H3C5500详细配置及说明
华三S5500交换机配置

基于多个VLAN 在一个端口
[H3C]interface GigabitEthernet 1/0/2 进入第二个端口设置
[H3C-GigabitEthernet1/0/2]port link-type trunk 端口的链路类型的树干
[H3C-GigabitEthernet1/0/2]port trunk permit vlan all 如果使用单独的就不用增加这项
[H3C]pim
static-rp 192.168.100.1
undo 删除
[H3C]undo vlan 103 删除vlan 103
[H3C]interface GigabitEthernet 1/0/3 进入端口3
Please wait........................................... Done.
[H3C-GigabitEthernet1/0/2]quit 设置好了第二个端口的VLAN可以通过所有
[H3C-GigabitEthernet1/0/2]port trunk permit vlan 122 在此端口上增加VLAN组
[H3C-Vlan-interface104]ip address 192.168.69.1 255.255.255.0 设置IP
步骤三:将所要配置端口加入到VLAN组
[H3C] interface GigabitEthernet 1/0/1 设置第一个端口
[H3C-GigabitEthernet1/0/1]port access vlan 101 设置端口一为VLAN 101组
[H3C-GigabitEthernet1/0/3]undo port link-type 删除port link-type
h3cs5500series参数

h3cs5500series参数
H3C S5500系列交换机是一款企业级网络设备,具有丰富的功能和参数。
以下是关于H3C S5500系列交换机的一些参数:
1. 端口数量,H3C S5500系列交换机通常提供多种端口配置,包括千兆以太网端口和万兆以太网端口,可以满足不同规模网络的需求。
2. 可扩展性,这个系列的交换机通常具有良好的可扩展性,可以支持灵活的端口扩展和堆叠功能,以满足不断增长的网络需求。
3. 交换容量,H3C S5500系列交换机具有高速的交换能力,支持大容量的数据传输,能够满足大型企业网络的需求。
4. 安全性,这个系列的交换机通常提供多种安全功能,包括访问控制列表(ACL)、端口安全、802.1X认证等,可以保护网络不受未经授权的访问和攻击。
5. 管理和监控,H3C S5500系列交换机通常支持远程管理和监控功能,可以通过Web界面、命令行界面(CLI)或SNMP协议进行
管理和监控。
6. 功耗和环保,这个系列的交换机通常具有较低的功耗设计,
符合节能环保的要求,有助于降低企业的能源消耗和运营成本。
总的来说,H3C S5500系列交换机是一款功能丰富、性能稳定、安全可靠的企业级网络设备,适用于大中型企业的局域网接入和汇聚,能够满足复杂网络环境下的需求。
希望以上信息能够全面回答
你的问题。
H3C 5500 -EI SI IRF 配置
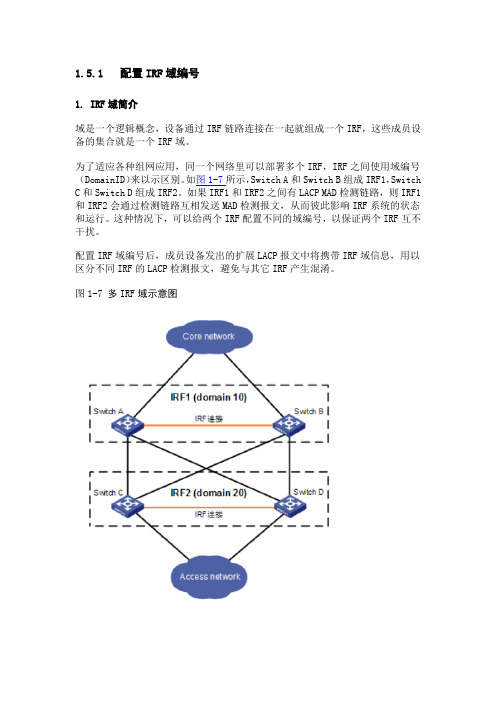
1.5.1 配置IRF域编号1. IRF域简介域是一个逻辑概念,设备通过IRF链路连接在一起就组成一个IRF,这些成员设备的集合就是一个IRF域。
为了适应各种组网应用,同一个网络里可以部署多个IRF,IRF之间使用域编号(DomainID)来以示区别。
如图1-7所示,Switch A和Switch B组成IRF1,Switch C和Switch D组成IRF2。
如果IRF1和IRF2之间有LACP MAD检测链路,则IRF1和IRF2会通过检测链路互相发送MAD检测报文,从而彼此影响IRF系统的状态和运行。
这种情况下,可以给两个IRF配置不同的域编号,以保证两个IRF互不干扰。
配置IRF域编号后,成员设备发出的扩展LACP报文中将携带IRF域信息,用以区分不同IRF的LACP检测报文,避免与其它IRF产生混淆。
图1-7 多IRF域示意图2. 配置IRF域编号表1-2 配置IRF域编号●IRF域编号的配臵必须在开启LACP MAD检测功能之前进行。
●建议用户为同一IRF中的成员设备配臵统一的IRF域编号,否则会影响LACP MAD检测功能的正常运行。
●在完成上述配臵后,在任意视图下执行display irf命令可以显示IRF域编号的配臵情况,通过查看显示信息验证配臵的效果。
1.5.2 配置成员编号IRF通过成员编号唯一的识别各成员设备,设备上的许多信息、配置与成员编号相关,比如接口(包括物理接口和逻辑接口)的编号以及接口下的配置、成员优先级的配置等。
●修改成员编号后,如果没有重启本设备,则原编号继续生效,各物理资源仍然使用原编号来标识;配置文件中,只有IRF端口的编号以及IRF端口下的配置、成员优先级的配置会跟着改变,其它配置均不会跟着改变。
●修改成员编号后,如果保存当前配置,重启本设备,则新的成员编号生效,需要用新编号来标识物理资源;配置文件中,只有IRF端口的编号以及IRF端口下的配置、成员优先级会继续生效,其它与成员编号相关的配置(比如普通物理接口的配置等)不再生效,需要重新配置。
H3C S5500 V2基本配置及配置命令

H3C S5500 V2 series基本配置之蔡仲巾千创作一、配置交换的web界面<h3c>sys(进入系统模式)[h3c]int vlan 1(进入虚接口VLAN 1)[h3c-int-vlan 1]undo ip address(清除原地址)[h3c-int-vlan 1]ip add 2.10.3.1 255.255.255.0(配置web界面ip地址)[h3c-int-vlan 1]quit(返回上一级)[h3c]ip http enable(启用web服务)[h3c]local-user admin(设置当地用户名、此处用户名admin)[h3c-admin]password simple admin(设置当地密码、此处密码admin)[h3c-admin]service-type telnet level 3(设置服务等级为3级)[h3c-admin]quit(返回上一级)[h3c]loal-user admin[h3c-admin]service-type terminal telnet http https(平安防护措施、认证方式)[h3c-admin]quit(返回上一级)注:以上配置完成后接入服务器用IE访问IP地址2.10.3.1访问二、交换机划分vlan<h3c>sys(进入系统模式)[h3c]vlan 2(划分vlan 2)[h3c-vlan 2]quit(返回上一级)[h3c]vlan 3(划分vlan 3)[h3c-vlan 3]quit(返回上一级)[h3c]vlan 2(进入vlan 2)[h3c-vlan 2]port g/0/1 to g1/0/12(对vlan 2进行端口划分-此处vlan 2划分到1-12端口)[h3c-vlan 2]quit(返回上一级)[h3c]vlan 3(进入vlan 3)[h3c-vlan 3]port g/0/13 to g1/0/24(对vlan 3进行端口划分-此处vlan3划分到13-24端口)注:以上配置是根据现场要求24口交换机划分两个vlan平分所有端口三、交换机VLAN IP 互通[h3c]int vlan 2[h3c-vlan-interface 2]ip add 192.168.2.1 255.255.255.0[h3c-vlan-interface 2]quit[h3c]int vlan 3[h3c-vlan-interface 3]ip add 192.168.3.1 255.255.255.0[h3c-vlan-interface 3]quit注:以上配置完成后能通过vlan 2 的端口与vlan 3 的端口互通。
H3C-S5500基本配置思路及实用命令

H3C S5500基本配置思路及实用命令1.总体配置思路:1)添加VLAN1,并将相应端口添加到该VLAN。
(在VLAN状态下才可一次将多个端口加入相应VLAN,interface e 1/0/1 to e 1/0/24)2)添加VLAN2,并将其置为管理VLAN(在#状态下management-vlan 2),才可设置其VLAN的IP地址。
3)添加静态路由。
4)配置端口TRUNK模式。
5)配置远程登录VTY认证。
6)配置本地用户。
2.进入特权模式System View<H3C> System ViewSystem View: return to User View with Ctrl+Z.[H3C]dis[H3C]display cur3.配置交换机主机名sysnamesysname H3C4.添加VLANvlan 1或在此状态下直接将相应端口加入该VLAN (否则只能一个口一个口的添加)Interface e 1/0/1 to e 1/0/245.配置管理VLAN-- management-vlanmanagement-vlan 26.给管理VLAN添加IP地址interface Vlan-interface1ip address 10.10.40.176 255.255.255.07.添加端口到VLAN:port access vlan 1interface GigabitEthernet1/0/2port access vlan 18.远程登录配置及3A认证模式user-interface vty 0 4authentication-mode scheme9.配置3A认证本地用户及属性local-user testpassword simple testpwdauthorization-attribute level 3service-type telnet可能的配置local-user testpassword simple testservice-type telnetlevel 310.将端口配置为Trunk口interface GigabitEthernet1/0/20port link-type trunkport trunk permit vlan all11.添加静态路由ip route-static 0.0.0.0 0.0.0.0 10.10.40.112.查看路由表display ip routing-table[H3C]display ip routing-tableRouting Tables: PublicDestinations : 7 Routes : 7Destination/Mask Proto Pre Cost NextHop Interface0.0.0.0/0 Static 60 0 10.10.40.1 Vlan210.10.40.0/24 Direct 0 0 10.10.40.180Vlan210.10.40.180/32 Direct 0 0 127.0.0.1 InLoop0127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0192.168.76.0/24 Direct 0 0 192.168.76.3Vlan76192.168.76.3/32 Direct 0 0 127.0.0.1 InLoop013.显示当前配置display current-configuration[H3C]display current-configuration14.查看端口及VLAN的up/down状态display brief interface[H3C]display brief interfaceThe brief information of interface(s) under route mode:Interface Link Protocol-link Protocol type Main IPNULL0 UP UP(spoofing) NULL --Vlan1 UP UP ETHERNET 192.168.76.3Vlan2 UP UP ETHERNET 10.10.40.180The brief information of interface(s) under bridge mode:Interface Link Speed Duplex Link-typePVIDGE1/0/1 UP 1G(a) full(a) access1GE1/0/2 DOWN auto auto access1GE1/0/3 DOWN auto auto access1GE1/0/9 DOWN auto auto access1GE1/0/10 DOWN auto auto access1display brief interface GigabitEthernet 1/0/1[H3C]display brief interface GigabitEthernet 1/0/1The brief information of interface(s) under bridge mode:Interface Link Speed Duplex Link-typePVIDGE1/0/1 UP 1G(a) full(a) access1display brief interface Vlan-interface 1[H3C]display brief interface Vlan-interface 1The brief information of interface(s) under route mode:Interface Link Protocol-link Protocol type Main IPVlan1 UP UP ETHERNET 192.168.76.315.查看MAC地址缓存表display mac-address[H3C]display mac-addressMAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)0000-e7a7-2374 1 Learned GigabitEthernet1/0/19 AGING0000-e8f1-6952 1 Learned GigabitEthernet1/0/19 AGING0001-6c41-9cee 1 Learned GigabitEthernet1/0/19 AGING000c-2919-0d6c 1 Learned GigabitEthernet1/0/19 AGING000c-2961-d8ea 1 Learned GigabitEthernet1/0/19 AGING16.查看某一端口的MAC地址缓存表display mac-address interface GigabitEthernet 1/0/1[H3C]display mac-address interface GigabitEthernet 1/0/1MAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)0016-3642-e888 1 Learned GigabitEthernet1/0/1 AGING0016-eca2-d69d 1 Learned GigabitEthernet1/0/1 AGING001c-25d8-77b6 1 Learned GigabitEthernet1/0/1 AGING0024-1d6e-6fbe 1 Learned GigabitEthernet1/0/1 AGING17.查看ARP缓存表display arp[H3C]display arpType: S-Static D-DynamicIP Address MAC Address VLAN ID Interface Aging Type192.168.76.56 0016-eca2-d69d 1 GE1/0/1 20D192.168.76.131 0016-3642-e888 1 GE1/0/1 19D192.168.76.171 0024-1d6e-6fbe 1 GE1/0/1 13D10.10.40.1 0018-742d-4fc0 2 GE1/0/19 14D192.168.76.1 0018-742d-4fc0 1 GE1/0/19 10D18.Tftp备份配置1)查看配置文件名及所在文件夹-dir配置文件名可能为startup.cfg或config.cfg配置文件可能在flash:/或unit1>flash:/目录下<jyzx-px-zhongxin>dir flash:/Directory of flash:/0 -rw- 8221183 Aug 11 2010 16:27:52s5500tpsi-cmw520-r2202p11.bin1 -rw- 2365 Apr 26 2000 12:13:58 startup.cfg(配置文件名)31496 KB total (23460 KB free)<jyzx-bg-3-d>dirDirectory of unit1>flash:/1 -rw- 3146 Jan 01 2004 00:00:00 config.def2 (*) -rw- 3711222 Mar 25 2011 16:51:52s31si_e-cmw310-r2211p07.bin3 (*) -rw- 886025 Jan 01 2004 00:00:00h3c-http3.1.9-0019.web4 (*) -rw- 2834 Apr 03 2000 01:20:33 config.cfg(配置文件名)7239 KB total (2739 KB free)(*) -with main attribute (b) -with backup attribute(*b) -with both main and backup attribute<jyzx-bg-4-x>tftp 172.16.8.91 put unit1>flash:/config.cfg 10.10.40.185.txtFile will be transferred in binary mode.Sending file to remote tftp server. Please wait... |TFTP: 2979 bytes sent in 0 second(s).File uploaded successfully.<jyzx-bg-4-x>dirDirectory of unit1>flash:/1 -rw- 3146 Jan 01 2004 00:00:00 config.def2 (*) -rw- 3711222 Mar 25 2011 16:51:52 s31si_e-cmw310-r2211p07.bin3 (*) -rw- 886025 Jan 01 2004 00:00:00 h3c-http3.1.9-0019.web4 (*) -rw- 2979 Apr 02 2000 07:17:02 config.cfg7239 KB total (2739 KB free)(*) -with main attribute (b) -with backup attribute(*b) -with both main and backup attribute2)配置可以使用tftp的ACLacl number 2000rule permit source 172.16.8.91 0[jyzx-px-zhongxin]acl number 2000[jyzx-px-zhongxin-acl-basic-2000]rule permit source 172.16.8.91 ?0 Wildcard bits : 0.0.0.0 ( a host )X.X.X.X Wildcard of source[jyzx-px-zhongxin-acl-basic-2000]rule permit source 172.16.8.91 03)配置tftp服务器- tftp-server acl 2000tftp-server acl 2000[jyzx-px-zhongxin]tftp-server acl 2000The ACL number does not exist or contains no rule. Continue? [Y/N]:y(如果还没有配置ACL,则会有此提示)[jyzx-px-zhongxin]tftp client source ip 172.16.8.914)备份配置文件到tftp软件所在目录下(在用户视图下,即“>”状态下)tftp 172.16.8.91 put flash:/startup.cfg (无目标文件名则表示与源文件名同名)tftp 172.16.8.91 put flash:/startup.cfg startup.txt(将配置文件保存为txt文件)<jyzx-px-zhongxin>tftp 172.16.8.91 put flash:/startup.cfgFile will be transferred in binary modeSending file to remote TFTP server. Please wait... \TFTP: 2365 bytes sent in 0 second(s).File uploaded successfully.<jyzx-px-zhongxin>tftp 172.16.8.91 put flash:/startup.cfg 10.10.40.177.txtFile will be transferred in binary modeSending file to remote TFTP server. Please wait... \TFTP: 2365 bytes sent in 0 second(s).File uploaded successfully.5)小结过程在特权状态下配置ACL和Tftp-server信息acl number 2000rule permit source 172.16.8.91 0quittftp-server acl 2000save在用户视图下备份配置tftp 172.16.8.91 put flash:/startup.cfg 10.10.40.177.txt19.关闭实时信息- undo info-center enable[jyzx-bg-4-x]undo info-center enable% Information center is disabled20.问题1:无法用system-view命令进入特权模式原因:因为local-user中用户认证属性设置不对,level 3必须设置。
h3c 5500三层交换机配置文档

interface GigabitEthernet1/0/7
port access vlan 11
mirroring-group 1 mirroring-port both
#
interface GigabitEthernet1/0/8
port access vlan 11
mirroring-group 1 mirroring-port both
#
interface GigabitEthernet1/0/5
port access vlan 11
mirroring-group 1 mirroring-port both
#
interface GigabitEthernet1/0/6
port access vlan 11
mirroring-group 1 mirroring-port both
snmp-agent target-host trap address udp-domain 10.10.30.27 udp-port 161 params
securityname public
#
user-interface aux 0 8
user-interface vty 0 4
authentication-mode scheme
authorization-attribute level 3
service-type telnet
#
interface Bridge-Aggregation2
port link-type trunk
port trunk permit vlan all
#
h3c-5500-24I交换机配置
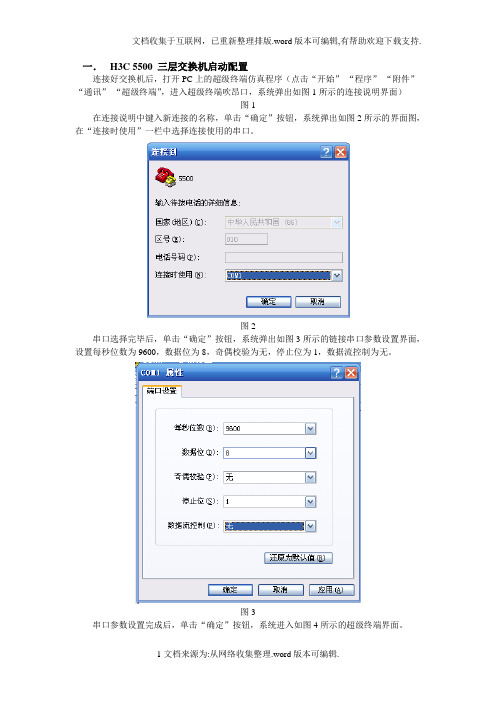
一.H3C 5500 三层交换机启动配置连接好交换机后,打开PC上的超级终端仿真程序(点击“开始”-“程序”-“附件”-“通讯”-“超级终端”,进入超级终端吹昂口,系统弹出如图1所示的连接说明界面)图1在连接说明中键入新连接的名称,单击“确定”按钮,系统弹出如图2所示的界面图,在“连接时使用”一栏中选择连接使用的串口。
图2串口选择完毕后,单击“确定”按钮,系统弹出如图3所示的链接串口参数设置界面,设置每秒位数为9600,数据位为8,奇偶校验为无,停止位为1,数据流控制为无。
图3串口参数设置完成后,单击“确定”按钮,系统进入如图4所示的超级终端界面。
图4在超级终端属性对话框中选择“文件/属性”菜单项,进入属性窗口。
点击属性窗口中的“设置”页签,进入属性设置窗口(如图5所示),在其中选择终端仿真为VT100,选择完成后,单击“确定”按钮。
图5交换机插上电源,终端启动bootrom,下面进入命令配置阶段。
二.H3C 5500 三层交换机详细配置操作及命令(1)首先创建VLANVLAN1为系统缺省VLAN,用户不能手工创建和删除。
保留VLAN是系统为实现特定功能预留的VLAN,用户也不能手工创建和删除。
不能通过undo vlan命令删除设备上动态学习到的VLAN。
(2)为每个创建好的VLAN设置IP口。
【举例】VLAN2命令:<h3c> system-view[h3c] vlan 2[h3c-vlan2] quit[h3c] interface vlan-interface 2[h3c-Vlan-interface2] ip address 24[h3c-Vlan-interface2] quitVLAN3命令:<h3c> system-view[h3c] vlan 3[h3c-vlan3] quit[h3c] interface vlan-interface 3[h3c-Vlan-interface3] ip address 24[h3c-Vlan-interface3] quit(3)设置动态链路聚合【举例】<h3c> system-view[h3c] interface bridge-aggregation 1[h3c-Bridge-Aggregation1] link-aggregation mode dynamic [h3c-Bridge-Aggregation1] port link-type trunk[h3c-Bridge-Aggregation1] port trunk permit vlan all[h3c-Bridge-Aggregation1] port trunk pvid vlan 2|3[h3c-Bridge-Aggregation1] quit[h3c] interface GigabitEthernet 1/0/24[GigabitEthernet1/0/24] port link-aggregation group 15500 到此配置完毕,接入二层交换机H3C-3600到端口1/0/24作为聚合端口。
H3C5500详细配置及说明

version 5.20, Release 1207#sysname dunan-s5500 设备重命名#super password level 3 simple abcd123456 设置串口连接密码#domain default enable system 说明性文字#telnet server enable telnet服务开启#loopback-detection enable 环回口连接开启#vlan 1description fileserver 注释VLAN连接区域#vlan 2description firewall#vlan 10description erp+sql+other#vlan 20description caiwu#vlan 30description waimao#vlan 40description bigoffice#vlan 50description jishubu#vlan 60description erchejian#vlan 70description huayi#vlan 80description zongcai#vlan 90description webser#vlan 130description wlan#radius scheme system#domain system 说明性文字access-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier c_vlan operator and 将ACL规则定义策略和行为这里和3600是不同的,分为三部if-match acl 3000traffic classifier a_vlan operator andif-match acl 3001#traffic behavior d_vlanfilter denytraffic behavior b_vlanfilter deny#qos policy p_vlanclassifier c_vlan behavior b_vlanqos policy t_vlanclassifier a_vlan behavior d_vlan#local-user h3c 设置web访问用户和密码并定义权限为最高password simple dafmservice-type telnetlevel 3#acl number 3000rule 0 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.90.0 0.0.0.255rule 1 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.90.0 0.0.0.255rule 2 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.20.0 0.0.0.255rule 3 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.30.0 0.0.0.255rule 4 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.40.0 0.0.0.255rule 5 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.50.0 0.0.0.255rule 6 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 7 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 8 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 9 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 10 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 11 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 12 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 13 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 14 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 15 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 16 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 rule 17 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 18 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 19 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.50.0 0.0.0.255 rule 20 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 21 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 22 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.90.0 0.0.0.255 rule 23 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 acl number 3001rule 0 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 rule 1 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.10.0 0.0.0.255 rule 2 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 3 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 4 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 5 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 6 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 7 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 8 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 建立高级访问控制列表并建立子规则#interface NULL0#interface Vlan-interface1ip address 192.168.1.1 255.255.255.0#interface Vlan-interface2ip address 192.168.2.2 255.255.255.0#interface Vlan-interface10ip address 192.168.10.1 255.255.255.0#interface Vlan-interface20ip address 192.168.20.1 255.255.255.0#interface Vlan-interface30ip address 192.168.30.1 255.255.255.0#interface Vlan-interface40ip address 192.168.40.1 255.255.255.0#interface Vlan-interface50ip address 192.168.50.1 255.255.255.0#interface Vlan-interface60ip address 192.168.60.1 255.255.255.0#interface Vlan-interface70ip address 192.168.70.1 255.255.255.0#interface Vlan-interface80ip address 192.168.80.1 255.255.255.0#interface Vlan-interface90ip address 192.168.90.1 255.255.255.0#interface Vlan-interface130ip address 192.168.130.1 255.255.255.0 配置VLAN网关,实际为设置vlan间路由#interface GigabitEthernet1/0/1port access vlan 10 将接口划入vlan#interface GigabitEthernet1/0/2port access vlan 10#interface GigabitEthernet1/0/3port access vlan 10#interface GigabitEthernet1/0/4port access vlan 90qos apply policy t_vlan inbound 定义策略到接口#interface GigabitEthernet1/0/5port access vlan 20#interface GigabitEthernet1/0/6port access vlan 20#port access vlan 30#interface GigabitEthernet1/0/8port access vlan 30#interface GigabitEthernet1/0/9port access vlan 40#interface GigabitEthernet1/0/10port access vlan 40#interface GigabitEthernet1/0/11port access vlan 50qos apply policy p_vlan inbound 定义策略到接口#interface GigabitEthernet1/0/12port access vlan 50qos apply policy p_vlan inbound定义策略到接口#interface GigabitEthernet1/0/13port access vlan 60#interface GigabitEthernet1/0/14port access vlan 60#interface GigabitEthernet1/0/15port access vlan 70#interface GigabitEthernet1/0/16port access vlan 70#interface GigabitEthernet1/0/17port access vlan 80qos apply policy p_vlan inbound定义策略到接口#interface GigabitEthernet1/0/18port access vlan 80qos apply policy p_vlan inbound 定义策略到接口#interface GigabitEthernet1/0/19port access vlan 130qos apply policy p_vlan inbound 定义策略到接口#port access vlan 130qos apply policy p_vlan inbound 定义策略到接口#interface GigabitEthernet1/0/21duplex fullflow-control#interface GigabitEthernet1/0/22#interface GigabitEthernet1/0/23port access vlan 2#interface GigabitEthernet1/0/24port access vlan 2#interface GigabitEthernet1/0/25shutdown#interface GigabitEthernet1/0/26shutdown#interface GigabitEthernet1/0/27shutdown#interface GigabitEthernet1/0/28shutdown#ip route-static 0.0.0.0 0.0.0.0 192.168.2.1 配置到防火墙的默认路由#snmp-agentsnmp-agent local-engineid 800063A20300E0FC123456snmp-agent sys-info version v3 简单网络管理协议的描述#load xml-configuration#user-interface aux 0 开启aux口和telnet访问的权限并设定串口访问密码authentication-mode passwordset authentication password simple abcd123456user-interface vty 0 4user privilege level 3set authentication password cipher ^BM!.#M()1=%X)AG\U/NCA!! protocol inbound telnet#。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
version 5.20, Release 1207sysname dunan-s5500 设备重命名super password level 3 simple abcd123456 设置串口连接密码 domain default enable system说明性文字telnet server enable telnet服务开启loopback-detection enable 环回口连接开启注释VLAN连接区域vlan 1description fileserver vlan 2description firewallvlan 10description erp+sql+other vlan 20description caiwu vlan 30description waimaovlan 40description bigofficevlan 50description jishubuvlan 60description erchejianvlan 70description huayivlan 80description zongcaivlan 90description webservlan 130description wlanradius scheme systemdomain system 说明性文字access-limit disablestate activeidle-cut disableself-service-url disable将ACL规则定义策略和行为这里和3600是不同的,分为三部traffic classifier c_vlan operator and if-match acl 3000traffic classifier a_vlan operator and if-match acl 3001traffic behavior d_vlanfilter denytraffic behavior b_vlanfilter denyqos policy p_vlanclassifier c_vlan behavior b_vlanqos policy t_vlanclassifier a_vlan behavior d_vlan设置web访问用户和密码并定义权限为最高local-user h3cpassword simple dafmservice-type telnetlevel 3建立高级访问控制列表并建立子规则acl number 3000rule 0 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.90.0 0.0.0.255 rule 1 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.90.0 0.0.0.255 rule 2 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 3 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 4 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 5 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.50.0 0.0.0.255 rule 6 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 7 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 8 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 9 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 10 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 11 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 12 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 13 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 14 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 15 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 16 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 rule 17 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 18 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 19 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.50.0 0.0.0.255 rule 20 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 21 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 22 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.90.0 0.0.0.255 rule 23 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 acl number 3001rule 0 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 rule 1 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.10.0 0.0.0.255 rule 2 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 3 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 4 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 5 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 6 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 7 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 8 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 配置VLAN网关,实际为设置vlan 间路由interface NULL0interface Vlan-interface 1ip address 192.168.1.1 255.255.255.0interface Vlan-interface 2ip address 192.168.2.2 255.255.255.0interface Vlan-interface 10ip address 192.168.10.1 255.255.255.0interface Vlan-interface 20ip address 192.168.20.1 255.255.255.0interface Vlan-interface 30ip address 192.168.30.1 255.255.255.0interface Vlan-interface 40ip address 192.168.40.1 255.255.255.0interface Vlan-interface 50ip address 192.168.50.1 255.255.255.0interface Vlan-interface 60ip address 192.168.60.1 255.255.255.0interface Vlan-interface 70ip address 192.168.70.1 255.255.255.0interface Vlan-interface 80ip address 192.168.80.1 255.255.255.0interface Vlan-interface 90ip address 192.168.90.1 255.255.255.0interface Vlan-interface 30ip address 192.168.130.1 255.255.255.0将接口划入vlaninterface GigabitEthernet1/0/1port access vlan 10interface GigabitEthernet1/0/2port access vlan 10interface GigabitEthernet1/0/3port access vlan 10interface GigabitEthernet1/0/4port access vlan 90定义策略到接口qos apply policy t_vlan inboundinterface GigabitEthernet1/0/5 port access vlan 20 interface GigabitEthernet1/0/6 port access vlan 20 interface GigabitEthernet1/0/7 port access vlan 30 interface GigabitEthernet1/0/8 port access vlan 30 interface GigabitEthernet1/0/9 port access vlan 40 interface GigabitEthernet1/0/10 port access vlan 40 interface GigabitEthernet1/0/11 port access vlan 50 定义策略到接口qos apply policy p_vlan inboundinterface GigabitEthernet1/0/12 port access vlan 50定义策略到接口qos apply policy p_vlan inboundinterface GigabitEthernet1/0/13 port access vlan 60 interface GigabitEthernet1/0/14 port access vlan 60 interface GigabitEthernet1/0/15 port access vlan 70 interface GigabitEthernet1/0/16 port access vlan 70 interface GigabitEthernet1/0/17 port access vlan 80定义策略到接口qos apply policy p_vlan inboundinterface GigabitEthernet1/0/18 port access vlan 80定义策略到接口qos apply policy p_vlan inboundinterface GigabitEthernet1/0/19 port access vlan 130定义策略到接口qos apply policy p_vlan inboundinterface GigabitEthernet1/0/20 port access vlan 130定义策略到接口qos apply policy p_vlan inboundinterface GigabitEthernet1/0/21 duplex full flow-control interface GigabitEthernet1/0/22interface GigabitEthernet1/0/23 port access vlan 2 interface GigabitEthernet1/0/24 port access vlan 2 interface GigabitEthernet1/0/25 shutdowninterface GigabitEthernet1/0/26 shutdowninterface GigabitEthernet1/0/27 shutdowninterface GigabitEthernet1/0/28 shutdown配置到防火墙的默认路由ip route-static 0.0.0.0 0.0.0.0 192.168.2.1简单网络管理协议的描述snmp-agentsnmp-agent local-engineid 800063A20300E0FC123456 snmp-agent sys-info version v3load xml-configuration开启aux口和telnet访问的权限并设定串口访问密码user-interface aux 0authentication-mode passwordset authentication password simple abcd123456user-interface vty 0 4user privilege level 3set authentication password cipher ^BM!.M()1=%X)AG\U/NCA!!protocol inbound telnet华为路由器交换机配置命令:交换机命令[Quidway]dis curr;显示当前配置[Quidway]display interfaces;显示接口信息[Quidway]display vlanall;显示路由信息[Quidway]display version;显示版本信息[Quidway]super password;修改特权用户密码[Quidway]sysname;交换机命名[Quidway]interface ethernet0/1;进入接口视图[Quidway]interface vlanx;进入接口视图[Quidway-Vlan-interfacex]ip address 10.65.1.1 255.255.0.0;配置VLAN的IP地址[Quidway]ip route-static 0.0.0.0 0.0.0.0 10.65.1.2;静态路由=网关[Quidway]rip;三层交换支持[Quidway]user-interface vty 0 4;进入虚拟终端[S3026-ui-vty0-4]authentication-mode password;设置口令模式[S3026-ui-vty0-4]set authentication-mode password simple222;设置口令[S3026-ui-vty0-4]user privilege level3;用户级别[Quidway]interface ethernet0/1;进入端口模式[Quidway]int e0/1;进入端口模式[Quidway-Ethernet0/1]duplex {half|full|auto};配置端口工作状态[Quidway-Ethernet0/1]speed{10|100|auto};配置端口工作速率[Quidway-Ethernet0/1]flow-control;配置端口流控[Quidway-Ethernet0/1]mdi{across|auto|normal};配置端口平接扭接[Quidway-Ethernet0/1]portlink-type{trunk|access|hybrid};设置端口工作模式[Quidway-Ethernet0/1]port access vlan3;当前端口加入到VLAN[Quidway-Ethernet0/2]port trunk permitvlan{ID|All};设trunk允许的VLAN[Quidway-Ethernet0/3]port trunk pvid vlan3;设置trunk端口的PVID [Quidway-Ethernet0/1]undoshutdown;激活端口[Quidway-Ethernet0/1]shutdown;关闭端口[Quidway-Ethernet0/1]quit;返回 [Quidway]vlan3;创建VLAN[Quidway-vlan3]port ethernet0/1;在VLAN中增加端口[Quidway-vlan3]port e0/1;简写方式[Quidway-vlan3]port ethernet0/1 to ethernet0/4;在VLAN中增加端口[Quidway-vlan3]port e0/1 to e0/4;简写方式[Quidway]monitor-port;指定镜像端口[Quidway]port mirror;指定被镜像端口[Quidway]port mirror int_listobserving-portint_typeint_num;指定镜像和被镜像[Quidway]description string;指定VLAN描述字符[Quidway]description;删除VLAN描述字符[Quidway]display vlan[vlan_id];查看VLAN设置[Quidway]stp{enable|disable};设置生成树,默认关闭[Quidway]stp priority 4096;设置交换机的优先级[Quidway]stp root{primary|secondary};设置为根或根的备份[Quidway-Ethernet0/1]stpcost200;设置交换机端口的花费[Quidway]link-aggregatione0/1toe0/4ingress|both;端口的聚合[Quidway]undolink-aggregatione0/1|all;始端口为通道号[SwitchA-vlanx]isolate-user-vlanenable;设置主vlan[SwitchA]isolate-user-vlansecondary;设置主vlan包括的子vlan[Quidway-Ethernet0/2]porthybridpvidvlan;设置vlan的pvid[Quidway-Ethernet0/2]porthybridpvid;删除vlan的pvid[Quidway-Ethernet0/2]porthybridvlanvlan_id_listuntagged;设置无标识的vlan 如果包的vlanid与PVId一致,则去掉vlan信息.默认PVID=1。
