AMP(安普)2011产品手册
安普变频器AMP1100用户手册第功能参数简表

下限频率~500.00 Hz
0.01
50.00
05H
b-6
下限频率
0.00 Hz~上限频率
0.01
0.50
06H
b-7
加、减速方式
0:直线 1:S 曲线
1
0
07H
b-8
加速时间 1
0.1~6000 秒
0.1
*
08H
b-9
减速时间 1
0.1~6000 秒
0.1
*
09H
b-10 REV/JOG 键功能选择 0:反转控制 1:点动控制
0.01~5.00
E-47 输入下限对应设定频率
0.00~上限频率
E-48 输入上限对应设定频率
0.00~上限频率
E-49 运行监控项目选择 2
0~19
E-50 运行监控项目选择 3
0~19
E-51 运行监控项目循环数量
1~3
E-52 停机监控项目选择
0~19
E-53 模拟输入通道滤波时间常数
0.01~5.00 秒
0.00~1.00V
E-41 II 输入下限电流
0.00mA~[E-42]
E-42 II 输入上限电流
[E-41]~20.00mA
代码
名称
设定范围
- 42 -
0.01
25.00
28H
0.01
30.00
29H
0.01
35.00
2AH
0.01
40.00
2BH
0.01
45.00
2CH
0.01
50.00
2DH
1:0~10V
b-17 AO 输出范围选择
AMP产品
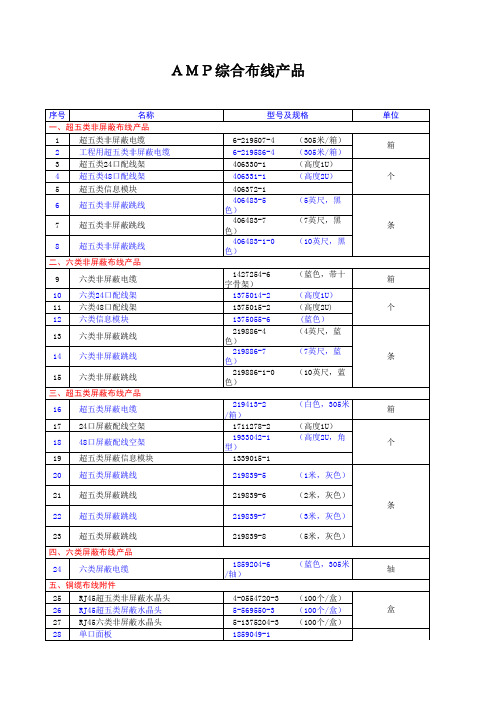
(1米,灰色) (2米,灰色) (3米,灰色) (5米,灰色) (蓝色,305米/
条
轴
五、铜缆布线附件 (100个/盒) (100个/盒) (100个/盒) 盒
个
31 水平环型线缆管理器 六、110语音(电话)系统布线产品 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 三类25对UTP电缆 语音50对UTP电缆 语音100对UTP电缆 100对挂墙式配线架套件 100对机架式110配线架 200对机架式110配线架 4对连接模块 5对连接模块
轴 套
个
语音(电话)模块 1对110XC到110XC跳线 1对110XC到110XC跳线 1对110XC到110XC跳线 2对110XC到110XC跳线 2对110XC到110XC跳线 2对110XC到110XC跳线 3对110XC到110XC跳线 3对110XC到110XC跳线 49 3对110XC到110XC跳线 50 4对110XC到110XC跳线 51 4对110XC到110XC跳线 52 4对110XC到110XC跳线 七、铜缆布线用工具产品 53 54 110打线工具(带刀头) RJ45压线钳
箱
个
二、六类非屏蔽布线产品 9 10 11 12 13 14 15 六类非屏蔽电缆 六类24口配线架 六类48口配线架 六类信息模块 六类非屏蔽跳线 六类非屏蔽跳线 六类非屏蔽跳线 (蓝色,带十字 (高度1U) (高度2U) ( 蓝色) (4英尺,蓝 (7英尺,蓝 (10英尺,蓝 箱 个
条
三、超五类屏蔽布线产品 16 17 18 超五类屏蔽电缆 24口屏蔽配线空架 48口屏蔽配线空架 (白色,305米/ (高度1U) (高度2U,角 箱
安普布线产品技术参数

(一)AMP NETCONNECT六类(Cat.6)产品技术规格(1)Cat.6非屏蔽低烟无卤(LSZH)双绞线技术规格(219585-2)•带宽:250MHz。
•标准:符合TIA/EIA 568B.2-1,IEC 61156-5 Cat.6等技术指标要求。
•结构:中间带十字架;•护套材料:低烟无卤(LSZH)•导体直径:23AWG•护套直径:6.0mm;•特性阻抗:100Ω±15Ω;1 MHz to 250 MHz•最大拉力:90N•材料:符合ROHS指令•第三方认证:丹麦Delta实验室认证, 北京产品质量监督检验所认证(2)Cat.6非屏蔽双绞线技术规格(1427254-6)•带宽:250MHz。
•标准:符合TIA/EIA 568B.2-1,ISO/IEC 11801B.2-1等技术指标要求。
•中间带十字架;•护套材料:聚氯乙烯(PVC)•导体直径:23AWG•护套直径:6.4mm;•防火等级:CM,符合UL 444,UL认证文件编号E138034•特性阻抗:100Ω±15Ω;1 MHz to 250 MHz•传输延迟: 最大536 ns/100 m. @ 250 MHz•延迟偏差: 最大45 ns•第三方认证:中国信息产业部通信产品质量监督检验中心认证,•材料:符合ROHS指令(3)Cat.6非屏蔽双绞线技术规格(9-1427200-6)Cat.6非屏蔽双绞线 (9-1427200-6) 1-300MHZ扫频测试典型性能指标值•带宽:300MHz•标准:符合TIA/EIA 568B.2-1,ISO/IEC 11801B.2-1等技术指标要求。
•中间带十字架;•护套材料:防火聚氯乙烯(PVC)•导体直径:23AWG•护套直径:6.4mm;•防火等级:CMR,符合UL 444,UL认证文件编号E138034•特性阻抗:100Ω±15Ω;1 MHz to 300 MHz•传输延迟: 最大535 ns/100 m. @ 300 MHz•延迟偏差: 最大45 ns•第三方认证:中国信息产业部通信产品质量监督检验中心认证,国家电线电缆质量监督检验中心,ETL认证•材料:符合ROHS指令(4)Cat.6非屏蔽信息插座规格(1375055-X)•支持T568A和T568任意安装方式•支持1000Base-T/TX,1.2Gbps ATM的应用,•电气性能完全满足TIA/EIA568-B.2-1 Category 6和ISO/IEC Category 6/Class E 性能要求;•保护装置:插座后面带线缆保护套•RJ-45插座接触针:8根接触针相互交叉•110端子:45度斜角,支持导体直径在22-24AWG之间的实心导线或者24-26AWG之间的多股软线•耐久性: RJ-45插座:至少750次插接 110端子:至少200次打接•最大电压:150VAC•工作温度:-40—70ºC•安装: 安装工具一次端接八根线。
温湿度模块AM2011产品手册说明书

温湿度模块AM2011产品手册更多详情请登陆:一、产品概述AM2011是湿敏电容型温湿度传感器,传感器信号采用模拟电压输出方式;本模块具有精度高,可靠性高,一致性好,且带有温度补偿,确保长期稳定性好,使用方便及价格低廉等特点,尤其适合对质量、成本要求比较苛刻的企业使用。
二、应用范围暖通空调、加湿器、除湿机、通迅、大气环境监测、工业过程控制、农业、测量仪表等应用领域。
三、产品亮点低功耗,小体积、带温度补偿、单片机校准线性输出、使用方便、成本低、完全互换、超长的信号传输距离、精确校准。
四、产品尺寸图(公差:±0.5mm)图1外形尺寸(单位:mm)五、接口定义5.1 引脚分配表1:引脚分配5.2 电源引脚(VDD GND)该模块的供电电压为4.2V ~5.5V,建议供电电压为5.0V。
5.3 电压输出信号线(Hout)湿度信号从该信号线以电压的形式输出,电压输出范围为0-3V,具体湿度与电压关系请参照电压与湿度特性表(表5)。
5.4 温度输出信号线(Tout)温度传感器为10K NTC B.3435热敏电阻而非模拟信号输出,用户需另加读取电路,测温范围为-40~80。
℃5.5 温度传感器接线方式示意图图3:温度接线方式示意图图2:引脚分配图六、传感器性能6.1相对湿度表2:相对湿度性能表6.2相对湿度最大误差(25℃)图4:25℃时相对湿度最大误差6.3温度温度传感器是NTC 10K 热敏电阻温度传感器参数如表3所示。
表3:10K NTC B.3435技术参数[1]此精度为出厂时检验时,传感器在25℃和5V ,条件下测试的精度指标,其不包括迟滞和非线性,且只适合非冷凝环境。
[2]在25℃和1m/s 气流的条件下,达到一阶响应63%所需要的时间。
[3]在挥发性有机混合物中数值可能会高一些。
七、电气特性电气特性,如能耗,输入、输出电压等,都取决于电源。
表4详细说明了该传感器的电气特性,若没有标明,则表示供电电压为5V。
[精彩]安普线夹应用说明
![[精彩]安普线夹应用说明](https://img.taocdn.com/s3/m/d087ccce3086bceb19e8b8f67c1cfad6195fe90a.png)
产品简介安普楔形线夹是一种用于配电系统的非承力型连接金具,用于铝绞线或钢芯铝绞线间的连接,铝绞线与铜绞线间的连接,以及在非严重污染地区的铜绞线间的连接。
安普楔形线夹由“C”形元件和楔块两部分组成“C”形元件弹簧作用和楔块的独特结构使之一改过去金具与导线的连接概念,而与所连接的导线共同构成一个“同呼吸”的能量存储系统。
采用安普先进的设计思想和生产工艺的楔形线夹大大地提高了线夹的过载能力和热循环能力,有效地降低了能量损耗,使由于线夹接触不良而引起的线路故障率降低到“0”。
为了配合所连接导线的不同直径,安普楔形线夹的安装配有不同的弹射芯,从而使线夹的安装力得到精确地控制,且完全免除了线夹安装中人为因素的影响。
线夹与导线接触的各线槽内均涂有抗氧剂,它不但能有效地防止导线和线夹的接触面因氧化或其它腐蚀而造成的表面劣化,并且其中所含的金属微粒子在安装时,楔块高速插入“C”形元件上的过程中,能有效地清除导线表面氧化层,从而使电气接触性能更好。
安装步骤1固定线夹将待连接的支线放在C元件的底部线槽,然后将C元件和支线一起挂在主线上。
在两导线间塞入楔块,然后用榔头将楔块定位,以确保正式安装前线夹定在原位。
2固定工具根据线夹的不同包装,选择合适的弹射芯并装入安装工具。
把工具在楔块上夹好定位,旋紧后盖及排气旋钮。
3安装线夹用榔头(最好500克以上)重击工具尾部一次以激发弹射芯,使楔块以高速插入C元件的主导线和支线之间。
这时C元件会略微张开,产生弹簧作用并使之与导线间产生恒定接触压力。
当楔块就位以后,楔块安装时所产生的锁扣能进一步确保楔块不脱落。
根据不同的安装线夹,选择不同的安普拆卸夹装在工具上,同时选用比安装所用的弹射芯弱一档的弹射芯来拆卸。
线夹的拆卸不会损伤导线。
注意事项:1)安装工具应在每一次使用后进行清洁,以免锈蚀2)弹射芯长期储存,应保持干燥环境,以防失效3)不同颜色的弹射芯在线夹安装时不能互换,以免损坏工具4)如安装工具失灵,请通知安普专业人员进行维修安普拆卸夹(在拆卸线夹时与安装工具配合使用)带电作业棒的四个简易操作步骤:1)支线以“临时固定线夹”暂固定。
安普产品技术说明

安普产品技术说明北京汇通融业科技发展有限公司安普产品技术说明一、 AMP布线系统的特点AMP布线系统以其系统完善性和制造工艺的精确性而著称于世。
它有以下几个特点:➢系统的完善性AMP开放式布线系统可以为用户提供的系统有AMP 110结构化布线系统(屏蔽与非屏蔽),AMP ACO开放式布线系统(屏蔽与非屏蔽),AMP光纤布线系统和AMP地毯下布线系统。
➢完善的产品线AMP布线产品包括六类非屏蔽/屏蔽双绞线综合布线系统、6类非屏蔽/屏蔽布线系统、MT-RJ光纤布线系统、XG Fiber 10G光纤、AMPTRAC智能布线系统、AMP标签打印软件等。
➢及时的供货期安普在国内拥有大规模的产品独资生产厂,以生产安普常规产品,同时安普在上海外高桥保税区设有大规模物流仓库,负责安普整个亚太区的货物储备、运输等物流,因此可以满足国内大项目及时的大规模供货。
➢制造工艺的精确性AMP公司作为连接器行业的领导者,开发了大量连接器的先进技术和专利,同时将这些先进技术应用于AMP NETCONNECT 综合布线的系统,所以AMP开放式布线系统特别强调管理子系统及信息墙座接口的制造工艺,因为不管是计算机网络还是话音系统或楼宇自控系统,其物理故障90%以发生在布线系统的连接部位。
AMP布线系统所有连接触部分都镀金或镀铂,非接触部分镀镍。
在结构设计时做到接触配合公差最小。
➢管理组件的美观实用性AMP的管理组件充分考虑到了实用与美观的结合,其水平跳线管理架全部采用带盖的方式,使得安装后的配线机柜更整齐美观。
AMP 布线产品从1993年正式开始进入中国市场以来取得了辉煌的业绩,销量增长了300多倍,用户遍布全国各行各业,AMP产品价廉物美的特征深入人心。
二、 AMP布线系统遵循的标准和规范1.ISO/IEC 11801-2002《建筑物通用布线标准2002》2.EIA/TIA 568B《商业建筑物通用布线标准》3.EIA/TIA 569 《商业建筑物通信布线线槽和空间标准》4.EIA/TIA-606《商业建筑物通信基础结构管理标准》5.EIA/TIA-607《商业建筑物布线连接和接地标准》6.TIA/EIA TSB67《非屏蔽双绞线传输性能现场测试规范》7.TIA/EIA TSB95《100 欧姆 4 对 5 类非屏蔽双绞线附加传输性能规范》8.ANSI/TIA/EIA568-B.2-1《100 欧姆 6 类非屏蔽双绞线传输性能规范》9.EIA/TIA TSB-72 标准集中式光纤布线系统标准10.EIA/TIA TSB-75标准开放办公室布线系统标准11.ISO/IEC 11801 国际综合布线六类信道标准12.EN50173 欧洲大楼综合布线系统标准13.EMC 欧洲电磁兼容性标准14.ANSI FDDI 美国国家标准:分布式光纤数据接口15.IEEE 802.3ae 国际电子电气工程师协会16.IEEE 802.5国际电子电气工程师协会国内标准和规范有:17.CECS 72:97 《建筑与建筑群综合布线系统设计规范》18.CECS 72:97 《建筑与建筑群综合布线系统施工及验收规范》19.YD/T 926.1-2001《大楼综合布线系统总规范》20.YD/T 926.2-2001《综合布线用电缆、光缆技术要求》21.YD/T 926.3-2001《综合布线用连接硬件技术要求》22.GB/T 50311-2000 建筑与建筑群综合布线系统工程设计规范23.GB/T 50312-2000 建筑与建筑群综合布线系统工程施工与验收规范24.GB/T 50314--2000 智能建筑设计标准25.GBT16-87建筑设计防火规范26.GBJ08-47-95智能建筑设计规范27.JGJ/T16-92民用建筑设计规范28.YD/926.2-2000大楼通信综合布线系统标准安普所有综合布线产品均通过UL和ETL国际认证。
思科AMP安装和最佳实践指南说明书

Enabling AMP on ContentSecurity Products (ESA/WSA)January 2017Version 2.2Bill Yazji****************C O N T E N T S E C U R I T Y–A M P B E S T P R A C T I C E SOverview:The vast majority of threats, attacks and nuisances faced by an organization often come through email in the form of spam, malware and blended attacks, as well as via normal every day web browsing.Cisco’s Email Security Appliances and Web Security Appliances include several different technologies and features to cut these threats off at the gateway, before they enter the organization, and this document will describe the best practice approaches to configuring our Advanced Malware Protection (AMP) feature.Advanced Malware Protection – AMP is provided to detect and act upon known, unknown, zero day or targeted attacks. – including a File Reputation SHA lookup, automated cloud sandboxing of files, and retrospective alerting and detection of changes in the threat level of a file after it has left the email chain, or after the file is downloaded to the end user’s workstation. The File Reputation and File Analysis Criteria for AMP for Cisco Content Security Products can be found here.This guide covers configuration and best practices on both the ESA and WSA products, along with general tips towards the end of the document.C O N F I G U R I N G A M P O N E M A I L S E C U R I T Y A P P L I A N C E(E S A) Email Security Appliance (ESA) Code Requirements:∙Minimum ESA Version 9.7.2-065∙Current Recommendation v10.0.0-203Security Management Appliance (SMA) Code Requirements:∙Minimum SMA Version 10.0.0-055∙Current Recommendation v10.0.0-096While AMP has been supported on ESA on releases since v8.5.5, there has been significant reporting and functionality enhancements since the original release. Customers are strongly recommended to follow the above recommendations for an optimal experience.When using a SMA for centralized reporting and message tracking, ensure the appropriately paired SMA release for the ESA release. You may reference the compatibility matrix here. Confirming Advanced Malware Protection (AMP) LicensingConfirm you have the appropriate licensing by navigating to System Administration > Feature Keys. You will need to have the File Reputation and File Analysis Keys listed and Active.Configuring Advanced Malware Protection (AMP)Once the keys are confirmed, navigate to Security Services > File Reputation and AnalysisUnder “Advanced Malware Protection,” click “Edit the Global Settings”You will want to Enable File Reputation, and Enable File Analysis. Cisco recommends enabling file analysis for all File Types.By default, File Reputation communicates on port tcp/32137. As many customer environments do not have this port open, it may be required check the “Use SSL” checkbox under Advanced Settings for File Reputation.This will ensure communication over tcp/443, which is more commonly permitted. Additionally, you can configure the File Reputation query over a proxy in this same configuration area.The final configuration item would be to ensure all of the ESA devices are configured with the same Reporting Group ID. This permits a SMA to review all the File Analysis reports for all of the ESA’s sending files for File Analysis. Without this, you can only access the File Analysis reports via the ESA that submitted the file.It is recommended to use something like COMPANYNAME-AMP. Despite the value recommendation below of a CCO ID, this is not an optimal item to use. If your organization already utilizes Threat Grid, and have access to use , the naming should be based on the Organization name from . This is found from looking at the User > My Account option on the Threat Grid portal. It is critical that every ESA has the same value in this space and that this matches what is configured on the SMA.In the event your organization has purchased a full ThreatGRID subscription, you are able to tie the samples from your ESA/SMA to this account. This can be achieved by opening a case with ThreatGRIDsupport(**********************)andprovidingtheDeviceIDsandSerialNumbers (or VLN) of your ESA/SMA architecture. More information can be found here. Please take note to understand that if using a virtual ESA (ESAv), that the VLN is part of the ID used for the integration with the full ThreatGRID subscription. If the VLN license file changes and the VLN changes, this needs to be updated with ThreatGRID support.Configuration on ESA: Security Services > File Reputation and Analysis. Note: It is critical to do this configuration at the machine level, not the cluster level.Configuration on SMA: Management Appliance > Centralized Services > Security AppliancesOnce the above items are completed. Click Submit at the bottom of the screen, then Commit the changes.The AMP configuration is now complete on the Email Security Appliance. Now, we must enable AMP services for the Incoming Mail flow. Note that AMP is not available for Outgoing Mail Policies.Navigate to Mail Policies > Incoming Mail Policies. For the Incoming Mail Policy, the following settings are recommended.Incoming emails with a file attachment will be first checked with the File Reputation Services of AMP. The SHA256 hash for the file is queried to the AMP cloud. If the file is known “malicious”– the configuration section “Messages with Malware Attachments” [above] will be followed. The configuration above will have any email with a known malware attachment dropped.In the event the File Reputation services determines the file is ‘unknown file,’the ESA will determine of the file is a supported file type for File Analysis. Keep in mind that while File Reputation supports most file types for SHA lookup, File Analysis has a smaller subset of supported file types. If the file is a supported file type for File Analysis, and if the pre-classification engine onthe ESA determines the file is one that could have malicious content, that file is sent to the cloud for File Analysis, and the configuration under “Messages with File Analysis Pending” [above] will be followed. The configuration above will have emails with files Pending Analysis be Quarantined based on the quarantine settings.File Analysis quarantine settings are configured under:Monitor > Policy, Virus and Outbreak Quarantines if on an ESA, and when using centralized quarantines on an SMA, under the Email Tab, then Message Quarantine > Policy, Virus and Outbreak Quarantines. Configuration of the File Analysis Quarantine is the same on either an ESA or SMA.Click on the “File Analysis” Quarantine.Cisco’s default Retention period is 1 hour, with a minimum recommended value of 30 minutes. Configuration is not recommended any shorter than 30 minutes. Once this time has expired, the Default Action will take please – either Delete or Release. The recommendation here is Release. If a customer chooses Delete, it is strongly recommended to have a longer Retention period.Configuring AMP on Web Security Appliance (WSA)Web Security Appliance Code Requirements:∙Minimum WSA Version v9.1.1-074∙Current Recommendation v9.1.1-074Security Management Appliance (SMA) Code Requirements:∙Minimum SMA Version 10.0.0-055∙Current Recommendation v10.0.0-096While AMP has been supported on WSA on releases since v8.0.5, there has been considerable reporting and functionality enhancements since the original release. Customersare strongly recommended to follow the above recommendations for an optimal experience. When using a SMA for centralized reporting and message tracking, ensure the appropriately paired SMA release for the WSA release. You may reference the compatibility matrix here.Confirming Advanced Malware Protection (AMP) LicensingConfirm you have the appropriate licensing by navigating to System Administration > Feature Keys. You will need to have the File Reputation and File Analysis Keys listed and Active.Configuring Advanced Malware Protection (AMP)Next, navigate to Security Services > Anti-Malware and Reputation in order to configure AMP. Under “Advanced Malware Protection,” click “Edit the Global Settings”You will want to Enable File Reputation, and Enable File Analysis. Cisco recommends enabling file analysis for all File Types.By default, File Reputation communicates on port tcp/32137. As many customer environments do not have this port open, it may be required to check the “Use SSL”checkbox under AdvancedSettings for File Reputation. This will ensure communication over tcp/443, which is more commonly permitted. Additionally, you can configure the File Reputation query over a proxy in this same configuration area.The final configuration item would be to ensure all of the WSA appliances are configured with the same Reporting Group ID. This permits a SMA to review all the File Analysis reports for all of the WSA’s sending files for File Analysis. Without this, you can only access the File Analysis reports via the WSA that submitted the file.It is recommended to use something like COMPANYNAME-AMP. Despite the value recommendation below of a CCO ID, this is not an optimal item to use. If your organization already utilizes Threat Grid, and have access to use , the naming should be based on the Organization name from . This is found from looking at the User > My Account option on the Threat Grid portal. It is critical that every WSA has the same value in this space and that this matches what is configured on the SMA.In the event your organization has purchased a full ThreatGRID subscription, you are able to tie the samples from your WSA/SMA to this account. This can be achieved by opening a case with ThreatGRIDsupport(**********************)andprovidingtheDeviceIDsandSerialNumbers (or VLN) of your WSA/SMA architecture. More information can be found here. Please take note to understand that if using a virtual WSA (WSAv), that the VLN is part of the ID used for the integration with the full ThreatGRID subscription. If the VLN license file changes and the VLN changes, this needs to be updated with ThreatGRID support.Configuration on WSA: Security Services > File Reputation and Analysis Configuration on SMA: Management Appliance > Centralized Services > Security AppliancesOnce the above items are completed. Click Submit at the bottom of the screen, then Commit the changes.You have successfully enabled the AMP services on the Web Security Appliance. Now, you must enable AMP services in the Access Policies. This configuration is quite simple.Under Web Security Manager > Access Policies you will need to configure Advanced Malware Protection under the Anti-Malware and Reputation Column. Click on the blue “Advanced Malware Protection”Once in the configuration, under “Advanced Malware Protection Settings” check the box to enable the “File Reputation and File Analysis” and configure the appliance to either Monitor or Block Known Malicious and High-Risk Files. Cisco recommends to Block these.Downloaded files will be first checked with the File Reputation Services of AMP. The SHA256 hash for the file is queried to the AMP cloud. If the file is known “malicious”– the configuration section “Known Malicious and High-Risk Files” [above] will be followed. The configuration above will have any file with a known malware blocked from transfer to the end client.In the event the File Reputation services determines the file is ‘unknown file,’ it will be passed to the end user. The WSA will determine of the file is a supported file type for File Analysis. Keep in mind that while File Reputation supports most file types for SHA lookup, File Analysis has a smaller subset of supported file types. The File Retrospection functionality will alert the administrator to any file that completes File Analysis with a “malicious” verdict. A report on the WSA (or SMA) will show what users downloaded these files for manual remediation.Timing of Processes and Verdict Updates∙There is no Service Level Agreement for timing of AMP processes, all information here is best-effort based on current processing∙The File Analysis process can take between 10 minutes to 1 hour (estimated, with average being on the lower end). When File Analysis is complete, the updated disposition will be pushed to the AMP cloud∙After a verdict is updated in the cloud, it currently takes approximate an hour for the retrospective verdict to be reflected on your content security appliance.∙The ESA & SMA File Analysis Quarantine checks for File Analysis Completion every 5 minutes, upon updated verdict it will release/block the email per the quarantine configuration.∙The WSA & ESA File Retrospection process checks the AMP Cloud every 15 minutes for updated file disposition∙The WSA & ESA cache file dispositions and update via retrospective events. The cache lives forever unless we need to empty the space, in that event the least recently used are cleared.AMP INSTALLATION AND BEST PRACTICES11 2016 Cisco and/or its affiliates. All rights reserved. This document is Customer facing.。
泰科电子安普布线AMP(全文)

泰科电子安普布线AMP(全文)目前数据中心面临的显著问题就是耗电量较大,同时数据中心产生的电子垃圾不能及时地回收再利用,服务器的使用效率没有达到最佳。
因此,“绿色环保的数据中心”将成为数据中心的发展方向。
安普布线数据中心系列产品针对数据中心要求,是高密度、高灵活性,以及节能环保的布线产品。
针对企业级数据中心区别于普通商业建筑的一些特殊或更严格的需求,泰科电子安普布线将电路板连接技术用在结构化布线的应用中,设计和开发了一系列专为数据中心布线而设计的解决方案――专利技术的高密度铜缆MRJ21双绞线布线系统、高密度的光纤MPO布线系统,以及数据中心线缆管理Hi-D解决方案。
泰科电子在减少系统停机时间和设备空间以及布线管理等方面提供了非常好的数据中心解决方案。
它不但节省机柜、管道的空间,也能提升整个数据中心布线的密度和布线的安装效率。
预端接的主干电缆、模块化的耦合器插盒以及集中的连接电缆提供了简单的即插即用的安装,同时减少了数据中心迁移过程中电缆的浪费,更加环保。
高密度连接器在很小的空间提供更多的端口,高可靠性提供真实的数据传输。
结合安普布线AMPTRAC智能布线管理系统,安普布线数据中心的铜缆和光纤系统解决方案提供了一个智能的布线网络监测系统,实时地跟踪布线系统和连接器件并减少网络中断时间。
同时,安普布线还为数据中心布线提供高密度的线缆管理系统。
系统具有高密度、美观整洁、方便散热等等特点,支持水平和垂直两种管理方式,为数据中心有序、整齐的线缆管理提供可靠的解决方案。
安普布线MPO高密度光纤连接系统,可以快速方便地安装高效数据中心和存储区域网络。
顶端接光缆组件和接线盒的结合使安装易如反掌。
在机架或墙壁安装的机箱中安装接线盒,拉好或布好干线光缆,然后把MPO连接器插入接线盒中。
网络在几分钟内就可搭好并运转,而不是数小时、数周或数月时间,不需要工具箱,没有消耗件,没有现场端接,不需要培训,而且使总开支达到最低。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
序号产品型号编号单位产品描述
AMP 六类非屏蔽
1六类4对非屏蔽双绞电缆1427254-6箱蓝色,305米/箱,防火等级CM
2六类4对非屏蔽双绞电缆9-1427200-6箱蓝色,305米/箱,防火等级CMR
3六类4对非屏蔽双绞电缆219585-2箱白色,305米/箱,防火等级LSZH
4六类4对非屏蔽信息模块8-1375055-x个1=浅杏黄色 -3=白色 -5=橙色 -7=红色 -8=黄色 -9=绿色 SL免工具5六类非屏蔽24口配线架1375014-2个高度1U,平面型,非屏蔽
6六类非屏蔽48口配线架1375015-2个高度2U,平面型,非屏蔽
7六类非屏24口蔽角型配线架1499600-2个高度1U,角型,非屏蔽
8六类非屏蔽跳线(4FT)1859246-4条灰色,防火等级CM
9六类非屏蔽跳线(7FT)1859246-7条灰色,防火等级CM
10六类非屏蔽跳线(10FT)1859246-1-0条灰色,防火等级CM
AMP 六类屏蔽
1六类屏蔽双绞线1859204-6箱蓝色,305/轴,250MHZ,防火等级CM
2六类屏蔽双绞线1427213-1箱白色,305/轴,250MHZ,防火等级LSZH
3六A类屏蔽双绞线1859222-2箱白色,305/轴,250MHZ,防火等级CM
4六A类屏蔽双绞线1859218-2箱白色,305/轴,250MHZ,防火等级LSZH
5六A类屏蔽24口配线架1933319-2个高度1U,平面型,屏蔽
6六A类屏蔽24口角型配线架1933321-2个高度1U,角型,屏蔽
7屏蔽24口平面型配线空架1933307-1个高度1U,平面型,屏蔽
8屏蔽24口角型配线空架1933309-1个高度1U,角型,屏蔽
9六类屏蔽信息模块1479552-1个六类SL型屏蔽模块,从侧面90°进线
10六类屏蔽信息模块8-1375188-1个六类SL型屏蔽模块,从后面180°进线
11六A类屏蔽信息模块1711160-2个六类SL型屏蔽模块,从后部入线,带防尘盖
12六A类屏蔽信息模块1711342-2个六类SL型屏蔽模块,从后部入线,不带防尘盖
13六类屏蔽跳线(1米)1427226-5条灰色1859300,粉红色1859293,防火等级CM
14六类屏蔽跳线(2米)1427226-6条灰色1859300,粉红色1859293,防火等级CM
15六类屏蔽跳线(3米)1427226-7条灰色1859300,粉红色1859293,防火等级CM
16六类屏蔽跳线(5米)1427226-8条灰色1859300,粉红色1859293,防火等级CM
AMP超五类非屏蔽。
