思科高端防火墙介绍
防火墙产品介绍

4.5 防火墙产品介绍
4.5.2 软件防火墙
2.Microsoft ISA Server软件防火墙 . 软件防火墙 是一个应用层防火墙、VPN和Web高速缓冲产品,旨在 改善用户的网络安全,实现了对应用层攻击的防护 ,同时对包 头部分以及应用层内容进行检测。 优点:安全、易于使用且经济高效 缺点:网络传输速度有所影响,网络资源的消耗,信息流 通的阻碍。
4-19
4.5 防火墙产品介绍
4.5.1 硬件防火墙
2.Quidway Eudemon(守护神 . 守护神)300防火墙 守护神 防火墙 是华为公司推出的基于网络处理器NP技术的硬件高速状 态防火墙,采用先进的动态检测技术(ASPF),具备电信级高 性能和高可靠性,普遍适用于大、中型企业及其分支机构。 特点是:拥有强大的防范Dos/DDoS攻击能力;提供丰 富的安全业务和灵活组网能力;拥有高性能的VPN网关;具备 强大的NAT业务能力;可实现灵活的P2P等流量识别和带宽管 理。
4-20
4.5 防火墙产品介绍
4.5.2 软件防火墙
1.CheckPoint软件防火墙 . 软件防火墙 2.Microsoft ISA Server软件防火墙 . 软件防火墙 3. 天网防火墙
4.5 防火墙产品介绍
4.5.2 软件防火墙
1.CheckPoint软件防火墙 . 软件防火墙 综合的、模块化的安全产品,基于策略的解决方案能够 让管理员指定网络访问按部署的时间段进行控制,它能够将处 理任务分散到一组工作站上,从而减轻相应防火墙服务器、工 作站的负担。 特点 :操作在操作系统的核心层 ,支持基于Web的多媒体 和UDP应用程序 ,采用多重验证模板和方法,使网络管理员非 常简单地验证客户端、会话和用户对网络的访问。
nsa 2650 技术参数

nsa 2650 技术参数
NSA 2650是一款由思科公司推出的网络安全设备,主要用于企业级网络安全防护和管理。
以下是关于NSA 2650的一些技术参数:
1. 防火墙性能,NSA 2650具有出色的防火墙性能,能够处理大量的网络流量和连接请求。
它通常具有高吞吐量和低延迟,以确保网络数据的快速传输和处理。
2. VPN性能,NSA 2650支持虚拟专用网络(VPN)功能,能够提供安全的远程访问和站点到站点连接。
它具有强大的加密和认证功能,能够保障数据在公共网络上的安全传输。
3. 接口和端口,NSA 2650通常配备有多个千兆以太网接口和其他类型的物理接口,以支持不同类型的网络连接和设备接入。
4. 安全功能,除了基本的防火墙和VPN功能外,NSA 2650还可能包含其他安全功能,如入侵检测和防御系统(IDS/IPS)、应用程序控制、安全威胁智能防护等,以提供全面的网络安全保护。
5. 管理和监控,NSA 2650通常具有易用的管理界面和丰富的
监控功能,能够帮助管理员轻松地配置和监视网络安全设备的运行状态和性能。
总的来说,NSA 2650是一款功能强大的企业级网络安全设备,具有出色的防火墙和VPN性能,丰富的安全功能以及易用的管理和监控能力,能够满足企业对网络安全的高要求。
希望这些信息能够帮助你了解NSA 2650的技术参数。
(产品管理)思科公司防火墙产品一览

(产品管理)思科公司防火墙产品一览思科公司PIX防火墙产品壹览思科公司防火墙系列产品特性壹览表PIX501PIX506E PIX515E-UR PIX525-UR,支持千兆PIX535-UR,支持千兆FWSM高端防火墙模块市场小型办公室家庭办公室远程办公室中小型分支机构大型企业大型企业+服务供应商大型企业+服务供应商许可用户个数10或者50无限无限无限无限无限VPN对等端最大数量1025200020002000N/A RAM(MB)1632642561GB2GB最大接口数(物理+逻辑)1个10BT+4个FE2个10BaseT810244096物理接口个数2个10BaseT4端口交换机2个10BaseT2个10/100+4个10/1002个10/100+6个FE/GE2个10/100+8个FE/GE4096双向吞吐量(Mbps)60100188360 1.7GHz 5.5G3DES(VAC/VAC+)(Mbps)316130145425N/AAES-128吞吐量(Mbps)4.530130135495N/AAES-256吞吐量(Mbps)3.425130135425N/A最大连接数7,50025,000130,000380,000500,0001,000,000每秒支持的最大连接数3807005,0007,5009,400100,000是否支持OSPF是是是是是是支持基于Web的设备管理方式是是是是是是是否支持简单VPN(easyVPN)是是是是是是支持虚拟防火墙否否是,7.0版本是,7.0版本是,7.0版本是,2.2版本,支持256个支持透明防火墙是,7.0版本是,7.0版本是,7.0版本是,7.0版本是,7.0版本是,2.2版本支持虚拟防火墙资源限制否否是,7.0版本是,7.0版本是,7.0版本是,2.2版本支持802.1qTrunk否否是是是是支持FailOver否否是是是是思科全系列防火墙详细功能特性列表产品型号CiscoFIX501CiscoFIX506E CiscoFIX515E CiscoFIX525CiscoFIX535CiscoFWSM 高端防火墙总结自动升级支持有有有有有有EasyVPN 支持(即向VPN 客户全面、自动推出策略)有有有有有有Stub 组播路由支持有有有有有有集成化入侵检则功能有有有有有有IP 语音防火墙支持有有有有有有PPTP 支持有有有有有有免费软件VPN 客户机有有有有有有免费软件VPN 客户机,带集成化个人防火墙有有有有有有运行模式-路由/交换网桥有有有有有有第2层(L2)透明模式防火墙有(7.0)有(7.0)有(7.0)有(7.0)有(7.0)有虚拟防火墙支持有(7.0)有(7.0)有(7.0)有(7.0)有(7.0)有业界认证ISCAFirewall 有有有有有有ICSAIPsec 有有有有有有通用标准(EAL4)无(但正于开发)无(但正于开发)无(但正于开发)无(但正于开发)无(但正于开发)无(但正于开发)FIPS-140Level2无(但正于开发)无(但正于开发)无(但正于开发)无(但正于开发)无(但正于开发)无(但正于开发)硬件信息外部接口类型10/100Base-T 10/100Base-T 10/100Base-T 10/100Base-T ,GE10/100Base-T ,GE10/100Base-T ,GE ,POS ,E1,广域网接口硬件结构CPU+ASIC+PCI 总线结构CPU+ASIC+PCI 总线结构CPU+ASIC+PCI 总线结构CPU+ASIC+PCI 总线结构CPU+ASIC+PCI 总线结构NP(NetworkPr ocesspr)结构防火墙防火墙类型状态检测状态检测状态检测状态检测状态检测状态检测防火墙算法专用ASA 自适应安全算法专用ASA 自适应安全算法专用ASA 自适应安全算法专用ASA 自适应安全算法专用ASA 自适应安全算法专用ASA 自适应安全算法所支持的预定义服务数(如FTP ,SMTP ,HTTP 等)108108108108108108容灾容错有有有有有有对象组支持有有有有有有支持和入侵检测系统的结合和互动有有有有有有IP语音(VoIP)防火墙支持SIP支持有有有有有有H.323支持有有有有有有Skinny支持有有有有有有DHCP选项66和150(IP电话/软电话自动配置)有有有有有有入侵保护所支持的IDS特征数595959595959对中央IDS控制台的报警通知有有有有有有FTP命令过滤有有有有有有针对SYN攻击的保护有有有有有有针对IP欺骗的保护有有有有有有邮件防护有有有有有有DNS防护有有有有有有"防攻击类型Ping-of-DeathPing-Flooding、TearDropUDP-FloodingSYN-FloodingKillWinWinNukeLANDIGMP2IP碎片源路由端口扫描IP-Spoofing"有有有有有有虚拟专用网(VPN)站点间VPN支持有有有有有有所支持的隧道协议IPsec,PPTP,IPsec/L2TP IPsec,PPTP,IPsec/L2TPIPsec,PPTP,IPsec/L2TPIPsec,PPTP,IPsec/L2TPIPsec,PPTP,IPsec/L2TPIPsec,PPTP,IPsec/L2TP所支持的加密算法DES,3DES,AES DES,3DES,AES DES,3DES,AES DES,3DES,AES DES,3DES,AES DES,3DES,AES 所支持的散列算法MD5,SHA-1MD5,SHA-1MD5,SHA-1MD5,SHA-1MD5,SHA-1MD5,SHA-1拆分隧道支持有有有有有有NAT透明性支持有有有有有有可作为VPN硬件客户端有有有有有有冗余VPN头端支持有有有有有有可作为远程VPN客户端的VPN头端有有有有有有可动态地向远程VPN客户端推出VPN策略有有有有有有支持X.509认证Entrust,VeriSign,Microsoft,Baltimore,RSAKeon Entrust,VeriSign,Microsoft,Baltimore,RSAKeonEntrust,VeriSign,Microsoft,Baltimore,RSAKeonEntrust,VeriSign,Microsoft,Baltimore,RSAKeonEntrust,VeriSign,Microsoft,Baltimore,RSAKeonEntrust,VeriSign,Microsoft,Baltimore,RSAKeon基于SCEP的X.509认证注册支持有有有有有有经由SCEP的CRL有有有有有有QoS支持有有有有有有动态路由支持有有有有有有地址管理DHCP服务器有有有有有有DHCP客户机有有有有有有DHCP中继有有有有有有NAT/PAT支持有有有有有有端口重定向有有有有有有双向NAT有有有有有有IP/MAC绑定功能有有有有有有内容过滤使用外部服务器的URL过滤(第三方)有(Websense和N2H2集成)有(Websense和N2H2集成)有(Websense和N2H2集成)有(Websense和N2H2集成)有(Websense和N2H2集成)有(Websense和N2H2集成)Java阻塞有有有有有有ActiveX阻塞有有有有有有用户验证防火墙上本地定义的用户列表有有有有有有经由RADIUS实现的用户列表有有有有有有经由TACACS/TACACS+实现的用户列表有有有有有有验证的服务HTTP,FTP,Telnet,VPN(经由ACS)HTTP,FTP,Telnet,VPN(经由ACS)HTTP,FTP,Telnet,VPN(经由ACS)HTTP,FTP,Telnet,VPN(经由ACS)HTTP,FTP,Telnet,VPN(经由ACS)HTTP,FTP,Telnet,VPN(经由ACS)设备级管理真正的即插即用(即工厂配置可用于大多有有有有有有数部署)基于Web的安全管理有有有有有有SSH支持有有有有有有SNMP支持有有有有有有经由图形进行的设备和性能监控有有有有有有单独管理员帐户数无限无限无限无限无限无限用于简化部署的全面VPN向导有有有有有有用于简化部署的全面防火墙向导有(包括ACL配置)有(包括ACL配置)有(包括ACL配置)有(包括ACL配置)有(包括ACL配置)有(包括ACL配置)管理员级别数16,可定制16,可定制16,可定制16,可定制16,可定制16,可定制集中管理应用名CiscoWorksVMS,PIXMIC CiscoWorksVMS,PIXMICCiscoWorksVMS,PIXMICCiscoWorksVMS,PIXMICCiscoWorksVMS,PIXMICCiscoWorksVMS,PIXMIC基于Web的安全管理有有有有有有用于配置升级的推/拉自动升级模型有有有有有有用于软件升级的推/拉自动升级模型有有有有有有企业级、工作流驱动管理有有有有有有。
思科ASA5500-X系列防火墙

Cisco Confidential
17
SDN Overview
© 2007 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
9
ASA 5585-X 提供IPS服务数据流分析
防火墙/入侵防御 /VPN的高性能结 合,独立硬件资源
© 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 10
SDN Overview
议程
Cisco安全产品线 Cisco ASA 5500-X产品亮点
1:Cluster技术--扩展性能 2:虚墙资源分配 3:IPS服务 4:真正的“云”防火墙 5:远程安全接入技术 6:VPN网关自动选择
SDN Overview
© 2007 Cisco Systems, Inc. All rights reserved.
14
SDN Overview
© 2007 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
思科安全移动方案使用举例——IPAD上VDI的安全访问
成功进入 VDI 里的 Windows 7 桌面!
UC HVD
WAN
VPN Tunnel IPAD Cisco ASA
SDN Overview
© 2007 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
4
在标称吞吐下的延迟
ASA5585 吞吐量/延迟
Cisco ASA 5585-X 高密度状态式防火墙数据手册说明书

Data SheetCisco ASA 5585-X Stateful FirewallToday’s enterprise networks struggle to keep up with a mobile workforce. Users expect on-demand access from their many devices, even as applications multiply and push performance levels. And of course security remains a priority. How do you scale and still preserve the integrity of the network? Start with the Cisco® ASA 5585-X Firewall, a compact yet high-density firewall that delivers tremendous scalability, performance, and security in a two-rack-unit (2RU) footprint.Using a single firewall blade, the Cisco ASA 5585-X meets the growing needs of dynamic organizations by providing eight times the performance density, very high VPN session counts, twice as many connections per second, and four times the connection capacity of any competitive firewall.Firewall FeaturesSupport for Layer 3 and Layer 4 stateful firewall inspection features, including access control and network address translation, enables organizations to keep existing stateful inspection policies that are essential for compliance regulations and securing critical data center resources.In addition to comprehensive stateful inspection capabilities, Layer 7 next-generation policies act intelligently on contextual information. Cisco AnyConnect® technology provides information on the type and location, and endpoint posture of a mobile device before it accesses the network, so that administrators can maintain high levels of network visibility, protection and control. Threat intelligence feeds from Cisco Collective Security Intelligence (CSI) use the global footprint of Cisco security deployments to analyze approximately one-third of the world’s Internet traffic for near-real-time protection from new and emerging threats.Flexible Deployment OptionsThe Cisco ASA 5585-X supports two hardware blades in a single 2RU chassis. The bottom slot (slot 0) hosts the ASA stateful inspection firewall module, while the top slot (slot 1) can be used for adding up to two Cisco ASA 5585-X I/O modules for high interface density for mission-critical data centers that require exceptional flexibility and security.ClusteringUsing Cisco ASA Software Release 9.0 and later, customers can combine up to 16 Cisco ASA 5585-X firewall modules in a single cluster for up to 640 Gbps of throughput, 2 million connections per second, and more than 100 million concurrent connections. This “pay as you grow” model enables organizations to purchase what they need today and dynamically add more when their performance needs grow. To protect high-performance data centers from internal and external threats, the cluster can be augmented by adding IPS modules.Cisco ASA software clustering delivers a consistent scaling factor, irrespective of the number of units in the cluster, for a linear and predictable increase in performance. Complexity is reduced, as no changes are required to existing Layer 2 and Layer 3 networks. Support for data center designs based on the Cisco Catalyst® 6500 Series Virtual Switching System (VSS) and the Cisco Nexus virtual PortChannel (vPC) as well as the Link Aggregation Control Protocol (LACP) provides high availability (HA) with better network integration.For operational efficiency, Cisco ASA clusters are easy to manage and troubleshoot as a single entity. Policies pushed to the master node are replicated across all the units within the cluster. The health, performance, and capacity statistics of the entire cluster, as well as individual units within the cluster, can be assessed from a single management console. Hitless software upgrades are supported for ease of device updates.Clustering supports HA in both active/active and active/passive modes. All units in the cluster actively pass traffic, and all connection information is replicated to at least one other unit in the cluster to support N+1 HA. In addition, single and multiple contexts are supported, along with routed and transparent modes. A single configuration is maintained across all units in the cluster using automatic configuration sync. Clusterwide statistics are provided to track resource usage.Cisco TrustSec IntegrationUsing Cisco ASA Software Release 9.0 and later, the Cisco ASA 5585-X provides context awareness through the integration of identity-based firewall security and Cisco TrustSec® security group tags for enhanced visibility and control. Identity-based firewall security provides more flexible access control to enforce policies based on user and group identities and the point of access. Administrators can write policies that correspond to business rules, a process that increases security, enhances ease of use, and requires fewer policies to manage. Similarly, Cisco TrustSec integration enables security group tags to be embedded into the network, providing administrators with the ability to develop and enforce better, more precise policies.Cut Costs While Improving Performance and SecurityThe Cisco ASA 5585-X Next-Generation Firewall delivers superior scalability, performance, and security to handle high data volumes without sacrificing performance. Most firewalls require up to 16RUs and 5100 watts to scale to the level of performance that the Cisco ASA 5585-X achieves with only 2RUs and 785 watts. This performance helps enterprises meet the increasing demands for network connectivity without the need to invest in additional data center space and incur the corresponding maintenance costs.Based on tests conducted by Cisco, the Cisco ASA 5585-X significantly reduces initial procurement costs by 80 percent, power consumption costs by 85 percent, and rack space requirements by 88 percent in addition to significant reductions in overall integration and management complexity and costs. In addition, you can install up to two firewall modules in a single Cisco ASA 5585-X chassis, providing scalability to 80 Gbps.Table 1 gives the capabilities of the four Cisco ASA 5585-X models.Table 1. Cisco ASA 5585-X Next-Generation Firewall Capabilities and CapacitiesEdge Edge Data center Data centerUnlimited Unlimited Unlimited Unlimited1 Maximum throughput with UDP traffic measured under ideal test conditions.2“Multiprotocol” refers to a traffic profile consisting primarily of TCP-based protocols and applications like HTTP, SMTP, FTP, IMAPv4, BitTorrent, and DNS.3 Available for the firewall feature set.4 VPN throughput and maximum peers depend on the ASA device configuration and VPN traffic patterns, including average packet size. These elements should be taken into consideration as part of your capacity planning. Throughput represents the maximum possible IPsec throughput. Maximum sessions may be further limited by your throughput requirements. AnyConnect licenses required. See the AnyConnect Ordering Guide for details. Maximum sessions may be further limited by your throughput requirements.5 AnyConnect licenses required. See the AnyConnect Ordering Guide for details. Maximum sessions may be further limited by your throughput requirements.6 Available for the firewall feature set.SafetyUL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 UL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 UL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 UL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 Electromagnetic compatibility (EMC)47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 Series47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 Series47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 Series47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 SeriesNote: Performance numbers were tested and validated with Cisco ASA Software Release 8.4.Cisco ASA 5585-X I/O ModulesMission-critical data centers running Cisco ASA Software Release 8.4.4 and later can use the top slot of the Cisco ASA 5585-X to add up to two Cisco ASA 5585-X I/O modules for exceptional flexibility and security. With two Cisco ASA 5585-X I/O modules, a single Cisco ASA 5585-X can support up to twenty 10 Gigabit Ethernet ports or up to fifty 1 Gigabit Ethernet ports. Using the Cisco ASA 5585-X Divider, the top slot is partitioned into two half-slots, with each I/O module occupying one half-slot. When only one I/O module is installed, a half-slot blank cover is required to cover the empty half-slot.Table 2 describes each of the Cisco ASA 5585-X I/O modules in more detail.Table 2.Cisco ASA 5585-X I/O ModulesTable 3 lists the 10 Gigabit Ethernet Enhanced Small Form-Factor Pluggable (SFP+) and 1 Gigabit Ethernet SFPs that are supported.Table 3. Supported SFP and SFP+ ModulesOptional DC Power SuppliesService providers and data centers that require data-center-powered equipment can purchase Cisco ASA 5585-X data center power supply modules with built-in fans. These power supplies deliver up to 1150 watts of data center power for Cisco ASA 5585-X Next-Generation Firewalls. Two data center power supplies are required for each Cisco ASA 5585-X chassis. The minimum software required is Cisco ASA Software Release 8.4.5.Warranty InformationFind warranty information on at the Product Warranties page.Ordering InformationHelp customers understand all the components or parts they need to purchase in order to install and use the product.To place an order, visit the Cisco How to Buy homepage.Table 4 lists part numbers for customer convenience. Table 4. Ordering InformationTo Download the SoftwareVisit the Cisco Software Center to download Cisco ASA Software.Service and SupportCisco services help you protect your network investment, improve network operations, and prepare your network for new applications to extend network intelligence and the power of your business.Included in the "Operate" phase of the service lifecycle are the Cisco Security IntelliShield® Alert Manager Service, Cisco SMARTnet™ services, the Cisco SP Base, and Cisco Services for IPS. These services are suitable for enterprise, commercial, and service provider customers.Cisco Security IntelliShield Alert Manager Service provides a customizable, web-based threat and vulnerability alert service that allows organizations to easily access timely, accurate, and credible information about potential vulnerabilities in their environment.Cisco Services for IPS supports modules, platforms, and bundles of platforms and modules that feature Cisco IPS capabilities. Cisco SMARTnet and Cisco SP Base support other products in this family.For More InformationFor more information, please visit the following links:●Cisco ASA 5500-X Series Next-Generation Firewalls:/en/US/products/ps6120/index.html●Cisco Cloud Web Security: /en/US/products/ps11720/index.html●Cisco TrustSec Solutions: /en/US/netsol/ns1051/index.html●Cisco AnyConnect: /go/anyconnect●Cisco AnyConnect Ordering Guide: /c/en/us/products/security/anyconnect-secure-mobility-client/sales-resources-listing.html●Cisco Security Manager: /en/US/products/ps6498/index.html●Cisco Adaptive Security Device Manager: /en/US/products/ps6121/index.html●Cisco Security Services: /en/US/products/svcs/ps2961/ps2952/serv_group_home.html。
思科 Cisco ASA 5500 系列防火墙
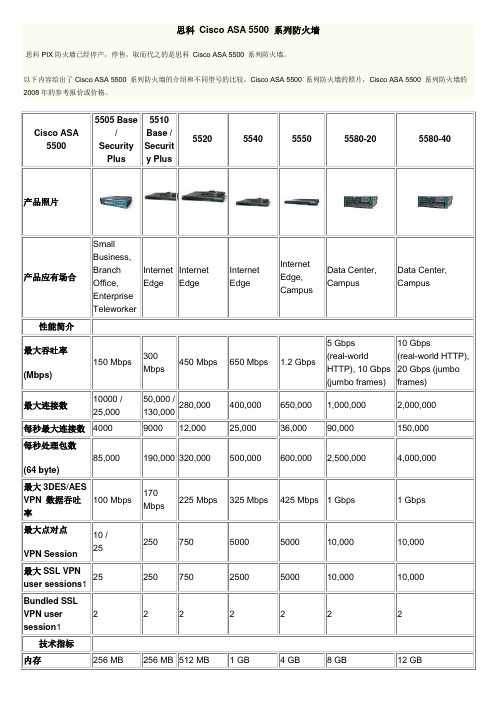
Not available
Not available
内容安全
(防病毒,防木马,文件拦截)
Not available
Yes (with CSC SSM)
Yes (with CSC SSM)
Yes (with CSC SSM)
Not available
Not available
Not available
Not available
Yes
Yes
Yes
Yes
Yes
High availability support4
Not supported
Stateless A/S
Not supported
A/A and A/S
A/A and A/S
A/A and A/S
A/A and A/S
ASA5540-K8
ASA 5540 Appliance with SW, HA, 4GE+1FE, DES
参考价格(人民币:元):112,167
ASA5550-K8
ASA 5550 Appliance with SW, HA, 8GE+1FE, DES
参考价格(人民币:元):131,967
512 MB
1 GB
4 GB
8 GB
12 GB
最小系统闪存
64 MB
64 MB
64 MB
64 MB
64 MB
1 GB
1 GB
接口2
8 port 10/100 switch with 2 Power over Ethernet ports
5-10/100 /
2-10/100/1000, 3-10/100
思科Firepower 新世代防火墙(NGFW)

資料表思科 Firepower 新世代防火牆 (NGFW)思科 Firepower ® NGFW (新世代防火牆)是業界首款完全整合、聚焦於威脅,並具備整合管理功能的新世代防火牆。
在遭受攻擊之前、中、後,思科 Firepower NGFW 獨家提供進階威脅保護。
遏止更多威脅獲得更多深入分析及早偵測,盡快行動降低複雜程度讓您的網路發揮更大效益效能亮點支援服務讓您的 IT 員工可以隨時直接聯絡思科技術表 1 簡要說明思科 Firepower 4100 系列 NFGW 、9300 系列資安設備,以及精選思科 ASA 5500-X 設備的效能亮點。
表 1.設備功能亮點1平均封包大小為 1024 個位元組的 HTTP 工作階段21024 個位元組的 TCP 防火牆效能注意:NGFW 效能會因網路和流量而有所不同。
請諮詢您的思科代表,尋求詳細的建置規模指引。
效能會因新軟體版本所做變更而有所變化。
思科 Firepower 2100 系列:業界首款啟用威脅檢查時,仍能維持效能不變的中程 NGFW思科 Firepower 4100 系列: 業界第一款 40 Gbps 介面的 1RU NGFW思科 Firepower 9300:超高效能的 NGFW ,可隨著需求成長而擴充思科 ASA 5500-X 系列:分公司、工業應用及網際網路邊際裝置適用的機型Firepower NGFWv ︰ 適用於虛擬和雲端環境的 NGFW平台影像支援思科 Firepower NGFW 包括應用程式可視性與控制 (AVC)、選購的新世代入侵防禦系統 (NGIPS)、思科® 進階惡意程式防護 (AMP) 網路版以及 URL 過濾功能。
思科 Firepower 2100 系列、4100 系列和 9300 設備皆使用思科 Firepower 威脅防禦軟體影像。
也可以使用思科 Firepower 2100 系列、4100 系列及 9300 裝置支援思科調適型安全設備 (ASA) 軟體映像。
ASA5500系列防火墙介绍

Cisco® ASA 5500 系列自适应安全设备是思科专门设计的解决方案,将最高的安全性和出色VPN服务与创新的可扩展服务架构有机地结合在一起。
作为思科自防御网络的核心组件,Cisco ASA 5500系列能够提供主动威胁防御,在网络受到威胁之前就能及时阻挡攻击,控制网络行为和应用流量,并提供灵活的VPN连接。
思科强大的多功能网络安全设备系列不但能为保护家庭办公室、分支机构、中小企业和大型企业网络提供广泛而深入的安全功能,还能降低实现这种新安全性相关的总体部署和运营成本及复杂性。
Cisco ASA 5500 系列在一个平台中有力地提供了多种已经获得市场验证的技术,无论从运营角度还是从经济角度看,都能够为多个地点部署各种安全服务。
利用其多功能安全组件,企业几乎不需要作任何两难选择,也不会面临任何风险,既可以提供强有力的安全保护,又可以降低在多个地点部署多台设备的运营成本。
Cisco ASA 5500系列包含全面的服务,通过为中小企业和大型企业定制的产品版本,能满足各种部署环境的特定需求。
这些版本为各地点提供了相应的服务,从而达到出色的保护效果。
每个版本都综合了一套Cisco ASA 5500系列的重点服务(如防火墙、IPSec和SSL VPN、IPS,以及Anti-X服务),以符合企业网络中特定环境的需要。
通过确保满足每个地点的安全需求,网络整体安全性也得到了提升。
图1. Cisco ASA 5500系列自适应安全设备Cisco ASA 5500 系列能够通过以下关键组件帮助企业更有效地管理网络并提供出色的投资保护:•经过市场验证的安全与VPN功能- 全特性、高性能的防火墙,入侵防御系统(IPS), Anti-X和IPSec/SSL VPN 技术提供了强大的应用安全性、基于用户和应用的访问控制、蠕虫与病毒防御、恶意软件防护、内容过滤以及远程用户/站点连接。
•可扩展的自适应识别与防御服务架构-利用Cisco ASA 5500系列的一个模块化服务处理和策略框架,企业可根据每个流量的情况,应用特定的安全或网络服务,提供高度精确的策略控制和各种防御服务,并简化流量处理。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
• (1)Intuitive single-device management and monitoring services with the cisco Adaptive Security Device Manger (ASDM) and enterprise-class multidevice management services through CISCO Security Manager (图形化界面网管)
14
三、CISCO ASA 产品介绍
2、CISCO ASA 类型:(2)CISCO ASA 5510
两种授权方式:base model and security plus model ► 高度 :1U ► maximum throughput :300Mb/s ► maximum connections : 50,000(130,000 security plus) ► maximum 3Des/AES throughput :170Mb/s ► maximum VPN session :250 ► maximum SSL VPN session : default 2 ► security context :0/0 (base) ; 2/5 (security plus) ► VLANS: 50 (100 security plus) ► high availability : base not support ( security plus A/A A/S) ► interface :5 fast Ethernet ports
6
3、Stateful packet filtering (状态化包过滤)
• 硬件防火墙主流技术,为穿越TCP和UDP流维护状态化表现
7
二、DMZ
• 1、 Demilitarized zone(非军事化区域),主要用于连接服务器和VPN 设备 • 2、 DMZ 连接的两种方式:
8
二、DMZ
• 3、 一种典型的FW连接方式:
• (1)highly flexble and extensible modular security policy framework (MPF) • (2)robust VPN services for secure stie-to-site and remote-access connections(IPSEC VPN) • (3)clientless and client-based secure sockets layer (SSL) VPN ( SSL VPN)
单击此处编辑母版标题样式 防火墙
2010年4月
1
一、防火墙的三种类型
• 1、Packet filtering (包过滤) • 2、Proxy server (代理服务器) • 3、Stateful packet filtering (状态化包过滤)
2
1、Packet filtering (包过滤)
• 访问控制列表A
3
2、Proxy server (代理服务器)
特点: • 两个TCP 会话 • 性能低下 • 支持的运用很少 (http/https/ftp) • 工作在OSI模型最高层,是最安全的防火墙
4
2、Proxy server (代理服务器)
• 软件防火墙的主流技术,经常为web流量使用代理服务器
21
五、 Security level
2、流量示意图:
22
五、 Security level
3、配置接口1: • (1)配置主机名:Ciscoasa(config)# hostname ASAFW • (2)配置Ethernet 0/0
ASAFW (config)# interface ethernet 0/0 ASAFW (config)# ip address 202.100.1.10 255.255.255.0 ASAFW (config)# nameif outside ASAFW (config)# no shutdown
23
五、 Security level
• (3)配置Ethernet 0/1
ASAFW(config)# interface e0/1 ASAFW(config)# no shutdown ASAFW(config) # interface e0/1.3 ASAFW(config-subif)# vlan 3 ASAFW(config-subif)# nameif inside ASAFW(config-subif)# ip address 10.1.1.10 255.255.255.0 ASAFW(config-subif)# interface e0/1.4 ASAFW(config-subif)# vlan 4 ASAFW(config-subif)# nameif MDZ ASAFW(config-subif)# security-level 50 ASAFW(config-subif)# ip address 192.168.1.10 255.255.255.0
5
3、Stateful packet filtering (状态化包过滤)
特点: • 为每一个TCP和UDP流维护stateful session flowe table(状体 化表项) • 返回数据包首先查询状态化表项,如果是以前连接的一部分, 就算被ACL拒绝也可以穿越防火墙 • 状态化表项维护: TCP源目端口,源目IP,序列号。Flag位 • 性能高,硬件防火墙的主流技术
17
三、CISCO ASA 产品介绍
2、CISCO ASA 类型:(5)其他
► CISCO ASA 5550 ► CISCO ASA 5580
18
四、 Service modules
• (1)ASA 可以使用Security Services Module (SSM) 扩展功能和特性。 SSM能够安装在5510 / 5520/ 5540 • (2)ASA 支持下列三种模块: ► Advanced inspection and prevention security services module (AIP SSM) (IPS模块) ► content security and control security services module (CSC SSM) ( 防病毒、URL过滤、防垃圾邮件) ► 4-Port Gigabit Ethernet SSM • (3) PIX 与 ASA区别: ► SSL VPN ► SSM ► VPN clustering and load balancing
9
三、CISCO ASA 产品介绍
1、CISCO ASA 特性介绍:( 一 )
• (1)state-of-art stateful packet inspection firewall (状态监控包过滤) • (2)user-based authentication of inbound and outbound connections (cut-through)
11
三、CISCO ASA 产品介绍
1、CISCO ASA 特性介绍:( 三)
• (1)multiple security contexts (vitual firewalls) within a single appliance( 多模式防火墙)
• (2)stateful active/active or active/standby failover capabilities that ensure resilient network protection (FO)
• (3)intergrated protocol and application inspection engines that examine packet streams at layers 4 through 7 (运用层过滤)
10
三、CISCO ASA 产品介绍
1、CISCO ASA 特性介绍: (二)
15
三、CISCO ASA 产品介绍
2、CISCO ASA 类型:(3)CISCO ASA 5520
► 高度 :1U ► maximum throughput :450Mb/s ► maximum connections : 280,000 ► maximum 3Des/AES throughput :225Mb/s ► maximum VPN session : 750 ► ssl vpn session : default 2 ( 10/25/50/100/250/500 or 750) ► security context :default 2 up to 20 ► VLANs :150 ► High availability : A/A A/S ► scalability : VPN clustering and load balancing ► interface : 4Gigabit Ethernet and 1 fast Ethernet
16
三、CISCO ASA 产品介绍
2、CISCO ASA 类型:(4)CISCO ASA 5540
► maximum throughput :650Mb/s ► maximum connections :400,000 ► maximum 3Des/AES throughput : 325Mb/s ► maximum VPN session :5000 ► SSL VPN session :default 2(10/25/50/100/250/500/750/1000/2500) ► security context : default ,up to 50 ► VLANs: 200 ► high Availability : A/A A/S ► scalability : vpn clustering and load balancing ► interface : 4 Gigabit Ethernet and 1 Fast Ethernet
