1 Chameleon A Software Infrastructure and Testbed for Reliable High-Speed Networked Computi
全球测试管理工具(TD)

全球测试管理工具
巨腾计算机信息科技(上海 有限公司 巨腾计算机信息科技 上海)有限公司 上海
E- Provider Consulting and Technology Inc.
© 2001 Mercury Interactive Corporation
性能管理的生命周期
Pre-deployment
© 2001 Mercury Interactive Corporation
基于需求的明确的测试计划
A Solid Test Plan is Based on Requirements
测试计划包含了测试设计思想、测试流程、命名 规则和其他测试属性等内容 • 将不断变化的需求和测试重点统一起来 • 将测试设计方法应用于具体测试的建立 • 协调不同来源的信息 • 为今后的测试任务提供统一的信息参考库
Analyzing Results Managing Defects
Analyzing Results Analyzing Results Load Testing Inside Firewall
Load Testing Outside Firewall
© 2001 Mercury Interactive Corporation
Analyzing Results
Analyzing Results Analyzing Results Load Testing Inside Firewall
Load Testing Outside Firewall
© 2001 Mercury Interactive Corporation
功能性和衰退性测试流程
© 2001 Mercury Interactive Corporation
SequenceManager Logix Controller-based Batch和排队解决方

SequenceManagerLogix Controller-based Batch and Sequencing SolutionA Scalable Batch Solution for Process Control ApplicationsA modern batch system must account for the growing need for architecture flexibility, true distribution of control, and scalability. SequenceManager software provides batch sequencing in the Logix family of controllers by adding powerful new capability closer to the process and opening new possibilities for skids, off network systems, and single unit control. SequenceManager allows you to configure operations in Studio 5000 Logix Designer®, run sequence in FactoryTalk® View SE, and to capture and display batch results.SequenceManager directs PhaseManager™ programs inside a Logix-based controller in an ordered sequence to implement process-oriented tasks for single unit or multiple independent unit operations. Using industry standard ISA-88 methodology, SequenceManager enables powerful and flexible sequencing capabilities that allow for the optimal control of sequential processes.With SequenceManager, you can deliver fast and reliable sequence execution while reducing infrastructure costs for standalone units and complete skid-based system functionality.Key BenefitsSequenceManager™ software significantly reduces engineering time for system integrators and process equipment builders while providing key controller-based batch management capabilities for end users. Key benefits include:• Enables distributed sequence execution • Fast and excellent reliability of sequence execution native to controller • Efficient sequence development and monitoring in core product • Integrated control and HMI solution for intuitive operation • Reduced infrastructure costs for small systems • Provides data necessary for sequence reportingDistributed Batch Management Based on Proven TechnologyBuilt Upon Rockwell AutomationIntegrated ArchitectureSequenceManager was built using the standard control and visualization capabilities found in Rockwell Automation® Integrated Architecture® software. SequenceManager is a new capability that is builtinto Logix firmware that uses visualization through FactoryTalk® View SE to create an integrated sequencing solution. Combined with event and reporting tools, SequenceManager software is a complete batch solution for single unit and skid-based process applications.Scalable Controller-based Solution SequenceManager allows flexible design for skid-based equipment to be developed, tested and delivered asa fully functioning standalone solution but, if needed, seamlessly integrated into a larger control system. This strategy provides the end user with the option to integrate equipment without imposing design constraints on the OEM delivering the skid. Additionally, it enables the end user to deliver equipment as a standalone system without the constraint to scale to a larger process solution in the future. This batch solution offers scalability to help prevent costly redesign and engineering.Flexibility to Meet Process Needs SequenceManager enables you to expand your process control on skid based equipment that performs repetitive tasks and decision-making abilities. By using the ISA-88 methodology, SequenceManager allows for control design that can be adopted to fit the needs of the process industries without the constraints of custom application code. Built-in state model handling provides for fast and easy configuration while maintainingcontrol of the process.Editor and ViewerAs a brand new program type in Studio 5000 Logix Designer®, SequenceManager™ software gives the user the power and flexibility necessary to create dynamic recipes to maximize the effectiveness of the process control system.Without limitations on steps and parameters, and the ability to run parallel phases, to branch, and to loop back and rerun steps, SequenceManager removes the barriers in achieving effective batch within the controller.Sequence ExecutionProcedural sequences are executed through nativefunctions in the controller. With an integrated ISA-88 state model, the control and states of phases can be assured. Standard batch functionality, such as manual control and active step changes, are included to give the operational flexibility that is needed to respond toabnormal process conditions.Allowing for an Intuitive Batch ApplicationResponsive batch interactions between the controller and equipment, along with intuitive operator interfaces, provide the core of a truly distributed batching strategy that drives ISA-88 procedural models.Allen-Bradley, FactoryTalk Batch, FactoryTalk® View SE, Integrated Architecture, Listen.Think.Solve., PhaseManager, PlantPAx, Rockwell Automation, Rockwell Software, SequenceManager, and Studio 5000 Logix Designer are trademarks of Rockwell Automation, Inc. Trademarks not belonging to Rockwell Automation are property of their respective companies.Operator ViewerFactoryTalk® View SE and ActiveX controls monitor and interact with a running procedural sequence through the HMI. Advance ActiveX controls provide an intuitive interface for controlling sequences and changingparameters from the operational environment. Improved capabilities allow the user to perform manual step changes and acquire control easily.Reporting and AnalyticsSequenceManager data generates events that are used to produce batch reports and procedural analysis. A separate event client transfers the event data from the Logixcontroller to a historical database. SequenceManager uses the same data structure and reports as FactoryTalk Batch, which provides a consistent and intuitive batch reporting tool among Rockwell Automation® Batch Solutions.Additional InformationVisit us at /processPublication PROCES-PP001A-EN-E – June 2016Copyright © 2016 Rockwell Automation, Inc. All Rights Reserved. Printed in USA.。
英语词汇量自测表(测测你的词汇量)
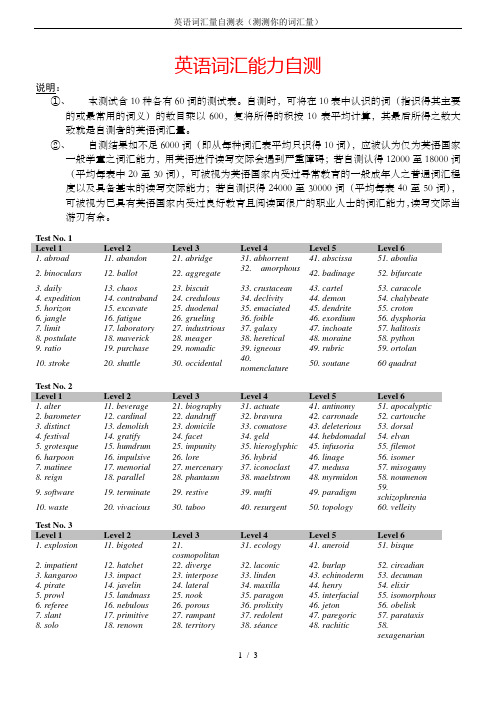
英语词汇能力自测说明:①、本测试含10种各有60词的测试表。
自测时,可将在10表中认识的词(指识得其主要的或最常用的词义)的数目乘以600,复将所得的积按10表平均计算,其最后所得之数大致就是自测者的英语词汇量。
②、自测结果如不足6000词(即从每种词汇表平均只识得10词),应被认为仅为英语国家一般学童之词汇能力,用英语进行读写交际会遇到严重障碍;若自测认得12000至18000词(平均每表中20至30词),可被视为英语国家内受过寻常教育的一般成年人之普通词汇程度以及具备基本的读写交际能力;若自测识得24000至30000词(平均每表40至50词),可被视为已具有英语国家内受过良好教育且阅读面很广的职业人士的词汇能力,读写交际当游刃有余。
Test No. 1Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. abroad 11. abandon 21. abridge 31. abhorrent 41. abscissa 51. aboulia2. binoculars 12. ballot 22. aggregate 32. amorphous42. badinage 52. bifurcate3. daily 13. chaos 23. biscuit 33. crustacean 43. cartel 53. caracole4. expedition 14. contraband 24. credulous 34. declivity 44. demon 54. chalybeate5. horizon 15. excavate 25. duodenal 35. emaciated 45. dendrite 55. croton6. jangle 16. fatigue 26. grueling 36. foible 46. exordium 56. dysphoria7. limit 17. laboratory 27. industrious 37. galaxy 47. inchoate 57. halitosis8. postulate 18. maverick 28. meager 38. heretical 48. moraine 58. python9. ratio 19. purchase 29. nomadic 39. igneous 49. rubric 59. ortolan10. stroke 20. shuttle 30. occidental 40.nomenclature50. soutane 60 quadratTest No. 2Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. alter 11. beverage 21. biography 31. actuate 41. antinomy 51. apocalyptic2. barometer 12. cardinal 22. dandruff 32. bravura 42. carronade 52. cartouche3. distinct 13. demolish 23. domicile 33. comatose 43. deleterious 53. dorsal4. festival 14. gratify 24. facet 34. geld 44. hebdomadal 54. elvan5. grotesque 15. humdrum 25. impunity 35. hieroglyphic 45. infusoria 55. filemot6. harpoon 16. impulsive 26. lore 36. hybrid 46. linage 56. isomer7. matinee 17. memorial 27. mercenary 37. iconoclast 47. medusa 57. misogamy8. reign 18. parallel 28. phantasm 38. maelstrom 48. myrmidon 58. noumenon9. software 19. terminate 29. restive 39. mufti 49. paradigm 59. schizophrenia10. waste 20. vivacious 30. taboo 40. resurgent 50. topology 60. velleity Test No. 3Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. explosion 11. bigoted 21.cosmopolitan31. ecology 41. aneroid 51. bisque2. impatient 12. hatchet 22. diverge 32. laconic 42. burlap 52. circadian3. kangaroo 13. impact 23. interpose 33. linden 43. echinoderm 53. decuman4. pirate 14. javelin 24. lateral 34. maxilla 44. henry 54. elixir5. prowl 15. landmass 25. nook 35. paragon 45. interfacial 55. isomorphous6. referee 16. nebulous 26. porous 36. prolixity 46. jeton 56. obelisk7. slant 17. primitive 27. rampant 37. redolent 47. paregoric 57. parataxis8. solo 18. renown 28. territory 38. séance 48. rachitic 58.sexagenarian9. unique 19. tradition 29. venereal 39. timbre 49. syncretism 59. tanagra10. weary 20. urban 30. yeoman 40. vellum 50. tanager 60. urticant Test No. 4Level 1 Level 2 Level 3 Level 4 Level 5 Level 61.belfry 11. besiege 21. aquiline 31. archive 41. bergamot 51. ablegate2. bulge 12. bronze 22. botanist 32. beriberi 42. brevier 52. algorism3. outlaw 13. gorge 23. cauldron 33. cornice 43. deemster 53. balsam4. package 14. import 24. furtive 34. denary 44. homologous 54. bezel5. pillage 15. judo 25. initiate 35. gratuitous 45. lamina 55. leat6. rental 16. ledger 26. jaded 36. hertz 46. largo 56. mittimus37. hiatus 47. pantheon 57. myopic7. riddle 17. limpid 27.kaleidoscopic8. swerve 18. penetrate 28. limelight 38. medial 48. refulgence 58. perforate9. vanish 19. resort 29. mutual 39. pellagra 49. savoury 59. prunella50. triolet 60. zoosterol 10. varnish 20. yoke 30. stratagem 40.valetudinarianTest No. 5Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. ballad 11. abyss 21. adaptable 31. calculus 41. aclinic 51. Babbittry2. canoe 12. bale 22. capsule 32. eczema 42. banshee 52. corrugate3. external 13. canyon 23. daub 33. gargantuan 43. illation 53. demitasse4. influx 14. exterminate 24. embargo 34. ibid. 44. keelson 54. gault5. lame 15. hub 25. garbage 35. laissez-faire 45. lachrymal 55. hypnotism36. literati 46. martingale 56. jejunum6. magazine 16. lizard 26.infrastructure7. martyr 17. obvious 27. liberate 37. neurology 47. newton 57. knap8. nexus 18. password 28. memento 38. obloquy 48. occipital 58. limnology9. patriot 19. rhythm 29. naturalize 39. patois 49. petrology 59. mithridatism10. patrol 20. stoppage 30. oblivion 40. rabid 50. ratlin(e) 60. umbilical Test No. 6Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. anthill 11. absurd 21. acoustics 31. botulism 41. chamfer 51. chameleon2. climate 12. collapse 22. bicker 32. cutaneous 42. eschatology 52. deadlight3. container 13. extortion 23. bludgeon 33. diocese 43. giaour 53. enchiridion4. endeavour 14. generation 24. dinosaur 34. distrait 44. imprest 54. geodic35. encyclical 45. lapidate 55. jokul5. immediately 15. immigrate 25.extemporaneous6. jingle 16. jealous 26. garbled 36. gamma 46. nadir 56. laches7. optimum 17. mature 27. lichen 37. lacerate 47. oblate 57. maud8. rhyme 18. raid 28. mattock 38. mandate 48. samphire 58. pedicular9. signal 19. satellite 29. outshine 39. methylene 49. satrap 59. spandrel10. tank 20. slipshod 30. perimeter 40. nacelle 50. ubiquity 60. vasospasm Test No. 7Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. humbug 11.21. alloy 31. agoraphobia 41. agnostic 51. acarpousautobiography2. ivy 12. concerto 22. brevity 32. barograph 42. boulevardier 52. charade3. legend 13. extinct 23. deportation 33.43. canticle 53. demersalconcatenation4. magnet 14. gladiator 24. hinterland 34. demography 44. homophone 54. eclampsia5. nickname 15. deputy 25. inscrutable 35. hierarchy 45. lacustrine 55. gonorrhoea6. probably 15. hooligan 26. linage 36. in vitro 46. marionette 56. masochism7. ripple 16. lanky 27. mortgage 37. megrim 47. natterjack 57. orthodontist8. situation 18. magistrate 28. omen 38. olfactory 48. Paleozoic 58.pseudonymity9. tattoo 19. nozzle 29. persecute 39. radian 49. pentathlon 59. ret10. vague 20. offend 30. repertoire 40. risque 50. reticle 60. sachemTest No. 8Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. batter 11. barbed 21. dabble 31. bodkin 41. apercu 51. crucian2. chest 12. chemistry 22. exhaust 32. clairvoyance 42. bleb 52.deuteragonist3. engineer 13. exception 23. filtrate 33. dirigible 43. decorticate 53. encaustic4. funnel 14. fascinating 24. garnish 34. epitome 44. gauss 54. hysteroid5. horn 15. gibberish 25. indifferent 35. histrionic 45. involute 55. immortelle6. mean 16. hydrogen 26. keel 36. logarithm 46. lambent 56. karma7. outrun 17. liter 27. metronome 37. panegyric 47. peculation 57.metamorphosis8. pinpoint 18. microscope 28. naive 38. rowel 48. recidivist 58. peen9. remove 19. shield 29. patronize 39. simpatico 49. semiotics 59. regelate10. search 20. suburb 30. reinforce 40. stricture 50. voodoo 60. serendipity Test No. 9Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. badger 11. brewer 21. breaker 31. chicanery 41. ablaut 51. chiliad2. capture 12. charity 22. cumbersome 32. gratis 42. belvedere 52. disembogue3. fresh 13. generosity 23. detention 33. holocaust 43. diminutive 53. gemmule4. hiss 14. idol 24. foyer 34. lethargic 44. gelation 54. idolum5. ire 15. lathe 25. humane 35. monograph 45. homogeneity 55. logo6. ladle 16. orderly 26. juggernaut 36. pinnace 46. morpheme 56. oroide7. mermaid 17. orient 27. kernel 37. ramify 47. pis aller 57. quintan8. parade 18. quest 28. lineal 38. scrutineer 48. psephology 58. raptatorial9. rear 19. routine 29. objective 39. tangential 49. regulus 59. scatology10. swindle 20. summit 30. sorcery 40. unction 50. sawder 60. triumvirate Test No. 10Level 1 Level 2 Level 3 Level 4 Level 5 Level 61. battery 11. crag 21. bristling 31. burnous 41. caucus 51. calamary2. collage 12. dwindling 22. devious 32. cadenza 42. eurhythmic 52. eparch53. fleur-de-lis 3. drowsy 13. easterly 23. entangle 33. debenture 43. habeascorpus4. forecast 14. hilt 24. graffito 34. flense 44. ichor 54. grangerize5. guilty 15. impetuous 25. precipitous 35. franklin 45. jussive 55. jacquard6. jellyfish 16. instinct 26. scramble 36. habiliment 46. limen 56. levigate7. mention 17. pike 27. summons 37. ignis iatuus 47. nescience 57. marsupial8. proverbial 18. regulation 28. territorial 38. jocund 48. obit 58. nepenthes9. result 19. verge 29. unkempt 39. mutability 49.59. obtestquerimonious60. thusly 10. screen 20. warehouse 30. vindicate 40. plebeian 50.thalassocracy。
Procedia Computer Science

Unlocking the promise of mobile value-added services byapplying new collaborative business models Original ResearchArticleTechnological Forecasting and Social Change , Volume 77, Issue 4, May 2010, Pages 678-693Peng-Ting Chen, Joe Z. Cheng Show preview | Related articles | Related reference work articlesPurchase $ 41.95 602 Software performance simulation strategies for high-level embedded system design Original ResearchArticlePerformance Evaluation , Volume 67, Issue 8, August2010, Pages 717-739Zhonglei Wang, Andreas Herkersdorf Close preview | Related articles |Related reference work articlesAbstract | Figures/Tables | ReferencesAbstractAs most embedded applications are realized in software, softwareperformance estimation is a very important issue in embedded system design.In the last decades, instruction set simulators (ISSs) have become anessential part of an embedded software design process. However, ISSs areeither slow or very difficult to develop. With the advent of multiprocessorsystems and their ever-increasing complexity, the software simulation strategybased on ISSs is no longer efficient enough for exploring the large designspace of multiprocessor systems in early design phases. Motivated by thelimitations of ISSs, a lot of recent research activities focused on softwaresimulation strategies based on native execution. In this article, we firstintroduce some existing software performance simulation strategies as well asour own approach for source level simulation, called SciSim , and provide adiscussion about their benefits and limitations. The main contribution of thisarticle is to introduce a new software performance simulation approach, callediSciSim (intermediate Source code instrumentation based Simulation), whichachieves high estimation accuracy, high simulation speed and lowPurchase $ 41.95implementation complexity. All these advantages make iSciSim well-suited for system level design. To show the benefits of the proposed approach, we present a quantitative comparison between iSciSim and the other discussed techniques, using a set of benchmarks.Article Outline1. Introduction2. Software performance simulation strategies2.1. Instruction set simulators2.2. Binary (Assembly) level simulation2.3. Source level simulation2.4. IR level simulation3. The SciSim approach for source level simulation3.1. Source code instrumentation3.2. Simulation3.3. Advantages and limitations of SciSim4. The iSciSim approach for performance simulation of compiler-optimized embedded software4.1. Intermediate source code generation4.2. Intermediate source code instrumentation4.2.1. Machine code extraction and mapping list construction4.2.2. Basic block list construction4.2.3. Static timing analysis4.2.4. Back-annotation of timing information4.3. Simulation4.3.1. Dynamic timing analysis4.3.2. Hardware and software co-simulation in SystemC5. Experimental results5.1. Source code vs. ISC5.2. Benchmarking SW simulation strategies 5.3. Dynamic cache simulation5.4. Simulation in SystemC6. Discussions and conclusions AcknowledgementsReferencesVitae603Computer anxiety and ICT integration in English classesamong Iranian EFL teachers Original Research ArticleProcedia Computer Science, Volume 3, 2011, Pages 203-209Mehrak Rahimi, Samaneh YadollahiClose preview | PDF (190 K) | Related articles | Related reference work articlesAbstract | ReferencesAbstractThe purpose of this study was to determine Iranian EFL teachers’ level of computeranxiety and its relationship with ICT integration into English classes and teachers’ personalcharacteristics. Data were collected from 254 Iranian EFL teachers by Computer AnxietyRating Scale, ICT integration rating scale, and a personal information questionnaire. Theresults indicated a positive relationship between computer anxiety and age; however,computer anxiety, gender, and experience of teaching were not found to be related. Aninverse correlation was found between computer anxiety and ICT integration. While ICTintegration correlated negatively with age and years of teaching experience, it was notfound to be related to gender.604An environmental decision support system for spatialassessment and selective remediation OriginalResearch ArticleEnvironmental Modelling & Software, Volume 26, Issue 6,June 2011, Pages 751-760Purchase$ 19.95Robert N. Stewart, S. Thomas Purucker Close preview | Related articles | Related reference work articles Abstract | Figures/Tables | ReferencesAbstractSpatial Analysis and Decision Assistance (SADA) is a Windows freewareprogram that incorporates spatial assessment tools for effective environmentalremediation. The software integrates modules for GIS, visualization,geospatial analysis, statistical analysis, human health and ecological riskassessment, cost/benefit analysis, sampling design, and decision support.SADA began as a simple tool for integrating risk assessment with spatialmodeling tools. It has since evolved into a freeware product primarily targetedfor spatial site investigation and soil remediation design, though itsapplications have extended into many diverse environmental disciplines thatemphasize the spatial distribution of data. Because of the variety of algorithmsincorporated, the user interface is engineered in a consistent and scalablemanner to expose additional functionality without a burdensome increase incomplexity. The scalable environment permits it to be used for both applicationand research goals, especially investigating spatial aspects important forestimating environmental exposures and designing efficient remedial designs.The result is a mature infrastructure with considerable environmental decisionsupport capabilities. We provide an overview of SADA’s central functions anddiscuss how the problem of integrating diverse models in a tractable mannerwas addressed.Article OutlineNomenclature1. Introduction2. Methods2.1. Sample design2.2. Data management and exploratory data analysis2.3. Spatial autocorrelation2.4. Spatial models3. Results 3.1. Scalable interfacing and decision support3.2. Risk assessment3.2.1. Human health risk3.2.2. Ecological risk3.3. Selective remedial design4. Discussion and ConclusionAcknowledgementsReferencesResearch highlights ► SADA is mature software for data visualization, processing, analysis, and modeling. ► User interface balances functional scalability and decision support. ► Widely used due to free availability and shallow learning curve . ► Integration of spatial estimation and risk tools allows for rich decision support. 605 CoDBT: A multi-source dynamic binary translator using hardware –software collaborativetechniques Original Research ArticleJournal of Systems Architecture , Volume 56, Issue 10,October 2010, Pages 500-508Haibing Guan, Bo Liu, Zhengwei Qi, Yindong Yang,Hongbo Yang, Alei LiangShow preview | Related articles | Related reference work articles Purchase $ 31.50606 An analysis of third-party logistics performance and service provision Original Research ArticleTransportation Research Part E: Logistics andTransportation Review , Volume 47, Issue 4, July 2011, Pages 547-570Chiung-Lin Liu, Andrew C. Lyons Purchase$ 41.95Show preview | Related articles | Related reference work articles 607 Intelligent QoS management for multimedia services support in wireless mobile ad hoc networks OriginalResearch ArticleComputer Networks , Volume 54, Issue 10, 1 July 2010, Pages 1692-1706Lyes Khoukhi, Soumaya Cherkaoui Show preview | Related articles | Related reference work articlesPurchase $ 31.50 608 Limit to improvement: Myth or reality?: Empirical analysis of historical improvement on threetechnologies influential in the evolution ofcivilization Original Research ArticleTechnological Forecasting and Social Change ,Volume 77,Issue 5, June 2010, Pages 712-729 Yu Sang Chang, Seung Jin Baek Show preview| Supplementary content| Related articles | Relatedreference work articlesPurchase $ 41.95 609An enhanced concept map approach to improving children’s storytelling ability Original Research ArticleComputers & Education , Volume 56, Issue 3, April 2011, Pages 873-884Chen-Chung Liu, Holly S.L. Chen, Ju-Ling Shih, Guo-Ting Huang, Baw-Jhiune Liu Show preview | Related articles | Related reference work articlesPurchase $ 24.95610Human –computer interaction: A stable discipline, a nascent science, and the growth of the longtail Original Research ArticleInteracting with Computers , Volume 22, Issue 1, January 2010,Pages 13-27Alan Dix Show preview | Related articles | Related reference work articlesPurchase$ 31.50 611Post-agility: What follows a decade of agility? Original Research ArticleInformation and Software Technology , Volume 53, Issue 5,May 2011, Pages 543-555Richard Baskerville, Jan Pries-Heje, Sabine MadsenShow preview | Related articles | Related reference work articlesPurchase $ 19.95612Confidentiality checking an object-oriented class hierarchy Original Research ArticleNetwork Security , Volume 2010, Issue 3, March 2010, Pages 16-20S. Chandra, R.A KhanShow preview | Related articles | Related reference work articlesPurchase $ 41.95 613 European national news Computer Law & Security Review , Volume 26, Issue 5, September 2010, Pages 558-563 Mark Turner Show preview | Related articles | Related reference work articlesPurchase $ 41.95 614 System engineering approach in the EU Test Blanket Systems Design Integration Original Research ArticleFusion Engineering and Design , In Press, CorrectedProof , Available online 23 February 2011D. Panayotov, P. Sardain, L.V. Boccaccini, J.-F. Salavy, F.Cismondi, L. Jourd’Heuil Show preview | Related articles | Related reference work articlesPurchase $ 27.95 615A knowledge engineering approach to developing mindtools for context-aware ubiquitouslearning Original Research ArticleComputers & Education, Volume 54, Issue 1, January 2010, Pages 289-297Hui-Chun Chu, Gwo-Jen Hwang, Chin-Chung Tsai Show preview | Related articles |Related reference work articles Purchase $ 24.95616“Hi Father”, “Hi Mother”: A multimodal analysis of a significant, identity changing phone call mediated onTV Original Research Article Journal of Pragmatics, Volume 42, Issue 2, February 2010,Pages 426-442Pirkko Raudaskoski Show preview | Related articles | Related reference work articlesPurchase $ 19.95 617Iterative Bayesian fuzzy clustering toward flexible icon-based assistive software for the disabled OriginalResearch ArticleInformation Sciences , Volume 180, Issue 3, 1 February 2010, Pages 325-340Purchase$ 37.95Sang Wan Lee, Yong Soo Kim, Kwang-Hyun Park,Zeungnam BienShow preview | Related articles | Related reference work articles 618 A framework of composable access control features: Preserving separation of access control concerns from models to code Original Research ArticleComputers & Security , Volume 29, Issue 3, May 2010, Pages 350-379Jaime A. Pavlich-Mariscal, Steven A. Demurjian, LaurentD. MichelShow preview | Related articles | Related reference work articlesPurchase $ 31.50 619 Needs, affect, and interactive products – Facets ofuser experience Original Research ArticleInteracting with Computers , Volume 22, Issue 5, September 2010, Pages 353-362Marc Hassenzahl, Sarah Diefenbach, Anja Göritz Show preview | Related articles | Related reference work articlesPurchase $ 31.50 620 An IT perspective on integrated environmental modelling: The SIAT case Original Research ArticleEcological Modelling , Volume 221, Issue 18, 10 September 2010,Pages 2167-2176P.J.F.M. Verweij, M.J.R. Knapen, W.P. de Winter, J.J.F. Wien, J.A. te Roller, S. Sieber, J.M.L. JansenShow preview | Related articles | Related reference work articlesPurchase $ 31.50。
软件测试英语面试题及答案

软件测试英语面试题及答案### 软件测试英语面试题及答案1. What is software testing?Software testing is the process of evaluating a software application or system to determine whether it meets the specified requirements and to identify any defects or issues that might be present. It is a key phase in the software development life cycle and plays a crucial role in ensuring the quality and reliability of the software product.Answer: Software testing is a systematic process that involves verifying and validating a software application to ensure it meets the requirements and is free from defects. It is essential to improve the quality of the software and to ensure that it functions correctly under various conditions.2. What are the different types of software testing?There are several types of software testing, including:- Functional Testing: Testing individual components or features for both expected and unexpected inputs and comparing the actual results with the expected results.- Non-functional Testing: Evaluating the performance, reliability, usability, and other attributes of the software. - Regression Testing: Ensuring that new changes to thesoftware have not adversely affected existing features.- Integration Testing: Testing the combination of software components to ensure they work together as expected.- System Testing: Testing the complete, integrated software system to evaluate its compliance with the specified requirements.- Acceptance Testing: The final testing stage where the software is tested to ensure it meets the user's acceptance criteria.Answer: The various types of software testing are designed to cover different aspects of software quality. They include functional, non-functional, regression, integration, system, and acceptance testing, each serving a specific purpose in the overall testing process.3. What is the difference between white box testing and black box testing?- White Box Testing: Also known as structural testing or code-based testing, it involves testing the software with knowledge of its internal structure and workings. It is used to check the internal logic and flow of the program.- Black Box Testing: This type of testing is performed without any knowledge of the internal workings of the application. It focuses on the functionality of the software and how it responds to inputs.Answer: White box testing requires an understanding of the software's internal code and structure, while black box testing is based on the software's functionality and externalbehavior. The choice between the two depends on the testing objectives and the information available to the tester.4. What is the purpose of test cases and test suites?Test cases are detailed descriptions of the test scenarios that are designed to verify specific aspects of the software. They include the input, expected results, and the steps to execute the test. A test suite is a collection of test cases that are grouped together to cover a particular feature or functionality of the software.Answer: Test cases and test suites are essential for structured testing. They provide a systematic approach to testing, ensuring that all aspects of the software are evaluated. Test cases help in identifying defects, while test suites help in organizing and prioritizing the testing efforts.5. How do you handle a situation where you find a bug that is not reproducible?When a bug is not reproducible, it can be challenging to diagnose and fix. The steps to handle such a situation include:- Documenting the Bug: Record all the details about the bug, including the steps taken, the environment, and any error messages.- Analyzing the Bug: Try to understand the conditions under which the bug might occur by analyzing the logs, code, andsystem state.- Isolating the Bug: Attempt to isolate the bug by changing one variable at a time to see if the bug can be reproduced. - Communicating with the Team: Discuss the bug with the development team to get insights and possible solutions.- Prioritizing the Bug: If the bug cannot be reproduced, it may be necessary to prioritize it based on its impact and the likelihood of it occurring again.Answer: Reproducibility is key to resolving bugs. However, when a bug is not reproducible, thorough documentation, analysis, isolation, communication, and prioritization are crucial steps in managing the issue effectively.6. How do you prioritize testing efforts?Prioritizing testing efforts is essential to ensure that the most critical parts of the software are tested first. The factors that influence prioritization include:- Risk Assessment: Testing areas with the highest risk of failure first.- Business Value: Prioritizing features that provide the most value to the business.- User Impact: Focusing on features that impact the user experience the most.- Resource Availability: Considering the availability of testing resources.- Development Progress: Aligning testing with the development schedule to ensure that testing is completed in time.Answer: Effective prioritization of testing efforts is a balance between risk, value, user impact, resource availability, and development progress. It's important to have a clear understanding。
供应链管理双语英文判断与选择翻译

1) A supply chain includes only the organizations directly involved in supplying components needed for manufacturing.一个供应链仅包括直接参与提供所需的元件制造业的组织。
Answer: FALSE2) A supply chain consists of all parties involved, directly or indirectly, in fulfilling a customer request. Answer: TRUE供应链由所有各方,直接或间接参与,满足客户要求。
3) A supply chain could be more accurately described as a supply network or supply web. Answer: TRUE供应链可以更准确地描述为供应网络。
4) The objective of every supply chain is to maximize the overall value generated. TRUE每一个供应链的目的是生成的整体价值最大化。
5) The objective of every supply chain is to maximize the value generated for the manufacturing component of the supply chain. Answer: FALSE每一个供应链的目标是最大化为供应链的制造组件生成价值。
6) Every supply chain must include all 5 stages. Answer: FALSE每个供应链必须包括所有 5 个阶段。
7) The cycle view of a supply chain holds that the processes in a supply chain are divided into a series of activities performed at the interface between successive stages. Answer: TRUE供应链周期认为供应链流程分为一系列的活动上演在连续阶段之间的接口。
Fujitsu fi Series扫描仪 PaperStream IP TWAIN和ISIS软件说明

PaperStream IP TWAIN and ISISPaperStream IP TWAIN and ISIS , available with any Fujitsu fi Series scanner, is an industry recognized and unique image enhancement software that delivers powerful image correction allowing documents to be quickly converted into exceptionally high-quality images. PaperStream IP TWAIN and ISIS alleviates the need to re-scan, therefore reducing time and resources, and prepares data for optimized capture results.Fujitsu Computer Products of America, Inc. (FCPA), is pleased to provide capture software that helps organizations leverage and optimize what is most important when processing documents - the data. FCPA’s software portfolio helps businesses increase efficiencies, reduce costs, and minimize resources. With these products, organizations can integrate a solution that best meets their business needs, so they can begin leveraging data immediately. Scalable, high-quality, and comprehensive, this software portfolio helps organizations meet their overall capture goals.Solutions Overview© Fujitsu. All rights reservedSoftware SolutionsCapture. Optimize. Access.Business Value and Benefits•Optimize data for business value with high-quality document processing and imaging •Increase productivity with scalable solutions serving any size company with any volume of paper•Reduce costs by leveraging a flexible pricing model with no hidden charges or volume packs •Increase operational efficiency with access to the Fujitsu comprehensive industry leading support teamPaperStream CapturePaperStream Capture is a simple front-end software that enhances the power and features of Fujitsu fi Series document scanners. PaperStream Capture is easy to use, needs minimal operator training time, and immediately increases productivity. Click on the profile icon for batch and ad hoc scanning, profile cloning or modifying, new profile and single button scanning creation using a clear, step-by-step interface and release options. PaperStream Capture is fully integrated with Fujitsu Scanner Central Admin (SCA) enabling seamless deployment updates and profiles to the entire scanner fleet at no additional charge.PaperStream Capture ProPaperStream Capture Pro is a high-quality, front-end document capture software that en-hances Fujitsu fi series superior scanning abilities with features that save time and money. PaperStream Capture Pro’s intuitive interface provides easy navigation from capture to release, with automatic image enhancements and assisted scan correction. Cost effective with no cost per click, the software is scalable and architected for distributed scanning. PaperStream Capture Pro is a simple solution that best fits organizations or departments that require an efficient, yet easy, way to convert paper documents into a digital file for high level data indexing and extraction.© Fujitsu. All rights reservedScanner Central Admin (SCA)Scanner Central Admin is a flexible and free software tool, integrated with Fujitsu fi Series scanners, that reduces administration time and increases efficiency by enabling the monitoring and maintenance of a large scanner fleet from one central module. Administrators can monitor scanner status, perform driver and software updates simultaneously, as well as manage multiple user accounts easily.For more information on FCPA’s capture software portfolio, please or attend one of our complimentary webinars offered bi-weekly.Learn More: /fcpasolutionsConnect with us!Technical Highlights• No click charges or volume packs • Captures documents from scanner or digital inputs • Distributed scanning models • Advanced document separation, classification, and indexing • Data extraction methods such as OCR, ICR, and OMR available • 100% web based offering • Integrates to repository of choice based on business needs • Releases into TIFF or PDF format • Frequent software updates •Customizable user profilesCommon Business Use Cases• AP invoice automationand processing • HR onboarding • Legal forms processing • Loan processing automation • Claims processing• Patient records management • Compliance inspection and audit reports •Mailroom automationAvailable with an Advanced Capture license is Mobile Capture , which enables usersto capture and send documents, images, and data anytime directly from an iOS or Android mobile device. Mobile Capture is the answer for organizations that have employees in the field and need an on-the-go, automated document solution. Simply capture documents and photos from a mobile or tablet camera and tag the content with searchable meta data.Advanced Capture Process FlowAdvanced CaptureAdvanced Capture Powered by Ephesoft* is an intuitive and powerful solution that helps organizations seamlessly automate document cap-ture and optimize data. The software reduces manual and time consuming tasks related to the important steps of document separation, classification, extraction, and data release. For organizations that process large amounts of documents on a regular and frequent basis, or need to efficiently leverage data post capture for additional business processes, Advanced Capture eliminates all capture complexi-ties. Advanced Capture is 100% web based, offers a flexible pricing model with no hidden charges or volume packs, and is also available for distributed capture for added scalability.Copyright 2015 Fujitsu Computer Products of America, Inc. All rights reserved. Fujitsu and the Fujitsu logo are registered trademarks. Statements herein are based on normaloperating conditions and are not intended to create any implied warranty of merchantability or fitness for a particular purpose. Fujitsu Computer Products of America, Inc. reserves the right to modify, at any time without notice these statements, our services, pricing, products, and their warranty and performance specifications.*Ephesoft is a third-party technology and platform partner。
碳中和英文介绍

碳中和英文介绍1Carbon neutrality is an incredibly important concept in today's world! It refers to achieving a balance between the amount of greenhouse gases produced and the amount removed from the atmosphere. The significance of carbon neutrality cannot be overstated! Look at the current state of global climate change. Rising temperatures, melting glaciers, and more frequent extreme weather events are all alarming signs. This is why carbon neutrality is so crucial! It is the key to alleviating the immense pressure on our environment.Some countries have taken effective policies and measures to achieve carbon neutrality. For instance, some have invested heavily in renewable energy sources like solar and wind power. They have also promoted energy efficiency in industries and buildings. Isn't it inspiring to see these efforts? Moreover, they have implemented strict regulations on emissions and encouraged public transportation and cycling. These measures not only contribute to reducing carbon emissions but also create a sustainable future for generations to come.In conclusion, achieving carbon neutrality is not just a goal; it is an urgent necessity for the well-being of our planet and all living beings on it. How can we not strive for it with all our might?Carbon neutrality is an incredibly important and challenging goal for our planet! How can we achieve it? One key approach is the widespread promotion of renewable energy applications. Take solar and wind power for instance. They are clean and sustainable, but there are significant technical and cost issues to overcome. The efficiency of solar panels needs to be improved, and the storage of energy generated by wind turbines remains a complex problem. How can we solve these?Another aspect is the transformation of traditional energy sources. Shifting from fossil fuels like coal and oil to cleaner alternatives is no easy task. The infrastructure for traditional energy is deeply established, and the costs and disruption of change can be substantial. But we must do it! We need to invest heavily in research and development to find more efficient and economical solutions.The journey towards carbon neutrality is full of difficulties and uncertainties. But can we give up? No! We must persevere and find innovative ways to make our planet a better place. It's not just a responsibility, it's an opportunity to create a sustainable future for generations to come. So, let's act now and strive towards this noble goal with all our might!Carbon neutrality is a revolutionary concept that is transforming various industries! It aims to balance the amount of carbon dioxide emissions with its removal from the atmosphere. Let's take the transportation industry as an example. The electrification of transportation is a key step towards carbon neutrality. Electric vehicles are becoming more and more popular, but there are challenges too! The construction of charging facilities is a major issue. How can we ensure there are enough charging stations to meet the demand? Another industry, manufacturing, is also making great efforts to reduce carbon emissions. They are improving production processes, using more energy-efficient technologies and materials. But questions remain. How can we ensure these efforts are sustainable and scalable? And what about the cost implications for businesses? The impact of carbon neutrality on industries is profound and complex. It requires innovation, collaboration, and a long-term commitment. But isn't it worth it for a sustainable future? We must keep striving to achieve this important goal and create a better world for generations to come!4Oh my goodness! The topic of carbon neutrality is of utmost significance in today's world. It's not just a matter for big industries orgovernments; it concerns each and every one of us!Let's think about our daily lives. For instance, choosing green transportation like cycling or using public transport instead of driving alone can make a huge difference! Can you imagine the reduction in carbon emissions that would result from such simple choices? And saving electricity is another vital aspect. Turning off lights when not in use, using energy-efficient appliances – these are small actions that accumulate into a significant impact.Let me tell you about some amazing environmental volunteers. They devote their time and energy to promoting carbon neutrality. They organize community events to raise awareness, encourage people to adopt eco-friendly habits, and even participate in tree-planting activities. Isn't it inspiring?We all have a role to play in achieving carbon neutrality. It's our responsibility to make conscious choices and take actions that contribute to a sustainable future. So, let's not wait any longer! Let's act now and make our planet a better place for generations to come. How wonderful it would be if we all do our part!5Carbon neutrality is not just a buzzword; it is a revolutionary concept that is reshaping the economic landscape. How does it relate to economic development? Let's explore!The emerging carbon trading market is a prime example of its positive impact. It provides a platform for businesses to trade carbon credits, driving economic growth and innovation. Imagine companies investing in clean energy projects to earn credits and sell them to those in need. Isn't it fascinating? This not only reduces emissions but also creates new economic opportunities.Many enterprises are also pioneering innovative business models in their pursuit of carbon neutrality. Take a tech company that develops energy-efficient software solutions for industries. By helping these industries reduce their carbon footprint, they not only contribute to the environment but also gain a competitive edge and attract investors.However, there are challenges too. The transition requires significant upfront investments. But isn't it worth it for a sustainable future? We must ask ourselves, are we ready to embrace these changes and seize the opportunities that carbon neutrality brings? The answer is a resounding yes! It is the key to a prosperous and eco-friendly economy.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Chameleon: A Software Infrastructure and Testbed for Reliable High-Speed Networked ComputingR.K.Iyer, Z.Kalbarczyk, S.BagchiCenter for Reliable and High-Performance ComputingUniversity of Illinois at Urbana-Champaign1308 W. Main St., Urbana, IL 61801E-mail: [iyer, kalbar, bagchi]@AbstractThis paper presents Chameleon, an adaptive infrastructure which allows different levels of availability requirements to be simultaneously supported in a single clustered environment. Fundamental components which constitute Chameleon are: (1) Fault Tolerance Manager(FTM) acting as an independent and intelligent entity capable of identifying and establishing the required fault tolerance strategy for executing the user application, (2) Reliable, Mobile and Intelligent Agents capable of migrating through the network and operating autonomously on behalf of the FTM according to built-in specifications and instructions, (3) Surrogate Manager operating as a pseudo-manager and capable of interacting with the user and supporting proper communications with the agents which monitor the application execution on remote hosts, (4) Host Daemons residing on each host and responsible for handshaking with the agents and monitoring the agents behavior, and (5) Software Libraries providing basic building blocks to create or re-engineer agents. A prototype implementation of Chameleon on a small LAN of heterogeneous machines connected to the high-speed Myrinet switch, is described.Keywords: adaptive fault-tolerance, highly available networked computing, error detection and recovery.1 IntroductionIn contemporary networked computing systems, a broad range of commercial and scientific applications which need varying degrees of availability must coexist. It is not cost effective to develop a reliable platform in each case. It is more efficient to build an infrastructure which provides the required levels of dependability based on application needs. It is also essential that the proposed alternatives be cost-effective. Hence, a primary issue to be addressed is how the envisioned infrastructure can leverage off-the-shelf components. There have been exhaustive studies on fault tolerance strategies (hardware and/or software implemented) capable of providing efficient mechanisms to deal with system operationalfailures. Most of these works however focused on specific application needs and thus provided piecemeal solutions. Little work has been done in addressing how to build reliable networked computing system out of unreliable computation nodes. As a result there is no comprehensive solution for providing a wide range of fault-tolerant services in a single networked environment. The most feasible way of understanding how such a software environment would fit on top of existing layers (like the operating system, the network interfaces, etc.) is to implement the infrastructure for providing a range of reliable services. So it has been attempted to integrate a wide variety of existing strategies into a single environment on top of the hardware and software of heterogeneous workstations on a LAN. A prototype implementation of the envisioned approach is expected to provide useful insights into its feasibility.This paper introduces and describes Chameleon, a software infrastructure capable of providing configurable (i.e., according to user specification) levels of fault tolerance in a networked computing environment. Methods and techniques supported by Chameleon are embodied in a set of specialized, reliable and intelligent Agents supported by a Fault Tolerance Manager (FTM) and its Surrogates to ensure that applications execute with the required levels of reliability. The components have been so designed that none of them is a single point of failure. Each of the components is active for a certain period e.g., during setting up the system configuration. In the case of a component failure during its active phase there is a provision for recovery, either by switching to backup or by regenerating the component. The broad goals of Chameleon are stated below:• Dynamic handling of changing failure criticality requirements: certain segments of the application may be deemed more critical than others. The FTM is capable of recognizing such demarcations and executing different segments using different configurations tuned to provide required reliability levels.• Adaptability to user-directed availability levels: the FTM, through the Agents and the available libraries of fault detection and recovery mechanisms, determines the user availability requirements and executes the application in the user-directed mode. Thus, unlike most existing implementations, it can adapt to user availability requirements with just the amount of overhead required for supporting the particular level.• Rapid error detection and recovery: Chameleon supports failure detection at three different levels:Application or process monitoring.The application executing at a remote host is monitored locally by the agents residing at the remote host. A misbehaving application raises an offending signal which is captured by the corresponding agent. Thus the detection is not tied up with the FTM.Agent monitoring. The agents are also monitored locally, by the Host Daemons residing on every host. The monitoring is through exceptions as well as i_am_alive messages.Node monitoring. Whether a particular computation node is up or down is monitored by the FTM through periodic heartbeat messages. The heartbeat scheme could be extended to include nodes sending out signatures containing information about the status of the various components, which would then be tallied at the FTM.• Providing reliability with unreliable hardware and software components : Chameleon does not pre-suppose any special reliable platforms for execution or any specialized software. The computation nodes are mainly regular workstations or personal computers. All nodes are expected to have pre-installed C++ compiler and interpreter for a scripting language such as TCL. The Fault Tolerance Manager needs to run with a high degree of reliability (e.g., in a primary/backup mode). This would make the cost of maintaining the FTM high, but it would be distributed among all the end-users.This approach seems to be much cheaper and more efficient than to provide a separate fault-tolerant machine to individual user. The point to be stressed is that Chameleon uses components off the shelf. Thus there is no specialized hardware requirements for the user machines, nor any thick pre-installed software layer. This makes for cost effective services.• Scaleable services : Chameleon provides a unified framework for allowing the system to scale in two major dimensions:Physical scalability - the system structure is based on a high-speed network such as Myrinet or ServerNet. In this environment adding new computation nodes will improve the system performance (because of high bandwidth of the underlying network) while communication overheads will grow slowly with system size.Fault tolerance scalability - Chameleon provides a general procedure for creating agents and extending functions of already existing agents. The FTM utilizes this procedure to generateagents for supporting the application dependent fault tolerance strategy. To support this approach, two basic libraries are provided: (1) library of building blocks and (2) library of agents. The building blocks are used in agent creation. The user is also allowed to develop his own basic building blocks which can be incorporated in an agent created by FTM.2Related ResearchThere are examples of highly fault-tolerant, distributed systems which have demonstrated that there are efficient solutions for providing highly reliable computations. For example, Tandem architecture groups servers (processing nodes) into failure masking server pair group, in Stratus architecture all components (e.g., CPU, I/O, communication controller) are implemented by paired microprocessors that execute identical instruction streams and continuously compare the results. These are, however, dedicated fault-tolerant architectures oriented to specific applications and offering static level of fault tolerance. In the common networked systems, the computation nodes are usually not fault-tolerant machines or have very little to support highly reliable services. The question to be asked is how to achieve high reliability with unreliable components?To be cost effective and operationally efficient, a promising solution is to use a specialized software layer for organizing the system components into a reliable computation environment. By adding a dedicated software layer capable of providing predictable, fault-tolerant behavior, reliability of the overall system can be significantly improved. Current approaches to reliable distributed computing are mainly based on exploiting distributed groups of cooperating processes. There is a number of studies that address various aspects of this paradigm e.g., process synchronization, jobs distribution, fault tolerance strategies, e.g., [1], [3]. These studies result in a number of tools to support the construction of reliable services, e.g., Isis [2], Totem [5], Delta-4 [7], Horus [8].Most of these approaches require specialized and complex software layer which must be installed in each computation node. For example, they heavily rely on underlying protocols for supporting group membership and atomic broadcast. As a primary objective of developing these systems is to provide a software environment for constructing distributed applications, the service availability issue is not often of a primary concern. Consequently, there is no dedicated mechanism for error detection and the fault tolerance is somewhat of “a side effect” of the use of the group communication approach. The systemusually relies on the error detection based on capturing the time-out in a response from one of the processes in the group. When the time-out is encountered, the group must reach a consensus as to which process failed and should be excluded from the group. Then, the process next in the hierarchy takes over.Recently, the Piranha system presented in [4] is an attempt to address the issue of service availability in the execution of a distributed application. Piranha is a CORBA-based tool for attaining high availability in distributed systems. CORBA, a Common Object Request Broker Architecture is widely used distributed standard which provides interoperability between applications on different machines in heterogeneous distributed environments and interconnects multiple object systems [6]. CORBA does not address issues of availability and reliability and cannot consistently detect partial failures in distributed applications. Piranha exploits the dynamic replication of objects for achieving high availability. However, the necessary software layer is thick as Piranha runs on Electra, a CORBA Object Request Broker supporting the object group abstraction, reliable multicast, state transfer, and virtual synchrony. In addition Electra is built on the top of group communication subsystems such as Isis and Horus.3Chameleon Infrastructure - OverviewChameleon (see Figure 1) provides an adaptive infrastructure which allows different levels of availability requirements to be simultaneously supported in a single, heterogeneous clustered environment. Fundamental components which constitute the Chameleon include: (1) Fault Tolerance Manager (FTM) acting as an independent and intelligent entity capable of identifying and establishing the required fault tolerance strategy for executing the user application, (2) Reliable, Mobile and Intelligent Agents capable of migrating through the network and operating autonomously on behalf of the FTM according to built-in specifications and instructions, (3) Surrogate Manager operating as a pseudo-manager for one particular application and capable of interacting with the user and supporting proper communications with the agents which monitor the application execution on remote hosts, (4) Host Daemons residing on each host and responsible for handshaking with the agents and monitoring the agents’ behavior, and (5) Software Libraries providing basic building blocks to create or re-engineer agents. The idea is that a failure of none of these individual entities should compromise the whole system.In the initialization phase, the FTM collects information about the system configuration and characteristics of individual nodes. Initialization agents are sent to hosts to obtain this data and to install the host daemons on participating machines. After successful initialization, Chameleon is ready for accepting the user requests. When a request arrives, the FTM designates a query agent to acquire the necessary information on the application specifics such as the required availability level, needed system resources, types of results etc. Based on the collected information on the application, the FTM can identify the necessary fault tolerance strategy and can designate set of agents to initiate and monitor the application. Creation of agents is performed according to a predefined procedure which utilizes two software libraries: (1) library of building blocks and (2) library of agents. The FTM may create new agents from the basic building blocks or may re-engineer already existing agents to extend their functions.Agents designated to support the application execution migrate through the network to the selected nodes, install themselves on the machines and initiate the application execution. In addition, a Surrogate Manager is spawned by the FTM and associated with each application. The Surrogate Manager can be allocated on any machine in the network (including the node running the FTM). It maintains copy of the system information supported by the FTM, provides reliable communications with the user and supervises the agents which monitor the application execution on the remote hosts.To ensure a rapid reaction to the application failures, the application is watched by the agent which installed the application at the remote host and started execution. The agent communicates to the appropriate Surrogate Manager detectable application misbehavior. As the agent itself may fail, it is watched by the host daemon which is capable of notifying the Surrogate Manager about agent failures. The Surrogate Manager can re-generate a new agent either to complete or to restart the application. Agents and Surrogate Managers once generated can act autonomously and the FTM is free to serve other user requests. As the Surrogate Managers are capable of performing the basic functions of the FTM, the application may complete even in presence of FTM failure. Errors and failures of the Surrogate Manager are directly reported to the FTM by the local Host Daemon monitoring the Surrogate Manager. The FTM, then re-initializes the application execution just as it would handle a new request. In order to detect node failures the FTM uses heartbeat messages which are sent with a predefined frequency. In the case of a node failure the application(s) executed on the node are migratedto other available nodes. To operate reliably, the FTM must be resilient to errors. The possible solution is to support a passive backup FTM which supports the system information and is updated each time the system state changes (typically when a new application is admitted to the environment or when an application exits from the environment).The Chameleon implementation does not use a specialized language framework. Rather it is based on widely available scripting languages, such as TCL and high level programming languages such as C++. The aim is to provide a relatively thin software layer which must be present in each machine in the environment. The implementation of Chameleon is not based around CORBA, the Object Management Group's standard for building distributed systems with the design goals of heterogeneity, interoperability and extensibility. The motivations behind this design choice were multiple. To build Chameleon around CORBA would necessitate a full CORBA implementation around all the nodes in the system. The CORBA software would include an ORB with its name registry, support of IDL (Interface Definition Language) stubbers, etc. While increasingly vendors are providing applications conforming to CORBA specifications, still the vast majority of the existing applications were not built around CORBA objects. For instance, Piranha [4] requires a highly sophisticated CORBA ORB implementation capable of supporting object groups and failure detection. Hence in an environment like Chameleon which addresses availability needs in a general system of networked workstations (as opposed to specialized systems built with CORBA objects, for example), it was not considered desirable to impose the overhead of CORBA object handling. The cost of CORBA standardization is paid in the form of performance degradation because of intermediate layers of interfaces that an application must go through. This conflicts with our other design goal of high speed error detection and recovery. The important point however is that we do not preclude the use of CORBA in future versions (or alternate versions whose goal may be slightly different e.g. to support CORBA applications only). We can port some of the CORBA layer along with the Host Daemons and the nodes would then be able to support CORBA applications. The ORB can be a centralized one residing on the dedicated FTM machine. The operative word is to support user-defined levels of availability without the burden of specialized software for prior installation at the user nodes. However we do not rule out CORBA extensions to the project in the future.The key features of Chameleon can be stated as follows:• Chameleon is the first infrastructure which explicitly addresses the dynamic adaptation to the user required availability level in a heterogeneous, multi-node system• Chameleon, by employing Reliable Agents and Surrogate Managers, maximizes the chances of the application to complete even if an entity of the infrastructure fails• Chameleon does not require thick software layer to be maintained by each computation nodeFigure 1: Reliable, Networked Computing Environment4Components of the SystemThis section presents a detailed description of components of the Chameleon. Basic functions, operational modes and component interactions are identified and characterized.4.1Fault Tolerance Manager (FTM)The Fault Tolerance Manager is an intelligent, independent, active entity which operates in the networked environment with the task of providing continuous execution of the user request despite errors. The FTM is built as a reliable unit operating on a dedicated server. The decision mechanism at the FTM is responsible for identifying the configuration to execute the user application (e.g. single machine with recovery), determining machines to be used for the chosen configuration and finallysetting up the environment for the particular mode of execution. The primary functions of the FTM can be summarized as follows:• mapping the network, i.e., identification of the network configuration and collecting information about the nodes in the system. The data about the nodes are collected in the designated data structure which is updated when the nodes join or depart the network.• invoking a daemon process on each node in the network for supporting node’s communication with FTM• collecting application specifications from the user• determining fault tolerance strategies for providing the application required availability level. The decision procedure is based on the application requirements and a data on prior history of failures and uses software libraries on error/failure detection and recovery techniques to compose final fault tolerance strategy.• generating a set of Agents and an associated Surrogate Manager for supporting the application execution according to earlier determined fault tolerance strategyIn order to support these functions, the FTM utilizes and maintains information about the system. Three tables are used to support system specific information: (1) system configuration table which contains information regarding the various hosts which are participating in the environment and (2) runtimeapplication table which contains information related to the various applications which are currentlyactive in the environment, and (3) application specification table which contains information on the user application. The basic data structures used to keep the information are given in Figure 2.Network mapping and host daemons initializationThe network mapping and the host daemons initialization is accomplished using initialization agents -init_agent().Figure 3 presents the general structure of the initialization agent. It is assumed that functions in the agent body, e.g., get_sys_info()are already implemented and exist in one of the software libraries supported by the FTM (software libraries are presented in the further sections).The initialization agent is responsible for setting up the system with the participating hosts. Whenever a host is plugged into the network, this agent is invoked and it executes steps necessary for the host to be recognizable by the FTM. The agent also sets up the Host Daemon (init_sys_daemon()), to handle communication with the FTM. A host on being plugged into the network needs to have an interface (e.g., a TCP configured port) capable of accepting the initialization agent from the FTM. The initialization agent queries for system parameters from the hosts (get_sys_info ()) such as the memoryavailability, the native operating system, and fills up the information in the system configuration table at the FTM (put_info(system_config_table)). This data structure is later used by the FTM for issuing system specific commands at the remote host as well as determining the availability of required resources for running a particular application at the machine.Communication with the userThe input to the system are the user’s requirements gather by the specialized query agent -user_query_agent()(see Figure 4). The information is specified in a predefined format given by the app_spec data structure(see Figure 2). The meaning of fields available in the format is discussed below.Scope of the specifications(specScope)- determines parts of the application which must be executed with different availability levels. This parameter can take two values: entire_appl and partial_appl. In the latter case, the user must provide explicit demarcation to identify individual segments of the application corresponding to the specified level(s) of reliability.Required reliability level(reliability) - specified as an integer starting from 1 (for the lowest reliability level) up to n. The predefined fault tolerance strategies are described in Section 4.2.Results of interest (results)-specified as variables of interest at the end of the execution of the application or as the output file into which the results of the application are saved.System resources required (resources)- specified as an amount of runtime memory required. Other applications required resources might include ghostscript, gnuplot for example.Number of machines (#machines)- determined as a number of machines on which copies of the application are to be executed.Voting strategy (vote) - specified as n_of_m, i.e., n among m machines must agree for application to succeed (this also includes “no_voting” strategy).Agreement criterion (agree) - specified as an exact match or match in a range of values defined in terms of absolute value or percentage variation from mean.Application time-out (timeOut) - an upper bound on the execution time of the application provided by the user. If the application does not terminate within this period, it is taken to have failed.Identification of Fault Tolerance StrategyThe FTM determines the required fault tolerance strategy based on the data collected during communication with the user. In order to facilitate this decision, the FTM utilizes the three system tables (system_config_table[], runtime_table[],applSpec_table[]).The general procedure in selecting/identifying a required fault tolerance strategy is presented in Figure 5.First, the FTM calls FT_strategy to identify whether the fixed level of availability is specified for the whole application. If so, the FTM calls FT_config to find which fault tolerance strategy to use. If the user specifies application regions with varying availability levels, the FTM calls instrument_appl()to identify the criticality levels, collects the data in a table and calls FT_config for determining appropriate fault tolerance strategies. The FT_config allows to distinguish among predefined strategies as well as the user might define his own approach(es). Functions single_machine_nr(), single_machine_r(), dual_exec(),tmr_exec()are used (by FT_config)to set up default fault tolerance strategies, single machine execution without recovery, single machine execution with recovery, duplicated execution, triple modular redundancy, respectively. The latter option in the FT_config is for supporting user specified strategy which can be incorporated into an agent. Each of these functions support a procedure for creating the necessary set of agents and surrogate manager capable of supporting the application execution.Examples of agent creations and characterizations of different fault tolerance strategies are given in the next section.4.2Reliable AgentsThe Agents are seen as a failure resilient carriers of information/stimulus to/from the Fault Tolerance Manager. They are designated by the FTM to perform the actions/operations needed for successful completion of the application in the designated mode. An agent is expected to be sufficiently intelligent to execute specified functions in an autonomous fashion. This is to prevent overload the FTM with too many tasks, which could reduce the FTM performance and thus decrease the utility of the environment. The primary characteristics of agents are: (1) mobility, (2) reliability, and (3) scalability (see Figure 6). Mobility. Agents migrate through a computer network in order to accomplish actions specified by the FTM. Well-known communication protocols like TCP/IP may be used to support the mobility.Figure 6: Primary Characteristics of AgentsReliability. Agents are resilient to the network or node failures. To achieve this, the agent code in the already existing libraries is tested rigorously against erroneous execution. It is also important to ensure that failure in the agent does not cause a crash of the application which it was in charge of executing or that the agent crash does not propagate out of the node. To meet this requirement, agents are watched by host daemons (the host daemon is notified which agent it will have to monitor for possible crash by the micro-operation monitor()) and if an agent fails, the daemon notifies the Surrogate Manager or the FTM (in the case of the Surrogate Manager failure). The agent is protected from the network corruption by guarding it with check sum.Scalability. Agents are easy to create or re-engineer using elementary blocks or already existing agents. The Chameleon provides a unified, general framework for creating new agents or extending functions of already existing agents. Consequently, the user can actively participate in developing agents, e.g., the user might provide an application specific detection mechanism to be incorporated into an agent. Two basic software libraries support this approach: (1) library of building primitives, and (2) library of agents.• Library of building blocks contains micro- and macro-operations for supporting application execution in the distributed environment. Agents can be created, modified, re-engineered using these bubbles. An example bubble is notify(target_machine, execution_mode, list_participating_machines). Section 3.4 provides more details on this library.• Library of agents contains hierarchically arranged already available agents which have the flexibility of extension: (1) basic agents, (2) agents extended from basic agents using primitive building blocks,。
