UbiRoad--- Semantic Middleware for Cooperative Traffic Systems and Services
随机分形搜索算法

随机分形搜索算法葛钱星;马良;刘勇【摘要】现有的元启发式算法大多是模仿生物的群体运动来解决优化问题.为了进一步给优化算法的设计提供新的思路,受自然生长现象的启发,提出了一种新型的元启发式算法—随机分形搜索算法.该算法利用分形的扩散特性进行寻优,其优化原理完全不同于现有的元启发式算法.其中,算法的扩散过程采用高斯随机游走方式来开发问题的搜索空间,而更新过程则分别对个体的分量及个体本身采用相应的更新策略来进行更新,以此进行全局搜索和局部搜索,从而形成了一个完整的优化系统.通过对一系列典型的测试函数优化问题的求解实验并与其他算法进行比较,结果表明随机分形搜索算法不仅具有较高的计算精度,而且具有较快的收敛速度.【期刊名称】《计算机技术与发展》【年(卷),期】2019(029)004【总页数】6页(P1-6)【关键词】随机分形;随机分形搜索算法;扩散;更新;最优化【作者】葛钱星;马良;刘勇【作者单位】上海理工大学,上海 200093;上海理工大学,上海 200093;上海理工大学,上海 200093【正文语种】中文【中图分类】TP301.60 引言近年来,元启发式算法取得了巨大的发展,出现了许多有代表性的方法。
例如,遗传算法(genetic algorithm,GA)是基于生物进化论中“自然选择、适者生存”规律而提出的优化方法;粒子群优化算法(particle swarm optimization,PSO)是基于鸟群觅食行为规律而提出的群体智能优化方法[1];人工蜂群算法(artificial bee colony,ABC)是基于蜜蜂群觅食行为特性而提出的优化方法[2];蚁群算法(ant colony,AC)是基于蚁群在觅食过程中的行为特性而提出的仿生类算法[3];引力搜索算法(gravitational search,GSA)是基于万有引力定律而提出的智能优化算法[4-5];布谷鸟搜索算法(cuckoo search,CS)是基于布谷鸟的寄生育雏的行为特性而提出的元启发式算法[6-7]。
人工智能领域中英文专有名词汇总
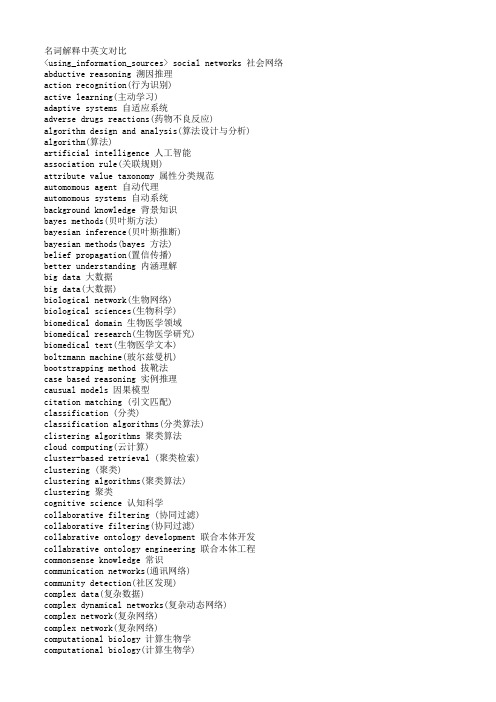
名词解释中英文对比<using_information_sources> social networks 社会网络abductive reasoning 溯因推理action recognition(行为识别)active learning(主动学习)adaptive systems 自适应系统adverse drugs reactions(药物不良反应)algorithm design and analysis(算法设计与分析) algorithm(算法)artificial intelligence 人工智能association rule(关联规则)attribute value taxonomy 属性分类规范automomous agent 自动代理automomous systems 自动系统background knowledge 背景知识bayes methods(贝叶斯方法)bayesian inference(贝叶斯推断)bayesian methods(bayes 方法)belief propagation(置信传播)better understanding 内涵理解big data 大数据big data(大数据)biological network(生物网络)biological sciences(生物科学)biomedical domain 生物医学领域biomedical research(生物医学研究)biomedical text(生物医学文本)boltzmann machine(玻尔兹曼机)bootstrapping method 拔靴法case based reasoning 实例推理causual models 因果模型citation matching (引文匹配)classification (分类)classification algorithms(分类算法)clistering algorithms 聚类算法cloud computing(云计算)cluster-based retrieval (聚类检索)clustering (聚类)clustering algorithms(聚类算法)clustering 聚类cognitive science 认知科学collaborative filtering (协同过滤)collaborative filtering(协同过滤)collabrative ontology development 联合本体开发collabrative ontology engineering 联合本体工程commonsense knowledge 常识communication networks(通讯网络)community detection(社区发现)complex data(复杂数据)complex dynamical networks(复杂动态网络)complex network(复杂网络)complex network(复杂网络)computational biology 计算生物学computational biology(计算生物学)computational complexity(计算复杂性) computational intelligence 智能计算computational modeling(计算模型)computer animation(计算机动画)computer networks(计算机网络)computer science 计算机科学concept clustering 概念聚类concept formation 概念形成concept learning 概念学习concept map 概念图concept model 概念模型concept modelling 概念模型conceptual model 概念模型conditional random field(条件随机场模型) conjunctive quries 合取查询constrained least squares (约束最小二乘) convex programming(凸规划)convolutional neural networks(卷积神经网络) customer relationship management(客户关系管理) data analysis(数据分析)data analysis(数据分析)data center(数据中心)data clustering (数据聚类)data compression(数据压缩)data envelopment analysis (数据包络分析)data fusion 数据融合data generation(数据生成)data handling(数据处理)data hierarchy (数据层次)data integration(数据整合)data integrity 数据完整性data intensive computing(数据密集型计算)data management 数据管理data management(数据管理)data management(数据管理)data miningdata mining 数据挖掘data model 数据模型data models(数据模型)data partitioning 数据划分data point(数据点)data privacy(数据隐私)data security(数据安全)data stream(数据流)data streams(数据流)data structure( 数据结构)data structure(数据结构)data visualisation(数据可视化)data visualization 数据可视化data visualization(数据可视化)data warehouse(数据仓库)data warehouses(数据仓库)data warehousing(数据仓库)database management systems(数据库管理系统)database management(数据库管理)date interlinking 日期互联date linking 日期链接Decision analysis(决策分析)decision maker 决策者decision making (决策)decision models 决策模型decision models 决策模型decision rule 决策规则decision support system 决策支持系统decision support systems (决策支持系统) decision tree(决策树)decission tree 决策树deep belief network(深度信念网络)deep learning(深度学习)defult reasoning 默认推理density estimation(密度估计)design methodology 设计方法论dimension reduction(降维) dimensionality reduction(降维)directed graph(有向图)disaster management 灾害管理disastrous event(灾难性事件)discovery(知识发现)dissimilarity (相异性)distributed databases 分布式数据库distributed databases(分布式数据库) distributed query 分布式查询document clustering (文档聚类)domain experts 领域专家domain knowledge 领域知识domain specific language 领域专用语言dynamic databases(动态数据库)dynamic logic 动态逻辑dynamic network(动态网络)dynamic system(动态系统)earth mover's distance(EMD 距离) education 教育efficient algorithm(有效算法)electric commerce 电子商务electronic health records(电子健康档案) entity disambiguation 实体消歧entity recognition 实体识别entity recognition(实体识别)entity resolution 实体解析event detection 事件检测event detection(事件检测)event extraction 事件抽取event identificaton 事件识别exhaustive indexing 完整索引expert system 专家系统expert systems(专家系统)explanation based learning 解释学习factor graph(因子图)feature extraction 特征提取feature extraction(特征提取)feature extraction(特征提取)feature selection (特征选择)feature selection 特征选择feature selection(特征选择)feature space 特征空间first order logic 一阶逻辑formal logic 形式逻辑formal meaning prepresentation 形式意义表示formal semantics 形式语义formal specification 形式描述frame based system 框为本的系统frequent itemsets(频繁项目集)frequent pattern(频繁模式)fuzzy clustering (模糊聚类)fuzzy clustering (模糊聚类)fuzzy clustering (模糊聚类)fuzzy data mining(模糊数据挖掘)fuzzy logic 模糊逻辑fuzzy set theory(模糊集合论)fuzzy set(模糊集)fuzzy sets 模糊集合fuzzy systems 模糊系统gaussian processes(高斯过程)gene expression data 基因表达数据gene expression(基因表达)generative model(生成模型)generative model(生成模型)genetic algorithm 遗传算法genome wide association study(全基因组关联分析) graph classification(图分类)graph classification(图分类)graph clustering(图聚类)graph data(图数据)graph data(图形数据)graph database 图数据库graph database(图数据库)graph mining(图挖掘)graph mining(图挖掘)graph partitioning 图划分graph query 图查询graph structure(图结构)graph theory(图论)graph theory(图论)graph theory(图论)graph theroy 图论graph visualization(图形可视化)graphical user interface 图形用户界面graphical user interfaces(图形用户界面)health care 卫生保健health care(卫生保健)heterogeneous data source 异构数据源heterogeneous data(异构数据)heterogeneous database 异构数据库heterogeneous information network(异构信息网络) heterogeneous network(异构网络)heterogenous ontology 异构本体heuristic rule 启发式规则hidden markov model(隐马尔可夫模型)hidden markov model(隐马尔可夫模型)hidden markov models(隐马尔可夫模型) hierarchical clustering (层次聚类) homogeneous network(同构网络)human centered computing 人机交互技术human computer interaction 人机交互human interaction 人机交互human robot interaction 人机交互image classification(图像分类)image clustering (图像聚类)image mining( 图像挖掘)image reconstruction(图像重建)image retrieval (图像检索)image segmentation(图像分割)inconsistent ontology 本体不一致incremental learning(增量学习)inductive learning (归纳学习)inference mechanisms 推理机制inference mechanisms(推理机制)inference rule 推理规则information cascades(信息追随)information diffusion(信息扩散)information extraction 信息提取information filtering(信息过滤)information filtering(信息过滤)information integration(信息集成)information network analysis(信息网络分析) information network mining(信息网络挖掘) information network(信息网络)information processing 信息处理information processing 信息处理information resource management (信息资源管理) information retrieval models(信息检索模型) information retrieval 信息检索information retrieval(信息检索)information retrieval(信息检索)information science 情报科学information sources 信息源information system( 信息系统)information system(信息系统)information technology(信息技术)information visualization(信息可视化)instance matching 实例匹配intelligent assistant 智能辅助intelligent systems 智能系统interaction network(交互网络)interactive visualization(交互式可视化)kernel function(核函数)kernel operator (核算子)keyword search(关键字检索)knowledege reuse 知识再利用knowledgeknowledgeknowledge acquisitionknowledge base 知识库knowledge based system 知识系统knowledge building 知识建构knowledge capture 知识获取knowledge construction 知识建构knowledge discovery(知识发现)knowledge extraction 知识提取knowledge fusion 知识融合knowledge integrationknowledge management systems 知识管理系统knowledge management 知识管理knowledge management(知识管理)knowledge model 知识模型knowledge reasoningknowledge representationknowledge representation(知识表达) knowledge sharing 知识共享knowledge storageknowledge technology 知识技术knowledge verification 知识验证language model(语言模型)language modeling approach(语言模型方法) large graph(大图)large graph(大图)learning(无监督学习)life science 生命科学linear programming(线性规划)link analysis (链接分析)link prediction(链接预测)link prediction(链接预测)link prediction(链接预测)linked data(关联数据)location based service(基于位置的服务) loclation based services(基于位置的服务) logic programming 逻辑编程logical implication 逻辑蕴涵logistic regression(logistic 回归)machine learning 机器学习machine translation(机器翻译)management system(管理系统)management( 知识管理)manifold learning(流形学习)markov chains 马尔可夫链markov processes(马尔可夫过程)matching function 匹配函数matrix decomposition(矩阵分解)matrix decomposition(矩阵分解)maximum likelihood estimation(最大似然估计)medical research(医学研究)mixture of gaussians(混合高斯模型)mobile computing(移动计算)multi agnet systems 多智能体系统multiagent systems 多智能体系统multimedia 多媒体natural language processing 自然语言处理natural language processing(自然语言处理) nearest neighbor (近邻)network analysis( 网络分析)network analysis(网络分析)network analysis(网络分析)network formation(组网)network structure(网络结构)network theory(网络理论)network topology(网络拓扑)network visualization(网络可视化)neural network(神经网络)neural networks (神经网络)neural networks(神经网络)nonlinear dynamics(非线性动力学)nonmonotonic reasoning 非单调推理nonnegative matrix factorization (非负矩阵分解) nonnegative matrix factorization(非负矩阵分解) object detection(目标检测)object oriented 面向对象object recognition(目标识别)object recognition(目标识别)online community(网络社区)online social network(在线社交网络)online social networks(在线社交网络)ontology alignment 本体映射ontology development 本体开发ontology engineering 本体工程ontology evolution 本体演化ontology extraction 本体抽取ontology interoperablity 互用性本体ontology language 本体语言ontology mapping 本体映射ontology matching 本体匹配ontology versioning 本体版本ontology 本体论open government data 政府公开数据opinion analysis(舆情分析)opinion mining(意见挖掘)opinion mining(意见挖掘)outlier detection(孤立点检测)parallel processing(并行处理)patient care(病人医疗护理)pattern classification(模式分类)pattern matching(模式匹配)pattern mining(模式挖掘)pattern recognition 模式识别pattern recognition(模式识别)pattern recognition(模式识别)personal data(个人数据)prediction algorithms(预测算法)predictive model 预测模型predictive models(预测模型)privacy preservation(隐私保护)probabilistic logic(概率逻辑)probabilistic logic(概率逻辑)probabilistic model(概率模型)probabilistic model(概率模型)probability distribution(概率分布)probability distribution(概率分布)project management(项目管理)pruning technique(修剪技术)quality management 质量管理query expansion(查询扩展)query language 查询语言query language(查询语言)query processing(查询处理)query rewrite 查询重写question answering system 问答系统random forest(随机森林)random graph(随机图)random processes(随机过程)random walk(随机游走)range query(范围查询)RDF database 资源描述框架数据库RDF query 资源描述框架查询RDF repository 资源描述框架存储库RDF storge 资源描述框架存储real time(实时)recommender system(推荐系统)recommender system(推荐系统)recommender systems 推荐系统recommender systems(推荐系统)record linkage 记录链接recurrent neural network(递归神经网络) regression(回归)reinforcement learning 强化学习reinforcement learning(强化学习)relation extraction 关系抽取relational database 关系数据库relational learning 关系学习relevance feedback (相关反馈)resource description framework 资源描述框架restricted boltzmann machines(受限玻尔兹曼机) retrieval models(检索模型)rough set theroy 粗糙集理论rough set 粗糙集rule based system 基于规则系统rule based 基于规则rule induction (规则归纳)rule learning (规则学习)rule learning 规则学习schema mapping 模式映射schema matching 模式匹配scientific domain 科学域search problems(搜索问题)semantic (web) technology 语义技术semantic analysis 语义分析semantic annotation 语义标注semantic computing 语义计算semantic integration 语义集成semantic interpretation 语义解释semantic model 语义模型semantic network 语义网络semantic relatedness 语义相关性semantic relation learning 语义关系学习semantic search 语义检索semantic similarity 语义相似度semantic similarity(语义相似度)semantic web rule language 语义网规则语言semantic web 语义网semantic web(语义网)semantic workflow 语义工作流semi supervised learning(半监督学习)sensor data(传感器数据)sensor networks(传感器网络)sentiment analysis(情感分析)sentiment analysis(情感分析)sequential pattern(序列模式)service oriented architecture 面向服务的体系结构shortest path(最短路径)similar kernel function(相似核函数)similarity measure(相似性度量)similarity relationship (相似关系)similarity search(相似搜索)similarity(相似性)situation aware 情境感知social behavior(社交行为)social influence(社会影响)social interaction(社交互动)social interaction(社交互动)social learning(社会学习)social life networks(社交生活网络)social machine 社交机器social media(社交媒体)social media(社交媒体)social media(社交媒体)social network analysis 社会网络分析social network analysis(社交网络分析)social network(社交网络)social network(社交网络)social science(社会科学)social tagging system(社交标签系统)social tagging(社交标签)social web(社交网页)sparse coding(稀疏编码)sparse matrices(稀疏矩阵)sparse representation(稀疏表示)spatial database(空间数据库)spatial reasoning 空间推理statistical analysis(统计分析)statistical model 统计模型string matching(串匹配)structural risk minimization (结构风险最小化) structured data 结构化数据subgraph matching 子图匹配subspace clustering(子空间聚类)supervised learning( 有support vector machine 支持向量机support vector machines(支持向量机)system dynamics(系统动力学)tag recommendation(标签推荐)taxonmy induction 感应规范temporal logic 时态逻辑temporal reasoning 时序推理text analysis(文本分析)text anaylsis 文本分析text classification (文本分类)text data(文本数据)text mining technique(文本挖掘技术)text mining 文本挖掘text mining(文本挖掘)text summarization(文本摘要)thesaurus alignment 同义对齐time frequency analysis(时频分析)time series analysis( 时time series data(时间序列数据)time series data(时间序列数据)time series(时间序列)topic model(主题模型)topic modeling(主题模型)transfer learning 迁移学习triple store 三元组存储uncertainty reasoning 不精确推理undirected graph(无向图)unified modeling language 统一建模语言unsupervisedupper bound(上界)user behavior(用户行为)user generated content(用户生成内容)utility mining(效用挖掘)visual analytics(可视化分析)visual content(视觉内容)visual representation(视觉表征)visualisation(可视化)visualization technique(可视化技术) visualization tool(可视化工具)web 2.0(网络2.0)web forum(web 论坛)web mining(网络挖掘)web of data 数据网web ontology lanuage 网络本体语言web pages(web 页面)web resource 网络资源web science 万维科学web search (网络检索)web usage mining(web 使用挖掘)wireless networks 无线网络world knowledge 世界知识world wide web 万维网world wide web(万维网)xml database 可扩展标志语言数据库附录 2 Data Mining 知识图谱(共包含二级节点15 个,三级节点93 个)间序列分析)监督学习)领域 二级分类 三级分类。
基于三角模糊数的车联网簇头节点选择方法

基于三角模糊数的车联网簇头节点选择方法
刘蕴 1,3 曹军芳 2 王凤琦 3
(1.周口职业技术学院,周口 466000;2.许昌职业技术学院,许昌 461000;3.长安大学,西安 710064)
【摘要】针对现有车联网簇头节点选择方法不足的问题,提出了一种基于三角模糊数的车联网簇头节点选择方法,依
2018 年 第 9 期
- 31 -
刘蕴,等:基于三角模糊数的车联网簇头节点选择方法
一个簇头可处理的节点数量、传输功率、能量消耗和移 动性等因素,并为上述因素赋不同的权重得到一个度量 标准,进而选取度量值最低的节点为簇头,该方法能够 实现较高的吞吐,但是因为存在较高的通信和计算负 载,无法满足高移动速度节点的需求,因此并不适用于 车联网环境;文献[9]基于近邻传播算法提出了一种基 于移动性的集簇机制,基于车辆间的距离完成簇头的选 取,该方法对移动性提供较好的支持,但存在长聚合延 迟及网络负载较高、吞吐较低等问题。针对现有方法的 不足,本文提出了一种基于三角模糊数的车联网簇头节 点选择方法,主要通过三角模糊数和学习机制完成车辆 节点加速度的预测,并通过定义的加权稳定因子完成簇 头节点的选取。
赖邻近车辆相对速度和相对距离完成簇头的选择。构建了一种典型车联网应用场景,提出了基于三角模糊数和学习机制
的车辆加速度预测方法,基于定义的加权稳定因子,设计了车联网簇头节点选择机制。基于 iTETRIS 构建了车联网仿真平
台进行测试分析,结果表明,与 CMCP 方法和 APROVE 方法相比,提出的簇头节点选择方法有效性较高。
a typical application scenario of IoVs was constructed. Secondly, a vehicle acceleration forecasting method was proposed
Palo Alto Networks Cortex XSOAR Threat Intelligenc

Cortex XSOAR ThreatI ntellig ence Manag ementThreat intelligence is at the core of every security operation. It applies to every security use case. Unfortunately, security teams are too overtaxed to truly take advantage of their threat intelligence, with thousands of alerts and millions of indicators coming at them daily. They require additional context, collaboration, and automation to extract true value. They need a solution that gives them the confidence to do their jobs effectively and shore up their defenses against the attacker’s next move.Cortex® X SOAR Threat Intelligence Management (TIM) takes a unique approach to native threat intelligence management, unifying aggregation, scoring, and sharing of threat intelligence with playbook-driven automation.Features and Capabilities Powerful, native centralized threat intel : Supercharge i nvestigations with instant access to the massive repository of built-in, high-fidelity Palo Alto Networks threat intelli -gence crowdsourced from the largest footprint of network, endpoint, and cloud intel sources (Tens of millions of mal -ware samples collected and firewall sessions analyzed daily).Indicator relationships : Indicator connections enable struc -tured relationships to be created between threat intelligence sources and incidents. These relationships surface importantcontext for security analysts on new threat actors and attack techniques.Hands-free automated playbooks with extensible integra-tions : Take automated action to shut down threats across more than 600 third-party products with purpose-built p laybooks based on proven SOAR capabilities.Granular indicator scoring and management : Take charge of your threat intel with playbook-based indicator lifecycle man -agement and transparent scoring that can be extended and customized with ease.Automated, multi-source feed aggregation : Eliminate manual tasks with automated playbooks to aggregate, parse, prioritize, and distribute relevant indicators in real time to security con -trols for continuous protection.Most comprehensive marketplace : The largest community of integrations with content packs that are prebuilt bundles of integrations, playbooks, dashboards, field subscription services, and all the dependencies needed to support specific security orchestration use cases. With 680+ prebuilt content packs of which 700+ are product integrations, you can buy i ntel on the go using Marketplace points.Business Value Figure 1:Control, enrich, and take actionwith playbook-driven automation Take Full Control Take complete control of your threat intelligence feeds Enrich Incident Response Make smarter incident response decisions by enriching every tool and process Actionable IntelClose the loop between intelligence and action withplaybook-driven automationFigure 2: Take control of your threat intel feedFigure 3:Make smarter decisions by enriching and prioritizing indicatorsFigure 4: Close the loop between intel and action with automationThreat Intelligence Combined with SOAR Security orchestration, automation, and response (SOAR) solutions have been developed to more seamlessly weave threat intelligence management into workflows by combin -ing TIM capabilities with incident management, orchestra -tion, and automation capabilities. Organizations looking for a threat intelligence platform often look for SOAR solutions that can weave threat intelligence into a more unified andautomated workflow—one that matches alerts both to their sources and to compiled threat intelligence data and that can automatically execute an appropriate response.As part of the extensible Cortex XSOAR platform, threat intel management unifies threat intelligence aggregation, scoring, and sharing with playbook-driven automation. It empowers security leaders with instant clarity into high-priority threats to drive the right response, in the right way, across the entire enterprise.way. Automated data enrichment of indicators provides ana-lysts with relevant threat data to make smarter decisions. Integrated case management allows for real-time collabora-tion, boosting operational efficiencies across teams, and auto-mated playbooks speed response across security use cases. Key Use CasesUse Case 1: Proactive Blocking of Known ThreatsChallengeThe security team needs to leverage threat intelligence to block or alert on known bad domains, IPs, hashes, etc. (indicators). The indicators are being collected from many different s ources, which need to be normalized, scored, and analyzed before the customer can push to security devices such as SIEM and firewall for alerting. Detection tools can only handle l imited amounts of threat intelligence data and need to constantly re-prioritize indicators.SolutionIndicator prioritization. Palo Alto Networks Threat Intelligence Management can ingest phishing alerts from email i nboxes through integrations. Once an alert is ingested, a playbook is Use Case 2: Dynamic Allow/Deny ListA dministratio nChallengeManual process for allow/deny lists. Managing a single allow list and updating across the enterprise can involve updating dozens of network devices. Security teams often have to liaise with firewall admins, IT teams, DevOps, and other teams to execute some parts of incident response.SolutionEliminate downtime by using automated playbooks to e xtract valid IP addresses and URLs to exclude from enforce-ment point EDLs, ensuring employees have access to these b usiness-critical applications at all times.Use Case 3: Cross-Functional IntelligenceS haringChallengeIntelligence sharing is unstructured. Most intelligence is still shared via unstructured formats such as email, PDF, blogs, etc. Sharing indicators of compromise is not enough. A dditional context is required for the shared intelligence to have value.Internal alerts3000 Tannery WaySanta Clara, CA 95054 Main: +1.408.753.4000 Sales: +1.866.320.4788 Support: +1.866.898.9087© 2021 Palo Alto Networks, Inc. Palo Alto Networks is a registeredt rademark of Palo Alto Networks. A list of our trademarks can be found at https:///company/trademarks.html. All other marks mentioned herein may be trademarks of their respective companies. cortex_ds_xsoar-threat-intelligence-management_062221SolutionIndicator connections enable structured relationships to be created between threat intelligence sources. These relation-ships surface important context for security analysts, threat analysts, and other incident response teams, who can collab-orate and resolve incidents via a single platform.Industry-Leading CustomerS uccessOur Customer Success team is dedicated to helping you get the best value from your Cortex XSOAR investments and giving you the utmost confidence that your business is safe. Here are our plans:• Standard Success, included with every Cortex XSOAR sub-scription, makes it easy for you to get started. You’ll have access to self-guided materials and online support tools to get you up and running quickly.• Premium Success, the recommended plan, includes every-thing in the Standard plan plus guided onboarding, custom workshops, 24/7 technical phone support, and access to the Customer Success team to give you a personalized ex-perience to help you realize optimal return on investment (ROI).Flexible DeploymentCortex XSOAR can be deployed on-premises, in a private cloud, or as a fully hosted solution. We offer the platform in multiple tiers to fit your needs.。
研究NLP100篇必读的论文---已整理可直接下载

研究NLP100篇必读的论⽂---已整理可直接下载100篇必读的NLP论⽂⾃⼰汇总的论⽂集,已更新链接:提取码:x7tnThis is a list of 100 important natural language processing (NLP) papers that serious students and researchers working in the field should probably know about and read.这是100篇重要的⾃然语⾔处理(NLP)论⽂的列表,认真的学⽣和研究⼈员在这个领域应该知道和阅读。
This list is compiled by .本榜单由编制。
I welcome any feedback on this list. 我欢迎对这个列表的任何反馈。
This list is originally based on the answers for a Quora question I posted years ago: .这个列表最初是基于我多年前在Quora上发布的⼀个问题的答案:[所有NLP学⽣都应该阅读的最重要的研究论⽂是什么?]( -are-the-most-important-research-paper -which-all-NLP-students-should- definitread)。
I thank all the people who contributed to the original post. 我感谢所有为原创⽂章做出贡献的⼈。
This list is far from complete or objective, and is evolving, as important papers are being published year after year.由于重要的论⽂年复⼀年地发表,这份清单还远远不够完整和客观,⽽且还在不断发展。
基于改进随机游走的复杂网络节点重要性评估

Operations Research and Fuzziology 运筹与模糊学, 2023, 13(1), 329-340 Published Online February 2023 in Hans. https:///journal/orf https:///10.12677/orf.2023.131036基于改进随机游走的复杂网络节点重要性评估蔡晓楠,郑中团*上海工程技术大学数理与统计学院,上海收稿日期:2023年1月23日;录用日期:2023年2月17日;发布日期:2023年2月23日摘要复杂系统可以抽象为复杂网络,重要节点评估与识别是复杂网络的一个热点问题。
针对网络拓扑结构和节点自身属性对有向复杂网络重要节点的影响,提出基于改进随机游走的节点重要性评估方法。
首先对节点的出度和入度分别附参数求出节点联合度数为节点质量,并通过调节参数评估节点出度与入度对节点重要性的影响;其次使用SimRank 算法得任意两个节点相似值的倒数为引力模型的距离,考虑节点间的拓扑结构;最后通过相对路径数比值做引力模型的系数,考虑节点间信息传播的影响效果。
任意两节点的作用力构造引力矩阵,将引力矩阵行归一化构造转移矩阵,然后随机游走对节点进行排序。
使用极大强连通性、极大弱连通性和脆弱性等评估指标在四个真实网络上进行实验对比,结果表明,提出的算法相比LeaderRank 、PageRank 、HITs 等方法能更准确地评估节点的重要性。
将复杂网络的多种特征进行融合,新创建的重要节点评估方法可以运用在生物领域和经济贸易领域等。
关键词有向复杂网络,节点重要度,节点相似性,引力模型,相对路径Evaluation of Node Importance in Complex Networks Based on Improved Random WalkXiaonan Cai, Zhongtuan Zheng *School of Mathematics, Physics and Statistics, Shanghai University of Engineering Science, Shanghai Received: Jan. 23rd, 2023; accepted: Feb. 17th, 2023; published: Feb. 23rd, 2023AbstractComplex systems can be abstracted as complex networks. The evaluation and identification of important nodes is a hot issue in complex networks Aiming at the influence of network topology*通讯作者。
2021最新5G恒山XX信息科技有限公司面试试题(含答案)

精选考试类应用文档,如果您需要使用本文档,请点击下载,另外祝您生活愉快,工作顺利,万事如意!精选考试类文档,如果需要,请下载,希望能帮助到你们!XX某公司5G考试题库及答案———解老师温馨提示:同学们,经过培训学习,你一定积累了很多知识,现在请认真、仔细地完成这张试题吧。
加油!一、单选题( )1.如下5G的关键技术中,不可以提升网络频谱效率的是?A.新信道编码B.256QAM高阶调整C.灵活子载波带宽D.MassiveMIMO正确答案:C( )2.HSS和SCEF之间的接口是_________________A. S6tB. S11C. S1D. S5正确答案:A( )3.5G可以配置的PCI有_________________个A. 504B. 512C. 1008D. 1024正确答案:C( )4.以下选项适用于URLLC场景的是_________________A.无人驾驶B.VRC.高清视频D.抄表业务正确答案:A( )5.5G2.5ms双周期帧结构支持的最大广播波束为_________________个A.2B.4C.7D.8正确答案:C( )6.低频信道传播损耗组成不包括_________________A.自由空间传播损耗B.穿透损耗C.雨衰和大气影响D.衍射绕射损耗正确答案:C( )7.一个BWP最少占用多少个RBA.14 ;B.20;C.24;D.28正确答案:C( )8.CU/DU分离之后,实现鲁棒性IP头压缩、加密解密等功能的网元是?A.AUD.U正确答案:C( )9.当TCI配置关联到两个RS资源,应该使用QCL为_________________的资源A. typeA;B. typeB;C. typeC;D. typeD。
正确答案:D( )10.5GNR下,DLLayermapping的时候当layer数大于_________________,codeword才是双流A.3B.5C.2D.4正确答案:D( )11.下列哪项是IDLE和INACTIVE态下共有的功能_________________A. UE的DRX由RRC层配置;B. 网络可以配置UE移动性;C. UE 储存AS上下文;D. 移动到其他RNA后执行RNA update;正确答案:B( )12.TS 38.211 ON NR是下面哪个协议_________________A.Physical channels and modulationB.NR and NG-RAN Overall DescriptionC.Radio Resource Control(RRC) ProtocolD.Base Station(BS) radio transmission and reception正确答案:A( )13.频域上,SS/PBCH block由多少个连续的RB构成A.24个;B.20个;C.12个;D.10个正确答案:B( )14.5G从3GPP哪个release版本开始的?_________________A.B、R15B.D、R17C.A、R14D.C、R16正确答案:A( )15.5G RAN2.0版本gNB主控单板以太网业务端口DEVIP最大支持配置是多少个C.5D.8正确答案:D( )16.短序列为NR新增的PRACH Preamble格式,R15共9种格式,其中C2格式最大小区覆盖半径为_________________A.9.29kmB.5.35kmC.3.86kmD.7.56km正确答案:A( )17.5GNR下,一个SS/PBCH block包含_________________个OFDM symbolsA. 1B. 2C. 3D. 4正确答案:D( )18.DCDU-12B为直流配电单元,为机柜内各部件提供多大的直流电源输入A.-24B.48C.-48D.24正确答案:C( )19.关于SS/PBCH block,以下说法错误的是_________________。
Cradlepoint COR IBR1100系列3G 4G LTE网络解决方案说明说明书

1Cradlepoint COR IBR1100/IBR1150 SpecificationsFigure 1: COR IBR1100Highly Available, Cloud-Managed Networking for Extreme ConditionsThe Cradlepoint COR IBR1100 Series is a compact, ruggedized 3G/4G/LTE networking solution designed for mission critical connectivity in the most challenging environments.Ideal for in-vehicle networks including police cars, ambulances, and mass transit, this cloudmanaged solution provides organizations the ability to scale deployments quickly and manage their vehicle networks easily in real-time.With an extensive list of safety and hardening certifications, the COR IBR1100 is engineered to protect against extreme temperatures, humidity, shocks, vibrations, dust, water splash, reverse polarity and transient voltage.Key Features• Cloud-managed for zero-touch deployment and intelligent management • Internal 3G/4G modem with secured SIM card access and dual SIM slots• LTE support for all major U.S. carriers and Europe/international operators (failover to HSPA+ or EVDO) • Software-defined radio supports multiple carriers (Gobi)• WiFi (IBR1100) and non-WiFi versions (IBR1150) available: IBR1100 includes dual-band dual-concurrent 2.4/5 GHz 802.11 a/b/g/n/ac WiFi; 2 x 2 MIMO with two external dualband antenna connectors • Ignition sensingRuggedized: protects against vibration, shock, dust, splash, & humidityBuilt-in transient and reverse polarity voltage protection; 9–36 DC voltage input range• Integrated temperature sensor• Three 10/100 Ethernet ports (LAN/WAN configurable)2• Antenna connectors for external cellular modem (two) and active GPS (one) • RS-232 serial portFigure 2: COR IBR1100 FrontFigure 3: COR IBR1100 BackFeaturesWAN• 4G LTE/HSPA+/EVDO (multi-carrier)• WiFi as WAN¹, with WPA2 Enterprise Authentication for WiFi-as-WAN³ • Failover/Failback • Load Balancing• Advanced Modem Failure Check • WAN Port Speed Control • WAN/LAN Affinity • IP PassthroughLAN• VLAN 802.1Q• DHCP Server, Client, Relay DNS and DNS Proxy DynDNS • UPnP • DMZ3• Multicast/Multicast Proxy• QoS (DSCP and Priority Queuing) • MAC Address FilteringWiFi¹• Dual-Band Dual-Concurrent • 802.11 a/b/g/n/ac• Up to 128 connected devices (64 per radio – 2.4 GHz and 5 GHz) • Multiple SSIDs: 2 per radio (4 total) • WPA2 Enterprise (WiFi) • Hotspot/Captive Portal • SSID-based PriorityManagement• Cradlepoint Enterprise Cloud Manager² • Web UI, API, CLI• Active GPS support on all models • Data Usage Alerts (router and per client) • Advanced Troubleshooting (support) • Device Alerts • SNMP • SMS control • Serial RedirectorVPN and Routing• IPsec Tunnel – up to 5 concurrent sessions • L2TP³ • GRE Tunnel • OSPF/BGP/RIP³ • Per-Interface Routing • Routing Rules • NAT-less Routing• Virtual Server/Port Forwarding • NEMO/DMNR³ • IPv6 • VRRP³ STP³ NHRP³Security4• RADIUS and TACACS+• 802.1x authentication for Ethernet • Zscaler integration³ • Certificate support • ALGs• MAC Address Filtering• Advanced Security Mode (local user management only) • Per-Client Web Filtering • IP Filtering• Content Filtering (basic) • Website FilteringCloud Optimized IP Communications• Automated WAN Failover/Failback support• WAN Affinity and QoS allow prioritization of VoIP services • Advanced VPN connectivity options to HQ• SIP ALG and NAT to allow VoIP and UC communications to traverse firewall • MAC Address Filtering• 802.1p/q for LAN QoS segmentation and treatment of VoIP on LAN • Private Network support (wired and 4G WAN) • Cloud-based management²1 – WiFi-related functions are only supported on IBR1100 models2 – Enterprise Cloud Manager requires a subscription3 – Requires an Extended Enterprise LicenseSpecificationsWAN• Integrated 4G LTE modem (with 3G failover)• Three LAN/WAN switchable 10/100 Ethernet ports – one default WAN (cable/DSL/T1/satellite/Metro Ethernet) • WiFi as WAN, Metro WiFi; 2x2 MIMO “N” 2.4 GHz or 5 GHz; 802.11 a/b/g/n/ac (IBR1100 only)5LAN• Dual-band dual-concurrent WiFi; 802.11 a/b/g/n/ac (IBR1100 only) • Three LAN/WAN switchable 10/100 Ethernet ports – two default LAN • Serial console support for out-of-band management of a connected device PORTS• Power • 2-wire GPIO • USB 2.0• 3 Ethernet LAN/WAN• 2 cellular antenna connectors (SMA) • 1 active GPS antenna connector (SMA) • 2 WiFi antenna connectors (R-SMA)• Serial DE-9 (commonly called “DB -9”) connector – RS-232 (out-of-band management of an external device requires a null modem adapter/cable) TEMPERATURE• −30° C to 70° C (−22 °F to +158 °F) operating • −40 °C to 85 °C (−40 °F to +185 °F) storage• Includes temperature sensor with options for alerts and automatic shutoff HUMIDITY (non-condensing)• 5% to 95% operating • 5% to 95% storage POWER• DC input steady state voltage range: 9–36 VDC (requires inline fuse for vehicle installations)– For 9–24 VDC installations, use a 3 A fuse – For > 24 VDC installations, use a 2.5 A fuse• Reverse polarity and transient voltage protection per ISO 7637-2 • Ignition sensing (automatic ON and time-delay OFF) • Power consumption:– idle: typical=400mA@12VDC (4.8W); worst case=800mA@12VDC (9.6W) – Tx/Rx: typical=650mA@12VDC (7.8W); worst case=1300mA@12VDC (15.6W) – 12VDC 2A adapter recommendedSIZE – 5.3 in x 4.4 in x 1.4 in (134 mm x 112 mm x 35 mm)6WEIGHT – 16.1 oz (457 g) CERTIFICATIONS• FCC, CE, IC• WiFi Alliance (IBR1100 only) – 802.11a/b/g/n certified, 802.11ac supported • Safety: UL/CUL, CB Scheme, EN60950-1 • Hazardous Locations: Class I, Div. 2 (pending)• Shock/Vibration/Humidity: compliant with MIL STD 810G and SAEJ1455• Ingress Protection: compliant with IP64 (includes protection from dust and splashing water) • Materials: WEEE, RoHS, RoHS-2, California Prop 65 • Vehicle: E-Mark, compliant with ISO 7637-2 • Telecom: PTCRB/CTIA, GCF-CC GPS• GPS Protocols: TAIP and NMEA 0183 V3.0 • Satellite channels: 12 channel, continuous tracking • 1 Hz refresh rate • Accuracy:– < 2m: 50% – < 5m: 90% • Acquisition:– Hot start: 1 second – Warm start: 29 seconds – Cold start: 32 seconds • Sensitivity– Tracking: −161 dBm (tracking sensitivity is the lowest GNSS signal level for which the device can still detect an in-view satellite 50% of the time when in sequential tracking mode) – Acquisition (standalone): −145 dBm (acquisition sensitivity is the lowest GNSS signal level for which the device can still detect an in-view satellite 50% of the time) • Operational limits: altitude < 6000 m or velocity < 100 m/s (either limit may be exceeded, but not both)What’s In The Box• Ruggedized router with integrated business-class 3G/4G modem; includes integrated mounting plate • Two meter locking power and GPIO cable (direct wire) Quick Start Guide with warranty informationNOTE: Due to the diverse needs of customers, the COR IBR1100/IBR1150 package does not include a power adapter or antennas. See the Accessories section below for several power and antenna options.7Feature Details• WAN Security – NAT, SPI, ALG, inbound filtering of IP addresses, port blocking, service filtering (FTP, SMTP, HTTP, RPL, SNMP, DNS, ICMP, NNTP, POP3, SSH), protocol filtering, WAN ping (allow/ignore) • Redundancy and Load Balancing – Failover/failback with 4G, 3G, Ethernet with rule selection, advanced load balancing options (round robin, spillover, data usage, rate), WAN failure detection, VRRP • Intelligent Routing – UPnP, DMZ, virtual server/port forwarding, routing rules, NATless routing, wired or wireless WAN-to-LAN IP passthrough, route management, perinterface routing, content filtering, IP filtering, website filtering, per-client Web filtering, local DHCP server, DHCP client, DHCP relay, DNS, DNS proxy; ALGs: PPTP, SIP, TFTP, FTP, IRC; MAC address filtering, Dynamic DNS, LAN/WAN affinity, VLAN 802.1Q (coming Q4), STP, enterprise routing protocols: BGP/OSPF/RIP, multicast proxy support, IP setting overrides, IPv6 support • Management – Enterprise Cloud Manager: cloud-enabled management and application platform (subscription-based); web-based GUI (local management), optional RADIUS or TACACS+ username/password; remote WAN web-based management w/ access control (HTTP, HTTPS); SNMP v1, v2c, & v3; CLI over SSH, SSH to serial, SSH to telnet; API; one-button firmware upgrade; modem configuration, update, and management; modem data usage w/ alerts, per-client data usage; custom AT scripting to modems • Performance & Health Monitoring – Advanced QoS with traffic shaping, with DSCP/DiffServe QoS, Modem Health Management (MHM) improves connectivity of modem, SSID-based priority, WAN port speed control, several levels of basic and advanced logging for troubleshooting • VPN (IPsec) – Tunnel, NAT-T, and transport modes; connect to Cradlepoint, Cisco/Linksys, CheckPoint, Watchguard, Juniper, SonicWall, Adtran and others; certificate support; Hash (MD5, SHA128, SHA256, SHA384, SHA512), Cipher (AES, 3DES, DES); support for 5 concurrent connections, GRE tunneling, L2TP support, multiple networks supported in a single tunnel, site-to-site dynamic VPN with NHRP • GPS – Active GPS antenna port; GUI mapping; multiple server reporting (coming Q4) with LAN and WAN options; TAIP and NMEA; custom intervals based on time and/or velocity (coming Q4)Support and Warranty∙ CradleCare Support Agreement available with technical support, software upgrades, and advanced hardware exchange – 1, 3, and 5 year optional.∙One-year limited hardware warranty available in the US and Canada; two-year limited hardware warranty for integrated EU products when purchased from an authorized EU distributor – extend warranty to 2, 3, or 5 yearsAccessoriesBecause of the diversity of customer needs, the COR IBR1100/IBR1150 does NOT include a power adapter or antennas in the box (it does include a direct wire power/GPIO cable for vehicle installation). Cradlepoint offers several accessory options for power adapters or antennas. Please see an associate for details.8Business-Grade Modem SpecificationsCOR IBR1100/IBR1150 models include an integrated 4G LTE modem – specific model names include a specific modem.Please note that LPE models are flexible and support bands for multiple cellular providers; however, only the frequency bands in bold below are supported by the listed provider.COR IBR1100LPE-VZ, COR IBR1150LPE-VZ – 4G LTE/HSPA+/EVDO• Technology : LTE , HSPA+, EVDO Rev A• Downlink Rates : LTE 100 Mbps, HSPA+ 21.1 Mbps, EVDO 3.1 Mbps (theoretical) • Uplink Rates : LTE 50 Mbps, HSPA+ 5.76 Mbps, EVDO 1.8 Mbps (theoretical) • Frequency Bands :– LTE Band 2 (1900 MHz), Band 4 – AWS (1700/2100 MHz), Band 5 (850 MHz), Band 13 (700 MHz), Band 17 (700 MHz), Band 25 (1900 MHz) – HSPA+/UMTS (850/900/1900/2100 MHz, AWS) – GSM/GPRS/EDGE (850/900/1800/1900 MHz) – CDMA EVDO Rev A/1xRTT (800/1900 MHz)• Power : LTE 23 dBm +/− 1, HSPA+ 23 dBm +/− 1, EVDO 24 dBm +0.5/−1 (typical conducted) • Antennas : two SMA male (plug), finger tighten only (maximum torque spec is 7 kgfcm) • GPS : active GPS support• Industry Standards & Certs : FCC。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
UbiRoad: Semantic Middleware for Cooperative Traffic Systems and ServicesVagan TerziyanMIT Department, University of Jyvaskyla P.O. Box 35 (Agora), 40014Jyvaskyla, Finlande-mail: vagan@jyu.fi Olena Kaykova, Dmytro Zhovtobryukh Agora Center, University of Jyvaskyla P.O. Box 35 (Agora), 40014Jyvaskyla, Finlande-mail: olena@cc.jyu.fi, dzhovto@cc.jyu.fiAbstract—Emerging traffic management systems and smart road environments are currently equipped with all necessary facilities to enable seamless mobile service provisioning to the users. However, advanced sensors and network architectures deployed within the traffic environment are insufficient to make mobile service provisioning autonomous and proactive, thus minimizing drivers’ distraction during their presence in the environment. An ideal system should provide solutions to the following two interoperability problems: interoperability between the in-car and roadside devices produced and programmed by different vendors and/or providers, and the need for seamless and flexible collaboration (including discovery, coordination, conflict resolution and negotiation) amongst the smart road devices and services. To tackle these problems, in this paper we propose UbiRoad middleware intending utilization of semantic languages and semantic technologies for declarative specification of devices’ and services’ behavior, application of software agents as engines executing those specifications, and establishment of common ontologies to facilitate and govern seamless interoperation of devices, services, remote systems and humans.Keywords- context-aware services; cooperative traffic; smart road; middleware; semantic technologies; agentsI.I NTRODUCTIONThere is about half of a billion drivers only in Europe, who wish driving to be more comfortable, efficient, ecological and less risky. Not far are the times when cars will themselves prevent accidents. People spend more time in vehicles and they are expecting also more possibilities to work and use various services while traveling, which requires new travel infrastructure and automation services [1]. These should combine various vehicles, their drivers and passengers, smart roads and appropriate Web services [2]. Recent wireless and internet technologies enable completely new possibilities to integrate available efforts into the new advanced traffic paradigm – cooperative traffic [3].Service-oriented architectures related to traffic management, smart roads and future context-aware services for drivers are closely integrated into the Internet of Things [4], which is a world where things can automatically communicate to computers and each other, providing services for human benefits. In such “Future Internet”, intelligence and knowledge will be distributed among an extremely large number of heterogeneous entities: sensors, actuators, devices, cars, road infrastructures, software applications, Web services, humans, and others. To realize this vision, there is a need for an open architecture, which will offer seamless connectivity and interworking between these heterogeneous entities. Moreover, ensuring collaboration, synchronization but also control of this distributed intelligence is a challenge that needs to be addressed, or the Internet of Things will become a chaotic, un-controlled and possibly dangerous environment since some actors of this Internet have impact on the real world (e.g., software or humans through actuators). Cooperative traffic domain enables interoperability between a large number of heterogeneous entities, while ensuring predictability and safety of their operation, is difficult without an extra layer of intelligence that will ensure the orchestration of these various actors according to well-defined goals, taking into account changing constraints, business objectives or regulations. This paper introduces such a middleware layer (UbiRoad). It provides cross-layer communication services (data-level interoperability) to the entities and extended multi-agent technologies will provide collaboration-support services (functional protocol-level interoperability and coordination) for these entities. The UbiRoad middleware concept apparently entails a vision of a multifaceted, multi-purpose and multipronged middleware platform applying multidisciplinary approach to extension and enhancement of the future smart traffic environments UbiRoad middleware should be rather seen as a meta-structure on top of the future intelligent transportation systems and services and as intelligent stratum between the smart road device layer and the future service oriented architectures.A first major problem to be addressed by UbiRoad is inherent heterogeneity, with respect to the nature of components, standards, data formats, protocols, etc., which creates significant obstacles for interoperability among the components of ubiquitous computing systems. This heterogeneity is likely to induce some integration costs that will become prohibitive at a very large scale preventing a rich ecosystem of applications to emerge. It is generally recognized that achieving the interoperability by imposing some rigid standards and making everyone comply could not be a case in open ubiquitous environments. Therefore, the interoperability requires existence of some middleware to act as the glue joining heterogeneous components together.The second major issue is to guarantee high level of safety. Since the IT infrastructure and through them users are going to have real actions in the real physical world throughvarious actuators we have to ensure that these actions are properly controlled and coordinated. Despite the wish to enable as many actors as possible to have access to physical world objects around the world to enable a large set of diverse applications, this should be done in a well-understood and safe manner. The “things” will have to exhibit some required behaviors that humans have adopted to assemble in cooperative traffic social interactions.The UbiRoad approach can be seen as studying the triangle of device-software-human interaction seen from the perspective of the above described scenarios. Henceforth we refer to “device” as to any monitored or controlled physical objects including e.g., vehicles. Substantial research results related to edges and vertices of this triangle have been (recently) reported [5, 6, 7] (e.g., efforts related to middleware for embedded systems, efforts related to integration of diverse software systems and services, etc). What is missing is an integrated coherent approach to cover the whole triangle. Moreover, many on the past research initiatives do not truly deal with the core topic, which is interoperability versus just interconnectivity. The components of cooperative traffic systems should be able not only to communicate and exchange data, but also to flexibly coordinate with each other, discover and use each other, learn about the location, status and capabilities of each other, and jointly engage in different traffic situations. Moreover, the components must achieve the above using an always-on, safe, robust and scalable means of interaction.Further in this paper, we argue in favor of fully interoperable (though heterogeneous), highly dynamic and extensible smart road environments. We present a specialized agent-driven middleware platform UbiRoad, in which each ubiquitous smart device (as well as each individual service exposed as an individually accessible entity through the environment) will be assigned a representative agent within UbiRoad. The resulting multi-agent system will be exploited as a mediation facility enabling rich cooperation capabilities (e.g., discovery, coordination, adaptability, and negotiation) amongst the devices inhabiting the smart traffic environment. Utilization of semantic technologies [8] in UbiRoad will ensure efficient and autonomous coordination among UbiRoad agents and will thus ensure interoperability between associated devices and services. Several UbiRoad ontologies are an important asset contributing to interoperability realization within future smart traffic environments. These ontologies are used not only for the benefit of UbiRoad middleware architecture, but also and most importantly for facilitation of interoperability and integration of existing and brand-new future devices, services and methodologies. Through appropriate declarative specification of smart road components’ behavior and using sophisticated choreographic control agents in a multimodal dynamic networked environment, the UbiRoad enables various devices and services to automatically discover each other and to configure complex services functionally composed of the individual services’ and devices’ functionalities.The rest of the paper is organized as follows: in ChapterII we are providing the motivating scenario for the new challenging requirements to traffic management systems; in Chapter III we list the requirements and related challenges to be addressed when designing such systems; in Chapter IV we provide possible solution for the challenges based on the concept and architecture of the so called Global Understanding Environment; in Chapter V we discuss some important and challenging features of appropriate agent-driven platform (UBIWARE) suitable for UbiRoad implementation, such as: semantic adapters and integrators (called ontonuts); semantic visualization technology (called for-eye); user-driven system configuration (via so called smart comments); and semantic blogging; in Chapter VI we briefly discuss on Traffic and Mobility ontology and semantic integration of heterogeneous traffic management systems; and we conclude in Chapter VII.II.M OTIVATING S CENARIOConsider the following story, in which we try to integrate several possible scenarios of future use for the UbiRoad middleware.(Beginning of the story) “Timo lives in Jyväskylä. Former researcher, he is a widely recognized expert in the field of intelligent software agents. Nowadays Timo owns a small IT business based in Jyväskylä, and his firm is often subcontracted by large IT and telecom enterprises to perform highly specialized development services. Therefore, Timo is a frequent guest in Helsinki and Helsinki region, where most of his company’s employers reside. Despite considerable distance between Jyväskylä and Helsinki, Timo likes neither airplanes, nor trains, and always travels inside Finland by car. Fortunately, he is a big cars-lover and a good driver.Timo arrived in Helsinki early in the morning and spent the whole day participating in a few various business meetings and research seminars. Now, when he is about to leave Helsinki, he feels very tired. He could stay in Helsinki overnight, but he has another important meeting scheduled for tomorrow at 7 am in Jyväskylä. Not to fall asleep on the way back to Jyväskylä, Timo drops by the nearest cafeteria and drinks a cup of strong coffee. Having felt a burst of energy after the sprightly drink, he gets into his car and leaves Helsinki at dusk. In the car Timo selects from his audio collection some nice invigorative music to listen to and sets the car control system’s operating mode to ‘exhaustion’ using the available on-board control panel. Timo knows that in this mode the awareness levels of a multitude of software agents, which inhabit his car and make it a part of the UbiRoad intelligent transportation system, reach the highest possible value. Now he feels much less vulnerable because of fatigue, as agents in this mode help significantly reduce exposure to various on-road risks. The in-car control system adjusts climate conditions (temperature, humidity, level of oxygen) to optimal levels with respect to the selected operating mode: it aims to maintain cool, fresh, oxygen-rich atmosphere inside the car in order to prevent the driver from falling asleep; and activates on-board alarm system, which is configured to give to the driver light and audio indication every 30 seconds (not allowing him falling asleep). Thecorresponding UbiRoad traffic agent (representing Timo and his car as a dynamic road user entity) sets own hazard level to ‘red’, thus notifying other road users of potential risks associated with its road user. When Timo drives onto the motorway going out of Helsinki, he feels much more comfortable and relaxed, as he is sure that all necessary measures of passive risk prevention have been undertaken and as he should no longer pay attention to the oncoming traffic (on motorways directions of traffic are separated).To shake himself up a bit, Timo switches to the left lane (each direction of the motorway connecting Helsinki and Lahti has two lanes) and starts overtaking all cars, which slowly go on the right lane. The speed limit on this motorway is 120 kmph and driving at it can be refreshing. After some time of such racing Timo however forgets about the speed, which immediately goes beyond 130 kmph, and the traffic agent monitoring velocity and controlling speed regimes detects inadmissibly excessive speed (via comparing actually measured vehicle’s velocity with the speed limit that the agent can read from RFID-enhanced traffic signs located on the sides of the road) and activates a loud beep tone combined with an appropriately marked blinking red LED on the control panel. Timo takes this as a timely signal to calm down, decelerates to the allowed speed limit and uses the cruise control functionality embedded into the steering wheel to fix the speed at the current level. Now he can release the accelerator completely and give his leg some rest.Timo utilizes voice control system to engage a travel estimator service and thus to find out the approximate time of his arrival in Jyväskylä. The specialized voice recognition system reads Timo’s oral instructions, interprets them and finally transforms them into the format recognizable by UbiRoad agents. Then the corresponding communication agent finds an appropriate travel estimator service in the Internet, negotiates service contract with the agent representing the service and finally invokes the service. The result of travel duration estimation, 2 hours and 10 minutes, appears on the LCD screen built in the control panel to the right of the driver’s seat. Timo decides to call home and let his wife know he is coming back soon. Timo’s mobile phone is already connected with the in-car control system via Bluetooth. Timo utilizes voice control to access his phone and then voice dial to call Anna. While the picked number is being dialed, playing music is automatically damped down, and as soon as the phone connection is established, the conversation is output through the in-car embedded speaker system. After several minutes of chatting with Anna, Timo notices that he is driving already in the neighborhood of Lahti. Here 3G telecommunication network is available. The communication agent immediately detects this and using the LCD screen asks Timo if he is willing to switch to a video call. Timo accepts the offer by pressing the corresponding button on the touch-sensitive screen. The communication agent immediately requests the video capture service from a tiny camera embedded in the control panel in front of the driver’s seat. Then it rearranges the current voice call session as a new video call session without interrupting the call and interweaves the audio component acquired through Timo’s hands-free microphone with the video component obtained by the in-car embedded video camera. A live view of Anna appears on the LCD screen of the control panel. However, as shifting driver’s focus to this side screen is inconvenient and distracting the driver from actual driving, the picture on the screen is instantly projected on the internal surface of the car’s windscreen just in front of the driver’s seat. The projected image is however semi-transparent not to impede driver’s clear view of the road.Timo finishes talking with his wife when Lahti is already left behind. He notices that twilight almost gave the place to solid night, but the motorway is still well illuminated. Timo decides to make a short stop at the picturesque roadside restaurant “Tähtihovi” in order to stretch his legs and have another cup of coffee before proceeding to the most difficult and boring part of his trip. Soon after this stop Timo should drive off the motorway to the side route leading to Jyväskylä. The traffic agent recognizes this major route change and reminds Timo of it well in advance using available visual indication means (LCD screen, projection on the windscreen, etc.) As Timo turns to the needed side road, he soon finds himself completely benighted as roadside lamps are uncommon here. He switches to upper beam to see at least something. Using embedded luminosity sensors, the agent monitoring external physical environment immediately detects severe lack of light on the road and activates built-in night vision system that multiply amplifies luminosity of the reflected light both in visible and infrared spectrum, thus being able to identify distant objects also by the heat they emit (e.g., oncoming cars, cyclists, pedestrians, elks, etc.). Such enhanced view of the road environment is projected on the internal surface of the car’s windscreen so that it maximally coincides with the driver’s field of view. Hence, Timo is now able to see everything much more clearly and recognize moving objects well in advance. What is more, in observed conditions of dark driving on a narrow bidirectional road the traffic agent starts to provide necessary assistance services such as improved navigation and automated signaling, e.g., a dynamically changing light-modulated traffic map of the neighborhood (specifically highlighting the route undertaken) is projected on the right side of the windscreen; upcoming turns and bends of the road are visually indicated (e.g., in the form of light arrows in the upper part of the windscreen); crossroads and cars approaching from the opposite direction are also identified for the driver in good time; switching from upper to lower beam (in proximity of oncoming cars) and back is performed automatically.Luckily, the road is almost empty at night, and Timo almost reaches Jyväskylä when he catches up a heavy truck slowly going ahead of his car. Road is constantly dodging and the road-bed is narrow to comfortably overtake the truck. Timo almost loses patience waiting for a more or less straight section of the road, and as soon as such sectionappears ahead, he confidently sends the car on the opposite lane and starts overtaking the truck. Suddenly he sees an opportune notification of an oncoming vehicle, which is still on the other side of the hill ahead of Timo and is thus unseen, but is quickly approaching. Perhaps, Timo is too tired as he makes an estimation error: he decides that he has enough space and time to complete the maneuver and continues overtaking. The oncoming car is however approaching too fast making head-on meeting with Timo’s car almost inevitable. Moreover, the truck being overtaken turns out to be a long road-train, and it is already too late to get back behind it because Timo’s car has passed more than a half of the truck’s length already, when Timo realizes that he fell a victim to his own fatigue and impatience, and that only a miracle can now save him from head-on collision with the other car. UbiRoad intelligence is such a miracle.The UbiRoad traffic agent that resides in Timo’s car establishes communication with the approaching car’s traffic agent immediately after it recognizes the presence of another vehicle in the proximity. At the same time it maintains communication with the traffic agent of the truck. The agents jointly monitor the process of rapprochement of the (three) vehicles. When Timo starts his overtaking maneuver, the traffic agents realize the situation is no longer standard. They integrate their individual traffic information, jointly reason upon it in the dynamic traffic context, and deduce that the collision is unavoidable. To prevent the traffic accident or any other dire consequences of Timo’s mistake, the agents must undertake active measures of risk mitigation. The traffic agents of the approaching car and the truck notify their drivers of the potentially critical hazardous traffic situation and forcibly decelerate their vehicles to buy Timo enough time for successful completion of the overtaking maneuver. For its part, Timo’s traffic agent aggressively visualizes the imperative “complete the maneuver”, thus granting some extra confidence to its driver, who is already close to panic. Given such clear instruction, Timo accelerates even more and safely completes the overtaking maneuver. In twenty minutes, when he, exhausted as a squeezed lemon, but happy to escape probably fatal traffic accident, parks his car in his parking slot, another in-car agent reads Timo’s schedule for tomorrow (stored in the organizer application within Timo’s mobile phone) and sets engine warming-up timer to 6.30 am …” (end of story).To be able to make this scenario a reality we have to face several challenges described in the next chapter.III.U BI R OAD M IDDLEWARE C HALLENGESA.InteroperabilityBy proclaiming interoperability as its major ultimate objective, UbiRoad approach deals with three major types of interoperability problem: technical interoperability (being the capability of devices, protocols and other technical standards to co-exist and interoperate), semantic interoperability (being the capability of various system components to treat and interpret exchanged data and information identically and share a common understanding of it), and pragmatic interoperability (being the capability of system components to capture willingness of partners to collaborate or, more generally, to capture their (and even human users’) intent). Technical interoperability will be achieved through the agent-based mediation between different devices and standards with the aid of special adapter components and tunneling mechanisms. Semantic interoperability is the main focus of the UbiRoad approach as it is a prerequisite for seamless information internetworking and integration, and for smooth autonomous communication between various resources within a smart traffic environment. Semantic interoperability can be achieved by exploitation of rich metadata describing informational objects and semantic resource descriptions written in compliance with well-established semantic standards and on the base of predefined domain ontologies and UbiRoad Ontologies. Pragmatic interoperability amongst smart space components is achieved through appropriate design of declarative specifications of such components’ behavior and on-the-fly agent-based identification of this behavior using given descriptions. Finally, the most innovative type of interoperability, which UbiRoad provides, is the so-called ‘cross-layer’ interoperability, e.g., interoperability between devices and services in a smart traffic environment. This particular class of interoperability problems is often difficult to solve even on individual basis. However, UbiRoad provides native support for cross-layer interoperation by implementing the paradigm of resource-oriented networking. This paradigm enforces unified treatment of various system components, e.g., devices, services, applications and even users, as different types of resources (Figure 1).Figure 1. Agent-driven smart road interoperabilityThe communication is then established between resources regardless their particular type provided that negotiation is performed by resources’ representing agents (associated with resources within smart traffic environmentsand beyond) as shown in Figure 1 and appropriate Semantic Web standards for unified resource description are used.B.Flexible CoordinationAs smart traffic environments are basically deployed to provide users with dynamically configured, customized, value-added and on-the-move autonomously operating services, UbiRoad targets establishment of such service creation and provisioning framework that would emphasize the above mentioned characteristics of ubiquitous services. Customization, personalization, added value, dynamicity and autonomy of services is to be achieved through construction and utilization of context-aware, adaptable and reconfigurable composite service networks. Service networks can be composed using declarative specifications of service models. Reconfigurability of service networks is made possible via utilization of hierarchical modeling of service control and its run-time execution. Dynamic adaptation of services is performed by special context-aware control components built in service networks. The traditional tradeoff “customization vs. autonomy” can be dealt with through a balanced use of user-aware goal-driven on-demand service composition, AI-enriched active context-awareness capturing user intent, and user-collaborative passive context-aware service composition. Though it is a challenging task, utilization of agent-based approach for service composition makes it much more flexible compared to traditional orchestration approaches. This difference in flexibility can be seen from the definition of the traditional Semantic Web services (SWS) given in [17] (“Self-contained, self-described, semantically marked-up software resources that can be published, discovered, composed and executed across the Web in a task-driven way”) and the definition of proactive (agent-driven) SWS given in [18] (“Self-contained, self-described, semantically marked-up proactive software resources that can be published, discovered, composed and executed across the Web in a task-driven way, and which behave to increase their utility and are the subject of negotiation and trade”). Agents can bring many valuable features into a service composition framework, e.g., precomposition, distributed hierarchical control of service networks (not requiring a dedicated underlying infrastructure), and enhanced negotiation of non-functional service parameters.C.Self-ManagementUbiRoad brings self-management aboard via presenting totally distributed agent-driven proactive management system. UbiRoad agents monitor various components, resources and properties within the system architecture and infrastructures belonging or otherwise interacting with the managed smart road environment, and react to changes occurred by reconfiguring the architecture in appropriate way with respect to the predefined (or inferred) configuration plan. Configuration plans basically represent enhanced business models, which are adhered to during accomplishment of communication procedures between different parties. Due to purely distributed layout of the agent system and outstanding agents’ programmability, merely all kinds of business models can be formalized and enacted by the UbiRoad management platform (due to richness of the utilized agent communication language and of the associated ontology base). In addition to this, UbiRoad agents are capable of learning via utilizing available data mining algorithms and further dynamically reconfiguring the managed architecture on the basis of acquired knowledge, thus being capable of inferring (also collaboratively) new configuration plans. UbiRoad can be deployed on top of any architectural model (including ad-hoc and peer-to-peer, which is of crucial importance for highly dynamic traffic environments) due to benefits of agent technologies and open resource interfaces. Also, the UbiRoad platform can make use of contextual information extracted from the managed networking environment in order to act as appropriately to the observed requirements and circumstances as possible.D.Trust and ReputationTrust is identified as one of the major and most crucial challenges of the future computing and communications. We envisage a semantic ontology-based approach to building a universal trust management system. To make trust descriptions interpretable and processable by autonomous trust management procedures and modules, trust data should be given explicit meaning via semantic annotation. Semantic trust concepts and properties will be utilized and interpreted using common trust ontologies. This approach to trust modeling is especially flexible because it allows for various trust models to be utilized throughout the system seamlesslyat the same time. Trust information can be incorporated as part of semantic resource descriptions and stored in dedicated places within the UbiRoad platform. Communication and retrieval of trust information will be accomplished through corresponding agent-to-agent communication. Agents representing communicating resources must be configured appropriately to handle all necessary trust management activities between the corresponding communication parties. Trust management procedures can be realized as a set of specific business scenarios in the form of agent configuration plans.E.Other ChallengesSpecifically, due to utilization of extended intelligent agent technology UbiRoad significantly contributes to realization or enhancement of the following important characteristics and functionalities of collaborative traffic environments:•Data mining and knowledge discovery (e.g., utilization of accumulated statistics of traffic accidents), whichmay be organized either by establishing centralizedWeb server with appropriate data processing services orby local processing of the analytics and exchanging ofit in a P2P manner;•Learning (e.g., case-based learning, when traffic agents can learn on sets of predefined examples of trafficsituations);。
