ccna1_8测试真题
CCNA中文版试题

CCNA认证试题一(附答案和解析)中文版(一)1、目前,我国应用最为广泛的LAN标准是基于()的以太网标准.(A) IEEE 802.1 (B) IEEE 802.2 (C) IEEE 802.3 (D) IEEE 802.5答案:C 现有标准:IEEE 802.1 局域网协议高层;IEEE 802.2 逻辑链路控制;IEEE 802.3 以太网IEEE 802.4 令牌总线;IEEE 802.5 令牌环IEEE 802.8 FDDIIEEE 802.11 无线局域网;记住IEEE802.1-------IEEE802.5的定义以太网是一种计算机局域网组网技术。
IEEE制定的IEEE 802.3标准给出了以太网的技术标准。
它规定了包括物理层的连线、电信号和介质访问层协议的内容。
以太网是当前应用最普遍的局域网技术。
它很大程度上取代了其他局域网标准,如令牌环、FDDI和ARCNET。
以太网的标准拓扑结构为总线型拓扑,但目前的快速以太网(100BASE-T、1000BASE-T标准)为了最大程度的减少冲突,最大程度的提高网络速度和使用效率,使用交换机(Switch)来进行网络连接和组织,这样,以太网的拓扑结构就成了星型,但在逻辑上,以太网仍然使用总线型拓扑的C***A/CD介质访问控制方法。
电气电子工程师协会或IEEE(Institute of Electrical and Electronics Engineers)是一个国际性的电子技术与信息科学工程师的协会。
建会于1963年1月1日。
总部在美国纽约市。
在150多个国家中它拥有300多个地方分会。
目前会员数是36万。
专业上它有35个专业学会和两个联合会。
IEEE发表多种杂志,学报,书籍和每年组织300多次专业会议。
IEEE定义的标准在工业界有极大的影响。
下面列出:IEEE802.3以太网标准802.3--------- 10Base以太网标准; 802.3u-------- 100Base-T(快速以太网)802.3z-------- 1000Base-X(光纤吉比特以太网)802.3ab-------- 1000Base-T(双绞线吉比特以太网)2、对于这样一个地址,192.168.19.255/20,下列说法正确的是: ()(A) 这是一个广播地址(B) 这是一个网络地址(C) 这是一个私有地址(D) 地址在192.168.19.0网段上(E) 地址在192.168.16.0网段上(F) 这是一个公有地址答案:CE注:IP地址中关键是看她的主机位,将子网掩码划为二进制,1对应上面的地址是网络位,0对应的地址是主机位192.168.19.255/20划为二进制为:11000000.10101000.00010011.1111111111111111.11111111.11110000.00000000主机位变成全0表示这个IP的网络地址主机槐涑扇?表示这个IP的广播地址RFC1918文件规定了保留作为局域网使用的私有地址:10.0.0.0 - 10.255.255.255 (10/8 prefix)172.16.0.0 - 172.31.255.255 (172.16/12 prefix)192.168.0.0 - 192.168.255.255 (192.168/16 prefix)3、Quidway系列路由器在执行数据包转发时,下列哪些项没有发生变化(假定没有使用地址转换技术)?()(A) 源端口号(B) 目的端口号(C) 源网络地址(D) 目的网络地址(E) 源MAC地址(F) 目的MAC地址答案:ABCD路由功能就是指选择一条从源网络到目的网络的路径,并进行数据包的转发。
Cisco CCNA 认证考试最新真题

Cisco CCNA 认证考试最新真题体验1. The command frame-relay map ip 10.121.16.8 102 broadcast was entered on the router. Which of the following statements is true concerning this command?A.This command should be executed from the global configuration mode.B.The IP address 10.121.16.8 is the local router port used to forward data.C.102 is the remote DLCI that will receive the information.D.The broadcast option allows packets, such as RIP updates, to be forwarded across the PVC2. While troubleshooting a network connectivity problem, a technician observes steady link lights on both the workstation NIC and the switch port to which the workstation is connected. However, when the ping command is issued from the workstation, the output message "Request timed out." is displayed. At which layer of the OSI model does the problem most likely exist?A.the session layerB.the network layerC.the data link layerD.the access layer3. In order to allow the establishment of a Telnet session with a router, which set of commands must be configured?A.router(config)# line console 0router(config-line)# enable password ciscoB.router(config)# line console 0router(config-line)# enable secret ciscorouter(config-line)# loginC.router(config)# line console 0router(config-line)# password ciscorouter(config-line)# loginD.router(config)# line vty 0router(config-line)# password cisco router(config-line)# login4. On point-to-point networks, OSPF hello packets are addressed to which address?A.127.0.0.1B.192.168.0.5C.224.0.0.5D.254.255.255.2555. What should be part of a comprehensive network security plan?A.Allow users to develop their own approach to network security.B.Physically secure network equipment from potential access by unauthorized individualsC.Encourage users to use personal information in their passwords to minimize the likelihood of passwords being forgottenD.Delay deployment of software patches and updates until their effect on end-user equipment is well known and widely reported6. During startup, the router displays the following error message:boot: cannot open "flash:" What will the router do next?A.Because of damaged flash memory, the router will fail the POST.B.It will attempt to locate the IOS from a TFTP server. If this fails, it will initiate the setup dialogC.It will attempt to locate the IOS from a TFTP server. If this fails, it will load a limited IOS from ROM.D.It will attempt to locate the configuration file from a TFTP server. If this fails, it will initiate the setup dialog7. At which OSI layer is a logical path created between two host systems?A.sessionB.transportworkD.physical8. A routing protocol is required that supports:1) routing update authentication2) an addressing scheme that conserves IP addresses3) multiple vendors4) a network with over 50 routersWhich routing protocol fulfills these requirements?A.RIPv1B.RIPv2C.EIGRPD.OSPF9. When a new trunk is configured on a 2950 switch, which VLANs by default are allowed over the trunk link?A.no VLANsB.all VLANsC.only VLANs 1 - 6D.only the VLANs that are specified when creating the trunk10. Which protocol provides a method of sharing VLAN configuration information between switches?A.VTPB.STPC.ISLD.802.1QDBDCB CCDBA博主的更多文章>>CCNA第一学期《Final Examination》2009-02-27 08:58:47 标签:CCNA[推送到技术圈]1请参见图示。
思科CCNA1第八章试题及答案英文版

1. 1. QuestionWhat is a result of connecting two or more switches together?o The number of broadcast domains is increased.o The size of the broadcast domain is increased.o The number of collision domains is reduced.o The size of the collision domain is increased.2. 2. QuestionRefer to the exhibit. How many broadcast domains are there?CCNA1 v6.0 Chapter 8 Exam 005o 1o 2o 3o43. 3. QuestionWhat are two reasons a network administrator might want to create subnets?(Choose two.)o simplifies network designo improves network performanceo easier to implement security policieso reduction in number of routers neededo reduction in number of switches needed4. 4. QuestionRefer to the exhibit. A company uses the address block of 128.107.0.0/16 for its network. What subnet mask would provide the maximum number of equal size subnets while providing enough host addresses for each subnet in the exhibit?CCNA1 v6.0 Chapter 8 Exam 007o 255.255.255.0o 255.255.255.128o 255.255.255.192o 255.255.255.224o 255.255.255.2405. 5. QuestionRefer to the exhibit. The network administrator has assigned the LAN of LBMISS an address range of 192.168.10.0. This address range has beensubnetted using a /29 prefix. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the newnetwork (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the properties of the workgroup server to allow connectivity to the Internet?CCNA1 v6.0 Chapter 8 Exam 004o IP address: 192.168.10.65 subnet mask: 255.255.255.240, default gateway: 192.168.10.76o IP address: 192.168.10.38 subnet mask: 255.255.255.240, default gateway: 192.168.10.33o IP address: 192.168.10.38 subnet mask: 255.255.255.248, default gateway: 192.168.10.33o IP address: 192.168.10.41 subnet mask: 255.255.255.248, default gateway: 192.168.10.46o IP address: 192.168.10.254 subnet mask: 255.255.255.0, defaultgateway: 192.168.10.16. 6. QuestionIf a network device has a mask of /28, how many IP addresses are available for hosts on this network?o 256o 254o 62o 32o 16o 147. 7. QuestionWhich subnet mask would be used if 5 host bits are available?o 255.255.255.0o 255.255.255.128o 255.255.255.224o 255.255.255.2408. 8. QuestionHow many host addresses are available on the network 172.16.128.0 with a subnet mask of 255.255.252.0?o 510o 512o1022o 1024o 2046o 20489. 9. QuestionHow many bits must be borrowed from the host portion of an address to accommodate a router with five connected networks?o twoo threeo fouro five10. 10. QuestionA network administrator wants to have the same network mask for allnetworks at a particular small site. The site has the following networks and number of devices:IP phones – 22 addressesPCs – 20 addresses neededPrinters – 2 addresses neededScanners – 2 addresses neededThe network administrator has deemed that 192.168.10.0/24 is to be the network used at this site. Which single subnet mask would make the most efficient use of the available addresses to use for the four subnetworks?o 255.255.255.0o 255.255.255.192o 255.255.255.224o 255.255.255.240o 255.255.255.248o 255.255.255.25211. 11. QuestionA company has a network address of 192.168.1.64 with a subnet mask of255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks wouldachieve that? (Choose two.)o 192.168.1.16/28o 192.168.1.64/27o 192.168.1.128/27o 192.168.1.96/28o 192.168.1.192/2812. 12. QuestionA network administrator is variably subnetting a network. The smallestsubnet has a mask of 255.255.255.248. How many usable host addresses will this subnet provide?o 4o 6o 8o 10o 1213. 13. QuestionRefer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224 for all subnets, how many total host addresses are unused in the assigned subnets?CCNA1 v6.0 Chapter 8 Exam 001o 56o 60o 64o 68o7214. 14. QuestionRefer to the exhibit. Considering the addresses already used and having to remain within the 10.16.10.0/24 network range, which subnet address could be assigned to the network containing 25 hosts?CCNA1 v6.0 Chapter 8 Exam 002o 10.16.10.160/26o 10.16.10.128/28o 10.16.10.64/27o 10.16.10.224/26o 10.16.10.240/27o 10.16.10.240/2815. 15. QuestionA network administrator needs to monitor network traffic to and fromservers in a data center. Which features of an IP addressing scheme should be applied to these devices?o random static addresses to improve securityo addresses from different subnets for redundancyo predictable static IP addresses for easier identificationo dynamic addresses to reduce the probability of duplicate addresses 16. 16. QuestionWhich two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)o It eliminates most address configuration errors.o It ensures that addresses are only applied to devices that require apermanent address.o It guarantees that every device that needs an address will get one.o It provides an address only to devices that are authorized to be connected to the network.o It reduces the burden on network support staff.17. 17. QuestionA DHCP server is used to assign IP addresses dynamically to the hosts on anetwork. The address pool is configured with 192.168.10.0/24. There are 3 printers on this network that need to use reserved static IP addresses from the pool. How many IP addresses in the pool are left to be assigned to other hosts?o 254o251o 252o 25318. 18. QuestionRefer to the exhibit. A company is deploying an IPv6 addressing scheme for its network. The company design document indicates that the subnet portion of the IPv6 addresses is used for the new hierarchical network design, with the s ite subsection to represent multiple geographical sites of the company, the s ub-site section to represent multiple campuses at each site, and thes ubnet section to indicate each network segment separated by routers. With such a scheme, what is the maximum number of subnets achievedper sub-site?CCNA1 v6.0 Chapter 8 Exam 003o 0o 4o16o 25619. 19. QuestionWhat is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?o 2001:DB8:BC15o 2001:DB8:BC15:Ao 2001:DB8:BC15:A:1o 2001:DB8:BC15:A:1220. 20. QuestionConsider the following range of addresses:2001:0DB8:BC15:00A0:0000::2001:0DB8:BC15:00A1:0000::2001:0DB8:BC15:00A2:0000::…2001:0DB8:BC15:00AF:0000::The prefix-length for the range of addresses is /6021. 21. QuestionMatch the subnetwork to a host address that would be included within the subnetwork. (Not all options are used.)CCNA1 v6.0 Chapter 8 Exam 0122. 22. QuestionRefer to the exhibit. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network. (Not all options are used.)CCNA1 v6.0 Chapter 8 Exam 006。
CCNA认证精彩试题中文+问题详解

CCNA认证试题一(附答案和解析)中文版(一)1、目前,我国应用最为广泛的LAN标准是基于()的以太网标准.(A) IEEE 802.1(B) IEEE 802.2(C) IEEE 802.3(D) IEEE 802.5答案:C参考知识点:现有标准:IEEE 802.1 局域网协议高层IEEE 802.2 逻辑链路控制IEEE 802.3 以太网IEEE 802.4 令牌总线IEEE 802.5 令牌环IEEE 802.8 FDDIIEEE 802.11 无线局域网记住IEEE802.1-------IEEE802.5的定义以太网是一种计算机局域网组网技术。
IEEE制定的IEEE 802.3标准给出了以太网的技术标准。
它规定了包括物理层的连线、电信号和介质访问层协议的内容。
以太网是当前应用最普遍的局域网技术。
它很大程度上取代了其他局域网标准,如令牌环、FDDI和ARCNET。
以太网的标准拓扑结构为总线型拓扑,但目前的快速以太网(100BASE-T、1000BASE-T标准)为了最大程度的减少冲突,最大程度的提高网络速度和使用效率,使用交换机(Switch)来进行网络连接和组织,这样,以太网的拓扑结构就成了星型,但在逻辑上,以太网仍然使用总线型拓扑的C***A/CD介质访问控制方法。
电气电子工程师协会或IEEE(Institute of Electrical and Electronics Engineers)是一个国际性的电子技术与信息科学工程师的协会。
建会于1963年1月1日。
总部在美国纽约市。
在150多个国家中它拥有300多个地方分会。
目前会员数是36万。
专业上它有35个专业学会和两个联合会。
IEEE发表多种杂志,学报,书籍和每年组织300多次专业会议。
IEEE定义的标准在工业界有极大的影响。
下面列出:IEEE802.3以太网标准802.3--------- 10Base以太网标准802.3u-------- 100Base-T(快速以太网)802.3z-------- 1000Base-X(光纤吉比特以太网)802.3ab-------- 1000Base-T(双绞线吉比特以太网)2、对于这样一个地址,192.168.19.255/20,下列说法正确的是: ()(A) 这是一个广播地址(B) 这是一个网络地址(C) 这是一个私有地址(D) 地址在192.168.19.0网段上(E) 地址在192.168.16.0网段上(F) 这是一个公有地址答案:CE注:IP地址中关键是看她的主机位,将子网掩码划为二进制,1对应上面的地址是网络位,0对应的地址是主机位192.168.19.255/20划为二进制为:11000000.10101000.00010011.1111111111111111.11111111.11110000.00000000主机位变成全0表示这个IP的网络地址主机槐涑扇?表示这个IP的广播地址RFC1918文件规定了保留作为局域网使用的私有地址:10.0.0.0 - 10.255.255.255 (10/8 prefix)172.16.0.0 - 172.31.255.255 (172.16/ 12 prefix)192.168.0.0 - 192.168.255.255 (192.168/16 prefix)3、Quidway系列路由器在执行数据包转发时,下列哪些项没有发生变化(假定没有使用地址转换技术)?()(A) 源端口号(B) 目的端口号(C) 源网络地址(D) 目的网络地址(E) 源MAC地址(F) 目的MAC地址答案:ABCD参考知识点:路由功能就是指选择一条从源网络到目的网络的路径,并进行数据包的转发。
完整版CCNA测试题库及答案

完整版CCNA测试题库及答案描述载波侦听多路由访问/冲突检测(CSMA/CD)的工作原理。
CSMA/CD是一种帮助设备均衡共享带宽的协议,可避免两台设备同时在网络介质上传输数据。
虽然他不能消除冲突,但有助于极大的减少冲突,进而避免重传,从而提高所的设备的数据传输效率。
区分半双工和全双工通信。
并指出两种方法的需求。
与半双工以太网使用一对导线不同,全双工以太网使用两队导线,全双工使用不同的导线来消除冲突,从而允许同时发送和接收数据,而半双工可接收或发送数据,但不能同时接收和发送数据,且仍会出现冲突。
要使用全双工,电缆两端的设备都必须支持全双工,并配置成一全双模式运行。
描述MAC地址的组成部分以及各部分包含的信息。
MAC(硬件)地址时一种使用十六进制表示的地址,长48位(6B)。
其中前24位(3B)称为OUI(Organizationally Unique Idebtifier,组织唯一表示符),有IEEE分配给NIC制造商;余下的部分呢唯一地标识了NIC识别十进制数对应的二进制值和十六进制值。
用这三种格式之一表示的任何数字都可以转换为其他两种格式,能够执行这种转换对理解IP地址和子网划分至关重要。
识别以太网帧中与数据链路层相关的字段。
在以太网中,与数据链路层相关的字段包括前导码,帧其实位置分隔符,目标MAC地址,源MAC地址,长度或者类型以及帧校验序列。
识别以太网布线相关的IEEE标准。
这些标准描述了各种电缆类型的功能和物理特征,包括(但不限于)10Base2、10Base5和10BaseT。
区分以太网电缆类型及其用途。
以太网电缆分3种:直通电缆,用于将PC或路由器的以太网接口连接到集线器或交换机;交叉电缆。
用于将集线器连接到集线器,集线器连接到交换机,交换机连接到交换机以及PC连接到PC;反转电缆,用于PC和路由器或交换机之间建立控制台连接。
描述数据封装过程及其在分组创建中的作用。
数据封装指的是在OSI模型各层给数据添加信息的过程,也成为分组创建。
CCNA题库8

CCNA题库8(没有写answer的题目,淡蓝色的选项为答案)106. Refer to the exhibit.What does the (*) represent in the output?A. Packet is destined for a local interface to the router.B. Packet was translated, but no response was received from the distant device.C. Packet was not translated, because no additional ports are available.D. Packet was translated and fast switched to the destination.107. Refer to the exhibit.What command sequence will enable PAT from the inside to outside network?A. (config) ip nat pool isp-net 1.2.4.2 netmask 255.255.255.0 overloadB. (config-if) ip nat outside overloadC. (config) ip nat inside source list 1 interface ethernet1 overloadD. (config-if) ip nat inside overload108. Refer to the exhibit. What will happen to HTTP traffic coming from the Internet that is destined for172.16.12.10 if the traffic is processed by this ACL?A. Traffic will be dropped per line 30 of the ACL.B. Traffic will be accepted per line 40 of the ACL.C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.D. Traffic will be accepted, because the source address is not covered by the ACL.109. What are three advantages of VLANs? (Choose three.)A. VLANs establish broadcast domains in switched networks.B. VLANs utilize packet filtering to enhance network security.C. VLANs provide a method of conserving IP addresses in large networks.D. VLANs provide a low-latency internetworking alternative to routed networks.E. VLANs allow access to network services based on department, not physical location.F. VLANs can greatly simplify adding, moving, or changing hosts on the network.110. An administrator would like to configure a switch over a virtual terminal connection from locations outside of the local LAN. Which of the following are required in order for the switch to be configured from a remote location? (Choose two.)A. The switch must be configured with an IP address, subnet mask, and default gateway.B. The switch must be connected to a router over a VLAN trunk.C. The switch must be reachable through a port connected to its management VLAN.D. The switch console port must be connected to the Ethernet LAN.E. The switch management VLAN must be created and have a membership of at least one switch port.F. The switch must be fully configured as an SNMP agent.111. Which of the following host addresses are members of networks that can be routed across the public Internet? (Choose three.)A. 10.172.13.65B. 172.16.223.125C. 172.64.12.29D. 192.168.23.252E. 198.234.12.95F. 212.193.48.254112. Given a subnet mask of 255.255.255.224, which of the following addresses can be assigned to network hosts? (Choose three.)A. 15.234.118.63B. 92.11.178.93C. 134.178.18.56D. 192.168.16.87E. 201.45.116.159F. 217.63.12.192113. Which of the following are benefits of VLANs? (Choose three.)A. They increase the size of collision domains.B. They allow logical grouping of users by function.C. They can enhance network security.D. They increase the size of broadcast domains while decreasing the number of collisiondomains.E. They increase the number of broadcast domains while decreasing the size of the broadcast domains.F. They simplify switch administration.114. Which router IOS commands can be used to troubleshoot LAN connectivity problems? (Choose three.)A. pingB. tracertC. ipconfigD. show ip routeE. winipcfgF. show interfaces115. Which of the following are true regarding bridges and switches? (Choose two.)A. Bridges are faster than switches because they have fewer ports.B. A switch is a multiport bridge.C. Bridges and switches learn MAC addresses by examining the source MAC address of each frame received.D. A bridgewill forward a broadcast but a switch will not.E. Bridges and switches increase the size of a collision domain.116. What are some of the advantages of using a router to segment the network? (Choose two.)A. Filtering can occur based on Layer 3 information.B. Broadcasts are eliminated.C. Routers generally cost less than switches.D. Broadcasts are not forwarded across the router.E. Adding a router to the network decreases latency.117. Which of the following statements are true regarding bridges and switches? (Choose3.)A. Switches are primarily software based while bridges are hardware based.B. Both bridges and switches forward Layer 2 broadcasts.C. Bridges are frequently faster than switches.D. Switches have a higher number of ports than most bridges.E. Bridges define broadcast domains while switches define collision domains.F. Both bridges and switches make forwarding decisions based on Layer 2 addresses.118. Which characteristics are representative of a link-state routing protocol? (Choose three.)A. provides common view of entire topologyB. exchanges routing tables with neighborsC. calculates shortest pathD. utilizes event-triggered updatesE. utilizes frequent periodic updates119. Which of the following statements describe the network shown in the graphic? (Choose two.)A. There are two broadcast domains in the network.B. There are four broadcast domains in the network.C. There are six broadcast domains in the network.D. There are four collision domains in the network.E. There are five collision domains in the network.F. There are seven collision domains in the network.120. A national retail chain needs to design an IP addressing scheme to support a nationwide network. The company needs a minimum of 300 sub-networks and a maximum of 50 host addresses per subnet. Working with only one Class B address, which of the following subnet masks will support an appropriate addressing scheme? (Choose two.)A. 255.255.255.0B. 255.255.255.128C. 255.255.252.0D. 255.255.255.224E. 255.255.255.192F. 255.255.248.0。
CCNA题库V18总结
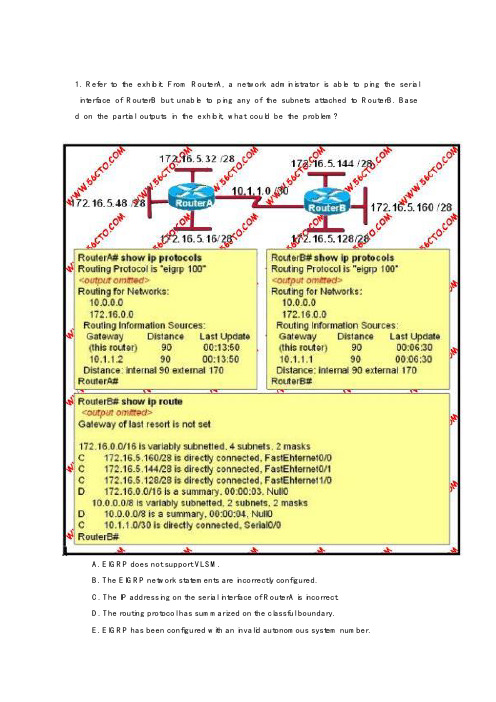
1. Refer to the exhibit. From RouterA, a network administrator is able to ping the serial interface of RouterB but unable to ping any of the subnets attached to RouterB. Base d on the partial outputs in the exhibit, what could be the problem?A. EIGRP does not support VLSM.B. The EIGRP network statements are incorrectly configured.C. The IP addressing on the serial interface of RouterA is incorrect.D. The routing protocol has summarized on the classful boundary.E. EIGRP has been configured with an invalid autonomous system number.Answer: D2. Refer to the exhibit. A junior network engineer has prepared the exhibited config uration file. What two statements are true of the planned configuration for interface fa0/1? (Choose two.)A. The two FastEthernet interfaces will require NAT configured on two outside serial interfaces.B. Address translation on fa0/1 is not required for DMZ Devices to access the Internet.C. The fa0/1 IP address overlaps with the space used by s0/0.D. The fa0/1 IP address is invalid for the IP subnet on which it resides.E. Internet hosts may not initiate connections to DMZ Devices through the configuration that is shown.Answer: BE3 Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.2950Switch(config-if)# switchport port-security2950Switch(config-if)# switchport port-security mac-address sticky2950Switch(config-if)# switchport port-security maximum 1The Ethernet frame that is shown arrives on interface fa0/1. What two functions wil l occur when this frame is received by 2950Switch? (Choose two.)A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.B. Only host A will be allowed to transmit frames on fa0/1.C. This frame will be discarded when it is received by 2950Switch.D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of2950Switch, will be forwarded out fa0/1.Answer: BD4. Refer to the exhibit. What will Router1 do when it receives the data frame show n? (Choose three.)A. Router1 will strip off the source MAC address and replace it with the MAC address0000.0c36.6965.B. Router1 will strip off the source IP address and replace it with the IP address192.168.40.1.C. Router1 will strip off the destination MAC address and replace it with the MAC address 0000.0c07.4320.D. Router1 will strip off the destination IP address and replace it with the IP address of 192.168.40.1.E. Router1 will forward the data packet out interface FastEthernet0/1.F. Router1 will forward the data packet out interface FastEthernet0/2.Answer: ACF5. A router has been configured to provide the nine users on the branch office LA N with Internet access,as shown in the diagram. It is found that some of the users on the LAN cannot reach the Internet. Based on the topology and router output s hown, which command should be issued on the router to correct the problem?A: Branch(config-if)# no shutdownB: Branch(config-if)# duplex fullC: Branch(config-if)# no keepaliveD: Branch(config-if)# ip address 192.168.10.30 255.255.255.240E: Branch(config-if)# bandwidth 100F: Branch(config-if)# encapsulation 802.3Answer: D6. Refer to the exhibit. When the hosts boot, hosts that are connected to the switc hes are having trouble getting a DHCP address from the DHCP server. Which ST P feature could minimize the effects of STP convergence for the hosts?A: port priorityB: PortFastC: BIDD: path costE: hold-down timerAnswer: B7. Refer to the exhibit. The partial frame in the graphic represents select header in formation within a frame arriving at a destination host. What can be determined fro m this information?A: The source host is a Telnet server.B: This frame contains the first segment in a Telnet session.C: The Layer 2 address of the source host is 192.168.14.2.D: The local host has received 42,335 bytes from the remote host as a part of this conversation.Answer: B8. A network administrator wants to control which user hosts can access the netwo rk based on their MAC address.What will prevent workstations with unauthorized M AC addresses from connecting to the network through a switch?A: BPDUB: port securityC: RSTPD: STPE: VTPF: blocking modeAnswer: B9. Refer to the exhibit. Workstation A must be able to telnet to switch SW-A through router RTA for management purposes. What must be configured for this connection to be successful?A: VLAN 1 on RTAB: default gateway on SW-AC: IP routing on SW-AD: cross-over cable connecting SW-A and RTAAnswer: B10. Which function does the Frame Relay DLCI provide with respect to RouterA?A: defines the signaling standard between RouterA and the frame switchB: identifies the circuit between RouterA and the frame switchC: identifies the circuit between RouterB and the frame switchD: identifies the encapsulation used between RouterA and RouterBE: defines the signaling standard between RouterB and the frame switchAnswer: B11. Refer to the exhibit. Given the partial configuration shown in the exhibit, why d o internal workstations on the 192.168.1.0 network fail to access the Internet?A: A NAT pool has not been defined.B: The wrong interface is overloaded.C: NAT has not been applied to the inside and outside interfaces.D: The access list has not been applied to the proper interface to allow traffic out of the internal network.Answer: C12. In a Frame Relay environment, what is the function of the DE bit?A: the activation of the LMI protocolB: the identification of the virtual circuitC: the identification of what routing updates to blockD: the identification of frames that are transmitted above the CIRE: the notification to the destination switch of network congestionAnswer: D13. The access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the fol lowing Telnet sessions will be blocked by this ACL? (Choose two.)A: from host A to host 5.1.1.10B: from host A to host 5.1.3.10C: from host B to host 5.1.2.10D: from host B to host 5.1.3.8E: from host C to host 5.1.3.10F: from host F to host 5.1.1.10Answer: BD14. A network administrator is designing a new corporate internetwork. The corporation is concerned aboutdowntime due to link failure and also about link costs. Which topology will provide some redundancy toincrease reliability for all sites but will cost less than a fully redundant topology?Answer: B15. You have finished physically installing an access point on the ceiling at your of fice. At a minimum, which parameter must be configured on the access point in or der to allow a wireless client to operate on it?A: AESB: PSKC: SSIDD: TKIPE: WEPAnswer: C16. What does a Layer 2 switch use to decide where to forward a received frame?A: source MAC addressB: source IP addressC: source switch portD: destination IP addressE: destination port addressF: destination MAC addressAnswer: F17. The exhibited network is stable and operating properly. Assuming that default STP configurations are running on both switches, which port will be in blocking mo de?A: Port Fa0/1 on Switch1B: Port Fa0/2 on Switch1C: Port Fa0/1 on Switch2D: Port Fa0/2 on Switch2Answer: A18. What Frame Relay mechanism is used to build the map illustrated in the accompanying graphic?A: ARPB: Inverse ARPC: inverse multiplexingD: LMI mappingE: proxy ARPAnswer: B19. The system LED is amber on a Cisco Catalyst 2950 series switch. What does this indicate?A: The system is malfunctioning.B: The system is not powered up.C: The system is powered up and operational.D: The system is forwarding traffic.E: The system is sensing excessive collisions.Answer: A20. Refer to the exhibit. The network administrator is configuring RTA to connect t o a non-Cisco network. Which two commands would be applied to the S0/0 WAN i nterface, but not to the Fa0/0 LAN interface?(Choose two.)A:speedB:no shutdownC:ip addressD:authentication papE:encapsulation pppAnswer: DE21. Which two of these are characteristics of the 802.1Q protocol? (Choose two.)A:It is used exclusively for tagging VLAN frames and does not address network reconvergence followingswitched network topology changes.B:It modifies the 802.3 frame header, and thus requires that the FCS be recomputed. C:It is a Layer 2 messaging protocol which maintains VLAN configurations across networks.D:It includes an 8-bit field which specifies the priority of a frame.E:It is a trunking protocol capable of carrying untagged frames.Answer: BE22. The network administrator has configured NAT as shown in the graphic. Some clients can access the Internet while others cannot. What should the network adm inistrator do to resolve this problem?A: Configure an IP NAT pool.B: Properly configure the ACL.C: Apply the ACL to the S0 interface.D: Configure another interface with the ip nat outside command.Answer: B23. Refer to the exhibit. When running OSPF, what would cause router A not to form an adjacency with router B?A: The loopback addresses are on different subnets.B: The values of the dead timers on the routers are different.C: Route summarization is enabled on both routers.D: The process identifier on router A is different than the process identifier on router B. Answer: B24. Which two methods are examples of implementing Layer 2 security on a Cisco switch? (Choose two.)A:disable trunk negotiation on the switchB:enable Cisco Discovery Protocol globally to monitor for malicious devicesC:configure a switch port host where appropriateD:enable HTTP access to the switch for security troubleshootingE:use only protected Telnet sessions to connect to the Cisco deviceF:install a modem on the auxiliary port for emergency accessAnswer: AC25. How is an EUI-64 format interface ID created from a 48-bit MAC address?A: by appending 0xFF to the MAC addressB: by prefixing the MAC address with 0xFFEEC: by prefixing the MAC address with 0xFF and appending 0xFF to itD: by inserting 0xFFFE between the upper three bytes and the lower three bytes of the MAC addressE: by prefixing the MAC address with 0xF and inserting 0xF after each of its first three bytesAnswer: D。
CCNA试题

CCNA认证试题一(附答案和解析)中文版(一)CCNA1 2007-09-30 15:49:59 阅读139 评论0 字号:大中小订阅1、目前,我国应用最为广泛的LAN标准是基于()的以太网标准.(A) IEEE 802.1(B) IEEE 802.2(C) IEEE 802.3(D) IEEE 802.5答案:C参考知识点:现有标准:IEEE 802.1 局域网协议高层IEEE 802.2 逻辑链路控制IEEE 802.3 以太网IEEE 802.4 令牌总线IEEE 802.5 令牌环IEEE 802.8 FDDIIEEE 802.11 无线局域网记住IEEE802.1-------IEEE802.5的定义以太网是一种计算机局域网组网技术。
IEEE制定的IEEE 802.3标准给出了以太网的技术标准。
它规定了包括物理层的连线、电信号和介质访问层协议的内容。
以太网是当前应用最普遍的局域网技术。
它很大程度上取代了其他局域网标准,如令牌环、FDDI和ARCNET。
以太网的标准拓扑结构为总线型拓扑,但目前的快速以太网(100BASE-T、1000BASE-T标准)为了最大程度的减少冲突,最大程度的提高网络速度和使用效率,使用交换机(Switch)来进行网络连接和组织,这样,以太网的拓扑结构就成了星型,但在逻辑上,以太网仍然使用总线型拓扑的C***A/CD介质访问控制方法。
电气电子工程师协会或IEEE(Institute of Electrical and Electronics Engineers)是一个国际性的电子技术与信息科学工程师的协会。
建会于1963年1月1日。
总部在美国纽约市。
在150多个国家中它拥有300多个地方分会。
目前会员数是36万。
专业上它有35个专业学会和两个联合会。
IEEE发表多种杂志,学报,书籍和每年组织300多次专业会议。
IEEE 定义的标准在工业界有极大的影响。
下面列出:IEEE802.3以太网标准802.3--------- 10Base以太网标准802.3u-------- 100Base-T(快速以太网)802.3z-------- 1000Base-X(光纤吉比特以太网)802.3ab-------- 1000Base-T(双绞线吉比特以太网)2、对于这样一个地址,192.168.19.255/20,下列说法正确的是: ()(A) 这是一个广播地址(B) 这是一个网络地址(C) 这是一个私有地址(D) 地址在192.168.19.0网段上(E) 地址在192.168.16.0网段上(F) 这是一个公有地址答案:CE注:IP地址中关键是看她的主机位,将子网掩码划为二进制,1对应上面的地址是网络位,0对应的地址是主机位192.168.19.255/20划为二进制为:11000000.10101000.00010011.1111111111111111.11111111.11110000.00000000主机位变成全0表示这个IP的网络地址主机槐涑扇?表示这个IP的广播地址RFC1918文件规定了保留作为局域网使用的私有地址:10.0.0.0 - 10.255.255.255 (10/8 prefix)172.16.0.0 - 172.31.255.255 (172.16/12 prefix)192.168.0.0 - 192.168.255.255 (192.168/16 prefix)3、Quidway系列路由器在执行数据包转发时,下列哪些项没有发生变化(假定没有使用地址转换技术)?()(A) 源端口号(B) 目的端口号(C) 源网络地址(D) 目的网络地址(E) 源MAC地址(F) 目的MAC地址答案:ABCD参考知识点:路由功能就是指选择一条从源网络到目的网络的路径,并进行数据包的转发。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1Which OSI layer is responsible for binary transmission, cable specification, and physical aspects of network communication
Presentation
Transport
Data Link
Physical
2A n installed fiber run can be checked for faults, integrity, and the performance of the media by using what device?
light injector
OTDR
TDR
multimeter
3When is a straight-through cable used in a network?
when connecting a router through the console port
when connecting one switch to another switch
when connecting a host to a switch
when connecting a router to another router
4W hich fiber connector supports full duplex Ethernet?
5Which type of cable run is most often associated with fiber-optic cable?
backbone cable
horizontal cable
patch cable
work area cable
6W hich of the following is a characteristic of single-mode fiber-optic cable?
generally uses LEDs as the light source
relatively larger core with multiple light paths
less expensive than multimode
generally uses lasers as the light source
7
Refer to the exhibit. Which type of Category 5 cable is used to make an Ethernet connection between Host A and Host B?
coax cable
rollover cable
crossover cable
straight-through cable
8I n LAN installations where potential electrical hazards or electromagnetic interference may be present, what type of media recommended for backbone cabling?
coax
fiber
Cat5e UTP
Cat6 UTP
STP
9In most business LANs, which connector is used with twisted-pair networking cable?
BNC
RJ-11
RJ-45
Type F
10What are three measures of data transfer? (Choose three.)
goodput
frequency
amplitude
throughput
crosstalk
bandwidth
11Which method of signal transmission uses radio waves to carry signals?
electrical
optical
wireless
acoustic
12W hich characteristics describe fiber optic cable? (Choose two.)
It is not affected by EMI or RFI.
Each pair of cables is wrapped in metallic foil.
It combines the technique of cancellation, shielding and twisting to protect data.
It has a maximum speed of 100 Mbps.
It is the most expensive type of LAN cabling.
13What is a primary role of the Physical layer in transmitting data on the network?
create the signals that represent the bits in each frame on to the media
provide physical addressing to the devices
determine the path packets take through the network
control data access to the media
14W hat characteristic of UTP cable helps reduce the effects of interference?
the metal braiding in the shielding
the reflective cladding around core
the twisting of the wires in the cable
the insulating material in the outer jacket
15What is considered a benefit of wireless as a media choice?
more host mobility
lower security risks
reduced susceptibility to interference
less impact of the surroundings on the effective coverage area
16W ith the use of unshielded twisted-pair copper wire in a network, what causes crosstalk within the cable pairs?
the magnetic field around the adjacent pairs of wire
the use of braided wire to shield the adjacent wire pairs
the reflection of the electrical wave back from the far end of the cable
the collision caused by two nodes trying to use the media simultaneously
17What is a possible effect of improperly applying a connector to a network cable?
Data will be forwarded to the wrong node.
Data transmitted through that cable may experience signal loss.
An improper signaling method will be implemented for data transmitted on that cable.
The encoding method for data sent on that cable will change to compensate for the improper connection.。
