A scalable, distributed algorithm for efficient task allocation
Analyzing the Scalability of Algorithms

Analyzing the Scalability ofAlgorithmsAlgorithms are essential tools used in various fields such as computer science, data analysis, and machine learning. The scalability of algorithms refers to their ability to handle increasing amounts of data or growing computational demands efficiently without compromising performance. In this article, we will delve into the concept of scalability of algorithms and discuss various factors that influence it.One of the key factors that affect the scalability of algorithms is the input size. As the amount of data increases, the algorithm should be able to process it within a reasonable time frame. The efficiency of an algorithm can be measured in terms of its time complexity, which describes how the running time of the algorithm grows with the size of the input. Algorithms with a lower time complexity are more scalable as they can handle larger inputs without a significant increase in processing time.Another important factor to consider is the space complexity of an algorithm. Space complexity refers to the amount of memory or storage space required by the algorithm to solve a problem. As the input size grows, the algorithm should not consume an excessive amount of memory, as this can lead to performance degradation or even failure to complete the computation. Algorithms with lower space complexity are more scalable as they can operate efficiently even with limited memory resources.Moreover, the structure and design of an algorithm can greatly impact its scalability. Algorithms that are well-structured and modularized are easier to scale as they can be optimized or parallelized to improve performance. Additionally, the choice of data structures and algorithms used within the main algorithm can influence its scalability. For example, utilizing efficient data structures such as arrays or hash tables can improve the scalability of the algorithm by reducing the time and space required for processing.Furthermore, the scalability of algorithms can also be affected by external factors such as hardware limitations or network constraints. Algorithms that are designed towork in a distributed system or parallel computing environment are more scalable as they can distribute the workload across multiple processing units. However, algorithms that rely on a single processor or have high communication overhead may not scale well when faced with increasing computational demands.In conclusion, analyzing the scalability of algorithms is crucial for ensuring optimal performance in handling large datasets or complex computational tasks. Understanding the factors that influence scalability, such as time complexity, space complexity, algorithm structure, and external constraints, can help developers and researchers design and implement scalable algorithms. By considering these factors and optimizing the algorithm accordingly, we can improve efficiency, reduce resource consumption, and achieve better performance in various applications.。
2015-2018系统集成项目管理工程师真题(上午英文试题)

2015-2018系统集成项⽬管理⼯程师真题(上午英⽂试题)2015-2018年系统集成项⽬管理师真题上午英⽂试题合集⼀、2015年上半年71、The()refers to the integration of complex physical machinery with networked sensors and software.It draws together fields such as machine learning,big data,the Internet of things andmachine-to-machine communication to ingest data from machines,analyze it(often in real-time),and use it to adjust operations.A.Industrial internetB.factory internetC.industrial webD.business internet72、Software engineers apply the principles of software engineering to thedesign,development,()testing,and evaluation of the software and systems that make computers or anything containing software work.A.requirementB.constructionC.serviceD.maintenance73、The work breakdown structure(WBS)has been widely used in management for software development project.()is generally NOT vaildated through the WBS.A.schedule and cost/doc/bdb6e5610d22590102020740be1e650e53eacf09.html anization structuringC.management coordinationD.quality of work74、is the output of the quality planning.A.Scope baselineB.Cost of qualityC.Scope checklistD.Quality checklist75、The features and functions that characterize a product,service,or result in a project are called()A.statement of workB.product scopeC.product qualityD.project scope71、Software engineering is the study and an application of engineering to the design,dvelopment,and(71)of software.A.maintenanceB.serviceC.runningD.deployment72、Cloud computing is a style of computing in which dynamically scalabledoften(72)resources are provided as a service over the internet.A.realB.rixedC.actualD.virtualized73、The Project Management Triangle is a model of the constraints of project management.These constraints have been listed scope(or quality),(73),and costA.resourceB.timeC.planD.tool74、Establishing a project(74)involves listen milestones,activities,and deliverables with intended start and finish dates,of which the scheduling of employees may be an element.A.cost management planB.riskmanagement planC.scope management planD.management schedule75、Risk management’s(75)is to assure uncertainty does not deflect the endeavor from the business goals.A.trendB.detailC.objectiveD.rule71、WLAN is increasingly popular because it enables cost-effective(71)among people and applications that were not possible in the past.A.Line B.Circuit C.Connection D.Interface(72)is not included in the main contents of the operation and maintenance of the information system.A.Daily operation and maintenance B.System changeC.Security management D.Business change73、In project time management,activity definition is the process of identifying and documenting the specific action to be performed to produce the project deliverables.(73)are not output of activity definition.A.Activity list B.Work Breakdown StructuresC.Activity Attributes D.Milestone Lists74、The customer asks your project to be completed6months earlier than planned.You think this target can be reached by-overlapping project activities.This approach is known as(74).A.balance engjneering B.fast-trackingC.Leveling D.Crashing75、The auditing function that provides feedback about the quality of output is referred to as(75).A.quality control B.quality planningC.quality assurance D.quality improvement71、____is a paradigm for enabling network access to a scalable and elasticpool of shareable physical or virtual resources with self-service provisioning and administration on-demand.A.VPNB.Big dataC.Cloud computingD.Cyber-Physical System72、Unlike more traditional embedded systems a full-fledged CPS is typically designed as a___of interacting elements with physical input and output instead of as stand alone decives.A.SystemB.mechanism/doc/bdb6e5610d22590102020740be1e650e53eacf09.html/doc/bdb6e5610d22590102020740be1e650e53eacf09.html work73、The___plan is aiming to integrate the Internet with traditionalindustries,and fuel economic growth.A.Internet Plus actionB.Internet actionC.Web Plus action/doc/bdb6e5610d22590102020740be1e650e53eacf09.html Plus action74、In order to facilitate configuration and change management,manual or automated tools may be used.Tool'selection should be based on the needs of____.A.Project manager/doc/bdb6e5610d22590102020740be1e650e53eacf09.html B membersC.Project stakeholdersD.Project Management Office(PMO)75、Human resource management is the management of human resources.It is a function in organizations designed to maximize employee____in sercice of an employer's objectives.A.workB.jobC.scopeD.performance71:The capability provided to the consumer is to use the provide's applications running on a c1oud infrastructure.The applications are accessible from various client devices through either a thin client interface,such as a web browser(e.g.,web-based E-mai1),or a program interface.A.IaaSB.PaaSC.SaaSD.DaaS(72)refers to the application of the Internet and other information techno1ogy in conventiona1industries.It is an incomplete equation where various Internets(mobi1e Internet,cloud computing,big data or Internet of Things)can be added to other fields,fostering new industries and business development.A.Internet plusB.Industry4.0C.Big dataD.Cloud computing73、For anyinformation system to serve its purpose,the ihformation must be(73)when itìs needed.A.integralB.availab1eC.irreplaceableD.confidential(74)is a project management technique for measuring projectPerformance progress.It has the ability to combine measurements of the project managementtriangle:scope,time and costs.A.Critica1path method(CPM)B.Earned value management(CEV)/doc/bdb6e5610d22590102020740be1e650e53eacf09.html present value method(NPVM)D.Expert judgment method(EJM)75、The key benefit of(75)is that it provides guidance and direction on how the project costs will be managed throughout the project.A.Plan Cost ManagementB.Control CostC.Estimate CostD.Determine Budget71、Retail firms analyze consumer sales trends and user preferences through internet user data.This belongsto()application areaA.big dataB.cloud computingC.internet of thingsD.artificial intelligence72、In the following cloud computing technology architecture,()represented by number3.A.PaaSB.SaaSC.IaaSD.cloud platform interface73、The seven basic qua1i ty too1s are used wi thin in the context of the PDCA Cycle to solve qua1ity-relatedprob1ems.These too1s are used in()in the fo11owing processes.A.p1an qua1ity namagementB.perform quality assuranceC.erform quality contro1D.perform quality improvement74、()is the process of implementing risk response plans,tracking identified risks,moni toring residualrisk,,identifying new risk,and evaluating risk process effectiveness throughout the project.A.Identify risksB.Contro1risksC.Plan risk responsesD.P1an risk management75、()is the approved version of the time-phased project budget,xcluding any management reserves,which can only be changed through formal change control precedures and is used as a basis for comparison to actua1results.A.The contro1accountsB.Funding requiremengC.The cost estimatesD.The cost baseline(71)is a programming model and an associated implementation for processing and generating big data sets with a parallel,distributed algorithm on a cluster.The model is a specialization of the split-apply-combine strategy for data analysis.A.HDFSB.ChukwaC.MapReduceD.HBase72、The IoT architecture can be divided into three layers.(72)is the key layer to realize the foundational capabilities which support the electronic devices interact with physical world.A.Sensing layer/doc/bdb6e5610d22590102020740be1e650e53eacf09.html work layerC.Application layerD.Operation layer73、Project Integration Management includes the processes and activities to identify, define,combine,unify,and coordinatethe various processes and project management activities within the Project Management Process Groups.(73)process does not belong to Project Integration Management.A.Developing project charterB.Developing project management planC.Analyzing project risksD.Monitoring and controlling project74、In project management and systems engineering,(74)is a deliverable-oriented breakdown of a project into smaller components.It is a key project deliverable that organizes the team's work into manageable sections.A.RBSB.PBSC.GBSD.WBS(75)is the sum of all budgets established for the work to be performed.A.CPIB.BACC.SPID.EAC⼋、2018年下半年71、Cloud storage is a model of computer of computer data storage in which the digital data is stored in logical pools.The physical storage spans multiple servers(sometimes in multiple locations),and the physical environment is typically owned and managed by a hosting company.As for the cloud concept,the cloud storage service is one kind of().A.IaaSB.PaaSC.SaaSD.DaaS72、()is a subset of artificial intelligence in the field of computer science that often uses statistical techniques give computers the ability to"learn"(i.e.,progressively improve performance on a specific task)with data.Without being explicitly programmed.A.Machine learningB.Program language learningC.Natural language learningD.Statistical learning73、Configuration management is focus on the specification of both the deliverables and the processes;While(73)is focused on identifying,documenting,and approving or rejecting changes to the project documents,deliverables,or baselines.A.cost managementB.change managementC.configuration managementD.capacity management74、Quality management ensures that an organization product or service is consistent.It has four main components:qualityplanning,quality assurance(74)_and quality improvement.A.quality objectiveB.quality policyC.quality controlD.quality system75、In a project plan,when the project manager schedules activities,he(or she)often uses ()method,precedence relationships between activities are represented by circles connected by one or more arrows.The length of the arrow represents the duration of the relevant activity.A.causality diagramB.Gantt chartC.histogramD.arrow diagram。
人简 历 吴维刚 - z 个人信息
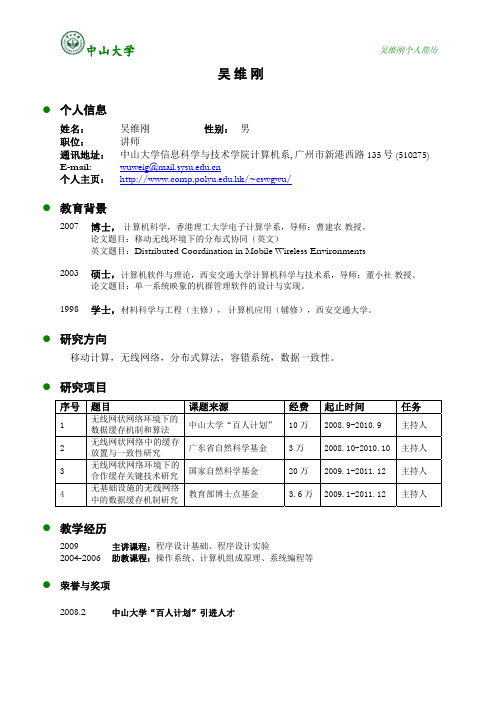
吴维刚z个人信息姓名:吴维刚性别:男职位:讲师通讯地址:中山大学信息科学与技术学院计算机系, 广州市新港西路135号 (510275) E-mail: wuweig@个人主页:.hk/~cswgwu/z教育背景2007 博士,计算机科学,香港理工大学电子计算学系,导师:曹建农教授。
论文题目:移动无线环境下的分布式协同(英文)英文题目:Distributed Coordination in Mobile Wireless Environments2003 硕士,计算机软件与理论,西安交通大学计算机科学与技术系,导师:董小社教授。
论文题目:单一系统映象的机群管理软件的设计与实现。
1998 学士,材料科学与工程(主修),计算机应用(辅修),西安交通大学。
z研究方向移动计算,无线网络,分布式算法,容错系统,数据一致性。
z研究项目序号题目课题来源经费起止时间任务1 无线网状网络环境下的数据缓存机制和算法中山大学“百人计划” 10万 2008.9-2010.9 主持人2 无线网状网络中的缓存放置与一致性研究广东省自然科学基金 3万 2008.10-2010.10 主持人3 无线网状网络环境下的合作缓存关键技术研究国家自然科学基金 20万 2009.1-2011.12 主持人4 无基础设施的无线网络中的数据缓存机制研究教育部博士点基金 3.6万2009.1-2011.12 主持人z教学经历2009主讲课程:程序设计基础、程序设计实验2004-2006 助教课程:操作系统、计算机组成原理、系统编程等z荣誉与奖项2008.2 中山大学“百人计划”引进人才z学术活动国际会议TPCEUC’09, EUC’08, ICCCN’08, NIMC’08, CODS’07, MSN’07论文评审期刊IEEE TC, IEEE TMC, JPDC, PMC会议ICDCS’08, MDM’08, ICPP’08, ICC’08DSN’07, PerCom’07, ICC’07, CCGrid07, AINA’07;ICDCS’06, PerCom’06, IPDPS’06;DSN’05, SRDS’05, ICCCN’05, Globecom’05.会议组织2005The 6th Int’l Workshop on Advanced Parallel Processing Technologies (APPT'05)2004The 2nd Int’l Symposium on Parallel and Distributed Processing and Applications (ISPA'04)z学术论文期刊论文:1.Weigang Wu, Jiannong Cao, Michel Raynal, Eventual Clusterer: a Modular Approach to DesigningHierarchical Consensus Protocols in MANETs, IEEE Transactions on Parallel and DistributedSystems (TPDS), 20(6), pp. 753-765, June 20092.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, Efficient Algorithms for Fault TolerantMobile Agent Execution, International Journal of High Performance Computing andNetworking(IJHPCN), 6(2), pp. 106-118, 20093.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, Using Asynchrony and Zero Degradation toSpeed up Indulgent Consensus Protocols, Journal of Parallel and Distributed Computing (JPDC),Elsevier, 68(7), Jul. 2008, pp. 984-996.4.Jin Yang, Jiannong Cao, Weigang Wu, Efficient Global Checkpointing Algorithms for MobileAgents, Concurrency and Computation: Practice and Experience, John Wiley & Sons, 20(7), May.2008, pp. 825-838.5.Weigang Wu, Jiannong Cao, Jin Yang, A Fault Tolerant Mutual Exclusion Algorithm for Mobile AdHoc Networks, Pervasive and Mobile Computing (PMC), Elsevier, 4(1), February 2008, pp. 139-160.6.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, Design and Performance Evaluation ofEfficient Consensus Protocols for Mobile Ad Hoc Networks, IEEE Transactions on Computers (TC),56(8), Aug. 2007, pp. 1055-1070.会议论文:1.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Contention-Aware Data Caching in Wireless Multi-hopAd Hoc Networks, 6th IEEE International Conference on Mobile Ad-hoc and SensorSystems(MASS’09), October 12 - 15, 2009, Macau2.Weigang Wu, Jiannon Cao, Xiaopeng Fan, Overhearing-aided Data Caching in Wireless Ad HocNetworks, 6th IEEE ICDCS International Workshop on Wireless Ad hoc and SensorNetworks (WWASN’09). June 22-26, 2009 Montreal, Canada3.Jiannong Cao, Kun Xie, Weigang Wu, Chuda Liu, et al., HAWK: Real-world Implementation ofHigh-performance Heterogeneous Wireless Network for Internet Access, 1st ICDCS International Workshop on Next Generation Network Architectures (NGNA’09), June 22-26, 2009Montreal, Canada.4.Ye Yan, Jiannong Cao, Chuda Liu, SeongWoo Kim, Weigang Wu, A Dual Re-authenticationScheme for Fast Handoff in IEEE 802.11 Wireless Mesh Networks, IEEE Wireless Communications and Networking Conference (WCNC’09), April 4 – 8, 2009. Budapest, Hungary.5.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Hui Cheng, Modeling Hierarchical Gossiping inReliable Multicast Protocols, Proc. The 2nd International Conference on Future Generation Communication and Networking(FGCN’08), December 2008, Sanya, Hainan Island, China.6.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Michel Raynal, On Modeling Fault Tolerance ofGossip-Based Reliable Multicast Protocols, Proc. of the 37th International Conference on Parallel Processing (ICPP’08), Portland, USA, Sep. 8 – 12 2008.7.Vaskar Raychoudhury, Jiannong Cao, Weigang Wu, Top K-leader Election in Wireless Ad HocNetworks, Proc. of the 17th International Conference on Computer Communication Networks (ICCCN'08), St. Thomas, US Virgin Islands, August 4-7, 2008.8.Jiannong Cao, Corentin Travers, Michel Raynal, Weigang Wu, The Eventual Leadership inDynamic Mobile Networking Environments, Proc. of the 13th IEEE Pacific Rim International Symposium on Dependable Computing (PRDC'07), Melbourne, Australia, December 17-19, 2007. 9.Weigang Wu, Jiannong Cao, Michel Raynal, A Dual-Token-based Fault Tolerant Mutual ExclusionAlgorithm for MANETs, Proc. of the 3rd International Conference on Mobile Ad-hoc and Sensor Networks (MSN’07), Beijing, China,12-14 December 2007.10.Weigang Wu, Jiannong Cao, Michel Raynal, The Eventual Clusterer Oracle and Its Application toConsensus in MANETs, Proc. of the 26th IEEE International Symposium on Reliable Distributed Systems (SRDS’07), Beijing China, Oct. 10-12, 2007.11.Jiannong Cao, Miaomiao Wang, Weigang Wu, Xianbing Wang, Stephen C.F. Chan, A GenericDistributed Monitor Construct for Programming Process Synchronization in Distributed Systems, Proc. of the5th International Symposium on Parallel and Distributed Processing and Applications (ISPA’07), Niagara Falls, Canada, Aug. 29-31, 200712.Jin Yang, Jiannong Cao, Weigang Wu, An Integrated Approach to Checkpointing in Mobile AgentSystems, Proc. of the 2nd International Conference on Semantics, Knowledge and Grid (SKG’06), Guilin, China, Nov. 1-3, 200613.Jin Yang, Jiannong Cao, Weigang Wu, Checkpoint Placement Algorithms for Mobile Agent System,Proc. of the5th International Conference on Grid and Cooperative Computing (GCC’06), Changsha, China, Oct. 21-23, 2006.14.Jiannong Cao, Michel Raynal, Xianbing Wang, Weigang Wu,The Power and Limit of AddingSynchronization Messages for Synchronous Agreement, Proc. of the 35th International Conference on Parallel Processing (ICPP’06), Columbus, USA, Aug. 14-18, 2006.15.Jin Yang, Jiannong Cao, Weigang Wu, Corentin Travers The Notification based Approach forImplementation Failure Detector, Proc. of the1st International Conference on Scalable Information System (InfoScale’06) , Hong Kong, May 29-Jun. 1, 2006.16.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, A Hierarchical Consensus Protocol forMobile Ad Hoc Networks, Proc. of the14th Euromicro Conference on Parallel, Distributed and Network based Processing (PDP’06), Montbéliard, France, Feb. 15~17, 2006.17.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, A Framework for Transactional MobileAgent Execution, Proc. of the4th International Conference on Grid and Cooperative Computing (GCC’05), Beijing, China, Nov. 30-Dec. 3, 2005.18.Jiannong Cao, Jin Yang, Weigang Wu, Chengzhong Xu, Exception Handling in DistributedWorkflow Systems Using Mobile Agents, Proc. of the IEEE International Conference on E-Business Engineering (ICEBE’05), Beijing, China, Oct. 18-20, 2005.19.Weigang Wu, Jiannong Cao, Jin Yang, A Scalable Mutual Exclusion Algorithm for Mobile Ad HocNetworks, Proc. of the14th International Conference on Computer Communications and Networks (ICCCN’05), San Diego, USA, Oct. 17-19, 2005.20.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, Parallel Algorithms for Fault-TolerantMobile Agent Execution, Proc. of the6th International Conference on Algorithms and Architectures(ICA3PP’05), Melbourne, Australia, Oct. 2-5, 2005.。
IOTDB

IOTDBIntroductionIOTDB, which stands for Internet of Things Database, is a time-series database specifically designed for storing and managing data generated by IoT devices. It provides a scalable and efficient solution for processing massive amounts of streaming data in real time.The rapid growth of IoT devices has created a need for a database that can handle the high volume and velocity of data generated by these devices. IOTDB aims to meet this need by providing a database system that combines the benefits of both time-series databases and IoT data management.FeaturesTime-Series DatabaseIOTDB is designed as a time-series database, which means it is optimized for storing and analyzing time-stamped data. Time-stamped data is common in IoT applications, where sensors and devices continuously generate data streams with time information. With its time-series database engine, IOTDB can efficiently handle the storage and retrieval of time-stamped data.Flexible Data ModelIOTDB provides a flexible data model that allows users to define their own schema for storing IoT data. This flexibility allows for the dynamic and heterogeneous nature of IoT data. The schema can be easily modified to accommodate new types of data or changes in the data structure.High PerformanceIOTDB is designed for high-performance data processing. It is built with a highly optimized storage engine and query processing engine that ensures fast data ingestion and retrieval. The database can handle large-scale data streams with low latency and high throughput.Distributed ArchitectureIOTDB supports a distributed architecture that allows for horizontal scalability and fault tolerance. By distributing data across multiple nodes, IOTDB can handle large volumes of data and provide high availability. The distributed architecture also enables seamless integration with other big data platforms, such as Hadoop and Spark, for further data processing and analysis.Advanced AnalyticsIOTDB provides various advanced analytics capabilities to derive insights from IoT data. It supports complex queries, such as aggregation, filtering, and window-based operations, to enable real-time analytics on streaming data. IOTDB alsointegrates with popular analytics tools, such as Apache Flink and Apache Kafka, to further enhance data analysis capabilities.Use CasesIndustrial Internet of Things (IIoT)IOTDB finds extensive applications in the Industrial Internet of Things (IIoT) domain. In IIoT, sensors and devices are deployed in industrial settings to monitor and control various processes. With IOTDB, organizations can efficiently store and analyze the massive amounts of time-stamped data generated by these sensors and devices. This enables real-time monitoring, predictive maintenance, and process optimization, leading to improved operational efficiency and reduced downtime.Smart Home AutomationIOTDB is also well-suited for smart home automation applications. In a smart home environment, numerous IoT devices, such as smart thermostats, lighting controls, and security cameras, generate data streams that need to be processed and analyzed. IOTDB enables homeowners to store and manage this data effectively, allowing for intelligent home automation, energy management, and security surveillance.Healthcare MonitoringWith the proliferation of wearable devices and healthcare sensors, there is a growing need to store and analyze healthcare data generated by patients. IOTDB provides a reliable and scalable solution for healthcare monitoringapplications. It allows healthcare providers to collect and analyze patient data in real time, enabling personalized healthcare, remote patient monitoring, and early warning systems.ConclusionIOTDB is a powerful time-series database specifically designed for handling IoT data. With its flexible data model, high performance, and advanced analytics capabilities, IOTDB enables efficient storage, retrieval, and analysis of massive amounts of streaming data. It finds applications in various domains, including industrial IoT, smart home automation, and healthcare monitoring. As IoT continues to grow and evolve, IOTDB provides a reliable and scalable foundation for managing and deriving insights from IoT data.。
Software-DefinedNetworking

Software⁃Defined Networking▶Zhili SunProfessor Zhili Sun is chair of communication networking at the Centre for Communication Systems Research,University of Sur⁃rey,UK.He received his BSc in mathematics from Nanjing Uni⁃versity,China,in 1982.He received his PhD in computer science from Lancaster University,UK,in 1991.From 1989to 1993,he worked as a postdoctoral research fellow at Queen Mary Universi⁃ty,London.He has worked in the capacity of principle investiga⁃tor and technical co ⁃coordinator on many projects within EU framework programs,within the EPSRC,and within industry.He has published more than 125papers in international journals andconference proceedings and has also authored book chapters.He was the sole author of Satellite Networking:Principles and Protocols,1st and 2nd editions,published by Wiley in 2005and 2014respectively.He was a contributing editor of IP Networking Over Next ⁃Generation Satellite Systems,published by Springer in 2008.He was also contributing editor of the textbook Satellite Communications Systems:Systems,Techniques and Technology,5th ed.,published by Wiley in 2009.His research interests include wire⁃less and sensor networks,satellite communications,mobile operating systems,Internet protocols and architecture,clod computing,SDN,multicast,and security.SSoftware⁃Defined Networking Zhili Sun,Jiandong Li,and Kun YangJune 2014Vol.12No.2ZTE COMMUNICATIONS 01oftware ⁃defined networking (SDN)is a promising technology for next ⁃generation networking and has attracted much attention from academics,network equipment manufacturer,network operators,andservice providers.It has found applications in mobile,data center,and enterprise networks.The SDN architecture has a centralized,programmable control plane that is separate from the data plane.SDN also provides the ability to control and manage virtualized resources and networks without requiring new hardware technologies.This is a major shift in networking technologies.The ITU ⁃T has been engaged in SDN standardization,and the European Telecommunications Standard Institute (ETSI)has been working on network function virtualization (NFV),which complements SDN.The Open Network Foundation (ONF)is a non⁃profit organization dedicated to promoting the adoption of open SDN.Recently,much work has been done on SDN to meet future network requirements.Network virtualization creates multiple virtual infrastruc⁃tures within a deployed infrastructure.These virtualized infra⁃structures can be created over a single physical infrastructure.Each virtual network can be isolated from each other and pro⁃grammed to meet user requirements in terms of resource func⁃tionality and capacity.This ensures that appropriate network resources are provided to the user.The SDN framework includes programmable control plane,data⁃forwarding plane abstraction,and methods to map the vir⁃tualized infrastructures onto the underlying physical network infrastructure.Key issues to be addressed are network resource isolation,network abstraction,topology awareness,quick reconfigurabili⁃ty,performance,programmability,management,mobility,secu⁃rity,and wireless network access.We received strong response to this call for papers on SDN from network operators,equipment manufacturers,universi⁃ties,and research institutes.Following a peer⁃review process,we selected nine papers for inclusion in this special issue.The first paper,“Network Function Virtualization Technolo⁃gy:Progess and Standardization ”discusses the main challeng⁃es in SDN faced by network carriers.This paper also discusses current standardization activities and research on NFV related to SDN.The second paper,“Service Parameter Exposure and Dy⁃namic Service Negotiation in SDN Environments,”discusses the ability of SDN to facilitate dynamic provisioning of network services.The paper focuses on two main aspects of the SDN framework:network abstraction and dynamic parameter expo⁃sure and negotiation.The third paper,“SDN⁃Based Broadband Network for Cloud Services,”discusses how SDN/NFV will be vital for construct⁃ing cloud⁃oriented broadband infrastructure,especially within data center networks and for interconnecting between data cen⁃▶Jiandong LiProfessor Jiandong Li received his BS,MS and PhD degrees from Xidian University,China,in 1982,1985and 1991.From 1990to 1994,he was an associate professor at Xidian University and be⁃came a full professor in 1994.In 1995,he undertook the role of PhD supervisor at Xidian University.From 2007to 2012,he was executive vice dean of the Graduate School of Xidian University.From 1997to 2006,he was dean of School of Telecommunica⁃tions Engineering,Xidian University.From 2001to 2003,he was a visiting professor at Cornell University.Professor Li has previ⁃ously been awarded the National Science Fund Award for Distin⁃guished Young Scholars.He is a senior member of the IEEE,a senior member of the China Institute of Electronics (CIE),and a fellow of the China Institute of Communica⁃tions (CIC).From 1993to 1994and then from 1999to 2000,he was a member of the Personal Communications Networks Specialist Group for China “863”Communication High Technology Program.He is also a member of the Broadband Wireless Mobile Com⁃munication Specialist Group,Ministry of Information Industry,China,and director of the Broadband Wireless IP Standard Work Group,Ministry of Information Industry,Chi⁃na.His main research interests include broadband wireless mobile communications,cognitive and software⁃defined radio,and wireless ad⁃hoc networks.▶Kun YangProfessor Kun Yang received his PhD degree from University Col⁃lege London.He received his MSc and BSc degrees from Jilin University,China.He is currently a chair professor in the School of Computer Science and Electronic Engineering,University of Essex,and leads the Network Convergence Laboratory there.Be⁃fore joining the University of Essex in 2003,he worked for sever⁃al years at University College London on EU research projects.His main research interests include heterogeneous wireless net⁃works,fixed⁃mobile convergence,future Internet technology and network virtualization,and cloud computing and networking.Hemanages research projects funded by sources such as UK EPSRC,EU FP7,and indus⁃try.He has published more than 150journal papers.He serves on the editorial boards of both IEEE and non⁃IEEE journals.He is a senior member of the IEEE and a fellow of IET.June 2014Vol.12No.2ZTE COMMUNICATIONS02Software⁃Defined NetworkingZhili Sun,Jiandong Li,and Kun Yangter networks.The authors propose SDN/NFV in broadband ac⁃cess to realize a virtualized residential gateway.The fourth paper,“D ⁃ZENIC:A Scalable Distributed SDN Controller Architecture,”describes a solution to minimizing the cost of network state distribution.This solution is a net⁃work control platform called D⁃ZNEIC that supports distribut⁃ed deployment and linear scale ⁃out by trading off complexity for scalabilityThe fifth paper,“Software⁃Defined Cellular Mobile Network Solutions,”describes current research on and solutions for soft⁃ware⁃defined cellular networks.It also discusses related speci⁃fications and possible research directions.The sixth paper,“SDN ⁃Based Data Offloading for 5G Mo⁃evolved with SDN abstraction in the mobile backhaul and en⁃hanced components that facilitate the move towards 5G.The seventh paper,“Integrating IPsec Within OpenFlow Ar⁃chitecture for Secure Group Communication,”discusses Inter⁃net Protocol security (IPsec)in the context of OpenFlow archi⁃tecture and SDN.The eighth paper,“Virtualized Wireless SDNs:Modelling Delay Through the Use of Stochastic Network Calculus,”de⁃scribes a delay model for a software ⁃defined wireless virtual network with some theoretical investigation into wireless SDN.The final paper,“Load Balancing Fat⁃Tree on Long⁃Lived Flows:Avoiding Congestions in Data Center Network,”de⁃scribes a dynamic load⁃balancing algorithm for fat tree in the。
2014-ICDE论文集总结

2014-ICDE论文集ICDE RESEARCH SESSIONSResearch Papers Session 1 Clustering●Incremental Cluster Evolution Tracking from Highly DynamicNetwork Data(s hxy)o Pei Lee* (UBC)o Laks V.S. Lakshmanan (UBC)o Evangelos Milios (Dalhousie University)摘要:Dynamic networks are commonly found in the current web age. In scenarios like social networks and social media,dynamic networks are noisy, are of large-scale and evolve quickly.In this paper, we focus on the cluster evolution tracking problemon highly dynamic networks, with clearapplication to eventevolution tracking. There are several previous works on datastream clustering using a node-by-node approach formaintainingclusters. However, handling of bulk updates, i.e., a subgraphat a time, is critical for achieving acceptable performance oververy large highly dynamic networks. We propose a subgraph-by subgraph incrementaltracking framework for cluster evolutionin this paper. To effectively illustrate the techniques in ourframework, we take the event evolution tracking task in socialstreams as an application, where a social stream and an eventare modeled as a dynamic post network and a dynamic clusterrespectively. By monitoring through a fading time window, weintroduce a skeletal graph to summarize the information in thedynamic network, and formalize cluster evolution patterns usinga group of primitive evolution operations and their algebra. Twoincremental computation algorithms are developed tomaintainclusters and track evolution patterns as time rolls on andthenetwork evolves. Our detailed experimental evaluation on largeTwitter datasets demonstrates that our framework can effectivelytrack the complete set of cluster evolution patterns in the wholelife cycle from highly dynamic networks on the fly.大意:动态网络(如社交网络)在网络时代非常常见。
一种改进的动态反馈负载均衡算法

一种改进的动态反馈负载均衡算法陈泰安【摘要】In the cluster system, the load balancing algorithm is one of the key factors that affect system performance. In order to further improve the performance of the cluster system, it is necessary to optimize the load balancing algorithm. In this paper, we proposed an improved load balancing algorithm based on dynamic feed-back after having a detailed analysis of the minimum connection algorithm and the DFB (Dynamic Feed-Back)algorithm. Through the collection of real-time performance parameters for each server, the algorithm dynamically calculate the probability of the distribution of the service node, and thus determine which service node should the user request be assigned to. Through the test of the three algorithm, we come to the conclusion that the algorithm can effectively improve the performance of the cluster system.%在集群系统中,负载均衡算法是影响系统性能的关键因素之一.为了进一步提高集群系统的性能,有必要对负载均衡算法进行优化.通过对最小连接算法和DFB(Dynamic Feed-Back)算法的详细分析,提出了一种改进的动态反馈负载均衡算法.该算法通过收集每台服务器的实时性能参数,动态地计算出各服务节点的分配概率,并由此决定用户请求分配给哪一个服务节点.通过对上述三种算法性能的测试,得出了该算法能够有效提高集群系统性能的结论.【期刊名称】《电子设计工程》【年(卷),期】2013(021)005【总页数】3页(P171-172,179)【关键词】分布式处理系统;负载均衡;动态反馈;集群;算法【作者】陈泰安【作者单位】武汉科技大学信息科学与工程学院,湖北武汉430081【正文语种】中文【中图分类】TP301.6随着网络需求的不断增加,集群服务器技术将以其高可靠、高性能的优势逐步取代以前单一服务器的工作模式,它提供了一个负载性能易于扩展的、高效可靠地服务器性能解决方案。
minio cors策略

minio cors策略MinIO is an open-source object storage service that allows users to store massive amounts of data in a scalable, distributed environment. One of the key features of MinIO is its support for Cross-Origin Resource Sharing (CORS) policies, which allow users to define who can access their data from different origins.MinIO's CORS policies help users control access to their data by specifying which domains are allowed to make cross-origin requests to the MinIO server. This is an important security feature that helps prevent unauthorized access to data and ensures that only trusted domains can interact with the MinIO server.Setting up CORS policies in MinIO is a simple process that can be done through the MinIO client or by directly editing the configuration file. Users can specify the allowed origins, methods, headers, and expose headers to define the behavior of their MinIO server when handling cross-origin requests. By carefully configuring these settings, users can ensure that their data remains secure while still allowing legitimate access from trusted sources.From a practical perspective, CORS policies in MinIO are essential for developers who need to build applications that access data stored in MinIO from different domains. By allowing specific domains to access the MinIO server, developers can create dynamic and interactive web applications that make use of the data stored in MinIO without compromising security.Additionally, CORS policies in MinIO can help organizations comply with regulatory requirements by ensuring that sensitive data is only accessed from approved sources. By defining strict CORS policies, organizations can prevent data breaches and maintain the integrity of their data, ultimately building trust among customers and stakeholders.Furthermore, the flexibility of MinIO's CORS policies allows users to customize their settings to meet specific use cases and requirements. Whether users want to enable CORS for a single domain or for multiple domains, MinIO provides the tools to create a tailored solution that fits their needs.In conclusion, setting up CORS policies in MinIO is a crucial step in ensuring the security and integrity of data stored in a MinIO server. By carefully configuring these policies, users can control access to their data, facilitate the development of web applications, comply with regulations, and customize settings to meet specific requirements. MinIO's support for CORS policies demonstrates its commitment to providing a secure and flexible object storage solution for users worldwide.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Pedro V. Sander
Harvard University 33 Oxford Street Cambridge, MA, USA
Denis Peleshchuk
Harvard University 33 Oxford Street Cambridge, MA, USA
Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. AAMAS’02, July 15-19, 2002, Bologna, Italy. Copyright 2002 ACM 1-58113-480-0/02/0007…$5.00.
Categories and Subject Descriptors
I.2.11 [Distributed Artificial Intelligence ]: Multiagent systems.
General Terms
Algorithms, Experimentation.
1. INTRODUCTION
Assigning agents to tasks in a non-centralized environment is a fundamental problem in multi-agent systems (MAS). The problem becomes even more challenging in settings in which a very large number of agents and tasks are spread in space, making communication among agents difficult or costly. We propose an algorithm for task allocation based on computational geometry techniques. The approach is applicable to domains in which agents’ and tasks’ geographical positions are known. In our experiments, the tasks are stationary, but agents are allowed to move. Agents are aware of other agents and tasks only within a proximity radius, which we refer to as the agent’s circle of visibility. The objective is to maximize the number of fulfilled
Barbara J. Grosz
Harvard University 33 Oxford Street Cambridge, MA, USA
pvs@ ABSTRACT
dpeleshc@
grosห้องสมุดไป่ตู้@
We present a distributed algorithm for task allocation in multiagent systems for settings in which agents and tasks are geographically dispersed in two-dimensional space. We describe a method that enables agents to determine individually how to move so that they are, as a group, efficiently assigned to tasks. The method comprises two algorithms and is especially useful in environments with very large numbers of agent and task nodes. One algorithm adapts computational geometry techniques to determine adjacency information for the agent nodes given the geographical positions of agents and tasks. This adjacency information is used to determine the visible nodes that are most relevant to an agent's decision making process and to eliminate those that it should not consider. The second algorithm uses local heuristics based solely on an agent's adjacent nodes to determine its course of action. This method yields improved task allocations compared to previous algorithms proposed for similar environments. We also present a modification to the second algorithm that improves performance in environments in which multiple agents are required to complete a single task.
a) Agents (gray), tasks (black)
b) Delaunay triangulation
Figure 1: Agents and tasks as vertices on the 2D plane with the Delaunay triangulation shown on the right. tasks. We do not consider other costs associated with the agents, such as distance traveled or awake time. This algorithm is useful in numerous domains, including the package delivery system of Shehory et al. [1998]; a taxi company, where the drivers are the agents and the passengers are the tasks; and the allocation of police forces with no central control. In this last case, it is critical to have a good distribution of agents (policemen) because a new task (a crime) can appear anywhere. The algorithm is fully distributed. Each agent determines its course of action with the objective of maximizing its own number of fulfilled tasks. To reduce communication costs, each agent bases its decision solely on a small set of adjacent task and agent nodes. The expected number of adjacent nodes remains low even if the density of agents and tasks is very high. Furthermore, the adjacent nodes are evenly distributed in all directions. For i nstance, it is undesirable to have all adjacent nodes of an agent be in the east direction, as that could lead to missing an opportunity to reach a nearby task to the west. Picking the n closest nodes could cause an imbalance. The algorithm computes a planar triangulation of the nodes at each time-step (Figure 1) and determine the adjacency of the nodes based on a subset of the edges of the triangulation. Section 2 presents an algorithm to efficiently compute a local set of neighbors adhering to the properties outlined above. This set provides each agent with a small set of desirable neighbors on which to base its decisions. Section 3 presents an algorithm for an agent to make decisions based solely on its adjacent nodes, rather than on all the nodes within its circle of visibility. This property of the algorithm minimizes the amount of communication and computation r equired by the agents. The adjacent nodes also provide enough information to allow the agents to spread themselves out evenly in space. Since all computations are done locally by individual agents, the algorithm scales very well.
