172.16.100.0/24IP描述接口设备名称地址F0/0 WAN 221.215.31.129/29 2600-R-1 - 192.168.1.1/24 F0/13L-Switch192.168.1.2/243550-S-1F0/12600-R-1 (config-if) #no shutdown----------------------------------2600-R-1(config-if)# int F0/12600-R-1 (config-if) #ip add 192.168.1.1 255.255.255.02600-R-1 (config-if) #no shutdown3550-S-1 (config) # int F0/13550-S-1 (config-if) # no switchport……….路由端口3550-S-1 (config-if) # ip add 192.168.1.2 255.255.255.03550-S-1 (config) # int vlan 1 ……………..管理 vlan3550-S-1 (config-if) # ip add 192.168.10.1 255.255.255.03550-S-1 (config-if) # int vlan 2……………研发中心3550-S-1 (config-if) # ip add 192.168.20.1 255.255.255.03550-S-1 (config-if) # int vlan 3……………质保部3550-S-1 (config-if) # ip add 192.168.30.1 255.255.255.03550-S-1 (config-if) # int vlan 4……………制造部3550-S-1 (config-if) # ip add 192.168.40.1 255.255.255.03550-S-1 (config-if) # int vlan 5……………设备部3550-S-1 (config-if) # ip add 192.168.50.1 255.255.255.03550-S-1 (config-if) # int vlan 6……………采购部3550-S-1 (config-if) # ip add 192.168.60.1 255.255.255.03550-S-1 (config-if) # int vlan 7……………销售部3550-S-1 (config-if) # ip add 192.168.70.1 255.255.255.03550-S-1 (config-if) # int vlan 8……………财务部3550-S-1 (config-if) # ip add 192.168.80.1 255.255.255.03550-S-1 (config-if) # int vlan 9……………管理部3550-S-1 (config-if) # ip add 192.168.90.1 255.255.255.03550-S-1 (config-if) # int vlan 100…………总经办3550-S-1 (config-if) # ip add192.168.100.1255.255.255.0 2.9 VTP 配置# vlan database config)3550-S-1(3550-S-1 (vlan) # vtp domain vtp13550-S-1 (vlan) # vtp server3550-S-1 (vlan) # vtp password 123vtp pruning……………………………..修剪3550-S-1 (vlan) #1 (vlan) # vlan2 name yfzx………………………..研发中心3550-S- 3550-S-1 (vlan) # vlan3 name zbb………………………....质保部 1 (vlan) # vlan4 name zzb…………………………制造部3550-S- 1 (vlan) # vlan5 name sbb…………………………设备部3550-S- 3550-S-1 (vlan) # vlan6 name cgb…………………………采购部 3550-S-1 (vlan) # vlan7 name xsb…………………………销售部 3550-S-1 (vlan) # vlan8 name xsb……………………….....财务部 1 (vlan) # vlan9 name xsb…………………………管理部3550-S------------------------------------------------------------2950-S-1 (vlan) #vtp domain vtp12950-S-1 (vlan) #vtp tran…………………透明模式(配置修改编号清零)客户模式2950-S-1 (vlan) #vtp client2950-S-1 (vlan) #vtp password 1232950-S-2 (vlan) #vtp domain vtp12950-S-2 (vlan) #vtp tran…………………透明模式(配置修改编号清零)客户模式2950-S-2 (vlan) #vtp client2950-S-2 (vlan) #vtp password 1232950-S-3 (vlan) #vtp domain vtp12950-S-3 (vlan) #vtp tran…………………透明模式(配置修改编号清零)客户模式2950-S-3 (vlan) #vtp client2950-S-3 (vlan) #vtp password 1232950-S-4 (vlan) #vtp domain vtp12950-S-4 (vlan) #vtp tran…………………透明模式(配置修改编号清零)客户模式2950-S-4 (vlan) #vtp client2950-S-4 (vlan) #vtp password 1233.路由配置2600-R-1(config)# ip route 0.0.0.0 0.0.0.0 f0/2……………...缺省路由2600-R-1(config)# ip route 192.168.0.0 255.255.0.0 192.168.1.23550- R -1 (config) # ip route 0.0.0.0 0.0.0.0 192.168.1.1 .45. NAT 2600-R-1(config)# access-list 101 permit ip 192.168.0.00.0.255.255 192.168.0.00.0.255.255……………………………...内部局部地址2600-R-1(config)# ip nat pool WAN 221.215.31.131221.215.31.134 prefix-len 29 ………………………………定义合法 IP 地址池2600-R-1(config)# ip nat inside sour list 101 pool WAN ……….实现地址转换2600-R-1(config)# int f0/12600-R-1(config-if)#ip nat inside………………………….定义 NAT inside 2600-R-1(config)# int f0/02600-R-1(config-if)# ip nat outside………………………..定义 NAT outside 端口Vlan流量控制制造部、设备部 vlan 实现互访,禁止访问其它部门 vlan制造部、设备部上班时间禁止访问 internet(8:00-12:00 2:00-6:00)研发中心、质保部 vlan 实现互访,禁止访问其它部门 vlan财务部 vlan 实现与采购部、销售部 vlan 的单向访问10.总经办 vlan 实现与财务部、管理部 vlan 的单向访问管理部 vlan 禁止访问其它部门 vlan各部门 vlan 都能访问服务器区3550-S-1(config) # time-range restrict3550-S-1(config-time-range) # periodic daily start 12:00 to 2:00 ……….设置时间范围3550-S-1 (config) # ip access-list extend yfzx……….研发中心 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.20.00.0.0.255…...….访问质保部3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any3550-S-1 (config) # ip access-list extend zbb……….质保部 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.10.00.0.0.255…...….访问研发中心3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any-------------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend zzb……….制造部 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.40.00.0.0.255…...….访问设备部3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any time-range restrict ……….上班时间禁止上网3550-S-1 (config) # ip access-list extend sbb……….设备部 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.30.0 0.0.0.255 …...….访问制造部3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区11.3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any-----------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend cgb……….采购部 ACL3550-S-1 (config-ext-nacl) # evaluate cwb-cgb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2553550-S-1 (config-ext-nacl) #permit ip any any----------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend xsb……….销售部 ACL3550-S-1 (config-ext-nacl) # evaluate cwb-xsb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2553550-S-1 (config-ext-nacl) #permit ip any any---------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend cwb……….财务部 ACL3550-S-1 (config-ext-nacl) # permint ip any 172.16.60.00.0.0.255 reflect cwb-cgb ………...创建自反 ACL cwb-cgb3550-S-1 (config-ext-nacl) # permint ip any 172.16.70.00.0.0.255 reflect cwb-xsb ………...创建自反 ACL cwb-xsb3550-S-1 (config-ext-nacl) # evaluate zjb-cwb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any--------------------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend cwb……….管理部 ACL3550-S-1 (config-ext-nacl) # evaluate zjb-glb …..计算匹配自反 ACL 3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any any12.----------------------------------------------------------------------------------------------------3550-S-1 (config) # ip access-list extend zjb……….总经办 ACL3550-S-1 (config-ext-nacl) # permint ip any 172.16.80.00.0.0.255 reflect zjb-cwb ………...创建自反 ACL zjb-cwb3550-S-1 (config-ext-nacl) # permint ip any 172.16.90.00.0.0.255 reflect zjb-glb ………...创建自反 ACL zjb-glb3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) # deny ip any 192.168.0.0 0.0.255.255 ……….禁止访问其它部门3550-S-1 (config-ext-nacl) # permit ip any anyACL 应用:3550-S-13550-S-1 (config) # int vlan 2 …………..研发中心3550-S-1 (config-if) #ip access-group yfzx in3550-S-1 (config) # int vlan 3 …………..质保部3550-S-1 (config-if) #ip access-group zbb in3550-S-1 (config) # int vlan 4 ……………制造部(config-if) #ip access-group zzb in…(略)附:关键字 established 的 ACL 应用(单向访问)3550-S-1 (config) # ip access-list extend cgb……….采购部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.80.0 0.0.0.0.255 estab3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.2553550-S-1 (config-ext-nacl) #permit ip any any3550-S-1 (config) # ip access-list extend xsb……….销售部 ACL3550-S-1 (config-ext-nacl) # permit ip any 172.16.80.0 0.0.0.0.255estab3550-S-1 (config-ext-nacl) # permit ip any 172.16.100.0 0.0.0.255 ………访问服务器区3550-S-1 (config-ext-nacl) #deny ip any 192.168.0.0 0.0.255.255 3550-S-1 (config-ext-nacl) #permit ip any any13。
cisco路由器双线接入配置

cisco路由器双线接入配置双线接入配置示例:1.背景和目标在本文档中,将详细介绍如何配置Cisco路由器实现双线接入。
双线接入是通过连接两个不同的ISP(互联网服务提供商)线路来实现高可靠性和带宽扩展的方法。
以下是配置的目标: - 实现双线接入,增加带宽并提高网络的高可用性。
- 设置适当的路由策略,以便在主线路故障时自动切换到备用线路。
2.设备和拓扑在本示例中,我们将使用以下设备进行配置:- Cisco路由器(模型:)- 两个ISP提供的线路(线路1和线路2)网络拓扑如下:```+-------------+---- ISP 1 -------- Line 1 ----+---------------+----+---------------+---- Cisco -------- 路由器 ----+---------------+----+---------------+---- ISP 2 -------- Line 2 ----+-------------+```3.物理连接进行双线接入配置之前,确保正确连接ISP提供的线路到Cisco路由器的相应接口。
线路1连接到接口GigabitEthernet0/0,线路2连接到接口GigabitEthernet0/1.4.IP 地质分配为了正确配置双线接入,您需要为每个接口分配一个IP地质。
例如:- 接口GigabitEthernet0/0:- IP地质.192.168.1.1- 子网掩码.255.255.255.0- 接口GigabitEthernet0/1:- IP地质.192.168.2.1- 子网掩码.255.255.255.0确保您将IP地质和子网掩码与实际环境相匹配。
5.配置路由器下面是如何配置Cisco路由器实现双线接入的基本步骤:5.1.创建静态路由配置静态路由以指定流量如何流向ISP线路。
使用以下命令创建静态路由:```ip route 0.0.0.0 0.0.0.0 <ISP基础路由器IP地质> global```5.2.配置路由跟踪配置路由跟踪以实现对主线路的连通性监控和故障切换功能。
典型Cisco网络拓扑案例
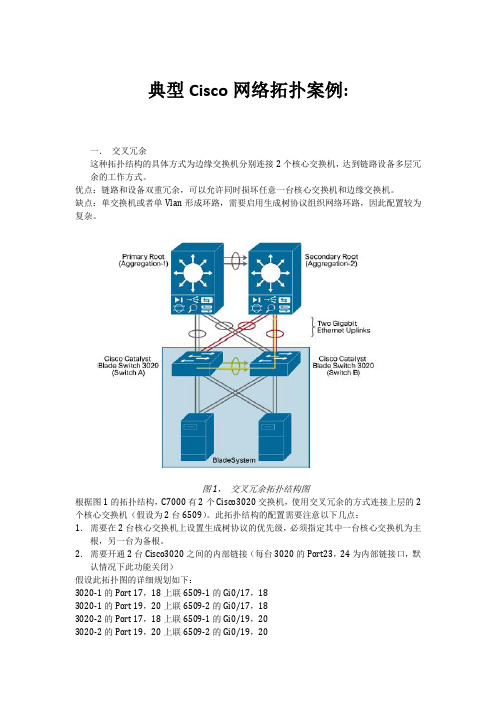
典型Cisco网络拓扑案例:一.交叉冗余这种拓扑结构的具体方式为边缘交换机分别连接2个核心交换机,达到链路设备多层冗余的工作方式。
优点:链路和设备双重冗余,可以允许同时损坏任意一台核心交换机和边缘交换机。
缺点:单交换机或者单Vlan形成环路,需要启用生成树协议组织网络环路,因此配置较为复杂。
图1,交叉冗余拓扑结构图根据图1的拓扑结构,C7000有2个Cisco3020交换机,使用交叉冗余的方式连接上层的2个核心交换机(假设为2台6509)。
此拓扑结构的配置需要注意以下几点:1.需要在2台核心交换机上设置生成树协议的优先级,必须指定其中一台核心交换机为主根,另一台为备根。
2.需要开通2台Cisco3020之间的内部链接(每台3020的Port23,24为内部链接口,默认情况下此功能关闭)假设此拓扑图的详细规划如下:3020-1的Port 17,18上联6509-1的Gi0/17,183020-1的Port 19,20上联6509-2的Gi0/17,183020-2的Port 17,18上联6509-1的Gi0/19,203020-2的Port 19,20上联6509-2的Gi0/19,20共有Vlan1,Vlan10,这2个Vlan的数据包需要传递到刀片服务器(需要802.1q封装协议)。
6509-1为Vlan1和Vlan10的主根,6509-2为Vlan1和Vlan10的备根。
详细配置步骤:(#之前的标示表示所需要配置此命令的交换机,比如6509-1就表示后面的命令需要在第一台6509上进行配置。
)6509-1#configure terminal #进入全局配置模式6509-1(config)#interface range gi0/17 - 18 #进入Gi0/17,18的配置菜单6509-1(config-if-range)#switchport mode trunk #配置Gi0/17,18的端口模式为trunk6509-1(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q6509-1(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan106509-1(config-if-range)#channel-group 1 mode active #配置Gi0/17,18的链路聚合,其模式为LACP-active6509-1(config-if-range)#end #结束Gi0/17,18的配置6509-1#configure terminal #进入全局配置模式6509-1(config)#interface range gi0/19 - 20 #进入Gi0/19,20的配置菜单6509-1(config-if-range)#switchport mode trunk #配置Gi0/19,20的端口模式为trunk 6509-1(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q6509-1(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan106509-1(config-if-range)#channel-group 2 mode active #配置Gi0/19,20的链路聚合,其模式为LACP-active6509-1(config-if-range)#end #结束Gi0/19,20的配置6509-1#configure terminal #进入全局配置模式6509-1(config)#spanning-tree vlan 1 root primary #配置6509-1为Vlan1的主根6509-1(config)#spanning-tree vlan vlan-10 root primary #配置6509-1为Vlan10的主根6509-1(config)#end #退出全局配置模式6509-1#copy running-config startup-config #保存以上配置6509-2#configure terminal #进入全局配置模式6509-2(config)#interface range gi0/17 - 18 #进入Gi0/17,18的配置菜单6509-2(config-if-range)#switchport mode trunk #配置Gi0/17,18的端口模式为trunk6509-2(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q6509-2(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan106509-2(config-if-range)#channel-group 1 mode active #配置Gi0/17,18的链路聚合,其模式为LACP-active6509-2(config-if-range)#end #结束Gi0/17,18的配置6509-2#configure terminal #进入全局配置模式6509-2(config)#interface range gi0/19 - 20 #进入Gi0/19,20的配置菜单6509-2(config-if-range)#switchport mode trunk #配置Gi0/19,20的端口模式为trunk 6509-2(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q6509-2(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan106509-2(config-if-range)#channel-group 2 mode active #配置Gi0/19,20的链路聚合,其模式为LACP-active6509-2(config-if-range)#end #结束Gi0/19,20的配置6509-2#configure terminal #进入全局配置模式6509-2(config)#spanning-tree vlan 1 root primary #配置6509-2为Vlan1的备根6509-2(config)#spanning-tree vlan vlan-10 root primary #配置6509-2为Vlan10的备根6509-2(config)#end#退出全局配置模式6509-2#copy running-config startup-config #保存以上配置3020-1#configure terminal #进入全局配置模式3020-1(config)#interface range gi0/17 - 18 #进入Gi0/17,18的配置菜单3020-1(config-if-range)#switchport mode trunk #配置Gi0/17,18的端口模式为trunk3020-1(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q3020-1(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan103020-1(config-if-range)#channel-group 1 mode active #配置Gi0/17,18的链路聚合,其模式为LACP-active3020-1(config-if-range)#end #结束Gi0/17,18的配置3020-1#configure terminal #进入全局配置模式3020-1(config)#interface range gi0/19 - 20 #进入Gi0/19,20的配置菜单3020-1(config-if-range)#switchport mode trunk #配置Gi0/19,20的端口模式为trunk3020-1(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q3020-1(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan103020-1(config-if-range)#channel-group 2 mode active #配置Gi0/19,20的链路聚合,其模式为LACP-active3020-1(config-if-range)#end #结束Gi0/19,20的配置3020-1#configure terminal #进入全局配置模式3020-1(config)# interface range gi0/23 - 124 #进入Gi0/23,24的配置菜单3020-1(config-if-range)#channel-group 3 mode active #配置Gi0/23,24的链路聚合,其模式为LACP-active3020-1(config-if-range)#media-type internal #打开Gi0/23,24的内部链接3020-1(config-if-range)#end #退出全局配置模式3020-1#configure terminal #进入全局配置模式3020-1(config)#vlan 1 #进入vlan1配置菜单3020-1(config-vlan)#remote-span #开启RSPAN3020-1(config-vlan)#end #退出全局配置模式3020-1#configure terminal #进入全局配置模式3020-1(config)#vlan 10 #进入vlan1配置菜单3020-1(config-vlan)#remote-span #开启RSPAN3020-1(config-vlan)#end #退出全局配置模式3020-1#copy running-config startup-config #保存以上配置3020-2#configure terminal #进入全局配置模式3020-2(config)#interface range gi0/17 - 18 #进入Gi0/17,18的配置菜单3020-2(config-if-range)#switchport mode trunk #配置Gi0/17,18的端口模式为trunk3020-2(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q3020-2(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan103020-2(config-if-range)#channel-group 1 mode active #配置Gi0/17,18的链路聚合,其模式为LACP-active3020-2(config-if-range)#end #结束Gi0/17,18的配置3020-2#configure terminal #进入全局配置模式3020-2(config)#interface range gi0/19 - 20 #进入Gi0/19,20的配置菜单3020-2(config-if-range)#switchport mode trunk #配置Gi0/19,20的端口模式为trunk3020-2(config-if-range)#switchport trunk encapsulation dot1q #配置trunk的封装模式为802.1q3020-2(config-if-range)#switchport trunk allowed vlan 1 , 10 #配置此trunk所允许的Vlan信息为Vlan1和Vlan103020-2(config-if-range)#channel-group 2 mode active #配置Gi0/19,20的链路聚合,其模式为LACP-active3020-2(config-if-range)#end #结束Gi0/19,20的配置3020-2#configure terminal #进入全局配置模式3020-2(config)# interface range gi0/23 - 124 #进入Gi0/23,24的配置菜单3020-2(config-if-range)#channel-group 3 mode active #配置Gi0/23,24的链路聚合,其模式为LACP-active3020-2(config-if-range)#media-type internal #打开Gi0/23,24的内部链接3020-2(config-if-range)#end #退出全局配置模式3020-2#configure terminal #进入全局配置模式3020-2(config)#vlan 1 #进入vlan1配置菜单3020-2(config-vlan)#remote-span #开启RSPAN3020-2(config-vlan)#end #退出全局配置模式3020-2#configure terminal #进入全局配置模式3020-2(config)#vlan 10 #进入vlan1配置菜单3020-2(config-vlan)#remote-span #开启RSPAN3020-2(config-vlan)#end #退出全局配置模式3020-2#copy running-config startup-config #保存以上配置至此,图1中所示的交换机层之间的配置全部完成,如果要再细化到C7000内部各刀片服务器所属的网卡划分可以使用”switchport access Vlan X”命令来执行。
cisco模拟器之------交换机、路由器、vlan的综合实例
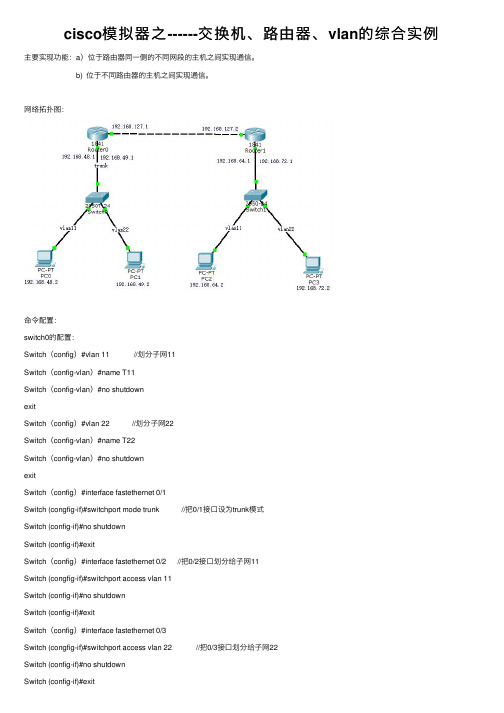
cisco模拟器之------交换机、路由器、vlan的综合实例主要实现功能:a)位于路由器同⼀侧的不同⽹段的主机之间实现通信。
b) 位于不同路由器的主机之间实现通信。
⽹络拓扑图:命令配置:switch0的配置:Switch(config)#vlan 11 //划分⼦⽹11Switch(config-vlan)#name T11Switch(config-vlan)#no shutdownexitSwitch(config)#vlan 22 //划分⼦⽹22Switch(config-vlan)#name T22Switch(config-vlan)#no shutdownexitSwitch(config)#interface fastethernet 0/1Switch (congfig-if)#switchport mode trunk //把0/1接⼝设为trunk模式Switch (config-if)#no shutdownSwitch (config-if)#exitSwitch(config)#interface fastethernet 0/2 //把0/2接⼝划分给⼦⽹11Switch (congfig-if)#switchport access vlan 11Switch (config-if)#no shutdownSwitch (config-if)#exitSwitch(config)#interface fastethernet 0/3Switch (congfig-if)#switchport access vlan 22 //把0/3接⼝划分给⼦⽹22Switch (config-if)#no shutdownSwitch (config-if)#exitSwitch1的配置:Switch(config)# vlan 11Switch(config-vlan)#name T11Switch(config-vlan)#no shutdownexitSwitch(config)# vlan 22Switch(config-vlan)#name T22Switch(config-vlan)#no shutdownexitSwitch(config)#interface fastethernet 0/1Switch (congfig-if)#switchport mode trunkSwitch (config-if)#no shutdownSwitch (config-if)#exitSwitch(config)#interface fastethernet 0/2Switch (congfig-if)#switchport access vlan 11Switch (config-if)#no shutdownSwitch (config-if)#exitSwitch(config)#interface fastethernet 0/3Switch (congfig-if)#switchport access vlan 22Switch (config-if)#no shutdownSwitch (config-if)#exitRouter0的配置:Switch (config)#int f0/1.1 //在0/1接⼝下划分⼦接⼝0/1.1Switch (config)#int f0/1.2 //在0/1接⼝下划分⼦接⼝0/1.2Switch(config)#interface fastethernet 0/1.1 //配置⼦接⼝0/1.1的路由信息Switch (congfig-subif)#encapsulation dot1Q 11 //单臂路由Switch (config-subif)#ip address 192.168.48.1 255.255.255.0Switch (config-subif)#exitSwitch(config)#interface fastethernet 0/1.2 //配置⼦接⼝0/1.2的路由信息Switch (congfig-subif)#encapsulation dot1Q 22 //单臂路由Switch (config-subif)#ip address 192.168.49.1 255.255.255.0Switch (config-subif)#exitSwitch(config)#interface fastethernet 0/1Switch (congfig-subif)#no shutdownSwitch (congfig-subif)#exitSwitch (congfig)#interface fastethernet 0/0 //配置接⼝0/0的路由信息Switch (config-subif)#ip address 192.168.127.1 255.255.255.0Switch (congfig-subif)#no shutdownSwitch (congfig-subif)#exitSwitch (config)#ip route 192.168.64.0 255.255.255.0 192.168.127.2 //配置静态路由协议Switch (config)#ip route 192.168.72.0 255.255.255.0 192.168.127.2Switch (config)#exitRouter1的配置:Switch (config)#int f0/1.1Switch (config)#int f0/1.2Switch(config)#interface fastethernet 0/1.1Switch (congfig-subif)#encapsulation dot1Q 11Switch (config-subif)#ip address 192.168.64.1 255.255.255.0Switch (config-subif)#exitSwitch(config)#interface fastethernet 0/1.2Switch (congfig-subif)#encapsulation dot1Q 22Switch (config-subif)#ip address 192.168.72.1 255.255.255.0Switch (config-subif)#exitSwitch(config)#interface fastethernet 0/1Switch (congfig-subif)#no shutdownSwitch (congfig-subif)#exitSwitch (congfig)#interface fastethernet 0/0Switch (config-subif)#ip address 192.168.127.2 255.255.255.0Switch (congfig-subif)#no shutdownSwitch (congfig-subif)#exitSwitch (config)#ip route 192.168.48.0 255.255.255.0 192.168.127.1Switch (config)#ip route 192.168.49.0 255.255.255.0 192.168.127.1Switch (config)#exit分别给各台主机配置ip以及其他信息:结果每台主机都可以通信。
Cisco WLC 2106+Cisco LAP 1242AG配置实例

显示 AP 管理接口设置信息 3.config wlan disable wlan-number
关闭该接 wlan 通讯 4.config interface address ap-manager ip-addr ip-netmask gateway
2.进入 AP 后,输入密码:Cisco(默认) 3.Show lwapp ip config
显示 ip 配置信息 4.Clear lwapp private-config 清除 lwapp 配置信息 5.Lwapp ap ip addrss 配置 ip 地址 6.Lwapp ap ip default-gateway 配置默认网关
802.11g2003 年 7 月,通过了第三种调变标准。其载波的频率为 2.4GHz(跟 802.11b 相同),原始传 送速度为 54Mbit/s,净传输速度约为 24.7Mbit/s(跟 802.11a 相同)。 二、Cisco 1242AG 配置命令
1.按住 Mode 按钮,插上 AP 电源,5s 左右松开 清除 AP 的配置信息
switchport access vlan 2
switchport mode access
!
interface FastEthernet0/4
switchport access vlan 2
switchport mode access
!
interface FastEthernet0/5
switchport access vlan 2
switchport mode access
!
interface FastEthernet0/6
Cisco路由器配置实例(经典)
实训报告实训一路由基本配置1、实验目的:路由器基本配置及ip设置2、拓扑结构图Router0 fa0/0: 192.168.11.1Fa0/1:192.168.1.1Router1 fa0/0: 192.168.11.2Fa0/1:192.168.2.1Znn1:192.168.1.2Znn2:192.168.2.23、实验步骤Router1Router>en 用户模式进入特权模式Router#conf t 特权模式进入全局模式Enter configuration commands, one per line. End with CNTL/Z.Router(config)#host rznn1 改名字为rznn1rznn1(config)#int fa0/0 进入fa0/0端口rznn1(config-if)#ip add 192.168.11.1 255.255.255.0 设置ip地址rznn1(config-if)#no sh 激活rznn1(config)#int fa0/1rznn1(config-if)#ip add 192.168.1.1 255.255.255.0rznn1(config-if)#no shrznn1(config-if)#exitrznn1(config)#exitrznn1#copy running-config startup-config 保存Destination filename [startup-config]? startup-configrznn1#conf trznn1(config)#enable secret password 222 设置密文rznn1#show ip interface b 显示Interface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.1 YES manual up up FastEthernet0/1 192.168.1.1 YES manual up upVlan1 unassigned YES manual administratively down downrouter 2outer>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host rznn2rznn2(config)#int fa0/0rznn2(config-if)#ip add 192.168.11.2 255.255.255.0rznn2(config-if)#no shrznn2(config)#int fa0/1rznn2(config-if)#ip add 192.168.2.1 255.255.255.0rznn2(config-if)#no shRznn2#copy running-config startup-config 保存Destination filename [startup-config]? startup-configrznn2(config-if)#exitrznn2(config)#exitrznn2#conf trznn2(config)#enable secret 222rznn2#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.2 YES manual up up FastEthernet0/1 192.168.2.1 YES manual up upVlan1 unassigned YES manual administratively down down实训二1、远程登录、密码设置及验证为路由器开设telnet端口,PC机可以远程登陆到Rznn3(Router 1)拓扑结构图Router0:192.168.1.1Pc:192.168.1.2步骤rznn3>rznn3>enrznn3#conf tEnter configuration commands, one per line. End with CNTL/Z.rznn3(config)#no ip domain lookuprznn3(config)#line cons 0rznn3(config-line)#password znnrznn3(config-line)#loginrznn3(config-line)#no exec-trznn3(config-line)#logg syncrznn3(config-line)#exitrznn3(config)#int fa0/0rznn3(config-if)#ip add 192.168.1.1 255.255.255.0rznn3(config-if)#no shrznn3(config-if)#exitrznn3(config)#line vty 0 4 打通五个端口rznn3(config-line)#password cisco 设置密码rznn3(config-line)#login 保存rznn3(config-line)#exit4、测试:实训三命令组1、目的:八条命令(no ip domain lookup\line cons 0\password\login\no exec-t\logg sync\show version\reload\copy running-config startup-config)\show cdp neighbors)2、拓扑结构图Router0 fa0/0: 192.168.11.1Router1 fa0/0: 192.168.11.23、步骤rznn1#conf tEnter configuration commands, one per line. End with CNTL/Z.1、rznn1(config)#no ip domain lookup 取消域名查找转换2、rznn1(config)#line cons 0 打开cons 0端口3、rznn1(config-line)#password znn 设置密码为znnrznn1(config-line)#login 保存rznn1(config-line)#no exec-t 设置永不超时4、rznn1(config-line)#logg sync 产生日志5、rznn1#show version 显示思科路由系统版本信息Cisco IOS Software, 2800 Software (C2800NM-ADVIPSERVICESK9-M), Version 12.4(15)T1, RELEASE SOFTWARE (fc2)Technical Support: /techsupportCopyright (c) 1986-2007 by Cisco Systems, Inc.Compiled Wed 18-Jul-07 06:21 by pt_rel_team6、rznn1#show cdp neighbors 查看路由器连接的相邻路由器的相关信息Capability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDrznn2 Fas 0/0 139 R C2800 Fas 0/07、rznn1#copy running-config startup-config 保存刚才指令Destination filename [startup-config]? startup-configBuilding configuration...[OK]8、rznn1#reload 重启路由器Proceed with reload? [confirm]System Bootstrap, Version 12.1(3r)T2, RELEASE SOFTWARE (fc1)Copyright (c) 2000 by cisco Systems, Inc.cisco 2811 (MPC860) processor (revision 0x200) with 60416K/5120K bytes of memorySelf decompressing the image :########################################################################## [OK] Restricted Rights Legendrznn1#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.1 YES manual up up FastEthernet0/1 192.168.1.1 YES manual up upVlan1 unassigned YES manual administratively down down9、rznn1(config-if)#ip add 192.168.3.1 255.255.255.0 重置ip地址rznn1#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.3.1 YES manual up up FastEthernet0/1 192.168.1.1 YES manual up up Vlan1 unassigned YES manual administratively down down实训四发现协议1、实训目的通过发现协议显示路由器相邻路由的端口信息2、拓扑结构Router0:192.168.11.1Router1:fa0/0 192.168.11.2Fa0/1 192.168.12.1Router2:192.168.12.23、步骤R1路由器Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to upr1(config-if)#r1(config-if)#exitr1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.1 YES manual up down FastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downR2 路由器Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r2r2(config)#int fa0/0r2(config-if)#ip add 192.168.11.2 255.255.255.0r2(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r2(config-if)#exitr2(config)#exitr2#%SYS-5-CONFIG_I: Configured from console by consoler2#conf tEnter configuration commands, one per line. End with CNTL/Z.r2(config)#int fa0/0r2(config-if)#int fa0/1r2(config-if)#ip add 192.168.12.1 255.255.255.0r2(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to upr2(config-if)#exitr2(config)#exitr2#%SYS-5-CONFIG_I: Configured from console by consoler2#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.2 YES manual up upFastEthernet0/1 192.168.12.1 YES manual up down Vlan1 unassigned YES manual administratively down downR3路由器Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r3r3(config)#int fa0/0r3(config-if)#ip add 192.168.12.2 255.255.255.0r3(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r3(config-if)#exitr3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by consoler3#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.12.2 YES manual up up FastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downR1发现邻居r1#show cdp neighborsCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDr2 Fas 0/0 165 R C2800 Fas 0/0R2发现邻居r2#show cdp neighborsCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDr1 Fas 0/0 176 R C1841 Fas 0/0r3 Fas 0/1 130 R C1841 Fas 0/0R3发现邻居r3#show cdp neighborsCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDr2 Fas 0/0 166 R C2800 Fas 0/14、总结show 命令(1)show ip interface b (显示端口ip信息)(2)show version (显示ios版本信息)(3)show running-config (显示刚才使用的命令配置信息)(4)show cdp neighbors (显示发现邻居直连设备信息)(5)show interface (显示所有端口详细信息)实训五静态路由1、实验目的:将不同网段的网络配通(ip route)Ip route语法:ip route 目标地址子网掩码相邻路由器接口地址Show ip route2、试验拓扑:Router0:192.168.11.1Router1:fa0/0 192.168.11.2Fa0/1 192.168.12.1Router2:192.168.12.23、实验步骤:Router1Router>enRouter#conf tRouter(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to upr1(config-if)#exitr1(config)#exitr1#show ip interface bInterface IP-Address OK? Method Status ProtocolFastEthernet0/0 192.168.11.1 YES manual up downFastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downr1#%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r1#ping 192.168.12.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:.....Success rate is 0 percent (0/5)r1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#ip route 192.168.12.0 255.255.255.0 192.168.11.2r1(config)#exitr1#ping 192.168.12.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 msr1#ping 192.168.12.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:.....Success rate is 0 percent (0/5)r1#ping 192.168.12.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 47/62/78 msr1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0S 192.168.12.0/24 [1/0] via 192.168.11.2Router3Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r3r3(config)#int fa0/0r3(config-if)#ip add 192.168.12.2 255.255.255.0r3(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r3(config-if)#exitr3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by consoler3#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.12.2 YES manual up up FastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downr3#conf tEnter configuration commands, one per line. End with CNTL/Z.r3(config)#ip route 192.168.11.0 255.255.255.0 192.168.12.1r3(config)#exitr3#ping 192.168.11.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.2, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 msr3#ping 192.168.11.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 62/62/63 msr3#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setS 192.168.11.0/24 [1/0] via 192.168.12.1C 192.168.12.0/24 is directly connected, FastEthernet0/04、默认路由Route 1r1>enr1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#no ip route 192.168.12.0 255.255.255.0 192.168.11.2%No matching route to deleter1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0r1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#ip route 0.0.0.0 0.0.0.0 192.168.11.2r1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.11.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, FastEthernet0/0S* 0.0.0.0/0 [1/0] via 192.168.11.2r1#ping 192.168.12.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 16/28/31 msr1#ping 192.168.12.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 62/62/63 msRoute 3r1>enr1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#no ip route 192.168.12.0 255.255.255.0 192.168.11.2%No matching route to deleter1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0r1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#ip route 0.0.0.0 0.0.0.0 192.168.11.2r1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.11.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, FastEthernet0/0S* 0.0.0.0/0 [1/0] via 192.168.11.2r3#ping 192.168.11.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 62/62/63 ms实训六动态路由RIP 协议1、实验目的使用配置动态路由启动Rip协议使用到的命令(router rip/network/show ip protocols/show ip route)2、实验拓扑R1 fa0/0 192.168.11.1R2 fa0/0 192.168.11.2fa0/1 192.168.12.1R3 fa0/0 192.168.12.23、实验步骤R1Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z. Router(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no shr1(config-if)#exitr1(config)#router ripr1(config-router)#network 192.168.11.0r1(config-router)#exitr1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoleR2Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z. Router(config)#host r2r2(config)#int fa0/0r2(config-if)#ip add 192.168.11.2 255.255.255.0r2(config-if)#no shr2(config-if)#exitr2(config)#int fa0/1r2(config-if)#ip add 192.168.12.1 255.255.255.0r2(config-if)#no shr2(config-if)#exitr2(config)#router ripr2(config-router)#network 192.168.11.0r2(config-router)#network 192.168.12.0r2(config-router)#exitr2(config)#exitr2#R3Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z. Router(config)#host r3r3(config)#int fa0/0r3(config-if)#ip add 192.168.12.2 255.255.255.0r3(config-if)#no shr3(config-if)#exitr3(config)#router ripr3(config-router)#network 192.168.12.0r3(config-router)#exitr3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by console4、实验测试R1r1#show ip protocolsRouting Protocol is "rip"Sending updates every 30 seconds, next due in 10 secondsInvalid after 180 seconds, hold down 180, flushed after 240 Outgoing update filter list for all interfaces is not setIncoming update filter list for all interfaces is not set Redistributing: ripDefault version control: send version 1, receive any version Interface Send Recv Triggered RIP Key-chain FastEthernet0/0 1 2 1Automatic network summarization is in effectMaximum path: 4Routing for Networks:192.168.11.0Passive Interface(s):Routing Information Sources:Gateway Distance Last UpdateDistance: (default is 120)r1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0R 192.168.12.0/24 [120/1] via 192.168.11.2, 00:00:24, FastEthernet0/0 r1#ping 192.168.12.0Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.0, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 msR2r2#show ip protocolsRouting Protocol is "rip"Sending updates every 30 seconds, next due in 21 secondsInvalid after 180 seconds, hold down 180, flushed after 240Outgoing update filter list for all interfaces is not setIncoming update filter list for all interfaces is not setRedistributing: ripDefault version control: send version 1, receive any versionInterface Send Recv Triggered RIP Key-chain FastEthernet0/0 1 2 1FastEthernet0/1 1 2 1Automatic network summarization is in effectMaximum path: 4Routing for Networks:192.168.11.0192.168.12.0Passive Interface(s):Routing Information Sources:Gateway Distance Last UpdateDistance: (default is 120)r2#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0C 192.168.12.0/24 is directly connected, FastEthernet0/1R3r3#show ip protocolsRouting Protocol is "rip"Sending updates every 30 seconds, next due in 15 secondsInvalid after 180 seconds, hold down 180, flushed after 240Outgoing update filter list for all interfaces is not setIncoming update filter list for all interfaces is not setRedistributing: ripDefault version control: send version 1, receive any versionInterface Send Recv Triggered RIP Key-chain FastEthernet0/0 1 2 1Automatic network summarization is in effectMaximum path: 4Routing for Networks:192.168.12.0Passive Interface(s):Routing Information Sources:Gateway Distance Last UpdateDistance: (default is 120)r3#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setR 192.168.11.0/24 [120/1] via 192.168.12.1, 00:00:04, FastEthernet0/0 C 192.168.12.0/24 is directly connected, FastEthernet0/0r3#ping 192.168.11.0Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.0, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 ms实训七负载平衡试训目的实现负载平衡实训拓扑R1 fa0/0 192.168.11.1R2 eth0/0/0 192.168.11.2Fa0/0 192.168.12.1Fa0/0 192.168.13.1R3 fa0/0 192.168.12.2Fa0/1 192.168.14.1R4 fa0/0 192.168.13.2Fa0/1 192.168.15.1R5 fa0/0 192.168.14.2Fa0/1 192.168.15.2实训步骤(R1 )r1>enR1#conf tR1(config)#ip route 0.0.0.0 0.0.0.0 192.168.11.2R1(config)#exitr1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.11.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, FastEthernet0/0S* 0.0.0.0/0 [1/0] via 192.168.11.2(R2)r2>enr2(config)#ip route 0.0.0.0 0.0.0.0 192.168.12.2r2(config)#ip route 0.0.0.0 0.0.0.0 192.168.13.2r2(config)#exitr2#%SYS-5-CONFIG_I: Configured from console by consoles% Ambiguous command: "s"r2#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.12.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, Ethernet0/0/0C 192.168.12.0/24 is directly connected, FastEthernet0/0C 192.168.13.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.12.2[1/0] via 192.168.13.2(R3)r3>enr3#conf tEnter configuration commands, one per line. End with CNTL/Z.r3(config)#ip route 0.0.0.0 0.0.0.0 192.168.12.1r3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by consoler3#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.12.1 to network 0.0.0.0C 192.168.12.0/24 is directly connected, FastEthernet0/0C 192.168.14.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.12.1(R4)r4>enr4#conf tEnter configuration commands, one per line. End with CNTL/Z.r4(config)#ip route 0.0.0.0 0.0.0.0 192.168.13.1r4(config)#exitr4#%SYS-5-CONFIG_I: Configured from console by consoler4#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.13.1 to network 0.0.0.0C 192.168.13.0/24 is directly connected, FastEthernet0/0C 192.168.15.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.13.1(R5)r5>enr5#conf tEnter configuration commands, one per line. End with CNTL/Z.r5(config)#ip route 0.0.0.0 0.0.0.0 192.168.14.1r5(config)#ip route 0.0.0.0 0.0.0.0 192.168.15.1r5(config)#exitr5#%SYS-5-CONFIG_I: Configured from console by consoler5#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.14.1 to network 0.0.0.0C 192.168.14.0/24 is directly connected, FastEthernet0/0C 192.168.15.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.14.1[1/0] via 192.168.15.1实训测试(R1)r1#ping 192.168.14.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.14.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 62/84/94 ms (R5)r5#ping 192.168.11.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 79/91/94 ms实训八DHCP 协议配置实训目的全网配通实训拓扑Fa0/0 192.168.11.1Fa0/1 192.168.12.1实训步骤Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no shr1(config-if)#exitr1(config)#int fa0/1r1(config-if)#ip add 192.168.12.1 255.255.255.0r1(config-if)#no shr1(config-if)#exitr1(config)#ip dhcp pool znn //配置一个根地址池znnr1(dhcp-config)#network 192.168.11.0 255.255.255.0 //为所有客户机动态分配的地址段r1(dhcp-config)#default-router 192.168.11.1 //为客户机配置默认的网关r1(dhcp-config)#dns-server 192.168.11.1 //为客户机配置DNS服务器r1(dhcp-config)#exitr1(config)#ip dhcp pool znn1r1(dhcp-config)#network 192.168.12.0 255.255.255.0r1(dhcp-config)#default-router 192.168.12.1r1(dhcp-config)#dns-server 192.168.12.1r1(dhcp-config)#exit。
组网工程实验报告

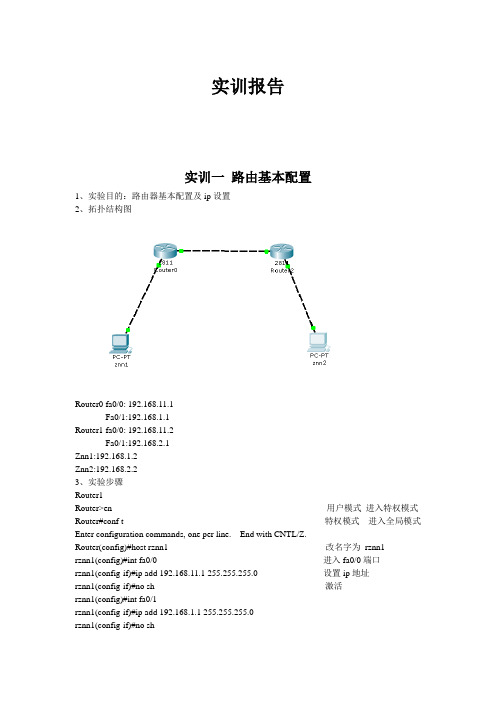
实验一各类接口配置姓名:班级:学号:地址表学习目标•在路由器和交换机上配置接口简介:本练习将在标准实验拓扑中的路由器和交换机上配置 IP 信息和说明。
任务 1:在路由器和交换机上配置接口步骤 1. 在路由器上配置接口单击路由器 R1-ISP。
使用CLI 选项卡和密码cisco 登录到路由器。
使用enable命令进入特权模式,使用密码class 进入特权执行模式,使用configure terminal 进入全局配置模式,进入全局配置模式。
输入命令interface fa0/0 进入 FastEthernet 接口的接口配置模式。
注意提示的变化。
输入命令ip address 192.168.254.253 255.255.255.0 以设置 IP 地址和子网掩码。
输入命令description Link to Eagle Server 以描述接口。
输入命令no shutdown 以启用接口。
输入命令exit 返回全局配置模式。
输入命令interface s0/0/0进入串行接口的接口配置模式。
输入命令ip address 10.10.10.6 255.255.255.252以设置 IP 地址和子网掩码。
此接口连接串行交叉电缆的 DCE 端。
输入命令clock rate 64000设置接口提供定时信号。
输入命令description Link to R2-Central以描述接口。
输入命令no shutdown以启用接口。
输入命令exit返回全局配置模式。
按Ctrl+z离开配置模式。
输入命令copy running-config startup-config将更改保存至NVRAM。
在提示出现时按Enter确认目的文件名。
输入命令show running-config和show interfaces以确认配置。
步骤 2. 在其它路由器上配置接口在路由器 R2-Central 上重复步骤 1,使用上表中的信息配置和验证接口。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
扑拓图
配置说明
C4000(config)#username r7 password 123 C4000(config)#interface serial 2 C4000(config-if)#ip add 172.16.3.1 255.255.255.0 C4000(config-if)#encapsulation ppp C4000(config-if)#ip nat outside C4000(config-if)#ip policy route-map fuzai C4000(config-if)#no shutdown C4000(config-if)#interface loopback 0 C4000(config-if)#ip add 9.9.9.9 255.255.255.0 C4000(config-if)#exit C4000(config)#interface e1 C4000(config-if)#ip add 172.16.1.1 255.255.255.0 C4000(config-if)#ip nat inside C4000(config-if)#no shutdown
2
配置介绍
扑拓图
S3和S6设置交换机名字和VTP客户机并设置VTP信息, 生成树模式.启用生成树的上行链路(全局参数).通向 S1.S2和s7.s8的链路为trunk。并把相应端口划入相应的 VLAN。 S1.S2和s7.s8分别配置VTP服务器.并配置VTP信息.以 太通道. 生成树的模式.生成树在各个VLAN中的根网桥和 备份根网桥.以及相应端口的TRUNK模式。每栋楼设置2 个VLAN.R2和R4上分别配置单臂路由.SHRP路由热备份. 因为VLAN划分为2个.故需要做2个热备组.指定各个VLAN 所在路由上的活跃和备份状态.第一栋建筑下行端口运行 OSPF协议AREA1中.上行行端口运行在AREA0中.第二栋 建筑下行端口运行OSPF协议AREA2中.上行行端口运行在 AREA0中.
5
配置说明
R6配置:(模拟帧中继)
扑拓图
Route>enable Route#conf t Route(config)#hos r6 R6(config)#frame-relay switching R6(onfig)#int s1 R6(config-if)#encapsulation frame-relay R6(config-if)#bandwidth 64 R6(config-if)#clock rate 64000 R6(config-if)#frame-relay lmi-type cisco R6(config-if)#frame-relay intf-type dce R6(config-if)#frame-relay route 200 interface serial 0 100 R6(config-if)#no shutdown
6
配置说明
扑拓图
R6(config)#interface serial 0 R6(config-if)#encapsulation frame-relay R6(config-if)# bandwidth 64 R6(config-if)#clock rate 64000 R6(config-if)#frame-relay lmi-type cisco R6(config-if)#frame-relay intf-type dce R6(config-if)#frame-relay route 100 interface s1 200 R6(config-if)#no shutdown
11
配置说明
R7配置(模拟Isp2网络) 扑拓图 Route>enable Route#conf t Route(config)#hostname r7 R7(config)#username C4000 password 123 R7(config)#interface serial 0 R7(config-if)#ip add 172.16.3.2 255.255.255.0 R7(config-if)#encapsulation ppp R7(config-if)#ppp authentication chap R7(config-if)#clock rate 64000 R7(config-if)#no shutdown
扑拓图
ISP1 R5 C4000
DLCI=200
S1 S1 f0/1 f0/5 S4 f0/3 f0/4 E1/2 E0/0 f0/2 f1/0/5 s7 f/0/2
Frame Relay Cloud
DLCI=100
S0
S1 S2 E0 E1 f0/1 f0/5
ppp chap
S0
ISP2 R7
R6
7
配置说明
C4000配置:(企业路由)
扑拓图
Route>enable Route#conf t Route(confg)#hos C4000 C4000(config)#interface serial 1 C4000(config-if)#ip add 172.16.2.1 255.255.255.0 C4000(config-if)#encapsulation frame-relay C4000(config-if)#frame-relay lmi-type cisco C4000(config-if)#frame-relay interface-dlci 100 C4000(config-if)#frame-relay map ip 172.16.2.2 100 broadcast C4000(config-if)#ip nat outside C4000(config-if)#ip policy route-map fuzai C4000(config-if)#no shutdown
3
配置介绍
扑拓图
S4和S5模拟BENET公司核心层设备cisco6509,因为核 心层属于交换网络,只负责快速的交换不同子公司数据. 故无须配制。 R6模拟外运营商网帧中继交换机R5模拟外网运营商帧 中继出口。 R7模拟外网另一个运营商。 R4000配置OSPF协议.只公布下行端口并运行在AREA0 中.做NAT转换.利用route-map实现线路冗余和负载均衡. 两个上行端口分别封装frame-relay和PPP通向外网。 R6配置帧中继交换机.指定通向R5和R4000的DLCI。 R5配置外网的测试IP地址。 R7配置外网的测试Iig)#interface e0 C4000(config-if)#ip add 172.16.4.1 255.255.255.0 C4000(config-if)#ip nat inside C4000(config-if)#no shutdown C4000(config)#access-list 1 permit 192.168.2.0 0.0.0.255 C4000(config)#access-list 1 permit 192.168.3.0 0.0.0.255 C4000(config)#access-list 1 permit 10.0.1.0 0.0.0.255 C4000(config)#access-list 1 permit 10.0.2.0 0.0.0.255 C4000(config)# access-list 2 permit 192.168.2.0 C4000(config)# access-list 2 permit 10.0.1.0 0.0.0.255 C4000(config)# access-list 3 permit 192.168.3.0 0.0.0.255 C4000(config)# access-list 3 permit 10.0.2.0 0.0.0.255 C4000(config)#route-map isp1 permit 20 C4000(config-route-map)#match ip address 1 C4000(config-route-map)#match interface serial 1
10
扑拓图
配置说明
C4000(config)#route-map isp2 permit 20 C4000(config-route-map)#match ip address 1 C4000(config-route-map)#route-map fuzai permit 10 C4000(config-route-map)#match ip address 2 C4000(config-route-map)#set default interface Serial1 C4000(config-route-map)#set ip default nex-hop 172.16.2.2 C4000(config-route-map)#route-map fuzai permit 20 C4000(config-route-map)#match ip address 3 C4000(config-route-map)#set default interface Serial2 C4000(config-route-map)#set ip default nex-hop 172.16.3.2 C4000(config)#ip nat inside source route-map isp1 interface serial 1 overload C4000(config)#ip nat inside source route-map isp2 interface serial 2 overload C4000(config)#ip route 0.0.0.0 0.0.0.0 172.16.2.2 C4000(config)#ip route 0.0.0.0 0.0.0.0 172.16.3.2 C4000(config-router)#router ospf 1 C4000(config-router)#network 172.16.4.1 0.0.0.0 a 0 C4000(config-router)#network 172.16.1.1 0.0.0.0 a 0 C4000(config-router)#default-information originate C4000(config-router)#exit
