网络布线端口对应表
交换机路由器常用端口号对照表
69 Trival File Transfer 79 Finger Server 80 HTTP 99 Metagram Relay Message transfer 102 agent(MTA)-X.400 over TCP/IP Post Office Protocol 109 -Version3 SUN公司的RPC服务所有 110 端口 113 Authentication Service Network News Transfer Protocol
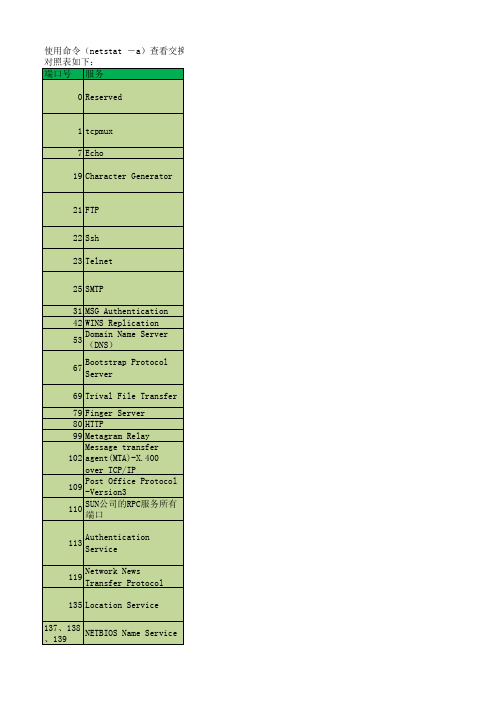
使用命令(netstat -a)查看交换机端口号信息 对照表如下: 端口号 服务 0 Reserved
1 tcpmux 7 Echo 19 Character Generator
21 FTP 22 Ssh 23 Telnet 25 SMTP 31 MSG Authentication 42 WINS Replication Domain Name Server 53 (DNS) 67 Bootstrap Protocol Server
)查看交换机端口号信息 说明 通常用于分析操作系统。这一方法能够工作是因为在一些系统中“0”是无效端 口,当你试图使用通常的闭合端口连接它时将产生不同的结果。一种典型的扫描,使用IP地址为 0.0.0.0,设置ACK位并在以太网层广播。 这显示有人在寻找SGI Irix机器。Irix是实现tcpmux的主要提供者,默认情况下tcpmux在这种系统中 被打开。Irix机器在发布是含有几个默认的无密码的帐户,如:IP、GUEST UUCP、NUUCP、DEMOS 、 TUTOR、DIAG、OUTOFBOX等。许多管理员在安装后忘记删除这些帐户。因此HACKER在INTERNET上搜索 能看到许多人搜索Fraggle放大器时,发送到X.X.X.0和X.X.X.255的信息。 这是一种仅仅发送字符的服务。UDP版本将会在收到UDP包后回应含有垃圾字符的包。TCP连接时会发 送含有垃圾字符的数据流直到连接关闭。HACKER利用IP欺骗可以发动DoS攻击。伪造两个chargen服务 器之间的UDP包。同样Fraggle DoS攻击向目标地址的这个端口广播一个带有伪造受害者IP的数据包, FTP服务器所开放的端口,用于上传、下载。最常见的攻击者用于寻找打开 anonymous的FTP服务器的方法。这些服务器带有可读写的目录。木马Doly Trojan、Fore、Invisible FTP、WebEx、WinCrash和Blade Runner所开放的端口。 PcAnywhere建立的TCP和这一端口的连接可能是为了寻找ssh。这一服务有许多弱点,如果配置成特定 的模式,许多使用RSAREF库的版本就会有不少的漏洞存在。 远程登录,入侵者在搜索远程登录UNIX的服务。大多数情况下扫描这一端口是为了找到机器运行的操 作系统。还有使用其他技术,入侵者也会找到密码。木马TinyTelnet Server就开放这个端口。 SMTP服务器所开放的端口,用于发送邮件。入侵者寻找SMTP服务器是为了传递他们的SPAM。入侵者的 帐户被关闭,他们需要连接到高带宽的E-MAIL服务器上,将简单的信息传递到不同的地址。木马 Antigen、Email Password Sender、Haebu Coceda、Shtrilitz Stealth、WinPC、WinSpy都开放这个 木马Master Paradise、Hackers Paradise开放此端口。 WINS复制 DNS服务器所开放的端口,入侵者可能是试图进行区域传递(TCP),欺骗DNS(UDP)或隐藏其他的通 信。因此防火墙常常过滤或记录此端口。 通过DSL和Cable modem的防火墙常会看见大量发送到广播地址255.255.255.255的数据。这些机器在 向DHCP服务器请求一个地址。HACKER常进入它们,分配一个地址把自己作为局部路由器而发起大量中 间人(man-in-middle)攻击。客户端向68端口广播请求配置,服务器向67端口广播回应请求。这种 许多服务器与bootp一起提供这项服务,便于从系统下载启动代码。但是它们常 常由于错误配置而使入侵者能从系统中窃取任何 文件。它们也可用于系统写入文件。 入侵者用于获得用户信息,查询操作系统,探测已知的缓冲区溢出错误,回应从自己机器到其他机器 用于网页浏览。木马Executor开放此端口。 后门程序ncx99开放此端口。 消息传输代理。 POP3服务器开放此端口,用于接收邮件,客户端访问服务器端的邮件服务。POP3服务有许多公认的弱 点。关于用户名和密码交 换缓冲区溢出的弱点至少有20个,这意味着入侵者可以在真正登陆前进入 常见RPC服务有rpc.mountd、NFS、rpc.statd、rpc.csmd、rpc.ttybd、amd等 说明:这是一个许多计算机上运行的协议,用于鉴别TCP连接的用户。使用标准的这种服务可以获得 许多计算机的信息。但是它可作为许多服务的记录器,尤其是FTP、POP、IMAP、SMTP和IRC等服务。 通常如果有许多客户通过防火墙访问这些服务,将会看到许多这个端口的连接请求。记住,如果阻断 这个端口客户端会感觉到在防火墙另一边与E-MAIL服务器的缓慢连接。许多防火墙支持TCP连接的阻 NEWS新闻组传输协议,承载USENET通信。这个端口的连接通常是人们在寻找USENET服务器。多数ISP 限制,只有他们的客户才能访问他们的新闻组服务器。打开新闻组服务器将允许发/读任何人的帖 Microsoft在这个端口运行DCE RPC end-point mapper为它的DCOM服务。这与UNIX 111端口的功能很 相似。使用DCOM和RPC的服务利用计算机上的end-point mapper注册它们的位置。远端客户连接到计 算机时,它们查找end-point mapper找到服务的位置。HACKER扫描计算机的这个端口是为了找到这个 其中137、138是UDP端口,当通过网上邻居传输文件时用这个端口。而139端口:通过这个端口进入的 连接试图获得NetBIOS/SMB服务。这个协议被用于windows文件和打印机共享和SAMBA。还有WINS
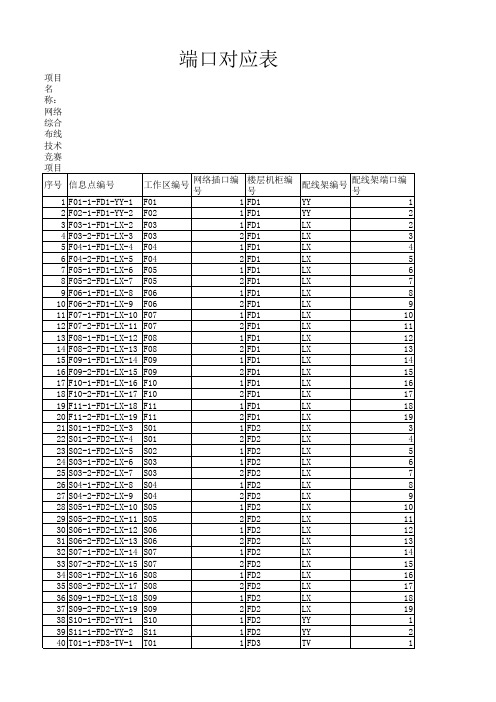
端口对应表
医院网络配线架端口对应表
0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6 0.0.7 0.0.8 0.0.9 0.0.10 0.0.11 0.0.12 0.0.13 0.0.14 0.0.15 0.0.16 0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6 0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6
0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6 0.0.7 0.0.8 0.0.9 0.0.10 0.0.11 0.0.12 0.0.13 0.0.14 0.0.15 0.0.16 0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6 0.0.7 0.0.8 0.0.9 0.0.10 0.0.11 0.0.12 0.0.13 0.0.14 0.0.15 0.0.16 0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6 0.0.7 0.0.8
1 2 3 4 5 6 7 8 1 2 3 4 5 DI1 DI2 DI3 DI4 DI5 DI6 DI7 DI8 DO1 DO2 DO3 DO4 DO5
0.0.1 0.0.2 0.0.3 0.0.4 0.0.5 0.0.6 0.0.7 0.0.8 0.0.1 0.0.2 0.0.3 0.0.4 0.0.5
PF-STA PF-TRIP PF-AM SF-STA SF-TRIP SF-AM
排风机运行状态 排风机故障报警 排风机手自动状态 送风机运行状态 送风机故障报警 送风机手自动状态
6DO TX-IO模块
TXM1.6R(2DO)
PF-CMD SF-CMD 排风机启停控制 送风机启停控制
6
DO6
0.0.6
很完整的网络端口表

一份很完整的网络端口表标题:一份很完整的网络端口表作者:孙空空时间:2010-11-2214:17 [font=verdana,geneva,lucida,]一份很完整的网络端口表--------------------------------------------------------------------------------1tcpmux TCP Port Service Multiplexer传输控制协议端口服务多路开关选择器2compressnet Management Utility compressnet管理实用程序3compressnet Compression Process压缩进程5rje Remote Job Entry远程作业登录7echo Echo回显9discard Discard丢弃11systat Active Users在线用户13daytime Daytime时间17qotd Quote of the Day每*引用18msp Message Send Protocol消息发送协议19chargen Character Generator字符发生器20ftp-data File Transfer[Default Data]文件传输协议(默认数据口)21ftp File Transfer[Control]文件传输协议(控制)22ssh SSH Remote Login Protocol SSH远程登录协议23telnet Telnet终端仿真协议24?any private mail system预留给个人用邮件系统25smtp Simple Mail Transfer简单邮件发送协议27nsw-fe NSW User System FE NSW用户系统现场工程师29msg-icp MSG ICP MSG ICP31msg-auth MSG Authentication MSG验证33dsp Display Support Protocol显示支持协议35?any private printer server预留给个人打印机服务37time Time时间38rap Route Access Protocol路由访问协议39rlp Resource Location Protocol资源定位协议41graphics Graphics图形42nameserver WINS Host Name Server WINS主机名服务43nicname Who Is"绰号"who is服务44mpm-flags MPM FLAGS Protocol MPM(消息处理模块)标志协议45mpm Message Processing Module[recv]消息处理模块46mpm-snd MPM[default send]消息处理模块(默认发送口)47ni-ftp NI FTP NI FTP48auditd Digital Audit Daemon数码音频后台服务49tacacs Login Host Protocol(TACACS)TACACS登录主机协议50re-mail-ck Remote Mail Checking Protocol远程邮件检查协议51la-maint IMP Logical Address Maintenance IMP(接口信息处理机)逻辑地址维护52xns-time XNS Time Protocol施乐网络服务系统时间协议53domain Domain Name Server域名服务器54xns-ch XNS Clearinghouse施乐网络服务系统票据交换55isi-gl ISI Graphics Language ISI图形语言56xns-auth XNS Authentication施乐网络服务系统验证57?any private terminal access预留个人用终端访问58xns-mail XNS Mail施乐网络服务系统邮件59?any private file service预留个人文件服务60?Unassigned未定义61ni-mail NI MAIL NI邮件?62acas ACA Services异步通63whois+whois+WHOIS+64covia Communications Integrator(CI)通讯接口65tacacs-ds TACACS-Database Service TACACS数据库服务66sql*net Oracle SQL*NET Oracle SQL*NET67bootps Bootstrap Protocol Server引导程序协议服务端68bootpc Bootstrap Protocol Client引导程序协议客户端69tftp Trivial File Transfer小型文件传输协议70gopher Gopher信息检索协议71netrjs-1Remote Job Service远程作业服务72netrjs-2Remote Job Service远程作业服务73netrjs-3Remote Job Service远程作业服务74netrjs-4Remote Job Service远程作业服务75?any private dial out service预留给个人拨出服务76deos Distributed External Object Store分布式外部对象存储77?any private RJE service预留给个人远程作业输入服务78vettcp vettcp修正TCP?79finger Finger FINGER(查询远程主机在线用户等信息) 80http World Wide Web HTTP全球信息网超文本传输协议81hosts2-ns HOSTS2Name Server HOST2名称服务82xfer XFER Utility传输实用程序83mit-ml-dev MIT ML Device模块化智能终端ML设备84ctf Common Trace Facility公用追踪设备85mit-ml-dev MIT ML Device模块化智能终端ML设备86mfcobol Micro Focus Cobol Micro Focus Cobol编程语言87?any private terminal link预留给个人终端连接88kerberos Kerberos Kerberros安全认证系统89su-mit-tg SU/MIT Telnet Gateway SU/MIT终端仿真网关90dnsix DNSIX Securit Attribute Token Map DNSIX安全属性标记图91mit-dov MIT Dover Spooler MIT Dover假脱机92npp Network Printing Protocol网络打印协议93dcp Device Control Protocol设备控制协议94objcall Tivoli Object Dispatcher Tivoli对象调度95supdup SUPDUP96dixie DIXIE Protocol Specification DIXIE协议规范97swift-rvf Swift Remote Virtural File Protocol快速远程虚拟文件协议98tacnews TAC News TAC(东京大学自动计算机?)新闻协议99metagram Metagram Relay[/font]标题:作者:孙空空时间:2010-11-2214:17 101/tcp hostname NIC Host Name Server102/tcp iso-tsap ISO-TSAP Class0103/tcp gppitnp Genesis Point-to-Point Trans Net104/tcp acr-nema ACR-NEMA Digital Imag.&Comm.300105/tcp cso CCSO name server protocol105/tcp csnet-ns Mailbox Name Nameserver106/tcp3com-tsmux3COM-TSMUX107/tcp rtelnet Remote Telnet Service108/tcp snagas SNA Gateway Access Server109/tcp pop2Post Office Protocol-Version2110/tcp pop3Post Office Protocol-Version3111/tcp sunrpc SUN Remote Procedure Call112/tcp mcidas McIDAS Data Transmission Protocol113/tcp ident114/tcp audionews Audio News Multicast115/tcp sftp Simple File Transfer Protocol116/tcp ansanotify ANSA REX Notify117/tcp uucp-path UUCP Path Service118/tcp sqlserv SQL Services119/tcp nntp Network News Transfer Protocol120/tcp cfdptkt CFDPTKT121/tcp erpc Encore Expedited Remote Pro.Call122/tcp smakynet SMAKYNET123/tcp ntp Network Time Protocol124/tcp ansatrader ANSA REX Trader125/tcp locus-map Locus PC-Interface Net Map Ser126/tcp unitary Unisys Unitary Login127/tcp locus-con Locus PC-Interface Conn Server128/tcp gss-xlicen GSS X License Verification129/tcp pwdgen Password Generator Protocol130/tcp cisco-fna cisco FNATIVE131/tcp cisco-tna cisco TNATIVE132/tcp cisco-sys cisco SYSMAINT133/tcp statsrv Statistics Service134/tcp ingres-net INGRES-NET Service135/tcp epmap DCE endpoint resolution136/tcp profile PROFILE Naming System137/tcp netbios-ns NETBIOS Name Service138/tcp netbios-dgm NETBIOS Datagram Service139/tcp netbios-ssn NETBIOS Session Service140/tcp emfis-data EMFIS Data Service141/tcp emfis-cntl EMFIS Control Service142/tcp bl-idm Britton-Lee IDM143/tcp imap Internet Message Access Protocol144/tcp uma Universal Management Architecture145/tcp uaac UAAC Protocol146/tcp iso-tp0ISO-IP0147/tcp iso-ip ISO-IP148/tcp jargon Jargon149/tcp aed-512AED512Emulation Service150/tcp sql-net SQL-NET151/tcp hems HEMS152/tcp bftp Background File Transfer Program153/tcp sgmp SGMP154/tcp netsc-prod NETSC155/tcp netsc-dev NETSC156/tcp sqlsrv SQL Service157/tcp knet-cmp KNET/VM Command/Message Protocol 158/tcp pcmail-srv PCMail Server159/tcp nss-routing NSS-Routing160/tcp sgmp-traps SGMP-TRAPS161/tcp snmp SNMP162/tcp snmptrap SNMPTRAP163/tcp cmip-man CMIP/TCP Manager164/tcp cmip-agent CMIP/TCP Agent165/tcp xns-courier Xerox166/tcp s-net Sirius Systems167/tcp namp NAMP168/tcp rsvd RSVD169/tcp send SEND170/tcp print-srv Network PostScript171/tcp multiplex Network Innovations Multiplex 172/tcp cl/1Network Innovations CL/1173/tcp xyplex-mux Xyplex174/tcp mailq MAILQ175/tcp vmnet VMNET176/tcp genrad-mux GENRAD-MUX177/tcp xdmcp X Display Manager Control Protocol 178/tcp nextstep NextStep Window Server179/tcp bgp Border Gateway Protocol180/tcp ris Intergraph181/tcp unify Unify182/tcp audit Unisys Audit SITP183/tcp ocbinder OCBinder184/tcp ocserver OCServer185/tcp remote-kis Remote-KIS186/tcp kis KIS Protocol187/tcp aci Application Communication Interface188/tcp mumps Plus Five磗MUMPS189/tcp qft Queued File Transport190/tcp gacp Gateway Access Control Protocol191/tcp prospero Prospero Directory Service192/tcp osu-nms OSU Network Monitoring System193/tcp srmp Spider Remote Monitoring Protocol194/tcp irc Internet Relay Chat Protocol195/tcp dn6-nlm-aud DNSIX Network Level Module Audit196/tcp dn6-smm-red DNSIX Session Mgt Module Audit Redir 197/tcp dls Directory Location Service198/tcp dls-mon Directory Location Service Monitor199/tcp smux SMUX200/tcp src IBM System Resource Controller201/tcp at-rtmp AppleTalk Routing Maintenance202/tcp at-nbp AppleTalk Name Binding203/tcp at-3AppleTalk Unused204/tcp at-echo AppleTalk Echo205/tcp at-5AppleTalk Unused206/tcp at-zis AppleTalk Zone Information207/tcp at-7AppleTalk Unused208/tcp at-8AppleTalk Unused209/tcp qmtp The Quick Mail Transfer Protocol210/tcp z39.50ANSI Z39.50211/tcp914c/g Texas Instruments914C/G Terminal212/tcp anet ATEXSSTR214/tcp vmpwscs VM PWSCS215/tcp softpc Insignia Solutions216/tcp CAIlic Computer Associates Int磍License Server 217/tcp dbase dBASE Unix218/tcp mpp Netix Message Posting Protocol219/tcp uarps Unisys ARPs220/tcp imap3Interactive Mail Access Protocol v3221/tcp fln-spx Berkeley rlogind with SPX auth222/tcp rsh-spx Berkeley rshd with SPX auth223/tcp cdc Certificate Distribution Center242/tcp direct Direct243/tcp sur-meas Survey Measurement244/tcp dayna Dayna245/tcp link LINK246/tcp dsp3270Display Systems Protocol247/tcp subntbcst_tftp SUBNTBCST_TFTP248/tcp bhfhs bhfhs256/tcp rap RAP257/tcp set Secure Electronic Transaction258/tcp yak-chat Yak Winsock Personal Chat259/tcp esro-gen Efficient Short Remote Operations260/tcp openport Openport263/tcp hdap HDAP264/tcp bgmp BGMP280/tcp http-mgmt http-mgmt309/tcp entrusttime EntrustTime310/tcp bhmds bhmds312/tcp vslmp VSLMP315/tcp dpsi DPSI316/tcp decauth decAuth317/tcp zannet Zannet321/tcp pip PIP344/tcp pdap Prospero Data Access Protocol345/tcp pawserv Perf Analysis Workbench346/tcp zserv Zebra server347/tcp fatserv Fatmen Server348/tcp csi-sgwp Cabletron Management Protocol349/tcp mftp mftp351/tcp matip-type-b MATIP Type B351/tcp bhoetty bhoetty(added5/21/97)353/tcp ndsauth NDSAUTH354/tcp bh611bh611357/tcp bhevent bhevent362/tcp srssend SRS Send365/tcp dtk DTK366/tcp odmr ODMR368/tcp qbikgdp QbikGDP371/tcp clearcase Clearcase372/tcp ulistproc ListProcessor373/tcp legent-1Legent Corporation374/tcp legent-2标题:作者:孙空空时间:2010-11-2214:180通常用于分析操作系统。
信息点端口对应表
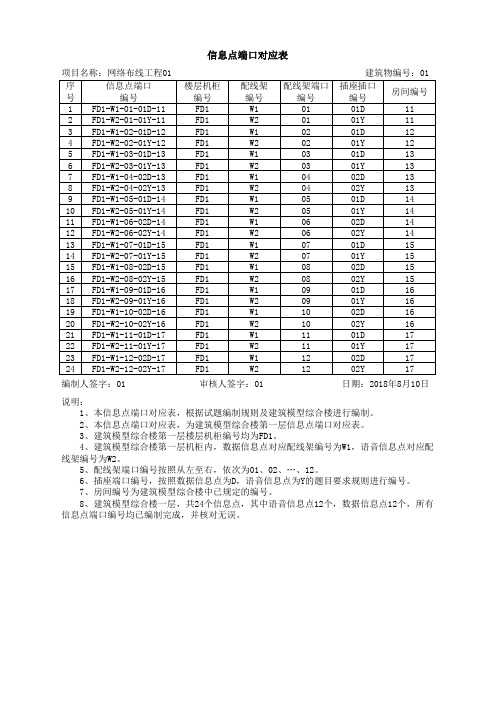
信息点端口对应表
项目名称:网络布线工程01 建筑物编号:01
编制人签字:01 审核人签字:01 日期:2018年8月10日说明:
1、本信息点端口对应表,根据试题编制规则及建筑模型综合楼进行编制。
2、本信息点端口对应表,为建筑模型综合楼第一层信息点端口对应表。
3、建筑模型综合楼第一层楼层机柜编号均为FD1。
4、建筑模型综合楼第一层机柜内,数据信息点对应配线架编号为W1,语音信息点对应配线架编号为W2。
5、配线架端口编号按照从左至右,依次为01、02、 (12)
6、插座端口编号,按照数据信息点为D,语音信息点为Y的题目要求规则进行编号。
7、房间编号为建筑模型综合楼中已规定的编号。
8、建筑模型综合楼一层,共24个信息点,其中语音信息点12个,数据信息点12个,所有信息点端口编号均已编制完成,并核对无误。
【VIP专享】综合布线技术表格及计算

配线架配线架与跳线架的区别配线架是管理子系统中最重要的组件,实现垂直子系统和水平子系统连接。
在网络工程中常用的配线架有双绞线配线架和光纤配线架。
跳线架看起来一排排象鱼骨头一样,也称为鱼骨架。
一般是电话连线使用的。
配线架有分支和分配功能,而跳线架只是起中继和中间转接的作用。
综合布线工程常用缩略词1CD建筑群配线设备2BD建筑物配线设备3FD楼层配线设备4TO信息插座模块工作区设计时,可按以下三步进行:根据楼层平面图计算每层楼布线面积。
估算信息引出插座数量,一般设计两种平面图供用户选择。
为基本型设计出每9平方米一个信息引出插座;为增强型或综合型设计出两个信息引出插座;确定信息引出插座的类型。
新建建筑一般采用暗装,旧楼改造一般采用明装计算:确定信息插座数量。
N=上取整(M/A)(N:信息插座数量,M:信息点数量,A:信息插座插孔数)P=N+N×3%(P:信息插座的总量,N为信息插座数量,N×3%为富余量)确定RJ-45接头的数量。
m=n×4+n×4×15%(m:总需求量,n:信息点的总量,n×4×15%:余量)线缆截面积计算:按照线缆直径6毫米计算双绞线的截面积。
S=d2×3.14/4=62×3.14/4=28.26其中:S---表示双绞线截面积d---双绞线直径线管规格一般用线管的外径表示,线管内布线容积截面积应该按照线管的内直径计算,管壁厚1毫米。
以管径25毫米PVC管为例,管内部直径为23毫米。
截面积为:S=d2×3.14/4=232×3.14/4=415.265线槽截面积计算线槽规格一般用线槽的外部长度和宽度表示,线槽内布线容积截面积计算按照线槽的内部长和宽计算,线槽壁厚1毫米以40×20线槽为例,线槽内部长38毫米,宽18毫米,其截面积计算如下:S=L×W=38×18=684纳双绞线最多数量计算线槽(管)内允许穿线的最大面积70%考虑线缆之间的间隙和拐弯等因素,浪费空间50-60%。
端口对照表

注意:由于一些应用软件占用了部分端口,因此此文件中的部分端口被注释掉了(注释的字符为://)。
TCP 1=TCP Port Service MultiplexerTCP 2=DeathTCP 5=Remote Job Entry,yoyoTCP 7=EchoTCP 11=SkunTCP 12=BomberTCP 16=SkunTCP 17=SkunTCP 18=消息传输协议,skunTCP 19=SkunTCP 20=FTP Data,AmandaTCP 21=文件传输,Back Construction,Blade Runner,Doly Trojan,Fore,FTPtrojan,Invisible FTP,Larva, WebEx,WinCrashTCP 22=远程登录协议TCP 23=远程登录(Telnet),Tiny Telnet Server (= TTS)TCP 25=电子邮件(SMTP),Ajan,Antigen,Email Password Sender,Happy99,Kuang2,ProMail trojan,Shtrilitz,Stealth,Tapiras,Terminator,WinPC,WinSpy,Haebu CocedaTCP 27=AssasinTCP 28=AmandaTCP 29=MSG ICPTCP 30=Agent 40421TCP 31=Agent 31,Hackers Paradise,Masters Paradise,Agent 40421TCP 37=Time,ADM wormTCP 39=SubSARITCP 41=DeepThroat,ForeplayTCP 42=Host Name ServerTCP 43=WHOISTCP 44=ArcticTCP 48=DRATTCP 49=主机登录协议TCP 50=DRATTCP 51=IMP Logical Address Maintenance,Fuck Lamers BackdoorTCP 52=MuSka52,SkunTCP 53=DNS,Bonk (DOS Exploit)TCP 54=MuSka52TCP 58=DMSetupTCP 59=DMSetupTCP 63=whois++TCP 64=Communications IntegratorTCP 65=TACACS-Database ServiceTCP 66=Oracle SQL*NET,AL-BarekiTCP 67=Bootstrap Protocol ServerTCP 68=Bootstrap Protocol ClientTCP 69=W32.Evala.Worm,BackGate Kit,Nimda,Pasana,Storm,Storm worm,Theef,Worm.Cycle.aTCP 70=Gopher服务,ADM wormTCP 79=用户查询(Finger),Firehotcker,ADM wormTCP 80=超文本服务器(Http),Executor,RingZeroTCP 81=Chubo,Worm.Bbeagle.qTCP 82=Netsky-ZTCP 88=Kerberos krb5服务TCP 99=Hidden PortTCP 102=消息传输代理TCP 108=SNA网关访问服务器TCP 109=Pop2TCP 110=电子邮件(Pop3),ProMailTCP 113=Kazimas, Auther IdnetTCP 115=简单文件传输协议TCP 118=SQL Services, Infector 1.4.2TCP 119=新闻组传输协议(Newsgroup(Nntp)), Happy 99TCP 121=JammerKiller, Bo jammerkillahTCP 123=网络时间协议(NTP),Net ControllerTCP 129=Password Generator ProtocolTCP 133=Infector 1.xTCP 135=微软DCE RPC end-point mapper服务TCP 137=微软Netbios Name服务(网上邻居传输文件使用)TCP 138=微软Netbios Name服务(网上邻居传输文件使用)TCP 139=微软Netbios Name服务(用于文件及打印机共享)TCP 142=NetTaxiTCP 143=IMAPTCP 146=FC Infector,InfectorTCP 150=NetBIOS Session ServiceTCP 156=SQL服务器TCP 161=SnmpTCP 162=Snmp-TrapTCP 170=A-TrojanTCP 177=X Display管理控制协议TCP 179=Border网关协议(BGP)TCP 190=网关访问控制协议(GACP)TCP 194=IrcTCP 197=目录定位服务(DLS)TCP 256=NirvanaTCP 315=The InvasorTCP 371=ClearCase版本管理软件TCP 389=Lightweight Directory Access Protocol (LDAP)TCP 396=Novell Netware over IPTCP 420=BreachTCP 421=TCP WrappersTCP 443=安全服务TCP 444=Simple Network Paging Protocol(SNPP)TCP 445=Microsoft-DSTCP 455=Fatal ConnectionsTCP 456=Hackers paradise,FuseSparkTCP 458=苹果公司QuickTimeTCP 513=GrloginTCP 514=RPC BackdoorTCP 531=Rasmin,Net666TCP 544=kerberos kshellTCP 546=DHCP ClientTCP 547=DHCP ServerTCP 548=Macintosh文件服务TCP 555=Ini-Killer,Phase Zero,Stealth SpyTCP 569=MSNTCP 605=SecretServiceTCP 606=Noknok8TCP 661=Noknok8TCP 666=Attack FTP,Satanz Backdoor,Back Construction,Dark Connection Inside 1.2 TCP 667=Noknok7.2TCP 668=Noknok6TCP 669=DP trojanTCP 692=GayOLTCP 707=WelchiaTCP 777=AIM SpyTCP 808=RemoteControl,WinHoleTCP 815=Everyone DarlingTCP 901=Backdoor.DevilTCP 911=Dark ShadowTCP 993=IMAPTCP 999=DeepThroatTCP 1000=Der SpaeherTCP 1001=Silencer,WebEx,Der SpaeherTCP 1003=BackDoorTCP 1010=DolyTCP 1011=DolyTCP 1012=DolyTCP 1015=DolyTCP 1016=DolyTCP 1020=VampireTCP 1023=Worm.Sasser.eTCP 1024=NetSpy.698(YAI)TCP 1059=nimreg//TCP 1025=NetSpy.698,Unused Windows Services Block//TCP 1026=Unused Windows Services Block//TCP 1027=Unused Windows Services Block//TCP 1028=Unused Windows Services Block//TCP 1029=Unused Windows Services Block//TCP 1030=Unused Windows Services Block//TCP 1033=Netspy//TCP 1035=Multidropper//TCP 1042=Bla//TCP 1045=Rasmin//TCP 1047=GateCrasher//TCP 1050=MiniCommandTCP 1069=Backdoor.TheefServer.202TCP 1070=Voice,Psyber Stream Server,Streaming Audio Trojan TCP 1080=Wingate,Worm.BugBear.B,Worm.Novarg.B//TCP 1090=Xtreme, VDOLive//TCP 1095=Rat//TCP 1097=Rat//TCP 1098=Rat//TCP 1099=RatTCP 1110=nfsd-keepaliveTCP 1111=Backdoor.AIMVisionTCP 1155=Network File Access//TCP 1170=Psyber Stream Server,Streaming Audio trojan,Voice //TCP 1200=NoBackO//TCP 1201=NoBackO//TCP 1207=Softwar//TCP 1212=Nirvana,Visul Killer//TCP 1234=Ultors//TCP 1243=BackDoor-G, SubSeven, SubSeven Apocalypse//TCP 1245=VooDoo Doll//TCP 1269=Mavericks Matrix//TCP 1313=Nirvana//TCP 1349=BioNetTCP 1433=Microsoft SQL服务//TCP 1441=Remote Storm//TCP 1492=FTP99CMP(BackOriffice.FTP)TCP 1503=NetMeeting T.120//TCP 1509=Psyber Streaming Server//TCP 1600=Shivka-Burka//TCP 1703=Exloiter 1.1TCP 1720=NetMeeting H.233 call SetupTCP 1731=NetMeeting音频调用控制//TCP 1807=SpySender//TCP 1966=Fake FTP 2000//TCP 1976=Custom port//TCP 1981=ShockraveTCP 1990=stun-p1 cisco STUN Priority 1 portTCP 1990=stun-p1 cisco STUN Priority 1 portTCP 1991=stun-p2 cisco STUN Priority 2 portTCP 1992=stun-p3 cisco STUN Priority 3 port,ipsendmsg IPsendmsg TCP 1993=snmp-tcp-port cisco SNMP TCP portTCP 1994=stun-port cisco serial tunnel portTCP 1995=perf-port cisco perf portTCP 1996=tr-rsrb-port cisco Remote SRB portTCP 1997=gdp-port cisco Gateway Discovery ProtocolTCP 1998=x25-svc-port cisco X.25 service (XOT)//TCP 1999=BackDoor, TransScout//TCP 2000=Der Spaeher,INsane NetworkTCP 2002=W32.Beagle.AX @mm//TCP 2001=Transmisson scout//TCP 2002=Transmisson scout//TCP 2003=Transmisson scout//TCP 2004=Transmisson scout//TCP 2005=TTransmisson scoutTCP 2011=cypressTCP 2015=raid-cs//TCP 2023=Ripper,Pass Ripper,Hack City Ripper ProTCP 2049=NFS//TCP 2115=Bugs//TCP 2121=Nirvana//TCP 2140=Deep Throat, The Invasor//TCP 2155=Nirvana//TCP 2208=RuX//TCP 2255=Illusion Mailer//TCP 2283=HVL Rat5//TCP 2300=PC Explorer//TCP 2311=Studio54TCP 2556=Worm.Bbeagle.q//TCP 2565=Striker//TCP 2583=WinCrash//TCP 2600=Digital RootBeer//TCP 2716=Prayer TrojanTCP 2745=Worm.BBeagle.k//TCP 2773=Backdoor,SubSeven//TCP 2774=SubSeven2.1&2.2//TCP 2801=Phineas Phucker//TCP 2989=Rat//TCP 3024=WinCrash trojanTCP 3127=Worm.NovargTCP 3128=RingZero,Worm.Novarg.B//TCP 3129=Masters Paradise//TCP 3150=Deep Throat, The InvasorTCP 3198=Worm.Novarg//TCP 3210=SchoolBusTCP 3332=Worm.Cycle.aTCP 3333=ProsiakTCP 3389=超级终端//TCP 3456=Terror//TCP 3459=Eclipse 2000//TCP 3700=Portal of Doom//TCP 3791=Eclypse//TCP 3801=EclypseTCP 3996=Portal of DoomTCP 4000=腾讯QQ客户端TCP 4060=Portal of DoomTCP 4092=WinCrashTCP 4242=VHMTCP 4267=SubSeven2.1&2.2TCP 4321=BoBoTCP 4444=Prosiak,Swift remoteTCP 4500=W32.HLLW.TufasTCP 4567=File NailTCP 4590=ICQTrojanTCP 4899=Remote Administrator服务器TCP 4950=ICQTrojanTCP 5000=WindowsXP服务器,Blazer 5,Bubbel,Back Door Setup,Sockets de Troie TCP 5001=Back Door Setup, Sockets de TroieTCP 5002=cd00r,ShaftTCP 5011=One of the Last Trojans (OOTLT) TCP 5025=WM Remote KeyLoggerTCP 5031=Firehotcker,Metropolitan,NetMetro TCP 5032=MetropolitanTCP 5190=ICQ QueryTCP 5321=FirehotckerTCP 5333=Backage Trojan Box 3TCP 5343=WCratTCP 5400=Blade Runner, BackConstruction1.2 TCP 5401=Blade Runner,Back Construction TCP 5402=Blade Runner,Back Construction TCP 5471=WinCrashTCP 5512=Illusion MailerTCP 5521=Illusion MailerTCP 5550=Xtcp,INsane NetworkTCP 5554=Worm.SasserTCP 5555=ServeMeTCP 5556=BO FacilTCP 5557=BO FacilTCP 5569=Robo-HackTCP 5598=BackDoor 2.03TCP 5631=PCAnyWhere dataTCP 5632=PCAnyWhereTCP 5637=PC CrasherTCP 5638=PC CrasherTCP 5698=BackDoorTCP 5714=Wincrash3TCP 5741=WinCrash3TCP 5742=WinCrashTCP 5760=Portmap Remote Root Linux Exploit TCP 5880=Y3K RATTCP 5881=Y3K RATTCP 5882=Y3K RATTCP 5888=Y3K RATTCP 5889=Y3K RATTCP 5900=WinVnc,Wise VGA广播端口TCP 6000=Backdoor.ABTCP 6006=Noknok8TCP 6129=Dameware Nt Utilities服务器TCP 6272=SecretServiceTCP 6267=广外女生TCP 6400=Backdoor.AB,The ThingTCP 6500=Devil 1.03TCP 6661=TemanTCP 6666=TCPshell.cTCP 6667=NT Remote Control,Wise 播放器接收端口TCP 6668=Wise Video广播端口TCP 6669=VampyreTCP 6670=DeepThroat,iPhoneTCP 6671=Deep Throat 3.0TCP 6711=SubSevenTCP 6712=SubSeven1.xTCP 6713=SubSevenTCP 6723=MstreamTCP 6767=NT Remote ControlTCP 6771=DeepThroatTCP 6776=BackDoor-G,SubSeven,2000 Cracks TCP 6777=Worm.BBeagleTCP 6789=Doly TrojanTCP 6838=MstreamTCP 6883=DeltaSourceTCP 6912=Shit HeepTCP 6939=IndoctrinationTCP 6969=GateCrasher, Priority, IRC 3TCP 6970=RealAudio,GateCrasherTCP 7000=Remote Grab,NetMonitor,SubSeven1.x TCP 7001=Freak88TCP 7201=NetMonitorTCP 7215=BackDoor-G, SubSevenTCP 7001=Freak88,Freak2kTCP 7300=NetMonitorTCP 7301=NetMonitorTCP 7306=NetMonitor,NetSpy 1.0TCP 7307=NetMonitor, ProcSpyTCP 7308=NetMonitor, X SpyTCP 7323=Sygate服务器端TCP 7424=Host ControlTCP 7597=QazTCP 7609=Snid X2TCP 7626=冰河TCP 7777=The ThingTCP 7789=Back Door Setup, ICQKillerTCP 7983=MstreamTCP 8000=腾讯OICQ服务器端,XDMATCP 8010=Wingate,LogfileTCP 8080=WWW 代理,Ring Zero,Chubo,Worm.Novarg.B TCP 8520=W32.Socay.WormTCP 8787=BackOfrice 2000TCP 8897=Hack Office,ArmageddonTCP 8989=ReconTCP 9000=NetministratorTCP 9325=MstreamTCP 9400=InCommand 1.0TCP 9401=InCommand 1.0TCP 9402=InCommand 1.0TCP 9872=Portal of DoomTCP 9873=Portal of DoomTCP 9874=Portal of DoomTCP 9875=Portal of DoomTCP 9876=Cyber AttackerTCP 9878=TransScoutTCP 9989=Ini-KillerTCP 9898=Worm.Win32.Dabber.aTCP 9999=Prayer TrojanTCP 10067=Portal of DoomTCP 10080=Worm.Novarg.BTCP 10084=SyphillisTCP 10085=SyphillisTCP 10086=SyphillisTCP 10101=BrainSpyTCP 10167=Portal Of DoomTCP 10168=Worm.Supnot.78858.c,Worm.LovGate.TTCP 10520=Acid ShiversTCP 10607=Coma trojanTCP 10666=AmbushTCP 11000=Senna SpyTCP 11050=Host ControlTCP 11051=Host ControlTCP 11223=Progenic,Hack '99KeyLoggerTCP 11831=TROJ_LATINUS.SVRTCP 12076=Gjamer, MSH.104bTCP 12223=Hack'99 KeyLoggerTCP 12345=GabanBus, NetBus 1.6/1.7, Pie Bill Gates, X-bill TCP 12346=GabanBus, NetBus 1.6/1.7, X-billTCP 12349=BioNetTCP 12361=Whack-a-moleTCP 12362=Whack-a-moleTCP 12363=Whack-a-moleTCP 12378=W32/Gibe@MMTCP 12456=NetBusTCP 12623=DUN ControlTCP 12624=ButtmanTCP 12631=WhackJob, WhackJob.NB1.7TCP 12701=Eclipse2000TCP 12754=MstreamTCP 13000=Senna SpyTCP 13010=Hacker BrazilTCP 13013=PsychwardTCP 13223=Tribal Voice的聊天程序PowWowTCP 13700=Kuang2 The VirusTCP 14456=SoleroTCP 14500=PC InvaderTCP 14501=PC InvaderTCP 14502=PC InvaderTCP 14503=PC InvaderTCP 15000=NetDaemon 1.0TCP 15092=Host ControlTCP 15104=MstreamTCP 16484=MosuckerTCP 16660=Stacheldraht (DDoS)TCP 16772=ICQ RevengeTCP 16959=PriorityTCP 16969=PriorityTCP 17027=提供广告服务的Conducent"adbot"共享软件TCP 17166=MosaicTCP 17300=Kuang2 The VirusTCP 17490=CrazyNetTCP 17500=CrazyNetTCP 17569=Infector 1.4.x + 1.6.xTCP 17777=NephronTCP 18753=Shaft (DDoS)TCP 19191=蓝色火焰TCP 19864=ICQ RevengeTCP 20000=Millennium II (GrilFriend)TCP 20001=Millennium II (GrilFriend)TCP 20002=AcidkoRTCP 20034=NetBus 2 ProTCP 20168=LovgateTCP 20203=Logged,ChupacabraTCP 20331=BlaTCP 20432=Shaft (DDoS)TCP 20808=Worm.LovGate.v.QQTCP 21544=Schwindler 1.82,GirlFriendTCP 21554=Schwindler 1.82,GirlFriend,Exloiter 1.0.1.2TCP 22222=Prosiak,RuX Uploader 2.0TCP 22784=Backdoor.IntruzzoTCP 23432=Asylum 0.1.3TCP 23456=Evil FTP, Ugly FTP, WhackJobTCP 23476=Donald DickTCP 23477=Donald DickTCP 23777=INet SpyTCP 26274=DeltaTCP 26681=Spy VoiceTCP 27374=Sub Seven 2.0+, Backdoor.BasteTCP 27444=Tribal Flood Network,TrinooTCP 27665=Tribal Flood Network,TrinooTCP 29431=Hack AttackTCP 29432=Hack AttackTCP 29104=Host ControlTCP 29559=TROJ_LATINUS.SVRTCP 29891=The UnexplainedTCP 30001=Terr0r32TCP 30003=Death,Lamers DeathTCP 30029=AOL trojanTCP 30100=NetSphere 1.27a,NetSphere 1.31TCP 30101=NetSphere 1.31,NetSphere 1.27aTCP 30102=NetSphere 1.27a,NetSphere 1.31TCP 30103=NetSphere 1.31TCP 30303=Sockets de TroieTCP 30947=IntruseTCP 30999=Kuang2TCP 21335=Tribal Flood Network,TrinooTCP 31336=Bo WhackTCP 31337=Baron Night,BO client,BO2,Bo Facil,BackFire,Back Orifice,DeepBO,Freak2k,NetSpyTCP 31338=NetSpy,Back Orifice,DeepBOTCP 31339=NetSpy DKTCP 31554=SchwindlerTCP 31666=BOWhackTCP 31778=Hack AttackTCP 31785=Hack AttackTCP 31787=Hack AttackTCP 31789=Hack AttackTCP 31791=Hack AttackTCP 31792=Hack AttackTCP 32100=PeanutBrittleTCP 32418=Acid BatteryTCP 33333=Prosiak,Blakharaz 1.0TCP 33577=Son Of PsychwardTCP 33777=Son Of PsychwardTCP 33911=Spirit 2001aTCP 34324=BigGluck,TN,Tiny Telnet Server TCP 34555=Trin00 (Windows) (DDoS)TCP 35555=Trin00 (Windows) (DDoS)TCP 36794=Worm.Bugbear-ATCP 37651=YATTCP 40412=The SpyTCP 40421=Agent 40421,Masters Paradise.96 TCP 40422=Masters ParadiseTCP 40423=Masters Paradise.97TCP 40425=Masters ParadiseTCP 40426=Masters Paradise 3.xTCP 41666=Remote BootTCP 43210=Schoolbus 1.6/2.0TCP 44444=Delta SourceTCP 44445=HappypigTCP 47252=ProsiakTCP 47262=DeltaTCP 47878=BirdSpy2TCP 49301=Online KeyloggerTCP 50505=Sockets de TroieTCP 50766=Fore, SchwindlerTCP 51966=CafeIniTCP 53001=Remote Windows ShutdownTCP 53217=Acid Battery 2000TCP 54283=Back Door-G, Sub7TCP 54320=Back Orifice 2000,SheepTCP 54321=School Bus .69-1.11,Sheep, BO2K TCP 57341=NetRaiderTCP 58008=BackDoor.TronTCP 58009=BackDoor.TronTCP 58339=ButtFunnelTCP 59211=BackDoor.DuckToyTCP 60000=Deep ThroatTCP 60068=Xzip 6000068TCP 60411=ConnectionTCP 60606=TROJ_BCKDOR.G2.A TCP 61466=TelecommandoTCP 61603=Bunker-killTCP 63485=Bunker-killTCP 65000=Devil, DDoSTCP 65432=Th3tr41t0r, The Traitor TCP 65530=TROJ_WINMITE.10TCP 65535=RC,Adore Worm/Linux TCP 69123=ShitHeepTCP 88798=Armageddon,Hack Office。
常见网络端口对照表(Excel)

端口协议描述状态0TCP,UDP保留端口;不使用(若发送过程不准备接受回复消息,则可以作为源端口)官方1TCP,UDP TCPMUX(传输控制协议端口服务多路开关选择器)官方5TCP,UDP RJE(远程作业登录)官方7TCP,UDP ECHO(回显)协议官方9TCP,UDP DISCARD(丢弃)协议官方11TCP,UDP SYSTAT协议官方13TCP,UDP DAYTIME协议官方15TCP,UDP NETSTAT协议官方17TCP,UDP QOTD(Quote of the Day,每日引用)协议官方18TCP,UDP消息发送协议官方19TCP,UDP CHARGEN(字符发生器)协议官方20TCP,UDP文件传输协议(FTP) - 默认数据端口官方21TCP,UDP文件传输协议(FTP) - 控制端口官方22TCP,UDP SSH (Secure Shell) - 远程登录协议,用于安全登录 文件传输(SCP,SFTP)及端口重官方23TCP,UDP Telnet 终端仿真协议 - 未加密文本通信官方25TCP,UDP SMTP(简单邮件传输协议) - 用于邮件服务器间的电子邮件传递官方26TCP,UDP RSFTP - 一个简单的类似FTP的协议非官方35TCP,UDP QMS Magicolor 2 printer非官方37TCP,UDP TIME时间协议官方39TCP,UDP Resource Location Protocol(资源定位协议)官方41TCP,UDP图形官方42TCP,UDP Host Name Server(主机名服务)官方42TCP,UDP WINS(WINS主机名服务)非官方43TCP WHOIS 协议官方49TCP,UDP TACACS 登录主机协议官方53TCP,UDP DNS(域名服务系统)官方56TCP,UDP远程访问协议官方57TCP MTP,邮件传输协议67UDP BOOTP(BootStrap协议)服务;同时用于DHCP(动态主机设定协议)官方68UDP BOOTP 客户端;同时用于DHCP(动态主机设定协议)官方69UDP TFTP(小型文件传输协议)官方70TCP Gopher信息检索协议官方79TCP Finger协议官方80TCP HTTP(超文本传输协议)- 用于传输网页官方81TCP HTTP预备(超文本传输协议)官方81TCP Torpark - Onion routing ORport非官方82UDP Torpark - 控制端口非官方88TCP Kerberos - 认证代理官方101TCP主机名102TCP ISO-TSAP 协议107TCP远程Telnet协议109TCP POP(Post Office Protocol),“邮局协议”,第2版110TCP POP3(“邮局协议”,第3版)- 用于接收电子邮件官方111TCP,UDP Sun协议官方113TCP ident - old server identification system, 仍然被IRC 服务器用来认证它的用户官方115TCP SFTP, 简单文件传输协议117TCP UUCP-PATH118TCP,UDP SQL 服务官方119TCP NNTP (Network News Transfer Protocol) - 用来收取新闻组的消息官方123UDP NTP (Network Time Protocol) - used for time synchronization官方135TCP,UDP EPMAP (End Point Mapper) / Microsoft RPC Locator Service官方137TCP,UDP NetBIOS NetBIOS Name Service官方138TCP,UDP NetBIOS NetBIOS Datagram Service官方139TCP,UDP NetBIOS NetBIOS Session Service官方143TCP,UDP IMAP4 (Internet Message Access Protocol 4) - used for retrieving E-mails官方152TCP,UDP BFTP, Background File Transfer Program153TCP,UDP SGMP, Simple Gateway Monitoring Protocol156TCP,UDP SQL Service官方158TCP,UDP DMSP, Distributed Mail Service Protocol161TCP,UDP SNMP (Simple Network Management Protocol)官方162TCP,UDP SNMPTRAP官方170TCP Print-srv179TCP BGP (Border Gateway Protocol)官方194TCP IRC (Internet Relay Chat)官方201TCP,UDP AppleTalk Routing Maintenance209TCP,UDP The Quick Mail Transfer Protocol213TCP,UDP IPX官方218TCP,UDP MPP, Message Posting Protocol220TCP,UDP IMAP, Interactive Mail Access Protocol, version 3259TCP,UDP ESRO, Efficient Short Remote Operations264TCP,UDP BGMP,Border Gateway Multicast Protocol308TCP Novastor Online Backup官方311TCP Apple Server-Admin-Tool, Workgroup-Manager-Tool318TCP,UDP TSP, Time Stamp Protocol323TCP,UDP IMMP, Internet Message Mapping Protocol383TCP,UDP HP OpenView HTTPs Operations Agent366TCP,UDP SMTP, Simple Mail Transfer Protocol. ODMR, On-Demand Mail Relay369TCP,UDP Rpc2portmap官方371TCP,UDP ClearCase albd官方384TCP,UDP A Remote Network Server System387TCP,UDP AURP, AppleTalk Update-based Routing Protocol389TCP,UDP LDAP (Lightweight Directory Access Protocol)官方401TCP,UDP UPS Uninterruptible Power Supply官方411TCP Direct Connect Hub port非官方412TCP Direct Connect Client-To-Client port非官方427TCP,UDP SLP (Service Location Protocol)官方443TCP HTTPS - HTTP Protocol over TLS/SSL (encrypted transmission)官方444TCP,UDP SNPP,Simple Network Paging Protocol445TCP Microsoft-DS (Active Directory,Windows shares, Sasser worm,Agobot, Zobotwor官方445UDP Microsoft-DS SMB file sharing官方464TCP,UDP Kerberos Change/Set password官方465TCP Cisco protocol官方465TCP SMTP over SSL非官方475TCP tcpnethaspsrv (Hasp services, TCP/IP version)官方497TCP dantz backup service官方500TCP,UDP ISAKMP,IKE-Internet Key Exchange官方502TCP,UDP Modbus,Protocol512TCP exec, Remote Process Execution512UDP comsat, together with biff:notifies users of new c.q. yet unread e-mail513TCP Login513UDP Who514TCP rsh514UDP syslog protocol - used for system logging官方515TCP Line Printer Daemon protocol - used in LPD printer servers517UDP Talk518UDP NTalk520TCP efs520UDP Routing - RIP官方513UDP Router524TCP,UDP NCP (NetWare Core Protocol) is used for a variety things such as access to pr官方525UDP Timed, Timeserver530TCP,UDP RPC官方531TCP,UDP AOL Instant Messenger, IRC非官方532TCP netnews533UDP netwall, For Emergency Broadcasts540TCP UUCP (Unix-to-Unix Copy Protocol)官方542TCP,UDP commerce (Commerce Applications)官方543TCP klogin, Kerberos login544TCP kshell, Kerberos Remote shell546TCP,UDP DHCPv6 client547TCP,UDP DHCPv6 server548TCP AFP(Apple Filing Protocol)550UDP new-rwho, new-who554TCP,UDP RTSP (Real Time Streaming Protocol)官方556TCP Remotefs, rfs, rfs_server560UDP rmonitor, Remote Monitor561UDP monitor563TCP,UDP NNTP protocol over TLS/SSL (NNTPS)官方587TCP email message submission(SMTP) (RFC 2476)官方591TCP FileMaker 6.0 (and later) Web Sharing (HTTP Alternate, see port 80)官方593TCP,UDP HTTP RPC Ep Map(RPC over HTTP, often used by DCOM services and Microsoft Exc官方604TCP TUNNEL631TCP,UDP IPP,Internet Printing Protocol636TCP,UDP LDAP over SSL (encrypted transmission, also known as LDAPS)官方639TCP,UDP MSDP, Multicast Source Discovery Protocol646TCP LDP, Label Distribution Protocol647TCP DHCP Failover Protocol648TCP RRP, Registry Registrar Protocol652TCP DTCP, Dynamic Tunnel Configuration Protocol654UDP AODV, Ad hoc On-Demand Distance Vector665TCP sun-dr, Remote Dynamic Reconfiguration非官方666UDP毁灭战士,电脑平台上的一系列第一人称射击游戏。
