BERULUB VPN 13 RINGLUB-1
cisco 双hub双dmvpn配置实例
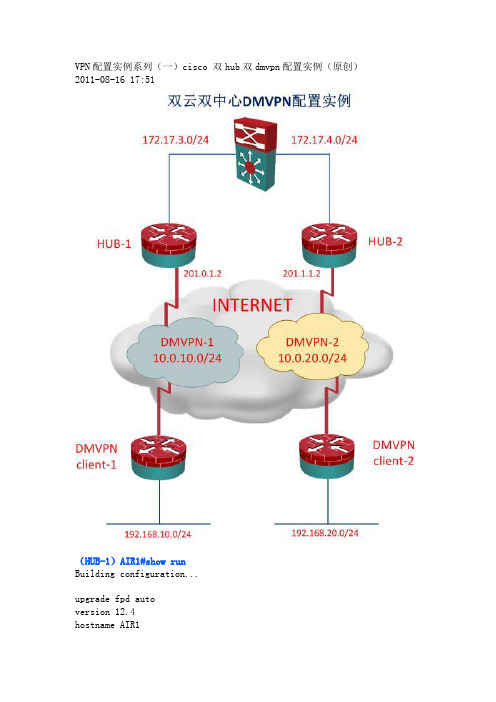
VPN配置实例系列(一)cisco 双hub双dmvpn配置实例(原创)2011-08-16 17:51(HUB-1)AIR1#show runBuilding configuration...upgrade fpd autoversion 12.4hostname AIR1aaa new-model!aaa authentication login login local noneaaa session-id commonip source-routeip cefno ip domain lookupno ipv6 cef!multilink bundle-name authenticatedusername cisco privilege 15 secret 5 $1$2HQI$6HPxKq33L6fHLOq.mNEJ6. archivelog confighidekeys!crypto isakmp policy 10hash md5authentication pre-sharegroup 2crypto isakmp key two.hub.key address!crypto ipsec transform-set two.hub.set esp-3des esp-md5-hmacmode transport!set transform-set two.hub.set!interface Loopback0ip address 1.1.4.1 255.255.255.0ip ospf network point-to-point!interface Tunnel0ip address 10.0.10.1 255.255.255.0no ip redirectsip mtu 1400ip nhrp map multicast dynamicip nhrp network-id 10ip nhrp holdtime 600ip ospf network broadcastip ospf priority 10delay 1000tunnel source Serial1/1tunnel mode gre multipointtunnel key 2012!interface FastEthernet0/0ip address 172.17.3.2 255.255.255.0duplex autospeed auto!interface Serial1/1ip address 201.0.1.2 255.255.255.0serial restart-delay 0router ospf 100router-id 1.1.4.1log-adjacency-changesnetwork 10.0.10.0 0.0.0.255 area 1network 172.17.3.0 0.0.0.255 area 0!ip forward-protocol ndip route 0.0.0.0 0.0.0.0 201.0.1.1line con 0exec-timeout 0 0logging synchronouslogin authentication loginstopbits 1line aux 0stopbits 1line vty 0 4!end-----------------------------------------------------(HUB-2)AIR2#show runBuilding configuration...version 12.4hostname AIR2enable password cisco!aaa new-model!aaa authentication login login local none!aaa session-id commonmemory-size iomem 5!ip cefno ip domain lookupip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticatedusername ezvpn password 0 ezvpnusername air2 secret 5 $1$iT8A$btPfNBneo8ShHP1pJwRyt/ archivelog confighidekeys!crypto isakmp policy 10hash md5authentication pre-sharegroup 2crypto isakmp key two.hub.key address .0 0.0.0.0!crypto ipsec transform-set two.hub.set esp-3des esp-md5-hmac mode transport!crypto ipsec profile two.hub.profileset transform-set two.hub.setinterface Loopback0ip address 1.1.7.1 255.255.255.0!interface Tunnel0ip address 10.0.20.1 255.255.255.0no ip redirectsip mtu 1400ip nhrp authentication two.authip nhrp map multicast dynamicip nhrp network-id 10ip nhrp holdtime 600ip ospf network broadcastip ospf priority 5delay 1000tunnel source Serial1/2tunnel mode gre multipointtunnel key 2012tunnel protection ipsec profile two.hub.profile!interface FastEthernet0/0ip address 172.17.4.2 255.255.255.0duplex autospeed auto!interface Serial1/0ip address 202.0.0.2 255.255.255.0serial restart-delay 0interface Serial1/2ip address 201.1.1.2 255.255.255.0serial restart-delay 0router ospf 100router-id 1.1.7.1log-adjacency-changesnetwork 10.0.20.0 0.0.0.255 area 1network 172.17.4.0 0.0.0.255 area 0ip route 0.0.0.0 0.0.0.0 201.1.1.1line con 0exec-timeout 0 0logging synchronouslogin authentication loginline aux 0login authentication loginline vty 0 4exec-timeout 0 0logging synchronouslogin authentication login!!end-----------------------------------------------------------------(SPOKE-1)IOSFW1#show runBuilding configuration...!version 12.4!hostname IOSFW1aaa new-modelaaa authentication login login local noneaaa session-id commonmemory-size iomem 5ip cefno ip domain lookupip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticatedusername cisco privilege 15 secret 5 $1$FfyS$.b/nQwuam1J17HEESibRB0 archivelog confighidekeyscrypto isakmp policy 10hash md5authentication pre-sharegroup 2crypto isakmp key two.hub.key address!crypto ipsec transform-set two.hub.set esp-3des esp-md5-hmacmode transport!set transform-set two.hub.setinterface Loopback0ip address 1.1.5.1 255.255.255.0!interface Tunnel0ip address 10.0.10.2 255.255.255.0ip mtu 1400ip nhrp maip nhrp network-id 10ip nhrp holdtime 300ip ospf network broadcastip ospf priority 0delay 1000tunnel source Serial1/0tunnel key 2012!interface Tunnel1ip address 10.0.20.2 255.255.255.0ip mtu 1400ip nhrp maip nhrp network-id 10ip nhrp holdtime 300ip ospf network broadcastip ospf priority 0delay 1000tunnel source Serial1/0tunnel key 2012!interface Serial1/0ip address 201.0.2.2 255.255.255.0serial restart-delay 0router ospf 100router-id 1.1.5.1log-adjacency-changesnetwork 10.0.10.0 0.0.0.255 area 1network 10.0.20.0 0.0.0.255 area 1network 192.168.10.0 0.0.0.255 area 1!ip forward-protocol ndip route 0.0.0.0 0.0.0.0 201.0.2.1line con 0exec-timeout 0 0logging synchronouslogin authentication loginline aux 0line vty 0 4!!end---------------------------------------------------------------------(SPOKE-2)IOSFW2#show runBuilding configuration...version 12.4no service password-encryption!hostname IOSFW2enable password cisco!aaa new-modelaaa authentication login login local noneaaa session-id commonmemory-size iomem 5ip cefno ip domain lookupip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticated!username iosfw2 secret 5 $1$.S/B$cBe/jtBt23/MpNaFaZ1320 archivelog confighidekeys!crypto isakmp policy 10hash md5authentication pre-sharegroup 2crypto isakmp key two.hub.key address .0 0.0.0.0!crypto ipsec transform-set two.hub.set esp-3des esp-md5-hmac mode transport!crypto ipsec profile two.hub.profileset transform-set two.hub.setinterface Loopback0ip address 1.1.6.1 255.255.255.0!interface Tunnel0ip address 10.0.10.3 255.255.255.0ip mtu 1400ip nhrp authentication two.authip nhrp ma.1 201.0.1.2ip nhrp network-id 10ip nhrp holdtime 300ip nhrp nhs 10.0.10.1ip ospf network broadcastip ospf priority 0delay 1000tunnel source Serial1/0tunnel destination 201.0.1.2tunnel key 2012tunnel protection ipsec profile two.hub.profile!interface Tunnel1ip address 10.0.20.3 255.255.255.0ip mtu 1400ip nhrp authentication two.authip nhrp ma.1 201.1.1.2ip nhrp network-id 10ip nhrp holdtime 300ip nhrp nhs 10.0.20.1ip ospf network broadcastip ospf priority 0delay 1000tunnel source Serial1/0tunnel destination 201.1.1.2tunnel key 2012tunnel protection ipsec profile two.hub.profile interface Serial1/0ip address 201.0.3.2 255.255.255.0serial restart-delay 0router ospf 100router-id 1.1.6.1log-adjacency-changesnetwork 10.0.10.0 0.0.0.255 area 1network 10.0.20.0 0.0.0.255 area 1network 192.168.20.0 0.0.0.255 area 1ip forward-protocol ndip route 0.0.0.0 0.0.0.0 201.0.3.1line con 0exec-timeout 0 0logging synchronouslogin authentication loginline aux 0login authentication loginline vty 0 4exec-timeout 0 0logging synchronouslogin authentication login!!endIOSFW1#show cry isa saIPv4 Crypto ISAKMP SAdst src state conn-id slot status201.0.1.2 201.0.2.2 QM_IDLE 1011 0 ACTIVE201.1.1.2 201.0.2.2 QM_IDLE 1014 0 ACTIVEIOSFW2#show cry isa saIPv4 Crypto ISAKMP SAdst src state conn-id slot status201.1.1.2 201.0.3.2 QM_IDLE 1002 0 ACTIVE201.0.1.2 201.0.3.2 QM_IDLE 1001 0 ACTIVEIOSFW1#show cry ipsec saprotected vrf: (none)local ident (addr/mask/prot/port): (201.0.2.2/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (201.0.1.2/255.255.255.255/47/0) current_peer 201.0.1.2 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 921, #pkts encrypt: 921, #pkts digest: 921#pkts decaps: 976, #pkts decrypt: 976, #pkts verify: 976#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 2, #recv errors 0local crypto endpt.: 201.0.2.2, remote crypto endpt.: 201.0.1.2path mtu 1500, ip mtu 1500, ip mtu idb Serial1/0current outbound spi: 0x116D44B0(292373680)IOSFW2#show cry ipsec saprotected vrf: (none)local ident (addr/mask/prot/port): (201.0.3.2/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (201.0.1.2/255.255.255.255/47/0) current_peer 201.0.1.2 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 791, #pkts encrypt: 791, #pkts digest: 791#pkts decaps: 849, #pkts decrypt: 849, #pkts verify: 849#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 1, #recv errors 0local crypto endpt.: 201.0.3.2, remote crypto endpt.: 201.0.1.2path mtu 1500, ip mtu 1500, ip mtu idb Serial1/0 current outbound spi: 0x38CD88C8(952993992)IOSFW1#show cry engine connect activeCrypto Engine ConnectionsIOSFW2#show cry engine connection activeCrypto Engine ConnectionsIOSFW1#show ip ospf neiNeighbor ID Pri State Dead Time Address Interface .1 5 FULL/DR 00:00:36 10.0.20.1 Tunnel11.1.4.1 10 FULL/DR 00:00:37 10.0.10.1 Tunnel0 IOSFW2#show ip ospf neiNeighbor ID Pri State Dead Time Address Interface .1 5 FULL/DR 00:00:34 10.0.20.1 Tunnel11.1.4.1 10 FULL/DR 00:00:33 10.0.10.1 Tunnel0。
FortiClient VPN 安装和配置手册说明书

Manual de Instalación y Configuración VPN UBO - FortiClientContenidoDescripción del servicio de VPN (3)Requisitos (3)Proceso de Descarga de FortiClient (4)Descarga para Windows (4)Descargas para Mac (OSX) (4)Proceso de Instalación de FortiClient (Windows) (5)Proceso de Instalación de FortiClient (Mac) (8)Configuración de FortiClient VPN (11)Conectarse a la VPN (12)Manual de Instalación FortiClient VPN Descripción del servicio de VPNVirtual Private Network, comúnmente conocida como VPN, permite establecer una conexión segura, la cual es cifrada entre dos puntos, como por ejemplo un computador de escritorio hasta la red interna de la Universidad Bernardo O’Higgins.Podrá acceder a los recursos internos como plataformas y/o sistemas que no están disponibles para acceder desde el exterior.RequisitosPara poder establecer un acceso vía VPN hacia la UBO, necesitará:➢Un computador o Notebook** / MacBook*** y conexión a Internet.➢Cuenta de usuario UBO, la cual es la misma que utiliza para ingresar a su correo @ubo.cl** La versión de Windows debe ser igual o superior a Windows 7***Si Utiliza MacBook, la versión de OSX debe ser igual o superior a 10.12 SierraProceso de Descarga de FortiClientDescarga para Windows1. Descargue FortiClient desde el siguiente enlace: VPN UBO2. Una vez descargado ejecute el instalador haciendo doble clic sobre él y continúe con elproceso de Instalación. Pág. 5Descargas para Mac (OSX)A.Descargue FortiClient desde el siguiente enlace Oficial: VPN MACB. Descargue FortiClient desde Nuestro Repositorio UBO: VPN MAC1. Haga clic en “Aceptar” para descargar el archivo .dmg2. Una vez terminada la descarga, realice sobre clic sobre el archivo descargado y vaya alapartado instalación para Mac (OSX) para continuar con la instalación y configuración.Proceso de Instalación de FortiClient (Windows)1. Se desplegarán las siguientes ventanas, a lo cual realice lo siguiente:Haga clic en “Yes, I have read and acept the” y luego clic en siguiente.2. En esta ventana, solo haga clic en “Next”, sin modificar ninguna opción3. Clic en “Next”4. Haga clic en “Install”, se le solicitará permiso de administrador, a lo cual debe seleccionar“SI”. El programa realizará el proceso de instalación.5. Haga clic en “Finish” para cerrar el instalador.6. En su escritorio tendrá el acceso directo a FortiClient. Ejecútelo. Vaya a la Pág. 11Proceso de Instalación de FortiClient (Mac) 1.Realice doble clic en el paquete de instalación previamente descargado. (Pág. 4)2.Haga clic en “abrir” y comenzará la descarga, luego presione “Install” o “Instalar”3.Haga Clic en continuar para comenzar el proceso.4.Presione “Continuar”5.Acepte el contrato de Licencia, “Acepto”6.Haga clic en “instalar”7.El sistema le solicitará sus credenciales de Administrador / UsuarioIntrodúzcala y presione “Instalar Software”, luego espera a que finalice el proceso.Presione “Cerrar” cuando se haya completado la instalación8.Finalizada la instalación, en la barra superior, presione el escudo de FortiClient y realice clic en“Abrir Consola de FortiClient”, se despegará la consola de configuración la cual debe configurar tal como se muestra en la Pág. 11Configuración de FortiClient VPN1. Para configurar FortiClient, realice un clic sobre “Acceso Remoto” en el menú lateralizquierdo y luego clic en “Configurar VPN”2. Debe ingresar los siguientes datos tal como se observa en la siguiente imagen adjuntay seleccionar las opciones destacadas.Sunombredeusuarioesigualaldesucorreo,****************Gateway: vpn.ubo.clPuerto: 1144311Conectarse a la VPN1.Sitúese en la pestaña de “Acceso Remoto” e ingrese su contraseña, luego clic en “Conectar”2.Cuando la conexión sea Exitosa, vera lo siguiente:12Si tiene problemas o dificultades respecto al área tecnológica, puede elevar un ticket de atención en la Mesa de Servicio víaserviciosti.ubo.cl13。
Lunix 端口一览表
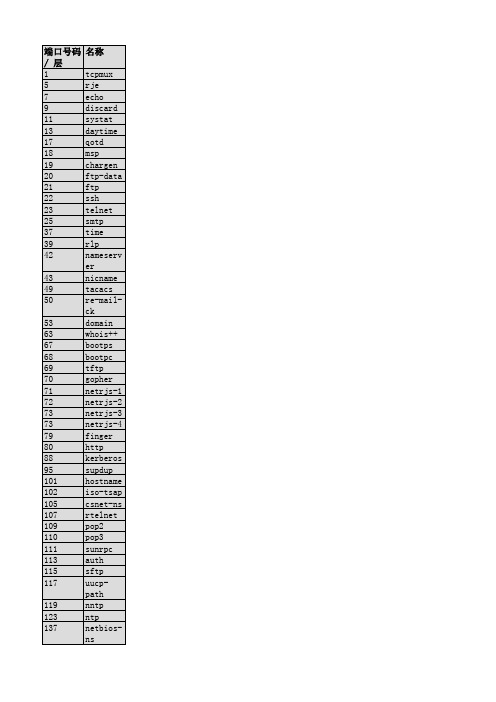
表 C-1. 著名端口
以下端口是 UNIX 特有service])是服务的守
表 C-2. UNIX 特有的端
表 C-3列举了由网络和软件社区向 IANA 提交的要在端口号码列表中正式注册的端口。
表 C-3. 注册的端口
表 C-4显示了一个和数据报传递协议(DDP)有关的端口列表。
DDP 在 AppleTalk 网络上被使用。
表 C-4. 数据报传递协
表 C-5是和 Kerberos 网络验证协议相关的端口列表。
在标记的地方,v5 代表 Kerberos 版本5协议。
注意,这些
表 C-5. Kerberos(工
表 C-6是一个未注册的端口列表。
这些端口可能被安装在你的红帽企业 Linux 系统上的服务或协议使用,或者它
特有的,涉及了从电子邮件到验证不等的服务。
在方括号内的名称(如 [service])是服务的守护进程名称或它的常
有的端口
举了由网络和软件社区向 IANA 提交的要在端口号码列表中正式注册的端口。
端口
示了一个和数据报传递协议(DDP)有关的端口列表。
DDP 在 AppleTalk 网络上被使用。
传递协议端口
和 Kerberos 网络验证协议相关的端口列表。
在标记的地方,v5 代表 Kerberos 版本5协议。
注意,这些端口没有在 IANA 注
s(工程 Athena/MIT)端口
rvices
c/services rvices
守护进程名称或它的常用别名。
没有在 IANA 注册。
GCF Field Trial requirements for GSM_GPRS_EGPRS

GLOBAL CERTIFICATION FORUM (GCF) LtdWork Item DescriptionField Trial requirements for GSM/GPRS/EGPRSReference: GCF WI-108Version: v3.1.0Date: 29.01.2010Document Type: Technical1 ScopeThe scope of this work item covers the renewal of Field Trial requirements for GSM/(E)GPRS including SIM/USIM.2 DescriptionThis Work Item description has been created to handle the renewal of GSM/(E)GPRS including SIM/USIM Field Trial requirements.3 JustificationField Trials are an integral part of the GCF scheme and therefore are required to evolve in conjunction with the implementation of associated mobile technology.4 Supporting companiesCSR, Ericsson Mobile Platforms, Motorola, NEC, Nokia, O2 UK, Orange France, RIM, Sony Ericsson, Vodafone Group, Broadcom, TIM, TeliaSonera5 RapporteurMarc OuwehandNokia CorporationTelephone: +358 40828 0908E-mail: marc.ouwehand@6 Affected bandsNote: GSM 850 and 1900 are outside the GCF certification scheme.7 Core Specifications8 Test SpecificationsNote: The operator expectations on each identified Field Trial Requirement can be derived from the GSMA PRD DG 11 ‘DG Field and Lab Trial Guidelines’, It is emphasised that DG.11 is only a guideline and that manufacturers may use their own test procedures.9 Work Item Certification Entry9.1 Work Item Certification Entry Criteria (CEC)N/A.9.2 Target Work Item Certification Entry Date / GCF-CC versionN/A10 Work Item Freeze and Completion CriteriaDuring the next PRP review this WI should be set to ‘Completed’.11 Conformance Test RequirementsN/A12 IOP Test RequirementsN/A13 Field Trial RequirementsFor BSS/MSC network dependent Field Trial Requirements (BM)For GPRS network dependent Field Trial Requirements (GPRS)For SIM/UICC dependent Field Trial Requirements (2GSIM)For SMSC dependent Field Trial Requirements (SMS)For Network/SIM/UICC/Client independent Field Trial Requirements (NI)14 Periodic Review PointsThe next PRP-review for this WI will be held at the t FT AG meeting during Q3 2010.15 Other commentsThe information below is coming from both WI’s, which during the FT AG #15 meeting has been merged into this WI.Former WI-028 Comments:- During the SG 25 meeting a concern was raised about the approval of this Work Item as well as the CR’s attached to this Work Item via 10 day rule process. The SG made clear that this approval process is not conform the official GCF rules. The SG supposed to approve this Work Item and CR’s. During the SG 25 meeting document S-06-053 was created and approved by the SG to give a mandate for approval via 10 day rule. This mandate applies only for CR’s concerning this Work Item.- Due to the introduction of this Work Item and Work Item 27 (HSDPA) it is required that GCF operators re-declare their status as GCF Qualified operator by using the new Annex B, which should be available in thePRD GCF-OP released in April 2006. The CR for this renewed Annex B is a part of this Work Item and will be uploaded as CR FT-06-022r4During the teleconference of 20.3.2006 there was agreed that an agenda point will be made for FT AG #04,3-4 May 2006 concerning re-declaration.- During the teleconference of 20.3.2006, there was noticed that the mandate for this Work Item didn’t include the EGPRS feature. Therefore it was agreed that the EGPRS topic will be put on the agendafor FT AG #04.Mr. M. Ouwehand (Nokia) will take care that there will be a discussion/input documentavailable for the FT AG #04.When WI-028 has been activated there was agreed to put a ‘transition period’ in place, due the fact that bythat time there were no enough FTQ ANNEX B documents available.During the FT AG #08, 2-3 May 2007, there has been agreed that the ‘transition period’ is ended by therelease of GCF-CC 3.26.0.Former WI-048 Comments:It was suggested during the FTAG meeting discussions of this WI that the most effective method ofadministrating and executing the EDGE classified test requirements while maintaining confidence in GCF FTfor both GPRS and EDGE networks is:a) Introduce a new classification called EDGEb) Copy all existing GPRS requirements to the EDGE Requirements.c) FT on GPRS NW Configurations do not need to perform the EDGE classified test requirementsd) FT on EDGE NW Configurations do not need to perform the GPRS classified test requirements.When this WI meet the CEC and therefore will be activated, it should be considered by FT AG to merge the EDGE Field Trial requirements table into the existing GPRS Field Trial requirements table as has been done with PS, HSDPA & EUL requirements table merge.The CR’s to GCF-CC related to this Work Item need to be submitted at the same time that CR to activate this Work item will be submitted.16 Document Change Record。
juniper防火墙之图解l2tp vpn配置
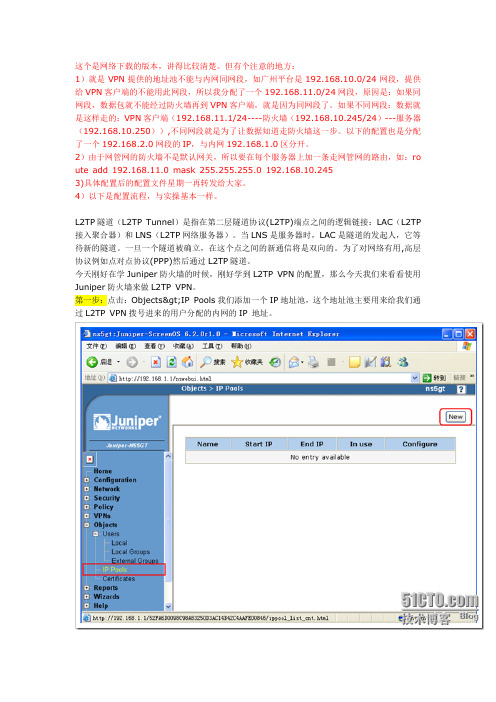
这个是网络下载的版本,讲得比较清楚。
但有个注意的地方:1)就是VPN提供的地址池不能与内网同网段,如广州平台是192.168.10.0/24网段,提供给VPN客户端的不能用此网段,所以我分配了一个192.168.11.0/24网段,原因是:如果同网段,数据包就不能经过防火墙再到VPN客户端,就是因为同网段了。
如果不同网段:数据就是这样走的:VPN客户端(192.168.11.1/24----防火墙(192.168.10.245/24)---服务器(192.168.10.250)),不同网段就是为了让数据知道走防火墙这一步。
以下的配置也是分配了一个192.168.2.0网段的IP,与内网192.168.1.0区分开。
2)由于网管网的防火墙不是默认网关,所以要在每个服务器上加一条走网管网的路由,如:ro ute add 192.168.11.0 mask 255.255.255.0 192.168.10.2453)具体配置后的配置文件星期一再转发给大家。
4)以下是配置流程,与实操基本一样。
L2TP隧道(L2TP Tunnel)是指在第二层隧道协议(L2TP)端点之间的逻辑链接:LAC(L2TP 接入聚合器)和LNS(L2TP网络服务器)。
当LNS是服务器时,LAC是隧道的发起人,它等待新的隧道。
一旦一个隧道被确立,在这个点之间的新通信将是双向的。
为了对网络有用,高层协议例如点对点协议(PPP)然后通过L2TP隧道。
今天刚好在学Juniper防火墙的时候,刚好学到L2TP VPN的配置,那么今天我们来看看使用Juniper防火墙来做L2TP VPN。
第一步:点击:Objects>IP Pools我们添加一个IP地址池,这个地址池主要用来给我们通过L2TP VPN拨号进来的用户分配的内网的IP 地址。
如上图:IP Pool Name就是给我们地址池起上一个名字,以便我们以后好调用。
Start IP:我们地址池起始的IP地址End IP:我们地址池结束的IP地址输入好以后点击OK就行了。
迅博NG系列VPN说明书

(二 )如何使 VPN 设备接入到互联网中 ,并使 VPN 服务正 (二) 设备接入到互联网中, 常运行
将外网线接到迅博 VPN 设备的 WAN 口, 点“网络设置” 菜单,选择上网方式, 如果做为 VPN 服务器使用,则可选择 ADSL 拨号或静态 IP 两种方式,输入相应的 配置参数,保存后,如果网线接入正常,则可以使 VPN 设备接入到互联网中。 电脑接入到互联网后,如果是 ADSL 拨号,则可以在“设备信息”—》 “连接信息 中”看到具体的 ADSL 拨号日志。或者在“调试工具”菜单中判断是否接入到互 联网。一旦接入到互联网,您可以让设备商远程进行其他配置。 然后对 VPN 进行配置,进入“VPN 配置”—》 “基本配置”菜单,选择 VPN 模式,输入序列号,增加相应的帐号信息,保存即可启动 VPN,并且在日志中可 以查看 VPN 运行信息。
六、迅博纯软件 VPN 服务器使用说明 ....................... 38
(一)WIN32 版本使用说明(WINDOWS XP/2003/SERVER 等)................................ 38 (二)LINUX 版本使用说明(X86 版).................................................................. 39
3 此说明书适用于:NG300/320、NG500/520、NG1200、NG2000 等型号,不同型号的差异以实物为准
迅博 VPN/防火墙使用说明书
其中上图的硬件标志 ID 是 128bit 标志码,每个设备唯一,可以用做 VPN 硬件绑定认证功能,这样可以保证更安全的接入。同时从设备信息中也可以看出 授权个数以及 VPN 的外网 IP 地址。 然后,进行网络设置, 如果是 ADSL 上网方式,则上网方式选择 PPPoE 拨号方式,如果是专线或 者前面有路由器的上网方式,则选择静态 IP 方式,如果 VPN 网关做分支使用, 则可以选择 DHCP 自动获取 IP 方式。 NG 系列产品支持双线互联网接入,如两条 ADSL 接入到互联网中,同时支 持负载均衡功能,支持高级策略路由功能,可以根据源 IP、端口号、目的 IP 、 目的端口号选路,同时支持电信网通选路功能。下面是具体的配置方法: 1、单线接入 外网线路 1 中选择上网方式,如果是专线用户选择静态 IP 方式, ADSL 用 户选择 PPPOE 拨号方式。如下图所示。输入配置信息后(由运营商提供) ,点保 存,大约 10 秒,配置即可生效。
DFBS MERV 13 高效滤网套件安装说明书
1. MERV 13 High Efficiency Filter Kit for FXSQ_TAVJU2. DFBS_A13 MERV 13 Filter SummaryFilter CabinetModelDFBS22A13 DFBS27A13 DFBS39A13 Indoor Unit FXSQ05TAVJU FXSQ07TAVJU FXSQ09TAVJU FXSQ12TAVJU FXSQ15TAVJU FXSQ18TAVJU # of Filters 1 1 2 Airflow (CFM) 281 281 318 335 530 600 FilterEfficiencyMERV 13Filter InitialPressure Loss(in. w.g.)0.08” 0.08” 0.10” 0.11” 0.13” 0.09”Dimensions(in. HxWxD)9.5” x 24.06” x 7” 9.5” x 29.9” x 7” 9.5” x 42” x 7”Filter Service Space (in.) Side Access:20”Side Access:27”Side Access:20”CabinetWeight(Gross)12 lbs 15 lbs 21 lbs Filter Type Disposable, synthetic, electrostatically charged, non-woven mediaReplacement Filter SQM13A20(6 per box)SQM13A25(6 per box)Filter CabinetModelDFBS39A13 DFBS55A13 DFBS61A13 Indoor Unit FXSQ24TAVJU FXSQ30TAVJU FXSQ36TAVJU FXSQ48TAVJU FXSQ54TAVJU # of Filters 2 2 3 Airflow (CFM) 742 812 1130 1307 1377 FilterEfficiencyMERV 13Filter InitialPressure Loss(in. w.g.)0.13” 0.15” 0.15” 0.19” 0.18”Dimensions(in. HxWxD)9.5” x 42” x 7” 9.5” x 57.4” x 7” 9.5” x 63.3 x 7”Filter Service Space (in.) Side Access:20”Side Access:27”Side Access:20”CabinetWeight(Gross)21 lbs 28 lbs 32 lbs Filter Type Disposable, synthetic, electrostatically charged, non-woven mediaReplacement Filter SQM13A20(6 per box)SQM13A25(6 per box)SQM13A20(6 per box)3. Installation of the DFBS_A13 MERV 13 Filter UnitBefore starting the installation work, carefully read the following Safety Precautions and observe them to ensure safety during work.∙Be sure to use only the specified components contained in this kit when installing. Failure to do so could lead to reduction in system performance and possible system failure.∙After installation, check that there is no abnormality during the trial operation.∙Select an installation location that conforms with the following conditions:1. Sufficient strength to bear the weight of the indoor unit and filter chamber; theindoor unit and the filter cabinet shall be supported independently of one anotheras necessary.2. The lower surface of a ceiling is not significantly inclined in such a way thatprevents proper, level installation of the indoor unit. Refer to the indoor unitinstallation manual for additional detail.3. Select a location that allows for adequate service space for replacing the filtermedia.4. Instructions for Filter Cabinet InstallationThe following instructions provide step-by-step instructions on how to install the filter cabinet to the indoor unit.4.1. Remove the factory mounted return air flange by removing the sheet metal screwsholding the flange in place.4.2. Reusing the factory sheet metal flange screws, start two screws in the two upperposition holes on the side rail as shown in Figure 1. These screws will help align theplacement of the filter box.Figure 14.3. Align the filter box mounting keyholes with the two sheet metal screws and hang the filterbox by insert the screw heads into the keyhole slots.4.4. Once the filter box is in place, install the remaining sheet metal screws and tighten.Refer to Figure 2.Figure 2。
VPN配置,类型及错误691的解决
VPN配置、类型详解及错误691的解决一、配置VPN1.右键点击“网络”-->“属性”,点击下面“设置新的连接或网络”2.选择“连接到工作区”3.选择“通过Internet使用虚拟专用网络(VPN)来连接”4.输入IP地址,目标名称,其中目标名称可以随便取名。
5.输入用户名和密码。
6.选择立即连接即可。
二、连接过程中报错误691的解决办法。
错误解决步骤:1.首先保证你用户密码正确.2.VPN连接属性-->安全选项标签下的VPN有三种类型:这里要选择你服务器对应的类型。
3.数据加密选择可选加密。
三、VPN类型详解:VPN 有如下几中类型:点对点隧道协议(PPTP)VPN 连接二层传输协议 IPsec(L2TP/IPsec)VPN 连接使用安全套接隧道协议(SSTP)的安全套接字层(SSL)加密的超文本传输协议(HTTP)VPN 连接VPN 重连接,可使用 Internet 协议安全(IPsec)隧道模式的 Internet 密钥交换版本 2(IKEv2)DirectAccess,混合使用公钥基础架构(PKI)、IPsec、SSL,以及 Internet 协议版本6(IPv6)VPN的实现技术1.隧道技术实现VPN的最关键部分是在公网上建立虚信道,而建立虚信道是利用隧道技术实现的,IP隧道的建立可以是在链路层和网络层。
第二层隧道主要是PPP连接,如PPTP,L2TP,其特点是协议简单,易于加密,适合远程拨号用户;第三层隧道是IPi nIP,如IPSec,其可靠性及扩展性优于第二层隧道,但没有前者简单直接。
2.隧道协议隧道是利用一种协议传输另一种协议的技术,即用隧道协议来实现VPN功能。
为创建隧道,隧道的客户机和服务器必须使用同样的隧道协议。
1) PPTP(点到点隧道协议)是一种用于让远程用户拨号连接到本地的ISP,通过因特网安全远程访问公司资源的新型技术。
它能将PPP(点到点协议)帧封装成I P数据包,以便能够在基于IP的互联网上进行传输。
DrayTek Vigor VPN Routers VPN Con
5
Step Three: Configure Remote Access Settings
➔ User Accounts and Authentication ◆ Check the box Enable this account ◆ Make sure the Idle Timeout is set to 0 seconds
VPN Configuration Guide
DrayTek Vigor VPN Routers
© 2022 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the written consent of equinux AG or equinux USA, Inc. Your rights to the software are governed by the accompanying software license agreement. The equinux logo is a trademark of equinux AG and equinux USA, Inc., registered in the U.S. and other countries. Other product and company names mentioned herein may be trademarks and/or registered trademarks of their respective companies. equinux shall have absolutely no liability for any direct or indirect, special or other consequential damages in connection with the use of this document or any change to the router in general, including without limitation, any lost profits, business, or data, even if equinux has been advised of the possibility of such damages. Every effort has been made to ensure that the information in this configuration guide is accurate. equinux is not responsible for printing or clerical errors. Revised February 2022 Apple, the Apple logo, macOS, and MacBook are trademarks of Apple Computer, Inc., registered in the U.S. and other countries.
非常全面的网络拓扑图图标
100BaseT Hub
uBR910 Cable DSU CDDI/ FDDI Concentrator
PC Adapter Card
Small Hub (10BaseT Hub)
Terminal Server
Icons: Cisco Products (Cont.)
Route/Switch Processor with and without Si
Satellite Dish
Satellite UPS, RPS
MAU
PAD Diskette (3.5" Floppy)
ONS 15540
Icons: Cisco Products (Cont.)
SC2200 Signaling Controller
VSC3000 Virtual Switch Controller
IP/TV Content Manager
IP/TV Broadcast Server
Voice Gateway
Channelized Pipe
Concatenated Payload
Optical CrossConnect
WDM Optical Fiber
ONS15104
SONET MUX
Optical Amplifier Digital CrossConnect
Optical Services Router
House, Regular and Blue
Telecommuter House (Color and Subdued)
Home Office
Medium Building, Regular, Subdued, and Blue
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
BERULUB VPN 13 RINGLUB
高温轮带油
产品描述 含有大量固体润滑剂的合成油。专用于高温高 负载的滑动摩擦面 在高温+2度00时º,C 液以体下蒸处发于,液在体摩润擦滑表状面态形,当成非遇到常稳更 定的固体润滑膜 特别提醒 在使用前轻摇润滑油容器,把固体润滑剂摇匀
典型应用 回转窑30体º润C滑到剂1150 ºC 很好的附着性 用在很热的部位仅有很少量的烟 优秀的抗磨损能力 不会产生硬或粘的残留物 不含溶剂和有毒重金属 可用手动喷枪加油
结构
颜色
密度 20 ºC
VKA 焊接负载
测试负荷等级 FZG
A/2, 76/50
磨损量
固体润滑剂
含量
基础油 闪点
倾点
g/ml N
Mg/kWh
ºC ºC
半流体 灰色
1.05
5000
>12 <0.2
石墨,铜,铝 大约 20% 合成油
>300
<-40
DIN 51 757 DIN51 350 DIN 51 354
DIN ISO 2592 DIN ISO 3016
KAIYA 2006-1-4
