Juniper SRX防火墙巡检命令
JuniperSRX系列防火墙日常监控命令

JuniperSRX系列防火墙日常监控命令Juniper SRX系列防火墙日常监控命令查看版本admin@#run show version查看机箱环境user@host> show chassis environmentuser@host> show chassis environment cbuser@host> show chassis environment cb 0user@host> show chassis environment pem查看机箱告警(正常情况下不能存在大量硬件错识信息)user@host> show chassis alarms查看日志信息(正常工作情况下,日志中不应该有大量重复的信息,如端口频繁up/down、大量用户认证失败信息等。
)user@host> show log messages查看机箱硬件信息user@host> show chassis hardware查看机箱路由引擎信息user@host> show chassis routing-engine查看机箱FPC信息user@host> show chassis fpcuser@host> show chassis fpc detailuser@host> show chassis fpc pic-status系统关机/重启user@host> request system halt/reboot板卡上线/下线user@host>request chassis fpc slot slot-number offlineuser@host>request chassis fpc slot slot-number online防火墙设备指示灯检查(直接查看防火墙前面板的LED 指示灯)Status :系统状态。
黄色闪烁表示系统正常启动;绿色闪烁表示系统正常工作。
juniper SRX 常用命令

juniper SRX 常用命令rollbackset interfaceset routing-options staticset system login user admin class super-userset system login user admin authentication plain-text-password 输入密码set system services sshset security zones security-zone untrust host-inbound-traffic system-services ssh/pingset security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services ssh /telnet/pingset security zones security-zone trust host-inbound-traffic system-services ssh /telnet /pingset security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services ssh /telnet/pingset security zones security-zone untrust interfaces ge-0/0/0 (不定义区域,无法配置NAT)set security zones security-zone trust interfaces ge-0/0/1###### set security zones security-zone trust interfaces ge-0/0/1 ???###### set interfaces interface-range interfaces-trust member ge-0/0/1 ????##################################################静态NAT:set security nat source rule-set interface-nat from zone trustset security nat source rule-set interface-nat to zone untrustset security nat source rule-set interface-nat rule rule1 match source-address 192.168.0.0/23 set security nat source rule-set interface-nat rule rule1 match destination-address 0.0.0.0/0 set security nat source rule-set interface-nat rule rule1 then source-nat interfaceset security zones security-zone trust address-book address 192 192.168.0.0/23set security zones security-zone trust address-book address-set 192nat address 192set security policies from-zone trust to-zone untrust policy 192nat match source-address anyset security policies from-zone trust to-zone untrust policy 192nat match destination-address any set security policies from-zone trust to-zone untrust policy 192nat match application anyset security policies from-zone trust to-zone untrust policy 192nat then permit#######################################################强制172.16.0.12走150出去(默认走物理接口146出去)set security nat source pool pool-1 address 121.9.255.112set security nat source rule-set sou-nat rule rule-mail match source-address 172.16.0.12/32set security nat source rule-set sou-nat rule rule-mail match destination-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-mail then source-nat pool pool-1insert security nat source rule-set sou-nat rule rule-mail before rule rule-sou##########################################################端口映射静态PAT: 从外到内set security nat proxy-arp interface ge-0/0/0.0 address 10.1.1.100/24set security nat proxy-arp interface ge-0/0/3.0 address 10.1.2.100/24set security nat destination pool dnat-pool-1 address 192.168.0.9/32set security nat destination pool dnat-pool-2 address 172.16.0.12/32set security nat destination rule-set dst-nat from zone untrustset security nat destination rule-set dst-nat rule rule3 match destination-address 10.1.1.100/24 set security nat destination rule-set dst-nat rule rule3 match destination-port 21set security nat destination rule-set dst-nat rule rule3 then destination-nat pool dnat-pool-1set security nat destination rule-set dst-nat rule rule2 match destination-address 10.1.2.100/24 set security nat destination rule-set dst-nat rule rule2 match destination-port 443set security nat destination rule-set dst-nat rule rule2 then destination-nat pool dnat-pool-2set security zones security-zone trust address-book address ftpserver 192.168.0.9set security zones security-zone trust address-book address mailserver 172.16.0.12set security zones security-zone trust address-book address-set servergroup address ftpserver set security zones security-zone trust address-book address-set servergroup address mailserverset security policies from-zone untrust to-zone trust policy static-nat match source-address any destination-address servergroup application junos-httpset security policies from-zone untrust to-zone trust policy static-nat match application junos-pop3set security policies from-zone untrust to-zone trust policy static-nat then permitset applications application 443 protocol tcpset applications application 443 destination-port 443##############################################################set security nat source rule-set sou-nat from zone trustset security nat source rule-set sou-nat to zone untrustset security nat source rule-set sou-nat rule rule-mail match source-address 172.16.0.30/32set security nat source rule-set sou-nat rule rule-mail match destination-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-mail then source-nat pool pool-1##############################################################管理端口:set system services web-management httpsset system services web-management httpset system services web-management http port 8084set system services web-management http interface allset system services web-management https system-generated-certificateset system services web-management http interface ge-0/0/0.0set system services web-management https interface ge-0/0/0.0###########################################################################定义端口地址池XXX_group:set applications application smtp_25 destination-port 25 protocol tcpset applications application pop3_110 destination-port 110 protocol tcpset applications application exchange_135 destination-port 135 protocol tcpset applications application smtp_465 destination-port 465 protocol tcpset applications application imap_993 destination-port 993 protocol tcpset applications application pop3_995 destination-port 995 protocol tcpset applications application-set mail_port_group application smtp_25set applications application-set XXX_group application smtpset applications application-set XXX_group application pop3引用XXX_group:set security policies from-zone untrust to-zone trust policy mail-policy match application XXX_group############################################################################## 反向静态NAT:从外到内set security nat static rule-set mail-static-nat from zone untrustset security nat static rule-set mail-static-nat rule mail1 match destination-address 121.9.255.150/32set security nat static rule-set mail-static-nat rule mail1 then static-nat prefix 172.16.0.12/32返回的安全Policy:set security policies from-zone untrust to-zone trust policy mail-policy match source-address any set security policies from-zone untrust to-zone trust policy mail-policy match destination-address Mail_serset security policies from-zone untrust to-zone trust policy mail-policy match application any(XXX_group)set security policies from-zone untrust to-zone trust policy mail-policy then permit插入insert Policy:set security zones security-zone trust address-book address deny_172 172.16.0.155set security policies from-zone trust to-zone untrust policy deny_172 match source-address deny_172set security policies from-zone trust to-zone untrust policy deny_172 match destination-address anyset security policies from-zone trust to-zone untrust policy deny_172 match application anyset security policies from-zone trust to-zone untrust policy deny_172 then denyinsert security policies from-zone trust to-zone untrust policy deny_172 before policy Trust2Utrust (Trust2Utrust允许上公网策略)#####################################################禁止192网段上网,只允许192.168.0.2,192.168.0.121上网set security zones security-zone trust address-book address deny_192 192.168.0.0/23set security zones security-zone trust address-book address permit_host_2 192.168.0.2/32set security zones security-zone trust address-book address permit_host_121 192.168.0.121/32 set security zones security-zone trust address-book address-set permit_192_online address FTP_serset security zones security-zone trust address-book address-set permit_192_online address permit_host_2set security zones security-zone trust address-book address-set permit_192_online address permit_host_121set security zones security-zone trust address-book address-set deny_192_online address deny_192返回的安全Policy:set security policies from-zone trust to-zone untrust policy permit_192_online match source-address permit_192_onlineset security policies from-zone trust to-zone untrust policy permit_192_online match destination-address anyset security policies from-zone trust to-zone untrust policy permit_192_online match application anyset security policies from-zone trust to-zone untrust policy permit_192_online then permitset security policies from-zone trust to-zone untrust policy deny_192_online match source-address deny_192_onlineset security policies from-zone trust to-zone untrust policy deny_192_online match destination-address anyset security policies from-zone trust to-zone untrust policy deny_192_online match application anyset security policies from-zone trust to-zone untrust policy deny_192_online then denyinsert security policies from-zone trust to-zone untrust policy permit_192_online before policy deny_172insert security policies from-zone trust to-zone untrust policy deny_192_online before policy deny_172###########################################################################配置WEB管理set system host-name Testset system root-authentication encrypted-password "$1$XKPZUqwc$/WdxM1Cc1GAB8gJ0nNCOt."set system name-server 202.96.128.166set system name-server 202.96.128.86set system login user admin uid 2001set system login user admin class super-userset system login user admin authentication encrypted-password HJuZerSULPfkAset system services sshset system services web-management http port 8084set system services web-management http interface allset system services web-management http interface ge-0/0/0.0set system services web-management https system-generated-certificateset system services web-management https interface ge-0/0/0.0set interfaces ge-0/0/0 unit 0 family inet address 192.168.8.125/24set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24set security zones security-zone untrust host-inbound-traffic system-services httpset security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services http###########################################################################开放Untrust服务端口set security zones security-zone untrust interfaces ge-0/0/0.0set security zones security-zone untrust host-inbound-traffic system-services allset security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services allset security zones security-zone trust interfaces ge-0/0/1.0set security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services all配置默认路由+NATset routing-options static route 0.0.0.0/0 next-hop 192.168.8.1set security nat source rule-set sou-nat from zone trustset security nat source rule-set sou-nat to zone untrustset security nat source rule-set sou-nat rule rule-sou match source-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-sou match destination-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-sou then source-nat interface内网放行策略:set security policies from-zone trust to-zone untrust policy in_out match source-address any set security policies from-zone trust to-zone untrust policy in_out match destination-address anyset security policies from-zone trust to-zone untrust policy in_out match application anyset security policies from-zone trust to-zone untrust policy in_out then permit########################################################################### UTM 功能中防病毒功能set security utm utm-policy test-policy anti-virus http-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus ftp upload-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus ftp download-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus smtp-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus pop3-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus imap-profile junos-av-defaultsset security utm utm-policy test-policy anti-spam smtp-profile junos-as-defaultsset security utm utm-policy test-policy traffic-options sessions-per-client over-limit log-and-permitset security utm utm-policy web-policy anti-virus http-profile junos-av-defaultsset security utm utm-policy web-policy traffic-options sessions-per-client over-limit log-and-permitset security policies from-zone trust to-zone untrust policy permit_192_online match source-address permit_192_onlineset security policies from-zone trust to-zone untrust policy permit_192_online match destination-address anyset security policies from-zone trust to-zone untrust policy permit_192_online match application anyset security policies from-zone trust to-zone untrust policy permit_192_online then permit application-services utm-policy web-policyset security policies from-zone untrust to-zone trust policy mail-policy match source-address any set security policies from-zone untrust to-zone trust policy mail-policy match destination-address Mail_serset security policies from-zone untrust to-zone trust policy mail-policy match application mail_port_groupset security policies from-zone untrust to-zone trust policy mail-policy then permit application-services utm-policy test-policyset security policies from-zone untrust to-zone trust policy Ftp-Policy match source-address any set security policies from-zone untrust to-zone trust policy Ftp-Policy match destination-address FTP_serset security policies from-zone untrust to-zone trust policy Ftp-Policy match application junos-ftp set security policies from-zone untrust to-zone trust policy Ftpmservices utm-policy test-policyadmin@KDS_FW> show security utm anti-spam statistics##########################################################dynamic VPN功能配置:run show chassis routing-engine (查看CPU使用user、空闲idle)show config |dis set| match utmshow log utmd-av | lastclear log utmd-av###########################################################抓包功能配置:Could you please configure the following traceoption and send the log file.You can create the packet filter as followed#set security flow traceoption file debug#set security flow traceoption flag basic-datapath#set security flow traceoption packet-filter filter1 source-prefix <ip-address> destination-prefix<ip-address> destination-port 80#set security flow traceoption packet-filter filter2 source-prefix <ip-address> destination-prefix <ip-address> destination-port 80#committhe second one is for the return traffic.show log debugrequest system license update。
JuniperSRX高端防火墙简明配置手册

Juniper SRX防火墙简明配置手册目录一、 JUNOS 操作系统介绍 (3)1.1层次化配置结构 (3)1.2 JunOS 配置管理 (4)1.3 SRX 主要配置内容 (4)二、 SRX 防火墙配置说明 (5)2.1初始安装 (5)2.1.1登陆 (5)2.1.2设置 root 用户口令 (9)2.1.3JSRP 初始化配置 (9)2.1.4设置远程登陆管理用户 (14)2.1.5远程管理 SRX相关配置 (15)2.1.6ZONE 及相关接口的配置 (15)2.2 Policy (16)2.3 NAT (17)2.3.1Interface based NAT (18)2.3.2Pool based Source NAT (18)2.3.3Pool base destination NAT (19)2.3.4Pool base Static NAT (20)2.4 IPSEC VPN (21)2.5 Application and ALG (22)三、 SRX 防火墙常规操作与维护 (22)3.1单机设备关机 (22)3.2单机设备重启 (23)3.3单机操作系统升级 (23)3.4双机模式下主备 SRX 关机 (23)3.5双机模式下主备设备重启 (24)3.6双机模式下操作系统升级 (24)3.7双机转发平面主备切换及切换后恢复 (25)3.8双机控制平面主备切换及切换后恢复 (25)3.9双机模式下更换备SRX (25)3.10双机模式下更换主SRX (26)3.11双机模式更换电源 (27)3.12双机模式更换故障板卡 (27)3.13配置备份及还原方法 (27)3.14密码修改方法 (28)3.15磁盘文件清理方法 (28)3.16密码恢复 (28)3.17常用监控维护命令 (29)四、 SRX 防火墙介绍 (31)Juniper SRX防火墙简明配置手册SRX系列防火墙是 Juniper 公司基于 JUNOS操作系统的安全系列产品,JUNOS集成了路由、交换、安全性和一系列丰富的网络服务。
常用网络设备巡检命令参考
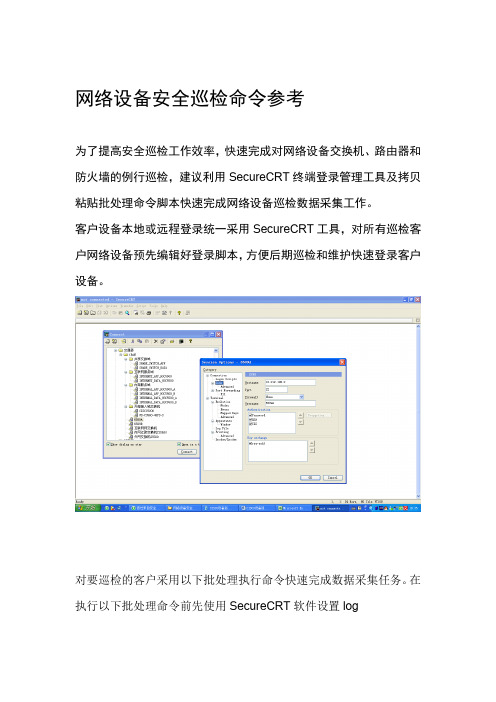
网络设备安全巡检命令参考为了提高安全巡检工作效率,快速完成对网络设备交换机、路由器和防火墙的例行巡检,建议利用SecureCRT终端登录管理工具及拷贝粘贴批处理命令脚本快速完成网络设备巡检数据采集工作。
客户设备本地或远程登录统一采用SecureCRT工具,对所有巡检客户网络设备预先编辑好登录脚本,方便后期巡检和维护快速登录客户设备。
对要巡检的客户采用以下批处理执行命令快速完成数据采集任务。
在执行以下批处理命令前先使用SecureCRT软件设置logsession到一个新建txt文件,然后选取全部以下命令拷贝粘贴到设备特权模式?下,以下命令所显示的信息会自动发送到新建的txt文件里。
.目录1 CISCO网络设备例行巡检数据采集任务 (3)1.1 CISCO交换机 (3)1.2 CISCO 路由器 (4)1.3 CISCO 防火墙 (4)1.4 CISCO网络设备巡检命令解释 (5)华为网络设备例行巡检数据采集任务................................................................................... 8 28 ................................................................................................................... 2.1 华为交换机8 ................................................................................................................... 2.2 华为路由器0 ..................................................................................... 12.3 华为网络设备巡检命令解释312 H3C网络设备例行巡检数据采集任务................................................................................2 交换机3.4 H3C ................................................................................................................ 12 3.5 H3C 路由器............................................................................................................... 13 H3C网络设备巡检命令解释.................................................................................... 13.64 14 港湾网络设备例行巡检数据采集任务.................................................................................4 4.7 港湾交换机................................................................................................................. 14 4.8 港湾路由器................................................................................................................1.4 .................................................................................... .14.9 港湾网络设备巡检命令解释5 1网络设备例行巡检数据采集任务HP .. (4)4 1交换机5.10 HP...................................................................................................................5 1.路由器5.11 HP .................................................................................................................5.网络设备巡检命令解释HP5.12 (1)1CISCO网络设备例行巡检数据采集任务1.1 CISCO交换机================================================================== terminal length 0show runnshow vershow ip socketshow ip socket detailshow tcpshow clockshow vtp statusshow vtp passshow env allshow inventoryshow spanning rootshow spanning blockshow spanningshow cdp neishow cdp nei detshow arpshow mac-address-tabledir all-show inter statusshow inter summshow inter | i errors|FastEthernet|GigabitEthernetclear countersshow proc cpu | ex 0.00%show proc memshow debugsh loggingshow ip routeterminal length 451.2 CISCO 路由器===================================================================== terminal length 0show vershow runnshow clockshow tcp brief allshow tcpshow env allshow inventoryshow cdp neishow cdp nei detshow arpdir all-show interfaceshow inter summshow inter | i errors|FastEthernet|GigabitEthernet|Serialclear countersshow proc cpu hisshow proc cpu | ex 0.00%show proc memshow debugshow access-listsh loggingshow ip routeterminal length 451.3 CISCO 防火墙====================================================================== terminal pager 0show runnshow vershow clockshow nameifshow inventoryshow resource usageshow asp dropshow conn countshow xlate countshow firewallshow perfmon detailshow ip audit countdir all-show interfaceshow inter | i errors|FastEthernet|GigabitEthernet|Serialclear countersshow cpu usashow memshow debugshow access-listsh loggingshow routeshow local-hostterminal pager 241.4 CISCO网络设备巡检命令解释======================================================================1terminal length 0 ;设置终端显示行数不做限制(使所有show命令完全显示,不做暂停)2show running-config ;查看当前设备配置3show version ;查看IOS版本信息及设备正常运行时间4show clock ;查看设备时钟信息5show tcp brief all ;查看当前设备开发的TCP服务状态6show vtp status ;查看交换机vtp配置模式7show vtp password ;查看交换机vtp配置口令8show env all ;查看设备温度,电源和风扇运转参数及是否报警(注意:中高端设备不带参数all)9show inventory ;调取设备内部板卡出厂模块型号及序列号(可作为资产梳理和设备维保依据)10show spanning-tree root ;查看交换机生成树根位置show spanning-tree block ;查看交换机11block端口show spanning-tree 12;查看全部VLAN生成树信息;查看邻接13show cdp neighborscisco设备基本信息;查看邻接cisco14设备详细信息show cdp neighbors detailshow mac-address-table ;通过查看MAC 地址表信息,确认目的MAC地址是否正确。
Juniper SRX系列防火墙日常监控命令

Juniper SRX系列防火墙日常监控命令查看版本admin@#run show version查看机箱环境user@host> show chassis environmentuser@host> show chassis environment cbuser@host> show chassis environment cb 0user@host> show chassis environment pem查看机箱告警(正常情况下不能存在大量硬件错识信息)user@host> show chassis alarms查看日志信息(正常工作情况下,日志中不应该有大量重复的信息,如端口频繁up/down、大量用户认证失败信息等。
)user@host> show log messages查看机箱硬件信息user@host> show chassis hardware查看机箱路由引擎信息user@host> show chassis routing-engine查看机箱FPC信息user@host> show chassis fpcuser@host> show chassis fpc detailuser@host> show chassis fpc pic-status系统关机/重启user@host> request system halt/reboot板卡上线/下线user@host>request chassis fpc slot slot-number offlineuser@host>request chassis fpc slot slot-number online防火墙设备指示灯检查(直接查看防火墙前面板的LED 指示灯)Status :系统状态。
黄色闪烁表示系统正常启动;绿色闪烁表示系统正常工作。
SRX防火墙日常监控命令

SRX 防火墙日常监控命令1、查看当前设备CPU、会话使用情况(正常情况下CPU峰值不要超过90%、并发连接数资源峰值不要超过MAX的80%)admin@#run op srx-monitor2、清除会话表admin@#run clear security flow session all (此操作必须要经过客户同意才可操作!慎用!)3、查看当前设备CPU使用情况(正常情况下CPU峰值不要超过90%)admin@#run show chassis routing-engine4、查看当前带宽使用情况admin@#run monitor interface traffic5、查询基于端口NAT地址翻译(正常情况下NAT翻译峰值不要超过MAX的90%)lab@srx5800a# run show security nat interface-nat-ports6、查看会话明细表(并发连接数资源峰值不要超过MAX的80%)admin@#run show security flow sessionadmin@#run show security flow session summary7、查看/清除ARP表admin@#run show arpadmin@#run clear arp8、查看设备时间(系统时间和当地时间、时区一致)admin@#run show system uptime9、查看接口状态(正在使用的接口应为UP或Active)admin@#run show interfaces terse10、查看光纤接口下的收发功率lab@mx480-2-re0# run show interfaces diagnostics optics ge-0/0/211、软件升级admin@#run request system software addftp://192.168.100.101/junos-srx3000-10.0R1.4-domestic.tgz no-copyno-validate unlink12、查看版本admin@#run show version13、查看机箱环境user@host> show chassis environmentuser@host> show chassis environment cbuser@host> show chassis environment cb 0user@host> show chassis environment pem14、查看机箱告警(正常情况下不能存在大量硬件错识信息)user@host> show chassis alarms15、查看日志信息(正常工作情况下,日志中不应该有大量重复的信息,如端口频繁up/down、大量用户认证失败信息等。
JUNIPER防火墙设备巡检文档

Juniper防火墙设备巡检使用命令-> get chassis输出信息显示所有模块运行OK此命令还可以看到设备各个模块的SN号及各个设备模块的型号。
-> get system该命令可显示IOS版本。
防火墙持续运行的时间。
最近一次的重启原因、防火墙主存的大小。
如果设备uptime时间比较短,一定在利用get system命令查看设备最近一次重启动的时间和原因,便于分析各种潜在风险。
-> get performance cpu使用get performance cpu命令检查防火墙短时间内(5分钟内)的CPU利用率。
Netscreen是基于硬件架构的高性能防火墙,很多计算工作由专用ASIC芯片完成,正常工作状态下防火墙CPU使用率应保持在50%以下,如出现CPU利用率过高情况需给予足够重视,应检查Session使用情况和各类告警信息,并检查网络中是否存在攻击流量。
通常情况下CPU利用率过高往往与攻击有关,可通过正确设置screening对应选项进行防范。
get memory显示了存储器的系统可用的内存。
NetScreen防火墙对内存的使用把握得十分准确,采用“预分配”机制,空载时内存使用率为约50-60%,随着流量不断增长,内存的使用率应基本保持稳定。
如果出现内存使用率高达90%时,需检查网络中是否存在攻击流量,并察看为debug分配的内存空间是否过大(get dbuf info单位为字节)。
-> get session info查看当前会话数量,:会话连接数不能太接近最大支持会话数,否则会过载,需要考虑升级设备-> get alarm event检查设备告警信息设备系统时间-> get nsrpnsrp状态正常备注: NSRP状态为active -> get config查看设备的配置信息。
Juniper SRX防火墙配置手册-命令行模式

Juniper SRX防火墙简明配置手册目录一、JUNOS操作系统介绍 (3)1.1 层次化配置结构 (3)1.2 JunOS配置管理 (4)1.3 SRX主要配置内容 (5)二、SRX防火墙配置对照说明 (6)2.1 初始安装 (6)2.1.1 登陆 (6)2.1.2 设置root用户口令 (6)2.1.3 设置远程登陆管理用户 (7)2.1.4 远程管理SRX相关配置 (7)2.2 Policy (8)2.3 NAT (8)2.3.1 Interface based NAT (9)2.3.2 Pool based Source NAT (10)2.3.3 Pool base destination NAT (11)2.3.4 Pool base Static NAT (12)2.4 IPSEC VPN (13)2.5 Application and ALG (15)2.6 JSRP (15)三、SRX防火墙常规操作与维护 (19)3.1 设备关机 (19)3.2设备重启 (20)3.3操作系统升级 (20)3.4密码恢复 (21)3.5常用监控维护命令 (22)Juniper SRX防火墙简明配置手册SRX系列防火墙是Juniper公司基于JUNOS操作系统的安全系列产品,JUNOS集成了路由、交换、安全性和一系列丰富的网络服务。
目前Juniper公司的全系列路由器产品、交换机产品和SRX安全产品均采用统一源代码的JUNOS操作系统,JUNOS是全球首款将转发与控制功能相隔离,并采用模块化软件架构的网络操作系统。
JUNOS作为电信级产品的精髓是Juniper真正成功的基石,它让企业级产品同样具有电信级的不间断运营特性,更好的安全性和管理特性,JUNOS软件创新的分布式架构为高性能、高可用、高可扩展的网络奠定了基础。
基于NP架构的SRX系列产品产品同时提供性能优异的防火墙、NAT、IPSEC、IPS、SSL VPN和UTM等全系列安全功能,其安全功能主要来源于已被广泛证明的ScreenOS操作系统。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Juniper SRX防火墙巡检命令
1. CPU利用率核查show chassis routing-engine
2. MEM利用率核查show chassis routing-engine
3. OSPF邻居关系核查show ospf neighbor
4. LDP端口状态检查show ldp interface
5. ISIS邻居关系检查show isis adjacency
6. BGP邻居关系检查show bgp neighbor
7. HSRP信息检查show vrrp extensive
8. 生成树STP信息检查
9. 电源状态核查show chassis environment pem
10. 风扇状态核查show chassis environment
11. 单板告警核查show chassis alarms
12. 单板状态核查show chassis fpc/show chassis fpc pic-status
13. 单板温度核查show chassis fpc/show chassis fpc pic-status
14. 单板固件版本信息检查show chassis fpc detail
15. 接口配置核查show configuration interfaces
16. 接口描述规范性核查show interface descriptions
17. AAA认证检查show configuration system
18. 引擎板冗余状态检查show configuration chassis redundancy
19. NTP状态核查show ntp associations
20. SYSLOG配置指向检查show configuration system syslog
21. TRAP配置指向检查
22. Telnet安全登录配置检查show configuration system login
23. DNS配置检查show configuration system name-server
24. 补丁版本核查show version。
