Juniper命令
juniper之常用命令

OSPF中路由重发布配置
enable ospf export direct [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]
show ospf
show access-list {<name> | port <portlist>}
show access-list-monitor
show ospf area <area identifier>
show ospf area detail
show ospf ase-summary
13.Access-Lists配置
create access-list icmp destination source
create access-list ip destination source ports
create access-list tcp destination source ports
6.port-channel配置
enable sharing <port> grouping <portlist> {port-based | address-based | round-robin}
show port sharing //查看配置
7.stp配置
enable stpd //启动生成树
show diag
show iparp
Juniper防火墙基本命令

Juniper防火墙基本命令Juniper防火墙基本命令常用查看命令Get int查看接口配置信息Get int ethx/x查看指定接口配置信息Get mip查看映射ip关系Get route查看路由表Get policy id x查看指定策略Get nsrp查看nsrp信息,后可接参数查看具体vsd组、端口监控设置等Get per cpu de查看cpu利用率信息Get per session de查看每秒新建会话信息Get session查看当前会话信息,后可匹配源地址、源端口、目的地址、目的端口、协议等选项Get session info查看当前会话数量Get system查看系统信息,包括当前os版本,接口信息,设备运行时间等Get chaiss查看设备及板卡序列号,查看设备运行温度Get counter stat查看所有接口计数信息Get counter stat ethx/x查看指定接口计数信息Get counter flow zone trust/untrust查看指定区域数据流信息Get counter screen zone untrust/trust查看指定区域攻击防护统计信息Get tech-support查看设备状态命令集,一般在出现故障时,收集该信息寻求JTAC支持常用设置命令Set int ethx/x zone trust/untrust/dmz/ha配置指定接口进入指定区域(trust/untrust/dmz/ha等)Set int ethx/x ip x.x.x.x/xx配置指定接口ip地址Set int ethx/x manage配置指定接口管理选项,打开所有管理选项Set int ethx/x manage web/telnet/ssl/ssh配置指定接口指定管理选项Set int ethx/x phy full 100mb配置指定接口速率及双工方式Set int ethx/x phy link-down配置指定接口shutdownSet nsrp vsd id 0 monitor interface ethx/x配置ha监控端口,如此端口断开,则设备发生主/备切换Exec nsrp vsd 0 mode backup手工进行设备主/备切换,在当前的主设备上执行set route 0.0.0.0/0 interface ethernet1/3 gateway 222.92.116.33配置路由,需同时指定下一跳接口及ip地址所有set命令,都可以通过unset命令来取消,相当于cisco中的no所有命令都可以通过“TAB”键进行命令补全,通过“?”来查看后续支持的命令防火墙基本配置create account [admin | user] <username> 回车输入密码:再次输入密码:configure account admin 回车输入密码:再次输入密码:2.port配置config ports <portlist> auto off {speed [10 | 100 | 1000]} duplex [half | full] auto off3.Vlan配置无论是核心还是接入层,都要先创建三个Vlan,并且将所有归于Default Vlan的端口删除:config vlan default del port allcreate vlan Servercreate vlan Usercreate vlan Manger定义802.1q标记config vlan Server tag 10config vlan User tag 20config vlan Manger tag 30设定Vlan网关地址:config vlan Server ipa 192.168.41.1/24config vlan User ipa 192.168.40.1/24config vlan Manger ipa 192.168.*.*/24Enable ipforwarding 启用ip路由转发,即vlan间路由Trunk 配置config vlan Server add port 1-3 tconfig vlan User add port 1-3 tconfig vlan manger add port 1-3 t4.VRRP配置enable vrrpconfigure vrrp add vlan UserVlanconfigure vrrp vlan UserVlan add master vrid 10 192.168.6.254configure vrrp vlan UserVlan authentication simple-password extremeconfigure vrrp vlan UserVlan vrid 10 priority 200configure vrrp vlan UserVlan vrid 10 advertisement-interval 15configure vrrp vlan UserVlan vrid 10 preempt5.端口镜像配置首先将端口从VLAN中删除enable mirroring to port 3 #选择3作为镜像口config mirroring add port 1 #把端口1的流量发送到3config mirroring add port 1 vlan default #把1和vlan default的流量都发送到36.port-channel配置enable sharing <port> grouping <portlist> {port-based | address-based | round-robin}show port sharing //查看配置7.stp配置enable stpd //启动生成树create stpd stp-name //创建一个生成树configure stpd <spanning tree name> add vlan <vlan name> {ports <portlist> [dot1d | emistp | pvst-plus]}configure stpd stpd1 priority 16384configure vlan marketing add ports 2-3 stpd stpd1 emistp8.DHCP 中继配置enable bootprelayconfig bootprelay add <dhcp server ip>9.NA T配置Enable nat #启用natStatic NA T Rule Exampleconfig nat add out_vlan_1 map source 192.168.1.12/32 to 216.52.8.32/32Dynamic NA T Rule Exampleconfig nat add out_vlan_1 map source 192.168.1.0/24 to 216.52.8.1 - 216.52.8.31Portmap NA T Rule Exampleconfig nat add out_vlan_2 map source 192.168.2.0/25 to 216.52.8.32 /28 both portmapPortmap Min-Max Exampleconfig nat add out_vlan_2 map source 192.168.2.128/25 to 216.52.8.64/28 tcp portmap 1024 - 819210.OSPF配置enable ospf 启用OSPF进程create ospf area <area identifier> 创建OSPF区域configure ospf routerid [automatic | <routerid>] 配置Routeridconfigure ospf add vlan [<vlan name> | all] area <area identifier> {passive} 把某个vlan加到某个Area中去,相当于Cisco中的network的作用configure ospf area <area identifier> add range <ipaddress> <mask> [advertise | noadvertise] {type-3 | type-7} 把某个网段加到某个Area中去,相当于Cisco中的network的作用configure ospf vlan <vlan name> neighbor add <ipaddress>OSPF中路由重发布配置enable ospf export direct [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]enable ospf export static [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]enable ospf originate-default {always} cost <metric> [ase-type-1 | ase-type-2] {tag <number>} enable ospf originate-router-id11.SNMP配置enable snmp accessenable snmp trapscreate access-profile <access profile> type [ipaddress | vlan]config snmp access-profile readonly [<access_profile> | none]配置snmp的只读访问列表,none 是去除config snmp access-profile readwrite [<access_profile> | none] 这是控制读写控制config snmp add trapreceiver <ip address> {port <udp_port>} community <communitystring> {from <source ip address>} 配置snmp接收host和团体字符串12.安全配置disable ip-option loose-source-routedisable ip-option strict-source-routedisable ip-option record-routedisable ip-option record-timestampdisable ipforwarding broadcastdisable udp-echo-serverdisable irdp vlan <vlan name>disable icmp redirectdisable web 关闭web方式访问交换机enable cpu-dos-protect13.Access-Lists配置create access-list icmp destination sourcecreate access-list ip destination source portscreate access-list tcp destination source portscreate access-list udp destination source ports14.默认路由配置config iproute add default <gateway>15.恢复出厂值,但不包括用户改的时间和用户帐号信息unconfig switch {all}16.检查配置show versionshow configshow sessionshow management 查看管理信息,以及snmp信息show bannershow ports configurationshow ports utilization ?show memory/show cpu-monitoringshow ospfshow access-list {<name> | port <portlist>}show access-list-monitorshow ospf area <area identifier>show ospf area detailshow ospf ase-summaryshow ospf interfaces {vlan <vlan name> | area <area identifier>} unconfigure ospf {vlan <vlan name> | area <area identifier>}switchshow switchshow configshow diagshow iparpshow iprouteshow ipstatshow logshow tech allshow version detail17.备份和升级软件download image [<hostname> | <ipaddress>] <filename> {primary | secondary}upload image [<hostname> | <ipaddress>] <filename> {primary | secondary}use image [primary | secondary]18.密码恢复。
Juniper华为H3C设备维护通用命令

Juniper华为H3C设备维护通用命令Juniper_华为_H3C设备维护常用命令1、[Router&Swithc]华为/H3C设备常规巡检命令#系统时间display clock#系统以及各单板软件版本display version#设备温度display environment#日志信息display logbuffer#单板运行状态display device#电源状态display device#风扇状态display device#CPU占用状态display cpu-usage#内存占用率display memory limit#接口流量display interface#接口、链路状态display interface#地址分配display current-configuration interface##路由扩散display current-configuration | include ospf#OSPF(Open Shortest Path First)配置display router id#路由信息display ip routing-table#端口统计数据display ip interface#当前配置文件display current-configuration#保存配置文件display saved-configuration端口使用状态display interface GigabitEthernet/T en-GigabitEthernet brief VLAN使用状态display ip interface brief2、脚本—华为display versiondis patch-informationdisplay clockdis dustproofdis frame-typedis healthdisplay cpu-usagedisplay memorydisplay memory limitdisplay devicedisplay device manuinfodisplay powerdisplay fandisplay voltagedir cfcard2:/dir cfcard:display device pic-statusdis switchover statedisplay environmentdisplay interfacedisplay logbufferdis alarmdis bootrom ethernetdisplay current-configurationdisplay current-configuration interface#display router iddisplay ip routing-tabledisplay ip interfacedisplay ip interface briefdisplay current-configurationdisplay saved-configurationdisplay diagnostic-information3、脚本—华为NE40edisplay version 查看VRP版本等信息dis patch-information 查看版本补丁display clock 查看时钟dis dustproof 防尘网信息Dis frame-type 显示NE40E机框类型dis health 显示系统资源的使用情况display cpu-usage 查看1分钟CPU利用率display memory 查看内存使用情况display memory limitdisplay device 查看母板信息display device manuinfodisplay power 查看电源状态display fan 查看风扇状态display voltage 查看板卡电压dir cfcard2:/ 查看设备crash信息dir cfcard: 查看设备cf卡信息display device pic-status 查看子卡型号,序列号(NE40E NE80E) dis switchover state 查看引擎HA情况display environmentdisplay interface 查看接口状态display logbuffer 查看日志dis alarm 查看设备告警dis bootrom ethernet 查看设备bootrom信息display current-configuration查看当前配置display current-configuration interface# 查看设备当前接口配置display router id 查看设备路由IDdisplay ip routing-table 查看设备路由display ip interface 查看设备接口情况display ip interface brief 查看设备接口状态display current-configuration 查看设备当前配置display saved-configuration 查看设备内存配置(相当show start)display diagnostic-information 抓取设备完整信息相对于show tech二、JUNIPER设备常用维护巡检命令1、脚本—JUNIPERshow system uptimeshow version detailshow chassis hardware detailshow chassis environment //显示设备的环境信息,包括温度、风扇状况、电源状况、路由引擎状况。
Juniper路由器配置命令介绍

层级子层级systemrouting-options loopbackPOSGEinterfaceprotocolISISOSPFBGPMPLS-RSVP/LDP MPLS-FRRMPBGPMPLS-VPN COS功能项set system hostname hostnameset system root-authentication plain-text-passwordset system login user lab class super-user authentication plain-text-passwordset system services telnet/ftp/name-ser dns-adds et interface lo0 description descriptionset interface lo0 unit 0 family inet address ip-addressset interface lo0 unit 0 family iso address iso-addressset interface so-slot/pic/port description descriptionset interface so-slot/pic/port mtu mtu-numberset interface so-slot/pic/port hold-time up ms down msset interface so-slot/pic/port encapsultation pppset interface so-slot/pic/port sonet-options fcs [32|16]set interface so-slot/pic/port sonet-options payload-scrambler set interface so-slot/pic/port sonet-options rfc-2615set interface so-slot/pic/port unit 0 family inet address ip-addressset interface so-slot/pic/port unit 0 family isoset interface so-slot/pic/port unit 0 family mplsset interface ge-slot/pic/port description descriptionset interface so-slot/pic/port mtu mtu-numberset interface so-slot/pic/port hold-time up ms down msset interface ge-slot/pic/port unit 0 family inet address ip-addressset interface ge-slot/pic/port unit 0 family isoset interface ge-slot/pic/port unit 0 family mplsset routing-options router-id router-idset routing-options autonomous-system as-numberset routing-options static route network/mask next-hop addressset protocols isis level [ 1 | 2 ] interfaceinterface.logical-numberset protocols isis lsp-lifetime secondsset protocols isis export export-policyset protocols isis spf-delay msset protocols isis rib-group inet rg-nameset protocols isis traffic-engineering shortcutsset protocols isis level [ 1 | 2 ] wide-metrics-onlyset protocols isis level [ 1 | 2 ] preference numberset protocols isis level [ 1 | 2 ] external-preference number set protocols isis level [ 1 | 2 ] disableset protocols isis interface interface-name lsp-interval msset protocols isis interface interface-nam level [ 1 | 2 ] metric numberset protocols isis interface interface-nam level [ 1 | 2 ]hello-interval secondsset protocols isis interface interface-nam level [ 1 | 2 ]hold-time secondsset protocols isis interface interface interface-nam passive set protocols ospf area XX interface interface.logical-number set protocols ospf interface interface.logical-number metric numberset protocols ospf interface interface interface.logical-number passivset protocols ospf traffic-engineeringset protocols bgp interface interface.logical-numberset protocols bgp group group-nameset protocols bgp group group-name type external/internalset protocols bgp group group-name peer-as 1234set protocols bgp group group-name neighbor X.X.X.Xset protocols bgp hold-time secondsset protocols bgp mtu-discoveryset protocols bgp out-delay secondsset protocols bgp log-updownset protocols bgp dampingset protocols bgp group group-name description descriptionet protocols bgp group group-name local-address group-namelocal-address addressset protocols bgp group group-name family inet anyset protocols bgp group group-name neighbor address description descriptionset interfaces interface.logical-number family mplsset protocols mpls interface.logical-numberset protocols ldp interface.logical-numberset protocols rsvp interface.logical-numberset protocols mpls label-switched-path test to 10.0.9.7set protocols mpls label-switched-path test ldp-tunnelingset protocols mpls label-switched-path test link-protectionset protocols rsvp interface so-0/0/3.0 link-protectionset protocols bgp group group-name family [inet|inet-vpn|inet6|inet6-vpn|l2vpn]set routing-instances instance-nameset routing-instances instance-name instance-type VRFset routing-instances instance-name interface interface-number set routing-instances instance-name route-distinguisher xxxx set routing-instances instance-name vrf-target target:xxxx:yyyy set routing-instances instance-name routing-options static route x.x.x.x/z next-hop x.x.x.xset routing-instances instance-name protocols ospf area XX interface interface-name.logical-numberset routing-instances instance-name protocols ospf export bgp-ospfset policy-options policy-statement bgp-ospf term 1 from protocol bgpset policy-options policy-statement bgp-ospf term 1 then accept命令解释备注配置设备名必选为root帐户设置密码新建用户名为lab的帐户,并设定密码配置路由器Telnet/ftp/dns服务配置端口描述配置IP地址配置ISO地址配置端口描述配置端口MTU配置端口up/down的damping时间配置端口封装为PPP配置端口FCS的位数配置端口打开payload-scrambler配置端口FCS 32,打开payload-scrambler,C2字节为0x16配置IP地址端口允许运行ISIS端口允许运行mpls配置端口描述配置端口MTU配置端口up/down的damping时间配置IP地址端口允许运行ISIS端口允许运行mpls配置路由器Router-ID配置路由器的AS号码配置静态路由配置聚合路由配置ISIS接口并将接口加入到相应的ISIS LEVEL里必选配置IS-IS的存活时间,LSP的refresh 时间为lsp-lifetime-317秒配置IS-IS的路由分发策略配置IS-IS的SPF的延迟配置IS-IS使用的路由组配置IS-IS使用TE的shortcuts配置IS-IS的Level使用wide-metric---支持TE必选配置IS-IS内部路由的管理距离配置IS-IS外部路由的管理距离配置IS-IS禁止运行Leve 1或者2配置IS-IS端口发送LSP的间隔配置IS-IS端口的Metric值配置IS-IS端口的IIH的间隔时间配置IS-IS端口的Hold时间配置IS-IS端口运行Passive模式配置OSPF接口并将接口加入到相应的OSPF AREA里必选配置OSPF端口的Metric值配置OSPF端口运行Passive模式配置OSPF支持流量工程(启用OPAQUE LSA)配置o spf端口的IIH的间隔时间配置BGP接口必选配置BGP组必选设定BGP组为EBGP或IBGP必选设定本组内的neighbor的AS号码必选设定本组内neighbor的session IP地址必选配置BGP的Hold-timer时间,Hello时间自动调整为Hold-time的1/3配置BGP的TCP进程的MSS为路径的最大值配置BGP的的路由发送延迟配置路由器纪录BGP的邻居up/down的变化配置BGP路由启用Damping算法配置BGP的组的描述配置和BGP的组内的邻居进行通讯的时候使用的本地地址配置BGP的Group内的邻居允许运行unicast 和multicast配置BGP的邻居的描述端口允许运行mpls配置将接口加到MPLS协议组里配置将接口加到LDP协议组里配置将接口加到rsvp协议组里配置名称为test的RSVP signaled LSP, 此LSP终结点为10.0.9.7在LDP TUNNEL的路由器上配置名称为test的RSVPsignaled, LSP使得LDP能够穿越RSVP LSP启用保护的LSP保护选项在RSVP协议里,启用保护选项配置本group下的BGP session的属性,inet是启用IP路由支持,此项为默认启用,inet-vpn是启用l3mbgp-vpn路由支持,启用任意非INET属性,会将inet禁用配置routing-instances配置routing-instances的VRF将逻辑接口加入到routing-instances里配置RD,确认RD在整个routing-instance里是唯一的配置RT,确认RT在整个routing-instance里是唯一的,并且同一个routing-instance里的多个PE上RT要相同配置PE-CE之间的静态路由,这里要注意,在PE-CE之间为以太网连接的情况下,一定要加一个特定的静态路由,目的地址为PE-CE之间的互联的IP子网,下一跳地址为对端CE的接口IP地址配置PE-CE之间的OSPF路由,这里要注意,一定要加一个特定的POLICY,目的是为了将从对端PE学到的VPN路由注入PE-CE之间运行的OSPF协议,使得两端的CE互相能学到对方的路由。
Juniper路由器配置命令介绍

Juniper路由器配置命令介绍Juniper路由器配置命令介绍⒈系统配置命令⑴ `set system hostname`:设置设备的主机名。
⑵ `set system domn-name`:设置设备的域名。
⑶ `set system login user`:设置设备的登录用户信息。
⒉接口配置命令⑴ `set interfaces interface-name unit logical-unit-number family inet address ip-address/subnet-mask`:配置接口的IP地址和子网掩码。
⑵ `set interfaces interface-name unit logical-unit-number family inet6 address ipv6-address/prefix-length`:配置接口的IPv6地址和前缀长度。
⑶ `set interfaces interface-name unit logical-unit-number vlan-id vlan-tagged`:配置接口的VLAN标签。
⒊路由配置命令⑴ `set routing-options static route destination next-hop`:配置静态路由。
⑵ `set protocols ospf area area-id`:配置OSPF路由协议。
⒋安全配置命令⑴ `set security zones security-zone zone-nameinterfaces interface-name`:将接口分配给安全区域。
⑵ `set security policies from-zone source-zone to-zone destination-zone policy policy-name then permit`:配置安全策略以允许数据流动。
⒌ VPN配置命令⑴ `set security ike proposal proposal-name authentication-method pre-shared-keys`:配置IKE提议的预共享密钥认证方法。
Juniper基础配置命令
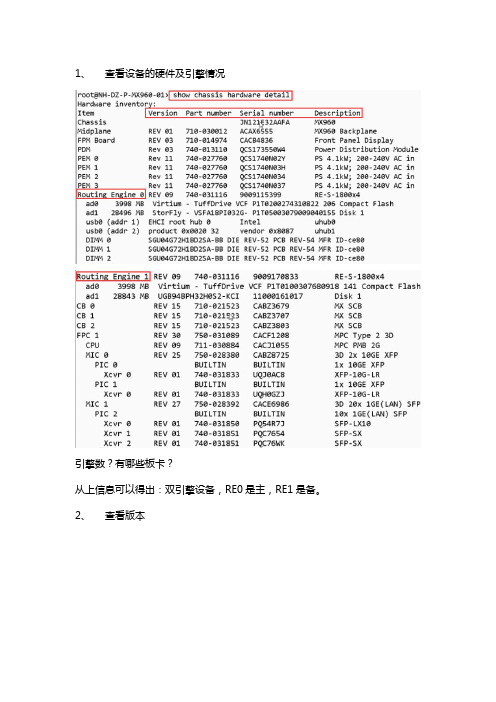
1、查看设备的硬件及引擎情况引擎数?有哪些板卡?从上信息可以得出:双引擎设备,RE0是主,RE1是备。
2、查看版本从上可看出:re0的版本是【12.3R4.6】re1的版本是【12.3R4.6】3、引擎切换4、查看当前引擎运行状态设备配置管理Juniper的配置存在2个地方:第一个:其中,juniper.conf.gz是当前的配置第二个:可以查看文件的实际配置内容:查看全局配置:或查看接口查看接口匹配信息查看路由协议信息或查看系统方面的信息查看之前的历史配置信息查看运行的文件回滚载入之前的某一个配置文件批量导入配置命令:带外管理口配置:set groups re0 interfaces fxp0 unit 0 family inet address 172.18.18.30/24set system time-zone Asia/Shanghaiset system root-authentication encrypted-password "$5$hmy2W7ar$TR/KP7qIckZ37QbfzSKJWpFW1QS70m1zAPQCsK4jth0" set system login user lab uid 2000set system login user lab class super-userset system login user lab authentication encrypted-password "$5$.Us1Dtb0$dIi5e/6/xp3IAUS/EXkntfTk3fDqESpZBNBLxrWVLHB"set system services ftpset system services sshset system services telnetset system syslog user * any emergencyset system syslog file messages any noticeset system syslog file messages authorization infoset system syslog file interactive-commands interactive-commands anyset logical-systems vr101set logical-systems vr102set interfaces ge-2/0/0 description link_to_Serv1set interfaces ge-2/0/0 unit 0 family inet address 11.1.1.1/24 deactivate interfaces ge-2/0/0 unit 0set interfaces ge-2/0/1 description link_to_Serv2set interfaces ge-2/0/1 unit 0 family inet address 11.1.2.1/24 deactivate interfaces ge-2/0/1 unit 0set routing-options static route 172.0.0.0/8 next-hop 172.18.18.254set routing-options static route 10.0.0.0/8 next-hop 172.18.18.254show configuration | display set |match traceoptionshow bgp summaryshow configuration | display set | match 100.125.154.9set protocols bgp group HZ-OOB2IN75 neighbor 100.125.154.9 export rpFW-ADCN2FW-POPshow bgp neighborshow route forwarding-tableshow configuration interfacesshow configuration policy-optionsshow configuration interfaces gr-0/0/0show configuration protocols bgpping 100.125.154.126 count 100ping 14.143.27.242 rapid count 300show configuration | display set | compare rollback 5 show version detail no-forwardingshow system core-dumps no-forwardingshow chassis alarms no-forwardingshow chassis hardware detail no-forwarding show system processes extensive no-forwarding show pfe statistics errorshow pfe statistics trafficshow chassis routing-engine no-forwarding show chassis environment no-forwarding show chassis firmware no-forwardingshow chassis fpc detailshow system boot-messages no-forwarding show system storage no-forwardingshow system virtual-memory no-forwardingshow system buffer no-forwardingshow system queues no-forwardingshow system statistics no-forwardingshow configuration | except SECRET-DATA | display omit show interfaces extensive no-forwardingshow network-access aaa statistics accountingshow route forwarding-table summaryshow ppp statistics extensiveshow accounting server statisticsshow system resource-monitor summaryshow shm-ipc statisticsshow interfaces diagnostics optics et-0/1/1。
juniper 配置命令

set dynamic-profiles vlan interfaces "$junos-interface-ifd-name" unit "$junos-interfaceunit" no-traps set dynamic-profiles vlan interfaces "$junos-interface-ifd-name" unit "$junos-interfaceunit" vlan-id "$junos-vlan-id" set dynamic-profiles vlan interfaces "$junos-interface-ifd-name" unit "$junos-interfaceunit" family inet policer disable-arp-policer set dynamic-profiles vlan interfaces "$junos-interface-ifd-name" unit "$junos-interfaceunit" family inet6 unnumbered-address lo0.0 set system commit synchronize set system dynamic-profile-options versioning set chassis network-services enhanced-ip set dynamic-profiles pppoe predefined-variable-defaults input-filter 10M set dynamic-profiles pppoe predefined-variable-defaults output-filter 10M set access profile sunrise-test authentication-order none set access profile none authentication-order none set access profile sunrise-test accounting order none set system commit synchronize run request routing-engine login re0 进入低层 可以开ftp 纯交换模式 当交换机用 ssh { + + + root-login deny; protocol-version v2;
juniper命令注解

juniper命令注解netscreen 设备管理配置netscreen 设备管理配置8实例分析:NETSCREEN 现有配置1.1时间设定set clock dst-off /自动调整时间关set clock ntp /设置NTP时间同步set clock timezone 9 /设置时区set vrouter trust-vr sharable /设置虑拟路由器trust-vr可以为其他VSYS系统共享1.2路由导出及自定义服务设定unset vrouter "trust-vr" auto-route-export /禁止路由器trust-vr的路由自动导出set service "CVS" protocol tcp src-port 0-65535 dst-port 2401-2401/自定义CVS服务协议为TCP 源端口为0-65535 目地端口为24011.3认证的设定set auth-server "Local" id 0 /设置认证SERVER为本地认证set auth-server "Local" server-name "Local" /设置本地认证SERVER名为LOCAL set auth default auth server "Local" /设置默认认证服务器为LOCAL1.4管理员的设定set admin name "netscreen" /设置管理员用户名set admin password "XXXXXX" /设置管理员密码set admin user "livedoorcn" password "XXXXXXX" privilege "all"/添加管理员用户livedoorcn及其权限为R-W1.5管理IP的设定set admin manager-ip xxx.174.65.0 255.255.255.0 /设置管理IPset admin manager-ip 10.0.71.136 255.255.255.255 /设置管理IPset admin manager-ip xxx.xxx.xxx.141 255.255.255.192 /设置管理IPset admin manager-ip xxx.xxx.xxx.246 255.255.255.255 /设置管理IPset admin manager-ip 10.0.71.139 255.255.255.255 /设置管理IPset admin manager-ip xxx.xxx.xxx.0 255.255.255.0 /设置管理IP1.6SSH及区域设定set admin scs password disable username netscreen /禁止用户的SSH密码认证set admin scs password disable username livedoorcn /禁止用户的SSH密码认证set admin auth timeout 10 /设置认证时间超时set admin auth server "Local" /设置管理认证服务器set zone "Trust" vrouter "trust-vr" /设置信任区域set zone "Untrust" vrouter "trust-vr" /设置非信任区域set zone "VLAN" vrouter "trust-vr" /设置VLAN区域set zone "Trust" tcp-rst /设置TRUST安全区超时回应RESET信息set zone "Untrust" block /封锁同一安全区中主机之间的信息流unset zone "Untrust" tcp-rst /设置UNTRUST安全区超时不回应RESET信息set zone "MGT" block /封锁同一安全区中主机之间的信息流set zone "VLAN" block /封锁同一安全区中主机之间的信息流set zone "VLAN" tcp-rst /设置TRUST安全区超时回应RESET信息1.7网络攻击保护选项的设定set zone "Trust" screen alarm-without-drop /设置告警但并不丢弃数据包set zone "Trust" screen icmp-flood /设置ICMP泛洪攻击保护set zone "Trust" screen udp-flood /设置UDP泛洪攻击保护set zone "Trust" screen winnuke /设置winnuke攻击保护set zone "Trust" screen port-scan /设置端口扫描攻击保护set zone "Trust" screen ip-sweep /设置IP地址扫描攻击保护set zone "Trust" screen tear-drop /设置tear-drop攻击保护set zone "Trust" screen syn-flood /设置SYN 泛滥攻击保护(DOS)set zone "Trust" screen ip-spoofing /设置IP欺骗攻击保护set zone "Trust" screen ping-death /设置PING-DEATH攻击保护set zone "Trust" screen ip-filter-src /设置禁示使用松散源路由或严格源路由选项set zone "Trust" screen land /设置陆地攻击保护set zone "Trust" screen tcp-no-flag /设置TCP无标志保护set zone "Trust" screen unknown-protocol /设置未知协议保护set zone "Trust" screen ip-bad-option /设置BAD选项保护set zone "Trust" screen ip-record-route /设置记录路由保护set zone "Trust" screen ip-timestamp-opt /设置时间戳保护set zone "Trust" screen ip-security-opt /设置IP安全选项保护(已不用)set zone "Trust" screen ip-loose-src-route /设置松散源路由(记录)set zone "Trust" screen ip-strict-src-route /设置严格源路由(记录)set zone "Trust" screen ip-stream-opt /设置IP选项流ID(费弃选项)set zone "Trust" screen icmp-large /设置icmp大包保护set zone "Trust" screen syn-fin /设置操作系统set zone "Trust" screen fin-no-ack /设置FIN但无ACK标志保护set zone "Trust" screen limit-session source-ip-based /设置源IP会话限制set zone "Trust" screen syn-ack-ack-proxy /设置同步代理泛滥保护set zone "Trust" screen block-frag /设置IP封包的碎片保护set zone "Trust" screen limit-session destination-ip-based /设置目的IP会话限制set zone "Untrust" screen tear-dropset zone "Untrust" screen syn-floodset zone "Untrust" screen ping-deathset zone "Untrust" screen ip-filter-srcset zone "Untrust" screen landset zone "V1-Untrust" screen tear-dropset zone "V1-Untrust" screen syn-floodset zone "V1-Untrust" screen ping-deathset zone "V1-Untrust" screen ip-filter-srcset zone "V1-Untrust" screen landset zone "Trust" screen limit-session destination-ip-based 1280 /设置目的IP会话限制1.8接口的设定set interface "trust" zone "Trust" /将接口trust绑定到trust安全区域set interface "untrust" zone "Untrust" /将接口untrust绑定到untrust安本区域unset interface vlan1 ip /没有设定VLAN IP地址set interface trust ip 10.0.71.1/24 /设置trust接口IP地址set interface trust nat /设置trust接口工作模式set interface untrust ip xxx.xxx.xxx.131/26 /设置untrust接口IP地址set interface untrust route /设置untrust接口工作模式set interface untrust gateway xxx.xxx.xxx.129 /设置untrust接口网关unset interface vlan1 bypass-others-ipsec /阻止NetScreen 设备通过IPSec信息流unset interface vlan1 bypass-non-ip /阻止所有非IP和非ARP 单点传送信息流set interface trust ip manageable /设置trust接口为可管理接口set interface untrust ip manageable /设置untrust接口为可管理接口set interface untrust manage ping /允许untrust接口PINGset interface untrust manage ssh /允许untrust接口可以SSH 管理set interface untrust manage web /允许untrust接口可以WEB 管理1.9MIP地址映射的设定set interface "untrust" mip xxx.xxx.xxx.135 host 10.0.71.135 netmask 255.255.255.255 vrouter "trust-vr" /设置MIP映射地址以下类同:set interface "untrust" mip xxx.xxx.xxx.133 host 10.0.71.133 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.134 host 10.0.71.134 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.136 host 10.0.71.136 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.139 host 10.0.71.139 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.140 host 10.0.71.140 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.132 host 10.0.71.132 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.142 host 10.0.71.142 netmask 255.255.255.255 vrouter "trust-vr"set interface "untrust" mip xxx.xxx.xxx.143 host 10.0.71.143 netmask 255.255.255.255 vrouter "trust-vr"。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Juniper 防火墙的策略配置
• 在Juniper设备中策略是一个重点,因为安全设备基本上都是基于策略的管理和运行,下面就Juniper的如何配置进行 简单的说明. 在Juniper防火墙中,区域是一个比较重要的感念,一般的Juniper设备都设置了Untrust,Trust和DMZ三个区域,也可 以根据实际的需要自行定义区域,比如电信行业经常的BOSS,OA区域。 具体的使用命令: netscreenisg1000->set zone id 1000 "boss" netscreenisg1000->set zone id 1001 "oa" 然后使用命令讲相关的防火墙接口加入Zone中,具体的命令:netscreenisg1000-> set interface "ethernet2/4" zone "boss" netscreenisg1000-> set interface "ethernet2/5" zone "oa" 并且在接口上配置相关的IP地址: netscreeenisg1000-> set interface ethernet2/4 ip 10.10.161.14/25 set interface ethernet2/4 route set interface ethernet2/5 ip 192.168.19.126/28 set interface ethernet2/5 nat 然后就是需要建立MIP/VIP. 比如需要建立一个MIP,私网地址10.10.81.54,公网地址10.10.161.54, 图形界面使用比较简单,比如ethernet1/1 是一个untrust区域的接口地址。 netscreeenisg1000->set policy id 22 from "Untrust" to "Trust" "Any" "MIP(10.10.161.31)" "ANY" permit log netscreeenisg1000->set policy id 19 from "Untrust" to "Trust" "Any" "MIP(10.10.161.105)" "HTTP" permit log 关于policy就写这么多,关于MIP的是使用后面会继续手写。
•
• • • •er 防火墙的管理
• 在实际的网络工程中,Juniper的防火墙产品被大量的应用在网络环境中。但是Juniper防火墙产品的配置也是大家比 较陌生的,下面就通过Juniper防火墙的使用来说明如何配置。 本次介绍的Juniper防火墙产品全部是在Juniper netscreen-ISG1000和Juniper netscreen-ISG2000中实现的.其中 Juniper netscreen-ISG1000的版本Software Version: 5.0.0r10a.4, Type: Firewall+VPN.Juniper netscreen-ISG2000 的版本Software Version: 6.0.0r4.0, Type: Firewall+VPN 1 Juniper防火墙产品的管理 对于防火墙产品的管理和配置主要有以下几个方法: (1)console 方式 Juniper防火墙和Cisco的路由器和防火墙之类的一样,初次配置需要使用console线缆进行配置,具体的参数设置和 Cisco的路由器和防火墙一致。在这里就具体的不说了。 (2)telnet或者ssh 对于使用telnet或者ssh进行管理Juniper防火墙,首先必须配置管理地址并且启用telnet或者ssh服务。在Juniper netscreen-ISG1000中默认的管理地址192.168.1.1,就可以使用telnet或者ssh工具进行远程管理。具体的使用命令 set interface ethernet1/1 manage telnet set interface ethernet1/1 manage ssh 比如;telnet 192.168.1.1 在Juniper netscreen-ISG2000中的默认地址为172.16.70.1/24 ,建议使用命令行进行修改。 set interface mgt ip 192.168.1.1/24 set interface mgt manage telnet, set interface mgt manage ssh, set interface mgt manage web (3)web方式管理 web方式管理和使用telnet或者ssh一样,首先要配置管理地址和启用web服务。 具体的命令为: set interface ethernet1/1 ip 192.168.193.33/28 set interface ethernet1/1 manage web 然后使用http://192.168.193.33来进行管理。
•
Juniper 防火墙常见命令
• Interfaces in vsys Root: Name IP Address Zone MAC VLAN State VSD mgt 172.16.70.1/24 MGT 001b.c06a.1080 - D eth1/1 192.168.19.33/28 Trust 0010.dbff.c070 - U 0 eth1/2 192.168.19.65/28 Trust 0010.dbff.c080 - U 0 eth1/3 192.168.19.49/28 Trust 0010.dbff.c090 (3) get arp netscreenisg2000-> get arp usage: 9/8192 miss: 0 always-on-dest: disabled ----------------------------------------------------------------------------------------IP Mac VR/Interface State Age Retry PakQue Sess_cnt ----------------------------------------------------------------------------------------192.168.19.161 002255e5c490 trust-vr/eth1/4 VLD 762 0 0 1373 192.168.19.46 000fe265a846 trust-vr/eth1/1 VLD 1167 0 0 56 192.168.19.62 00127fa7e351 trust-vr/eth1/3 VLD 761 0 0 395 192.168.19.30 00000c07ac02 trust-vr/red1 VLD 964 0 0 (4)get mip netscreenisg2000-> get mip Total MIPs under Root configured:78 Max:20000. -------------------------------------------------------------------------------Map IP Host IP Interface VRouter -------------------------------------------------------------------------------219.14.172.6/32 192.168.4.3 ethernet1/5 trust-vr 219.14.172.7/32 192.168.2.80 ethernet1/5 trust-vr 219.14.172.71/32 192.168.12.23 ethernet1/5 trust-vr 219.14.172.72/32 192.168.2.101 ethernet1/5 trust-vr (5)get vip netscreeisg2000-> get vip Virtual IP Interface Port Service Server/Port 219.23.178.10 ethernet3/3 9080 9080 192.168.4.5/9080(OK) 219.23.17.10 ethernet3/3 22 SSH 192.168.4.145/22(OK)
•
• •
• •
Juniper 防火墙常见命令
• 常见的命令 (1)get system netscreenisg2000-> get system Product Name: NetScreen-2000 Serial Number: XXXXXXXX, Control Number: 00000000 Hardware Version: 3010(0)-(04), FPGA checksum: 00000000, VLAN1 IP (0.0.0.0) Software Version: 6.0.0r4.0, Type: Firewall+VPN OS Loader Version: 1.1.5 Compiled by build_master at: Fri Jan 11 14:27:42 PST 2008 Base Mac: 001b.c06a.1080 File Name: default (nsISG2000.6.0.0r4.0), Checksum: 1e5d880f , Total Memory: 2048MB Date 06/04/2009 08:28:24, Daylight Saving Time disabled The Network Time Protocol is Disabled Up 805 hours 29 minutes 18 seconds Since 01May2009:18:59:06 Total Device Resets: 0 (2) get interface netscreenisg2000-> get interface A - Active, I - Inactive, U - Up, D - Down, R - Ready
