Spatial-Spectral Joint Detection for Wideband Spectrum Sensing in Cognitive Radio Networks
两种类型线阵在声场环境下的探测和测向性能仿真研究

摘要阵列的探测和测向性能与实际海洋环境关系较大,不考虑环境特性影响仅基于理想环境下的阵列探测和测向性能与实际使用效果往往存在较大偏差,对实际使用的指导性并不理想。
论文主要对两种类型线阵在声场环境下的探测测向性能进行了仿真研究。
相对于传统理想模型的直线阵探测方法性能仿真研究,论文通过结合声场仿真模型对声场环境下的接收信号进行仿真,来模拟实际声场传播对探测性能的影响;研究了利用大量均匀分布噪声源和海洋环境谱特性滤波器进行仿真来获得具有空间相关性和海洋噪声谱特性的阵列海洋环境噪声信号的仿真方法;然后将仿真的信号和噪声与分裂子阵和等间距线阵的实际测向处理方法相结合进行性能分析,给出更符合实际情况的阵列探测和测向性能仿真分析结果。
首先,对声场环境下的声纳基阵接收信号进行了建模仿真研究。
针对不同工作频段使用两种声仿真软件Kraken和Bellhop来生成声场分布特征,其中利用基于简正波模型的Kraken软件针对低频声场建模仿真,利用基于射线模型的Bellhop软件针对中高频声场单位脉冲响应进行建模仿真。
基于低频和高频信号分别给出两种在声场环境影响下的阵列接收的原始波形信号仿真方法。
然后,对获得具有特定频谱特性的环境噪声和具有空间相关特性的阵列接收环境噪声进行仿真研究。
常规阵列信号处理中常采用统计独立的高斯白噪声进行性能仿真,这与实际海洋环境噪声特性相距甚远。
论文首先利用频域采样法设计了海洋环境噪声频谱滤波器,生成按照一定频谱衰减规律的非白海洋环境噪声,然后利用多声源空间均匀分布的方式来生成具有空间相关性的阵列接收海洋环境噪声,使阵列接收噪声更符合实际。
最后,分别针对分裂子阵线阵和等间距直线阵探测测向性能进行了性能仿真研究。
分裂子阵主要针对中高频宽带连续谱信号,采用两级处理的方式,获得时空处理增益,其中空间处理采用子阵预成多波束来获得空间处理增益,时间处理采用两个子阵对应波束互相关来获得时间处理增益,然后通过拼接后的相关峰实现对目标的探测和测向处理。
多波段红外目标的空谱关联检测算法

㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀空间电子技术SPACE ELECTRONIC TECHNOLOGY㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀2021年第2期多波段红外目标的空谱关联检测算法①南京宏,张义超,李重远,解永锋,陈㊀益(北京宇航系统工程研究所,北京㊀100076)㊀㊀摘㊀要:针对高速运动空中目标在远距离探测过程中能量微弱㊁信噪比低的问题,本文提出了多波段红外目标的空谱关联检测算法㊂首先利用目标的红外成像特性实现噪声滤除㊁目标增强与背景抑制,提升图像对比度,并利用连通域分割方法实现潜在目标区域提取㊂在此基础上,构建目标和背景的多波段光谱特征库,采用RX异常检测算法有效剔除单一波段的虚警,得到多波段红外图像的空谱关联目标检测结果㊂基于不同背景㊁不同光照条件场景下的多波段红外图像数据进行仿真实验㊂实验结果表明,多波段空谱关联检测结果优于任意单一波段的检测结果,目标检测准确率达到98.35%,而虚警率仅为7.5ˑ10-7,验证了本文算法对于远距离目标检测的有效性㊂关键词:多波段;红外图像;空谱关联;目标检测中图分类号:V444.3㊀㊀㊀文献标识码:A㊀㊀㊀文章编号:1674-7135(2021)02-0048-07D O I:10.3969/j.issn.1674-7135.2021.02.008Spatial spectrum correlation detection algorithm formultiple band infrared targetNAN Jinghong,ZHANG Yichao,LI Zhongyuan,XIE Yongfeng,CHEN Yi(Beijing Institute of Aerospace Systems Engineering,Beijing㊀100076,China)Abstract:Aiming to the weak energy and low signal-to-noise ratio of remote and high speed aerial target,the spatial spectrum correlation detection algorithm for multiple band infrared target is proposed.Firstly,the infrared imaging character-istic of target is utilized to filter the noise,together with the target enhancement and background suppression,which improves the contrast of image.Then the connected domain segmentation method is used to extract the potential target area.Besides, the spectrum feature library of multiple band target and background is built,and the RX anomaly detection algorithm is uti-lized to eliminate the false alarm in single band effectively.The spatial spectrum correlation target detection result of the mul-tiple band infrared image is obtained.Simulation experiments are carried out based on multiple band infrared image under different background and illumination conditions.Experimental results demonstrate that the spatial spectrum correlation de-tection result of multiple band is superior to the single band detection result.The target detection accuracy is98.35%,while the false alarm rate is only7.5ˑ10-7,which verifies the effectiveness of the proposed algorithm for remote target detection.Key words:multiple band;infrared image;spatial spectrum correlation;target detection0㊀引言空中目标监视任务日益严峻,呈现出目标多元㊁特性复杂㊁广域分布等特点㊂红外传感器[1]具有功耗低㊁重量轻㊁隐蔽性强等优势,广泛用于民用和军事领域㊂由于高速信号处理芯片㊁数字图像处理等技术的不断发展,红外图像目标检测得到不断拓展和充实完善,形成了大量理论体系[2]㊂按照红外传感器与目标的不同距离阶段划分,红外目标检测算84①收稿日期:2020-07-25;修回日期:2021-03-13㊂作者简介:南京宏(1993 ),助理工程师,主要研究方向为光学/红外目标检测识别㊂E-mail:jinghongnan@ 通讯作者:张义超(1986 ),高级工程师,主要研究方向为空间飞行器电气系统设计㊂E-mail:yichao.zhang@法包括弱小目标检测算法和面目标检测算法㊂在弱小目标检测阶段,目标与红外传感器距离远,由于大气衰减㊁光学散射等因素,目标成像面积小,通常只占几个像素而不具有形状㊁纹理和结构信息,且易受背景噪声干扰,具有一定检测难度㊂国内外学者设计了众多的红外目标检测方法,传统的单帧图像检测方法包括最大均值滤波[3]㊁To-phat滤波[4,5]和小波变换[6]等,但是上述方法在目标信噪比较低时的虚警率高㊂为了同时实现低虚警率和高检测率,利用基于多显著图融合的方法[7,8]和基于稀疏表示的方法[9]实现低信噪比红外目标检测,但是上述方法由于迭代计算导致实时性差㊂近年来出现了基于人类视觉系统(HVS)的红外弱小目标检测方法[10-13],该系列方法通过定义和计算目标与周围背景的局部对比度实现背景抑制和目标增强,从而有效提取目标㊂然而,上述方法仅采用单一波段的红外图像完成目标检测,而超远距离的空中目标成像能量微弱㊁信噪比低,仍存在检测率低㊁虚警率高的问题㊂针对上述问题,本文研究多波段红外目标的空谱关联检测算法㊂1㊀基于空谱关联的多波段红外目标检测算法本文以多波段红外视频为输入信息,针对目标远距离成像能量微弱㊁信噪比低的问题,提出了空谱关联的目标检测算法,总体算法流程如图1所示,包括局部对比度提升的多尺度目标空域检测㊁多波段红外图像的潜在目标光谱鉴别两部分㊂图1㊀基于空谱关联的目标检测总体算法流程Fig.1㊀The overall flow of spatial spectrum correlation target detection algorithm 1.1㊀局部对比度提升的多尺度目标空域检测1.1.1㊀多波段红外图像预处理传统的图像预处理方法包括中值滤波和均值滤波㊂然而,针对远距离目标探测的目标信噪比低㊁点源分布特点,上述预处理方法存在噪声和目标同时滤除的问题㊂由于目标中心点对其八邻域存在一定的红外辐射影响,而噪声中心点孤立存在,所以噪声八邻域的灰度值都很小㊂利用目标邻域与噪声邻域的差异性,本文设计目标保护的高效去噪方法:d cen=18ð8i=1|I cen-I i|(1)㊀㊀其中,d cen表示中心像素灰度值与其八邻域像素灰度值差值的绝对值之和,I cen表示中心像素灰度值,I i表示邻域像素i的灰度值㊂I(x,y)=I(x,y)㊀㊀㊀㊀㊀㊀d cenɤTh dmediumfilter(I(x,y))d cen>Th d{(2)㊀㊀式(2)中,设定阈值Th d,I(x,y)为图像位置(x, y)处的灰度值,mediumfilter(㊃)表示3ˑ3中值滤波㊂在图像预处理过程中,计算每一个像素点的d cen,并与Th d进行比较,如果大于该阈值,则认为是潜在的噪声点,并采用3ˑ3中值滤波进行去噪,否则保留原始灰度值㊂1.1.2㊀多尺度块局部对比度计算在完成图像预处理后,图像存在目标及少量背景噪声㊂本文采用一种多尺度块局部对比度测量方法,进行目标增强和背景抑制,提升目标信噪比㊂针对红外目标局部对比度高于背景局部对比度的特点进行算法设计㊂由于目标面积不超过3ˑ3像素,所以给定尺度sˑs(s=2,3),则中心块区域设为T,其八邻域为B㊂图2㊀图像块八连通域结构图Fig.2㊀Connected domain structure of image block942021年第2期南京宏,等:多波段红外目标的空谱关联检测算法㊀㊀定义目标T 与背景B i 的不相似度为:D (T )=d (T ,B 1)d (T ,B 2)㊀︙d (T ,B 8)æèççççöø÷÷÷÷(3)㊀㊀其中:d (T ,B i )=m T -m B i (i =1,2, ,8)(4)㊀㊀m T 和m B i 分别为中心块区域及其背景区域的灰度均值,计算块局部对比度:d n =d (T ,B i )ˑd (T ,B i +4)(5)㊀㊀由于d n 包含四个值,选择最小值d min 作为当前中心块的局部对比度值㊂采用图像滑窗的方式计算多尺度s ˑs (s =2,3)的局部对比度㊂以多尺度最大响应值代替原始区域像素值并构建对比度响应图,即可实现红外目标增强与背景抑制㊂依据公式(6)对对比度图进行阈值分割和目标提取㊂图像局部对比度图的均值为μ,方差为σ,则定义二值化全局阈值T :T =μ+kσ(6)㊀㊀其中,k 是可调节参数㊂在完成图像阈值分割后,统计二值化图像中的连通体作为目标候选区域,并提取质心位置,得到单帧空间域潜在目标位置结果,如图3所示㊂(a)短波图像㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀(b)中波图像㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀(c)长波图像㊀㊀图3㊀图像增强及潜在目标检测结果Fig.3㊀Image enhancement and potential target detection result㊀㊀由图3可知,在同一探测场景不同波段图像中,潜在目标检测结果存在差异㊂图中圆圈标记了三个5空间电子技术2021年第2期波段均检测到的潜在目标㊂所以需要实现多波段红外图像的目标光谱鉴别㊂1.2㊀多波段红外图像的潜在目标光谱鉴别1.2.1㊀潜在目标及背景光谱提取根据多波段红外图像的潜在目标检测结果,得到数据Y =[Y 1,Y 2,Y 3]T =[y 1,y 2, y N ],其中,Y k 为第k (k [1,3]个波段图像灰度值,y i 为第i (i [1,N ])个潜在目标像元的质心位置,N 为潜在目标像元总数㊂为了实现多波段红外图像的潜在目标光谱鉴别,首先需要采集潜在目标光谱和背景光谱,为分析光谱特征的差异性奠定基础,如图4所示㊂图4㊀多波段红外图像的潜在目标及背景光谱提取结果Fig.4㊀Spectrum extraction result of potential target and background in multiple band infrared image㊀㊀分析图4可知,背景光谱整体平滑且灰度值较低,而潜在目标光谱中部分波段的灰度值较高㊂然而,部分潜在目标受到噪声的影响需要剔除㊂所以利用光谱信息保留有效目标㊂1.2.2㊀多波段图像RX 异常检测为了描述目标光谱与背景光谱的差异性,采用RX 异常检测方法,设F 0表示异常不存在,F 1表示异常存在,则二元假设可表示为:F 0ʒy =O nF 1ʒy =s t +O n(7)㊀㊀式中,O n 表示背景噪声向量,s i 表示异常像元(目标)的光谱向量㊂假设待检验的光谱向量y i 来源于两个具有相同协方差矩阵C b 与不同均值的高斯分布㊂在假设F 0下,y i (背景)服从高斯分布N (0,C b );在另一假设F 1下,y i (目标)服从高斯分布N (s t ,C b ),则针对潜在目标光谱集合中的像元y i ,RX 方法的光谱检测结果可表示为:RX (y i )=(y i -yb )T C -1b (y i -yb )(8)㊀㊀式中,yb ㊁C b 分别为背景光谱的均值向量与协方差矩阵㊂设y bset =[y b 1,y b 2, ,y bN ]为背景像元集合,N 为背景像元总数,则yb ㊁C b 的计算公式为:yb =1N ðNi =1y bi(9)C b =1N ðNi =1(y bi -y b )(y bi -y b )T (10)㊀㊀设阈值为η=mean(RX ),如果RX (y i )ȡη,则像元y i 为空谱检测的目标结果㊂2㊀结果分析首先分析目标检测性能评价指标,并对算法进行定量分析和定性分析㊂2.1㊀性能评价指标本文采用平均检测准确率(TPR )和平均虚警率(FAR )两个指标进行定量分析:TPR =D nR nˑ100%(11)FAR =F pT pˑ100%(12)式中,D n 表示实际检测到的目标数量,R n 表示真实存在的目标数量,F p 表示误检测的像素总数,T p 表示图像全部像素数㊂2.2㊀算法定量分析本文提出的多波段红外目标的空谱关联检测算152021年第2期南京宏,等:多波段红外目标的空谱关联检测算法法包括空间域候选目标检测和光谱域目标精确鉴别两部分内容,实现 空间域快速提取+光谱域精确鉴别 的空谱关联检测㊂本文采用3类背景㊁2类光照条件共计6种典型场景,每个场景中包含180帧多波段图像(短波红外㊁中波红外㊁长波红外),每帧图像中包含3个目标和一定的背景噪声,分阶段验证本文算法的性能㊂2.2.1㊀单波段图像的空间域目标检测结果分析本文提出的空间域目标快速提取算法模块包含多波段红外图像预处理和多尺度块局部对比度计算两部分内容㊂基于6种典型场景的中波红外图像,将本文算法与三种通用的单帧图像目标检测算法LCM[11]㊁MPCM[12]和HB-MLCM[13]进行性能对比,结果如表1所示㊂表1㊀本文空间域检测方法与其它算法的性能对比结果Tab.1㊀Result comparison of our spatial domain detection method and other detection methods 评价指标LCM MPCM HB-MLCM本文方法平均TPR61.32%79.43%85.70%90.73%平均FAR7.12ˑ10-6 3.17ˑ10-6 2.79ˑ10-6 1.11ˑ10-6㊀㊀由表1可知,基于6种典型场景的中波红外图像,本文空间域检测方法的平均TPR为90.73%,平均FAR为1.11ˑ10-6,均优于其它三种对比的方法㊂结果表明本文采用的 图像空间域预处理+多尺度块局部对比度计算 可以有效剔除噪声,提高检测率并降低虚警率㊂2.2.2㊀多波段图像的光谱域目标检测结果分析在单波段图像空间域目标检测结果分析的基础上,对比单波段目标检测与多波段空谱关联检测的结果,如表2所示㊂表2㊀单波段目标检测与多波段空谱关联检测结果对比Tab.2㊀Result comparison of single band target detection and multiple band correlation detection 评价指标短波红外中波红外长波红外多波段红外平均TPR92.04%90.73%88.58%98.35%平均FAR 1.11ˑ10-6 1.11ˑ10-6 1.09ˑ10-67.50ˑ10-7㊀㊀由表2可知,多波段空谱关联检测的准确率和虚警率均优于单一波段㊂其中,多波段检测的平均TPR为98.35%,性能优于短波约6%㊁优于中波约8%㊁优于长波约10%;而多波段检测的虚警率比任意单一波段降低了约30%㊂所以,多波段空谱关联检测结果优于任意单一波段的空域检测结果,验证了 空谱关联检测 的有效性㊂2.3㊀算法定性分析本文定性分析算法结果,场景中包含180帧多波段图像,每帧图像包含3个目标和一定的背景噪声㊂为了方便展示,将目标检测结果用红色矩形框标记在中波输入图像㊂多波段红外目标检测结果如图5所示㊂在第135帧至第160帧图像(以5帧为间隔)中,均准确检测到目标1㊁目标2和目标3,在第155帧存在两个虚警,在第135㊁140㊁145㊁150㊁160帧不存在虚警㊂本文提出的多波段红外目标空谱关联检测算法适用于不同背景和不同光照条件,在保持较低虚警率的前提下,可以有效检测目标㊂25空间电子技术2021年第2期图5㊀多波段红外目标检测结果Fig.5㊀Multiple band infrared target detection result3㊀结论针对远距离多波段空中目标探测,本文提出了基于空谱关联的多波段红外目标检测算法,基于局部对比度提升的多尺度目标检测实现潜在目标提取,并利用多波段红外图像的潜在目标光谱鉴别实现虚警剔除㊂利用多波段(短波1μm~3μm㊁中波352021年第2期南京宏,等:多波段红外目标的空谱关联检测算法3μm~5μm㊁长波8μm~10μm)红外图像数据,在不同背景㊁不同光照条件的场景下验证了空谱关联目标检测算法性能㊂实验结果表明:多波段空谱关联检测结果优于任意单一波段的检测结果,目标检测准确率达到98.35%,而虚警率仅为7.5ˑ10-7㊂参考文献:[1]㊀孙刚.大视场红外搜索系统目标检测关键技术研究[D].长沙:国防科学技术大学,2015.[2]㊀温和,段崇棣,王伟伟,等.一种稳健的多帧联合虚假航迹剔除算法[J].空间电子技术,2019,16(2):40-47.[3]㊀DESHPANDE S D,MENG H E,VENKATESWARLU R,et al.Max-mean and Max-median Filters for Detection ofSmall Targets[C]//SPIE's International Symposium onOptical Science,Engineering,and Instrumentation,1999,3809:74-83.[4]㊀BAI X Z,ZHOU F G.Analysis of New Top-hat Transfor-mation and The Application for Infrared Dim Small TargetDetection[J].Pattern Recognition,2010,43(6):2145-2156.[5]㊀刘晓磊,董小萌,潘忠石,等.空中隐身目标天基探测技术浅析[J].空间电子技术,2020,17(3):8-12. [6]㊀LI L Q,TANG Y Y.Wavelet-hough Transform with Appli-cations in Edge and Target Detections[J].InternationalJournal of Wavelets Multiresolution and Information Pro-cessing,2006,4(3):567-587.[7]㊀NASIRI M,MOSAVI M R,MIRZAKUCHAKI S.IR SmallTarget Detection Based on Human Visual Attention UsingPulsed Discrete Cosine Transform[J].IET Image Pro-cessing,2017,11(6):397-405.[8]㊀DONG L L,WANG B,ZHAO M,et al.Robust InfraredMaritime Target Detection Based on Visual Attention andSpatiotemporal Filtering[J].IEEE Transactions on Geo-science and Remote Sensing,2017,55(5):3037-3050.[9]㊀GAO C Q,MENG D Y,YANG Y,et al.Infrared Patch-im-age Model for Small Target Detection in A Single Image[J].IEEE Transactions on Image Processing,2013,22(12):4996-5009.[10]㊀HAN J H,MA Y,ZHOU B,et al.A Robust InfraredSmall Target Detection Algorithm Based on Human Vis-ual System[J].IEEE Geoscience and Remote SensingLetters,2014,11(12):2168-2172.[11]㊀CHEN C L P,LI H,WEI Y T,et al.A Local ContrastMethod for Small Infrared Target Detection[J].IEEETransactions on Geoscience and Remote Sensing,2014,52(1):574-581.[12]㊀WEI Y T,YOU X G,LI H.Multiscale Patch-based Con-trast Measure for Small Infrared Target Detection[J].Pattern Recognition,2016,58(4):216-226. [13]㊀SHI Y F,WEI Y T,YAO H,et al.High-boost-basedMultiscale Local Contrast Measure for Infrared SmallTarget Detection[J].IEEE Geoscience and RemoteSensing Letters,2018,15(1):33-37.45空间电子技术2021年第2期。
面向高光谱图像的目标检测研究

第44卷第6期航天返回与遥感2023年12月SPACECRAFT RECOVERY & REMOTE SENSING45面向高光谱图像的目标检测研究高大化贺昱董宇波*刘丹华李浩勇石光明(西安电子科技大学,西安710071)摘要现有的高光谱目标检测方法是通过逐像素分类而实现,导致了检测速度缓慢。
物体级目标检测的发展为高光谱图像实时目标检测带来了希望。
为了实现实时高光谱图像目标检测,文章提出了一种基于目标检测模型YOLO的卷积神经网络算法。
首先,该算法提出了用多尺度光谱注意力网络(Res2NetSE)来提取空谱特征,能够提升多尺度目标检测效果并能更有效地提取关键波段信息;其次,该算法提出了一个空间增强的特征金字塔模块(Spatial Enhanced FPN,SFPN)用于特征融合,提升了神经网络的感受野和多尺度性能;最后,该算法设计了FIOU(Fantastic IoU)损失函数,提升了预测框定位精度。
实验结果表明,所提出的算法能够有效提取空间域和光谱域信息特征,分别在平均准确率上提升了14.19%、8.01%和5.38%,与现有方法相比表现出更出色的性能。
文章的算法为高光谱图像的物体级目标检测提供了一种有效的解决方案,有望推动高光谱图像分析领域的进一步发展。
关键词光谱注意力特征金字塔高光谱目标检测物体级目标检测高光谱图像处理中图分类号: TP753文献标志码: A 文章编号: 1009-8518(2023)06-0045-12DOI: 10.3969/j.issn.1009-8518.2023.06.005Object Detection for Hyperspectral ImagesGAO Dahua HE Yu DONG Yubo*LIU Danhua LI Haoyong SHI Guangming(Xidian University, Xiʹan 710071, China)Abstract Existing hyperspectral image (HSI) target detection methods rely on pixel-wise classification, resulting in slow detection speed. The development of object detection offers hope for real-time HSI target detection. To achieve real-time HSI target detection, this paper proposes a Convolutional Neural Network (CNN) algorithm based on YOLO. Firstly, the algorithm introduces a multi-scale spectral attention network (Res2NetSE) to extract spectral features, thereby improving multi-scale target detection and effectively capturing critical spectral information. Secondly, the algorithm presents a Spatial Enhanced Feature Pyramid Module (SFPN) for feature fusion, further enhancing the neural network's receptive field and multi-scale performance.Finally, the algorithm designs a Fantastic IoU (FIOU) loss function to enhance the precision of predicted bounding boxes. Experimental results demonstrate that the proposed algorithm can effectively extract spatial and spectral features, achieving performance improvements of 14.19%, 8.01%, and 5.38% in terms of mean average precision (mAP) when compared to existing methods. The proposed algorithm offers an effective solution for real-time object detection in HSIs, with the potential to advance the analysis of HSI further.收稿日期:2023-06-30基金项目:国家重点研发计划项目(2019YFA0706604);国家自然科学基金(61976169,62293483,62205260)引用格式:高大化, 贺昱, 董宇波, 等. 面向高光谱图像的目标检测研究[J]. 航天返回与遥感, 2023, 44(6): 45-56.GAO Dahua, HE Yu, DONG Yubo, et al. Object Detection for Hyperspectral Images[J]. Spacecraft Recovery &Remote Sensing, 2023, 44(6): 45-56. (in Chinese)46航天返回与遥感2023年第44卷Keywords spectral attention; feature pyramid networks; HSI target detection; object detection; HSI processing0 引言高光谱成像技术是利用成像光谱仪,在光谱覆盖范围内的数十或数百条光谱波段对目标物体连续成像。
华为SecoManager安全控制器产品介绍说明书
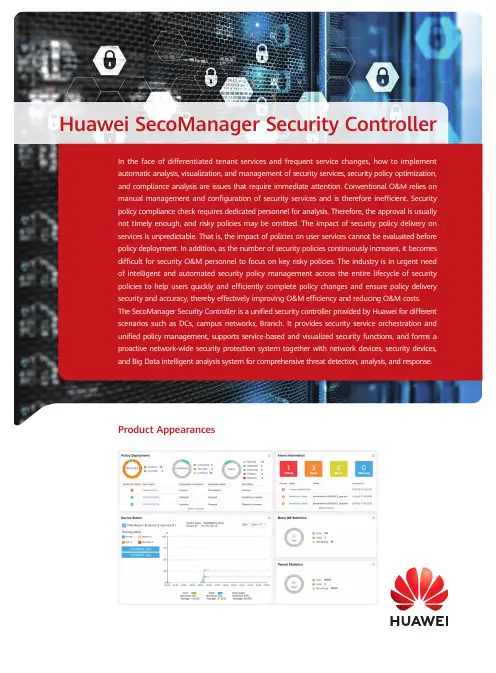
Huawei SecoManager Security ControllerIn the face of differentiated tenant services and frequent service changes, how to implementautomatic analysis, visualization, and management of security services, security policy optimization,and compliance analysis are issues that require immediate attention. Conventional O&M relies onmanual management and configuration of security services and is therefore inefficient. Securitypolicy compliance check requires dedicated personnel for analysis. Therefore, the approval is usuallynot timely enough, and risky policies may be omitted. The impact of security policy delivery onservices is unpredictable. That is, the impact of policies on user services cannot be evaluated beforepolicy deployment. In addition, as the number of security policies continuously increases, it becomesdifficult for security O&M personnel to focus on key risky policies. The industry is in urgent needof intelligent and automated security policy management across the entire lifecycle of securitypolicies to help users quickly and efficiently complete policy changes and ensure policy deliverysecurity and accuracy, thereby effectively improving O&M efficiency and reducing O&M costs.The SecoManager Security Controller is a unified security controller provided by Huawei for differentscenarios such as DCs, campus networks, Branch. It provides security service orchestration andunified policy management, supports service-based and visualized security functions, and forms aproactive network-wide security protection system together with network devices, security devices,and Big Data intelligent analysis system for comprehensive threat detection, analysis, and response.Product AppearancesProduct HighlightsMulti-dimensional and automatic policy orchestration, security service deployment within minutes• Application mutual access mapping and application-based policy management: Policymanagement transitions from the IP address-based perspective to the application mutual access relationship-based perspective. Mutual-access relationships of applications on the network are abstracted with applications at the core to visualize your application services so that you can gain full visibility into the services, effectively reducing the number of security policies. The model-based application policy model aims to reduce your configuration workload and simplify network-wide policy management.• Policy management based on service partitions: Policy management transitions from thesecurity zone-based perspective to the service partition-based perspective. Conventional network zones are divided into security zones, such as the Trust, Untrust, DMZ, and Local zones. In a scenario with a large number of security devices and a large network scale, factors of security zone, device, policy, service rollout, and service change are intertwined, making it difficult to visualize services and to effectively guide the design of security policies. However, if security policies are managed, controlled, and maintained from the perspective of service partitions, users need to pay attention only to service partitions and security services but not the mapping among security zones, devices, and services, which effectively reduces the complexity of security policy design.Service partition-based FW1untrusttrustDMZ XXX FW2untrust trustDMZ XXX FW3untrust trust DMZ XXX InternetGuest partition R&D partition Data storage partitionExternal service partition Internal service partition• Management scope of devices and policies defined by protected network segments to facilitate policy orchestration: A protected network segment is a basic model of security service orchestration and can be considered as a range of user network segments protected by a firewall.It can be configured manually or through network topology learning. The SecoManager Security Controller detects the mapping between a user service IP address and a firewall. During automatic policy orchestration, the SecoManager Security Controller automatically finds the firewall that carries a policy based on the source and destination addresses of the policy.• Automatic security service deployment: Diversified security services bring security assurance for data center operations. Technologies such as protected network segment, automatic policy orchestration, and automatic traffic diversion based on service function chains (SFCs) enable differentiated tenant security policies. Policies can be automatically tiered, split, and combined so that you can gain visibility into policies.Intelligent policy O&M to reduce O&M costs by 80%• Policy compliance check: Security policy compliance check needs to be confirmed by the security approval owner. The average number of policies to be approved per day ranges from several to hundreds. Because the tool does not support all rules, the policies need to be manually analyzed one by one, resulting in a heavy approval workload and requiring a dedicated owner to spend hours in doing so. The SecoManager Security Controller supports defining whitelists, risk rules, and hybrid rules for compliance check. After a policy is submitted to the SecoManager Security Controller, the SecoManager Security Controller checks the policy based on the defined check rules and reports the check result and security level to the security approval owner in a timely manner.In this way, low-risk policies can be automatically approved, and the security approval owner needs to pay attention only to non-compliant policy items, improving the approval efficiency and avoiding the issues that the approval is not timely and that a risky policy is omitted.• Policy simulation: Based on the learning result of service mutual access relationships, the policies to be deployed are compared, and their deployment is simulated to assess the impact of the deployment, effectively reducing the risks brought by policy deployment to services.• Redundant policy deletion: After a policy is deployed, redundancy analysis and hit analysis are performed for policies on the entire network, and the policy tuning algorithm is used, deleting redundant policies and helping you focus on policies closely relevant to services.Network collaboration and security association for closed-loop threat handling within minutes • Collaboration with network for threat handling: In a conventional data center, application deployment often takes a long time. The application service team relies on the network team to deploy the network; the network team needs to understand the requirements of the application service team to deploy a network that is suitable for the application service team. The SecoManager Security Controller learns mappings between service policies and security policies based on the network topology, and collaborates with the data center SDN management and control system (IMaster NCE-Fabric) or campus SDN management and control system to divert tenant traffic to corresponding security devices based on SFCs on demand. The SecoManager Security Controller automatically synchronizes information about the tenants, VPCs, network topology (including logical routers, logical switches, logical firewalls, and subnets), EPGs, and SFCs from the SDN management and control system and combines the learned application service mutual access relationships to automatically orchestrate and deliver security policies, implementing security-network synergy.• Collaboration with security: Advanced persistent threats (APTs) threaten national infrastructure of the finance, energy, government, and other sectors. Attackers exploit 0-day vulnerabilities, use advanced evasion techniques, combine multiple attack means such as worm and ransomware, and may remain latent for a long period of time before they actually initiate attacks. The Big Data security product HiSec Insight can effectively identify unknown threats based on network behavior analysis and correlation analysis technologies. The threat handling method, namely isolation or blocking, is determined based on the threat severity. For north-south threats, the SecoManager Security Controller delivers quintuple blocking policies to security devices. For east-west threats, isolation requests are delivered to the network SDN management and control system to control switches or routers to isolate threatened hosts.Product Deployment• Independent deployment: The SecoManager Security Controller is deployed on a server or VM as independent software.• Integrated deployment: The SecoManager Security Controller and SDN management and control system are deployed on the same physical server and same VM.Database• Collaboration with the SDN management and control system to detect network topology changes and implement tenant-based automatic security service deployment.• North-south threat blocking, east-west threat isolation, and refined SDN network security control through SFC-based traffic diversion.• Interworking with the cloud platform to automatically convert service policies to security policies. Product SpecificationsOrdering InformationNote: This product ordering list is for reference only. For product subscription, please consult Huawei representatives. GENERAL DISCLAIMERThe information in this document may contain predictive statement including, without limitation, statements regarding the future financial and operating results, future product portfolios, new technologies, etc. There are a number of factors that could cause actual results and developments to differ materially from those expressed or implied in the predictive statements. Therefore, such information is provided for reference purpose only and constitutes neither an offer nor an acceptance. Huawei may change the information at any time without notice.Copyright © 2020 HUAWEI TECHNOLOGIES CO., LTD. All Rights Reserved.。
简析两种不同数据采集方式对卫星干扰源定位性能的影响

Radio Wave Guard电波卫士DCW55数字通信世界2020.120 引言卫星干扰源定位普遍采用双星定位技术对干扰源上行站进行定位,而双星定位结果的精度主要取决于双星星历的精度,目前,定位卫星干扰源使用的星历主要从国外公开网站下载。
公开星历若直接用于卫星干扰源定位,定位误差为几百千米至几千千米,此时定位结果完全失去意义。
为了得到较为精确的定位结果,干扰源定位系统需要发射多个上行站地理位置分散的参考源信号用以校准双星星历,其中,参考源信号是指受干扰卫星上已知频点及上行站位置的星上信号。
通过对星历校准,定位结果精度可提升至几十千米量级。
当前,主流定位系统对参考源及干扰信号的采集方式普遍为窄带模式,该模式会给星历校准模型引入额外的误差,随着 AD 技术的迅速发展,基于 500 MHz 超宽带采集的卫星干扰源定位系统已投入使用,能够提升卫星干扰源定位精度。
1 双星定位原理当某颗地球静止轨道卫星受到干扰时,干扰源天线的主瓣对着目标卫星(以下简称主星),干扰源天线的某个旁瓣对着用以辅助定位的某一颗卫星(以下简称邻星)。
由于两颗卫星的位置不一样,使两路信号到达接收站的时间不一致而产生时差TDOA (Time Difference of Arrival ),定位系统基于地球固定坐标系在地图上得出一条TDOA 线;由于两颗卫星运动速度的不一致使两路信号被接收时产生多普勒频差FDOA (Frequency Difference of Arriva ),定位系统在地图上得出一条FDOA 线,两条线的交点即为干扰源上行站位置。
描述卫星位置和速度的信息称之为星历。
干扰源定位的精度对星历精度高度敏感,例如,星历如果在速度上存在0.2 m/s 的误差,将导致定位结果偏离实际干扰源地点多达上千千米。
所以,星历校正技术是定位系统的关键技术。
图1 双星定位示意图2 引入参考源的定位方程简析两种不同数据采集方式对卫星干扰源定位性能的影响李思静,蔡鸿昀,周 平(国家无线电监测中心深圳监测站,广东 深圳 518120)摘要:卫星干扰源定位中,1个目标信号和5个参考信号随机分布在一段带宽上面,如果采集卡能一次将6个信号同时采集,则为宽带采集模式;若6个信号需要分批次采集,则为窄带采集模式。
GF2遥感影像预处理全流程

GF2遥感影像预处理全流程GF2遥感影像数据集处理写在前头:为个⼈学习的总结,过段时间会把IDL⾃动化处理的代码整理上传,该⽂章参考了很多⼤佬的博⽂,稍后会整理⼀并给出。
数据分析:以GF2_PMS1为例:命名规则:GF2_PMS1_E55.4_N25.3_20210205_L1A0005457874GF2:⾼分⼆号PMS1:⼀台PMS多光谱相机E55.4_N25.3:经纬度20210205:时间L1A:级别0005457874:编号⽂件说明:⽂件总览MSS多光谱图像:空间分辨率低,光谱分辨率⾼PAN全⾊图像:空间分辨率⾼,光谱分辨率低rpb ⽂件:⽤于图像正射校正xml ⽂件:图像对应参数⽂件总览⾼分影像处理流程:1.辐射定标(⼤⽓校正的准备⼯作):⼀般来讲,辐射定标就是将图像的数字量化值(DN )转化为辐射亮度值或者反射率或者表⾯温度等物理量的处理过程。
2.⼤⽓校正:当太阳辐射通过⼤⽓以某种⽅式⼊射到物体表⾯然后再反射回传感器,由于⼤⽓⽓溶胶、地形和邻近地物等影像,使得原始影像包含物体表⾯,⼤⽓,以及太阳的信息等信息的综合。
⽽如果我们想要了解某⼀物体表⾯的光谱属性,我们必须将它的反射信息从⼤⽓和太阳的信息中分离出来,这就需要进⾏⼤⽓校正过程。
3.正射校正(⼏何校正):先进⾏辐射定标和⼤⽓校正,然后进⾏⼏何校正。
因为⼏何校正的时候会重采样,重采样会改变像元值,从⽽影响辐射定标和⼤⽓校正的结果。
4.NOTE :辐射校正=辐射定标+⼤⽓校正全⾊图像不进⾏⼤⽓校正以GF2_PMS1为例:多光谱图像(MSS )与全⾊图像(PAN ):PAN总览图PAN部分细节图多光谱图像(MSS):辐射定标部分(Radiometric Calibration):辐射定标步骤:说明⽰例右击然后点击View Metadata,可以看到影像的元数据信息,点击Spectral,查看辐射定标系数,可与中国资源卫星中⼼下载得到的绝对辐射定标系数对⽐。
什么是回声定位-蝙蝠和人类世界(中英)
什么是回声定位?动物和人类世界的定义和例子回声定位是某些动物用来在低能见度区域定位物体的生理过程。
动物发出高音波,从物体上反弹,返回“回声”,并为它们提供有关物体大小和距离的信息。
这样,即使在看不见的情况下,他们也能够绘制并导航周围的环境。
该技能主要用于夜间活动、深挖洞或生活在大洋中的动物。
因为他们生活或狩猎在光线极少或完全黑暗的地方,所以他们已经进化到不再依赖视觉,而是使用声音来创造他们周围环境的心理形象。
动物的大脑已经进化到能够理解这些回声,它们会根据音高、音量和方向等特定的声音特征来导航周围环境或寻找猎物。
遵循类似的概念,一些盲人已经能够通过点击他们的舌头来训练自己使用回声定位。
Echolocation is a physiological process that certain animals use to locate objects in areas of low visibility. The animals emitshigh-pitched sound waves that bounce off objects, returning an “echo” and providing them information about the object’s size and distance. This way, they are able to map out and navigate their surroundings even when unable to see.The skill is mainly reserved for animals who are nocturnal, deep burrowing, or live in large oceans. Because they live or hunt in areas of minimal light or complete darkness, they have evolved to rely less on sight, using sound to create a mental image of their surroundings instead. The animals' brains, which have evolved to understand these echoes, pick up on specific sound features like pitch, volume, and direction to navigate their surroundings or find prey.Following a similar concept, some people who are blind have been able to train themselves to use echolocation by clicking their tongues.How Does Echolocation Work?To use echolocation, an animal must first create some kind of sound pulse. Typically, the sounds consist of high-pitched or ultrasonic squeaks or clicks. Then, they listen back for the echoes from the emitted sound waves bouncing off objects within their environment. Bats and other animals that use echolocation are specially tuned to the properties of these echos. If the sound comes back quickly, the animal knows the object is closer; if the sound is more intense, it knows the object is bigger. Even the echo’s pitch helps the animal map its surroundings. An object in motion towards them creates ahigher pitch, and objects moving in the opposite direction result in a lower-pitched returning echo.Studies on echolocation signals have found genetic similarities between species that use echolocation. Specifically, orcas and bats, who’ve shared specific changes in a set of 18 genes connected to cochlear ganglion development (the group of neuron cells responsible for transmitting information from the ear to the brain).1 Echolocation isn’t just reserved for nature anymore, either. Modern technologies have borrowed the concept for systems like sonar used for submarines to navigate, and ultrasound used in medicine to display images of the body.Animal EcholocationThe same way that humans can see through the reflection of light, echolocating a nimals can “see” through the reflection of sound. The throat of a bat has particular muscles that allow it to emit ultrasonic sounds, while its ears have unique folds that make them extremely sensitive to the direction of sounds. While hunting at night, bats let out a series of clicks and squeaks that are sometimes so high-pitched that they are undetectable to the human ear. When the sound reaches an object, it bounces back, creating an echo and informing the bat ofits surroundings. This helps the bat, for example, catch an insect in mid-flight.Studies on bat social communication show that bats use echolocation to respond to certain social situations and distinguish between sexes or individuals, as well. Wild male bats sometimes discriminate approaching bats based solely on their echolocation calls, producing aggressive vocalizations towards other males and courtship vocalizations after hearing female echolocation calls.2Toothed whales, like dolphins and sperm whales, use echolocation to navigate the dark, murky waters deep beneath the ocean’s surface. Echolocating dolphins and whales push ultrasonic clicks through their nasal passages, sending the sounds into the marine environment to locate and distinguish objects from near or far distances.The sperm whale’s head, one of the largest anatomical structures found in the animal kingdom, is filled with spermaceti (a waxy material) that helps sound waves bounce off the massive plate in its skull. The force focuses the sound waves into a narrow beam to allow for more accurate echolocation even over ranges of up to 60 kilometers. Beluga whales use the squishy round part of their foreheads(called a “melon”) to echolocate, focusing signals similarly to sperm whales.Human EcholocationEcholocation is most commonly associated with non-human animals like bats and dolphins, but some people have also mastered the skill. Even though they aren’t capable of hearing the high-pitched ultrasound that bats use for echolocation, some people who are blind have taught themselves to use noises and listen to the returning echoes to make better sense of their surroundings. Experiments in human echolocation have found that those who train in “human sonar” may present better performance and target detection if they make emissions with higher spectral frequencies.3 Others have discovered that human echolocation actually activates the visual brain.4Perhaps the most famous human echolocator is Daniel Kish, president of World Access for the Blind and an expert in human echolocation. Kish, who has been blind since he was 13 months old, uses mouth clicking sounds to navigate, listening to echoes as they reflect from surfaces and objects around him. He travels the world teaching other people to use sonar and has been instrumental in raising awareness for human echolocation and inspiring attention among the scientific community. In an interview with Smithsonian Magazine, Kish described his unique experience with echolocation:It’s flashes. You do get a continuous sort of vision, the way you might if you used flashes to light up a darkened scene. It comes into clarity and focus with every flash, a kind of three-dimensional fuzzy geometry. It is in 3D, it has a 3D perspective, and it is a sense of space and spatial relationships. You have a depth of structure, and you have position and dimension. You also have a pretty strong sense of density and texture, that are sort of like the color, if you will, of flash sonar.。
SPOT多光谱影像与全色波段融合
SPOT多光谱影像与全色波段融合
SPOT多光谱影像的分辨率为20m分辨率,全色为10m分辨率
1、在实习数据路径下打开s_0417_2.bil(多光谱数据)和s_0417_1.bil(全色波段数据),加载到显示窗口中,查看其范围和大小(前者为1418x1114,后者为2835x2227),确定采样系数。
2、在主菜单中选择Basic Tools-Resize Data(Spatial/Spectral),选择多光谱文件(s_0417_2.bil)单击OK。
3、在Resize Data Parameters对话框中的xfac和yfac文本框中分别键入1.999,以使重采样后的图像大小与全色波段一致。
键入输出文件名,单击OK。
4、与前述一样,将重采样图像加载到显示窗口中,在主菜单中选择
Transform-Image Sharpening-HSV,选择重采样图像的显示索引号,单击OK,再选择全色波段作为高分辨输入图像:
5、单击OK,键入输出文件名,单击OK,执行融合,查看结果,并比较其与多波段合成影像与全波段灰度影像的区别。
下图为融合图像:。
基于面部多特征跨层融合网络的驾驶员疲劳检测方法
第38卷第6期2023年12月安 徽 工 程 大 学 学 报J o u r n a l o fA n h u i P o l y t e c h n i cU n i v e r s i t y V o l .38N o .6D e c .2023文章编号:1672-2477(2023)06-0064-08收稿日期:2023-06-13基金项目:安徽省高校优秀青年基金项目(2023A H 030020)作者简介:徐文奇(1991-),男,浙江宁波人,助理实验师,硕士㊂通信作者:胡耀聪(1992-),男,安徽芜湖人,讲师,博士㊂基于面部多特征跨层融合网络的驾驶员疲劳检测方法徐文奇,胡耀聪*(安徽工程大学电气工程学院,安徽芜湖 241000)摘要:针对现有驾驶员疲劳检测很大程度依赖于局部疲劳相关信息提取而导致检测准确度不足的问题,本文提出了一种基于面部多特征融合的驾驶员疲劳检测算法,能够对整体面部疲劳状态进行特征学习,从而实现更精确的驾驶员疲劳状态检测㊂提出的驾驶员人脸疲劳检测算法包含3个步骤:首先使用M T C N N 网络检测面部关键点并截取脸部㊁眼部㊁嘴部图像区域;其次设计一种面部多特征跨层融合网络,实现不同面部区域之间的信息交互与疲劳相关特征提取,进而通过多标签分类对单帧图像面部疲劳相关属性进行识别;最后使用L S TM 对长时间序列进行建模,实现最终的驾驶员疲劳状态检测㊂本文提出的驾驶员疲劳检测算法在N T HU -D D D 数据集进行了测试,对比实验验证了该方法的可行性和有效性㊂关 键 词:疲劳相关信息;多特征跨层融合;多标签分类;长时间序列中图分类号:T P 391.41 文献标志码:A伴随公共交通的快速发展和车辆数量的指数级增长,交通安全已成为世界各地亟待解决的问题㊂世界卫生组织近来调查显示,全球由交通事故导致死亡人数每24秒新增1例,每年由车祸导致死亡人数超13万[1]㊂由司机长时间驾驶或睡眠不足导致的疲劳驾驶是造成交通事故死亡的重要原因之一㊂因此,驾驶员疲劳检测的研究对智能交通系统具有重要意义[2-4]㊂计算机视觉算法是基于视频的疲劳驾驶检测系统的核心技术㊂近期研究中,学者们已经提出了几种算法来实现疲劳驾驶检测㊂通常来说,一个完整的驾驶员疲劳检测框架主要包含以下3个步骤:(1)人脸检测:通过目标检测器逐帧检测驾驶员面部并对关键点进行定位;(2)特征提取:通过传统的特征描述子[5-7]或深度学习模型[8-12]来学习与疲劳驾驶相关的信息;(3)疲劳判定:依赖帧间信息判别驾驶员疲劳程度㊂面部特征提取是驾驶员疲劳检测的关键,然而现有的方法通常仅关注局部区域的疲劳相关属性,例如眼睑闭合时间(P e r c e n t a g e o f E y e l i dC l o s u r e ,P E R C L O S )[13]㊁嘴角张合比(M o u t hA s pe c tR a t i o ,MA R )[14]等,而忽略了全局面部特征表示,致使疲劳检测精度较低㊂为了解决这个问题,本文设计了面部多特征跨层融合网络来进行精确的驾驶员疲劳检测,首先使用MT C N N 网络检测面部关键点并截取脸部㊁眼部㊁嘴部图像区域;其次设计一种面部多特征跨层融合网络,实现不同面部区域之间的信息交互与疲劳相关特征提取,进而通过多标签分类对单帧图像的面部疲劳相关属性进行识别;最后使用L S T M 对长时间序列进行建模,实现最终的驾驶员疲劳状态检测㊂1 疲劳检测算法1.1 面部关键点检测本研究采用多任务级联卷积神经网络(M u l t i -t a s kC a s c a d eC o n v o l u t i o n a lN e u r a lN e t w o r k ,MT C N N )模型[15]进行人脸关键点检测,它包含3个子网络:P -N e t ㊁R -N e t 和O -N e t,模型结构如图2所示㊂具体来说,MT C N N 模型的推理流程包含以下步骤:(1)对输入图像进行缩放操作,设定缩放因子为γ,并将原始图像以{1,γ,γ2, ,γn}的比例进行缩放,从而生成一组不同尺度的图像㊂(2)P -N e t:采用全卷积神经网络结构,用于初步标定人脸边界框㊂通过3个浅层卷积提取面部特征,粗略地搜索人脸候选区域㊂(3)R -N e t :包含3个卷积层和1个全连接层,用于进一步剔除错误和重复的人脸框,其输入为P -N e t 检测出的候选区域,采用卷积层实现特征细化,最后通过回归判定出候选区域中是否包含人脸㊁人脸中心偏移量㊁人脸关键点坐标㊂(4)O -N e t :包含4个卷积层和1个全连接层,用于输出最终的人脸关键点检测结果㊂MT C -N N 模型可以准确地检测出视频图像中的人脸区域并定位出关键点,为后续的疲劳特征提取和疲劳状态检测打下了基础㊂图1 驾驶员人脸疲劳检测算法整体框架图2 M T C N N 模型结构示意图1.2 面部疲劳属性识别疲劳状态主要表现在面部全局纹理㊁眼睑闭合程度㊁嘴角张合程度等相关属性㊂面部多特征跨层融合网络模型如图3所示㊂由图3可知,此网络模型包含脸部特征提取网络分支F -b r a n c h ㊁眼部特征提取网络分支E -b r a n c h ㊁嘴部特征提取网络分支M -b r a n c h ,分别从人脸㊁眼睛和嘴巴3个图像区域学习疲劳相关信息,对应的输入尺寸为:128×128㊁64×64㊁64×64㊂特征提取网络分支F -b r a n c h ㊁E -b r a n c h 和M -b r a n c h借鉴了M o b i l e N e t -V 2网络结构,有效地平衡了模型性能与计算复杂度㊂具体来说,它采用了深度可分离卷积运算,即将标准的3×3卷积分操作拆分为逐点卷积(P o i n t w i s eC o n v o l u t i o n )和逐通道卷积(C h a n n e l -w i s eC o n v o l u t i o n ),降低了模型的参数量和浮点计算数;其次瓶颈层采用倒置残差模块(I n v e r t e dR e s i d u -a l sB l o c k )结构,即先通道升维,后通道降维的策略,在保持网络深度的同时,增加了特征图的维度;此外,倒置残差模块的最后1个卷积层使用线性激活函数代替R e L U 激活函数,用于解决特征丢失与梯度弥散问题㊂面部多特征跨层融合网络模型能够学习不同面部区域的疲劳相关信息,具体运算过程可以定义为:F (l )f a c e =F b r a n c h (F (l -1)f a c e |θ(l )f a c e )=θ(l )f a c e ×F (l -1)f a c e ,(1)F (l )e y e s =E b r a n c h (F (l -1)e y e s |θ(l )e y e s )=θ(l )e y e s ×F (l -1)e ye s ,(2)㊃56㊃第6期徐文奇,等:基于面部多特征跨层融合网络的驾驶员疲劳检测方法F (l )m o u t h =M b r a n c h (F (l -1)m o u t h |θ(l )m o u t h )=θ(l )m o u t h ×F (l -1)m o u t h ,(3)其中,F (l )f a c e ㊁F (l )e ye s ㊁F (l )m o u t h 分别表示面部㊁眼部㊁嘴部网络分支在第l 层提取的特征图;θ(l )f a c e ㊁θ(l )e ye s ㊁θ(l)m o u t h 表示其对应的相关参数㊂图3 面部多特征跨层融合网络模型需要注意的是,为了进一步促进不同面部区域的疲劳相关信息交互,面部多特征跨层融合网络采用了跨层连接单元,用于对不同网络分支的中间层特征图进行融合,即通过1×1卷积将E -b r a n c h 与M -b r a n c h 学习的眼部区域信息与嘴部区域信息进行特征映射,接着将其与F -b r a n c h 学习的全局面部特征进行拼接,并通过1×1卷积实现维度变换㊂此外,全局均值池化层用于将F -b r a n c h ㊁E -b r a n c h 与M -b r a n c h 网络分支中的最后一层(L 层)卷积特征图进行降维,具体可以定义为:^f =A v g P o o l i n g (F (L )f a c e ⊕F (L )e ye s ⊕F (L )m o u t h ),(4)其中,A v g P o o l i n g (㊃)表示全局均值池化操作;⊕表示特征通道合并;^f 表示融合后得到的全局疲劳状态表征㊂本文采用了多标签分类方法对单帧图像的面部疲劳相关属性进行判别,主要涉及全局属性(正常/垂头)㊁眼部属性(正常/闭眼)和嘴部属性(正常/打哈欠)㊂多标签分类损失具体可以定义如下:c jk =s o f t m a x (f |θk )=e x p (θj k ㊃f )∑j'e x p (θj 'k ㊃f ),(5)L c l s =-∑Jj =1∑Kk =1δk ㊃l k ㊃l o g (c j k ),(6)其中,c jk 表示s o f t m a x 分类器计算出的第k 个疲劳相关属性被分类为第j 个类别的概率;θk 为该分类器的相关参数;L c l s 为单个样本的损失;δk 表示第k 个疲劳相关属性的权重参数;l k 表示第k 个疲劳相关属性的真实值标签㊂1.3 面部疲劳状态检测疲劳是一种连续出现的长时间面部状态,因此仅仅依赖于单帧图像表现出的面部疲劳相关属性仍然难以实现精确的疲劳状态检测㊂基于此,本文采用长短期记忆网络模型(L o n g S h o r t -t e r m N e t w o r k ,L S T N )逐帧对面部疲劳相关属性进行编码,建模长时序信息,最终输出疲劳检测结果㊂L S T N 单元的输入门i (t )用于调制输入信号z (t ),记忆单元m (t )记录了当前的记忆状态,L S T N 单元的输出h (t )由遗忘门f (t )和输出门o (t )共同决定,面部多特征跨层融合网络疲劳逐帧计算疲劳相关属性c (t ),而双向长短期记忆网络以该属性作为输入,并输出每帧图像的疲劳得分,运算过程可表示为:i (t )=σ(W i c (t )+R i h (t -1)+b i ,(7)㊃66㊃安 徽 工 程 大 学 学 报第38卷f (t )=σ(W f c (t )+R f h (t -1)+b f ,(8)o (t )=σ(W o c (t )+R o h (t -1)+b o ,(9)z (t )=φ(W z c (t )+R z h (t -1)+b z ,(10)m (t )=i (t )⊗z (t )+f (t )⊗m (t -1),(11)h (t )=o (t )⊗φ(m (t )),(12)其中,W 表示当前状态输入的权重矩阵;R 表示上一个状态输出的权重矩阵;b 表示阈值项;σ为s i g m o i d 函数;φ为双正切函数;⊗表示元素内积㊂L S T N 单元的输出取决于当前时刻的疲劳相关属性和之前时刻的疲劳相关属性,实现了长时序信息融合㊂2 算法实现与结果2.1 实验环境本文在U b u n t u18.04操作系统下,通过P y -t o r c h 开源工具构建MT C N N 模型㊁面部多特征跨层融合网络模型与L S T N 网络模型,并应用于驾驶员疲劳识别任务中,实验相关配置与具体参数如表1所示㊂表1 实验平台相关配置与具体参数相关配置具体参数主机D e l l P o w e r E d g eT 440C P U I n t e l C o r e i 7-9700G P UN V I D I A G e f o r c eR T X 3090操作系统U b u n t u16.04P yt h o n 版本P yt h o n3.8P yt o r c h 版本P yt o r c h1.132.2 实验数据集N T HU -D D D 是一个公开的驾驶员疲劳识别数据集,由中国台湾清华大学发布㊂该数据集中的所有视频都是由带有主动红外L E D 的彩色摄像头拍摄的㊂录制视频的参与者在模拟驾驶环境中进行正常驾驶和疲劳驾驶,并可以分为五种场景条件:白天不佩戴眼镜㊁白天佩戴眼镜㊁白天佩戴墨镜㊁夜晚不佩戴眼镜㊁夜晚佩戴眼镜,如图4所示㊂录制的视频分辨率为640×480,每秒30帧㊂此外,N T HU -D D D 数据集包含每一帧图像的疲劳相关信息标注,涉及全局状态(正常/垂头)㊁眼睛(正常/闭眼)和嘴巴(正常/打哈欠)㊂本实验借鉴了文献[16]的数据处理方法,即采用滑动窗口对完整视频进行截取,截取片段的帧长设置为300帧㊂N T HU -D D D 数据集中的360段完整的训练视频可以被拆分为2390个时间片段,涉及1572个正常驾驶片段和818个疲劳驾驶片段;20段完整的测试视频可以被拆分为602个时间片段,涉及348个正常驾驶片段和254个疲劳驾驶片段㊂图4 N T HU -D D D 数据集示例样本2.3 实验评价指标本文实验的评价指标包括检测率(D e t e c t i o nR a t e ,D R )㊁误报率(F a l s eA l a r m R a t e ,F A R )㊁准确率(A c c u r a c y Ra t e ,A R ),分别可以定义为:㊃76㊃第6期徐文奇,等:基于面部多特征跨层融合网络的驾驶员疲劳检测方法D R =T pT p +F n ×100%,(13)F A R =F pT n +F p×100%,(14)D R =T p +T nT p +T n +F p +F n×100%,(15)其中,T p ㊁F p ㊁T n 和F n 分别表示真阳性㊁假阳性㊁真阴性㊁假阴性的样本数量㊂2.4 实验结果比较本实验主要采用检测率㊁误报率和准确率这3个指标评估面部多特征跨层融合网络模型的性能并与现有的驾驶员疲劳识别方法和模型做了比较㊂对比方法主要涉及三类:第一类是基于规则的疲劳检测算法,例如P E R C L O S [13]㊁MA R [14]等㊂第二类是结合传统的特征描述子和机器学习算法进行驾驶员疲劳检测,例如S L A F s -R F [17]㊁L B P T O P -S V M [18]等;第三类是基于深度学习的驾驶员疲劳识别方法,例如M S T N [19]㊁D D D -I A A [20]㊁3D C N N -F F [21]㊂本文所提出的基于面部多特征融合的驾驶员疲劳检测算法及其对比模型在相同的D e l lP o w e r E d g eT 440计算平台上进行训练与测试,模型训练过程中的超参数设置如表2所示㊂实验统一采用MT C N N 模型截取驾驶员人脸区域,通过不同模型提取疲劳相关特征,并最终判定驾驶员是否处于疲劳状态㊂表3列出了不同模型在N T HU -D D D 数据集上的识别精度对比结果㊂表2 模型训练的超参数设置超参数配置具体参数初始学习率0.001学习率下降间隔纪元数100学习率调整倍数0.1迭代纪元数500优化器类型A d a m 优化器批样本数16表3 各种疲劳识别算法在N T HU -D D D 数据集上的识别精度对比方法名称N T HU -D D D D R /%F A R /%A R /%P E R C L O S [13]65.419.873.9MA R[14]55.928.764.7S L A F s -R F [17]72.022.175.4L B P T O P -S VM [18]74.020.477.2M S T N[19]85.011.287.2D D D -I A A [2]81.919.081.43D C N N -C A L [21]80.321.579.2F B r a n c h -L S T N 79.513.583.6E B r a n c h -L S T N 78.723.077.9M B r a n c h -L S T N 67.724.772.1面部多特征跨层融合网络-L S T N (本文方法)89.48.690.5文献[13]和文献[14]分别将眼睑闭合时间(P E R C L O S )和嘴角张合比(MA R )作为规则用于评判驾驶员疲劳程度,这类方法在N T HU -D D D 数据集上的表现不佳,准确率分别为73.9%㊁70.6%㊂文献[17]和文献[18]结合了传统的特征描述子和机器学习算法判定驾驶员疲劳状态,其中,文献[17]融合了梯度方向特征和关键点运动矢量,接着随机森林分类器判定驾驶员是否处于疲劳状态;文献[18]使用了三维局部二值模式L B P -T O P 描述子提取面部动态纹理特征,并通过S VM 对提取的特征进行分类,进而检测驾驶员疲劳状态;实验结果表明,基于传统特征描述子的疲劳检测算法性能优于基于规则的疲劳检测算法㊂文献[19]㊁文献[20]和文献[21]构建了深度学习模型进行端到端的疲劳特征提取和疲劳检测㊂具体来说,文献[19]提出了一种多阶段时空网络模型(M u l t i s t a g eS p a t i a l -t e m p o r a lN e t w o r k ,M S T N ),其中C N N 模型从单帧图片中提取人脸疲劳相关特征,L S T N 模型用于建模长时序信息,并输出疲劳检测结果㊂文献[20]提出了D D D -I A A 驾驶员疲劳检测框架,其中A l e x N e t ㊁F l o w I m a g e N e t 和V G G F a c e 分别用于提取全局环㊃86㊃安 徽 工 程 大 学 学 报第38卷境信息㊁帧间动作信息和面部细节轮廓信息,最后采用分数融合检测驾驶员是否处于疲劳状态㊂文献[21]中提出了一种3D C N N -C A L 的疲劳检测框架,该框架首先使用三维卷积网络提取连续时间段的疲劳相关信息,接着借助条件自适应学习获取全局场景信息,最终通过特征融合识别驾驶员疲劳状态㊂实验结果显示文献[19]提出的M S T N 模型优于其他对比方法,该算法在N T HU -D D D 数据集上的检测率㊁误报率和准确率分别为85.0%㊁11.2%和87.2%㊂本文提出的面部多特征跨层融合网络包含3个网络分支:F -b r a n c h ㊁E -b r a n c h 与M -b r a n c h ,分别从人脸㊁眼睛和嘴巴3个图像区域学习疲劳相关信息,并通过跨层连接单元实现不同分支的信息交互㊂从实验结果可以看出,单独的脸部㊁眼部或嘴部特征提取网络分支在N T HU -D D D 数据集上的检测精度不高,而将3个网络分支进行跨层融合后,模型的性能得到了显著提升,检测率㊁误报率和准确率分别达到了89.4%㊁8.6%㊁90.5%,优于其他对比模型㊂面部多特征跨层融合网络模型在五种不同场景条件下的精度表现如表4所示,这五种场景包括白天不佩戴眼睛㊁白天佩戴眼镜㊁白天佩戴墨镜㊁夜间不佩戴眼镜㊁夜间佩戴眼镜㊂实验结果表明,本文提出的算法在白天条件下的检测精度要高于夜间条件下的检测精度,不佩戴眼镜情况下的检测精度要高于佩戴眼镜或佩戴墨镜情况下的检测精度㊂表4 本文提出的疲劳识别算法在N T HU -D D D 数据集中不同场景条件下的识别精度对比场景类型D R /%F A R /%A R /%白天不佩戴眼镜98.12.997.6白天佩戴眼镜94.05.494.3白天佩戴墨镜75.018.678.6夜间不佩戴眼镜92.38.791.7夜间佩戴眼镜85.59.288.5所有场景89.48.690.5图5 疲劳检测效果示意图本文提出的疲劳检测算法的效果示意图如图5所示,从图中可以看出MT C N N 网络可以准确地定位出人脸关键点,进而对脸部㊁眼部和嘴部区域进行截取;面部多特征跨层融合网络模型能够有效地判断出单帧图片的面部疲劳相关属性,而L S T N 网络结合了当前时刻与之前时刻的疲劳相关属性,并输出最终的疲劳检测结果㊂㊃96㊃第6期徐文奇,等:基于面部多特征跨层融合网络的驾驶员疲劳检测方法㊃07㊃安 徽 工 程 大 学 学 报第38卷3 结论本文针对现有驾驶员疲劳检测很大程度依赖于局部疲劳相关信息提取而导致检测准确度不足的问题,提出了一种基于面部多特征融合的驾驶员疲劳检测算法㊂首先使用MT C N N网络检测面部关键点并截取脸部㊁眼部㊁嘴部图像区域;其次设计一种面部多特征跨层融合网络,实现不同面部区域之间的信息交互与疲劳相关特征提取,进而通过多标签分类对单帧图像的面部疲劳相关属性进行识别;最后使用L S T N 对长时间序列进行建模,实现最终的驾驶员疲劳状态检测㊂本文提出的驾驶员疲劳检测算法在N T HU-D D D数据集进行了测试,对比实验验证了该方法的可行性和有效性㊂然而如何进一步提升复杂光照环境下的驾驶员疲劳检测的精度,这将是接下来的重点研究工作㊂参考文献:[1] 胡耀聪.基于深度学习的驾驶员行为与疲劳识别方法研究[D].南京:东南大学,2021.[2] S I N G H D,MOHA NCK.D e e p s p a t i o-t e m p o r a l r e p r e s e n t a t i o n f o r d e t e c t i o n o f r o a d a c c i d e n t s u s i n g s t a c k e d a u t o e n c o d-e r[J].I E E ET r a n s a c t i o n s o n I n t e l l i g e n tT r a n s p o r t a t i o nS y s t e m s,2019,20(3):879-887.[3] K A P L A N S,G U V E N S A N M A,Y A V U Z A G,e ta l.D r i v e rb e h a v i o ra n a l y s i sf o rs a f ed r i v i n g:as u r v e y[J].I E E ET r a n s a c t i o n s o n I n t e l l i g e n tT r a n s p o r t a t i o nS y s t e m s,2015,16(6):3017-3032.[4] R AM Z A N M,K HA N H U,AWA NS M,e t a l.As u r v e y o n s t a t e-o f-t h e-a r t d r o w s i n e s s d e t e c t i o n t e c h n i q u e s[J].I E E EA c c e s s,2019(7):61904-61919.[5] 朱艳,谢忠志,于雯,等.低光照环境下基于面部特征点的疲劳驾驶检测技术[J].汽车安全与节能学报,2022,13(2):282-289.[6] 胡峰松,程哲坤,徐青云,等.基于多特征融合的疲劳驾驶状态识别方法研究[J].湖南大学学报(自然科学版),2022,49(4):100-107.[7] 陆荣秀,张笔豪,莫振龙.基于脸部特征和头部姿态的疲劳检测方法[J].系统仿真学报,2022,34(10):2279-2292.[8] 熊群芳,林军,岳伟.基于深度学习的疲劳驾驶状态检测方法[J].控制与信息技术,2018(6):91-95.[9] 郑伟成,李学伟,刘宏哲,等.基于深度学习的疲劳驾驶检测算法[J].计算机工程,2020,46(7):21-29.[10]李响.基于深度学习的面部疲劳信息检测方法研究与实现[D].长春:东北师范大学,2021.[11]A HM E D M,MA S O O DS,A HMA D M,e t a l.I n t e l l i g e n td r i v e rd r o w s i n e s sd e t e c t i o nf o r t r a f f i cs a f e t y b a s e do n m u l t iC N Nd e e p m o d e l a n d f a c i a l s u b s a m p l i n g[J].I E E ET r a n s a c t i o n s o n I n t e l l i g e n tT r a n s p o r t a t i o nS y s t e m s,2022,23(10):19743-19752.[12]Q I A N K,K O I K ET,N A K AMU R A T,e t a l.L e a r n i n g m u l t i m o d a l r e p r e s e n t a t i o n s f o rd r o w s i n e s sd e t e c t i o n[J].I E E ET r a n s a c t i o n s o n I n t e l l i g e n tT r a n s p o r t a t i o nS y s t e m s,2022,23(8):11539-11548.[13]周壮壮,陈艳,唐苏,等.基于P E R C L O S的眼部疲劳检测系统研究[J].集成电路应用,2021,38(2):48-49.[14]王霞,仝美娇,王蒙军.基于嘴部内轮廓特征的疲劳检测[J].科学技术与工程,2016,16(26):240-244.[15]Z HA N G K,Z HA N GZ,L I Z,e t a l.J o i n t f a c e d e t e c t i o n a n d a l i g n m e n t u s i n g m u l t i t a s k c a s c a d e d c o n v o l u t i o n a l n e t w o r k s[J].I E E ES i g n a l P r o c e s s i n g L e t t e r s,2016(10):1499-1503.[16]黄志亮.基于深度学习的驾驶员疲劳检测技术研究[D].南京:东南大学,2019.[17]L Y UJ,Z HA N G H,Y U A N ZJ.J o i n t s h a p ea n dl o c a l a p p e a r a n c e f e a t u r e s f o rr e a l-t i m ed r i v e rd r o w s i n e s sd e t e c t i o n[C]//A s i a nC o n f e r e n c e o nC o m p u t e rV i s i o n.T a i p e i:S p r i n g e r,2017:178-194.[18]赵磊.基于深度学习和面部多源动态行为融合的驾驶员疲劳检测方法研究[D].山东:山东大学,2018.[19]S H I H T H,H S UCT.M S T N:m u l t i s t a g e s p a t i a l-t e m p o r a l n e t w o r k f o r d r i v e r d r o w s i n e s s d e t e c t i o n[C]//A s i a nC o n f e r-e n c e o nC o m p u t e rV i s i o n.T a i p e i:S p r i n g e r,2016:146-153.[20]P A R KS,P A NF,K A N GS,e t a l.D r i v e r d r o w s i n e s s d e t e c t i o n s y s t e mb a s e d o n f e a t u r e r e p r e s e n t a t i o n l e a r n i n g u s i n g v a-r i o u s d e e p n e t w o r k s[C]//A s i a nC o n f e r e n c e o nC o m p u t e rV i s i o n.T a i p e i:S p r i n g e r,2017:154-164.[21]Y UJ,P A R KS,L E ES,e t a l.D r i v e rd r o w s i n e s sd e t e c t i o nu s i n g c o n d i t i o n-a d a p t i v e r e p r e s e n t a t i o n l e a r n i n g f r a m e w o r k[J].I E E ET r a n s a c t i o n s o n I n t e l l i g e n tT r a n s p o r t a t i o nS y s t e m s.2019,20(11):4206-4218.D r i v e rF a t i g u eD e t e c t i o n M e t h o dB a s e d o n F a c i a lM u l t i -f e a t u r eC r o s s -l a ye rF u s i o nN e t w o r k X U W e n q i ,HU Y a o c o n g*(S c h o o l o fE l e c t r i c a l E n g i n e e r i n g ,A n h u i P o l y t e c h n i cU n i v e r s i t y,W u h u241000,C h i n a )A b s t r a c t :T h i s p a p e r p r o p o s e d a d r i v e r f a t i g u e d e t e c t i o n a l g o r i t h mb a s e do n f a c i a lm u l t i -f e a t u r e f u s i o n .I t c a n l e a r n f e a t u r e s f r o mt h e o v e r a l l f a c i a l f a t ig u e s t a t e .Th e c u r r e n t d ri v e r f a t i g u e d e t e c t i o nh e a v i l y re l i e d o n e x t r a c t i n g l o c a l d r o w s i n e s s r e l a t e d i nf o r m a t i o n ,r e s u l t i ng i n i n s u f f i c i e n t d e t e c t i o n a c c u r a c y.H o w e v e r ,t h em e t h o d c a na c h i e v em o r e a c c u r a t e d r i v e r f a t i g u e s t a t e d e t e c t i o n .T h e p r o p o s e dd r i v e r f a c e f a t i g u e d e -t e c t i o na l g o r i t h mc o n s i s t s o f t h r e e s t e p s .F i r s t l y ,MT C N Nn e t w o r kw a su s e d t od e t e c t f a c i a l k e yp o i n t s a n de x t r a c t f a c i a l ,e y e ,a n d m o u t h i m a g e r e g i o n s ;S e c o n d l y ,a f a c i a lm u l t i f e a t u r e c r o s s l a y e r f u s i o nn e t -w o r kw a s d e s i g n e d t o a c h i e v e i n f o r m a t i o n e x c h a n g e a n d f a t i g u e r e l a t e d -f e a t u r e e x t r a c t i o nb e t w e e n d i f f e r -e n tf a c i a l r eg i o n s ,a n dth e nr e c o g ni z e df a c i a l f a t i g u er e l a t e da t t r i b u t e s i ns i n g l ef r a m e i m a g e st h r o u gh m u l t i -l a b e l c l a s s i f i c a t i o n ;F i n a l l y ,L S T M w a su s e dt o m o d e l t h e l o n g t i m es e r i e sa n da c h i e v e dt h e f i n a l d e t e c t i o no f d r i v e r f a t i g u e s t a t u s .T h e p r o p o s e dd r i v e r f a t i g u e d e t e c t i o n a l g o r i t h m w a s t e s t e d o n t h eN T -HU -D D Dd a t a s e t ,a n d c o m p a r a t i v e e x p e r i m e n t s v e r i f i e d t h e f e a s i b i l i t y a n d e f f e c t i v e n e s s o f t h i sm e t h o d .K e y w o r d s :d r o w s i n e s s -r e l a t e d i n f o r m a t i o n ;c r o s s -l a y e r f e a t u r e i n t e r a c t i o n ;m u l t i -l a b e l c l a s s i f i c a t i o n ;l o n g -t i m e s e qu e n c e (上接第63页)I m p r o v e m e n t o f S L A M A l go r i t h mf o rP o i n t a n dL i n eV i s i o n B a s e d o nG r a d i e n tD e n s i t yL IM i n g h a o 1,2,C H E N M e n g y u a n 1,2*,G O N GP e n g h a o 1,2,L O N G H a i ya n 3(1.S c h o o l o fE l e c t r i c a l E n g i n e e r i n g ,A n h u i P o l y t e c h n i cU n i v e r s i t y,W u h u241000,C h i n a ;2.K e y L a b o r a t o r y o fA d v a n c e dP e r c e p t i o na n d I n t e l l i g e n tC o n t r o l o fH i g h -e n dE q u i p m e n t ,A n h u i P o l y t e c h n i cU n i v e r s i t y,W u h u241000,C h i n a ;3.S c h o o l o fE l e c t r i c a l a n dE l e c t r o n i cE n g i n e e r i n g ,A n h u i I n s t i t u t e o f I n f o r m a t i o nT e c h n o l o g y,W u h u241000,C h i n a )A b s t r a c t :A i m i n g a t t h e p r o b l e m st h a t t h ev i s u a l s y n c h r o n o u s l o c a l i z a t i o na n d m a p b u i l d i n g (S L AM )m e t h o d i s l i k e l y t o c a u s e i m a g eb l u r i n t h e r a pi d c a m e r am o v e m e n t ,a n d t h a t t h e e x t r a c t i o no f c e n t e r l i n e f e a t u r e s i nd e n s es c e n e s i s l i k e l y t oc a u s e i n f o r m a t i o nr e d u n d a n c y ,a ni m p r o v e d p o i n ta n dl i n ev i s u a l S L AMa l g o r i t h mi n t e g r a t i n g g r a d i e n t d e n s i t y i s p r o p o s e d .T h e a l go r i t h mf i r s t u s e s t h e n u m b e r o f f e a t u r e p o i n t sb e t w e e n t h e f r o n t a n db a c k i m a g e f r a m e s t o f i l t e r t h e b l u r r e d i m a ge ,a n d t h e nu s e sG a u s s i a nb l u r t oo p t i m i z e t h e p r o c e s s i n g t o o b t a i nb e t t e rm a t c h i n g i m a ge f r a m e s .T h e n ,t h e p o i n t f e a t u r e i n f o r m a t i o n i s u s e d t o j u d g ew h e t h e r t h e l i n e f e a t u r e i s i n t r o d u c e d ,a n d t h e i m a g e p i x e l d e n s i t y g r a d i e n t i s i n t r o d u c e d t o o p t i m i z e t h eL S D (l i n e s e g m e n t d e t e c t i o n )l i n e f e a t u r e f r o m m u l t i -d i m e n s i o n s ,a n d t h e s t a b l e l i n e f e a t u r e i s e x t r a c t e d t o i m p r o v e t h e s u b s e q u e n tm a t c h i n gq u a l i t y .F i n a l l y,t h e e r r o r f u n c t i o n i s c o n s t r u c t e db a s e d o n t h e p o i n t a n d l i n e c h a r a c t e r i s t i c e r r o r t om i n i m i z e t h e p r o j e c t i o ne r r o r a n d i m p r o v e t h e p o s e e s t i m a -t i o na c c u r a c y .T h e a l g o r i t h mi s t e s t e d i nT UMd a t a s e t ,a n d t h e e x p e r i m e n t a l r e s u l t s s h o wt h a t t h e a l g o -r i t h mc a ne f f e c t i v e l y i m p r o v et h er o b u s t n e s so f f e a t u r ee x t r a c t i o n ,t h e r e b y i m p r o v i n g t h ea c c u r a c y of c a m e r a p o s e e s t i m a t i o na n dm a p p i n g.K e y w o r d s :s y n c h r o n o u s p o s i t i o n i n g a n dm a p p i n g ;g r a d i e n t i n f o r m a t i o n ;l i n e f e a t u r e e x t r a c t i o n ;p o i n t a n d l i n e f u s i o n ;i n f o r m a t i o ne n t r o p y㊃17㊃第6期徐文奇,等:基于面部多特征跨层融合网络的驾驶员疲劳检测方法。
重采样
ENVI中重采样的三种方法优劣比较:重采样:由于输出图像的像元点在输入图像中的行列号不是或不全是整数关系,所以需要根据输出图像上的各像元在输入图像中的位置,对原始图像按一定规则重新采样,进行亮度值的插值运算,建立新的图像矩阵.最邻近法: 将最邻近的像元值赋予新像元.优点:不引入新的像元值,适合分类前使用;有利于区分植被类型,确定湖泊浑浊程度,温度等;计算简单,速度快。
缺点:最大可产生半个像元的位置偏移,改变了像元值的几何连续性,原图中某些线状特征会被扭曲或变粗成块状。
双线性内插法: 使用邻近4 个点的像元值,按照其据内插点的距离赋予不同的权重,进行线性内插.优点: 图像平滑,无台阶现象。
线状特征的块状化现象减少;空间位置精度更高。
缺点: 像元被平均,有低频卷积滤波效果,破坏了原来的像元值,在波谱识别分类分析中,会引起一些问题。
边缘被平滑,不利于边缘检测。
三次卷积内插法: 使用内插点周围的16 个像元值,用三次卷积函数进行内插.优点: 高频信息损失少,可将噪声平滑,对边缘有所增强,具有均衡化和清晰化的效果。
缺点: 破坏了原来的像元值,计算量大.内插方法的选择除了考虑图像的显示要求及计算量外,在做分类时还要考虑内插结果对分类的影响,特别是当纹理信息为分类的主要信息时。
研究表明,最近邻采样将严重改变原图像的纹理信息。
因此,当纹理信息为分类主要信息时,不宜选用最近邻采样。
双线性内插及三次卷积内插将减少图像异质性,增加图像同构型,其中,双线性内插方法使这种变化更为明显。
昨天同学问我,1:25W的影像怎么弄成1:50W,我感觉应该是重采样吧,缩小一倍就可以了,其实这个步骤也很简单,打开ENVI,单击主菜单的第二个“Basic Tools”--“Resize Data (Spatial/Spectral)”此时会弹出“Resize Data Input File”对话框如图,之后选中需要重采样的图像(影像可以之前打开,也可以在'Open'--'New File'中打开),单击“OK”会弹出“Resize Data Paramcters”对话框,如图编号1设置影像的分辨率,2是重采样模型,3设置保存的路径和名称,当然可以选择Memory,单击“OK”等待就可以了。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
‡
arXiv:0801.3049v1 [cs.IT] 19 Jan 2008
ABSTRACT Spectrum sensing is an essential functionality that enables cognitive radios to detect spectral holes and opportunistically use under-utilized frequency bands without causing harmful interference to primary networks. Since individual cognitive radios might not be able to reliably detect weak primary signals due to channel fading/shadowing, this paper proposes a cooperative wideband spectrum sensing scheme, referred to as spatial-spectral joint detection, which is based on a linear combination of the local statistics from spatially distributed multiple cognitive radios. The cooperative sensing problem is formulated into an optimization problem, for which suboptimal but efficient solutions can be obtained through mathematical transformation under practical conditions. Index Terms— Spectrum sensing, distributed detection, nonlinear optimization, and cognitive radio. 1. INTRODUCTION As an essential functionality of cognitive radio (CR) networks [1], spectrum sensing needs to reliably detect weak primary radio signals of possibly-unknown formats. Generally, spectrum sensing techniques can be classified into three categories: energy detection, matched filter coherent detection [2], and cyclostationary feature detection. Since non-coherent energy detection is simple and able to generate the spectrum-occupancy information quickly, we adopt it as the building block for constructing the proposed wideband spectrum sensing schemes. The literature on wideband spectrum sensing for CR networks is limited. An earlier approach is to use a tunable narrowband bandpass filter at the RF front-end to sense one narrow frequency band at a time, over which the existing narrowband spectrum sensing techniques can be applied. In order to search over multiple frequency bands at a time, the RF frontend needs a wideband architecture, and spectrum sensing usually operates over an estimate of the power spectral density (PSD) of the wideband signal. In [3], wavelet transformation
SPATIAL-SPECTRAL JOINT DETECTION FOR WIDEBAND SPECTRUM SENSING IN COGNITIVE RADIO NETWORKS Zhi Quan† , Shuguang Cui‡ , Ali H. Sayed† , and H. Vincent Poor§
This research was supported in part by NSF under Grants ANI-0338807, CNS-06-25637, ECS-06-01266, ECS-07-25441, CNS-06-25637, and by DoD under Grant HOTRN-07-1-0037.
Spectrum holes
Subbands occupied by primary users
M −1
Yk =
m=0
|Rk (m)|
2
k = 0, 1, . . . , K − 1
(6)
and the decision rule is given by
Department of Electrical Engineering, University of California, Los Angeles, CA 90095 Department of Electrical and Computer Engineering, Texas A&M University, College Station, TX 77843 § Department of Electrical Engineering, Princeton University, Princeton, NJ 08544 Email: {quan, sayed}@, cui@, poor@
was used to estimate the PSD over a wide frequency range given its multi-resolution features. However, no prior work attempts to make decisions over multiple frequency bands jointly, which is essential for implementing efficient CR networks. In this paper, we consider the situation in which spectrum sensing is compromised by destructive channel conditions between the target-under-detection and the detecting cognitive radios, which makes it hard to distinguish between a white spectrum and a weak signal. We propose a cooperative wideband spectrum sensing scheme that exploits the spatial diversity among cognitive radios to improve the sensing reliability. The cooperation is based on a linear combination of local statistics from spatially distributed cognitive radios [4] [5], where the signals are assigned different weights according to their positive contributions to joint sensing. In such a scenario, we treat the design of distributed wideband spectrum sensing as a spatial-spectral joint detection problem, which is further formulated into an optimization problem with the objective of maximizing the overall opportunistic throughput under constraints on the interference to primary users. Through mathematical reformulation, we derive a suboptimal but efficient solution for the optimization problem, which can considerably improve sensing performance. 2. SYSTEM MODEL Consider a primary communication system (e.g., multicarrier based) over a wideband channel that is divided into K nonoverlapping subchannels. At a particular time, some of the K subchannels might not be used by the primary users and are available for opportunistic spectrum access. Multiuser orthogonal frequency division multiplexing (OFDM) schemes are suitable candidates for such a scenario since they make it convenient to nullify or activate some portion of multiple narrow bands. We model the detection problem over the subband k as one to choose between hypothesis H0,k (“0”), which represents the absence of primary signals, and hypothesis H1,k (“1”), which represents the presence of primary signals. An illustration where only some of the K bands are occupied by primary users is illustrated in Fig. 1. The crucial task of spec-
