【精品文档】封印者资料-实用word文档 (9页)
文本文档

【解救姜尚、魔炉、解救杨戬】
解救姜尚可以得到 冰封之门的钥匙,钥匙可以打开通往去磨炉路上的门。
位置:从树魔区过去,打掉岩石,左边有个传送门进去。
魔炉 爆补天神石,用于合成超神器,伏魔剑,映月弓,流云仗
解救杨戬可以得到神符,带着神符可以去挑战地长灵蛇。
位置:基地左上方传送门进去,白虎上方。
如果人品不好,重击+重生,也是打BOSS必备的。
神将师,必备修罗假面。
后期30波之后的怪物,特别是33和34波,还有最后的BOSS。建议丢弃无界神魔配,换成修罗假面,修罗护腕,修罗手镯,其中的一个。减少伤害,比较耐抗。
战绩算法
a.每杀100怪战绩+1 ,早点快速刷怪较好
b.每答对一次有奖问答战绩+1,每答错一次战绩-1
这两者,都是每分钟加属性的装备。
五大专属武器对应五个专属英雄,每分钟增加2000属性。
五大专属武器对于非专属英雄,每分钟增加1200属性。
圣灵归刃,任何英雄,都是每分钟2000属性。
我的建议 ,专属英雄出专属武器,非专属英雄也是出五大专属中的一个。
对于非专属英雄为什么要出五大专属其中之一,而不是圣灵归刃。原因:圣灵归刃,需要杀9个BOOS,其中8个BOSS还要看RP爆出四神兵和四灵珠,光这点很耗费时间,但是时间是宝贵的。早出专属武器有好处,专属武器,技能增强,属性增强,每分钟还加属性,打后面的BOSS和装备都给力。
光辉金套装可以用元素晶体升级3级,100%成功
4级和MAX用新月晶体升级,升4级成功率为80%,升MAX成功率为70%
战神甲=光辉金套装+补天神石
【无界战甲】=诛神甲+伏魔战铠+大补天石(神圣龙爆)
2952020-ISTQB-sample-question-paperspart-1

ISTQB CertificationSample Question PapersCopyright © Abhishek Kumar TiwariAll rights reserved. No part of this material may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without prior permission from the owner. Contact the owner for the information on foreign rights.Question Paper 1:1.An input field takes the year of birth between 1900 and 2004The boundary values for testing this field area.0,1900,2004,2005b.1900, 2004c.1899,1900,2004,2005d.1899, 1900, 1901,2003,2004,20052.Which one of the following are non-functional testing methods?a.System testingability testingc.Performance testingd.Both b & c3.Which of the following tools would be involved in the automation of regressiontest?a.Data testerb.Boundary testerc.Capture/Playbackd.Output comparator.4.Incorrect form of Logic coverage is:a.Statement Coverageb.Pole Coveragec.Condition Coveraged.Path Coverage5.Which of the following is not a quality characteristic listed in ISO 9126 Standard?a.Functionalityabilityc.Supportabilityd.Maintainability6.To test a function, the programmer has to write a _________, which calls thefunction to be tested and passes it test data.a.Stubb.Driverc.Proxyd.None of the above7.Boundary value testinga.Is the same as equivalence partitioning testsb.Test boundary conditions on, below and above the edges of input andoutput equivalence classesc.Tests combinations of input circumstancesd.Is used in white box testing strategy8.Pick the best definition of qualitya.Quality is job oneb.Zero defectsc.Conformance to requirementsd.Work as designed9.Fault Masking isa.Error condition hiding another error conditionb.Creating a test case which does not reveal a faultc.Masking a fault by developerd.Masking a fault by a tester10.One Key reason why developers have difficulty testing their own work is :ck of technical documentationck of test tools on the market for developersck of trainingck of Objectivity11.During the software development process, at what point can the test process start?a.When the code is complete.b.When the design is complete.c.When the software requirements have been approved.d.When the first code module is ready for unit testing12.In a review meeting a moderator is a person whoa.Takes minutes of the meetingb.Mediates between peoplec.Takes telephone callsd.Writes the documents to be reviewed13.Given the Following programIF X < YTHEN Statement 1;ELSE IF Y >= ZTHEN Statement 2;ENDMcCabe’s Cyclomatic Complexity is :a. 2b. 3c. 4d. 514.How many test cases are necessary to cover all the possible sequences ofstatements (paths) for the following program fragment? Assume that the twoconditions are independent of each other : -…………if (Condition 1)then statement 1else statement 2fiif (Condition 2)then statement 3fi…………a.Test Casesb. 3 Test Casesc. 4 Test Casesd.Not achievable15. Acceptance test cases are based on what?a.Requirementsb.Designc.Coded.Decision table16. “How much testing is enough?”a.This question is impossible to answerb.This question is easy to answerc.The answer depends on the risk for your industry, contract and specialrequirementsd.This answer depends on the maturity of your developers17. A common test technique during component test isa.Statement and branch testingability testingc.Security testingd.Performance testing18.Statement Coverage will not check for the following.a.Missing Statementsb.Unused Branchesc.Dead Coded.Unused Statement19.Independent Verification & Validation isa.Done by the Developerb.Done by the Test Engineersc.Done By Managementd.Done by an Entity Outside the Project’s sphere of influence20.Code Coverage is used as a measure of what ?a.Defectsb.Trends analysisc.Test Effectivenessd.Time Spent TestingQuestion Paper 2:Q2Regression testing should be performed:v) every week w) after the software has changed x) as often as possible y) when the environment has changed z) when the project manager says NOTE: Only one answer per question Q1A deviation from the specified or expected behaviour that is visible to end-users is called:a) an error b) a faulta) v & w are true, x, y & z are false b) w, x & y are true, v & z are false c) w & y are true, v, x & z are false d) w is true, v, x, y & z are falseQ3IEEE 829 test plan documentation standard contains all of the following except c) a failure d) a defecta) test items b) test deliverables c) test tasks d) test specificationsQ4When should testing be stopped?a) when all the planned tests have been run b) when time has run outc) when all faults have been fixed correctlyd) it depends on the risks for the system being testedQ5Order numbers on a stock control system can range between 10000 and 99999 inclusive. Which of the following inputs might be a result of designing tests for only valid equivalence classes and valid boundaries?a) 1000, 50000, 99999 b) 9999, 50000, 100000 c) 10000, 50000, 99999 d) 10000, 99999, 100000Q6 Consider the following statements about early test design:i. early test design can prevent fault multiplicationii. faults found during early test design are more expensive to fixiii. early test design can find faultsiv. early test design can cause changes to the requirementsv. early test design normally takes more efforta) i, iii & iv are true; ii & v are falseb) iii & iv are true; i, ii & v are falsec) i, iii, iv & v are true; ii is falsed) i & ii are true; iii, iv & v are falseQ7 Non-functional system testing includes:a) testing to see where the system does not function correctlyb) testing quality attributes of the system including performance and usabilityc) testing a system function using only the software required for that functiond) testing for functions that should not existQ8 Which of the following is NOT part of configuration management?a) auditing conformance to ISO 9000b) status accounting of configuration itemsc) identification of test versionsd) controlled library accessQ9Which of the following is the main purpose of the integration strategy for integration testing in the small?a) to ensure that all of the small modules are tested adequatelyb) to ensure that the system interfaces to other systems and networksc) to specify which modules to combine when, and how many at onced) to specify how the software should be divided into modulesQ10 What is the purpose of a test completion criterion?a) to know when a specific test has finished its executionb) to ensure that the test case specification is completec) to set the criteria used in generating test inputsd) to determine when to stop testingQ11 Consider the following statements:i. an incident may be closed without being fixed.ii. incidents may not be raised against documentation.iii. the final stage of incident tracking is fixing.iv. the incident record does not include information on test environments.a) ii is true, i, iii and iv are falseb) i is true, ii, iii and iv are falsec) i and iv are true, ii and iii are falsed) i and ii are true, iii and iv are falseQ12 Given the following code, which statement is true about the minimum number of test cases required for full statement and branch coverage?Read pRead qIF p+q > 100 THENPrint"Large"ENDIFIF p > 50 THENPrint "p Large"ENDIFa) 1 test for statement coverage, 3 for branch coverageb) 1 test for statement coverage, 2 for branch coveragec) 1 test for statement coverage, 1 for branch coveraged) 2 tests for statement coverage, 2 for branch coverageQ13 Consider the following statements:i. 100% statement coverage guarantees 100% branch coverage.ii. 100% branch coverage guarantees 100% statement coverage.iii. 100% branch coverage guarantees 100% decision coverage.iv. 100% decision coverage guarantees 100% branch coverage.v. 100% statement coverage guarantees 100% decision coverage.a) ii is True; i, iii, iv & v are Falseb) i & v are True; ii, iii & iv are Falsec) ii & iii are True; i, iv & v are Falsed) ii, iii & iv are True; i & v are FalseQ14 Functional system testing is:a) testing that the system functions with other systemsb) testing that the components that comprise the system function togetherc) testing the end to end functionality of the system as a wholed) testing the system performs functions within specified response timesQ15 Incidents would not be raised against:a) requirementsb) documentationc) test casesd) improvements suggested by usersQ16 Which of the following items would not come under Configuration Management?a) operating systemsb) test documentationc) live datad) user requirement documentsQ17 Maintenance testing is:a) updating tests when the software has changedb) testing a released system that has been changedc) testing by users to ensure that the system meets a business needd) testing to maintain business advantageQ18 What can static analysis NOT find?a) the use of a variable before it has been definedb) unreachable (“dead”) codec) memory leaksd) array bound violationsQ19 Which of the following techniques is NOT a black box technique?a) state transition testingb) LCSAJc) syntax testingd) boundary value analysisQ20 Beta testing is:a) performed by customers at their own siteb) performed by customers at the software developer's sitec) performed by an Independent Test Teamd) performed as early as possible in the lifecycleQ21 Given the following types of tool, which tools would typically be used by developers, and which by an independent system test team?analysisi. statictestingii. performancemanagementiii. testanalysisiv. dynamica) developers would typically use i and iv; test team ii and iiib) developers would typically use i and iii; test team ii and ivc) developers would typically use ii and iv; test team i and iiid) developers would typically use i, iii and iv; test team iiQ22 The main focus of acceptance testing is:a) finding faults in the systemb) ensuring that the system is acceptable to all usersc) testing the system with other systemsd) testing from a business perspectiveQ23 Which of the following statements about component testing is FALSE?a) black box test design techniques all have an associated test measurement techniqueb) white box test design techniques all have an associated test measurement techniquec) cyclomatic complexity is not a test measurement techniqued) black box test measurement techniques all have an associated test design techniqueQ24 Which of the following statements is NOT true?a) inspection is the most formal review processb) inspections should be led by a trained leaderc) managers can perform inspections on management documentsd) inspection is appropriate even when there are no written documentsQ25 A typical commercial test execution tool would be able to perform all of the following, EXCEPT:a) calculating expected outputsb) comparison of expected outcomes with actual outcomesc) recording test inputsd) reading test values from a data fileQ26 The difference between re-testing and regression testing is:a) re-testing ensures the original fault has been removed; regression testing looks forunexpected side-effectsb) re-testing looks for unexpected side-effects; regression testing ensures the original fault hasbeen removedc) re-testing is done after faults are fixed; regression testing is done earlierd) re-testing is done by developers; regression testing is done by independent testersQ27 Expected results are:a) only important in system testingb) only used in component testingc) most useful when specified in advanced) derived from the codeQ28 What type of review requires formal entry and exit criteria, including metrics:a) walkthroughb) inspectionc) management reviewd) post project reviewQ29 Which of the following uses Impact Analysis most?a) component testingb) non-functional system testingc) user acceptance testingd) maintenance testingQ30 What is NOT included in typical costs for an inspection process?a) setting up forms and databasesb) analysing metrics and improving processesc) writing the documents to be inspectedd) time spent on the document outside the meetingQ31 Which of the following is NOT a reasonable test objective:a) to find faults in the softwareb) to prove that the software has no faultsc) to give confidence in the softwared) to find performance problemsQ32 Which expression best matches the following characteristics of the review processes:1. led by the author2. undocumented3. no management participation4. led by a moderator or leader5. uses entry and exit criterias) inspectiont) peer reviewu) informal reviewv) walkthrougha) s = 4 and 5, t = 3, u = 2, v = 1b) s = 4, t = 3, u = 2 and 5, v = 1c) s = 1 and 5, t = 3, u = 2, v = 4d) s = 4 and 5, t = 1, u= 2, v = 3Q33 Which of the following is NOT part of system testing?a) business process-based testingb) performance, load and stress testingc) usability testingd) top-down integration testingQ34 Which statement about expected outcomes is FALSE?a) expected outcomes are defined by the software's behaviourb) expected outcomes are derived from a specification, not from the codec) expected outcomes should be predicted before a test is rund) expected outcomes may include timing constraints such as response timesQ35 The standard that gives definitions of testing terms is:a) ISO/IEC 12207b) BS 7925-1c) ANSI/IEEE 829d) ANSI/IEEE 729Q36 The cost of fixing a fault:a) is not importantb) increases the later a fault is foundc) decreases the later a fault is foundd) can never be determinedQ37 Which of the following is NOT included in the Test Plan document of the Test Documentation Standard?a) what is not to be testedb) test environment propertiesc) quality plansd) schedules and deadlinesQ38 Could reviews or inspections be considered part of testing?a) no, because they apply to development documentationb) no, because they are normally applied before testingc) yes, because both help detect faults and improve qualityd) yes, because testing includes all non-constructive activitiesQ39 Which of the following is not part of performance testing?a) measuring response timesb) recovery testingc) simulating many usersd) generating many transactionsQ40 Error guessing is best used:a) after more formal techniques have been appliedb) as the first approach to deriving test casesc) by inexperienced testersd) after the system has gone liveQuestion Paper 3:1. What is failure?A. Deviation from expected result to actual resultB. Defect in the software.C. Error in the program code.D. Fault in the system.2. People who don’t participate in technical reviewsA. AnalystsB. ManagementC. DevelopersD. Testers3. What type of testing is done to supplement the rigorous testing?A. Regression testing.B. Integration testing.C. Error GuessingD. System testing.4. Capture and replay facilities are least likely to be used to ….A. Performance testingB. Recovery testingC. GUI testingD. User requirements.5. What is the smallest number of test cases required toProvide 100% branch coverage?If(x>y) x=x+1; else y=y+1;while(x>y){y=x*y; x=x+1;}A. 1B. 2C. 3D. 46. Cyclomatic complexity is used to calculateA. number of independent paths in the basis set of a programB. number of binary decisions + 1C. upper bound for the number of tests that must be conducted to ensure that all statements have been executed at least onceD. number of branches and decisions7. If a candidate is given an exam of 40 questions, should get 25 marks to pass (61%) and should get 80% for distinction, what is equivalence class.A. 23, 24, 25B. 0, 12, 25C. 30, 36, 39D. 32,37,408. Match the following:1. Test estimation2. Test control3. Test monitoringa. measures of tracking processb. effort required to perform activitiesc. reallocation of resourcesA. 1-b, 2-c, 3-aB. 1-b, 2-a, 3-cC. 1-c, 2-a, 3-bD. 1-a, 2-b, 3-c9. One of the following is not a part of white box testing asper BS7925-II standards.A. Random testingB. Data Flow testing.C. Statement testing.D. Syntax testing.10. Exclusive use of white box testing in a test-phase will:A. Ensure the test item is adequately tested.B. Make the need for black-box testing redundant.C. Run the risk that the requirements are not satisfied.D. Suffices for the unit testing phase.11. Match the following.1. Configuration identification2. Configuration control3. Status reporting4. Configuration auditinga. Maintains of CI’s in a libraryb. Checks on the contents of the libraryc. Function recording and tracking problems.d. Requires the all CI’s and their versions in the systemare knownA. 1-d, 2-c, 3-d, 4-a.B. 1-d, 2-a, 3-c, 4-b.C. 1-a, 2-b, 3-d, 4-c.D. 1-c, 2-b, 3-a, 4-d.12. Cost of the reviews will not include.A. Review process itselfB. Metrics analysisC. Tool support.D. Process improvement.13. What type of testing will you perform on internet banking solution?A. System integrationB. Functional testingC. Non-functional testing.D. Requirements testing14. Which tool will be used to test the flag memory leaks and unassigned pointersA. Dynamic analysis toolB. Static Analysis tool.C. Maintenance tool.D. Configuration tool.15. Which of the following is not included in Test Plan.A. Features to be tested.B. Environmental needs.C. Suspension criteria.D. Expected results.16. A piece of software has been given….what tests in the Following will you perform?1) Test the areas most critical to business processes2) Test the areas where faults will be maximum3) Test the easiest functionalitiesA. 1&2 are true and 3 is false.B. 1,2&3 are true.C. 1 is true, 2&3 are false.D. 1&2 are false, 3 is true.17. Amount of testing performed will not depend onA. Risks involvedB. Contractual requirementsC. Legal requirementsD. Test data.18. Which of the following provides the biggest potential cost saving from use of CAST?A. Test managementB. Test designC. Test planningD. Test execution19. Testing is not done to ….A. Find faultsB. Improve qualityC. Check user friendliness.D. Improve software accuracy20. Software quality is not relevant to …A. CorrectnessB. UsabilityC. ViabilityD. Reusability.21. Which of the following are false?A. Incidents should always be investigated and resolved.B. Incidents occur when expected and actual results differ.C. Incidents can be analyzed to assist in test process improvement.D. An incident can be raised against documentation.22. Which of the following is a type of non-functional testing?A. Usability testing.B. Statement Coverage.C. Dataflow testing.D. Cause-effect graphing.23. To make a test effective it is most important that:A. It is easy to execute.B. It is designed to detect faults if present.C. The expected outcome is specified before execution.D. It is unlikely to delay progress.24. Error guessing is:A. An appropriate way of deriving system tests.B. Only used if good requirements are not available.C. Only used when good requirements are available.D. The most appropriate way of deriving system tests.25. A standard for software testing terminology is:A. IEEE 802.11B. ISO 9001C. BS 7925-1D. BS 7925-226. Which of the following is true of V-model?A. It includes the verification of designs.B. It states that modules are tested against user requirements.C. It specifies the test techniques to be used.D. It only models the testing phase.27. Which of the following is NOT part of a high level test plan?A. Functions not to be tested.B. Environmental requirements.C. Analysis of Specifications.D. Entry and Exit criteria.28. When do you stop testing?A. When the specified number of faults are found.B. When the test completion criteria are met.C. When all high and medium priority tests are complete.D. When all statements have been executed.29. Which of the following is least important in test management?A. Estimating test duration.B. Incident Management.C. Configuration Management.D. De-bugging.30. How would you estimate the amount of re-testing likely to be required?A. Metrics from previous similar projects.B. Discussions with the development team.C. Time allocated for regression testing.D. Both A & B.31. Which of the following statements is true of static analysis:A. Compiling code is not a form of static analysis.B. Static analysis need not be performed before imperative code is executed.C. Static analysis can find faults that are hard to find withdynamic testing.D. Extensive statistic analysis will not be needed if white-Box testing is to be performed.32. Regression testing always involvesA. Testing whether a known software fault been fixed.B. Executing a large number of different tests.C. Testing whether modifications have introduced adverseside effects.D. Using a test automation tool.33. A field failure occurs when multiple users access a system.Which of the following is true?A. This is an acceptable risk of a multi-user system.B. Insufficient functional testing has been performed.C. This indicates an important non-functional requirement was not specified and tested.D. It is not possible to test against such events prior to release.34. Integration testing in the large involves:A. Testing the system when combined with other systems.B. Testing a sub-system using stubs and drivers.C. Testing a system with a large number of users.D. Combing software components and testing them in onego.35. Data flow analysis studies:A. How rapidly data is transferred through a program.B. The rate of change of data values as a program executes.C. The use of data on paths through the code.D. The intrinsic complexity of the code.36. The oracle assumption is that:A. There is some existing system against which test outputmay be checked.B. The tester knows everything about the software undertest.C. The tester can routinely identify the correct outcome ofa test.D. Tools are used to check the results of testing.36 The following text will be used in Q.37 and Q.38. In a system designed to work out the tax to be paid:An employee has $4000 of salary tax freeThe next $1500 is taxed at 10%The next $28000 is taxed at 22%Any further amount is taxed at 40%37. To the nearest $ which of these is a valid Boundary Value Analysis test case?A. $1500B. $32001C. $28000D. $3350138. Which of these groups of numbers would fall into the same equivalence class?A. $5800; $28000; $32000B. $0; $200; $4200C. $5200; $5500; $28000D. $28001; $32000; $3500039. Which of the following is NOT a characteristic of User Acceptance Testing?A. Use of automated test execution tools.B. Testing performed by users.C. Testing against acceptance test criteria.D. Integration of system with user documentation.40. For software to be reliable it must:A. Be easy to maintain.B. Be unlikely to cause a failure.C. Never fail under any circumstances.D. Be written according to coding standardsQuestion Paper 4:1 We split testing into distinct stages primarily because:a) Each test stage has a different purpose.b) It is easier to manage testing in stages.c) We can run different tests in different environments.d) The more stages we have, the better the testing.2 Which of the following is likely to benefit most from the use of test tools providing test capture and replay facilities?a) Regression testingb) Integration testingc) System testingd) User acceptance testing3 Which of the following statements is NOT correct?a) A minimal test set that achieves 100% LCSAJ coverage will also achieve 100% branch coverage.b) A minimal test set that achieves 100% path coverage will also achieve 100% statement coverage.c) A minimal test set that achieves 100% path coverage will generally detect more faults than one that achieves 100% statement coverage.d) A minimal test set that achieves 100% statement coverage will generally detect more faults than one that achieves 100% branch coverage.4 Which of the following requirements is testable?a) The system shall be user friendly.b) The safety-critical parts of the system shall contain 0 faults.c) The response time shall be less than one second for the specified design load.d) The system shall be built to be portable.5 Analyse the following highly simplified procedure:Ask: “What type of ticket do you require, single or return?”IF the customer wants ‘return’Ask: “What rate, Standard or Cheap-day?”IF the customer replies ‘Cheap-day’Say: “That will be £11:20”ELSESay: “That will be £19:50”ENDIFELSESay: “That will be £9:75”ENDIFNow decide the minimum number of tests that are needed to ensure that allthe questions have been asked, all combinations have occurred and allreplies given.a) 3b) 4c) 5d) 66 Error guessing:a) supplements formal test design techniques.b) can only be used in component, integration and system testing.c) is only performed in user acceptance testing.d) is not repeatable and should not be used.7 Which of the following is NOT true of test coverage criteria?a) Test coverage criteria can be measured in terms of items exercised by a test suite.b) A measure of test coverage criteria is the percentage of user requirements covered.c) A measure of test coverage criteria is the percentage of faults found.d) Test coverage criteria are often used when specifying test completion criteria.8 In prioritising what to test, the most important objective is to:a) find as many faults as possible.b) test high risk areas.c) obtain good test coverage.d) test whatever is easiest to test.9 Given the following sets of test management terms (v-z), and activity descriptions (1-5), which one of the following best pairs the two sets?v – test controlw – test monitoringx - test estimationy - incident managementz - configuration control1 - calculation of required test resources2 - maintenance of record of test results3 - re-allocation of resources when tests overrun4 - report on deviation from test plan5 - tracking of anomalous test resultsa) v-3,w-2,x-1,y-5,z-4b) v-2,w-5,x-1,y-4,z-3c) v-3,w-4,x-1,y-5,z-2d) v-2,w-1,x-4,y-3,z-510 Which one of the following statements about system testing is NOT true?a) System tests are often performed by independent teams.b) Functional testing is used more than structural testing.c) Faults found during system tests can be very expensive to fix.d) End-users should be involved in system tests.11 Which of the following is false?。
科学文献

The presence of these two patterns in both humans and mouse suggests their importance in the evolution of mammalian X chromo-somes.Our sample of functional retroposed genes in the mammalian genomes is likely at least an order of magnitude smaller than the actual number(10,11).Notably,our analyses exclude retrocopies maintaining introns,such as partially processed retrogenes(35)or chi-meric genes(36),which would implicate even more genes.Finally,other mechanisms of interchromosomal gene movement are also likely influenced by the aforementioned se-lective forces.Thus,we expect many more genes to be subject to the gene traffic de-scribed herein.To elucidate the age of retrogene move-ments,we dated the human duplications involv-ing X-linked parents or retrogenes both by comparison to the mouse genome sequence and by sequence divergence analysis(16).Most copies that escape X linkage(12/15)as well as most copies that obtain X linkage(10/13)orig-inated before the human-mouse split(Fig.2, tables S7and S8).Duplicates in the mouse genome show the same pattern,consistent with this notion.Thus,both patterns result from an-cient evolutionary forces common to eutherian mammals.However,this process appears to be an ongoing characteristic of eutherian X evolu-tion,because6/28events have occurred subse-quent to the human-mouse split in the human lineage,6/33retropositions have occurred with-in the pastϳ80million years in the mouse lineage,and some of these retroduplicate pairs have high sequence similarity(Ͼ95%)at syn-onymous sites.This chromosome-biased gene origination appears to be an important process actively driving the differentiation of the X chromosome in mammals and suggests that this differentiation is still in progress.References and Noteshn,N.M.Pearson,K.Jegalian,Nature Rev.Genet.2,207(2001).2.H.Skaletsky et al.,Nature423,825(2003).3.J.A.Marshall Graves et al.,Cytogenet.Genome Res.96,161(2002).4.J.R.McCarrey,Bioscience44,20(1994).5.M.J.Lercher,A.O.Urrutia,L.D.Hurst,Mol.Biol.Evol.20,1113(2003).6.P.J.Wang,J.R.McCarrey,F.Yang,D.C.Page,NatureGenet.27,422(2001).7.J.C.Venter et al.,Science291,1304(2001).8.B.Lewin,Genes VII(Oxford University Press,NewYork,2000).9.E.Betran,K.Thornton,M.Long,Genome Res.12,1854(2002).10.P.M.Harrison et al.,Genome Res.12,272(2002).11.L.Z.Strichman-Almashanu,M.Bustin,ndsman,Genome Res.13,800(2003).12.E.Betra´n,W.Wang,L.Jin,M.Long,Mol.Biol.Evol.19,654(2002).13.J.Brosius,Science251,753(1991).nder et al.,Nature409,860(2001).15.T.Hubbard et al.,Nucleic.Acids.Res.30,38(2002).16.Materials and methods are available as supportingmaterial on Science Online.17.R.H.Waterston et al.,Nature420,520(2002).18.Z.Zhang,P.Harrison,M.Gerstein,Genome Res.12,1466(2002).19.C.-I.Wu,E.Y.Xu,Trends Genet.19,243(2003).20.C.Richler,H.Soreq,J.Wahrman,Nature Genet.2,192(1992).21.H.H.Dahl et al.,Genomics8,225(1990).22.D.J.Elliott et al.,Hum.Mol.Genet.9,2117(2000).23.M.Taira et al.,J.Biol.Chem.265,16491(1990).24.B.Dass et al.,J.Biol.Chem.276,8044(2001).25.M.Parisi et al.,Science299,697(2003).26.J.M.Ranz,C.I.Castillo-Davis,C.D.Meiklejohn,D.L.Hartl,Science300,1742(2003).27.V.Reinke et al.,Mol.Cell6,605(2000).28.T.Fujii et al.,EMBO Rep.3,367(2002).29.A.Kong et al.,Nature Genet.31,241(2002).30.H.A.Wichman,Genetica86,287(1992).ngley et al.,Genet.Res.52,223(1988).32.J.A.Bailey,L.Carrel,A.Chakravarti,E.E.Eichler,Proc.Natl.Acad.Sci.U.S.A.97,6634(2000).33.Z.Gu,H.Wang,A.Nekrutenko,W.H.Li,Gene259,81(2000).34.B.Charlesworth,J.A.Coyne,N.H.Barton,Am.Nat.130,113(1987).35.M.B.Soares et al.,Mol.Cell.Biol.5,2090(1985).36.A.Courseaux,J.-L.Nahon,Science291,1293(2001).37.We thank K.Thornton,Y.Chen,T.Nagylaki,C.-I.Wu,J.Spofford,B.L.Sidlauskas,T.M.Martin,and twoanonymous reviewers for helpful comments.Sup-ported by grants NSF Career MCB-0238168and NIHGM-065429-01A1;a Packard Fellowship(to M.L.),anNSF Predoctoral Fellowship(to J.J.E.),an EmmyNoether fellowship from the Deutsche Forschungs-gemeinschaft(to H.K.);and the startup funds(to E.B.)from University of Texas at Arlington.Supporting Online Material/cgi/content/full/303/5657/537/DC1Materials and MethodsTables S1to S9Fig.S1References4August2003;accepted26November2003A Map of the Interactome Networkof the Metazoan C.elegansSiming Li,1*Christopher M.Armstrong,1*Nicolas Bertin,1*Hui Ge,1*Stuart Milstein,1*Mike Boxem,1*Pierre-Olivier Vidalain,1*Jing-Dong J.Han,1*Alban Chesneau,1,2*Tong Hao,1Debra S.Goldberg,3Ning Li,1Monica Martinez,1Jean-Franc¸ois Rual,1,4Philippe Lamesch,1,4Lai Xu,5†Muneesh Tewari,1Sharyl L.Wong,3Lan V.Zhang,3Gabriel F.Berriz,3Laurent Jacotot,1‡Philippe Vaglio,1‡Je´roˆme Reboul,1§Tomoko Hirozane-Kishikawa,1Qianru Li,1Harrison W.Gabel,1Ahmed Elewa,1ሻBridget Baumgartner,5Debra J.Rose,6Haiyuan Yu,7Stephanie Bosak,8Reynaldo Sequerra,8Andrew Fraser,9Susan E.Mango,10 William M.Saxton,6Susan Strome,6Sander van den Heuvel,11Fabio Piano,12Jean Vandenhaute,4Claude Sardet,2Mark Gerstein,7Lynn Doucette-Stamm,8Kristin C.Gunsalus,12 J.Wade Harper,5†Michael E.Cusick,1Frederick P.Roth,3David E.Hill,1¶Marc Vidal1¶#To initiate studies on how protein-protein interaction(or“interactome”)networksrelate to multicellular functions,we have mapped a large fraction of the Caeno-rhabditis elegans interactome network.Starting with a subset of metazoan-specificproteins,more than4000interactions were identified from high-throughput,yeasttwo-hybrid(HTϭY2H)screens.Independent coaffinity purification assays exper-imentally validated the overall quality of this Y2H data set.Together with alreadydescribed Y2H interactions and interologs predicted in silico,the current version ofthe Worm Interactome(WI5)map containsϳ5500interactions.Topological andbiological features of this interactome network,as well as its integration withphenome and transcriptome data sets,lead to numerous biological hypotheses.To further understand biological processes,it isimportant to consider protein functions in thecontext of complex molecular networks.Thestudy of such networks requires the availabilityof proteome-wide protein-protein interaction,or“interactome,”maps.The yeast Saccharomy-ces cerevisiae has been used to develop a eu-karyotic unicellular interactome map(1–6).Caenorhabditis elegans is an ideal model forstudying how protein networks relate to multi-cellularity.Here we investigate its interactomenetwork with HT-Y2H.As Y2H baits,we selected a set of3024worm predicted proteins that relate directly orindirectly to multicellular functions(7).Gateway-cloned open reading frames(ORFs)were available in the C.elegans ORFeome1.1(8)for1978of these selected proteins.Ofthese,81autoactivated the Y2H GAL1::HIS3reporter gene as Gal4DNA binding domainfusions(DB-X),and24others conferred tox-icity to yeast cells.The remaining1873baitswere screened against two different Gal4ac-tivation domain libraries(AD-wrmcDNA andAD-ORFeome1.0),each with distinct,yet complementary,advantages(7).We maximized the specificity of the Y2H system by applying stringent experimental and bioinformatics criteria(fig.S1).To eliminate interactions that originated from nonspecific promoter activation,we only considered DB-X–AD-Y pairs if they activated at least two out of three different Gal4-responsive promoters. Positives were subsequently retested in fresh yeast cells,and their AD-Y identities were de-termined with interaction sequence tags(ISTs) obtained by sequencing the corresponding polymerase chain reaction(PCR)products(9). The AD-Y reading frame was verified for each IST to avoid the recovery of out-of-frame pep-tides.In total,ϳ16,000ISTs were obtained.Having applied those criteria,we subdivided the interactions into three confidence classes (fig.S1):those that were found at least three times independently and for which the AD-Y junction is in frame(“Core-1,”858interactions); those in frame found fewer than three times and that passed the retest(“Core-2,”1299interac-tions);and all other Y2H interactions found inour screens(“Non-Core,”1892interactions).The Core data set(Core-1and Core-2)contains2157high-confidence interactions between502DB-X baits and1039AD-Y preys.After col-lapsing22interactions that occur in both DB-X–AD-Y and DB-Y–AD-X configurations,a totalof2135unique interactions are obtained(tableS1).The Non-Core data set contains1892inter-actions between531DB-X baits and1395AD-Y preys.Altogether,Core and Non-Coreconstitute the“First-Pass”data set,with a total of4027distinct interactions.Out of2783and1505interactions found with AD-wrmcDNA and AD-ORFeome1.0,respectively,239interactionswere identified with both libraries.To estimate the coverage of the HT-Y2Hdata sets,we manually searched the baitsscreened here for known interactors inWormPD(10).This search gave rise to108interactions,referred to as the“literature”data set(table S1).The Core and Non-Coredata sets recapitulated eight and two interac-tions in this benchmark data set,respectively.Thus,our overall rate of coverage for theFirst-Pass data set isϳ10%[(8ϩ2)/108)].To evaluate the accuracy of the HT-Y2H datasets,we reasoned that interactions detected in twodifferent binding assays are unlikely to be exper-imental false-positives.A representative sample ofY2H interaction pairs from each of these threesubsets(33for Core-1,62for Core-2,and48forNon-Core)was randomly selected,and tested in acoaffinity purification(co-AP)glutathioneS-transferase(GST)pull-down assay(Fig.1).Baitand prey ORFs were transiently transfected into293T cells as GST-bait and Myc-prey fusions,respectively.For potential interaction pairs whereboth proteins were expressed at detectable levels,the co-AP success rates were14out of17(82%)for Core-1,17out of29(59%)for Core-2,and8out of23(35%)for Non-Core(table S2).Thesedata demonstrate that our three data sets contain alarge proportion of highly reliable interactions andcorroborate their expected relative qualities.In addition to experimental screens,we alsoperformed in silico searches for potentially con-served interactions,or“interologs,”whose or-thologous pairs are known to interact in one ormore other species(9,11).Starting from ahigh-confidence yeast interaction data set(7),reciprocal best-hit BLAST searches(E-valueՅ10Ϫ6)were performed against the worm pre-dicted proteome.In all,949potential worminterologs were identified,constituting the in-terologs data set(7).In addition,the Y2Hinteractome maps that have been previouslygenerated for individual biological processes(including vulval development,protein degra-dation,DNA damage response,and germlineformation)(9,12–14)were pooled to define the“scaffold”data set.The HT-Y2H,literature,interologs,and scaffold data sets were com-bined into Worm Interactome version5(WI5),containing5534interactions and connecting15%of the C.elegans proteome(table S1).WI5gives rise to a giant network component of2898nodes connected by5460edges(Fig.2A).Similar to other biological networks(15),theworm interactome network exhibits small-world and scale-free properties(Fig.2B)(7).This data set also allowed us to analyze whetheror not evolutionary recent proteins tend topreferentially interact with each other ratherthan with ancient proteins.We subdivided thenodes of the network into three classes:748proteins with a clear ortholog in yeast(“an-cient”),1314proteins with a clear ortholog inDrosophila,Arabidopsis,or humans but not inyeast(“multicellular”),and836proteins withno detectable ortholog outside of C.elegans(“worm”)(7).These three groups seem to con-nect equally well with each other(Fig.2C),whichsuggests that new cellular functions rely on acombination of evolutionarily new and ancientelements,consonant with the classic proposal ofevolution as a tinkerer that modifies and adds topre-existing structures to create new ones(16).Previous studies have related interactomedata with genome-wide expression(transcrip-1Dana-Farber Cancer Institute and Department of Genetics,Harvard Medical School,44Binney Street, Boston,MA02115,USA.2Institut de Ge´ne´tique Mo-le´culaire,Centre National de la Recherche Scienti-fique UMR5535,1919Route de Mende,34293Mont-pellier Cedex5,France.3Department of Biological Chemistry and Molecular Pharmacology,Harvard Medical School,250Longwood Avenue,Boston,MA 02115,USA.4Unite´de Recherche en Biologie Mole´cu-laire,Faculte´s Notre-Dame de la Paix,61Rue de Bruxelles,5000Namur,Belgium.5Verna and Marrs Department of Biochemistry and Molecular Biology, Program in Cell and Molecular Biology,Biophysics, and Biology,Baylor College of Medicine,One Baylor Plaza,Houston,TX77030,USA.6Department of Bi-ology,Indiana University,Jordan Hall142,1001East Third Street,Bloomington,IN47405,USA.7Depart-ment of Molecular Biophysics and Biochemistry and Department of Computer Science,Yale University, 266Whitney Avenue,New Haven,CT06520,USA. 8Agencourt Bioscience Corporation,100Cummings Center,Suite107G,Beverly,MA01915,USA.9The Wellcome Trust Sanger Institute,Wellcome Trust Ge-nome Campus,Hinxton,Cambridge,CB101SA,UK. 10Huntsman Cancer Institute,University of Utah, 2000Circle of Hope,Salt Lake City,UT84112,USA.11Massachusetts General Hospital Cancer Center, Building149,13th Street,Charlestown,MA02129, USA.12Department of Biology,New York University, 1009Silver Building,100Washington Square East, New York,NY10003,USA.*These authors contributed equally to this work.†Present address:Department of Pathology,Harvard Medical School,200Longwood Avenue,Boston,MA 02115,USA.‡Present address:Modul-Bio,232Boulevard Sainte-Marguerite,13009Marseille,France.§Present address:INSERM,Unite´119,Institut Paoli Calmettes,13009Marseille,France.Present address:Program in Gene Function and Ex-pression,University of Massachusetts,55Lake Ave-nue,North Worcester,MA01605,USA.¶Present address:Center for Cancer Systems Biology and Department of Cancer Biology,Dana-Farber Cancer Institute and Department of Genetics,Harvard Medical School,44Binney Street,Boston,MA02115,USA.#To whom correspondence should be addressed.E-mail:marc_vidal@.Fig.1.Coaffinity purification assays.Shown are10examples from the Core-1,Core-2,and Non-Core data sets.The top panels show Myc-tagged prey expression after affinity purification on glutathione-Sepharose,demonstrating binding to GST-bait.The middle and bottom panels show expression of Myc-prey and GST-bait,respectively.The lanes alternate between extracts expressing GST-bait proteins(ϩ)and GST alone(–).ORF pairs are identified in table S1with the lane number corresponding to the order in which they appear in the table.tome)and phenotypic profiling (phenome)data in S.cerevisiae (17).To investigate to what extent different functional genomic assays should correlate in the context of a multicellular organism,we overlapped WI5with C.elegans transcriptome and phenome data sets.Based on a C.elegans transcriptome com-pendium data set (18),we calculated Pearson correlation coefficients (PCCs)for gene pairs involved in Y2H interactions and compared them with randomized data sets (Fig.2D).About 150Core interactions (9.5%)corre-sponded to gene pairs with significantly high-er PCCs than expected from random (P Ͻ0.05)(table S3).Thus,those pairs can be considered “more biologically likely ”be-cause two completely independent approach-es point to a functional relationship between the corresponding genes.The remaining pairs are labeled “without additional evidence.”Indeed,it is important to note that lack of coexpression does not suggest that the corre-sponding interactions are irrelevant.Indeed,75%of literature pairs,defined as biological-ly relevant,do not correlate with transcrip-tome data (Fig.2D).We also systematically examined Y2H interactions where both proteins belong to common C.elegans expression clusters,or “Topomap mountains ”(18).As an example,a highly connected subnetwork derived from mountain 29(Fig.2E)contains seven pro-teins (ABU-1,ABU-8,ABU-11,PQN-5,PQN-54,PQN-57,and PQN-71)that share common domains (DUF139domain and cysteine-rich repeat).Furthermore,these pro-teins are all expressed in the pharynx (19–21),which suggests that they may act togeth-er in pharynx function or development.For relatively small-scale S.cerevisiae and C.elegans interactome data sets,physical interactions pointed to genes that share sim-ilar phenotypes when knocked out or knocked down (17).To evaluate this idea for the C.elegans interactome,we assembled a collection of phenotypic data based on RNA interference (RNAi)knockdown experiments from WormBase (7,22),and we calculated the percentage of protein interaction pairs that share embryonic lethal phenotypes for the interaction data sets and theirrandomizedFig.2.Analysis of the WI5network.(A )Nodes (representing proteins)are colored according to their phylogenic class:ancient (red),multicellular (yellow),and worm (blue).Edges represent protein-protein interactions.The inset highlights a small part of the network.(B )The proportion of proteins,P(k ),with different numbers of interacting partners,k ,is shown for C.elegans proteins used as baits or preys and for S.cerevisiae proteins.(C )The pie charts show the proportion of interacting preys found in Y2H screens that fall into each phylogenic class.Also shown is the distribution of all preys found and all preys searched in the AD-ORFeome1.0library.(D )Overlap with transcriptome (see text)(18),Pearson correlation coefficients (PCCs)were calculated and graphed for each pair of proteins in the interaction data sets and their corresponding randomized data sets.The red area to the right corresponds to interactions that show a significant relationship to expression profiling data (P Ͻ0.05).(E )Interac-tions between proteins in Topomap mountain 29(18).The dash-circled proteins belong to the same paralogous family (sharing more than 80%homology)and are thus collapsed into one set of interactions.(F )Proportion of interaction pairs where both genes are embryonic lethal (P Ͻ10–7).controls and found a twofold enrichment for the Core and First-Pass data sets (Fig.2F).Similar correlations were also observed for the maternal sterile phenotype and four groups of postembryonic phenotypes (23).Because protein-protein interactions for which both genes are coexpressed across many conditions and show similar pheno-type(s)when knocked down should be considered particularly likely,the global cor-relations described above illustrate how biological hypotheses can be derived from overlapping interactome,transcriptome,and phenome data sets (table S3).In S.cerevisiae ,two proteins that have many interaction partners in common are more likely to be related biologically (24).We exam-ined the C.elegans interactome network for the presence of highly connected neighborhoods by determining the mutual clustering coefficient between proteins in the network (table S4)(24).As an example,we examined the properties of one of the clusters containing such a high-scoring protein pair:VAB-3/C49A1.4(Fig.3).VAB-3and C49A1.4have strong similarity to the products of the Drosophila genes eyeless (ey )and eyes absent (eya ),respectively,but not to each other.EY and EYA are components of a conserved network of transcription factors that regulate eye development (25).VAB-3and C49A1.4are part of a highly interconnected subnetwork in WI5(Fig.3)with proteins that are known or suspected to be functionally linked to VAB-3and C49A1.4,or to their respective orthologs in other organisms.These include (i)EGL-27,which negatively regulates MAB-5in her-maphrodites (26)and is linked to MAB-5through C49A1.4;(ii)WRT-2,an interactor of C49A1.4with similarity to Drosophila Hedgehog,which alleviates repression of eya expression by Cubitus interruptus (27);and (iii)CEH-33and CEH-35,two of four mem-bers of the sine oculis homeobox gene fami-ly,which is involved in the same Drosophila regulatory network of transcription factors as ey and eya (28).Finally,eight proteins in this cluster are annotated in WormPD as involved in membrane function,which suggests a functional relationship between the eyeless transcription network and membrane activity.Together with interologs and previously described interactions,the Y2H data set pro-vides functional hypotheses for thousands of uncharacterized proteins in the C.elegans proteome.Integration with other functional genomic data indicates that the correlation between transcriptome and interactome data,although significant,is lower than what would be expected from observations made in yeast (17).This observation applies to both the Y2H data set described here and well-characterized worm interactions from the literature-derived data set (Fig.2D).This may occur because,unlike unicellular organ-isms,metazoans are complicated by the fact that biological processes may occur different-ly in the organism,across various organs,tissues,or single cells.Our current interactome map also illustrates how a human interactome project would benefit from an ORFeome cloning project using re-combinational cloning systems,such as Gate-way (8).Indeed,recombinationally cloned ORFs can be shuffled at will into various ex-pression vectors needed for different types of protein interaction assays,as exemplified by our ability to transfer bait-and prey-encoding ORFs into Myc-and GST-tagged vectors to validate Y2H interactions.References and Notes1.E.M.Marcotte et al .,Science 285,751(1999).2.M.Pellegrini,E.M.Marcotte,M.J.Thompson,D.Eisenberg,T.O.Yeates,Proc.Natl.Acad.Sci.U.S.A.96,4285(1999).3.P.Uetz et al .,Nature 403,623(2000).4.T.Ito et al .,Proc.Natl.Acad.Sci.U.S.A.98,4569(2001).5.Y.Ho et al .,Nature 415,180(2002).6.A.C.Gavin et al .,Nature 415,141(2002).7.See supporting material on Science Online.8.J.Reboul et al .,Nat.Genet.34,35(2003).9.A.J.M.Walhout,R.Sordella,X.Lu,J.L.Hartley,Science 287,116(2000).10.M.C.Costanzo et al .,Nucleic Acids Res.29,75(2001).11.L.R.Matthews et al .,Genome Res.11,2120(2001).12.A.Davy et al .,EMBO Rep.2,821(2001).13.S.J.Boulton et al .,Science 295,127(2002).14.A.J.M.Walhout et al .,Curr.Biol.12,1952(2002).15.S.H.Strogatz,Nature 410,268(2001).16.F.Jacob,Science 196,1161(1977).17.H.Ge,A.J.M.Walhout,M.Vidal,Trends Genet.19,551(2003).18.S.K.Kim et al .,Science 293,2087(2001).19.J.Gaudet,S.E.Mango,Science 295,821(2002).20.M.Hanazawa,M.Mochii,N.Ueno,Y.Kohara,Y.Iino,Proc.Natl.Acad.Sci.U.S.A.98,8686(2001).21.F.Urano et al .,J.Cell Biol.158,639(2002).22.L.Stein,P.Sternberg,R.Durbin,J.Thierry-Mieg,J.Spieth,Nucleic Acids Res.29,82(2001).23.H.Ge,unpublished observations.24.D.S.Goldberg,F.P.Roth,Proc.Natl.Acad.Sci.U.S.A.100,4372(2003).25.S.Wawersik,R.L.Maas,Hum.Mol.Genet.9,917(2000).26.Q.Ch’ng,C.Kenyon,Development 126,3303(1999).27.K.S.Pappu et al .,Development 130,3053(2003).28.C.Dozier,H.Kagoshima,G.Niklaus,G.Cassata,T.R.Burglin,Dev.Biol.236,289(2001).29.We thank members of M.V.’s laboratory for theirinput and help;C.Boone,G.Achaz and D.Allinger for discussions;the sequencing staff at Agencourt Bio-sciences for technical assistance;the ORFeome meet-ing participants for their input;C.McCowan,T.Cling-ingsmith,and C.You for administrative assistance;and C.Fraughton for laboratory support.This work was supported by a grant from NHGRI and NIGMS awarded to M.V.Other support includes an NSF award (K.C.G.);NIGMS grants (S.v.d.H.,S.E.M.,J.W.H.);a Department of Defense Predoctoral Fellow-ship (B.B.);an award from the Ligue Nationale Contre Le Cancer (e ´quipe labelise ´e)(C.S.,A.C.);an institu-tional HHMI grant (F.P.R.,G.F.B);and Fellowships from EMBO (P.-O.V.),NSF (D.S.G),Ryan,Milton (S.L.W.),Fu (L.V.Z.),and Leukemia Research Founda-tion (M.E.).Supporting Online Material/cgi/content/full/1091403/DC1Material and Methods Fig.S1Table S1to S5References11September 2003;accepted 1December 2003Published online 2January 2004;10.1126/science.1091403Include this information when citing thispaper.Fig.3.Graphical representation of a highly interconnected subnetwork around VAB-3and C49A1.4.Biological functional classes were obtained from WormPD (10).。
科学文献

Abstract
This paper examines the consequences of the interaction between temporal period doubling and spatial pattern formation. We propose a simple discrete time, spatially continuous system, where the discrete time dynamics incorporates period doubling and the spatial operator imposes patterning at a preferred length scale. We nd that this model displays a variety of bifurcations between di erent spatio-temporal states and these bifurcations are generic in that they do not depend on the details of the model. The results from our simple model bear remarkable similarities with recent experiments on a vertically vibrated granular layer. PACS numbers: 81.05.Rm,46.10.+z, 47.54.+r, 05.45.+b
1
In this paper we examine the consequences of the interaction between temporal period do
OA-22
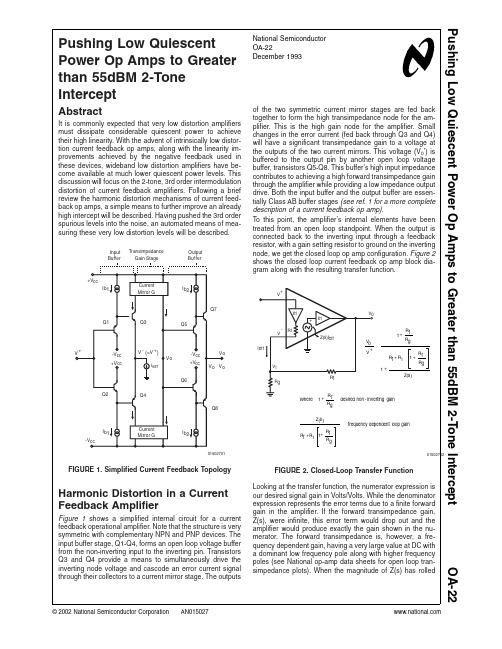
Input Transimpedance
Buffer
Gain Stage
Output Buf fer
+Vcc I b1
Current Mirror G
I b2
National Semiconductor OA-22 December 1993
of the two symmetric current mirror stages are fed back together to form the high transimpedance node for the amplifier. This is the high gain node for the amplifier. Small changes in the error current (fed back through Q3 and Q4) will have a significant transimpedance gain to a voltage at the outputs of the two current mirrors. This voltage (Vo’) is buffered to the output pin by another open loop voltage buffer, transistors Q5-Q8. This buffer’s high input impedance contributes to achieving a high forward transimpedance gain through the amplifier while providing a low impedance output drive. Both the input buffer and the output buffer are essentially Class AB buffer stages (see ref. 1 for a more complete description of a current feedback op amp). To this point, the amplifier’s internal elements have been treated from an open loop standpoint. When the output is connected back to the inverting input through a feedback resistor, with a gain setting resistor to ground on the inverting node, we get the closed loop op amp configuration. Figure 2 shows the closed loop current feedback op amp block diagram along with the resulting transfer function.
190-622

Exam:190-622Titl e :Notes Domino 6 Managing Servers and Users��Ver : 01.09.06QUESTION 1Which one of the following explains why Hans cannot retrieve an HTML file whichhe knows is on the Domain server?A. The CGI script are not enabled.B. The default URL is set to ?Open.C. Hans has Depositor access to the Domino server.D. The HTML files are not located in the HTML directory listed in the server or Web site configuration documents.Answer: AQUESTION 2Jim's Notes workstation's Smart Upgrade did not work. Which one of the following could be the cause of Smart Upgrade failing?A. Jim did not access his mail database.B. Jim's Personal Address Book has the filename JIM.NSF.C. Jim's Location document does not correctly specify his home server.D. Jim does not have administrator access to his Windows 2000 workstation. Answer: AQUESTION 3When a policy selected for a particular user?A. During registrationB. During workstation setupC. When the user's certifier ID is createdD. When the user accesses their mail serverAnswer: BQUESTION 4Jessica wants to assign an explicit policy to a user. Which one of the following documents should be modified to assign the policy to the user?A. The policy documentB. The user's Person documentC. The office Location documentD. The mail server's configuration documentAnswer: BQUESTION 5Which one of the following statements about the Smart Upgrade database isTRUE?A. The database must have ODS version 41.B. The database must have the filesystem SMUPKIT.NSFC. The database must contain the relevant Notes RS information.D. The database must exist on at least one server in the domain.Answer: DQUESTION 6Amy wants to decommission an existing source server. Before transferring the applications, she runs a Decommission Server Analysis report. Which one of the following types of information does this tool provide?A. Source server information onlyB. Target server information onlyC. A compression between source server and target serverD. A detailed report of everything transferred from the souce server to te target server once the transfer takes placeAnswer: CQUESTION 7In addition to Notes database, which one of the following files on a Domino server should be backed up in order that new users can created in case of the server?A. The CACHE.DSK fileB. Certifier ID filesC. The user's DESKTOP.DSK fileD. The server's BOOKMARK.NSF file.Answer: BQUESTION 8Brie left the Create New Replicas field blank in a Server document. Who can create new replica databases on that server?A. No oneB. AdministratorsC. Local Domain ServerD. Everyone in the domainAnswer: AQUESTION 9Which one of the following statements about the compact server task is TRUE?A. The compact process re-indexes views.B. By default, compact runs every day at 3 P.M.C. Compact may be scheduled via a program document.D. Compact is listed in the TASKS line on all Notes 6/6.5 workstations.Answer: CQUESTION 10Josh has cross certified the /BOX organization to his /ACME organization. An administrator from the BOX organization has cross certified the /ACME to the/BOX organization. When a /BOX server attempts to assess a /ACME server, it receives a " You are not authorized to access this server" error. Which one of the following could be the cause of this error?A. The Box server's ID does not contain a copy of the Acme certifier.B. The Box server's ID file needs to be updated with the cross certificate.C. The Box administrator needs to add the Box server to the LocalDomainServer group.D. The Box server has not been granted access to the Acme server in the Acme server document.Answer: DQUESTION 11Suzanne, a Notes administrator sets the "Allow Anonymous Notes connections" setting in the Server document to yes. Which one of the following levels of accesswill Bob, Notes user, have when he accesses a database with the following settings:-Default- Editor*/ACME - ReaderAnonymous - AuthorOtherDomainServer -NoAccessA. ReaderB. AuthorC. DefaultD. No AccessAnswer: BQUESTION 12Amy is setting up session-based name-and-password authentication. Which one ofthe following is required for this to work?A. JavaB. COBRAC. CookiesD. JavaScriptAnswer: CQUESTION 13Jeff cross certified the Organizational Unit (OU) /NYC/ACME with his organization's /BOX Organizational (O) certifier. Which one of the following statements are correct for this scenario?A. Users or server with /NYC/BOX certificate can access /ACME servers.B. Users with an ACME ID can access any of Box's severs that have a /NYC/BOX certificate.C. Any user or server ID with the /NYC/ACME certificate can access any server in the /BOX organization if they have the appropriate cress certificate.D. Server with the /NYC/ACME certificate can access any server in the /BOX organization if they have the appropriate cress certificate but no .NYC/AME user can access /BOX servers.Answer: AQUESTION 14Robert's windows 200 Domain server has frozen with no error output on theserver's screen or other indication that anything is wrong. Which on of the followig can cause this problem?A. The server was replicating with another serverB. The server's transaction log was being updated.C. Robert has forced mail routing to another server.D. Microsoft windows Quick Edit mode was enabled for the server console window. Answer: DQUESTION 15Bob left the Create New Databases field empty in a Server document. Who is authorized to create new databases on the server?A. No oneB. Administrators onlyC. LocalDomainServer onlyD. Anyone with access to the serverAnswer: DQUESTION 16Which one of the following statements about transaction logging is TRUE?A. The transaction log is always named TRANSLG.NSFB. Transaction logging must be enabled on all Domain 6/6.5 servers.C. All database changes are written to a transaction log in a batch.D. Transaction logging is enabled by default on all Domain 6/6.5 servers. Answer: CQUESTION 17Raul wants to review reads and writes to databases from various Notes user. Where would he locate this information?A. LOG.NSFB. DOMLOG.NSFC. ACTINFO.NSFD. ACTIVIOTY.NSFAnswer: AQUESTION 18Which one of the following statements about Domino SSL server security is TRUE?A. SSL must be enabled for all server ports.B. SSL can only be enabled for POP3, IMAP and SMTP.C. If a server is using SSL, users must access the server using a browser.D. You can require SSL connections for all databases on a server or for an individual database.Answer: DQUESTION 19Dawn used the Administration Process (AdminP) to convert a non-roaming Note user to a roaming Notes user. In which one of the following does the Administration Process update the user's status from non-roaming to roaming?A. Person documentB. Server documentC. Location documentD. Configuration documentAnswer: AQUESTION 20Orin changes the name of a group using the Domino Administrator client. How often does the Administration process (AdminP) update group names in Author and Reader Names fields?A. DailyB. HourlyC. WeeklyD. ImmediatelyAnswer: CQUESTION 21Jonathan has been moved out of one group and into another. How long before this change will be effective throughout the seventeen servers in his domain?A. One hour.B. ImmediatelyC. It is dependent on the replication schedule for NAMES.NSF.D. The Administrator Process (AsminP) will change his group membership throughout the domain within 24 hours.Answer: CQUESTION 22Maria got married ad changed her last name. She needs to have her name changedin the Domino Directory. Which one of the Following actions did the administrator use to change Maria's name?A. Edit PersonB. Move to folderC. Rename Selected PeopleD. Recertify Selected PeopleAnswer: CQUESTION 23Karen uses the Administration Process (AdminP) to move a user's main file to a different mail server. Which one of the following must Karen do in order for thenew mail file to be created and the old mail file to be deleted?A. Update the user's Location documents.B. Modify the mailserver field in the user's person documentC. Approve the deletion of the old mail file in the ADMIN4.NSF database.D. Give the user rights to create new databases on the new mail server.Answer: CQUESTION 24When a user is deleted from the Domino Directory, which one of the following tasks must be approved in the ADMIN4.NSF database by the administrator before theAdministration process (AdminP) performs the task?A. Remove the user from groups.B. Delete the user's mail database.C. Add the user to a Terminations groupD. Remove the Person document from the domain's Domino Directly.Answer: BQUESTION 25Jennifer is moving user from /Madrid/ACME to /Boston/ACME. Which one of the following will she need to perform this task?A. The Web Administrator clientB. Just the destination certifierC. Author access to the domain's Domino DirectoryD. Both the /Madrid/ACME and the /Boston/ACME certifier ID filesAnswer: DQUESTION 26Which one of the following processes ensures that group names in ACLs are updated when an administrator changes the name of the group in the domain's Domino Directory?A. UpdateB. UpdallC. ConvertD. Administration Process (AdminP)Answer: DQUESTION 27Which one of the following may cause the error "You are not authorized to use the server on remote consol"?A. The user is not authorized to use the server.B. The server does not allow remote administration.C. The user's ID file is not cress certified with the server.D. The person in not listed in the Administrators field of the Server document. Answer: DQUESTION 28Jose wants to see the replication topology map of his Notes domain. To see this topology, what must he do?A. Load the MAPS EXTRACTOR server task.B. Load the TOPMAPS EXTRACTOR server task.C. Load the MAPTOP EXTRACTOR server task.D. Load the TOPOLOGY EXTRACTOR server task.Answer: AQUESTION 29Which one of the following would be helped by using the Mail Trace feature?A. A user cannot read encrypted e-mail.B. All mail messages to a particular user are not routing properly.C. Mail is not routing from outside your domain to your domain's mail servers.D. Mail messages from one user in your domain are not routing properly to external users.Answer: BQUESTION 30Geoff wants to force replication of NAMES.NSF between ServerA/Acme and ServerB/Acme. Which one of the following console commands will accomplish this?A. LOAD REPLICATIONB. REP SERVERA SERVERBC. REP SERVERB/ACME NAMESD. TELL SERVERA REP SERVERB NAMESAnswer: CQUESTION 31Both Server A and Server B are in the domain and in the same Domain Network Name. What is the minimum number of Connection Documents needed for replication to occur in both directions?A. TwoB. OneC. ThreeD. NoneAnswer: BQUESTION 32Which one of the following may prevent the Administration Process (AdimnP)from updating a user's name in their ID file?A. The user accepted the name change.B. The CERTLOG.NSF database does not include a copy of the user's certificate.C. The user's name is not listed in the Domino Directory's Access Control List (ACL).D. The user did not accept the name change in the first twenty-four hours after the administrator initiated it.Answer: BQUESTION 33An agent that is designed to run "On schedule more than once daily" does not complete. Which one of the following could cause this problem?A. The agent must be initiated by user action.B. The agent can only run hourly, weekly or monthly.C. The developer must start the agent manually the first time.D. The agent has exceeded the value in the Max Execution time in the Agent Manager settings of the Server document.Answer: DQUESTION 34Koki, a Domino administrator, is trying to move a server within the certification hierarchy by running the administration Process task. He recertifies the server witha different certifier ID but the change never tasks place. Which one of the following will cause the recertifying process to fail?A. The server has a hierarchical certificate.B. The Administration Process was enabled.C. The Certification Log was placed on the Domino Administrator workstation.D. A replica copy of the Administration Requests database was placed was placed on every server in the domain.Answer: CQUESTION 35Which one of the following may cause the error "You are not autjorized to accessthe server"?A. The user's ID file has expired.B. The server's ID file has expired.C. The cross certificate exists on both directions.D. The Access List in the Server document denies the user access.Answer: DWhich one of the following types of information is stored in an .NSD file?A. Current server statusB. Notes storage directoriesC. Information regarding a system crashD. HTTP access information for the serverAnswer: CQUESTION 37Both Server A and Server B are in the Acme domain, are correctly listed in DNS, are in the same Domino Network Name. How many Connection Document are required mail to route for Server B and from Server A to Server B and form Server B to Server A?A. OneB. TwoC. ThreeD. NoneAnswer: DQUESTION 38Which one of the following may cause the error "Unable to find path to server" on a Notes workstation?A. The user's ID file has expired.B. Server's hostname is not resolving.C. The Personal Address Book has been deleted.D. Server does to have a Connection document to the server.Answer: BQUESTION 39Jeff is trying to create a replica of STATUS.NSF but is unable to create the local copy. Which one of the following could cause this problem?A. Jeff only has Reader access in the database's Access Control List (ACL).B. Jeff only has Author access in the database's Access Control List (ACL).C. Jeff only has Editor access in the database's Access Control List (ACL).D. Jeff has not been given the right to replicate or copy documents in the database's Access Control List (ACL).Answer: DWhat is the minimum level of access a Notes 6/6 5 user must have to run the Out of Office agent?A. AuthorB. EditorC. ManagerD. DesignerAnswer: BQUESTION 41Jose is creating a new password for himself. Which one of the following will password quality checking indicate as the least secure password?A. Mixed case passphrasesB. All uppercase passwordsC. Passphrases containing numbers and punctuationD. Would found in Notes dictionaries during spell checkAnswer: DQUESTION 42Kurt created an event generator. Which one of the following will this do?A. Restart the event task.B. Initiate a task a server.C. Create entries in the EVLOG.NSF databases.D. Monitor a task a task or statistic by probing a server.Answer: AQUESTION 43Which one of the following controls when an agent runs on a server?A. The Agent Manager taskB. Server document, Agent Settings field.C. Configuration document, Agent Setting filed.D. The AGENTSCHED parameter in the server's NOTES.INI file.Answer: BQUESTION 44Why did Sophia create an event handler?A. To define a threshold for a statistic.B. So that server sets quotas on database size.C. In order to have the server log events to the EVENTS4.NSF database.D. To be notified via page if the server's available disk space fails below 25%. Answer: DQUESTION 45What is the DOMLOG.NSF database used for?A. To track all users who access the Domino serverB. To track users who access the Domino server via HTTPC. To track users who access the Domino server via NNTPD. To track user who authenticate with the Domino server.Answer: BQUESTION 46Which one of the following best describes the available directory architecture in a Domino 6 domain?A. A centralized directory architectureB. Both distributed and centralized directory architecturesC. None of the answers applyD. A distributed directory architectureAnswer: BNotes & Domino 6 supports both a distributed directory architecture and a central directory architecture.In a Distributed Directory architecture in a Domino domain, in which all servers use the standard Domino Directory in a central directory architecture,some servers store Configuration Directories (contains configuration settings only) and then use the standard Domino Directories on remote servers for lookups. QUESTION 47What is the significance of Kit Type=1 and where is it located?A. Server, in the Notes.iniB. Workstation, in the server documentC. Workstation, in the Notes.iniD. Server, in the configuration documentAnswer: CSpecifies which program you are running:1 - Workstation2 - ServerQUESTION 48Which on of the following is the proper syntax for forcing replication via a Domino server console command?A. Replicate [databasename] servernameB. Replicate servername [databasename]C. Replicate sourceservname/sourcedatabasenamedestinatationservername/destinationdatabasenameD. Replicate servername/databasenameAnswer: BSyntax: Replicate servername [databasename]Description: Forces replication between two servers (the server where you enter this command and the server you specify). Use the server's full hierarchical name. If the server name is more than one word, enclose the entire name in quotes. To force replication of a particular database that the servers have in common, specify the database name after the server name. The initiating server (where you're currently working) first pulls changes from the other server, and then gives the other server the opportunity to pull changes from it. You can use this command to distribute changes quickly or to troubleshoot a replication or communication problem.QUESTION 49Mary needs to rebuild all used views in her database. Which one of the following commands could she issue on the Domino server console?A. UPDALL -ALLB. UPDALL -*C. UPDALL -RD. UPDALL -XAnswer: CRebuild: All used viewsUPDALL -RRebuilds all used views. Using this option is resource-intensive, so use it as a last resort to solve corruption problems with a specific database.QUESTION 50What database is created when you run the Decommission Server Analysis tool?A. Log AnalysisB. DecommissionC. Server analysisD. ResultsAnswer: DWhen you run the Decommission Server Analysis tool, you create a Results databasecontaining detailed information comparing the source server and the target server. The source server is the server being removed from service, and the target server is the server taking the place of the source server. The source and the target servers must be Domino servers that have hierarchical names and that are in the same domain.QUESTION 51Which of the following uniquely identifies a document across all replicas of a database?A. UNIDB. NotelIDC. ReplicalDD. OFIDAnswer: AThe UNID (universal ID) is a 32-character combination of hexadecimal digits (0-9, A-F) that uniquely identifies a document across all replicas of a database.QUESTION 52A Program document can not be used to run which of the following types of commands or programs?A. API programsB. UNIX shell scriptsC. OS/2 command filesD. Java appletsAnswer: DA Program document is used to automatically run a server task at a specific time. You can also use a Program document to run an OS/2 command file, a UNIX shell script or program, or an API program. You can use the Program document to schedule tasksand/or programs.QUESTION 53Sandra has migrated all of her users and applications from Nagano/CertFX toMoscow/CertFX. Which one of the following can she use to ensure she has transferred all database and settings?A. Tivoli Server Analyzer for Lotus DominoB. The administration client action "Show Server Difference"C. Cluster comparison toolD. Server decommission Analysis toolAnswer: DThe Decommission Server Analysis tool generates a categorized list of items that were analyzed. Each category represents a different aspect of a server's configuration thatneeds attention. Within each category, items are listed alphabetically. Each item lists any differences between the source and the target server's settings or values. In the Results database, you can view the categorized list of the items that were analyzed. QUESTION 54A Security Policy Settings document controls which of the following?A. The Notes and Internet passwordsB. None of the aboveC. The administration ECL as well as Notes and Internet passwordsD. The administration ECL as well as Internet passwordsAnswer: CA Security policy settings document controls the Administration ECL as well as Notes and Internet passwords.QUESTION 55Which one of the following can you specify in the setup profile when performing a seamless upgrade?A. To which groups the client must be addedB. Which mail file template to apply according to the Lotus Notes client versionC. All of the aboveD. Which address book template to apply according to the Lotus Notes client version Answer: BWhen the Domino server receives the call to upgrade a mail file template, the server checks for a Desktop policy settings document or Setup Profile assigned to the user. The Desktop policy settings document and the Setup Profile contain a "Mail Template Information" section. This section is new to Setup Profiles in Notes 6. In this section, you can specify which mail file template to apply according to the Lotus Notes client version. QUESTION 56Which one of the following is not an Event Generator document?A. TCP server even generatorB. NRPC server event generatorC. Task status event generatorD. Statistic event generatorAnswer: BMonitoring Configuration documents define and configure what constitutes an event and how the event is handled. You can also use these documents to customize the message that appears on screen when an event occurs. The Monitoring Configuration documents are stored in EVENTS4.NSF.Event Generator documents are also stored in the Monitoring Configuration database, EVENTS4.NSF.QUESTION 57Which one fo the following best describes the information that can be found in the DOMLOG.nsf database?A. Both Lotus Notes and web activity on the Domino serverB. Lotus Notes activity on the Domino serverC. Web activity on the Domino serverD. Activity trends and health reporting of the Domino serverAnswer: CYou can log your server activity and Web server requests to the Domino Web server log (DOMLOG.NSF) database. This option may be preferable if you want to create views and view data in different ways. Logging to a database is somewhat slower than logging to text files, especially at very busy sites, and the size of the database can become large so that maintenance becomes an issue. However, if you use the Domino Web server log, you can treat this information as you would other Notes databases, and you can use built-in features to analyze the results.QUESTION 58Michael needs to force replicate between the following two servers:Notes Hub/Tools/ CertkillerSametime Hub/Tools/ CertkillerMichael is using a remote console on SametimeMichael is using a remote console on Sametime Hub/Tools/ Certkiller . Which oneof the following Domino server console commands did he issue?A. REPLICATE NotesHubB. REPLICATE Notes HubC. REPLICATE Notes Hub/Tools/ CertkillerD. REPLICATE Notes Hub/Tools/ Certkiller "Answer: DSyntax: Replicate servername [databasename]Description: Forces replication between two servers (the server where you enter this command and the server you specify). Use the server's full hierarchical name. If the server name is more than one word, enclose the entire name in quotes. To force replication of a particular database that the servers have in common, specify the database name after the server name. The initiating server (where you're currently working) first pulls changes from the other server, and then gives the other server the opportunity to pull changes from it. You can use this command to distribute changes quickly or to troubleshoot a replication or communication problem.Which one of the following is not an available policy settings document?A. Ecplicit policiesB. Exception policiesC. Implied policiesD. Organizational policiesAnswer: CA policy is a collection of individual policy settings documents.There are three types of policies: Organizational policies, Explicit policies and Exception policies.Organizational policies are applied automatically to users or groups based on the organizational structure.Explicit policies, like they sound, are assigned explicitly. They apply settings directly to a user, instead of through the organizational hierarchy.Exception policies allow users to control their own user settings.QUESTION 60Which one of the following statements about transaction logging is TRUE?A. Transaction logging is used to support Domino clusteringB. Logged transactions are stored in memoryC. Logged transactions are written to disk in a batchD. Transaction logging is enabled by default on all Domino 6 serversAnswer: CTransaction logging captures all the changes that are made to databases and writes them to a transaction log. The logged transactions are written to disk in a batch when resources are available or at specified intervals.QUESTION 61Hoke needs to make design changes to forms and views of a production database.He plans to make the changes locally in a template and then have the server updatethe production database with the changes. Which one of the following server tasksdoes the administrator run in order for the changes to be propagated?A. The REPLICA server taskB. The FIXUP -D server taskC. The DESIGN server taskD. The UPDALL server taskAnswer: CThe DESIGN or designer task updates all database design elements from their master template(s). The DESIGN task runs daily by default at 1 AM.A user has been added to a group with author access in the salesdatabase. When she enters the database she finds that she is able to change her co-workers documents as well as her own. Why?A. She is listed individually in the ACL with reader accessB. The ACL has become corrupt and needs fixed upC. None of the aboveD. She is listed in another group in the ACL with editor accessAnswer: DA name is included in two or more groups. The name receives the access of the group with the highest access.QUESTION 63Many needs to rebuild all used views in her database. Which one of the following commands could she issue on the Domino server console?A. UPDALL -RB. UPDALL -XC. UPDALL -ALLD. UPDALL -*Answer: ARebuild: All used viewsUPDALL -RRebuilds all used views. Using this option is resource-intensive, so use it as a last resort to solve corruption problems with a specific database.QUESTION 64Which one of the following should not be included in a NNN?A. Domino servers on a WANB. Domino servers on Dial-upC. None of the aboveD. Domino servers on a LANAnswer: BThe Domino Server Setup program automatically places all servers that are in a Domino domain and that run the same network protocol in the same Notes named network (NNN). In the Server document, the setup program assigns each NNN a default name in the format portname network.After you complete the Server Setup program, rename the NNN for each network port in the Server document. It is useful if the name reflects both the location of the network and its protocol. For example, if your company has a TCP/IP network and has LANs in Boston and San Francisco, change the name of the NNN in Boston to "TCPIP Boston。
C族四级任务

C族4级战斗任务&故事线任务V1.1奥运最新版攻略 (2)前言 (2)任务地点介绍 (2)任务基本社会技能 (2)任务基本配置 (2)任务介绍 (3)狂暴 (3)阻止小偷 (3)货柜递送 (3)侦察1/3(古斯塔) (4)侦察1/3(血袭者) (4)侦察2/3(古斯塔/血袭者) (4)侦察3/3(古斯塔/血袭者) (4)袭击 (5)海盗屠杀 (5)海盗侵略 (5)双匪劫(古斯塔) (6)双匪劫(血袭者) (6)无赖的奴隶贩子1/2 (6)无赖的奴隶贩子2/2 (6)大举进犯 (7)自由无人机的骚扰 (7)无人机的袭击 (7)抢救矿冶设施 (8)扎XXX的右使者 (8)危难中的少女 (8)古斯塔斯间谍 (9)血袭者间谍 (9)未授权的军队 (9)拦截走私船 (10)疤痕 (10)世界碰撞(古斯塔) (10)世界碰撞(血袭者) (11)复仇之火(古斯塔) (11)复仇之火(血袭者) (11)古斯塔斯(天使的妄想)的妄想 (12)截击破坏者 (13)死人不会说话 (13)封锁线 (13)腹背受敌(1/5) (14)腹背受敌(3/5) (14)腹背受敌(4/5) (15)腹背受敌(5/5) (15)故事线任务可以增加势力声望 (15)绑架(A Case Of Kidnapping) (15)船厂盗窃犯(古斯塔)(Shipyard Theft) (16)船厂盗窃犯(血袭者)(Shipyard Theft) (16)隐藏行踪(Covering Your Tracks) (16)C族4级战斗任务&故事线任务V1.1奥运最新版攻略前言相信大家对于我写的/thread-126838-1-1.html这个帖子有点印象,当时写这个帖子的时候比较仓促,而且正好处于LP比较值钱的时候,所以我当时这个帖子是以如何快速得到LP为主要目的,因此可能不适合很多新来做任务的朋友,加上时间已经过去4个月了,所以特地在奥运期间,重新将该任务帖子整理编辑,以方便新人老人共勉,另外该帖完成后地址会在C任务党频道“CE龙门客栈”中置顶,还望各位多多支持,谢谢。
New Microsoft Word Document

贪婪洞窟看了个游戏贪婪洞窟,评价很高,下载后感觉很好玩。
现在玩到噩梦61层,谈谈个人玩的经验首先,贪婪洞窟是个比较耗费时间的游戏(对于平民玩家)。
贪婪洞窟符文前期地图会刷符文,加攻击、加防御、加蓝、加魔力。
贪婪洞窟任务不充值又想拿钻石的方法只有做任务了,每十层会有35个任务,运气好的可以拿到400+加钻石。
贪婪洞窟老奶奶商店转动转盘前上传存档,,如果没有转到好东西可以,再下载可以让再次转动转盘。
贪婪洞窟科恩帽子科恩帽子,可以说是要玩穿整个游戏必备的装备,同时去老奶奶哪里买个手套,多刷刷买双幸运高的手套。
加点方面我选择的是吸血流:属性点主加攻击,防御,血量。
核心技能:虹吸斩,三连击。
主要装备属性选择:攻击,防御,生命,魔法恢复。
加点方面,幸运必点10,技能下方辅助技能点左边叁个陷阱隔空顺移点陷阱抗性是因为陷阱真的很痛,隔空可以远远拿装,顺移则是方便跑路。
1-20层,没什么可说的,随便凑凑一身金装,然后把武器强化+3继续闯到20打boss。
前期任务好做,尽量多做做任务赚钻石。
钻石前期留着不要用。
21-40层,初期比较费劲,慢慢做任务,等40层之前的任务做的差不多的时候,一身的装备也应该可以打boss了,boss比较简单,从21-40层开始刷药水,带够药水就可以过boss了,很简单。
40层boss开始掉至关重要的装备了贪婪洞窟科恩帽子,这时候做任务、成就等得的钻石应该也有1500+了,这时候先去老奶奶那里买科恩手套,同时尽可能的强化。
41-之后的所有楼层打法,首先科恩双件套备齐,尽可能穿一身强化+3的幸运装,每层开始前先穿幸运装进入,各种摸箱子,41层之后就开始出现橙装了,当身上装备大多都是+3的金装时候就可以打boss了,当然装备的优先级是攻击,防御,生命,魔法恢复。
这里说说魔法恢复,这个是为你攥药水过boss最核心的属性了。
保证普通关卡回魔在20以上就行,做好这些就可以轻轻松松的过boss了,普通100层很简单,个人幸运属性到200+,摸箱子基本一趟10+金装,3+橙装。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
本文部分内容来自网络整理,本司不为其真实性负责,如有异议或侵权请及时联系,本司将立即删除!
== 本文为word格式,下载后可方便编辑和修改! ==
封印者资料
篇一:龙抽老埃
龙抽老埃FTK
青眼白龙*3
被封印者的左腕*1
被封印者的右足*1
被封印者的左足*1
被封印者的右腕*1
青眼卡通龙*2
被封印的艾克佐迪亚*1
龙骑兵团-叉龙*3
传说的白石*3
一时休战*1
抵价购物*3
调和的宝札*3
哥布林暴发户*3
星球改造*2
卡通目录*3
无之炼狱*3
强欲而谦虚之壶*1
超再生能力*2
龙之溪谷*3
老埃5部件
白石3
青眼3
护卫龙3
暗之量产工厂3
超再生3
八抽3
调和的宝札3
QQ壶2
一时休战3
暗黑取引3
成金3
死者转生1
魔法石2
军大会八强(积分第六名)
卡组类型:秒杀型
适用禁卡表:201X0901制限卡表卡组构架:
【Main DECK:40】
■Monst(来自:WWw. : 封印者资料 )er Cards:12
1 Left Arm of the Forbidden One1 Right Arm of the Forbidden One1 Left Leg of the Forbidden One1 Right Leg of the Forbidden One1 Exodia the Forbidden One3 Cardcar D 卡片汽车·D
3 Swift Scarecrow 速攻的稻草人1 Sangan 三眼
Spell Cards:9
1 Heavy Storm 大风暴
2 Pot of Duality 强欲而谦虚之壶
3 One Day of Peace 一时休战3 Upstart Goblin 哥布林暴发户■Trap Card:19
2 Waboku 和睦的使者
2 Threatening Roar 威吓之咆哮
3 Accumulated Fortune 积累的幸福3 Jar of Greed 强欲之瓶
3 Hope for Escape 对活路的希望3 Gift Card 礼品卡
3 Reckless Greed 无谋的贪欲
篇二:禁卡表
交换蛙
胜利龙混沌帝龙 -终焉的使者- 杀人蛇御用守护者混沌之黑魔术师电子壶千眼纳祭神处刑人-摩休罗神圣魔术师暗黑俯冲轰炸机月读命命运英雄圆盘人恶魔弗兰肯同族感染病毒纤维壶电子鱼人-枪手(New,无限制?禁止)魔导科学家精神脑魔(New,限制?禁止)八汰鸟救援猫噩梦之蜃气楼爱恶作剧的双子恶魔王家的神殿收押苦涩的选择强引的番兵强夺强欲之壶心变雷击次元融合生还的宝札洗脑蝶之短剑-回音天使的施舍鹰身女妖的羽毛扫过早的埋葬
突然変异
大寒波质量加速器遗言状王宫的敕命现世与冥界的逆转第六感刻之封印破坏轮最终一战!死之卡组破坏病毒
黑森林的魔女
限制卡:
元素英雄天空侠欧尼斯特混沌战士 -开辟的使者-(New,禁止?限制)剑斗兽枪斗三眼怪真六武众-紫炎(New,无限制?限制)僵尸带菌者暗黑武装龙蒲公英狮深渊的暗杀者科技属超图书馆员(New,无限制?限制)星骸龙(New,准限制?限制)新宇宙侠·大地鼹鼠死灵之颜冰结界之龙三叉龙冰结界之龙光枪龙被封印的艾克佐迪亚被封印者的右足被封印者的右腕被封印者的左足被封印者的左腕方程式同调士(New,无限制?限制)黑羽-月影之卡鲁特黑羽-疾风之盖尔
棉花糖。
