A comparison of the management models of protected areas between China and the southern Africa r
与相似英语短语

与相似英语短语她的长相与她的母亲很相似。
下面是店铺给大家整理的与相似英语短语的相关知识,供大家参阅!与相似英语短语篇11. They seem to enjoy contact with like cells.它们好像喜欢与相似的细胞靠拢.2. The comparison must be made in a meaningful manner and must not be misleading.被评估企业与相似企业的比较应当有实际意义,并且不会引起误导.3. There must be a reasonable basis for comparison with the similar businesses in the market approach.采用市场途径必须具有与相似企业进行比较的适当基础.4. The user is OK will extraction data and similar data join, process these data.用户可以将可读取的数据与相似数据连接, 并处理这些数据.5. Please compare with others of similar age and experience and then mark in the appropriate box.请就下列项目与相似年龄及经验者做一比较,在适当空格做记.6. Stylistically, Weller is treading a similar path to that of Lenny Kravitz.在风格上,韦勒与伦尼·克拉维茨走着相似的路子。
7. There are significant parallels with the 1980s.与20世纪80年代有明显相似之处。
8. The basic design of the car is very similar to that of earlier models.这种汽车的基本设计与早期的样式非常相似。
(英语毕业论文)从女性主义视角分析电影《末路狂花》中塞尔玛的人物性格

最新英语专业全英原创毕业论文,都是近期写作1 合作原则视角下探析广告语篇中省略的会话含意2 林黛玉和简.爱不同命运的对比3 《飘》的成长主题解读4 人性的堕落——解析《蝇王》人性恶的主题5 商务英语信函中名词化结构的翻译6 英语商务合同的文体特点及其汉译7 家庭教育对保罗的影响:品读《儿子与情人》8 星巴克营销策略研究9 Why is Valentine’s Day More Popular than Qi Xi —Cultural Analysis of Traditional Festivals10 On the Narrative Arts of Hemingway's Short Stories----A Case Study of"A Clean Well-lighted Place"11 关联理论视角下的英语新闻标题研究12 论福克纳《八月之光》中的耶稣形象13 图式理论在高中英语阅读教学中的应用14 A Comparative Study on American and Chinese V alues Based on Friends15 矛盾的女性主义观—读乔治.艾略特的《弗罗斯河上的磨房》16 英汉汽车广告中常用“滑溜词”的对比分析17 宋词英译中的模因传播分析18 多丽丝·莱辛的《金色笔记》中的怀旧情绪19 A Psychological Analysis on Self-identity Loss of Black People in The Bluest Eye20 解析哈代《远离尘嚣》中的悲剧因素2122 从道德角度分析简.奥斯丁《劝导》中的女主人公安妮.艾略特23 论密西西比河对马克.吐温和《哈克贝利.费恩历险记》的影响24 中美婚姻观对比研究25 生活在夹缝中的畸形人——评《小镇畸人》26 An Analysis of the Fool in King Lear from the Perspective of New Historicism27 中式英语成因之分析28 文化差异对中美商务谈判的影响29 论《呼啸山庄》中两代人爱情模式的异同30 功能对等视角下汉语广告的英译策略31 埃德加爱伦坡短篇小说中美女的命运32 英语会话中间接拒绝语的语用研究33 现代社会的荒诞性——从黑色幽默解读《毛猿》34 从中西方节日看中西文化差异35 用本我,自我,超我的弗洛伊德理论来解析《红字》36 Where Should Gone With the Wind Go?——Study on The Disputes Among Critics of Gone With the Wind37 国际商务谈判中模糊语言应用的语用分析38 英语体育新闻中模糊语言的词汇特点及其翻译对策39 从语义翻译与交际翻译看《红楼梦》中诗词的汉译英40 A Lost New Woman in Patriarchal Society–Esthe r Greenwood’s Madness in Sylvia Plath’s The Bell Jar41 论《英国病人》中角色的自我认知42 On Instructional Designs for the Teaching of English Listening in Junior Middle School43 Study on Characteristics of American Black English from Social Perspectives44 On Dynamic E quivalence and Theory of ―Three Beauties‖—with Xu Y uanchong’s Translation of Tang Poems as an Illustration45 浅析《了不起的盖茨比》中的象征46 霍桑在《红字》中对人的罪恶的探究47 从曼诺林角度研究圣地亚哥形象48 美国价值观在电影《当幸福来敲门》中的体现49 跨文化背景下广告汉英翻译策略研究50 《喜福会》中的中美文化冲突51 《贵妇的画像》的过渡性特征的分析研究52 试析商务英语的修辞特征及其汉译53 从高中生生理和心理的角度探讨PPT使用的利弊54 (日语系毕业论文)义务教育的发展—就择校问题进行的探讨55 解析《麦田里的守望者》中霍尔顿的性格特征及其成因56 The Developments of Marriage View over Three Periods in the West57 英汉动物习语的隐喻认知分析58 建构主义学习理论在中学英语教学中的应用59 《傲慢与偏见》中的灰姑娘情节60 现代汉语量词英译研究61 爱默生超验主义对世纪美国人生观的影响——以《论自助》为例62 “自爱这罪恶占据着我的眼睛”:莎士比亚《十四行诗》中的自恋情结63 被忽略的人群--詹姆斯乔伊斯《都柏林人》女性角色分析64 教师在农村初中英语游戏教学中的角色分析--以某中学为例65 A Semantic Analysis of the Written Errors Committed by Chinese English Majors66 探析《雾都孤儿》中作者的乐观主义67 从《看不见的人》中透视美国黑人寻找自我的心路历程68 On Dickinson’s Ch oice of Nature as the Theme of Her Poems69 由女性“奴性”潜意识解析玛利娅姆多舛命运70 《老友记》中话语标记语的语用主观性研究71 浅析中西价值观差异对跨文化交际的影响及其解决方法72 《老人与海》中的象征主义73 分析数字“九”极其倍数的英译74 《海的女儿》中安徒生的悲剧情结分析75 On Symbolism in The Wizard of Oz76 英语委婉语的内涵77 英语流行歌曲中隐喻的功能分析——以后街男孩的歌曲为例78 从跨文化角度对商标翻译的研究79 A Comparative Study on Chinese and American Education80 中西酒店文化比较及探讨81 浅谈英语教学中体态语的运用82 论新闻英语中的选词及其翻译83 论小说《苔丝》中环境描写的作用84 On Michael Moore's Fahrenheit / From the Rhetoric Perspective85 从《纯真年代》的女性角色看旧纽约的女性地位86 浅析商务英语的语言特点及翻译87 A Freudian Psychoanalytical Interpretation of Catherine and Heathcliff in Wuthering Heights88 Movie Lines Imitation and Language Learning89 《红楼梦》人名翻译的归化与异化90 英语委婉语的认知分析91 Pragmatic Empathy and Chinese-English Translation92 人性的堕落——解析《蝇王》人性恶的主题93 小学英语学习策略及研究94 中美商务谈判中恭维语的分析95 On Morality in Shakespeare’s Macbeth96 人格、环境与命运——以弗洛伊德“人格结构理论”分析《还乡》中的主要人物命运97 浅析《两个新嫁娘》中的不同婚姻观98 《威尼斯商人》中鲍西亚形象浅析99 论模糊语言在广告英语中的功能与运用100 幽默元素在英语电影和电视剧中的翻译101 On Hardy’s Meliorism: An Analysis of Tess of the d’Urbervilles102 命运与性格--浅论《哈姆雷特》的悲剧因素103 Analysis on the Withdrawal of Feminism in The Great Gatsby104 素质教育下农村小学英语现状初探--以某县为例105 归化和异化在影片名翻译中的应用106 试论旅游文本英译策略107 一个典型的拜伦式英雄——论《呼啸山庄》中的希斯克利夫108 《弗兰肯斯坦》的悲剧性109 中外大学校训翻译分析110 中西方饮食文化对比111 第二语言习得中的正迁移与负迁移112 论斯嘉丽的形象特征分析113 分析文化差异在国际商务谈判中的影响114 从消费社会学探析《了不起的盖茨比》中盖茨比美国梦的幻灭115 “适者生存”——从社会达尔文主义看《热爱生命》116 论《杀死一只知更鸟》中的象征117 《荆棘鸟》女性意识浅析118 Tragic Elements——An analysis of the protagonist Holden’s growth experience in The Catcher in the Rye119 To Obey or Rebel –A Study of Female Characters in Moment in Peking120 浅论《儿子与情人》中劳伦斯的心里分析技巧121 王尔德童话《夜莺与玫瑰》中的唯美主义122 性别话语模式的社会语言学研究123 从关联理论看商务信函的礼貌策略124 从合作原则看《傲慢与偏见》中的会话含义125 论《简爱》对当代女性爱情观的启示126 An Analysis on Shear's Personality in The Bridge on the River Kwai127 中学生英语自主学习能力的培养128 On Application of TBLT to Junior High School Oral English Teaching129 An Analysis of Tess’s Tragedy in Tess of the D’Urbervilles130 从《喜福会》母女代沟看中西文化冲突131 浅谈提高高中生英语写作能力的途径132 浅论《黑天鹅》电影的象征手法运用133 试论《出狱》中“房子”的意象134 论《牧师的黑面纱》中的宗教讽刺135 相同的追求,不同的命运——《红楼梦》中的林黛玉和《傲慢与偏见》中的伊丽莎白比较136 女性主义家园乌托邦思想的构建--论夏洛特.吉尔曼在《戴安莎的作为》137 方位介词“over”的隐喻含义研究138 《哈利波特》中的励志精神139 外贸英语函电的文体特征及翻译对策140 从海明威的死亡哲学看麦康伯的死亡141 D.H.劳伦斯《东西》中象征主义的运用142 《还乡》中的生态女性主义解读143 英语词汇的文化内涵及词汇教学144 从认知语言学角度浅析网络语言中的隐喻现象145 背诵在中学英语学习中的作用146 从女性主义视角分析《纯真年代》中两位女主人公的不同爱情观147 花园小径句在英语阅读中的分析148 Discourse Analysis on the Translation of Person of the Year, an Editorial in the Time Magazine149 The Analysis of Promotion Strategy of L’Oréal in China150 听说法与交际法的区别151 The Glossology and Translation of Rhetorical Devices of Harry Potter152 场独立和场依存对不同主题阅读材料的影响研究153 从《男孩们女孩们》看身份问题对艾丽斯.门罗文学创作的影响154 英汉被动句语义特征对比分析155 《麦田里的守望者》中霍尔顿的性格分析156 On the Words and Expressions Belittling the Female157 Angel’s Face, Devil’s Heart—The Degeneration of Dorian Gray in The Picture of Dorian Gray158 论美国文学中的自然主义产生的社会文化根源159 The Alternation of Language: A Study of Microblogging V ocabulary160 英文商务信函的语言特点和写作原则161 分析《贵妇画像》中伊莎贝尔的个性特点162 任务型教学在新课标初中英语教学中的应用163 跨文化商务活动中的交际与礼仪164 目的论指导下的广告意译165 Comparison of models of Human Resource Management between East and West166 概念隐喻视角下看莎士比亚十四行诗167 从“老人与海”译本比较研究看理解在翻译中的重要性168 对意象翻译的初步研究169 论《最危险的游戏》中的生态伦理混乱170 《哈利波特》系列小说的浪漫主义情节分析171 中西方家庭教育对比研究——从《傅雷家书》和《致儿家书》的对比172 习语翻译中的文化缺省和补偿173 Translation Strategy on Culturally-loaded Expressions in Prison Break 174 英汉植物词文化内涵的比较研究175 中英颜色词及象征意义176 《占有》中维多利亚时代女权主义者的爱情观分析177 论《紫色》中的女权主义178 如何有效地扩展大学生英语词汇179 英文小说中的中国文化认同——《京华烟云》赏析180 有关“生命”概念隐喻的英汉对比研究181 浅析跨文化交际中的体态语182 凯瑟琳与苔丝悲剧命运的比较183 解读《喜福会》的中国式母爱184 中学生英语自主学习能力的培养185 英汉“去除”类运动事件表达异同的对比研究186 紫色中女人意识的觉醒187 英汉职业委婉语中“礼貌原则”之对比分析188 论企业国际化中的品牌翻译开题报告+论文( )189 英语委婉语的语用分析190 《还乡》中游苔莎的悲剧命运分析191 从跨文化角度浅析化妆品商标翻译192 中西婚姻文化差异193 The Use of Body Language in Teaching194 中国旅游指南的中译英研究(开题报告+论)195 模糊语在国际商务谈判中的语用功能研究196 中西方时间观差异分析197 希腊神话对英语语言的影响198 达尔文主义视角下的《卡斯特桥市长》199 Comparison of Color Words between Chinese and English Culture200 The Tragic Destiny of Brett Ashley in The Sun Also Rises。
高考英语:阅读复杂句分析题

2023届高考英语一轮复习阅读复杂句分析题【例题精讲】1. But the human mind can glimpse a rapidly changing scene and immediately disregard the 98 percent that is irrelevant, instantaneously focusing on the monkey at the side of a winding forest road or the single suspicious face in a big crowd.2.A comparison of British geological publications over the last century and a half reveals not simply an increasing emphasis on the primacy of research, but also a changing definition of what constitutes an acceptable research paper.,3. I believe that the most important forces behind the massive M&A wave are the same that underlie the globalization process: falling transportation and communication costs, lower trade and investment barriers and enlarged markets that require enlarged operations capable of meeting customers demands.4. It is entirely reasonable for auditors to believe that scientists who know exactly where they are going and how they will get there should not bedistracted by the necessity of keeping one eye on the cash register while the other eye is on the microscope.5. Instead, we are treated to fine hypocritical spectacles, which now more than ever seem in ample supply: the critic of American materialism with a Southampton summer home; the publisher of radical books who takes his meals in three-star restaurants; the journalist advocating participatory democracy in all phases of life, whose own children are enrolled in private schools.6.Their methods do not attempt to estimate the actual biomass (the amount of living biological matter) of fish species in particular parts of the ocean, but rather changes in that biomass over time.7. One leading authority says that these intensely powerful mental events can be not only harnessed but actually brought under conscious control, to help us sleep and feel better.8.But it is a little upsetting to read in the explanatory notes that a certain line describes a fight between a Turkish and a Bulgarian officer on a bridge off which they both fall into the river—and then to find that the line consists ofthe noise of their falling and the weights of the officers, "Pluff! Pluff! A hundred and eighty-five kilograms."9.But if robots are to reach the next stage of laborsaving utility, they will have to operate with less human supervision and be able to make at least a few decisions for them- selves—goals that pose a real challenge.10. There is, as Robert Rubin, the treasury secretary, says, a “disjunction”between the mass of business anecdote that points to a leap in productivity and the picture reflected by the statistics.练习1. It’s a real whodunit and the frustration when you realise what’s going on is horribly enjoyable.分析:_________________翻译:__________________________2. I mention the single parent with four kids running the show and I talk about the dad coaching a team that his kids aren’t even on.分析:_________________翻译:______________________________3. I’m secretly relieved because I know there’s real power in sharing volunteer responsibilities among many.分析:_________________翻译:___________________________4. That relief is coupled with a deep understanding of why the same people keep coming back for more: Connecting to the community as you freely give your time, money, skills, or services provides a real joy.分析:_________________翻译:___________________________5. In that sense, I’m pretty sure volunteering is more of a selfish act than I’d freely like to admit.分析:________________翻译:___________________________6. However, if others benefit in the process, and I get some reward too, does it really matter where my motivation lies?分析:________________翻译:___________________________7. Only at dinnertime are we eating together anymore,74 percent,according to statistics from the report.分析:__________________翻译:___________________________8. It is depending on NASA HUNCH high school class, like the one science teachers Gene Gordon and Donna Himmelberg lead at Fairport High School in Fairport, New York.分析:_______________翻译:__________________________9. Another way of setting realistic goals is to analyze your short and long term objectives, keeping in mind your beliefs, values and strengths.分析:_____________________翻译:_____________________________10. Lin-Manuel Miranda wrote this musical about Alexander Hamilton, in which the birth of America is presented as an immigrant story.分析:_____________翻译:_______________________11. Chinese models are the faces of beauty and fashion campaigns that sell dreams to women all over the world, which means Chinese women are not just consumers of fashion —they are central to its movement.分析:___________________翻译:____________________________12. …not only are today’s top Western designers being influenced by China —some of the best designers of contemporary fashion are themselves Chinese.分析:__________________翻译:___________________________13 The trend, then, was toward the “penny paper”—a term referring to papers made widely available to the public.分析:______________翻译:________________________14. After running hundreds of tests, the researchers noted that the monkeys would go for the higher values more than half the time, indicating that they were performing a calculation, not just memorizing the value of each combination.分析:________________翻译:__________________________15. When the team examined the results of the experiment more closely, they noticed that the monkeys tended to underestimate a sum compared with a single symbol when the two were close in value —sometimes choosing, for example, a 13 over the sum of 8 and 6.分析:_________________翻译:__________________________16. While I have only listed two of each, there are obviously many other situations that can arise.分析:________________翻译:_________________________17. Before asking questions about the course design, read the syllabus and learning management system information to be sure the answer isn’t hiding in plain sight.分析:________________翻译:___________________________18. Go to the government website to learn about programs and online tools available to help people under 30 build skills, find a job or start businesses all year round.分析:_______________翻译:______________________19. Through the Summer Employment Opportunities program, students are hired each year in a variety of summer positions across the Provincial Public Service, its related agencies and community groups.分析:______________翻译:_____________________20. With shining dark eyes, he seems like the kind of kid who would enjoy public speaking.分析:______________翻译:_______________________21. Whaley recalls how at the beginning of the year, when called upon to read, Chris would excuse himself to go to the bathroom.分析:_______________22. “It takes a lot for any student,”Whaley explains, “especially for a student who is learning English as their new language, to feel confident enough to say, ‘I don’t know, but I want to know.’”分析:______________翻译:_________________________23. This smart keyboard precisely measures the cadence with which one types and the pressure fingers apply to each key.分析:_________________翻译:__________________________24. The keyboard could offer a strong layer of security by analyzing things like the force of a user’s typing and the time between key presses.分析:_______________翻译:_________________________25. The keyboard can determine people’s identities, and by extension, whether they should be given access to the computer it’s connected to —regardless of whether someone gets the password right.分析:_________________翻译:__________________________27. Data collected from the device could be used to recognize different participants based on how they typed, with very low error rates.分析:_______________28. If the air you’re breathing is clean—which it would be if you’re away from the smog of cities—then the air is filled with life-giving, energizing oxygen.分析:__________________翻译:_____________________________29. Does Kilimanjaro deserve its reputation as a crowded mountain with lines of tourists ruining the atmosphere of peace?分析:_______________翻译:___________________________30. Scientists have responded by noting that hungry bears may be congregating around human settlements, leading to the illusion that populations are higher than they actually are.分析:________________翻译:__________________________31. There was a bit of me that didn’t want to love this when everyone else on the planet did, but the horror story is brilliant.分析:_______________翻译:_________________________。
云应用安全指南说明书

Table of contentsIntroduction (3)Convenience at a cost? (3)Build cloud-native applications from the AppSec perspective (5)Understand shared responsibility and infrastructure security in the cloud (5)Address software vulnerabilities: Application security testing (6)Secure your system design: Infrastructure as code (7)Maintain your software security initiative in the cloud (7)How Synopsys helps (8)Plan your deployment (8)Prepare your applications (9)Train your staff in cloud security (9)91% of companies invested in the cloud are concerned about cloud security.1IntroductionMoving to the cloud once meant taking a leap of faith into unknown territory. That’s no longer the case, as an increasing number of companies are using cloud services as the foundation for their infrastructure and/or application stacks to accomplish these goals:• Reduce capital expenditure. Organizations don’t need to create their own networks, purchase their own servers, or build their own data centers to house them.• Achieve scalability. Organizations that need an elastic model for allocating and consuming resources can quickly provision, scale, and release those resources.• Control operating costs. IT teams don’t have to worry about infrastructure maintenance and couldpotentially reduce or reallocate headcount.However, of the companies invested in the cloud, an overwhelming majority (91%) are concerned about cloud security.1 The tension between security concerns and the financial benefits of the cloud is putting pressure on security teams to keep pace with cloud adoption and growth. This presents a challenge for IT because cloud deployment and cloud-native software development require a fundamental change in approaches to security.For organizations considering a move to the cloud, this means deliberately planning and implementing neworganizational policies, skills, and activities. For those that have developed a DevOps culture and the corresponding toolchain to support their workflows, it means integrating security into that toolchain to further establish and reinforce its efficiencies within the cloud.In this eBook, we’ll discuss how organizations canproactively address risk management withinthe cloud. We’ll uncover the unexpectedsecurity challenges many organizationsface when shifting their applications andworkloads to the cloud, and we’ll discussthe security implications of building cloud-native applications. Read on to ensureyou’re prepared.Convenience at a cost?The advantages of the cloud are well-documented, yet concerns aboutsecurity remain the biggest reason moreorganizations aren’t completely adopting it.In the 2018 Cloud Security Spotlight Report,organizations mentioned general securityrisks (39%) and data security, loss, andleakage risks (38%) as two of the top barriersto cloud adoption.2 The top spot went to lackof staff resources or expertise (42%).No amount of monitoring, patching, or firewall protection can keep your applications safe if a hacker is determined to exploit them. In fact, because cloud service providers (CSPs) focus on doing everything they can to bolster the security of the hosting environments they provide, the point of greatest security weakness is the application itself.Even if you host only a portion of your sensitive data and applications in the cloud, your entire portfolio may be at risk if your cloud applications have security defects or you’re using your cloud provider’s security controls unsecurely. It’s likely that your cloud applications interface with your on-premises applications via database connection points. If threat agents find a path into an unsecure application, they can pivot—penetrating more applications and higher-value assets in your own network.Consider some of the most common security concerns about public clouds today:Table 1. Biggest security concerns in public clouds38%39%42%Data security, loss, and leakage risks General security risks Lack of staff resources or expertiseBuild cloud-native applications from the AppSec perspective At the end of the day, application development in the cloud is effectively the same as it is on-premises, but the application security approach with regard to infrastructure is new. In other words, to have a cloud-first security posture, organizations must extend testing for security vulnerabilities beyond the applications themselves to the underlying infrastructure stack. The first step in this process is understanding the relationship between you and your cloud service provider.Understand shared responsibility and infrastructure security in the cloudWhile there are many advantages of migrating workloads to a cloud environment, CSPs are increasingly delineating where their responsibility for security and compliance ends and the customer’s begins. This division of security labor is called shared responsibility, and it’s important to understand what you’re responsible for. Gartner notes that in the near future, at least 95% of cloud security failures will be the customer’s fault.3In IaaS models, for example, your cloud provider provides the infrastructure (servers, virtualization, storage, and networking), and you run virtual machines on that infrastructure. Your cloud provider may give you access to security features, such as database configuration, firewall controls, clustering, and group settings. How you put these building blocks together is up to you. If you don’t set them up and customize them correctly, you could compromise your security posture.Table 2. A comparison of cloud service modelsAn example of this is the highly publicized, and completely avoidable, Amazon Simple Storage Service (S3) bucket breaches. According to reports published last year, up to 7% of S3 servers can be accessed by the public without authentication, and as many as 35% are unencrypted.4These statistics highlight the importance of addressing security controls in your application architecture and implementing them correctly in your cloud environment. Organizations moving to the cloud must think differently about entitlements and authorization to account for new types of connections between services, databases, and multiple applications. Otherwise, they risk opening themselves up to these types of breaches.At the very least, you should follow these best practices for ensuring cloud architecture security:1. Keep IT up-to-date with current cloud security practices. Expertly trained cloud security professionals know how to identify and respond to potential threats. They remain one of the best ways to help protect your organization in the shared responsibility model.2. Use your software security tools and the security features of your CSP . It’s important to use both the security features already built into your cloud solution and third-party software to ensure you have implemented proper cloud security controls.3. Implement security in containerized / virtual machine (VM) environments. Many cloud providers use open source software components or container technology to develop and deploy applications, which can introduce unforeseen security weaknesses.Address software vulnerabilities: Application security testingFinding and fixing software vulnerabilities in the cloud requires all the same activities as it does on-premises. As a first step, you should use application security testing tools to help identify security weaknesses in code. The types of tools you should use vary based on a host of factors, but here are some techniques to consider:• Static application security testing (SAST) analyzes source code to identify vulnerabilities during development.• Software composition analysis (SCA) detects third-party open source components in source code and binaries. It’s useful for building containers and application images.1.2.3.• Interactive application security testing (IAST) performs runtime code analysis through instrumentation during testing.• Dynamic application security testing (DAST) allows you to conduct penetration testing inrunning applications.Secure your system design: Infrastructure as codeApplication security testing is a crucial step in preparing your applications for cloud migration, but it won’t solve all the problems that could affect your cloud deployment. Many problems that occur in cloud deployments result not from flaws in code but from misconfigurations, design flaws, and architectural weaknesses.• A skilled testing expert can perform threat modeling to model real-life scenarios with manual business logic testing. Threat modeling exposes vulnerabilities and can help you address them.• An architect with an understanding of security controls and frameworks can perform an architecture risk analysis . An ARA can help you design an architecture that lowers your risk of a security breach.Maintain your software security initiative in the cloud Automation and containerization help organizations build fast and deliver continuously, but they can makemanaging security a challenge. Using cloud security controls securely and building security into the continuous integration (CI) pipeline in your cloud development environment gives you the visibility, agility, and speed you need for fast, continuous delivery. As you continue to use the cloud, you must focus on developing a mature software security initiative there. That initiative should include these six security capabilities:1. Identity and access management (IAM). IAM forms the backbone of cloud security deployment. You mustbe able to establish an account and have the appropriate level of privileges to provision or orchestrateresources. At the very least, you should:• Conduct audits for sources of authentication and authorization.• Establish policies and procedures for appropriate user groups.• Determine roles and responsibilities for minimal human access to production systems.2. Data protection. Safeguarding important data is a critical piece of building and operating informationsystems in the cloud. You must:• Evaluate your inventory and classification of data assets.• Establish policies and procedures for safeguarding data in transit and at rest.• Evaluate compliance requirements based on business needs and risk tolerance.• Identify opportunities for encryption and responsible retention of data.3. Infrastructure security. The foundational infrastructure for your cloud must be inherently secure,whether it is public, private, or hybrid. When you assess this capability, review the network topology forsegmentation and multitenancy concerns. Also look for:• Network, computing, and storage requirements• Access control requirements• Provisioning needs for automation and orchestration opportunities1.2.3.4. Logging and monitoring. Logging and monitoring is key to providing greater visibility into occurrenceswithin a cloud environment in real time, or near real time. Recommended activities:• Obtain inventory lists of logging assets to identify aggregation, correlation, and analysis opportunities.• Establish policies and procedures for alerting and notifications.• Determine appropriate thresholds for critical business functions.• Identify an appropriate set of tools for logging and monitoring activities.5. Incident response. You need a solid incident response plan to contain an event and return to a knowngood state. To assess your incident response plan:• Conduct an audit to categorize critical business functions and assign risk profiles.• Review policies and procedures for incident response, alerts, and notifications.• Establish metrics to determine the severity of incidents and assign an appropriate response.6. Vulnerability and configuration analysis. Using an automated security mechanism for bothconfiguration management and vulnerability assessments can be a cost-effective approach forcloud environments.How Synopsys helpsNo matter where you are in your cloud migration, the Synopsys portfolio of products and services will help you make effective, and externally defensible, risk acceptance decisions about the use of public clouds.Plan your deploymentWe can advise you on how to take full advantage of the security controls and capabilities of your cloud provider. Our services help developers and security professionals decrease their time to market without sacrificing security.• Create a Maturity Action Plan (MAP). Provide a plan and roadmap to enhance your software security as a part of your cloud migration strategy with our Cloud Security MAP .• Implement cloud security policies . You probably have a security policy in place, but we can ensure that it’s updated to cover cloud concepts and help you establish platform security baselines.• Complete a Cloud Configuration Review . Unlike traditional pen testing, a configuration review provides insight into how effective your cloud applications are at using your cloud provider’s security controls to4.5.6.Prepare your applicationsBefore you migrate your applications to the cloud, we can identify and prioritize the security risks affecting them.• SDLC integration. Integrate Black Duck scans using AWS Code Services or supported development tools, such as CodeBuild, CodePipeline, Visual Studio, Eclipse, Jenkins, and Artifactory.• Ongoing monitoring.o Coverity is a powerful SAST solution that helps you find and fix common software vulnerabilities in your source code.o Black Duck is a comprehensive SCA solution for managing risk from open source and third-party software. Our industry-leading scanning algorithms and KnowledgeBase ensure completeopen source identification coverage originating from over 13,000 sources and over 80programming languages.o Seeker IAST correlates code and dataflow at runtime to ensure every identified vulnerability is real and exploitable and uncover complex vulnerabilities and logic flaws other tools can’t.• CI pipeline integration. Integrate SAST and open source scans into your CI pipelines to increase speed and agility while ensuring security and compliance.• Secure containers. Ensure the security and compliance of your containers using Black Duck for ElasticContainer Registry or the Elastic Kubernetes Service.Train your staff in cloud securityOur cloud instructor-led training (IL T) and assessments teach your team to identify and resolve missing or weak security controls affecting your product. Your team will also learn security best practices for your cloud service provider and become better equipped to mitigate security flaws affecting your applications, reducing your risk.Synopsys can help you secure your apps in the cloud.Learn more©2020 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks isavailable at /copyright.html. All other names mentioned herein are trademarks or registered trademarks of their respective owners.05/11/20.eb - The Ultimate Guide to Securing Your Cloud Apps-2020.。
德英两国医疗保障模式比较分析俾斯麦模式和贝弗里奇模式

德英两国医疗保障模式比较分析:俾斯麦模式和贝弗里奇模式丁纯2013-1-7 15:05:54 来源:《财经论丛》(杭州)2009年1期【英文标题】A Comparative Analysis of the Medical Security Models of Germany and Great Britain: Model of Bismarck and Model of Beveridge【作者简介】丁纯,复旦大学经济学院教授,博士。
(上海 200433)【内容提要】本文通过对德国社会医疗保障体制(俾斯麦模式)和英国全民医疗保障体系(贝弗里奇模式)的基本理念、筹资、偿付、服务提供规制的描述,勾勒出两大体制的核心特征,分析它们面临的问题和挑战,并对其改革进行了评判,在此基础上指出了对我国医疗保障制度改革的借鉴意义。
Briefly describing the fundamental concepts as well as the financing, reimbursement, and service arrangement of the German social health system(Bismarck model)and the British National Health Services(Beveridge model), the paper outlines the characteristics and institutional arrangement of the two systems, analyses the problems and challenges they are facing with and comments their reforms which have been carried out. On the basis of the comparison of the two models, the paper points out the significance to the health care system reform in China.【关键词】俾斯麦模式/贝弗里奇模式/全民医疗服务/社会医疗保障Bismarck model/Beveridge model/NHS/social health insurance1998年以来,我国医疗体制中以“看病贵、看病难”为核心的诸多问题一直没有得到解决,标志着城市医疗改革的流产,其结果又重新回到了医疗保障模式的选择阶段。
化学基础英文4_aromaticity芳香族化合物
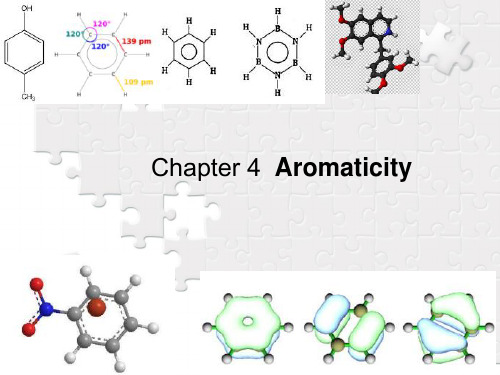
For comparison, reactions of cyclohexene, a typical alkene, with these reagents are also shown. As experimental evidence for a wide assortment of compounds was acquired, those incorporating this exceptionally stable six-carbon core came to be called "aromatic".
If benzene is forced to react by increasing the temperature and/or by addition of a catalyst, It undergoes substitution reactions rather than the addition reactions that are typical of alkenes. This further confirms the previous indication that the sixcarbon benzene core is unusually stable to chemical modification.
In practice, 1,3-cyclohexadiene is slightly more stable than expected, by about 2 kcal, presumably due to conjugation of the double bonds. Benzene, however, is an extraordinary 36 kcal/mole more stable than expected. This sort of stability enhancement is now accepted as a characteristic of all aromatic compounds.
国外地下综合管廊运维管理对比
国外地下综合管廊运维管理对比作者:王曦许淑惠徐荣吉塞音吉雅来源:《科技资讯》2018年第16期摘要:综合管廊的建设发展避免了路面开挖对交通的影响。
管廊的运维管理是保障综合管廊安全、高效运营的重要基石。
法国,日本,新加坡,德国四个国家在综合管廊运维管理方面提出了相应的法律法规和管理创新方法。
文章从法律法规、创新管理方法、监督管理模式三个方面进行分析和对比。
分析对比表明:相同之处是四个国家都非常注重在法律法规方面的建设和完善;都运用信息化管理系统,对管廊进行实时监控;都是以国家监督为主。
不同之处是法国所使用的机器人技术最为先进;日本法律法规最为完善和全面;新加坡的运维管理理念最为科学;德国的运营模式最为新颖。
关键词:综合管廊运维管理法律法规创新管理方法监督管理模式中图分类号:TU99 文献标识码:A 文章编号:1672-3791(2018)06(a)-0115-04Abstract:The construction and development of utility tunnel avoids the impact of road excavation on traffic. The operation and maintenance management of utility tunnel is an important cornerstone for ensuring the safe and efficient operation of utility tunnel. Four countries in France,Japan, Singapore and Germany have put forward corresponding laws and regulations and management innovation methods in the management of utility tunnel. The article analyzes and contrasts the three aspects of laws and regulations, innovative management methods, and supervision and management models. Analysis and comparison show that: something in common ground is that the four countries all pay great attention to the construction and improvement of laws and regulations; both use information management systems to monitor the corridors in real time;The difference is that the robot technology used in France is the most advanced; the laws and regulations in Japan are the most complete and comprehensive; the concept of operation and maintenance management in Singapore is the most scientific; the operating model in Germany is the most novel.Key Words: Utility tunnel; Operation and maintenance management; Laws and regulations; Innovation management method; Supervision and management model综合管廊代表着城市地下管线建设和发展的方向,是城市市政基础设施现代化的标志之一[1]。
中期答辩外文翻译
模糊系统与数学131(2002)101-106一个基于方案模糊信息的多属性决策方法Zhi-Ping Fan a,b , Jian Ma b,∗ , Quan Zhang b信息与决策部门,工商管理学院,东北大学,沈阳110006,中国部门的信息系统,香港大学,83Tat中港大道,九龙,香港摘要本文研究了对多属性决策方案的问题。
本文提出了一种新的方法来解决决策问题,也就是决策者对于他/她的偏好方案的一个模糊的关系。
对re.ect决策者的偏好信息,构建一个最优化模型来评估属性权重然后选择最理想的替代品。
最后,用一个例子来说明所提出的问题。
2001由Elsevier Science公司出版。
关键词:多属性决策;模糊偏好信息;方案排序1 引言在多属性决策(MADM)问题里,决策者往往需要选择或者排序非均匀和相互冲突的属性[3,14]。
MADM是在现实世界中许多的情况下出现的一个决策性问题[3,6,14,19,20],例如,在生产计划的问题上,生产速度,质量和运营成本都要考虑选择满意的方案。
大量的研究工作一直在进行一个多属性决策问题,其中之一的研究热点就是模糊集理论的应用解决不精确信息的多属性决策问题以[3,4,24]为代表的模糊条款。
通讯作者。
电话: +852-2788-8514 传真: +852-2784-4198电子邮件地址: isjian@.hk (J. Ma).0165-0114/01/$-见前页c 2001 由Elsevier科学有限公司出版PII: S0165-0114(01)00258-5在多属性决策问题里,决策者的偏好信息经常被用来排列替代品,然而,决策者的判断因形式和深度而异。
决策者可能不代表他/她所有喜欢的,或者可能代表他/她的属性或替代偏好的形式。
决策者的判断能力也各种各样。
解决多属性决策问题可以分成三类,根据决策者给出diEerent形式的偏好信息[3,14]:(1)无偏好信息[2,8,12]的方法,(2)与属性[1,5,7,9,22]信息;(3)对替代品[3,14,16,17,20,23]信息的方法。
2000 英语2 阅读text3
2000 英语2 阅读text3全文共3篇示例,供读者参考篇1Title: The Influence of Technology on SocietyIn today's modern world, technology has become an integral part of our everyday lives. From smartphones to social media to artificial intelligence, technology has revolutionized the way we communicate, work, and live. However, as our reliance on technology continues to grow, it is important to consider the impact that it has on society as a whole.One of the most significant ways in which technology has influenced society is through communication. With the advent of smartphones and social media platforms, we are now able to connect with people from all around the world instantly. This has made communication more efficient and convenient, but it has also raised concerns about privacy and security. Our personal information is now more vulnerable to hacking and misuse, leading to potential risks for individuals and organizations.Furthermore, the rise of automation and artificial intelligence has transformed the way we work. Many routine tasks that wereonce performed by humans are now being automated, leading to increased efficiency and productivity. However, this has also resulted in job displacement and a growing digital divide between those who have the skills to adapt to new technologies and those who do not. It is important for society to address these issues and find ways to ensure that technology benefits everyone, not just a select few.Moreover, technology has also had a profound impact on our daily lives. From shopping online to streaming movies to using virtual reality, technology has made our lives more convenient and enjoyable. However, this constant connection to technology has also led to concerns about addiction and mental health. Many people now spend hours each day staring at screens, which can have negative effects on their physical and mental well-being. It is crucial for society to find a balance between using technology for our benefit and knowing when to disconnect and engage in real-world interactions.In conclusion, technology has had a profound influence on society in both positive and negative ways. While it has improved communication, efficiency, and convenience, it has also raised concerns about privacy, job displacement, addiction, and mental health. It is important for society to address these issues and findways to use technology responsibly and ethically. By doing so, we can ensure that technology continues to benefit society and improve our lives for the better.篇2The article titled "Text3: The Benefits of Traveling Abroad" explores the advantages of traveling to different countries, learning about new cultures, and experiencing new ways of life. The author discusses how traveling can broaden our horizons, improve our communication skills, and enhance our understanding of the world.One of the main benefits of traveling abroad is the opportunity to immerse ourselves in a different culture. By experiencing firsthand the customs, traditions, and lifestyles of other countries, we can gain a deeper appreciation for diversity and become more open-minded individuals. Traveling allows us to break out of our comfort zones and challenge our preconceived notions about the world.Additionally, traveling abroad can greatly improve our communication skills. When we visit a foreign country, we are forced to interact with people who may not speak the same language as us. This can help us develop patience, adaptability,and the ability to communicate effectively even in challenging situations. Furthermore, learning a new language or improving our language skills through immersion can greatly enhance our personal and professional opportunities.Another benefit of traveling abroad is the opportunity to expand our knowledge and understanding of the world. By visiting historical sites, museums, and cultural landmarks, we can learn about the rich history and heritage of different countries. This can help us gain a better understanding of global issues, build empathy for people from different backgrounds, and develop a more nuanced perspective on international affairs.Moreover, traveling abroad can have a positive impact on our personal growth and development. It can help us become more independent, self-reliant, and resilient individuals. By navigating unfamiliar environments, overcoming language barriers, and adapting to new situations, we can build our confidence and expand our comfort zones. Traveling can also provide us with valuable life experiences, memories, and connections that can enrich our lives in lasting ways.In conclusion, traveling abroad offers numerous benefits for personal, social, and professional growth. It can help us become more open-minded, improve our communication skills, expandour knowledge of the world, and facilitate our personal development. As we explore new countries, cultures, and experiences, we have the opportunity to gain valuable insights, broaden our perspectives, and become more well-rounded individuals. So pack your bags, book your tickets, and embark on a journey of discovery and self-discovery through traveling abroad.篇3Text 3 presents a comparison between two types of weather forecasting methods: numerical models and human forecasters. The text explores the advantages and limitations of each method, as well as the potential benefits of combining the two approaches.Numerical weather models are computer-generated simulations that use mathematical equations to predict future weather conditions based on current observations. These models are able to analyze vast amounts of data and provide detailed forecasts for specific locations. They are also able to predict weather patterns that human forecasters may not be able to detect.On the other hand, human forecasters rely on their expertise and experience to interpret weather patterns and make predictions. They are able to take into account factors that numerical models may not consider, such as local terrain and atmospheric conditions. Human forecasters are also able to communicate their forecasts in a more understandable and accessible way for the general public.Despite their strengths, both numerical models and human forecasters have limitations. Numerical models may be limited by inaccuracies in the data they rely on, as well as by the inherent complexity of weather systems. Human forecasters are subject to biases and errors in judgment, which can affect the accuracy of their predictions.However, there is potential for synergy between the two methods. By integrating numerical models with human expertise, forecasters can combine the strengths of both approaches to improve the accuracy and reliability of weather forecasts. For example, human forecasters can use their knowledge to evaluate and interpret the output of numerical models, identifying potential errors or inconsistencies.Overall, the text suggests that a combination of numerical models and human forecasters may be the most effectiveapproach to weather forecasting. By leveraging the strengths of both methods, forecasters can provide more accurate and reliable forecasts to the public, helping to mitigate the impact of severe weather events and improve overall preparedness.。
(英语毕业论文)中美消费观的差异
英语专业全英原创毕业论文,公布的题目可以用于免费参考1 对小妇人心灵成长历程的探索2 《尤利西斯》的象征艺术3 浅析如何通过英语原版电影学习英语4 浅析亚里士多德悲剧情节观在《呼啸山庄》中的体现5 Listening in Interpretation6 以“三美论”对比《登高》两个英译版本的“意美”与“音美”7 《麦田里的守望者》中霍尔顿的反叛和自我救赎8 On the Influence of Social Environment on Pip’s Growth in Great Exp ectation9 关于英语谚语翻译的一些意见10 汉英谚语中关于文化价值观的比较11 “垮掉的一代”没有垮——简析《在路上》中年轻人的生活观12 The Effects of Family Education on Personalities in Little Women13 论教师的非语言行为在课堂教学中的作用14 论希斯克利夫出走的必然性15 文化差异对于中美商务谈判的影响16 论英语词汇中性别歧视现象及其产生的根源17 称呼语中的语码转换解析18 浅析隐藏在“面纱”之后的伯莎梅森19 本题目是全英文原创论文,需要完整可以联系QQ:80599074920 《远大前程》匹普与《了不起的盖茨比》盖茨比悲剧命运成因之比较21 国际商务英语合同翻译策略研究22 英语语篇连贯中的词汇衔接23 浅析初中生英语写作问题及对策24 论英语新闻中的模糊语言25 谈双关语的翻译26 从《看不见的人》中透视美国黑人寻找自我的心路历程27 源于真爱的结合:简爱的婚姻对当代人的启示28 《玻璃动物园》中的逃避主义解读29 A Comparison of the English Color Terms30 英汉广告中的双关语及其互译31 透过《老人与海》看海明威的人生哲学32 A Comparative Study on the Celebrations of Traditional Chinese and Western Festivals33 从中美家庭差异看集体主义与个体主义34 进退维艰的女性—《儿子与情人》的女性主义分析35 从概念隐喻看寓言的语篇连贯36 英语商务合同的文体特点及其汉译37 浅谈中美饮食文化差异38 《飘》中郝思嘉是现代女性的楷模39 从荣格的原型理论看《蝇王》中杰克的形象40 新课标下初中英语教师角色转变的研究41 从《马丁伊登》分析杰克伦敦的“超人”思想42 从关联理论看《茶馆》两个英译本中修辞格的处理43 英文歌曲在提高英语专业学生口语能力方面的作用4445 Y ellow Peril–the Image of Fu Manchu in the West46 英文商标的汉译47 中外青年婚姻观念差异——从《柳堡的故事》和《傲慢与偏见》中进行对比48 从礼貌原则探析酒店服务英语49 论《哈姆雷特》中的双关语50 聊天室中网络英语缩略词浅析51 Y ou-attitude 在商务信函中的运用52 从跨文化视角看文化定势及偏见在非言语交际中的影响53 中西文化中颜色词的象征意义54 浅谈数字翻译中的文化因素55 委婉语与英语交际56 场独立和场依存对不同主题阅读材料的影响研究57 思维导图在初中英语阅读教学中的应用58 《玻璃动物园》中的逃避主义解读59 枯萎玫瑰的爱和南方传统:威廉福克纳《献给艾米丽的一朵玫瑰花》中的颜色象征分析60 从对等功能理论看《卡斯特桥市长》中的比喻修辞61 浅析《美国的悲剧》中克莱德的悲剧命运62 布什总统演讲词中幽默话语的语用功能分析63 量词“片”与“piece”的语法化对比研究64 英语学习中语法的功能65 从儒学与基督教的角度探析中西文化差异66 从审美视角分析中国古典诗词的英译67 儿童本位主义在儿童文学翻译中的应用—《哈克贝利费恩历险记》两种译本的对比分析68 中英死亡委婉语对比分析69 浅析《理智与情感》中简奥斯汀的婚姻观70 新闻翻译中“编译”的合理性分析71 The Application of Task -Based Language Teaching in Middle School English Instruction72 中西方生死观之比较73 浅析隐藏在“面纱”之后的伯莎梅森74 社会语言学视角下女性语言的特点75 Comparison of models of Human Resource Management between East and West76 On the Unique Narrating Methods and Writing Skills in Brideshead Revisited77 A Comparison of the English Color Terms78 商务合同的语篇特征及其汉英翻译策略7980 《呼啸山庄》中男主人公希斯克利夫复仇动机分析81 A Comparison of the English Color Terms82 对话中语用意义的理论视角83 《愤怒的葡萄》中的圣经原型84 从阿里巴巴BB电子商务平台论中小企业的发展趋势85 On Dual Personality in Dr. Jekyll and Mr. Hyde from the Perspective of Freud's Psychoanalytic Theory86 英文商标名翻译的原则与策略87 论跨文化商务交际中的非语言交际的重要性88 探讨宗教在世界战争史中所扮演的角色89 维多利亚时期的艺术对文学的影响——以白衣女人为例90 从主位述位的角度阐述英语口语的连贯性91 论中美商务谈判风格的差异92 从象征手法浅析《了不起的盖茨比》中爵士时代的特征93 分析《贵妇画像》中伊莎贝尔的个性特点94 The Characters and Personality of American Slang95 从文化负载词褒贬意义看中西文化差异96 初中英语教师提问策略对课堂师生互动的影响97 情感教学在初中英语课堂中的理论和实践98 英汉颜色词的文化内涵99 非言语交际在中西文化中的差异100 An Analysis of the Religious Elements in Robinson Crusoe101 非语言交际中体语的文化分析102 从《嘉莉妹妹》看美国梦与道德观103 商务英语合同的翻译特点及策略研究104 汉语新词及其英译策略研究105 《一位女士的画像》伊莎贝尔婚姻悲剧的原因分析106 文化视野下的中美家庭教育方法的比较107 论自然主义在《野性的呼唤》中的体现108 A Comparison between Chinese and American Family Education109 海丝特白兰—清教时代的新女性110 DOTA游戏英雄名称汉译策略111 丁尼生《鹰》与休斯《鹰之栖息》的对比分析112 从合作原则和礼貌原则的角度分析赵丽蓉的小品113 从电影《七宗罪》看‘七宗罪’与基督教传统的关系114 Wi lliam Wordsworth’s Romantic Nature in Daffodils115 功能对等理论在新闻英语翻译中的应用116 浅析《他们眼望上苍》中女性意识的觉醒117 A Comparison of the English Color Terms118 A Study on the Cross-Cultural Management in the Sino-American Joint-V enture Enterprises --With Special Reference to Changan & Ford Motor Company119 从文化视角浅析英汉数字的翻译120 《圣诞欢歌》中斯克罗吉的性格分析121 马克吐温和哈克贝利芬青少年时期的比较研究122 Cooperative Learning: An Effective Way to Improve Junior Students’ Integrative Language Ability123 论美国黑人说唱乐的语言特色及其社会影响124 浅析好莱坞英雄主义中的传统英雄和反英雄形象125 《幸存者回忆录》中多丽丝莱辛的生态观126 《等待野蛮人》中的寓言式写作手法127 英语歧义初探及其排除方法128 Ethic V alues about Marriage and Sex in the Bible129 钱钟书翻译研究130 A Comparison of the English Color Terms131 跨文化交际中的中西方时间观念132 莫言小说《红高粱》中的转喻133134 中国奢侈品的营销之道135 从《麦琪的礼物》和《爱的牺牲》分析欧亨利的写作特色136 《药》的两个英译本中翻译技巧比较137138 《小城畸人》里的象征主义手法分析139 浅析英汉颜色词的文化内涵及翻译140 论《厄舍古屋的倒塌》的哥特式写作风格141 透过《德伯家的苔丝》看哈代托马斯的宗教观142 英语习语翻译中的“功能对等”143 Black Women's Searching for Identity in Toni Morrison's Sula144 英语阅读有效教学活动设计研究145 《哈克贝里·费恩历险记》中哈克和吉姆的人物形象分析146 被压抑的堕落的人性——《包法利夫人》女主人公性格分析147 教师在初中教学中对学生的评价148 从中英广告词中分析概念隐喻149 从《儿子与情人》谈家庭失和与失衡150 政府工作报告中衔接手段对比及翻译151 臻于完美的人物魅力——对简奥斯丁《劝导》中的女主人公的分析152 中西方爱情悲剧故事的比较分析——以“梁祝”和《罗密欧与朱丽叶》为例153 归化和异化翻译策略的研究154 从中英文动物隐喻看中国与英语国家的文化差异155 从英语口语与书面语的不同谈如何正确使用英语口语156 功能翻译理论指导下的中国旅游资料英译157 目的论指导下的广告意译158 《逃离》中卡拉的女性意识觉醒159 A Comparison of the English Color Terms160 A Comparison of the English Color Terms161 英汉委婉语对比研究162 A Comparison of the English Color Terms163 A Study of Narrative V oice in Jodi Picoult’s My Sister’s Keeper164 浅析《追风筝的人》中风筝的象征意义165 女王还是奴隶:女性主义辉映下的珀涅罗珀166 英语专业学生词汇学习策略特点研究167 《了不起的盖茨比》中的象征艺术168 巧克力包装的研究169 论《阿芒提拉多酒桶》中文学手法的运用及其艺术效果170 理智的喜剧,情感的悲剧析《理智与情感》中的婚姻观171 灰姑娘情结在《理智与情感》中的表现172 从《海狼》看杰克伦敦的女性观173 Major Barriers in Listening Comprehension of College Students174 形合与意合对比研究及翻译策略175 On the Gender Differences in Speech Act176 《贵妇画像》主题和写作艺术特征177 对盖茨比的美国梦幻灭的分析178 《欲望号街车》中的主要人物的性格与命运分析179 论美国精神在《阿甘正传》中的反映180 《丧钟为谁而鸣》的生态女性主义解读181 文化语境与语言交际能力的培养182 从生态女性主义角度看《德伯家的苔丝》中的爱情悲剧183 解析名词化与商务语篇的汉英翻译184 从文化差异的角度看《红楼梦》颜色词的英译185 解读《纯真年代》中的爱伦的悲剧原因186 从电视剧《绝望主妇》看委婉语的交际功能187 动物习语翻译中的归化和异化188 情景教学法在小学英语教学中的运用189 中式菜肴名称的语言特点及其英译190 中美饮食文化差异及其相互影响191 根据空缺理论在跨文化交际中如何翻译数字192 张爱玲与简奥斯汀的讽刺艺术比较193 论弗吉尼亚伍尔夫《海浪》的人物刻画194 Pursuing a Harmonious Man-Woman Relationship In The Thorn Birds 195 从《老友记》看美国幽默196 情景教学法在小学英语课堂中的应用197 从思维模式看中西方文化差异198 Cultural Differences in Business Negotiations: East and West199 对林语堂的《吾国与吾民》几种中译本比较研究200 《玻璃动物园》中的逃避主义解读。
