数据中心防火墙参数
USG6300E系列防火墙规格参数

支持 支持 支持 支持 支持
千兆NGFW(USG6300/USG6500)
USG6308E
USG6312E
USG6322E
300~500
400~600
500~700
800Mbps
1Gbps
2Gbps
120万
180万
240万
8万
可视化多维度报表呈现,支持用户、应用、内容、时间、流量、威胁、URL等多维度呈现报表。 通过华为安全中心平台生成“网络安全分析报告”,对当前网络的安全状态进行评估,并给出相关优化建议。
全面支持IPV4/IPV6下 的多种路由协议,如RIP 、OSPF、BGP、IS-IS、 ACL6等;
透明、路由、混合部署模式。
度:5%~95%
温度:-40℃~70℃ /湿度:5%~95%
一体化防护
应用识别与管控
入侵防御与Web防护 防病毒 数据防泄漏 带宽管理 URL过滤 行为和内容审计 业务智能选路 VPN SSL加密流量检测
集传统防火墙、VPN、 入侵防御、防病毒、数 据防泄漏、带宽管理、 本地URL过滤等多种功 能于一身,全局配置视 图和一体化策略管理。
可作为代理检测并防御隐藏在SSL加密流量中的威胁,包括入侵防御、防病毒、内容过滤、URL过滤等应用层防护。
基于用户的防护 云管理 安全虚拟化 智能策略管理(SmartPolicy)
丰富的报表
路由特性 部署方式
支持多种用户认证方式,包括本地、RADIUS、Hwtacacs、AD、CA、LDAP、单点登录、MAC认证、免认证等。
100~240V -
60W
100~240V -
华为HiSecEngine USG6300E系列新一代防火墙V600R007C00规格清单(含详细参数)

路由特性
全面支持IPV4/IPV6下的多种路由协议,如RIP、OSPF、BGP、IS-IS、ACL6等;
全面支持I
部署方式
1:仅供参考,根据实际网络环境 的2:不最同大可吞能吐会量有是差以异1。518字节包长 流量在理想环境下测试得出,实际 情况会因现网情况不同而出现变化 。 3:性能数据是在理想环境下测试得出,实际情况会因现网情况不同而出现变化。
现,支持用户、应用、内容、时间、流量、威胁、URL等多维度呈现报表。 “网络安全分析报告”,对当前网络的安全状态进行评估,并给出相关优化建议。
全面支持IPV4/IPV6下的多种路由协议,如RIP、OSPF、BGP、IS-IS、IPv6RD、ACL6等;
透明、路由、混合部署模式。
5.8KG
1U盒式 442*420*43.6
5.8KG
1U盒式 442*420*43.6
5.8KG
1U盒式
442*420*43.6
7.6KG 选配2.5英寸形 态硬盘,支持 SSD 240GB/ HDD 1TB
标配单电源,选配双电源
100~240V -
35W
100~240V -
35W
100~240V -
丰富的报表
支持防火墙向云管理平台自动注册,云管理平台对防
支持多种安全业务的虚拟化,包括防火墙、入侵防御、反病毒、VPN等。不
预置常用防护场景模板,快速部署安全策 自动评估安全策略存在的风险,智能
支持策略冲突和冗余检测,发现冗余的和长期未使 可视化多维度报表呈现,支持用户、应用、内容、时间、流 通过华为安全中心平台生成“网络安全分析报告”,对当前网络的
透明、路由、混合部署模
W(USG6300/USG6500) USG6315E-AC 400~600 1 Gbps 180万 8万 1Gbps 4,000 500 15,000 50
华为防火墙配置使用手册(自己写)[4]
![华为防火墙配置使用手册(自己写)[4]](https://img.taocdn.com/s3/m/2085ce1fcdbff121dd36a32d7375a417866fc10f.png)
华为防火墙配置使用手册(自己写)华为防火墙配置使用手册一、概述二、防火墙基本概念包过滤防火墙:它只根据数据包的源地址、目的地址、协议类型和端口号等信息进行过滤,不对数据包的内容进行分析。
它的优点是处理速度快,开消小,但是安全性较低,不能阻挠应用层的攻击。
状态检测防火墙:它在包过滤防火墙的基础上,增加了对数据包的连接状态的跟踪和记录,可以识别出非法的连接请求和数据包,并拒绝通过。
它的优点是安全性较高,可以阻挠一些常见的攻击,但是处理速度较慢,开消较大。
应用代理防火墙:它对数据包的内容进行深度分析,可以识别出不同的应用协议和服务,并根据应用层的规则进行过滤。
它的优点是安全性最高,可以阻挠复杂的攻击,但是处理速度最慢,开消最大。
访问控制:它可以根据源地址、目的地址、协议类型、端口号、应用类型等信息对网络流量进行分类和过滤,实现对内外网之间访问权限的控制和管理。
虚拟专网:它可以建立安全隧道,实现不同地域或者组织之间的数据加密传输,保证数据的机密性、完整性和可用性。
内容安全:它可以对网络流量中携带的内容进行检查和过滤,如、网页、文件等,并根据预定义的规则进行拦截或者放行。
用户认证:它可以对网络访问者进行身份验证,如用户名、密码、证书等,并根据不同的用户或者用户组分配不同的访问权限和策略。
流量管理:它可以对网络流量进行统计和监控,如流量量、流量速率、流量方向等,并根据预定义的规则进行限制或者优化。
日志审计:它可以记录并保存网络流量的相关信息,如源地址、目的地址、协议类型、端口号、应用类型、过滤结果等,并提供查询和分析的功能。
三、防火墙配置方法命令行界面:它是一种基于文本的配置方式,用户可以通过控制台或者远程终端访问防火墙,并输入相应的命令进行配置。
它的优点是灵便性高,可以实现细致的配置和管理,但是需要用户熟悉命令的语法和逻辑。
图形用户界面:它是一种基于图形的配置方式,用户可以通过浏览器或者客户端软件访问防火墙,并通过或者拖拽等操作进行配置。
数据中心防火墙方案

03
异步处理
采用异步处理技术减少用户等待时间,提高用户体验和响应速度。
07
可用性保障
高可用性设计
冗余设计
为了确保数据中心的防火墙在任何情况下都能持续工作,应采 用冗余设计,包括冗余电源、冗余网络接口等。
负载均衡
通过负载均衡,可以将数据流量分散到多个防火墙设备上,以 提高系统的可用性和性能。
快速恢复
SSL/TLS协议
使用SSL/TLS协议对数据传输过程进行加密,确保数据在传输过 程中不被窃取或篡改。
加密算法选择
选择适合的加密算法,如AES、RSA等,根据实际需求选择合适 的加密算法。
06
性能优化
网络优化
网络架构优化
采用分布式、层次化的网络架构,减少网络复杂 性和瓶颈,提高网络吞吐量和响应速度。
负载均衡
通过负载均衡技术将网络流量分配到多个服务器 或网络设备上,以提高网络处理能力和吞吐量。
网络流量分析
对网络流量进行实时监测和分析,识别和解决网 络瓶颈和性能问题。
系统优化
硬件优化
选用高性能的硬件设备,如高性能的CPU、内存和存储设备,提高系统处理能力和响应速 度。
操作系统优化
对操作系统进行定制和优化,去除不必要的组件和服务,减少系统资源占用和性能瓶颈。
软件设计
操作系统
选择专业的操作系统,能够提供安全、稳定、高效的运行环境。
防火墙软件
选择专业的防火墙软件,能够提供强大的防护功能和安全策略管 理。
病毒防护软件
选择专业的病毒防护软件,能够有效地防止病毒攻击和恶意软件 的入侵。
架构设计
分层设计
将防火墙分为多个层次,能够提高防火墙的防护 能力和效率。
深信服应用防火墙参数

支持多个内部地址映射到同一个公网地址、多个内部地址映射到多个公网地址、内部地址到公网地址一一映射、源地址和目的地址同时转换、外部网络主机访问内部服务器、支持DNS映射功能
可配置支持地址转换的有效时间
支持多种NAT ALG,包括DNS、FTP、H.323、SIP等
IPSecVPN功能
支持AES、DES、3DES、MD5、SHA1、DH、RC4等算法,并且支持扩展国密办SCB2等其他加密算法支持MD5及SHA-1验证算法
病毒库数量
支持10万条以上的病毒库,并且可以自动或者手动升级
流控
应用特征识别库
*支持对1000种以上应用2000种以上的应用动作(需提供截图证明)
应用流控
*支持基于应用类型划分与带宽分配
网站流控
*支持基于网站类型的划分与带宽分配
文件流控
支持基于文件类型划分与分配带宽
WEB安全防护
URL过滤
*对用户web行为进行过滤,保护用户免受攻击;支持只过滤HTTP GET、HTTP POST、HTTPS等应用行为;并进行阻断和记录日志
文件类型过滤
*支持针对上传、下载等操作进行文件过滤;支持自定义文件类型进行过滤;支持基于时间表的策略制定;支持的处理动作包括:阻断和记录日志
ActiveX过滤
*支持基于签名证书的ActiveX过滤;支持添加白名单和合法网站列表;支持基于应用类型的ActiveX过滤,如视频、在线杀毒、娱乐等;
脚本过滤
抗攻击特性
支持防御Land、Smurf、Fraggle、WinNuke、Ping of Death、Tear Drop、IP Spoofing、SYN Flood、ICMP Flood、UDP Flood、DNS Query Flood、ARP欺骗攻击防范、ARP主动反向查询、TCP报文标志位不合法攻击防范、支持IP SYN速度限制、超大ICMP报文攻击防范、地址/端口扫描的防范、DoS/DDoS攻击防范、ICMP重定向或不可达报文控制等功能,此外还支持静态和动态黑名单功能、MAC和IP绑定功能
数据中心环境要求与检测标准

数据中心环境要求与检测标准随着信息技术的快速发展,数据中心已成为现代社会的重要组成部分,承担着处理、存储和管理海量信息的重要任务。
为了确保数据中心的稳定运行和数据安全,对数据中心环境的要求与检测标准变得尤为重要。
一、数据中心环境要求1、温度和湿度:数据中心要求严格的温度和湿度范围。
温度过高可能导致设备过热,影响性能甚至引发故障。
湿度过低可能会导致静电问题,湿度过高则可能导致设备腐蚀。
因此,一般要求温度在20-25℃之间,湿度在40%-60%之间。
2、空气质量:数据中心内的空气质量也会影响设备的运行。
过多的尘埃、污染物或酸性气体可能会腐蚀设备或干扰其正常运行。
因此,需要定期清洁和过滤数据中心内的空气。
3、电力供应:数据中心需要稳定的电力供应,任何电力中断都可能导致数据丢失或设备故障。
因此,建议使用不间断电源(UPS)以确保电力供应的连续性。
4、防火防灾:数据中心应具备有效的防火和防灾措施。
火灾和自然灾害都可能对数据中心造成严重损害,因此必须采取适当的预防措施。
5、噪声和振动:噪声和振动可能会干扰数据中心的正常运行。
因此,需要采取措施来减少这些影响,例如使用隔音材料和减震设备。
二、数据中心检测标准1、设备性能:定期检查和维护数据中心的设备,确保其性能正常。
应定期进行硬件和软件的更新和升级,以保持最佳性能。
2、温度和湿度:定期检查数据中心的温度和湿度,确保其在规定的范围内。
如果发现任何异常,应立即采取行动进行调整。
3、空气质量:定期进行空气质量检测,确保数据中心内没有过多的尘埃、污染物或酸性气体。
4、电力供应:定期检查电力供应的稳定性和UPS的性能。
如果发现任何问题,应立即采取行动解决。
5、防火防灾:定期检查防火和防灾设施的性能和状态,确保其在良好的工作状态。
6、噪声和振动:定期检查数据中心的噪声和振动水平,确保其不会干扰设备的正常运行。
为了确保数据中心的稳定运行和数据安全,必须严格遵守上述环境要求和检测标准。
H3C防火墙技术参数
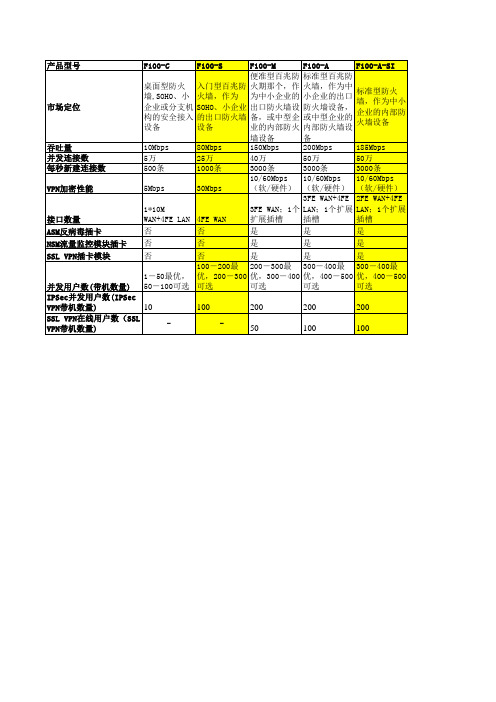
吞吐量 并发连接数 每秒新建连接数 VPN加密性能 VPN加密性能
接口数量 ASM反病毒插卡 ASM反病毒插卡 NSM流量监控模块插卡 NSM流量监控模块插卡 VPN插卡模块 SSL VPN插卡模块
并发用户数(带机数量) 并发用户数( 带机数量) IPSec并发用户数 并发用户数( IPSec并发用户数(IPSec 10 VPN带机数量 带机数量) VPN带机数量) VPN在线用户数 在线用户数( SSL VPN在线用户数(SSL VPN带机数量 带机数量) VPN带机数量)
F100-C
F100-S
F100-A-SI 标准型防火 墙,作为中小 企业的内部防 火墙设备 185Mbps 50万 3000条 10/60Mbps (软/硬件) 2FE WAN+4FE LAN;1个扩展 插槽 是 是 是 300-400最 优,400-500 可选
100
-
200 50
200 100
F100-M 便准型百兆防 桌面型防火 入门型百兆防 火期那个,作 墙,SOHO、小 火墙,作为 为中小企业的 企业或分支机 SOHO、小企业 出口防火墙设 构的安全接入 的出口防火墙 备,或中型企 设备 设备 业的内部防火 墙设备 10Mbps 80Mbps 150Mbps 5万 25万 40万 500条 1000条 3000条 10/60Mbps 5Mbps 30Mbps (软/硬件)
F100-A 标准型百兆防 火墙,作为中 小企业的出口 防火墙设备, 或中型企业的 内部防火墙设 备 200Mbps 50万 3000条 10/60Mbps (软/硬件) 3FE WAN+4FE 1*10M 3FE WAN;1个 LAN;1个扩展 WAN+4FE LAN 4FE WAN 扩展插槽 插槽 否 否 是 是 否 否 是 是 否 否 是 是 100-200最 200-300最 300-400最 1-50最优, 优,200-300 优,300-400 优,400-500 50-100可选 可选 可选 可选
Hillstone X系列数据中心防火墙X10800说明书

Hillstone X-SeriesData Center Firewall X10800X10800The Hillstone X10800 Data Center Firewall offers outstanding performance, reliability, andscalability, for high-speed service providers, large enterprises and carrier networks. The product is based on an innovative fully distributed architecture that fully implements firewalls with high throughput, concurrent connections, and new sessions. Hillstone X10800 also supportslarge-capacity virtual firewalls, providing flexible security services for virtualized environments, and features such as application identification, traffic management, intrusion prevention, and attack prevention to fully protect data center network security.FrontRearProduct HighlightHigh Performance based on Elastic Security ArchitectureWith traffic explosively increasing, data center firewalls need powerful capabilities to handle high traffic and massive concurrent user access, as well as the ability to effectively cope with sudden bursts of user activity. Therefore, data center firewalls must not only have high throughput but also extremely high concurrent connections and new session processing capabilities.The Hillstone X10800 Data Center Firewall adopts an inno-vative, fully distributed architecture to implement distributed high-speed processing of service traffic on Service Modules (SSMs) and Interface Modules (IOMs) through intelligent traffic distribution algorithms. Through patented resource management algorithms, it allows for the full potential of dis-tributed multi-core processor platforms, to further increase the performance of firewall concurrent connections, new sessions per second, and achieve a fullly linear expansionof system performance. The X10800 data center firewall can process up to 1 Tbps, up to 10 million new sessionsper second, and up to 480 million concurrent connections. The device can provide up to 44 100GE interfaces, 88 10G interfaces, or 22 40GE interface, 132 10G interface expansion capabilities. Moreover, the packet forwarding delay is less than 10us, which can fully meet a data center’s demand for real-time service forwarding.Carrier Grade ReliabilityThe hardware and software of the X10800 data center fire-wall delivers 99.999% carrier-grade reliability. It can support active/active or active/passive mode redundant deployment solutions to ensure uninterrupted service during single failure. The entire system adopts a modular design, supporting con-trol module redundancy, service module redundancy, inter-face module redundancy and switching module redundancy, and all modules are hot-swappable.The X10800 data center firewall supports multi-mode and single-mode optical port bypass modules. When the device is running under a special condition, such as power off, the system will start in Bypass mode to ensure uninterrupted operation of business. It also provides power redundancy, fan redundancy and other key components to guarantee reliability.Twin-mode HA effectively solves the problem of asymmetric traffic in redundant data centers. The firewall twin-mode isa highly reliable networking mode building on dual-device backup. Two sets of active/passive firewalls in the two data centers are connected via a dedicated data link and control link. The two sets of devices synchronize session information and configuration information with each other.Leading Virtual Firewall TechnologyVirtualization technology is more and more widely used in data centers. The X10800 data center firewall can logically divide a physical firewall into upwards of 1000 virtual fire-walls for the data center’s virtualization needs, providing virtual firewall support capabilities for large data centers. At the same time, users can dynamically set resource for each virtual firewall based on actual business conditions, suchas CPUs, sessions, number of policies, ports, etc., to ensure flexible changes in service traffic in a virtualized environment. Each virtual firewall system of X10800 data center firewalls not only has independent system resources, but also can be individually and granularly managed to provide independent security management planes for different services or users. Granular Application Control and Comprehensive SecurityThe X10800 data center firewall uses advanced in-depth application identification technology to accurately iden-tify thousands of network applications based on protocol features, behavior characteristics, and correlation analysis, including hundreds of mobile applications and encrypted P2P applications. It provides sophisticated and flexible application security controls.The X10800 data center firewall provides intrusion prevention technology based on deep application identification, proto-col detection, and attack principle analysis. It can effectively detect threats such as Trojans, worms, spyware, vulnerability attacks, and escape attacks, and provide users with L2-L7Product Highlight (Continued) FeaturesNetwork Services• Dynamic routing (OSPF, BGP, RIPv2)• Static and Policy routing• Route controlled by application• Built-in DHCP, NTP, DNS Server and DNS proxy • Tap mode – connects to SPAN port• Interface modes: sniffer, port aggregated, loopback, VLANS (802.1Q and Trunking)• L2/L3 switching & routing• Virtual wire (Layer 1) transparent inline deploymentFirewall• Operating modes: NAT/route, transparent (bridge), and mixed mode• Policy objects: predefined, custom, and object grouping• Security policy based on application, role and geo-location• Application Level Gateways and session support: MSRCP, PPTP, RAS, RSH, SIP, FTP, TFTP, HTTP, dcerpc, dns-tcp, dns-udp, H.245 0, H.245 1, H.323 • NAT and ALG support: NAT46, NAT64, NAT444, SNAT, DNAT, PAT, Full Cone NAT, STUN• NAT configuration: per policy and central NAT table• VoIP: SIP/H.323/SCCP NAT traversal, RTP pin holing• Global policy management view• Security policy redundancy inspection, policygroup, policy configuration rollback• Policy Assistant for easy detailed policydeployment• Policy analyzing and invalid policy cleanup• Comprehensive DNS policy• Schedules: one-time and recurringIntrusion Prevention• Protocol anomaly detection, rate-based detection,custom signatures, manual, automatic push orpull signature updates, integrated threat encyclo-pedia• IPS Actions: default, monitor, block, reset(attackers IP or victim IP, incoming interface) withexpiry time• Packet logging option• Filter Based Selection: severity, target, OS, appli-cation or protocol• IP exemption from specific IPS signatures• IDS sniffer mode• IPv4 and IPv6 rate based DoS protection withthreshold settings against TCP Syn flood, TCP/UDP/SCTP port scan, ICMP sweep, TCP/UDP/SCIP/ICMP session flooding (source/destination)• Active bypass with bypass interfaces• Predefined prevention configurationAnti-Virus• Manual, automatic push or pull signature updates• Flow-based Antivirus: protocols include HTTP,SMTP, POP3, IMAP, FTP/SFTP• Compressed file virus scanningAttack Defense• Abnormal protocol attack defense• Anti-DoS/DDoS, including SYN Flood, DNS QueryFlood defense• ARP attack defenseURL Filtering• Abnormal protocol attack defense• Anti-DoS/DDoS, including SYN Flood, DNS QueryFlood defense• ARP attack defense• Flow-based web filtering inspection• Manually defined web filtering based on URL, webcontent and MIME header• Dynamic web filtering with cloud-based real-timecategorization database: over 140 million URLswith 64 categories (8 of which are security related)• Additional web filtering features:- Filter Java Applet, ActiveX or cookie- Block HTTP Post- Log search keywords- Exempt scanning encrypted connections oncertain categories for privacy• Web filtering profile override: allows administratorto temporarily assign different profiles to user/group/IP• Web filter local categories and category ratingoverridenetwork security. Among them, Web protection function can meet the deep security protection requirements of Web server; Botnet filtering function can protect internal hosts from infection.The X10800 data center firewall supports URL filtering for tens of millions of URL signature library. It can help admin-istrators easily implement web browsing access control and avoid threat infiltration of malicious URLs. It also provides Anti-virus feature that can effectively detect and block mal-wares with low latency.The intelligent bandwidth management of X10800 data center firewall is based on deep application identification and user identification. Combined with service application priorities, the X10800 data center firewall can implement fine-grained, two-layer, eight-level traffic control based on policies and provide elastic QoS functions. Used with functions such as session restrictions, policies, routing, link load balancing, and server load balancing, it can provide users with more flexible traffic management solutions.Strong Network AdaptabilityThe X10800 data center firewall fully supports next-genera-tion Internet deployment technologies (including dual-stack, tunnel, DNS64/NAT64 and other transitional technologies). It also has mature NAT444 capabilities to support static mapping of fixed-port block of external network addresses to intranet addresses. It can generate logs based on session and user for easy traceability. Enhanced NAT functions (Full-cone NAT, port multiplexing, etc.) can fully meet the require-ments of current ISP networks and reduce the cost of user network construction.The X10800 data center firewall provides full compliance with standard IPSec VPN capabilities and integrates third-gen-eration SSL VPN to provide users with high-performance, high-capacity, and full-scale VPN solution. At the same time, its unique plug-and-play VPN greatly simplifies configuration and maintenance challenges and provides users with convenient and remote secure access services.IP Reputation• Identify and filter traffic from risky IPs such as botnet hosts, spammers, Tor nodes, breached hosts, and brute force attacks• Logging, dropping packets, or blocking for different types of risky IP traffic• Regular IP reputation signature database upgrade Endpoint Identification and Control• Support to identify endpoint IP, endpoint quantity, on-line time, off-line time, and on-line duration • Support 10 operation systems, including Windows, iOS, Android, etc.• Support query based on IP, endpoint quantity, control policy and status etc.• Support the identification of accessed endpoints quantity across layer 3, logging and interference on overrun IP• Redirect page display after custom interference operation• Supports blocking operations on overrun IP Application Control• Over 3,000 applications that can be filtered by name, category, subcategory, technology and risk • Each application contains a description, risk factors, dependencies, typical ports used, and URLs for additional reference• Actions: block, reset session, monitor, traffic shaping• Identify and control cloud applications in the cloud • Provide multi-dimensional monitoring and statistics for cloud applications, including risk category and characteristicsQuality of Service (QoS)• Max/guaranteed bandwidth tunnels or IP/user basis• Tunnel allocation based on security domain, interface, address, user/user group, server/server group, application/app group, TOS, VLAN• Bandwidth allocated by time, priority, or equal bandwidth sharing• Type of Service (TOS) and Differentiated Services (DiffServ) support• Prioritized allocation of remaining bandwidth • Maximum concurrent connections per IP• Bandwidth allocation based on URL category • Bandwidth limit by delaying access for user or IP • Automatic expiration cleanup and manual cleanup of user used trafficServer Load Balancing• Weighted hashing, weighted least-connection, and weighted round-robin• Session protection, session persistence and session status monitoring• Server health check, session monitoring and session protectionLink Load Balancing• Bi-directional link load balancing• Outbound link load balancing includes policy based routing, ECMP and weighted, embeddedISP routing and dynamic detection• Inbound link load balancing supports SmartDNSand dynamic detection• Automatic link switching based on bandwidth,latency, jitter, connectivity, application etc.• Link health inspection with ARP, PING, and DNSVPN• IPSec VPN- IPSEC Phase 1 mode: aggressive and main IDprotection mode- Peer acceptance options: any ID, specific ID, ID indialup user group- Supports IKEv1 and IKEv2 (RFC 4306)- Authentication method: certificate andpre-shared key- IKE mode configuration support (as server orclient)- DHCP over IPSEC- Configurable IKE encryption key expiry, NATtraversal keep alive frequency- Phase 1/Phase 2 Proposal encryption: DES,3DES, AES128, AES192, AES256- Phase 1/Phase 2 Proposal authentication:MD5, SHA1, SHA256, SHA384,SHA512- Phase 1/Phase 2 Diffie-Hellman support: 1,2,5- XAuth as server mode and for dialup users- Dead peer detection- Replay detection- Autokey keep-alive for Phase 2 SA• IPSEC VPN realm support: allows multiple customSSL VPN logins associated with user groups (URLpaths, design)• IPSEC VPN configuration options: route-based orpolicy based• IPSEC VPN deployment modes: gateway-to-gateway, full mesh, hub-and-spoke, redundanttunnel, VPN termination in transparent mode• One time login prevents concurrent logins with thesame username• SSL portal concurrent users limiting• SSL VPN port forwarding module encrypts clientdata and sends the data to the application server• Supports clients that run iOS, Android, andWindows XP/Vista including 64-bit Windows OS• Host integrity checking and OS checking prior toSSL tunnel connections• MAC host check per portal• Cache cleaning option prior to ending SSL VPNsession• L2TP client and server mode, L2TP over IPSEC,and GRE over IPSEC• View and manage IPSEC and SSL VPN connec-tions• PnPVPNIPv6• Management over IPv6, IPv6 logging and HA• IPv6 tunneling, DNS64/NAT64 etc• IPv6 routing protocols, including static routing,policy routing, ISIS, RIPng, OSPFv3 and BGP4+• IPS, Application identification, URL filtering,Access control, ND attack defense, iQoS• Track address detectionVSYS• System resource allocation to each VSYS• CPU virtualization• Non-root VSYS support firewall, IPSec VPN, SSLVPN, IPS, URL filtering• VSYS monitoring and statisticHigh Availability• Redundant heartbeat interfaces• Active/Active and Active/Passive mode• Standalone session synchronization• HA reserved management interface• Failover:- Port, local & remote link monitoring- Stateful failover- Sub-second failover- Failure notification• Deployment options:- HA with link aggregation- Full mesh HA- Geographically dispersed HATwin-mode HA• High availability mode among multiple devices• Multiple HA deployment modes• Configuration and session synchronization amongmultiple devicesUser and Device Identity• Local user database• Remote user authentication: TACACS+, LDAP,Radius, Active• Single-sign-on: Windows AD• 2-factor authentication: 3rd party support,integrated token server with physical and SMS• User and device-based policies• User group synchronization based on AD andLDAP• Support for 802.1X, SSO Proxy• WebAuth page customization• Interface based Authentication• Agentless ADSSO (AD Polling)• Use authentication synchronization based onSSO-monitor• Support MAC-based user authenticationAdministration• Management access: HTTP/HTTPS, SSH, telnet,console• Central Management: Hillstone Security Manager(HSM), web service APIs• System Integration: SNMP, syslog, alliancepartnerships• Rapid deployment: USB auto-install, local andremote script execution• Dynamic real-time dashboard status and drill-inmonitoring widgets• Language support: EnglishFW Throughput (Maximum) (1)IPSec Throughput (Maximum) (2)IMIX Throughput(3)NGFW Throughput (4)Threat Protection Throughput (5)Concurrent Sessions (Maximum)New Sessions/s(6)IPS Throughput (Maximum) (7)Virtual Systems (Default/Max)I/O ModuleMaximum InterfacesMaximum Power Consumption Power SupplyManagement Interfaces Network Interfaces Expansion Module Slot Dimension (W × D × H)WeightCompliance and CertificateSpecificationsSG-6000-X10800Logs & Reporting• Logging facilities: local memory and storage (if available), multiple syslog servers and multiple Hillstone Security Audit (HSA) platforms • Encrypted logging and log integrity with HSA scheduled batch log uploading• Reliable logging using TCP option (RFC 3195) • Detailed traffic logs: forwarded, violated sessions, local traffic, invalid packets, URL etc.• Comprehensive event logs: system and adminis -trative activity audits, routing & networking, VPN, user authentications, WiFi related events• IP and service port name resolution option • Brief traffic log format option• Three predefined reports: Security, Flow and network reports• User defined reporting• Reports can be exported in PDF , Wordl and HTML via Email and FTPStatistics and Monitoring• Application, URL, threat events statistic and monitoring• Real-time traffic statistic and analytics• System information such as concurrent session, CPU, Memory and temperature• iQOS traffic statistic and monitoring, link status monitoring• Support traffic information collection and forwarding via Netflow (v9.0)Module OptionsDescriptionmodule 100GE, 10GE interface moduleQoS service module Security control moduleNetwork Interface4 QSFP28 100GEinterfaces, 8 SFP+ 10Gbinterfaces, transceiver notincluded N/AN/ASlot expansion slot Occupies 1 universal expansion slot expansion slot Occupies 1 universal expansion slot expansion slot Occupies 1 universal expansion slot Weight12.67 lb (5.75 kg)12.56 lb (5.70 kg)7.6 lb (3.45 kg)NOTES:(1) FW Throughput data is obtained under single-stack UDP traffic with 1518-byte packet size;(2) IPSec throughput data is obtained under Preshare Key AES256+SHA-1 configuration and 1400-byte packet size packet; (3) IMIX throughput data is obtained under UDP traffic mix (68 byte : 512 byte : 1518 byte =5:7:1);(4) NGFW throughput data is obtained under 64 Kbytes HTTP traffic with application control and IPS enabled;(5) Threat protection throughput data is obtained under 64 Kbytes HTTP traffic with application control, IPS, AV and URL filtering enabled; (6) New Sessions/s is obtained under TCP traffic;(7) IPS throughput data is obtained under bi-direction HTTP traffic detection with all IPS rules being turned on;(8) At least 3 AC power modules are required for full load operation with AC power, and at least 4 DC power modules are required for full load operation with DC power.Unless specified otherwise, all performance, capacity and functionality are based on StoneOS5.5R7. Results may vary based on StoneOS ® version and deployment.IOM-P100-300IOM-P40-300SWM-300QSM-300SSM-300SCM-300。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
提供智能策略分析功能,支持策略命中分析、策略冗余分析、策略冲突检查,并且可在WEB界面显示检测结果:红色为冗余策略,绿色为冲突策略;
内置攻击检测引擎,采用协议分析、模式识别、统计阀值和流量异常监视等综合技术手段来判断入侵行为;支持web攻击识别和防护,如跨站脚本攻击、SQL注入攻击;支持超过4200+攻击特征库,同时支持自定义特征库,设备厂商为CNNVD一级支撑单位,能够确保每周至少更新1次攻击特征库。
支持日志本地存储,可对不同类型日志设置存储空间;同时支持外发至SYSLOG服务器,可将多条日志合并成一条日志传送到日志服务器中,可选择对日志传输是否加密,设定8位的加密密钥
日志查看可划分பைடு நூலகம்管理日志、系统日志、策略日志、应用行为日志等四大模块,具体包含用户、连接、流量、NAT、审计、HA、APT、未知威胁等20个日志类别;
支持基于IPv6的应用层检测(FTP\TFTP)、病毒过滤、URL过滤、ADS、IPS检测
支持在一台物理设备上划分出128个相互独立的虚拟系统,可根据连接配额及连接新建速率为每个虚拟系统分配资源;
支持配置文件、系统服务等系统功能虚拟化,支持路由、链路聚合等网络功能虚拟化,支持安全策略、NAT策略、带宽管理、认证策略、IPV6功能、URL过滤、异常行为分析、病毒过滤、内容过滤、审计、报表等安全功能虚拟化;
支持根据应用对通过设备的数据报文流量进行统计,包括应用总流量排名和各个应用的协议名称、总流量、上行流量、下行流量、新建连接数、当前会话数以及流速;
支持根据用户/用户组对通过设备的数据报文流量进行统计,包括用户总流量排名和各个用户的用户名、认证类型、上行流量、下行流量、新建会话数、当前会话数以及流速;
内置统计智能学习算法,对特定地址对象建立监控策略,基于新建、并发、流量等数据与上一周期记录值进行比较判定是否异常,如果存在异常则报警;
内置不低于15类预定义报表模板,支持根据通信流量、上网行为、威胁统计等来源数据库自定义报表模板;支持一次性报表及周期性报表,可自定义统计时间;
支持独立配置审计策略,同时也可将指定的IP地址、URL、应用加入白名单,不进行数据审计;
支持一对一SNAT、多对一SNAT、一对一DNAT、双向NAT、NoNAT等多种转换方式;支持StickyNAT开关,使相同源IP的数据包经过地址转换后为其转换的源IP地址相同;
支持MAP66功能,将从内部发往Internet的数据包的源IPv6地址修改为全球单播源IPv6地址,实现IPv6网络间的地址转换;
支持网站访问审计:审计指定类别的URL地址、审计命中指定关键字的网页标题和网页内容;
支持邮件内容审计:对接收/发送邮件行为及邮件内容进行审计;FTP审计:对FTP上传/下载行为及文件内容进行审计;
提供完善的审计数据查询功能,方便管理员对用户的上网行为进行审查和分析。支持对用户上网行为进行完整的审计数据查询,包括访问网站、邮件收发、论坛微博、FTP等;同时支持对用户上网流量时长进行完整的审计数据查询,包括服务端IP、用户名、协议、上行流量、下行流量、总流量、时间等;
支持根据服务器对通过设备的数据报文流量进行统计,包括各个服务器的服务器IP、上行流量、下行流量、总流量以及新建会话数;
支持指定监控时间周期,包括:实时、最近1小时、最近1天、最近1周、最近1月等;
支持根据按照病毒防御、入侵防御、APT防御、ADS攻击进行威胁统计,可按照威胁类型/攻击者/受害者三种方式进行威胁排名。
内置病毒检测引擎,支持HTTP/SMTP/POP3/FTP/IM等协议的病毒防御,对每种协议数据流的检测方向可选双向、上传、下载;
内置至少2种专业反病毒厂商或研究机构的病毒特征库,符合等级保护相关标准对网关防病毒特征库和主机防病毒特征库异构的要求。病毒特征库规模超过400万
支持病毒白名单,用户可以根据实际业务需求将特定威胁进行排除;
支持智能DNS及DNSDocting功能,能够将来自内部网络的域名解析请求定向到真实内网资源,提高访问效率,同时支持通过配置多条DNSDoctoring,实现内网资源服务器的负载均衡
支持IPv6安全控制策略设置,能针对IPv6的目的/源地址、目的/源服务端口、区域、服务、时间、扩展头属性等条件进行安全访问规则的设置;
数据中心防火墙参数
系统具备防病毒、入侵防御功能模块,带3年升级服务
★硬件基于X86多核架构,1U机架产品,配置不低于6个10/100/1000BASE-T接口和2个SFP插槽,2个可插拨的扩展槽,双电源。
防火墙吞吐率不低于8Gbps,并发连接数不低于220万
支持路由、交换、混合、虚拟线工作模式;
为提高链路可靠性,需支持手工链路聚合及LACP链路聚合,提供不少于11种的负载分担算法,灵活实现对聚合组内业务流量的负载分担;
