Assurance Package EAL1 Common Criteria Arrangement The President of the Federal Office
Websphere各版本功能对比
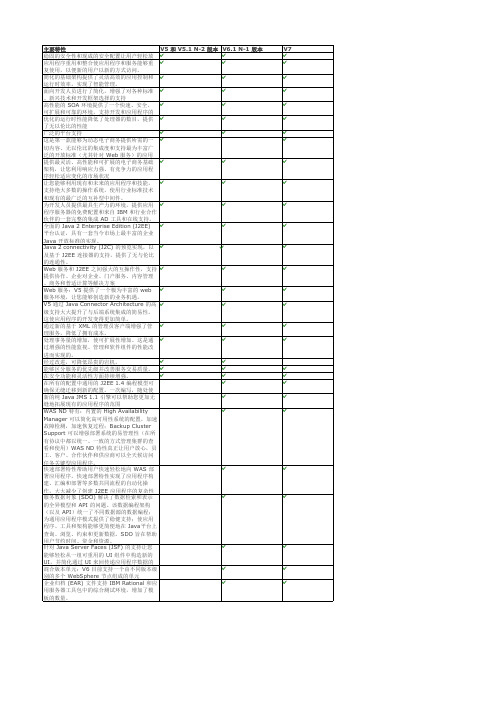
主要特性V5 和 V5.1 N-2 版本V6.1 N-1 版本V7稳固的安全性和现成的安全配置让用户轻松放应用程序重用和整合使应用程序和服务能够重复使用,以便新的用户以新的方式访问。
简化的基础架构提供了灵活高效的应用控制和运行时效率,实现了智能管理。
面向开发人员进行了简化,增强了对各种标准、新兴技术和开发框架选择的支持高性能的 SOA 环境提供了一个快速、安全、可扩展和可靠的环境,支持开发和应用程序的优化的运行时性能降低了处理器的数目,提供了无以伦比的性能广泛的平台支持这是第一款能够为动态电子商务提供所需的一切内容、无以伦比的集成度和支持最为丰富广泛的开放标准(尤其针对 Web 服务)的应用提供最灵活、高性能和可扩展的电子商务基础架构,让您利用响应力强、有竞争力的应用程序轻松适应变化的市场状况让您能够利用现有和未来的应用程序和技能,支持绝大多数的操作系统,使用行业标准技术和现有的最广泛的互补型中间件。
为开发人员提供最具生产力的环境,提供应用程序服务器的免费配置和来自 IBM 和行业合作伙伴的一套完整的集成 AD 工具和在线支持。
全面的 Java 2 Enterprise Edition (J2EE)平台认证,具有一套当今市场上最丰富的企业Java 开放标准的实现。
Java 2 connectivity (J2C) 的预览实现,以及基于 J2EE 连接器的支持,提供了无与伦比的连通性。
Web 服务和 J2EE 之间强大的互操作性,支持提供协作、企业对企业、门户服务、内容管理、商务和普适计算等解决方案Web 服务:V5 提供了一个极为丰富的 web服务环境,让您能够创造新的业务机遇。
V5 通过 Java Connector Architecture 的高级支持大大提升了与后端系统集成的简易性。
这使应用程序的开发变得更加简单。
通过新的基于 XML 的管理员客户端增强了管理服务,降低了拥有成本。
处理事务量的增加,使可扩展性增加。
CC:通用准则

CC:通用准则CC:通用准则(Common Criteria)EAL:评估保证级(Evaluation Assurance Level) IT:信息技术(Information Technology)PP:保护轮廓(Protection Profile)SF:安全功能(Security Function)SFP:安全功能策略(Security Function Policy) SOF:功能强度(Strength of Function) ST:安全目标(Security Target)TOE:评估对象(Target of Evaluation) TSC: TSF控制范围(TSF Scope of Control) TSF:TOE安全功能(TOE Security Functions) TSFI:TSF接口(TSF Interface)TSP: TOE安全策略(TOE Security Policy)3.3 术语表3.3.1 资产assets由TOE安全策略保护的信息或资源。
3.3.2 赋值 assignment规定组件中的一个特定参数。
3.3.3 保证 assurance实体达到其安全性目的的信任基础。
3.3.4 攻击潜力 attack potential可察觉的成功实施攻击的可能性,如果发起攻击,其程度用攻击者的专业水平、资源和动机来表示。
3.3.5 增强 augmentation将GB XXXX第3部分若干个保证组件加入到EAL或保证包中。
3.3.6 鉴别数据 authentication data用于验证用户所声称身份的信息。
3.3.7 授权用户 authorised user依据TSP可以执行某项操作的用户。
3.3.8 类 class具有共同目的的子类的集合。
3.3.9 组件 component可包含在PP、ST或一个包中的最小可选元素集。
3.3.10 连通性 connectivity允许与TOE之外的IT实体进行交互的TOE特性,包括在任何环境和配置下通过任意距离的有线或无线方式的数据交换。
cc eal认证的经历

cc eal认证的经历CC EAL(Common Criteria Evaluation Assurance Level)认证是一种国际标准,用于评估计算机系统安全性和可信度。
本文将详细介绍我个人的CC EAL认证经历,并逐步回答与此相关的问题。
第一步:了解CC EAL认证在开始我的CC EAL认证之旅之前,我首先进行了相关的背景调查和研究,以确保对该认证的了解。
CC EAL认证旨在确保计算机系统在设计、实施和运行中满足一系列确定的安全需求和标准。
该认证共分为7个级别,从EAL1到EAL7,每个级别都有不同的安全要求和验证方法。
第二步:确定认证级别在我了解了CC EAL认证的基本概念之后,我需要确定我想要获得的认证级别。
作为一个初学者,我决定从EAL1开始,逐步提高级别,以为将来的职业发展打下坚实的基础。
我了解到,每个级别都有不同的安全要求和测试标准,需要花费不同的时间和资源。
第三步:选择认证机构接下来,我开始寻找合适的CC EAL认证机构来进行认证评估。
我对不同机构进行了比较,并考虑了他们的声誉、专业知识和能力。
最终,我选择了一家被国际认可的认证机构,他们有丰富的经验和专业的评估团队。
第四步:准备认证材料在确定认证机构后,我开始准备所需的认证材料。
这些材料包括系统说明、安全需求规范、设计文档、实施和部署细节等。
我花费了相当长的时间来确保我的材料准确、完整,并符合CC EAL认证的要求。
第五步:进行安全评估当所有准备工作完成后,我的系统就被提交给认证机构进行安全评估。
他们的专业评估团队对系统进行详细审查,并执行一系列针对不同安全方面的测试。
这些测试包括漏洞扫描、密码强度测试、访问控制验证等。
第六步:修正和改进在评估过程中,认证机构发现了一些安全漏洞和不足之处。
我接受了他们的建议,并着手修复和改进我的系统。
这包括加强访问控制、更新密码策略、修复软件漏洞等。
在完成这些改进后,我重新提交了我的系统以进行第二轮评估。
软件安全评估等级标准

软件安全评估等级标准
软件安全评估等级标准是一种用于衡量和评估软件安全性的标准体系。
以下是国际上常用的软件安全评估等级标准:
1. Common Criteria(公共标准):由国际标准化组织(ISO)和国际电子技术委员会(IEC)共同开发的一套软件安全评估标准。
它将软件安全评估分为七个等级,从最低到最高分别为EAL1到EAL7。
每个等级都有一系列要求和测试方法,用于评估和验证软件的安全性。
2. National Information Assurance Partnership(NIAP):美国国家信息保障伙伴关系组织制定的软件安全评估标准。
该标准将软件安全评估分为四个等级,从最低到最高分别为EAL1到EAL4。
EAL4是最高级别,要求对软件的设计、开发和测试进行全面的验证和审计。
3. Trusted Computer System Evaluation Criteria(TCSEC):由美国国防部开发的软件安全评估等级标准。
该标准将软件安全评估分为六个等级,从最低到最高分别为D到A。
每个等级都有一系列要求和测试方法,用于评估和验证软件的安全性。
4. ISO/IEC 27001:国际标准化组织和国际电子技术委员会联合制定的信息安全管理体系标准。
该标准关注整个信息系统的安全管理,包括软件的安全性评估和管理。
这些标准都有各自的特点和适用范围,可以根据具体的需求选择合适的标准进行软件安全评估。
安全保护等级标准介绍

2020/11/16
安全保护等级标准介绍
安全保护等级
安全保护等级标准介绍
安全保护等级
n 定量分析 n 安全保护措施的可信度 n 可比性
安全保护等级标准介绍
主导问题
n TCSEC(Trusted Computer Security Evaluation Criteria)简介
n PP是描述满足特定消费者需求的、 独立于实现的一组安全要求,回答 “在安全方案中需要什么”。
n ST是依赖于实现的一组安全要求与 说明,用来指定TOE评估基础。回答 “在安全方案中提供什么”。
安全保护等级标准介绍
PP内容
安全保护等级标准介绍
ST内容
安全保护等级标准介绍
描述语言
n CC的安全要求:
安全保护等级标准介绍
总结:《准则》与CC 的比较
n 内容结构
n CC分为安全功能要求与安全保证要求,保证 要求层层递进;《准则》十个安全要素,层 层递进。
n 信任度
n 《准则》——对实现安全功能的安全保护措 施抵抗威胁与攻击的能力的一种度量;CC是 对实现安全功能的整个过程的一种信任度。
安全保护等级标准介绍
n 功能元素:独立的,可标识的最小安全 功能要求。
n 依赖性
安全保护等级标准介绍
说明
n 允许的功能组件操作
n 反复:覆盖一个要求的多个方面。 n 赋值:满足特定的安全目标。 n 选择:缩小一个组件元素的范围。 n 细化
安全保护等级标准介绍
类示例图
安全保护等级标准介绍
安全保证要求
n 共10类:
n APE类:PP评估 n ASE类:ST评估 n ACM类:配置管理 n ADO类:交付和运行 n ADV类:开发
通用准则CC标准与认证简介

下图阐述了认证的主要过程。
4
4.1
-PP:An implementation-independent set of security requirements for a category of TOEs that meet specific consumer need.
-满足特定用户需求、与一类TOE实现无关的一组安全要求。
3.3.1.1.7其他各种威胁
3.3.1.2在使用环境中对TOE的威胁
3.3.1.2.1与信息泄漏相关的威胁
3.3.1.2.2对象窃取相关的威胁
3.3.1.2.3与信息修改相关的威胁
3.3.2对TOE使用环境的威胁
3.4组织安全策略
3.2威胁
描述对资产的威胁
3.3组织安全策略
TOE必须遵守的组织安全策略
国内外已经对应用级防火墙、包过滤防火墙、智能卡、IDS、PKI等开发了相应的PP。
其内容见下图:
图表4保护轮廓内容
PP内容简述
注:该PP内容简述只是针对一般性PP而言,具体的PP可能会对内容略有变更。为了便于理解,增加了目前国内某一类TOE的PP作为索引。
项目
内容
对应的索引内容
1. PP引言
1.1 PP标识
3.2
编制和修订认证文档:
认证活动中最主要的一项工作就是提交并修订各类认证文档。认证文档所需的文档会根据所申请的EAL级别的不同而略有不同。但是一些常见的文档,如,功能规范、高层设计、低层设计等文档还是需要的。
TOE样品测试
TOE的样品测试也需要较长的时间。测试的依据就是提交的各类文档。
现场审查。
通过查阅文件和记录、现场观察和询问等方式进行现场审核。
商用OS安全评估等级

商用OS安全评估等级商用OS安全评估等级是指对商用操作系统(Commercial Off-The-Shelf Operating System,COTS OS)进行安全评估时所使用的评估等级。
这些等级用于衡量商用操作系统的安全性能和可信度,以便用户能够根据其安全需求来选择适合的操作系统。
商用OS安全评估等级通常按照国际标准进行划分,例如美国国家安全局(National Security Agency,NSA)的信息保护评估等级(Information Assurance Evaluation Ratings)、欧洲计算机事务良好安全操作(Common Criteria Evaluation Assurance Level,CC EAL)和国防信息系统安全认证联盟(Defence Information Systems Security Accreditation Alliance,DISSAA)等。
通常,商用OS安全评估等级从低到高分别为:1. 非认证等级:指操作系统未经过任何安全评估或认证。
2. 评估等级1(EAL1):提供基本的功能性和安全性保证。
3. 评估等级2(EAL2):具有加强的设计和实施安全功能。
4. 评估等级3(EAL3):提供严格的设计和实施安全功能。
5. 评估等级4(EAL4):具有高度的设计和实施安全功能。
6. 评估等级5(EAL5):提供非常严格的设计和实施安全功能。
7. 评估等级6(EAL6):具备高度可验证和安全设计的特征。
8. 评估等级7(EAL7):提供最高级别的保护,具备高度可验证和安全设计的特征,并具有高度透明度。
不同国家和组织对商用OS的安全评估等级可能存在一定差异,用户在选择操作系统时应根据自身的安全需求和可信度要求进行评估和选择。
CISP笔记

Cisp笔记一、信息安全标准●我国标准分为:国家标准、行业标准、地方标准、企业标准。
●国际通行“标准化七原理”➢原理1---简化➢原理2---协商一致➢原理3---实践、运用➢原理4---选择、固定➢原理5---修订➢原理6---技术要求+试验方法+抽样➢原理7---强制性适应于:安全、健康、环保等●我国通行“标准化八字原理”➢“统一”原理➢“简化”原理➢“协调”原理➢“最优”化原理●IETF(170多个RFC、12个工作组)●关键的概念:➢评估对象—— TOE(Target of Evaluation)➢保护轮廓——PP (Protection Profile)➢安全目标——ST( Security Target)➢功能(Function)➢保证(Assurance)➢组件(Component)➢包(Package)➢评估保证级——EAL( Evaluation Assurance Level)●评估保证级➢EAL1—功能测试➢EAL2—结构测试➢EAL3—系统地测试和检查➢EAL4—系统地设计、测试和复查➢EAL5—半形式化设计和测试(无隐蔽通道)➢EAL6—半形式化验证的设计和测试➢EAL7—形式化验证的设计和测试二、物理安全1、机房等级:➢A类:对计算机机房的安全有严格的要求,有完善的计算机机房安全措施。
该类机房放置需要最高安全性和可靠性的系统和设备。
➢B类:对计算机机房的安全有较严格的要求,有较完善的计算机机房安全措施。
它的安全性介于A类和C类之间。
➢C类:对计算机机房的安全有基本的要求,有基本的计算机机房安全措施。
该类机房存放只需要最低限度的安全性和可靠性的一般性系统。
2、机房地板类型➢复合地板(机房采用)➢木制地板➢金属底板3、人员安全管理➢背景调查➢入职审查及面试➢离职前谈话三、windows安全1、Windows系统的安全架构(6个安全要素)➢Audit(审计)➢Administration(管理)➢Encryption(加密)➢Access Control(访问控制)➢User Authentication(用户认证)➢Corporate Security Policy(公共安全策略)2、Windows系统的安全组件➢访问控制的判断(Discretion access control)按照C2级别的定义,Windows 支持对象的访问控制的判断。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Bundesamt für Sicherheit in der InformationstechnikBSI-PP-0013-2005 Low Assurance Protection Profile for a VPN gateway, Version 1.4 developed by SRC Security Research & Consulting GmbH- Bundesamt für Sicherheit in der Informationstechnik, Postfach 20 03 63, D-53133 Bonn Telefon +49 228 9582-0, Infoline +49 228 9582-111, Telefax +49 228 9582-455Bundesamt für Sicherheit in der InformationstechnikCertificate BSI-PP-0013-2005 Low Assurance Protection Profile for a VPN gateway, Version 1.4developed byCommon Criteria ArrangementSRC Security Research & Consulting GmbH Assurance Package : EAL1The President of the Federal Office for Information SecurityBonn, June 15th, 2005Dr. HelmbrechtL.S.The Protection Profile mentioned above was evaluated at an accredited and licenced/approved evaluation facility using the Common Methodology for IT Security Evaluation, Version 2.4 Revision 256 including Draft Interpretations #1 - #17 for conformance to the Common Criteria for IT Security Evaluation, Version 2.4, Revision 256. This certificate applies only to the specific version and release of the Protection Profile and in conjunction with the complete Certification Report. The evaluation has been conducted in accordance with the provisions of the certification scheme of the Federal Office for Information Security. The conclusions of the evaluation facility in the evaluation technical report are consistent with the evidence adduced. This certificate is not an endorsement of the Protection Profile by the Federal Office for Information Security or any other organisation that recognises or gives effect to this certificate, and no warranty of the Protection Profile by the Federal Office for Information Security or any other organisation that recognises or gives effect to this certificate, is either expressed or implied.Bundesamt für Sicherheit in der Informationstechnik Godesberger Allee 185 - 189 – D-53175 Bonn – Postfach 20 03 63 – D-53133 Bonn Telefon (0228) 9582-0 – Telefax (0228) 9582-455 – Infoline (0228) 9582-111BSI-PP-0013-2005Certification ReportPreliminary RemarksUnder the BSIG1 Act, the Federal Office for Information Security (BSI) has the task of issuing certificates for information technology products as well as for Protection Profiles (PP). A PP defines an implementation-independent set of IT security requirements for a category of TOEs which are intended to meet common consumer needs for IT security. The development and certification of a PP or the reference to an existent one gives consumers the possibility to express their IT security needs without referring to a special product. Product or system certifications can be based on Protection Profiles. For products which have been certified based on a Protection Profile an individual certificate will be issued. Certification of the Protection Profile is carried out on the instigation of the BSI. A part of the procedure is the technical examination (evaluation) of the Protection Profile according to Common Criteria [1]. According to the decree issued by the Bundesministerium des Innern (Federal Ministry of the Interior) on February 22nd, 2005 the BSI is authorised to issue certificates on the basis of CC, Version 2.4, Revision 256. The evaluation is carried out by an evaluation facility recognised by the BSI or by the BSI itself. The result of the certification procedure is the present Certification Report. This report contains among others the certificate (summarised assessment) and the detailed Certification Results.1Act setting up the Federal Office for Information Security (BSI-Errichtungsgesetz, BSIG) of th December 17 , 1990, Bundesgesetzblatt I p. 2834VCertification ReportBSI-PP-0013-2005ContentsPart A: Certification Part B: Certification Results Annex: Protection ProfileVIBSI-PP-0013-2005Certification ReportA1CertificationSpecifications of the Certification ProcedureThe certification body conducts the procedure according to the criteria laid down in the following: · · · · · · · BSIG2 BSI Certification Ordinance3 BSI Schedule of Costs4 Special decrees issued by the Bundesministerium des Innern (Federal Ministry of the Interior) DIN EN 45011 BSI Certification – Description of the Procedure [3] Procedure for the Issuance of a PP certificate by the BSICommon Criteria for Information Technology Security Evaluation, Version 2.4, Revision 256 [1] Common Methodology for IT Security Evaluation, Version 2.4, Revision 256 with the CC v2.4 Draft Interpretations #1 - #17 [2]·2Act setting up the Federal Office for Information Security (BSI-Errichtungsgesetz, BSIG) of th December 17 , 1990, Bundesgesetzblatt I p. 2834 Ordinance on the Procedure for Issuance of a Certificate by the Federal Office for th Information Security (BSI-Zertifizierungsverordnung, BSIZertV) of July 07 , 1992, Bundesgesetzblatt I p. 1230 Schedule of Cost for Official Procedures of the Federal Office for Information Security (BSIrd Kostenverordnung, BSI-KostV) of March 03 , 2005, Bundesgesetzblatt I p. 51934A-1Certification ReportBSI-PP-0013-20052Recognition AgreementsIn order to avoid multiple certification of the same Protection Profile in different countries a mutual recognition of Protection Profile certificates under certain conditions was agreed. An arrangement (Common Criteria Arrangement) on the mutual recognition of certificates based on the CC evaluation assurance levels up to and including EAL 4 was signed in May 2000. It includes also the recognition of Protection Profiles based on the CC. The arrangement was signed by the national bodies of Australia, Canada, Finland France, Germany, Greece, Italy, The Netherlands, New Zealand, Norway, Spain, United Kingdom and the United States. Israel joined the arrangement in November 2000, Sweden in February 2002, Austria in November 2002, Hungary and Turkey in September 2003, Japan in November 2003, the Czech Republic in September 2004, the Republic of Singapore in March 2005 and India in April 2005.A-2BSI-PP-0013-2005Certification Report3Performance of Evaluation and CertificationThe certification body monitors each individual evaluation to ensure a uniform procedure, a uniform interpretation of the criteria and uniform ratings. The Low Assurance Protection Profile for a VPN gateway, Version 1.4 has undergone the certification procedure at the BSI. The evaluation of the Low Assurance Protection Profile for a VPN gateway, Version 1.4 was conducted by the TNO ITSEF BV. The evaluation facility of TNO ITSEF BV is an evaluation facility (ITSEF)5 recognised by BSI. Author is SRC Security Research & Consulting GmbH. The certification was concluded with · the comparability check and · the preparation of this Certification Report. This work was completed by the BSI on June 15th, 2005.5Information Technology Security Evaluation FacilityA-3Certification ReportBSI-PP-0013-20054PublicationThe following Certification Results contain pages B-1 to B-8. The Low Assurance Protection Profile for a VPN gateway, Version 1.4 has been included in the BSI list of certified and registered Protection Profiles, which is published regularly (see also Internet: http:// www.bsi.bund.de). Further information can be obtained via the BSI-Infoline +49 228/9582-111. Further copies of this Certification Report may be ordered from the BSI6. The Certification Report may also be obtained in electronic form at the internet address stated above.6- Bundesamt für Sicherheit in der Informationstechnik, Postfach 20 03 63, D-53133 Bonn Telefon +49 228 9582-0, Infoline +49 228 9582-111, Telefax +49 228 9582-455A-4B CertificationResultsContent of the Certification ResultsOverview (2)1 PP2 Security Functional Requirements (4)Package (4)3 Assurance4 StrengthFunctions (4)of5 Results of the Evaluation (4)6 Definitions (6)7 Bibliography (7)1 PPOverviewThis Low Assurance Protection Profile for a VPN gateway, Version 1.4 is established by SRC Security Reasearch & Consulting GmbH as basis for the development of STs for a VPN gateway which is used to build up a virtual private network as depicted in figure 1 on the next page. A Virtual Private Network, or VPN, is a private communication network communicating over a public network, i.e. the Internet. Normally, a local network is protected against unauthorised access from the public network by means of a firewall which limits the permitted types of traffic. The TOE provides a remote authorised user a full connection into the local network without bypassing this protection against unauthorised users.This connection is established by a so called VPN tunnel between a VPN gateway on the side of the network and a VPN client on the side of the remote user, which is a reduced form of a gateway. Also two networks can be connected via two VPN gateways, in which case, one of the VPN gateways plays the role of the server and the other gateway plays the role of the client. There is no difference in the functionality offered by the VPN client irrespective of whether the remote VPN client is actually a single personal computer running a trusted VPN client software application or a VPN gateway device attached to a remote LAN.The TOE provides the following functionality:· identifying and authenticating remote VPN users or networks,· building up VPN tunnels between the TOE and the VPN client by exchanging cryptographic keys and using agreed cryptographic algorithms and · routing network traffic between the two sides of the VPN tunnel.The VPN message traffic is carried on public networking infrastructure using standard protocols. VPNs use cryptographic tunnelling protocols to provide the necessary confidentiality (preventing snooping), sender authentication (preventing identity spoofing), and message integrity (preventing message alteration) to achieve the privacy intended. Such techniques can provide secure communications over possibly insecure networks.Typical VPN protocols are:· IPSec (IP security), the most common protocol specified by an IETF working group,· OpenVPN, a SSL based encryption available for many operating systems,· and proprietary protocols likeo PPTP (point-to-point tunneling protocol) oro L2F (Layer 2 Forwarding) as well aso L2TP (Layer 2 Tunnelling Protocol).The TOE requires a supporting computing platform equipped with a connection to the public network as well as the local network to provide its functionality. Furthermore, the communication between the local network and the public network will be only through the TOE. This object will be supported by the use of a firewall that is configured to allow the minimum set of traffic to pass that isrequired for the operation of the TOE and any other services that are exposed to the outside world.Figure 1: The TOE and its operational environment2 Security Functional RequirementsThis section contains the functional requirements that must be satisfied by a TOE claiming compliance to the Low Assurance Protection Profile for a VPN gateway, Version 1.4.All functional requirements are drawn from Common Criteria Part 2.SFRs Component-NameFDP_ACC.1Subset access controlFDP_ACF.1Security attribute based access controlFIA_ATD.1 User attribute definitionFIA_UAU.2 User authentication before any actionFIA_UID.2 User identification before any actionFMT_MSA.1 Management of security attributesFMT_MSA.3Static attribute initialisationFMT_SMF.1 Specification of management functionsFMT_SMR.1 Security rolesFPT_RVM.1 Non-bypassability of the TSPFPT_SEP.1 TSF domain separationFTP_ITC.1 Inter-TSF trusted channelPackage3 AssuranceThe security assurance requirements are based entirely on the assurance components defined in Part 3 of the Common Criteria. The assurance require-ments are assurance level EAL1 (Evaluation Assurance Level 1).4 Strength of FunctionsThe strength of function examination is no more part of the CC, Version 2.4, Revision 256.5 Results of the EvaluationThe Evaluation Technical Report (ETR) [7] was provided by the ITSEF according to the Common Criteria [1], the Methodology [2], the requirements of the scheme [3] and all interpretations and guidelines of the scheme [4] as relevant for the TOE.The verdicts for the CC, Part 3 assurance components (according to EAL1 and the class ASE for the Security Target evaluation) are summarised in the following table.CC Aspect ResultCC Class APE PASS.APE_CCL.1 PASS.APE_ECD.1 PASS.APE_INT.1 PASS.APE_OBJ.0 PASS.APE_REQ.1 PASS.The Low Assurance Protection Profile for a VPN gateway, Version 1.4 meets the requirements for Protection Profiles as specified in class APE and Draft Interpretation #2 of the CC, Version 2.4, Revision 256.6 Definitions6.1 AcronymsCC Common Criteria for IT Security EvaluationLevelEAL EvaluationAssuranceTechnologyIT InformationITSEF Information Technology Security Evaluation FacilityLAPP Low Assurance Protection ProfileProfilePP ProtectionFunctionSF SecuritySFP Security Function PolicyTargetST SecurityofEvaluationTOE Target6.2 GlossaryAugmentation - The addition of one or more assurance component(s) from Part 3 to an EAL or assurance package.Extension - The addition to an ST or PP of functional requirements not contained in Part 2 and/or assurance requirements not contained in Part 3 of the CC.Formal - Expressed in a restricted syntax language with defined semantics based on well-established mathematical concepts.Informal - Expressed in natural language.Object - An entity within the TSC that contains or receives information and upon which subjects perform operations.Protection Profile - An implementation-independent set of security require-ments for a category of TOEs that meet specific consumer needs.Security Function - A part or parts of the TOE that have to be relied upon for enforcing a closely related subset of the rules from the TSP.Security Target - A set of security requirements and specifications to be used as the basis for evaluation of an identified TOE.Semiformal - Expressed in a restricted syntax language with defined seman-tics.Subject - An entity within the TSC that causes operations to be performed.Target of Evaluation - An IT product or system and its associated administrator and user guidance documentation that is the subject of an evalua-tion.TOE Security Functions - A set consisting of all hardware, software, and firm-ware of the TOE that must be relied upon for the correct enforcement of the TSP.TOE Security Policy - A set of rules that regulate how assets are managed, protected and distributed within a TOE.TSF Scope of Control - The set of interactions that can occur with or within a TOE and are subject to the rules of the TSP.7 Bibliography[1] Common Criteria for Information Technology Security Evaluation,Version 2.4, Revision 256[2] Common Methodology for Information Security Evaluation,Version 2.4, Revision 256 with the CC v2.4 Draft Interpretations#1 - #17[3] BSI Certification – Description of the Procedure (BSI 7125)[4] Applicaton Notes and Interpretations of the Scheme (AIS) asrelevant for the TOE[5] German IT Security Certificates (BSI 7148, BSI 7149)[6] Low Assurance Protection Profile for a VPN gateway, Version1.4, 29.04.2005[7] Evaluation Technical Report (ETR), Version 2.0, 01.06.2005This page is intentionally left blank.Annex: Protection Profile。
