DES c#加密 源码
DES算法的C语言实现
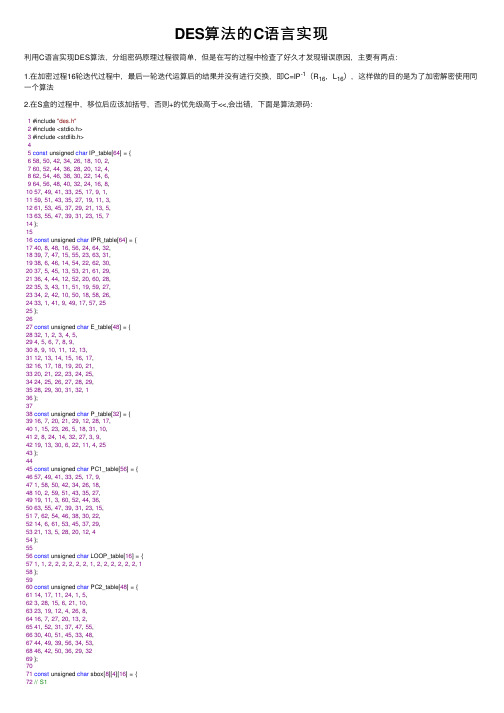
DES算法的C语⾔实现利⽤C语⾔实现DES算法,分组密码原理过程很简单,但是在写的过程中检查了好久才发现错误原因,主要有两点:1.在加密过程16轮迭代过程中,最后⼀轮迭代运算后的结果并没有进⾏交换,即C=IP-1(R16,L16),这样做的⽬的是为了加密解密使⽤同⼀个算法2.在S盒的过程中,移位后应该加括号,否则+的优先级⾼于<<,会出错,下⾯是算法源码:1 #include "des.h"2 #include <stdio.h>3 #include <stdlib.h>45const unsigned char IP_table[64] = {658, 50, 42, 34, 26, 18, 10, 2,760, 52, 44, 36, 28, 20, 12, 4,862, 54, 46, 38, 30, 22, 14, 6,964, 56, 48, 40, 32, 24, 16, 8,1057, 49, 41, 33, 25, 17, 9, 1,1159, 51, 43, 35, 27, 19, 11, 3,1261, 53, 45, 37, 29, 21, 13, 5,1363, 55, 47, 39, 31, 23, 15, 714 };1516const unsigned char IPR_table[64] = {1740, 8, 48, 16, 56, 24, 64, 32,1839, 7, 47, 15, 55, 23, 63, 31,1938, 6, 46, 14, 54, 22, 62, 30,2037, 5, 45, 13, 53, 21, 61, 29,2136, 4, 44, 12, 52, 20, 60, 28,2235, 3, 43, 11, 51, 19, 59, 27,2334, 2, 42, 10, 50, 18, 58, 26,2433, 1, 41, 9, 49, 17, 57, 2525 };2627const unsigned char E_table[48] = {2832, 1, 2, 3, 4, 5,294, 5, 6, 7, 8, 9,308, 9, 10, 11, 12, 13,3112, 13, 14, 15, 16, 17,3216, 17, 18, 19, 20, 21,3320, 21, 22, 23, 24, 25,3424, 25, 26, 27, 28, 29,3528, 29, 30, 31, 32, 136 };3738const unsigned char P_table[32] = {3916, 7, 20, 21, 29, 12, 28, 17,401, 15, 23, 26, 5, 18, 31, 10,412, 8, 24, 14, 32, 27, 3, 9,4219, 13, 30, 6, 22, 11, 4, 2543 };4445const unsigned char PC1_table[56] = {4657, 49, 41, 33, 25, 17, 9,471, 58, 50, 42, 34, 26, 18,4810, 2, 59, 51, 43, 35, 27,4919, 11, 3, 60, 52, 44, 36,5063, 55, 47, 39, 31, 23, 15,517, 62, 54, 46, 38, 30, 22,5214, 6, 61, 53, 45, 37, 29,5321, 13, 5, 28, 20, 12, 454 };5556const unsigned char LOOP_table[16] = {571, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 158 };5960const unsigned char PC2_table[48] = {6114, 17, 11, 24, 1, 5,623, 28, 15, 6, 21, 10,6323, 19, 12, 4, 26, 8,6416, 7, 27, 20, 13, 2,6541, 52, 31, 37, 47, 55,6630, 40, 51, 45, 33, 48,6744, 49, 39, 56, 34, 53,6846, 42, 50, 36, 29, 3269 };7071const unsigned char sbox[8][4][16] = {72// S17314, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7,740, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8,754, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0,7615, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13,77//S27815, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10,793, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5,800, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15,8113, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9,82//S38310, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8,8413, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1,8513, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7,861, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12,87//S4887, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15,8913, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9,9010, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4,913, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14,92//S5932, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9,9414, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6,954, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14,9611, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3,97//S69812, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11,9910, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8,1009, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6,1014, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13,102//S71034, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1,10413, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6,1051, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2,1066, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12,107//S810813, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7,1091, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2,1107, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8,1112, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11112 };113114void ByteToBit(unsigned char* out, const unsigned char* in, const int bits){115for(int i=0;i<bits;i++)116out[i]=(in[i/8]>>(7-i%8))&1;117 }118119void BitToByte(unsigned char* out, const unsigned char* in, const int bits){120 memset(out, 0, (bits + 7) / 8);121for(int i=0;i<bits;i++)122out[i/8]|=in[i]<<(7-i%8);123 }124125void Transform(unsigned char* out,const unsigned char* in, const unsigned char* table, const int len){ 126 unsigned char tmp[64] = {0};127for (int i = 0; i < len; i++)128 tmp[i] = in[table[i] - 1];129 memcpy(out, tmp, len);130 }131132void RotateL(unsigned char* in, const int len, int loop){133static unsigned char tmp[64];134 memcpy(tmp, in, len);135 memcpy(in, in + loop, len - loop);136 memcpy(in + len - loop, tmp, loop);137 }138139static unsigned char subKey[16][48] = { 0 };140void setKey(const unsigned char* in){141char key[64] = { 0 };142 ByteToBit(key, in, 64);143char temp[56]={0};144 Transform(temp, key, PC1_table, 56);145for(int i=0;i<16;i++){146 RotateL(temp, 28, LOOP_table[i]);147 RotateL(temp + 28, 28, LOOP_table[i]);148 Transform(subKey[i], temp, PC2_table, 48);149 }150 }151152void xor(unsigned char* in1,const unsigned char* in2,int len){153for(int i=0;i<len;i++)154 in1[i]^=in2[i];155 }156157void sbox_exchange(unsigned char* out,const unsigned char* in){158char row, column;159for (int i = 0; i < 8; i++){160char num = 0;161 row = (in[6 * i]<<1)+ in[6 * i + 5];162 column = (in[6 * i + 1] << 3) + (in[6 * i + 2] << 2) + (in[6 * i + 3] << 1) + in[6 * i + 4]; 163 num = sbox[i][row][column];164for (int j = 0; j < 4; j++)165 {166out[4 * i + j] = (num >> (3 - j)) & 1;167 }168 }169 }170171void F_func(unsigned char* out,const unsigned char* in,unsigned char* subKey){172 unsigned char temp[48]={0};173 unsigned char res[32]={0};174 Transform(temp, in, E_table, 48);175 xor(temp,subKey,48);176 sbox_exchange(res,temp);177 Transform(out, res, P_table, 32);178 }179180void encryptDES(unsigned char* out,const unsigned char* in, const unsigned char* key){ 181 unsigned char input[64] = { 0 };182 unsigned char output[64] = { 0 };183 unsigned char tmp[64] = { 0 };184 ByteToBit(input, in, 64);185 Transform(tmp, input, IP_table, 64);186char* Li = &tmp[0], *Ri = &tmp[32];187 setKey(key);188for(int i=0;i<16;i++){189char temp[32]={0};190 memcpy(temp,Ri,32);191 F_func(Ri, Ri,subKey[i]);192 xor(Ri, Li, 32);193 memcpy(Li,temp,32);194 }195 RotateL(tmp, 64, 32);//the input is LR,output is RL196 Transform(output, tmp, IPR_table, 64);197 BitToByte(out, output,64);198 }199200void decryptDES(unsigned char* out,const unsigned char* in, const unsigned char* key){ 201 unsigned char input[64] = { 0 };202 unsigned char output[64] = { 0 };203 unsigned char tmp[64] = { 0 };204 ByteToBit(input, in, 64);205 Transform(tmp, input, IP_table, 64);206char* Li = &tmp[0], *Ri = &tmp[32];207 setKey(key);208 RotateL(tmp, 64, 32);209for (int i = 0; i < 16; i++){210char temp[32] = { 0 };211 memcpy(temp, Li, 32);212 F_func(Li, Li,subKey[15 - i]);213 xor(Li, Ri, 32);214 memcpy(Ri, temp, 32);215 }216 Transform(output, tmp, IPR_table, 64);217 BitToByte(out, output, 64);218 }。
用c语言实现des算法

用c语言实现des算法由于DES算法被广泛应用于加密和数据安全方面,因此在计算机科学领域,了解和实现DES算法是非常重要的。
C语言是一种强大的编程语言,其通用性和高效性使其成为实现DES算法的理想选择。
以下是使用C语言实现DES算法的步骤和方法:1.将明文和密钥转换为二进制格式在DES算法中,明文和密钥必须先转换为二进制格式才能进行加密或解密操作。
可以使用一个字符串数组来存储明文和密钥,然后使用C 语言的位运算符将每个字符转换为二进制格式。
2.对明文进行初始置换DES算法的第一步是对明文进行初始置换。
可以使用一个int型数据来存储初始置换后的结果。
3.密钥生成使用密钥生成算法来生成16个48位的子密钥。
可以使用一个二维数组来存储每个子密钥。
4.将初始置换后的明文分为左右两个部分将初始置换后的明文分为左右两个部分,每个部分32位。
5.进行16轮迭代在每轮迭代中,右半部分32位的明文和48位的子密钥进行异或运算,然后使用S盒置换和P盒置换来处理数据。
最后将结果与左半部分32位的明文异或,以更新下一轮迭代所需的数据。
6.合并左右两个部分在进行最后一轮迭代后,将左右两个部分合并成一段64位的二进制数据。
7.进行最后的逆置换使用逆置换来处理上一步生成的64位二进制数据,以生成最终的密文。
实现DES算法需要一定的数学知识和编程技能,因此建议有一定编程基础的人才尝试实现此算法。
列表:1.使用C语言实现DES算法步骤2.将明文和密钥转换为二进制格式的方法3.对明文进行初始置换的具体过程4.密钥生成算法的原理和实现方法5.如何将初始置换后的明文分为左右两个部分6.DES算法16轮迭代的详细过程7.如何合并左右两个部分的数据8.DES算法中的最后一步逆置换的作用和过程9.DES算法的应用场景和重要性10.如何使用C语言实现DES算法的具体步骤和技巧。
数论基础答案

数论基础答案【篇一:现代密码学(谷利泽)课后题答案】>第一章判断题选择题1、1949年,( a )发表题为《保密系统的通信理论》的文章,为密码系统建立了理论基础,从此密码学成了一门科学。
a、shannonb、diffiec、hellmand、shamir2、一个密码系统至少由明文、密文、加密算法、解密算法和密钥5部分组成,而其安全性是由( d)决定的。
a、加密算法b、解密算法c、加解密算法d、密钥3、计算和估计出破译密码系统的计算量下限,利用已有的最好方法破译它的所需要的代价超出了破译者的破译能力(如时间、空间、资金等资源),那么该密码系统的安全性是( b )。
a无条件安全b计算安全c可证明安全d实际安全4、根据密码分析者所掌握的分析资料的不通,密码分析一般可分为4类:唯密文攻击、已知明文攻击、选择明文攻击、选择密文攻击,其中破译难度最大的是( d )。
a、唯密文攻击b、已知明文攻击c、选择明文攻击d、选择密文攻击填空题:5、1976年,w.diffie和m.hellman在密码学的新方向一文中提出了公开密钥密码的思想,从而开创了现代密码学的新领域。
6、密码学的发展过程中,两个质的飞跃分别指1949年香农发表的保密系统的通信理论和公钥密码思想。
7、密码学是研究信息寄信息系统安全的科学,密码学又分为密码编码学和密码分析学。
8、一个保密系统一般是明文、密文、密钥、加密算法、解密算法5部分组成的。
9、密码体制是指实现加密和解密功能的密码方案,从使用密钥策略上,可分为对称和非对称。
10、对称密码体制又称为秘密密钥密码体制,它包括分组密码和序列密码。
第二章选择题:1、字母频率分析法对(b )算法最有效。
a、置换密码b、单表代换密码c、多表代换密码d、序列密码2、(d)算法抵抗频率分析攻击能力最强,而对已知明文攻击最弱。
a仿射密码b维吉利亚密码c轮转密码d希尔密码3、重合指数法对(c)算法的破解最有效。
DES加解密算法C语言源代码

DES加解密算法C语言源代码以下是一个实现DES加解密算法的C语言源代码,包含了加密和解密函数。
请注意,这个代码只是为了演示DES算法的工作原理,并不是一个完整的、安全的加密算法实现。
```c#include <stdio.h>#include <stdint.h>typedef structuint8_t key[8];uint8_t subkeys[16][6];} DESKey;void generateSubkeys(uint8_t* key, uint8_t subkeys[16][6]) //略过子密钥生成算法的具体实现//这里只是假设生成的子密钥都是随机的,实际生成过程要更复杂for (int i = 0; i < 16; i++)for (int j = 0; j < 6; j++)subkeys[i][j] = (i+j) % 256;}}void DES(uint8_t* input, uint8_t key[8], uint8_t* output, int encrypt)//略过DES加密算法的具体实现DESKey desKey;for (int i = 0; i < 8; i++)desKey.key[i] = key[i];}generateSubkeys(key, desKey.subkeys);//这里只是假设输入输出是8字节长,实际上可以支持任意长度//执行加解密操作if (encrypt)printf("Encrypting: ");} elseprintf("Decrypting: ");}for (int i = 0; i < 8; i++)output[i] = encrypt ? input[i] ^ desKey.subkeys[0][i%6] : input[i] ^ desKey.subkeys[15][i%6];printf("%02X ", output[i]);}printf("\n");int maiuint8_t input[8] = {0x12, 0x34, 0x56, 0x78, 0x9A, 0xBC, 0xDE, 0xF0};uint8_t key[8] = {0xA1, 0xB2, 0xC3, 0xD4, 0xE5, 0xF6, 0x07,0x08};uint8_t output[8];DES(input, key, output, 1);DES(output, key, output, 0);return 0;```在这个代码中,`generateSubkeys` 函数用于生成 16 个子密钥,之后分别在加密和解密函数 `DES` 中使用。
C语言加密与解密算法

C语言加密与解密算法在计算机科学与信息安全领域,加密与解密算法起着至关重要的作用。
加密算法用于将原始数据转换为不可读的密文,而解密算法则用于将密文还原为可读的原始数据。
C语言是一种常用的编程语言,具备高效性和灵活性,适用于加密与解密算法的开发。
本文将介绍几种常用的C语言加密与解密算法。
一、凯撒密码算法凯撒密码算法是一种最简单的替换加密算法,通过将字母按照固定的偏移量进行替换来实现加密与解密。
以下是一个简单的C语言凯撒密码实现例子:```c#include <stdio.h>void caesarEncrypt(char* message, int key) {int i = 0;while (message[i] != '\0') {if (message[i] >= 'a' && message[i] <= 'z') {message[i] = (message[i] - 'a' + key) % 26 + 'a';} else if (message[i] >= 'A' && message[i] <= 'Z') {message[i] = (message[i] - 'A' + key) % 26 + 'A';}i++;}}void caesarDecrypt(char* message, int key) {int i = 0;while (message[i] != '\0') {if (message[i] >= 'a' && message[i] <= 'z') {message[i] = (message[i] - 'a' - key + 26) % 26 + 'a'; } else if (message[i] >= 'A' && message[i] <= 'Z') {message[i] = (message[i] - 'A' - key + 26) % 26 + 'A'; }i++;}}int main() {char message[] = "Hello, World!";int key = 3;printf("Original message: %s\n", message);caesarEncrypt(message, key);printf("Encrypted message: %s\n", message);caesarDecrypt(message, key);printf("Decrypted message: %s\n", message);return 0;}```以上程序演示了凯撒密码的加密与解密过程,通过指定偏移量实现对消息的加密与解密。
des加密算法c语言源代码

#include<iostream.h>int IP[64] = {58,50,42,34,26,18,10,2,60,52,44,36,28,20,12,4,62,54,46,38,30,22,14,6,64,56,48,40,32,24,16,8,57,49,41,33,25,17,9,1,59,51,43,35,27,19,11,3,61,53,45,37,29,21,13,5,63,55,47,39,31,23,15,7};int IP_1[64] = {40,8,48,16,56,24,64,32,39,7,47,15,55,23,63,31,38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29,36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,34,2,42,10,50,18,58,26,33,1,41,9,49,17,57,25};int E[48] = {32,1, 2, 3, 4, 5,4, 5, 6, 7, 8, 9,8, 9, 10,11,12,13,12,13,14,15,16,17,16,17,18,19,20,21,20,21,22,23,24,25,24,25,26,27,28,29,28,29,30,31,32,1};int P[32]={16 ,7 , 20 , 21 ,29,12 ,28 , 17 ,1, 15 ,23 , 26 ,5, 18 ,31 , 10 ,2, 8 , 24 , 14 ,32,27, 3 , 9 ,19,13, 30 , 6 ,22,11 ,4 , 25 };void Char_to_Int(unsigned char in[],int out[],int len){for(int i=0;i<len;i++)out[i]=int(in[i]);}void Int_to_Char(int in[],unsigned char out[],int len){for(int i=0;i<len;i++)out[i]=char(in[i]);}void B_to_H(int in[],unsigned char out[]){for(int i=0;i<16;i++){int temp=in[i*4]*8+in[i*4+1]*4+in[i*4+2]*2+in[i*4+3];switch(temp){case 10 :out[i]='A';break;case 11 :out[i]='B';break;case 12 :out[i]='C';break;case 13 :out[i]='D';break;case 14 :out[i]='E';break;case 15 :out[i]='F';break;default :out[i]=unsigned char(temp+48);break;}}}void H_to_B(unsigned char in[],int out[]){for(int i=0;i<16;i++)switch(in[i]){case 'A':out[i*4]=1;out[i*4+1]=0;out[i*4+2]=1;out[i*4+3]=0;break;case 'B':out[i*4]=1;out[i*4+1]=0;out[i*4+2]=1;out[i*4+3]=1;break;case 'C':out[i*4]=1;out[i*4+1]=1;out[i*4+2]=0;out[i*4+3]=0;break;case 'D':out[i*4]=1;out[i*4+1]=1;out[i*4+2]=0;out[i*4+3]=1;break;case 'E':out[i*4]=1;out[i*4+1]=1;out[i*4+2]=1;out[i*4+3]=0;break;case 'F':out[i*4]=1;out[i*4+1]=1;out[i*4+2]=1;out[i*4+3]=1;break;case '0':out[i*4]=0;out[i*4+1]=0;out[i*4+2]=0;out[i*4+3]=0;break;case '1':out[i*4]=0;out[i*4+1]=0;out[i*4+2]=0;out[i*4+3]=1;break;case '2':out[i*4]=0;out[i*4+1]=0;out[i*4+2]=1;out[i*4+3]=0;break;case '3':out[i*4]=0;out[i*4+1]=0;out[i*4+2]=1;out[i*4+3]=1;break;case '4':out[i*4]=0;out[i*4+1]=1;out[i*4+2]=0;out[i*4+3]=0;break;case '5':out[i*4]=0;out[i*4+1]=1;out[i*4+2]=0;out[i*4+3]=1;break;case '6':out[i*4]=0;out[i*4+1]=1;out[i*4+2]=1;out[i*4+3]=0;break;case '7':out[i*4]=0;out[i*4+1]=1;out[i*4+2]=1;out[i*4+3]=1;break;case '8':out[i*4]=1;out[i*4+1]=0;out[i*4+2]=0;out[i*4+3]=0;break;case '9':out[i*4]=1;out[i*4+1]=0;out[i*4+2]=0;out[i*4+3]=1;break;}}void O_to_B(int in[],int out[],int len){int i,j;for(i=0;i<len;i++)for(j=i*len+7;j>=i*len;j--){out[j]=in[i]%2; in[i]=in[i]/2;}}void B_to_O(int in[],int out[],int len){int j;for(int i=0;i<len;i++){j=8*i;out[i]=in[j]*128+in[j+1]*64+in[j+2]*32+in[j+3]*16+in[j+4]*8+in[j+5]*4+in[j+6]*2+in[j+7]*1;}}void Convert(int in[],int out[],int table[],int len){for(int i=0;i<len;i++)out[i]=in[table[i]-1];}void Divide(int in[],int out1[],int out2[],int len){for(int i=0;i<len;i++)if(i<len/2)out1[i]=in[i];elseout2[i-len/2]=in[i];}//正确void Combine(int in1[],int in2[],int out[],int len){for(int i=0;i<len;i++)if(i<len/2)out[i]=in1[i];elseout[i]=in2[i-len/2];}//正确void RLC1(int in[],int out[],int len){int temp=in[0];for(int i=0;i<len-1;i++)out[i]=in[i+1];out[len-1]=temp;}//正确void RLC2(int in[],int out[],int len){int temp1=in[0],temp2=in[1];for(int i=0;i<len-2;i++)out[i]=in[i+2];out[len-2]=temp1;out[len-1]=temp2;}//正确void COPY(int in[],int out[],int len){for(int i=0;i<len;i++)out[i]=in[i];}//ZHENGQUEvoid XOR(int in1[],int in2[],int out[],int len){for(int i=0;i<len;i++)out[i]=(in1[i]+in2[i])%2;}void GetKey(unsigned char in[],int out[16][48]){int i;int Msg_Int[8],Msg_Bin[64],Msg_Bin_PC1[56],Key_Bin[56],C[17][28],D[17][28];char Msg_H[16];int PC1[56]={57,49,41,33,25,17,9,1,58,50,42,34,26,18,10,2,59,51,43,35,27,19,11,3,60,52,44,36,63,55,47,39,31,23,15,7,62,54,46,38,30,22,14,6,61,53,45,37,29,21,13,5,28,20,12,4},PC2[48]={14,17,11,24,1,5,3,28,15,6,21,10,23,19,12,4,26,8,16,7,27,20,13,2,41,52,31,37,47,55,30,40,51,45,33,48,44,49,39,56,34,53,46,42,50,36,29,32};Char_to_Int(in,Msg_Int,8);//正确O_to_B(Msg_Int,Msg_Bin,8);//正确cout<<endl;Convert(Msg_Bin,Msg_Bin_PC1,PC1,56); Divide(Msg_Bin_PC1,C[0],D[0],56);for(i=0;i<16;i++){if(i==0){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else if(i==1){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else if(i==8){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else if(i==15){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else{RLC2(C[i],C[i+1],28);RLC2(D[i],D[i+1],28);}Combine(C[i+1],D[i+1],Key_Bin,56);Convert(Key_Bin,out[i],PC2,48);}} //生成子密钥正确void S_box(int in[],int out[]){int i;int SBox[8][64] ={{14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7,0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8,4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0,15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13},{15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10,3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5,0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15,13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9},{10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8,13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1,13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7,1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12},{7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15,13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9,10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4,3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14},{2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9,14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6,4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14,11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3,},{12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11,10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8,9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6,4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13},{4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6,1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2,6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12},{13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11}};int s1,s3,s2[8];for(i=0;i<8;i++){s1=in[i*6]*2+in[i*6+5]*1;s3=in[i*6+1]*8+in[i*6+2]*4+in[i*6+3]*2+in[i*6+4]*1;s2[i]=SBox[i][s1*16+s3];}int j;for(i=0;i<8;i++)for(j=i*4+3;j>=i*4;j--){out[j]=s2[i]%2; s2[i]=s2[i]/2;}}void Encode(unsigned char in[],unsigned char Final_H[],int K[16][48]){int i;intORINT[8],ORBYTE[64],FinalBYTE[64],LR[64],R48[48],S_in[48],S_out[32],F_RL[32],FinalINT[8],L[17] [32],R[17][32];char ORH[16];Char_to_Int(in,ORINT,8);cout<<""<<endl;O_to_B(ORINT,ORBYTE,8);Convert(ORBYTE,LR,IP,64);Divide(LR,L[0],R[0],64);for(i=1;i<17;i++){Convert(R[i-1],R48,E,48);XOR(R48,K[i-1],S_in,48);S_box(S_in,S_out);Convert(S_out,F_RL,P,32);XOR(F_RL,L[i-1],R[i],32);COPY(R[i-1],L[i],32);}Combine(R[16],L[16],LR,64);Convert(LR,FinalBYTE,IP_1,64);cout<<"二进制的密文:"<<endl;for(i=0;i<64;i++){cout<<FinalBYTE[i];}cout<<endl<<endl;B_to_H(FinalBYTE,Final_H);}void DeCode(unsigned char in[],unsigned char Final_H[],int K[16][48]){int i;intORINT[8],ORBYTE[64],LR[64],R48[48],S_in[48],S_out[32],F_RL[32],FinalBYTE[64],FinalINT[8],L[17] [32],R[17][32];char ORH[16];Char_to_Int(in,ORINT,8);cout<<""<<endl;O_to_B(ORINT,ORBYTE,8);Convert(ORBYTE,LR,IP,64);Divide(LR,L[0],R[0],64);for(i=1;i<17;i++){COPY(R[i-1],L[i],32);Convert(R[i-1],R48,E,48);XOR(R48,K[16-i],S_in,48);S_box(S_in,S_out);Convert(S_out,F_RL,P,32);XOR(L[i-1],F_RL,R[i],32);}Combine(R[16],L[16],LR,64);Convert(LR,FinalBYTE,IP_1,64);B_to_H(FinalBYTE,Final_H);}void main(){int i;unsigned char Msg[8],UnCodeMsg[16],CodeMsg[16],Key[8],Msg_H[16],CodeChar[8];int SKey[16][48];int OrByte[64],OrInt[8],FinalByte[64],FinalInt[8];cout<<"请输入明文:"<<endl;for(i=0;i<8;i++)cin>>Msg[i];cout<<"请输入初始密钥:"<<endl;for(i=0;i<8;i++)cin>>Key[i];GetKey(Key,SKey);Encode(Msg,CodeMsg,SKey);cout<<"十六进制的密文:"<<endl;for(i=0;i<16;i++)cout<<CodeMsg[i];cout<<endl;cout<<"字符型密文:"<<endl;H_to_B(CodeMsg,FinalByte);B_to_O(FinalByte,FinalInt,8);Int_to_Char(FinalInt,CodeChar,8);for(i=0;i<8;i++)cout<<CodeChar[i];cout<<endl;cout<<"请输入十六进制的密文:"<<endl;for(i=0;i<16;i++)cin>>CodeMsg[i];B_to_O(FinalByte,FinalInt,8);Int_to_Char(FinalInt,CodeChar,8);cout<<"请输入解密密钥:"<<endl;for(i=0;i<8;i++)cin>>Key[i];GetKey(Key,SKey);DeCode(CodeChar,Msg_H,SKey);//for(i=0;i<16;i++)// cout<<Msg_H[i];cout<<endl;H_to_B(Msg_H,OrByte);B_to_O(OrByte,OrInt,8);Int_to_Char(OrInt,Msg,8);cout<<"明文是:"<<endl;for(i=0;i<8;i++)cout<<Msg[i];cout<<endl;}。
CIF 和DES 区别

CIF 和DES 是国际贸易中常见的贸易术语,分别译为Cost Insurance and Freight(named port of shipment)成本,保险费加运费(指定目的港);Delivered EX Ship(named port of shipment)目的港船上交货(指定目的港)。
在实际的操作中,两者之间存在很多的异同。
本文试就两者之间在买卖双方履行合同过程中对责任、费用的承担、风险的划分等问题进行分析比较,总结出异同点,以助于更深刻地理解和掌握这两个贸易术语的含义,进一步减少交易中遇到的纠纷,使国际贸易更顺利的进行。
一相同点1 CIF与DES均仅使用于海上或内河运输方式。
在合同中的术语后面都需注明目的港。
2 进出口报关手续的办理责任分配相同。
均是卖方负责办理出口清关,而由买方负责进口报关。
3 如果需要,运输合同与保险合同均由卖方分别与承运人和保险公司签订。
4 价格的构成相同。
CIF的价格均包括成本、运费和保险费。
DES 中,如果卖方需要办理保险,则DES 的价格也由成本、运费和保险费构成。
二不同点1 交货的方式不同目前,在国际上有关贸易术语的案例中,《2000年国际贸易术语解释通则》(简称《2000 通则》)所含术语最多,而且进行了与时俱进的多次修订,成为使用最广,影响最大和最权威的一种国际贸易惯例。
《2000 通则》将13 种贸易术语分成E、F、C、D组,其中C 组贸易术语和D 组贸易术语的主要区别是C 组术语为象征性交货,即交单即交货;而D 组术语为实际交货,即交单还需交货。
这也就是CIF与DES 的一个主要区别:CIF 属于象征性交货;DES属于实际交货。
2 风险的划分界限即交货点不同CIF 术语货物的风险转移点是装运港的船舷,卖方负责货物越过船舷之前的风险和运费,而一旦货物越过了船舷,则发生的一切风险和费用均由买方承担。
DES 术语的风险划分点为目的港船上,在货物运抵目的港船上之前的费用和风险均由卖方负责。
C语言实现CBC模式DES加密

C语⾔实现CBC模式DES加密#define SECTION_SIZE 8 //每段密⽂字节数,DES为8个字节64位#define GET_BIT(x,y) (x |((BYTE)0xff <<9-y) | ((BYTE)0xff >>y)) //将X的第Y位保留,其余位置1#define FORM_DWORD(p1,p2,p3,p4) ((((DWORD)p1) <<24) | (((DWORD)p2) <<16) | (((DWORD)p3) <<8) | ((DWORD)p4)) //四个字节形成⼀个双字#define FORM_BYTE(x,y) ((BYTE)((x & ((DWORD)0xffffffff << 8*(4-y)) & ((DWORD)0xffffffff >> (y-1)*8)) >>(4-y)*8))//将双字X的第Y个字节提取出来#define GET_BIT_LOW(x,y) ((x & ( (BYTE)0xff<<(8-y)) & (BYTE)0xff >> (y-1)) >> (8-y)) //拿到字节X的第Y位//#define ENCRPT //如果定义则为加密,⽆定义为解密#define CHANGE //未⽤//------------------------------------------------------------------------------------------BYTE DisPlaceIPTable[] = { 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4,62, 54, 46, 38, 30, 22, 14, 6, 64, 56, 48, 40, 32, 24, 16, 8,57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3,61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7};BYTE DisPlaceRIPTable[] = { 40, 8, 48, 16, 56, 24, 64, 32, 39, 7, 47, 15, 55, 23, 63, 31,38, 6, 46, 14, 54, 22, 62, 30, 37, 5, 45, 13, 53, 21, 61, 29,36, 4, 44, 12, 52, 20, 60, 28, 35, 3, 43, 11, 51, 19, 59, 27,34, 2, 42, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25};BYTE DisPlaceKEYTable[] = { 57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 27, 19, 11, 3, 60, 52, 44, 36,63, 55, 47, 39, 31, 23, 15, 7, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 28, 20, 12, 4, };BYTE MoveCount[] = { 1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1 };BYTE PC_2[] = { 14, 17, 11, 24, 1, 5, 3, 28, 15, 6, 21, 10, 23, 19, 12, 4, 26, 8, 16, 7, 27, 20, 13, 2,41, 52, 31, 37, 47, 55, 30, 40, 51, 45, 33, 48, 44, 49, 39, 56, 34, 53, 46, 42, 50, 36, 29, 32 };BYTE E_Table[] = { 32, 1, 2, 3, 4, 5,4, 5, 6, 7, 8, 9,8, 9, 10, 11, 12, 13,12, 13, 14, 15, 16, 17,16, 17, 18, 19, 20, 21,20, 21, 22, 23, 24, 25,24, 25, 26, 27, 28, 29,28, 29, 30, 31, 32, 1 };BYTE S1[4][16] = { 14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7,0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8,4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0,15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13};BYTE S2[4][16] = { 15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10,3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5,0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15,13, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9 };BYTE S3[4][16] = { 10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8,13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1,13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7,1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12 };BYTE S4[4][16] = { 7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15,13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9,10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4,3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14 };BYTE S5[4][16] = { 2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9,14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6,4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14,11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3 };BYTE S6[4][16] = { 12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11,10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8,9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6,4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13 };BYTE S7[4][16] = { 4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1,13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6,1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2,6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12 };BYTE S8[4][16] = { 13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7,1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2,7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8,2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11 };BYTE result[] = { 16, 7, 20, 21, 29, 12, 28, 17, 1, 15, 23, 26, 5, 18, 31, 10,2, 8, 24, 14, 32, 27, 3, 9, 19, 13, 30, 6, 22, 11, 4, 25 };//---------------------------------------------------------------------------------typedef struct _BIT{BYTE a : 1;BYTE b : 1;BYTE c : 1;BYTE d : 1;BYTE e : 1;BYTE f : 1;}BIT,*PBIT;typedef struct _8_BIT{BYTE a : 1;BYTE b : 1;BYTE c : 1;BYTE d : 1;BYTE e : 1;BYTE f : 1;BYTE g : 1;BYTE h : 1;}E_BIT,*P4_BIT;LPVOID getTable(int index);DWORD data_rl(DWORD x, BYTE y, BYTE z);PBYTE SHL_Connect(PBYTE p1, PBYTE p2, int index);void ExchangeDword(PVOID p1, PVOID p2);void DisPlaceItem(PVOID fileVa, PBYTE KEY, int length);// DESEncryption.cpp : Defines the entry point for the console application.//#include "stdafx.h"#include "windows.h"#include "myEncpy.h"int _tmain(int argc, _TCHAR* argv[]){//get plaintextHANDLE hFile = CreateFile(L"d:\\a.txt", GENERIC_ALL, FILE_SHARE_READ, 0, OPEN_EXISTING, FILE_ATTRIBUTE_READONLY, NULL); if (hFile == INVALID_HANDLE_VALUE){printf_s("can not create file... d:a.txt");system("pause");return0;}HANDLE hFileMapping = CreateFileMapping(hFile, 0, PAGE_READWRITE, 0, 0, L"myshare");if (hFileMapping == INVALID_HANDLE_VALUE){printf_s("can not create filemapping");system("pause");return0;}LPVOID fileVa = MapViewOfFile(hFileMapping, FILE_MAP_ALL_ACCESS, 0, 0, 0);if (fileVa == NULL){printf_s("can not get mapview");system("pause");return0;}//printf_s("%s\n", fileVa);//使⽤内存映射打开⼤⽂件//---------------------------------------------------------------//get parameter,key,subkeyBYTE KEY[8] = { 'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h' }; //定义密钥DisPlaceItem(KEY, DisPlaceKEYTable,7);PBYTE SubKey[16];BYTE C0[4] = { KEY[0], KEY[1], KEY[2], KEY[3]&0xf0 };BYTE D0[4] = { KEY[3] & 0x0f, KEY[4], KEY[5], KEY[6] };for (int i = 0; i < 16; i++){PBYTE p = SHL_Connect(C0, D0, i);DisPlaceItem(p, PC_2, 6);SubKey[i] = p; //⽣成16个⼦密钥}//-----------------// begain encrypBYTE CBC_IV[] = { 0x11, 0x32, 0x43, 0x54, 0x65, 0x76, 0x87, 0xa8 };//初始化向量未向PBYTE fileOffset =(PBYTE)fileVa; //明⽂起始位置DWORD fileSize = GetFileSize(hFile, 0); //得到明⽂⼤⼩for (DWORD index = 0; index < fileSize / SECTION_SIZE ; index ++) //⽬前只针对凑满8个字节的部分进⾏加密{fileOffset = fileOffset + index *SECTION_SIZE;//for (int i = 0; i < SECTION_SIZE; i++)//{// *(fileOffset + i) ^= CBC_IV[i];//}#ifdef CHANGEDisPlaceItem(fileOffset, DisPlaceIPTable, 8); //IP置换#endif#ifdef ENCRPTfor (int j =0; j <16; j++)#elsefor (int j = 15; j >= 0; j--){#endifBYTE L0[4], R0[6];memcpy(L0, fileOffset, 4);memcpy(R0, fileOffset + 4, 4); //分别拿到左边右边4个字节#ifdef ENCRPTif (j !=15)#elseif (j != 0)#endifmemcpy(fileOffset, R0, 4); //如果不是最后⼀次加密或者解密,则右边直接写回左边elsememcpy(fileOffset + 4, R0, 4);DisPlaceItem(R0, E_Table, 6); //扩展置换PBYTE pbyte1 = SubKey[j];for (int i = 0; i < 6; i++){R0[i] ^= pbyte1[i]; //与右边进⾏异或}//partion----------------------------------------BIT mybit[8] = {0};///////////////////////BYTE t[48]; //把6字节分为6位⼀组共8组int tIndex = 1;int rIdex = 0;for (int i = 0; i < 48; i++){BYTE a = R0[rIdex];t[i] = GET_BIT_LOW(R0[rIdex], tIndex);if (tIndex % 8 == 0){rIdex++;tIndex = 1;}else{tIndex++;}}tIndex = 0;for (int i = 0; i < 48; i+=6){mybit[tIndex].a = t[i];mybit[tIndex].b = t[i+1];mybit[tIndex].c = t[i+2];mybit[tIndex].d = t[i+3];mybit[tIndex].e = t[i+4];mybit[tIndex].f = t[i+5];tIndex++;}//此时mybit⾥⾯放着分组之后的每⼀位////////////////////////BYTE Str[4];int EIndex = 0;BYTE(*tempTable)[16] = 0;for (char i = 0; i < 8; i += 2) //根据mybit拿到表中的数并组合成str{tempTable = (BYTE(*)[16])getTable(i + 1);BYTE sum1 = tempTable[mybit[i].a*2 + mybit[i].f][mybit[i].b*8 + mybit[i].c*4 + mybit[i].d*2 + mybit[i].e];tempTable = (BYTE(*)[16])getTable(i + 2);BYTE sum2 = tempTable[mybit[i + 1].a*2 + mybit[i + 1].f][mybit[i + 1].b*8 + mybit[i + 1].c*4 + mybit[i + 1].d*2 + mybit[i + 1].e]; BYTE sum = sum1 << 4 | sum2;memcpy(Str + EIndex, &sum, 1);EIndex++;}#ifdef CHANGEDisPlaceItem(Str, result, 4); //结果与左边置换#endiffor (int i = 0; i < 4; i++){L0[i] ^= Str[i];}#ifdef ENCRPTif (j != 15)#elseif (j != 0) //将左边写到右边#endifmemcpy(fileOffset + 4, L0, 4);elsememcpy(fileOffset, L0, 4);}#ifdef CHANGEDisPlaceItem(fileOffset, DisPlaceRIPTable, 8);//IP逆置换#endif//memcpy(CBC_IV, fileOffset, 8);//-----------------------------------------------}printf_s("got it");for (int i = 0; i < 16; i++){free(SubKey[i]);}CloseHandle(hFile);CloseHandle(hFileMapping);UnmapViewOfFile(fileVa);system("pause");return0;}void DisPlaceItem(PVOID fileVa,PBYTE KEY,int length) //fileva为需要置换的内容⾸地址 key为置换表,length为输出字节数{PBYTE File = (PBYTE)fileVa;BYTE Result[8] ;memset(Result, 0xff, 8);int DisIndex = 1;for (int i = 0; i < length; i++){int bitofEach = 1;while (true){BYTE temp1 = KEY[DisIndex-1];BYTE ByteIndex = temp1 / 8;ByteIndex = temp1 % 8 == 0 ? ByteIndex -1 : ByteIndex;BYTE BitIndex = temp1- ByteIndex*8;BYTE temptemp = *(File + ByteIndex);if (bitofEach < BitIndex){temptemp = *(File + ByteIndex) << (BitIndex - bitofEach);}else if (bitofEach>BitIndex){temptemp = *(File + ByteIndex) >> (bitofEach - BitIndex);}BYTE t = GET_BIT(temptemp, bitofEach);Result[i] = Result[i] & GET_BIT(temptemp, bitofEach);if (DisIndex % 8 == 0)break;DisIndex++;bitofEach++;}DisIndex++;}memcpy(fileVa, Result, length);}PBYTE SHL_Connect(PBYTE p1, PBYTE p2, int index) //循环移位并连接{PBYTE pbyte = (PBYTE)malloc(7);DWORD d1 = FORM_DWORD(p1[0], p1[1], p1[2], p1[3]);DWORD d2 = FORM_DWORD(p2[0], p2[1], p2[2], p2[3]) <<4;d1 = data_rl(d1, MoveCount[index], 32);d2 = data_rl(d2, MoveCount[index], 32) >>4;for (int i = 0; i < 4; i++){*(p1 + i) = FORM_BYTE(d1, i + 1);*(p2 + i) = FORM_BYTE(d2, i + 1);}memcpy(pbyte, p1, 3);BYTE temp = p1[3] | p2[0];*(pbyte + 3) = temp;memcpy(pbyte + 4, p2, 3);return pbyte;}DWORD data_rl(DWORD x, BYTE y, BYTE z) //移位的实现{DWORD temp;temp = x >> (y - z );temp = temp << 4;x = x << z;x = x | temp;return x;}LPVOID getTable(int index) {switch (index){case1:return S1;break;case2:return S2;break;case3:return S3;break;case4:return S4;break;case5:return S5;break;case6:return S6;break;case7:return S7;break;case8:return S8;break;default:break;}}。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
//名称空间
using System;
using System.Security.Cryptography;
using System.IO;
using System.Text;
public class ClsDES
{
//构造函数
public void ClsDES()
{
}
//方法
//加密方法
public static string Encrypt(string pToEncrypt, string sKey)
{
DESCryptoServiceProvider des = new DESCryptoServiceProvider();
//把字符串放到byte数组中
//原来使用的UTF8编码,我改成Unicode编码了,不行
byte[] inputByteArray = Encoding.Default.GetBytes(pToEncrypt);
//byte[] inputByteArray=Encoding.Unicode.GetBytes(pToEncrypt);
//建立加密对象的密钥和偏移量
//原文使用ASCIIEncoding.ASCII方法的GetBytes方法
//使得输入密码必须输入英文文本
des.Key = ASCIIEncoding.ASCII.GetBytes(sKey);
des.IV = ASCIIEncoding.ASCII.GetBytes(sKey);
MemoryStream ms = new MemoryStream();
CryptoStream cs = new CryptoStream(ms,
des.CreateEncryptor(),CryptoStreamMode.Write);
//Write the byte array into the crypto stream
//(It will end up in the memory stream)
cs.Write(inputByteArray, 0, inputByteArray.Length);
cs.FlushFinalBlock();
//Get the data back from the memory stream, and into a string
StringBuilder ret = new StringBuilder();
foreach(byte b in ms.ToArray())
{
//Format as hex
ret.AppendFormat("{0:X2}", b);
}
ret.ToString();
return ret.ToString();
}
//解密方法
public static string Decrypt(string pToDecrypt, string sKey)
{
DESCryptoServiceProvider des = new DESCryptoServiceProvider();
//Put the input string into the byte array
byte[] inputByteArray = new byte[pToDecrypt.Length / 2];
for(int x = 0; x < pToDecrypt.Length / 2; x++)
{
int i = (Convert.ToInt32(pToDecrypt.Substring(x * 2, 2), 16));
inputByteArray[x] = (byte)i;
}
//建立加密对象的密钥和偏移量,此值重要,不能修改
des.Key = ASCIIEncoding.ASCII.GetBytes(sKey);
des.IV = ASCIIEncoding.ASCII.GetBytes(sKey);
MemoryStream ms = new MemoryStream();
CryptoStream cs = new CryptoStream(ms,
des.CreateDecryptor(),CryptoStreamMode.Write);
//Flush the data through the crypto stream into the memory stream
cs.Write(inputByteArray, 0, inputByteArray.Length);
cs.FlushFinalBlock();
//Get the decrypted data back from the memory stream
//建立StringBuild对象,CreateDecrypt使用的是流对象,必须把解密后的文本变成流对象
StringBuilder ret = new StringBuilder();
return System.Text.Encoding.Default.GetString(ms.ToArray());
}
}。
