计算机英语选择题
计算机专业英语2013影印版课后答案(ComputingEssentials2013)选择题

计算机专业英语2013影印版课后答案(ComputingEssentials2013)选择题计算机专业英语2013影印版课后答案(Computing Essentials 2013)选择题Multiple 11. The keyboard, mouse, monitor, and system unit are:hardware output devices storage devices software2. Programs that coordinate computer resources, provide an interface, and run applications are known as:application programs operating systemsstorage systems utility programs3. A browser is an example of a:basic application specialized programsystem application utility program4. Although not as powerful as a supercomputer, this type of computer is capable of great processing speeds and data storage.mainframe media center midrange netbook5. The smallest type of microcomputer:netbook handheld midrange tablet PC6. RAM is a type of:computer memory network secondary storage 7. Unlike memory, this type of storage holds data and programs even after electrical power to the computer system has been turned off.primary RAM ROM secondary8. The type of file created by word processors to save, for example, memos, term papers, and letters.database document presentation worksheet9. The change in connectivity that uses the Internet and the Web to shift many computer activities from a user’s comput er to computers on the Internet.cloud computing high definition network USB10. The largest network in the world is [the]:Facbeook Internet Web USBMultiple 21. The network that connects computers all over the world.CERN Internet LAN Web2. The rules for exchanging data between computers.DSL protocols Web WWW3. Client-based e-mail accounts require this special program to be installed on your computer.e-mail client hyperlink Java utility4. Communities of individuals who share a common interest typically create Facebook:clients groups pages profiles5. E-mail that does not require an e-mail program installed on a user's computer is known as:blog podcast Webmail utility6. A very well-known microblog.LinkedIn MySpace Twitter Wikipedia7. These programs continually look for new information and update search services’ database programs.filters IM spiders wikis8. A type of search engine that submits requests to other search engines, organizes their responses, eliminates duplicate responses, orders hits, and then provides an edited list.directory search ISPmetasearch engine specialized search engine9. This is th e Internet’s equivalent to traditional cash.digital cash e-commerce icash Internet dollars 10. Using file transfer utility software, you can copy files to your computer from specially configured servers on the Internet. This is called:downloading filtering blogging uploadingMultiple 31. This type of software works with end users, application software, and computer hardware to handle the majority of technical details.application general purpose system utility2. A rectangular area that can contain a document, program, or message.dialog box form frame window3. Programs that create text-based documents.DBMS suites spreadsheets word processors 4. Programs that organize, analyze, and graph numeric data such as budgets and financial reports.DBMS suites spreadsheets word processors5. In a spreadsheet, the intersection of a row and column creates a:cell formula function label6. A collection of related data that is the electronic equivalent of a file cabinet.cell database document table7. A database tool that will quickly rearrange a table’s records according to a selected field.filter sort spreadsheet word processor8. Programs that combine a variety of visual objects to create attractive, visually interesting presentations.DBMS presentation graphics spreadsheet word processor 9. The primary disadvantage of this type of package is that the capabilities of each function are not as extensive as in individual programs.integrated office software utility10. A type of suite stored at a server on the Internet and available anywhere through Internet access.cloud integrated office utilityMultiple 41. These specialized graphics programs combine text and graphics to create publications of professional quality.desktop publishing programs image editorsimage galleries illustration programs2. Also known as drawing programs.desktop publishing programs image editorsimage galleries illustration programs3. Graphics programs used to create and edit vector images.desktop publishing programs image editorsimage galleries illustration programs4. An essential multimedia feature that allows user participation.Flash interactivity immersion raster5. Special programs used to create multimedia presentations.desktop publishing programs Flash editorsimage editors multimedia authoring programs 6. A widely used interactive animation application from Adobe.ACTION Flash Fuzzy WYSIWYG7. Programs for Web site design and HTML coding are called Web page editors orapps HTML editors VR programs Web editors8. This area of artificial intelligence is also known as expert systems.acoustics knowledge-based systems robotics virtual reality 9. A type of artificial intelligence that uses a database to provide assistance to users.acoustics expert systems robotics virtual reality 10. Another name for the database used in expert systems that contains specific facts and rules.access table expert table knowledge base rule baseMultiple 51. What type of software works with users, application software, and computer hardware to handle the majority of technical details?dapplication desktop Linux system2. The programs that convert programming instructions written by programmers into a language that computers understand and process are language: converters linguists managers translators3. The ability to switch between different applications stored in memory is called:diversion multitasking operational interference programming 4. Graphic representations for a program, type of file, or function: app icon image software5. This operating system feature is controlled by a mouse and changes shape depending on its current function.dialog box menu mouse pointer6. The operating system based on Linux, designed for Netbook computers, and focused on Internet connectivity throughcloud computing:Chrome Mac Unix Windows7. The mobile operating system developed by Apple and originally called iPhone OS:Android BlackBerry OS IOS Mac OS8. A utility program that makes copies of files to be used in case the originals are lost or damaged:Backup and Restore Disk Cleanup Disk Defragmenter Compactor 9. A troubleshooting utility that identifies and eliminates nonessential files, frees up valuable disk space, and improves system performance:Backup and Restore Disk Cleanup Disk Defragmenter Compactor 10. Windows makes it easy to update drivers with Windows:Backup Restore Driver UpdateMultiple 61. This container houses most of the electrical components for a computer system.carrier package system board system unit TV tuner2. Similar to notebooks, this system unit specializes in on-the-go Web browsing and e-mail access.chassis desktop media center netbook3. Computers can only recognize this type of electronic signal.analog bus digital maximum4. The main or motherboard is also known as the:computer board processor mobile system system board 5. How many bytes can a 32-bit-word computer access at one time?1 48 166. In a microcomputer system, the central processing unit is contained on a single:bus chip module RAM7. This type of memory divides large programs into parts and stores the parts ona secondary storage device.direct expanded random-access virtual8. Also known as NIC, this adapter card is used to connect a computer to a:AIA expansion graphics network9. This provides a pathway to connect parts of the CPU to each other.bus Plug and Play wired wireless10. Older ports that have largely been replaced by faster, more flexible ports are called:buses expandable legacy renderedMultiple 71. Most keyboards use an arrangement of keys known as:Alpha Daisy OptiKey QWERTY2. The device that controls a pointer displayed on the monitor.cord mouse printer scanner3. Also known as a roller ball, this device controls the pointer by rotating a ball with your thumb.trackball joystick cordless mouse stylus4. The type of screen that can be touched with more than one finger and supports zooming in and out by pinching and stretching your fingers.digital dynamic multitouch OLED5. Flatbed and document are types of:headsets HDTVs monitors scanners6. Device used by banks to automatically read those unusual numbers on the bottom of checks and deposit slips.MICR FDIC OMR UPC7. The most widely used audio-input device.mouse VR microphone TFT8. The monitor feature that specifies how often a displayed image is updated.aspect ratio dot pitch refresh rate resolution rate 9. Handheld, book-sized devices that display text and graphics.e-book readers HDTV lasers whiteboards10. This technology allows television stations to broadcast their programming directly to smartphones, computers, and digital media players.CRT HDTV LED Mobile DTVMultiple 81. RAM is sometimes referred to as:primary storage ratio active memoryread only memory secondary storage2. The actual physical material that holds the data and programs.primary storage media disk access3. Measures how tightly these charges can be packed next to one another on the disk.density cylinders tracks sectors4. When a read/write head makes contact with the hard disk’s surface, it causesa head:crash land pit scratch5. This hard-disk performance enhancement anticipates data needs.disk caching file compression file decompression RAID6. This type of storage uses pits and lands to represent 1s and 0s.cloud hard disk optical solid state7. DVD stands for:digital versatile disc digital video datadynamic versatile disc dynamic video disc8. USB drives are also known as:flash drives optical drives ports universal state bus9. An organizational strategy to promote efficient and safe use of data across the networks.cloud dynamic data mission statemententerprise storage system RAID10. A mass storage device that provides access to data archived on tapes.file system NAS RAID system tape libraryMultiple 91. The concept related to using computer networks to link people and resources.connectivity GPS TCP/IP Wi-Fi2. A high-frequency transmission cable that delivers television signals as well as connects computers in a network. coaxial hi def 3-D twisted pair3. A short-range radio communication standard that transmits data over short distances of up to approximately 30 feet. Bluetooth broadband DSL TCP/IP4. The speed with which a modem transmits data is called its:digital velocity dynamic rate modular rating transfer rate5. The bandwidth typically used for DSL, cable, and satellite connections to the Internet.baseband broadband medium band voiceband6. Every computer on the Internet has a unique numeric address called a(n):IP address DNS broadcast packet7. Sometimes referred to as a LAN adapter, these expansion cards connect a computer to a network.PCMCIA NIC server VPN8. A device that allows one LAN to be linked to other LANs or to larger networks.IDS network gateway PAN switch9. Typically using Wi-Fi technology, these wireless access points are typically available from public places such as coffee shops, libraries, bookstores, colleges, and universities.hotspots extranets PANs LANs10. Star, tree, and mesh are three types of network:topologies protocols strategies devicesMultiple 101. The three primary privacy issues are accuracy, property, and:access ethics ownership security2. To easily get names, addresses, and other details about a person using only his or her telephone number, government authorities and others use a(n): adware cookie keystroke logger reverse directory worm3. Browsers store the locations of sites visited in a:history menu tool bar firewall4. The browser mode that eliminates history files and blocks most cookies.detect insert privacy sleep5. The information that people voluntarily post in social networking sites, blogs, and photo- and video-sharing sites is used to create their:access approval firewall online identity phish6. Computer criminals who specialize in stealing, trading, and using stolen credit cards over the Internet are known as: carders card scammers cyber traders identity thieves7. Programs that come into a computer system disguised as something else are called:Trojan horses viruses Web bugs zombies8. The use of the Internet, cell phones, or other devices to send or post content intended to hurt or embarrass another person is known as:cyber-bullying online harassmentsocial media discrimination unethical communication9. Special hardware and software used to con trol access to a corporation’s private network is known as a(n):antivirus program communication gatefirewall spyware removal program10. To prevent copyright violations, corporations often use:ACT DRM VPN WPAMultiple 111. People who react to technology by thinking computers are magic boxes capable of solving all kinds of problems that computers really can’t handle are: cynics frustrated na?ve proactive2. The type of person that looks at technology in a positive realistic way is:cynical proactive na?ve frustrated3. Books, journals, and trade associations are the best sources to help you:develop personal contacts develop specialtieslook for innovative opportunities maintain your computer competency 4. If your career is in marketing, it makes sense to develop a specialty in:database desktop publishingprogramming systems analysis and design5. What computer professional repairs and installs computer components and systems?computer technician data entry workerdesktop publisher software engineer6. What computer professional designs, tests, and researches encryption procedures?cryptographer network administratorprogrammer software engineer7. What computer professional uses database management software to determine the most efficient ways to organize and access data?cryptographer database administratorprogrammer software engineer8. What computer professional oversees the work of programmers, computer specialists, systems analysts, and other computer professionals?information systems manager network managersoftware engineer technical writer9. What computer professional creates, tests, and troubleshoots computer programs?network manager programmersoftware engineer technical writer10. What computer professional plans and designs information systems?network manager programmersoftware engineer systems analyst。
人教版五年级英语计算机操作指令练习题50题【含答案解析】

人教版五年级英语计算机操作指令练习题50题【含答案解析】1. Tom wants to start his computer. He should click ____.A. "Shut Down"B. "Restart"C. "Power On"答案:C。
解析:“Power On”的意思是开机,是启动计算机时需要点击的选项。
A选项“Shut Down”是关机的意思,用于关闭计算机,不能用于开机操作。
B 选项“Restart”是重启的意思,不是开机操作。
2. When you finish using the computer, if you want to turn it off completely, you should choose ____.A. "Sleep"B. "Hibernate"C. "Shut Down"答案:C。
解析:“Shut Down”是完全关闭计算机的操作指令。
A选项“Sleep”是使计算机进入睡眠模式,计算机并没有完全关闭。
B选项“Hibernate”是休眠模式,也不是完全关闭计算机。
3. The computer is not working well, and you want to start it again. Which option should you click?A. "Log Off"B. "Restart"C. "Cancel"答案:B。
解析:“Restart”是重启计算机的操作,当计算机运行出现问题时可以选择重启来解决一些问题。
A选项“Log Off”是注销用户的操作,与重启计算机无关。
C选项“Cancel”通常是取消某个操作,而不是重启计算机。
4. Lily sees a button on the computer screen that says "Power Off". What will happen if she clicks it?A. The computer will restartB. The computer will turn offC. The computer will go to sleep答案:B。
计算机专业英语测试题及答案

计算机专业英语测试题一、词汇测试题(每小题1分,共20分)(一).Translate the following words and expressions into Chinese (共10分,每题1分)1.Cyber cafe2.microcomputer3.ROM4.Object-oriented programming5.utility program6.system specification7.database administrator8.modulator-demodulator9.client/server model10.spreadsheet program(二).Translate the following terms or phrases from Chinese into English (共10分,每题1分)1.中央处理器2.广域网3.超级计算机4.电子商务5.计算机安全6.计算机文化7.网站8.域名9.数据库管理系统10.软件工程二、完型填空题(每空1分,共20分)Fill in each of the blanks with one of the words given in the list following each paragraph, making changes if necessary:1. Computer hardware is the involved in the of a computer and consists of the that can be physically handled. The function of these components is typically divided into three main categories: , , and . Components in these categories connect to , specifically, the computer’s central unit (CPU), the electronic that provides the computational ability and control of the computer, via wires or circuitry called bus.microprocessors component processing functionoutput equipment input circuitry storage2.In the relational model, data is organized in two-dimensionalcalled . There is no or structure imposed on the data. The tables or relations are, however, related to each other. The database management system (RDBMS) the data so that its external is a of relation or tables. This does not mean that data is stored as tables: the physical of the data is independent of the way in which the is logically organized.hierarchical set organize relational relationdata storage view network table三、英译汉题(每题10分,共20分)Translate the following passage from English into Chinese:1.The field of computer science has grown rapidly since the1950s due to the increase in their use. Computer programs have undergone many changes during this time in response to user need and advances in technology. Newer ideas in computing such as parallel computing, distributed computing, and artificial intelligence, have radically altered the traditional concepts that once determined program form and function. In parallelcomputing parts of a problem are worked on simultaneously by different processors, and this speed up the solution of the problem. Another type of parallel computing called distributed computing use CPUs from many interconnected computers to solve problems. Research into artificial intelligence (AI) has led to several other new styles of programming.2.High-level languages are commonly classified asprocedure-oriented, functional, objected-oriented, logic languages. The most common high-level languages today are procedure-oriented languages. In these languages, one or more related blocks of statements that perform some complete function are grouped together into a program module, or procedure, and given a name such as “procedure A”. If the same sequence of operations is needed elsewhere in the program, a simple statement can be used to refer back to the procedure. In essence, a procedure is just a mini-program. A large program can be constructed by grouping together procedures that perform different tasks.四、汉译英题(20分)最著名的互联网例子是因特网。
计算机专业英语模拟试题附参考答案

计算机专业英语模拟试题一参考答案一、词汇(选择一个最合适的词汇,将对应的英文字母填入空格内。
每题1分,共10分)1、 B refers to the parts of the computer that you can see and touch.A. SoftwareB. HardwareC. HardshipD. Instruction2、primary memory which is stored on chips located A .A. on the motherboardB. outsideC. inside the processorD. on the CPU3、The display screen is the most common C device used to show you what the computer is doing.A. inputB. printingC. outputD. electronic4、Windows gives you more control over the A you work.A. operationB. wayC. energyD. power5、The most important program on any computer is A .A. Operating SystemB. VirusC. softwareD. Office 20006、There are D separate products that form the Windows 2000。
A. only oneB. twoC. threeD. four7、C might best be D as a 'medium-level language'.A. developedB. decodedC. programmedD. described8、Anti-Virus protects your computer from viruses by C your computer's memory and disk devices.A. deletingB. changingC. scanningD. replacing9、Multimedia will become increasingly D throughout every aspect of our lives.A. passB. preciseC. permitD. pervasive10、Communication through the Internet, the C performs the reverse function.A. A station controller (STACO)B. DTEC. Data communications equipment (DCE)D. CRT二、语法——单项选择题(每小题1.5分,共15分)1、The girl I saw D brown hair and blue eyes.A. had sheB. she hadC. herD. had2、I didn't hear the phone last night, I D asleep.A. must beB. must have beenC. should beD. should have been3、He was glad to find the fire A brightly.A. burningB. burnedC. to bumD. have bum4、Though D by what he said ,she didn't believe in him.A. attractingB. she attractedC. attractedD. have been attracted5、 D that ,I could do it much better.A. If I doB. If I were doC. Were I to doD. Were I do6、It was in this very place A I bought the laser printer.A. whereB. whenC. in whichD. that7、He is old enough to tell right C wrong.A. ofB. inC. fromD. to8、 A he did was quite wrong.A. WhatB. ThatC. IfD. Which9、 C , we missed our plane.A. The train being lateB. To be lateC. The train is being lateD. The train which is late10、I wish that I C the concert last night.A. couldB. have attendedC. could have attendedD. attended三、多选(每小题2分,共20分)1、Windows 2000 is abda. new lease of Windows c. the same as Windows NTb. an inventive technology d. used for building a scalable network2、C++ is abc .a. object-oriented c. extended from Cb. procedure-oriented d. a superset of C3、Office automation is ad .a. the application of computer c. communications technologyb. the computer d. used to improve the productivity of people4、Microsoft Office Professional 2000 include abcd .a. Word 2000 c. Excel 2000b. PowerPoint 2000 d. Outlook 20005、Types of media include abd .a. text c. animationb. full-motion video d. audio6、Modem is c .a. a modulator c. a modulator/demodulatorb. a demodulator d. a data set7、The Internet is acd .a. as a common internet c. constrained by a set of IP suiteb. a specific kind of internet d. defined as the network of networks8、Viruses can delay their attack for abcd .a. daysb. weeksc. monthsd. years9、The attributes of the stack are b .a. FIFO c. queueb. LIFO d. built into their circuitry10、With an Internet connection you can get some of the basic services available are:abcda. E-mailb. Telnetc. FTPd. Usenet news四、完形填空(选择一个最合适的答案,将对应的英文字母填入空格内。
计算机专业英语模拟试题及参考答案

A. for, on
B. for, under
C. for, in
D. for, into
6、 Mrs. Snow B in the office for two years before she got a raise.
A. have been working B. had been working C. has been working D. was working
b. animators
d. photographs
8、The end equipment in a communication system includes acd
a. computers
c. CRTs
b. DCE
d. keyboards
9、Applications in the Internet can be found everywhere: abc
d. slowing your PC down
四、 完形填空(选择一个最合适的答案,将对应的英文字母填入空格内。每小题 2 分,共 10 分)
Programs do ( 1 ) the work for us, when we perform tasks ( 2 ) the computer. The
A. linker
B. compiler
C. interpreter
D. computer
9、 The RGB value is composed of A components.
A. one
B. two
C. three
D. four
10、 A virus is a A .
A. program
B. computer
计算机专业英语试题含答案

计算机专业英语试题2Ⅰ. Vocabulary(词汇)(30分)(一).Translate the following words and expressions into Chinese(写出下列词组的汉语。
)(共10分,每题1分)1.operating system2.white box testing3.hard disk4.management information system5.electronic commerce6.relational database7.software engineering8. software maintenance9. menu bar10.network security(二).Fill in the blanks with the corresponding English abbreviations.(根据汉语写出相应的英语缩写。
) (共10分,每题1分)1.只读存储器 2.广域网3.传输控制协议 4.文件传送[输]协议5.通用串行总线 6.面向对象编程7.集成开发环境 8.结构化查询语言9.数据库管理系统 10.开放系统互连(三)Match the following words and expressions in the left column with those similar in meaning in the right column.(将左列的词汇与右列相应的汉语匹配。
)(10分,每空1分)1. application software a. 音频2. machine language b. 应用软件3. structured programming c. 机器语言4. functional testing d. 软件测试5. memory e. 结构化程序设计6. relational database f. 内存7. firewall g. 功能测试8. software testing h. 关系数据库9. hacker i. 黑客10. audio j. 防火墙1. 6.2. 7.3. 8.4. 9.5. 10.Ⅱ. Comprehension(阅读理解)(一)Fill in the blanks with suitable words or expressions from the list given below, and change the form wherenecessary. (从下面方框中选择合适的词或表达,以其适当的形式填空。
商务英语计算机学考选择题测试

商务英语计算机学考选择题测试测试时间30分钟基本信息:[矩阵文本题] *01.利用计算机对指纹进行识别、对图像和声音进行处理属于________应用领域。
[单选题] *A. 科学计算B. 自动控制C. 辅助设计D. 信息处理(正确答案)02.超市收款时扫描货物的条形码,这属于对信息的________ 。
[单选题] *A. 输入(正确答案)B. 输出C. 显示D. 打印03.小明购置了一台家用计算机,它的配置为:Intel(R) Core(TM)i3-2350M .30GHz/4GB/500GB,请问哪个参数表示硬盘大小_______。
[单选题] *A. 2350MBB. 2.3GBC. 4GBD. 500GB(正确答案)04.ROM是________的缩写。
[单选题] *A. 硬盘储存器B. 随机存储器C. 只读存储器(正确答案)D. 光盘存储器05.在计算机的性能指标中,________决定CPU单位时间内的运算次数。
[单选题] *A. 字长B. 主频(正确答案)C. 存储容量D. 存取周期06.以下属于操作系统的是_________。
[单选题] *A. QQB. Windows 7(正确答案)C. 微信D. Word07.想要恢复一个最小化窗口,可以用鼠标左键单击________中该窗口的按钮。
[单选题] *A. 任务栏(正确答案)B. 桌面C. 文件夹D. “开始”菜单08.小明想跟妈妈视频聊天,下列哪种软件无法实现_________。
[单选题] *A. 微信B. QQC. FaceTimeD. E-mail(正确答案)09.接收电子邮件时,收到的邮件中带有回形针标志,说明该邮件_________。
[单选题] *A. 是转发邮件B. 含有附件(正确答案)C. 是未读邮件D. 是垃圾邮件10.《摔跤吧!爸爸》根据真人真事改编,讲述曾经的摔跤冠军辛格培养两个女儿成为女子摔跤冠军,打破印度传统的励志故事。
《计算机专业英语》第01章在线测试
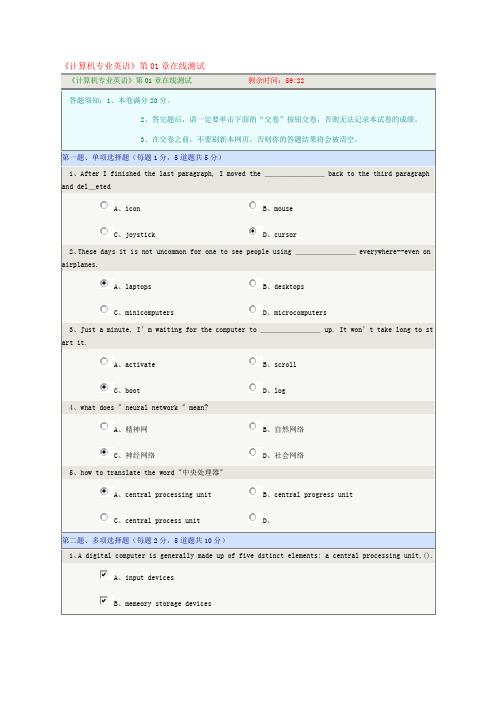
《计算机专业英语》第01章在线测试A BC DThese days it is not uncommon for one to see people usingA BC DJust a minute, I m waiting for the computer to ________A BC Dwhat does " neural network " mean?A BC Dhow to translate the word "A BC DC、output devicesD、a busE、crt screen2、According to the text,modern digital computers can be divided into four major categories on the basis of cost and performance.They are __________________.A、microcomputersB、workstationC、lenovoD、mainframesE、note bookF、minicomputers3、One of trends in computer development is _________,the effort to compress more circui t elements into smaller and smaller ______spaceA、microminiaturizationB、micromoduleC、chipD、chat4、We can define a computer as a device that ______________________A、accepts inputB、deal everythingC、processes dataD、stores dataE、produces output5、A program is a sequence of ________ that can be executed by a computer.It can either be built into the hardware or exist independently in the form of ________.正确错误Computer is able to do different kinds of tasks.正确错误There are no differences between the information processor and human (正确错误In the future, computers are capable of original thoughts.正确错误Information can be input only by people.正确错误。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
计算机英语选择题(1) A large main memory can be used forstoring a,b,c .a. datab. operating systemc. applicationsd. interface(2) Early computer solved c,d problems.a. controlb. business applicationsc. engineeringd. mathematical(3) The system manager used by a fast processor cana,b,c .a. reset a systemb. monitor processor’s core temperaturec. monito r processor’s supply voltagesd. connect a network(4) We can say a bus is simply a,c,d .a. a group of wiresb. a wirec. a 8-bit busd. a 16-bit bus(5) A computer system user generally more cares for b,c,d .a. physical size of the computerb. storage sizec. speed of computationd. efficiency of the computer(6) According to the physical size of computers we canclassify thecomputers into a,b,c,d .a. microcomputerb. minicomputerc. mainframed. supercomputer(7) The basic hardware components of any computerinclude a,b,c,d .a. CPUb. main memoryc. input devicesd. output devices(8) The following devices are belong to the mass storages a,b,d .a. DVDb. CD-ROMc. moused. disk(1) Cache is a,c,d .a. fastb. slowc. relatively smalld. high cost(2) Information stored in semiconductor RAMis b,c .a. permanentb. nonpermanentc. volatiled. non volatile(3) We use paged virtual memory to a,b,c,d.a. extend the size of memoryb. increase bandwidth of the diskc. reduce latency of the diskd. store large program and data set(4)We read data on the disk by a,d .(5) The three desiderata of memory system are b,c .a.independentb. exclusivec.closely approximated todayd. Less approximated tomorrow(6) The processor performance would be high as we reference instructions and data from b,d.a. hard diskb. cachec. floppy diskd. memory(7) Page frame is used in a .a. real memoryb. virtual memoryc. diskd. cache(8) In order to increase our computer’s performance we need to a,b,c ,a. have a L2 cacheb. buy a L2 cachec. have a much larger main memoryd. buy a L1 cache(1) RISC is b,c,d .a. abbreviation of complex instruction set computerb. abbreviation of reduced instruction set computerc. guided to be built from studying the execution behavior of high-level language programsd. used for many computer manufacturers nowadays(2) To enhance performance of a computer system we should a,b,d .a. improve the pattern of referencing operandb. optimize the simple movement of datac. use IF and LOOP instructions as many as possibled. optimize the basic sequence control mechanism(5) Register storage has b,d .a. a large capacityb. a small capacityc. the slower speedd. the faster speed(6) Instruction format in RISC has a,c,d .a. one kindb. many kindsc. a few kindsd. one or a few kinds(7) CISC machine instructions compared with RISC machine are a,d .a. more complicatedb. more simplec. more faster to be executedd. more slower to be executed(8) Functions of the compiler used in RISCare b,c,d .a. to compile a high level language programb. to optimize register usagec. to maximize register usaged. to allocate registers to those variables that will beused the most in a given time period(9) One machine cycle in RISC has c .a. two machine instructionsb. three machineinstructionsc. one machine instructiond. four machineinstructions(10) The register file is a,c,d .a. physically smallb. physically largec. one the same chip as the CPUd. addressed by much shorter addresses Operating systems and middleware b,c,da. have less in commonb. both can support other softwarec. have much in commond. both can support application programs2. An operating system provides the services in its API by a,c,da. using the features of the hardwareb. offering database accessibilityc. using disk drive’s abilityd. offering fixed-length blocks of data4. Middleware lies in b,c,da. the top of the layering vertical stackb. the middle of the layering vertical stackc. the top of an operating systemd. the middle of interactions between different application programs5. The following products of software are belong to middleware a,b,ca. IBM’s Web Sphere MQb. Java 2 Platformc. J2EEd. Oracle6. A mechanism for translating Internet hostnames into IP addresses is a,c,da. typically outside of operating system kernelb. typically inside of operating system kernelc. equipped into the general-purpose operating systemd. as a middleware by author’s definition7. With middleware we can b,c,da. run programs on a centralized computer system onlyb. keep computations largely isolated from undesirable interactionsc. run programs on different computer systemd. allow computations to communicate with one another8. Middleware has mechanisms to support controlled interaction through a,b,c,da. communicationb. namingc. persistent storaged. coordination1. Before you turn the power on with a new computer, you should make sure a,b,c,d.a. the computer is already out of the boxb. appropriate cables are correctly connectedc. the computer system has been set upd. appropriate software have been installed2. An asleep state is a,c,d .a. a low power standby modeb. indicated by the indicator light putting outc. used for saving energyd. used to lessen wear-and tear on the computer4. During the boot procedure we can see a,b,conthe screen.a. amount of memoryb. the number of attached devicesc. the operating system being usedd. beeps and whirling noises5. A user interface we said here is a,b,d .a. an interaction between an operating system anda userb. an interaction between an application program and a userc. an interface between a computer and its peripheral deviced. a text-based user interface or GUI6. Today Microsoft’s ope rating system Windows hasa variety of versions, they are a,b,c,d.a. Windows 2007b. Windows 2003c. Windows XPd. Windows vista7. The Windows desktop contains common elements, such as .a. desktop iconsb. taskbarc. Start buttond. task button9. With the window of the GUI we can use.a. menusb. dialog boxesc. iconsd. documents10. Main menu category in some Microsoft programs .a. is a menu bar at the top of many windowsb. can display a pull-down menusc. can’t display a drop-down menusd. can display personalized menus1. Upgrading a computer system means .a. buying new hardwareb. buying new softwarec. extending the life of your current systemd. keeping your computer in present situation2. To formulate an upgrade strategy, you should consider .a. the PC adheres to a well-supported standardb. you anticipate all your future needsc. there is room for additional expansion cardsd. there is room for memory3. Some common hardware upgrades nclude.a. adding more RAMb. installingADSLc. adding an image scannerd. installing a color printer4. The ways to seriously upgrade an Intel 80486- based PC include .a. installing the most modern softwareb. replacing the motherboardc. replacing other items inside the system unitd. just purchasing a new PC5. Relationship between version and release in a software is .a. version has major numberb. release has minor numberc. version typically increase its number in increments of 1d. release typically increase its number in increments of 0.1 or 0.016. Compatible mode of the software products can be categorized into .a. upwardb. downwardc. crossd. aboveall1. A Wide Area Network can..a. cover a wide geographical areab. link two or more LANsc. link two LANs onlyd. be created by individual users2. According to the flow of information on a transmission facility we can categorize WANinto network.a. circuit switchedb. packet switchedc. local aread. Lease d. line3. In packet switched networks data send in..a. byteb. piecesc. framed. packet4. The most important items contained in a packet should be.a. data to be transmittedb. header of the packetc. tail of the packetd. date5. The popular approaches we used in the packet switched network are .a. circuit switchingb. datagramc. virtual circuitd. real circuit6. In the datagram mode when datagrams arrive at their destination, the datagrams .a. may be out of orderb. must be in orderc. should be reorderedd. may lose7. In the virtual circuit mode all packets sent by a user at a time belong to .a. a messageb. a sessionc. different messagesd. different sessions8. Main characteristics of the leased line networks are .a. the line is private for the userb. the user has himself inter-exchangec. very short response timed. the user computer is always physically connected to the line8. Main characteristics of the leased line networks are .a. the line is private for the userb. the user has himself inter-exchangec. very short response timed. the user computer is always physically connected to the line9. A typical frame relay network has .a. seven componentsb. five componentsc. six componentsd. five major physical components and one "virtual" components10. Router has the following name .a. ARPANETb. IMP (Interface Message Processor)c. gatewayd. IS (Intermediate System)11. In Fig.4-6 a router creates a logical path between networks, these networksinclude .a. FDDIb. Token Busc. Token Ringd. Ethernet12. Encapsulation is used here for data delivering on .a. the circuit switchingb. the physical pathc. the analog circuitd. the logical path1. Connecting to the Internet usually includes the following decisions type of .a. deviceb. connectionc. userd. Internet serviceprovider2. Which device can be used to access the Internet ? .a. PCb.DVDc. notebook computerd. Internetappliance3. Following device belongs to the one of dial-up connection .a.HFCb. modemc. dedicate line devicedd. ADSL4. Using a PC we can retrieve much contents from the Web, they are .a. Web pagesb. multimedia contentsc. video clipsd. music files5. Mobile Web is used for usually.a. notebook computersb. mobile phonesc. handheld computersd. pagers6. When we use a dial-up connection to access the Internet, we need .a. a TV cableb. a regulartelephone linec. a modemd. a temporary IPaddress7. ADSL works at a rate of .a. asymmetric transmissionb. symmetric transmissionc. asymmetric transmission with 9Mb/s downstreamd. asymmetric transmission with 16K-64Kb/s upstream8. We can find the following facilities in an HFC system .a. optical fiberb. coaxial cablec. cable modemd. head end9. With the dedicated connection to connect the Internet we should .a. use dial-up connectionb. keep a continual connectionc. use a static IP addressd. keep a temporary connection10. If some one wants to use mobile wireless connection, he or her should have.a. mobile deviceb. a fixed radioconnectionc. Web-enable cell phoned. a mobile transceiver(1) The true goal of ERP is .a. to integrate all departmentsb. to integrate all functionsc. to work across a companyd.d.to work on a single computer system(2) To do ERP right the ways should change.a. people do their jobsb. you do business with ERPc. you do business without ERPd. people do their jobs with ERP(3) ERP can serve the needs of people in.a. financeb. human resourcesc. warehoused. all above(4) Real transformational ERP efforts usually run .a. five yearsb. three yearsc. two yearsd. one year(5) A business process should include .a. order fulfillmentb. shipping goodsc. billing for the orderd. understanding the customer’s cre dit rating(6) Companies that measure their products by flow rather than individual units arecompanies.a. utilityb. oilc. chemicald. mechanicalparts(7) With ERP, the customer service representatives .a. are just typistsb. are no longer just typistsc. should be business peopled. should not be business people(8) With the manufacturing companiescansave time, increase productivity and reduce headcount.a. standardizing manufacturing processesb. using a single, integrated computer systemc. using ERPd. in-basket mode1. Internet telephony system aresystems.a. synchronous distributedb. asynchronous distributedc. so called as IP telephonyd. synchronous centralized2. The operating platforms that are currently supported by the various Internet telephonysystem include .a. QoSb. UNIXc. Windowsd. Mac3. With an Internet telephone system developed by using Java applet users should .a. have a standard web browser with Java supportb. install the telephony system every time they want to talkc. worry about the underlying workings of a telephony systemd. have a network connection4. The following components are the basic ones of an Internet telephony system .a. host computerb. modemc. local area networkd. router5. The communication p rocess that the caller’s telephony system handled includes .a. acquiring the real-time voice datab. digitizing the analogue signalsc. compressing the digitized datad. decrypting the digitized data6. The communication process that the recipient’s telephony system handled includes .a. encrypting the digitized datab. receiving incoming datac. decompressing incoming datad. playing back on the audio output device7. The major problems encountered in the current Internet telephone are .a. the working model of the best-effort Internetb. transmitting delayc. transmitting delay jittersd. packet loss8. We can find the following voice recovery methods .a. silence substitutionb. waveform substitutionc. sample interpolationd. embedded speech coding9. When we make a distance telephony call such as from Beijing to Guangzhou with Internet telephony system, we should pay communication fees that include .a. transcontinental telephone callsb. local telephone callsc. ISP’s feesd. nominal standard Internet connectivity charges10. The current Internet telephony systems .a. are launched as stand-alone applicationsb. must be downloaded prior to operationc. must purchase a new version of thesoftware of the system for upgradingd. must be installed prior to operation1. The Web took a bold step forward, it .a. was spurred by little-known technologiesb. was spurred by well-known technologiesc. shattered the traditional usage model of the Webd. kept the traditional usage model of the Web2. In order to develop a new web application model we should use some technologies, such as .a. traditional web browsersb. JavaScript remotingc. web remote procedure callsd. dynamic updating3. Using Ajax we can .a. perform the web interactionb. transmit only a small amount of information to and from the serverc. give the user the most responsive experience possibled. substitute the traditional web application model4. In the traditional web application model the browser .a. has an Ajax engineb. is responsible for initiating requests to the Web serverc. is responsible for processing requests from the Web serverd. sends a HTML request to the Web server5. Ajax engine is .a. a JavaScript objectb. a JavaScript functionc. responsible for linking to another resourced. responsible for executing the request from the Web server6. The traditional Web server would serveup .a. JavaScriptb. CSSc. HTMLd. images7. After receiving a server response the Ajax engine .a. goes into actionb. provides a link to another Web pagec. often parses the datad. makes several changes to the user interface8. To make an Ajax solution we must use the following technologies: .a.CSSb. HTML/XHTMLc. DOMd. JavaScript9. With Ajax engine we can .a. transfer less information than the traditional Web application modelb. update user interface more fasterc. work more quicklyd. transfer more information than the traditional web application model10. The data that the Ajax engine can useshould be .a. plain textb. understood by the Ajax enginec. XMLd. any other data format。
