Mapping Functions and Data Redistribution for Parallel Files
Process Mapping Traing

FMEA Training
6
Building a Process Map
What is a work process?
INPUT
PROCESS
OUTPUT
Transformation (Value-Added) Steps
FMEA Training
7
Building a Process Map
Process Scope
True
FMEA Training
3
Example of a Process Map
Sales
Customer places order
Typical Order Fulfillment Process
Order Entry
Warehousing
Transportation
Is order Yes Send order to
understandings Enables rigorous, thorough examination of the
outputs and inputs
Increases probability of capturing all the y’s and x’s Increases probability of getting to y = f(x). Identification of outputs needing measurement studies
• Identify Major Inputs and Customer Outputs for the Suspect Process
• Identify Possible Connections
FMEA Training
3.1Theconceptsoffunction(函数的基本概念)3.2解读

F1,F2 are functions from A to B ,F3 (F4 ) is not
a function from A to B .
计算机科学与技术学院
第三章 Functions ( 函数) 【Example2】 Determine whether the relation
is a function.
, f({x})={f(x)}(x∈A)
计算机科学与技术学院
第三章 Functions ( 函数)
For the image we have Theorem 3.1.1 Let f : A→B. For any X A ,Y
A,we have
(1)f(X∪Y)=f(X)∪f(Y)
f(X)∩f(Y) (3)f(X)-f(Y) f(X-Y) (2)f(X∩Y)
计算机科学与技术学院
第三章 Functions ( 函数)
a 1
b
2 3
c 4 d
5
Graph 3.1.3
计算机科学与技术学院
第三章 Functions ( 函数)
由于函数归结为关系,因而函数的
表示及运算可归结为集合的表示及运算,
函数的相等的概念、包含概念,也便归
结为关系相等的概念及包含概念。
计算机科学与技术学院
from ρ1, ρ2, they have two properties as follows:
(1) The domain of ρ3(ρ4,ρ5 ,ρ6 ) is the set A; (2) For an element x∈A , there exists a unique y∈B such that 〈x, y〉∈ρ3(ρ4,ρ5 ,ρ6 ) .
人工智能领域中英文专有名词汇总
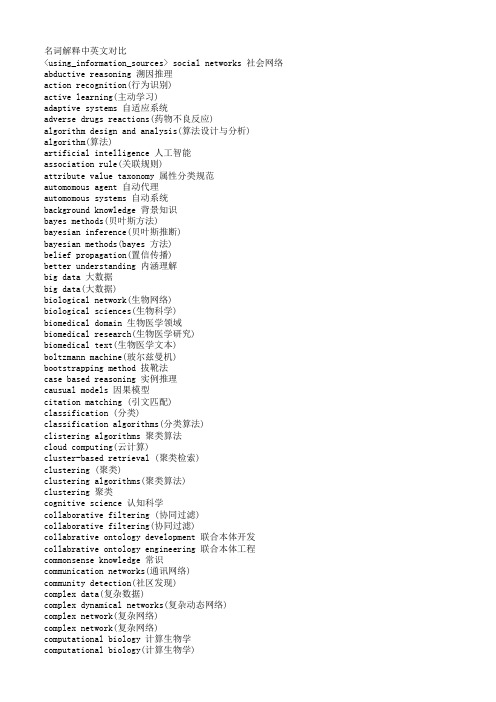
名词解释中英文对比<using_information_sources> social networks 社会网络abductive reasoning 溯因推理action recognition(行为识别)active learning(主动学习)adaptive systems 自适应系统adverse drugs reactions(药物不良反应)algorithm design and analysis(算法设计与分析) algorithm(算法)artificial intelligence 人工智能association rule(关联规则)attribute value taxonomy 属性分类规范automomous agent 自动代理automomous systems 自动系统background knowledge 背景知识bayes methods(贝叶斯方法)bayesian inference(贝叶斯推断)bayesian methods(bayes 方法)belief propagation(置信传播)better understanding 内涵理解big data 大数据big data(大数据)biological network(生物网络)biological sciences(生物科学)biomedical domain 生物医学领域biomedical research(生物医学研究)biomedical text(生物医学文本)boltzmann machine(玻尔兹曼机)bootstrapping method 拔靴法case based reasoning 实例推理causual models 因果模型citation matching (引文匹配)classification (分类)classification algorithms(分类算法)clistering algorithms 聚类算法cloud computing(云计算)cluster-based retrieval (聚类检索)clustering (聚类)clustering algorithms(聚类算法)clustering 聚类cognitive science 认知科学collaborative filtering (协同过滤)collaborative filtering(协同过滤)collabrative ontology development 联合本体开发collabrative ontology engineering 联合本体工程commonsense knowledge 常识communication networks(通讯网络)community detection(社区发现)complex data(复杂数据)complex dynamical networks(复杂动态网络)complex network(复杂网络)complex network(复杂网络)computational biology 计算生物学computational biology(计算生物学)computational complexity(计算复杂性) computational intelligence 智能计算computational modeling(计算模型)computer animation(计算机动画)computer networks(计算机网络)computer science 计算机科学concept clustering 概念聚类concept formation 概念形成concept learning 概念学习concept map 概念图concept model 概念模型concept modelling 概念模型conceptual model 概念模型conditional random field(条件随机场模型) conjunctive quries 合取查询constrained least squares (约束最小二乘) convex programming(凸规划)convolutional neural networks(卷积神经网络) customer relationship management(客户关系管理) data analysis(数据分析)data analysis(数据分析)data center(数据中心)data clustering (数据聚类)data compression(数据压缩)data envelopment analysis (数据包络分析)data fusion 数据融合data generation(数据生成)data handling(数据处理)data hierarchy (数据层次)data integration(数据整合)data integrity 数据完整性data intensive computing(数据密集型计算)data management 数据管理data management(数据管理)data management(数据管理)data miningdata mining 数据挖掘data model 数据模型data models(数据模型)data partitioning 数据划分data point(数据点)data privacy(数据隐私)data security(数据安全)data stream(数据流)data streams(数据流)data structure( 数据结构)data structure(数据结构)data visualisation(数据可视化)data visualization 数据可视化data visualization(数据可视化)data warehouse(数据仓库)data warehouses(数据仓库)data warehousing(数据仓库)database management systems(数据库管理系统)database management(数据库管理)date interlinking 日期互联date linking 日期链接Decision analysis(决策分析)decision maker 决策者decision making (决策)decision models 决策模型decision models 决策模型decision rule 决策规则decision support system 决策支持系统decision support systems (决策支持系统) decision tree(决策树)decission tree 决策树deep belief network(深度信念网络)deep learning(深度学习)defult reasoning 默认推理density estimation(密度估计)design methodology 设计方法论dimension reduction(降维) dimensionality reduction(降维)directed graph(有向图)disaster management 灾害管理disastrous event(灾难性事件)discovery(知识发现)dissimilarity (相异性)distributed databases 分布式数据库distributed databases(分布式数据库) distributed query 分布式查询document clustering (文档聚类)domain experts 领域专家domain knowledge 领域知识domain specific language 领域专用语言dynamic databases(动态数据库)dynamic logic 动态逻辑dynamic network(动态网络)dynamic system(动态系统)earth mover's distance(EMD 距离) education 教育efficient algorithm(有效算法)electric commerce 电子商务electronic health records(电子健康档案) entity disambiguation 实体消歧entity recognition 实体识别entity recognition(实体识别)entity resolution 实体解析event detection 事件检测event detection(事件检测)event extraction 事件抽取event identificaton 事件识别exhaustive indexing 完整索引expert system 专家系统expert systems(专家系统)explanation based learning 解释学习factor graph(因子图)feature extraction 特征提取feature extraction(特征提取)feature extraction(特征提取)feature selection (特征选择)feature selection 特征选择feature selection(特征选择)feature space 特征空间first order logic 一阶逻辑formal logic 形式逻辑formal meaning prepresentation 形式意义表示formal semantics 形式语义formal specification 形式描述frame based system 框为本的系统frequent itemsets(频繁项目集)frequent pattern(频繁模式)fuzzy clustering (模糊聚类)fuzzy clustering (模糊聚类)fuzzy clustering (模糊聚类)fuzzy data mining(模糊数据挖掘)fuzzy logic 模糊逻辑fuzzy set theory(模糊集合论)fuzzy set(模糊集)fuzzy sets 模糊集合fuzzy systems 模糊系统gaussian processes(高斯过程)gene expression data 基因表达数据gene expression(基因表达)generative model(生成模型)generative model(生成模型)genetic algorithm 遗传算法genome wide association study(全基因组关联分析) graph classification(图分类)graph classification(图分类)graph clustering(图聚类)graph data(图数据)graph data(图形数据)graph database 图数据库graph database(图数据库)graph mining(图挖掘)graph mining(图挖掘)graph partitioning 图划分graph query 图查询graph structure(图结构)graph theory(图论)graph theory(图论)graph theory(图论)graph theroy 图论graph visualization(图形可视化)graphical user interface 图形用户界面graphical user interfaces(图形用户界面)health care 卫生保健health care(卫生保健)heterogeneous data source 异构数据源heterogeneous data(异构数据)heterogeneous database 异构数据库heterogeneous information network(异构信息网络) heterogeneous network(异构网络)heterogenous ontology 异构本体heuristic rule 启发式规则hidden markov model(隐马尔可夫模型)hidden markov model(隐马尔可夫模型)hidden markov models(隐马尔可夫模型) hierarchical clustering (层次聚类) homogeneous network(同构网络)human centered computing 人机交互技术human computer interaction 人机交互human interaction 人机交互human robot interaction 人机交互image classification(图像分类)image clustering (图像聚类)image mining( 图像挖掘)image reconstruction(图像重建)image retrieval (图像检索)image segmentation(图像分割)inconsistent ontology 本体不一致incremental learning(增量学习)inductive learning (归纳学习)inference mechanisms 推理机制inference mechanisms(推理机制)inference rule 推理规则information cascades(信息追随)information diffusion(信息扩散)information extraction 信息提取information filtering(信息过滤)information filtering(信息过滤)information integration(信息集成)information network analysis(信息网络分析) information network mining(信息网络挖掘) information network(信息网络)information processing 信息处理information processing 信息处理information resource management (信息资源管理) information retrieval models(信息检索模型) information retrieval 信息检索information retrieval(信息检索)information retrieval(信息检索)information science 情报科学information sources 信息源information system( 信息系统)information system(信息系统)information technology(信息技术)information visualization(信息可视化)instance matching 实例匹配intelligent assistant 智能辅助intelligent systems 智能系统interaction network(交互网络)interactive visualization(交互式可视化)kernel function(核函数)kernel operator (核算子)keyword search(关键字检索)knowledege reuse 知识再利用knowledgeknowledgeknowledge acquisitionknowledge base 知识库knowledge based system 知识系统knowledge building 知识建构knowledge capture 知识获取knowledge construction 知识建构knowledge discovery(知识发现)knowledge extraction 知识提取knowledge fusion 知识融合knowledge integrationknowledge management systems 知识管理系统knowledge management 知识管理knowledge management(知识管理)knowledge model 知识模型knowledge reasoningknowledge representationknowledge representation(知识表达) knowledge sharing 知识共享knowledge storageknowledge technology 知识技术knowledge verification 知识验证language model(语言模型)language modeling approach(语言模型方法) large graph(大图)large graph(大图)learning(无监督学习)life science 生命科学linear programming(线性规划)link analysis (链接分析)link prediction(链接预测)link prediction(链接预测)link prediction(链接预测)linked data(关联数据)location based service(基于位置的服务) loclation based services(基于位置的服务) logic programming 逻辑编程logical implication 逻辑蕴涵logistic regression(logistic 回归)machine learning 机器学习machine translation(机器翻译)management system(管理系统)management( 知识管理)manifold learning(流形学习)markov chains 马尔可夫链markov processes(马尔可夫过程)matching function 匹配函数matrix decomposition(矩阵分解)matrix decomposition(矩阵分解)maximum likelihood estimation(最大似然估计)medical research(医学研究)mixture of gaussians(混合高斯模型)mobile computing(移动计算)multi agnet systems 多智能体系统multiagent systems 多智能体系统multimedia 多媒体natural language processing 自然语言处理natural language processing(自然语言处理) nearest neighbor (近邻)network analysis( 网络分析)network analysis(网络分析)network analysis(网络分析)network formation(组网)network structure(网络结构)network theory(网络理论)network topology(网络拓扑)network visualization(网络可视化)neural network(神经网络)neural networks (神经网络)neural networks(神经网络)nonlinear dynamics(非线性动力学)nonmonotonic reasoning 非单调推理nonnegative matrix factorization (非负矩阵分解) nonnegative matrix factorization(非负矩阵分解) object detection(目标检测)object oriented 面向对象object recognition(目标识别)object recognition(目标识别)online community(网络社区)online social network(在线社交网络)online social networks(在线社交网络)ontology alignment 本体映射ontology development 本体开发ontology engineering 本体工程ontology evolution 本体演化ontology extraction 本体抽取ontology interoperablity 互用性本体ontology language 本体语言ontology mapping 本体映射ontology matching 本体匹配ontology versioning 本体版本ontology 本体论open government data 政府公开数据opinion analysis(舆情分析)opinion mining(意见挖掘)opinion mining(意见挖掘)outlier detection(孤立点检测)parallel processing(并行处理)patient care(病人医疗护理)pattern classification(模式分类)pattern matching(模式匹配)pattern mining(模式挖掘)pattern recognition 模式识别pattern recognition(模式识别)pattern recognition(模式识别)personal data(个人数据)prediction algorithms(预测算法)predictive model 预测模型predictive models(预测模型)privacy preservation(隐私保护)probabilistic logic(概率逻辑)probabilistic logic(概率逻辑)probabilistic model(概率模型)probabilistic model(概率模型)probability distribution(概率分布)probability distribution(概率分布)project management(项目管理)pruning technique(修剪技术)quality management 质量管理query expansion(查询扩展)query language 查询语言query language(查询语言)query processing(查询处理)query rewrite 查询重写question answering system 问答系统random forest(随机森林)random graph(随机图)random processes(随机过程)random walk(随机游走)range query(范围查询)RDF database 资源描述框架数据库RDF query 资源描述框架查询RDF repository 资源描述框架存储库RDF storge 资源描述框架存储real time(实时)recommender system(推荐系统)recommender system(推荐系统)recommender systems 推荐系统recommender systems(推荐系统)record linkage 记录链接recurrent neural network(递归神经网络) regression(回归)reinforcement learning 强化学习reinforcement learning(强化学习)relation extraction 关系抽取relational database 关系数据库relational learning 关系学习relevance feedback (相关反馈)resource description framework 资源描述框架restricted boltzmann machines(受限玻尔兹曼机) retrieval models(检索模型)rough set theroy 粗糙集理论rough set 粗糙集rule based system 基于规则系统rule based 基于规则rule induction (规则归纳)rule learning (规则学习)rule learning 规则学习schema mapping 模式映射schema matching 模式匹配scientific domain 科学域search problems(搜索问题)semantic (web) technology 语义技术semantic analysis 语义分析semantic annotation 语义标注semantic computing 语义计算semantic integration 语义集成semantic interpretation 语义解释semantic model 语义模型semantic network 语义网络semantic relatedness 语义相关性semantic relation learning 语义关系学习semantic search 语义检索semantic similarity 语义相似度semantic similarity(语义相似度)semantic web rule language 语义网规则语言semantic web 语义网semantic web(语义网)semantic workflow 语义工作流semi supervised learning(半监督学习)sensor data(传感器数据)sensor networks(传感器网络)sentiment analysis(情感分析)sentiment analysis(情感分析)sequential pattern(序列模式)service oriented architecture 面向服务的体系结构shortest path(最短路径)similar kernel function(相似核函数)similarity measure(相似性度量)similarity relationship (相似关系)similarity search(相似搜索)similarity(相似性)situation aware 情境感知social behavior(社交行为)social influence(社会影响)social interaction(社交互动)social interaction(社交互动)social learning(社会学习)social life networks(社交生活网络)social machine 社交机器social media(社交媒体)social media(社交媒体)social media(社交媒体)social network analysis 社会网络分析social network analysis(社交网络分析)social network(社交网络)social network(社交网络)social science(社会科学)social tagging system(社交标签系统)social tagging(社交标签)social web(社交网页)sparse coding(稀疏编码)sparse matrices(稀疏矩阵)sparse representation(稀疏表示)spatial database(空间数据库)spatial reasoning 空间推理statistical analysis(统计分析)statistical model 统计模型string matching(串匹配)structural risk minimization (结构风险最小化) structured data 结构化数据subgraph matching 子图匹配subspace clustering(子空间聚类)supervised learning( 有support vector machine 支持向量机support vector machines(支持向量机)system dynamics(系统动力学)tag recommendation(标签推荐)taxonmy induction 感应规范temporal logic 时态逻辑temporal reasoning 时序推理text analysis(文本分析)text anaylsis 文本分析text classification (文本分类)text data(文本数据)text mining technique(文本挖掘技术)text mining 文本挖掘text mining(文本挖掘)text summarization(文本摘要)thesaurus alignment 同义对齐time frequency analysis(时频分析)time series analysis( 时time series data(时间序列数据)time series data(时间序列数据)time series(时间序列)topic model(主题模型)topic modeling(主题模型)transfer learning 迁移学习triple store 三元组存储uncertainty reasoning 不精确推理undirected graph(无向图)unified modeling language 统一建模语言unsupervisedupper bound(上界)user behavior(用户行为)user generated content(用户生成内容)utility mining(效用挖掘)visual analytics(可视化分析)visual content(视觉内容)visual representation(视觉表征)visualisation(可视化)visualization technique(可视化技术) visualization tool(可视化工具)web 2.0(网络2.0)web forum(web 论坛)web mining(网络挖掘)web of data 数据网web ontology lanuage 网络本体语言web pages(web 页面)web resource 网络资源web science 万维科学web search (网络检索)web usage mining(web 使用挖掘)wireless networks 无线网络world knowledge 世界知识world wide web 万维网world wide web(万维网)xml database 可扩展标志语言数据库附录 2 Data Mining 知识图谱(共包含二级节点15 个,三级节点93 个)间序列分析)监督学习)领域 二级分类 三级分类。
谈谈数据项目中的Datamapping(数据映射)

谈谈数据项目中的Datamapping(数据映射)概述企业数据正变得越来越分散和庞大。
与此同时,对企业来说,利用数据并将其转化为可操作的见解,变得比以往任何时候都更加重要。
然而,如今的企业从不同的数据点收集信息,它们可能并不总是使用同一种语言。
数据映射对于许多数据处理的成功至关重要。
数据映射中的一个错误可能会波及整个组织,导致重复的错误,并最终导致不准确的分析。
几乎每个企业都会在某个时候在系统之间移动数据。
不同的系统以不同的方式存储相似的数据。
因此,为了移动和合并数据进行分析或其他任务,需要一个数据地图来确保数据准确地到达目的地。
对于像数据集成、数据迁移、数据仓库自动化、数据同步、自动数据提取或其他数据管理项目这样的过程,数据映射的质量将决定要分析的数据的质量。
数据映射过程用于集成所有不同的数据源并理解它们。
一什么是数据映射数据映射是从一个或多个源文件中提取数据字段,并将它们与目标文件中相关的目标字段进行匹配的过程。
数据映射还通过提取、转换和将数据加载到目标系统来帮助强化数据质量。
任何数据处理(包括ETL)的初始步骤都是数据映射。
企业可以使用映射数据产生相关的见解,以提高业务效率。
在数据映射过程中,源数据被定向到目标数据库。
目标数据库可以是关系数据库或CSV文档——这取决于用例。
在大多数情况下,公司使用数据映射模板来匹配从一个数据库系统到另一个数据库系统的字段。
下面是一个数据映射模板示例,以阐明如何从excel源进行映射。
在下图中,Excel源中的“Name”、“Email”和“Phone”字段被映射到Delimited文件中的相关字段,这是我们的目标。
源到目标映射集成任务的复杂性各不相同。
复杂程度取决于数据层次结构以及源和目标数据结构之间的差异。
无论是内部部署还是云计算,每个业务应用程序都使用元数据来解释构成数据和语义规则的数据字段和属性。
这些规则控制数据在应用程序或存储库中的存储方式。
目标是确保从源到目的的无缝传输过程,而不丢失任何数据。
机器学习与数据挖掘笔试面试题

Why do we combine multiple trees? What is Random Forest? Why would you prefer it to SVM? Logistic regression: Link to Logistic regression Here's a nice tutorial What is logistic regression? How do we train a logistic regression model? How do we interpret its coefficients? Support Vector Machines A tutorial on SVM can be found and What is the maximal margin classifier? How this margin can be achieved and why is it beneficial? How do we train SVM? What about hard SVM and soft SVM? What is a kernel? Explain the Kernel trick Which kernels do you know? How to choose a kernel? Neural Networks Here's a link to on Coursera What is an Artificial Neural Network? How to train an ANN? What is back propagation? How does a neural network with three layers (one input layer, one inner layer and one output layer) compare to a logistic regression? What is deep learning? What is CNN (Convolution Neural Network) or RNN (Recurrent Neural Network)? Other models: What other models do you know? How can we use Naive Bayes classifier for categorical features? What if some features are numerical? Tradeoffs between different types of classification models. How to choose the best one? Compare logistic regression with decision trees and neural networks. and What is Regularization? Which problem does Regularization try to solve? Ans. used to address the overfitting problem, it penalizes your loss function by adding a multiple of an L1 (LASSO) or an L2 (Ridge) norm of your weights vector w (it is the vector of the learned parameters in your linear regression). What does it mean (practically) for a design matrix to be "ill-conditioned"? When might you want to use ridge regression instead of traditional linear regression? What is the difference between the L1 and L2 regularization? Why (geometrically) does LASSO produce solutions with zero-valued coefficients (as opposed to ridge)? and What is the purpose of dimensionality reduction and why do we need it? Are dimensionality reduction techniques supervised or not? Are all of them are (un)supervised? What ways of reducing dimensionality do you know? Is feature selection a dimensionality reduction technique? What is the difference between feature selection and feature extraction? Is it beneficial to perform dimensionality reduction before fitting an SVM? Why or why not? and Why do you need to use cluster analysis? Give examples of some cluster analysis methods? Differentiate between partitioning method and hierarchical methods. Explain K-Means and its objective? How do you select K for K-Means?
Google开源激光SLAM算法论文原文

As-built floor plans are useful for a variety of applications. Manual surveys to collect this data for building management tasks typically combine computed-aided design (CAD) with laser tape measures. These methods are slow and, by employing human preconceptions of buildings as collections of straight lines, do not always accurately describe the true nature of the space. Using SLAM, it is possible to swiftly and accurately survey buildings of sizes and complexities that would take orders of magnitude longer to survey manually.
1All authors are at Google.
loop closure detection. Some methods focus on improving on the computational cost by matching on extracted features from the laser scans [4]. Other approaches for loop closure detection include histogram-based matching [6], feature detection in scan data,and using machine learning [7].
FileMapping析疑(文件映射适合使用的几种情况)
FileMapping析疑(文件映射适合使用的几种情况)最初接触File Mapping是为了能够方便地处理一个几百兆的大文件,当时查了些资料大概了解了一下就匆匆动手了,因为知其然而不知其所以然,在使用过程中遇到了不少问题,今天在这里就是想把这些历史遗留问题解决掉。
问题一、Mapping有“映射”之意,那么在该语境中形成映射关系的双方是谁,也就是从哪里映射到哪里呢?要回答这个问题,我们必须要对虚拟内存有所了解。
现在操作系统中,大多都使用虚拟内存技术来对内存进行管理。
通过虚拟内存,操作系统给予了每个进程一个统一的地址空间。
在32位操作系统中,该地址空间的大小达到 2^32个,也就是4G了。
从一个进程的角度看来,这4G的地址空间是自己独享的,也就是说,如果操作系统允许的话,我可以访问这4G地址空间中的任何一个。
当然,操作系统是不可能让一个进程随心所欲地使用这些地址的。
下面,我们来看看这些地址具体是怎样分配的:上面这个图大家应该都很熟悉,它是Linux中进程的内存映象。
我们可以看到,在4G的地址空间中,我们先从下往上看, 0~0x08047ffff(大概128M左右)是系统保留的,不能使用。
read-only segment和read/write segment用以存放系统加载器从可执行文件中载入的代码段以及数据段等内容。
运行时堆大家应该都比较清楚,是动态分配内存的地方,我们通过malloc和free等函数动态在堆中分配和释放内存,堆的大小是往上增长的,最大可达到0x3FFFFFFF 处。
好,到这里我们在从上往下看,0xc0000000以上是核心虚拟内存,专门为操作系统核心的数据结构以及代码预留的,一般用户进程无权使用。
然后就到了栈区了,这里是系统保存跟函数操作有关的数据,如局部变量,函数参数等内容。
与堆不一样,栈是从上往下增长的,其栈顶通过寄存器esp指出。
那么被堆和栈夹着的区域是干什么的呢?原来,那是用来放动态共享库的。
希尔伯特曲线 空间索引
希尔伯特曲线空间索引希尔伯特曲线是一种用于空间索引的曲线。
它是由德国数学家David Hilbert在20世纪初提出的,并被广泛应用于计算机科学领域。
希尔伯特曲线具有压缩和空间局部性等优点,适合用于多维空间中的数据索引和查询。
希尔伯特曲线是一条连续的曲线,被用于将多维空间的坐标映射到一维空间中。
这种映射方式使得相邻的数据在一维空间中的位置尽可能接近,从而提高了数据的局部性。
希尔伯特曲线的构建是通过重复应用一种特定的模式来完成的。
具体来说,希尔伯特曲线是通过将二维平面中的点映射到一维空间中的一条曲线上。
在构造过程中,将平面分成四个等分,并按照特定的顺序连接这四个小块,形成一条分形曲线。
然后,再将每个小块按照同样的方式划分,重复上述过程,直到达到所需的精度。
通过这种方式,平面中的点可以被映射到曲线上,并保持它们在曲线中的相对邻近性。
希尔伯特曲线的具体构造方式可以通过迭代算法来实现。
在每一次迭代中,需要将平面分成四个等分,并根据特定的连接顺序将这四个小块连接起来。
通常,这种连接顺序可以由一个二进制编码来表示,其中每一位表示用于连接的小块的位置。
一旦构建完成了希尔伯特曲线,就可以将多维空间中的数据点映射到曲线上。
这种映射方式可以用于索引和查询多维空间中的数据。
例如,在二维空间中,可以将每个数据点的坐标映射到希尔伯特曲线上,并使用曲线上的位置来代表该数据点。
这样,相邻的数据点在曲线上也会相互靠近,从而提高查询效率。
希尔伯特曲线在计算机科学领域有广泛的应用。
一方面,它被用于提高空间数据的存储和查询效率。
例如,在地理信息系统中,可以使用希尔伯特曲线对地理空间数据进行索引,从而快速地查询特定区域内的数据。
另一方面,希尔伯特曲线也可以用于数据压缩和图像处理等领域。
通过将二维空间中的数据点映射到一维空间中,可以减少数据的维度,并提高处理效率。
总而言之,希尔伯特曲线是一种用于空间索引的有效工具。
它能够将多维空间中的数据点映射到一维空间中的曲线上,并保持它们在曲线上的相邻性。
计算机编程算法常用英语术语
计算机编程算法常用英语术语
导语:算法是指解题方案的准确而完整的描述,是一系列解决问题的清晰指令,算法代表着用系统的方法描述解决问题的策略机制。
下面是YJBYS小编收集整理的有关计算机算法的英语词汇,欢迎参考!
Median and Selection 中位数
Generating Permutations 排列生成
Generating Subsets 子集生成
Generating Partitions 划分生成
Generating Graphs 图的生成
Data Structures 基本数据结构
Dictionaries 字典
Priority Queues 堆
Graph Data Structures 图
Set Data Structures 集合
Kd-Trees 线段树
Numerical Problems 数值问题
Solving Linear Equations 线性方程组
Bandwidth Reduction 带宽压缩
Matrix Multiplication 矩阵乘法
Determinants and Permanents 行列式
Constrained and Unconstrained Optimization 最值问题
Linear Programming 线性规划
Random Number Generation 随机数生成
Factoring and Primality Testing 因子分解/质数判定
Arbitrary Precision Arithmetic 高精度计算。
MXM工具包:一种用于特征选择、交叉验证和贝叶斯网络的R包说明书
A very brief guide to using MXMMichail Tsagris,Vincenzo Lagani,Ioannis Tsamardinos1IntroductionMXM is an R package which contains functions for feature selection,cross-validation and Bayesian Networks.The main functionalities focus on feature selection for different types of data.We highlight the option for parallel computing and the fact that some of the functions have been either partially or fully implemented in C++.As for the other ones,we always try to make them faster.2Feature selection related functionsMXM offers many feature selection algorithms,namely MMPC,SES,MMMB,FBED,forward and backward regression.The target set of variables to be selected,ideally what we want to discover, is called Markov Blanket and it consists of the parents,children and parents of children(spouses) of the variable of interest assuming a Bayesian Network for all variables.MMPC stands for Max-Min Parents and Children.The idea is to use the Max-Min heuristic when choosing variables to put in the selected variables set and proceed in this way.Parents and Children comes from the fact that the algorithm will identify the parents and children of the variable of interest assuming a Bayesian Network.What it will not recover is the spouses of the children of the variable of interest.For more information the reader is addressed to[23].MMMB(Max-Min Markov Blanket)extends the MMPC to discovering the spouses of the variable of interest[19].SES(Statistically Equivalent Signatures)on the other hand extends MMPC to discovering statistically equivalent sets of the selected variables[18,9].Forward and Backward selection are the two classical procedures.The functionalities or the flexibility offered by all these algorithms is their ability to handle many types of dependent variables,such as continuous,survival,categorical(ordinal,nominal, binary),longitudinal.Let us now see all of them one by one.The relevant functions are1.MMPC and SES.SES uses MMPC to return multiple statistically equivalent sets of vari-ables.MMPC returns only one set of variables.In all cases,the log-likelihood ratio test is used to assess the significance of a variable.These algorithms accept categorical only, continuous only or mixed data in the predictor variables side.2.wald.mmpc and wald.ses.SES uses MMPC using the Wald test.These two algorithmsaccept continuous predictor variables only.3.perm.mmpc and perm.ses.SES uses MMPC where the p-value is obtained using per-mutations.Similarly to the Wald versions,these two algorithms accept continuous predictor variables only.4.ma.mmpc and ma.ses.MMPC and SES for multiple datasets measuring the same variables(dependent and predictors).5.MMPC.temporal and SES.temporal.Both of these algorithms are the usual SES andMMPC modified for correlated data,such as clustered or longitudinal.The predictor vari-ables can only be continuous.6.fbed.reg.The FBED feature selection method[2].The log-likelihood ratio test or the eBIC(BIC is a special case)can be used.7.fbed.glmm.reg.FBED with generalised linear mixed models for repeated measures orclustered data.8.fbed.ge.reg.FBED with GEE for repeated measures or clustered data.9.ebic.bsreg.Backward selection method using the eBIC.10.fs.reg.Forward regression method for all types of predictor variables and for most of theavailable tests below.11.glm.fsreg Forward regression method for logistic and Poisson regression in specific.Theuser can call this directly if he knows his data.12.lm.fsreg.Forward regression method for normal linear regression.The user can call thisdirectly if he knows his data.13.bic.fsreg.Forward regression using BIC only to add a new variable.No statistical test isperformed.14.bic.glm.fsreg.The same as before but for linear,logistic and Poisson regression(GLMs).15.bs.reg.Backward regression method for all types of predictor variables and for most of theavailable tests below.16.glm.bsreg.Backward regression method for linear,logistic and Poisson regression(GLMs).17.iamb.The IAMB algorithm[20]which stands for Incremental Association Markov Blanket.The algorithm performs a forward regression at first,followed by a backward regression offering two options.Either the usual backward regression is performed or a faster variation, but perhaps less correct variation.In the usual backward regression,at every step the least significant variable is removed.In the IAMB original version all non significant variables are removed at every step.18.mmmb.This algorithm works for continuous or categorical data only.After applying theMMPC algorithm one can go to the selected variables and perform MMPC on each of them.A list with the available options for this argument is given below.Make sure you include the test name within””when you supply it.Most of these tests come in their Wald and perm (permutation based)versions.In their Wald or perm versions,they may have slightly different acronyms,for example waldBinary or WaldOrdinal denote the logistic and ordinal regression respectively.1.testIndFisher.This is a standard test of independence when both the target and the setof predictor variables are continuous(continuous-continuous).2.testIndSpearman.This is a non-parametric alternative to testIndFisher test[6].3.testIndReg.In the case of target-predictors being continuous-mixed or continuous-categorical,the suggested test is via the standard linear regression.If the robust option is selected,M estimators[11]are used.If the target variable consists of proportions or percentages(within the(0,1)interval),the logit transformation is applied beforehand.4.testIndRQ.Another robust alternative to testIndReg for the case of continuous-mixed(or continuous-continuous)variables is the testIndRQ.If the target variable consists of proportions or percentages(within the(0,1)interval),the logit transformation is applied beforehand.5.testIndBeta.When the target is proportion(or percentage,i.e.,between0and1,notinclusive)the user can fit a regression model assuming a beta distribution[5].The predictor variables can be either continuous,categorical or mixed.6.testIndPois.When the target is discrete,and in specific count data,the default test isvia the Poisson regression.The predictor variables can be either continuous,categorical or mixed.7.testIndNB.As an alternative to the Poisson regression,we have included the Negativebinomial regression to capture cases of overdispersion[8].The predictor variables can be either continuous,categorical or mixed.8.testIndZIP.When the number of zeros is more than expected under a Poisson model,thezero inflated poisson regression is to be employed[10].The predictor variables can be either continuous,categorical or mixed.9.testIndLogistic.When the target is categorical with only two outcomes,success or failurefor example,then a binary logistic regression is to be used.Whether regression or classifi-cation is the task of interest,this method is applicable.The advantage of this over a linear or quadratic discriminant analysis is that it allows for categorical predictor variables as well and for mixed types of predictors.10.testIndMultinom.If the target has more than two outcomes,but it is of nominal type(political party,nationality,preferred basketball team),there is no ordering of the outcomes,multinomial logistic regression will be employed.Again,this regression is suitable for clas-sification purposes as well and it to allows for categorical predictor variables.The predictor variables can be either continuous,categorical or mixed.11.testIndOrdinal.This is a special case of multinomial regression,in which case the outcomeshave an ordering,such as not satisfied,neutral,satisfied.The appropriate method is ordinal logistic regression.The predictor variables can be either continuous,categorical or mixed.12.testIndTobit(Tobit regression for left censored data).Suppose you have measurements forwhich values below some value were not recorded.These are left censored values and by using a normal distribution we can by pass this difficulty.The predictor variables can be either continuous,categorical or mixed.13.testIndBinom.When the target variable is a matrix of two columns,where the first one isthe number of successes and the second one is the number of trials,binomial regression is to be used.The predictor variables can be either continuous,categorical or mixed.14.gSquare.If all variables,both the target and predictors are categorical the default test isthe G2test of independence.An alternative to the gSquare test is the testIndLogistic.With the latter,depending on the nature of the target,binary,un-ordered multinomial or ordered multinomial the appropriate regression model is fitted.The predictor variables can be either continuous,categorical or mixed.15.censIndCR.For the case of time-to-event data,a Cox regression model[4]is employed.Thepredictor variables can be either continuous,categorical or mixed.16.censIndWR.A second model for the case of time-to-event data,a Weibull regression modelis employed[14,13].Unlike the semi-parametric Cox model,the Weibull model is fully parametric.The predictor variables can be either continuous,categorical or mixed.17.censIndER.A third model for the case of time-to-event data,an exponential regressionmodel is employed.The predictor variables can be either continuous,categorical or mixed.This is a special case of the Weibull model.18.testIndIGreg.When you have non negative data,i.e.the target variable takes positivevalues(including0),a suggested regression is based on the the inverse Gaussian distribution.The link function is not the inverse of the square root as expected,but the logarithm.This is to ensure that the fitted values will be always be non negative.An alternative model is the Weibull regression(censIndWR).The predictor variables can be either continuous, categorical or mixed.19.testIndGamma(Gamma regression).Gamma distribution is designed for strictly positivedata(greater than zero).It is used in reliability analysis,as an alternative to the Weibull regression.This test however does not accept censored data,just the usual numeric data.The predictor variables can be either continuous,categorical or mixed.20.testIndNormLog(Gaussian regression with a log link).Gaussian regression using the loglink(instead of the identity)allows non negative data to be handled naturally.Unlike the gamma or the inverse gaussian regression zeros are allowed.The predictor variables can be either continuous,categorical or mixed.21.testIndClogit.When the data come from a case-control study,the suitable test is via con-ditional logistic regression[7].The predictor variables can be either continuous,categorical or mixed.22.testIndMVReg.In the case of multivariate continuous target,the suggested test is viaa multivariate linear regression.The target variable can be compositional data as well[1].These are positive data,whose vectors sum to1.They can sum to any constant,as long as it the same,but for convenience reasons we assume that they are normalised to sum to1.In this case the additive log-ratio transformation(multivariate logit transformation)is applied beforehand.The predictor variables can be either continuous,categorical or mixed.23.testIndGLMMReg.In the case of a longitudinal or clustered target(continuous,propor-tions within0and1(not inclusive)),the suggested test is via a(generalised)linear mixed model[12].The predictor variables can only be continuous.This test is only applicable in SES.temporal and MMPC.temporal.24.testIndGLMMPois.In the case of a longitudinal or clustered target(counts),the suggestedtest is via a(generalised)linear mixed model[12].The predictor variables can only be continuous.This test is only applicable in SES.temporal and MMPC.temporal.25.testIndGLMMLogistic.In the case of a longitudinal or clustered target(binary),thesuggested test is via a(generalised)linear mixed model[12].The predictor variables can only be continuous.This test is only applicable in SES.temporal and MMPC.temporal.To avoid any mistakes or wrongly selected test by the algorithms you are advised to select the test you want to use.All of these tests can be used with SES and MMPC,forward and backward regression methods.MMMB accepts only testIndFisher,testIndSpearman and gSquare.The reason for this is that MMMB was designed for variables(dependent and predictors)of the same type.For more info the user should see the help page of each function.2.1A more detailed look at some arguments of the feature selection algorithmsSES,MMPC,MMMB,forward and backward regression offer the option for robust tests(the argument robust).This is currently supported for the case of Pearson correlation coefficient and linear regression at the moment.We plan to extend this option to binary logistic and Poisson regression as well.These algorithms have an argument user test.In the case that the user wants to use his own test,for example,mytest,he can supply it in this argument as is,without””. For all previously mentioned regression based conditional independence tests,the argument works as test=”testIndFisher”.In the case of the user test it works as user test=mytest.The max kargument must always be at least1for SES,MMPC and MMMB,otherwise it is a simple filtering of the variables.The argument ncores offers the option for parallel implementation of the first step of the algorithms.The filtering step,where the significance of each predictor is assessed.If you have a few thousands of variables,maybe this option will do no significant improvement.But, if you have more and a”difficult”regression test,such as quantile regression(testIndRQ),then with4cores this could reduce the computational time of the first step up to nearly50%.For the Poisson,logistic and normal linear regression we have included C++codes to speed up this process,without the use of parallel.The FBED(Forward Backward Early Dropping)is a variant of the Forward selection is per-formed in the first phase followed by the usual backward regression.In some,the variation is that every non significant variable is dropped until no mre significant variables are found or there is no variable left.The forward and backward regression methods have a few different arguments.For example stopping which can be either”BIC”or”adjrsq”,with the latter being used only in the linear regression case.Every time a variable is significant it is added in the selected variables set.But, it may be the case,that it is actually not necessary and for this reason we also calculate the BIC of the relevant model at each step.If the difference BIC is less than the tol(argument)threshold value the variable does not enter the set and the algorithm stops.The forward and backward regression methods can proceed via the BIC as well.At every step of the algorithm,the BIC of the relevant model is calculated and if the BIC of the model including a candidate variable is reduced by more that the tol(argument)threshold value that variable is added.Otherwise the variable is not included and the algorithm stops.2.2Other relevant functionsOnce SES or MMPC are finished,the user might want to see the model produced.For this reason the functions ses.model and mmpc.model can be used.If the user wants to get some summarised results with MMPC for many combinations of max k and treshold values he can use the mmpc.path function.Ridge regression(ridge.reg and ridge.cv)have been implemented. Note that ridge regression is currently offered only for linear regression with continuous predictor variables.As for some miscellaneous,we have implemented the zero inflated Poisson and beta regression models,should the user want to use them.2.3Cross-validationcv.ses and cv.mmpc perform a K-fold cross validation for most of the aforementioned regression models.There are many metric functions to be used,appropriate for each case.The folds can be generated in a stratified fashion when the dependent variable is categorical.3NetworksCurrently three algorithms for constructing Bayesian Networks(or their skeleton)are offered,plus modifications.MMHC(Max-Min Hill-Climbing)[23],(mmhc.skel)which constructs the skeleton of the Bayesian Network(BN).This has the option of running SES[18]instead.MMHC(Max-Min Hill-Climbing)[23],(local.mmhc.skel)which constructs the skeleton around a selected node.It identifies the Parents and Children of that node and then finds their Parents and Children.MMPC followed by the PC rules.This is the command mmpc.or.PC algorithm[15](pc.skel for which the orientation rules(pc.or)have been implemented as well.Both of these algorithms accept continuous only,categorical data only or a mix of continuous,multinomial and ordinal.The skeleton of the PC algorithm has the option for permutation based conditional independence tests[21].The functions ci.mm and ci.fast perform a symmetric test with mixed data(continuous, ordinal and binary data)[17].This is employed by the PC algorithm as well.Bootstrap of the PC algorithm to estimate the confidence of the edges(pc.skel.boot).PC skeleton with repeated measures(glmm.pc.skel).This uses the symetric test proposed by[17]with generalised linear models.Skeleton of a network with continuous data using forward selection.The command work does a similar to MMHC task.It goes to every variable and instead applying the MMPC algorithm it applies the forward selection regression.All data must be continuous,since the Pearson correlation is used.The algorithm is fast,since the forward regression with the Pearson correlation is very fast.We also have utility functions,such as1.rdag and rdag2.Data simulation assuming a BN[3].2.findDescendants and findAncestors.Descendants and ancestors of a node(variable)ina given Bayesian Network.3.dag2eg.Transforming a DAG into an essential(mixed)graph,its class of equivalent DAGs.4.equivdags.Checking whether two DAGs are equivalent.5.is.dag.In fact this checks whether cycles are present by trying to topologically sort theedges.BNs do not allow for cycles.6.mb.The Markov Blanket of a node(variable)given a Bayesian Network.7.nei.The neighbours of a node(variable)given an undirected graph.8.undir.path.All paths between two nodes in an undirected graph.9.transitiveClosure.The transitive closure of an adjacency matrix,with and without arrow-heads.10.bn.skel.utils.Estimation of false discovery rate[22],plus AUC and ROC curves based onthe p-values.11.bn.skel.utils2.Estimation of the confidence of the edges[16],plus AUC and ROC curvesbased on the confidences.12.plotnetwork.Interactive plot of a graph.4AcknowledgmentsThe research leading to these results has received funding from the European Research Coun-cil under the European Union’s Seventh Framework Programme(FP/2007-2013)/ERC Grant Agreement n.617393.References[1]John Aitchison.The statistical analysis of compositional data.Chapman and Hall London,1986.[2]Giorgos Borboudakis and Ioannis Tsamardinos.Forward-Backward Selection with Early Drop-ping,2017.[3]Diego Colombo and Marloes H Maathuis.Order-independent constraint-based causal structurelearning.Journal of Machine Learning Research,15(1):3741–3782,2014.[4]David Henry Cox.Regression Models and Life-Tables.Journal of the Royal Statistical Society,34(2):187–220,1972.[5]Silvia Ferrari and Francisco Cribari-Neto.Beta regression for modelling rates and proportions.Journal of Applied Statistics,31(7):799–815,2004.[6]Edgar C Fieller and Egon S Pearson.Tests for rank correlation coefficients:II.Biometrika,48:29–40,1961.[7]Mitchell H Gail,Jay H Lubin,and Lawrence V Rubinstein.Likelihood calculations for matchedcase-control studies and survival studies with tied death times.Biometrika,68(3):703–707, 1981.[8]Joseph M Hilbe.Negative binomial regression.Cambridge University Press,2011.[9]Vincenzo Lagani,Giorgos Athineou,Alessio Farcomeni,Michail Tsagris,and IoannisTsamardinos.Feature Selection with the R Package MXM:Discovering Statistically-Equivalent Feature Subsets.Journal of Statistical Software,80(7),2017.[10]Diane Lambert.Zero-inflated Poisson regression,with an application to defects in manufac-turing.Technometrics,34(1):1–14,1992.[11]RARD Maronna,Douglas Martin,and Victor Yohai.Robust statistics.John Wiley&Sons,Chichester.ISBN,2006.[12]Jose Pinheiro and Douglas Bates.Mixed-effects models in S and S-PLUS.Springer Science&Business Media,2006.[13]FW Scholz.Maximum likelihood estimation for type I censored Weibull data including co-variates,1996.[14]Richard L Smith.Weibull regression models for reliability data.Reliability Engineering&System Safety,34(1):55–76,1991.[15]Peter Spirtes,Clark Glymour,and Richard Scheines.Causation,Prediction,and Search.TheMIT Press,second edi edition,12001.[16]Sofia Triantafillou,Ioannis Tsamardinos,and Anna Roumpelaki.Learning neighborhoods ofhigh confidence in constraint-based causal discovery.In European Workshop on Probabilistic Graphical Models,pages487–502.Springer,2014.[17]Michail Tsagris,Giorgos Borboudakis,Vincenzo Lagani,and Ioannis Tsamardinos.Constraint-based Causal Discovery with Mixed Data.In The2017ACM SIGKDD Work-shop on Causal Discovery,14/8/2017,Halifax,Nova Scotia,Canada,2017.[18]I.Tsamardinos,gani,and D.Pappas.Discovering multiple,equivalent biomarker sig-natures.In In Proceedings of the7th conference of the Hellenic Society for Computational Biology&Bioinformatics,Heraklion,Crete,Greece,2012.[19]Ioannis Tsamardinos,Constantin F Aliferis,and Alexander Statnikov.Time and sampleefficient discovery of Markov blankets and direct causal relations.In Proceedings of the ninth ACM SIGKDD international conference on Knowledge discovery and data mining,pages673–678.ACM,2003.[20]Ioannis Tsamardinos,Constantin F Aliferis,Alexander R Statnikov,and Er Statnikov.Al-gorithms for Large Scale Markov Blanket Discovery.In FLAIRS conference,volume2,pages 376–380,2003.[21]Ioannis Tsamardinos and Giorgos Borboudakis.Permutation testing improves Bayesian net-work learning.In ECML PKDD’10Proceedings of the2010European conference on Machine learning and knowledge discovery in databases,pages322–337.Springer-Verlag,2010.[22]Ioannis Tsamardinos and Laura E Brown.Bounding the False Discovery Rate in LocalBayesian Network Learning.In AAAI,pages1100–1105,2008.[23]Ioannis Tsamardinos,Laura E.Brown,and Constantin F.Aliferis.The Max-Min Hill-ClimbingBayesian Network Structure Learning Algorithm.Machine Learning,65(1):31–78,2006.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Mapping Functions and Data Redistribution for Parallel FilesFlorin Isaila Walter F.TichyDepartment of Computer ScienceUniversity of Karlsruhe,GermanyE-mail:florin,tichy@a.deAbstractA parallelfile may be physically stored on several inde-pendent disks and logically partitioned by several proces-sors.This paper presents general algorithms for mapping between two arbitrary distributions of a parallelfile.Eachof the two distributions may be physical or logical.The algorithms are optimized for multidimensional array parti-tions.We motivate our approach and present potential uti-lizations.We compare and contrast with related work.The paper also presents a study case,the employment of map-ping functions and redistribution algorithms in a parallel file system.1IntroductionThe discrepancy between processor and memory speed on one side,and disks,on the other side,has been identi-fied as a major drawback for applications with intensive I/O activity.For addressing this problem,some parallelfile sys-tems[5,6,4,3,13,2]and libraries[15,11]have employed mechanisms such as striping afile on several independent disks and allowing parallelfile access.Another main problems in parallel I/O is efficiently handling byte granularity,non-contiguous I/O.For in-stance,parallel scientific applications often access thefiles non-contiguously or their contiguous accesses translates into non-contiguous disk accesses[12].MPI-IO[11]and Vesta[3]allow setting linear views on non-contiguousfile data,whereas Galley Parallel File System[13]offers the user a nested strided interface.Parallel I/O access characterization studies[12,1,16, 17]have found the poor match between I/O access pat-terns of applications and physical layout of data on disks as a large source of I/O usage inefficiency.First,a poor match can cause fragmentation of data on the disks of the I/O nodes and complex index computations of accesses are needed.Second,the fragmentation of data results in send-ing lots of small messages over the network instead of a few large ones.Message aggregation is possible,but the costs for gathering and scattering are not negligible.Third, the contention of related processes at I/O nodes can lead to overload and can hinder the parallelism.Fourth,poor spa-cial locality of data on the disks of the I/O nodes translates into disk access other than sequential.Fifth,a poor match also increases the probability of false sharing within thefile blocks.The studies have also found that the most used data struc-tures of parallel scientific applications are multidimensional arrays[12].The arrays are typically stored on parallel disks and partitioned between processors.Therefore the appli-cation would benefit from mapping functions between pro-cessors and disks,that efficiently exploit the regularity of multidimensional array partitions.Motivated by these considerations,we have designed a parallelfile model,that allows arbitrary logical and physi-cal partitions,while being optimized for multidimensional array distributions.Thefile can be physically partitioned into subfiles,written on parallel disks.Additionally,parallel applications may set logical views on thefile using the same model.The same data representation is used for both logi-cal and physical ing this parallelfile model, we implemented general mapping functions between linear files and subfiles or views and vice versa.We also designed a general data redistribution algorithm,used for conversion between arbitrary distributions.In this paper we will present the parallelfile model,along with mapping functions and a data redistribution algorithm used to convert between two partitions of the samefile.For more examples and details please see the extended version of this paper[8].Section2compares and contrasts our ap-proach with related work.In section3,we motivate the choice of our design and present some potential applica-tions.Section4presents the mathematical representation used forfile partitions.Section5introduces the parallelfile model.Section6describes mapping functions between two partitions of the samefile.Section7outlines an algorithm used for data redistribution of two partitions of afile.Sec-tion8presents a case study,a particular implementation ofmapping functions and redistribution algorithm in a parallel file system.Section9contains conclusions and our future plans.2Related workAt the core of ourfile model is a representation for regu-lar data distributions called PITF ALLS(Processor Indexed Tagged F Amily of Line Segments)[14].PITFALLS were used in the PARADIGM compiler for automatic generation of efficient array redistribution routines at University of Illi-nois.In order to be able to express a larger number of ac-cess types,we have extended the PITFALLS representation to nested PITFALLS,as we show in section4.Based on PITFALLS representation,they present a redistribution al-gorithm that is specific for multidimensional arrays.They compute the intersection of distributions independently on each array dimension.The multidimensional intersection result is the union of these intersections.The independent computation is possible,because it is performed for two dis-tributions of the same array.For instance,this will not gen-erally work if the array has to be redistributed to another array with different sizes of at least one dimension.Our re-distribution algorithm uses their intersection algorithm for one dimension and generalizes the redistribution,such that array redistribution is efficiently performed and the redistri-bution can be performed between arbitrary patterns.The nCube parallel I/O system[5]builds mapping func-tions between processor’s views of afile and disks using address bit permutations.The mappings are performed for multidimensional array distributions on disks or at the pro-cessors.The major deficiency of this approach is that all array sizes must be powers of two.Our mapping functions are general and therefore,a superset of those from nCube. The Vesta Parallel File System[3]allowsfile physical partitioning into subfiles and logical partitions into views. The partitioning scheme,and therefore the mappings,are restricted only to data sets that can be partitioned into two dimensional rectangular arrays.Our data representation and mappings allows efficient physical and logical partitioning of n dimensional arrays,not necessary partitioned into rect-angular blocks.Additionally,arbitrary physical and logical distributions are possible.MPI-IO[11]file model,like ours,allowsfiles to be log-ically partitioned into arbitrary views.The view is mapped on linearfiles of severalfile systems.Each particularfile system uses its particular scheme for physically storing the file on disks.Our approach encompasses logical and physi-cal distribution in a single model,allowing for relating and optimizing them.Thefile in Galley Parallel File System[13]is a linear addressable sequence of bytes,which consists of subfiles, structured as a collection of forks.Non-contiguous I/O is supported by a nested strided operation user interface.Our file model is unitary with respect to physical and logical partitioning.Non-contiguous I/O is realized by setting a linear view on the data set and accessing it contiguously. This has the advantage that,once the view is set,the set of indices corresponding to the mappings are computed and all subsequent access operation will use them.Therefore, a view operation can be eventually amortized over several accesses.Panda[15]is a high-level library that allows regular dis-tributions both on disks and in memory and implements disk and memory array redistributions on thefly.Ourfile model is thought as a low-level implementation that can also ex-press irregular distributions and can be used by a high-level implementation as Panda.3Motivation and utilizationAs shown in section1,large sources of parallel I/O system inefficiencies are the poor match between logical and physical distribution of afile,as well as inefficient non-contiguous I/O handling.In the related work section, we have outlined several approaches for mapping the log-ical partition of afile to its physical partition that address these drawbacks.Our main goal is to introduce a parallel file model that generalizes ideas presented in earlier work, along with useful procedures for mapping between two dif-ferent instances of the model.As we show in detail in section4,a nested PITFALLS represents a subset of afile’s data as a set of non-contiguous segments of thefile.This linear addressable subset is called subfile,if it is physically stored on a disk,and view if it is a logical entity.There three main reasons for choosing nested PITFALLS as the core of our data representation:They can compactly represent regular distributions of data.Therefore,support for any High-Performance Fortran-style[9]BLOCK and CYCLIC based data distribution on disk and in memory is a straightforward application of our approach.Their regularity is used for building efficient mapping functions and redistribution algorithm.They can represent arbitrary distributions of data.For instance,MPI data types[10]can be build on top of them. Mapping functions,described in detail in section6,are used to map between afile offset and an element(subfile or view)of a partition of thefile,and vice-versa.There-fore,mapping function compositions may be used for map-ping between two elements of two different partitions,as we show in subsection6.2.However,by converting between two different distribu-tions,it would be inefficient to map each byte from one dis-tribution to another.Instead of that,we use a redistribution algorithm,described in section7,that maps between parti-Figure1.FALLS example:tions non-contiguous segments of bytes,instead of singular bytes.The mapping functions and data redistribution algorithm most important benefits are:They can be used in parallelfile systems or libraries. Section8presents a case of applying them in a parallelfile system.MPI-IO libraryfile model[11]can be also imple-mented using ourfile model and mappings.They can be used for any combination of redistri-butions:disk-disk,disk-memory,memory-disk,memory-memory.They allow for relating the logical and physical par-titions of the samefile and therefore,to improve perfor-mance.For instance,using the redistribution algorithm it is possible to implement disk redistribution on thefly,like in Panda[15],in order to better suit the layout to a certain access pattern.Multidimensional array redistribution is efficiently handled,by using the regularity of the array partition.A high utilization of network bandwidth can be ob-tained for non-contiguous access.The end of section7 shows the computation of the mappings of a non-contiguous pattern to a linear buffer and subsection8outlines how the data representation is used for scatter and gather operations in a parallelfile system.The scatter and gather procedures can be also used to implement MPI’s pack and unpack op-erations.Data redistribution allows also to better partition the data,in order to alleviate disk contention and improve the load balance of several disks,and,therefore,to increase the efficiency of programs performing parallel disk access.4Data representationOur data representation is an extension of PITFALLS (Processor Indexed Tagged FAmily of Line Segments),in-troduced in[14].In this subsection,we will present the el-ements of PITFALLS,necessary for understanding this pa-per.Line segment.A line segment(LS)is a pair of numbers which describes a contiguous portion of afile starting at offset and ending at.FAmily of Line Segments(FALLS).A family of line segments(F ALLS)is a tuple representing a set of equally spaced,equally sized line segments.The left index of thefirst LS is,the right index of thefirstInner FALLS (0,0,2,2)Figure2.Nested FALLS exampleLS is and the distance between every2LS’s is called a stride and is denoted by.A FALLS’s block is defined as the bytes contained between and.A line segment can be represented as the FALLS.Figure1 shows an example of.Nested FALLS.A nested F ALLS is a tuplerepresenting a FALLS together with a set of in-ner nested FALLS.The inner FALLS’s are located be-tween and and are relative to the left index of the outer FALLS.In constructing a nested FALLS it is advisable to start from the outer FALLS to inner FALLS.Figure2shows an example of a nested FALLS. The outer FALLS are pictured with thick line.A nested FALLS can be represented as a tree.Each of the node of the tree contains a FALLS and its children are the inner FALLS of.PITFALLS and nested PITFALLS.For regular distri-butions,a set of nested FALLS can be shortly expressed us-ing the nested PITF ALLS representation[14,7].However, for the sake of simplicity,in this paper we will use only the nested FALLS representation,because each nested PIT-FALLS is just a compact representation of a set of nested FALLS.Size.A nested FALLS is a set of indices which represent a subset of afile.The size of a nested FALLS,denoted by,is the number of bytes in the subset defined by. The size of a set of nested FALLS is the sum of sizes of all its elements.For instance,the size of the nested FALLS fromfigure2is4.5Thefile modelThis section presents ourfile model,which can be ap-plied both for partitioning thefile into subfiles,which are physically written to disks,and views,which are logical en-tities.Both subfiles and views are linear addressable and are described by sets of nested FALLS.For the rest of this section the discussion about subfiles applies also for views. Afile in our model is a linear addressable sequence of bytes,consisting of a displacement and a partitioning pat-tern.The displacement is an absolute byte position rel-ative to the beginning of thefile.The partitioning pat-tern consists of the union of sets of nested FALLS,each of which defines a subfile.non-overlapping regions of thefile.Additionally,must de-scribe a contiguous region.The partitioning pattern mapsPartitioning Partitioning Partitioning Partitioning Partitioning File displacementSubfile 0Subfile 1Subfile 2defined by FALLS (0,1,6,1)defined by FALLS (2,3,6,1)defined by FALLS (4,5,6,1)Figure 3.File partitioning exampleeach byte of the file on a pair subfile-position within subfile,and is applied repeatedly throughout the linear space of the file,starting at the displacement.We define the size of thepartitioning pattern ,denoted by,to be the sum of the sizes of all of its nested FALLS.Figure 3illustrates a file,having displacement ,physically partitioned into 3subfiles,defined by FALLS ,,and.The size of the partitioning pattern is 6.Thearrows represent mappings from the file’s linear space to the subfile linear space.6Mapping functionsGiven one partition of a file ,this section shows how to build mapping functions MAP and MAP be-tween a file offset and the offset of one of the partition el-ements .For instance,if the partition element is described by the set of nested FALLS and the partition size is ,as in the figure 3,the byte at file offset 10maps on the byte with subfile offset 2(MAP )and vice-versa(MAP ).Using the mapping func-tion and its reverse,we then show how to map between two different partitions of the same file.6.1Mapping a file on a subfileMAPcomputes the mapping of a position from the linear space of the file on the linear space of the subfile defined by ,where belongs to the partitioning pattern ,starting at displacement .The MAP is the sum of the map value of the beginning of the current partitioning pattern and the map of the position within the partitioning pattern.MAP()1:divMAP-AUXmodMAP-AUX computes the mapping from a file to a partition element for a set of nested FALLS .Line 1of MAP-AUX identifies the nested FALLS of onto which maps.The returned map value (line 2)is the sum of total size of previous FALLS and the mapping onto ,relative to ,the beginning of .MAP-AUX()1:2:returnMAP-AUXmodMAP-AUX maps position of the file onto the lin-ear space described by the nested FALLS .The returned value is the sum of the sizes of the previous blocks of and the mapping on the set of inner FALLS,relative to the current block begin.MAP-AUX ()1:if then 2:return div mod3:else 4:return divMAP-AUXmodFor instance,for the partition element described by,where the partition size is and displace-ment is in the figure 3(b),the file-partition element map-ping is computed by the function:Notice that computes the mapping of x on the partition element defined by ,only if x belongs to one of the line segments of .For instance,in figure 3,the byte at file offset 5doesn’t map on partition element 0.However,it is possible to slightly modify MAP-AUX ,to compute the mapping of either the next or the previous byte of the file,which directly maps on a given partition element.The idea is to detect when lies outside any block of and to update to the position of the end of the current stride (next byte mapping)or of the end of the previous block(previous byte mapping),before executing the body of MAP-AUX .For figure 3,the previous map of byte at file offset on partition element 0is the byte at offset 1and the next map is the byte at offset 2.The reverse mapping,MAP ,is described in an extended version of this paper[8].6.2Mapping between different partitionsGiven two partition elements defined by and and be-longing to two different partitions of the same file,we com-pute the direct mapping of between and as MAP MAP .For instance,in the figure 4(b),the mapping of the byte at offset 4from partition element on the par-tition element is MAP MAP .Because MAP represents the inverse of MAP ,for the same we have:As a consequence,given a physical partition into subfile and a logical partition into views,described by the same pa-rameters,each view maps exactly on a subfile.Therefore,every contiguous access of the view translates into a con-tiguous access of the subfile.This represents the optimal physical distribution for a given logical distribution.7Redistribution algorithmGiven two partitions of the samefile,the goal is to re-distribute thefile data from one partition to the other.In this section we will show how the intersection is performed between two elements of two differentfile partitions.The intersection algorithm computes the set of nested FALLS that can be used to represent data common to two sets of nested FALLS,belonging to two givenfile partitions.The intersection result is then projected on the linear space of each of the two intersected partition elements,as described at the end of the section.FALLS intersection algorithm.Our nested FALLS in-tersection algorithm uses the FALLS intersection algorithm from[14],INTERSECT-FALLS().INTERSECT-FALLS efficiently computes the set of nested FALLS,rep-resenting the indices of data common to both and. In order to make the computation efficient,the algorithm uses the period of the intersection result(the lowest com-mon multiplier of the strides of and)and consid-ers just pairs of line segments of and that intersect. For example,infigure4,INTERSECT-FALLS((0,7,16,2), (0,3,8,4))=(0,3,16,2).Cutting a FALLS.The procedure CUT-FALLS(,,) computes the set of FALLS which results from cutting a FALLS between an inferior limit and superior limit .The resulting FALLS are computed relative to.We use this procedure in the nested FALLS intersection al-gorithm.For example,cutting the FALLSfromfigure1between and results in set,computed rela-tive to.Intersection of sets of nested FALLS.We are ready now to describe the algorithm for intersecting sets of nested FALLS and,belonging to the partitioning patterns and,starting at displacements and.The algorithm assumes,without loss of generality,that the nested FALLS trees have the same height.If they don’t,the height of the shorter tree can be transformed by adding outer FALLS.In the PREPROCESS phase of INTERSECT,and ,and implicitly and,are extended over a size equal to the lowest common multiplier of the sizes of and.Subsequently,they are aligned at the maximum of the two displacements,by cutting and extending the parti-tioning pattern starting at the lowest displacement.After preprocessing,the two partitioning patterns have the same displacements and the same sizes and can be intersected. INTERSECT()1:PREPROCESS2:returnINTERSECT-AUX(INTERSECT-AUX computes the intersection between two sets of nested FALLS and,by recursively travers-ing the FALLS trees(line10),after intersecting the FALLS0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 310 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31(a) Logical and physical partitioning(file form)the view defined by(c)Projection of onthe subfile defined by(b)Projection ofFigure4.Nested FALLS intersection algo-rithmpairwise(line8).INTERSECT-AUX considersfirst all possible pairs such that and.The FALLS is cut between the left and right index of inter-section of outer FALLS of and(line4),and. The indices and are computed relative to outer FALLS of,and are received as parameters of recursive call from line10.The same discussion applies to(line5).CUT-FALLS is used for assuring the property of inner FALLS being relative to left index of outer FALLS.The FALLS re-sulting from cutting and,are subsequently pairwise intersected(line8).INTERSECT-AUX()1:2:for all do3:for all do4:CUT-FALLS()5:CUT-FALLS()6:for all do7:for all do8:INTERSECT-FALLS()9:for all do10:INTERSECT-AUX(modmod modmod)11:returnFor instance,figure4shows the intersection ofand,belonging to partitioning patterns of size 32.The intersection result is.Intersection Projection.The previous algorithm com-putes the intersection of the two sets of FALLS and .Consequently,is a subset of both and.The data indices of,and are represented infile linear space.An intersection projection is a set of indices that represent the data common to the intersected partition ele-ments in the linear space of one of them.It is computed by using the mapping function from subsection6.1.Please see [8]for details.For instance,in the example fromfigure4,PROJ(c)and PROJ(d).8Case study:a parallelfile systemThis section shows the usage of the mapping functions and the intersection algorithm in the data operations of Clusterfile parallelfile system.We will present only parts of Clusterfile relevant to the discussion.For a detailed descrip-tion,please see[7].Because the write and read are reverse symmetrical,we will present only the write operation.We will accompany our description by an example shown in figure5,for the view and subfile presented infigure4. 8.1Write implementationClusterfile divides the cluster nodes in two sets,which may or may not overlap:compute nodes and I/O nodes.A file may be physically partitioned into subfiles and logically partitioned into views by using thefile model described in section5.The subfiles are stored on the disks of the I/O nodes.The views on afile may be set by the applications running on the compute nodes.Scatter and gather.Suppose we are given a set on nested FALLS,a left and a right limit,and,respec-tively.We have implemented two procedures,used by data operations,for copying data between the non-contiguous regions defined by and a contiguous buffer(or a subfile).GATHER copies the non-contiguous data,as defined by the nested FALLS between and,from buffer from to a contiguous buffer(or to a subfile).For instance,infigure5(b),the com-pute node gathers the data between andfrom a view to the buffer,using the set of FALLS.The copy in the reverse direction can be performed by SCATTER.The imple-mentation consists of the recursive traversal of the set of trees representation of the nested FALLS from.Copying operations take place at the leafs of the tree.View set.When a compute node sets a view,described by,on an openfile,with displacement and parti-tioning pattern,the intersection between and each of the subfiles is computed.The projection of the intersec-tion on,,is computed and stored at compute node.The projection of the intersection on,, is computed and sent to I/O node of the corresponding sub-file.The example fromfigure5(b)shows the projections and,for a view and one subfile. The write operation.Suppose that a compute node has opened afile defined by and and has set a view on it.As previously shown,the compute node stores,and the I/O node of subfile stores ,for all.We will show next thesteps(a)Compute node maps and on the subfileFile(b)Communication between compute node and I/O nodeCOMPUTE NODEI/O NODEFigure5.Write operation in Clusterfileinvolved in writing a contiguous portion of the view,be-tween and,from a buffer to thefile(see also thefigure5and the following two pseudocode fragments). For each subfile described by(1)and intersecting (2),the compute node computes the mapping of andon the subfile,and,respectively(3and4)and then sends them to the I/O server of subfile(5).Subse-quently,if is contiguous between and, is sent directly to the I/O server(7).Otherwise the non-contiguous regions of are gathered in the buffer(9) and sent to the I/O node(10).1:for all do2:if then3:4:5:Send of subfile to the I/O server of6:if is contiguous between and then 7:Send bytes between and to I/O server of subfile defined by8:else9:GATHER()10:Send to to I/O server of subfile defined byThe I/O server receives a write request to a subfile de-Si-Lo.dis.c12293444346b5142032191r31001455c10969407614b5065685900r33304018c1136241422309b518170319375r318015136c1222650180793b503549671358r296056475 Table1.Write time breakdown at compute node.fined by between and(1)and the data to be writ-ten in buffer(2).If is contiguous,is written contiguously to the subfile(4).Otherwise the data is scattered from to thefile(6).1:Receive and from compute node2:Receive the data in3:if is contiguous between and then 4:Write to subfile between and5:else6:SCATTER()8.2Experimental results.The goal of our experiments is to measure the overhead associated with the phases of data operations that involve the mapping functions and the redistribution algorithm and to investigate how it relates to the total time in a particular implementation.We performed our experiments on a clus-ter of16Pentium III800MHz,having256kB L2cache and 512MB RAM,interconnected by Myrinet.Each machine is equipped with IDE disks.They were all running LINUX kernels.Eight nodes were used:four compute nodes and four I/O nodes.We wrote a benchmark that writes and reads a two dimensional matrix to and from afile in Clusterfile. We repeated the experiment for different sizes of the ma-trix:,,,. All the matrix sizes are in bytes.For each size,we phys-ically partitioned thefile into four subfiles in three ways: square blocks(),blocks of columns()and blocks of rows ().Each subfile was written to one I/O node.For each size and each physical partition,we logically partitioned thefile among four processors in blocks of rows.We measured the timings for different phases,when the I/O nodes are writ-ing to their buffer caches and to their disks.Table1showsSi-Lo.ze dis.c87r1278r45512r3593b261512r2717c1096r10622r11942048r41684b49192048r41179Table2.Scatter time at I/O nodethe average results for one compute node,and table2the average results for one I/O node.All measurements were repeated ten times and the mean computed.The standard deviation for all measurements was within4%of the mean value.Given a physical and a logical partitioning,represents the time to perform the intersection and to compute the pro-jections.It doesn’t vary significantly with the matrix size. As expected,is small for the same partitions,and larger when the partitions don’t match.It is worth noting that has to be paid only at view setting and can be amortized over several accesses.The time to map the access interval extremities of the view on the subfile(lines3and4from thefirst pseudocode) is very small.It is when a view and a subfile perfectly overlap.The gather time(line9from thefirst pseudocode frag-ment)consists of copying operations,by using the indices precomputed at view setting.As a consequence it increases with the size of the matrix,because there is more data to copy.For a given matrix size,is largest when the parti-tions match poorly,because repartitioning results in many small pieces of data which are assembled in a buffer.It is for an optimal matching,for all sizes,because no copying is needed,before sending the data over the network.For a given size,the times and contain the interval between sending thefirst write request at one I/O node and receiving the last acknowledgment,as measured at the compute node.Because I/O servers are running in parallel,and are limited by the slowest I/O server. The scatter times and contain the times to write a non-contiguous buffer to buffer cache,and to disk,respec-tively.We didn’t optimize the contiguous write case to write directly from the network card to buffer cache.Therefore, we perform an additional copy.Consequently,thefigures for all three pairs of distributions are close for big messages.。
