CCNA 3 Final Exam
CCNA02-final3

1Which of the following are required when adding a network to the OSPF routing process conf iguration? (Choose three.)network addressloopback addressautonomous system numbersubnet maskwildcard maskarea ID2Using default settings, what is the next step in the router boot sequence after t he IOS loads from flash?Perf orm the POST routine.Search for a backup IOS in ROM.Load the bootstrap program f rom ROM.Load the running-config file from RAM.Locate and load the startup-config file from NVRAM.3Refer to the exhibit. What is the most efficient summarization of the routes attached to router R1?198.18.0.0/16198.18.48.0/21198.18.32.0/22198.18.48.0/23198.18.49.0/23198.18.52.0/224Refer to the exhibit. When troubleshooting a network, it is important to interpret the output of various router commands. On the basis of the exhibit, which three statem (Choose three.)The missing information f or Blank 1 is the command show ip route .The missing information f or Blank 1 is the command debug ip route .The missing information f or Blank 2 is the number 100.The missing information f or Blank 2 is the number 120.The missing information f or Blank 3 is the letter R.The missing information f or Blank 3 is the letter C.5Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose t wo.)10.0.0.0/864.100.0.0/16128.107.0.0/16172.16.40.0/24192.168.1.0/24192.168.2.0/246When presented with multiple valid routes to a destination, what criteria does a router use to determine which routes to add to the routing table?The router selects the routes with the best metric. All routes that hav e the same best metric are added to the routing table.The router f irst selects routes with the lowest administrative distance. The resulting routes are then prioritized by metric and the routes with the best metric arouting table.The router selects the routes with the lowest administrativ e distance. All routes with the same lowest administrative distanc e are added to the routing table.The router installs all routes in the routing table but uses the route with the best metric most when load balancing.7Refer to the exhibit. All routers in the network are running RIPv2 and EIGRP with default routing protocol settings and have interfaces configured with the bandwidths t exhibit. Which protocol will be used and how will traffic between the Router1 LAN and Router5 LAN be routed through the network?RIPv2 will load balance across both paths between Router1 and Router5.EIGRP will load balance across both paths between Router1 and Router5.RIPv2 traffic will use the path Router1, Router2, Router5 because it has the least hops.EIGRP traffic will use the path Router1, Router3, Router4, Router5 because it has the best metric.8Of the listed routing protocols, which two will propogate LSPs to all neighbors? (Choose two.)IS-ISEIGRPOSPFRIPv1RIPv29Refer to the exhibit. Routers 1 and 2 are directly connected over a serial link. Pings are f ailing between the two routers. W hat change by the administrator will correctSet the encapsulation on both routers to PPP.Decrease the bandwidth on Serial 0/1/0 on router 2 to 1544.Change the cable that connects the routers to a crossover cable.Change the IP address on Serial 0/1/0 on router 2 to 192.168.0.1/30.10Refer to the exhibit. Which three statements are true of the routing table for Router1? (Choose three.)The route to network 172.16.0.0 has an AD of 156160.Network 192.168.0.16 can best be reached using FastEthernet0/0.The AD of EIGRP routes has been manually changed to a value other than the default value.Router1 is running both the EIGRP and OSPF routing process.Network 172.17.0.0 can only be reached using a default route.No default route has been conf igured.11Which statement correctly describes a feasible successor in EIGRP?It is a primary route that is stored in the routing table.It is a backup route that is stored in the routing table.It is a primary route that is stored in the topology table.It is a backup route that is stored in the topology table.12Refer to the exhibit. A ping from R1 to 10.1.1.2 is successful, but a ping from R1 to 192.168.2.0 fails. What is the cause of this problem?There is no gateway of last resort at R1.The serial interf ace between the two routers is down.A default route is not configured on R1.The static route for 192.168.2.0 is incorrectly conf igured.13Refer to the exhibit. A network administrator has run the show interface command. The output of this command is displayed. What is the first step that is required toSwitch the cable with a known working cable.Issue the no shutdown command on the interface.Configure the interf ace as a loopback interface.Set the encapsulation for the interface.14Which two locations can be the source of the Cisco IOS that is used by a router during the bootup process? (Choose two.)flash memoryRAMNVRAMTFTP serverconfiguration register15All routers in a network are configured in a single OSPF area with the same priority value. No loopback interface has been set on any of the routers. Which secondrouters use to determine the router ID?The highest MAC address among the active interfaces of the network will be used.There will be no router ID until a loopback interf ace is configured.The highest IP address among the activ e FastEthernet interfaces that are running OSPF will be used.The highest IP address among the activ e interfaces will be used.16Refer to the exhibit. A network administrator has conf igured OSPF using the following command:network 192.168.1.32 0.0.0.31 area 0Which router interf ace will participate in OSPF?FastEthernet0/0FastEthernet0/1Serial0/0/0Serial0/0/117Refer to the exhibit. All routers are properly configured with default configurations and are running the OSPF routing protocol. The network is f ully converged. A host on th with a host on the 192.168.2.0/24 network.Which path will be used to transmit the data?The data will be transmitted v ia R3-R2.The data will be transmitted v ia R3-R1-R2.The traffic will be load-balanced between two paths — one via R3-R2, and the other via R3-R1-R2.The data will be transmitted v ia R3-R2, and the other path via R3-R1-R2 will be retained as the backup path.18Which two situations require the use of a link-state protocol? (Choose two.)Fast convergence of the network is critical.The network is very large.The network administrator has limited knowledge to configure and troubleshoot routing protocols.The network is a flat network.The capacity of the router is low.19Refer to the exhibit. What is the meaning of the highlighted value 120?It is the metric that is calculated by the routing protocol.It is the v alue that is used by the DUAL algorithm to determine the bandwidth for the link.It is the administrative distance of the routing protocol.It is the hold-down time, measured in seconds, before the next update.20In a lab test environment, a router has learned about network 172.16.1.0 through four different dynamic routing processes. Which route will be used to reach this nD 172.16.1.0/24 [90/2195456] via 192.168.200.1, 00:00:09, Serial0/0/0O 172.16.1.0/24 [110/1012] via 192.168.200.1, 00:00:22, Serial0/0/0R 172.16.1.0/24 [120/1] via 192.168.200.1, 00:00:17, Serial0/0/0I 172.16.1.0/24 [100/1192] via 192.168.200.1, 00:00:09, Serial0/0/021Which statement is true about the RIPv1 protocol?It is a link-state routing protocol.It excludes subnet information from the routing updates.It uses the DUAL algorithm to insert backup routes into the topology table.It uses classless routing as the default method on the router.22Refer to the exhibit. The 10.4.0.0 network f ails. What mechanism prevents R2 f rom receiving false update information regarding the 10.4.0.0 network?split horizonhold-down timersroute poisoningtriggered updates23Which statement is true about the metrics used by routing protocols?A metric is a value used by a particular routing protocol to compare paths to remote networks.A common metric is used by all routing protocols.The metric with the highest value is installed in the routing table.The router may use only one parameter at a time to calculate the metric.24Refer to the exhibit. Both routers are using the RIPv2 routing protocol and static routes are undef ined. R1 can ping 192.168.2.1 and 10.1.1.2, but is unable to ping 192.16 What is the reason for the ping f ailure?The serial interf ace between two routers is down.R2 is not forwarding the routing updates.The 192.168.4.0 network is not included in the RIP configuration of R2.RIPv1 needs to be configured.25Which statement correctly describes a feature of RIP?RIP is a link-state routing protocol.RIP uses only one metric—hop count— for path selection.Adv ertised routes with hop counts greater than 10 are unreachable.Messages are broadcast every 10 seconds.26Refer to the exhibit. When the show cdp neighbors command is issued f rom router C, which devices will be displayed in the output?B, DA, B, DD, SWH-2SWH-1, A, BSWH-1, SWH-2A, B, D, SWH-1, SWH-227Refer to the exhibit. Although R2 is conf igured correctly, host A is unable to access the Internet. What are two static routes that can be c onfigured on R1, either of which w (Choose two.)ip route 0.0.0.0 0.0.0.0 Fa0/0ip route 0.0.0.0 0.0.0.0 Fa0/1ip route 0.0.0.0 0.0.0.0 10.1.1.1ip route 0.0.0.0 0.0.0.0 10.1.1.2ip route 209.165.202.0 255.255.255.0 10.1.1.128Which component is typically used to connect the WIC interface of a router to a CSU/DSU?V.35 cableRJ-45 adaptercrossover cablestraight-through cable29Refer to the exhibit. Which combination of IP address and subnet mask can be used on the serial interf ace of Router2 in order to put the interf ace in the same networ interface of Router1?IP 172.16.0.18, subnet mask 255.255.255.0IP 172.16.32.15, subnet mask 255.255.255.240IP 172.16.0.18, subnet mask 255.255.255.252IP 172.16.32.18, subnet mask 255.255.255.25230Refer to the exhibit. Which host has a combination of IP address and subnet mask on the same network as Fa0/0 of Router1?host Ahost Bhost Chost D31Refer to the exhibit. OSPF is used f or the routing protocol and all interf aces are configured with the correct IP addresses and subnet masks. During testing, it is foun unable to form an adjacency with R2. What is the cause of this problem?Both routers have been configured with incorrect router IDs.Both routers have been configured in different OSPF areas.Both routers have been configured with an incorrect network type.Both routers have been configured with different hello and dead intervals.32You hav e been asked to explain converged networks to a trainee. How would you accurately describe a converged network?A network is converged when all routers have f ormed an adjacency.A network is converged immediately after a topology change has occurred.A network is converged when all routers flush the unreachable networks from their routing tables.A network is converged after all routers share the same information, calculate best paths, and update their routing tables.33 A network administrator is in charge of two separate networks that share a single building. What dev ice will be required to connect the two networks and add a comthe Internet that can be shared?hubrouteraccess pointEthernet switch34Which port should a terminal emulator be connected to in order to access a router without network connectivity?T1serialconsoleFastEthernet35Refer to the exhibit. What needs to be done to allow these two routers to connect successf ully?Add a clock rate to S0/0/0 on R1.Add an interface description to S0/0/1 on R2.Change the serial interface on R2 to S0/0/0 so that it matches R1.Change the IP address of S0/0/1 on R2 so that it is in the same subnet as R1.36Refer to the exhibit. Based on the partial output in the exhibit, why can users establish a console connection to this router without entering a password?The login command was not entered on the console line.The enable password should be an enable secret password.No username and password combination has been configured.Console connections cannot be conf igured to require users to provide passwords.37Refer to the exhibit. When a static IP address is being configured on the host, what address should be used for the default gateway?10.1.1.110.1.1.2172.16.1.1192.168.1.138Refer to the exhibit. The entire 192.168.1.0 network has been allocated to address hosts in the diagram. Utilizing VLSM with contiguous address blocks, which set of pref ixes could be used to create an addressing solution with a minimum waste of IP addresses?39What is a function of a router?It extends the Layer 2 broadcast domain.It eliminates collisions among PCs on the same local network.It provides connectivity among PCs on the same physical segment.It forwards packets to different IP networks based on Layer 3 inf ormation.40Refer to the exhibit. Which solution provides the most efficient use of router resources for forwarding traffic between BR and HQ?RIPRIPv2EIGRPstatic routes41Refer to the exhibit. A network administrator configures a static route on router R1 to reach the 192.168.1.0/24 network. Which IP address should be used as the next ip route command?192.168.1.1192.168.2.1192.135.250.1192.135.250.242Refer to the exhibit. The network is conf igured with RIPv2. However, network administrators notice that communication cannot be successfully completed f rom one L network administrator issues the show ip route command on the HQ router. Based on the output, what should be done to correct the problem?Disable the load balancing feature of RIPv2.Issue the no auto-summary command for RIPv2.Replace RIPv2 with EIGRP which supports VLSM.Make sure that the network statements include the correct subnet mask.43Which protocol is used by EIGRP to deliver and receive update packets?FTPRTPTCPTFTPUDP44Refer to the exhibit. What OSPF network statements are required for the router B to adv ertise the three networks that are attached?router ospf 1network 10.0.0.0 0.0.0.255 area 0router ospf 1network 10.1.1.0 0.3.255.255 area 0network 10.10.1.0 0.255.255.255 area 0network 10.20.1.0 0.255.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.255.255 area 0network 10.20.1.0 0.0.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.0.255 area 0network 10.20.1.0 0.0.0.255 area 045Which two v alues are used by default to calculate a metric in EIGRP? (Choose two.) loaddelayreliabilityhop countbandwidth46Refer to the exhibit. Which statement is true concerning the routing configuration?Using dy namic routing instead of static routing would hav e required f ewer configuration steps.The 10.1.1.0/24 and 10.1.2.0/24 routes have adjacent boundaries and should be summarized.Packets routed to the R2 Fast Ethernet interface require two routing table lookups.The static route will not work correctly.47Refer to the exhibit. On the basis of the show running-config output, which option correctly ref lects the routes that will be listed in the R2 routing table?48Refer to the exhibit. Which command should be issued to configure the address of the router interface that is attached to this computer?Router(config-if)# ip address 192.168.2.1 255.255.255.0Router(config-if)# ip address 192.168.2.2 255.255.255.0Router(config-if)# ip address 192.168.0.1 255.255.255.0Router(config-if)# ip address 192.168.0.2 255.255.255.049Refer to the exhibit. Which route will be removed from the routing table if manual EIGRP summarization is disabled on the Serial0/0/0 interface of Router3?0.0.0.0/0172.16.0.0/16172.16.1.0/24172.16.3.0/3050Refer to the exhibit. All interfaces are addressed and f unctioning correctly. The network administrator runs the tracert command on host A. Which two f acts could be output of this command? (Choose two.)The gateway for Host A is missing or improperly conf igured.The gateway for Host B is missing or improperly conf igured.The entry for 192.168.1.0/24 is missing f rom the routing table of R1.The entry for 192.168.1.0/24 is missing f rom the routing table of R2.The entry for 192.168.2.0/24 is missing f rom the routing table of R1.The entry for 192.168.2.0/24 is missing f rom the routing table of R2.。
CCNA Exploration 3 LAN Switching and Wireless Final Exam

Refer to the exhibit. The switches are configured for VTP as shown. Which two statements correctly describe the operation of these switches? (Choose two.)23A new VLAN can be added to Switch1 and that information will be added only to Switch2.A new VLAN can be added to Switch1 and that information will be added to Switch2 and Switch4.An existing VLAN can be deleted from Switch4 and that VLAN will be deleted from Switch1 and Switch2.An existing VLAN can be deleted from Switch2 and that VLAN will be deleted from Switch1 and Switch4.A new VLAN can be added to Switch4 and that information will be added to Switch1, Switch2, and Switch3.A new VLAN can be added to Switch3 and that information will be added to Switch1, Switch2, and Switch4.2Refer to the exhibit. Switch SW2 has been newly purchased and added to the network. What configuration should be applied to SW2 so that it participates in the same VTP domain as switch SW1, receives VLAN information from SW1, and synchronizes VLAN information?3Disable VTP pruning on SW2.Configure SW2 in VTP transparent mode.Configure SW2 with the VTP domain password.Configure SW2 as a VTP server with a higher revision number.3Refer to the exhibit. What will allow a host on VLAN 40 on switch X to communicate with a host in VLAN 40 on switch Y?3QoSroutingtrunkingVPN4Which parameter is used to uniquely identify one wireless network from another?1SSIDOFDMWEPDSSS5Refer to the exhibit. What three statements describe why Host1 and Host2 are unable to communicate? (Choose three.)134The switch ports are on different VLANs.The switch IP address is on the wrong subnet.The hosts are configured on different logical networks.A router is required to forward traffic between Host1 and Host2.The VLAN port assignments must be contiguous for each VLAN.The host default gateway addresses must be on the same logical network.6Refer to the exhibit. The network administrator enters the configuration shown to allow both SSH and Telnet connections to the switch. The Telnet connections fail. What is the most likely cause of this problem?3The SSH version number is wrong.SSH has been configured on the wrong line.Telnet and SSH cannot be configured simultaneously.The transport input command is configured incorrectly.7Refer to the exhibit. The network administrator needs to setup Switch1 for remote access from HostA. The show ip interface brief is issued on Router1 and the show interfaces trunk command is issued on the Switch1 to verify the current status. The administrator applies the additional configuration shown in the exhibit to Switch1. However, the telnet from HostA fails. What additional commands need to be applied to the switch?4Switch(config)# interface vlan 1Switch(config-if)# ip address 10.1.1.250 255.255.255.0Switch(config-if)# no shutdownSwitch(config-if)# ip default-gateway 10.1.10.254Switch(config)# interface vlan 1Switch(config-if)# ip address 10.1.50.250 255.255.255.0Switch(config-if)# no shutdownSwitch(config-if)# ip default-gateway 10.1.50.254Switch(config)# interface vlan 5Switch(config-if)# ip address 10.1.5.250 255.255.255.0Switch(config-if)# no shutdownSwitch(config-if)# ip default-gateway 10.1.5.254Switch(config)# interface vlan 10Switch(config-if)# ip address 10.1.10.250 255.255.255.0Switch(config-if)# no shutdownSwitch(config-if)# ip default-gateway 10.1.10.254Switch(config)# interface vlan 10Switch(config-if)# ip address 10.1.1.250 255.255.255.0Switch(config-if)# no shutdownSwitch(config-if)# ip default-gateway 10.1.10.254Switch(config)# interface vlan 50Switch(config-if)# ip address 10.1.10.250 255.255.255.0Switch(config-if)# no shutdownSwitch(config-if)# ip default-gateway 10.1.10.2548What three tasks should be performed before moving a Catalyst switch to another VTP management domain? (Choose three.)126Select the correct VTP mode and version.Configure the switch with the name of the new management domain.Download the VTP database from the VTP server in the new domain.Configure the VTP server in the new domain to recognize the BID of the switch.Reset the VTP counters to allow the switch to synchronize with the other switches in the new domain.Verify that the switch has a lower configuration revision number than the other switches in the new domain.9Refer to the exhibit. Computer A sends a broadcast message. Which devices will see the broadcast?3computer Bcomputer B and Router1computer C and Router1computer B, computer D, computer E and Router1computer B, computer C, computer D, computer E and Router1computer A, computer B, computer C, computer D, computer E and Router110Which three statements are correct concerning the default configuration of a new switch? (Choose three.)346Spanning Tree Protocol is disabled.Enable password is configured as cisco.All switch ports are assigned to VLAN1.The flash directory contains the IOS image.VLAN1 is configured with a management IP address.All interfaces are set to auto-negotiation of speed and duplex.11Refer to the exhibit. Switch SW2 was tested in a lab environment and then inserted into a production network without reloading its configuration. After the trunk link between SW1 and SW2 was brought up, all users lost connectivity to the network. What could be the source of the problem?3All the VLANs were pruned from the trunk port between SW1 and SW2. SW1 and SW2 cannot be both set as VTP servers in the same VTP domain.VTP configuration revision number of SW2 was higher than the configuration revision number of SW1.The additional VLANs from SW2 created more VLANs than the VLAN database of SW1 could contain.12In which mode is a VTP switch operating if it has been configured to only forward VTP advertisements?4clientrootservertransparent13Refer to the exhibit. The hosts connected to switch SW1 are not able to communicate with the hosts in the same VLANs connected to switch SW2. What should be done to fix the problem?2Configure VLANs with different VLAN IDs on switch SW2.Reconfigure the trunk port on switch SW2 with static trunk configuration.Introduce a Layer 3 device or a switch with Layer 3 capability in the topology.Apply IP addresses that are in the same subnet to the interfaces used to connect SW1 and SW2.14Refer to the exhibit. What does STATIC indicate in the output that is shown?2The switch will not allow any other device to connect to port Fa0/15.Traffic destined for MAC address 0000.c123.5432 will be forwarded to Fa0/15.This entry will be removed and refreshed every 300 seconds to keep it in the table.The switch learned this MAC address from the source address in a frame received on Fa0/15.When processing a frame, the switch does not have to perform a lookup to determine the final destination port.15Refer to the exhibit. Both switches are interconnected via a trunk link. Host A and host B are on the default VLAN but are not able to exchange traffic. What should be done to fix the problem?4Allow all VLANs on the trunk link.Remove the native VLAN from the trunk.Include a router or switch with Layer 3 capabilities.Configure the same native VLAN on both ends of the trunk.16What are two benefits of the IEEE 802.11n standard over the IEEE 802.11G? (Choose two.)35requires less equipmentprovides improved rangepermits increased data rateshas a single-input and a single-outputneeds no hardware upgrade for compatibility17Refer to the exhibit. How does SW1 manage traffic coming from Host A?4SW1 drops the traffic because it is untagged.SW1 leaves the traffic untagged and forwards it over the trunk.SW1 tags the traffic with the lowest VLAN ID value and forwards it over the trunk link.SW1 encapsulates the traffic with 802.1Q encapsulation and forwards it over the trunk link.18Refer to the exhibit. Which two statements are true regarding what the cost value of 23 represents for Switch4? (Choose two.)13This cost represents the lowest cost path for Switch4 to the root switch.A cost of 23 is the value being advertised out port 16 on the switch upstream (closer) to the root switch.Switch4 adds the cost of a Fast Ethernet link to 23 to determine its total cost to reach the root switch.Switch4 is connected via a Fast Ethernet link to an upstream switch that in turn is directly connected to the root switch via a Gigabit Ethernet link.The root switch is advertising a cost of 23, which is lower than any other switch in the VLAN0001 spanning-tree domain.19Why is it important that the network administrator consider the spanning-tree network diameter when choosing the root bridge?2The network diameter limitation is 9.BPDUs may be discarded because of expiring timers.The cabling distance between the switches is 100 meters.The network diameter must be set to the number of meters of the cable between the root bridge and its farthest connected switch.20Refer to the exhibit. After the listed commands are entered into router R1 and switch S1, the administrator enters the show interface fa0/1 trunk and gets the results shown. What is the likely problem?2The trunk is established, but no VLANs have been configured to use it.The trunk has not been established because the router does not support dynamic trunking protocol.The router, the switch, or both must be configured with the dynamic desirable option for dynamic trunking protocol to establish a trunk.The router is missing the dynamic trunking protocol statements necessary to form a trunk.21Refer to the exhibit. A new host needs to be connected to VLAN 1. Which IP addresses should be assigned to this new host?2192.168.1.11 /28192.168.1.22 /28192.168.1.33 /28192.168.1.44 /28192.168.1.55 /2822Which statement regarding the service password-encryption command is true?3The service password-encryption command is entered at the privileged EXEC mode prompt.The service password-encryption command encrypts only passwords for the console and VTY ports.The service password-encryption command encrypts all previously unencrypted passwords in the running configuration.To see the passwords encrypted by the service password-encryption command, enter the no service password-encryption command.23What is the purpose of issuing the command switchport mode access on a switch interface?4disable port securitymake the port operationaloverride the default port behaviorforce the port to be a part of a single vlan24Refer to the exhibit. Spanning-tree port priorities are 128 for all interfaces. The network administrator enters the spanning-tree vlan 1 root primary command on S4. Which two port results are correct? (Choose two.)25S1 Gi0/1 becomes a root port.S2 Gi0/2 becomes a non-designated port.S3 Gi0/1 becomes a non-designated port.S4 Gi0/1 becomes a root port.S4 Gi0/2 becomes a designated port.25What two radio frequency bands are designated by the ITU-R as unlicensed for industrial, scientific, and medical (ISM) communities and are therefore supported by IEEE 802.11? (Choose two.)359 MHz750 MHz2.4 GHz7.7 GHz5 GHz900 GHz26Refer to the exhibit. An Ethernet switch has developed the CAM table shown. What action will the switch take when it receives the frame shown at the bottom of the exhibit?1forward the frame out all interfaces except Interface3add station 00-00-3D-1F-11-05 to Interface2 in the forwarding tableforward the frame out Interface3discard the frameforward the frame out all interfacesforward the frame out Interface227Refer to the exhibit. A network administrator has segmented the network into two VLANs and configured Router1 for inter-VLAN routing. A test of the network, however, shows that hosts on each VLAN can only access local resources and not resources on the other VLAN. What is the most likely cause of this problem?1Switch port Fa0/1 is not trunking.Router interface Fa0/0 is possibly down.No routing protocol is configured on Router1.One of the router subinterfaces is possibly down.28Refer to the exhibit. The network administrator needs to remove the east-hosts VLAN and use the switch port from that VLAN in one of the existing VLANs. What two commands should be used when completely removing VLAN 2 from S1-Central while leaving the switch and all its interfaces operational? (Choose two.)35S1-Central# reloadS1-Central# erase flash:S1-Central(config)# no vlan 2S1-Central# delete flash:vlan.datS1-Central(config-if)# switchport access vlan 329Which three statements are true regarding router-on-a-stick inter-VLAN routing? (Choose three.)136requires the use of subinterfaces on the routerrequires an access link between the router and Layer 2 switchmore cost-efficient and scalable than using multiple physical interfacesrequires each subinterface to be configured with the no shutdown commandcan impact performance if many VLANs compete for bandwidth on a single router interfacemakes troubleshooting the inter-VLAN routing configuration much less complex than when using multiple physical interfaces30Refer to the exhibit. Which statement is true regarding the information shown?1Only one VLAN is currently configured to use the trunk links.The switch negotiated trunk links for interfaces Fa0/1 and Gi0/1.A Cisco proprietary protocol is in use for interfaces Fa0/1 and Gi0/1. Interfaces Gi0/1 and Fa0/1 are allowed to carry data from multiple VLANs.31Refer to the exhibit. What does "FORWARDING" mean in the command output shown?1The switch is sending and receiving data frames.The switch is receiving BPDUs, but not sending data frames.The switch is participating in an election process by forwarding the BPDUs it receives.The switch is receiving BPDUs and populating the MAC address table, but not sending data.32Refer to the exhibit. Each switch is shown with its MAC address. Which switch will be elected as the spanning-tree root bridge if the switches are configured with their default priority values?6switch Aswitch Bswitch Cswitch Dswitch Eswitch F33Which two statements describe Spanning Tree Protocol? (Choose two.)13 It eliminates Layer 2 loops in network topologies.It eliminates the need for redundant physical paths in network topologies. It can only be used in networks in which Layer 2 switching is in use.It can only be used in networks where both routers and switches are used together.It can only be used in networks where routers are installed.34Refer to the exhibit. What is the consequence if SW1 port F0/1 is configured as an edge port?2SW1 port F0/1 transitions to the learning state.SW1 port F0/1 can generate a temporary loop.SW1 port F0/1 becomes a non-designated port.SW1 port F0/2 no longer passes BPDUs to SW4.35Refer to the exhibit. Which three options correctly identify information that could be associated with this output?(Choose three.)123Interface FastEthernet3/0/0 is subinterfaced.A non-proprietary trunking protocol is in use.The configuration is appropriate for a router-on-a-stick network design.A shutdown command has been applied to interface FastEthernet3/0/0.Interface FastEthernet3/0/0.3 is mapped to the default management VLAN.An IP address should be applied to FastEthernet3/0/0 for correct data routing.36Refer to the exhibit. R1 is configured for traditional inter-VLAN routing. R1 can ping computer 3 but cannot ping computer 1. What is a possible cause for this failure?1S1 port Fa0/11 is in the wrong VLAN.R1 does not have an active routing protocol.The IP address of computer 1 is in the wrong logical network.Router interface Fa0/0 has the wrong trunk encapsulation type configured.37Refer to the exhibit. The switches in the exhibit have VTP pruning enabled. Which VLANs will be pruned from switch SW3?1VLAN 10 and VLAN 20VLAN 1, VLAN 10, and VLAN 20VLAN 1, VLAN 1002 through 1005VLAN 1, VLAN 10, VLAN 20, VLAN 1002 through 100538Refer to the exhibit. Which two facts can be confirmed by this output? (Choose two.)45This switch shows no configuration revision errors.This switch has established two-way communication with the neighboring devices.This switch is configured to advertise its VLAN configuration to other VTP-enabled switches in the same VTP domain.This switch will drop all VTP advertisements that come from the switches that are configured in the same VTP domain.This switch will cause no disruption in the VTP domain operations if therest of the switches in the same VTP domain have a higher configuration revision number.39Refer to the exhibit. A network administrator needs to implementinter-VLAN routing on a hierarchical network. On which devices should the inter-VLAN routing be configured?2AS1 and AS2DS1 and DS2Gateway and CS1Gateway, CS1, DS1, and DS240Which method establishes an administrative connection for configuring the Linksys WRT300N wireless access point?3Associate with the access point and then open a HyperTerminal session with the access point.Physically connect to the access point and then reboot the computer to launch the configuration software.From a computer in the same IP subnet as the access point, enter the default IP address of the access point in a web browser.Modify the TCP/IP properties of the computer connected to the access point so that it exists on the same network, and then reboot your computer to establish a connection.41What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value?1All VLANs will be allowed across the trunk.Only VLAN 1 will be allowed across the trunk.Only the native VLAN will be allowed across the trunk.The switches will negotiate via VTP which VLANs to allow across the trunk.42Refer to the exhibit. What will happen when frames that contain an unknown source address reach interface fa0/24?2A syslog message will be logged.Fa0/24 will become error-disabled.The incoming frames will be dropped.The security violation count will be incremented.43Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology?3Cat-ACat-BCat-CCat-D44What are three benefits of a hierarchical network model? (Choose three.)136reduced contention for bandwidthreduced size of the physical layoutincreased fault tolerance of the networkelimination of the need for wiring closetselimination of the need for layer three functionalitysimplification of management and troubleshooting45Refer to the exhibit. Router RA receives a packet with a source address of 192.168.1.65 and a destination address of 192.168.1.85. What will the router do with this packet?5The router will forward the packet out interface FastEthernet 0/1.1.The router will forward the packet out interface FastEthernet 0/1.2.The router will forward the packet out interface FastEthernet 0/1.3.The router will forward the packet out interface FastEthernet 0/1.2 and interface FastEthernet 0/1.3.The router will ignore the packet because the source and destination are on the same broadcast domain.The router will drop the packet since no network that includes the source address is attached to the router.46Refer to the exhibit. All hosts are in listen mode. Host 1 and Host 4 both transmit data at the same time. How do the hosts respond on the network? (Choose two.)15After the end of the jam signal, a backoff algorithm is invoked.Hosts 1 and 4 are operating full duplex so no collision will exist. The hub will block the port connected to Host 4 to prevent a collision.Hosts 1 and 4 are assigned shorter backoff values to provide them priority to access the media.If a host has data to transmit after the backoff period of that host, the host checks to determine if the line is idle before transmitting.47Refer to the exhibit. Hosts A and B, connected to hub HB1, attempt to transmit a frame at the same time but a collision occurs. Which hosts will receive the collision jamming signal?2only hosts A and Bonly hosts A, B, and Conly hosts A, B, C, and Donly hosts A, B, C, and E48Refer to the exhibit. Hosts PC_A and PC_B send traffic simultaneously, and the frames from the transmitting stations collide. What is the last device to receive the collision?3hub HB1switch SW1router R1switch SW2router R2switch SW449Refer to the exhibit. Which two statements are true about the operation of the interfaces? (Choose two.)25Incoming traffic with VLAN ID 0 is processed by interface fa0/0.Incoming traffic that has a VLAN ID of 2 is processed by subinterface fa0/0.2.Both subinterfaces remain up with line protocol up, even if fa0/0 line protocol is down.Subinterfaces use unique MAC addresses by adding the 802.1Q VLAN ID to the hardware address.Traffic inbound on this router is processed by different subinterfaces, depending on the VLAN from which the traffic originated.50Which identifier is used to keep track of frames that are destined for a particular wireless client?2AIDSSIDBSSIDESSID51Refer to the exhibit. On the basis of the configuration shown, how will an Ethernet frame on port GigabitEthernet0/1 be modified?3802.1Q encapsulation prepends a 4-byte tag field in front of the original Ethernet frame and recomputes the frame check sequence (FCS) on the modified frame.802.1Q encapsulation inserts a 4-byte tag field into the original Ethernet frame between the source address and type/length fields and recomputes the frame check sequence (FCS) on the modified frame.802.1Q encapsulation prepends an 802.1p field in front of the original Ethernet frame and recomputes the frame check sequence (FCS) on the modified frame.802.1Q encapsulation inserts an 802.1p field into the original Ethernet frame between the source address and type/length fields and recomputes the frame check sequence (FCS) on the modified frame.52What two methods can be used to remove MAC address table entries from a switch? (Choose two.)13Power cycle the switch to clear all dynamically learned addresses.The clear switching-tables command will remove statically configured entries.The clear mac-address-table command will remove statically and dynamically configured table entries.The erase flash command will clear all statically configured table entries.Statically configured MAC addresses will automatically be removed from the address table 300 minutes after the last activity on a switch port.53What happens when the crypto key zeroize rsa command is entered on a switch configured with the transport input ssh command on the vty lines?4A new RSA key pair is created.The switch defaults to allowing Telnet connections only.The switch is no longer able to make SSH connections as an SSH client.The switch allows remote connections only after a new RSA key pair is generated.Date Exam was Taken: 05/17/2008。
思科ccna第3学期_final_第1套_V_4
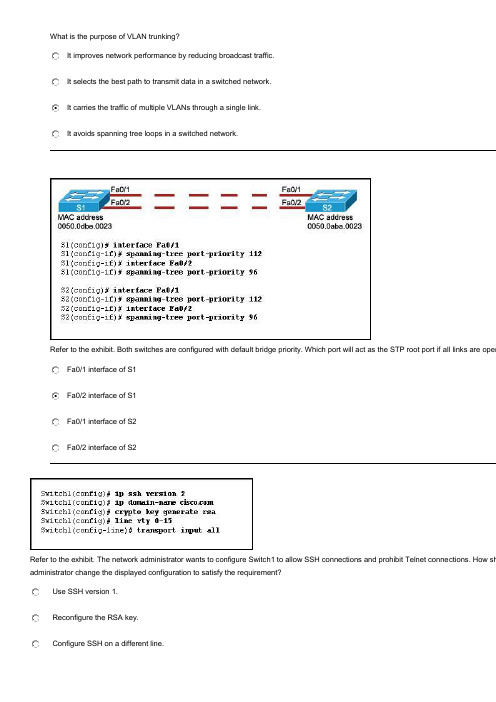
What is the purpose of VLAN trunking?It improves network performance by reducing broadcast traffic.It selects the best path to transmit data in a switched network.It carries the traffic of multiple VLANs through a single link.It avoids spanning tree loops in a switched network.Refer to the exhibit. Both switches are configured with default bridge priority. Which port will act as the STP root port if all links are oper Fa0/1 interface of S1Fa0/2 interface of S1Fa0/1 interface of S2Fa0/2 interface of S2Refer to the exhibit. The network administrator wants to configure Switch1 to allow SSH connections and prohibit Telnet conne ctions. How sh administrator change the displayed configuration to satisfy the requirement?Use SSH version 1.Reconfigure the RSA key.Configure SSH on a different line.Modify the transport input command.Refer to the exhibit. Which two facts about STP can be determined from the displayed output? (Choose two.)Switch S1 has the lowest configured STP priority in the network.Switch S1 is configured as the root bridge for VLAN1.Fa0/21 is the root port of switch S1.Fa0/22 is the redundant link.Fa0/24 is considered the best path to the root bridge.Which statement correctly describes the spanning-tree path cost?It is calculated based on the total number of switches connected in a loop.It is calculated based on the utilization of all the switches along a given path.It is calculated based on the bridge priority of the switches along a given path.It is calculated based on the sum of the port cost value, determined by link speed, for each switch port along a given path What are two requirements for configuring inter-VLAN routing using the router-on-a-stick model? (Choose two.)Each subinterface should be configured with its own IP address, subnet mask, and unique VLAN assignment.The physical interface of the router must be connected to a trunk link on the adjacent switch.The number of physical interfaces on the router should match the number of VLANs.Different static VLANs should be assigned to different interfaces of the router.The router should be configured as the VTP serverRefer to the exhibit. Which two options correctly describe the router configuration that is shown? (Choose two.)Routing between the 192.168.1.0 and 192.168.3.0 networks will not succeed until a routing protocol is configured on the route r.VLANs have not been appropriately configured on the router subinterfaces.The configuration is appropriate for a router-on-a-stick network design.Trunking has been appropriately configured on the router subinterfaces.An IP address should be applied to interface Fa0/1 for routing to occurRefer to the exhibit. What is true of the configuration of switch S1?A Cisco proprietary protocol is in use for ports Fa0/1 and Fa0/3.Switch ports Fa0/1 and Fa0/3 have been configured with the switchport mode access command.Untagged frames received on ports Fa0/1 and Fa0/3 will be placed on VLAN 1.Switch ports Fa0/1 and Fa0/3 are configured to carry data from multiple VLANs.Refer to the exhibit. Switches S2 and S3 are properly connected using an ethernet cable. A network administrator has configured both s is unable to propagate VLANs to S2. What could be the reason for this?The VTP configuration revision is different on both switches.The VTP domains are different on both switches.VTP pruning is disabled.VTP v2 is disabled.Refer to the exhibit. Router R1 is properly configured for router on a stick inter-VLAN routing, but PC1 is unable to ping PC2. What needs problem?Rename VLAN1.Connect one more port of S1 to R1.Configure the Fa0/1 port of S1 as a trunk port.Move the Fa0/0 interface of R1 to another VLAN.Refer to the exhibit. Router R-West and switch S-West1 are connected via a single ethernet cable between the router interface fa0/0 an fa0/1. The router and switch have been configured with the commands that are displayed in the exhib it. The network administrator ente trunk command and receives the output as shown. What is the cause of the "not-trunking" status for switch port Fa0/1?The trunk is established, but no VLANs have been configured to use it.The router is missing the dynamic trunking protocol statements necessary to form a trunk.Because the router does not support Dynamic Trunking Protocol, the trunk has not been established.The router, the switch, or both must be configured with the dynamic desirable option for Dynamic Trunking Protocol to establish aRefer to the exhibit. All trunk links are operational and all VLANs are allowed on all trunk links. An ARP request is sent by computer 5. W receive this message?only computer 4computer 3 and RTR-Acomputer 4 and RTR-Acomputer 1, computer 2, computer 4, and RTR-Acomputer 1, computer 2, computer 3, computer 4, and RTR-Aall of the computers and the routerRefer to the exhibit. A network administrator enters the displayed commands to configure VLAN 30. What is the result of running these commVLAN 30 will be added to S1, S2, and S3, but not to S4.VLAN 30 will be pruned from the VLAN database of S3.VLAN 30 will be added to the VLAN database of S3 but will not be propagated to S4, S2 or S1.VLAN 30 will not be added to the VLAN database of S3 and an error message will be displayedRefer to the exhibit. VTP pruning is enabled in the VTP domain that is shown. How will switch ST-1 handle Layer 2 broadcast traf host A on switch ST-C?It will be dropped.It will be forwarded out port Fa0/5 only.It will be forwarded out ports Fa0/5 and Fa0/10.It will be forwarded out ports Fa0/5, Fa0/10, and Fa0/15Refer to the exhibit. The devices in the network are operational and configured as indicated in the exhibit. However, hosts A and D other. What is the most likely cause of this problem?The link between the switches is up but not trunked.The Fa0/11 interface of Switch1 is not configured as a trunk.Hosts A and D are configured with IP addresses from different subnets.VLAN 20 and VLAN 30 are not allowed on the trunk between the switches.After unpacking a new Linksys WRT300N wireless multifunction device, a user needs to change the default administrator passwor d and make other configuration changes. What must the user do to access the device in order to make these changes?Use a wireless client to associate with the WRT300N and then open a HyperTerminal session with the device.Establish a wired connection with the device and then reboot the attached computer to launch the configuration software.Establish a wired connection from a computer in the same IP subnet as the WRT300N and enter the default IP address of the device into a web browser on the computer.Modify the TCP/IP properties of the computer that is connected to the WRT300N so that the computer and the WRT300N exist on the same network. Then reboot the computer to establish a connection.Refer to the exhibit. How is port Gi1/1 on SWT-A functioning in the spanning-tree topology?It is sending and receiving data frames.It is receiving BPDUs, but not sending data frames.It is participating in the election process by forwarding the BPDUs it receives.It is receiving BPDUs and populating the MAC address table, but not sending data.Refer to the exhibit. The switches have been configured as shown. The hosts that are connected to switch 101-2FL are not able to communicate with the hosts in their corresponding VLANs that are connected to switch 101-3FL. What should be done to fix the problem?Configure port Fa0/2 on switch 101-3FL as a static trunk link.Introduce a Layer 3 device or a switch with Layer 3 capability into the topology.Utilize the switchport trunk allowed vlan all command on switch 101-3FL to permit the VLAN traffic.Apply IP addresses that are in the same subnet to the interfaces that are used to connect switches 101-2FL and 101-3FLAfter listening for the presence of a signal on the network media, hosts A and C transmit data at the same time. In what two ways do the hosts respond to this situation? (Choose two.)The hosts transmit a jam signal to ensure that all hosts on the network are aware that a collision has occured.Because they are operating in full-duplex mode, the hosts resume listening for traffic in preparation for sending future messages.Because the hub will temporarily block traffic from one of the hosts, that host will be allowed to transmit once the wire is clear.Hosts A and C are assigned shorter backoff values to provide them priority to access the media for retransmission.After the backoff period of a host, the host checks to determine if the line is idle before retransmittingRefer to the exhibit. Hosts PC_A and PC_B send traffic simultaneously, and the frames from the transmitting stations collide.What is the last device to receive the collision?hub HB1switch SW1router R1switch SW2router R2switch SW4Refer to the exhibit. Switch SW2 has been newly purchased and added to the network. What configuration should be applied to SW2 so thatit participates in the same VTP domain as switch SW1, receives VLAN information from SW1, and synchronizes VLAN information?Disable VTP pruning on SW2.Configure SW2 in VTP transparent mode.Configure SW2 with the VTP domain password.Configure SW2 as a VTP server with a higher revision numberWhen configuring a router to act as an SSH server, what should be configured before issuing the crypto key generate rsacommand?the security domain namethe VTP domain namethe IP domain namethe host nameRefer to the exhibit. The switch VTY lines have been properly configured, but PC1 is unable to remotely manage the switch. How can this problem be resolved?Configure the Fa0/1 interface of the switch in trunk mode.Configure a default gateway on the switch.Configure the native VLAN on the switch.Configure the Fa0/1 interface of the switch to allow all VLANsRefer to the exhibit. A network administrator has segmented the network into two VLANs. The connected hosts can only access r esources in their own VLAN. What is the most scalable and cost effective solution to allow inter-VLAN communication in this network?Replace S1 with a router that has one FastEthernet interface for each PC.Add a second switch and divide the PCs so that each VLAN is connected to its own switch.Configure a router with two subinterfaces on one of its FastEthernet ports and connect it to S1 using a trunk link.Connect a router to a port on S1 and assign the IP address of VLAN1 to the connecting router interfaceRefer to the exhibit. An administrator documented the output of a CAM table from an Ethernet switch as shown. What action will the switch take when it receives the frame shown at the bottom of the exhibit?discard the frameforward the frame out port 2forward the frame out port 3forward the frame out all portsforward the frame out all ports except port 3add station 00-00-3D-1F-11-05 to port 2 in the forwarding tableWhich statement regarding the service password-encryption command is true?The service password-encryption command is entered at the privileged EXEC mode prompt.The service password-encryption command encrypts only passwords for the console and VTY ports.The service password-encryption command encrypts all previously unencrypted passwords in the running configuration.To see the passwords encrypted by the service password-encryption command, enter the no servicepassword-encryption commandWhich statement correctly describes the function of a Layer 2 switch?It performs switching and filtering based on the destination network layer address.It automatically uses STP to prevent switching loops in redundant topologies.It uses VTP to allow data from multiple VLANs to travel across a single link.It routes packets between different LAN segmentsWhich three statements are correct concerning the default configuration of a new switch? (Choose three.)It is configured in VTP server mode.STP is automatically enabled.The first VTY line is automatically configured to allow remote connections.VLAN1 is configured with a management IP address.All switch ports are assigned to VLAN1.The enable password is configured as ciscoRefer to the exhibit. How will switch S2 manage traffic coming from host PC1?S2 will drop the traffic, unless it is management traffic.S2 will tag the frame with VLAN ID 99 when it forwards it over the trunk link.S2 will leave the traffic untagged when it forwards it over a trunk link.S2 will tag the traffic with the highest VLAN ID value when it forwards it over the trunk link.Refer to the exhibit. The network administrator needs to remove the east-hosts VLAN and use the switch port from that VLAN in one of the existing VLANs. Which two sets of commands should be used when completely removing VLAN 2 from S1-Central while leaving the switch and all its interfaces operational? (Choose two.)S1-Central>enableS1-Central# reloadS1-Central>enableS1-Central# erase flash:S1-Central>enableS1-Central# delete flash:vlan.datS1-Central>enableS1-Central# configure terminalS1-Central(config)# no vlan 2S1-Central>enableS1-Central# configure terminalS1-Central(config-if)# interface fastethernet 0/1 S1-Central(config-if)# switchport access vlan 3Refer to the exhibit. The network administrator configures both switches as displayed. However, host C is unable to ping host D and host E is unable to ping host F. What action should the administrator take to enable this communication?Include a router in the topology.Associate hosts A and B with VLAN 10 instead of VLAN 1.Remove the native VLAN from the trunk.Configure one trunk port in the dynamic desirable mode.Add the switchport nonegotiate command to the configuration of S2Which two statements are correct about wireless infrastructure components? (Choose two.)An AP converts the TCP/IP data packets from their 802.11 frame encapsulation format to the 802.3 Ethernetframe format on the wired Ethernet network.A wireless AP does not require any physical connection to allow wireless clients to access the Internet.An AP is a layer 2 device, similar to a switch, that provides dedicated bandwidth to each connected wireless host.Collisions do not occur between wireless NICs and APs.The wireless router performs the roles of AP and router.Refer to the exhibit. The switches are configured for VTP as shown. Which two statements correctly describe the operation of these switches? (Choose two.)A new VLAN can be added to Switch1 and that information will be added only to Switch2.A new VLAN can be added to Switch1 and that information will be added to Switch2 and Switch4.An existing VLAN can be deleted from Switch4 and that VLAN will be deleted from Switch1 and Switch2.An existing VLAN can be deleted from Switch2 and that VLAN will be deleted from Switch1 and Switch4.A new VLAN can be added to Switch4 and that information will be added to Switch1, Switch2, and Switch3.A new VLAN can be added to Switch3 and that information will be added to Switch1, Switch2, and Switch4A new switch is to be added to an exis ting network in a remote office. The network administrator does not wantthe technicians in the remote office to be able to add new VLANs to the switch, but the switch should receive VLAN updates from the VTP domain. Which two steps must be performed to configure VTP on the new switch to meet these conditions? (Choose two.)Configure an IP address on the new switch.Configure the existing VTP domain name on the new switch.Configure all ports of both switches to access mode.Configure the new switch as a VTP client.Enable VTP pruningWhich two statements describe Spanning Tree Protocol? (Choose two.)It is only used at Layer 2.It is configured on routers.It eliminates Layer 2 loops in network topologies.It limits the number of valid MAC addresses allowed on a port.It allows VLAN information to propagate to other switches in the network.Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology?Cat-ACat-BCat-CCat-DRefer to the exhibit. What three statements describe why Host1 and Host2 are unable to communicate? (Choose three.)The switch ports are on different VLANs.The switch IP address is on the wrong subnet.The hosts are configured on different logical networks.A router is required to forward traffic between Host1 and Host2.The VLAN port assignments must be contiguous for each VLAN.The host default gateway addresses must be on the same logical network.Refer to the exhibit. A new host needs to be connected to VLAN 3. Which IP address should be assigned to this new host?192.168.1.22 /28192.168.1.31 /28192.168.1.32 /28192.168.1.52 /28192.168.1.63 /28Refer to the exhibit. Router RA receives a packet with a source address of 192.168.1.65 and a destination address of 192.168.1.161. What will the router do with this packet?The router will drop the packet.The router will forward the packet out interface FastEthernet 0/1.1.The router will forward the packet out interface FastEthernet 0/1.2.The router will forward the packet out interface FastEthernet 0/1.3.The router will forward the packet out interface FastEthernet 0/1.2 and interface FastEthernet 0/1.3Refer to the exhibit. On which of the devices in this network should routing between VLANs take place?the core layer devicesthe access layer devicesthe distribution layer devicesthe core and distribution layer devicesRefer to the exhibit. The teacher host is connected to port Fa0/7 on switch STW. A student has decided to share access to the Internet by attaching a hub and laptop to STW as shown. What will be the result of the student making this connection?The Fa0/7 port of STW will be shutdown.The student will gain full access to the Internet.Both the teacher and student will be able to receive data but only the teacher will be able to send.The frames from the laptop will be dropped, but the teacher host will maintain connectivity with the network.Refer to the exhibit. In what two ways will the router handle VLAN traffic that is received on the trunk? (Choose two.)Traffic to VLAN 1 received by the router interface Fa0/0 will be dropped by the router.Because interface Fa0/0 requires an IP address, the router will not be able to route between the VLANs.Packets that are received from network 192.168.20.0 /24 will be handled by subinterface Fa0/0.20.The router will use subinterface MAC addresses to identify the VLAN traffic that is received on the physical interface.The router will continue to process traffic from the attached VLANs even if the physical interface goes downRefer to the exhibit. Switch SW-A is to be used as a temporary replacement for another switch in the VTP Studentdomain. What two pieces of information are indicated from the exhibited output? (Choose two.)The other switches in the domain can be running either VTP version 1 or 2.There is a risk that the switch may cause incorrect VLAN information to be sent through the domain.VTP will block frame forwarding on at least one redundant trunk port that is configured on this switch.VLAN configuration changes made on this switch will be sent to other devices in the VTP domain.This switch will update its VLAN configuration when VLAN changes are made on a VTP server in the same domainWhat are three benefits of employing a hierarchical network design? (Choose three.)Hierarchically designed networks can more easily be expanded to suit future needs.Hierarchical design models enhance existing bandwidth through the use of link aggregation.The hierarchical model allows for specialized functionality at each layer, simplifying devicemanagement.Use of a hierarchical design allows replacement of redundant devices with high-capacity network equipment.A hierarchical design uses firewalls instead of complicated port-based and distribution layer securitypolicies.The hierarchical model allows the use of high-performance switches at all design layers, thus allowing for a fully-meshed topologyRefer to the exhibit. Hosts A and B attempt to transmit a frame at the same time and a collision occurs. When will host D be able to transmit?immediatelyafter sending its jam signalafter host A and host B have completed transmissionafter the jam signal clears and its backoff delay expiresWhat provides an authentication mechanism for 802.11-based wireless networks?DSSSOFDMSSIDWPARefer to the exhibit. What is the effect of setting the security mode to WEP on the Linksys integrated router?WEP identifies the wireless LAN.WEP allows the access point to inform clients of its presence.WEP translates IP addresses into easy-to-remember domain names.WEP encrypts data between the wireless client and the access point.WEP ensures that only authenticated users are allowed access to the WLAN.WEP translates an internal address or group of addresses into an outside, public address.Refer to the exhibit. SW-T has been configured with a single trunking interface. Which VLANs will be allowed across the trunk?Only VLAN 1 will be allowed across the trunk.All configured VLANs will be allowed across the trunk.Only the native VLAN will be allowed across the trunk.Only the the management and native VLANs will be allowed across the trunk.Only VLANs that are configured on the VTP server in the dom ain will be allowed across the trunkRefer to the exhibit. What does the term DYNAMIC indicate in the output that is shown?This entry can only be removed from the MAC address table by a network administrator.When forwarding a frame to the device with address 0060.5c5b.cd23, the switch does not have to perform a lookup to determine the final destination port.Only the device with MAC address 0060.5c5b.cd23 will be allowed to connect to port Fa0/18.The switch learned this MAC address from the source address in a frame received on Fa0/18.Refer to the exhibit. What is the purpose of the configuration commands that are shown?to activate port Fa0/10to make the port a member of VLAN 30to activate port security on port Fa0/10to add VLAN 30 to the trunk that is connected to port Fa0/10。
CCNA思科第三学期ESwitchingExam正确答案

单臂路由器VLAN间路由有哪三项特征?(选择三项。
)需要使用VTP需要使用子接口减少广播域的数量使用过多VLAN时会影响性能需要在路由器和至少一台交换机之间采用接入链路比用于VLAN间路由的其它方法更加经济规定至少要在路由器和交换机之间使用两个交换机端口如果将允许使用中继链路的VLAN范围设置为默认值,表示允许哪些VLAN?仅管理VLAN除扩展范围VLAN之外的所有VLAN除VLAN1和VLAN1002-1005之外的所有VLAN所有的VLAN请参见图示。
哪一个口令可让管理员进入特权执行模式?c isco1c isco2c isco3c isco请参见图示。
假设所有交换机的网桥优先级值都那么哪台交换机将当选为生成树拓扑的根桥?C at-AC at-BC at-CC at-D请参见图示。
最近安装了SW1用于取代集线器。
主机1和主机4同时设备会如何处理此事件?(选择两项。
)当冲突发生时,会调用回退算法。
由于主机1和主机4都连接到交换机,因此不会发生冲突。
交换机将根据交换机MAC地址表中的信息将数据转发到相应的端口。
主机2和主机3会获分配更短的回退值,从而获得访问介质的优先权。
为了防止再发生冲突,交换机会在设定时间内阻塞与主机2、主机3和主机4连接的端口。
请参见图示。
网络管理员需要删除并将属于该VLAN的交换机端口用到一个现有VLAN中。
如果要从S1-Central完全删除VLAN2,同时保证交换机及其所有接口工作正两组命令?(选择两项。
)S1-Central>enable S1-Central#reloadS1-Central>enable S1-Central#eraseflash:S1-Central>enable S1-Central#deleteflash:S1-Central>enable S1-Central#configureterminal S1-Central(config)#novlan2S1-Central>enable S1-Central#configureterminal S1-Central(config-if)#interfacefastethernet0/1S1-Central(config-if)#switch请参见图示。
final exam 2 CCNA 第三学期(免费下载)
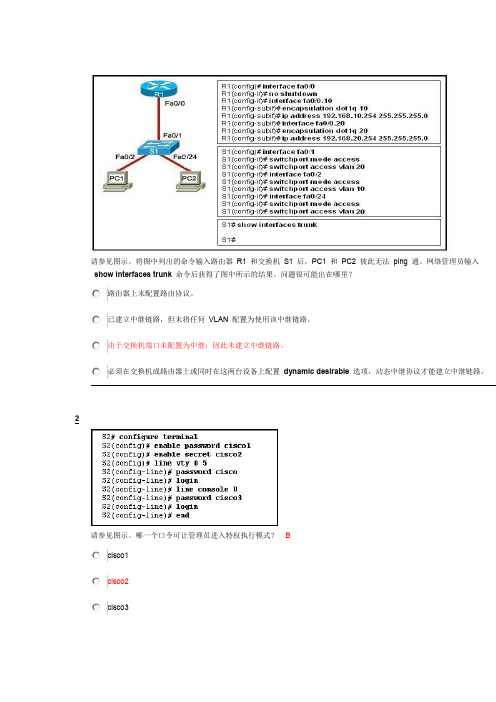
请参见图示。
将图中列出的命令输入路由器R1 和交换机S1 后,PC1 和PC2 彼此无法ping 通。
网络管理员输入show interfaces trunk命令后获得了图中所示的结果。
问题很可能出在哪里?路由器上未配置路由协议。
已建立中继链路,但未将任何VLAN 配置为使用该中继链路。
由于交换机端口未配置为中继,因此未建立中继链路。
必须在交换机或路由器上或同时在这两台设备上配置dynamic desirable选项,动态中继协议才能建立中继链路。
2请参见图示。
哪一个口令可让管理员进入特权执行模式?Bcisco1cisco2cisco3Cisco3下列关于service password-encryption命令的说法中哪项正确?cservice password-encryption命令应在特权执行模式提示符下输入。
service password-encryption命令只加密控制台与VTY 端口的口令。
service password-encryption命令对运行配置中先前未加密的所有口令进行加密。
若要查看通过service password-encryption命令加密的口令,可输入no service password-encryption命令。
4请参见图示。
RTB 被配置为进行传统的VLAN 间路由。
RTB 可以ping 通计算机 A 但无法ping 通计算机B。
此故障的原因可能是什么?Fa0/11 端口处于错误的VLAN 中。
RTB 上没有有效的路由协议。
计算机 B 的IP 地址在错误的逻辑网络中。
路由器的Fa0/1 接口上配置了错误的中继封装类型。
5请参见图示。
最近安装了SW1 用于取代集线器。
主机1 和主机 4 同时传送数据。
网络设备会如何处理此事件?(选择两当冲突发生时,会调用回退算法。
A D由于主机 1 和主机4 都连接到交换机,因此不会发生冲突。
交换机将根据交换机MAC 地址表中的信息将数据转发到相应的端口。
ccna_第三学期期末考试

1.VLAN 中继有何用途?通过减少广播流量提高网络性能。
选择在交换网络中传输数据的最佳路径。
通过一条链路传送多个VLAN 的流量。
避免交换网络中出现生成树环路。
请参见图示。
两台交换机都配置有默认的网桥优先级。
如果所有链路都在相同的带宽下运行,哪个端口将作为STP 根端口?S1 的Fa0/1 接口S1 的Fa0/2 接口S2 的Fa0/1 接口S2 的Fa0/2 接口请参见图示。
从图中显示的输出可以得到有关STP 的哪两项结论?(选择两项。
)交换机S1 所配置的STP 优先级值在该网络中最低。
交换机S1 被配置为VLAN1 的根桥。
Fa0/21 是交换机S1 的根端口。
Fa0/22 是冗余链路。
Fa0/24 被视为通往根桥的最佳路径。
下列哪种说法正确描述了生成树路径开销?根据环路中连接的交换机总数计算。
根据给定路径上所有交换机的使用率计算。
根据给定路径上交换机的网桥优先级计算。
根据给定路径上每个交换机端口的端口开销值(由端口速度决定)的总和计算。
使用单臂路由器模型配置VLAN 间路由有哪两项要求?(选择两项。
)每个子接口都应配置有自己的IP 地址、子网掩码和唯一的VLAN 分配。
路由器的物理接口必须连接到相邻交换机上的中继链路。
路由器的物理接口数量应该与VLAN 数量匹配。
应该将不同的静态VLAN 分配给路由器的不同接口。
路由器应该配置为VTP 服务器。
请参见图示。
下列哪两项正确描述了图中所示的路由器配置。
(选择两项。
)在路由器上配置路由协议之前,网络192.168.1.0 与网络192.168.3.0 之间无法成功路由。
路由器子接口上未正确配置VLAN。
该配置适用于单臂路由器网络设计。
路由器子接口上未正确配置中继。
应该为接口Fa0/1 分配IP 地址,否则无法进行路由请参见图示。
下列有关交换机S1 配置的说法中哪项正确?端口Fa0/1 和Fa0/3 使用的是Cisco 专有协议。
已使用switchport mode access命令配置交换机的Fa0/1 和Fa0/3 端口。
CCNA 4 - Final Exam (B)
CCNA 4 - Final Exam (B)Posted by beotron at 9:23 PM1. Identify the factors that contribute to congestion on an Ethernet LAN. (Choose three.)• improper placement of enterprise level servers• addition of hosts to a physical segment• replacement of hubs with workgroup switches• increasing use of bandwidth intensive network applications• migration to full-duplex Ethernet within the LAN2. Which of the following are examples of TCP/IP application layer protocols? (Choose three.)• a terminal emulation protocol that supports remote console connections with various network devices • a protocol created by IBM that makes it easier for mainframes to connect t o remote offices• a protocol responsible for transporting electronic mail on TCP/IP networks and the Internet• a protocol that controls the rate at which data is sent to another computer• a protocol that exchanges network management information between a network device and a management console3. Which of the following eliminates switching loops?• hold-down timers• poison reverse• spanning tree protocol• time to live• split horizon protocol4. The show cdp neighbors command is a very useful network troubleshooting tool. Using the output in the graphic, select the statements that are true. (Choose two.)• CDP operates at the network layer of the OSI model.• The output of this command displays information about directly connected Cisco devices only.• The switch is attached to the SanJose1 FastEthernet0/21 interface.• SanJose1 is running CDP version 12.0.• SanJose1 has two fully operational, cdp-enabled Cisco switches directly connected to it.• SanJose2 is a 2600 series router running several routed protocols5. A network administrator can ping the Denver router, but gets a ‘Password Required but None Set’ message when trying to connect remotely via Telnet. Which command sequence must be applied to the Denver router to allow remote access?• Router(c onfig)# line console 0Router(config-line)# loginRouter(config-line)# password cisco• Router(config)# line vty 0 4Router(config-line)# loginRouter(config-line)# password cisco• Router(config)# line virtual terminalRouter(config-line)# enable loginRouter(config-line)# password cisco• Router(config)# line vty 0 4Router(config-line)# enable secretRouter(config-line)# password ciscoRouter(config)# enable secret ciscoRouter(config)# enable cisco6. Which of the following is associated with link-state routing protocols?• low processor overhead• poison reverse• routing loops• split horizon• shortest-path first calculations7. A router does not load its configuration after a power failure. After running the showstartup-configuration command, the adminstrator finds that the original configuration is intact. What is the cause of this problem?• The configuration register is set for 0×2100.• The configuration register is set for 0×2101.• The configuration register is set for 0×2102.• The configurati on register is set for 0×2142.• Boot system commands are not configured.• Flash memory is empty causing the router to bypass the configuration in NVRAM• Nederst på formularen8. Which commands are used to verify the content and placement of access control lists? (Choose three.) • show ip interface• show ip route• show processes• show running-config• show cdp neighbor• show access-lists9. Which of the following are required when creating a standard access control list? (Choose two.)• destination ad dress and wildcard mask• source address and wildcard mask• subnet mask and wildcard mask• access list number between 100 and 199 or 2000 and 2699• access list number between 1 and 99 or 1300 to 199910. Which of the following are keywords that can be used in an access control list to replace a dotted decimal wildcard mask? (Choose two.)• most• host• all• any• some• sum11. Refer to the diagram. All ports on Switch A are in the Sales VLAN and all ports on Switch B are in the Accounting VLAN. How many broadcast domains and how many collision domains are shown? (Choose two).• 3 collision domains• 3 broadcast domains• 5 broadcast domains• 9 collision domains• 10 collision domains• 13 collision domains12. Refer to the graphic. Using the most efficient IP addressing scheme and VLSM, which address can be configured on one of the serial interfaces?• 192.168.16.63/27• 192.168.16.158/27• 192.168.16.192/27• 192.168.16.113/30• 192.168.16.145/30• 192.168.16.193/3013. What is the purpose of the Spanning Tree Protocol (STP)?• prevents Layer 2 loops• prevents routing loops on a router• creates smaller collision domains• creates smaller broadcast domains• allows Cisco devices to exchange routing table updates14. What is the purpose of a loopback address when using the OSPF routing protocol?• activates the OSPF neighboring process• ensures a persistent router ID for the OSPF process• provides a backdoor for connectivity during the convergence process• streamlines and speeds up the convergence pr ocess15. Which statement is true regarding states of the IEEE 802.1d Spanning Tree Protocol?• Ports are manually configured to be in the forwarding state.• Ports listen and learn before going into the forwarding state.• Ports must be blocked before the y can be placed in the disabled state.• It takes 15 seconds for a port to go from blocking to forwarding16. Which sequence of commands is used to configure a loopback address on a router?• Router1(config)# interface loopback 1Router1(config-if)# ip address 192.168.1.1Router1(config)# interface serial 0/0• Router1(config-if)# loopback 1Router1(config-if)# ip address 192.168.1.1Router1(config)# interface serial 0/0• Router1(config-if)# loopback 1Router1(config-if)# ip address 192.168.1.1 255.255.255.0• Router1(config)# interface loopback 1Router1(config-if)# ip address 192.168.1.1 255.255.255.25517. Which routing protocols are classful and do not support VLSM? (Choose two.)• EIGRP• OSPF• RIP v1• RIP v2• IGRP18. Refer to the graphic. Two switches are connected together through a trunk port. SW2 displays the message shown. Which of the following will solve the duplex mismatch?• SW1(config)# interface fastethernet 0/1SW1(config-if)# duplex full• SW1(config)# interface fastethernet 0/1SW1(config-if)# full-duplex• SW2(config)# interface fastethernet 0/1SW2(config-if)# duplex full• SW2(config)# interface fastethernet 0/1SW2(config-if)# full-duplex19. Refer to the graphic. Two routers have been configured to use EIGRP. Packets are not being forwarded between the two routers. What could be the problem?• EIGRP does not support VLSM.• The routers were not configured to monitor neighbor adjacency changes.• The default bandwidth was used on the routers.• An incorrect IP address was configured on a router interface.20. According to the the provided router output, which of the following statements is true regarding PPP operation?• Only the link-establishment phase completed successfully.• Only the network-layer phase completed successfully.• Neither the link-establishment phase nor the the network-layer phase completed successfully.• Both the link-establishment and network-layer phase completed successfully21. Frame Relay is configured over a point-to-point connection between two routers. The output of the show frame-relay pvc command indicates that the status of this PVC is inactive. Which of the following devices could be the source of the problem? (Choose two.)• local router• local Frame Relay switch• remote router• remote Frame Relay switch• R3 has the following configuration:• R3# show running-config• –some output text omitted–• interface serial0/0• bandwidth 128• ip address 192.168.11.2 255.255.255.0• encapsulation frame-relay• frame-relay map ip 192.168.11.2 30 broadcast22. After the command R3# debug frame-relay packet is executed, a ping is issued from R3 to R1 but is unsuccessful. Based on the output of the debug command shown in the graphic and the router configuration, what might be problem?• No clock rate assigned.• There is an incorrect DLCI number in the map statement.• An incorrect IP address exists in the map statement.• The encapsulation command is missing the broadcast keywor d23. Which statements are true regarding the Frame Relay LMI? (Choose three.)• The LMI provides a virtual circuit (VC) status mechanism.• The LMI type must always be manually configured.• The available LMI types are NI1, DMS100 and 5ESS.• The LMI types supported by Cisco routers are CISCO and IETF.• The LMI type configured on the router must match the one used on the Frame Relay switch.• The LMI uses reserved DLCIs to exchange messages between the DTE and DCE24. Which statement describes the process that occurs in Network Address Translation (NAT) overloading?• Multiple private IP addresses are mapped to one public IP address.• The number of usable addresses assigned to a company is divided into smaller manageable groups.• A pool of IP addres ses are mapped to one or more MAC addresses.• The router acts as a DHCP server and assigns multiple public IP addresses for each private IP address configured25. Which two statements are true about the committed information rate on a Frame Relay link? (Choose two.)• The sum of the CIRs for all PVCs must be less than the port speed.• The sum of the CIRs for all PVCs must equal the port speed.• The sum of the CIRs for all PVCs can be greater than the port speed.• The DE bit will be set on frames that ar e transmitted in excess of the CIR.• Frames that are transmitted at greater than the CIR will be discarded at the source.• It is impossible to transmit frames at a rate in excess of the CIR26. Which of the following commands would be used to troubleshoot the processing of call control functions such as call setup, signaling, and termination?• show interface bri0/0• show isdn active• debug isdn q921• debug isdn q931• debug ppp negotiation• debug ppp authentication27. Which of the following statements are true regarding PPP? (Choose three.)• PPP can use synchronous and asynchronous physical media.• PPP can only be used between two Cisco devices.• PPP carries packets from several network layer protocols in LCPs.• PPP uses LCPs to establish, config ure, and test the data link connection.• PPP uses LCPs to agree on format options such as authentication, compression, and error detection28. A network administrator is evaluating authentication protocols for a PPP link. Which of the following reasons might lead to the selection of CHAP over PAP as the authentication protocol? (Choose three.) • establishes identities with a two-way handshake• uses a three-way authentication periodically during the session to reconfirm identities• control by the remote h ost of the frequency and timing of login events• transmits login information in encrypted format• uses an unpredictable variable challenge value to prevent playback attacks• makes authorized network administrator intervention a requirement to establish each session29. Why are static routes often used with ISDN DDR?• They are more stable than dynamic routing protocols.• They are more accurate than dynamic routing protocols because they are put in by a network administrator.• They are easier to modify when a faster technology is installed.• They prevent the unnecessary activation of the link30. Assuming that four bits have been borrowed to make subnets, identify the subnet network addresses. (Choose three.)• 192.168.14.8• 192.168.14.16• 192.168.14.24• 192.168.14.32• 192.168.14.148• 192.168.14.20831. A switch can be configured for three different forwarding modes based on how much of a frame is received before the forwarding process begins. Each of the numbered arrows in the accompanying graphic signifies the point in a frame where a particular forwarding mode will begin. Which one of the following groups reflects the sequence of forwarding modes signified by the numbered arrows?• 1) fast forward• 2) fragment free• 3) store-and-forward• 1) sto re-and-forward2) fragment free3) fast forward• 1) fragment free2) fast forward3) store-and-forward• 1) fast forward2) store-and-forward3) fragment free32. Which of the following commands will display a communication message on a router before the router prompt is shown?• banner motd * Property of TLC. UNAUTHORIZED USERS WILL BE PROSECUTED TO THE FULL EXTENT OF THE LAW. *• message Property of TLC. UNAUTHORIZED USERS WILL BE PROSECUTED TO THE FULL EXTENT OF THE LAW.• banner * Property of TLC. UNAU THORIZED USERS WILL BE PROSECUTED TO THE FULL EXTENT OF THE LAW. *• hostname (Property of TLC. UNAUTHORIZED USERS WILL BE PROSECUTED TO THE FULL EXTENT OF THE LAW.)• Øverst på formularen33. A router needs to be added to OSPF area 0. Which commands should be used to enable OSPF on the router? (Choose two.)• RouterA(config)# router ospf• RouterA(config)# router ospf 1• RouterA(config-router)# network 192.168.2.0 0.0.0.255 0• RouterA(config-router)# network 192.168.2.0 0.0.0.255 area 0• RouterA(config-router)# network 192.168.2.0 255.255.255.0 034. Refer to the graphic. Which of the following commands will configure router A for OSPF?• router ospf 1network 192.168.10.0• router ospf 1network 192.168.10.64 0.0.0.63 area 0network 192.168.10.192 0.0.0.3 area 0• router ospf 1network 192.168.10.64 255.255.255.192network 192.168.10.192 255.255.255.252• router ospf 1network 192.168.10.0 area 035. Which of the following protocols would exchange information between routers to share network addresses and their metrics?• TCP• RIP• CSMA/CD• Ethernet36. Which ISDN device can be directly connected to a two-wire local loop in a North American city?• a router with a serial interface• a router with an S/T interface• a router with a U interface• an ISDN terminal adapter37. The output of the show ip interfaces brief command indicates that Serial0 is up but the line protocol is down. Which of the following are possible causes for the line protocol being in the down state? (Choose two.)• The clock rate is not set on the DTE.• An incorrect default gateway is set on the router.• A network is missing from the routing protocol configuration.• The encapsulation on the Serial0 interface is incorrect.• Keepalives are not being sent by the remote device38. Which of the following is a characteristics of TCP? (Choose two.)• data transport reliability• best path determination• establishing, maintaining, and terminating virtual circuits• encapsulation of packets in a data frame with source and destination MAC addresses• best-effort datagram delivery39. Which statement is true regarding the command ip route 192.168.7.24 255.255.255.248 192.168.7.9? (Choose two.)• A packet destined for host 192.168.7.30 will be forwarded to address 192.168.7.9.• 192.168.7.9 i s the destination network for this route.• 192.168.7.24 is the next-hop router in this command.• This command is issued from the interface configuration mode.• This command is used to define a static route40. Which of the following application layer protocols use TCP? (Choose three.)• SMTP• FTP• SNMP• HTTP• TFTP• DHCP41. Which terms refer to Frame Relay congestion management mechanisms? (Choose three.)• BECN• DLCI• DE• FECN• LMI• Inverse ARP42. Which of the following router commands will verify that a path exists to a destination network?• Router# show ip interfaces brief• Router# show ip route• Router# show cdp neighbors• Router# show running-config• Router# show protocols43. When EIGRP is configured on a router, which table of DUAL information is used to calculate the best route to each destination router?• router table• topology table• DUAL table• CAM table• ARP table44. Refer to the graphic. Routers A and B have EIGRP configured and automatic summarization has been disabled on both routers. Which of the following commands is used on router A to summarize the attached routes, and to which interface is this command applied? (Choose two)• ip summary-address eigrp 1 192.168.10.64 255.255.255.192• ip area-range eigrp 1 192.168.10.80 255.255.255.224• summary-address 192.168.10.80 0.0.0.31• ip summary-address eigrp 1 192.168.10.64 0.0.0.63• serial interface on router A• serial interface on router B45. A router with two LAN interfaces, two WAN interfaces, and two loopback interfaces configured is operating with OSPF as its routing protocol. What is used by the OSPF process to assign the router ID? • the IP address of the interface configured with priority 0• the OSPF area ID configured on the interface with the highest IP addres s• the loopback with the highest IP address configured• the highest IP address on the LAN interfaces• the highest IP address configured on the WAN interfaces46. Given the IP address and subnet mask of 172.16.134.56 255.255.255.224, on which subnetwork does this address reside?• 172.0.0.0• 172.16.134.0• 172.16.134.32• 172.16.134.48• 172.16.134.47• 172.16.134.6347. Which commands show when the last IGRP routing update was received? (Choose two.)• Router# show ip protocols• Router# show version• Router# show interfaces• Router# show ip updates• Router# show ip route48. When using access control lists to filter traffic, which of the following is used to track multiple sessions occurring between hosts?• IP addresses• subnet masks• port numbers• routed protocols• routing protocols• interfaces49. Given the IP address and subnet mask of 172.16.134.64 255.255.255.224, which of the following would describe this address?• This is a useable host address.• This is a broadcast address.• This is a network address.• This is not a valid address50. The company network shown in the drawing has to be subnetted. The company has leased the ClassC IP address of 200.1.2.0. Which of the following network addresses and masks would be appropriate for one of the subnetworks?• 200.1.2.96 255.255.255.192• 200.1.2.160 255.255.255.224• 200.1.2.80 255.255.255.224• 200.1.2.32 255.255.255.240。
CCNA考试流程及注意事项(很详细)
CCNA考试流程及注意事项(很详细哦)希望你能仔细看完,肯定会对你有一点点帮助1,关于CCNA备考CCNA备考主要以题库为主,当然,前期的课本还有视频是必须要看的。
现在网上流传的都是确切的V31版,题库总共有400道题左右,其中选择题占385都左右,托图题占10都左右,实验题5到左右,其中有三道ACL 、EIGRP 、VTP排错是必考题。
2,关于CCNA考试CCNA考试总共1000分,825分通过,考试时间120分钟。
总共从题库中抽取50道题,45到选择,2道实验,三道必考的实验ACL EIGRP VTP排错,其中实验在考试中占很大的比例,即使你选择和托图都对,实验也对了两道,也很可能会挂,所以实验题很重要,所以三道实验最少也得对2.5道以上。
NA考试考场流程提前预约考试,确认之后考试当天提前去考场(提前去开始提前开始的,但是不能迟到),别忘了带两个有效证件,身份证是必须的,其他一个证件可以是驾照,学生证,暂住证等等。
在考场之后考场MM会拿去你的证件复印,好了之后在VUE上签名,照相等。
手续办完之后就可以近考场了,注意哦,不能携带任何东西哦。
4、问卷调查考试系统分为VUE和Prometric两种,系统不同,开始的问卷调查内容也略有不同,但是不用担心,统选B相对安全,选完一道点NEXT,一直到END。
因为B选项通常表示考生水平一般,抽取的考题也不会太难。
注意:其中有一个调查是问你是否已满18周岁,一定要选已满18周岁(YES)。
最后一个调查是问你是否同意CISCO的协议,这个一定要选“同意”,如果您选“不同意”,那么你也就不用考试了。
曾经有位仁兄选了不同意,结果题目一直没有出现,一问考场,人家解释:你连CISCO的协议都不同意,你还考什么?不用考了。
要想再考,得再交一次考试费,重新注册这门考试。
协议过后,调查问卷页面右下角点END选项,考试系统自动开始从服务器抽取题目,题目前一天已由考试中心从澳洲下载完毕,暂存于服务器中。
CCNA_第三学期__期末完整版考试
1CCNA 第三学期 期末While monitoring LAN traffic, a network technician notices an excessive number of broadcasts. Which two steps could be included in the processes that are needed to reduce the number of broadcasts onthe network? (Choose two.)Replace any existing hubs with switches.Add a Layer 3 device to route between networks.Subnet the existing IP network to create two networks.Increase the backbone speed by three times the current speed.Add additional switches and spread out the number of hosts evenly between them.2What advantage does cut-through switching provide?It enables QoSIt forwards frames quickly.It provides an analysis of frames.It allows reduction of traffic by using error checking to drop corrupt frames.3Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology?Cat-ACat-BCat-CCat-D4W hich stackable switch feature allows for interconnection of multiple switches and will provide a cost effective solution for networks that require high bandwidth and high availability?modular line cardsspecial backplane portdedicated gigabyte line portsaggregated FastEthernet ports5Refer to the exhibit. This switch is to be added to the production network. Which two facts about VLANs and VTP operation can be confirmed by this output? (Choose two.)The network administrator will be able to configure VLANs of local significance on this switch.VLANs can only be added to the VLAN database on this switch by a VTP advertisement.All VLANs that are configured on this switch will be sent to all other switches in the same VTP domain.This switch will drop all VTP advertisements that come from switches that are configured in the same VTP domain.Adding this switch to the network will cause no disruption in the VTP domain operations if the rest of the switches in the same VTP domain have a higher configuration revision number.6Refer to the exhibit. The hosts connected to switch SW1 are not able to communicate with the hosts in the same VLANs connected to switch SW2. What should be done to fix the problem?Configure VLANs with different VLAN IDs on switch SW2.Reconfigure the trunk port on switch SW2 with static trunk configuration.Introduce a Layer 3 device or a switch with Layer 3 capability in the topology.Apply IP addresses that are in the same subnet to the interfaces used to connect SW1 and SW2.7Refer to the exhibit. A new host needs to be connected to VLAN 3. Which IP address should beassigned to this new host?192.168.1.22 /28192.168.1.31 /28192.168.1.32 /28192.168.1.52 /28192.168.1.63 /288Refer to the exhibit. SW-T has been configured with a single trunking interface. Which VLANs will be allowed across the trunk?Only VLAN 1 will be allowed across the trunk.All configured VLANs will be allowed across the trunk.Only the native VLAN will be allowed across the trunk.Only the the management and native VLANs will be allowed across the trunk.Only VLANs that are configured on the VTP server in the domain will be allowed across the trunk.9Refer to the exhibit. How will switch S2 manage traffic coming from host PC1?S2 will drop the traffic, unless it is management traffic.S2 will tag the frame with VLAN ID 99 when it forwards it over the trunk link.S2 will leave the traffic untagged when it forwards it over a trunk link.S2 will tag the traffic with the highest VLAN ID value when it forwards it over the trunk link. 10Refer to the exhibit. Both switches are interconnected via a trunk link. Host A and host B are on the default VLAN but are not able to exchange traffic. What should be done to fix the problem?Allow all VLANs on the trunk link.Remove the native VLAN from the trunk.Include a router or switch with Layer 3 capabilities.Configure the same native VLAN on both ends of the trunk.11Refer to the exhibit. What does the term DYNAMIC indicate in the output that is shown?This entry can only be removed from the MAC address table by a network administrator.When forwarding a frame to the device with address 0060.5c5b.cd23, the switch does not have to perform a lookup to determine the final destination port.Only the device with MAC address 0060.5c5b.cd23 will be allowed to connect to port Fa0/18.The switch learned this MAC address from the source address in a frame received on Fa0/18.12W hy is MAC address filtering considered a poor choice in securing a WLAN?Available bandwidth is reduced.MAC addresses are easily spoofed.APs are more susceptible to DoS attacks.The payload encryption is easily broken.13How does a switch that is configured for 802.1Q trunking handle untagged frames that are receivedon a trunk port?The frames are dropped.The frames are assigned to the native VLAN.The frames are assigned to the default VLAN.The frames are assigned to the management VLAN.14Refer to the exhibit. Which three options correctly describe the router configuration that is shown?(Choose three.)An IEEE standard trunking protocol is in use.Interface Fa0/1 has been configured with subinterfaces.The shutdown command has been applied to interface Fa0/1.Interface Fa0/1.3 is mapped to the default management VLAN.The configuration is appropriate for a router-on-a-stick network design.An IP address should be applied to interface Fa0/1 for routing to occur.15RSTP is enabled in a switched network that is active and converged. Which switch port type assumesa discarding state on non-root switches?root portedge portalternate portdesignated port16What provides an authentication mechanism for 802.11-based wireless networks?DSSSOFDMSSIDWPA17W hat is the benefit of the auto-MDIX feature on a Cisco Catalyst switch?dynamically assigns a new management VLAN IDautonegotiates IP address information for initial management connectionsallows the use of straight-through patch cables regardless of connected device typesplaces a port immediately in the forwarding state to reduce the time for the spanning tree toreconverge18Refer to the exhibit. VTP pruning is enabled in the VTP domain that is shown. How will switch ST-1 handle Layer 2 broadcast traffic originating from host A on switch ST-C?It will be dropped.It will be forwarded out port Fa0/5 only.It will be forwarded out ports Fa0/5 and Fa0/10.It will be forwarded out ports Fa0/5, Fa0/10, and Fa0/15.19Refer to the exhibit. The network administrator wants to allow both SSH and Telnet connections to Switch1. However, the SSH connections fail. What is the most likely cause of this problem?The RSA key has been removed.SSH has been configured on the wrong line.The transport input command is applied incorrectly.The domain name has been configured in the wrong configuration mode.20Refer to the exhibit. The devices in the network are operational and configured as indicated in the exhibit. However, hosts B and D cannot ping each other. What is the most likely cause of this problem?The link between the switches is up but not trunked.The Fa0/11 interface of Switch1 is not configured as a trunk.Hosts B and D are configured with IP addresses from different subnets.VLAN 20 and VLAN 30 are not allowed on the trunk between the switches.21Refer to the exhibit. Hosts A and B, connected to hub HB1, attempt to transmit a frame at the same time but a collision occurs. Which hosts will receive the collision jamming signal?only hosts A and Bonly hosts A, B, and Conly hosts A, B, C, and Donly hosts A, B, C, and E22 A network administrator implements inter-VLAN routing by configuring subinterfaces on a router.What is one important fact that must be considered?The physical interface must have an IP address configured.The subinterface numbers must match the VLAN ID number.The no shutdown command must be issued on each subinterface.The IP address of each router subinterface must be used as the default gateway for hosts on the corresponding VLAN.23W hat is the purpose of VLAN trunking?It improves network performance by reducing broadcast traffic.It selects the best path to transmit data in a switched network.It carries the traffic of multiple VLANs through a single link.It avoids spanning tree loops in a switched network.24Which parameter is used to uniquely identify one wireless network from another?SSIDOFDMWEPDSSS25W hich layers should support QoS in a hierarchical network?only the distribution and core layersonly the access and distribution layersthe access, distribution, and core layers26Refer to the exhibit. What does "FORWARDING" mean in the command output shown?The switch is sending and receiving data frames.The switch is receiving BPDUs, but not sending data frames.The switch is participating in an election process by forwarding the BPDUs it receives.The switch is receiving BPDUs and populating the MAC address table, but not sending data.27Refer to the exhibit. A network administrator is configuring RT1 for inter-VLAN routing. The switch is configured correctly and is functional. Host1, Host2, and Host3 cannot communicate with each other.Based on the router configuration, what is causing the problem?Interface Fa0/0 is missing IP address configuration information.IP addresses on the subinterfaces are incorrectly matched to the VLANs.Each subinterface of Fa0/0 needs separate no shutdown commands.Routers do not support 892.1Q encapsulation on subinterfaces.28Which switch forwarding method should be used on a network that employs frame classification based on an assigned Quality of Service (QoS) value?cut-throughfast-forwardfragment-freestore-and-forward29Refer to the exhibit. A network administrator has segmented the network into two VLANs. The connected hosts can only access resources in their own VLAN. What is the most scalable and cost effective solution to allow inter-VLAN communication in this network?Replace S1 with a router that has one FastEthernet interface for each PC.Add a second switch and divide the PCs so that each VLAN is connected to its own switch.Configure a router with two subinterfaces on one of its FastEthernet ports and connect it to S1 using a trunk link.Connect a router to a port on S1 and assign the IP address of VLAN1 to the connecting router interface.30Refer to the exhibit. A network administrator issues the show interfaces fastEthernet 0/8switchport command to check the status of the port. What can be concluded from the output?Port Fa0/8 is configured as a trunk with 802.1q encapsulation.Port Fa0/8 is configured as a trunk in VLAN 1.Port Fa0/8 is configured in access mode and associated with VLAN 1.31What will be the effect of the command S1# copy system:running-configtftp://172.16.2.155/tokyo-config?The IOS will be copied to the TFTP server.The configuration file named tokyo-config will overwrite the startup configuration file on S1.The running configuration file on S1 will be saved via TFTP to a file named tokyo-config.The contents of NVRAM on S1 will become the startup configuration file on the tokyo switch.32W hich three statements are correct concerning the default configuration of a new switch? (Choose three.)It is configured in VTP server mode.STP is automatically enabled.The first VTY line is automatically configured to allow remote connections.VLAN1 is configured with a management IP address.All switch ports are assigned to VLAN1.The enable password is configured as cisco.33Refer to the exhibit. What would happen if the network administrator moved the network cable of Host A from interface Fa0/1 to Fa0/3 on switch SW1?Host A remains a member of VLAN 10, because the router is routing traffic between VLANs.Host A is no longer a member of VLAN 10, because port Fa0/3 has been manually assigned to VLAN 30.Host A remains a member of VLAN 10, because the switch provides dynamic VLAN assignment for the port.Host A maintains connectivity to all members of VLAN 10, because it is connected to the same physical network.Host A is no longer a member of VLAN 10, but because port Fa0/3 was unused, it is now amember of VLAN 1.34Refer to the exhibit. Switches S2 and S3 are properly connected using an ethernet cable. A network administrator has configured both switches with VTP, but S3 is unable to propagate VLANs to S2.What could be the reason for this?The VTP configuration revision is different on both switches.The VTP domains are different on both switches.VTP pruning is disabled.VTP v2 is disabled.35Refer to the exhibit. Users A and B are reporting intermittent connectivity problems. Pre-installation surveys showed strong signal strength from the AP locations to the client locations. Outside electricalIncrease the distance between the clients.Change the channel on AP-B to 6 or 11.Place AP-A and AP-B on the same wireless channel.36I n which mode is a VTP switch operating if it does not allow for the creation of local VLANs but it does accept VLAN updates from other switches in the same domain?clientrootservertransparent37Refer to the exhibit. The Layer 2 switching design that is shown has been implemented in a campus environment that is using Spanning Tree Protocol. All inter-switch links that are shown are trunks.Whenever an inter-switch link fails, the network takes nearly a minute to completely converge. How can the convergence time be reduced?Increase the capacity of the distribution and core trunk links to 10 Gb/s.Use Layer 3 switching on the core switch.Implement Rapid Spanning Tree Protocol.38Refer to the exhibit. Router R1 is properly configured for router on a stick inter-VLAN routing, but PC1 is unable to ping PC2. What needs to be done to resolve the problem?Rename VLAN1.Connect one more port of S1 to R1.Configure the Fa0/1 port of S1 as a trunk port.Move the Fa0/0 interface of R1 to another VLAN.39What is a result of improperly implementing a network with redundancy at Layer 2?an increase of unicast and multicast errors at Layer 3a decrease in the amount of broadcast trafficend device malfunction because of broadcast storms40W hy is it important that the network administrator consider the spanning-tree network diameter when choosing the root bridge?The network diameter limitation is 9.BPDUs may be discarded because of expiring timers.The cabling distance between the switches is 100 meters.The network diameter must be set to the number of meters of the cable between the root bridge and its farthest connected switch.41Refer to the exhibit. A network administrator needs to add IP phones to the network. To whichdevices should the IP phones connect?AS1 and AS2DS1 and DS2DS1, DS2, and CS1AS1, AS2, DS1, and DS242Which device or devices should have the Spanning Tree Protocol enabled to prevent host traffic from creating a broadcast storm?Core_S1Access_S2 and Access_S3Core_S1, Access_S2, and Access_S3Core_S1, Access_S2, Access_S3, and R143Refer to the exhibit. All edge ports are configured with the spanning-tree portfast command. Host1 is recently connected to port Fa0/1 on switch SW1 . Which statement is true about the status of port Fa0/1?The port will transition into blocking state.The port will transition immediately into forwarding state.The port will transition into blocking state and then immediately into forwarding state.The port will transition into blocking state and immediately transition through the listening and learning states.44A network administrator enables sticky learning on all access mode interfaces of a Catalyst switch, saves the configuration, then connects hosts to the switch. After the switch operates for several days, the administrator reboots the switch without saving the running configuration. What is the result?All previously learned MAC addresses are lost.The switch reverts to non-sticky dynamic learning.Connected hosts are no longer able to communicate with the switch.Previously learned sticky addresses are retained in the switch configuration.45The network administrator wants to configure a switch to pass VLAN update information to other switches in the domain but not update its own local VLAN database. Which two steps should the administrator perform to achieve this? (Choose two.)Reset the VTP counters.Configure VTP version 1 on the switch.Configure the VTP mode of the switch to transparent.Verify that the switch has a higher configuration revision number.Configure the switch with the same VTP domain name as other switches in the network.46Which statement regarding the service password-encryption command is true?The service password-encryption command is entered at the privileged EXEC mode prompt.The service password-encryption command encrypts only passwords for the console and VTY ports.The service password-encryption command encrypts all previously unencrypted passwords in the running configuration.To see the passwords encrypted by the service password-encryption command, enter the no service password-encryption command.47Refer to the exhibit. The network consists of four hubs and a switch. The hosts connected to each hub are assigned addresses in the respective VLAN as shown. PC1 on VLAN 1 becomes infected with a virus and initiates a continuous IP broadcast. Which hubs will receive the broadcasts?Hub AHubs A and BHubs A and CHubs A, B, C, and D48 A wireless LAN access point will convert traffic between which two frame encapsulation types?802.1 and 802.11802.3 and 802.11802.3 and 802.16802.5 and 802.1649I n the implementation of PVST+ in a specific VLAN where all switches have default spanning tree priorities, which spanning-tree command setting could be assigned to force one of the Catalyst switches to become and remain the root bridge?root primarypriority 8192priority 2048spanning-tree mode rapid pvst50Refer to the exhibit. The teacher host is connected to port Fa0/7 on switch STW. A student hasdecided to share access to the Internet by attaching a hub and laptop to STW as shown. What will be the result of the student making this connection?The Fa0/7 port of STW will be shutdown.The student will gain full access to the Internet.Both the teacher and student will be able to receive data but only the teacher will be able to send.The frames from the laptop will be dropped, but the teacher host will maintain connectivity with the network.51Refer to the exhibit. Switch SW2 was tested in a lab environment and then inserted into a production network without reloading its configuration. After the trunk link between SW1 and SW2 was brought up, all users lost connectivity to the network. What could be the source of the problem?All the VLANs were pruned from the trunk port between SW1 and SW2.SW1 and SW2 cannot be both set as VTP servers in the same VTP domain.VTP configuration revision number of SW2 was higher than the configuration revision number of SW1.The additional VLANs from SW2 created more VLANs than the VLAN database of SW1 could contain.。
CCNA 1 Final Exam Answer v5
It aborts the current command and returns to configuration mode. It exits configuration mode and returns to user EXEC mode. It moves the cursor to the beginning of the next line. It completes the remainder of a partially typed word in a command.
2. A host is accessing a Web server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.)
CCNA 1 Final Exam Answer 003 (v5.02, 2015)
My Switch(config)#? Switch(config)#? MySwitch(config)#? My(config)#? Switch#
11. Refer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator uses Telnet to connect to the switch, which password is needed to access user EXEC mode?
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1. Which address is used by an IPv6 EIGRP router as thesource for hello messages?o the 32-bit router IDo the IPv6 global unicast address that is configured on the interfaceo the all-EIGRP-routers multicast addresso the interface IPv6 link-local address2. Which two statements are correct about EIGRPacknowledgment packets? (Choose two.)o The packets are sent in response to hello packets.o The packets are used to discover neighbors that are connected on an interface.o The packets are sent as unicast.o The packets require confirmation.o The packets are unreliable.3. When are EIGRP update packets sent?o only when necessaryo when learned routes age outo every 5 seconds via multicasto every 30 seconds via broadcast4. Refer to the exhibit. Which two conclusions can be derivedfrom the output? (Choose two.)o There is one feasible successor to network 192.168.1.8/30.o The network 192.168.10.8/30 can be reached through 192.168.11.1.o The reported distance to network 192.168.1.0/24 is 41024256.o The neighbor 172.16.6.1 meets the feasibility condition to reach the 192.168.1.0/24 network.o Router R1 has two successors to the 172.16.3.0/24 network.5. Refer to the exhibit. Which route or routes will beadvertised to the router ISP if autosummarization isenabled?o10.0.0.0/8o10.1.0.0/16o10.1.0.0/28o10.1.1.0/24 10.1.2.0/24 10.1.3.0/24 10.1.4.0/286. Refer to the exhibit. What can be concluded about network192.168.1.0 in the R2 routing table?o This network has been learned from an internal router within the same area.o This network was learned through summary LSAs from an ABR.o This network is directly connected to the interface GigabitEthernet0/0.o This network should be used to forward traffic toward external networks.7. Refer to the exhibit. A company has migrated from singlearea OSPF to multiarea. However, none of the users fromnetwork 192.168.1.0/24 in the new area can be reached by anyone in the Branch1 office. From the output in theexhibit, what is the problem?o There are no interarea routes in the routing table for network 192.168.1.0.o The OSPF routing process is inactive.o The link to the new area is down.o The router has not established any adjacencies with other OSPF routers.8. When does an OSPF router become an ABR?o when the router has interfaces in different areaso when the router is configured as an ABR by the network administratoro when the router has the highest router IDo when the router has an OSPF priority of 09. What is a difference between the Cisco IOS 12 and IOS 15versions?o The IOS 12 version has commands that are not available in the 15 version.o The IOS version 15 license key is unique to each device, whereas the IOS version 12 license key is not device specific.o Every Cisco ISR G2 platform router includes a universal image in the IOS12 versions, but not the IOS 15 versions.o IOS version 12.4(20)T1 is a mainline release, whereas IOS version15.1(1)T1 is a new feature release.10. A network administrator issues the command R1(config)#license boot module c1900 technology-package securityk9 on a router. What is the effect of this command?o The IOS will prompt the user to reboot the router.o The features in the Security package are available immediately.o The IOS will prompt the user to provide a UDI in order to activate the license.o The Evaluation Right-To-Use license for the Security technology package is activated.11. A network administrator is troubleshooting slowperformance in a Layer 2 switched network. Uponexamining the IP header, the administrator notices that the TTL value is not decreasing. Why is the TTL value notdecreasing?o This is the normal behavior for a Layer 2 network.o The MAC address table is full.o The VLAN database is corrupt.o The inbound interface is set for half duplex.12. A network administrator enters the spanning-tree portfastbpduguard default command. What is the result of thiscommand being issued on a Cisco switch?o Any switch port will be error-disabled if it receives a BPDU.o Any trunk ports will be allowed to connect to the network immediately, rather than waiting to converge.o Any switch port that has been configured with PortFast will be error-disabled if it receives a BPDU.o Any switch port that receives a BPDU will ignore the BPDU message.13. An STP instance has failed and frames are flooding thenetwork. What action should be taken by the networkadministrator?o A response from the network administrator is not required because the TTL field will eventually stop the frames from flooding the network.o Spanning tree should be disabled for that STP instance until the problem is located.o Broadcast traffic should be investigated and eliminated from the network.o Redundant links should be physically removed until the STP instance is repaired.14. A network engineer is configuring a LAN with a redundantfirst hop to make better use of the available networkresources. Which protocol should the engineerimplement?o FHRPo GLBPo HSRPo VRRP15. Which mode configuration setting would allow formationof an EtherChannel link between switches SW1 and SW2 without sending negotiation traffic?o SW1: on SW2: ono SW1: desirable SW2: desirableo SW1: auto SW2: auto trunking enabled on both switcheso SW1: auto SW2: auto PortFast enabled on both switcheso SW1: passive SW2: active16. What are two requirements to be able to configure anEtherChannel between two switches? (Choose two.)o The interfaces that are involved need to be contiguous on the switch.o All the interfaces need to work at the same speed.o All the interfaces need to be working in the same duplex mode.o All interfaces need to be assigned to different VLANs.o Different allowed ranges of VLANs must exist on each end.17. When should EIGRP automatic summarization be turnedoff?o when a router has not discovered a neighbor within three minuteso when a router has more than three active interfaceso when a network contains discontiguous network addresseso when a router has less than five active interfaceso when a network addressing scheme uses VLSM18. What two conditions have to be met in order to form acluster that includes 5 access points? (Choose two.)o Clustering mode must be enabled on the APs.o At least two controllers are needed to form the cluster.o The APs have to be connected on the same network segment.o The APs must all be configured to use different radio modes.o The APs must use different cluster names.19. A network engineer is troubleshooting a newly deployedwireless network that is using the latest 802.11 standards.When users access high bandwidth services such asstreaming video, the wireless network performance ispoor. To improve performance the network engineerdecides to configure a 5 Ghz frequency band SSID and train users to use that SSID for streaming media services.Why might this solution improve the wireless networkperformance for that type of service?o The 5 GHz band has a greater range and is therefore likely to be interference-free.o Requiring the users to switch to the 5 GHz band for streaming media is inconvenient and will result in fewer users accessing these services.o The 5 GHz band has more channels and is less crowded than the 2.4 GHz band, which makes it more suited to streaming multimedia.o The only users that can switch to the 5 GHz band will be those with the latest wireless NICs, which will reduce usage.20. What method of wireless authentication is dependent ona RADIUS authentication server?o WEPo WPA Personalo WPA2 Personalo WPA2 Enterprise21. Refer to the exhibit. What two pieces of information couldbe determined by a network administrator from thisoutput? (Choose two.)o R1 is participating in multiarea OSPF.o The OSPF process number that is being used is 0.o Interface Fa0/1 is not participating in the OSPF process.o R1 is the distribution point for the routers that are attached to the 10.0.0.4 network.o The metric that will be installed in the routing table for the 10.0.0.0 route will be 65 (64+1).22. A remote classroom can successfully access video-intensive streaming lectures via wired computers.However, when an 802.11n wireless access point isinstalled and used with 25 wireless laptops to access the same lectures, poor audio and video quality isexperienced. Which wireless solution would improve the performance for the laptops?o Decrease the power of the wireless transmitter.o Add another access point.o Upgrade the access point to one that can route.o Adjust the wireless NICs in the laptops to operate at 10GHz to be compatible with 802.11n.23. What are the two methods that are used by a wireless NICto discover an AP? (Choose two.)o sending an ARP requesto delivering a broadcast frameo transmitting a probe requesto initiating a three-way handshakeo receiving a broadcast beacon frame24. When will a router that is running EIGRP put a destinationnetwork in the active state?o when the EIGRP domain is convergedo when there is outgoing traffic toward the destination networko when there is an EIGRP message from the successor of the destination networko when the connection to the successor of the destination network fails and there is no feasible successor available25. Which wireless network topology is being configured by atechnician who is installing a keyboard, a mouse, andheadphones, each of which uses Bluetooth?o ad hoc modeo hotspoto infrastructure modeo mixed mode26. What is a wireless modulation technique used by 802.11WLAN standards that can implement MIMO?o BSSo DSSSo FHSSo OFDM27. Refer to the exhibit. A network administrator issues theshow ipv6 eigrp neighbors command. Which conclusion can be drawn based on the output?o The link-local addresses of neighbor routers interfaces are configured manually.o R1 has two neighbors. They connect to R1 through their S0/0/0 and S0/0/1 interfaces.o The neighbor with the link-local address FE80::5 is the first EIGRP neighbor that is learned by R1.o If R1 does not receive a hello packet from the neighbor with the link-local address FE80::5 in 2 seconds, it will declare the neighbor router is down.28. A network engineer is troubleshooting a single-areaOSPFv3 implementation across routers R1, R2, and R3.During the verification of the implementation, it is noted that the routing tables on R1 and R2 do not include theentry for a remote LAN on R3. Examination of R3 shows the following:1.that all interfaces have correct addressing2.that the routing process has been globally configured3.that correct router adjacencies have formedWhat additional action taken on R3 could solve the problem?o Enable the OSPFv3 routing process on the interface connected to the remote LAN.o Use the network command to configure the LAN network under the global routing process.o Force DR/BDR elections to occur where required.o Restart the OPSFv3 routing process.29. A network administrator in a branch office is configuringEIGRP authentication between the branch office router and the headquarters office router. Which security credential is needed for the authentication process?o a randomly generated key with the crypto key generate rsa commando the username and password configured on the headquarters office router o the hostname of the headquarters office router and a common passwordo a common key configured with the key-string command inside a key chain30. For troubleshooting missing EIGRP routes on a router,what three types of information can be collected using the show ip protocols command? (Choose three.)o any interfaces that are enabled for EIGRP authenticationo any interfaces on the router that are configured as passiveo the IP addresses that are configured on adjacent routerso any ACLs that are affecting the EIGRP routing processo networks that are unadvertised by the EIGRP routing protocolo the local interface that is used to establish an adjacency with EIGRP neighbors31. Refer to the exhibit. A network technician istroubleshooting missing OSPFv3 routes on a router. What is the cause of the problem based on the commando There is a problem with the OSPFv3 adjacency between the local router and the router that is using the neighbor ID 2.2.2.2.o The local router has formed complete neighbor adjacencies, but must be in a 2WAY state for the router databases to be fully synchronized.o The dead time must be higher than 30 for all routers to form neighbor adjacencies.o The neighbor IDs are incorrect. The interfaces must use only IPv6 addresses to ensure fully synchronized routing databases.32. A network engineer is implementing security on allcompany routers. Which two commands must be issued to force authentication via the password 1C34dE for allOSPF-enabled interfaces in the backbone area of thecompany network? (Choose two.)o ip ospf message-digest-key 1 md5 1C34dEo area 1 authentication message-digesto username OSPF password 1C34dEo enable password 1C34dEo area 0 authentication message-digest33. Which port role is assigned to the switch port that has thelowest cost to reach the root bridge?o root porto non-designated porto designated porto disabled port34. Refer to the exhibit. A network administrator is attemptingto upgrade the IOS system image on a Cisco 2901 router.After the new image has been downloaded and copied to the TFTP server, what command should be issued on the router before the IOS system image is upgraded on theo dir flash:o ping 10.10.10.1o copy tftp: flash0:o ping 10.10.10.235. A set of switches is being connected in a LAN topology.Which STP bridge priority value will make it least likely for the switch to be selected as the root?o4096o32768o61440o6553536. What are two features of OSPF interarea routesummarization? (Choose two.)o ASBRs perform all OSPF summarization.o Routes within an area are summarized by the ABR.o ABRs advertise the summarized routes into the backbone.o Type 3 and type 5 LSAs are used to propagate summarized routes by default.o Route summarization results in high network traffic and router overhead.37. Refer to the exhibit. What are two results of issuing thedisplayed commands on S1, S2, and S3? (Choose two.)o S1 will automatically adjust the priority to be the lowest.o S1 will automatically adjust the priority to be the highest.o S3 can be elected as a secondary bridge.o S2 can become root bridge if S3 fails.o S2 can become root bridge if S1 fails.38. Refer to the exhibit. Which two conclusions can be drawnfrom the output? (Choose two.)o The EtherChannel is down.o The port channel ID is 2.o The port channel is a Layer 3 channel.o The bundle is fully operational.o The load-balancing method used is source port to destination port. 39. Refer to the exhibit. Interface FastEthernet 0/1 on S1 isconnected to Interface FastEthernet 0/1 on S2, andInterface FastEthernet 0/2 on S1 is connected to Interface FastEthernet 0/2 on S2. What are two errors in the presentEtherChannel configurations? (Choose two.)o The trunk mode is not allowed for EtherChannel bundles.o Two auto modes cannot form a bundle.o Desirable mode is not compatible with on mode.o The channel group is inconsistent.o The interface port channel ID should be different in both switches. 40. Which technology is an open protocol standard thatallows switches to automatically bundle physical ports into a single logical link?o Multilink PPPo DTPo LACPo PAgP41. A network administrator has configured an EtherChannelbetween two switches that are connected via four trunk links. If the physical interface for one of the trunk linkschanges to a down state, what happens to theEtherChannel?o The EtherChannel will transition to a down state.o Spanning Tree Protocol will recalculate the remaining trunk links.o The EtherChannel will remain functional.o Spanning Tree Protocol will transition the failed physical interface into forwarding mode.42. Refer to the exhibit. Based on the command outputshown, what is the status of the EtherChannel?o The EtherChannel is dynamic and is using ports Fa0/10 and Fa0/11 as passive ports.o The EtherChannel is down as evidenced by the protocol field being empty.o The EtherChannel is partially functional as indicated by the P flags for the FastEthernet ports.o The EtherChannel is in use and functional as indicated by the SU and P flags in the command output.43. Refer to the exhibit. If router B is to be configured forEIGRP AS 100, which configuration must be entered?o B(config-router)# network 192.168.10.4 0.0.0.3 B(config-router)# network 192.168.10.8 0.0.0.3o B(config-router)# network 192.168.10.4 0.0.0.3 B(config-router)# network 192.168.10.8 0.0.0.3 B(config-router)#network 192.168.10.1280.0.0.63o B(config-router)# network 192.168.10.4 255.255.255.248 B(config-router)# network 192.168.10.8 255.255.255.248 B(config-router)#network192.168.10.128 255.255.255.192o B(config-router)# network 192.168.10.0 255.255.255.0o B(config-router)# network 192.168.10.4 0.0.0.3 B(config-router)# network 192.168.10.8 0.0.0.3 B(config-router)# network 192.168.10.640.0.0.63 B(config-router)# network 192.168.10.128 0.0.0.63 B(config-router)# network 192.168.10.192 0.0.0.63o B(config-router)# network 192.168.10.0 0.0.0.25544. Refer to the exhibit. When the show ip ospf neighborcommand is given from the R1# prompt, no output isshown. However, when the show ip interface briefcommand is given, all interfaces are showing up and up.What is the most likely problem?o R2 has not brought the S0/0/1 interface up yet.o R1 or R2 does not have a loopback interface that is configured yet.o The ISP has not configured a static route for the ABC Company yet.o R1 or R2 does not have a network statement for the 172.16.100.0 network.o R1 has not sent a default route down to R2 by using the default-information originate command.45. Refer to the exhibit. Which destination MAC address isused when frames are sent from the workstation to thedefault gateway?o MAC address of the forwarding routero MAC addresses of both the forwarding and standby routerso MAC address of the standby routero MAC address of the virtual router46. If a company wants to upgrade a Cisco 2800 router fromIOS 12.4T, what IOS should be recommended for a stable router platform?o12.5To13.1To14.0o15.1M47. What is the purpose of the Cisco PAK?o It is a key for enabling an IOS feature set.o It is a proprietary encryption algorithm.o It is a compression file type used when installing IOS 15 or an IOS upgrade.o It is a way to compress an existing IOS so that a newer IOS version can be co-installed on a router.48. What are two reasons to implement passive interfaces inthe EIGRP configuration of a Cisco router? (Choose two.)o to provide increased network securityo to shut down unused interfaceso to avoid unnecessary update traffico to mitigate attacks coming from the interfaceso to exclude interfaces from load balancing49. Fill in the blank.EIGRP keeps feasible successor routes inthe topology table.50. Fill in the blank.The backbone area interconnects with all other OSPF area types.51. Fill in the blank. Use the acronym.Which encryptionprotocol is used by the WPA2 shared key authentication technique? AES52. Match each OSPF LSA description with its type. (Not alloptions are used.)53. Match the CLI command prompt with the command orresponse entered when backing up Release 15 IOS imageto an IPv6 TFTP server. (Not all options are used.)54. Which characteristic would most influence a networkdesign engineer to select a multilayer switch over a Layer2 switch?o ability to build a routing tableo ability to aggregate multiple ports for maximum data throughputo ability to provide power to directly-attached devices and the switch itself o ability to have multiple forwarding paths through the switched network based on VLAN number(s)55. A network designer is considering whether to implementa switch block on the company network. What is theprimary advantage of deploying a switch block?o A single core router provides all the routing between VLANs.o The failure of a switch block will not impact all end users.o This is a security feature that is available on all new Catalyst switches.o This is network application software that prevents the failure of a singleo network device.56. Which action should be taken when planning forredundancy on a hierarchical network design?o immediately replace a non-functioning module, service or device on a networko continually purchase backup equipment for the networko implement STP portfast between the switches on the networko add alternate physical paths for data to traverse the network57. Which technological factor determines the impact of afailure domain?o the number of layers of the hierarchical networko the number of users on the access layero the role of the malfunctioning deviceo the forwarding rate of the switches used on the access layer58. What are three access layer switch features that areconsidered when designing a network? (Choose three.)o broadcast traffic containmento failover capabilityo forwarding rateo port densityo Power over Etherneto speed of convergence59. What are two requirements when using out-of-bandconfiguration of a Cisco IOS network device? (Choosetwo.)o HTTP access to the deviceo a terminal emulation cliento Telnet or SSH access to the deviceo a direct connection to the console or AUX porto a connection to an operational network interface on the device60. In a large enterprise network, which two functions areperformed by routers at the distribution layer? (Choosetwo.)o connect remote networkso provide Power over Ethernet to deviceso connect users to the networko provide data traffic securityo provide a high-speed network backboneUpdated 05 April 20151. Refer to the exhibit. Which switch will be the root bridgeafter the election process is complete?CCNA3 Final Exam updated 001o S1o S2o S3o S42. Refer to the exhibit. What are the possible port roles forports A, B, C, and D in this RSTP-enabled network?CCNA3 Final Exam updated 002o alternate, root, designated, rooto designated, root, alternate, rooto alternate, designated, root, rooto designated, alternate, root, root3. Refer to the exhibit. A network administrator is configuringPVST+ for the three switches. What will be a result ofentering these commands?CCNA3 Final Exam updated 003o S1 will set the priority value for VLAN 10 to 0.o S2 will set the priority value for VLAN 10 to 24576.o S3 will set the priority value for VLAN 30 to 8192.o S1 will set the priority value for VLAN 20 to 24596.4. A network administrator is analyzing the features that aresupported by different first-hop router redundancyprotocols. Which statement is a feature that is associated with GLBP?o GLBP allows load balancing between routers.o It is nonproprietary.o It uses a virtual router master.o It works together with VRRP.5. A network administrator is analyzing the features that aresupported by different first-hop router redundancyprotocols. Which statement describes a feature that isassociated with HSRP?o HSRP uses active and standby routers.o It uses ICMP messages in order to assign the default gateway to hosts.o It allows load balancing between a group of redundant routers.o HSRP is nonproprietary.6. Which function is provided by EtherChannel?o spreading traffic across multiple physical WAN linkso dividing the bandwidth of a single link into separate time slotso enabling traffic from multiple VLANs to travel over a single Layer 2 linko creating one logical link by using multiple physical links between two LAN switches7. Which two channel group modes would place an interfacein a negotiating state using PAgP? (Choose two.)o ono desirableo activeo autoo passive8. At a local college, students are allowed to connect to thewireless network without using a password. Which mode is the access point using?o networko openo passiveo shared-key9. Which wireless encryption method is the most secure?o WPAo WEPo WPA2 with TKIPo WPA2 with AES10. Users on an IEEE 801.11n network are complaining ofslow speeds. The network administrator checks the APand verifies it is operating properly. What can be done to improve the wireless performance in the network?o Split the wireless traffic between the 802.11n 2.4 GHz band and the 5 GHz band.o Change the authentication method on the AP.o Switch to an 802.11g AP.o Set the AP to mixed mode.11. What are two methods to make the OSPF routing protocolmore secure? (Choose two.)o Use only OSPFv3.o Use MD5 authentication.o Use the enable secret command.o When feasible, create a VPN tunnel between each OSPF neighbor adjacency.o Use the passive-interface command on LAN interfaces that areconnected only to end-user devices.12. Refer to the exhibit. A network technician istroubleshooting missing OSPFv3 routes on a router. What is the cause of the problem based on the commandoutput?CCNA3 Final Exam updated 004o There is a problem with the OSPFv3 adjacency between the local router and the router that is using the neighbor ID 2.2.2.2.o The local router has formed complete neighbor adjacencies, but must be in a 2WAY state for the router databases to be fully synchronized.o The dead time must be higher than 30 for all routers to form neighbor adjacencies.o The neighbor IDs are incorrect. The interfaces must use only IPv6 addresses to ensure fully synchronized routing databases.13. Which type of OSPF LSA represents an external route andis propagated across the entire OSPF domain?o type 1o type 2o type 3o type 4o type 514. An administrator issues the router eigrp 100 command ona router. What is the number 100 used for?o as the autonomous system numbero as the number of neighbors supported by this routero as the length of time this router will wait to hear hello packets from a neighboro as the maximum bandwidth of the fastest interface on the router15. A network administrator wants to verify the default delayvalues for the interfaces on an EIGRP-enabled router.Which command will display these values?o show ip protocolso show running-configo show interfaceso show ip route16. Which two parameters does EIGRP use by default tocalculate the best path? (Choose two.)o delayo MTUo reliabilityo transmit and receive loado bandwidth17. By default, how many equal cost routes to the samedestination can be installed in the routing table of a Cisco router?o 2o4o16o3218. When a Cisco router is configured with fast-switching,how are packets distributed over equal-cost paths?o on a per-packet basiso on a per-interface basiso on a per-path-load basiso on a per-destination basis19. Refer to the exhibit. Router CiscoVille has been partiallyconfigured for EIGRP authentication. What is missing that would allow successful authentication between EIGRPneighbors?。
