Key Account Management(Slides)-Tiger
体验商务英语综合教程1第二版-unit1【2024版】
Someone who works on a telephone switchboard, who you can call for help
An expert who studies financial data and recommends financial actions
Key Language:
Learn different Job Titles Learn countries and nationalities
Reading: Describing People
Skills Introducing yourself and others
Case Study Aloha in Hawaii
Key Language1 NhomakorabeaJob Titles
Match the words and the meanings
Business English
accountant cashier analyst
A person who takes and gives out money in a bank or shop
One that gives expert professional advice
One who uses the art of combining pictures, words and decoration in the production of books, magazines, etc
Business English
the company’s product strategy. S.A. :French abbreviation for “company limited”. senior manager:a position which falls between
Key Account全攻略
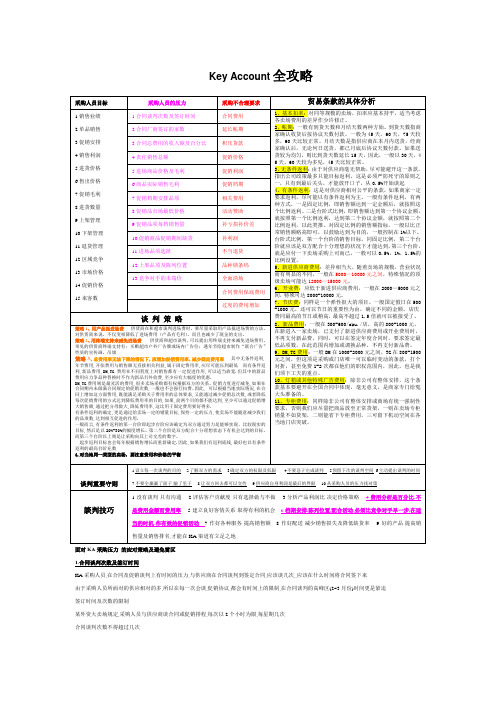
Key Account全攻略面对KA采购压力的应对策略及避免雷区1.合同谈判次数及签订时间KA采购人员,在合同及促销谈判上有时间的压力,与供应商在合同谈判到签定合同,应该谈几次,,应该在什么时间将合同签下来.由于采购人员所面对的供应相对的多,所以在每一次会谈,促销协议,都会有时间上的限制,在合同谈判的高峰区(2~3月份)时间更是紧迫. 签订时间及次数的限制某外资大卖场规定,采购人员与供应商谈合同或促销排程,每次以2个小时为限,每星期几次.合同谈判次数不得超过几次.在规定时间(3~5月以前)内一定要将今年所有合同签订下来实际案例:某供应商KA渠道经理与某外资KA客户第一次商谈今年合同内时,拿回一纸草约,回公司后仔细一算与去年比较大部份费用都增加一倍.供应商KA渠道经理与KA经理商谈后,认为无法签订此合同,协商之后认为以拖时间的方式来处理.公司与该客交易5,6年,了解该客的游戏规则,就是该KA客户本身有给采购人员时间的压力.时间期限在那一方?所以时间在那一方的身上压力就会在谁的身上.可以以二种方式来谈判一定要做的客户不谈重点,只谈方向及未来共同发展的愿景如果不是今年的重点客户2.合同厂商签订的家数采购人员负责的部门内所有的品项,KA大卖场都会给采购人员今年度必须要签定合同的家数.以前年的签订家数作为依据,因为每一家厂家或供应商会给卖场带来相对的合同收入(业外收入).采购所负责的部门必须签订5家,每家合同收入100万,共可收入500万.如果今年少了一家厂家来签订合同,要由其它四家来支撑另外100万是不可能的事.合同厂商签订的家数签订合同家数也是合同业外收入的保障,采购若未能作到合同签订家数,更不用谈可以达到合同总费用的收入额.采购人员将无法达成合同家数及合同总收入的二项指标了解KA客户签约数每年都有供应商因为无法支付大额的合同费用及运行费用而退出KA渠道的经营,相对也有新的供应商会想要进入这个现代渠道.我们必须了解有几家供应商会续约,有几家退出KA渠道,有几家新供应商会与KA渠道客户签订合同.3.合同总费用的收入额及百分比.延伸KA采购第2项压力,如果采购人员可以完成上述的指标, 才会有机会达成第3项指标,在合同谈判的过程是否可以百分百都拿到100万,可能在谈判的过程及年度结束后才能知道有无达成的可能,那就和采购人员的预估能力及判断力有关.KA合同费用有些是固定收取(保低),有些费用是依销售额的百分收取的.3.合同总费用的收入额及百分比.当然KA大卖场主管给采购人员压力,采购人员就会将压力给厂家,因此有些KA大卖场会制定不合理条款来保障他们的费用收入.例如:某卖场就会在合同设计成:1.销售额达1000万时给15%,超过1000万以15%比率给费用,另外年度返佣就会以合同签订收费.2.未超过1000万时必须给予150万保障费用入.每年在新合同谈判时KA大卖场主管会给采购人员,明年合同签定费用总收入及费用比.4.KA采购责任销售额KA大卖场采购人员和销售人员一样都有销售总额的责任目标,部门必须在今年达成多少销售总额,他们有一定的压力, 因为KA大卖场给的陈列空间及销售品项是有所限制,所以KA大卖场采购人员必须在品牌上有所选择.KA大卖场采购人员一个很重要的工作,就是活动安排与促销活动.促销是KA大卖场采购人员获取大量销售额的来源.进场商品价格及毛利.每家KA大卖场本身有设定一个商品的正常销售毛利,这就关系到进货价格及售出价格,例如:某KA大卖场的毛利率要求是30%,如果厂家给予进价为7元,KA大卖场将以10元卖出所得到的就是30%的毛利率.如果供厂家的建议零售价为10元,KA大卖场零售价定为8.5元时进价将只有6.4元,公司的利润比将无法支撑费用,但如果依然卖10元将失去市场竞争力,如果要做促销就必须加大促销力度才会有促销销的效果.有的KA大卖场是以你厂家给的进价加30%订价,有的KA大卖场会要求市场最低价在给30%的毛利.6.商品实际销售毛利.当年度结束后,KA大卖场主管会对采购人员进行,商品实际销售毛利的评估,毛利评估方式以商品卖出价格发票金额减去商品进价金额,得到销售毛利额销售毛利额除于卖出价格发票金额等于商品实际销售毛利率.有些KA大卖场的采购人员会在年低结束前,计算自己所负责的部门品项的商品实际销售毛利率,如果采购人员无法达成这项指标会转而向厂家要补毛利的费用或产品,有时KA大卖场的采购人员会要求,促销期间保持原毛利的作法,来确保该项指标的完成.7.促销档期安排品项KA大卖场的采购人员有一个很重要的指标就是在每一个促销档期内必安排几个上DM的促销品项,其实也就是收取DM费用金额指标,因此有时KA 大卖场的采购人员会主动要求上DM促销.有些KA大卖场在年度合同签订每年必须要安排及个档期的DM促销,上几次TG来保障该项指标的达成.8.促销品市场最低价格.促销品的价格将影响的实际的促销销售量,但主要的关键问题是在DM促销时KA大卖场会要求是市场最低价,如果在不同KA大卖场作相同品项及档期时,各KA大卖场会比较自己是不是市场最低价,如果不是将会互相竞争将价格向下修正,以达最低价格的目的.9.促销品项每档销售量.KA大卖场的采购人员在安排促销产品促销品项时会考虑一个重要因素,就是上一档期的促销效果,也就是促销档期内的实际销售量,如果你的产品无法在一个档期有合乎KA大卖场的上DM做TG的标准,KA大卖场的采购人员是不会让你的产品有机会上DM促销的,因而KA大卖场会在每一次促销档结后做档期促销检讨无法达标的KA大卖场的采购人员会受到严重的考核.10.促销商品促销期间缺货KA大卖场采购人员的压力中-促销期间的促销品项缺货.促销期产生严重缺货将受到门店的追讨门店主管于档期成效研讨会时,提出强烈的抗议.KA大卖场的采购人员会在促销前,中全力追货,而且在合同上订定缺货罚款条款.11.进场品项选择及陈列位置.KA大卖场的采购人员每一年都会要求厂家进场的品项,主要原因有可以增加业外收入及增加卖场品项的活络,大卖场也会给采购人员品项及陈列位置的限制,所以KA大卖场会有品项的淘汰制,来确保销售的达成.12.竞争对手的未端消费者价格.KA大卖场的采购人员有一个固定的工作就是调查竞争对手的未端消费者价格,以确保竞争力,了解市场行情以便与厂家谈判.大卖场可以为供应商提供的资源有:1.账期的优惠和结账的优先。
企业管理培训 Managing Key Account 大客户管理

• 负责建立可持 续性的关系 • 和指定客户紧 密协作 • 在客户和公司 之间建立信任 和信心 • 保证公司对待 客户有礼貌和 尊重
Key Account Management
Page 10
Problem Solver 解决问题
• Account Manager must be adept at solving problems • All issues and problems must be resolved quickly • Account Manager can never avoid addressing a problem or issue between customer and company
Page 7
Focal Point 联系人
• Primary interface between customer and company • Must be actively aware of all customer issues, problems, needs • Responsible for insuring customer’s and company’s message is understood
• 和选定客户建立并维持业务 关系 • 将利润潜力最大程度发挥 • 在最大限度内发展客户
– 收益、交易量、成本吸收等
• Provide “base” business for the company, business unit or product line • Catalyst to introduce a new product or open a new market • Improve the forecasting process
国际商务英语写作模板:商业计划书

国际商务英语写作模板:商业计划书篇一:商业计划书模板---英文版精编资料商业计划书模板---英文版BUSINESS PLAN TEMPLATEBUSINESS PLAN[My Company]123 MainStreetAnytown, USA -4567[Your Name][DATE]TABLE OF CONTENTS...商业计划书商业计划书模板---英文版BUSINESS PLAN TEMPLATEBUSINESS PLAN[My Company]123 Main StreetAnytown, USA 10000123-45671[Your Name][DATE]2TABLE OF CONTENTSExecutiveSummary ........................................... ................................................... .. (1)Management ........................................ ................................................... ................................................... . (2)[Company] History ........................................... ................................................... .. (5)[Product/Service] Description ....................................... ................................................... . (7)Objectives......................................... ................................................... ................................................... .. (9)Competitors ....................................... ................................................... ................................................... .. (10)Competitive Advantages ........................................ ................................................... .. (11)Innovation ........................................ ................................................... ................................................... . (13)Pricing ........................................... ................................................... ................................................... (14)Specific Markets ........................................... (15)Growth Strategy .......................................... ................................................... . (16)Market Size and Share ............................................. ................................................... (17)Targeting New Markets ........................................... ................................................... . (18)Location .......................................... ................................................... ................................................... .. (19)Manufacturing Plan .............................................. (20)Research & Development ....................................... ................................................... . (21)Historical Financial Data .............................................. ................................................... .. (22)Proforma Financial Data .............................................. ................................................... .. (23)Proforma Balance Sheet ............................................. ................................................... (26)Cost Control ........................................... ................................................... (27)Effects of Loan or Investment ........................................ ................................................... (28)Attachments ....................................... ................................................... ................................................... . (29)3Executive Summary [My Company] was formed as a [proprietorship, partnership, corporation] in [Month, Year] in [City, State], by [John Doe] in response to the following market conditions:[Startup, growth] opportunities exist in [Product/Service].The need for use of efficient distribution (转载于: 小龙文档网:国际商务英语写作模板:商业计划书)and financial methods in these overlooked markets.[I/We] have several customers who are willing to place large [orders,contracts] within the next three months.Several other prospective [customers/clients] have expressed serious interest in doing business within six months. [I/We] previously owned a company that was active in the widget markets. Over the past few years I spent much time studying ways to improve overall performance and increase profits. This plan is a result of that study. The basic components of this plan are:1. Competitive pricing2. Expand the markets3. Increased advertising4. Lower our unit costs,5. Thereby achieving higher profits.1. Sign contracts2. Increased advertising3. Increase office staffTo this end, [I/we] need investment from private individuals and/or companies. A total of $XXX isbeing raised which will be used to finance working capital, plant and equipment. The company will be incorporated and common stock issued to investors. The company will be run as a [proprietorship, partnership, corporation].Financial Goals Sales Net Income Earnings pershareYear 1 $25,000 .01 Year 2 $250,000 .12 Year 3 $375,000 .141Management[Name] [Title]??[Experience]??Sales growth from zero to $1,000,000 in five years.??Led market in market share - 30%.Formulated advertising budgets & campaigns.Pioneered new distribution channels. Established national sales force.Established national repair & service centers.Brought new and innovative products to the market.Designed point-of-purchase materials.[Education}University of BostonBoston, MA- Computer SciencesPresidentJohn Q. Doe, Chief Executive Officer, and Director since February 1988 and President since January 1990. Mr. Doe was the founder and Chief Executive Officer of the original operating company known as Random Excess, Inc. He has had experience in the widget field with his own firm, John Doe Co., of Oshkosh (Wisconsin), from 1980 to 1987. This firm was sold to FatCat Widgets, Inc. in 1987.篇二:商务英语写作(商业计划书写作格式)商务英语写作:商业计划书写作格式XX-03-24 13:39:08 来源:爱词霸资讯官网封面 (Title page)企业的名称和地址Name and address of business负责人的姓名和地址Name(s) and address(es) of principals企业的性质Nature of business报告机密性的陈述Statement of confidentiality目录 (Table of contents)1. 概述/总结 (Executive summary)2. 行业及市场分析 (Industry analysis)对未来的展望和发展趋势 (Future outlook and trends)竞争者分析 (Analysis of competitors)市场划分 (Market segmentation)行业预测 (Industry forecasts)3. 企业的描述 (The description of the venture)企业的宗旨和目标(Mission statement and objectives)产品或服务的描述 (Description of the product or service)企业的规模 (Size of business)产品的进一步开发(Future potential/product development)竞争优势 (Competitive advantage)办公设备和人员 (Office equipment and personnel)创业者的背景 (Backgrounds of entrepreneurs)4. 生产计划 (Production plan)制造过程/被分包的数量 (Manufacturing process /amount subcontracted)选址 (Location)厂房 (Physical plant)机器和设备 (Machinery and equipment)原材料的供应情况 (Sources of raw materials to be supplied)生产能力和提高的可能性 (Output limitations, if any, and scale-up possibilities)质量控制计划 (Quality control plans)5. 营销计划 (The marketing plan)定价 (Pricing)分销 (Distribution)促销 (Promotion)产品预测 (Product forecasts)预见的涨价 (Anticipated mark-up)竞争对手的反应 (Competitors’ response)市场份额预测 (Market share projection)控制 (Controls)6. 组织计划 (Organizational plan)所有权的形式 (Form of ownership)合作者或主要股权所有人的身份 (Identificationof partners or principal shareholders)负责人的权利 (Authority of principals)管理层成员的背景 (Management team background) 组织成员的角色和责任(Roles and responsibilities of members of organization)7. 风险与对策分析(Assessment of risks)企业弱点的评价 (Evaluate weakness if business)新技术 (New technologies)应急计划 (Contingency plan)8. 财务计划 (Financial plan)各种业绩比率和投资回报 (Summary of performance ratios, ROI etc.)销售预测 (Sales forecasts)财务预测的假设(Assumptions underpinning financial forecasts)损益表(Income statement / Profit and loss statement)预测现金流量表 (Cash flow projections)资产负债预估表 (Pro forma balance sheet)量本利分析 (Break-even analysis)资金来源和运用 (Sources and applications offunds)9. 融资需求 (Financing requirements)融资前的活动小结 (Summary of operations prior to financing)现在的股东和未付债款 (Current shareholders, loans outstanding)资金需要量及时间 (Funds required and timing)投资回报 (The deal on offer)资本负债比率和盈利与利息比率(Anticipated gearing and interest cover)投资者退出方式 (Exit routes for investors)附录 (Appendix)1. 管理人员简历 (Management team biographies)2. 职业咨询人员背景(Names and details of professional advisors)3. 技术参数和图纸 (Technical data and drawings)4. 专利、版权、设计等(Details of patents, copyright, designs)5. 审计的报表 (Audited accounts)6. 信件 (Letters)7. 市场调研数据 (Market research data)8. 租约或合同 (Leaser or contracts)9. 供应商的报价单 (Price lists from suppliers)10. 客户的订单 (Orders from customers)篇三:英文商业计划书模板英语商业计划书(Business Plan)第一讲:概述第二讲:现状分析第三讲:目标确定第四讲:组织结构第五讲:产品分析第六讲:市场分析第七讲:市场策略第八讲:生产分析第九讲:财务分析第十讲:附件第一讲:概述(executive summary)概述是整个商业计划的第一部分,相当于整个商业计划的浓缩,使整个商业计划的精华所在。
Oracle常用SQL命令

Oracle常⽤SQL命令创建表空间1.创建默认表空间WLP_DATCREATE TABLESPACE "MYSPACE" DATAFILE'D:\oracle\oradata\orcl\data/WLP_DAT.dbf' SIZE 32M REUSE AUTOEXTEND ON NEXT 32MLOGGING EXTENT MANAGEMENT LOCAL SEGMENT SPACE MANAGEMENT AUTO;2.创建临时表空间WLP_TEMP(⽤于缓存,可以不建)ALTER TABLESPACE "TEMP" ADD TEMPFILE'D:\oracle\oradata\orcl\data/WLP_TEMP.dbf' SIZE 32m REUSE autoextend on next 32m;创建⽤户并授权1CREATE USER "WLPING" PROFILE "DEFAULT"2 IDENTIFIED BY "123456"3DEFAULT TABLESPACE "MYSPACE" //默认指定表空间4TEMPORARY TABLESPACE "TEMP" //指定缓存表空间5 ACCOUNT UNLOCK; //⽤户⾮锁定67GRANT EXECUTE ON dbms_comparison TO "WLPING";8GRANT UNLIMITED TABLESPACE TO "XIR_MD";9GRANT "CONNECT" TO "XIR_MD";10GRANT "RESOURCE" TO "XIR_MD";1112-- GRANT DBA TO XIR_MD;PROFILE:Oracle系统中的profile可以⽤来对⽤户所能使⽤的数据库资源进⾏限制,使⽤Create Profile命令创建⼀个Profile,⽤它来实现对数据库资源的限制使⽤,如果把该profile分配给⽤户,则该⽤户所能使⽤的数据库资源都在该profile的限制之内。
五个关键成功自动化营销的秘密:B2B客户密码解密说明书

Five Keys to Successful Automated Marketing How to crack the B2B customer codeFind the best B2B prospects andconvert them into loyal customersIn the past,B2B transactions occurred in face-to-face meetings as a sales professional worked a product demo,business luncheon,or boardroom presentation to influence a customer and close the deal.Today,however,B2B stakeholders perform much of their product and service research online.In fact, 33%of buyers spent more time researching products in2020than they did before the pandemic.49%said they spent time doing extra research to ensure products meet their data security requirements.1As your prospects research and evaluate your offerings,they leave behind valuable clues to their intent.Understanding these clues—cracking the code—can help you tailor your messages to them,thereby providing them a more relevant,personalized experience.As a result,business-savvy marketing and sales departments have embraced marketing automation platforms,so their respective teams can work together on one common platform,reach B2B customers online,and drive revenue.“The average buyer uses6.9 information sources to makea purchase decision.”B2B Buying Disconnect, Trust PilotLast accessed August18,2021 (Complete form to download)“64%of marketers say marketing automation contributes tomore sales.”E-commerce Marketing Trend Report,Spotler and , Last accessed August18,2021 (Complete form to download)Marketing automation platforms automate repetitive manual tasks for email campaigns,web forms,and landing pages,thereby freeing your marketing team to be more efficient,productive,and strategic.Equally important,marketing automation can align marketing and sales teams with vital revenue-producing tasks such as:Generating,nurturing,and scoring sales leadsImproving customer loyalty and long-term engagementCross-selling and upsellingMeasuring marketing ROIAs B2B buying has moved online,marketing automation has become a must-have technology for marketing and sales.Companies that embrace automated marketing often see increased revenue and decreased marketing costs.This is because marketing automation enables companies to automatically reach customers and prospects across multiple channels and cost-effectively target them with context-appropriate and personalized messages.Indeed,many B2B marketing professionals say marketing automation is critical to their company’s long-term business success. Deciphering the B2B customer codeHow marketing automation providesB2B companies with a competitive advantageWhen a user visits your website and spends several minutes watching a video about a product,it’s important to know who the visitor is and their intent.Is this visitor a college intern conducting market research?A mid-level manager who’s heard about the features of a competing product?Or a senior executive who is poised to pull the trigger on a large purchase?Marketing automation platforms collect,analyze,and decipher various online clues to help paint a more accurate picture of your customers and their intent. Identifiers like cookies,device IDs,and other digital tools establish the identity of an online visitor.An accurate visitor profile is then created with information from other data sources,such as a job title.A marketing automation platform also provides insights based on a prospect’s behavior—such as the amount of time a person spent on a product landing page,which blog posts they read,and even if they started to sign up for a webinar but didn’t complete the web form.Once the marketing automation platform has identified where the prospect is in the sales journey,marketing and sales can target the prospect with context-appropriate,personalized messages and offers.Using a marketing automation platform to crack these B2B customer codes will give you a significant competitive advantage over your peers who don’t.Some of the top reasons for using a marketing automation platform are to:“95%of marketers say marketing automation was successful in helping them achieve primary objectives.”Marketing Automation Integration Survey, Ascend2and research partners,Last accessed August18,2021•Generate higher-quality leads•Increase revenue•Align sales and marketingCompanies that can accurately decipher a B2B customer code are on the path to increased lead conversion rates,shortened sales cycles,and improved win rates. Five keys to successful online marketingTransforming marketing vision into business realityA marketing automation platform provides B2B companies with the technological foundation needed to achieve five key goals of effective online marketing:1.Know your customersUnlike any other marketing solution,marketing automation enables acompany to aggregate relevant profile data from various online and offline sources to create a complete view of customers.In addition to your own proprietary customer data,you can add data from third-party vendors and other outside sources,including information abouta company’s demographics,organization,and buying patterns.And you canintegrate multiple marketing channels—such as email,mobile,and web—into a single marketing system to create comprehensive customer profiles.An integrated view of your customers’data helps you target them withappropriate and personalized messages.The payoff?Companies thatrecognize their customers and continually nurture them with marketingautomation see a significant increase in qualified leads.2.Crack the code on customer journeysMarketing automation’s robust tracking and analytics capabilities helpmarketing and sales teams understand a prospect’s online behavior—such as which stage of the sales funnel the prospect is in with precision.Thisenables you to deliver the right marketing message or sale offer at theoptimal time.A marketing automation platform can also alert you in real-time when aspecific customer visits your website.This allows you to providepersonalized content immediately after that customer’s visit,increasing the odds of a sale.Moreover,your ability to deliver relevant marketing collateral demonstrates value and helps advance the customer through the salescycle.3.Provide informed,personalized experiencesCustomers take different routes to purchasing a product or service.As they progress along their paths,their information needs and behaviors change.A prospect who is at the consideration stage may download a white paperabout industry trends.Further down the sales funnel,a prospect may review technical specifications and an implementation guide.Marketing automation will allow you to adapt your customer outreach with informed,personalized messages that meet the prospect’s needs at each stage and advance them to the next stage in the sales funnel.Suppose you’re hosting a conference in Las Vegas and your targetdemographic is senior risk management executives in the Midwest.Theprospects who fit the description will receive a personalized email invitation.The executives who open your email will receive precise,targeted messages based on whether they accept,reject,or ignore your invitation.The oneswho accept will receive a confirmation email and a reminder email or textmessage on the day of the conference.And at,or soon after,the conference,a salesperson will follow up with the executives.After the conference,the executives who decline the invitation will receive a “We hope to see you next time”email and a“This is what you missed” email.As for the executives who ignored the email invitation,they will seesponsored ads on Facebook,LinkedIn,and elsewhere for a designatedperiod of time until they accept or decline the invitation.This ability to provide informed,personalized messages is why B2Bmarketers use marketing automation for everything from scoring leads to automating lead flow and data integration to sending highly targetednurture emails.4.Reach your customers anywhereMarketing automation empowers marketing and sales to executepersonalized experiences across multiple channels,including email,direct mail,phone campaigns,mobile,social media,and online initiatives.When you can reach customers and prospects everywhere with sales-relevant insights and content,this helps close deals faster.And asmentioned earlier,marketing automation lets you learn about a customer’s online activity in real-time.The more targeted,personalized content your customers receive,the more time they’re likely to spend exploring yourwebsite.So you should consider every possible touchpoint and interaction—and maximize the impact of each.5.Drive revenue and marketing ROICMOs at top-performing companies say the most compelling reason forusing marketing automation is to increase revenue.This is hardly surprising given marketing automation’s ability to identify the best sales leads andnurture them through the sales funnel until they are ready to pull the trigger on a deal.One of the chief ways marketing automation decreases marketing costs and improves ROI is through better time management.Time is one of an employee’s most precious resources.With marketingautomation,marketers can spend their time on important initiatives,such as finding the best prospects,not manually sifting through sales leads orjuggling multiple marketing systems.Many users of marketing automation say its biggest benefit is its ability to save time.All told,marketing automation users often realize a substantial increase in sales productivity and a significant reduction in marketing overhead. How Oracle Eloqua Marketing Automation cracks the B2Bcustomer codeOracle Eloqua helps marketers manage the entire customer journey.You can leverage the industry’s richest data set in tandem with adaptive marketing tools developed for your specific needs.The result:prospects and customers receive relevant,consistent,and contextual experiences across multiple channels.One B2B company that has benefited from using Oracle Eloqua Marketing is Dow Jones, a business and financial news company.Dow Jones uses Oracle Eloqua to provide essential integration between its marketing and sales technologies—scoring leads,sending customer mail,ensuring clean data,and making sure that the right customer marketing permissions are in place.Oracle Eloqua functions in the background,leaving Dow Jones marketers free to focus on adding the essential creative elements required to make marketing work. During a one-year transformation,the B2B marketing team doubled the number of forms created,improved conversion rates by73%,and increased email marketing campaigns by36%.The sales team uses Profiler,an Oracle Eloqua sales tool,to present valuable information about contacts in rich format embedded in the sales team’s Salesforce workflow.Oracle Eloqua Marketing Automation empowers B2B companies to:1.Target the right customers at the right timeOracle Eloqua enables marketers to present personalized campaigns across email,display,search,web,video,and mobile.And its lead and campaign management tools ensure that you can deliver the right messages to the right customer at the right time.In addition to its targeted,personalizedcampaigns,Oracle Eloqua will help you generate new sales leads.And you can extend your global reach as Oracle Eloqua is now integrated withWeChat,China’s most popular messaging platform.B2B companies can use WeChat activity data for their cross-channel campaigns.2.Deliver intelligent,personalized marketingOracle Eloqua lets you strategically filter and segment customers based on their attributes,behavior,and geography to deliver targeted,personalized marketing.It collects and analyzes different profile data,customer behavior data,and third-party data so you’ll have a single comprehensive view ofeach customer.As part of Oracle’s marketing suite of solutions,OracleEloqua boasts a best-in-class partner ecosystem that delivers a diverseportfolio of innovative and fully integrated marketing technologies.Thiscentralized interface allows you to organize and assess your campaignsacross paid,owned,and earned channels to drive greater revenue.3.Understand a customer’s real intentThanks to Oracle’s marketing suite of solutions,Oracle Eloqua has access to the industry’s richest data set,so it can take unknown customer profiles and transform them into real-life prospects.It can also add information fromthird-party data sources and use identity resolution technology to createaccurate and fully detailed customer profiles.This comprehensive customer profile,plus a unified view of a customer’s behavior across email,socialmedia,and other channels,allows you to understand a customer’s intentions like never before.4.Measure marketing impactOracle Eloqua helps CMOs and their teams better analyze and report various customer metrics.CMOs are increasingly putting customers at the center of everything they do:leadership,strategy,and operations.As a result,spend on loyalty and retention marketing will increase by30%in2021while spend in other areas slows.4Use Oracle Eloqua’s intuitive digital whiteboard todesign multichannel campaigns and visualize every step in the campaign, ensuring that your customer messaging is precise.Also,Oracle Eloqua’s lead and campaign management tools provide you with immediate reporting and insights so you can improve your marketing efficiency.5.Align marketing and sales for greater ROIOracle Eloqua unifies various sources of intelligence about a buyer,such as email opens,web activity,social activity,and form submissions to create a comprehensive buyer profile that helps sales engage with the buyer about their specific interests or concerns.Collaboration between marketing andsales is enhanced as Oracle Eloqua pulls together all relevantcommunications,highlighting a buyer's interests and sales funnel status and the buyer’s multichannel activities in the sales cycle.This and otherinformation can be easily shared between marketing and sales—and isreadily available in the customer relationship management system. ConclusionTarget customers at every stage of the funnelB2B customers have moved much of their product research online and usually contact a company late in the sales cycle.Marketing automation helps marketing and sales work together to reach customers at every sales funnel stage with targeted,personalized messages. Marketing automation also automates many of the manual,repetitive tasks pertaining to customer data,email campaigns,and social media,enabling you to devote your time and energy to more rewarding strategic initiatives.“Spend on loyalty and retention marketing in2021 will increase by 30%while spend in other areas slows.”Predictions2021: Accelerating Out of the Crisis,ForresterLast accessed August18,2021 (Complete form to download)Key takeawaysThe average buyer uses6.9information sources to make a purchasedecision.1Marketing automation platforms can help you understand the intent ofprospects and customers and provide them with contextually informedand personalized messages in real-time,increasing the odds of a sale.Marketing automation enables B2B companies to deliver acomprehensive customer experience from the first interaction to theclosing sale.Marketing automation empowers marketing to devote their time andenergy to important strategic initiatives instead of time-intensivemanual tasks.B2B marketing professionals almost universally agree that automatedmarketing is critical to long-term business success.About Oracle MarketingB2B and B2C marketers use Oracle’s marketing,an integrated portfolio of applications,to drive sales,brand,and customer loyalty.Oracle’s marketing suite of solutions offers the industry’s richest data sets and most adaptive intelligence so marketers can deliver irresistible,consistent,and connected experiences to customers wherever they are and however they choose to engage.Sources1“B2B Buying Disconnect,”Trust Pilot,last accessed August 18,2021 (Complete form to download)2.“E-commerce Marketing Trend Report,”Spotler and , ,last accessed August 18,2021(Complete form to download)3.“Marketing Automation Integration Survey,”Ascend2and research partners, ,last accessed August 18,20214. Predictions2021:Accelerating Out Of The Crisis,Forrester,last accessed August 18,2021(Complete form to download)For more information,visit: /cx/marketingConnect with usCall+1.800.ORACLE1or visit .Outside North America,find your local office at:/contact./oracle/oracleCopyright©2021,Oracle and/or its affiliates.All rights reserved.This document is provided for information purposes only,and the contents hereof are subject to change without notice.This document is not warranted to be error-free,nor subject to any other warranties or conditions,whether expressed orally or implied in law,including implied warranties and conditions of merchantability or fitness for a particular purpose.We specifically disclaim any liability with respect to this document,and no contractual obligations are formed either directly or indirectly by this document.This document may not be reproduced or transmitted in any form or by any means,electronic or mechanical,for any purpose,without our prior written permission.This device has not been authorized as required by the rules of the Federal Communications Commission.This device is not,and may not be,offered for sale or lease,or sold or leased,until authorization is obtained.Oracle and Java are registered trademarks of Oracle and/or its affiliates.Other names may be trademarks of their respective owners.Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation.All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International,Inc.AMD,Opteron,the AMD logo,and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices.UNIX is a registered trademark of The Open Group.0120Disclaimer:If you are unsure whether your data sheet needs a disclaimer,read the revenue recognition policy.If you have further questions about your content and the disclaimer requirements,e-mail********************.。
北京版小学英语Unit7Whatarethetwelveanimals?Lesson23-24课件
Listen and match
Let's do
Eric is the big brother. Who is the second, third, fourth, and fifth child in the family?
Sentences
1)询问和回答十二生肖的轮回频率: -How often does each animal come around? -Every twelve years.
选词(组)填空 1. Happy Year __o_f_ the Tiger! 2. We Chinese _n_a_m__e_dthe years after twelve animals. 3. My __b_ir_t_h_-_y_e_a_r_ animal is the dragon. 4. I __w_a_s_ born in October. 5. _H__o_w__o_ft_e_n_ do you take a trip?
Sara: How often does each animal come around? 每只动物多久来一次?
Yangyang: Every twelve years. I was born in the year of the tiger, so my birth-year
每12年一次。
生肖
animal is the tiger.
练一练
rat dragon snake rooster dentist practice emperor season
蛇 国王 练习 季节
龙 老鼠 牙医 公鸡
练一练
rat dragon snake rooster dentist practice emperor season
KeyGuard 关键管理系统 安装和操作手册说明书
The Key Management system.Installation and operation manualTable of contents1. Installation of the Key management system (2)1.1. Cabinet installation (2)1.2. Control panel installation (2)1.3. Ethernet connection (3)1.4. Add On cabinet connection (4)1.5. Connection of control signals (6)1.6. Card Reader replacement (7)1.7. Mains and Ground connection (7)1.8. Battery connection (8)1.9. Adding keys (8)1.10. Use of sealed key boxes (8)1.11. Maintenance (8)2. Initial system startup (9)3. Operator Manual (11)3.1. Configuring access modes for keys (11)3.1.1. Issuing a key (11)3.1.2. Return keys (14)3.1.3. Emergency release of the keys (14)4. Technical data (15)1.Installation of the Key management system1.1.Cabinet installationInstallation of the system unit is carried out by 4 screws (included) to the wall. The wall should be strong enough to carry out 50 kg of the cabinet.1.2.Control panel installationThe control panel is mounted by means of one of the two brackets supplied with the device. One bracket is designed to secure the control panel from the bottom of the unit at an angle of 45%. Another bracket can be used to install the control panel from the right side of the unit.Bottom installationRight side installationRight side installationTo install the control panel, preliminary, it is necessary to knock out a square hole for the connection of the connecting wires. The hole has a slot on the contour of the laser and is easily removed. Similar round holes are located along the entire perimeter of the cabinet. They can be used to connect power wires and communication interfaces.The brackets of the control panel have some freedom of fastening, which makes it possible to precisely adjust the position of the panel, push it close, or slightly push the panel away from the housing. The bracket for horizontal fastening to the right of the unit has the ability to rotate about its axis, i.e. Allows you to fix the panel at a small angle.The panel is connected to the unit by a flat cable to the connector X5 or X6 of the battery charging module and control outputs (Fig. 1). The second connector is used to connect the keys modules.1.3.Ethernet connectionControl panel has a patch-cord Ethernet cable. You could use the adapter (included) if you need longer cable.1.4.Add On cabinet connectionIt is possible to connect several Add-on cabinets to the one control panel.Add-On cabinet connectionFig. 1Attention! It is important to use the insulating tube (included) to protect cable from sharp edges of.Attention! All Add-on cabinets must be grounded as well as the main cabinet.For any additional Key module or Add On cabinet it is required to set up the address on a DIP switches on a back panel of key modules. Left 4 switches set up the cabinet number and the right switches the module number.For your convenience flat cables for the Add-On cabinets and control panel are additionally equipped with the extra sockets male and female. So you could plug and play add on cabinets in any side.It is not possible to make a mistake with the sockets all connectors are identical.1.5.Connection of control signalsSystem could trigger up to 5 control signals from Battery module. You could link those signals to the Building Alarm system or to CCTV systems. Outputs could be programmed to the different events: alarm, faults, door open, close, key return and remove and so on.X1, X2 connectors have 4 solid state relays. Contacts are 250v 100mA 30 Om.Programming of the outputs and relays is carried out via the SecuriProx Studio configuration program.Connectors are removable. You can remove the connector to connect the wires and put it back on later.1.6.Card Reader replacementIf necessary, you can use readers of a different format. To do this, you must turn off the readers that come with the kit and connect the new ones to the X4 and X1 connectors of the control panel. Use the +, -, D0, D1 terminals. The format of the reader is selected using the SecuriProx Studio configuration program. The controller understands Wiegand interface up to 82 bits.Connectors X4, X1 Control panel1.7.Mains and Ground connectionThe key storage system has an internal input voltage of24V with automatic switching to battery operation. Foroperation from 90-240V the standard power supply unit from“Phoenix contact” is delivered.The mains connection should be done to the terminal«L» for the «Line» (in general brown wire) and to theterminal «N» for the «Neutral» wire (in general blue). Foryour convenience it is possible that the Key managementsystem will be equipped with the extra switch. IN this casethe «Line» wire should be connected to the switch terminal.Attention ! The metal cabinet of the unit, control paneland all the add-on cabinets must be grounded with aseparate grounding wire directly to the common ground ofthe building.1.8.Battery connectionAfter installing the entire system and connecting all interfaces, you need to connect the batteries.Attention! The system will not start up when only rechargeable batteries are connected. The main power supply is required to start. During normal operation, the system automatically charges batteries and monitors their operability.1.9.Adding keysThe keys are attached to the key fob with a 3 mm shacklemade of stainless steel. Shackle are disposable. Those. After fixingthe shackle in the key fob, it can not be pulled out. To replace thekey on the key fob, it is necessary to cut the shackle (bottom) atthe base of the key fob. A new ring with a new key should push the remainder of the old shackle into the key fob and fix the new shackle. The Key Fob has a chip with a unique number so the system could recognize the key by its key fob. Programming of the key fob, key name and number is possible with the help of the program SecuriProx Studio (supplied).With the help of software, you can read information from key storage systems for all unknown keyfobs (new keyfobs not entered into the system).e of sealed key boxesIn order to increase security, it ispossible to use key boxes to storekeys. In this case, the keys are alsoattached to intelligent key fobs with aunique chip, and then the key with thekey fob is inserted into a box, whichcan be sealed in the standard way. Thedelivery kit can include standard-sizeboxes (70 mm) and elongated boxesfor long safe keys of up to 105 mmlong (the size from the center of the hole to the tip of the key)1.11.MaintenanceKey storage requires service.Periodically (once a year or more often if necessary), it is necessary to lubricate the door hinges, movable parts of the lock (tongue) and the electro-latch with a silicone lubricant spray.2.Initial system startupThe system is programmed using SecuriProx Studio software (included in the package). In order for the key storage system to initially connect to the SecuriProx Studio server, you must set the IP address of the device, the server's IP address and other network parameters on the key storage system.To enter the initial settings mode, press the Settings button on the battery charging module (located inside the main unit from the right side). On the tab "IP settings" it is necessary to set the IP address of the device, the IP address of the server, and other network parameters. The default port of the server is 8000. If this port is already occupied on the server, then it is possible to change it. In this case, you must also change the port number and on the server itself. See the installation instructions for the software. To apply the changed settings, you must save them and reboot the device.The "Module Settings" tab allows you to check the connection with all key modules in the system. When the power is turned on, the system automatically searches for all connected modules and remembers their presence.The "Test" button is available on the "Module Settings" tab. This option allows you to test the cells for the keys presence, to check up the solenoids operation, Switch On the upper light and unlock the door lock.On the "Information" tab, you can see the serial number and version of the device, voltage settings. Including voltage and internal resistance of the battery. Check up the readers operation. There are also available the operating time since the last switching on and the total number of door openings.3.Operator ManualSIMPLE AND CONVENIENTA large touch screen allows not only tomanage the key storage system simply andeasily, but also to quickly get any informationyou are interesting. For example who andwhen got the key or which key cabinet withinthe site contains an actual key. You can alsogenerate and print reports of any kind with the software provided in the kit.Two Wiegand readers (hand in/ hand out) and a fingerprint reader from the world leader in biometric technologies of the French company Morpho Safran are could be integrated into the display case. The system allows access to the key storages without entering any additional information - all you need is a card or a fingerprint. When integrating with security alarm systems, messages from the security alarm can be displayed on-line. In particular, object protection status and confirmation of zone installation/ removal.3.1.Configuring access modes for keysAll system settings are carried out using SecuriProx Studio software (included in the package). To configure users, keys, key lists, time zones, access levels, and report generation, see the description for the SecuriProx Studio software package.3.1.1.Issuing a keyTo get a key present your card to the right reader (with a card reader option) or enter you ID and Password. In the case the Card & Code option set. You should present your card And enter the Password.For the finger print reader option you could present your finger for the authorization. In this case there is possibility to set up different access level for the different fingers. For example for the first (if you’re a manager and have access to all the doors) for the first finger you could set up the full access to the system and for the second finger you could set up only your room key. In this case you could use the second finger for everyday use and the first one in case of emergency.In case you are allowed to get single key. The system will unlock the door and light up and unlock the cell with your key.In case you are allowed to take several keys to you will get a menu with only your key list. You could check the status of keys (In, Out, Blocked, Wrong time to get) You can choose one or several keys and press Remove button. System will open the door and show you location and unlock the cells of the keys.To make things easy there are some options you could use.∙Filter – Remove from the list all the keys which is Out, blocked or prohibited to take by time. You will see only available and allowed for you to take keys.∙Find – You could search you key in a list. You could enter the name of the key or key number. In case you found list of keys you could choose one or several keyand press remove button or get back to the main screen to continue.∙Groups – There is a possibility to get a whole group of keys. You need to press Group tab, choose the required group of keys or several groups of keys andpress remove or exit to continue. The group of keys could have a time zone. Incase you come to the wrong time it will be back light by RED and have a statusTime – that means that you no permission to get this keys in this moment.∙Hostory – The last 16 events by every key is available directly from the touch screen of the control panel. Time & Date, event (In, Out & alarms) The personname and phone number also available in case it is enabled by software.∙Return – You always could switch to return mode.As soon as you choose key, several keys or group of keys just press Remove button. The system will unlock the door. In case several cabinets are present. The requared cabinet will be indicated by Flash Strip light at the top. When you open the Door The requared Cell will Flash and unlocks. You could take keys ione by one. After receiving all the keys you should close the door. The alarm will be triggered in case you will forget. All the time settings (open the door, unlock the cell and close the door you could adjust inthe software). There is an option to disable door sensor. In this case no alarm will triggered in case you will not close the door in time.All the removed returned keys will be shown on a screen.In case the system has a link to security system you will see the report to Arm of alarm zone.3.1.2.Return keysTo return the key or group of keys you should present your card to the left reader or enter ID and Password.You are allowed to return the key in any location. The system will read the Key Fob information and recognize the key and remember it location. The next day you will get this key from this location.As soon you return all the key you should close the door. Alarm will be triggered in case too is not closed.3.1.3.Emergency release of the keysIn case of a fault of the system there is an option to get keys manually. You should open the front door by emergency key, the same key will open the inner door. As soon you the inner compartment you could release keys by pooling magnets pins of the keys.4.Technical data。
FortiAuthenticator 身份验证与身份管理系统说明书
FortiAuthenticator FSSO Features§Enables identity and role-based security policies in the Fortinet secured enterprise network without the need for additional authentication through integration with Active Directory§Strengthens enterprise security by simplifying and centralizing the management of user identity informationAdditional FortiAuthenticator Features§Secure Two-factor / OTP Authentication with full support for FortiToken §RADIUS and LDAP Authentication§Certificate management for enterprise VPN deployment §IEEE802.1X support for wired and wireless network securitycommunicating this information to FortiGate devices for use in Identity-Based Policies.FortiAuthenticator delivers transparent identification via a wide range of methods: §Polling of an Active Directory Domain Controller;§Integration with FortiAuthenticator Single Sign-On Mobility Agent which detects login, IP address changes and logout;§FSSO Portal based authentication with tracking widgets to reduce the need for repeated authentications;§Monitoring of RADIUS Accounting Start records.DATA SHEETFortiAuthenticator ™User Identity Management and SIngle Sign-OnDATA SHEET: FortiAuthenticator ™HIGHLIGHTSFortiAuthenticator Single Sign-On User Identification MethodsFortiAuthenticator can identify users through a varied range of methods and integrate with third party LDAP or Active Directory systems to apply group or role data to the user and communicate with FortiGate for use in Identity based policies. FortiAuthenticator is completely flexible and can utilize these methods in combination. For example, in a large enterprise,primary method for transparent authentication with fallback to the portal for non-domain systems or guest users.Key Features & BenefitsFSSO Transparent User IdentificationZero impact for enterprise users.Integration with LDAP and AD for group membership Utilizes existing systems for network authorization information, reducing deployment times and streamlining management processes. Integration with existing procedures for user management.Wide range of user identification methods Flexible user identification methods for integration with the most diverse of enterprise environments.Enablement of identity and role-based securityAllows security administrator to give users access to the relevant network and application resources appropriate to their role, while retaining control and minimizing risk.DATA SHEET: FortiAuthenticator ™HIGHLIGHTSAdditional FunctionalityStrong User Identity with Two-factor Authentication FortiAuthenticator extends two-factor authentication capability to multiple FortiGate appliances and to third party solutions that support RADIUS or LDAP authentication. User identity information from FortiAuthenticator combined with authentication information from FortiToken ensures that only authorized individuals are granted access to your organization’s sensitive information. This additional layer of security greatly reduces the possibility of data leaks while helping companies meet audit requirements associated with government and business privacy regulations. FortiAuthenticator supports the widest range of tokens possible to suit your user requirements. With the physical time-based FortiToken 200, FortiToken Mobile (for iOS and Android), e-mail and SMS tokens, FortiAuthenticator has token options for all users and scenarios. Two-factor authentication can be used to control access to applications such as FortiGate management, SSL and IPsec VPN, Wireless Captive Portal login and third-party, RADIUS compliant networking equipment.To streamline local user management, FortiAuthenticator includes user self-registration and password recovery features.Enterprise Certificate Based VPNsSite-to-site VPNs often provide access direct to the heart of the enterprise network from many remote locations. Often these VPNs are secured simply by a preshared key, which, if compromised, could give access to the whole network. FortiOS support certificate-based VPNs; however, use of certificate secured VPNs has been limited, primarily due to the overhead and complexity introduced by certificate management. FortiAuthenticator removes this overhead involved by streamlining the bulk deployment of certificates for VPN use in a FortiGate environment by cooperating with FortiManager for the configuration and automating the secure certificate delivery via the SCEP protocol.For client-based certificate VPNs, certificates can be created and stored on the FortiToken 300 USB Certificate store. This secure, pin-protected certificate store is compatible with FortiClient and can be used to enhance the security of client VPN connections in conjunction with FortiAuthenticator.Additional Features & BenefitsRADIUS and LDAP User Authentication Local Authentication database with RADIUS and LDAP interfaces centralizes user management.Wide Range of Strong Authentication MethodsStrong authentication provided by FortiAuthenticator via hardware tokens, e-mail, SMS, e-mail and digital certificates help to enhance password security and mitigate the risk of password disclosure, replay or brute forcing.User Self-registration and Password Recovery Reduces the need for administrator intervention by allowing the user to perform their own registration and resolve their own password issues, which also improves user satisfaction.Integration with Active Directory and LDAP Integration with existing directory simplifies deployment, speeds up installation times and reutilizes existing development.Certificate Management Streamlined certificate management enables rapid, cost-effective deployment of certificate-based authentication methods such as VPN.802.1X AuthenticationDeliver enterprise port access control to validate users connection to the LAN and Wireless LAN to prevent unauthorized access to the network.DATA SHEET: FortiAuthenticator ™SPECIFICATIONSFortiAuthenticator 400CFortiAuthenticator 3000DFortiAuthenticator 1000D FortiAuthenticator 200D FortiAuthenticator Virtual ApplianceFortiAuthenticator 400E FortiAuthenticator 200EDATA SHEET: FortiAuthenticator™Maximum Virtual CPUs SupportedUnlimited Virtual NICs Required (Minimum / Maximum) 1 / 4Virtual Machine Storage (Minimum / Maximum) 60 GB / 2 TB Virtual Machine Memory Required (Minimum / Maximum)512 MB / 64 GBHigh Availability SupportActive-Passive HA and Config Sync HASPECIFICATIONSUL/cUL, CB, GOSTUL/cUL, CB, GOSTGLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 905 rue Albert Einstein Valbonne 06560Alpes-Maritimes, France Tel: +33.4.8987.0500APAC SALES OFFICE 300 Beach Road 20-01The Concourse Singapore 199555Tel: +65.6395.2788LATIN AMERICA SALES OFFICE Sawgrass Lakes Center13450 W. Sunrise Blvd., Suite 430 Sunrise, FL 33323United StatesTel: +1.954.368.9990Copyright© 2016 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary and may be significantly less effective than the metrics stated herein. Network variables, different network environments and other conditions may negatively affect performance results and other metrics stated herein. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet and any such commitment shall be limited by the disclaimers in this paragraph and other limitations in the written contract. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests, and in no event will Fortinet be responsible for events or issues that are outside of its reasonable control. Notwithstanding anything to the contrary, Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.DATA SHEET: FortiAuthenticator ™ProductSKU DescriptionFortiAuthenticator 200D FAC-200D 4x GE RJ45 ports, 1x 1 TB HDD.FortiAuthenticator 200E FAC-200E 4x GE RJ45 ports, 1x 1 TB HDD.FortiAuthenticator 400C FAC-400C 4x GE RJ45 ports, 1x 1 TB HDD.FortiAuthenticator 400E FAC-400E 4x GE RJ45 ports, 2x 1 TB HDD.FortiAuthenticator 1000D FAC-1000D-E07S 4x GE RJ45 ports, 2x GE SFP , 2x 2 TB HDD.FortiAuthenticator 3000D FAC-3000D 4x GE RJ45 ports, 2x GE SFP , 2x 2 TB HDD.FortiAuthenticator-VM LicenseFAC-VM-Base Base FortiAuthenticator-VM with 100 user license. Unlimited vCPU.FAC-VM-100-UG FortiAuthenticator-VM with 100 user license upgrade. FAC-VM-1000-UG FortiAuthenticator-VM with 1,000 user license upgrade.FAC-VM-10000-UG FortiAuthenticator-VM with 10,000 user license upgrade.FAC-VM-100000-UG FortiAuthenticator-VM with 100,000 user license upgrade.FC1-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–500 users).FC2-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–1100 users).FC3-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–5100 users).FC4-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–10100 users).FC8-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–25100 users).FC5-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–50100 users).FC6-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–100100 users).FC9-10-0ACVM-248-02-12 1 Year 24x7 FortiCare Contract (1–500100 users).FC7-10-0ACVM-248-02-121 Year 24x7 FortiCare Contract (1–1M users).ORDER INFORMATION。
Key-Account 市场变化与未来
讲师:黄国书
Key-Account 市场环境变化与未来 Key-
什么是市场环境的急剧变化? 什么是市场环境的急剧变化?
过去/现在 未 来 店头行销 客户管理 客户物流 直销服务 全面行销
产品行销 通路管理 单点配送 缩短通路 客户满意
Key-Account 市市场环境变化与未来 Key-
(专业领航)
Key-Account 市场环境变化与未来 Key-
客户管理 (Account Management)
店内执行 (Retail Execution)
物流效益 (Logistic Effectireness)
行销支援/控管 (Trade Marketing Support / Control)
什么是市场环境的急剧变化? 什么是市场环境的急剧变化?
过去/现在 强调推力 销售管理 人力作业 计划销售 追求成长 市场直觉 跟着老板 未 来 加强拉力 店内执行 电脑化作业 策略经营 健康发展 市场依据 领着老板
Key-Account 市场环境变化与未来 Key-
迈向高峰
相对第一
(学习专业)
绝对第一
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
获得尽可能多的独立销售订单;
长期目标
在与客户达成交易的过程中建立健康的客户 关系,使购买不断地重复。
© Copyright By Harbourlink Consultant Associates
明确你的单一销售标的
特定、并可度量 有时间限度
针对一个客户的产出
是单一的而非多重的
© Copyright By Harbourlink Consultant Associates
成长和困境模式的差异
模式 成长 现状 好 变革的方向 增长 提高或完善 所需的方案 锦上添花 具有优势
困境
糟
脱离 保护或恢复
最快的 有效的
© Copyright By Harbourlink Consultant Associates
第三应对模式:不关心
采取行动的可能性:低
需要的
结果
DC
“为什么要档我的道?
第四应对模式:过度信心
采取行动的可能性:零
现状
• 对现状的错误判断 • 眼界过低 • 对变革有强大的阻力
OC
需要的
结果
“谁想要你的提案,我从未有过如此好的感受?”
© Copyright By Harbourlink Consultant Associates
对付“过度信心”的策略
给他一点时间,过度自信者很快会 陷入困境之中。
“赢”和“结果”
“结果”的性质 “赢”的性质
1. 结果是产品对公司业 务流程的影响 2. 结果是可量化的 3. 结果是公司(组织) 的
1. 赢是个人自我承诺的 实现 2. 赢是不可量化的 3. 赢是个人的
© Copyright By Harbourlink Consultant Associates
标识须加倍关注的
策略领域,会有危 害,也可能是机会。 标识可以抵消或降 低你的策略地位中 的威胁之处;
© Copyright By Harbourlink Consultant Associates
开始你的策略性销售历程(作业)
列出你的“单一销售标的”
找出“变数” 区别是“机会”还是“威胁”
对购买作出最终的批准
特定销售中只有一个这样的角色,但可能 是一组人员,例如一个小组、委员会。
作用:
控制支出 授权放行 对资源的选择性应用 否决权 影响这一组织的最后防线
关注点:
会提出的问题: “ 这个投资能给我们带来什么样的回报?” “这对我们组织的影响将会怎样?
© Copyright By Harbourlink Consultant Associates
你的销售位置
对“标的”们对你的提案看法如何?
他们将会向你提出哪些问题?
他们对其他供应商的提案又如何看?
© Copyright By Harbourlink Consultant Associates
作业:销售位置
© Copyright By Harbourlink Consultant Associates
© Copyright By Harbourlink Consultant Associates
找寻合格的教练
一名好教练要符合3个标准: 1.你对这个人要有信心。 2.教练在你的目标客户中有信誉。
3.教练喜欢你的解决方案。
© Copyright By Harbourlink Consultant Associates
影响你实现销售标的的变数
市场的变化 技术的更新 产品线增加 竞争的加剧
营销策略变化
企业人员的变动 组织结构的重组
© Copyright By Harbourlink Consultant Associates
红灯 / 绿灯
标记 性质 应用
代表“小心”或
“危险”,帮助你 红灯 警惕问题。 代表你与竞争者地 不同之处 - 差异 绿灯 化区域
关注点:
会提出的问题: 这些会满足必需的性能指标么?
© Copyright By Harbourlink Consultant Associates
谁可能担任技术购买者?
法律顾问
会计咨询顾问
采购代理
人事经理
政府代表
© Copyright By Harbourlink Consultant Associates
角色: 数量:
作用:
评价产品或服务对于他们所做工作的影响 通常是几个或很多
使用或管理你提供的产品或服务的人 这些人将在你所提供的解决方案中生活 你产品/服务的成功直接关系到使用者的 成功 他们所从事的工作
关注点:
会提出的问题: “在我的工作或部门中它将怎样地工作?”
© Copyright By Harbourlink Consultant Associates
低成本的拥有 符合预算 提高生产力 可盈利 平稳的现金流 弹性
使用性购买者
可靠性 提高效率 提高技能 完成任务 解决问题 更好/更快/更容易完成工作 容易使用和学习
技术性购买者
符合标准 及时生产 最好的技术解决方法 可靠性 低价
找出购买影响者(作业)
© Copyright By Harbourlink Consultant Associates
购买者四种应对模式
第一应对模式 成 长 第三应对模式 困境
G
(Growth)
第二应对模式 困境
DC
(Don’t Care)
第四应对模式 过度信心
T
(Trouble)
OC
(Over Confident)
寻找经济性购买者的五个关键点
1. 这宗交易的金额大小 2. 购买公司的业务状况 3. 购买公司与你或你公司之间的关系 4. 购买公司对你产品或服务的认识 5. 购买行为与购买公司期望之间的密切程度
© Copyright By Harbourlink Consultant Associates
使用性购买影响者
© Copyright By Harbourlink Consultant Associates
第一应对模式:成长
采取行动的可能性:高
需要的
结果
G
差距
今天的
现状
“你的提案是降低或消除这一差距的吗?”
© Copyright By Harbourlink Consultant Associates
成长模式的特征用词
不能忽视使用购买者
© Copyright By Harbourlink Consultant Associates
技术性购买影响者
角色: 数量:
作用:
筛选供应商 几个或很多
在可衡量方面对你的产品进行检验 守门员-无权作出最终的决定,但有否 决权 可以因为说明书以及技术性原因说“不 ” 符合他们需求的性能指标
技术性购买影响者 (技术购买者)
Technical Buying Influences
使用性购买影响者 (使用购买者)
User Buying Influences
教练
Coach
© Copyright By Harbourlink Consultant Associates
经济性购买影响者
角色:
数量:
分析机会和威胁:红灯
必要信息的缺损
信息的不确定性
任何没有接触到的购买影响者
购买影响者中出现的新面孔
重组
© Copyright By Harbourlink Consultant Associates
绿灯——你的优势杠杆
优势是与竞争对手对比而存在
可以改善你销售地位的机会 与你单一销售标的相关
减少价格竞争
© Copyright By Harbourlink Consultant Associates
削减红灯?
利用绿灯 (优势杠杆法) 努力改变 忽视障碍
© Copyright By Harbourlink Consultant Associates
绿灯/红灯双重原理
找到弱势 (红灯)
找到优势 (绿灯)
© Copyright By Harbourlink Consultant Associates
再次强调:
关注购买者组合的整体
© Copyright By Harbourlink Consultant Associates
应对模式(作业)
© Copyright By Harbourlink Consultant Associates
今天的
现状
© Copyright By Harbourlink Consultant Associates
“不关心模式” 三种转变条件
1.购买者看见了成长和困境的出现。
2.购买者感受到来自另外一个处于成长或 困境的购买影响者压力。 3.你能展示一个购买者所未能看到的差距 存在。
© Copyright By Harbourlink Consultant Associates
Trainer: Tiger Yuan Date: Nov. 20-21, 2002
© Copyright By Harbourlink Consultant Associates
导言
策略性销售的概述
© Copyright By Harbourlink Consultant Associates
传统销售的困惑!?
© Copyright By Harbourlink Consultant Associates
识别复杂销售
购买组织有多个选择
销售组织有多个选择
买卖双方组织均有多层面的责任体系
购买组织的决策流程复杂,并可能有外部人士 参与
© Copyright By Harbourlink Consultant Associates
