03-60-475Secure EmailProject 1
Outlook2003邮箱配置方法
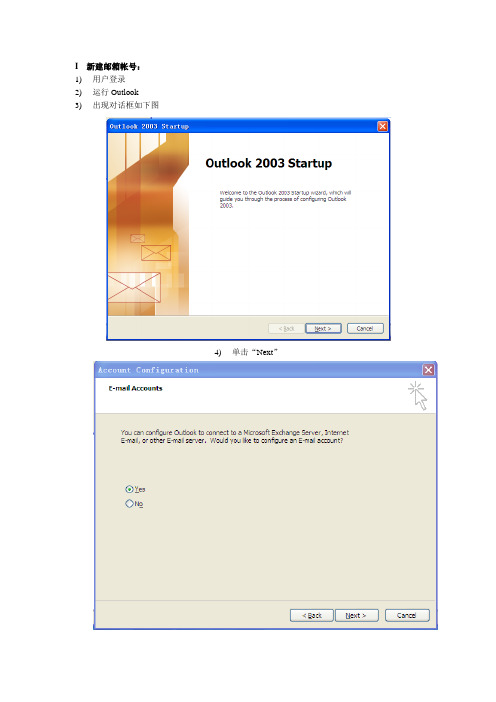
I 新建邮箱帐号:
1)用户登录
2)运行Outlook
3)出现对话框如下图
4)单击“Next”
5)点选“Yes”,单击“Next”
6)点选“Microsoft Exchange Server”单击“Next”
7)在Microsof Exchange Server文本框中输入:ausyd02
8) 在User Name 文本框中输入用户ID 9) 单击“Check Name ”填写认证信息
II 配置outlook2003可通过Internet 收发邮件: 1) 单击“More Setting ”
2) 在Security 选项卡中勾选下图标注的地方:
3)在connection 选项卡中点选下图标注的地
3) 方;
勾选此处
勾选此处
然后点击此按纽
4)输入地址:,并更改认证方式为Basic Authentication,单击“OK”
输入此地址
更改为此认证方式
III 为用户创建Personal Folder
1)在控制面板双击Mail,在弹出的窗口中点选E-mail Accounts
点击此按纽
5)点选View or change existing e-mail accounts,单击“Next”
6)单击“New Outlook Data File”按钮
7)在弹出的对话框选择新建PST文件,单击“OK”点击此按纽
点击此按纽
点击此按纽
8)选择路径到D盘新建一个文件夹命名为Email,将Personal Folder保存在该文件夹下:
9)点击“OK”。
FortiMail

1FortiMail™ for Email SecurityPowerful Appliances and Virtual Machines for Scalable Email Security ProtectionWith best-in-class performance validated by independent testing firms, FortiMail delivers advanced multi-layeredprotection against the full spectrum of email-borne threats. Powered by FortiGuard Labs threat intelligence and integrated into the Fortinet Security Fabric, FortiMail helps yourorganization prevent, detect, and respond to email-based threats including spam, phishing, malware, zero-day threats, impersonation, and Business Email Compromise (BEC) attacks.DATA SHEETProtection Against Email-borne ThreatsPowerful anti-spam and anti-malware are complemented by advanced techniques like outbreak protection, content disarm and reconstruction, sandbox analysis, impersonation detection, and other technologies to stop unwanted bulk email, phishing, ransomware, business email compromise, and targeted attacks.Validated PerformanceFortinet is one of the only email security vendors to consistently prove the efficacy of FortiMail through independent testing. For instance, FortiMail earned a AAA rating from SE Labs and a 99.78% Spam Capture Rate from Virus Bulletin.Fabric-enabled Email SecurityIntegrations with Fortinet products as well as third-partycomponents help you adopt a proactive approach to security by sharing IoCs across a seamless Security Fabric. It also enables advanced and complementary email security protection for Microsoft 365 environments through API-level integration.Powered by FortiGuard LabsFortinet FortiMail is powered by threat intelligence from FortiGuard Labs. With visibility across 500,000 customer environments worldwide, FortiGuard Labs is one of the preeminent threat research teams in existence.Check the box against :9Spam 9Phishing9Spear-phishing and whalephishing9Malicious Attachments and URLs 9Ransomware 9Zero-day Threats 9Impersonation9Business Email Compromise(BEC)Email security solutions for organizations that prefer full control and management over their email security infrastructure.DATA SHEET | FortiMail™2FEATURESProactive Email SecurityFortiMail addresses the full spectrum of risks that email poses to organizations, fortified by FortiGuard Labs’ global visibility and intelligence on the latest threats.Multi-Layered Anti-SpamMultiple sender, protocol and content inspection techniques shield users from spam and junk mail. Using a combination of reputation analysis, connection filtering, authentication and recipient verification methods allows for fast and accurate email protection. Checks include IP, domain, sender, SPF, DKIM, DMARC and geographical restrictions.Finally, message structure and content are analyzed based on the digital signature, keywords in context, image analysis, embedded URIs, and more advanced techniques such as behavior analysis and spam outbreak protection. Working together, these techniques consistently identify and block a verified 99.7% of spam in real-world conditions.Powerful Anti-MalwareCombining multiple static with dynamic technologies that include signature, heuristic, and behavioral techniques along with virus outbreak prevention, FortiMail protects against awide range of constantly evolving threats.Advanced Threat ProtectionFor an even stronger defense against the very latest threat classes like business email compromise and targeted attacks, FortiMail offers optional content disarm and reconstruction, sandbox analysis, sophisticated spoof detection, and more.Integrated Data Loss PreventionA robust set of capabilities for data loss prevention and email encryption safely deliver sensitive emails and protect against the inadvertent loss of data. These features facilitate compliance with corporate policies and industry regulations.Intuitive ControlsReal-time dashboards, rich reporting, centralized quarantine and simple to use end-user controls allow organizations to get running and realize value quickly. An intuitive user interface combined with flexible MTA and mail-handling capabilities give full visibility and easy control over email traffic.DATA SHEET | FortiMail™FEATURESIntegration with the Fortinet Security FabricThe future of email security is platform- or fabric-enabled tocounter the growing sophistication of threats and multi-vectorcampaigns. As part of the Fortinet Security Fabric, Indicatorsof Compromise and other telemetry can be shared forenhanced security across your entire security infrastructure.IT and security teams are able to more completely connectthe dots to identify multi-vector campaigns by sophisticatedactors. In addition, intensive and repetitive workflowsincluding response can be automated to reduce the burdenon security operations teams.Industry Recognized, Top-Rated PerformanceFortiMail delivers superior performance as measured by independent third-party testers.99.9% Detection of malicious emails across malware types and across malwarefamilies94%Overall Detection Rate99.78%Spam Catch Rate100%+Wildlist Detection Rate344We want full control.Manage it for us.Virtual Machines and appliances for teams who want total control over their infrastructure and email security.Email security as a service for teams who just want to focus on monitoring and responding to email threats. Fortinet handles the infrastructure.Read the FortiMail Cloud data sheet >DATA SHEET | FortiMail™FEATURESHigh Performance, Flexible DeploymentScale easily to handle millions of messages per hour. Serving organizations of all sizes, Fortinet provides a wide range of deployment models and operation modes to best match your organization’s email security needs.Appliances and Virtual MachinesFortiMail Appliances and virtual machines are for organizations that prefer full control and management over their email security infrastructure for on-premise and cloud use cases.§Appliances for on-premise environments§Virtual machines for running on popular hypervisor platforms including:§VMWare§Citrix XenServer§Hyper-V§KVM§AWS§AzureFortiMail CloudFortiMail Cloud for organizations that want simple, easy-to-use email security as-a-service for both on-premise and cloud-based email services.Operation ModesDeployment ModelsGateway ModeProvides inbound and outbound proxy mail transfer agent(MTA) services for existing email gateways. A simple DNSMX record change redirects email to FortiMail for analysis.FortiMail then relays safe email to its destination email serverfor delivery.Microsoft 365 API IntegrationFortiMail can be deployed out of line to simplify deployment,so no MX record change is required, and leverage the nativeMicrosoft 365 API to deliver threat detection and post-delivery message clawback. Broad flexibility is possiblewith clawback to create policies that address complianceor unique business requirements, such as building searchparameters based on keywords, file name, or content type.These capabilities can serve as powerful complements tonative Microsoft security features to bolster overall efficacyand reduce risk.Transparent ModeTransparent mode eliminates the need to change the DNSMX record, or to change the existing email server networkconfiguration. Transparent mode is particularly appealing forservice providers that want to extend email security servicesto their customer bases. Not available with FortiMail Cloud.Server ModeThe FortiMail device acts as a standalone messaging serverwith full SMTP email server functionality, including flexiblesupport for secure POP3, IMAP, and WebMail access.5DATA SHEET | FortiMail™6FEATURES99.7% Spam Detection Rate✓⃝✓⃝✓⃝Advanced Multi-Layer Malware Detection✓⃝✓⃝✓⃝Inbound and Outbound Filtering ✓⃝✓⃝✓⃝Integration with Customer LDAP ✓⃝✓⃝✓⃝Secure Message Delivery (TLS)✓⃝✓⃝✓⃝Message Tracking ✓⃝✓⃝✓⃝Virus Outbreak Service✓⃝✓⃝✓⃝Identity-Based Encryption (IBE)✓⃝✓⃝✓⃝Reporting✓⃝✓⃝✓⃝Email Data Loss Prevention✓⃝✓⃝✓⃝Content Disarm and Reconstruction ✓⃝✓⃝URL Click Protection ✓⃝✓⃝Impersonation Analysis ✓⃝✓⃝Cloud Sandboxing✓⃝✓⃝Real-time Scanning of Microsoft 365 Mailboxes ✓⃝Scheduled Scanning of Microsoft 365 Mailboxes✓⃝Post-delivery Clawback of Newly Discovered Email Threats✓⃝Additional Add-on CapabilitiesEmail ContinuityEmail Continuity for FortiMail Cloud is designed to protect valuable productivity by providing emergency mailbox services when organizations experience an outage in their email services.FortiIsolatorFortiIsolator allows users to browse the web in an isolated environment, which renders safe content in a remote container.Dynamic Image Analysis ServiceProtects your organization and employees against inappropriate and sexually explicit images.DATA SHEET | FortiMail™FEATURES SUMMARYMicrosoft 365 Integration– Post-delivery threat clawback– Scheduled scan– Real-time scanning– Internal mail scanning Advanced RMA SupportProfessional services and installation support options7DATA SHEET | FortiMail™8Criteria NDPP, FIPS 140-2 CompliantCriteria NDPP, FIPS 140-2 CompliantCriteria NDPP, FIPS 140-2 Compliant* Protected Email Domains is the total number of email domains that can be configured on the appliance.Domain Associations can be used to enable additional domains which share configuration with the primary domain to which they are assigned. ** Tested using FortiMail 7.0SPECIFICATIONSDATA SHEET | FortiMail™SPECIFICATIONS140-2 Compliant FIPS 140-2 Compliant* Protected Email Domains is the total number of email domains that can be configured on the appliance.Domain Associations can be used to enable additional domains which share configuration with the primary domain to which they are assigned.** Tested using FortiMail 7.09DATA SHEET | FortiMail™10SPECIFICATIONSProtected Email Domains ******2070500100015002000Recipient-Based Policies (Domain / System) — Incoming or Outgoing 60 /300400 / 1500800 / 3000800 / 30001500 / 75001500 / 7500Server Mode Mailboxes1504001500200030003000Antispam, Antivirus, Authentication, and Content Profiles (per Domain / per System)50 / 6050 / 20050 / 40050 / 40050 / 60050 / 600Data Loss Prevention No Yes Yes Yes Yes Yes Centralized Quarantine No Yes Yes Yes Yes Yes Microsoft 365 API IntegrationNoOptionalOptionalOptionalOptionalOptional* Recommended sizing for Gateway and Transparent deployments. For Server Mode, see Server Mode Mailbox metric. If unsure, please validate the model selection by checking the peak mail flow rates and average message size detail with a FortiMail specialist.** FortiMail 7.0.1 has been validated on Nutanix AHV 20201105.2096 and AOS 5.20.1.1.*** Transparent mode deployment is not fully supported on Microsoft HyperV and cloud hypervisors due to limitations in the available network configurations.**** For the initial VM setup, 250GB is required to install the default Fortinet OVF file. After deployment, the default OVF file can be deleted and the disk space set no less than 50 GB.***** ************************************************************************************************************************************.****** Protected Email Domains is the total number of email domains that can be configured on the appliance. Domain Associations can be used to enable additional domains which share configuration with the primary domain to which they are assigned. Advanced management license increases the protected domain limit by 50%.DATA SHEET | FortiMail™ORDER INFORMATIONFor information on ordering, please talk with your Fortinet account manager, or refer to the Ordering Guide for a full list of FortiMail-related SKUs and pricing information. Copyright © 2022 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and FortiGuard, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.Fortinet is committed to driving progress and sustainability for all through cybersecurity, with respect for human rights and ethical business practices, making possible a digital world you can always trust. You represent and warrant to Fortinet that you will not use Fortinet’s products and services to engage in, or support in any way, violations or abuses of human rights, including those involving illegal censorship, surveillance, detention, or excessive use of force. Users of Fortinet products are required to comply with the Fortinet EULA (https:///content/dam/fortinet/assets/legal/EULA.pdf) and report any suspected violations of the EULA via the procedures outlined in the Fortinet Whistleblower Policy (https:///domain/media/en/gui/19775/Whistleblower_Policy.pdf).FML-DAT-R56-20220706。
TMailer电子邮件系统普通用户操作手册(标准版)

TMailer电子邮件系统普通用户操作手册广州市泰禾创信计算机信息技术有限公司二零一一年三月目录第一章阅读指南 (1)1.1手册分册 (1)1.2使用建议 (1)第二章操作指南 (2)2.1首页 (2)2.1.1业务描述 (2)2.1.2操作指南 (2)2.2邮件功能 (3)2.2.1业务概况 (3)2.2.2收邮件 (4)2.2.3读邮件 (5)2.2.4发邮件 (6)2.2.5邮件标记功能 (8)2.2.6邮件文件夹管理 (10)2.3地址簿功能 (11)2.3.1业务概况 (11)2.3.2联系人管理 (11)2.3.3联系人组管理 (12)2.3.4地址簿文件夹管理 (13)2.4日程管理功能 (14)2.4.1业务描述 (14)2.4.2操作指南 (15)2.5网络硬盘功能 (17)2.5.1业务概况 (17)2.5.2网络硬盘文件夹管理 (17)2.5.3文件操作管理 (18)2.5.4修改显示视图 (19)2.6设置功能 (20)2.6.1业务概况 (20)2.6.2常规设置 (21)2.6.3邮件设置 (22)2.6.4写信设置 (24)2.6.5签名设置 (25)2.6.6地址簿设置 (26)2.6.7日程管理设置 (27)2.6.8账户设置 (28)2.6.9垃圾邮件选项设置 (28)2.6.10邮件过滤器设置 (29)2.6.11快捷方式设置 (31)1.1手册分册本文档为《TMailer电子邮件系统普通用户操作手册》,共1册;与之相关的文档有:《TMailer电子邮件系统管理员配置手册》、《TMailer电子邮件系统树形管理员操作手册》。
1.2使用建议如果你需要使用或指导别人使用TMailer所提供的各项服务或功能,你则需要先详细阅读本文档。
服务供应商可能需要向其用户提供其系统的操作使用说明。
这些向最终用户提供的操作使用说明可以参考本文档中的内容,并结合具体的TMailer产品客户化的情况予以必要的增删或修改。
维克多二级词汇

维克多二级词汇二星级核心词汇1. absence2. absent3. absolutely4. abuse5. accent6. acceptance7. accessible8. accidentally9. accountant10. accuse11. accustomed12. ache13. addicted14. adjustment15. administration16. advocate17. agricultural18. album19. allowance20. alongside21. aloud22. ambulance23. amused24. amusement25. analysis26. angel27. angle28. anniversary29. annoyed30. annual31. anonymous32. Antarctic33. Antarctica34. anyhow35. apparent36. applicant37. appoint 38. appreciation39. appropriate40. approval41. approximately42. Arctic43. arise44. armchair45. arouse46. arrest47. artificial48. ash49. assist50. assistance51. astonish52. astronaut53. athletic54. automatic55. avenue56. awful57. awkward58. bachelor59. backward60. backwards61. bamboo62. banana63. bark64. bathe65. BC/B.C.66. beard67. bench68. beneath69. beneficial70. bestseller71. bet72. bin73. birthplace74. blackboard75. bless76. blog77. blues78. boil79. bomb80. bond81. bookseller82. bookshelf83. boom84. boost85. botany86. bow87. brake88. breakthrough89. breast90. brick91. bride92. brilliant93. brochure94. broom95. bug96. bulb97. bullet98. bump99. bunch 100. butter 101. buzz 102. calculate 103. calendar 104. calorie 105. camel 106. can 107. cancel 108. candidate 109. candy 110. cap 111. capable 112. captain 113. capture 114. carrot 115. cartoon 116. cassette 117. cast 118. casual119. catalog/catalogue 120. category121. cattle122. cautious123. CD124. champion 125. changeable 126. chapter127. characteristic 128. chart129. cheers130. cheese131. chess132. chest133. chew134. chorus135. cigar136. circumstance 137. civil138. clarify139. classification 140. classify141. claw142. clay143. click144. clinic145. coke146. collapse147. commission 148. commit149. commitment 150. committee 151. compose 152. concentration 153. concerning 154. concrete 155. confusing 156. congratulate 157. conquer 158. conscious 159. consciousness 160. considerable 161. considerate 162. consult163. consultant 164. consume 165. contemporary 166. contract 167. contrast 168. convinced 169. cookie170. cooperate 171. corn172. correspondence 173. courtyard 174. criticism 175. crossroads 176. cultivate 177. curriculum 178. curtain180. dam181. damp182. dawn183. daytime 184. deadline 185. deadly186. decorate 187. decoration 188. deed189. define190. delicate 191. delightful 192. demonstrate 193. depart194. dependent 195. deposit196. depth197. despair198. dessert199. destruction 200. detect201. devoted 202. dial203. dialogue/dialog 204. diamond 205. digest206. dim207. disability 208. discount210. distinct211. distinction212. distribute213. disturbing214. division215. divorce216. donate217. donation218. doorway219. dormitory220. download221. downward222. draft223. drag224. dramatic225. drawer226. drill227. drown228. drum229. duck230. DVD231. eagle232. earnings 233. ease234. Easter235. easy-going 236. ecosystem 237. edit238. educator 239. elder240. elevator241. embarrassing 242. embarrassment 243. emperor 244. emphasis 245. enjoyment 246. enlarge247. enterprise 248. entertain 249. envy 250. erupt251. evaluate252. eve253. evil254. exhausted 255. exit256. expand257. expedition 258. export259. extension 260. extreme261. eyesight262. fade263. faint264. fancy265. fantastic266. fantasy 267. fare268. farthest269. fashionable270. fasten271. feast272. feather273. fetch274. fever275. file276. file277. fist278. flame279. flashlight280. flavor(u)r281. flesh282. flour283. flu284. fluency 285. fly286. fog287. foggy 288. foolish 289. forecast 290. fork291. fortunate 292. fountain 293. fox294. frame 295. fridge 296. fulfill 297. funeral 298. fur299. furthermore 300. garbage 301. garment 302. gene 303. gesture 304. ghost 305. giant 306. gifted 307. glare 308. globe 309. golf310. goose 311. govern 312. gradual313. grain 314. gram 315. grammar 316. grandparent 317. grandson 318. grasp 319. grassland 320. grave 321. greedy 322. grill323. hamburger 324. hammer 325. handbag 326. handshake 327. handsome 328. harbor(u)r 329. hardship 330. hardware 331. hardworking 332. harmony 333. heal334. heated 335. heaven 336. helmet 337. hen338. heritage 339. heroine 340. hers341. highlight 342. high-rise344. horizon 345. horrible 346. horror 347. hurricane 348. hut349. ice-cream 350. identity 351. immigrant 352. implication 353. incident 354. incredible 355. independence 356. industrial 357. initial358. ink359. inn360. inner361. innocent 362. inspect 363. institution 364. instruct 365. internal 366. interval 367. investigate 368. iron369. irrigation 370. jeans371. jet372. jewel374. jungle 375. junior 376. justice 377. keen378. kilogram(me) 379. kingdom 380. knife381. label382. lamp383. landlord 384. lane385. lap386. latter 387. laundry 388. league 389. leap390. leather 391. lightning 392. lip393. liquid 394. litre395. location 396. logic397. long-term 398. loose 399. lord400. lorry401. loudly 402. loudspeaker403. lung 404. machinery 405. mailbox 406. man-made 407. mature 408. maximum 409. mayor 410. mechanic 411. mechanical 412. medium 413. memorial 414. mend 415. mess 416. midday 417. mild 418. millionaire 419. mine 420. mineral 421. ministry 422. miserable 423. misfortune 424. mislead 425. mist 426. mistaken 427. mixture 428. modem 429. modest 430. mommy 431. monument 432. mop433. moreover434. motherland435. motorbike436. motorcycle437. mountainous438. mud439. murder440. mysterious441. nail442. narrowly443. nationality444. nationwide445. naughty446. navy447. neat448. necessity449. necklace450. neglect451. negotiate452. nephew453. nerve454. nevertheless455. nickname456. niece457. nonstop458. notebook459. novelist460. numerous461. nutrition462. objective 463. observation 464. occupy 465. offence 466.officially 467. oneself 468. opera 469. operator 470. opportunity 471. oppose 472. optimistic 473. oral474. organ 475. origin 476. originally 477. outcome 478. outing 479. outline 480. outlook 481. overall 482. overcoat 483. overhead 484. overnight 485. overtake 486. owing 487. ownership 488. pacific 489. packet 490. pale491. panda 492. pardon 493. passer-by 494. patent 495. pavement 496. peasant 497. pedestrian 498. percentage 499. performer 500. personnel 501. philosopher502. pianist503. pig504. pill505. pillow506. pin507. pine508. pink509. pioneer510. playmate511. plot512. plough513. plug514. poisonous515. polar516. polish517. postage518. postman519. pot520. potato521. preference522. pregnant523. presence 524. presentation 525. preserve 526. primitive 527. printing 528. priority 529. privately 530. procedure 531. progressive 532. prohibit 533. promotion 534. pronounce 535. pronunciation 536. proposal 537. propose 538. protest 539. province 540. punishment 541. purple 542. pyramid 543. qualification 544. qualified 545. quiz546. quote 547. rabbit 548. radiation 549. rag550. rainbow 551. rank552. raw553. ray554. realistic555. rebuild556. receiver557. reception 558. recite559. recommendation 560. record561. reduction 562. reference 563. reflection 564. reform565. refresh566. refrigerator 567. regulate568. regulation 569. reject570. relay571. relevant572. relief573. religion574. representative 575. republic576. resemble 577. reservation 578. resist579. restrict580. resume581. retell582. reuse583. reveal 584. revision 585. resolution 586. rewrite 587. ridiculous 588. right-handed 589. ripe590. romantic 591. rot592. routine 593. row594. rumour 595. sacrifice 596. sailor 597. salad 598. salt599. salty600. satisfactory 601. scan602. scar603. skeptical 604. schoolbag 605. schoolboy 606. schooling 607. schoolmate 608. scold 609. scratch 610. sculpture 611. seal612. seaside613. secondary 614. secure 615. selfish 616. separation 617. session 618. settlement 619. sew620. shallow 621. sharpen 622. shell623. shift624. shopkeeper 625. shortcoming 626. shortly 627. shorts 628. shrink 629. sickness 630. sidewalk 631. signature 632. significance 633. Sincerely 634. skate 635. skillful 636. skip637. skirt638. slavery 639. slim640. slip641. snowy 642. soap643. soccer644. sock645. somewhat 646. sorrow647. southwest 648. souvenir 649. specifically 650. spell651. spelling 652. spiritual 653. split654. spoil655. spokesman 656. sponsor 657. stable658. stadium 659. starve660. statistics 661. status662. steady663. steam664. storage 665. stove666. straightforward 667. straw668. strawberry 669. stretch670. strictly671. stroke672. studio673. submit674. substitute675. suck676. summary677. sunglasses678. sunrise679. super680. superior681. swallow682. swell683. sweat684. sympathetic685. table tennis686. tailor687. tank688. tap689. tasty690. taxpayer691. teamwork692. technician693. telescope694. temple695. tense 696. terrify 697. territory 698. theft699. theirs 700. thirst701. thirsty 702. thorough 703. thread 704. threat 705. throat 706. tick707. tidy708. tight709. tin710. toast712. toilet713. tone714. torch715. tourism 716. towel717. tractor 718. tragedy 719. tram720. transform 721. translation 722. translator 723. tremble 724. trial725. troublesome 726. trunk727. tube728. tune729. tutor730. twist731. typewriter 732. tyre733. uncertain 734. unconscious735. undergo736. undertake737. undoubtedly738. uneasy739. unemployed740. unfair741. unfortunate742. universe743. unlikely744. unwilling745. up-to-date746. upwards747. urgent748. vain749. valid751. vice 752. violent 753. visa 754. visible 755. vision 756. visual 757. vital 758. vitamin 759. vivid 760. vocabulary 761. volleyball 762. volume 763. voluntary 764. vote 765. wage 766. wagon 767. waitress 768. wander 769. ward 770. weaken 771. weed 772. weekday 773. well 774. wheat 775. whereas 776. widespread 777. wind 778. windy 779. wipe780. wisely 781. witness 782. wool 783. worthwhile 784. worthy 785. wrist 786. X-ray 787. yawn 788. yearly 789. yell。
Exchange_2003_反垃圾邮件动手篇

Exchange 2003 反垃圾邮件技术动手实验实验手册1. 实验目的通过动手操作,深入了解Exchange 2003 反垃圾邮件的技术与原理,掌握Exchange 2003 反垃圾邮件的工具与方法。
2. 实验场景为比较全面地验收和实验Exchange 2003反垃圾邮件的各种场景,本实验涉及一个服务器端和一个客户机端。
3. 实验环境配置实验涉及的Exchange 2003邮件服务器具体配置如下:▪活动目录域:此域中的域控制器即为Exchange 2003邮件服务器:✓ IP:192.168.0.2✓根域中的第一台域控制器。
同时具备五个操作主机角色、全局编目GC功能、以及DNS服务功能。
▪客户机:antispam-client此为邮件客户端,安装Outlook 2003、垃圾邮件模拟发送工具✓ IP:192.168.0.3✓确认安装微软补丁(KB902953)▪其他配置:✓管理员Adminisrator口令:Password01!▪虚拟机配置:该实验在Microsoft Vitrual PC 2004虚拟机环境中运行。
为保证性能,主机要求1G内存,10G空闲硬盘空间。
该实验用到以下虚拟硬盘文件:✓AntiSPAM-Server.vhd Exchange 2003 Server硬盘镜像文件。
✓AntiSPAM-Server.vmc Exchange 2003 Server虚拟机配置文件。
✓AntiSpam-Client.vhd Outlook 2003客户机硬盘镜像文件。
✓AntiSpam-Client.vmc Outlook 2003客户机虚拟机配置文件。
将光盘中的以上文件复制到本地硬盘。
双击相应的.vmc文件,或在VirtualPC Console控制台中选中相关虚拟机,点击Start,即可打开虚拟机。
打开虚拟机前请确认所有虚拟机已启动Undo功能。
•说明:•本课程以动手实验为主,讲稿仅用于给学员提供实验内容的基本概念和纲要。
Fortinet FortiMail安全入门指南说明书

Securing Your Enterprise Office 365 with FortiMailThe appeal for Office 365 from Microsoft is readily apparent: nn A full suite of mission-critical business applicationsnn A “no operations” modelnn Always-on cloud distributionnn Disaster recovery and data security built inPlus many others. And Microsoft has done a first-rate job of making Office 365 both a complete solution and one that is easy to adopt. Microsoft has even built in layers of security—starting with physical security at their world-class data centers with layers on top for DDoS, encryption, anti-malware, and other critical security capabilities.While Microsoft has delivered a full-suite solution in Office 365, many organizations have a need for a “next-generation” level of security for their Office deployment. With the release of FortiMail in Azure (https:///en-us/marketplace/partners/ fortinet/fortinet-fortimail/) joining Forti M ail Cloud, not only is this level of security available but it is ready to deploy from directly within Microsoft’s Cloud environment.FortiMail Complements Office 365 Security in Microsoft’s CloudOne of the driving use cases for FortiMail has been added protection of Microsoft Office and Office 365. For customers looking for advanced threat protection a nd compliance, there’s a proven partnership with FortiMail + Microsoft Office solutions. What FortiMail brings to your Office 365 environment is:nn Top VBSpam + an ti-spam and anti-phishingnn NSS Labs Recommended detection and preventionnn Granular-level details on threats—including notifications on emails/docs that have been cleansednn Identity-based encryptionnn Predefined dictionaries that are customizableFortiMail is an integrated component of the Fortinet Security Fabric which ensures that not only can advanced email attacks be stopped at an early stage, but intelligence about the full attack lifecycle can be dynamically generated and distributed throughout the organization. And, because it’s delivered by Fortinet, FortiMail is backed by Fortinet’s industry-leading FortiGuard threat research, so you can rest easy knowing your mission-critical business applications are protected.Why FortiMail and Office 365?When Fortinet embarked on designing and developing FortiMail, the foundational design point was to ensure that communication and documents reach their destinations in a timely manner. Once this was established as the foundation, Fortinet went about building a security solution that fully protected customer communication without compromising the speed of business needed. The end result is an enterprise-class email security solution built with a“Low-Impact Scanning” approach: 1SOLUTION BRIEF: SECURING YOUR ENTERPRISE OFFICE 365 WITH FORTIMAILWhat’s the Catch—Must Be Difficult to Set Up, Right?Answer: No—the FortiMail + Office 365 setup is easy and straightforward. FortiMail has been working with Microsoft Office products for years, and FortiMail can be easily added either during the initial Office 365 setup or as an add-on later. Below is one reference architecture for the FortiMail + Office 365 solution. As you can see, not only is the next-generation protection available but all of the near-instantaneous processing takes place within Microsoft Cloud.Copyright © 2018 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.GLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 905 rue Albert Einstein Valbonne06560, Alpes-Maritimes, FranceTel +33 4 8987 0500APAC SALES OFFICE 300 Beach Road 20-01The Concourse Singapore 199555Tel: +65.6513.3730LATIN AMERICA SALES OFFICE Paseo de la Reforma 412 piso 16Col. Juarez C.P . 06600 México D.F.Tel: 011-52-(55) 5524-8428December 12, 2018Microsoft runs their software as a service (SaaS—Office 365 is a SaaS service) and their infrastructure as a service (IaaS—Microsoft Azure delivers both IaaS and platform as a service) on logically and physically separated infrastructure. However, all of Microsoft’s Cloud operates within a single autonomous system (AS). With this design, your information is secure, is delivered rapidly, and never has to leave Microsoft’s world-class network. Our FortiMail + Office 365 Cookbook can be found here: /how-to-integrate-fortimail-into-office-365/.You can find our FortiMail in A zure here: https://azure. /en-us/marketplace/partners/fortinet/fortinet-fortimail/.For more information on our Microsoft Azure program @Fortinet, please visit our Azure site: https:///azure .FortiMail Excels with Independent TestingFortinet is committed to rigorous independent testing and FortiMail is the most validated email security in the industry. It routinely earns top marks in Virus Bulletin VBSpam testing, ICSA ATD Email Certification, NSS Labs Breach Prevention Group Tests and SE Labs Email Security Services Testing. For more detail visit our certifications page: https:///corporate/about-us/product-certifications.htmlAbout Fortinet FortiMailFortiMail is provided by Fortinet, Inc., ( ),a recognized global security leader. Fortinet’s FortiMail Secure Email Gateway provides protection to organizations against message-born threats, and it provides a turnkey approach to secure and clean corporate email. FortiMail provid es high-performance mail routing and security by utilizing a range of high-accuracy, anti-spam filters coupled with FortiGuard’sindustry-leading antimalware and advanced threat protection s . This is complement by a full range of data controls- includingDLP, email encryption and more.。
电子邮件

双击这里, 打开浏览器
在地址栏输入提供免费 邮箱的网址,打开网页
点击这里就可以 开始注册新的电 子邮箱
输入你自己设定的用户名,该用 户名将会成为你的邮箱地址的一 部分
温馨提示: 用户名只能由英文字母a~z, 数字0~9,下划线组成;起始字 单击“下一步” 符已经是英文字母;长度为 继续注册 6~20个字符
电子邮件:electronic mail ,简称E-mail, 是一种用电子手段提供信息交换的通 信方式,是Internet应用最广的服务。 用户可以用非常低廉的价格,以非常 快速的方式,与世界上仸何一个角落 的网络用户联系,这些电子邮件可以 是文字、数据库、图象、声音、视频 等各种方式,使用时并不要求双方同 时在线。
@ 读 作 "
at
"
打开浏览器, 在地址栏输入网址, 打开网页
输入用户名及密码, 然后单击登录
输入收件人完整的email地址
单击这里,可 以添加图片、 音乐、视频等 多媒体文件
主题相当于作文的 题目,可填写信件 的中心内容,是可 选项
这是编辑区,相 当于信纸,用来 编写信件的内容 选中要添加 的文件后, 单击打开
电子邮件E-mail
肇庆市实验中学 陈维欣
——小猪兄妹的故事
普通邮寄
邮局
电子邮件
邮局
电子邮件真是一种快捷、方便、 廉价、图文并茂的邮寄方式,它 可以做到足不出户就能将信件发 送到世界任何一个地方。
认识电子邮件
如何申请免费电子邮箱
电子邮箱的表示方法 编写及发送电子邮件 接收电子邮件
认识电子邮件
利用电子邮箱发送带附件的邮件 接收电子邮件
登录 http://192.168.0.118学科资料栏可以下 载本课件及相关资料。 如有疑问可发邮件到 itwxchen2007@ 或登录我的BLOG 留言与我讨论。
E-mail的设置和使用

E-mail的设置和使用收发电子邮件与通过邮局寄信一样,同样要求给出正确的地址,才能将它送到目的地。
在Internet的电子邮件系统中,每个用户有一个或几个E-mail地址;与E-mail地址紧密相关的概念还有E-mail帐号,E-mail帐号是为了使用E-mail地址接收和发送E-mail所需要的,用来登录到电子邮件服务器上的用户密码。
■申请E-mail邮箱的途径1.到当地电信部门申请相对永久、可靠的E-mail邮箱。
苏州用户的电子邮箱容量为2M。
2.寻求Internet上提供的免费邮箱服务(如:、等)提供免费邮箱服务的网址:■Outlook Express的使用在桌面上实现了全球范围的联机通讯,并可管理多个邮件和新闻帐号及轻松快捷地浏览邮件。
“开始”菜单下的“程序”中“Outlook Express”。
运行Outlook Express如果第一次运行Outlook Express,会弹出Internet连接向导对话框。
可以根据自己的实际情况及向导的提示设置好Internet连接,然后进入Outlook Express,以后每次运行Outlook Express时,就可以直接进入。
1.在“Internet连接向导”对话框中,选中“手动设置Internet连接或通过局域网连接”,单击“下一步”。
2.选择“通过电话线和调制解调器连接”,单击“下一步”。
3.键人通过拨号连人ISP所用的电话号码(如:163、169,ISDN用户:463、469)4.键人用于登陆到ISP的用户名和密码,单击“下一步”。
5.可以在弹出的对话框中修改连接名,然后点去“下一步”。
6.在弹出的对话框中选择“否”,即暂不设置Internet邮件帐号,单击“下一步”。
若想现在设置Internet邮件帐号,可单击“是”,然后进入“添加邮件帐号”进行设置。
7单击“完成”。
■添加邮件帐号1.在“工具”菜单中,单击“帐号”。
如图(6-1)图(6-1)2.在“Internet帐号”对话框中,单击“添加”按钮,选择邮件,以打开Internet连接向导。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
OnSite
Installation/Enrollment
Review the System Requirement
Enroll for a Digital Certificate Configure Outlook Email Account Verify the recipient also has Secure Email
OnSite
How it Works
– When registering for secure e-mail 2 keys are generated :
• a public key, which is stored in the Global
Address List : this is used for encrypting messages sent to you by others.
Masud Hasan 03-60-475 Secure Email
Project 1
Secure Email
It uses Digital Certificate combined with S/MIME capable email clients to digitally sign and encrypt E-mail
OnSite
QUESTIONS
Only easy ones will be answered! Kidding~~
OnSite
Configuring Outlook
OnSite
Configuring Outlook
OnSite
Sending Secure Email
•Encryption should not be set as a default
•To send a signed or encrypted message:
OnSite
Receiving Secure Email
•No action needs to be taken
•An encrypted message cannot be viewed in the preview pane, it must be opened •The lock and seal icons will appear on the message showing that it has been encrypted and signed
System Requirements
•Operating Systems: Windows 98 native &
Second Edition, Windows NT with Service Pack 5, Windows 2000 Power User or with a patch installed by an administrator. •Browsers: IE V5sp1 or later, 128 bit encryption enabled (domestic version) •Email programs: Outlook 98 or 2000 •Disk Space: Minimal •Intel platform. The computer must have at least a 100 MHZ Pentium processor.
OnSite
Enrollment Steps
OnSite
Enrollment Steps
OnSite
Configuring Outlook
•The user must configure their security settings in Outlook to recognize and make use of their newly downloaded personal certificate. This would involve:
- Click the lock and seal icons on the toolbar of a new message
-or-Go to Options on the toolbar of a new message and check Encrypt Message and Add Digital Signature
Digital Certificate
•A digital certificate is an electronic means of establishing your credentials when doing business or other transactions on the Web. It is issued by a certification authority (CA). It contains your name, a serial number, expiration dates, a copy of the certificate holder's public key (used for encrypting and decrypting messages and digital signatures), and the digital signature of the certificate-issuing authority so that a recipient can verify that the certificate is real.
OnSite
Services/ Mechanisms and Algorithm Used
Services in a security protocol
Signatures
Encryption
Hashing
RSA
DES
SHAI
OnSite
How you can secure your Email?
OnSite
Supported Platforms
•IE 5.0 SP1 or better is the only web browser currently supported for enrollment. •Wireless handheld and palmtop devices are not currently supported for secure email. •Outlook Web Access does not currently support secure email. •Alternatives to the standard solution such as PGP may not be used for secure email.
OnSite
Conclusion
I have been able to improve my knowledge in Computer Security by learning this tool.
My second project will be able to provide more details about PGP mail client using leading encryption techniques and to compare two different technologies for same purpose. Until then, Thanks for listening and good luck for Midterm.
• There are free digital certificates in the web. • Microsoft Email Clients have S/MIME protocol •Unix user can use it too •Following all the steps, you can secure your email.
S/MIME Client
– There are currently two actively proposed methods for providing these security services: S/MIME and PGP (both in its early incarnation as PGP/MIME, and as the new OpenPGP standard). – Microsoft Outlook: S/MIME Client.
-Selecting a Signing Certificate -Choosing a hash algorithm
-Deciding on a name and format for the settings
-Having clear text signed messages sent
OnSite
• a private key, which is stored in the mail
client (Outlook) on your pc : is used for digitally signing your own messages, and for decrypting encrypted messages sent to you.
Two Basic Features
– The two basic features of Email security are privacy (only the intended recipient can read the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently.
