最新ccnp的试题全中文
思科认证CCNP经典试题

思科认证CCNP经典试题第一部分填空题1、在Cisco体系的IGP协议中,RIP的A-D管理距离是,EIGRP 的域内A-D管理距离是,EIGRP的域外A-D管理距离是OSPF的A-D管理距离是。
BGP 从EBGP学习到的路由学到路由的A-D管理距离是; BGP从IBGP学习到的路由学到路由的A-D管理距离是。
2、BGP的默认MED值为;其中MED越越优选被用于选路;BGP从邻居哪里学到的权重为;BGP自己本路由产生的路由(始发路由)产生权重是;BGP 的默认本地优先级为:。
3、BGP的邻居分为和。
4、OSPF在那个区域(有区域0,区域1,区域2)广播多路访问(比如以太网,没有出现外部网络),在区域0可以看到类LSA。
如果想看到2类LSA,必须在网络类型;在NSSA区域可以看到类LSA,在纯粹的NASS区域内是否有5类LSA?(回答是或者否)。
5、HSRP包括哪六种状态?6、OSPF在MA网络链路类型的HELLO报文作用?(3种)7、IPV6的本地链路地址是;本地站点地址是。
(没有/10的写法)8、在选择STP的角色(身份)有哪些?,默认STP的收敛时间为。
配置了portfast后,收敛时间会小于。
9、OSPF发送hello包的组播地址是,EIGRP组播地址是;HSRP 发送hello包组播地址是;VRRP发送hello 包的组播地址是。
10、目前以太通道最多可以使用条物理线缆逻辑捆绑成一个以太通道接口?形成以太通道方式有。
11、BGP在EBGP中使用属性避免AS间的环路(确保无环),该属性属于BGP的必遵属性,其中还有哪两个是BGP公认必遵属性为和。
第二部分选择1、在对基于CEF的多层交换(MLS)进行排错的时候,例如解决无法到达特定的IP目标等问题,首先需要先查看哪两张表去验证错误?()A、IP路由表和路由表B、IP路由和CEF邻接关系表C、TCAM中的IP CEF FIB和邻接关系表D、IP路由表和ARP表2、EIGRP位一个混合距离矢量协议,在METRIC值中使用K1-K5五个K值,默认情况下,使用K值分别是()A、K1,K2 B K3,K4 C、K1,K5 D、K1,K33、OSPF中router-id能标识一台设备的身份,下面说法正确的是()A、先选举手工配置,然后选择设备loopback地址大的,在选运行了宣告进OSPF最大的物理接口最大的地址。
CCNP最新题库 SWITCH 642-813-2
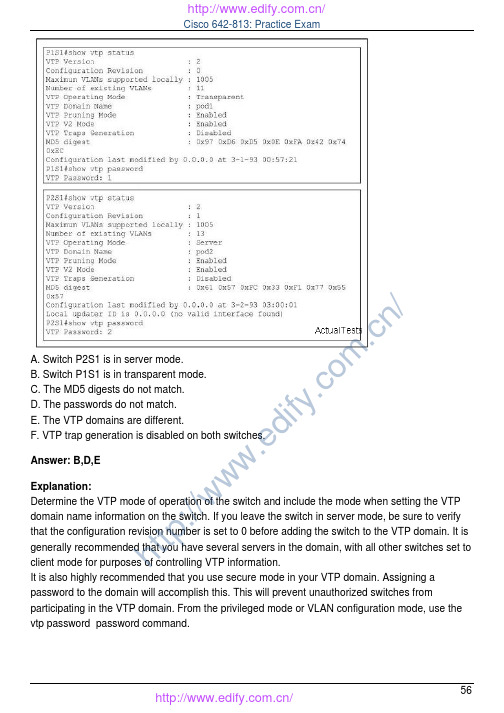
A. Switch P2S1 is in server mode.B. Switch P1S1 is in transparent mode.C. The MD5 digests do not match.D. The passwords do not match.E. The VTP domains are different.F. VTP trap generation is disabled on both switches.Answer: B,D,EExplanation:Determine the VTP mode of operation of the switch and include the mode when setting the VTP domain name information on the switch. If you leave the switch in server mode, be sure to verify that the configuration revision number is set to 0 before adding the switch to the VTP domain. It is generally recommended that you have several servers in the domain, with all other switches set to client mode for purposes of controlling VTP information.It is also highly recommended that you use secure mode in your VTP domain. Assigning a password to the domain will accomplish this. This will prevent unauthorized switches fromparticipating in the VTP domain. From the privileged mode or VLAN configuration mode, use the vtp password password command.h t t p://www.ed if y.co m .cn /QUESTION NO: 75Refer to the exhibit. Based upon the output of show vlan on switch CAT2, what can we conclude about interfaces Fa0/13 and Fa0/14?A. that interfaces Fa0/13 and Fa0/14 are in VLAN 1B. that interfaces Fa0/13 and Fa0/14 are downC. that interfaces Fa0/13 and Fa0/14 are trunk interfacesD. that interfaces Fa0/13 and Fa0/14have a domain mismatch with another switchE. that interfaces Fa0/13 and Fa0/14have a duplex mismatch with another switchAnswer: CExplanation:trunk - This setting places the port in permanent trunking mode. The corresponding switch port at the other end of the trunk should be similarly configured because negotiation is not allowed. You should also manually configure the encapsulation mode.show vlan: This commands shows the vlan, ports belonging to VLAN means that port on access mode. It doesn't shows the port on trunk mode.QUESTION NO: 76Refer to the exhibit. On the basis of the output generated by the show commands, which two statements are true? (Choose two.)h t t p://www.ed if y.co m .cn /A. Because it is configured as a trunk interface, interface gigabitethernet 0/1 does not appear in the show vlan output.B. VLAN 1 will not be encapsulated with an 802.1q header.C. There are no native VLANs configured on the trunk.D. VLAN 2 will not be encapsulated with an 802.1q header.E. All interfaces on the switch have been configured as access ports.F. Because it has not been assigned to any VLAN, interface gigabitethernet 0/1 does not appear in the show vlan output.Answer: A,BExplanation:h t t p://www.ed if y.co m .cn /The IEEE 802.1Q protocol can also carry VLAN associations over trunk links. However, this frame identification method is standardized, allowing VLAN trunks to exist and operate between equipment from multiple vendors.In particular, the IEEE 802.1Q standard defines an architecture for VLAN use, services provided with VLANs, and protocols and algorithms used to provide VLAN services.Like Cisco ISL, IEEE 802.1Q can be used for VLAN identification with Ethernet trunks. Instead of encapsulating each frame with a VLAN ID header and trailer, 802.1Q embeds its tagging information within the Layer 2 frame. This method is referred to as single-tagging or internal tagging .802.1Q also introduces the concept of a native VLAN on a trunk. Frames belonging to this VLAN are not encapsulated with any tagging information. In the event that an end station is connected to an 802.1Q trunk link, the end station can receive and understand only the native VLAN frames.This provides a simple way to offer full trunk encapsulation to the devices that can understand it,while giving normal access stations some inherent connectivity over the trunk.show vlan: This commands shows the vlan, ports belonging to VLAN means that port on access mode. It doesn't show the port on trunk mode.QUESTION NO: 77Refer to the exhibit and the show interfaces fastethernet0/1 switchport outputs. Users in VLAN 5on switch SW_A complain that they do not have connectivity to the users in VLAN 5 on switch SW_B. What should be done to fix the problem?A. Configure the same number of VLANs on both switches.h t t p://www.ed if y.co m .cn /B. Create switch virtual interfaces (SVI) on both switches to route the traffic.C. Define VLAN 5 in the allowed list for the trunk port on SW_A.D. Disable pruning for all VLANs in both switches.E. Define VLAN 5 in the allowed list for the trunk port on SW_BAnswer: CExplanation:switchport trunk allowed vlan , defines which VLANs can be trunked over thelink . By default, a switch transports all active VLANs (1 to 4094) over a trunk link. There might be times when the trunk link should not carry all VLANs. For example, broadcasts are forwarded to every switch port on a VLAN-including the trunk link because it, too, is a member of the VLAN.If the VLAN does not extend past the far end of the trunk link, propagating broadcasts across the trunk makes no sense.Section 8: Document results of VLAN implementation and verification (0 Questions)QUESTION NO: 78Refer to the exhibit. An attacker is connected to interface Fa0/11 on switch A-SW2 and attempts to establish a DHCP server for a man-in-middle attack. Which recommendation, if followed, would mitigate this type of attack?A. All switch ports in the Building Access block should be configured as DHCP untrusted ports.B. All switch ports in the Building Access block should be configured as DHCP trusted ports.h t t p://www.ed if y.co m .cn /C. All switch ports connecting to servers in the Server Farm block should be configured as DHCP untrusted ports.D. All switch ports connecting to hosts in the Building Access block should be configured as DHCP trusted ports.E. All switch ports in the Server Farm block should be configured as DHCP untrusted ports.F. All switch ports connecting to hosts in the Building Access block should be configured as DHCP untrusted ports.Answer: FExplanation:One of the ways that an attacker can gain access to network traffic is to spoof responses that would be sent by a valid DHCP server. The DHCP spoofing device replies to client DHCPrequests. The legitimate server may reply also, but if the spoofing device is on the same segment as the client, its reply to the client may arrive first.The intruder's DHCP reply offers an IP address and supporting information that designates the intruder as the default gateway or Domain Name System (DNS) server. In the case of a gateway,the clients will then forward packets to the attacking device, which will in turn send them to the desired destination. This is referred to as a "man-in-the-middle" attack, and it may go entirely undetected as the intruder intercepts the data flow through the network.Untrusted ports are those that are not explicitly configured as trusted. A DHCP binding table is built for untrusted ports. Each entry contains the client MAC address, IP address, lease time,binding type, VLAN number, and port ID recorded as clients make DHCP requests. The table is then used to filter subsequent DHCP traffic. From a DHCP snooping perspective, untrusted access ports should not send any DHCP server responses, such as DHCPOFFER, DHCPACK,DHCPNAK .QUESTION NO: 79You are responsible for increasing the security within the Company LAN. Of the following choices listed below, which is true regarding layer 2 security and mitigation techniques?A. Enable root guard to mitigate ARP address spoofing attacks.B. Configure DHCP spoofing to mitigate ARP address spoofing attacks.C. Configure PVLANs to mitigate MAC address flooding attacks.D. Enable root guard to mitigate DHCP spoofing attacks.E. Configure dynamic APR inspection (DAI) to mitigate IP address spoofing on DHCP untrusted ports.F. Configure port security to mitigate MAC address floodingG. None of the other alternatives applyAnswer: Fh t t p://www.ed if y.co m .cn /Explanation:Use the port security commands to mitigate MAC-spoofing attacks. The port security command provides the capability to specify the MAC address of the system connected to a particular port.The command also provides the ability to specify an action to take if a port-security violationoccurs. However, as with the CAM table-overflow attack mitigation, specifying a MAC address on every port is an unmanageable solution. Hold-down timers in the interface configuration menu can be used to mitigate ARP spoofing attacks by setting the length of time an entry will stay in the ARP cache.Reference: /networksecurity/NetworkSecurity.htmlSection 2: Create an implementation plan for the Security solution (3 Questions)QUESTION NO: 80You work as a network technician at . Your boss, Mrs. Tess King, is interested in switch spoofing. She asks you how an attacker would collect information with VLAN hoping through switch spoofing. You should tell her that the attacking station...A. es VTP to collect VLAN information that is sent out and then tags itself with the domain information in order to capture the data.B. ...will generate frames with two 802.1Q headers to cause the switch to forward the frames to a VLAN that would be inaccessible to the attacker through legitimate means.C. es DTP to negotiate trunking with a switch port and captures all traffic that is allowed on the trunk.D. ...tags itself with all usable VLANs to capture data that is passed through the switch, regardless of the VLAN to which the data belongs.E. None of the other alternatives applyAnswer: CExplanation:DTP should be disabled for all user ports on a switch. If the port is left with DTP auto-configured (default on many switches), an attacker can connect and arbitrarily cause the port to start trunking and therefore pass all VLAN information.Reference:/en/US/solutions/ns340/ns517/ns224/ns376/net_design_guidance0900aecd800ebd1e.pdfQUESTION NO: 81h t t p://www.ed if y.co m .cn /The Company security administrator is concerned with layer 2 network attacks. Which two statements about these attacks are true? (Select two)A. ARP spoofing attacks are attempts to redirect traffic to an attacking host by encapsulating a false 802.1Q header on a frame and causing traffic to be delivered to the wrong VLAN.B. ARP spoofing attacks are attempts to redirect traffic to an attacking host by sending an ARP message with a forged identity to a transmitting host.C. MAC address flooding is an attempt to force a switch to send all information out every port by overloading the MAC address table.D. ARP spoofing attacks are attempts to redirect traffic to an attacking host by sending an ARP packet that contains the forged address of the next hop router.E. MAC address flooding is an attempt to redirect traffic to a single port by associating that port with all MAC addresses in the VLAN.Answer: B,CExplanation:Content Addressable Memory ( CAM ) Table Overflow (MAC address Flooding)Content Addressable Memory (CAM) tables are limited in size. If enough entries are entered into the CAM table before other entries are expired, the CAM table fills up to the point that no new entries can be accepted. Typically, a network intruder floods the switch with a large number of invalid source Media Access Control (MAC) addresses until the CAM table fills up. When thatoccurs, the switch floods all ports with incoming traffic because it cannot find the port number for a particular MAC address in the CAM table. The switch, in essence, acts like a hub. If the intruder does not maintain the flood of invalid-source MAC addresses, the switch eventually times out older MAC address entries from the CAM table and begins to act like a switch again. CAM tableoverflow only floods traffic within the local VLAN so the intruder only sees traffic within the local VLAN to which he or she is connected.The CAM table overflow attack can be mitigated by configuring port security on the switch. This option provides for either the specification of the MAC addresses on a particular switch port or the specification of the number of MAC addresses that can be learned by a switch port. When an invalid MAC address is detected on the port, the switch can either block the offending MAC address or shut down the port. The specification of MAC addresses on switch ports is far too unmanageable a solution for a production environment. A limit of the number of MAC addresses on a switch port is manageable. A more administratively scalable solution is the implementation of dynamic port security at the switch. In order to implement dynamic port security, specify a maximum number of MAC addresses that will be learned.Address Resolution Protocol (ARP) SpoofingARP is used to map IP addressing to MAC addresses in a local area network segment where hosts of the same subnet reside. Normally, a host sends out a broadcast ARP request to find the MAC address of another host with a particular IP address, and an ARP response comes from the host whose address matches the request. The requesting host then caches this ARP response.Within the ARP protocol, another provision is made for hosts to perform unsolicited ARP replies.h t t p://www.ed if y.co m .cn /The unsolicited ARP replies are called Gratuitous ARP (GARP). GARP can be exploited maliciously by an attacker to spoof the identity of an IP address on a LAN segment. This istypically used to spoof the identity between two hosts or all traffic to and from a default gateway in a "man-in-the-middle" attack.When an ARP reply is crafted, a network attacker can make his or her system appear to be the destination host sought by the sender. The ARP reply causes the sender to store the MACaddress of the network attacker's system in the ARP cache. This MAC address is also stored by the switch in its CAM table. In this way, the network attacker has inserted the MAC address of his or her system into both the switch CAM table and the ARP cache of the sender. This allows the network attacker to intercept frames destined for the host that he or she is spoofing.Reference:/en/US/products/hw/switches/ps5023/products_configuration_example09186a00807c4101.shtmlQUESTION NO: 82The Company security administrator wants to prevent DHCP spoofing. Which statement is true about DHCP spoofing operation?A. DHCP spoofing and SPAN cannot be used on the same port of a switch.B. To prevent a DHCP spoofing, the DHCP server must create a static ARP entry that cannot be updated by a dynamic ARP packet.C. To prevent a DHCP spoofing, the switch must have DHCP server services disabled and a static entry pointing towards the DHCP server.D. DHCP spoofing can be prevented by placing all unused ports in an unused VLAN.E. None of the other alternatives apply.Answer: BExplanation:About DHCP Spoofing:Suppose that an attacker could bring up a rogue DHCP server on a machine in the same subnet as that same client PC. Now when the client broadcasts its DHCP request, the rogue server could send a carefully crafted DHCP reply with its own IP address substituted as the default gateway.When the client receives the reply, it begins using the spoofed gateway address. Packets destined for addresses outside the local subnet then go to the attacker's machine first. The attacker can forward the packets to the correct destination, but in the meantime, it can examine every packet that it intercepts. In effect, this becomes a type of man-in-the-middle attack; the attacker is wedged into the path and the client doesn't realize it.About ARP:h t t p://www.ed if y.co m .cn /Hosts normally use the Address Resolution Protocol (ARP) to resolve an unknown MAC address when the IP address is known. If a MAC address is needed so that a packet can be forwarded at Layer 2, a host broadcasts an ARP request that contains the IP address of the target in question.If any other host is using that IP address, it responds with an ARP reply containing its MAC address.To prevent a DHCP spoofing, the DHCP server must create a static ARP entry that cannot be updated by a dynamic ARP packetSection 3: Create a verification plan for the Security solution (4 Questions)QUESTION NO: 83Refer to the exhibit. What will happen to traffic within VLAN 14 with a source address of 172.16.10.5?A. The traffic will be forwarded to the router processor for further processing.B. The traffic will be dropped.C. The traffic will be forwarded to the TCAM for further processing.D. The traffic will be forwarded without further processing.Answer: BExplanation:VLAN maps, also known as VLAN ACLs or VACLs, can filter all traffic traversing a switch. VLAN maps can be configured on the switch to filter all packets that are routed into or out of a VLAN, or are bridged within a VLAN. VLAN maps are used strictly for security packet filtering. Unlike routerh t t p://www.ed if y.co m .cn /ACLs, VLAN maps are not defined by direction (input or output).To create a VLAN map and apply it to one or more VLANs, perform these steps: Create the standard or extended IP ACLs or named MAC extended ACLs to be applied to the VLAN. This access-list will select the traffic that will be either forwarded or dropped by the access-map. Only traffic matching the 'permit' condition in an access-list will be passed to the access-map for further processing. Enter the vlan access-map access-map-name [ sequence ] global configuration command to create a VLAN ACL map entry. Each access-map can have multiple entries. The order of these entries is determined by the sequence . If no sequence number is entered, access-map entries are added with sequence numbers in increments of 10. In access map configuration mode, optionally enter an action forward or action drop . The default is to forward traffic. Also enter the match command to specify an IP packet or a non-IP packet (with only a known MAC address),and to match the packet against one or more ACLs (standard or extended). Use the vlan filter access-map-name vlan-list vlan-list global configuration command to apply a VLAN map to one or more VLANs. A single access-map can be used on multiple VLANs.QUESTION NO: 84Company is implementing 802.1X in order to increase network security. In the use of 802.1X access control, which three protocols are allowed through the switch port before authentication takes place? (Select three)A. EAP-over-LANB. EAP MD5C. STPD. protocols not filtered by an ACLE. CDPF. TACACS+Answer: A,C,EExplanation:The IEEE 802.1x standard defines a port-based access control and authentication protocol that restricts unauthorized workstations from connecting to a LAN through publicly accessible switch ports. The authentication server authenticates each workstation that is connected to a switch port before making available any services offered by the switch or the LAN. Until the workstation is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL) traffic through the port to which the workstation is connected. After authentication succeeds, normal traffic can pass through the port.The Authentication server performs the actual authentication of the client. The authentication server validates the identity of the client and notifies the switch whether or not the client is authorized to access the LAN and switch services. Because the switch acts as the proxy, theh t t p://www.ed if y.co m .cn /authentication service is transparent to the client. In this release, the Remote Authentication Dial-In User Service (RADIUS) security system with Extensible Authentication Protocol (EAP)extensions is the only supported authentication server; it is available in Cisco Secure Access Control Server version 3.0. RADIUS operates in a client/server model in which secureauthentication information is exchanged between the RADIUS server and one or more RADIUS clients.Spanning-Tree Protocol (STP) is a Layer 2 protocol that utilizes a special-purpose algorithm to discover physical loops in a network and effect a logical loop-free topology. STP creates a loop-free tree structure consisting of leaves and branches that span the entire Layer 2 network. The actual mechanics of how bridges communicate and how the STP algorithm works will be discussed at length in the following topics. Note that the terms bridge and switch are used interchangeably when discussing STP. In addition, unless otherwise indicated, connections between switches are assumed to be trunks.CDP is a Cisco proprietary protocol that operates at the Data Link layer. One unique feature about operating at Layer 2 is that CDP functions regardless of what Physical layer media you are using (UTP, fiber, and so on) and what Network layer routed protocols you are running (IP, IPX,AppleTalk, and so on). CDP is enabled on all Cisco devices by default, and is multicast every 60seconds out of all functioning interfaces, enabling neighbor Cisco devices to collect information about each other. Although this is a multicast message, Cisco switches do not flood that out to all their neighbors as they do a normal multicast or broadcast.For STP, CDP and EAP-over-LAN are allowed before Authentication.QUESTION NO: 85Refer to the exhibit. The web servers WS_1 and WS_2 need to be accessed by external and internal users. For security reasons, the servers should not communicate with each other,although they are located on the same subnet. The servers do need, however, to communicate with a database server located in the inside network. What configuration will isolate the servers from each other?h t t p://www.ed if y.co m .cn /A. The switch ports 3/1 and 3/2 will be defined as secondary VLAN community ports. The ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.B. The switch ports 3/1 and 3/2 and the ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.C. The switch ports 3/1 and 3/2 and the ports connecting to the two firewalls will be defined as primary VLAN community ports.D. The switch ports 3/1 and 3/2 will be defined as secondary VLAN isolated ports. The ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.Answer: DExplanation:Service providers often have devices from multiple clients, in addition to their own servers, on a single Demilitarized Zone (DMZ) segment or VLAN. As security issues proliferate, it becomes necessary to provide traffic isolation between devices, even though they may exist on the same Layer 3 segment and VLAN. Catalyst 6500/4500 switches implement PVLANs to keep some switch ports shared and some switch ports isolated, although all ports exist on the same VLAN.The 2950 and 3550 support "protected ports," which are functionality similar to PVLANs on a per-switch basis.A port in a PVLAN can be one of three types:Isolated: An isolated port has complete Layer 2 separation from other ports within the same PVLAN, except for the promiscuous port. PVLANs block all traffic to isolated ports, except the traffic from promiscuous ports. Traffic received from an isolated port is forwarded to only promiscuous ports.Promiscuous: A promiscuous port can communicate with all ports within the PVLAN, including the community and isolated ports. The default gateway for the segment would likely be hosted on a promiscuous port, given that all devices in the PVLAN will need to communicate with that port. Community: Community ports communicate among themselves and with their promiscuous ports.These interfaces are isolated at Layer 2 from all other interfaces in other communities, or in isolated ports within their PVLAN.QUESTION NO: 86VLAN maps have been configured on switch R1. Which of the following actions are taken in a VLAN map that does not contain a match clause?A. Implicit deny feature at end of list.B. Implicit deny feature at start of list.C. Implicit forward feature at end of listD. Implicit forward feature at start of list.Answer: Ah t t p://www.ed if y.co m .cn /Explanation:Each VLAN access map can consist of one or more map sequences, each sequence with a match clause and an action clause. The match clause specifies IP, IPX, or MAC ACLs for traffic filtering and the action clause specifies the action to be taken when a match occurs. When a flow matches a permit ACL entry the associated action is taken and the flow is not checked against theremaining sequences. When a flow matches a deny ACL entry, it will be checked against the next ACL in the same sequence or the next sequence. If a flow does not match any ACL entry and at least one ACL is configured for that packet type, the packet is denied.Reference:/en/US/products/hw/switches/ps700/products_configuration_guide_chapter09186a008007f4d4.htmlSection 4: Configure port security features (6 Questions)QUESTION NO: 87A Company switch was configured as shown below:switchport mode access switchport port-securityswitchport port-security maximum 2switchport port-security mac-address 0002.0002.0002switchport port-security violation shutdownGiven the configuration output shown above, what happens when a host with the MAC address of 0003.0003.0003 is directly connected to the switch port?A. The host will be allowed to connect.B. The port will shut down.C. The host can only connect through a hub/switch where 0002.0002.0002 is already connected.D. The host will be refused access.E. None of the other alternatives applyAnswer: AExplanation:Steps of Implementing Port Security:h t t p://www.ed if y.co m .cn /In Exhibit two MAC addresses are allowed so that host will be allowed to connect.QUESTION NO: 88Refer to the exhibit. Which interface or interfaces on switch SW_A can have the port security feature enabled?A. Ports 0/1 and 0/2B. The trunk port 0/22 and the EtherChannel portsh t t p://www.ed if y.co m .cn /C. Ports 0/1, 0/2 and 0/3D. Ports 0/1, 0/2, 0/3, the trunk port 0/22 and the EtherChannel portsE. Port 0/1F. Ports 0/1, 0/2, 0/3 and the trunk port 0/22Answer: CExplanation:Port security is a feature supported on Cisco Catalyst switches that restricts a switch port to a specific set or number of MAC addresses. Those addresses can be learned dynamically or configured statically. The port will then provide access to frames from only those addresses. If,however, the number of addresses is limited to four but no specific MAC addresses areconfigured, the port will allow any four MAC addresses to be learned dynamically, and port access will be limited to those four dynamically learned addresses. A port security feature called "sticky learning," available on some switch platforms, combines the features of dynamically learned and statically configured addresses. When this feature is configured on an interface, the interface converts dynamically learned addresses to "sticky secure" addresses. This adds them to the running configuration as if they were configured using the switchport port-security mac-address command.QUESTION NO: 89Refer to the exhibit. Based on the running configuration that is shown for interface FastEthernet0/2, what two conclusions can be deduced? (Choose two.)A. Connecting a host with MAC address 0000.0000.4147 will move interface FastEthernet0/2 into error disabled state.B. The host with address 0000.0000.4141 is removed from the secure address list after 5 seconds of inactivity.h t t p://www.ed if y.co m .cn /。
最新CCNP-思科认证题目

网络系统构建技术总复习一、不定项选择题1、在Windows 2003/2008 的TCP/IP 网络中,IP 地址有两种设定方法,它们分别是(B、D)。
A. 通过DHCP 和DNS 设定B. 通过DHCP 及人工指定C. 通过子网掩码和缺省网关给定D. 通过网络自动生成2、如果所在的局域网中存在DHCP 服务器,那么在Windows 平台下安装TCP/IP网络时,就可以(B )。
A. 去掉IP 地址的设置B. 从DHCP 服务器中自动获得一个IP 地址C. 设置一个有效的固定IP 地址D. 任意设置一个IP 地址3、如果用户所安装的TCP/IP 网络与其他网络或与Internet 相连,则必须(D )。
A. 设定DHCPB. 设置WINSC. 给定任意一个IP 地址D. 指定缺省网关4.在Windows 2003/2008 的TCP/IP 网络中,要求各个连网计算机的IP 地址在本域范围内( B )。
A. 使用同一个IP 地址B. 惟一C. 任意设定D. 不惟一5、在设置静态ip地址时,(A、C、D )参数有时是可以不设置的。
(选择三项)A. 网关B. 子网掩码C. 首选域名服务器D. 备用域名服务器6、在邮件地址mackenzre@中,(B)表示域名。
(选择一项)A. MackenzreB. C. mackenzre@7、一台服务器准备作为网络的文件服务器,管理员正在对该服务器的硬盘进行规划。
如果用户希望读写速度最快,他应将硬盘规划为(C ),如果用户希望对系统分区进行容错,他应将硬盘规划为(D ),如果用户希望对数据进行容错,并保证较高的磁盘利用率,他应将硬盘规划为( E )。
A. 简单卷B. 跨区卷C. 带区卷D. 镜像卷E. RAID-5卷8、使用域控制器来集中管理域账户,你安装域控制器必须具备以下条件(A、B )。
(选择二项)A. 操作系统版本是Windows server 2003或者Windows Server 2008B. 本地磁盘至少有一个NTFS分区C. 本地磁盘必须全部是NTFS分区D. 有相应的DNS服务器支持9、一位系统管理员在安装Windows Server 2003/2008的过程中,在安装向导的网络设置页面中选择了“典型设置”,那么当服务器安装完成后将其连接到公司的网络,它的IP地址会( B )。
CCNP试题

Network Study CIT AnswersThis material is owned and maintained by Digital Concepts, it is licensed exclusively for single user use1.What switching is supported on the 7500 series router with a VIP, that is not availablewithout the VIP?!Process switching!Distributed Switching!Frame switching!VIP Switching2.Which CCO utility is able to parse and display usable information from the output“Show stack” command?!Bug Navigator II!Stack Decoder!Stack Debugger!Stack Navigator a product that can collect RMON information so engineers can Analyze it?!Netsys baseliner!Traffic Director!Network sniffer!VLAN Director4.If performance on a VLAN is slow what is the cause? (choose all that apply)!Bad NetworkAdapter, or line module!Misconfigure VLAN encapsulation!Cable problem!Incompatible releases of the Cisco™ IOS major version number!Error seting for Full duplex or Half duplex!ATM MTU is fragmenting packets in LANE environment!Decoding encrypted frames is cause the router to slow down.!Somebody accidentally caused a static discharge5.If you issue show IPX traffic and you get a bad hop count which of the followingscenarios could be causing the error?!You have set incompatible frame types configured on server and router!You have a backdoor bridge between segments!You have more than 16 hops between IPX networks!Your SAP table is corrupt and is causing packet loops6.If a CSE asks for the output of the show stack what is the error?!Software error!Hardware error!Cable problem!The CSE does not have a clue yet.7.Which of the following is important to remember when troubleshooting fiber opticconnections? (choose all that apply)!Cables not punched down correctly!asymmetric connectivity!attenuation over short distances!proper shielding from interference8.In the ISL 802.10 specification, packet tagging of an Ethernet frame is accomplishedusing three fields, for a total of 30 bytes. Which of the following are fields found in a validEthernet/ISL frame?!FCS!VTP identifier!VLAN ID!Port of Origin!Destination MAC address!ISL protocol versionExplanation: Ethernet frames are encapsualtion with 30 bytres of information, the 30 bytes are usied in three fields to incidate VLAN ID, the port of origin for the frame, and an FCS. The FCS is checked by the port receiving the switching bus.9.In the following diagram which devices will show no CDP information? (choose all thatapply)!Cisco™ router configured as a bridge!Wan Switch!Cisco™ router on the other side of a frame relay network!Cisco™ router connected via an ATM connectionExplanation: CDP is not available over ATM because it requires broadcasts, which are not available on ATM. ATM LANE supports CDP10.What command do you use to show the current status of router? Including the date ofLast reboot and the amount of RAM installed?!Show running-config!Show statup-config!show version!show controllers11.Which of the following could cause a delay in STP forward delay?!Avoid turning on multiple subinterfaces which could cause loops!Do not use both IEEE and Digital bridging!Configure a root bridge which is slow to converge12.Which of the following Service Access Point Identifiers (SAPI) values are important tolook for when viewing the output of a “debug isdn q921” command? (choose all that apply)!SAPI 63 – Layer 2 management used for processes including TEI assignment!SAPI 64 – Used for call control!SAPI 65 – TEI negotiation parameters!SAPI 3 – indication that the message type is layer 3 signaling (from Q.931)!SAPI 0 – Indiciation that the message type is Layer 3 signaling (from Q.931)Note: SAPI 65, and 3 are not accuarately described in this question.13.What switching mode will the router use if you have debugging enabled?!Store and forward switching!Fast Switching!Priority switching!Process switching!Distributing Switching14.What command when executed in the proper context will cause debugging informationto be displayed on a virtual terminal (non-console)?!debug terminal!terminal monitor!logging ouptut terminal!debug output vty 0 415.Which of the following answers can trigger and ISDN call to be placed?? (choose all thatapply)!From user exec “call destination-name” command!From priveledged mode use “call destination-name”!DDR due to interesting traffic being seen!Incoming call, with the “collect” bit set to one.16.You are troubleshooting a frame relay connection, when you put the CSU on both sidesinto loopback, and you see DLCI 0, and 1023 come active. When the circuit is not in loopback no DLCI’s are active. What is the next step?!Disable DLCI autodetect and map the DLCI’s manually!Verify that one of the routers is using a cross over serial cable!check the encapsulation your using on both sides and make sure it is compatible!contact the service provider17.What are the functions of the NetSYS tool?!Taking samples of network performance for baselining!Network simulation/modeling software!performing advanced packet capture and decoding features!managing VLAN id’s and configurations18.Why is process switching slow?!The encryption takes more time to decode the packet!Every packet must be examined, and no flow data is kept!The destination mac is processed at the end of the frame!The packet must be processed by each interface (incoming and outgoing)19.On the frame-relay DTE/DCE which configuration element will the router autosense inIOS version 11.2 and later?!DLCI!LMI!Encapsulation!Network type20.What show command would you issue to show tech support routers condition?!Show version!Show buffers!Show memory!Show tech-supportExplanation: the show tech-support command gives the CSE an easy way to list all sorts of useful information, typically they will also ask for a “show running-config”21.What is the proper pin-out for an ISDN RJ45 connector on the TE end?!Pin1 - TX, Pin 2 - TX, Pin 3 - RX, Pin 4 -RX!Pin3 - TX, Pin 4 - RX, Pin 5 - RX, Pin 6 -TX!Pin 4 - RX, Pin 5 -TX!Pin 4 –TX, Pin 5 – RX22.Cisco IOS provides commands to troubleshoot ISDN BRI layer 2 & 3. First enter thecommand _____ for Layer 2 debug and the enter command ______ for Layer 3 debug!Debug isdn layer2 / debug isdn layer3!Show isdn datalink / show isdn transport!Debug isdn q219 / debug isdn q319!Debug isdn q921 / debug isdn q931!Note The ISDN switch provides the network interface defined by Q.921. This debug command does not display data link layer access procedures taking place within the ISDN network (that is, procedures taking place on the network side of the ISDN connection).23.When you issue a “show ipx traffic” you see that the router has a high number of packetswith a “bad hop count” what does this mean? (choose 1)!Your network is experiencing a count to infinity problem.!Packets were discarded because their hop count exceeded 16.!You have disabled split horizon, and packets are looping.!Packets are being received without the hop count field set.Explanation: A possible cause of this is a backdoor bridge between segments which could happen if you disabled spanning tree.24.If a CSE asks for the output of the show stack which of the following does he/shesuspect? (choose all that apply)!Misconfigure router!Bad Ram!Invalid boot prom!Bad Flash!Corrupt IOS imageExplanation: This was a trick question, in order to get a stack trace you must be able to get into bootstrap mode > so it isn’t a valid boot prom, and a poorly configured router doesn’t usually require a stack trace to figure out what’ Basically a show stack means the CSE suspects a HARDWARE problem.25.What command can you use to view information specifically about the D channel of aBRI line?!Show isdn status!Show controller bri!Show dialer 0!Show int bri 0Explanation: this is a trick question, the full answer is “show controllers bri”, but the command “show controller bri” will work just fine.26.You are using a gigabit ethernet module on a Catalyst 2924M connected to a third partygigabit switch, during heavy loads you are continually having data overrun issues, what is theprobable cause of this problem?!The catalyst 2924M backplane can’t handle the full bandwidth!You need to increase the amount of ram in the catalyst switch!You need to enable symmetric flow control!Ouji board says sunspots.Explanation: Gigabit ports can use either assymetric (default) or symmetric flow control. In an assymetric model the local port to performs flow control of the remote port. If the local port is congested, it can request the remote port to stop transmitting. When the congestion clears, the local port requests that the remote port begin transmitting. In a symmetric model the the local port to perform flow control only if the remote port can also perform flow control of the local port. If the remote port cannot perform flow control, the local port also will not.27.Which of the following are true about the ISL specification? (choose all that apply)!It contains three fields, the header, the original packet and the FCS at the end!It is supported by Ethernet, FDDI, token ring and ATM!The virtual lan ID is a 15 bit number, which is different for each host on a vlan!ISL puts a CRC at the end of the frame which covers both the header and the encapsulated packet.Explanation: ISL is not directly supported by ATM, although you could use it in a ATM LANE configuration. The virtual lan ID is 15 bits, and is different for each VLAN. This 15 bit value is referred to as the COLOR of the VLAN.28.What command will send debugging output to the console?!In console configuration mode, “Logging console level”!In line 0 configuration mode, “logging console level”!In global configuration mode, “logging console level”29.Which command tells you if there are problems with the packets on the ISL trunk beingeither misconfigured or being sent/received on the wrong ISL subinterface.!Show vlan status!Debug vlan ip!Debug vlan packet!Debug vlan isl30.Which of the following devices will show no CDP information? (choose all that apply)! A Cisco™ router configured as a bridge, with the statement “no ip route” in its configuration!An ATM interface on a Catalyst 5000! A router with the statement “no cdp enable” on all interfaces! A non Cisco™ switch! A serial interface with a misconfigured encapsulation31.What command do you use to show current status of router? Date of Last reboot?!Show memory!Show status!Show version!Show running-config!Show startup-information32.What does the command “IPX ping-default Novell” accomplish? (choose all that apply)!Configures the router to respond to all novell format IPX pings.!Configures the router to send to novell format IPX pings by default.!Sends an IPX ping packet of default size to the server name “Novell”.!Configures the router to ignore Cisco™ pings.33.Which of the following is true about FDDI? (choose all that apply)!FDDI supports both synchronous and asynchronous traffic management!Synchronous bandwidth is allocated using an 8 level priority scheme!Devices that can only use Asynchronous bandwidth are guaranteed to have their data deliever in a timely fashion.!Synchronous devices may fully utilize the network, by using a reserved tokenExplanation: Asynchronous bandwidth is allocated using an 8 level priority scheme. Asychronous bandwidth is what is left over after all devices which have been allocated synchronous bandwidth are finished. Synchronous bandwidth is allocated to devices which needa continous stream of data, such as voice or video.34.Which of the following are CCO bug toolkit resources?!Bug Navigator!Bug Finder!Bug Alert!Bug Hunter!Bug Watcher!Bug sprayExplanation: there are only three resources in the Bug Toolkit II which are Bug Navigator, Bug Alert, and Bug Watcher.35.In Spanning Tree Protocol what happens to a port if no information has been received bythe end of a forwarding delay?!The port transitions to blocked state!The port transitions to forward state!The port transitions to learning state!The port transitions to listening state!The port becomes the root bridgeExplanation: As BPDU information is updated and/or timed-out, the Spanning Tree is recalculated and ports may transition from the blocked state to the forwarding state and vice versa. That is, as a result of new BPDU information, a previously blocked port may learn that it is now the root port or the designated port for a given segment. Rather than transition directly from the blocked state to the forwarding state, ports transition through two intermediate states: a listening state and a learning state. The bridge will remain in each state for a preset period of time, called the forwarding delay. In the listening state, a port waits for information indicating that it should return to the blocked state. If, by the end of the forwarding delay time, no such information is received, the port transitions to the learning state. In the learning state, a port still blocks the receiving and forwarding of frames, but received frames are examined and the corresponding location information is stored, as described above. At the end of a second forwarding delay time, the port transitions from the learning state to the forwarding state, thereby allowing frames to be forwarded and received at the port.36.When you issue a “show ipx traffic” you see that the router has a high number of packetswith a “packets pitched” what does this mean? (choose all that apply)! A high number of packets were discarded due to high load!The router has received its own broadcast many times!Packets are being dropped due to their TTL being expired.!You probably have a loop somewhere on your network!The router is probably mistaking IPX for SPX!You don’t have the correct frame type selected.Explanation: The packets pitched counter is the number of times a router has received its own broadcast packets.37.What debug command would you issue to see if rip routing is operating properly?!___________Answer: debug ip rip38.On the frame-relay DTE/DCE which configuration element will the router autosense?!Frame Type!Encapsulation!Network layer protoocols (eg: ppp)!LMI type39.Which of the following scenarios could be solved by using an IPX static sap on a router?(choose all that apply)!You want clients to ignore broadcasts from certain servers!You want clients to always use services of a particular server!You want clients to login to one server, in case another server might be down!You want to remove the additional load of distributing saps from a server.Explanation: Servers use SAP to advertise their services via broadcast packets. Routers store this information in the SAP table, also known as the Server Information Table (SIT). This table is updated dynamically. You might want to explicitly add an entry to the SIT so that clients always use the services of a particular server. Static SAP assignments always override any identical entries in the SAP table that are learned dynamically, regardless of hop count. If a dynamic route that is associated with a static SAP entry is lost or deleted, the router will not announce the static SAP entry until it relearns the route.40.What are the two ways to configure a VLAN?!By using a NMP in the switch!By using an RSM in the switch!By attaching a route to a VLAN trunking port using 802.1Q encapsulation!By attaching a router to a VLAN trunking port using ISL encapsulation41.If a VLAN is slow or non-operational, which of the following are possible causes of theproblem?!Incorrect VLAN trunking protocol is configured!Incorrect encapsulation on the VLAN42.Which of the following Cisco™ products can collect RMON information so engineerscan analyze it later?!Vlan director!TrafficDirector!CiscoWorks for Switched Internetworks Campus!CiscoWorks 2000!Netsys baselinerAnswer: TrafficDirector can collect RMON information, and traffic director is included inside of CiscoWorks for Switched Internetworks Campus.43.Which utility performs decodes of a stack trace (show stack) and may be useful forCisco™ TAC support?!Bug navigator II!Troubleshooting Assistant!Stack Decoder!Management ToolkitAnswer: The Stack decoder is a tool which can be found on CCO, paste in the output of a “show stack” command after an error has occurred and the stack decoder tool will comment the stack trace with meaningful comments.44.What type of switching is supported on the 7500 series router with a VIP installed?!Priority switching!Fast switching!Weighted fair switching!Distributed switching!ASIC based switchingAnswer: The Cisco 7000 family Versatile Interface Processor (VIP) is based on a RISC engine optimized for I/O functions. Either one or two port adapters or daughter boards may be attached to a VIP, to provide the media- specific interfaces to the network. A key feature of the VIP technology is its ability to receive route information from the master RSP. Based on route data received from the RSP, a VIP is able to make its own autonomous, multilayer switching decisions, thereby providing distributed switching, which is just one of many features supported by the VIP technology. The VIP supports:High port densities. As higher densities of the VIP technology become available, users will be able to cost-effectively add additional ports to either the Cisco 7000 or Cisco 7500 platforms.Mixed Media. The port adapter design enables different media types to be deployed on the same VIP, which enables maximum chassis slot utilization.Packet memory. Each VIP contains its own packet memory, thus distributing and greatly increasing the amount of packet memory available in the system. This is a particularly important feature in environments where there are large round-trip propagation delays (trans-Atlantic or trans-Pacific for example), bursty traffic conditions, or where there may be many high-speed media pointing to a small number of slower-speed media.Feature Offload. Each VIP can run a subset of the Cisco IOS software. With Feature Offload, it will be possible to distribute some of the more processor-intensive functions from the RSP throughout the rest of the system.Distributed switching. This is the "CiscoFusion in a box" feature that enables scalable switching performance.45.One way to check why line protocol Frame Relay is down, is to check for timingproblems with myseq & myseen keepalive events, command to show:!debug serial interface!show interface serial!show frame relay lmi!debug frame-relay pvc46.What is the true statement about embedded RMON Agent & SwitchProbe!functions in Catalyst software!SPAN is option of switch Probe function!functions use all RMON groups as well as RMON!function of switch probe offers an in-band link to network manager!RFC 1757 RMON groups supported are statistics, events, history & alarms!Functions can monitor segment as long as they use 10BaseT or 100BaseT47.To check timeliness of ISDN events in a log/ debug filter, what command can configurerouter to indicate how many milliseconds have occurred between events displayed:!_____________Answer: Use the command “service timestamps” puts a date and time in your log so you can tell how much time has elapsed between events. However this command SPECIFICALLY asks for MILLISECONDS between events so you would need to use the form “service timestamps log datetime msec”48.What are the allowed encapsulation in the output of “show interface atm” command?!AAL5, PVC, SVC!VC, VPI, VCI!SNAP, NSAP!AAL5, AAL4, AAL1!AAL4, AAL5, LANE!None of the aboveAnswer: Valid encapsulations for ATM are AAL5, PVC and SVC.Example:Switch# show interface atm 1/0/0ATM1/0/0 is up, line protocol is upHardware is oc3suniMTU 4470 bytes, sub MTU 4470, BW 156250 Kbit, DLY 0 usec, rely 255/255, load 1/255Encapsulation ATM, loopback not set, keepalive not supportedLast input 00:00:00, output 00:00:00, output hang neverLast clearing of "show interface" counters neverQueueing strategy: fifoOutput queue 0/40, 0 drops; input queue 0/75, 0 drops5 minute input rate 0 bits/sec, 0 packets/sec5 minute output rate 0 bits/sec, 0 packets/sec527152 packets input, 27939056 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants, 0 throttles0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort527246 packets output, 27944038 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 output buffer failures, 0 output buffers swapped outSwitch#This should not be confused with the “show atm interface atm command” which gives the following output?Switch# show atm interface atm 1/0/0Interface: ATM1/0/0 Port-type: oc3suniIF Status: UP Admin Status: upAuto-config: enabled AutoCfgState: completedIF-Side: Network IF-type: NNIUni-type: not applicable Uni-version: not applicableMax-VPI-bits: 8 Max-VCI-bits: 14Max-VP: 255 Max-VC: 16383ConfMaxSvpcVpi: 255 CurrMaxSvpcVpi: 255ConfMaxSvccVpi: 255 CurrMaxSvccVpi: 255ConfMinSvccVci: 33 CurrMinSvccVci: 33Svc Upc Intent: pass Signalling: EnabledATM Address for Soft VC: 47.0091.8100.0000.0040.0b0a.2a81.4000.0c80.8000.00Configured virtual links:PVCLs SoftVCLs SVCLs TVCLs PVPLs SoftVPLs SVPLs Total-Cfgd Inst-Conns4 0 0 0 0 0 0 4 4Logical ports(VP-tunnels): 0Input cells: 528135 Output cells: 5282355 minute input rate: 0 bits/sec, 0 cells/sec5 minute output rate: 0 bits/sec, 0 cells/secInput AAL5 pkts: 344844, Output AAL5 pkts: 344878, AAL5 crc errors: 0Switch#49.Which is not cause for complete interface reset?!problem with clocking signal!problem with Frame relay!hardware problem with router interface!interface counters cleared with clear interface!packets sequenced for transmission are not send for several ms!router restart interface due to persistent line protocolAnswer: The following are causes for interface resets: Congestion on link (typically associated with output drops), Bad line causing CD transitions, Possible hardware problem at the CSU, DSU, or switch50.Which is NOT one of IOS defined functional area of network management?!fault management!security management!accounting management!Quality of service management!Configuration & name managementExplanation: Cisco defines five network management functional areas which include: fault management, performance management, configuration management (which includes device management), accounting management (which is included in performance management applications), and security management. Configuration management does not include name management.51.When you see the Link LEDs flash orange during Catalyst 5000 power-up sequence,what is indicated?! A module was not correctly inserted into slot, or has failed!power-up sequence is underway & not yet completed!more than 1 fan, power supply or supervisor clock is disabled!network management autodiscovery process us underway!traffic testing process of interface loopback has not yet completedAnswer: When dealing with the Link light, If the port is operational, the LED is green. If the link has been disabled by software, the LED is orange. If the link is bad and has been disabled due to a hardware failure, the LED flashes orange. If no signal is detected, the LED is off.52.Because it moves packets, frames or cells from buffer to buffer with simplerdetermination of traffic source & destination switching is!not performed in routers!able to use more intensive processing!part of protocol's best path decision!moving data to its ultimate destination!affected by lower latency than routing53.where are special processes like debug packet filtering, sending error log entries to asyslog server & SNMP processing done?!route switch processor!Netflow error processor!Si switch processor!Autonomous switch processor!CxBus diagnostic processor54.For troubleshooting cables, which test helps to eliminate uncertainties about cable breaks,cable plant & punch down connections?! change ports used on switch & determine if problem goes away!check cable length, impedance and continuity with a network monitor!replace network adapter card at user device end & retest!Visually inspect cable connectors., the adapter ( and/ interface port & punchdown block termination)!replace cable with an external cable known to be good55. When do you need to set a default gateway in a UNIX environment?!When the hosts are connected to an internetwork!When the hosts are running routed!When the hosts are not running routed!When the hosts are acting as a firewall?Explanation: A Unix host running routed will learn its default gateway through RIP. If the host is not running routed then you will need to set its default gateway.56.Which of the following are tools of Cisco Support online?!Troubleshooting Assistant!TAC Assistance!Software Bug Toolkit II!Online OrderingExplanation: The Cisco website offers many helpful features including the ability to search technical database , an open question and answer forum, a mailing list archive, a troubleshooting assistant, a software bug toolkit, accesspath configuration tools, ip subnet calculator, stack decoder, 3600 memory calculator, tac case instructions, the ability to open and update TAC cases, and the ability to order cisco products online in the “Cisco™ Marketplace” area of the CCO website. Cisco™ Marketplace is the name of the area where you may perform online ordering.57.Which command would you use to display statistics such as missed datagrams, memoryerrors, buffer errors, and overflow errors for the first ethernet interface on a Cisco router?!Show interface ethernet 0!Show controllers ethernet 0!Show ethernet 0 errors!Show interface ethernet 0 errorsExplanation: While the show interface ethernet 0 will give you a certain amount of errors it will not give you any errors which actually occurred on the interface (meaning internal hardware errors). Memory errors indicate you may have a hardware problem with your router.58.Which command would you use to display the router images stored in NVRAM?!Show internal memory!Show flash!Show nvram!Show epromExplanation: the show flash displays the contents of the system flash memory, these images can be used to boot from. Here is a sample output:Router1>show flashSystem flash directory:File Length Name/status1 189**** ****ios-11.16.bin[1898616 bytes used, 2295688 available, 4194304 total]4096K bytes of processor board System flash (Read/Write)59.Which command displays statistics for the buffer pools in router?!Show memory!Show buffers!Show pools!Show memory buffersExplanation: Use the show buffers EXEC command to display statistics for the buffer pools on the network server. The router has one pool of queuing elements and five pools of packet buffers of different sizes. For each pool, the network server keeps counts of the number of buffers outstanding, the number of buffers in the free list, and the maximum number of buffers allowed in the free list. show buffers [type number]] | all]show buffers [interface [type number]] [alloc [dump]]CS# show buffersBuffer elements:421 in free list (500 max allowed)409 hits, 0 misses, 0 createdPublic buffer pools:Small buffers, 104 bytes (total 50, permanent 50):50 in free list (20 min, 150 max allowed)277 hits, 0 misses, 0 trims, 0 createdMiddle buffers, 600 bytes (total 25, permanent 25):24 in free list (10 min, 75 max allowed)19 hits, 0 misses, 0 trims, 0 createdBig buffers, 1524 bytes (total 50, permanent 50):50 in free list (5 min, 40 max allowed)。
CCNP 试题

唐钢集团CCNP课程培训测试题姓名:成绩:一、选择题:(单选,共20题,每题4分)1.如下图所示,拓扑表中,数字3011840 和3128695 代表什么?-------------------------()A.应用于该路由器EIGRP 路由的路由度量B.路由信息来源的可信度C.到目的网络的跳数和带宽的复合度量D.由EIGRP 邻居通告的网络总度量2.请参见图示。
该公司在编号为10 的自治系统中使用EIGRP。
路由器A 和路由器B 所连接网络上的主机能够相互ping 通。
但是,192.168.3.0 网络上的用户无法访问192.168.1.32 网络上的用户。
此问题最可能的原因是什么?---------------------------------------------------()A启用了无类IP,从而导致数据包被丢弃。
B路由器C 上未使用network 192.168.1.32 命令。
C没有将路由器配置在相同的EIGRP 路由域中。
D网络自动总结导致各子网的路由被丢弃。
3.请参见图示。
网络192.168.0.0/28 断开。
Router2 会立即向Router1 和Router3 发送什么类型的数据包?---------------------------------------------------------------------------------------------------()A查询网络192.168.0.0/28 的查询数据包B到224.0.0.9 的确认数据包C发送到255.255.255.255 的更新数据包D包含R2 新路由表的数据包发送到192.168.1.1 和192.168.2.1 的单播更新数据包4.请参见图示。
所有接口都已配置为如图所示的带宽。
假设所有路由器都是使用默认的EIGRP 配置作为路由协议,那么从172.16.1.0/16 网络发往192.168.200.0/24 网络的数据包会采用哪一条路径?--------------------------------------------------------------------------------------------------------------------()A. A-B-EB. A-C-EC. A-D-ED.数据包会在A、B、E 和A、C、E 路径之间实施负载均衡。
CCNP资料1

1.何为融合网络?答:融合网络指的是在同一个网络中同时传输数据、语音和视频数据流。
2.IIN包含哪三个阶段?答:集成传输、集成服务和集成应用3.SONA框架包含下面哪些层?(b、c、e)a.接入层b.网路基础设施层c.交互式服务层d.企业边缘层e.应用层f.边缘分发层4.Cisco企业架构由哪些部分组成?答:园区、数据中心、分支机构、远程办公人员和WAN。
5.层次网络模型包含下面哪些层?(a.c.d)a.接入层b.网络基础设施层c.核心层d.分发层e.应用层f.边缘分发层g.网络管理层6.请描述企业复合网络模型的每个功能区域。
答:企业复合网络模型首先将网络划分成三个功能区域。
企业园区:该功能区域包含组建高度健壮的层次园区网所需的模块。
企业边缘:该功能区域聚合了企业网边缘上各种网络元件的连接性,包括到远程站点、Internet和远程用服务提供商边缘:该区域并不是由组织实现的,而用于提供到服务提供商的连接性。
7.功能区域“企业园区”包含哪些模块?答:企业园区功能区域包含下述模块:楼宇模块、楼宇分发模块、核心模块、边缘分发模块、服务器模块和管理模块。
8.下面哪些是实施网络变更的结构化方法中的步骤?(a、b、d)a.实施解决方案b.编写包含实施解决方案和实施结果的文档c.排除运营故障d.制定实施计划9.Cisco生命周期服务包括哪6个阶段?10.实施计划是在Cisco生命周期服务的哪个阶段制定的?11.制定实施计划之前必须收集下面哪些信息?a.验证测试的结果b.具体的网络信息c.现有网络的依存关系d.实施报告e.建议使用的资源12.您正在规划网络的路由协议变更,并在做任何修改前提交实施计划以获得批准。
该计划应包含下面哪些信息?a.项目联系人清单b.验证步骤c.要使用的工具d.实施任务e.设备位置信息13.下列哪种情形不适合使用静态路由?a.管理员需要完全控制路由器使用的路由b.需要为动态获悉的路由提供一条备用路由c.需要快速汇聚14.静态路由存在哪两个缺点?a.拓扑发生变化后需要重新配置b.度量值很复杂c.涉及汇聚d.无法动态发现路由15.对于其目标网络没有出现在路由表的数据流,根据什么来转发它们?a.动态区域b.默认路由c.边界网关d.黑洞(black hole)16.命令show ip route通常显示下列哪两项信息?a.下一跳b.度量值c.CDPd.主机名17.使用动态路由协议时,管理员在什么地方配置路由协议?a.每个区域中b.每个中间系统上c.每台路由器上d.每个最后求助的网关上18.下列哪项不是动态路由协议?a.RIPv1b.CDPc.EIGRPd.BGPe.RIPv219.度量值是什么?a.路由算法使用的度量标准b.一组用于管理网络资源的技术c.TCP/IP网络中的域间路由d.限制输入/输出速度的服务20.下列哪种路由协议只使用主网络来指定参与路由协议的接口?a.EIGRPb.RIPv1c.BGPd.OSPF21.ODR使用什么来在分支(末节)路由器和中央路由器之间传输网络信息?a.度量值b.BGPc.汇聚d.CDPe.TCPf.UDP22.下列哪项不是一种路由协议类型?a.链路状态b.默认c.高级距离矢量d.距离矢量23.什么是自动汇总?24.判断正误:非连续子网指的是属于同一个主网络,但被另一个主网络隔开的子网。
ccnp题库

FCAPSFault Management ‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐ FConfiguration Management ‐‐‐‐‐‐‐ CAccounting Management ‐‐‐‐‐‐‐‐‐‐ AQuestion 2FCAPS–model defined by the International Organization for Standardization (ISO).ITIL–framework for it profTNM–network management model is the Telecommunications Standardization Sector’s (ITU-T) Cisco lifecycle–model is often referred to as the PPDIOO modelQuestion 3EEM .IP SLA‐‐‐‐‐‐‐‐‐‐‐‐‐‐ CLISDM .CNA‐‐‐‐‐‐‐‐‐‐‐‐‐‐ GUIFTP ,TFTP,SCP‐‐‐‐‐‐‐‐‐‐‐‐‐‐ BackupCLI(command-line interface,命令行界面)GUI(Graphical User Interface,图形用户界面)SDM(Security Device Manager)是Cisco公司提供的全新图形化路由器管理工具;EEM(Embeded Event Manager)是Cisco IOS的嵌入式事件管理器;1)FCAPS (network maintenance model defined by the ISO)F – FaultC – ConfigA – Accounting2) What happens when running the command: logging console warnings.1-2- warning, notification, error, debugging…3- just warning logging4- warning, critical, alert, emergenciesAnswer:warning, critical, alert, emergencies(Notice this line doesn’t have the word “error”)3) what will be alternative for:ip ftp username xxxxxxip ftp password yyyyyyAnswer:ip http client username xxxxxxip http client password yyyyyy4) Network Maintenance: Choose from the list 2 network maintaining types.Answer:Structured and Interrupt Driven5) access-list 199 permit tcp host 10.1.1.1 host 172.16.1.1access-list 199 permit tcp host 172.16.1.1 host 10.1.1.1debug ip packet 199What would be the output shown on the console?Only communication between host 10.1.1.1 and host 172.16.1.16) what will happen if u configure two router as NTP server (something like that )Answer:The router will choose the best reliable server and will synchronise with it.7) The interface is up and protocol is up. When do u get these messages.%LINEPROTO‐5‐UPDOWN: Line protocol on Interface FastEthernet0/14, changed state to up %LINKDOWN‐3‐SERIAL:Answer:Emergency 0 Alerts 1 Critical 2 Errors 3 Warning4Notification 5 Informational 6 Debugging 78)Serial line is up,protocol is also up?But cdp neighbor not working?Answer:Data link layer.T1:ospf authentication1.Client is unable to ping R1’s serial interface from the client.Problem was disable authentification on R1, check where authentication is not given under router ospf of R1. (use ipv4 Layer 3)conf R1 was:interface Serial0/0.12 point-to-pointip address 10.1.1.1 255.255.255.252ip nat insideip ospf message-digest-key 1 md5 TSHOOTrouter ospf 1log-adjacency-changesnetwork 10.1.1.0 0.0.0.3 area 12default-information originate alwaysconf R2 was:interface Serial0/0.12 point-to-pointip address 10.1.1.2 255.255.255.252ip ospf authentication message-digestip ospf message-digest-key 1 md5 TSHOOTAnswer: on R1 need comand in router modearea 12 authentication message-digestAns1) R1Ans2) ipv4 OSPFAns3) ip ospf authentication message-digest command must be given on s0/0/0T2:HSRP TRACKHSRP: DSW1 does not become active.conf on dw1:track 1 ip route 10.1.21.128 255.255.0.0 metric thresholdthreshold metric up 1 down 2track 10 ip route 10.2.21.128 255.255.255.0 metric thresholdthreshold metric up 63 down 64interface Vlan10ip address 10.2.1.1 255.255.255.0standby 10 ip 10.2.1.254standby 10 priority 200standby 10 preemptstandby 10 track 1 decrement 60Answer: (use IPv4 Layer 3 Topology)On dsw 1 interface vlan 10 mode run:no standby 10 track 1 decrement 60standby 10 track 10 decrement 60(ip for track command not exact for real exam)Ans1) DSW1Ans2) HSRPAns3) delete the command with track 1 and enter the command with track 10.T3:BGP NeighborProblem: R1 is not able to ping 209.65.200.226.configuration on R1:router bgp 65001no synchronizationbgp log-neighbor-changesnetwork 209.65.200.224 mask 255.255.255.252neighbor 209.56.200.226 remote-as 65002no auto-summarycheck bgp neighborship. **** show ip bgp sum****The neighbor’s address in the neighbor command is wrong under router BGP. (use ipv4 Layer 3) Answer: need change on router mode on R1 neighbor 209.65.200.226Ans1) R1Ans2) BGPAns3) delete the wrong neighbor statement and enter the correct neighbor address in the neighbor command (change 209.56.200.226 to 209.65.200.226)T4:NAT ACLClient is not able to ping the web server, but the routers can ping the server. NA T problem. (use ipv4 Layer 3)problem on R1 Nat aclAnswer:add to acl 1 permit ip 10.2.1.0 0.0.0.255Ans1) R1Ans2) IP NA TAns3) under NA T access list, enter the command permit 10.2.0.0 0.0.255.255T5:R1 ACLClient is not able to ping the server. Except for R1, no one else can ping the server. (use ipv4 Layer 3)Problem:on R1 acl blocking ipacl something like this:deny 10.2.1.0deny 10.1.4.0deny 10.1.1.0Answer: add permit 209.65.200.224 0.0.0.3command to R1′s ACLAns1) R1Ans2) IPv4 Layer3 SecurityAns3) Add permit 209.65.200.224 0.0.0.3 to R1′s ACLT6: VLAN filterClient 1 is not able to ping the server. Unable to ping DSW1(Use L2 Diagram).Vlan Access map is applied on DSW1 blocking the ip address of client 10.2.1.3Ans1) DSW1Ans2) Vlan access mapAns3)No vlan filter 10T7:Port SecurityClient 1 is not able to ping the serverSituation: Unable to ping DSW1(User layer 2).On ASW1 portsecurity mac 0000.0000.0001, interface in err-disable stateAnswer:on asw1 delele portsecurity & do on interfaces shutdown, no shutdownAns1)ASW1Ans2)Port securityAns3)On fa1/0/1 and fa1/0/2 do disable port security and do shut, no shut.T8:SWItchport vlan 10Client 1 is not able to ping the serverSituation: Unable to ping DSW1 & in port channel configuratioin of ASW1 vlan 10 is not allowed. (Use L2 Diagram)On ASW1, on interfaces fa0/1, fa0/2 switchport access vlan 1Answer: on ASW1 change switchport access vlan 1 to switchport access vlan 10Ans1)ASW1Ans2)Access vlanAns3)give command: interface range fa1/0/1-/2 switchport access vlan 10T9:Switchport trunk.cant ping to web server 209.65.200.241Situation: Unable to ping DSW1 & in port channel configuratioin of ASW1 vlan 10 is not allowed. (Use L2 Diagram)question was about EtherChanelclient can’t obtain ip address(169.x.x.x)on ASW1 trunks allow vlan 20,200Answ: on port channel 13, 23 disables all vlans and give switchport trunk allowed vlan 10,200 Ans1)ASW1Ans2)Switch to switch connectivityAns3)int range portchannel13,portchannel23switchport trunk allowed vlan noneswitchport trunl allowed vlan 10,200T10:Eigrp asClient 1 is not able to ping the serverSituation: Unable to ping R4 fast ethernet port from dsw1.Check ip eigrp neighbors from DSW1 you will not see R4 as neighbor.(use ipv4 Layer 3)On DSW1 & DWS2 the EIGRP AS number is 10 (router eigrp 10) but on R4 it is 1 (router eigrp 1)Answ: change router AS on R4 from 1 to 10Ans1) R4Ans2) IP4 EIGRPAns3) Change eigrp AS number from 1 to 10T11:eitrp to ospfClient 1 is not able to ping the serverSituation: Unable to ping serial interface of R4 from the clients.On R4 in router eigrp:redistribute ospf 1 route-map EIGRP_to_OSPFBUT route-map was named:route-map EIGRP->OSPFAnswer:change in router eigrp router-map nameAns1) R4Ans2) route redistributionAns3) change the name of the route-map under the router EIGRP or router OSPF process from ‘to’to ‘->’.T12:IPV6 ospfIPV6 loopback of R2 cannot be pinged from DSW1’s loopback.Situation: ipv6 ospf was not enabled on R2’s serial interface connecting to R3. (use ipv6 Layer 3) Answer:interface configuration mode:ipv6 ospf 6 area 12Ans1) R2Ans2) IPV6 ospfAns3) on the serial interface of R2, enter the command ipv6 ospf 6 area 0 (make sure to check the IPV6 topology before choose Answer 3 because the options look similar)Device Error DescriptionASW11. Access port not in VLAN 102. Port Channel not allowing VLAN 103. Port SecurityDSW1 1. HSRP track 102. VLAN filterR1 1. Wrong IP of BGP neighbor2. NAT – Access list3. Redistribute access-listR2 1. IPv6: enable OSPF2. OSPF AuthenticationR4 1. EIGRP – wrong AS2. Redistribute (“to” & -> )1、access vlan的vlan 给错了2、port-security导致端口被errdisable3、V ACL4、EIGRP的AS号配置错误5、OSPF的authentication有问题,6、OSPF到EIGRP的redistribut的route-map名字写过了7、NA T的inside pool没有包含client的网段8、BGP的neighbor ip写错了,209.65.200.226写成了209.56.200.2269、到ISP的出接口的ACL少了一条permit10、其中一台接入交换机的Trunk allowed的VLAN少了VLAN 1011、HSRP的track语句指定有问题12、IPV6,R2的其中一个接口没有enable IPV6 OSPF。
最新IT认证 CCNP 642-813认证考试题库

pdf文档可能在WAP端浏览体验不佳。建议您优先选择TXT,或下载源文件到本机查看。
The safer , easier way to help you pass any IT exams.
3/9
The safer , easier way to help you pass any IT exams.
A. 20 percent of the traffic on a network segment should be local B. no more than 20 percent of the network traffic should be able to move across a backbone. C. no more than 80 percent of the network traffic should be able to move across a backbone. D. 80 percent of the traffic on a network segment should be local Answer: B,D 8.The Company LAN is becoming saturated with broadcasts and multicast traffic. What could you do to help a network with many multicasts and broadcasts? A. Creating smaller broadcast domains by implementing VLANs. B. Separate nodes into different hubs. C. Creating larger broadcast domains by implementing VLANs. D. Separate nodes into different switches. E. All of the above. Answer: A 9.The Company LAN switches are being configured to support the use of Dynamic VLANs. Which of the following are true of dynamic VLAN membership? (Select all that apply) A. VLAN membership of a user always remains the same even when he/she is moved to another location. B. VLAN membership of a user always changes when he/she is moved to another location. C. Membership can be static or dynamic. D. Membership can be static only. E. None of the other alternatives apply. Answer: A,C 10.The Company LAN switches are being configured to support the use of Dynamic VLANs. What should be considered when implementing a dynamic VLAN solution? (Select two) A. Each switch port is assigned to a specific VLAN. B. Dynamic VLANs require a VLAN Membership Policy Server. C. Devices are in the same VLAN regardless of which port they attach to. D. Dynamic VLAN assignments are made through the command line interface. Answer: B,C 11.In the three-layer hierarchical network design model; what's associated with the access layer? (Select two) A. optimized transport structure B. high port density C. boundary definition D. data encryption E. local VLANs F. route summaries Answer: B,E 12.You are assigning VLANs to the ports of switch R1. What VLAN number value is an assigned to
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CCNP级别网络工程师面试题
1、解决路由环问题的方法有(ABD) A. 水平分割 B. 路由保持法 C. 路由器重启
D. 定义路由权的最大值
2、下面哪一项正确描述了路由协议(C) A. 允许数据包在主机间传送的一种协议 B. 定义数据包中域的格式和用法的一种方式
C. 通过执行一个算法来完成路由选择的一种协议
D. 指定MAC地址和IP地址捆绑的方式和时间的一种协议 3、以下哪些内容是路由信息中所不包含的(A) A. 源地址 B. 下一跳 C. 目标网络
D. 路由权值
4、以下说法那些是正确的(BD)
A. 路由优先级与路由权值的计算是一致的
B. 路由权的计算可能基于路径某单一特性计算,也可能基于路径多种属性
C. 如果几个动态路由协议都找到了到达同一目标网络的最佳路由,这几条路由都会被加入路由表中
D. 动态路由协议是按照路由的路由权值来判断路由的好坏,并且每一种路由协议的判断方法都是不一样的 5、IGP的作用范围是(C) A. 区域内 B. 局域网内 C. 自治系统内 D. 自然子网范围内
6、距离矢量协议包括(AB) A. RIP B. BGP C. IS-IS D. OSPF
7、关于矢量距离算法以下那些说法是错误的(A) A. 矢量距离算法不会产生路由环路问题 B. 矢量距离算法是靠传递路由信息来实现的
C. 路由信息的矢量表示法是(目标网络,metric)
D. 使用矢量距离算法的协议只从自己的邻居获得信息
求职胜经/简历亮出你的精彩简历写作技巧,...面试前准备才是...
8、如果一个内部网络对外的出口只有一个,那么最好配置(A) A. 缺省路由 B. 主机路由 C. 动态路由 9、BGP是在(D)之间传播路由的协议 A. 主机 B. 子网
C. 区域(area)
D. 自治系统(AS)
10、在路由器中,如果去往同一目的地有多条路由,则决定最佳路由的因素有(AC) A. 路由的优先级 B. 路由的发布者 C. 路由的metirc值 D. 路由的生存时间 11、在RIP协议中,计算metric值的参数是(D) A. MTU B. 时延 C. 带宽
D. 路由跳数
12、路由协议存在路由自环问题(A) A. RIP B. BGP C. OSPF D. IS-IS
13、下列关于链路状态算法的说法正确的是:(bc ) A. 链路状态是对路由的描述
B. 链路状态是对网络拓扑结构的描述
C. 链路状态算法本身不会产生自环路由
D. OSPF 和RIP都使用链路状态算法
14、在OSPF同一区域(区域A)内,下列说法正确的是(d ) A. 每台路由器生成的LSA都是相同的
B. 每台路由器根据该最短路径树计算出的路由都是相同的
C. 每台路由器根据该LSDB
计算出的最短路径树都是相同的 D. 每台路由器的区域A的LSDB(链路状态数据库)都是相同的 15、在一个运行OSPF的自治系统之内:(ad ) A. 骨干区域自身也必须是连通的 B. 非骨干区域自身也必须是连通的
C. 必须存在一个骨干区域 ( 区域号为0 )
D. 非骨干区域与骨干区域必须直接相连或逻辑上相连
16、下列关于OSPF协议的说法正确的是:(abd ) A. OSPF支持基于接口的报文验证
B. OSPF支持到同一目的地址的多条等值路由
C. OSPF是一个基于链路状态算法的边界网关路由协议
D. OSPF发现的路由可以根据不同的类型而有不同的优先级 17、禁止 RIP 协议的路由聚合功能的命令是(c ) A. undo rip B. auto-summany
C. undo auto-summany
D. undo network 10.0.0.0
18、下列静态路由配置正确的是
(d) A. ip route 129.1.0.0 16 serial 0 B. ip route 10.0.0.2 16 129.1.0.0 C. ip route 129.1.0.0 16
10.0.0.2
D. ip route 129.1.0.0 255.255.0.0 10.0.0.2 19、以下不属于动态路由协议的是(d) A. RIP B. ICMP C. IS-IS
D. OSPf
20、三种路由协议RIP 、OSPF 、BGP和静态路由各自得到了一条到达目标网络,在华为路由器默认情况下,最终选选定(b) 路由作为最优路由 A. RIP B. OSPF C. BGP
D. 静态路由 21、IGP 包括如下哪些协议(acd) A. RIP B. BGP C. IS-IS D. OSPF
22、路由环问题会引起(abd ) A. 慢收敛 B. 广播风暴 C. 路由器重起
D. 路由不一致
23、以下哪些路由表项要由网络管理员手动配置(a ) A. 静态路由
B. 直接路由
C. 动态路由
D. 以上说法都不正确
24、在运行Windows98的计算机中配置网关,类似于在路由器中配置(a) A. 直接路由 B. 默认路由 C. 动态路由 D. 间接路由
25、关于RIP协议,下列说法正确的有:(ac ) A. RIP协议是一种IGP B. RIP协议是一种EGP
C. RIP协议是一种距离矢量路由协议
D. RIP协议是一种链路状态路由协议。
