2015_A high capacity data hidingalgorithm for H_264_AVC video
Dahuasecurity DSS7016D-S2产品说明书
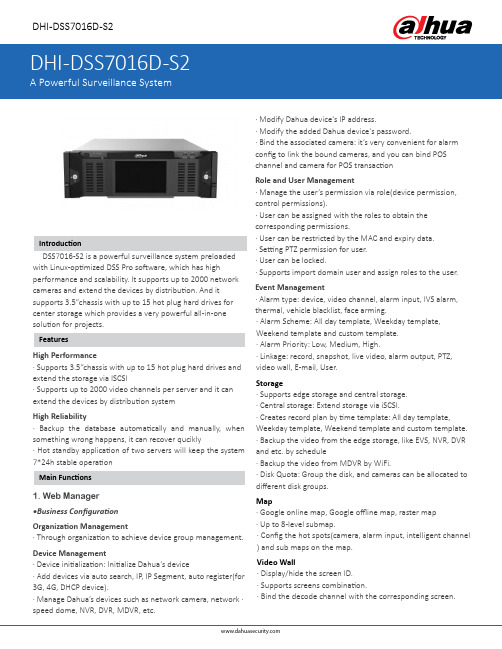
DHI-DSS7016D-S2· Modify Dahua device's IP address.· Modify the added Dahua device's password.· Bind the associated camera: it’s very convenient for alarm config to link the bound cameras, and you can bind POS channel and camera for POS transactionRole and User Management· Manage the user’s permission via role(device permission,control permissions).· User can be assigned with the roles to obtain the corresponding permissions.· User can be restricted by the MAC and expiry data.· Setting PTZ permission for user.· User can be locked.· Supports import domain user and assign roles to the user.Event Management· Alarm type: device, video channel, alarm input, IVS alarm,thermal, vehicle blacklist, face arming.· Alarm Scheme: All day template, Weekday template,Weekend template and custom template.· Alarm Priority: Low, Medium, High.· Linkage: record, snapshot, live video, alarm output, PTZ,video wall, E-mail, User.Storage· Supports edge storage and central storage.· Central storage: Extend storage via iSCSI.· Creates record plan by time template: All day template,Weekday template, Weekend template and custom template.· Backup the video from the edge storage, like EVS, NVR, DVR and etc. by schedule· Backup the video from MDVR by WiFi.· Disk Quota: Group the disk, and cameras can be allocated to different disk groups.Map· Google online map, Google offline map, raster map · Up to 8-level submap.· Config the hot spots(camera, alarm input, intelligent channel ) and sub maps on the map.Video Wall· Display/hide the screen ID.· Supports screens combination.· Bind the decode channel with the corresponding screen.with Linux-optimized DSS Pro software, which has highperformance and scalability. It supports up to 2000 network cameras and extend the devices by distribution. And it supports 3.5”chassis with up to 15 hot plug hard drives for center storage which provides a very powerful all-in-oneHigh Performance· Supports 3.5”chassis with up to 15 hot plug hard drives and extend the storage via ISCSI· Supports up to 2000 video channels per server and it can extend the devices by distribution systemHigh Reliability· Backup the database automatically and manually, when something wrong happens, it can recover qucikly· Hot standby application of two servers will keep the system1. Web Manager •Business ConfigurationOrganization Management· Through organization to achieve device group management.Device Management· Device initialization: Initialize Dahua's device· Add devices via auto search, IP , IP Segment, auto register(for 3G, 4G, DHCP device).· Manage Dahua’s devices such as network camera, network ·speed dome, NVR, DVR, MDVR, etc.DHI-DSS7016D-S2Face Database· Face library management.· Adding face one by one · Import faces in batches· Set person type for face, you can add person type by yourself.· Send face library to face recognition devices, and config the similarity.Vehicle Blacklist· Vehicle Blacklist management· Vehicle blacklist arming and disarming · Import and export vehicle blacklistAverage Speed· Location configuration· Region configuration(Start location, end location, length,minimum speed, max speed)Store Management · Config store layout· Config the resources to the store· Config the store location to get weather information.•System MaintenanceBackup and Restore· Automatically backup system database (daily, week, month).· Manually backup system database.· Restore system database from server or local file.System Dashboard· Overview and detail system information.· Running Status: CPU, storage, bandwidth.· Service, device and user online information, device health report.· Event Information Statistics: total events and processed · Source Information: Video channel, alarm channel.Log· System, admin, client log.· Search and export log.Other Functions · Supports https· Device time calibration· Setting log, alarm info, POS data, heatmap storage time Service Management · Delete the slave server· Enable and disable slave server 2. Control ClientLive View· Displays device tree. Show/hide offline device.· Displays the device IP address or device name on the device tree· View real-time video.· Common layout (1,4,6,8,9,13,16,20,25,36,64 ) and customized layout.· PTZ control · Electric focus· Manual recording(store on PC or central storage)· Snapshot· Instant playback · Digital zoom· Fisheye dewarping· Fisheye and speed dome smart tracking · Smart tracking for panoramic camera.· Audio talk· Set alarm window· Quickly decode the video to video wall.· Turn on/off the audio in live view· Region of interest: Divide one window into 4 or 6 parts, one shows whole image, others show the detail.· Display map in Live View· Save the current live view as a view.· Up to 4 Live View tabs.· Supports adding channel to favorite· Video tour by device, Org, Favorite, View.· Quickly switch to playback.· Supports NKB1000 to control camera on Live View · POS transaction overlay · Set POS overlay style · Adjust the video image· Adjust the display mode(full screen and original)Playback· Replay from the front-end devices or central storage · Video filter: normal, motion, alarm · Sync play· Reverse playback· Slow and fast forward (up to 64X and 1/64X)· Playback frame-by-frame· Lock or mark the important record for central storage.· Download the video, supports avi, dav, flv, mp4, asf.· Decode the video to video wall.· Fisheye dewarping · Adjust the video image · Snapshot· Quickly switch to live view· Adjust the display mode(full screen and original)· Common layout (1,4,6,8,9,13,16,20,25,36 ) and custom layoutDHI-DSS7016D-S2Download Center· Download record from central storage or device, supports avi, dav, flv, mp4, asf.· Download record by timeline, files or tags.· Supports multi-task download.Event· Real-time and history alarm info.· Alarm detail info, like live video, record and pictures from related camera, alarm source location on the map.· Acknowledge the alarm.· Arming control for alarm source · Forwards the alarm to relevant user· Manually send alarm email to relevant person· Search alarm by alarm source, alarm time, status, handle user, priority.· Search alarm events and export the alarm list.Video Wall· Decode the real-time video to wall · Manually/automatically decode to wall.· Manage the video wall split· Change the stream type of video channel.· Adding box, turning on/off screen and getting the video stream to control client· Tour the video channel in one screen.· Schedule plan: Setting the running task on timeline.· Tour plan: looping different tasks, and each task has duration time.· Supports NKB1000 to control video wall.Map· View the live video and playback on the map· Supports the area or length calculating for GIS map· Supports visible range and initial angle(only available for part PTZ model ).· Alarm source turns red and flickers on the map when alarm occurs.People Counting· People counting: Provides daily, weekly, monthly, yearly reports.· Heatmap· Exports the people counting and heatmap data.Face Recognition· Automatically captures faces in the camera field of view · Extracts face attribute information from captured face.· Real-time face comparison· Quickly register face to face library · Searching face via face attribute· Searching face via uploading a face image · Searching comparison records.· Generate the track for the specific face· Generate daily, weekly, monthly attribute report based on the gender and ageANPR· Real-time license plate recognition · Vehicle passed record· Generates vehicle trajectory based on license plate and time info.· Search arming record Other functions · GPU decoding· Connect NKB via USB 3. Mobile ClientHistory Record· Show recently viewed channels, you can open live video or playback via history records.· Up to 20 history records, then replace the oldest operation record.Live View· Open more than one channel at same time, up to 16channels· Three stream type: HD(high definition), SD(standard definition), FL(Fluency)· Supports PTZ control· Supports horizontal screen play · One-key switch to playback· Snapshot, local record, audio talkPlayback· Replay device record and center record(Up to 8X and 1/8X)· The calendar shows whether there is a video on that day · Supports Snapshot· Manually do local record· Supports 1X, 2X, 3X, 4X, 1/2X, 1/4X, 1/8X playback Alarm Centre· Subscribe the alarm · Alarm processing· Alarm video and alarm picture · Alarm searchMap· Supports Google map· Displays the video channel on the map · View video and do playback.Favorite· Quickly view video of channel added to the favorite Files Management· View picture and video via local fileDHI-DSS7016D-S2*1 The maximum number when add only video devices*2 The maximum number when add only POS devicesDHI-DSS7016D-S21- Power Button 4- Network Light 2- Hard Device Light 5- USB 2.03- Alarm Light 6- Lock1- Power Interface 5- Audio Input/Output 2- RS485 6- VGA3- Giga Lan Port 1~4 7- HDMI Port 1~34- SAS 8- RESET(Reserve)Rev 001.001© 2016 Dahua . All rights reserved. Design and specifications are subject to change without notice.。
海康威视 DS-AT1000S 432系列存储系统介绍说明书

IntroductionDS-AT1000S/432 series storage system is a storageproduct with huge capacity and high-density design. A4U chassis provides up to 432 TB capacity. Compared togeneral storage product, DS-AT1000S reduces the totalcost at up to 50%. iRAID technology realizes an intensivemanagement for storage space and data, and protectsthe data security from substructure. Support periodicHDD replacement, which guarantees the product availability.Key FeatureHuge Capacity and High Density● A 4U chassis provides up to 432 TB capacity●High-density design reduces the installation space requirement and transportation costLow consumptionFor 18 TB enterprise HDD, lower consumption for each terabyte at 50%Security and Reliability●iRAID technology and N + M redundant mechanism allow up to 2 error HDDs in a single RAID●HDD encryption technology protects data security by only allowing Hikvision device to read the data in HDD Maintenance-Free●Rebuild fault HDD on-demand●HDD periodic automatic replacementStream Data Management Structure of High PerformanceBased on the bottom layer management structure of the stream media, it solves the problem that the damaged file system will lead to file unreadability or loss and ensures no file fragments will be produced during overwriting Direct Storage of Mixed Stream●Supports mixed storage of video stream and SMART stream●Supports camera access through protocols including RTSP, ONVIF, etc.iRAIDErasure encoding and iRAID technologies ensure data integrity even when 2 HDDs in a single RAID are failed. If the number of error HDD exceeds redundant limit, other HDDs can still be read and writtenAbundant Application●Continuous recording, manual recording, and alarm recordingUser-Friendly Operation and Maintenance●Supports one-key configuration to improve system configuration efficiency●Raises device maintenance efficiency via abundant alarm management methods, like alarm via indicators,and emails.Specification Model DS-AT1000S/432Performance Video (2 Mbps stream + rebuilding)400-chController Processor64-bit multi-core processor Cache16 GB, extendable to 32 GBStorage HDD slot24 (the device is packaged with 24 HDDs) Interface SATACapacity Up to 18 TB per HDDRAID iRAID, RAID5, RAID6Disk Disk detection pre-alarm and repair Logical volume Recording volume managementRecording Recording type Continuous recording, manual recording, and alarm recordingVideo protection Video loss alarmSearch and downloadLog in storage system to search, play, and download videos. Supportsearching videos by time, and event typeMaintenance and Management Management method GUI based on web, serial port CLI, platform Alarm method Audio, indicator, GUINetwork Protocol RTSP, ONVIF, HKSDKExternal interface Data network interface4, 1000 Mbps Ethernet interfaceManagement networkinterface1, 1000 Mbps Ethernet interfaceSAS interface1COM interface1, RS-232USB interface 2 × USB 3.0, 2 × USB 2.0VGA interface Supported (VGA and RS-232 interface cannot be used at the same time) IPMI interface SupportedGeneral Power supply100 to 240 VAC/47 to 63Hz, redundant power supply Power consumption(with HDDs)≤ 369.8 WEnvironmenttemperature●Working: 5 °C to 40 °C (41 °F to 104 °F)●Storing: -20 °C to +70 °C (-4 °F to +158 °F) Environment humidity●Working: 20% to 80% RH (non-condensing/frozen)●Storing: 5% to 90% RH (non-condensing/frozen) Dimensions (W × D × H)445 ×175 × 746 mm (17.5 × 6.9 × 29.4 inch)Weight (without HDDs)≤ 40 kg (88.2 lb)Physical InterfaceNo. Name No. Name 1 Power module 1 8 SAS interface2 COM interface 9 Data network interface3 3 Two USB interfaces 10 Management network interface4 Two USB interfaces 11 Power module 25 Data network interface 1 12 IPMI6 Data network interface 2 13 Data network interface 4 7VGA interfaceAvailable Model DS-AT1000S/432。
Oracle Server X9-2L 数据表说明书

Oracle Server X9-2LOracle Server X9-2L is the ideal 2U platform for databases, enterprise storage, and big data solutions. Supporting the standard and enterprise editions of Oracle Database, this server delivers best-in-class database reliability in single-node configurations. With support for up to 132.8 TB of high-bandwidth NVM Express (NVMe) flash storage, Oracle Database using its Database Smart Flash Cache feature, as well as NoSQL and Hadoop applications can be significantly accelerated. Optimized for compute, memory, I/O, and storage density simultaneously, Oracle Server X9-2L delivers extreme storage capacity at lower cost when combined with Oracle Linux, or Oracle Solaris with ZFS file system compression. Each server comes with built-in, proactive fault detection and advanced diagnostics, along with firmware that is already optimized for Oracle software, to deliver extreme reliability.Product OverviewOracle Server X9-2L is a two-socket server designed and built specifically for the demands of enterprise workloads. It is a crucial building block in Oracle engineered systems and Oracle Cloud Infrastructure. Powered by one Platinum, two Gold, or one Silver Intel® Xeon® Scalable Processor Third Generation models with up to 32 cores per socket, along with 32 memory slots, this server offers high-performance processors plus the most dense flash storage options in a 2U enclosure. Oracle Server X9-2L is the most balanced and highest performing 2U enterprise server in its class because it offers optimal core and memory density combined with high I/O throughput.In addition to optimized processing power and storage density, Oracle ServerX9-2L offers 10 PCIe 4.0 expansion slots (two 16-lane and eight 8-lane) for maximal I/O card and port density. With 576 gigabytes per second of bidirectional I/O bandwidth, Oracle Server X9-2L can handle the most demanding enterprise workloads.Oracle Server X9-2L offers best-in-class reliability, serviceability, and availability (RAS) features that increase overall uptime of the server. This extreme reliability makes Oracle Server X9-2L the best choice for single-node Oracle Database deployments in remote or branch office locations. Real-time monitoring of the health of the CPU, memory, and I/O subsystems, coupled with off lining capability of failed components, increases the system availability. Building on the firmware-level problem detection, Oracle Linux and Oracle Solaris are enhanced to provide fault detection capabilities when running on Oracle Server X9-2L. In Key FeaturesMost flash-dense andenergy-efficient 2Uenterprise-class serverTwo Intel® Xeon® Scalable Processor Third GenerationCPUsThirty-two DIMM slots with maximum memory of 2 TB Ten PCIe Gen 4 slotsUp to 216 TB SAS-3 disk storage in 12 slots instandard configurationsUp to 132.8 TB NVM Express high-bandwidth all-flashconfigurationOracle Integrated Lights Out Manager (ILOM)Key BenefitsReduce vulnerability tocyberattacksAccelerate Oracle Database, NoSQL, and Hadoopapplications using Oracle’sunique NVM Express design Satisfy demands ofenterprise applications withextreme I/O card densityIncrease uptime with built-in diagnostics and faultdetection from Oracle Linuxand Oracle SolarisIncrease storage capacity 15x compared to previousgeneration, combiningextreme compute power with Oracle Solaris and ZFScompressionMaximize system power efficiency with OracleAdvanced System CoolingMaximize IT productivity by running Oracle software onOracle hardwareaddition, exhaustive system diagnostics and hardware-assisted error reporting and logging enable identification of failed components for ease of service.To help users achieve accelerated performance of Oracle Database, Oracle Server X9-2L supports hot-swappable, high-bandwidth flash that combines with Database Smart Flash Cache to drive down cost per database transaction. In the all-flash configuration, with Oracle’s unique NVM Express design, Oracle Server X9-2L supports up to 12 small form factor NVMe drives and up to eight NVMe add-in cards, for a total capacity of 132.8 TB. This massive flash capacity also benefits NoSQL and Hadoop applications, reducing network infrastructure needs and accelerating performance with 120 GB per second of total NVMe bidirectional bandwidth.For maximizing storage capacity, Oracle Server X9-2L is also offered in a standard 12-disk configuration, with 3.5-inch large form factor disk slots accommodating high-capacity hard disk drives (HDDs). A maximum 216 TB of direct-attached storage makes Oracle Server X9-2L ideally suited as a storage server. The compute power of this server can be used to extend storage density even further with Oracle Solaris and ZFS file system compression to achieve up to 15x compression of data without significant performance impact. Oracle Server X9-2L is also well suited for other storage-dense implementations, such as video compression and transcoding, which require a balanced combination of compute power and storage capacity at the same time.Oracle Server X9-2L ships with Oracle ILOM 5.0, a cloud-ready service processor designed for today's security challenges. Oracle ILOM provides real-time monitoring and management of all system and chassis functions as well as enables remote management of Oracle servers. Oracle ILOM uses advanced service processor hardware with built-in hardening and encryption as well as improved interfaces to reduce the attack surface and improve overall security. Oracle ILOM has improved firmware image validation through the use of improved firmware image signing. This mechanism provides silicon-anchored service processor firmware validation that cryptographically prevents malicious firmware from booting. After Oracle ILOM's boot code is validated by the hardware, a chain of trust allows each subsequent firmware component in the boot process to be validated. Finally, with a focus on security assurance, using secure coding and testing methodologies, Oracle is able to maximize firmware security by working to prevent and remediate vulnerabilities prior to release. With advanced system cooling that is unique to Oracle, Oracle Server X9-2L achieves system efficiencies that result in power savings and maximum uptime. Oracle Advanced System Cooling utilizes remote temperature sensors for fan speed control, minimizing power consumption while keeping optimal temperatures inside the server. These remote temperature sensors are designed into key areas of this server to ensure efficient fan usage by organizing all major subsystems into cooling zones. This technology helps reduce energy consumption in a way that other servers cannot.Oracle Premier Support customers have access to My Oracle Support and multi-server management tools in Oracle Enterprise Manager, a critical component that enables application-to-disk system management including servers, virtual Key ValueOracle Server X9-2L is the most storage-dense, versatile two-socket server in its class for the enterprise data center, packing the optimal balance of compute power, memory capacity, and I/O capacity into a compact and energy-efficient 2U enclosure. Related productsOracle Server X9-2Oracle Server X8-8Related servicesThe following services are available from Oracle Customer Support:SupportInstallationEco-optimization servicesmachines, databases, storage, and networking enterprise wide in a single pane of glass. Oracle Enterprise Manager enables Exadata, database, and systems administrators to proactively monitor the availability and health of their systems and to execute corrective actions without user intervention, enabling maximum service levels and simplified support.With industry-leading in-depth security spanning its entire portfolio of software and systems, Oracle believes that security must be built in at every layer of the IT environment. In order to build x86 servers with end-to-end security, Oracle maintains 100 percent in-house design, controls 100 percent of the supply chain, and controls 100 percent of the firmware source code. Oracle’s x86 servers enable only secure protocols out of the box to prevent unauthorized access at point of install. For even greater security, customers running Oracle Ksplice on Oracle’s x86 servers will benefit greatly from zero downtime patching of the Oracle Linux kernel.Oracle is driven to produce the most reliable and highest performing x86 systems in its class, with security-in-depth features layered into these servers, for two reasons: Oracle Cloud Infrastructure and Oracle Engineered Systems. At their foundation, these rapidly expanding cloud and converged infrastructure businesses run on Oracle’s x86 servers. To ensure that Oracle’s SaaS, PaaS, and IaaS offerings operate at the highest levels of efficiency, only enterprise-class features are designed into these systems, along with significant co-development among cloud, hardware, and software engineering. Judicious component selection, extensive integration, and robust real-world testing enable the optimal performance and reliability critical to these core businesses. All the same features and benefits available in Oracle’s cloud are standard in Oracle’s x86 standalone servers, helping customers to easily transition from on-premises applications to cloud with guaranteed compatibility and efficiency.Oracle Server X9-2L System SpecificationsCache•Level 1: 32 KB instruction and 32 KB data L1 cache per core•Level 2: 1 MB shared data and instruction L2 cache per core•Level 3: up to 1.375 MB shared inclusive L3 cache per coreMain Memory•Thirty-two DIMM slots provide up to 2 TB of DDR4 DIMM memory•RDIMM options: 32 GB or 64 GB at DDR4-3200 dual rankInterfaces Standard I/O•One 1000BASE-T network management Ethernet port•One 1000BASE-T host management Ethernet port•One RJ-45 serial management port•One rear USB 3.0 port•Expansion bus: 10 PCIe 4.0 slots, two x16 and eight x8 slots•Supports LP-PCIe cards including Ethernet, FC, SAS and flashStorage•Twelve 3.5-inch front hot-swappable disk bays plus two internal M.2boot drives•Disk bays can be populated with 3.5-inch 18 TB HDDs or 2.5-inch 6.8 or 3.84 NVMesolid-state drives (SSDs)•PCIe flash•Sixteen-port 12 Gb/sec RAID HBA supporting levels: 0, 1, 5, 6, 10, 50, and 60 with 1GB of DDR3 onboard memory with flash memory backup via SAS-3 HBA PCIe cardHigh-Bandwidth Flash•All flash configuration—up to 132.8 TB in the all-flash configuration (maximum of12 hot-swappable 6.8 TB NVMe SSDs and eight 6.4 TB NVMe PCIe cards)NVMe functionality in 3.5-inch disk bays 8-11 requires an Oracle NVMeretimer that is installed in PCIe slot 10Systems Management Interfaces•Dedicated 1000BASE-T network management Ethernet port (10/100/1000 Gb/sec)•One 1000BASE-T host management Ethernet port (10/100/1000 Gb/sec)•In-band, out-of-band, and side-band network management access•One RJ-45 serial management portService ProcessorOracle Integrated Lights Out Manager (Oracle ILOM) provides:•Remote keyboard, video, and mouse redirection•Full remote management through command-line, IPMI, and browser interfaces•Remote media capability (USB, DVD, CD, and ISO image)•Advanced power management and monitoring•Active Directory, LDAP, and RADIUS support•Dual Oracle ILOM flash•Direct virtual media redirection•FIPS 140-2 mode using OpenSSL FIPS certification (#1747)Monitoring•Comprehensive fault detection and notification•In-band, out-of-band, and side-band SNMP monitoring v2c and v3•Syslog and SMTP alerts•Automatic creation of a service request for key hardware faults with Oracleautomated service request (ASR)Oracle Enterprise Manager•Advanced monitoring and management of hardware and software•Deployment and provisioning of databases•Cloud and virtualization management•Inventory control and patch management•OS observability for performance monitoring and tuning•Single pane of glass for management of entire Oracle deployments, including onpremises and Oracle CloudSoftware Operating Systems•Oracle Linux•Oracle SolarisVirtualization•Oracle KVMFor more information on software go to: Oracle Server X9-2L Options & DownloadsOperating Environment •Ambient Operating temperature: 5°C to 40°C (41°F to 104°F)•Ambient Non-operating temperature: -40°C to 68°C (-40°F to 154°F)•Operating relative humidity: 10% to 90%, noncondensing•Non-operating relative humidity: up to 93%, noncondensing•Operating altitude: Maximum ambient operating temperature is derated by 1°C per 300 m of elevation beyond 900 m, up to a maximum altitude of 3000 m•Non-operating altitude: up to 39,370 feet (12,000 m)•Acoustic noise-Maximum condition: 7.1 Bels A weightedIdle condition: 7.0 Bels A weightedConnect with usCall +1.800.ORACLE1 or visit . Outside North America, find your local office at: /contact. /oracle /oracleCopyright © 2023, Oracle and/or its affiliates. All rights reserved. This document is provided for information purposes only, and the contents hereof are subject to change without notice. This document is not warranted to be error-free, nor subject to any other warranties or conditions, whether expressed orally or implied in law, including implied warranties and conditions of merchantability or fitness for a particular purpose. We specifically disclaim any liability with respect to this document, and no contractual obligations are formed either directly or indirectly by this document. This document may not be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without our prior written permission.This device has not been authorized as required by the rules of the Federal Communications Commission. This device is not, and may not be, offered for sale or lease, or sold or leased, until authorization is obtained.Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners.Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. AMD, Opteron, the AMD logo, and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices. UNIX is a registered trademark of The Open Group. 0120Disclaimer: If you are unsure whether your data sheet needs a disclaimer, read the revenue recognition policy. If you have further questions about your content and the disclaimer requirements, e-mail ********************.。
XenDesktop 7.7 - 微软价值合作篇深入解析

18
© 2015 Citrix
Exchange Online
Benefits
Description
Online Mode
Constant network connection to Exchange
Cached Exchange Mode
Creates local copy of Exchange mailbox
6 © 2015 Citrix
Better End User Experience
Extending HDX Technology
What’s New
• • • • • • • • FrameHawk & ThinWire+ Instant App Access HTML5 client Accelerated graphics performance Improved USB Integration Virtual IP loopback HDX Mobile SDK v2 HDX RealTime Optimization Pack for Lync/Skype
Universal Print Server
Driver
Network Printer
16
© 2015 Citrix
Optimized printing for all devices
90 80 70
Megabytes Transmitted
Universal Print Driver
• Compresses print job across wire • Simplifies management of XenApp VMs
Extend RDS and VDI with XenApp and XenDesktop
美格尔新产品:DC电阻捕捉仪MIT515、MIT525、MIT1025和MIT1525说明书

DESCRIPTIONMegger’s new range of DC insulation testers MIT515, MIT525,MIT1025 and MIT1525 are targeted at original equipment manufacturers and industrial companies. The top of the rangeMIT1525 performs insulation resistance tests up to 15 kV with a30 TΩ maximum resistance and an accuracy of ±5 % from 1 MΩup to 3 TΩ. The MIT515 offers IR, DAR and PI functions but has no memory functionality. MIT525, MIT1025 and MIT1525 have a full suite of test modes as well as on-board memory and the ability to stream data/download data to a PC/laptop. Instrument productivity is a focus of the new MIT range which offers rapid charge batteries and operation from an AC source if the batteries are flat. Rapid charge batteries enable > 60 minutes testing after a 30 minute charge.MIT515: 5 kV IRT with PI and DAR but no memoryMIT525: 5 kV IRT with all test modes including a ramp test plus advanced memory functions with recall to screen, RTC for time/dat stamp of results and USB cable interface to PC/PowerDBMIT1025: 10 kV IRT with all test modes including a ramp test plus advanced memory functions with recall to screen, RTC for time/dat stamp of results and USB cable interface to PC/PowerDBMIT1525: 15 kV IRT with all test modes including a ramp test plus advanced memory functions with recall to screen, RTC for time/dat stamp of results and USB cable interface to PC/PowerDBSafety rating is not compromised on the MIT range with all terminals safety rated to CAT IV 600 V to 3000 m (5 kV, 10 kV) or CAT IV 1000 V to 3000 m (15 kV). A range of 5 kV and 10 kV test leads are available plus dedicated 15 kV test leads which are double insulated with clips designed for 15 kV creepage paths. The 15 kV leads are supplied in a holdall. Suitably rated HV gloves and other personal protection equipment are required to be worn when testing.The MIT range share dual case design which includes a tough outer case to protect the tester from knocks/drops and an inner fire retardant case. The IP rating is IP 65 case closed eliminating moisture and dust ingress.An intuitive user interface ensures no lost time remembering how to use the tester. Simplicity of operation is achieved with two rotary switches and the large backlight display which enables multiple results to be displayed simultaneously. A graphical quick start guide is provided inside the lid to assist first time users.Five preset voltage ranges are provided in insulation test mode, plus a user settable lock voltage range. Preconfigured diagnostic tests include Polarisation Index (PI), Dielectric Absorption Ratio (DAR), dielectric discharge (DD), Stepped Voltage (SV) and ramp test. Advanced memory storage includes time/date stamping of results, logging of data and recall of results to screen. A fully isolatedUSB interface is used for safe transfer of data to Megger’s asset management software; PowerDB Pro, Advanced and Lite packages.Test leads are double insulated t with clamps rated at 3 kV t equivalent to 6 kV single insulation for the medium clip leadset and 5 kV t equivalent to 10 kV single insulation for the large clip. The 15k V leadset is insulated to 15 kV.Advanced memory storage includes time/date stamping of results, logging of data and recall of results to screen. A fully isolated USBMIT515, MIT525, MIT1025, MIT15255 kV, 10 kV, 15 kV DC Insulation Resistance TestersMIT515, MIT525, MIT1025, MIT15255 kV, 10 kV, 15 kV DC Insulationresistance testers■■Measures up to 30 TΩ■■Safety rated up to CAT IV 1000 V to 3000 m■■Unique dual-case design - additional userprotection■■Operates from battery or AC mains supply■■Rapid charge Li-ion battery■■Advanced memory with time/date stampdevice interface (type B) is used for safe transfer of data to Megger’s PowerDB / Pro, Advanced and Lite asset management software. (MIT525, MIT1025 nd MIT1525 only)APPLICATIONThe Insulation Resistance (IR) test is a quantitative test which indicates the effectiveness of a product’s electrical insulation. Applications include cables, transformers, motors/generators, circuit breakers and bushings. Common insulation tests are the “spot test”, a 1 minute IR test and a 10 minute Polarisation Index (PI) test, where PI is the ratio R10min / R1min and is temperature independent.FEATURES AND BENEFITS■■Insulation resistance up to 30 TΩ @ 15 kV , 20 TΩ @ 10kV , 10 TΩ@ 5 kV■■IR, Timed IR, DAR, PI, DD, SV and ramp diagnostic tests ■■High current – 3 mA short circuit current■■High noise immunity – 3 mA (5 kV and 10 kV) 6 mA (15 kV) ofnoise rejection■■Li-ion battery – up to 6 hrs continuous testing @ 5 kV with a100M load, battery meets IEC 2133■■Safety rating: CAT IV 600 V to 3000 m (5 kV , 10 kV) CAT IV 1000V to 3000 m (15 kV)■■Large LCD display with backlight■■Dedicated voltmeter function (30 V to 660 V)■■Advanced memory, on screen recall and real time clock for date/time stamped results (MIT525, MIT1025 and MIT1525 only)■■Download of on-board results via USB interface (MIT525,MIT1025 and MIT1525 only)■■Recorded temperature (measured by independent instruments)can be saved with test result (MIT525, MIT1025 and MIT1525 only)■■PowerDB Lite asset management software supplied (MIT525,MIT1025 and MIT1525 only)■■MIT515, MIT525 and MIT1025 safety rated at CAT IV 600 V(maintained to 3000 m altitude)■■MIT1525 safety rated at CAT IV 1000 V (maintained to 3000 maltitude)SPECIFICATIONSAC voltage (auto-ranging)5 kV , 10 kV: 90-264 V rms, 47- 63 Hz 100 VA15 kV: 90-264 V rms, 47- 63 Hz 200 VABattery charge time 2.5 hours deep discharge, 2 hours normal dischargeBattery life11.1 V , 5.2Ah Li-ion batteries, meet IEC 62133:2003, MIT1525 has 2 battery packsBattery life MIT515, MIT525: 6 hours (typical) continuous testing at 5 kV with a 100 MΩ load Battery life MIT1025: 4.5 hours (typical) continuoust esting at 10 kV with a 100 MΩ load Battery life MIT1525: 4.5 hours (typical) continuous t esting at 15 kV with a 100 MΩ load Test voltageMIT515, MIT525:250 V , 500 V , 1000 V , 2500 V , 5000 V , V L MIT1025:500 V , 1000 V , 2500 V , 5000 V , 10000 V , V L MIT1525:1000 V , 2500 V , 5000 V , 10000 V , 15000 V , V L Lock test voltage100 V L to 1 kV in 10 V steps, 1 kV to 5 kV in 25 V steps, 5 kV to 15 kV in 25 V steps Test voltage accuracy+4%, -0%, ±10 V nominal test voltage at 1 GΩ load (0°C to 30°C)Resistance range10 kΩ to 15 TΩ @ 5 kV , 10 kΩ to 20 TΩ @ 10 kV , 10 kΩ to 30 TΩ @ 15 kVAccuracyMIT515, MIT525 accuracy (23 °C) 5000 V 2500 V 1000 V 500 V250 V±5% from 1MΩ to 1 TΩ 500 GΩ 200 GΩ 100 GΩ 50 GΩ ±20% from 1MΩ to 10 TΩ 5 TΩ 2 TΩ 1 TΩ 500 GΩ MIT1025 accuracy (23 ºC) 10 kV 5000 V 2500 V 1000 V500 V±5% from 1MΩ to 2 TΩ 1 TΩ 500 GΩ 200 GΩ 100 GΩ±20% from 1MΩ to 20 TΩ 10 TΩ 5 TΩ 2 TΩ1 TΩMIT1525 accuracy (23 ºC) 15 kV 10 kV 5000 V 2500 V 1000 V ±5% from 1MΩ to 3 TΩ 2 TΩ 1 TΩ 500 GΩ 200 GΩ±20% from 1MΩ to 30 TΩ20 TΩ10 TΩ5 TΩ2 TΩGuard terminal performanceGuards out parallel leakageresistance down to 250 kΩ with a maximum additional resistance error of 1% with a 100 MΩ load DisplayAnalogue : 100 kΩ to 10 TΩDigital: 10 kΩ to max a above Short circuit/charge current 3 mA @ 5 kV , 10 kV , 15 kV Insulation testAlarm: 100 kΩ to 10 GΩTEST LEADS SUPPLIEDThe MIT515. MIT525, MIT1025 and the MIT1525 are all supplied with test leads that are compliant with the requirements ofIEC61010-031:2008. The 5 kV models are supplied with one 3m lead-set with medium sized clips. The 10 kV models are supplied with two 3m lead-sets, one with medium sized clips and the other with large clips with insulation suited to 10 kV use and the 15 kV models supplied with a 3m lead-set, with large clips with insulation suited to 15 kV use.These leads are designed based on Megger’s extensive knowledge of insulation testing using the latest technology. The leads are in compliance with IEC61010-31:2008 which requires a fully insulated clip design.MEDIUM INSULATED TEST CLIP 3 M X 3 LEADSET - 5 KV AND 10 KVThese test leads are supplied as standard on MIT515, MIT525 and the MIT1025.These clips are designed for clamping on larger diameter test pieces but where space is at a premium.The insulation is designed only to protect the user from the output of Megger 5 kV and 10 kV (set below 6 kV) insulation resistance testers. The clips cannot in any circumstance be relied on to protect the user from live ac systems above 600 V a.c., r.m.s. in an CAT IV environment.Cable insulation rating: 12 kV dc (marked on cable)Cable type: flexible dual insulated silicon (inner insulation layer coloured white tohighlight damageCapacitor chargeMIT515, MIT525 <3 s/μF at 3 mA to 5 kV MIT1025 <5 s/μF at 3 mA to 10 kV MIT1525 <7.5 s/μF at 3 mA to 15 kV Capacitor discharge<120 ms/μF to discharge from 5000 V to 50 V (MIT515 and MIT525)<250 ms/μF to discharge from 10000 V to 50 V (MIT1025)<3500 ms/μF to discharge from 15000 V to 50 V (MIT1525)Capacitance range With test voltage set above 500 VMIT515, MIT525 MIT1025: 10 nF to 25 μF MIT1525: 10 nF to 50 μFCapacitance measurement accuracy ±10% ±5 nF Current range 0.01 nA to 6 mACurrent accuracy ±5% ±0.2 nA at all voltages (23 °C)InterferenceMIT515, MIT525: 3 mA from 450 V to 5 kV MIT1025: 3 mA from 960 V to 10 kV MIT1525: 6 mA from 2100 V to 15 kV Voltmeter range 30 V to 660 V ac or dc, 45Hz – 65Hz Voltmeter accuracy ±3%, ±3VTimer range Up to 99 minutes 59 seconds, 15 second minimum setting Memory capacity5.5 hours logging @ 5 sec intervals(MIT525, MIT1025 and MIT1525 only)Test modesMIT515: IR, IR(t), DAR, PIMIT525, MIT1025 and MIT1525: IR, IR(t), DAR, PI, SV , DD, ramp testInterfaceUSB type B (device)(MIT525, MIT1025 and MIT1525 only)Real time output1 Hz output readings (V , I, R) (MIT525, MIT1025 and MIT1525 only)ENVIRONMENTAL Maximum altitude3000 m (5 kV , 10 kV)3000 m (15 kV)Operating temperature range -20 °C to 50 °C Storage temperature range -25 °C to 65 °CHumidity 90% RH non-condensing at 40 °C IP rating IP65 (lid closed), IP40 (lid open)SAFETYMIT515, MIT525 MIT1025: CAT IV 600 V to 3000 m altitude MIT1525: CAT IV 1000 V to 3000 m altitude Meets the requirements of IEC 61010-1,TEST LEADS SUPPLIED CONT.MEDIUM INSULATED TEST CLIP 3 M X 3 LEADSET - 15 KVThese test leads are supplied as an option on the MIT1525.These clips are designed for clamping on larger diameter test pieces but where space is at a premium.The insulation is designed only to protect the user from the output of Megger 15 kV (set below 6 kV) insulation resistance testers.The clips cannot in any circumstance be relied on to protectthe user from live ac systems above 1000 V a.c., r.m.s. in an CAT IV environment.Cable insulationrating: 15 kV dc(marked on cable)Cable type: flexibledual insulated silicon(inner insulation layercoloured white tohighlight damage These test leads may also be supplied in none standard lengths to suit a particular application.Please contact Megger for a quotation. Minimum order quantities may apply.LARGE INSULATED TEST CLIP 3 M X 3 LEADSET These test leads are supplied as standard on MIT1025 and MIT1525 Models (different leadset dependant on model)These clips are designed for clamping on larger diameter test pieces. The insulation is designed only to protect the user from the output of Megger 5 kV, 10 kV and 15 kV insulation resistance testers.The clips cannot in any circumstance be relied on to protect the user from live ac systems above 600 V a.c., r.m.s. in an CAT IV environment.10 kV lead setCable insulation rating:12 kV dc (marked on cable)Cable type: flexible dualinsulated silicon (innerinsulation layer colouredwhite to highlight damage)15 kV lead setCable insulation rating:18 kV dc (marked on cable)Cable type: flexible dualinsulated silicon (innerinsulation layer colouredwhite to highlight damage) The design of the lead sets is intended to facilitate connectionto a variety of de-energized systems for the purpose of making insulation resistance measurements. In all cases it is the responsibility of the user to employ safe working practices and verify that the system is safe before connection. Even isolated systems may exhibit significant capacitance which will become highly charged during the application of the insulation test. This charge can be lethal and connections, including the leads and clips, should never be touched during the test. The system must be safely discharged before touching connections.DESIGNED FOR EVERYDAY USETest leads are a key component of any precision instrument and that safety, long life, and the ability to provide reliable connections to a variety of test pieces found in everyday applications are of the utmost importance. Megger design test leads for both safety and practical operation.LOCKING HV INSULATED PLUGS/NON-REMOVABLE TEST CLIPSAll Megger 5 kV, 10 kV and 15 kV insulation testing test leads are fitted with unique locking HV plugs and non-removable test clips. This reduces the likelihood of a plug or clip inadvertently losing electrical connection and the capacitance of a long cable remaining lethally charged.With the arrows on the plug finger guard horizontal on the instrument as shown to lock. Twist 90º to to unlock. In addition,for the same reason, the test clips are not removable from the test lead.PRACTICAL INSULATION DESIGNMoving jaw fingers maintain the clips touch proof safety when clip is closed but flex back to allow metal teeth of the clip to contact test piece unimpeded when in use.Megger clip beingtested with IECstandard testfinger for creepageand clearance.PRACTICAL JAW DESIGNCurved jaws allow reliable connection around test piecesand flat jaw tips provide excellent connection and grippingof individual wires.OPTIONAL TEST LEADSMEDIUM AND LARGE TEST CLIPSTest leads above with medium and large size insulated clips are available supplied as an option in 5m, 8m, 10m and 15m lengths. These are listed in the ordering information panel at the endof this data sheet. These test leads may also be suppliedin non-standard lengths to suit a particular application/ requirement. Please contact Megger for a quotation, minimum order quantities may apply.Versions available for all MIT modelsCOMPACT TEST CLIP LEADSThese clips are designed for clamping on test pieces where access is limited. There is no insulation on these clips.Extreme caremust be taken toavoid electric shockwhen connecting/disconnecting dueto the bare metallicclips.Cable insulationrating: 12 kV dc(marked on cable) Cable type: flexible dual insulated silicon (inner insulation layer coloured white to highlight damage)Fits: MIT515, MIT525 and MIT1025COMPACT TEST CLIP WITH 5 OR 10 KV SCREENED CABLEThe clips are designed for clamping on test pieces where access is limited. There is no insulation on these clips. Extreme care must be taken to avoid electric shock when connecting/ disconnecting due to the bare metallic clips.The screened test lead set consists of:■■A black/negative test lead that has been screened.■■A red/positive test lead that is not screened.Cable insulation rating: 5 kV or 10 kV dcCable type: flexible screened PVCNote: Screened test leadsare an important accessoryfor those working in highnoise environments, and/or locations where testlead leakage could be aproblem.Fits: MIT515, MIT525 andMIT1025LARGE TEST CLIP WITH 15 KV SCREENED CABLE Relative motion between unshielded long leads for a D.C. test causes a variation in capacitance between them. This in turn causes very low frequency currents to flow, creating interference with the D.C. being measured. In addition induced current from nearby cables or radiated noise from corona around HV bushings can interfere with measurements causing unstable readings. This can be greatly reduced by using a screened lead set.The screened test lead set consists of:■■A black/negative test lead that has been screened.■■A red/positive test lead that is not screened.Cable insulation rating: 15 kV dcCable type: flexiblescreened PVCNote: Screened test leadsare an important accessoryfor those working in highnoise environments, and/or locations where test leadleakage could be a problem.Fits: MIT1525CONTROL CIRCUIT TEST LEAD SETSThis probe and clip leadset is designed for testing low voltage circuits with test voltages up to 1 kV.The insulation is designed only to protect the user from the outputof Megger 5 kV, 10 kV and 15 kVinsulation resistance testers setto a maximum output voltage of1 kV. Do not use this leadset atvoltages above 1 kV.Cable insulation rating: 1 kV dcFUSED TEST PROBE AND CLIP LEAD SETThis fused probe and clip leadset is designed for testing low voltage circuits with test voltages up to 1 kV. The leadset is GS38 compliant, fitted with FF500mA 50 kA fuses, which allows voltage measurements to be made in safety when using the user selectable voltage measuring range on the MIT515, MIT525, MIT1025 and MIT1525 instruments.The insulation is designed only toprotect the user from the output ofMegger 5 kV and 10 kV insulationresistance testers set to a maximumoutput voltage of 1 kV. Do not usethis leadset at voltages above 1 kV.Cable insulation rating: 1 kVMore detailed information can be found on the 5 kV, 10 kV and 15 kV insulation tester lead sets application note. This document can be downloadedfrom: UKArchcliffe Road Dover CT17 9EN EnglandT +44 (0) 1304 502101 F +44 (0) 1304 207342 ******************UNITED STATES4271 Bronze WayDallas TX 75237-1019 USAT 800 723 2861 (USA only)T +1 214 333 3201F +1 214 331 7399******************OTHER TECHNICAL SALES OFFICESValley Forge USA, College Station USA,Sydney AUSTRALIA, Danderyd SWEDEN,Ontario CANADA, Trappes FRANCE,Oberursel GERMANY, Aargau SWITZERLAND,Kingdom of BAHRAIN, Mumbai INDIA,Johannesburg SOUTH AFRICA, Chonburi THAILANDCERTIFICATION ISORegistered to ISO 9001:2000 Cert. no. Q 09290MIT515--MIT525--MIT1025--MIT1525_DS_en_V06Megger is a registered trademarkDescription Order Code Description Order CodeMIT515-UK 1001-935 MIT515-US 1001-936 MIT515-EU 1001-937 MIT515-AU 1001-938 MIT525-UK 1001-939 MIT525-US 1001-940 MIT525-EU 1001-941 MIT525-AU 1001-942 MIT1025-UK 1001-943 MIT1025-US 1001-944 MIT1025-EU 1001-945 MIT1025-AU 1001-946 MIT1525 UK 1002-907 MIT1525 US 1002-909 MIT1525 EU 1002-908 MIT1525 AU 1002-910Included AccessoriesPower leadUSB cablePowerDB Lite softwareProduct information CDIncluded accessories (5 kV, 10 kV, 15kV)3 m lead set, medium size insulated clips(MIT515 and MIT525 only) 1002-531 3 m leadset x 3, large insulated clips(MIT1025 only) 1002-534 3m leadset x 3, large 15 kV insulated clips(MIT1525 only) 1002-949Optional Accessories 1 kV test lead sets(MIT515, MIT525, MIT1025 only)Fused test probe and clip lead set 1002-913 CONTROL CIRCUIT TEST SET 6220-822Optional accessories – 1 kV test lead sets(MIT1525 only)Fused test lead set with probes and clips(2 x leads, 1.25m) 1005-265 Control circuit test lead set (2 x leads, 3m) 1005-264HV test leads sest (MIT515, MIT525, MIT1025 only)* These test leads may also be supplied in non-standard lengths to suit a particular application / requirement. Please contact Megger for a quotation, minimum order quantities may apply.3 x 5 m with large insulated clips 1002-6453 x 8 with large insulated clips 1002-6463 x 10 m with large insulated clips 1002-6473 x 15 m with large insulated clips 1002-6483 x 5 m with medium insulated clips 1002-6413 x 8 m with medium insulated clips 1002-6423 x 10 m with medium insulated clips 1002-6433 x 15 m with medium insulated clips 1002-644 COMPACT, BARE TEST CLIP: Lead length: 3 m 8101-181 COMPACT, BARE TEST CLIP: Lead length:5 m 8101-182 COMPACT, BARE TEST CLIP: Lead length: 15 m 8101-183HV test lead sets (MIT1525 only)5 m lead set, large size insulated clips (3 x leads) 1005-25910 m lead set, large size insulated clips (3 x leads) 1005-26015 m lead set, large size insulated clips (3 x leads) 1005-2613 m lead set, medium size insulated clips (3 x leads) 1005-26210 m lead set, medium size insulated clips (3 x leads) 1005-263Screened - HV test lead sets(MIT515, MIT525, MIT1025 only)1 x 3 m, wtih 5 kV screened un-insulatedsmall clips 6220-8351 x 15 m, with 5 kV screened un-insulatedsmall clips 6311-0803 m, 10 kV screened un-insulated small clips 6220-83410 m, 10 kV screened un-insulated small clips 6220-86115 m, 10 kV screened un-insulated small clips 6220-833Screened HV test lead sets (MIT1525 only)3 m, 15 kV screened, large size insulated clips,supplied in carry holdall 1005-26610 m, 15 kV screened, large size insulated clips,supplied in carry holdall 1005-26715 m, 15 kV screened, large size insulated clips,supplied in carry holdall 1005-26820 m, 15 kV screened, large size insulated clips,supplied in carry holdall 1005-269OtherCB101; 5 kV Calibration Box 6311-077 Calibration certificate - CB101 1000-113 UKAS calibration certificate CB101 1000-047。
CW2015-电量计芯片datasheet
CW2015-DS V2.1
Mob:13510032582 QQ:316224953 Mail:fred@gold-luck.com
CW2015
Low-Cost Fuel Gauge IC with Low-SOC Alert
Features
System-Side or Pack-Side Fuel Gauging 3% Maximum Total SOC Measurement Error 14-bit Delta Sigma ADC for Temperature and Cell
Order Information
Name
CW201erature -20℃ to 70℃ -20℃ to 70℃
Package TDFN8 CSP9
Package Mark 2015CSAD 2015CSAC
Cellwise copyright reserved
UNITS V
V
V
DC Electrical Characteristics
(2.5≤VDD≤4.5, TA= -20 to 70OC, unless otherwise specified.)
PARAMETER
SYMBOL
CONDITIONS
Min. Typ. Max.
Active Current Sleep-Mode Current Time-Based Accuracy ADC input resistor ADC resolution
Cellwise copyright reserved
2
Gas Gauge IC Series
CW2015-DS V2.1
超强劲 LED 头灯 用户手册说明书
User ManualFeaturesPurpose-designed for hiking, climbing, camping and general outdoor recreationAll metal high-performance dual-beam headlampAluminum “unibody” construction is highly rugged and providesexcellent cooling performanceUtilizes a premium CREE XM-L2 (T6) LEDPowered by a single 18650 lithium-ion battery for up to 565 lumens of outputHigh-efficiency circuit provides up to 400 hours of runtimeA custom catoptrics-based system produces an extremely wide 100° beam angleLight housing provides 90° vertical movement to eliminate illumination dead-zonesDirect access to red light mode with a runtime of up to 145 hoursInnovative single button two-stage switch is remarkably user-friendly (patented)Ten rapidly switchable brightness modes to select fromIntegrated red/green power indicator light displays remaining battery power (patented)Power indicator secondary function displays battery voltage accurate to 0.1VIntegrated temperature sensor and intelligent temperature control ensure stable and safe useHigh-efficiency regulation circuit provides unwavering output Toughened ultra-clear mineral glass with anti-reflective coating Constructed from aero-grade aluminum alloy Rugged HAIII military grade hard-anodizedComfortable chafe-free and breathable nylon headbandWaterproof in accordance with IPX-8 (two meters submersible) Impact resistant to 1.5 meters Tail stand capabilityDimensionsLength: 86mm (3.39”)Diameter: 32mm (1.26”)Weight : 130g (4.59oz)(without battery)AccessoriesSpare O-ringBattery Installation1. Insert batteries with the positive (+) and negative (-) ends corresponding to the diagram below.2. Tighten the tail cap by aligning the two gold pins on the inside of the tail cap with the corresponding holes on the flashlight body and rotate®The All-Round Flashlight ExpertTURBOHIGHMIDLOWLUMENS350LUMENS565LUMENS170LUMENS351h 15min 2h 45min 6h 15minLOWERLUMENS1400h 32h 2h 15min 5h 15min250h25h1h85m (Beam Distance)1820cd (Peak Beam Intensity)IPX-8, 2m (Waterproof AND Submersible)1.5m (Impact Resistant)1×186502×CR123NITECORE (SYSMAX) is a member of PLATO, participating in and helping to develop the ANSI/NEMA FL1 standard of measurement. Product testing data is in accordance with these internationally recognized scientific standards.HC50NOTICEThe above data has been measured in accordance with the international flashlight testing standards ANSI/NEMA FL1 using one x 3.7V 2600mAh Nitecore 18650 battery and 2 x 3V 1550mAh Nitecore CR123 batteries under laboratory conditions. The data may vary slightly during real-world use due to battery type, individual usage habits and environmental factors.Each time a battery is inserted, the power indicator light will blink to indicate battery voltage. Please refer to the “Power Tips” section of this manual for details.WARNINGEnsure when turning the HC50 on, the beam is directed away from the eyes of people or animals.General OperationThe HC50 utilizes a 2-stage switch similar to a camera shutter button. The light’s numerous functions are selected according to the depth the switch is pressed.With the light turned off, fully press and release within a second to turn on. The brightness level displayed will be the last level that was used. Repeat to turn off.Brightness SelectionWith the light turned on, press the switch half way down repeatedly to cycle through the following output modes: ultra-low, low, medium, high and turbo. A given brightness level will be memorized each time the light is turned off while that level is displayed.NB:1. Medium brightness is the default brightness level when loading a battery for the first time.2. Every time the main white LED lamp is turned on, an integrated red / green light will illuminate to indicate battery status. Please refer to the “Power Tips” section of this manual for details.Special Police Warning / SOS mode and Location BeaconWith the light turned on, fully press the switch twice in quick succession to turn on the police warning mode. Half press the switch repeatedly to cycle through location beacon, SOS and police warning modes. Fully press to exit special mode and turn the light off.Output & RuntimeSYSMAX Industry Co., Ltd.TEL: +86-20-83862000 FAX: +86-20-83882723 E-mail: *****************Web: Address : Rm1407-08, Glorious Tower, 850 East DongfengPrecaution: When the headlamp is hot, do not attempt to cool it bysubmerging in liquid as differences in internal and external air pressure may cause water ingress and irreparable damage.Changing BatteriesWhen the power indicator blinks rapidly it means the batteries need to be replaced or recharged. Alternatively if the light becomes dim or unresponsive this also indicates batteries need to be replaced.MaintenanceEvery 6 months, threads should be wiped with a clean cloth followed by a thin coating of silicon-based lubricant.Warranty ServiceAll NITECORE® products are warranted for quality. DOA / defective products can be exchanged for replacement through a localdistributor/dealer within the 14 days of purchase. After 14 days, alldefective / malfunctioning NITECORE® products will be repaired free of charge for a period of 18 months from the date of purchase. After 18 months, a limited warranty applies, covering the cost of labor andmaintenance, but not the cost of accessories or replacement parts. The warranty is nullified in all of the following situations:1. The product(s) is/are broken down, reconstructed and/or modified by unauthorized parties.2. The product(s) is/are damaged through improper use.3. The product(s) is/are damaged by leakage of batteries.For the latest information on NITECORE® products and services, please contact your national NITECORE® distributor or send an email to ********************Please follow our facebook for more info: NITECORE Flashlights®ALL-ROUND Flashlight ExpertRed Light Illumination / Signal lightWith the light turned off, press the switch all the way down and hold for more than one second to enter into red light illumination mode (1.2 lumens).When in red light mode, press the switch half way repeatedly to cycle through red light signal mode and standard red light mode. Fully press the switch to turn the light off.Power TipsWhenever the main lamp (white LED) is switched on, a power indicator built into the switch will either illuminate or blink green or red to indicate battery status.1. When main light is turned on, the green power indicatior will illuminate for two seconds when power levels are over 50%.2. When main light is turned on, the red power indicatior will illuminate for two seconds when power levels are below 50%.3. With the main light turned on, the red power indicator will blink rapidly when power levels are very low and the battery needs to be recharged and replaced.4. Each time a new battery is inserted, the green power indicator light will blink in various sequences to indicate battery voltage (accurate to ±0.1V). For example, when battery voltage is at a maximum of 4.2V, the power indicator will blink 4 times in quick succession, followed by a one second pause and then two more successive blinks, indicating a total battery voltage of 4.2V.Thermal protectionAs the HC50 is very compact, extended operation in turbo mode will cause the body temperature to continually rise, thus making it too hot to use comfortably. As a result, NITECORE does not recommend using the HC50 in turbo mode for extended periods. To prevent overheating,the HC50 will lower its output after three minutes' used of Turbo mode. The HC50’s built-in thermal protection sensor prevents overheating and will automatically reduce output when a temperature of 55°C is reached. This function ensures user safety and protects the headlamp from failure / damage.。
阿尔法冷(Alphacool)Eisblock Aurora Acryl GPX-A AMD Rad
What is it?Alphacool Eisblock Aurora Acryl GPX-AAMD Radeon RX 5700 XT Asrock T aichi X8 8G OCHighlightsThe Alphacool Aurora Acryl GPX Eisblock combines style with performance and extensive digital RGB lighting. With experience of over 16 years, Alphacool the ability to create GPU blocks that represent high quality and fantastic performance. This perfectly describes the Aurora Acryl GPX Eisblock.- Digital RGB lighting - Nickel-plated copper block - Nickel-plated copper block- Significant increase in performance compared to previous models - Patented screw plugsArticle textThe Alphacool Aurora Acryl GPX Eisblock combines style with performance and extensive digital RGB lighting. With experience of over 16 years, Alphacool the ability to create GPU blocks that represent high quality and fantastic performance. This perfectly describes the Aurora Acryl GPX EisblockMore Performance!During the development of the EIsblock Aurora GPX graphic card GPU block, we wanted to further in-crease the performance. The first step was to move the cooler closer to the individual components by reducing the thermal pads to a thickness of 1 mm. Next, we reduced the thickness of the nickel-plated copper block. Instead of 7 mm, it is now only 5.5 mm thick. The water flow inside the cooler has also been optimized. All important components such as the voltage transformers and the memory are now significantly better and more effectively cooled by the water. All this ensures a significant increase in cool-ing performance.New Design!The Eisblock Aurora GPX cooler has been designed so that lighting is more important than the previous models. The addressable digital RGB LEDs are embedded directly into the cooling block and run along the entire cooling block. The effect is an illumination of the entire cooling block. No corner or edge re-mains unlit by the aRGB LEDs. The new design is more angular with all edges bevelled. This promotes better light diffusion in the water cooler due to the reflections on these bevels. In addition, they create various contours, which give the Aurora GPX Eisblock cooler its very own unique identity.Copper or Aluminium?Of course, Alphacool only uses copper for its water coolers. With the Aurora GPX Eisblock, the copper is nickel-plated. Compared to its predecessor models, Alphacool has improved the nickel plating even fur-ther, which has considerably increased the acid resistance. This means that the nickel should resist flaking. Why does Alphacool rely on copper instead of aluminium? Simply, copper has almost twice the thermal conductivity of aluminium and is therefore clearly the better material for water cooling.Is There Anything Else New?The Eisblock Aurora GPX also relies on the new patented stop fittings, which sit flush with the surface of the terminal. The Alphacool logo now sits in the corner on the top and is also fully illuminated. On the front of the terminal you can see the corresponding names of the compatible graphic card types. Of course, these are also fully illuminated by the digital LEDs. IN and OUT are now marked by small trian-gles. They are easily recognizable and fit perfectly into the entire aesthetics of the graphic card water cooler.The Alphacool Aurora GPX Acryl is a complete redevelopment of the previous Alphacool graphics card water coolers. No technical compromises were made, but the entire technical know-how flowed into the development and implementation.。
富士通SPARC M12-2S服务器说明书
DatasheetFujitsu SPARC M12-2S Unix ServerThe Fujitsu SPARC M12-2S server is a high-performance, flexible and scalable system based on the latest SPARC64TM XII processor, delivering high availability for mission-critical enterprise workloads and cloud computingProduct OverviewThe Fujitsu SPARC M12-2S server is a flexible and scalable system based on the latest SPARC64 XII (“twelve ”) processor, delivering high performance and high availability for mission-critical enterprise workloads and cloud computing. The SPARC64 XII processor core is up to 2.5 times faster compared to the previous generation SPARC64 core. Innovative Software on Chip capabilities deliver dramatic performance increases by implementing key software functions directly in the processor. The Fujitsu SPARC M12-2S system can scale from 1 to 8 processors using a modulararchitecture, with the flexibility to create large, scale-up and/or scale-out serverconfigurations. In addition, customers can enjoy the benefits of Capacity on Demand with core-level activation, as well as physical partitioning capabilities and a suite of built-in virtualization technologies included at no cost.Flexibility and Scalability for Mission Critical CloudsThe Fujitsu SPARC M12-2S server offers high reliability and outstanding processor core performance and provides flexible scalability by virtue of a modular Building Blockexpansion methodology. The Fujitsu SPARC M12-2S server can scale up to 8 processors and 768 threads or can be used in scale-out configurations for parallel distributedprocessing. The Fujitsu SPARC M12-2S is an ideal server for traditional enterprise-classworkloads such as large-scale onlinetransaction processing (OLTP),business intelligence and data warehousing (BIDW), enterprise resource planning (ERP), and customer relationship management (CRM), as well as new environments in cloud computing or big data processing.Maximum FlexibilityEach Fujitsu SPARC M12-2S Building Block‘s minimum configuration includes oneprocessor. With core-level CPU activation, a minimum of just two processor cores must be activated initially. Core resources can begradually expanded, as needed, in increments of a single core using activation keys. Cores are activated dynamically while the system remains operational. In addition, the Fujitsu SPARC M12-2S Building Block Architecture can be used to create a large, scale-up server with as many as 8 processors and up to 12 TB of memory. Each Fujitsu SPARC M12-2S four rack unit (4RU) Building Block can scale to 24 cores and 192 threads. A Fujitsu SPARC M12-2S server can scale dynamically from 1 to 4 Building Blocks, for maximum configuration flexibility. The Building Blocks are connected via a Fujitsu-developed interconnecttechnology that ensures high bandwidth, low latency, and linear scalability. The server can also be flexibly deployed and operated in a scale-out configuration.■Up to eight 12-core, 4.25 GHz SPARC64 XII processors for a total of 96 cores and 768 powerful threads ■Superior enterprise application performance for small to large ERP, BIDW, SCM, CRM, Big Data, and Analytics workloads■Maximum cost savings with efficient consolidation of a large number of applications with diverse requirements on a single server■Flexible main memory configurations: from 64 GB to 12 TB, and supporting mixed DIMM capacities ■Radically improved response times and throughput performance by running entire databases in memory, eliminating costly disk accesses■Mainframe-class reliability, availability, and serviceability (RAS) capabilities ■Robust RAS features availability to support the most demanding 24/7 mission-critical applications■Modular Building Block Architecture■Dynamically expand resources easily and economicallyfrom 1 to 8 processor sockets■High-speed interconnect technology■Linear scaling from 1 Building Block to 4 Building Blocks tohandle planned and unplanned workload growth■Core-based CPU Activation■Ability to pay for only the resources that are needed,minimizing initial investment and avoiding expensiveupgrades■Fast and economical system capacity growth in incrementsas small as a single processor core with no downtime■Software-on-Chip instructions implementing key software functions directly in SPARC64 XII processors ■Drastic performance gains for a wide range of applications such as encryption, decimal arithmetic operations, anddatabase accelerators built into each CPU core■ 1.5 times higher memory access performance by adopting DDR4 memory directly attached to each processoraccelerates Oracle Database in-memory dramatically■New Vapor and Liquid Loop Cooling (VLLC) technology for innovative and compact system design ■Twice the cooling performance of Liquid Looping Cooling (LLC) technology used in Fujitsu M10 servers■Dramatic reduction in space and completely self-contained, requiring no maintenance■Layered virtualization including Oracle VM Server for SPARC and Oracle Solaris Zones technologies ■Higher levels of system utilization and cost reduction with flexible resource configurations■Massive server consolidation without the need to acquire additional software■Supports Oracle Solaris 11 and Oracle Solaris 10, also Solaris 9 and 8 with Oracle Solaris Legacy Container ■Investment protection for application software as well as system management and administration expertise,avoiding costly and complex migrations■Oracle Solaris Binary Application Guarantee■Preservation of software investments with guaranteedcompatibility, allowing existing SPARC Solaris applicationsto run unmodifiedFeatures and benefitsWorld-Class Enterprise Performance with Extreme Core Technology Fujitsu SPARC M12 servers featuring the 12-core SPARC64 XII processor provide superior performance for mission-critical enterprise workloads and cloud computing. Employing proven Fujitsu supercomputer technology for highly parallel computing and an innovative cooling technology to achieve low latency access time between memory and CPU, the Fujitsu SPARC M12 servers can process large amounts of data in a short period of time. These technologies provide superior performance for enterprise workloads such as online transaction processing (OLTP), enterprise resource planning (ERP), business intelligence and data warehousing (BIDW), supply chain management (SCM), and customer relationship management (CRM), as well as new environments in cloud computing or data processing.Pay as You Grow Dynamic ScalabilityThe modern enterprise needs a flexible platform that provides superior performance and availability for current application environments as well as the ability to scale for future growth and technological needs. The Fujitsu SPARC M12-2S server features unique dynamic scaling to grow as the business grows. With CPU Activation, customers can activate CPU resources on a CPU core basis and expand from a single CPU socket and two cores, while paying for only the processor cores that are needed. In addition, Fujitsu SPARC M12-2S allows for the gradual addition of resources such as CPU, memory, and PCIe slots through the dynamic addition of Building Blocks connected via the high-speed interconnect. Together, CPU Activation and Building Block Architecture enable rapid, granular and cost-effective growth from a very small configuration up to as many as 8 CPU sockets and 96 processor cores.High Availability for Mission-Critical ApplicationsThe Fujitsu SPARC M12-2S server delivers high availability to support demanding mission-critical applications. It comes with mainframe-class reliability, availability, and serviceability (RAS) features including automatic recovery with instruction retry, extended error-correcting code (ECC) protection, guaranteed data path integrity, configurable memory mirroring, and many more RAS capabilities. Furthermore, major system components are redundant and hot-swappable for increased availability and serviceability. Innovative Software on Chip TechnologyFujitsu SPARC M12-2S servers feature Software on Chip (SWoC) technology, which implements common software code sequences directly in the processor hardware, offering significant enhancements for key database functions. Two Software on Chip technologies, SIMD (Single Instruction Multiple Data) and decimal floating point ALUs (Arithmetic Logical Units), directly accelerate Oracle Database in-memory processing with specific hardware instructions. SWoC encryption acceleration is also implemented, providing high-speed encryption processing (encryption/decryption) using the Oracle Solaris encryption library. Also, the load placed on the CPU when the database is encrypted is reduced and a secure work environment can be configured.New High-Efficiency Cooling TechnologyThe new Fujitsu hybrid cooling technology, Vapor and Liquid Loop Cooling (VLLC), in Fujitsu SPARC M12-2S servers is an innovative high-efficiency vapor and liquid cooling technology that maximizes performance, minimizes space, and reduces noise. VLLC achieves twice the cooling performance of Liquid Loop Cooling (LLC) used in FujitsuM10 servers. VLLC also dramatically improves the internal layout of the server, allowing CPUs and memory to be packed closer together; reducing memory latency. VLLC is completely self-contained and requires no maintenance. This efficient cooling system can lead to significant cost savings for businesses.Advanced Virtualization and ConsolidationSPARC processor-based servers are among the world’s best consolidation and virtualization platforms. The Fujitsu SPARC M12-2S server supports up to 4 physical partitions, and as many as 256 Oracle VM Server for SPARC domains per physical partition, enabling massive server consolidation and cost savings.Oracle Solaris: The World’s Most Advanced Enterprise Operating SystemThe Fujitsu SPARC M12-2S server supports Oracle Solaris 11 and Oracle Solaris 10. In addition, all Fujitsu SPARC M12 servers benefit from the Oracle Solaris Binary Application Guarantee, with guaranteed binary and source-code compatibility for legacy applications. Oracle Solaris offers the powerful Solaris ZFS file systems and unmatched capabilities such as dynamic tracing (DTrace), cryptographic infrastructure, user and process rights management, and the Oracle Solaris IP Filter. In addition, Oracle Solaris 9 and 8 are supported using Oracle Solaris Legacy Containers.TopicsSpecificationsProcessorCPU SPARC64 XII: 12-core processor, 8 Simultaneous Multithreading threads per core,Two instruction pipelines per core, SPARC V9 architecture, Error Checking andCorrection (ECC) protectionLevel 1 cache per core64 K data cache and 64 K instruction cacheLevel 2 cache per core512 KBLevel 3 cache per CPU socket32 MBClock speed 4.25 GHzSoftware on Chip features•SIMD Single Instruction Multiple Data Vector Processing•Extended Floating-Point Registers•Decimal Floating-Point Processing. IEEE 754 standard and Oracle Number•Cryptographic Processing. Supported encryption modes are AES, DES, 3DES,DH, DSA, ECC, RSA and SHASystemCPU•Up to 2 CPUs: 1 Building Block configuration•Up to 8 CPUs: 4 Building Block configurationMain memory•Up to 3 TB per unit, with 64 GB DIMMs: 1 Building Block configuration•Up to 12 TB per unit, with 64 GB DIMMs: 4 Building Block configurationI/O•8 PCI Express 3.0 short, low-profile slots (eight lanes):1 Building Block configuration•32 PCI Express 3.0 short, low-profile slots (eight lanes):4 Building Block configuration•Up to 352 PCI Express slots with optional PCI Expansion Units•4-port 10GbE, 1 SAS-2 port, 2-port USB per Building BlockMemory bandwidth (per chip)153 GB/secService processor One per Building BlockStorageLocal storage Up to eight 600 GB or 1.2 TB internal 2.5-in. SAS HDDs or 400 GB or 800GB eMLCSAS SSDs (can be mixed)SoftwareOperating system Control Domain:•Oracle Solaris 11.4 + SRU 11.4.48.126.1 or later*Guest Domains:•Oracle Solaris 11.4 or later•Oracle Solaris 11.3 or later•Oracle Solaris 11.2 or later•Oracle Solaris 11.1 or later•Oracle Solaris 10 1/13**•Oracle Solaris 10 8/11**•Oracle Solaris 10 9/10*** The following operating systems are supported on the condition that theoptional LAN card is mounted, because they cannot use the onboard LAN:Oracle Solaris 11.3 SRU 11.3.17.5.0 or laterOracle Solaris 11.2 SRU 11.2.15.5.1Oracle Solaris 11.1 SRU 11.1.21.4.1Oracle Solaris 10 1/13 150310-03 or laterSoftware** Plus required patchesOracle Solaris 9 or 8 branded zones run within an Oracle Solaris 10 domain.Please see the Fujitsu SPARC M12 Systems Product Notes manual for SRU/patchrequirements.Software included•Oracle Solaris 11.4 or later, which includes Oracle VM Server for SPARC•Oracle Solaris ZFS (default file system)Management software •XSCF monitoring/control facility•XSCF software, which manages hardware configuration and health, domainconfiguration and status, error monitoring, and notifications.System monitoring Oracle Enterprise Manager Ops Center 12c Release 3 Update 2 or laterOracle Enterprise Manager Cloud Control 13c Release 1 or laterVirtualization Built-in, no-cost Oracle VM Server for SPARC provides the flexibility and power ofrunning multiple logical domains in a single server. Multiple Oracle Solaris Zonesmay be run within a single Oracle VM Server for SPARC logical domain.Reliability, Availability, and ServiceabilityKey features •End-to-end ECC protection•Guaranteed data path integrity•Automatic recovery with instruction retry•Dynamic L1, L2 and L3 cache way degradation•ECC and Extended ECC protection for memory, memory mirroring, periodicmemory patrol, and predictive self-healing•Hardware redundancy in memory (when mirroring), HDD, SSD(SoftwareRAID), PCI cards (Multipath configuration), power system, PSU, fan, vaporand liquid cooling pumps, and XSCF (on configuraions with two or moreBuilding Blocks)•Hot-pluggable HDD/SSD, PSU, PCIe cards, fans, and XSCF (on configuraionswith two or more Building Blocks)•Live operating system upgrades•Firmware updates during system operationEnvironmentAC power 200 V to 240 V ±10% (50/60 Hz)Power consumption Single Building Block maximum 3,292 W4 Building Blocks maximum 13,168 WOperating temperature •5° to 35° C (41° to 95° F) at an altitude of 0 m to 500 m•5° to 33° C (41° to 91° F) at an altitude of 501 m to 1,000m•5° to 31° C (41° to 88° F) at an altitude of 1,001 m to 1,500 m•5° to 29° C (41° to 84° F) at an altitude of 1,501 m to 3,000 mNon-operating temperature-25° C to 60° C (-13° F to 140° F) (packed)0 to 50° C (32° F to 122° F) (non-packed)Altitude Up to 3,000 m (9,843 ft.)Acoustic Noise•8.2 B (1 CPU) / 8.5 B (2 CPUs)•64 dB (1 CPU) / 68 dB (2 CPUs)Cooling 11,850 kJ/h per Building BlockDimensions and Weight per Building BlockHeight17.5 cm (6.9 in.)Width44.0 cm (17.3 in.)Depth80.0 cm (31.5 in.)Weight60 kg (132.3 lb.)RegulationsSafety•UL/CSA 60950-1, UL/CSA 62368-1, EN 62368-1, IEC 60950-1, and IECRegulations62368-1 CB Scheme with all country differences EMC•Emissions: FCC 47 CFR 15, ICES-003, EN 55032, KN32, EN 61000-3-2, EN61000-3-3, JIS C 61000-3-2•Immunity: EN 55035, KN35Productshttps:///global/products/ In addition to the Fujitsu SPARC M12 Server, Fujitsu offers a full portfolio of other computing products.Computing products■ S torage systems: ETERNUS■ S erver: PRIMERGY , PRIMEQUEST, Fujitsu SPARC M12, BS2000/OSD Mainframe ■ C lient Computing Devices: LIFEBOOK, STYLISTIC, ESPRIMO, FUTRO, CELSIUS ■ P eripherals: Fujitsu Displays, Accessories ■ S oftware ■ N etworkProduct Support Services with differentservice levels agreements are recommended to safeguard each product and ensure smooth IT operation.Solutionshttps:///global/solutions The Fujitsu solutions combine reliable Fujitsu products with the best in services, know-how and worldwide partnerships.Fujitsu's Solutions include parts of one or more activity groups (e.g., planning,implementation, support, management, and training services) and are designed to solve a specific business need.Infrastructure Solutions are customerofferings created by bringing Fujitsu’s best products, services and technologies together with those from partners to deliver benefit to our customers’ businesses .Industry Solutions are tailored to meet the needs of specific verticals.Business and Technology Solutions provide a variety of technologies developed to tackle specific business issues such as security and sustainability, across many verticals.Serviceshttps:///global/services/ Several customizable Fujitsu Service offerings ensure that IT makes a realdifference and delivers true business value. We do this by leveraging our extensive experience in managing large, complex, transformational IT programs to help clients in planning, delivering and operating IT services in a challenging and changing business environment.Application Services support the development, integration, testing,deployment and on-going management of both custom developed and packagedapplications. The services focus on delivering business and productivity improvements for organizations.Business Services respond to the challenge of planning, delivering and operating IT in a complex and changing IT environment. Managed Infrastructure Services enable customers to deliver the optimal ITenvironment to meet their needs – achieving high levels of IT service quality andperformance for data center and end user environments.Environment - Fujitsu GlobalFujitsu Green Policy Innovation is ourworldwide project for reducing burdens on the environment. Using our global know-how, we aim to resolve issues of environmental energy efficiency through IT. Please find further information at:Learn more about Fujitsu, please contact your Fujitsu sales representative, Fujitsu business partner,or visit our website.https:///sparc© Copyright 2023 Fujitsu limitedFujitsu, the Fujitsu logo, [other Fujitsu trademarks /registered trademarks] are trademarks or registered trademarks ofFujitsu Limited in Japan and other countries.Technical data subject to modification and delivery subject to availability. Any liability that the data and illustrations are complete, actual or correct is excluded. Designations may be trademarks and/or copyrights of the respective manufacturer, the use of which by third parties for their own purposes may infringe the rights of such owner.More informationContact FUJITSUFujitsu SPARC M12 Server https:///sparc 2023-07-11 WW -EN。
[11]-1Data Hiding in Binary Image for Authentication and Annotation
Data Hiding in Binary Image for Authenticationand AnnotationMin Wu,Member,IEEE,and Bede Liu,Fellow,IEEEAbstract—This paper proposes a new method to embed data in binary images,including scanned text,figures,and signatures.The method manipulates“flippable”pixels to enforce specific block-based relationship in order to embed a significant amount of data without causing noticeable artifacts.Shuffling is applied before em-bedding to equalize the uneven embedding capacity from region to region.The hidden data can be extracted without using the orig-inal image,and can also be accurately extracted after high quality printing and scanning with the help of a few registration marks. The proposed data embedding method can be used to detect unau-thorized use of a digitized signature,and annotate or authenticate binary documents.The paper also presents analysis and discus-sions on robustness and security issues.Index Terms—Annotation,authentication,binary image,data hiding,digital watermarking.I.I NTRODUCTIOND IGITAL watermarking and data hiding techniques havebeen proposed for a variety of digital media applications, including ownership protection,copy control,annotation,and authentication.Most prior works on image data hiding are for color and grayscale images in which the pixels take on a wide range of values[2]–[9].For most pixels,changing the pixel values by a small amount may not be noticeable under normal viewing conditions.This property of human visual system plays a key role in watermarking of perceptual data[5],[6].For im-ages in which the pixels take value from only a few possibilities, hiding data without causing visible artifacts becomes more dif-ficult.In particular,flipping white or black pixels that are not on the boundary is likely to introduce visible artifacts in binary images.Hiding data in binary image,though difficult,is getting higher demands from our everyday life.An increasingly large number of digital binary images have been used in business. Handwritten signatures captured by electronic signing pads are digitally stored and used as records for credit card payment by many department stores and for parcel delivery by major courier services such as the United Parcel Service(UPS).WordManuscript received April1,2001;revised March28,2002.This work was supported in part by a New Jersey State R&D Excellence Award,NSF Grants MIP-9408462and CCR-0133704,and an Intel Technology for Education2000 Grant.Part of this work was presented at the IEEE International Conference on Multimedia&Expo(ICME’00)[1].The associate editor coordinating the review of this manuscript and approving it for publication was Dr.Sankar Basu. M.Wu was with the Department of Electrical Engineering,Princeton Univer-sity,Princeton,NJ08544USA.She is now with the Department of Electrical and Computer Engineering,University of Maryland,College Park,MD20742 USA(e-mail:minwu@).B.Liu is with the Department of Electrical Engineering,Princeton University, Princeton,NJ08544USA(e-mail:liu@).Digital Object Identifier10.1109/TMM.2004.830814processing software like Microsoft Word allows a user to store his/her signature in a binary imagefile for inclusion at specified locations of an electronic document.The documents signed in such a way can be sent directly to a fax machine or be dis-tributed across a network.The unauthorized use of a signature, such as copying it onto an unauthorized payment,is becoming a serious concern.In addition,a variety of important docu-ments,such as social security records,insurance information, andfinancial documents,have also been digitized and stored. Because of the ease to copy and edit digital images,annotation and authentication of binary images as well as detection of tampering are very important.This paper discusses data hiding techniques for these authen-tication and annotation purposes,possibly as an alternative to or in conjunction with the cryptographic authentication approach. Such targeted applications calls for fragile or semifragile em-bedding of many bits.It should be stressed that while it is de-sirable for the embedded data to have some robustness against minor distortion and preferably to withstand printing and scan-ning,the robustness of embedded data against intentional re-moval or other obliteration is not a primary concern.This is be-cause an adversary in authentication applications would have much more incentive to counterfeit valid embedded data than to remove them,and there is no obvious threat of removing em-bedded data in many annotation applications.Several methods for hiding data in specific types of binary images have been proposed in literature.Matsui et al.[10] embedded information in dithered images by manipulating the dithering patterns and in fax images by manipulating the run-lengths.Maxemchuk et al.[11]changed line spacing and character spacing to embed information in textual images for bulk electronic publications.These approaches cannot be easily extended to other binary images and the amount of data that can be hidden is limited.In[12],Koch and Zhao proposed a data hiding algorithm which enforces the ratio of black versus white pixels in a block to be larger or smaller than1.Although the algorithm aims at robustly hiding information in binary image,it is vulnerable to many distortions/attacks,and it is not secure enough to be directly applied for authentication or other fragile use.The number of bits that can be embedded is limited because the particular enforcing approach has difficulty in dealing with blocks that have low or high percentage of black pixels.However,the idea of enforcing properties of a group of pixels via the local manipulation of a small number of pixels can be extended as a general framework of data embedding.Another approach of marking a binary document is proposed in[13]by treating a binary image as a grayscale one and manipulating the luminance of dark pixels slightly so that1520-9210/04$+20.00©2004IEEEFig.1.Block diagram of the embedding and extraction process in binary images for authentication and/or annotation.the change is imperceptible to human eyes yet detectable by scanners.This approach,targeted at intelligent copier systems, is not applicable to bilevel images hence is beyond the scope of this paper.The bilevel constraint also limits the extension of many approaches proposed for grayscale or color images to binary images.For example,applying the spread spectrum embedding,a transform-domain additive approach proposed by Cox et al.[5],to binary image would not only cause an-noying noise on the black–white boundaries,but also have reduced robustness hence limited embedding capacity due to the post-embedding binarization that ensures the marked image is still a bilevel one[14].For these additive embeddings,hiding a large amount of data and detecting without the original binary image is particularly difficult.In summary,these previously proposed approaches either cannot be easily extended to other binary images,or can only embed a small amount of data.We propose a new approach that can hide a moderate amount of data in general binary images,including scanned text,fig-ures,and signatures.The hidden data can be extracted without using the original unmarked image,and can also be extracted after high quality printing and scanning with the help of a few registration marks.The approach can be used to verify whether a binary document has been tampered with or not,and to hide annotation labels or other side information.The paper is organized as follows.The proposed approach is presented in Section II and illustrated using three applications in Section III.Further discussions on robustness and security are given in Section IV,including such issues as recovering hidden data from high quality printing-and-scanning.Section V con-cludes the paper and suggests a few directions of future work.II.P ROPOSED M ETHODThere are two basic ways to manipulate binary images for hiding data.Thefirst class of approaches changes low-level fea-tures such asflipping a black pixel to white or vice versa.The second class of approaches changes high-level features such as modifying the thickness of strokes,curvature,spacing,and relative positions.Since the number of parameters that can be changed by the second class of approaches is limited,especially under the requirements of invisibility and blind detection(i.e., without using the original image in detection),the amount of data that can be hidden is usually limited except for special types of images[11].We focus in this paper on thefirst class of approaches.An image is partitioned into blocks and afixed number of bits are embedded in each block by changing some pixels in that block. For simplicity,we shall show how to embed one bit in each block.Three issues will be discussed:1)how to select pixels for modification so as to introduce as little visual artifacts as pos-sible,2)how to embed data in each block using theseflippable pixels,and3)why to embed the same number of bits in each block and how to enhance the efficiency.The entire process of embedding and extraction is illustrated in Fig.1.A.Flippable PixelsThere is little discussion in the literature on a human visual model for binary images.A simple criterion,proposed in[12],is to onlyflip boundary pixels for high contrast image such as text image,and to only introduce new pixel patterns that are rather isolated for dithered image.We take the human perceptual factor into account by studying each pixel and its immediate neighbors to establish a score of how unnoticeable a change on that pixel will cause.The score is between0and1,with0indicating no flipping.Flipping pixels with higher scores generally introduces less artifacts thanflipping a lower one.To assignflippability score manually according only to neigh-borhood patterns has the shortcomings that the storage of every pattern can be huge(except for small neighborhood)and that such afixed assignment does not offerflexibility for binary im-ages with different characteristics.Our approach in this paper is to determine the scores dynamically by observing the smooth-ness and connectivity.The smoothness is measured by the hori-zontal,vertical,and diagonal transitions in a local window(e.g.,33),and the connectivity is measured by the number of the black and white clusters.For example,theflipping of the center pixel in Fig.2(b)is more noticeable than that in Fig.2(a).We order all33patterns in terms of how unnoticeable the change of the center pixel will be.We then examine a larger neighbor-hood,say55,to refine the score.Special cases are also han-dled in larger neighborhood so as to avoid introducing noise on special patterns such as sharp corners.By changing the param-eters in our procedure,we can easily adjust the intrusiveness of different kind of artifacts and tailor to different types of binary images.Details of our approach are given in the Appendix.Fig.2.Two examples of 323neighborhood,for which flipping the center pixel to white in (a)is less noticeable than that in(b).Fig.3.Example illustrating a boundary pixel could become “non flippable ”after flipping.B.Embedding MechanismDirectly encoding the hidden information in flippable pixels (e.g.,set to black if to embed a “0”and to white if to embed a “1”)may not allow the extraction of embedded data without the original image.The reason is that the embedding process may change a flippable pixel in the original image to a pixel that may no longer be considered flippable.As a simple example,sup-pose only black pixels that are immediately adjacent to white pixels are considered as “flippable ”.One such flippable pixel,marked by thick boundary in Fig.3(a),is changed to white to carry a “1”,as shown in Fig.3(b).It can be seen that after em-bedding,this pixel is no longer considered flippable if applying the same rule.This simple example shows the dif ficulty for the detector to correctly identify which pixel carries hidden infor-mation without using the original image.Instead of encoding the hidden information directly in flip-pable pixels,we embed data by manipulating pixels with high flippability scores to enforce a certain relationship on low-level features of a group of pixels.One possibility is to use the total number of black pixels in a block as a feature.To embed a “0”in a block,some pixels are changed so that the total number of black pixels in that block is an even number.Similarly,to embed a “1”,the number of black pixels is enforced to an odd number.We may also choose a “quantization ”step size Q and force the total number of black pixels in a block to be 2kQ forsome integer k in order to embed a “0”,and tobeto embed a “1”.A larger Q gives higher tolerance to noise at the expense of decreased image quality.This “odd –even ”embed-ding can be viewed as a special case of lookup table embedding similar to that in [8],[9].These two approaches are illustrated in Fig.4,where each possible quantized number of black pixels per block is mapped to 0or 1.While other relationship enforcing techniques [15]are possible,we shall use in this paper the en-forcing of odd or even number of black pixels in a block.The above approaches can be characterized more generallyby(1)where istheoriginalfeature,is the feature value afterembedding,is the bit to be embeddedin feature,and Fig.4.Illustration of odd –even mapping and table lookupmapping.is a prescribed mapping from feature values to hidden data values {0,1}.Detection is done by checking the enforcedrelationship:(2)where is the feature extracted fromthe block of a testimage,and is the estimated value of the embedded bit inthe block.If the same bit is repeatedly embedded in more than one block,majority voting is performed to determine which bit has been hidden.More sophisticated coding than simple repetition can also be used to achieve a certain level of tradeoff between robustness and capacity.C.Uneven Embedding Capacity and ShufflingAs outlined earlier,we embed multiple bits by dividing an image into blocks and hiding one bit in each block via the en-forcement of odd –even relationship.However,the distribution of flippable pixels may vary dramatically from block to block.For example,no data can be embedded in the uniformly white or black regions,while regions with text and drawing may have quite a few flippable pixels,especially on the nonsmooth boundary.This uneven embedding capacity can be seen from Fig.5where the pixels with high flippability scores,indicated by black dots in Fig.5(b),are on the rugged boundaries.General approaches to handling uneven embedding capacity have been discussed in [15],[16].Regarding the uneven em-bedding capacity in a binary image,using variable embedding rate from block to block is not feasible for the following rea-sons.First,a detector has to know exactly how many bits are embedded in each block.Any mistake in estimating the number of embedded bits is likely to cause errors in decoding the hidden data for the current block,and the error can propagate to the fol-lowing blocks.Second,the overhead for conveying this side in-formation via embedding is signi ficant and could be even larger than the actual number of bits that can be hidden.We therefore adopt constant embedding rate to embed the same number of bits in each region and use shuf fling to equalize the uneven em-bedding capacity from region to region [15],[17].Fig.6shows the flippable pixels before and after a random permutation of all pixels,and Fig.7shows the histogram of the number of flippable pixels per1616-pixel block.It is seen that the distribution before shuf fling extends from zero to 40flippables per block and that about 20%of the blocks do not have any flippable pixels.The distribution after shuf fling,shown in the dotted line,concentrates in the range of ten to 20,and allshuf fled blocks have flippable pixels.Letbe the number of blocks each havingexactly flippablepixels,the total number ofpixels,the blocksize,the number ofFig.5.(a)A binary signature image and (b)its pixels with high flippability scores shown inblack.Fig.6.Distributions of flippable pixels per 16216-pixel block of the binary image in Fig.5:(a)before shuf fling and (b)after shuf fling.blocks,and the percentage of flippable pixels.1It can then be shown [15],[16]that the mean and variance of each normalizedbinof the histogramas(3)(4)For the signature image of ig.5,wehaveThe analytic results are shown in Fig.8,along with the simula-tion results from 1000random shuf fles.The statistics of blocks with no or few flippables are also shown in Table I.The anal-ysis and simulation are seen to agree well,and the percentage of blocks with no or few flippables is extremely low.Error cor-rection coding can be used to handle a very small number of blocks that have no flippable pixels.As illustrated by the block diagram in Fig.1,the embedding of one bit per block described in Section II-B is performed in the shuf fled domain,and inverse shuf fling is performed to get a marked image.We would like to point out that shuf fling does not produce more flippable pixels.It dynamically assigns the flippable pixels in active regions and along rugged boundaries to carry more data than less active regions.This is done without the need of speci-fying much side information that is image dependent.Shuf fling1Inthis analysis,we set a threshold of 0.1on the flippability score and con-sider the pixels with score higher than this as flippable.Fig.7.Histogram of flippable pixels per 16216-pixel block of the binary image in Fig.5:(solid line)before shuf fling and (dotted-dash line)after shuf fling.Fig.8.Analysis and simulation of the statistical behavior of shuf fling for thebinary image in Fig.5(a).also enhances security since the receiver side needs the shuf-fling table or a key for generating the table to correctly extract the hidden data.III.A PPLICATIONS AND E XPERIMENTAL R ESULTSThe proposed data hiding for binary image is targeted mainly at authentication and annotation.In this section,we present three speci fic applications along with experimental results.A.“Signature in Signature ”Using archived signatures for unintended purposes is a po-tential concern toward the increasingly popular deployment of digitized signature in our everyday life.A “Signature in Signa-ture ”2system annotates the signer ’s signature with the data that is related to the signed documents,so that the unauthorized use of a signature can be detected [18].2Herethe second “signature ”refers to the actual digital version of a person ’ssignature,while the first “signature ”refers to a checksum related to the docu-ment content or other annotation information.TABLE IA NALYSIS AND S IMULATION OF THEB LOCKS W ITH N O OR F EW F LIPPABLE P IXELS B EFORE AND A FTER S HUFFLING FOR THE B INARY I MAGE IN F IG .5(a)Fig.9.“Signature in Signature ”:(a)original image;(b)marked copy with seven letters (49bits)embedded in;(c)difference between the original and the marked (shown in black).The data hiding method proposed in this paper can be ap-plied to annotating a signature in such applications as faxing signed documents and storing digitized signatures as transac-tion pared with the traditional cryptographic au-thentication approach [19]that has been used in secure com-munication,the proposed data embedding based approach has the advantage of being user-friendly,easy to visualize,and in-tegrating the authentication data with the signature image in a seamless way.An example is demonstrated in Fig.9,in which seven char-acters (49bits)are embedded in a28761signature.The em-bedding rate is one bit per block of 320pixels.Fig.9(a)is the original signature;Fig.9(b)is the signature after embedding,which is indistinguishable from the original;and Fig.9(c)shows where the altered pixels are.3B.Invisible Annotation for Line DrawingsArtists may wish to annotate their drawings with information,such as the creation date and location,in such a way that the an-notation data interfere minimally with perceptual appreciation.Our proposed data hiding approach can be used to invisibly an-notate line drawings such as the120150picture of Fig.10.In this example,a character string of the date “01/01/2000”is embedded in Fig.10(b).C.Tamper Detection for Binary DocumentA large number of important documents have been digitized and stored for records.The authentication of these digital docu-ments as well as the detection of possible tampering are impor-tant concerns.The data hiding techniques proposed in this paper can be applied for these purposes,as an alternative to or in con-junction with the cryptographic authentication approach.More3The gray areas in Fig.9(c),Fig.10(c)and Fig.11(d)visualize the strokes andthe background,respectively.We show them in gray to assist viewers associating the difference between the original and the marked image with their precise location in the images.The pixelwise differences are indicated by black pixels.speci fically,data are be embedded in an image in such a fragile way that it will be obliterated if the image is altered and/or that it no longer matches some properties of the image,indicating the tampering of content [16].The hidden data can be an easily recognized pattern,or some features or their digest version re-lated to the content of the host image.Shown in Fig.11(a)is a part of a U.S.patent document,con-sisting of10001000pixels.This binary image contains texts,drawings,lines,and bar codes.Fig.11(b)is a visually identical figure,but with 976bits embedded in it using the proposed tech-niques.In this particular example,800bits of the embedded data come from a “PUEE ”pattern shown in Fig.11(g).If the date “1998”on the top is changed to “1999”,the extracted data will be the random pattern shown in Fig.11(g),indicating that alter-ation was made.IV .R OBUSTNESS AND S ECURITY C ONSIDERATIONS In this section,we discuss a few robustness and security is-sues of the proposed scheme.Other considerations associated with shuf fling,such as the methods for handling bad shuf fles and for adaptively choosing the block size,can be found in [15],[16].A.Analysis and Enhancement of RobustnessThe robustness against noise of the embedding presented in Section II-B is quite limited,and generally depends on whether and how much quantization we applied [15],[16].Let us con-sider the simple odd –even case with no quantization,i.e.,the total number of black pixels is enforced to an even number to embed a “0”,and to an odd number to embed a “1”.When a single pixel is changed due to noise,the bit embedded in the block to which the pixel belongs will be decoded in error.When several pixels in an embedding block are subject to be changed,whether or not the bit can be decoded correctly depends on how many pixels are flipped;if the change is independent from pixel to pixel and is withprobability for eachof pixelswhere,the probability of getting a wrongly decoded bitis(5)The errorprobabilityis small forsmall andsmall .In this case,error correction encoding can be applied to correct errors if accurate decoding of hidden data is preferred.When is close to 0.5,sois ,implying the dif ficulty in embedding and extracting data reliably.Notice that because of shuf fling,the assumption of independent change is likely to hold even if the noise involves nearby pixels.This is because adjacent pixels in the original image will be distributed to several blocks.If theFig.10.Invisible annotation for line drawings:(a)original image;(b)marked copy with ten-letter date information (70bits)embedded in;(c)difference between the original and the marked (shown inblack).Fig.11.Data hiding in binary document image:(a)original copy;(b)marked copy with 976-bit embedded in;(c)magni fied original image;(d)difference between original and marked (shown in black);(e)magni fied marked image;(f)portion of the image where alteration is done on the marked image by changing “1998”to “1999”;(g)among the 976-bit hidden data,800bits form a “PUEE ”pattern;the 800-bit data pattern extracted after alteration is visually random and signi ficantly different from the originally embedded “PUEE ”.total number of changed pixels in the whole image is small (no matter whether they are close to each other in the original image or far away),it is likely that most of those pixels are involved in different embedding blocks hence the extracted bits from those blocks will be wrong.On the other hand,if many pixels have been changed,each embedding block may include several of these pixels and the decoded bit from each block is wrong with approximately 0.5probability.This implies that the decoded data are rather random,as what we have seen in Fig.11(g).The case of incorporating quantization can be analyzed similarly.Besides the noise involving flipping of individual pixels,mis-alignment is another cause of decoding errors.For this matter,using shuf fling has the disadvantage of increasing the sensi-tivity against geometric distortion such as translation.This is due to the shift-variant property of the shuf fling operation,i.e.,the shuf fling result of a shifted image is very different from that of the nonshifted one.To alleviate the sensitivity with respect of translation,we can put the hidden data in a cropped part of the image,as shown in Fig.12.Without loss of generality,we con-sider the case of black foreground and white background.The upper-left point of the data hiding region is determined by the uppermost and leftmost black pixel,and the lower-right point is by the lowermost and rightmost black pixel.The data hiding re-gion therefore covers all black pixels.This approach can reduce the shifting sensitivity as long as both embedding and detection systems agree on the protocol and no cropping or addition of the outermost black pixels occurs.Fig.12.Illustration of achieving robustness against small translation.Here we use the outermost black pixel to determine a data hiding region (indicated by a dash box)covering all blackpixels.Fig.13.Recovering binary image from high quality printing and scanning:(a)specially designed dotted signature box helps the recovery;(b)estimated centers of each original pixel are shown in light color in this zoomed-in view.In addition to the above approach,adding registration marks such as a signature line helps survive high-resolution printing and scanning.In general,recovering image from printing and scanning with precision as high as one pixel is a nontrivial task,because this D/A-A/D process may result in small rota-tion,up-scaling of an unknown factor,and noisy boundary.If resolution-wise one pixel in the original image corresponds to only one pixel in the scanned version,it will be very dif ficult to combat the distortion introduced by the D/A-A/D process.On the other hand,if signi ficant oversampling is performed so that one original pixel corresponds to a number of pixels in the scanned version,it would be possible to sample at the center of each “original ”pixel,and avoid the noise introduced on the boundary and/or by the rounding errors in deskewing.Registration marks can help us identify the boundary and the size of the original image as well as correct skewing.We noted that while the size of one original pixel in terms of pixels in the scanned image may be estimated from a well-designed registration mark (e.g.,we may estimate that one original pixel corresponds to88pixels in a scanned image),minor errors in such estimation could be accumulated when we determine the width and height of the original image up to single pixel precision.To overcome this problem,we impose constraints on the width and height of original signature images,for example,to be multiples of 50.Fig.13(a)shows one possible way to handle the recovery by adding a dotted signature box that resembles what has been commonly used in the current practice of signing.The four corner marks of the signature box and the dash line segments on the four sides at an interval of 50pixels horizontally and of 25pixels vertically serve as a ruler to facilitate the recovery.In this experiment,we printed out the signature imageviaFig.14.Pixels that touch each others by 90(i.e.,(i;j 61)or (i 61;j ))or by 45(i.e.,(i +1;j 61)or (i 01;j 61))and that have the same pixel value are often considered as connected .the Microsoft Word 2000program (with image importing resolution 72dpi)using an HP LJ4100DTN laser printer,and scan back with 600dpi resolution and 256gray levels using a Microtek 3600scanner.The image is binarized with a threshold that equals to the average of the maximum and minimum of scanned luminance values.We use the registration marks to determine the image boundary,to perform deskewing,and to compute the proper scaling factor.The estimated center of each original pixel on the scanned version is shown in Fig.13(b).Sampling at those pixels can recover the original digital image perfectly from the scanned one hence allow the embedded data to be extracted correctly.More detailed discussion on recovering of binary image from printing and scanning can be found in [16].The above mentioned approaches fall in the category of vis-ible registration.The key purpose is to use the marks as refer-ence to determine the boundary of binary image and the scaling factor after the printing-and-scanning process,and in turn,re-cover the image accurately.It should be noted that the accurate recovery of image is needed regardless of how the authentication data is stored (invisibly or visibly).Although we can attach au-thentication data separately,for example,to put a message digest or a cryptographic digital signature in the form of a text string or。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
RESEARCH ARTICLEA high capacity data hiding algorithm for H.264/AVC videoMehdi Fallahpour1*,Shervin Shirmohammadi1and Mohammad Ghanbari21School of Electrical Engineering and Computer Science(EECS),University of Ottawa,Ottawa,Ontario,Canada2School of Electrical and Computer Engineering,University of Tehran,Tehran,IranABSTRACTThis article presents an information hiding algorithm for H.264/AVC video stream.It utilizes position of the last nonzero level of quantized discrete cosine transform block to embed information bits.Because only the high-frequency levels are changed,it can guarantee a high peak signal-to-noise ratio and slight increase in bit rate after the watermark embedding. The extraction process is not complex;thus,the proposed technique is an excellent solution for real-time applications such as broadcasting.Experimental results on several test sequences demonstrate that the proposed approach can realize blind extraction with real-time performance;it also provides very high capacity,low distortion and increase in bit rate by about 0.5%.Copyright©2015John Wiley&Sons,Ltd.KEYWORDSvideo data hiding;H.264/AVC;DCT;watermarking;multimedia security*CorrespondenceMehdi Fallahpour,School of Electrical Engineering and Computer Science(EECS),University of Ottawa,Ottawa,Ontario,Canada.E-mail:mfallah@site.uottawa.ca1.INTRODUCTIONWith the progress of computer and broadband internet tech-nologies,nowadays,it is possible to stream high-quality video and to watch video online.Websites such as YouTube,DailyMotion and iFilm provide free watching and download services,whereas portable devices such as iPod,smartphone and tablet make it possible to playback a video anywhere anytime.Thus,digital video has become a popular multimedia content for both online and offline en-vironments.Therefore,it is important to discover ways to protect the contents from malicious use and to design effi-cient methods to search the desired contents in the database, secure ways to provide extra features for upgraded viewers and reliable techniques to recover from transmission error for uninterrupted viewing for the future of digital video.Data hiding methods embed a secret signal directly into the original media in an imperceptible manner.In video data hiding,the watermark can be embedded either into an uncompressed video sequence(raw data)or compressed video stream although the great majority of streamed video through the Internet are compressed,so data hiding in com-pressed video has a wider impact than data hiding in un-compressed video.Transparency,capacity and security are three major challenging issues of a video data hiding system.Robustness is a property of a watermarking system,which is considered in some applications such as copyright pro-tection.In data hiding applications,robustness is not a pri-ority because such applications are more aimed to achieve high transparency along with embedding a great deal of se-cret bits[1].The application of our proposed algorithm is mainly in covert communication and error concealment, but it can also be used in scenarios such as[2]where data hiding techniques are used to measure the quality of the compressed video in the absence of the original reference (such as reduced reference model),by predicting the qual-ity from the degradations of the extracted hidden message. Another application of data hiding can be seen in[3], which uses data hiding to enable real-time scene change detection in compressed video.Finally,data hiding is a suitable solution for error detection and concealment in video transmission,where edge orientation information and number of bits of a block are embedded in the bit stream for that purpose[4].In general,the existing data hiding systems rely on em-bedding information bits in discrete cosine transform (DCT)coefficients,motion vectors(MVs),quantization scale or prediction modes.Li et al.[5]used DCT coeffi-cients and the parity of the quantized coefficients to hide a message.The work in[6]presents a solution for using the magnitude of MVs for data hiding.The least significant SECURITY AND COMMUNICATION NETWORKSSecurity works2015;8:2947–2955Published online17March2015in Wiley Online Library().DOI:10.1002/sec.1221 Copyright©2015John Wiley&Sons,Ltd.2947bit of both components of candidate MVs are used to em-bed a secret message.The candidate MVs are chosen on the basis of the prediction error of the underlying macro-block.MVs related to high prediction errors are selected.A prediction error threshold per frame is calculated and transmitted in the video bit stream to guide the decoder in recognizing the MVs that carry the secret information bits.Hu et al.[7]proposed the use of intraprediction modes to embed secret message bits.Furthermore,the work in[8]utilizes the block types and modes of intracoded blocks of H.264/AVC to hide message bits. Data hiding technique can also be applied before compres-sion,such as embedding hidden messages into the pixels and then compressing them as I-frames[9].Recently,several researchers have focused on devel-oping data hiding systems in the compressed domain [10–16].However,the complex encoding nature of mod-ern encoders such as H.264/AVC[17]creates several constraints for hiding data in the coded video sequences. The restrictions include the following:(1)Embedding even a little data into the coded videosequence would result in a great deal of changeson both the bit rate and the reproduced videoquality.(2)It is difficult to make a cost effective trade-off be-tween the bit-rate increase and video quality degra-dation when embedding secret data into the codedbit stream.(3)To increase hiding capacity,increase in bit rate orvideo quality degradation is sacrificed[18].Because of these constraints,designing a video data hid-ing system in the compressed domain is more difficult than other domains.Two methods[19,20]have applied the tra-ditional reversible methods to H.264/AVC directly.Lie et al.[19]utilize difference expansion[21]to embed secret bits into the quantized discrete cosine transform(QDCT) coefficients for error concealment,whereas Chung et al.[20]suggest an efficient algorithm that utilizes histogram shifting[22]through QDCT coefficients to embed MVs for error concealment,but considering the histogram shifting rules,the system shouldfind the peak and zero points to shift and embed data from the embedding target. According to the context-adaptive variable-length coding (VLC)rule[23],changing the number of QDCT coeffi-cients or the length of the VLC words can significantly increase the bit rate or reduce the peak signal-to-noise ratio(PSNR).In our proposed method,after performing DCT and quantization phases in H.264/AVC,some4×4blocks are selected for embedding.The method takes advantage of high-frequency levels to gain from lower sensitivity of the human visual system to higher frequency distortions.Em-bedding in the low-frequency levels of4×4blocks,which carry perceptually important information,results in obvious quality distortion in the watermarked video.Therefore,in the proposed scheme,the last nonzero(LNZ)QDCT coefficients of4×4blocks are used,which are in the high-frequency band to embed the watermark.The scheme utilizes the positions of the LNZ levels to embed informa-tion bits.Experimental results and analysis presented in Section3will demonstrate that the suggested system pro-vides very high capacity and low-quality degradation while limiting the bit-rate increase to about0.5%.It should be noted that,although in this paper,H.264/ AVC is chosen to demonstrate the proposed method,there is no loss of generality and the method can be applied to any modern video codec,such as the high efficiency video coding(HEVC),which transforms macroblocks using DCT or operations similar to DTC,leading to frequency coefficients.The rest of the paper is organized as follows. In Section2,the proposed data hiding scheme is presented. Section3introduces the experimental results.Finally, Section4gives some concluding remarks.2.THE PROPOSED DATA HIDING SCHEMEAccording to the applications,several video compression standards,such as MPEG-2,Motion Picture Expert Group 4Part2(MPEG-4),Windows Media Video9Codec (VC-1),Motion Picture Expert Group4Part10(H.264 AVC)and On2True-Motion VP6(VP6)can be employed. Almost all video compressions are block DCT based.In these codecs,every frame is divided into blocks where cod-ing operations are applied on DCT coefficients.However, in H.264/AVC like other DCT block-based compression codecs,motion estimation,prediction,entropy coding and compression tricks are applied on each block.The use of DCT coefficients for embedding the water-mark is very challenging in both compressed image and video(such as JPEG and H.264)because compression does not leave much room for watermark location.For the H.264/AVC video codec,the QDCT coefficients and the MVs are the most used parameters for embedding the information bits.Low-frequency,middle-frequency or high-frequency QDCT coefficients may be selected to embed the watermark on the basis of the requirements of the application in terms of robustness or fragility.For the embedding process,the choice of the DCT coefficients usually relies on the human visual properties to mask the introduced degradation by the watermark.In our proposed method,robustness is not a priority;thus,the high-frequency coefficients are chosen because they introduce less perceptual artefacts.The grey area in Figure1shows the locations of high-frequency coefficients suitable for embedding the signature.In H.264/AVC,applying motion estimation,prediction, DCT and quantization results in blocks with value close to one.Because DCT values are quantized,a significant num-ber of QDCT values are converted to zero.In most blocks, there is an LNZ QDCT level.Zigzag scanning for each 4×4block is used for locating LNZ levels.The position of LNZ plays a key role in embedding secret bits in theWatermarking M.Fallahpour,S.Shirmohammadi and M.Ghanbari 2948Security works2015;8:2947–2955©2015John Wiley&Sons,Ltd.DOI:10.1002/secsuggested system.Figure 2provides statistics of position of LNZ for different quarter common intermediate format (QCIF)video tests.This figure illustrates in how many blocks the position of LNZ is equal to P i ,1≤P i ≤16.All positions can be used for embedding secret bits but changing low-frequency and middle-frequency compo-nents may cause signi ficant distortion.Thus,high-frequency levels are used for embedding the watermark.Blue bins in Figure 2show the number of LNZ levels in high-frequency area.2.1.EmbeddingEvery block of 4×4,which at least has a high-frequency coef ficient,can be selected for data hiding.Thr is de fined as a threshold for modi fication of the LNZ position.More speci fically,if the position of the LNZ is greater than Thr ,the block is chosen for embedding,and a single bit isembedded in it.The embedding process for each block af-ter the quantization phase is performed by the following steps:(1)To improve the security,encrypt the embedded wa-termark stream Ws by a key called K ,to form the watermark stream S .S ¼E K ;Ws ðÞwhere E is the encryption operation.(2)For each 4×4block,find the position of the LNZlevel.(3)If the position is higher than Thr ,the block has ahigh-frequency element and is a candidate for embedding,and the embedding process continues.Otherwise return to step 2for the next block.(4)For each selected block,modify the position ofLNZ level (P i )based on S i (the i th bit of the stream)as follows:P ′i ¼P i if P i is even and S i is 0P i þ1if P i is odd and S i is 0P i þ1if P i is even ;P i <16and S i is 1P i if P i is odd and S i is 1P i À1if P i is 16and S i is 18>>>>>><>>>>>>:where S i is the encrypted watermark bit of the i th block.Figure 1.Selected high-frequency area in each 4×4block.50001000015000200002500030000350004000045000ContainerForemanMobileNewsTennis12345678910111213141516Figure 2.Positions of the last nonzero(LNZ)level for five different QCIF test video sequences.Figure 3.Embedding and detecting flowchart.WatermarkingM.Fallahpour,S.Shirmohammadi and M.Ghanbari 2949Security works 2015;8:2947–2955©2015John Wiley &Sons,Ltd.DOI:10.1002/secAfter the aforementioned embedding steps,the block is ready for other steps of the H.264/AVC coding process such as context-adaptive VLC.Figure3shows the embedding and detecting procedures. After decoding the H.264/AVC stream,which includes wa-termark detection,the Luma(Y)and two chrominance (UV)components(YUV)file and the extracted secret bits are obtained.In H.264/AVC,changing the quantization parameter (QP)results in varying the number of non-zero levels in the macroblocks.It is evident that when QP is low,there are more non-zero levels compared with high QP,increas-ing the embedding capacity.2.2.DetectingThe embedded watermark bits are extracted in the decoding process of H.264/AVC where the quantized DCT levels for each MB are entropy decoded.For each block,the following steps result in extracting the embed-ded bits from each block(1)Find the position of the LNZ level.(2)If the position of LNZ is higher than Thr,follow thefollowing steps;otherwise start from step one forthe next block.(3)In the selected block,the embedded bit can beextracted as follows:S i¼0if P′is even 1if P′is odd (where S i is the extracted bit of the i th selected block in the decoder and P′is the position of the LNZ in the current block.To obtain the raw watermark stream,we need to decrypt the extracted stream by the encryption key.In general,efficiency,complexity,energy usage and sim-plicity are more important in the decoder implementa-tion because it is at the client side with limited resources compared with the server side,which has more resources.Also,some delay in the encoder is ac-ceptable because it is carried out only once for a video. So,low complexity and simplicity in implementation are critical points in designing the decoder.One advan-tage of our proposed technique is its simplicity in implementation at the decoder,allowing it to run for various real-time applications.3.EXPERIMENTAL RESULTS AND ANALYSISTo verify the performance of the proposed information hiding system,it has been tested on several test video sequences such as Container,Foreman,Mobile,News and Tennis in QCIF format(176×144pixels),as shown in Figure4.As the watermark is embedded in blocks of 4×4pixels,the embedding algorithm is independent of the resolution of the video.The original video streams are obtained by the H.264/ AVC reference software version JM12.2[24],and the pro-posed method is integrated within the H.264/AVC codec. The most important configuration parameters of the refer-ence software are given in Table I.The rest of the encoder parameters have retained their default values.Also,it is worth to note that in parts A and B,Thr isfixed at9,Figure4.Video test sequences.Watermarking M.Fallahpour,S.Shirmohammadi and M.Ghanbari2950Security works2015;8:2947–2955©2015John Wiley&Sons,Ltd.DOI:10.1002/secwhereas in part C,changing the Thr itself will be discussed.Capacity is defined as the number of bits embedded in one frame or1s of the video.In this article,the capacity is measured and compared with other schemes in terms of embedded bits in a QCIF frame.In an ideal case,there must be no perceptible difference between the watermarked and the original digital contents;that is,the watermark data should be transparent to the user.Embedding in the compressed domain such as H.264/ AVC changes the bit rate of the compressed stream.In most cases,watermark embedding increases the bit rate. The bit-rate increase should be in an acceptable range. For example,the increase in bit rate should not be larger than the watermark bits sent out of band.The trade-off between capacity,transparency and bit rate is the main challenge for video data hiding in the com-pressed domain.In an ideal case,a very high capacity and very transparent scheme without any changes of bit rate are demanded.Practically,achieving all these requirements at the same time is extremely difficult if not impossible. Therefore,depending on the priorities of the data hiding system and the particular application,a trade-off between these properties must be attained.The rest of this section has three parts.In thefirst and second parts,the capacity,bit-rate increase and transpar-ency of the system are presented.The third part provides comparison with the existing methods.3.1.Capacity and bit-rate increaseThe embedding method uses high-frequency LNZ level to hide information.Changing QP varies the number of LNZ levels in the high-frequency area of blocks,where increas-ing QP decreases the number of high-frequency LNZ and results in more compression.Figure5shows how increas-ing QP reduces the amount of embedded bits.It is obvious that when the video sequence is more compressed,there is less vacancy for embedding data bits.Almost any modification in QDCT levels causes the bit rate to increase.Table II presents the original bit rate (H.264/AVC compression without data embedding), marked bit rate(H.264/AVC compression with data embedding)and the effect of the proposed embedding algorithm on the compression process in terms of the dif-ference between the original and marked bit rates.The av-erage capacity is354.8bits per QCIF frame,and the average bit-rate increase is0.47%.3.2.TransparencyPeak signal-to-noise ratio can be used as a measure of transparency of the embedding process.Although PSNR is a very popular and widely used evaluation technique,it is known that its correlation to subjective quality measures is not always good because it reflects only the luminance/ chrominance degradations and neglects the behaviour of human perception.Perhaps,a more reliable measuring de-vice is the Structural Similarity Index(SSIM)[25]. Whereas PSNR measures errors between the original and marked image,SSIM measures the structural distortion,lu-minance and contrast differences between the two frames. The main idea behind SSIM is that the human vision sys-tem is specialized in extracting structural information from the viewingfield,and it is not specialized in extracting the errors.Therefore,a measurement on structural distortion can give a better correlation to subjective impressions. Many different quality assessment techniques canbeFigure5.Capacity and QP forfive video test sequences.Table I.Configuration parameters of the JM software.Profile BaselineLevel3Intra period1Frame rate30Rate distortion optimization OnNumber of encoded frames100Watermarking M.Fallahpour,S.Shirmohammadi and M.Ghanbari2951 Security works2015;8:2947–2955©2015John Wiley&Sons,Ltd.DOI:10.1002/secT a b l e I I .C a p a c i t y a n d b i t r a t e (k b p s )f o r a v e r a g e o f 100f r a m e s f o r fiv e v i d e o s e q u e n c e s w i t h d i f f e r e n t q u a n t i z a t i o n p a r a m e t e r (Q P ).Q P =24Q P =34Q P =44O r i g i n a lM a r k e d D i f f e r e n c e (%)O r i g i n a l M a r k e d D i f f e r e n c e (%)O r i g i n a l M a r k e d D i f f e r e n c e (%)C o n t a i n e rB i t r a t e 1146.6891153.3010.58462.9288467.35680.96157.956158.280.21C a p a c i t y 591.34226.8110.51F o r e m a nB i t r a t e 1133.151141.0420.70429.876433.31760.80170.1432170.3270.11C a p a c i t y 498.58116.037.01M o b i l eB i t r a t e 3165.2813174.2570.281570.4161580.1820.62509.6136510.8040.23C a p a c i t y 1328.22890.1790.52N e w sB i t r a t e 1124.591131.9480.65508.5576511.40640.56197.5296197.70.09C a p a c i t y 405.62131.168.77T e n n i sB i t r a t e 1376.2011382.6810.47449.4024452.16720.62157.0344157.38480.22C a p a c i t y 807.72182.8527.58A v e r a g eB i t r a t e 1589.1821596.6460.536684.2362688.8860.712238.4554238.8610.17C a p a c i t y 726.296309.40428.876T a b l e I I I .T r a n s p a r e n c y i n t e r m o f p e a k s i g n a l -t o -n o i s e r a t i o (P S N R ;i n d B )a n d S t r u c t u r a l S i m i l a r i t y I n d e x (S S I M )f o r a v e r a g e o f 100f r a m e s f o r fiv e v i d e o s e q u e n c e s w i t h d i f f e r e n t q u a n t i z a t i o n p a r a m e t e r (Q P ).Q P =24Q P =34Q P =44O r i g i n a l M a r k e d D i f f e r e n c e O r i g i n a l M a r k e d D i f f e r e n c e O r i g i n a l M a r k e dD i f f e r e n c eC o n t a i n e rP S N R 39.4836.662.8232.3731.251.1325.7125.640.07S S I M 0.957720.950550.007170.897810.891410.006400.783970.782690.00128F o r e m a nP S N R 39.3537.861.4932.2531.800.4525.7825.680.10S S I M 0.969260.965810.003450.904130.901300.002830.737570.736580.00099M o b i l eP S N R 37.9031.406.5028.7326.202.5221.0920.840.25S S I M 0.989330.978320.011010.928080.904820.023260.671690.662420.00927N e w sP S N R 40.4338.811.6232.7232.110.6125.4725.410.06S S I M 0.981160.978530.002630.929170.926770.002400.766710.766390.00032T e n n i sP S N R 38.5535.592.9631.5930.640.9526.1825.990.19S S I M 0.948270.935890.012370.795080.788370.006710.667470.664550.00292A v e r a g eP S N R 39.14236.0643.07831.53230.41.13224.84624.7120.134S S I M 0.9691480.961820.0073260.8908540.8825340.008320.7254820.7225260.002956WatermarkingM.Fallahpour,S.Shirmohammadi and M.Ghanbari2952Security works 2015;8:2947–2955©2015John Wiley &Sons,Ltd.DOI:10.1002/secestablished from this assumption but Wang et al.suggested a simple and effective index algorithm [25].Structural Similarity Index is in the range of 0–1,where 0shows zero correlation (i.e.,the reference frame is entirely different from the target)and 1indicates that they are iden-tical.Table III presents the PSNR and SSIM for 100frames of each test sequence with three different QP values (QP =24,34,44).The last two rows are the averages of the five sequences for PSNR and SSIM.The overall aver-age results for all three QPs show a quality degradation of 1.4dB in terms of PSNR and 0.0061for SSIM.The extraction process at the decoder is not complex,which makes the scheme a perfect solution for real-time applications.3.3.Changing thresholdTo show the effects of changing the threshold,Thr ,capac-ity and transparency are measured while Thr is set to 7,9and 11.As Table IV shows,when Thr is equal to 7,there are more LNZ positions changing,which results in more capacity and more distortion compared with when Thr is 9.Moreover,when Thr is equal to 11,there are fewer LNZ positions changing,which leads to less capacity and better transparency compared with when Thr is 9.As such,we can say that there is an inverse relationship between Thr and capacity,whereas there is a direct relationship between Thr and transparency.parison with the existing methods As each data hiding method has its own special properties under different conditions,it is dif ficult to provide a very accurate comparison.Nevertheless,the proposed method can be compared with some existing methods as explained as follows.Yang et al .[8]proposes an information hiding algo-rithm based on intra-prediction modes and matrix coding for H.264/AVC video stream.Yang et al .[8]improves the data hiding algorithm proposed by Hu et al.[26].Yang et al .[8]and Su et al .[26]provide low distortion;however,their capacity is very low,and also,the bit-rate increase is considerable.Ma et al .[27]introduces a high-capacity scheme,which increases the bit rate dramati-cally.Lin et al .[9]enhances the scheme of Ma et al .[27]in terms of capacity and bit-rate increase,but it does not provide general results and only compares its scheme with [27].The original capacity,PSNR and SSIM (with-out embedding)are not reported in [9],so it is really dif-ficult to know the ef ficiency of the system.Mansouri et al.[28]present a high-capacity method,whereas the bit-rate increase is considerable and transparency is not reported.As Table V shows,simulated outcome in a wide range of QPs,24–44.The capacity of the proposed method is very high,and although [27]provides more capacity,the bit-rate increase in [27]is about seveb times more than the proposed method.Noorkami and Merereau [29]and Gong and Lu [30]provide good capacity,but the bit-rate increase is five and eight times more than ours,respec-tively.Also,Noorkami and Merereau [29]distort the im-age by about 6.5dB,which may not be acceptable for many applications.Gong and Lu [30]reduces the quality of the frames by about 3.7dB,which is about three times more than the proposed algorithm.Our suggested scheme presents the best bit-rate in-crease,less than half of the best reported method.On the basis of the SSIM results,our proposed method is veryTable IV.Capacity and transparency for average of 100frames for five video sequences with different thresholds whereQP =24.Thr 7911Container Capacity 754.96591.34334.77PSNR 35.4436.6638.81Foreman Capacity 725.33498.58224.22PSNR 36.7637.8639.2Mobile Capacity 1492.661328.221060.56PSNR 28.0831.435.68News Capacity 549.64405.62311.16PSNR 37.638.8139.15Tennis Capacity 993.76807.72709.04PSNR 34.9335.5936.45AverageCapacity 903.27726.296527.95PSNR34.56236.06437.858PSNR,peak signal-to-noise ratio.Table parison in terms of capacity,bit-rate increase and transparency.Method QP Capacity bits per frameBit-rate increase (%)PSNR degradation SSIM degradation [8]Not reported33–42 1.60.02Not reported [26]2825–40 2.80.02Not reported [27]28840 3.6 2.1Not reported[9]18–43Not reported1.68~6Just marked SSIM is reported [28]Not reported 274 1.1Not reportedNot reported [29]Not reported 764 3.8 6.5Not reported [30]Not reported 766 2.3 3.7Not reportedProposed24–443550.471.40.0061QP,quantization parameter;PSNR,peak signal-to-noise ratio;SSIM,Structural Similarity Index.WatermarkingM.Fallahpour,S.Shirmohammadi and M.Ghanbari 2953Security works 2015;8:2947–2955©2015John Wiley &Sons,Ltd.DOI:10.1002/sectransparent.However,because other schemes do not pro-vide SSIM,comparison in terms of PSNR is also provided in the table.4.CONCLUSIONSTo design an efficient and low complexity method,the em-bedding and extracting of watermarks are integrated with the coding and decoding routines of H.264/AVC.The in-formation hiding system utilizes position of the LNZ level of QDCT block to embed the information bits.To assure transparency to the human visual system,the high-frequency levels are changed.Changing just high-frequency levels can guarantee a high PSNR,SSIM and slight bit-rate increase after the watermark embedding.As the extraction procedure is not complex,the pro-posed technique is an excellent solution for real-time appli-cations such as broadcasting.Experimental results on several test sequences prove that the proposed approach can realize blind extraction with real-time performance,de-livers very high capacity and low distortion and also keeps the bit-rate increase by about0.005. REFERENCES1.Stefan Winkler EDG,Ebrahimi T.Toward perceptualmetrics for video watermark evaluation.SPIE2003;5203:371–378.2.Carli M,Farais M,Gelasca ED,Tedesco R,Neri A.Quality assessment using data hiding on perceptually important areas.In Proc.IEEE Int.Conf.Image Processing,ICIP.Magazzini de Cotone Modulo9 Genova:Italy,2005;III-1200-3–III-1200-3.3.Kapotas S,Skodras A.A new data hiding scheme forscene change detection in H.264encoded video se-quences.In Proc.IEEE Int.Conf.Multimedia Expo ICME.Hanover,Germany,2008;277–280.4.Yilmaz A,Aydin A.Error detection and concealmentfor video transmission using information hiding.Sig-nal Processing:Image Communication2008;23(4): 298–312.5.Li Y,Chen H-X,Zhao Y.A new method of data hid-ing based on H.264encoded video sequences.In Proc.IEEE Int.Conf.Signal Processing,ICSP.Beijing, China,2010;1833–1836.6.Aly HA.Data hiding in motion vectors of compressedvideo based on their associated prediction error.IEEE Transactions on Information Forensics and Security 2011;6(1):14–18.7.Hu Y,Zhang C,Su rmation hiding based onintra prediction modes H.264/AVC.In Proc.IEEE Int.Conf.Multimedia and Expo,ICME.Beijing, China,2007;1231–1234.8.Yang G,Li J,He Y,Kang Z.An information hiding al-gorithm based on intra-prediction modes and matrix coding for H.264/AVC video stream.AEU Interna-tional Journal of Electronics and Communications 2011;65(4):331–337.9.Lin T-J,Chung K-L,Chang P-C,Huang Y-H,Liao H-YM,Fang C-Y.An improved DCT-based perturbation scheme for high capacity data hiding in H.264/AVC intra frames.Journal of Systems and Software2013;86:604–614.10.Lin YC,Li JH.Data hiding with rate-distortion optimi-zation on H.264AVC Video.In Pro.23th IPPR Conf.on Computer Vision,Graphics,and Image Processing, CVGIP.Kaohsiung,Taiwan,2010;15–17.11.Huang X,Abe Y,Echizen I.Capacity adaptive syn-chronized acoustic steganography scheme.Journal of Information Hiding&Multimedia Signal Processing 2010;1(2):72–90.12.Lin SD,Chuang CY,Chen MJ.A WatermarkingScheme by Changing the Number of Nonzero Coeffi-cients in H.264/AVC Encoder.In Pro.22th IPPR Con-ference on Computer Vision,Graphics,and Image Processing,CVGIP,Aug.23–25,2009.13.Jiang X,Sun T,Zhou Y,Shi Y.A drift compensationalgorithm for H.264/AVC video robust watermarking scheme.Digital Forensics and Watermarking2012;7128:30–41.14.Tang Jian,Zheng Jianfeng,Guo Li.H.264/AVC com-pressed domain data hiding algorithm based on in-loop compensation.Image and Signal Processing(CISP), 20114th International Congress on.Vol.1.IEEE,2011.15.Mehmood N,Mushtaq M.Blind watermarking schemefor H.264/AVC based on intra4×4prediction modes.Future Information Technology,Application,and Ser-vice2012;179:1–7.16.Huo W,Zhu Y,Chen H.A controllable error-driftelimination scheme for watermarking algorithm in H.264/AVC stream.IEEE Transactions on Signal Pro-cessing2011;18(9):535–538.17.Richardson IEG.H.264and MPEG-4Video Compres-sion:Video Coding for Next Generation Multimedia.John Wiley&Sons Ltd:New Jersey,2003.18.Shahid Z,Chaumont M,Puech W.Considering the re-construction loop for data hiding of intra and inter frames of H.264/AVC.In Pro.European Signal Processing Conf.,EUSIPCO.EURASIP:Glasgow,Scotland,2009.19.Lie WN,Lin TCI,Tsai DC,Lin GS.Error resilientcoding based on reversible data embedding technique for H.264/AVC video.In Proc.of IEEE International Conf.on Multimedia and Expo,ICME.Amsterdam, The Netherlands,2005.20.Chung KL,Huang YH,Chang PC,Liao HYM.Re-versible data hiding based approach for intra frameWatermarking M.Fallahpour,S.Shirmohammadi and M.Ghanbari 2954Security works2015;8:2947–2955©2015John Wiley&Sons,Ltd.DOI:10.1002/sec。
