Covariance Based Signal Detections for Cognitive Radio
阵形畸变对拖线阵三维探测性能的影响及补偿技术

阵形畸变对拖线阵三维探测性能的影响及补偿技术王思秀【摘要】针对拖曳阵阵形畸变导致的目标检测不准确问题,首先,分析了阵形畸变对拖线阵三维探测性能的影响,并论证了利用实际阵形在垂直方向形成的孔径实现对目标深度信息提取可行性;然后,依据拖线阵中姿态与深度传感器监测数据,提出一种基于阵形自动拟合的三维补偿技术;最后,通过三维补偿技术修正导向矢量,降低导向矢量与协方差矩阵之间不匹配度,解决阵形畸变所导致的目标检测不准确问题.数值仿真结果表明,对畸变阵形进行三维阵形估计和补偿,实现了对未知目标的三维探测,且避免了标校声源对拖线阵实时探测目标的影响,便于工程应用.%For the discontinuous problem of the target detection caused by the array shape distortion of the towed line array,firstly,the influence of the array shape distortion on the 3D detection performance is ana-lyzed,and the feasibility of extracting target depth information is demonstrated via the actual array shape forming the aperture in the vertical direction. Then,according to the monitoring data of the attitude sensor and depth sensor,a 3D compensation technique based on array shape automatic fitting is proposed. Final-ly,the steering vector is modified by the 3D compensation technique to reduce the mismatch between the steering vector and covariance matrix,and the discontinuous problem of the target detection caused by the array shape distortion is solved. The results of numerical simulation show that,estimation of the 3D array shape and compensation for the distortion array shape can achieve 3D detection of underwaterunknown tar-get,avoid the influence of calibration source on the real-time detecting target,and is convenient for engi-neering application.【期刊名称】《电讯技术》【年(卷),期】2018(058)002【总页数】7页(P145-151)【关键词】水下目标探测;拖线阵;阵形畸变;深度信息提取;三维补偿;三维探测【作者】王思秀【作者单位】新疆财经大学计算机科学与工程学院,乌鲁木齐830012【正文语种】中文【中图分类】TN911.71 引言受重力、浮力、流体阻力、海流、平台机动等多种因素影响,拖线阵在实际应用中,其实际阵形与理想阵形存在一定偏差,对探测性能存在一定影响。
结合场景分类的近岸区域SAR舰船目标快速检测方法

Vol. 36 No. 12Dec72020第36卷第12期2020年12月信号处理Jouana-ooSogna-Paoce s ong文章编号:1003-0530(2020)12-2123-08结合场景分类的近岸区域SAR 舰船目标快速检测方法付晓雅王兆成(河北工业大学电子信息工程学院,天津300401)摘 要:合成孔径雷达(Synthetic Aperture Radar , SAR )图像场景通常较大,深层卷积网络用于SAR 舰船目标检测时通常需要密集滑窗提取子图像预处理,然后利用目标检测网络直接对子图像进行目标检测,该过程存在大量信息冗余,极大影响了目标检测效率的提升。
在近岸区域下陆地场景偏多且场景复杂,针对以上问题,本文提出了一种结合场景分类的近岸区域SAR 舰船快速目标检测方法(SC-SSD ),该方法主要包含两个阶段:场景分类 阶段和目标检测阶段。
它们分别是由场景分类网络(Convolutional Neural Network for Scene Classification ,SC-CNN ) 和目标检测网络(Singe Shot Detector ,SSD )构成。
其中SC-CNN 可以快速粗略筛选出可能包含舰船的子图像,然后将筛选出的子图像输入到SSD 网络中实现精细化的舰船目标检测。
基于高分辨率SAR 舰船检测数据集AIR-SARShip-C.0的实验结果表明,提出方法相比于传统舰船检测方法,在保持较高的检测精度的同时,具有明显更快的检测速度。
关键词:合成孔径雷达图像;场景分类;舰船目标检测中图分类号:TN957.51 文献标识码:A DOI : 10. 16798/j. issn. 1003-0530. 2020.12.019引用格式:付晓雅,王兆成.结合场景分类的近岸区域SAR 舰船目标快速检测方法[J ].信号处理,2020, 36(12) : 2123-2130. DOI : 10. 16798/j. issn. 1003-0530.2020.12.019.Reference format : Fu Xiaoya ,Wang Zhaocheng. SAR Ship Target Rapid Detection Method Combined with Scene Cmssifi- cation in the Inshore Region [ J ]. Journal of Signal Processing ,2020,36(12) : 2123-2130. DOI : 10. 16798/j. issn. 10030530.2020.12.019.SAR Ship Target Rapid Detection Method Combiner withSceee Classidcation in the Inshore RegionFu Xiaoyy Wang Zhaocheng(School of Electronics and Information Engineering ,Hebei University of Technology ,Tianjin 300401,China)Abshraeh : SyniheiocApeaiuaeRadaa ( SAR ) omagesceneosusua e yeaage , deep coneoeuioonaeneiwoak ooaSARshop iaagei detection usua/y requires dense sliding window to extract sub-image pre-processing ,and then use the target detection net work to directly target detection sub-image ,the process has a large number of iformation redundancy ,which greatly a/ectsthe efficiency of target detection. In the inshore region , there are many land scenes and complex scenes ,for the aboveproblems ,this paper proposes a fast target detection method ( SC-SSD ) for SAR ships in the near-shore region combinedwoih sceneceassooocaioon , whoch maoneyconsosisooiwosiages : scenecea s ooocaioon siageand iaageideiecioon siage.TheyconsosiooConeoeuioonaeNeuaaeNeiwoak ooaSceneCea s ooocaioon ( SC-CNN ) and SongeeShoiDeiecioa ( SSD ) , aespecioeeey.TheSC-CNNcan quockeyand coaaseeyooeieaouiihesub-omagesihaimayconiaon shops , and ihen onpuiiheooeieaed sub-oma-收稿日期:2020-10-12"修回日期:2020-12-30基金项目:国家自然科学基金(62001155)2124信号处理第36卷ges to the SSD network to realize fine-coined ship target detection.The experimental results based on the high-resolution SAR ship detection dataset AIR-SARShip-1.0show that the proposed method X significantly faster than the WadiXonal ship detection method while maintaining a higher detection accuracy.Key words:SAR image;scene classification;ship target detection1引言合成孔径雷达(Synthetic Aperture Radar,SAR)是一种主动式的微波成像传感器,具有不受任何天气条件限制,全天时,全天候,作用距离远的技术优势,在军事和民用领域发挥着重要的作用*1+)其中,港口和海上区域的舰船检测是一个重要的研究方向,对SAR图像舰船进行有效的检测有利于海上运输管理,渔业管理,舰船油污探测等[2])传统的SAR图像舰船目标检测方法包括两个步骤:检测,鉴别。
稀疏距离扩展目标自适应检测及性能分析

第39卷第7期自动化学报Vol.39,No.7 2013年7月ACTA AUTOMATICA SINICA July,2013稀疏距离扩展目标自适应检测及性能分析魏广芬1苏峰2简涛2摘要在球不变随机向量杂波背景下,研究了稀疏距离扩展目标的自适应检测问题.基于有序检测理论,利用协方差矩阵估计方法,分析了自适应检测器(Adaptive detector,AD).其中,基于采样协方差矩阵(Sample covariance matrix,SCM)和归一化采样协方差矩阵(Normalized sample covariance matrix,NSCM),分别建立了AD-SCM和AD-NSCM检测器.从恒虚警率特性和检测性能综合来看,AD-NSCM的性能优于AD-SCM和已有的修正广义似然比检测器.最后,通过仿真实验验证了所提方法的有效性.关键词稀疏距离扩展目标,自适应检测,采样协方差矩阵,归一化采样协方差矩阵,有序统计量引用格式魏广芬,苏峰,简涛.稀疏距离扩展目标自适应检测及性能分析.自动化学报,2013,39(7):1126−1132DOI10.3724/SP.J.1004.2013.01126Sparsely Range-spread Target Detector and Performance AssessmentWEI Guang-Fen1SU Feng2JIAN Tao2Abstract In the background where the clutter is modeled as a spherically invariant random vector,the adaptive detection of sparsely range-spread targets is addressed.By exploiting the order statistics and the covariance matrix estimators,the adaptive detector(AD)is assessed.Herein,the detectors of AD-SCM and AD-NSCM are proposed based on the sample covariance matrix(SCM)and normalized sample covariance matrix(NSCM),respectively.In terms of constant false alarm rate properties and detection performance,the AD-NSCM outperforms the AD-SCM and the existing detector of modified generalized likelihood ratio.Finally,the performance assessment conducted by simulation confirms the effectiveness of the proposed detectors.Key words Sparsely range-spread target,adaptive detection(AD),sample covariance matrix(SCM),normalized sample covariance matrix(NSCM),order statisticsCitation Wei Guang-Fen,Su Feng,Jian Tao.Sparsely range-spread target detector and performance assessment.Acta Automatica Sinica,2013,39(7):1126−1132低分辨率雷达的目标尺寸小于距离分辨率,这种目标常称之为点目标[1].通过采用脉冲压缩技术,高分辨率雷达能够在空间上把一个目标分解成许多散射点[2−3],目标回波在雷达径向上的多个散射点分布在不同的距离分辨单元中,形成距离扩展目标[4].在许多情况下,距离扩展目标的散射点密度是稀疏的,可将这种目标简称为“稀疏距离扩展目标”.目前,高斯背景下的距离扩展目标检测已取得一定进收稿日期2011-12-28录用日期2012-08-27Manuscript received December28,2011;accepted August27, 2012国家自然科学基金(61174007,61102166),山东省优秀中青年科学家科研奖励基金(BS2010DX022)资助Supported by National Natural Science Foundation of China (61174007,61102166)and the Scientific Research Founda-tion for Outstanding Young Scientists of Shandong Province (BS2010DX022)本文责任编委韩崇昭Recommended by Associate Editor HAN Chong-Zhao1.山东工商学院信息与电子工程学院烟台2640052.海军航空工程学院信息融合技术研究所烟台2640011.School of Information and Electronics,Shandong Institute of Business and Technology,Yantai2640052.Research Insti-tute of Information Fusion,Naval Aeronautical and Astronauti-cal University,Yantai264001展,其中,针对估计参数空间过大的问题,文献[5]提出了一种无需辅助数据的检测器,简称为修正的广义似然比检验(Modified generalized likelihood ratio test,MGLRT)检测器,其在高斯背景下是有界恒虚警率(Constant false alarm rate,CFAR)的.但在高距离分辨率的条件下,背景杂波呈现出诸多的非高斯特性[1],高斯背景下获得的检测器已无法有效检测目标.在非高斯背景下,文献[6]研究了已知杂波协方差矩阵条件下的距离扩展目标检测;而通过利用不含目标信号的辅助数据,文献[7]和文献[8]分别针对距离扩展目标和距离–多普勒二维分布式目标展开了自适应检测研究.需要指出的是,以上自适应检测方法[7−8]都是基于辅助数据的.当无法获得满足条件的辅助数据时,实现非高斯背景下距离扩展目标的自适应检测具有重要意义.文献[9]基于迭代估计方法实现了自适应检测,但迭代估计计算量较大,如何在保证性能的同时减小计算量,也是值得探讨的问题.7期魏广芬等:稀疏距离扩展目标自适应检测及性能分析1127稀疏距离扩展目标的散射点只占据目标距离扩展范围的一部分,与含纯杂波的距离分辨单元幅值相比,含目标散射点的距离分辨单元幅值明显更高,这就为实现目标的自适应检测提供了条件.本文针对非高斯杂波中的稀疏距离扩展目标检测问题,在不需要辅助数据的条件下,首先,采用有序统计检测理论和协方差矩阵估计方法,粗略估计目标散射点单元集合;然后,进一步利用适当估计方法获得协方差矩阵的精确估计,设计了自适应检测器(Adaptivedetector,AD),并通过仿真实验验证了检测器的有效性.1问题观测数据来源于N个阵元的线性阵列天线,需跨过K个可能存在目标的距离分辨单元z t,t=1,···,K,判决一个距离扩展目标的存在与否.假设可能的目标完全包含在这些数据中,并且忽略目标距离走动的问题.在杂波背景下,待解决的检测问题可由以下二元假设检验公式来表达.H0:z t=c t,t=1,···,KH1:z t=αt p+c t,t=1,···,K(1)其中,p=(1,e jφ,e j2φ,···,e j(N−1)φ)T/√N表示已知单位导向矢量,即p H p=1,这里(·)H表示共轭转置,φ表示相移常量,(·)T表示转置,αt,t=1,···,K是反映目标幅度的未知参数.非高斯杂波可用球不变随机向量建模[10],由于中心极限定理在较小区域的杂波范围内仍是有效的,球不变随机向量可以表示为两个分量的乘积:一个是反映受照区域反射率的时空“慢变化”纹理分量,另一个是变化“较快”的“散斑”高斯过程.那么,距离分辨单元t的N维杂波向量c t为c t=√τt·ηt,t=1,···,K(2)其中,ηt=(ηt(1),ηt(2),···,ηt(N))T是零均值协方差矩阵为Σ的复高斯随机向量,非负的纹理分量τt与ηt相互独立,其用来描述杂波功率在不同距离分辨单元间的起伏,且服从未知分布fτ.另外,杂波协方差矩阵结构Σ可以表示为Σ=E{ηt ηHt}(3)距离扩展目标完全包含在K个距离分辨单元的滑窗中,假设一个等效散射点最多只占据一个距离分辨单元,即目标等效散射点数目与其所占据的距离分辨单元数目是相等的.通常目标散射点是稀疏分布的,与含纯杂波的距离分辨单元相比,有散射点的距离分辨单元幅值往往更高.含目标等效散射点的距离分辨单元数目用h0表示,而其所对应的距离分辨单元下标用集合Θh表示.为了简化分析,假设h0是已知的,若其未知,可利用模型阶数选择方法获得合适的估计值[11].如前所述,对距离扩展目标的检测只需在距离分辨单元Θh内进行,式(1)表示的假设检验问题可以进一步表示为H0:z t=c t,t∈ΘhH1:z t=αt p+c t,t∈Θh(4)在分布fτ未知的条件下,距离分辨单元t的杂波是条件高斯的,其相应的方差为τt.由于幅度αt 未知而向量p已知,针对不同假设,观测向量z t的联合概率密度可表示为t∈Θhf(z t|τt,H0)=t∈Θh1πNτN t det(Σ)×exp[−1τtz HtΣ−1z t](5)t∈Θhf(z t|αt,τt,H1)=t∈Θh1πNτN t det(Σ)×exp−1τt(z t−αt p)HΣ−1(z t−αt p)(6)其中,det(·)表示方阵的行列式.2检测器实现在未知集合Θh的条件下,为了获得估计的参数集合ˆΘh,这里先假设已知矩阵Σ.由于未知参数α={αt|t∈Θh}和τ={τt|t∈Θh},可利用广义似然比检验(GLRT)原理进行检测器设计[12].在矩阵Σ已知的条件下,根据GLRT原理,对于似然比中的未知参数,可用最大似然(Maximum likelihood,ML)估计进行替换,即考虑如下二元判决:maxτmaxαt∈Θhf(z t|αt,τt,H1)maxτt∈Θhf(z t|τt,H0)H1><H0T0(7)在H1假设下求得αt的ML估计为[13]ˆαt=p HΣ−1z tp HΣ−1p(8)将ˆαt代入式(7)后,可进一步在不同假设条件下求得τt的ML估计:H0:ˆτt=1Nz HtΣ−1z t(9) H1:ˆτt=1N(z t−ˆαt p)HΣ−1(z t−ˆαt p)(10)1128自动化学报39卷将式(8)∼(10)代入式(7)中,可得自然对数形式的GLRT判决为λ1=−Nt∈Θh0ln1−|p HΣ−1z t|2(z H tΣ−1z t)(p HΣ−1p)H1><H0T1(11)令w t=|p HΣ−1z t|2(z H tΣ−1z t)(p HΣ−1p)(12)值得注意的是,w t的结构类似于一个归一化匹配滤波器(权向量为Σ−1p)[14].可以看出,式(12)的分子部分p HΣ−1z t等效于给定距离分辨单元观测z t经过匹配滤波后的结果[14].而分母部分的两项z HtΣ−1z t和p HΣ−1p起到了归一化处理的作用,因此,w t是距离单元观测z t经过匹配滤波后模平方的归一化,可以看作是距离单元观测经归一化匹配滤波后的能量.由于目标完全包含在K个单元的距离滑窗中,且距离扩展目标等效散射点所占据的距离分辨单元幅值往往大于纯杂波的距离分辨单元幅值,因此,可通过归一化能量w t,t=1,···,K中最大的h0个值来确定未知集合ˆΘh.实际应用中协方差矩阵结构Σ往往是未知的,为了确定集合ˆΘh,需先对协方差矩阵结构进行估计.如前所述,纹理分量τt的分布fτ是未知的,因此,协方差矩阵结构Σ的ML估计不能通过期望最大化得到[13].本文考虑两种协方差矩阵估计方法.一种是高斯背景下的经典采样协方差矩阵(Sample covariance matrix,SCM),其可以表示为ˆΣSCM =1RRr=1y r y Hr(13)其中,y r,r=1,···,R表示可用于估计的R个数据.当R≥N时,SCM是以概率为1非奇异的,同时也是正定Hermitian矩阵[12].另外,在非高斯背景下,也常常利用辅助数据获得归一化采样协方差矩阵(Normalized sample covariance matrix, NSCM),可以表示为ˆΣNSCM =1RRr=1Ny Hry ry r y Hr(14)与文献[9]类似,针对稀疏距离扩展目标的自适应检测,AD检测器的实现分为如下三个步骤.步骤1.基于SCM或NSCM方法,利用K个待检测单元的观测数据获得初步估计矩阵ˆΣ1,进一步将估计矩阵ˆΣ1代入式(12)中,可得到初步估计ˆw(1)t.对ˆw(1)t,t=1,···,K按升序排列,可得如下有序序列:0≤ˆw(1)(1)≤···≤ˆw(1)(t)≤···≤ˆw(1)(K)≤1(15)步骤2.考虑有序序列的K−h0个最小值(即ˆw(1)(t),t=1,···,K−h0),并用Ωh表示相应距离分辨单元下标的集合.为了获得可逆的估计矩阵,需满足K−h0≥N.根据之前的分析,集合Ωh中的距离分辨单元极可能只包含纯杂波,故可以利用Ωh0对应的距离分辨单元观测值,精确估计矩阵Σ,并采用与初步估计中相同的估计方法(SCM或NSCM),进一步获得较为精确的协方差矩阵结构估计ˆΣ2.利用ˆΣ2代替式(12)中的未知矩阵Σ,得到w t的精确估计值用ˆw(2)(t)表示.对ˆw(2)(t),t=1,···,K按升序排列,可得如下有序序列:0≤ˆw(2)(1)≤···≤ˆw(2)(t)≤···≤ˆw(2)(K)≤1(16)考虑有序序列的h0个最大值(即ˆw(2)(t),t=K−h0+1,···,K),并用ˆΘh表示相应距离分辨单元下标的集合.步骤3.将距离分辨单元下标的集合ˆΘh和协方差矩阵的精确估计ˆΣ2代入式(11)中,获得自适应检测器AD的检测统计量可以表示为λ2=−NKt=K−h0+1ln(1−ˆw(2)(t))=−Nt∈ˆΘhln[1−|p HˆΣ−12z t|2(z H tˆΣ−12z t)(p HˆΣ−12p)]H1><H0T2(17)需要说明的是,在存在目标散射点的情况下,步骤1的初步估计矩阵不可避免地引入了估计误差,虽然这种误差在步骤2中得到了一定的抑制,但它仍将影响后续精确估计矩阵的精度.在存在辅助数据的前提下,为了获得良好的检测性能,一般要求辅助数据个数不小于阵元数N的两倍[15].在待检测单元数K不变的情况下,可利用的纯杂波单元数(K−h0)将随着散射点个数的增加而减小,因此,此处需等价满足(K−h0)≥2N.进一步考虑到步骤1中散射点单元所引起的估计误差,实际应用中可能需要更大的(K−h0)/N值以弥补步骤1中导致的性能损失,具体取值将在接下来的性能评估中给出.由于采用不同的估计方法会获得不同的自适应检测器,在这里,我们分别将采用SCM和NSCM估计方法获得的相应检测器简称为AD-SCM和AD-NSCM.由于本文的自适应检测器中ˆΘh和ˆΣ2均受到协方差矩阵估计方法的影响,因此,有必要评估自适应距离扩展目标检测器的CFAR特性,这将在接下来的性能分析中进行.7期魏广芬等:稀疏距离扩展目标自适应检测及性能分析1129 3性能评估本节对稀疏距离扩展目标自适应检测器AD-SCM和AD-NSCM进行了CFAR特性和检测性能评估,并与无需辅助数据的MGLRT检测器[5]进行了比较分析.利用Toeplitz矩阵对Σ进行建模,具体采用指数相关结构,在杂波一阶相关系数为γ的条件下,第m行第n列的矩阵元素为[Σ]m,n=γ|m−n|,1≤m,n≤N(18)利用Γ分布对纹理分量的分布fτ进行建模:fτ(x)=LbLΓ(L)x L−1e−(L b)x,x≥0(19)其中,Γ(·)是Gamma函数,均值b代表了平均杂波功率;参数L表示分布fτ的非高斯拖尾特征,具体来说,随着L的减小,函数fτ的拖尾将增大,而杂波的非高斯尖峰程度将增大.采用蒙特卡罗方法计算相应的检测概率P d和虚警概率P fa.根据前面的假设,在所有距离分辨单元均存在杂波的条件下,目标等效散射点只存在于h0个距离分辨单元中,且一个等效散射点最多只占据一个距离分辨单元.在所有K个距离分辨单元上,每个单元的目标或杂波的平均功率分别用σ2s 或σ2c表示.对于存在目标散射点的距离分辨单元(t∈Θh),用零均值独立复高斯变量对等效散射点建模,即目标散射点幅度在不同距离分辨单元间瑞利起伏;相应的方差表示为E{|αt|2}=εtσ2sK(εt表示单个散射点占目标总能量的比率).由|αt|2,t=1,···,K的独立性可知,检测性能与散射点在待检测单元中的位置无关.几种典型的散射点分布模型如表1所示.其中,Model 1中的目标能量等量分布在h0个距离分辨单元范围内;Model2∼4中某个距离分辨单元具有大部分能量,而剩下的能量在其余距离分辨单元中等量分布.Model5相当于点目标,是Model2∼4的极端特例.输入信杂比(Signal to clutter ratio,SCR)定义为K个距离分辨单元内的平均信杂比,即SCR=σ2sσ2cp HΣ−1p(20)为了便于CFAR特性评估,需针对杂波功率水平(对应于b)、尖峰程度(对应于L)和协方差矩阵结构(对应于γ)的不同情况,分析检测器的检测阈值与虚警概率间的关系.相关研究表明[9],在非高斯杂波下MGLRT是非CFAR的,即高斯背景下获得的MGLRT检测器不适用于非高斯背景.为了便于比较,在K=15,h0=3,N=2,L=0.1,1,γ=0,0.5,0.9和b=1,10条件下,图1和图2分别给出了AD-SCM和AD-NSCM的检测阈值(De-tection threshold)与虚警概率(False alarm prob-ability)的关系曲线.图1表明,AD-SCM检测器对杂波协方差矩阵结构和功率水平具有自适应性,但对杂波尖峰不具有适应能力.而图2说明,AD-NSCM对杂波尖峰和杂波功率水平具有CFAR特性,但其检测阈值仍受协方差矩阵结构的轻微影响.综合来看,AD-NSCM的检测阈值在不同杂波条件下的鲁棒性更好.图1K=15,N=2,L=0.1,1,γ=0,0.5,0.9,b=1,10,h0=3时,AD-SCM的CFAR特性曲线Fig.1CFAR curves of AD-SCM for K=15,N=2, L=0.1,1,γ=0,0.5,0.9,b=1,10,h0=3表1不同散射点分布模型的εt值Table1Values ofεt for typical scatters models目标距离分辨单元12···h0Model11h01h01h01h0Model20.50.5h0−10.5h0−10.5h0−1Model30.90.1h0−10.1h0−10.1h0−1Model40.990.01h0−10.01h0−10.01h0−1Model510001130自动化学报39卷图2K=15,N=2,L=0.1,1,γ=0,0.5,0.9,b=1,10,h0=3时,AD-NSCM的CFAR特性曲线Fig.2CFAR curves of AD-NSCM for K=15,N=2, L=0.1,1,γ=0,0.5,0.9,b=1,10,h0=3接下来分析AD检测器的检测性能.图3给出了MGLRT、AD-SCM和AD-NSCM的性能曲线.可以看出,AD-NSCM的检测性能最优,MGLRT 其次,而AD-SCM的检测性能最差.从以上分析综合来看,与MGLRT和AD-SCM相比,AD-NSCM 在CFAR特性和检测性能方面均具有一定的优势.下文将重点对AD-NSCM的检测性能展开分析.图3K=15,N=2,L=1,γ=0.9,h0=3,P fa=10−4, Model1时,MGLRT,AD-SCM和AD-NSCM的检测性能曲线Fig.3Detectability curves of MGLRT,AD-SCM and AD-NSCM for K=15,N=2,L=1,γ=0.9,h0=3,P fa=10−4,Model1首先,针对表1中5种不同模型,图4评估了散射点能量分布对AD-NSCM检测性能的影响.可以看出,随着距离分辨单元间散射点能量分布的均匀性增加,检测性能逐渐改善.为了便于分析,下文中主要针对Model1模型.另外,在不同的散射点密度条件下,图5分析了AD-NSCM检测性能.由图5可知,当h0<7时,协方差矩阵结构的估计误差较小,其对检测性能的影响也较小,当散射点数目增加时,检测器可利用的目标能量增大,AD-NSCM的检测性能得到一定的改善.当h0≥7时,协方差矩阵结构的估计误差影响较大,当散射点数目增加时,进行矩阵估计所用的观测数据量减少,估计矩阵的误差加大,导致较为严重的检测损失,且损失量高于增加散射点数目所获得的性能增益,并引起总检测性能的退化.综合来看,当h0<K/2时,AD-NSCM 的检测性能较好.图4K=15,N=2,L=1,γ=0.9,h0=3,P fa=10−4, Model1∼5对应的AD-NSCM检测性能曲线Fig.4Detectability curves of AD-NSCM for K=15, N=2,L=1,γ=0.9,h0=3,P fa=10−4,Model1∼5图5K=15,N=2,L=1,γ=0.9,P fa=10−4,Model 1时,h0=2,4,6,7,8,10,12对应的AD-NSCM检测性能曲线Fig.5Detectability curves of AD-NSCM for K=15, N=2,L=1,γ=0.9,P fa=10−4,Model1,h0=2,4,6,7,8,10,12在不同杂波尖峰条件下,图6给出了AD-NSCM检测性能.由图6可知,随着L的减小,杂波尖峰程度增大,AD-NSCM的检测性能有所改善.图7给出了不同杂波相关性对应的检测性能曲线.可以看出,杂波一阶相关系数的变化对检测性能几乎没有影响,说明AD-NSCM对杂波相关性7期魏广芬等:稀疏距离扩展目标自适应检测及性能分析1131的变化具有良好适应性.图8进一步分析了阵元数变化(N =2,4,6,8)对AD-NSCM 检测性能的影响.可以看出,在阵元数N ≤4的条件下,当N 增加时,检测性能有所提高;而在N >4的条件下,当N 增加时,检测性能反而有所下降.可能的原因是,当进行矩阵估计所用的观测数据量不变时(R =K −h 0=12),N 的增加会导致协方差矩阵维数变大,待估参量的数目增加,估计精度下降,并直接引起检测性能的退化.综合来看,当K −h 0≥3N 时,AD-NSCM 的检测性能较好.图6K =15,N =2,γ=0.9,h 0=3,P fa =10−4,Model 1时,L =0.5,1,2,10对应的AD-NSCM 检测性能曲线Fig.6Detectability curves of AD-NSCM for K =15,N =2,γ=0.9,h 0=3,P fa =10−4,Model 1,L =0.5,1,2,10图7K =15,N =2,L =1,h 0=3,P fa =10−4,Model 1时,γ=0,0.5,0.9对应的AD-NSCM 检测性能曲线Fig.7Detectability curves of AD-NSCM for K =15,N =2,L =1,h 0=3,P fa =10−4,Model 1,γ=0,0.5,0.94结论本文研究了非高斯杂波中的稀疏距离扩展目标检测问题.在不需要辅助数据的条件下,基于SCM 和NSCM 估计器,分别建立了AD-SCM 和AD-NSCM 检测器.从CFAR 特性和检测性能综合来看,AD-NSCM 的性能优于AD-SCM 和MGLRT.对于典型的非高斯杂波环境,随着杂波尖峰程度的增大,AD-NSCM 的检测性能得到提高,且其对杂波相关性的变化也具有良好适应性.另外,对于h 0<K/2的稀疏距离扩展目标,在K −h 0≥3N 条件下,AD-NSCM 能获得满意的检测性能.需要说明的是,与文献[9]中的检测器相比,AD-NSCM 虽然减小了计算量,但也牺牲了部分CFAR 特性.如何减小检测器对散射点信息的依赖性,是下一步需要研究的问题.图8K =15,L =1,γ=0.9,h 0=3,P fa =10−4,Model 1时,N =2,4,6,8对应的AD-NSCM 检测性能曲线Fig.8Detectability curves of AD-NSCM for K =15,L =1,γ=0.9,h 0=3,P fa =10−4,Model 1,N =2,4,6,8References1Zhou Yu,Zhang Lin-Rang,Liu Xin,Liu Nan.Adap-tive detection based on Bayesian approach in heteroge-neous environments.Acta Automatica Sinica ,2011,37(10):1206−1212(周宇,张林让,刘昕,刘楠.非均匀杂波环境下基于贝叶斯方法的自适应检测.自动化学报,2011,37(10):1206−1212)2He Chu,Liu Ming,Feng Qian,Deng Xin-Ping.PolIn-SAR image classification based on compressed sensing and multi-scale pyramid.Acta Automatica Sinica ,2011,37(7):820−827(何楚,刘明,冯倩,邓新萍.基于多尺度压缩感知金字塔的极化干涉SAR 图像分类.自动化学报,2011,37(7):820−827)3Zhu Yi-Long,Fan Hong-Qi,Lu Zai-Qi,Fu Qiang.A radar target maneuver detection algorithm based on the one-dimensional high resolution Doppler profile.Acta Automat-ica Sinica ,2011,37(8):901−914(祝依龙,范红旗,卢再奇,付强.基于高分辨一维多普勒像的雷达目标机动检测算法.自动化学报,2011,37(8):901−914)4Jian T,He Y,Su F,Qu C W,Ping D F.High resolu-tion radar target adaptive detector and performance assess-ment.Journal of Systems Engineering and Electronics ,2011,22(2):212−2185Gerlach K,Steiner M J.Adaptive detection of range dis-tributed targets.IEEE Transactions on Signal Processing ,1999,47(7):1844−18511132自动化学报39卷6Gerlach K.Spatially distributed target detection in non-Gaussian clutter.IEEE Transactions on Aerospace and Elec-tronic Systems,1999,35(3):926−9347Conte E,De Maio A,Ricci G.CFAR detection of distributed targets in non-Gaussian disturbance.IEEE Transactions on Aerospace and Electronic Systems,2002,38(2):612−6218Bon N,Khenchaf A,Garello R.GLRT subspace detection for range and Doppler distributed targets.IEEE Transac-tions on Aerospace and Electronic Systems,2008,44(2): 678−6969Jian Tao,Su Feng,He You,Li Bing-Rong,Gu Xue-Feng.Distributed target detection without secondary data.Acta Aeronautica et Astronautica Sinica,2011,32(8): 1542−1547(简涛,苏峰,何友,李炳荣,顾雪峰.无需辅助数据的分布式目标自适应检测器.航空学报,2011,32(8):1542−1547)10Jian T,He Y,Su F,Qu C W,Gu X F.Performance charac-terization of two adaptive range-spread target detectors for unwanted signal.In:Proceedings of the9th International Conference on Signal Processing.Beijing,China:IEEE, 2008.2326−232911Gini F,Bordoni F,Farina A.Multiple radar targets de-tection by exploiting induced amplitude modulation.IEEE Transactions on Signal Processing,2004,52(4):903−913 12Kay S M.Fundamentals of Statistical Signal Processing, vol.2:Detection Theory.New York:Prentice-Hall,1998.196−26013Kay S M.Fundamentals of Statistical Signal Processing, vol.1:Estimation Theory.New York:Prentice-Hall,1993.157−21814Kraut S,Scharf L L,McWhorter L T.Adaptive subspace detectors.IEEE Transactions on Signal Processing,2001, 49(1):1−1615Reed I S,Mallett J D,Brennan L E.Rapid convergence rate in adaptive arrays.IEEE Transactions on Aerospace and Electronic Systems,1974,10(6):853−863魏广芬博士,山东工商学院副教授.2005年获得大连理工大学机械电子工程专业工学博士学位.主要研究方向为传感器检测与信号处理理论及技术.本文通信作者.E-mail:*******************(WEI Guang-Fen Ph.D.,associateprofessor at Shandong Institute of Busi-ness and Technology.She received her Ph.D.degree from Dalian University of Technology in2005.Her research in-terest covers theory and technology of sensor detection and signal processing.Corresponding author of this paper.)苏峰博士,海军航空工程学院信息融合技术研究所讲师.主要研究方向为雷达信号检测与信号处理.E-mail:*****************(SU Feng Ph.D.,lecturer at NavalAeronautical and Astronautical Univer-sity.His research interest covers radarsignal detection and signal processing.)简涛博士,海军航空工程学院信息融合技术研究所讲师.主要研究方向为雷达信号检测与信号处理.E-mail:********************.cn(JIAN Tao Ph.D.,lecturer at NavalAeronautical and Astronautical Univer-sity.His research interest covers radarsignal detection and signal processing.)。
IEEESignalProcessingSociety:IEEE信号处理学会
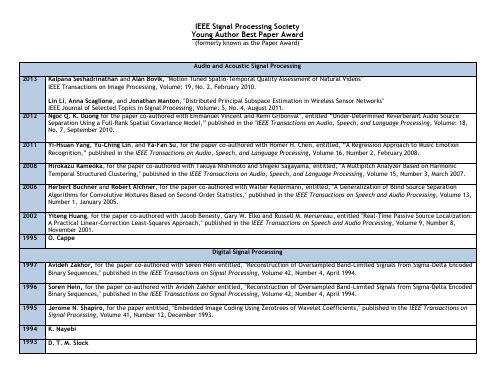
Jerome N. Shapiro, for the paper entitled, "Embedded Image Coding Using Zerotrees of Wavelet Coefficients," published in the IEEE Transactions on Signal Processing, Volume 41, Number 12, December 1993.
Digital Signal Processing
Avideh Zakhor, for the paper co-authored with Søren Hein entitled, "Reconstruction of Oversampled Band-Limited Signals from Sigma-Delta Encoded Binary Sequences," published in the IEEE Transactions on Signal Processing, Volume 42, Number 4, April 1994.
复合高斯海杂波背景雷达目标检测算法

学校代码10701分类号TN95学号1702110045密级公开西安电子科技大学博士学位论文复合高斯海杂波背景雷达目标检测算法作者姓名:薛健一级学科:信息与通信工程二级学科:信号与信息处理学位类别:工学博士指导教师姓名、职称:水鹏朗教授学院:电子工程学院提交日期:2020年06月Radar target detection methods in compound-Gaussian sea clutterA Dissertation submitted toXIDIAN UNIVERSITYin partial fulfillment of the requirementsfor the degree of Doctor of Philosophyin Electrical EngineeringByXue JianSupervisor:Shui Penglang Title:ProfessorJune2020摘要摘要雷达在对海探测时会不可避免地接收到来自海面和各类目标的散射信号,海上目标种类繁多且海面回波特性复杂多变,因此在复杂海杂波背景下有效检测海面目标信号一直是雷达领域研究的热点。
低分辨率或者大擦地角的海杂波往往使用高斯模型描述,然而随着分辨率的提高或者擦地角的减小,海杂波不再服从高斯模型,而是表现出强烈的非高斯特性。
传统针对高斯模型的自适应相干检测器在非高斯海杂波背景下会出现高的虚警概率或者低的检测概率。
再者,当在非均匀海杂波环境中用于估计杂波协方差矩阵的参考单元数量不足时,自适应相干检测器的检测性能会出现严重退化。
因此,为了在非高斯非均匀海杂波背景下提高雷达对目标的检测能力,本文进行了如下的工作:1、针对非高斯海杂波具有的重拖尾现象和参考单元不足时自适应相干检测器性能损失严重的问题,研究了协方差矩阵未知但具有斜对称结构的复合高斯海杂波背景下雷达点目标自适应相干检测方法。
在广义帕累托分布和逆高斯纹理复合高斯分布杂波下,基于两步广义似然比检验(Generalized Likelihood Ratio Test,GLRT)、Rao检验和Wald检验分别推导了相应的自适应相干检测器。
基于二次协方差矩阵的频谱感知算法

基于二次协方差矩阵的频谱感知算法韩仕鹏;赵知劲;戴绍港【摘要】协方差矩阵频谱感知算法不需要主用户先验信息,易于实现,但是,低信噪比时,协方差矩阵元素间差异变小,检测性能有待提高.为此,利用噪声的二次协方差矩阵方差大、主用户信号的二次协方差矩阵元素的相关性增强等特点,提出利用二次协方差矩阵方差和对角线元素的判决统计量,推导出判决门限.AWGN信道和Rayleigh信道下的仿真结果表明:新方法在低虚警概率条件下,检测性能有明显提升,同时抗噪声不确定度和抗频偏性能均有改进.【期刊名称】《杭州电子科技大学学报》【年(卷),期】2019(039)003【总页数】6页(P10-14,20)【关键词】认知无线电;频谱感知;二次协方差矩阵;低虚警概率【作者】韩仕鹏;赵知劲;戴绍港【作者单位】杭州电子科技大学通信工程学院,浙江杭州 310018;杭州电子科技大学通信工程学院,浙江杭州 310018;杭州电子科技大学通信工程学院,浙江杭州310018【正文语种】中文【中图分类】TN9250 引言认知无线电是一种提高频谱利用率的新技术,频谱感知[1]是认知无线电关键技术之一。
经典的频谱感知方法包括能量检测法(Energy Detection,ED)[2]、匹配滤波器检测法(Matching Filter Detection,MFD)[3]和循环平稳特征检测法(Cyclostationary Feature Detection,CFD)[4]。
能量检测法计算复杂度低,但需要得到噪声功率,对噪声不确定性敏感;匹配滤波器检测法可以最大化检测概率,但需要知道完整的主用户先验信息,实际应用难实现;循环平稳特征检测法有更好的盲检测性能,但算法复杂度高,信号检测时间长。
为了改进上述方法,提出了基于协方差矩阵频谱感知算法。
协方差矩阵频谱感知算法不需要主用户先验信息,计算简单,是一类更有效的频谱感知算法[5]。
文献[6]提出最大特征值检测(Maximum Eigenvalue Detection,MED)算法,采用样本协方差矩阵的最大特征值作为检验统计量,随机矩阵理论(Random Matrix,RMT)方法设置阈值,不需要信号的先验消息,可有效避免噪声波动。
A_glimpse_into_the_future_of_ID

a glimpse into the future of idby Tim Bass<bass@>Tim Bass is the CEO and managing director for Silk Road, a consulting business inWashington, D.C. specializing in network design, management, and security.and Dave Gruber<david.gruber@>Dave Gruber, Lt. Col., is the communications squadron commander at Hickam AFB,Hawaii.Cyberspace is a complex dimension of both enabling and inhibiting data flows in electronic data networks. Current-generation intrusion-detection systems (IDSes) are not technologically advanced enough to create the situational knowledge required to monitor and protect these networks effectively. Next-generation IDSes will fuse data, combining short-term sensor data with long-term knowledge databases to create cyberspace situational awareness. This article offers a glimpse into the foggy crystal ball of future ID systems.Before diving into the technical discussion, we ask the reader to keep in mind the generic model of a datagram traversing the Internet. Figure 1 illustrates an IP datagram moving in a store-and-forward environment from source to destination; it is routed on the basis of a destination address with an uncertain source address decrementing the datagram time-to-live (TTL) at every router hop[1]. The datagram is routed through major Internet and IP transit providers.There is a striking similarity between the transit of a datagram on the Internet and an airplane through airspace, between future network management and air traffic control (ATC). At a very high abstract level, the concepts used to monitor objects in airspace apply to monitoring objects in networks. The Federal Aviation Administration (FAA) divides airspace management into two distinct entities. On the one hand, local controllers guide aircraft into and out of the airspace surrounding an airport. Their job is to maintain awareness of the location of all aircraft in their vicinity, ensure properseparation, identify threats to aircraft, and manage the overall safety of passengers. Functionally, this is similar to the role of network controllers, who must control the environment within their administrative domains. The network administrator must ensure that the proper ports are open and that the information is not delayed, that collisions are kept to a minimum, and that the integrity of the delivery systems is not compromised.Figure 1. Network object flow pathThis is similar to the situational awareness required in current-generation ATC. The FAA controls the routes between source and destination (airports), and airport authorities control the airports (as both router and host), maintaining the safety of the payload (passengers) and the transport agent (the airplane). The success of ATC depends on the fusion of data and information from short-term and long-term knowledge sources to create airspace situational awareness. This role is remarkably similar to network operators in future complex internetwork environments. As an example, consider the FAA and the National Weather Service as they monitor the weather. A change in environment can cause the FAA to make changes in air routes and landing criteria. This is similar to service providers keeping an eye out for unfavorable conditions in networks — for example, the loss of a major Internet transit network; severe congestion on major interdomain links; or attacks against routers, computers, and information. The same data-fusion concepts are shared across the airspace management functions and organizations. We expect that a similar fusion paradigm will occur with network management, Internet Traffic Control (ITC), and future intrusion-detection systems. Of course, this will not occur overnight (and may never become as comprehensive as ATC), but the analogy does help provide a glimpse into the future of ID.Figure 2. Hierarchy of IDS data-fusion inferencesFigure 2 illustrates the levels of situational knowledge inference required to support both the air traffic controller and the network manager. Sophisticated electronics must identify objects against a noise-saturated environment, track the objects, calculate their velocity, and estimate the projected threat. These are nontrivial technical requirements.Figure 3. Cyberattack with multiple sources andtargetsFigure 4. Intrusion-detection data fusionExperienced network-security professionals generally agree that current-generation intrusion-detection systems are not technically advanced enough to detect multiple, complex non-signature-based cyberattacks, illustrated in Figure 3. Next-generation cyberspace IDSes require the fusion of data from heterogeneous distributed network sensors, modeled in Figure 4.Historical Intrusion Detection SystemsWe offer a brief review of the state of the art of current-generation ID systems, from our recent ACM paper[2].Internet ID systems historically examine operating-system audit trails and Internet traffic[5, 6] to help insure the availability, confidentiality, and integrity of critical information infrastructures. ID systems attempt to protect information infrastructures against denial-of-service attacks, unauthorized disclosure of information, and the modification or destruction of data. The automated detection and immediate reporting ofthese events are required to respond to information attacks against networks and computers. The basic approaches to intrusion detection today may be summarized as: known pattern templates, threatening behavior templates, traffic analysis,statistical-anomaly detection, and state-based detection. These systems have not matured to a level where sophisticated network-centric attacks are reliably detected, verified, and assessed.[2]Computer intrusion-detection systems were introduced in the mid-1980s to complement conventional approaches to computer security. IDS designers often cite Denning's[5] 1987 intrusion-detection model built on host-based subject profiles, systems objects, audit logs, anomaly records, and activity rules. The underlying ID construct is arules-based pattern-matching system whereby audit trails are matched against subject profiles to detect computer misuse based on logins, program executions, and file access. The subject-anomaly model was applied in the design of many host-based IDSes, among them Intrusion Detection Expert System (IDES)[7]; Network Intrusion Detection Expert System (NDIX)[9]; and Wisdom & Sense (W&S), Haystack, and Network Anomaly Detection and Intrusion Reporter (NADIR) [10]. Other ID systems are also based on the Denning model; an excellent survey of them may be found in Mukherjee et al.[6]. The basic detection algorithms used in these systems include:weighted functions to detect deviations from normal usage patterns qcovariance-matrix—based approaches for normal usage profiling qrules-based expert-systems approach to detect security eventsqThe second-leading technical approach to present-day intrusion detection is themulti-host network-based IDS. Heberlein et al. extended the Denning model to traffic analysis on Ethernet-based networks with the Network Security Monitor (NSM) framework[11]. This was further extended with the Distributed Intrusion Detection System (DIDS), which combined host-based intrusion detection with network-traffic monitoring[6, 8]. Current commercial IDSes such as Real Secure by ISS and Computer Misuse Detection System (CMDS) by SAIC have distributed architectures using either rules-based detection, statistical-anomaly detection, or both.A significant challenge remains for IDS designers to fuse sensor, threat, and situational information from numerous heterogeneous distributed agents, system managers, and databases. Coherent pictures that can be used by network controllers to visualize and evaluate the security of cyberspace is required. Next, we review the basic principles of the art and science of multisensor data fusion applied to future ID systems in Bass[2] and Bass[3] to create highly reliable next-generation intrusion-detection systems that identify, track, and assess complex threat situations.Internet Situational Data FusionIn a typical military command-and-control (C2) system, data-fusion sensors are used to observe electromagnetic radiation, acoustic and thermal energy, nuclear particles, infrared radiation, noise, and other signals. In cyberspace ID systems the sensors are different because the environmental dimension is different. Instead of a missile launch and supersonic transport through the atmosphere, cyberspace sensors observeinformation flowing in networks. However, just as C2 operational personnel are interested in the origin, velocity, threat, and targets of a warhead, network-security personnel are interested in the identity, rate of attacks, threats, and targets of malicious intruders and criminals[2]. Input into next-generation IDSes consists of sensor data, commands, and a priori data from established databases. For example, the system input would be data from numerous distributed packet sniffers, system log files, SNMP traps and queries, signature-based ID systems, user-profile databases, system messages, threat databases, and operator commands. (See Figure 4.)The output of fusion-based ID systems consists of estimates of the identity (and possibly the location) of a threat source, the malicious activity, taxonomy of the threats, the attack rates, and an assessment of the potential severity of damage to the projected target(s). We extrapolated from Waltz[12] to suggest possible generic sensor characteristics of next-generation network fusion systems[2]:Detection Performance is the detection characteristics — false-alarm rate, qdetection probabilities, and ranges — for an intrusion characteristic against agiven network-centric noise background. For example, when detecting malicious activity, nonmalicious activity is typically modelled as noise.Spatial/Temporal Resolution is the ability to distinguish between two or more qnetwork-centric objects in space or time.Spatial Coverage is the span of coverage, or field of view, of the sensor (i.e., the qspatial coverage of a system log file is the computer system processes and system calls being monitored).Detection/Tracking Mode is the mode of operation of the sensor (i.e., scanning, qsingle or multiple network object tracking).Target Revisit Rate is the rate at which a network object or event is revisited by qthe sensor to perform measurements.Measurement Accuracy is the statistical probability that the sensor measurement qor observation is accurate and reliable.Measurement Dimensionality is the number of measurement variables for network qobject categories.Hard vs. Soft Data Reporting is the decision status of the sensor reports. (I.e., can qa command decision be made without correlation, or does the sensor requireconfirmation?)Detection/Tracking Reporting is the characteristic of the sensor with regard to qreporting events. (Does the sensor maintain a time-sequence of the events? type of historical event buffers?)In our fusion model, situational data is collected from network sensors with elementary observation primitives; identifiers, times of observation, and descriptions. The raw data requires calibration and filtering, referred to as Data Refinement (short-term knowledge). Object Refinement is a process that correlates data in time (and space if required); the data is assigned appropriate weighted metrics. Observations may be associated, paired, and classified according to intrusion-detection primitives.Situation Refinement (mid-term knowledge) provides situational knowledge and awareness after objects have been aligned, correlated, and placed in context in an object base. Aggregated sets of objects are detected by their coordinated behavior, dependencies, common points of origin, common protocols, common targets, correlated attack rates, or other high-level attributes.In the interdomain construct of Figure 1, network objects and data flows will be identified and tracked by placing sensors at or between the interdomain gateways. Without going into the details, it can be shown that temporal resolution of the cyberspace situational awareness is directly proportional to the ratio of the transit time of the datagram and the sensory fusion process and inference time.As an analogy we offer the tracking of an object in aerospace — for example, a projectile. If the intercept time of a projectile is greater than the time used by radar or another tracking system and other required processing, then it is not possible to track and react to the object before the projectile hits the target. For example, if the datagram will reach its destination in 30ms, then the decision-fusion process required for network situational awareness must be much less than 30ms. Highly critical situational awareness can be achieved by networking the sensors (and optional command and control links) out-of-band. Current-generation systems use in-band processing, which can only achieve limited temporal resolution.Extensible Threat Taxonomy FusionThe number of IP packets processed by the Internet gateways of Figure 5 is enormous. Gateway sensors acquire and forward proportionally large amounts of data to packet analysis and correlation processes. For example, a router processing 100,000 packets per second on a high-speed interface, logging 14 bytes of information per packet, produces approximately 1.4 MBPS of data per sensor. It is clear that distributed sensors in network-centric IP fusion systems require local processing. Consequently, sensor output data should be reduced at the sensor to minimize central fusion processing and transport overhead costs.Figure 5. Gateway sensors on ID fusion networkWe focus here on the sensor output by outlining an example extensible taxonomy framework of TCP/IP-based threats. Antony[14] discusses database requirements for fusion system and situational knowledge. He states that knowledge is either declarativeor procedural. Declarative knowledge is passive factual knowledge or knowledge of relationships (e.g., files). Procedural knowledge is a special case of declarative knowledge represented as patterns, algorithms, and transformations.Entity relationships are the most fundamental declarative models for sensor data representation. Binaries trees, family trees, and general taxonomies are examples of the elemental database relationships required for situational analysis; the vast majority can be represented by the SQL command[14]:SELECT(attribute) FROM (table) WHERE (condition)With this basic database model and data-selection primitives in mind, we offered a framework TCP/IP threat taxonomy[3]. This framework was offered as an extensible context-dependent TCP/IP threat tree based on the SNMP management information base (MIB) concept. The SNMP MIB concept for representing context-dependent data is well suited for network-centric threats (and countermeasures).Threats to TCP/IP at the physical layer are service disruptions caused by natural disasters such as fires or flooding, cuts to cables, malfunctioning transceivers, and other hardware failures. Threats to the network layer include IP source-address spoofing and route-cache poisoning. An extensible context-dependent framework for this is illustrated in Figures 6, 7, and 8.Figure 6. Example TCP/IP threat subtreeFigure 7. Example IP transport threat subtreeFigure 8. Example TCP transport threat subtreeThree primary data flows (services) exist on the Internet: User Datagram Protocol (UDP), Transmission Control Protocol (TCP), and Internet Control Message Protocol (ICMP)[1]. Domain Name System (DNS) cache poisoning and UDP port-flooding denial-of-service attacks are examples of two vulnerabilities exploited using UDP services. The ping-of-death and ICMP redirect bombs are examples of Internet attacks based on ICMP. TCP vulnerabilities include TCP sequence number and SYN flood attacks, as illustrated in Figure 8.Security threats and countermeasures can be represented using the ASN.1 MIB notation. For example, a TCP SYN flood attack could be represented with the following OBJECT IDENTIFIER (OID):tcpSYNFlood OID ::= { iso 3.6.1.5.1.3.1.1 }Additional sub-object examples for tcpSYNFlood OID could be the source address or the target address of the malicious SYN packet and a counter with the number of SYN floods:tcpSYNFlood.source OID ::= { iso 3.6.1.5.1.3.1.1.1 } tcpSYNFlood.dest OID ::= { iso 3.6.1.5.1.3.1.1.1.2 } tcpSYNFlood.number OID ::= { iso 3.6.1.5.1.3.1.1.1.3 } Developing an extensible TCP/IP security threat MIB is a solid first step on the road to creating Internet ID fusion systems. Other long-term knowledge databases include context-dependent countermeasure, threat profiles, and attack-capabilities databases. ConclusionFuture reliable services that provide long-term threat, countermeasure, and other security-related information to fusion systems are similar to the current state of the art of weather forecasting and threat assessment. Fusion from multiple short-term sensors further processed with long-term knowledge creates short mid-term situational awareness. Situational awareness is required to operate and survive in a complex world with both friendly and hostile activities.All intelligent biological organisms fuse short-term and long-term knowledge to create situational awareness. Humans continually create and redefine systems that help us increase and refine our situational knowledge. These systems include air traffic control, battlefield management, early-warning systems, and robotics. There are strong indications, based on our work in both the Air Force and commercial industry, that future ID systems will shift toward more advanced fusion-based models.Our crystal ball is as foggy as yours, but if the developments in situational awareness systems in air traffic control over the past 40 years are any indication, then Internet traffic-control systems and next-generation intrusion-detection systems have a significant and challenging future in store for all of us.References[1] Stevens, R. TCP/IP Illustrated, Volume 1: The Protocols. Reading, MA:Addison-Wesley, 1994.[2] Bass, T. "Intrusion Detection Systems and Multisensor Data Fusion: Creating Cyberspace Situational Awareness." Communications of the ACM. Forthcoming, 1999.[3] Bass, T. "Multisensor Data Fusion for Next Generation Distributed Intrusion Detection Systems." 1999 IRIS National Symposium on Sensor and Data Fusion, May 1999.[4] Bass, T.; Freyre, A.; Gruber, D.; and Watt., G. "E-Mail Bombs and Countermeasures: Cyber Attacks on Availability and Brand Integrity." IEEE Network, March/April 1998, pp. 10-17.[5] Denning, D. "An Intrusion-Detection Model." IEEE Transactions on Software Engineering, February 1987, pp. 222-232.[6] Mukherjee, B.; Heberlein, L.; and Levitt, K. "Network Intrusion Detection." IEEE Network Magazine, May/June 1994, pp. 26-41.[7] Denning, D., et al. "A Prototype IDES: A Real Time Intrusion Detection Expert System." Computer Science Laboratory, SRI International, August 1987.[8] Snapp. S. et al. "A System for Distributed Intrusion Detection." Proceedings of IEEE COMPCON, March 1991, pp. 170-176.[9] Bauer, D. and Koblentz, M. "NDIX — An Expert System for Real-Time Network Intrusion Detection." Proceedings of the IEEE Computer Networking Symposium, April 1988, pp. 98-106.[10] Hochberg et al. "NADIR: An Automated System for Detecting Network Intrusion and Misuse." Computers & Security, Elsevier Science Publishers, 1993, pp. 235-248. [11] Heberlein, L. et al. "A Network Security Monitor." Proceedings of the IEEE Computer Society Symposium, Research in Security and Privacy, May 1990, pp.296-303.[12] Waltz, E., and Llinas, J. Multisensor Data Fusion. Boston: Artech House, 1990.[13] Waltz, E. Information Warfare Principles and Operations. Boston: Artech House, 1998.[14] Antony, R. Principles of Data Fusion Automation. Boston: Artech House, 1995.Need help? Use our Contacts page. Last changed: 16 Nov. 1999 mc Issue index;login: indexUSENIX home。
高检测概率协方差矩阵机会协作频谱感知

1引言
目前,随着视频多媒体无线通信业务的飞速 发展,频谱资源紧缺成为日益严峻的问题。而部 分频谱资源竞争激烈和部分频谱资源空闲逐渐成 为无线频谱资源利用的主要矛盾之一。静态频谱 分配和动态频谱感知接入方式的矛盾直接造成了 可用无线频谱资源不足,但实际频谱资源浪费较 多的问题,导致频谱资源利用率低下。近年来, 认知无线电(cognitive radio, CR)被提出,且成 为频谱管理的重要解决方案之一E。其主要在软 件无线电基础上,增加了频谱感知和自适应功能。 其中,频谱感知一般可分为能量检测(energy detection, ED)【同、匹配滤波器检测®叭循环平 稳特征检测旳°]和基于协方差检测川切等,但现有 能量检测类方法往往存在噪声不确定等缺陷。匹 配滤波器检测法和循环平稳检测法虽在低信噪比 情况下表现优异,但前者需发送用户先验信息, 后者计算量大、复杂度高,导致其无法实用。协 方差检测法利用接收到的不同信号和噪声,通过 采样、判决,在无需发送端信号信息、信道条件 及同步的情况下,即可获得较好检测精度。但该 算法在样本数量较少情况下性能不佳,且还需通 过改进采样频率等来提高其实用性。另外,在协 作传输方面,传统协方差矩阵检测法也不适用于 机会协作方案。如参考文献[14]所提双门限协方 差矩阵检测虽然提高了频谱感知性能,但接收信 号协方差计算量大,检测时间长,并不利于实用 推广。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
time (noise uncertainty). There are two types of noise
uncertainty: receiver device noise uncertainty and envi-
ronment noise uncertainty. There are several sources of
本页已使用福昕阅读器进行编辑。 福昕软件(C)2005-2010,版权所有, 仅供试用。
Covariance Based Signal Detections For Cognitive Radio
Yonghong Zeng and Ying-Chang Liang Institute for Infocomm Research, A*STAR, Singapore
receiver device noise uncertainty [9], [10], [11], [12]: (a)
non-linearity of components; (b) thermal noise in compo-
nents (non-uniform, time-varying). The environment noise 噪 uncertainty may be caused by transmissions of other users 声
Key words: Signal detection, Sensing, Sensing algorithm, Cognitive radio, WRAN, 802.22
I. Introduction
A “cognitive Radio” is a radio which is able to sense the spectral environment over a wide frequency band and exploit this information to opportunistically provide wireless links that best meet the user communications requirements [1], [2], [3], [4]. Unique to cognitive radio operation is the requirement that the radio is able to sense the environment over huge swath of spectrum and adapt to it. That is, it is necessary to dynamically detect the existence of signals of primary users. In December 2003, the FCC issued a Notice of Proposed Rule Making that identifies cognitive radio as the candidate for implementing negotiated/opportunistic spectrum sharing [5]. In response to this, from 2004, the IEEE has formed the 802.22 Working Group to develop a standard for wireless regional area networks (WRAN) based on cognitive radio technology [6], [7], [8]. WRAN systems will operate on the VHF/UHF bands that are currently allocated for TV broadcasting services and other services such as wireless microphone. In particular, a WRAN system will be able to sense the spectrum, identify unused TV channels, and utilize these channels to provide broadband services for fixed wireless subscribers.
[16]. These algorithms have di&erent requirements and
advantages/disadvantages. Energy detection is a major
and basic method. Unlike other methods, energy detection
does not need any information of the signal to be detected
and is robust to unknown multipath fading. However,
energy detection is vulnerable to the noise uncertainty
Emails: {yhzeng, ycliang}@.sg
Abstract– Sensing (signal detection) is a fundamental problem in cognitive radio. The statistical covariances of signal and noise are usually di&erent. In this paper, this property is used to di&erentiate signal from noise. The sample covariance matrix of the received signal is computed and transformed based on the receiving filter. Then two detection methods are proposed based on the transformed sample covariance matrix. One is the covariance absolute value (CAV) detection and the other is the covariance Frobenius norm (CFN) detection. Theoretical analysis and threshold setting for the algorithms are discussed. Both methods do not need any information of the signal, the channel and noise power as a priori. Simulations based on captured ATSC DTV signals are presented to verify the methods.
dramatically (can be 10dB or even higher), while un-
known multipath will cause coherent detection methods
unreliable. Thirdly, noise/interference level changes with
overcome this shortage, we propose new methods based
on the statistical covariance or auto-correlations of the
received signal. correlations of
The statistical covariance matrices or autosignal and noise are generally di&erent.
性 limited and the complexity of the sensing scheme should 来 be low. When a cognitive user is using a spectral band 源
and a primary user is turned on, the cognitive user must
algorithm to have low complexity.
There have been some sensing algorithms including
the energy detection [13], [9], the matched filtering
(MF) [9], [8] and cyclostationary detection [14], [15],
the received SNR may be well below -20dB. Secondly,
fading and multipath in wireless signal complicate the
problem. Fading will cause the signal power fluctuates
(unintentional (close-by) or intentional (far-away)). Due 不
to noise uncertainty, in practice, it is very di^cult to 确 obtain the accurate noise power. Fourthly, sensing time is 定
detect the primary user’s signal and vacant the channel
in a very short time (to avoid interference to the primary
