使用centos+openssl搭建CA签发证书
openssl 证书流程 -回复

openssl 证书流程-回复关于openssl证书流程的文章,我将一步一步回答以下主题:[1. openssl 的基本概述],[2. 生成私钥和公钥],[3. 创建证书签署请求],[4. 提取证书根公钥],[5. 签署证书请求],[6. 配置和使用证书]。
1. openssl的基本概述:OpenSSL是一个开源的加密工具包,它提供了多种密码学功能,包括用于生成加密密钥、证书操作和协议支持等。
在证书流程中,OpenSSL被用来生成私钥和公钥、创建证书签署请求、签署证书请求以及配置和使用证书。
2. 生成私钥和公钥:生成私钥和公钥是使用openssl创建证书的第一步。
私钥是用于签署和解密数据的关键部分,必须保密保存。
公钥则用于验证签名和加密数据。
在命令行中,可以使用以下openssl命令生成私钥和公钥:openssl genrsa -out private.key 2048openssl rsa -in private.key -pubout -out public.key这将生成一个2048位长度的RSA私钥(private.key)和对应的公钥(public.key)。
3. 创建证书签署请求:证书签署请求(CSR)包含待签署证书的相关信息,如公钥和组织信息。
CSR 需要使用私钥签名,因此保持私钥的机密性非常重要。
使用以下openssl 命令创建一个CSR:openssl req -new -key private.key -out certificate.csr这将使用私钥(private.key)生成一个新的CSR文件(certificate.csr)。
4. 提取证书根公钥:在签署证书请求之前,需要从证书根公钥中提取公钥。
这将用于验证签名和验证证书。
可以使用以下openssl命令从CSR文件中提取证书根公钥:openssl req -in certificate.csr -noout -pubkey -out root.pem这将从CSR文件(certificate.csr)中提取证书根公钥,并将其保存到root.pem文件中。
OpenSSL签名流程
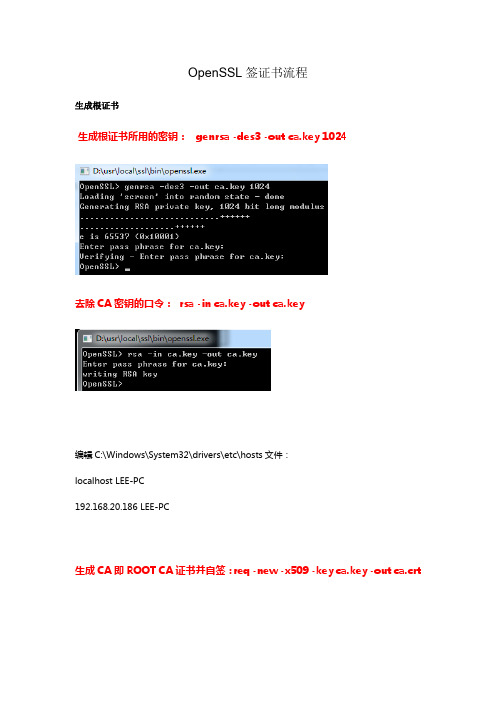
OpenSSL签证书流程生成根证书生成根证书所用的密钥: genrsa -des3 -out ca.key 1024去除CA密钥的口令:rsa -in ca.key -out ca.key编辑C:\Windows\System32\drivers\etc\hosts文件:localhost LEE-PC192.168.20.186 LEE-PC生成CA即ROOT CA证书并自签:req -new -x509 -key ca.key -out ca.crt将“ca.crt”安装到我们的IE的信任域里。
生成Web服务器端证书生成Web服务器端证书密钥:genrsa -des3 -out server.key 1024去除CA密钥的口令:rsa -in server.key -out server.key生成Web服务器端证书的签名请求:req –new –key server.key –out server.csrD:\tools\openssl-1.0.1g\apps\demoCA下,建立“文件夹”newcerts编辑修改f修改:dir = D:\\tools\\openssl-1.0.1g\\apps\\demoCA用Root CA去对Web服务器的证书请求即csr(certificate request)进行签名认证:ca –in server.csr –out server.crt –cert ca.crt –keyfile ca.key提示全部输入y点击生成的server.crt生成Tomcat的SSL证书生成JKS密钥对:keytool -genkey -keystore tcps.jks -alias tcps -keyalg RSA -keysize 1024 -validity 3650 -dname "CN=LEE-PC, OU=TCPS, O=TCPS, L=TJ, S=TJ, C=CN"生成JSK的CSR:keytool -certreq -alias tcps -sigalg "MD5withRSA" -file tcps.csr -keystore tcps.jks使用openssl结合ca.crt与ca.key为jsk的csr来签名认证并产生jks格式的crt:openssl x509 -req -in tcps.csr -out tcps.crt -CA ca.crt -CAkey ca.key -days 3650 -CAcreateserial -sha1 -trustout -CA ca.crt -CAkey ca.key -days 3650 -CAserial ca.srl -sha1 -trustout生成符合x509格式的jks文件将Root CA导入jks信任域:keytool -import -alias rootca -trustcacerts -file ca.crt -keystore tcps.jks补链,补信任链:keytool -import -alias tcps -file tcps.crt -keystore tcps.jks。
使用centos+openssl搭建CA签发证书

一、安装centos系统,如下图:二、使用openssl建立CA并颁发证书,使用root用户登录centos系统[root@localhost ~]# mkdir certs[root@localhost ~]# cd certs[root@localhost certs]# /etc/pki/tls/misc/CA -newcaCA certificate filename (or enter to create)Making CA certificate ...Generating a 2048 bit RSA private key ....................................................................................................................................................+++ .+++writing new private key to '/etc/pki/CA/private/./cakey.pem'Enter PEM pass phrase:Verifying - Enter PEM pass phrase:-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:beijingLocality Name (eg, city) [Default City]:beijingOrganization Name (eg, company) [Default Company Ltd]:opzoonOrganizational Unit Name (eg, section) []:opzoonCommon Name (eg, your name or your server's hostname) []:Email Address []:tac@Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:111111An optional company name []:opzoonUsing configuration from /etc/pki/tls/fEnter pass phrase for /etc/pki/CA/private/./cakey.pem:Check that the request matches the signatureSignature okCertificate Details:Serial Number:ec:01:11:fd:2f:3f:25:c1ValidityNot Before: Feb 1 21:21:43 2012 GMTNot After : Jan 31 21:21:43 2015 GMTSubject:countryName = CNstateOrProvinceName = beijingorganizationName = opzoonorganizationalUnitName = opzooncommonName = emailAddress = tac@X509v3 extensions:X509v3 Subject Key Identifier:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32X509v3 Authority Key Identifier:keyid:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32X509v3 Basic Constraints:CA:TRUECertificate is to be certified until Jan 31 21:21:43 2015 GMT (1095 days)Write out database with 1 new entriesData Base Updated[root@localhost certs]#[root@localhost certs]# cd /etc/pki/CA/[root@localhost CA]# openssl x509 -in cacert.pem -days 3650 -out cacert.pem -signkey ./private/cakey.pemGetting Private keyEnter pass phrase for ./private/cakey.pem:[root@localhost CA]#[root@localhost CA]# cd /root/certs/[root@localhost certs]# /etc/pki/tls/misc/CA -newreqGenerating a 2048 bit RSA private key ....................................................+++.............+++writing new private key to 'newkey.pem'Enter PEM pass phrase:Verifying - Enter PEM pass phrase:-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:fujianLocality Name (eg, city) [Default City]:fuzhouOrganization Name (eg, company) [Default Company Ltd]:opzoon Organizational Unit Name (eg, section) []:opzoonCommon Name (eg, your name or your server's hostname) []: Email Address []:fujian@Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:fuzhouAn optional company name []:opzoonRequest is in newreq.pem, private key is in newkey.pem[root@localhost certs]#[root@localhost certs]# /etc/pki/tls/misc/CA -signUsing configuration from /etc/pki/tls/fEnter pass phrase for /etc/pki/CA/private/cakey.pem:Check that the request matches the signatureSignature okCertificate Details:Serial Number:ec:01:11:fd:2f:3f:25:c2ValidityNot Before: Feb 1 21:45:55 2012 GMTNot After : Jan 31 21:45:55 2013 GMTSubject:countryName = CNstateOrProvinceName = fujianlocalityName = fuzhouorganizationName = opzoonorganizationalUnitName = opzooncommonName = emailAddress = fujian@X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:32:5A:E6:00:EC:A5:88:C5:AB:73:17:77:F1:D3:08:A8:FE:2D:B3:EE X509v3 Authority Key Identifier:keyid:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32Certificate is to be certified until Jan 31 21:45:55 2013 GMT (365 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base UpdatedCertificate:Data:Version: 3 (0x2)Serial Number:ec:01:11:fd:2f:3f:25:c2Signature Algorithm: sha1WithRSAEncryptionIssuer: C=CN, ST=beijing, O=opzoon, OU=opzoon, CN=/emailAddress=tac@ValidityNot Before: Feb 1 21:45:55 2012 GMTNot After : Jan 31 21:45:55 2013 GMTSubject: C=CN, ST=fujian, L=fuzhou, O=opzoon, OU=opzoon, CN=/emailAddress=fujian@Subject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)Modulus:00:d8:29:e0:c8:fe:a7:fa:44:b0:1a:2b:72:f5:66:1c:48:da:e8:7c:33:28:b0:7d:20:df:b5:24:1e:99:51:78:aa:6e:87:cd:0d:e0:6e:ea:cd:52:30:1f:87:67:98:1a:8a:37:f4:16:ad:22:60:05:18:5e:16:21:b1:48:31:29:7b:6d:ae:58:a1:5c:07:04:37:72:7b:41:37:89:63:ec:af:35:9a:06:47:3f:2c:c6:53:db:68:22:63:ad:85:a0:21:cc:0b:f3:05:a5:1d:26:07:c5:ec:1a:e3:06:88:18:52:e7:65:4a:1a:9d:c1:1e:cb:f6:db:f5:3f:0f:37:01:8f:8c:05:c7:bf:8f:eb:d2:32:71:ae:70:10:d7:ef:52:86:37:d2:6d:a9:05:24:91:c1:b5:57:38:0e:83:8d:90:fb:16:9f:2c:a6:bc:d1:2e:ef:3e:f7:50:b3:54:cf:d9:98:ef:a2:12:ad:ba:c8:4e:ce:b6:ce:91:2d:8a:63:cd:e3:6e:8d:f0:72:b1:67:90:36:f1:e9:06:9f:45:73:08:2a:4a:4d:a3:66:c5:00:59:fd:81:2e:57:da:8c:8d:c9:22:b1:f3:8d:77:0b:a2:e8:8f:54:2d:bc:8f:58:b3:3c:2d:4b:1a:10:fa:3e:43:8b:20:3f:e0:24:fc:23:c0:2d:5dExponent: 65537 (0x10001)X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:32:5A:E6:00:EC:A5:88:C5:AB:73:17:77:F1:D3:08:A8:FE:2D:B3:EE X509v3 Authority Key Identifier:keyid:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32Signature Algorithm: sha1WithRSAEncryptiona0:e3:bf:1e:3b:88:e0:86:15:ed:7b:17:80:88:c9:2f:c2:ce:ba:f4:c9:96:81:07:9e:42:51:ed:a8:47:0b:3a:c5:01:6b:1d:2d:dc:6d:8a:8a:57:bc:c9:7a:a7:02:e3:35:eb:79:f4:f7:6f:6b:fd:11:49:d8:4d:10:d8:bc:7c:31:7a:7d:0f:c9:92:2e:d6:01:90:11:2b:96:f3:11:d9:ad:af:97:a5:53:c9:f2:cd:58:9b:65:cd:52:d8:80:88:dc:c5:c3:5a:09:c5:87:46:81:57:e0:af:fe:16:9a:1c:50:a6:b3:ef:2a:ef:ab:ff:ec:a9:b3:42:e6:ec:c6:a5:70:43:bc:56:27:aa:e9:76:5b:02:84:2b:ea:96:e4:92:4f:4e:90:cb:94:05:d8:d2:ca:b3:2d:91:4f:ee:a1:a3:4a:70:91:cf:e4:1f:45:72:39:ca:f1:25:80:1a:4c:8a:ce:ec:bc:dd:61:57:75:ff:06:84:16:5f:f1:03:9a:9e:56:14:18:a8:95:14:2b:53:83:65:55:93:7c:59:0e:53:e0:c7:bd:99:2c:36:b7:57:f3:53:c8:e2:86:80:30:6f:31:5d:66:cf:19:91:68:9d:50:5c:20:dc:8b:e6:61:9d:0c:56:a9:c7:3f:6f:13:26:06:0e:b9:51:d0:26:a4:ee-----BEGIN CERTIFICATE-----MIIEAjCCAuqgAwIBAgIJAOwBEf0vPyXCMA0GCSqGSIb3DQEBBQUAMHgxCzAJBgNV BAYTAkNOMRAwDgYDVQQIDAdiZWlqaW5nMQ8wDQYDVQQKDAZvcHpvb24xDzANBgNV BAsMBm9wem9vbjEWMBQGA1UEAwwNb3B6b29uLmNvbS5jbjEdMBsGCSqGSIb3DQEJ ARYOdGFjQG9wem9vbi5jb20wHhcNMTIwMjAxMjE0NTU1WhcNMTMwMTMxMjE0NTU1 WjCBizELMAkGA1UEBhMCQ04xDzANBgNVBAgMBmZ1amlhbjEPMA0GA1UEBwwGZnV6 aG91MQ8wDQYDVQQKDAZvcHpvb24xDzANBgNVBAsMBm9wem9vbjEWMBQGA1UEAwwN b3B6b29uLmNvbS5jbjEgMB4GCSqGSIb3DQEJARYRZnVqaWFuQG9wem9vbi5jb20w ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDYKeDI/qf6RLAaK3L1ZhxI2uh8MyiwfSDftSQemVF4qm6HzQ3gburNUjAfh2eYGoo39BatImAFGF4WIbFIMSl7ba5YoVwHBDdye0E3iWPsrzWaBkc/LMZT22giY62FoCHMC/MFpR0mB8XsGuMGiBhS52VKGp3BHsv22/U/DzcBj4wFx7+P69Iyca5wENfvUoY30m2pBSSRwbVXOA6DjZD7Fp8sprzRLu8+91CzVM/ZmO+iEq26yE7Ots6RLYpjzeNujfBysWeQNvHpBp9FcwgqSk2jZsUAWf2BLlfajI3JIrHzjXcLouiPVC28j1izPC1LGhD6PkOLID/gJPwjwC1d AgMBAAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2Vu ZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBQyWuYA7KWIxatzF3fx0wio/i2z7jAfBgNVHSMEGDAWgBTivFEbLh50r06TDW7UrOUwNbRQMjANBgkqhkiG9w0BAQUF AAOCAQEAoOO/HjuI4IYV7XsXgIjJL8LOuvTJloEHnkJR7ahHCzrFAWsdLdxtiopXvMl6pwLjNet59Pdva/0RSdhNENi8fDF6fQ/Jki7WAZARK5bzEdmtr5elU8nyzVibZc1S2ICI3MXDWgnFh0aBV+Cv/haaHFCms+8q76v/7KmzQubsxqVwQ7xWJ6rpdlsC hCvqluSST06Qy5QF2NLKsy2RT+6ho0pwkc/kH0VyOcrxJYAaTIrO7LzdYVd1/waEFl/xA5qeVhQYqJUUK1ODZVWTfFkOU+DHvZksNrdX81PI4oaAMG8xXWbPGZFonVBcINyL5mGdDFapxz9vEyYGDrlR0Cak7g==-----END CERTIFICATE-----Signed certificate is in newcert.pem[root@localhost certs]# lsnewcert.pemnewkey.pemnewreq.pem到此CA的建立和证书的制作已经完成,其中newcert.pem为证书文件,newkey.pem为证书密钥文件,/etc/pki/CA/目录下的cacert.pem为CA证书。
使用OpenSSL建立根CA及自签名证书制作过程

使用OpenSSL建立根CA及自签名证书制作过程2009-12-24 11:35:32| 分类:openssl |字号订阅Openssl版本:0.9.8 版本,可从处下载。
1.先建立如下目录结构:$home/testca # testca 是待建CA的主目录├─newcerts/ # newcerts子目录将存放CA签发过的数组证书(备份目录)├─private/ # private目录用来存放CA私钥└─conf/ # conf目录用来存放简化openssl命令行参数用的配置文件此外使用命令echo "01" > serialtouch index.txt在ca根目录下创建文件serial (用来存放下一个证书的序列号) 和indext.txt (证书信息数据库文件)。
1.生成CA的私钥和自签名证书 (根证书)创建配置文件:vi "$HOME/testca/conf/gentestca.conf"文件内容如下:####################################[ req ]default_keyfile = /home/cx/testCA/private/cakey.pemdefault_md = md5prompt = nodistinguished_name = ca_distinguished_namex509_extensions = ca_extensions[ ca_distinguished_name ]organizationName = ssorganizationalUnitName = sstccommonName = sstcCAemailAddress = GChen2@ #自己的邮件地址[ ca_extensions ]basicConstraints = CA:true########################################然后执行命令如下:cd "$HOME/testca"openssl req -x509 -newkey rsa:2048 -out cacert.pem -outform PEM -days 2190 -config "$HOME/testca/conf/gentestca.conf"执行过程中需要输入CA私钥的保护密码,假设我们输入密码: 888888可以用如下命令查看一下CA自己证书的内容openssl x509 -in cacert.pem -text –noout创建一个配置文件,以便后续CA日常操作中使用vi "$HOME/testca/conf/testca.conf"文件内容如下:########################################[ ca ]default_ca = testca # The default ca section[ testca ]dir = /home/cx/testCA # top dirdatabase = $dir/index.txt # index file.new_certs_dir = $dir/newcerts # new certs dircertificate = $dir/cacert.pem # The CA certserial = $dir/serial # serial no fileprivate_key = $dir/private/cakey.pem # CA private keyRANDFILE = $dir/private/.rand # random number filedefault_days = 365 # how long to certify fordefault_crl_days= 30 # how long before next CRLdefault_md = md5 # message digest method to useunique_subject = no # Set to 'no' to allow creation of# several ctificates with same subject.Policy = policy_any # default policy[ policy_any ]countryName = optionalstateOrProvinceName = optionallocalityName = optionalorganizationName = optionalorganizationalUnitName = optionalcommonName = suppliedemailAddress = optional########################################1.自己生成公钥密钥,并用测试CA签发数字证书我们在平时测试时,可以自己用openssl为服务器或用户生成公钥密钥,并用上面创建的CA签发对应私钥(密钥)的数字证书。
openssl,CA证书生成命令集合

多级证书平时我们自己签发CA证书再签发服务器证书的场景其实都非常简单。
浏览器把自签CA导入后,就可以信任由这个CA直接签发的服务器证书。
但是实际上网站使用的证书肯定都不是由根CA直接签发的,比如淘宝登陆服务器使用的证书。
我之前是自己写了脚本由自签CA直接签发服务器证书,为了真清楚的理解一下证书链的作用就直接使用openssl先签发2层的子CA,再由子CA去签发服务器证书。
手动签发证书的脚本如下:生成自签CA# cat makerootca.sh#!/bin/bashDIR=/root/ssl.test2mkdir -p $DIR/demoCA/{private,newcerts}touch $DIR/demoCA/index.txtecho 01 > $DIR/demoCA/serialopensslgenrsa -des3 -out $DIR/demoCA/private/cakey.pem 2048opensslreq -new -x509 -days 3650 -key $DIR/demoCA/private/cakey.pem -out$DIR/demoCA/careq.pem签发二级CA的脚本f/root/ssl.test2# cat no2domain.sh#!/bin/bash[ $# -ne 1 ] && echo "$0 NAME" && exitNAME=$1DIR=/root/ssl.test2/autogetmkdir -p $DIRopensslgenrsa -des3 -out $DIR/$NAME.key 2048openssl x509 -in $DIR/../demoCA/careq.pem -noout -textopensslrsa -in $DIR/$NAME.key -out $DIR/$NAME.keyopensslreq -new -days 3650 -key $DIR/$NAME.key -out $DIR/$NAME.csropensslca -extensions v3_ca -in $DIR/$NAME.csr -config $DIR/../f -days 3000 -out $DIR/$NAME.crt -cert $DIR/../demoCA/careq.pem -keyfile$DIR/../demoCA/private/cakey.pem签发三级CA的脚本# cat no3domain.sh#!/bin/bash#[ $# -ne 1 ] && echo "$0 NAME" && exitNAME=calv3DIR=/root/ssl.test2/autogetopensslgenrsa -des3 -out $DIR/$NAME.key 2048openssl x509 -in $DIR/../demoCA/careq.pem -noout -textopensslrsa -in $DIR/$NAME.key -out $DIR/$NAME.keyopensslreq -new -days 3650 -key $DIR/$NAME.key -out $DIR/$NAME.csropensslca -in $DIR/$NAME.csr -extensions v3_ca -config $DIR/../f -days 3000-out $DIR/$NAME.crt -cert $DIR/calv2.crt -keyfile $DIR/calv2.key由三级CA签发服务器证书的脚本# cat no4domain.sh#!/bin/bash[ $# -ne 1 ] && echo "$0 NAME" && exitNAME=$1DIR=/root/ssl.test2/autogetopensslgenrsa -des3 -out $DIR/$NAME.key 2048openssl x509 -in $DIR/../demoCA/careq.pem -noout -textopensslrsa -in $DIR/$NAME.key -out $DIR/$NAME.keyopensslreq -new -days 3650 -key $DIR/$NAME.key -out $DIR/$NAME.csropensslca -in $DIR/$NAME.csr -config $DIR/../f -days 3000 -out $DIR/$NAME.crt -cert $DIR/calv3.crt -keyfile $DIR/calv3.keyopenssl pkcs12 -export -inkey $DIR/$NAME.key -in $DIR/$NAME.crt -out$DIR/$NAME.p12openssl x509 -in $DIR/$NAME.crt -noout -text > $DIR/$NAME.txtsh no4domain.sh当我们把使用三级CA签发的服务器证书配置在nginx上时,在已经导入根CA的浏览器上肯定是会遇到证书报警的,然后依次把三级CA(no3.crt )和二级CA(no2.crt)追加到服务器证书后面,浏览器ssl链接成功,点击证书查看如下图:========================================================================== =================[weigw@TESTsrc]$ opensslrsa -in privatekey.key -pubout -out pubkey.key writing RSA key格式转换:(证书、私钥、公钥)(PEM <—–>DER)[weigw@TESTsrc]$ openssl x509 -in cacert.crt -inform. PEM -out cacert.der -outform. DER[weigw@TESTsrc]$[weigw@TESTsrc]$ opensslrsa -in privatekey.key -inform. PEM -out privatekey.der -outform. DERwriting RSA key[weigw@TESTsrc]$ opensslrsa -pubin -in pubkey.key -inform. PEM -pubout -out pubkey.der-outform. DERwriting RSA key从DER格式转换成PEM格式一样,就是把inform的格式改成DERoutform的格式改成PEM即可。
openssl做证书的方法 -回复

openssl做证书的方法-回复OpenSSL 是一个开源的软件包,可用于创建安全套接字层(SSL)和传输层安全性(TLS)协议的证书。
证书是用于身份验证和数据加密的数字文件。
下面将一步一步介绍OpenSSL 的使用方法来生成证书。
第一步:安装OpenSSL首先,您需要安装OpenSSL 软件包。
根据您的操作系统,可以在OpenSSL 官方网站(OpenSSL 在您的系统上可用。
第二步:生成私钥要生成证书,首先需要生成一个私钥。
私钥用于生成和验证证书,因此它必须严格保密。
您可以使用以下命令在命令行中生成私钥:openssl genpkey -algorithm RSA -out private.key此命令将使用RSA 算法生成一个私钥,并将其保存在private.key 文件中。
确保将文件保存在安全的位置,并为其设置适当的权限,以防止未经授权访问。
第三步:生成证书请求生成了私钥后,接下来需要生成证书请求。
证书请求包含您的公钥以及有关您身份的信息。
以下命令将生成证书请求:openssl req -new -key private.key -out certificate.csr在此命令中,-key 参数指定您的私钥文件,-out 参数指定将保存证书请求的文件名。
您将被要求输入与您身份相关的信息,如名称、单位、电子邮件地址等。
确保在输入这些信息时提供准确的数据。
第四步:自签名证书生成证书请求后,您可以使用OpenSSL 生成一个自签名证书。
自签名证书是由您自己颁发的,因此在一些特定情况下可能不被所有设备或应用程序接受。
但它在测试和开发环境中非常有用。
以下命令将生成自签名证书:openssl x509 -req -in certificate.csr -signkey private.key -out certificate.crt此命令使用您之前生成的私钥和证书请求来创建一个自签名证书。
最后的证书将保存在certificate.crt 文件中。
用openssl的demo脚本创建自签证书

openssl req -new -key server.key -out server.csr -config f
openssl genrsa -des3 -out client.key 1024
openssl ca -in client.csr -out client.crt -cert ca.crt -keyfile ca.key -config f
cat client.crt client.key > client.pem
cat server.crt server.key > server.pem
openssl req -new -key client.key -out client.csr -config f
openssl req -new -x509 -keyout ca.key -out ca.crt -config f
openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key -config f
1.首先要生成服务器端的私钥(key文件):
openssl genrsa -des3 -out server.key 1024
运行时会提示输入密码,此密码用于加密key文件(参数des3便是指加密算法,当然也可以选用其他你认为安全的算法.),以后每当需读取此文件(通过openssl提供的命令或API)都需输入口令.如果觉得不方便,也可以去除这个口令,但一定要采取其他的保护措施!
openssl req -new -x509 -keyout ca.key -out ca.crt
利用openssl签署CA证书的方法

利⽤openssl签署CA证书的⽅法证书的⽅法签署CA证书虽然在安装MOD_SSL时已经使⽤ make certificate 命令建⽴了服务器的证书签名,但是有时你可能需要改变它。
有很多⾃动的脚本可以实现它,但是最可靠的⽅法是⼿⼯签署证书。
下⾯就两种⽅法做⼀下总结:⼀、⼿⼯⾸先我假定你已经安装好了openssl和MOD_SSL,如果你的openssl安装时的prefix设置为/usr/local/openssl,那么把/usr/local/openssl/bin加⼊执⾏⽂件查找路径。
还需要MOD_SSL源代码中的⼀个脚本,它在MOD_SSL的源代码⽬录树下的pkg.contrib⽬录中,⽂件名为 sign.sh。
将它拷贝到 /usr/local/openssl/bin 中。
第⼀步:先建⽴⼀个 CA 的证书,⾸先为 CA 创建⼀个 RSA 私⽤密钥,[S-1]openssl genrsa -des3 -out ca.key 1024系统提⽰输⼊ PEM pass phrase,也就是密码,输⼊后牢记它。
⽣成 ca.key ⽂件,将⽂件属性改为400,并放在安全的地⽅。
[S-2]chmod 400 ca.key你可以⽤下列命令查看它的内容,[S-3]openssl rsa -noout -text -in ca.key利⽤ CA 的 RSA 密钥创建⼀个⾃签署的 CA 证书(X.509结构)[S-4]openssl req -new -x509 -days 3650 -key ca.key -out ca.crt然后需要输⼊下列信息:Country Name: cn 两个字母的国家代号State or Province Name: An Hui 省份名称Locality Name: Bengbu 城市名称Organization Name: Family Network 公司名称Organizational Unit Name: Home 部门名称Common Name: Chen Yang 你的姓名Email Address: sunstorm@ Email地址⽣成 ca.crt ⽂件,将⽂件属性改为400,并放在安全的地⽅。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
一、安装centos系统,如下图:二、使用openssl建立CA并颁发证书,使用root用户登录centos系统[root@localhost ~]# mkdir certs[root@localhost ~]# cd certs[root@localhost certs]# /etc/pki/tls/misc/CA -newcaCA certificate filename (or enter to create)Making CA certificate ...Generating a 2048 bit RSA private key ....................................................................................................................................................+++ .+++writing new private key to '/etc/pki/CA/private/./cakey.pem'Enter PEM pass phrase:Verifying - Enter PEM pass phrase:-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:beijingLocality Name (eg, city) [Default City]:beijingOrganization Name (eg, company) [Default Company Ltd]:opzoonOrganizational Unit Name (eg, section) []:opzoonCommon Name (eg, your name or your server's hostname) []:Email Address []:tac@Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:111111An optional company name []:opzoonUsing configuration from /etc/pki/tls/fEnter pass phrase for /etc/pki/CA/private/./cakey.pem:Check that the request matches the signatureSignature okCertificate Details:Serial Number:ec:01:11:fd:2f:3f:25:c1ValidityNot Before: Feb 1 21:21:43 2012 GMTNot After : Jan 31 21:21:43 2015 GMTSubject:countryName = CNstateOrProvinceName = beijingorganizationName = opzoonorganizationalUnitName = opzooncommonName = emailAddress = tac@X509v3 extensions:X509v3 Subject Key Identifier:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32X509v3 Authority Key Identifier:keyid:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32X509v3 Basic Constraints:CA:TRUECertificate is to be certified until Jan 31 21:21:43 2015 GMT (1095 days)Write out database with 1 new entriesData Base Updated[root@localhost certs]#[root@localhost certs]# cd /etc/pki/CA/[root@localhost CA]# openssl x509 -in cacert.pem -days 3650 -out cacert.pem -signkey ./private/cakey.pemGetting Private keyEnter pass phrase for ./private/cakey.pem:[root@localhost CA]#[root@localhost CA]# cd /root/certs/[root@localhost certs]# /etc/pki/tls/misc/CA -newreqGenerating a 2048 bit RSA private key ....................................................+++.............+++writing new private key to 'newkey.pem'Enter PEM pass phrase:Verifying - Enter PEM pass phrase:-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:fujianLocality Name (eg, city) [Default City]:fuzhouOrganization Name (eg, company) [Default Company Ltd]:opzoon Organizational Unit Name (eg, section) []:opzoonCommon Name (eg, your name or your server's hostname) []: Email Address []:fujian@Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:fuzhouAn optional company name []:opzoonRequest is in newreq.pem, private key is in newkey.pem[root@localhost certs]#[root@localhost certs]# /etc/pki/tls/misc/CA -signUsing configuration from /etc/pki/tls/fEnter pass phrase for /etc/pki/CA/private/cakey.pem:Check that the request matches the signatureSignature okCertificate Details:Serial Number:ec:01:11:fd:2f:3f:25:c2ValidityNot Before: Feb 1 21:45:55 2012 GMTNot After : Jan 31 21:45:55 2013 GMTSubject:countryName = CNstateOrProvinceName = fujianlocalityName = fuzhouorganizationName = opzoonorganizationalUnitName = opzooncommonName = emailAddress = fujian@X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:32:5A:E6:00:EC:A5:88:C5:AB:73:17:77:F1:D3:08:A8:FE:2D:B3:EE X509v3 Authority Key Identifier:keyid:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32Certificate is to be certified until Jan 31 21:45:55 2013 GMT (365 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base UpdatedCertificate:Data:Version: 3 (0x2)Serial Number:ec:01:11:fd:2f:3f:25:c2Signature Algorithm: sha1WithRSAEncryptionIssuer: C=CN, ST=beijing, O=opzoon, OU=opzoon, CN=/emailAddress=tac@ValidityNot Before: Feb 1 21:45:55 2012 GMTNot After : Jan 31 21:45:55 2013 GMTSubject: C=CN, ST=fujian, L=fuzhou, O=opzoon, OU=opzoon, CN=/emailAddress=fujian@Subject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)Modulus:00:d8:29:e0:c8:fe:a7:fa:44:b0:1a:2b:72:f5:66:1c:48:da:e8:7c:33:28:b0:7d:20:df:b5:24:1e:99:51:78:aa:6e:87:cd:0d:e0:6e:ea:cd:52:30:1f:87:67:98:1a:8a:37:f4:16:ad:22:60:05:18:5e:16:21:b1:48:31:29:7b:6d:ae:58:a1:5c:07:04:37:72:7b:41:37:89:63:ec:af:35:9a:06:47:3f:2c:c6:53:db:68:22:63:ad:85:a0:21:cc:0b:f3:05:a5:1d:26:07:c5:ec:1a:e3:06:88:18:52:e7:65:4a:1a:9d:c1:1e:cb:f6:db:f5:3f:0f:37:01:8f:8c:05:c7:bf:8f:eb:d2:32:71:ae:70:10:d7:ef:52:86:37:d2:6d:a9:05:24:91:c1:b5:57:38:0e:83:8d:90:fb:16:9f:2c:a6:bc:d1:2e:ef:3e:f7:50:b3:54:cf:d9:98:ef:a2:12:ad:ba:c8:4e:ce:b6:ce:91:2d:8a:63:cd:e3:6e:8d:f0:72:b1:67:90:36:f1:e9:06:9f:45:73:08:2a:4a:4d:a3:66:c5:00:59:fd:81:2e:57:da:8c:8d:c9:22:b1:f3:8d:77:0b:a2:e8:8f:54:2d:bc:8f:58:b3:3c:2d:4b:1a:10:fa:3e:43:8b:20:3f:e0:24:fc:23:c0:2d:5dExponent: 65537 (0x10001)X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:32:5A:E6:00:EC:A5:88:C5:AB:73:17:77:F1:D3:08:A8:FE:2D:B3:EE X509v3 Authority Key Identifier:keyid:E2:BC:51:1B:2E:1E:74:AF:4E:93:0D:6E:D4:AC:E5:30:35:B4:50:32Signature Algorithm: sha1WithRSAEncryptiona0:e3:bf:1e:3b:88:e0:86:15:ed:7b:17:80:88:c9:2f:c2:ce:ba:f4:c9:96:81:07:9e:42:51:ed:a8:47:0b:3a:c5:01:6b:1d:2d:dc:6d:8a:8a:57:bc:c9:7a:a7:02:e3:35:eb:79:f4:f7:6f:6b:fd:11:49:d8:4d:10:d8:bc:7c:31:7a:7d:0f:c9:92:2e:d6:01:90:11:2b:96:f3:11:d9:ad:af:97:a5:53:c9:f2:cd:58:9b:65:cd:52:d8:80:88:dc:c5:c3:5a:09:c5:87:46:81:57:e0:af:fe:16:9a:1c:50:a6:b3:ef:2a:ef:ab:ff:ec:a9:b3:42:e6:ec:c6:a5:70:43:bc:56:27:aa:e9:76:5b:02:84:2b:ea:96:e4:92:4f:4e:90:cb:94:05:d8:d2:ca:b3:2d:91:4f:ee:a1:a3:4a:70:91:cf:e4:1f:45:72:39:ca:f1:25:80:1a:4c:8a:ce:ec:bc:dd:61:57:75:ff:06:84:16:5f:f1:03:9a:9e:56:14:18:a8:95:14:2b:53:83:65:55:93:7c:59:0e:53:e0:c7:bd:99:2c:36:b7:57:f3:53:c8:e2:86:80:30:6f:31:5d:66:cf:19:91:68:9d:50:5c:20:dc:8b:e6:61:9d:0c:56:a9:c7:3f:6f:13:26:06:0e:b9:51:d0:26:a4:ee-----BEGIN CERTIFICATE-----MIIEAjCCAuqgAwIBAgIJAOwBEf0vPyXCMA0GCSqGSIb3DQEBBQUAMHgxCzAJBgNV BAYTAkNOMRAwDgYDVQQIDAdiZWlqaW5nMQ8wDQYDVQQKDAZvcHpvb24xDzANBgNV BAsMBm9wem9vbjEWMBQGA1UEAwwNb3B6b29uLmNvbS5jbjEdMBsGCSqGSIb3DQEJ ARYOdGFjQG9wem9vbi5jb20wHhcNMTIwMjAxMjE0NTU1WhcNMTMwMTMxMjE0NTU1 WjCBizELMAkGA1UEBhMCQ04xDzANBgNVBAgMBmZ1amlhbjEPMA0GA1UEBwwGZnV6 aG91MQ8wDQYDVQQKDAZvcHpvb24xDzANBgNVBAsMBm9wem9vbjEWMBQGA1UEAwwN b3B6b29uLmNvbS5jbjEgMB4GCSqGSIb3DQEJARYRZnVqaWFuQG9wem9vbi5jb20w ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDYKeDI/qf6RLAaK3L1ZhxI2uh8MyiwfSDftSQemVF4qm6HzQ3gburNUjAfh2eYGoo39BatImAFGF4WIbFIMSl7ba5YoVwHBDdye0E3iWPsrzWaBkc/LMZT22giY62FoCHMC/MFpR0mB8XsGuMGiBhS52VKGp3BHsv22/U/DzcBj4wFx7+P69Iyca5wENfvUoY30m2pBSSRwbVXOA6DjZD7Fp8sprzRLu8+91CzVM/ZmO+iEq26yE7Ots6RLYpjzeNujfBysWeQNvHpBp9FcwgqSk2jZsUAWf2BLlfajI3JIrHzjXcLouiPVC28j1izPC1LGhD6PkOLID/gJPwjwC1d AgMBAAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2Vu ZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBQyWuYA7KWIxatzF3fx0wio/i2z7jAfBgNVHSMEGDAWgBTivFEbLh50r06TDW7UrOUwNbRQMjANBgkqhkiG9w0BAQUF AAOCAQEAoOO/HjuI4IYV7XsXgIjJL8LOuvTJloEHnkJR7ahHCzrFAWsdLdxtiopXvMl6pwLjNet59Pdva/0RSdhNENi8fDF6fQ/Jki7WAZARK5bzEdmtr5elU8nyzVibZc1S2ICI3MXDWgnFh0aBV+Cv/haaHFCms+8q76v/7KmzQubsxqVwQ7xWJ6rpdlsC hCvqluSST06Qy5QF2NLKsy2RT+6ho0pwkc/kH0VyOcrxJYAaTIrO7LzdYVd1/waEFl/xA5qeVhQYqJUUK1ODZVWTfFkOU+DHvZksNrdX81PI4oaAMG8xXWbPGZFonVBcINyL5mGdDFapxz9vEyYGDrlR0Cak7g==-----END CERTIFICATE-----Signed certificate is in newcert.pem[root@localhost certs]# lsnewcert.pemnewkey.pemnewreq.pem到此CA的建立和证书的制作已经完成,其中newcert.pem为证书文件,newkey.pem为证书密钥文件,/etc/pki/CA/目录下的cacert.pem为CA证书。
